#Datatag
Explore tagged Tumblr posts
Text
Masterpost of informational posts
All posts are written for everyone, including those with no prior computer science education. If you know how to write an email and have used a computer at least sparingly, you are qualified for understanding these posts. :)
What is a DDoS
What are the types of malware
Vulnerabilities and Exploits (old and somewhat outdated)
Example of how malware can enter your computer
What are botnets and sinkholes
How does passwords work
Guide for getting a safer password
Here are various malware-related posts you may find interesting:
Stuxnet
The North Korean bank heist
5 vintage famous malware
Trickbot the Trickster malware (old and not up to date)
jRAT the spy and controller (old and not up to date)
Evil malware
New to Linux? Here's a quick guide for using the terminal:
Part 1: Introduction
Part 2: Commands
Part 3: Flags
Part 4: Shortcuts
If you have any questions, request for a topic I should write about, or if there is something in these posts that you don't understand, please send me a message/ask and I'll try my best to help you. :)

- unichrome
Bonus: RGB terminal
#datatag#masterpost#malware#cybersecurity#infosec#security#hacking#linux#information#informative#computer science
424 notes
·
View notes
Text
What is data labeling?
Data labeling is a fundamental step in the machine learning pipeline, enabling algorithms to learn and make accurate predictions. EnFuse Solutions, a leading data labeling company, provides high-quality services with expert annotators who ensure accurate, consistent labeling for training robust and reliable machine learning and AI models. Contact today to learn more!
#DataLabeling#DataLabelingServices#DataAnnotation#DataTagging#LabeledData#SupervisedLearningData#AITrainingData#MachineLearningDataPrep#AnnotationSolutions#DataLabelingServicesIndia#DataLabelingCompanies#EnFuseSolutions#EnFuseSolutionsIndia
0 notes
Text
What is data labeling and annotation?
Data labeling and annotation involve tagging datasets like images, text, or audio with informative labels to train machine learning models. EnFuse Solutions India specializes in providing these services, enabling algorithms to understand input patterns, facilitating accurate predictions, and enhancing the performance of AI applications across various industries.
#DataLabeling#DataAnnotation#AnnotationServices#DataTagging#AITrainingData#AnnotationExperts#DataLabelingServicesIndia#BestDataLabelingCompanies#EnFuseDataLabeling#EnFuseSolutions#EnFuseSolutionsIndia
0 notes
Text
AI Tagging In Social Media: Revolutionizing Content Management And Trend Identification
In this article, we delve into the transformative role of AI in social media content tagging, with a special emphasis on leveraging AI-powered image and text recognition to categorize content and uncover trends. Embrace the power of AI in social media content management and trend identification by forging a partnership with EnFuse Solutions today.
#TaggingSolutions#TagManagementSolutions#TaggingServices#DataTagging#AIMLServices#EnFuseSolutions#EnFuseSolutionsIndia
0 notes
Text
So here's problem.
As I've shown before, each project has a file of magical "script tags" used to pull from the dictionaries that store much of a game project's data- species, moves, possibly even the scripts used when you talk to characters. It's wonderful. The Mondo "engine" has a base scripttags class that contains very basic script tags that almost any project will use, like "name" and "type". Users are to create a scripttag file extending the base scripttags to add any new tags they might need. The project-specific scripttags can't be made into a singleton because of course it doesn't exist in the base Mondo project (of course the user could singletonize it themselves regardless, but I want to make it kind of Just Work as-is), so certain workarounds have to be employed. For example, the species files…
A base "species-handler" file is provided in the base project. This extends the base scripttags so it can check against them for things like getting base stats…
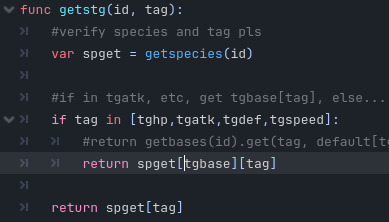
In the user's project, you make a species.gd file containing all your species data. This can of course extend the project-specific scripttags file; this scripttags file extends the base scripttags file, so you have access to all tags.
Finally in the user's project, a project-specific species-handler is created to add any extra rules that might need to be followed; for example, an additional base stat, or special checks. This extends the base species-handler. It loads the project-specific species file and sets a "species" variable to point to the species file's species dictionary so it can be easily accessed. (These variables are declared in the base handler so its functions can still "see" them.) Now this file doesn't have direct access to the project-defined species tags, but it does have… the loaded file the species dictionary came from, which extends the project-specific script tags. So just name the variable that's loaded into something handy (here it's "sp") and get tags with sp.whatevertag. Beautiful!

Now consider the following: battle scene. As explained before this is a chain of extends using battle script files available in the base project. The user can define their own battle scenes and insert their own file full of defined functions and data in between battle-utils and their own created scenes. But there's a problem- battle-basis, from which all battle scenes ultimately extend, is a base project file. And you know what base project files can't do?… That's right, extend project-specific script tags.
Actually, having typed all this out I've already figured out the solution, just give battle scenes access to species-handler. But let's discuss how that's to be done.
So the way data-handler works is that, after checking the specified project folder and replacing it with default-project if it's not found (that's so I can just upload the code without my own folders and it works right out of the box), it checks for certain predefined files and loads them up:
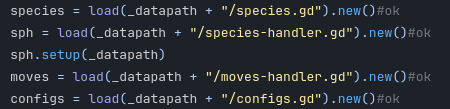
(These should probably each get their own error checking and load the default if not found; it won't have any useable data but that way it at least has a default stuff.) Data-handler is a global singleton, so anything can access it from anywhere. So like if you're talking to an NPC in the field and they're like, "oh your (species name) is so cool!" and you want it to get the same of the species instead of whatever nickname you've given it, you call data.sph.getname(partymon[n].species_id) or the like. Voila. So everything has access to the species data and getter functions (as well as moves, eventually abilities, etc). And you remember what we just got done explaining? Species-handler has access to species, which extends the project-specific datatags. So, all the battlescene needs to do is, on creation, grab a pointer to species from data, and it can use that to access the tags. Magical! Oh and it might as well grab a pointer to species-handler and move-handler and whatnot in the first place because it obviously is going to be using them a hell of a lot, might as well give them a bit of a shorter path.
Also, the way scripttags are handled right now is to give them a unique filename and class_name, so they can much more easily be slapped on an extends, so data-handler wouldn't be able to find it… could use a predefined file name but unique class names I guess. That would just give things like battle scenes a more direct access to them. Might be better to do that.
Also also this was all completely pointless because the dictionary setup is probably temporary and I should move over to using resources like a normal person.
Anyway, I've started working on what I talked about before, cleaning up the move-execution code and what to do with fainted mons, and have started considering what to do about project-specific battle code. Like, implementing special moves/attack/defense in a Pokemon clone, or changing up the damage calculation. I've come up with the idea of a battle-engine object, loaded by data-handler and instantiated by each battle scene either on creation or per-battle, that can communicate with and effect battle scenes. This object can hold variables for the user's unique battle field stuff, like field effects, and can hold the damage calculation functions. And since it's a unique file to the project, it can extend the project's own script tags. I like that, I think I'll do that.
... Which actually solves the above problem because battle-engine can and should have access to moves, species and scripttags, and is the main thing that will be using them! Ha ha.
0 notes
Photo

Say hello to the new crotch rocket. #zx9r #kawasakininja #900 #bestcolours #ninja #c1 #lowmiles #renthal #datatag #datatool #supersprox https://www.instagram.com/p/CAsrNc7npqq/?igshid=11r7chps16g7r
0 notes
Text
The biggest heist that almost was
Let me tell you about the most insane bank heist that is going to sound like I'm just leaking the script for the next American hacking movie. The goal? Steal one billion USD. And it all began with an email and a printer, which as we all know is where problems usually start. Another weapon in this heist was... Weekends and time zones.
As usual, no prior computer science education needed.
What happened?
On the morning of February 5th 2016, a printer had stopped working in the central bank of Bangladesh (Bangladesh Bank). But it wasn't just any printer, it was the printer responsible for printing all the records of the multimillion transfers going in and out of the bank. When the poor employees finally won the printer battle and had it resume normal operation, they saw a very concerning account transfer in the records that was coming out. The bank had an USD account in the USA, at Federal Reserve Bank, with approximately 1 billlion Dollars in it, and the Federal Reserve Bank had received instructions to drain almost the entire amount. In the records that came out in the printer, the American bank had attempted to urgently message the Bangladesh bank regarding this transfer, but couldn't get through to them. This was because the hack had actually started the day before, Thursday 4th, at around 20:00 Bangladesh time, when the bank was closed. However, USA had just started their day, giving the American bank plenty of time to follow through with the instructions from the Bangladesh bank to drain their entire account while they were closed. And that wasn't the end of it, as weekends are from Friday to Saturday in Bangladesh, meaning that the Bangladesh bank headquarters in Dhaka wouldn't discover this withdrawal until Sunday morning. That's when they immediately tried to reach the American bank, which of course didn't work as over there it was Saturday evening, and the American weekend is from Saturday to Sunday, meaning that they wouldn't be reachable until Monday.
You see what I mean by the hackers using time zones and weekends, finding the perfect time for the American bank to execute their orders while Bangladesh discovers the withdrawal several days too late, and again several days too late for Americans to be reachable. But it didn't stop there with their timehacking.
The money had to go somewhere from the American bank, and it would be stupid to send it directly to the hackers own account without laundering the money first. So they had set up four different bank accounts in the Philippines, using fake names and credentials. Why the Philippines? Because the Lunar new year was on Monday the 8th, which is a holiday and holiday means no bank activities in either Bangladesh or the Philippines, buying the hackers even more time. As a final act, they messed with the printer responsible for printing transaction records, adding another few hours to their schedule. Moon and stars really aligned perfectly for this plan.
But how did they do it?
It all began one year prior, in January 2015, with an email sent to several employees at the Bangladesh Bank. The email seemingly contained a job application from a person who didn't actually exist, but who was very polite in his request for a position at the bank, with a link to his CV and cover letter. Naturally this link led to a document with a little surprise gift - malware. Since the heist happened, at least one of the recipients must have clicked the link, and successfully deployed a RAT - Remote Access Trojan, malware that lets you control a computer from the comfort of your own home, as well as a toolkit with various malware to move from computer to computer, avoiding discovery, and covering their tracks.
From there, the hackers slowly made their way through the bank offices network, one step at a time to avoid setting off alarms, looking for any computer that had control of the banks SWIFT setup. SWIFT lets banks transfer large amounts of money between themselves and other banks connected to SWIFT. And as soon as they found one of those computers, they stopped. They didn't need to hack SWIFT in the traditional sense of the word - since they operated in a bank computer, the SWIFT-software assumed they naturally had to be bank employees. However, one of the parts of the malware used in the heist was for manipulating the SWIFT system, as the hackers weren't physically there to press anything. Additionally, since they were laying dormant for the time to strike, they needed to keep an eye out for SWIFT updates that could detect any tampering with the system, and adapt accordingly.
Then they waited many months for the stars to align on February 4th, 2016.
There were 35 transfers made by the hackers from the American bank account, totaling almost 1 billion USD, but there were two of these tiny little seemingly insignificant details that prevented this from becoming the worlds largest bank heist in history. The hackers biggest enemy became this concept known as “words”.
The Philippine bank accounts were all located in the same RCBC Bank office on Jupiter Street in Manila. And this would be the hackers downfall, as USA had sanctions put on an Iranian cargo ship called Jupiter. Since the transactions went to a recipient that contained the word “Jupiter”, it created a security alert in the Federal Reserve Bank that the employees needed to investigate. When they saw what was going on, they managed to stop all but five of the initial 35 transactions, thus “only” roughly 100 million USD made it to the Philippines. The Bangladesh bank requested to reverse the transactions, but since the money was in the Philippines, they would need bureaucracy in form of a court order to reclaim the money, and we all know that's not a 5 minute project. It was when Bangladesh filed the court order in late February that the case became public (since court orders are public documents) and the news broke to the country.
Once in the RCBC bank accounts, the money arrived on Friday the 5th and was immediately moved again. First the 100 million was converted to local currency, and some of it was withdrawn in cash, while the rest was sent off to other hacker-controlled locations. And this is where the second tiny little detail cut off even more of the hackers precious payday. 20 million USD had been sent to Shalika Foundation, a charity organisation in Sri Lanka. But, once again the hackers worst enemy - words - decided to strike again. A typo was made in their transaction, sending the money to “Shalika Fundation”, and a bank employee who must have had their morning coffee spotted this typo and rejected the transfer and kept the funds frozen. This left the hackers with 80 million USD.
✨Now comes the money laundering!✨
There was a second reason for choosing the Philippines as deposit zone; gambling is legal and the casinos had no money laundering regulations imposed. The accomplices of the heist booked private rooms in two casinos located in Manila - Solaire and Midas - and proceeded to purchase tokens to gamble for with the stolen money. Since they played with a room consisting of their fellow accomplices, winning was not really much of a challenge. Then the tokens could be exchanged back to money that would now be clean. To avoid suspicion, they didn't gamble all of the money at once, but over the course of several weeks gambled away the dirty money to clean money.
Who was behind it?
It's normally difficult to pinpoint where the more sophisticated hacking groups come from. Oftentimes, they will leave false clues behind that points to another group so they will face more trouble instead of the group that did it. They may even place clues from several different groups, just to mess with the analysts. It's also quite common to simply “steal” a way of working from another group, or use a leaked/stolen tool from another group (criminals aren't safe from other criminals, especially not in this business) - there are new malware coming out all the time with code that is just a slight modification of a well-known malware actor that had their source code leaked or simply had hired the same programmer. Or they may leave no clues as to who was behind it. Attribution to the guilty part is usually the single most difficult mission in IT-security - often it's just pure guesswork with little to no solid evidence to back it up, if you're lucky there's circumstantial evidence.
This case was no different. The first clue came from the IP the bad guys used to connect to the Bangladesh bank from. It was located in Pyongyang, North Korea. But, as I mentioned, this is not a conclusive verdict, as the IP may simply be planted false evidence to throw the analysts off their track. After the heist, the hackers used a data-wiper to scrub as much of their malware off the bank systems, but they didn't succeed in deleting all of it, some of the tools were still present, including the wiper.
Due to the scale of this operation, it caught the attention of every single IT-security person and IT-security company worldwide, who all of course wanted to know who and how they did it. With the remaining malware, a joint effort was made, comparing malware code to other malware code for similarities. Some was found in Poland, after an analyst noted the similarities from another suspected North Korean hack. Some was found in another infamous North Korean hack targeting Sony Pictures. More and more signs pointed towards the same actor. Some were false leads, the hackers seemed to be wanting to implicate the Russians did it, but failed quite miserably at that, just sprinkling random Russian words into the malware and making it way too obvious it was a ruse.
You may not believe this, but the North Korean government has one of the most notorious hacking groups in the world, known as the Lazarus Group. Some of its more well-known adventures include an extremely data-destructive hack of Sony Pictures (as punishment for releasing “The Interview”), creation of the ransomware WannaCry which was used against many targets worldwide (including hospitals), and various attempts at gathering information from governments and government-affiliated corporations all over the world. And, of course, this heist.
Eventually, after months of collaboration all over the world, the final verdict fell on North Korea, and specifically one of their programmers. His name is Park Jin Hyok, and worked for Chosun Expo - a front company for the North Korean government, located in Dalian (China) who used the funds of the fake corporation gained from legitimate programming jobs from customers worldwide to create the malware and plan the heist with all of its expenses. Of course he wasn't the sole person involved in this project, but it's the only person we know was in it.
This particular heist had been meticulously planned for several years, and Park Jin Hyok had moved to Dalian, set up fake IDs and built a network of contacts there to avoid suspicion. However, he didn't manage to delete all of his online footprints, and became the number one suspect when his internet activities suddenly came from Pyongyang, North Korea.
Additionally, several Chinese business men - many associated with the casino industry in China's Macau territory - were also charged and arrested for assisting with setting up the gambling rooms and coordinating the money laundering process. One unknown Chinese business man managed to get away with 31 million USD of the 80 million that remained after the heist, and as you would expect, he was never to be seen again.
With the middlemen from China paid off, not much remained of the original 1 billion to North Korea. But the heist has fascinated the whole IT-security world nonetheless.
I remember when the news of this case dropped to the IT-security world, who all wanted to take part in the hunt. It was a very fun time, we were all sitting at the edge of our seats waiting for the next update. I hope it was at least somewhat exciting for you too to read about, and thank you for reading this long post! If you liked it, please consider reblogging as it motivates me to write more. You may also like malware stuff I've written about before, such as Stuxnet or just plain evil malware that is a threat to our daily lives.
As always my inbox is open if you have any questions.
94 notes
·
View notes
Text
New Post has been published on Superbike News
New Post has been published on http://superbike-news.co.uk/wordpress/jake-dixon-smashes-assen-records-to-claim-pole-from-mackenzie-by-0-004s/
Jake Dixon smashes Assen records to claim pole from Mackenzie by 0.004s!
Jake Dixon claimed pole position by just 0.004s in an intense battle for the top spot in Datatag Qualifying for the Bennetts British Superbike Championship at Assen this afternoon, edging out front row debutant Tarran Mackenzie and standings leader Leon Haslam.
A hectic Datatag Qualifying kicked off with Haslam setting the initial pace in Q1, setting the fastest time of the weekend ahead of Josh Brookes after the first flying laps, but Dixon was attacking and soon he had moved to the top with a time of 1m:35.716s.
Haslam held second ahead of Mackenzie and Tommy Bridewell who had pushed up the order after returning to action following his free practice crash this morning. Showdown contender Bradley Ray nudged his way into the top 18 to make the cut for Q2, but Danny Buchan ended the session in the gravel and will start 18th on the FS-3 Racing Kawasaki tomorrow as he was unable to take part in the second stage.
In Q2 the pace was electrifying with the top 16 riders lapping inside the existing lap record, however for Showdown contender Ray it wasn’t enough and he will start 16th on the grid for tomorrow’s opening race.
Peter Hickman was another of the Showdown contenders to miss out on Q3; he was pushed outside the top nine in the final moments as Honda Racing’s Jason O’Halloran moved into contention, but at the front Dixon was pushing hard.
The RAF Regular & Reserves Kawasaki set the benchmark in Q2 with the fastest ever Bennetts BSB lap of Assen with a time of 1m:35.579s to head off Haslam and Glenn Irwin on the Be Wiser Ducati.
Gino Rea had been impressing on the OMG Suzuki and a crash at turn 15 put the OMG Suzuki rider out of contention for Q3 as he starts from eleventh on the grid ahead of James Ellison and Michael Laverty for race one.
The top nine then returned to the track for one final time in Q3 and although the pace wasn’t as fast as the previous session it was Glenn Irwin who headed the times after the first flying laps. A lap later and Bridewell had surged ahead to prove he was back in contention despite his earlier huge crash.
Dixon though went to the top, but Mackenzie then displaced him at the top of the times, however Dixon wasn’t done and he had another lap to fight for the pole position which he did to move ahead by just 0.004s.
Haslam will complete the front row as he bids to extend his advantage tomorrow with Glenn Irwin heading row two ahead of Bridewell and Brookes. Tyco BMW’s Christian Iddon returned to Q3 and he will start seventh on the grid ahead of Honda Racing’s Dan Linfoot and O’Halloran.
Bennetts British Superbike Championship, Assen, Datatag Qualifying result:
Jake Dixon (RAF Regular & Reserves Kawasaki) 1m:35.639s
Tarran Mackenzie (McAMS Yamaha) +0.004s
Leon Haslam (JG Speedfit Kawasaki) +0.248s
Glenn Irwin (Be Wiser Ducati) +0.423s
Tommy Bridewell (Moto Rapido Ducati) +0.514s
Josh Brookes (McAMS Yamaha) +0.723s
Christian Iddon (Tyco BMW) +1.173s
Dan Linfoot (Honda Racing) +1.256s
Jason O’Halloran (Honda Racing) +1.580s
For more information visit www.britishsuperbike.com
Jake Dixon (RAF Regular & Reserves Kawasaki) Pole position “I haven’t been feeling the best so far this weekend; I started to feel a bit ill midweek and the team said it would pass, but hopefully tomorrow is a step towards feeling better again!
“We have worked hard on race distance during free practice and it was really great to do the fast laps in qualifying on the softer option tyre as it is nice to try and find the limit of what you have to offer.
“Overall I am happy with qualifying and the feeling we have for tomorrow. I have done my homework and so hopefully that will pay off in the races so we can try to close down Leon again.”
British Superbike
jQuery(document).ready(function($) if(typeof(gg_galleria_init) == "function") gg_galleria_show("#5bafb58f39398");gg_galleria_init("#5bafb58f39398");); Grid Girls Gallery by Grid Girls UK
jQuery(document).ready(function($) if(typeof(gg_galleria_init) == "function") gg_galleria_show("#5bafb58f508e8");gg_galleria_init("#5bafb58f508e8"););
0 notes
Text
Who are the leading players in the data annotation tools market?
Data annotation market is highly competitive, with a mix of established companies and innovative newcomers offering a variety of tools and services. Depending on your specific needs—whether it's image, video, or text annotation—companies like EnFuse Solutions can provide the right solutions to support your AI initiatives.
#DataAnnotation#DataAnnotationTools#DataLabeling#AnnotationServices#AIDataLabeling#MachineLearningData#TrainingData#ImageAnnotation#TextAnnotation#VideoAnnotation#DataTagging#AIModelTraining#AnnotationMarketLeaders#EnFuseSolutions#EnFuseSolutionsIndia
0 notes
Photo
Danooct1 has a video demonstrating this Pikachu worm that attempts to wipe your data. However he couldn't get the mass emailing of the malware to function; it's supposed to email itself to all your contacts.
So I looked into the anatomy of the Pikachu worm and found the email text it tries to send to your friends:

"Great friend!
Pikachu from Pokemon Theme have some friendly words to say. "
And the absolutely not suspicious attachment PikachuPokemon.exe

pikachu will now destroy your computer :3
15K notes
·
View notes
Text
What are the types of data annotation?
Choosing the right type of data annotation is essential for the success of any AI project. It not only improves the accuracy of machine learning models but also enhances the overall efficiency and reliability of the system. EnFuse Solutions stands out as the best data annotation service provider in India. Whether text, image, video, audio, or 3D data annotation, EnFuse Solutions delivers top-notch services to meet specific project needs.
#DataAnnotation#TypesOfDataAnnotation#DataLabeling#AIDataAnnotation#MLDataAnnotation#ImageAnnotation#TextAnnotation#VideoAnnotation#AudioAnnotation#SemanticAnnotation#BoundingBoxAnnotation#PolygonAnnotation#DataTagging#AnnotationForAI#AnnotationForML#TrainingDataAnnotation#DataAnnotationServices#AIAnnotationServices#DataAnnotationIndia#EnFuseAIAnnotation#EnFuseDataAnnotation#EnFuseSolutions
0 notes
Text
WE BUILD MORE THAN JUST WEBSITES, WE BUILD BRANDS.
Founded in 2013, DATATAG was borne out of the deepest convictions that mixing empathy, technology and a touch of creativity could greatly change the way a brand behaves and portrays itself. We combine these features mentioned above to ensure that we provide a better solution- approach to enable small and large brands to be able to understand as well as communicate efficiently with their large number of audience and provide it consultancy service in india as well.
#datatag#datatag web service#it consultant in delhi#digital marketing company#digital marketing services
0 notes
Text
Well I did it fellas, I hit the point where making things extend "scripttags" breaks a functionality. (':
So here's a menu. When made on the fly it defaults in position to the top left corner. We want to reposition it to above the textbox or something. Should be easy right?

But it's not! Scripttags at its base is a plain "Node", so it has no goddamn position attribute. And changing it to a Node2D breaks the 3D maps that have their scripts changed to extend scripttags, even though (or I guess because) the node itself is still shown as a Node3D or whatever in the scenetree.
So it's probably time to go back to having scripttags be an autoloaded global singleton and just use dt.whatevertagname (global singleton 'dt' being datatags... should maybe be renamed to scripttags/st idk). But I really like being able to throw around tag names without any additional qualifier like that, and also I'm a stubborn idiot. So, like I start considering alternatives.
The opbase objects used for the menu options are proper Node2Ds (or sprites or whatever it was), so they can be positioned, which of course is a core feature of the menu system and already used to, you know, make the menu look like that. So the point to position the menu at could be passed in to each menu option and they could all move themselves in unison to the right place based on that. Also it occurs to me that the only place the menus use scripttags is the battle option menus that need to eg display move types and names based on the ID. So I could just change menus to proper Node2Ds and have just the battle menu use dt.whatever, and leave the 3D map nodes that extend scripttags for their scripts to, uh, hopefully not need anything from Node3D. I might actually just do that.
0 notes
Text
Salice Levante Helmet
FREE SHIPPING WITH THIS ITEM
Description
Iconic Italian flag design
Aero helmet reduces resistance against wind
14 specially designed aeration slits guarantee excellent ventilation
Rear LED safety light with multiple settings
Removable hypoallergenic and breathable mesh bug liner (replacements available)
Datatag ICE label (In case of Emergency). Sunglasses
Removable Chin Strap
Graphics Link in with ITA Salice
Lightweight aero-mould design - 250g (52-58) 270g (56-62)
0 notes
Text
METAs LF RFID 嵌入式螺絲硬標籤 , METAs LF RFID 125 KHz Embedded Screw Hard Tags ( PXL80301 )
METAs LF RFID 嵌入式螺絲硬標籤 , METAs LF RFID 125 KHz Embedded Screw Hard Tags ( PXL80301 ) —- METAs RFID Team METAs LF RFID 嵌入式螺絲硬標籤 , METAs LF RFID 125 KHz Embedded Screw Hard Tags ( PXL80301 ) Superior RFID Applications 卓越的 RFID 應用 Encoding of workpiece carriers in path conveyors in industrial manufacturing 工業製造過程中路徑輸送機中��件載體的編碼 Product Spec 產品規格 Specification conditionsSpecification dataTag…

View On WordPress
0 notes
Text
How To Turn Off Tutorial In Minecraft 81
You can power the block by running redstone signal into it (through powered redstone dust or repeater/comparator pointed into it) or by powering the block directly with a lever or a button. How i turn off all intensive server activity halt on my minecraft server?

Minecraft 1.5 Lights that Turn on at Night and Off from www.youtube.com
How to turn off tutorial in minecraft. 2.5 how to get mammoths, smilodon and dodos. In minecraft, the beacon is an item in the game that allows you to create a beam of light in the sky, generate a light source (light level 15), and give a status effect to nearby players. Type %appdata% in the search bar on the left bottom corner.
About press copyright contact us creators. Finding the right folder [] There should be a way to turn these off.
2.2 how to breed dinosaurs. Save the file, launch your minecraft game, and enter a multiplayer server or single player world to check if you did it correctly. Turning on cheats through this menu does not affect other minecraft worlds that you have prevously created, just the world that you are creating now.
(starting in minecraft 1.13, use the /tag command to remove a tag from a player) /scoreboard players tag remove [datatag] to list the tags for a player (in minecraft 1.12 and older): It's a survival experience about staying alive in your own fantastic world that's also a creative space to build almost anything you can imagine! We know minecraft can be intimidating to newcomers so we've assembled this simple guide to get you started.
You can do it in the settings of the game , if you scroll you should find the button to disable them. The minecraft launcher includes audio cues to help players navigate the login and launch experience. Quick way to find it is by pushing these keys on your keyboard ctrl + f and typing tutorial in the search box.
Make sure you have your minecraft closed for this to work. To find the option file do as follows: This article focuses on singleplayer hardcore strategies, many, but not all, of which can apply to other.
0 notes