#Cybersecurity
Text
DDoS Attack Against AO3: Correcting Misinformation
Normally I don't make any posts like this, but I have an interest in cybersecurity and sadly I've seen people are being really ignorant about this recent DDoS attack against the site AO3 (Archive of Our Own), so I thought I'd remind people of a few things:
Anonymous Sudan appears to have no actual link to Sudan at all, or to any previous hacktivist groups that once operated there. This masquerade is probably based in anti-immigration and other racist sentiments, and utilizing those sentiments in other people to scare people and set up Muslims and Sudanese people as a target. This should be obvious from the language used in their note, but this was already known prior to this particular attack.
This so-called Anonymous Sudan has actually been very active recently—remember that they claimed to attack Reddit, Flickr, Riot Games, a huge number of Microsoft web portals like OneDrive and Outlook, etc. before AO3, so AO3 was totally a logical target for them since they've gone after smaller entities before. DDoS attacks like this are easy for any script kiddie to set up, so it's not weird that they'd go for a smaller target like this.
Honestly this group of posers probably just wants money, everybody. They sent AO3 a ransom note asking for Bitcoin (and just in case people don't know, do not pay a ransom if at all possible if this ever happens to you).
My advice to people who've noticed this attack is two-fold: calm down since this is part of a larger pattern that has literally resulted in basically no loss for the end-user of any of the sites, and... I don't really know a better way to put this, but don't believe everything you read. A religiously-motivated hate group wouldn't use terms like "LGBTQ+" and "smuts," and it's so blatantly obvious that the timing of every single one of these attacks is being used to smear Muslims and Sudanese people if you think about current events for like. One second. And if you look up Anonymous Sudan, you'll see their string of attacks and how all experts know that they have nothing to do with Sudan at all. Even AO3 itself told everybody that the group is lying about their motivations... though I think I'd go further than that personally because even their name itself is almost certainly a total sham.
To be clear: this post isn't targeted at anyone in particular. I've just seen a lot of people falling for this overall or not realizing this is part of a pattern, and I also wanted to remind everyone that this isn't anything to be concerned about. What is something to be concerned about is not doing research or thinking critically and then unwittingly spreading racist ideas.
25K notes
·
View notes
Text
NEW FROM ME: so i guess i hacked samsung?!
a short bug bounty write up on how i randomly stumbled onto samsung cloud infrastructure
(not an april fools bit)
5K notes
·
View notes
Text
Hey y'all, there's been a zero-day vulnerability found in WinRAR, so you gotta update it if you're on an older version (anything below 6.24/6.23). It doesn't auto update so you need to do it manually. It's been around for a few months and has been fixed, but if you don't update your shit then your computer will still be vulnerable.
please reblog this so that people learn about it or whatever (10/19/23)
10K notes
·
View notes
Text
August 2016: Australia’s national census night fails after authorities report the website is receiving a sophisticated DDOS attack that has taken it offline.
It was later revealed that the so called “attack” was actually just the entire population of Australia attempting to complete the census.
8K notes
·
View notes
Text
Hey everyone. Friendly reminder that if you get a pm such as this, DO NOT click ANY suspicious links. Or any links in general. These are bots made to steal your data, and do not have your best interests in mind. Instead, you should click „Mark as spam.“ to remove the message.
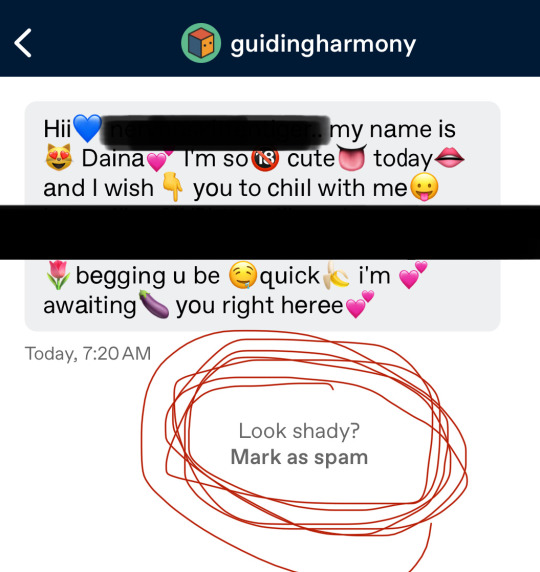
Again; NEVER CLICK THESE LINKS. Just mark as spam and move on with your day.
3K notes
·
View notes
Text

ㅇㅅㅇ (use firefox)
2K notes
·
View notes
Text

#cyberpunk#cybercore#cyberpunk 2077#cybersecurity#cyberpunk photomode#cyber y2k#cyberpunk art#cyberpunk v#cybernetics#cyberpunk aesthetic#cyberpunk oc
736 notes
·
View notes
Text




Hackers (1995)
#hackers#macintosh#cyber security#prank#funny pranks#school hacks#fire alarm#cyberpunk#cyberpunk movies#gifs#gifset#umbrella#cybersecurity#cyberspace#macos#mac os#retro computing#apple mac#hypercard
518 notes
·
View notes
Text

You other web hosts can't deny
That when a load time's more than an itty bitty wait
And a hacker's in your space
You get...
Well, pretty upset. That's not something to take lightly.
That's why you shouldn't settle for those other web hosts.
You need WordPress VIP: the world's most popular content management system, built with enterprise-grade security and reliability. 🤝
#baby got backends#wordpress vip#enterprise wordpress#wordpress#cms#content management#marketing#web security#cybersecurity
5K notes
·
View notes
Text
Spies are supposed to be good at keeping secrets, but soldiers in 8200 like to talk about their service. Technically, David said, he combed through data from a base in central Israel to determine where bombs should fall. But at the end of the day, he assured me, the military was really more of a networking opportunity—a surefire way to land a high-paying gig at Google or Facebook. As his time in the army neared an end, he turned his work surveilling the occupied Palestinian territories into a line on a corporate CV, toured high-tech companies in Central Tel Aviv, and was connected to cybersecurity CEOs over WhatsApp.
While some soldiers in 8200 spend their time monitoring Hezbollah cells in Lebanon or waging covert war against Iran, others are tasked with managing Israel’s high-tech military occupation of Palestine. The destructive effects of Israel’s surveillance regime in the West Bank and Gaza are well-documented, but veterans of intelligence units who surveilled Palestinians often describe their work as removed from the reality of occupation. David was just one of many veterans I spoke with who framed his service in the parlance of high-tech careerism: as another kind of DevOps, product management, or data analysis. These days, intelligence units are structured in the image of tech conglomerates, and tech conglomerates are contracted to do the work of intelligence units. From Israeli military bases to Silicon Valley corporate campuses, warfare has simply become a white-collar tech job.
263 notes
·
View notes
Link
“Despite endless warnings highlighting the dangers of the digital world, there is a growing acceptance that, in return for the speed and convenience of the internet, we must relinquish a little of our privacy. It’s a trade-off, trusting that the institutions we most rely on—banks, insurance companies, government agencies—will keep our personal details safe. Seldom, however, are we without a major hacking story.”
It's been 41 years since the movie "WarGames" introduced many to the concept of hacking. In our latest #longreads reading list, Chris Wheatley rounds up some sobering and fascinating pieces about cyberattacks (and those who undertake them). Read it here.
505 notes
·
View notes
Text
402 notes
·
View notes
Text
reminder not to do what i almost did just now and tell tumblr what your high school mascot is/was just because someone made a fun poll about it, because that's a SECURITY QUESTION ON A BUNCH OF YOUR PASSWORD-PROTECTED PLATFORMS
230 notes
·
View notes
Text
I remember attending those "girls in technology" programs and they just felt very alienating. You visited several places involving tech and they were all guys talking like you had no idea what anything is. No women in sight except receptionists/cleaners.
The program that intended me to join the tech industry just further hammered home that I don't belong there.
The best "girls in tech" was me working my way in by myself and gaining the self-esteem and confidence to not only not give a shit, but also thinking the men don't know shit more than I did, and are in most cases hired because they're men who feels entitled to a position in IT because they man and man logical.
I don't know how many incompetent men I've met in my career path that think they are a gift from the IT gods.
My tip for the girls/women reading this is gain the self-esteem enough to ignore what men are doing and wants us to be. Find your own path based on your skill. I can guarantee that an incompetent male will take many job positions but as your skill grow and as the men fail (often upwards) sooner or later the employer don't have any choice other than hiring you.
And then it's your time to shine. I almost immediately became the top malware analyst they had as I sharpened my skills every day while the men thought they did a good enough job because they were hired after all.
Then they'll ask you how you're so good at it, and that's worth the struggle you went through.
So don't give up on your dream blah blah basically ignore men, ignore their strategies for getting hired, you know what to do and you know how to get better. Find other women and encourage each other ok? You can do this! 💕
532 notes
·
View notes
Text
SCAM ALERT: Cryptocurrency related but can affect trans people buying HRT. I was probably 10 seconds away from having money stolen and I know what I'm doing. (Crypto Clipper)
Today I was helping a trans friend order some DIY HRT. A lot of DIY HRT places only accept cryptocurrency for security reasons. I am not looking to promote cryptocurrency or anything associated with it, but if you may be forced to use it for HRT or other reasons, you need to know this.
In general if you are forced to use crypto, you should use the cheapest coin your supplier will accept. If it is cheap, that means there is not a lot of activity on the chain and energy use will be less. I used one called Zcash as it was the cheapest one the site accepted but that's not really relevant.
I used an old coinbase account I had used for similar situations in the past. I was doing it on her PC. I got the instructions to pay on the HRT site, and I pasted the wallet address into Coinbase and just before I hit send I noticed the wallet address I had pasted didn't match the wallet address I had copied.
I looked it up and found this is from a form of malware called a Crypto Clipper, that detects when you have copied a crypto address, and makes you paste a different one so it can steal your money. I am lucky I noticed. To remedy it, I installed the free trial of Malwarebytes on her PC to remove malware, and completed the crypto transaction on my PC, and confirmed that the wallet address matched what the HRT site had given me.
I managed to avoid falling for it but it's such an easy thing to fall for, especially if you have avoided crypto thus far for extremely understandable reasons. Be careful out there! It could happen to anyone.
#trans#hrt#trans hrt#diy hrt#crypto#cryptocurrency#bitcoin#scam#scams#psa#important psa#important#virus#malware#cybersecurity
191 notes
·
View notes
Text


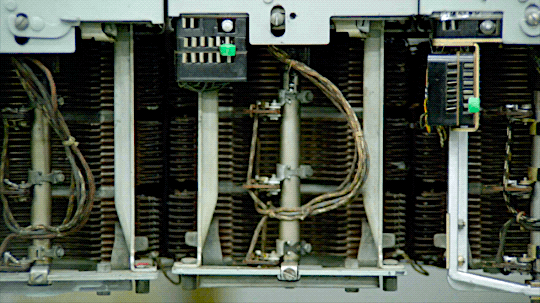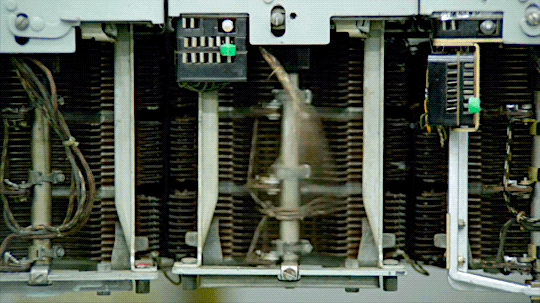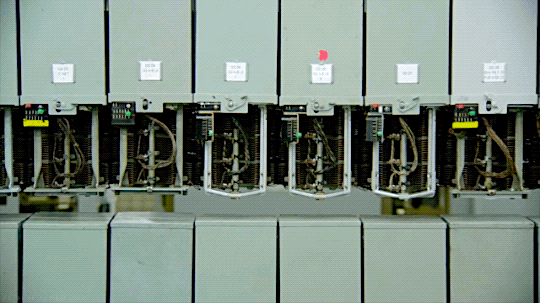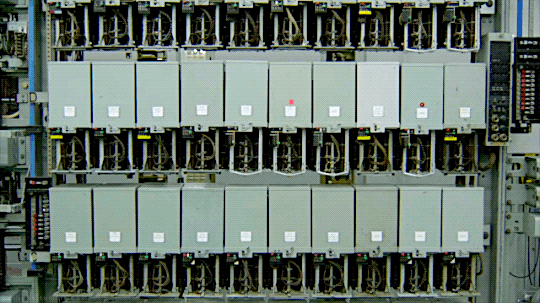

Underground: The Julian Assange Story (2012)
An old analog telephone exchange.
----
In the analog telephone exchange era, phone hacking techniques were often referred to as "phreaking."
Phreaking involved exploiting vulnerabilities in the telephone network to make free long-distance calls, manipulate phone systems, or access restricted information.
Phreakers used various methods, such as tone dialing, blue boxes, and red boxes, to bypass billing systems and gain unauthorized access to phone networks.
#cyberpunk aesthetic#electronics#vintage electronics#cyberpunk#cyberpunk movies#computer#hacking#hackers#cybersecurity#gifs#gifset#telephone#80s#eighties#vintage#nostalgia#nostalgic#aesthetic#analog#analogue
509 notes
·
View notes