#Download trend micro antivirus
Text
Download trend micro antivirus

Will Trend Micro™ remove malicious software? The entire Trend Micro™ anti-malware software program is absolutely free to all Online Banking users. Philanthropy Chinese Business Islamic Banking Agriculture Public Sector Education Healthcare Franchise Motor Dealership Tourismĭemos KYC / FICA Debit order + recipient switching Electronic Alerts The dti initiatives Business Hub eBucks Rewards for Business DocTrail™ CIPC Instant Accounting Solutions Instant Payroll Instant Cashflow Instant Invoicing SLOW 24/7 Business Desk FNB Business Fundaba nav» Marketplace Prepaid products Overdraft Loans Debtor Finance Leveraged Finance Private Equity Vumela Securities Based Lending Selective Invoice Discounting Asset Based Finance Alternative Energy Solutions Commercial Property Finance Fleet Servicesįoreign Exchange International Trade Structured Trade + Commodity Finance Business Global Account (CFC account) Save and Invest 3PIM (3rd Party Investment Manager) With nearly 30 years of Internet security leadership, industry experts recognize Trend Micro Security as delivering 100% protection against web threats.First Business Zero (R0 - R5 million p.a) Gold Business (R0 - R5 million p.a) Platinum Business (R5 million - R60 million p.a)īusiness Accounts Credit Cards Cash Solutions Merchant Services eWallet Pro Staffing Solutions ATM Solutions Ways to bank Fleet Services Guarantees
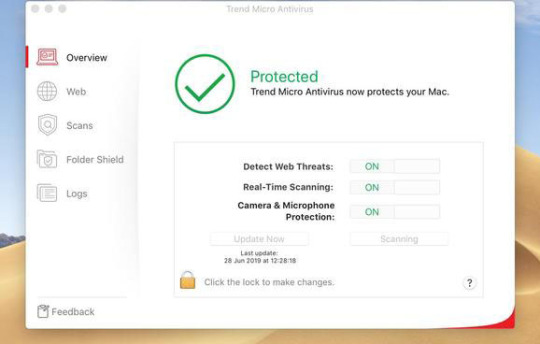
Privacy on social networks, including parental controls.
Advanced anti-ransomware technology so your files won't be held hostage.
Effective protection against new and rapidly evolving threats.
Protection for multiple devices across multiple operating systems.
Folder Shield can even protect cloud synced folders such as Dropbox, Google Drive and Microsoft OneDrive. Maximum Security keeps your valuable files safe from ransomware with Folder Shield which only allows authorized applications to access the protected folders such as your documents, photos, music and videos. It also helps secure your privacy on social networks and includes parental controls. It protects against viruses, malware, identity theft, ransomware and evolving threats. Trend Micro Maximum Security provides comprehensive, multi-device protection using advanced machine learning based technology. Apart from a few quirks, it demonstrates a nice balance of considerate features, and it really shines in up-to-date security, with the numbers to prove it. Trend Micro Titanium Maximum Security combines good design with excellent malware protection. Quitting notifications individually can be a chore, though you can switch out this behavior in the settings menu. Luckily, uninstallation is as simple as unchecking the box in the settings panel.Īggressive: Titanium Maximum Security sometimes considers certain legitimate programs to be malicious and prevents them from running, taking a "better safe than sorry" approach. Though that practice is common, it's annoying, and you may be caught by surprise. Consĭefault toolbar installation: Titanium Maximum Security installs a toolbar in popular browsers like Chrome and Firefox without opt-in or -out during installation. Third-party tester AV-Test confirms Titanium Maximum Security's effective protection: It scored a perfect 100 for protection in malware scanning and beating industry averages. When we plugged in an infected disk, Titanium Maximum Security quickly deleted the file and displayed a notification from the taskbar with assuring language. Security: Trend Micro quickly responds to security vulnerabilities and automatically removes suspected Trojan horses and malicious files. Though full scans are naturally longer, we found the quick scan especially fast and responsive. That's great, because we often want to shut down after running long tests, especially full scans - this way you can initiate overnight scanning and go to bed. This is present during the scanning process, so you don't have to dig through menus. Scanning: One option we appreciate is the ability to shut down the PC after finishing a scan. Though not exactly minimal, Titanium Maximum Security's five-tab header layout feels uncluttered and easy to navigate. Tabs have nice mouseover effects, and the overall app has a modern feel and original visual direction. The interface has a clean, organized menu layout. Prosĭesign: Trend Micro Titanium Maximum Security shares the same interface as its lesser brothers, the Antivirus and Internet Security editions. This review focuses on desktop performance. In addition to a robust malware scanner, Titanium Maximum Security offers a built-in password manager, an in-app Web browser, and a packaged set of tools for protecting and managing your Android device. Trend Micro Titanium Maximum Security is the second-highest antivirus offering from Trend Micro.

0 notes
Text
can you have a vpn with trend micro
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you have a vpn with trend micro
VPN compatibility with Trend Micro
In the digital age where online privacy and security are paramount, the compatibility of VPN services with antivirus software is a critical consideration for many users. One such antivirus software that users often inquire about is Trend Micro.
Trend Micro is a renowned name in the cybersecurity realm, known for its robust protection against various online threats such as malware, ransomware, and phishing attacks. When it comes to VPN compatibility, users will be pleased to know that Trend Micro works seamlessly with most VPN services available in the market.
Whether you're using a VPN for accessing geo-restricted content, safeguarding your online activities from prying eyes, or simply ensuring anonymity while browsing the web, you can rest assured that Trend Micro will complement your VPN usage.
By running Trend Micro alongside your chosen VPN service, you can enjoy an added layer of protection against malicious websites, suspicious downloads, and other online hazards. Furthermore, the combination of VPN and Trend Micro enhances your privacy by encrypting your internet traffic and shielding your sensitive information from potential cyber threats.
It's important to note that while Trend Micro and VPN services are compatible, users should always ensure that both software are kept up-to-date to maximize their effectiveness in combating evolving online threats. Additionally, users should verify compatibility between specific VPN providers and Trend Micro versions to avoid any potential compatibility issues.
In conclusion, the compatibility of VPN services with Trend Micro offers users a comprehensive approach to safeguarding their online presence. By leveraging the combined strengths of both tools, users can enjoy enhanced privacy, security, and peace of mind while navigating the digital landscape.
Trend Micro VPN integration
Trend Micro is a trusted name in cybersecurity, known for its innovative solutions that protect individuals and businesses from digital threats. Their latest development in this realm is the integration of a VPN service into their existing suite of products, promising enhanced privacy and security for users.
VPN, or Virtual Private Network, is a technology that allows users to create a secure connection over the internet, ensuring that their data remains encrypted and protected. By integrating a VPN service into their offerings, Trend Micro aims to provide an all-encompassing solution that not only safeguards against malware and viruses but also shields users from potential privacy breaches and data theft.
The Trend Micro VPN integration is designed to be seamless and user-friendly, making it easy for individuals and organizations to activate and utilize. With just a few clicks, users can establish a secure connection that masks their real IP address, preventing third parties from tracking their online activities and location.
Furthermore, the VPN service offered by Trend Micro boasts high-speed connections and a wide network of servers located across the globe, ensuring reliable performance and unrestricted access to content from anywhere in the world. Whether browsing the web, accessing sensitive information, or connecting to public Wi-Fi networks, users can rest assured that their data is safe and their privacy is maintained.
In conclusion, the integration of a VPN service into Trend Micro's cybersecurity suite represents a significant advancement in digital protection, allowing users to fortify their defenses against a myriad of online threats. By prioritizing privacy and security, Trend Micro continues to solidify its reputation as a leader in the cybersecurity industry.
Using a VPN alongside Trend Micro
Title: Maximizing Security: Using a VPN alongside Trend Micro
In today's digital landscape, safeguarding your online activities has become more crucial than ever. With cyber threats lurking around every corner, employing multiple layers of protection is a smart strategy. One effective combination is utilizing a Virtual Private Network (VPN) in conjunction with reputable antivirus software like Trend Micro.
A VPN adds an extra layer of security by encrypting your internet connection, shielding your data from prying eyes. It creates a secure tunnel between your device and the internet, preventing hackers, ISPs, and even government agencies from intercepting your online activities. This encryption is especially vital when connecting to public Wi-Fi networks, where cybercriminals often lurk, waiting to exploit vulnerable connections.
When paired with Trend Micro, a leading antivirus solution known for its robust threat detection capabilities, the security benefits are further enhanced. While Trend Micro focuses on identifying and blocking malware, ransomware, and other malicious threats, a VPN complements this by safeguarding your online privacy and anonymity.
Together, a VPN and Trend Micro provide a comprehensive defense against a wide range of cyber threats. Whether you're browsing the web, streaming content, or conducting online transactions, you can have peace of mind knowing that your sensitive information is protected.
Moreover, using a VPN alongside Trend Micro allows you to access geo-restricted content and bypass censorship imposed by certain websites or governments. By masking your IP address and routing your internet traffic through servers located in different regions, a VPN grants you unrestricted access to the global internet.
In conclusion, combining a VPN with Trend Micro offers a robust defense against cyber threats while preserving your online privacy and freedom. By investing in these security measures, you can navigate the digital world with confidence, knowing that your personal information remains secure and your online activities remain private.
Trend Micro and VPN coexistence
When it comes to cybersecurity, ensuring the coexistence of Trend Micro and a VPN is crucial for maintaining optimal protection of your online activities. Trend Micro is a leading provider of antivirus and internet security software, while a Virtual Private Network (VPN) is essential for safeguarding your online privacy and data security.
Using Trend Micro alongside a VPN can enhance your overall cybersecurity posture by combining the threat detection capabilities of Trend Micro with the privacy and anonymity features of a VPN. Trend Micro's real-time scanning and malware detection capabilities can provide an additional layer of defense against various online threats, including viruses, ransomware, and phishing attacks.
By using a VPN in conjunction with Trend Micro, you can encrypt your internet connection and route your online traffic through secure servers, making it difficult for cybercriminals to intercept your data. This added layer of encryption ensures that your online activities, such as browsing the web, accessing sensitive information, or online banking, remain private and secure.
However, it is essential to configure both Trend Micro and the VPN properly to avoid conflicts that may impact their performance. Make sure to whitelist the VPN application in Trend Micro's settings to prevent any issues with connectivity or performance. Additionally, keep both software up to date to ensure they can effectively protect you from the latest cyber threats.
In conclusion, the coexistence of Trend Micro and a VPN can provide comprehensive protection for your online activities, combining the strengths of both solutions to enhance your cybersecurity defenses and safeguard your digital privacy.
VPN functionality with Trend Micro
Title: Maximizing Online Security: Understanding VPN Functionality with Trend Micro
In today's digitally interconnected world, safeguarding sensitive data and maintaining online privacy is paramount. One potent tool in achieving this is a Virtual Private Network (VPN), which encrypts internet traffic and routes it through secure servers, shielding users from prying eyes and potential cyber threats. Trend Micro, a leading cybersecurity provider, offers advanced VPN functionality integrated into its suite of protection tools, enhancing users' online security experience.
One key feature of Trend Micro's VPN is its robust encryption protocols, which create a secure tunnel for data transmission. By encrypting data packets, it becomes nearly impossible for hackers or malicious entities to intercept and decipher sensitive information such as passwords, financial details, or personal communications. This ensures that users can browse the web, conduct transactions, and communicate online with confidence, knowing their data is shielded from unauthorized access.
Moreover, Trend Micro's VPN offers a diverse network of servers strategically located across the globe. This not only ensures reliable connectivity but also enables users to bypass geo-restrictions and access content from different regions. Whether streaming favorite shows, accessing restricted websites, or connecting to public Wi-Fi hotspots, users can enjoy unrestricted internet access while maintaining anonymity and security.
Furthermore, Trend Micro integrates additional security features into its VPN solution, such as ad and malware blocking. By filtering out potentially harmful content at the network level, users are shielded from online threats, including malicious ads, phishing attempts, and malware-infected websites. This proactive approach to cybersecurity complements the core functionality of the VPN, providing comprehensive protection against a wide range of online hazards.
In conclusion, VPN functionality with Trend Micro offers a multifaceted approach to online security, combining robust encryption, global server network, and integrated threat protection. Whether browsing the web from home, traveling abroad, or accessing sensitive information on the go, users can trust Trend Micro to safeguard their digital presence effectively. With threats evolving constantly, investing in a reliable VPN solution is a proactive step towards ensuring a secure and private online experience.
0 notes
Text
Virtual Mobile Infrastructure Market: Growth Factors
According to a recently published market study report by Future Market Insights, the virtual mobile infrastructure market had global sales of US$ 155.7 million in 2023. The market is anticipated to increase by 8.3% between 2023 and 2033, reaching a valuation of US$ 346.6 million. Services are predicted to generate the highest amount of revenue between 2023 and 2033, with a CAGR of 8.3%.
Some of the factors driving the growth of the global Virtual Mobile Infrastructure Market include improved information security, cheaper hardware and running costs, and simplified services of the flexible work environment through a single control center. Virtual Mobile Infrastructure is a method of storing the working configuration of a portable device in the cloud. When virtualized infrastructure is installed, the application begins to run on a virtual machine in the central server.
Over the forecast period, the market for mobile virtual network operators is likely to be driven by the increased usage of data and value-added offerings such as online broadcasts and M-commerce-based services. Increased smartphone adoption and the resulting increase in mobile subscriber base are expected to significantly boost to industry development.
Don’t miss this opportunity for success. Claim your sample report and dominate the wired interface market now @
https://www.futuremarketinsights.com/reports/sample/rep-gb-15537
Mobile virtual network providers offer a wide range of consumer demands, however, they do not control the whole infrastructure or radio frequency license. It improves security by removing the need for employees to download a mobile app or keep sensitive company data on their mobile devices, such as smartphones and tablets. Furthermore, virtual mobile infrastructure enables administrators to centrally set up and deploy multiple mobile workplaces to their employees, making mobile workplace administration simple and efficient.
“The increased usage of data and value-added services such as online broadcasts and M-commerce based services is boosting the market for services in Virtual Mobile Infrastructure.” comments a Future Market Insights analyst.
Competitive Landscape
Lebara Group, Lyca Mobile, TalkTalk Group, Giffgaff, Poste Mobile SpA, Virgin Mobile, and TracFone Wireless Inc. are the key players in the virtual mobile infrastructure market.
Some of the key developments in the virtual mobile infrastructure market include:
In October 2021, Avast Safe Browser PRO, a premium edition of their safe browser, has been introduced by Avast, the company behind one of the most popular antivirus programs.
In September 2021, Trend Micro Incorporated, launched a new safe room for Indian cloud users. To be sovereign and private, will assist the country in storing data securely within it.
Report a Customization for any Query @
https://www.futuremarketinsights.com/customization-available/rep-gb-15537
More Insights Available
Future Market Insights, in its new offering, presents an unbiased analysis of the Virtual Mobile Infrastructure Market, presenting historical market data (2015-2021) and forecast statistics for the period of 2022-2032.
The study reveals extensive growth in Virtual Mobile Infrastructure Market in terms of Component (Platforms, Services), Deployment Type (Cloud, On-premises), and Vertical (BFSI, Healthcare, Manufacturing, IT and Telecom, Government, Others), across five regions (North America, Latin America, Europe, Asia Pacific and Middle East & Africa).
Market Segments Covered in Virtual Mobile Infrastructure Market Analysis
By Component:
Platforms
Services
By Deployment Type:
Cloud
On-premises
By Vertical:
BFSI
Healthcare
Manufacturing
IT and Telecom
Government
Others
0 notes
Text
Ensuring Endpoint Security with Trend Micro Antivirus

In today’s digital landscape, where cybersecurity threats are becoming more sophisticated and prevalent, ensuring endpoint security has never been more critical. With the rise of remote work and the widespread use of connected devices, the need for robust security solutions is paramount. One such solution that has gained prominence is Trend Micro Antivirus. In this article, we will explore the significance of Endpoint Security, delve into the features of Trend Micro Antivirus, and understand how it can effectively safeguard your digital environment.
The Importance of Endpoint Security
Endpoint security involves protecting the various endpoints or devices within a network from malicious attacks or unauthorized access. As the entry points to a network, endpoints include devices such as laptops, smartphones, tablets, and servers. With cybercriminals constantly evolving their tactics, organizations and individuals alike must adopt comprehensive security measures to mitigate risks.
Understanding Trend Micro Antivirus
How Does Trend Micro Antivirus Work?
Trend Micro Antivirus is designed to detect, prevent, and eliminate various forms of malware, including viruses, spyware, Trojans, and ransomware. It employs advanced algorithms and heuristics to identify suspicious behavior and patterns, ensuring that potential threats are stopped in their tracks.
Key Features of Trend Micro Antivirus
Trend Micro Antivirus offers a range of features to provide comprehensive protection:
Real-time Threat Monitoring
The antivirus continuously monitors your device, files, and online activities in real time. It promptly detects and blocks threats before they can cause harm.
Web and Email Protection
Trend Micro safeguards your web browsing and email communication, preventing you from inadvertently accessing malicious websites or downloading infected attachments.
Ransomware Safeguard
With the rise of ransomware attacks, Trend Micro includes a robust ransomware protection feature that secures your files against encryption by malicious actors.
Benefits of Using Trend Micro Antivirus
Easy Installation Process
Installing Trend Micro Antivirus is hassle-free, and the setup wizard guides you through the process step by step. You can have the software up and running in no time.
Intuitive User Interface
The user interface is designed with simplicity in mind. Even if you’re not a tech-savvy individual, navigating through the software and accessing its features is straightforward.
Customizable Scanning Options
Trend Micro Antivirus offers different scanning options to suit your needs:
Full System Scan
A comprehensive scan of all files and folders on your device, ensuring thorough protection.
Quick Scan
A swift scan of commonly targeted areas for rapid threat detection.
Custom Scan
Allows you to choose specific files or folders for scanning, giving you control over the scanning process.
Regular Updates for Maximum Protection
Trend Micro consistently updates its antivirus database to stay ahead of emerging threats. These updates ensure that the antivirus can identify and neutralize the latest forms of malware effectively.
Compatibility with Various Operating Systems
Whether you’re using Windows, macOS, or other operating systems, Trend Micro Antivirus offers compatibility, ensuring that users across different platforms can enjoy its protective features.
Performance Impact and System Requirements
Trend Micro Antivirus is designed to have minimal impact on your system’s performance. It operates in the background without causing slowdowns or disruptions.
Pricing Plans and Licensing Options
Trend Micro provides flexible pricing plans and licensing options to cater to individual users, families, and businesses of varying sizes. This allows you to choose a plan that suits your needs and budget.
Testimonials from Satisfied Users
Many users have praised Trend Micro Antivirus for its effectiveness in detecting and preventing malware. Users highlight its user-friendly interface and reliable protection against cyber threats.
How to Get Started with Trend Micro Antivirus
To start using Trend Micro Antivirus and fortify your endpoint security, follow these simple steps:
Visit the official website at https://www.cloudtechtiq.com/endpoint-security.
Choose the appropriate pricing plan based on your requirements.
Download and install the antivirus software following the provided instructions.
Run a full system scan to ensure your device is secure from the outset.
Enjoy peace of mind as Trend Micro safeguards your digital life.
Conclusion
In an era of escalating cyber threats, having robust endpoint security is no longer optional — it’s a necessity. Trend Micro Antivirus offers a powerful solution that combines advanced threat detection with a user-friendly experience. By leveraging its features, you can browse the web, communicate via email, and use your devices without constantly worrying about potential threats
0 notes
Text
9 Ways to Stay Cyber-Secure While Working From Home

Working from home can be a great way to save time and money, but it also comes with its own set of cybersecurity risks. In this blog post, Tech Info Galaxy presents nine ways to stay cyber-secure while working from home. We’ll cover everything from protecting your computer to securing your data to staying safe online. Plus, we’ll provide tips for business owners who want to keep their data secure. Stay safe and stay productive!
1. Protected Yourself with Antivirus Software and a Firewall
When working from home, your computer must be properly protected. This means using anti-virus software and a firewall. Antivirus software protects your computer against viruses, while a firewall helps protect your computer from hackers and other online threats. If you don’t have anti-virus software installed on your computer, here are some of the leading products on the market:
Norton AntiVirus
McAfee AntiVirus
Trend Micro Antivirus+ Security
Kaspersky Internet Security
Bitdefender Internet Security
To set up a firewall, you’ll need to go into your computer’s settings. For Windows users, this is done by going to Control Panel > System and Security > Windows Firewall. For Mac users, this is done by going to System Preferences > Security & Privacy > Firewall. Once you’re in the firewall settings, you’ll need to turn on the firewall and add any exceptions for programs that need access to your computer.
2. Keep Your Operating System and Software Up to Date
One of the simplest and most effective ways to stay cyber-secure is to ensure that your operating system and software are always up to date. Hackers are constantly finding new ways to exploit vulnerabilities in outdated systems, so it’s important to keep yours patched and protected. You can usually set your system to update automatically, or Computer World explains that you can check for updates manually.
3. Create Strong Passwords
Using strong passwords is crucial when working from home. All your passwords on all your devices and accounts should be long, complex, and unique.
It’s essential not to use the same passwords on multiple accounts, as this makes it easier for hackers to gain access to your information. You should also change your passwords regularly.
4. Be Careful about What Files You Download and Open
Be vigilant about what files you download and open. Many viruses and malware are spread through email attachments and file downloads, so be cautious about where your information comes from. Before opening any file, scrutinize it for anything suspicious, like unexpected attachments or strange file extensions. If in doubt, don’t open it.
5. Use a Digital Signature
Digital signatures are a great way to keep your documents and data secure when sending them online. They allow you to electronically sign a document, providing a layer of security and assurance that the document has not been tampered with. This is particularly important for sensitive information, such as financial or legal documents.
When using a digital signature, use a strong password and change it regularly. Also, be sure to store your signature key in a safe place. You won’t be able to digitally sign any documents if you lose your key....read more
0 notes
Text
KSA Cybersecurity Market is Expected to Gain Momentum from the Technological Advancements and Government Initiatives along with Covid Incited surge in Demand: Ken Research
Buy Now
Government strict regulations such as ECC and Cybersecurity Framework by SAMA will act as a catalyst for the surging growth of the cybersecurity market in KSA. Shifting to cloud infrastructure as companies look for a hybrid mode of working will assist the growth of the industry.
Covid 19 has not only forced people to spend time more time online but has also led to the swift evolution of cybersecurity in KSA. Innovative antivirus solutions have become incredibly important to facilitate live streaming and e-learning.
The recent MoU signed between Saudi NCA and the US Department of Homeland Security is expected to aid the cybersecurity industry focusing on several areas such as sharing cyber threats information between both countries
Strong Government Push: Strict regulations by the government such as ECC and Cybersecurity Framework by SAMA will also act as a catalyst for the surging growth of the cybersecurity market in Saudi Arabia. Coupled with that, the launch of smart city projects such as NEOM will also provide the much-needed push to the sector.
Technological Advancements in Cybersecurity Services: Advancements in encryption technologies, firewalls, MDR, XDR, EDR, digital forensic investigation, and GRC services among others are expected in the coming years. These advancements will lead to a more secure internet network in the Saudi Arabian cyberspace during the forecast period.
Demand for Big Data and 5G Rollout: The cybersecurity market in Saudi Arabia is estimated to expand at a high CAGR in between 2021 and 2026E attributed to increasing demand for big data, a high surging internet penetration rate and roll out of 5G services across the nation. The more connected the nation will become, the more will be the demand for cybersecurity services among users.
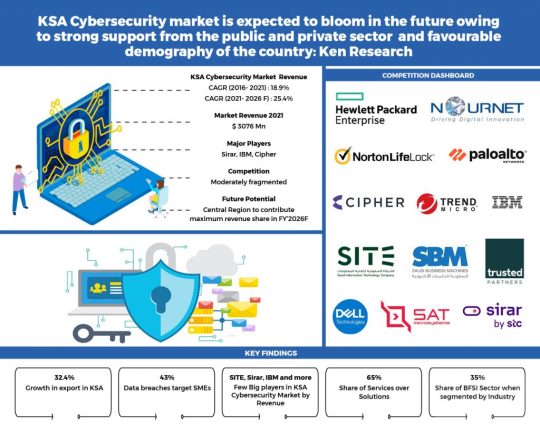
The report titled “KSA Cybersecurity Market Outlook to 2026E- Gauging the opportunities for foreign investment in the cybersecurity market” provides a comprehensive analysis of the potential of the Cybersecurity industry in Kingdom of Saudi Arabia. The report covers various aspects including the current cyber threat scenario and major cyberattacks in the country, revenue generated from cybersecurity, its segmentations viz Component, Deployment Type, Region, End User (Medium and Small Enterprises vs Large Enterprises), by Industry, major trends and developments, issues and challenges, government regulations and product analysis. The report concludes with market projections for future of the industry including forecasted industry size by revenue along with analyst recommendations and key market opportunities.
Key Segments Covered in KSA Cybersecurity Market:
By Component (By Revenue), 2021 and 2026F
Solutions
Services
By Deployment Type (By Revenue), 2021 and 2026F
On-Premise
Cloud
By Region (By Revenue), 2021 and 2026F
Northern
Western
Eastern
Central
Southern
Ask for Customization
By User (By Revenue), 2021 and 2026F
Medium and Small Enterprises
Large Enterprises

By Industry (By Revenue), 2021 and 2026F
BFSI
Government Sector
IT
Telecom
E-Commerce
Healthcare
Retail
Others includes food industry and more
Key Target Audience
Technology Companies
Cybersecurity Companies
Banking and Financial Institutions
Cybersecurity Service Providers
Government Agencies
Cybersecurity Consultants
Time Period Captured in the Report:
Historical Period: 2016-2021
Forecast Period: 2021-2026
Download Free Sample
Key Companies Covered:
SITE
Sirar by STC
IBM
Palo Alto Networks
SBM
Cipher
NourNet
Trusted Partners
Trend Micro Incorporated
Hewlett Packard Enterprise
Norton LifeLock Inc.
Dell Technologies
SAT Microsystems
Key Topics Covered in the Report:
KSA Country Profile and Population Analysis
Operating Model of Cybersecurity Companies
KSA Cybersecurity Market Size and Segmentations
Growth Drivers of KSA Cybersecurity Market
Porter’s Five Forces Analysis of KSA Cybersecurity Market
Government Rules and Regulations in KSA Cybersecurity Market
Government Initiatives in KSA Cybersecurity Market
Key Trends and Developments in KSA Cybersecurity Market
Role of Cutting-Edge Technology in Developing Cybersecurity Solutions and Applications in KSA
Issues and Challenges of KSA Cybersecurity Market
Demand Side Analysis
Analyst Recommendations
Case Studies
Research Methodology
For more information on the research report, refer to below links:
KSA Cybersecurity Market Outlook to 2026E
Related Reports
Cybersecurity Market: Current Analysis and Forecast: Ken Research
Global Financial Cyber Security Market Development Strategy Pre and Post COVID-19, by Corporate Strategy Analysis, Landscape, Type, Application, and Leading 20 Countries: Ken Research
Global Automotive Cybersecurity Market Research Report with Opportunities and Strategies to Boost Growth- COVID-19 Impact and Recovery: Ken Research
0 notes
Text
Visitor Behavior Intelligence Software Market to See Booming Growth | Stampede, Sensing feeling, Purple, Aislelabs flow
The latest study released on the Global Visitor Behavior Intelligence Software Market by AMA Research evaluates market size, trend, and forecast to 2027. The Visitor Behavior Intelligence Software market study covers significant research data and proofs to be a handy resource document for managers, analysts, industry experts and other key people to have ready-to-access and self-analyzed study to help understand market trends, growth drivers, opportunities and upcoming challenges and about the competitors.
Key Players in This Report Include:
Cisco (United States), Purple (United States), My wi-fi networks (Canada), Sensing feeling (United States), Aislelabs flow (Canada), Stampede (United States), Auruba analytics and location engine (United States), Bloom intelligence (United States), Botbit (Argentina), Tanaza cloud (Italy)
Download Sample Report PDF (Including Full TOC, Table & Figures) @ https://www.advancemarketanalytics.com/sample-report/115258-global-visitor-behavior-intelligence-software-market#utm_source=OpenPRVinay
Definition:
Visitor behavior intelligence software helps to monitor the action of visitor from the data sources such as people counters, guest Wi-Fi, or camera. It enables to understand interactions, motivations, and experiences. It also provides insights to the customer journey and behavior of these visitors. Visitor behavior intelligence tool also connects to the data sources such as social media, customer data platforms, and third party data sources which gives holistic view of visitor experience. After connecting with data sources, it provides insights to brick and mortar locations which are similar to e commerce platform.
Market Drivers:
• Increasing Concerns over the Data Privacy is Fueling the Market Growth
• Adoption of Visitor Behavior Intelligence Software in Small Enterprises
Market Trend:
• Technological Developments in Visitor Behavior Intelligence
Market Opportunities:
• Increasing Product Demand from Key Geographic Areas
The Global Visitor Behavior Intelligence Software Market segments and Market Data Break Down are illuminated below:
by Platform (Windows, Android, IOS), Organization size (Large Enterprises, SMEs), Features (Antivirus, Whitelists, Antispam filtering, Content filtering, Visit tracking, Dashboards, Others), Subscription (Monthly, Annually, One time license)
Global Visitor Behavior Intelligence Software market report highlights information regarding the current and future industry trends, growth patterns, as well as it offers business strategies to help the stakeholders in making sound decisions that may help to ensure the profit trajectory over the forecast years.
Have a query? Market an enquiry before purchase @ https://www.advancemarketanalytics.com/enquiry-before-buy/115258-global-visitor-behavior-intelligence-software-market#utm_source=OpenPRVinay
Geographically, the detailed analysis of consumption, revenue, market share, and growth rate of the following regions:
• The Middle East and Africa (South Africa, Saudi Arabia, UAE, Israel, Egypt, etc.)
• North America (United States, Mexico & Canada)
• South America (Brazil, Venezuela, Argentina, Ecuador, Peru, Colombia, etc.)
• Europe (Turkey, Spain, Turkey, Netherlands Denmark, Belgium, Switzerland, Germany, Russia UK, Italy, France, etc.)
• Asia-Pacific (Taiwan, Hong Kong, Singapore, Vietnam, China, Malaysia, Japan, Philippines, Korea, Thailand, India, Indonesia, and Australia).
Objectives of the Report
• -To carefully analyze and forecast the size of the Visitor Behavior Intelligence Software market by value and volume.
• -To estimate the market shares of major segments of the Visitor Behavior Intelligence Software
• -To showcase the development of the Visitor Behavior Intelligence Software market in different parts of the world.
• -To analyze and study micro-markets in terms of their contributions to the Visitor Behavior Intelligence Software market, their prospects, and individual growth trends.
• -To offer precise and useful details about factors affecting the growth of the Visitor Behavior Intelligence Software
• -To provide a meticulous assessment of crucial business strategies used by leading companies operating in the Visitor Behavior Intelligence Software market, which include research and development, collaborations, agreements, partnerships, acquisitions, mergers, new developments, and product launches.
Buy Complete Assessment of Visitor Behavior Intelligence Software market Now @ https://www.advancemarketanalytics.com/buy-now?format=1&report=115258#utm_source=OpenPRVinay
Major highlights from Table of Contents:
Visitor Behavior Intelligence Software Market Study Coverage:
• It includes major manufacturers, emerging player's growth story, and major business segments of Visitor Behavior Intelligence Software market, years considered, and research objectives. Additionally, segmentation on the basis of the type of product, application, and technology.
• Visitor Behavior Intelligence Software Market Executive Summary: It gives a summary of overall studies, growth rate, available market, competitive landscape, market drivers, trends, and issues, and macroscopic indicators.
• Visitor Behavior Intelligence Software Market Production by Region Visitor Behavior Intelligence Software Market Profile of Manufacturers-players are studied on the basis of SWOT, their products, production, value, financials, and other vital factors.
• Key Points Covered in Visitor Behavior Intelligence Software Market Report:
• Visitor Behavior Intelligence Software Overview, Definition and Classification Market drivers and barriers
• Visitor Behavior Intelligence Software Market Competition by Manufacturers
• Impact Analysis of COVID-19 on Visitor Behavior Intelligence Software Market
• Visitor Behavior Intelligence Software Capacity, Production, Revenue (Value) by Region (2021-2027)
• Visitor Behavior Intelligence Software Supply (Production), Consumption, Export, Import by Region (2021-2027)
• Visitor Behavior Intelligence Software Production, Revenue (Value), Price Trend by Type {Payment Gateway, Merchant Account, Subscription Management,}
• Visitor Behavior Intelligence Software Manufacturers Profiles/Analysis Visitor Behavior Intelligence Software Manufacturing Cost Analysis, Industrial/Supply Chain Analysis, Sourcing Strategy and Downstream Buyers, Marketing
• Strategy by Key Manufacturers/Players, Connected Distributors/Traders Standardization, Regulatory and collaborative initiatives, Industry road map and value chain Market Effect Factors Analysis.
Browse Complete Summary and Table of Content @ https://www.advancemarketanalytics.com/reports/115258-global-visitor-behavior-intelligence-software-market#utm_source=OpenPRVinay
Key questions answered
• How feasible is Visitor Behavior Intelligence Software market for long-term investment?
• What are influencing factors driving the demand for Visitor Behavior Intelligence Software near future?
• What is the impact analysis of various factors in the Global Visitor Behavior Intelligence Software market growth?
• What are the recent trends in the regional market and how successful they are?
Thanks for reading this article; you can also get individual chapter wise section or region wise report version like North America, Middle East, Africa, Europe or LATAM, Southeast Asia.
0 notes
Text
How to trend micro install on new computer with activation code
What is a Trend Micro Install?
When you buy a new computer, one of the first things you need to do is install an antivirus program. But what exactly is a micro install?
A micro install is a type of software installation that is designed to be quick and easy. Unlike a traditional installation, which can take several minutes or even hours, a micro install can be completed in just a few seconds.
One of the biggest benefits of using a micro install is that it doesn’t require any user input. That means you don’t have to click through any prompts or agree to any terms and conditions. Simply download the software and run the installer.
Another advantage of micro installs is that they are often much smaller in size than traditional installations. That means they take up less disk space and use fewer resources, which can be especially important on older or slower computers.
If you’re looking for an antivirus program for your new computer, Trend Micro offers a variety of options that can be installed using a micro installer. To get started, simply choose the product that best meets your needs and then follow the instructions on the download page.
How to find the micro install on your new computer?
If you're like most people, you probably don't know how to find the micro install on your new computer. Here's a quick guide to help you out.
1. First, open up your computer's web browser and type in "www.trendmicro.com/install" into the address bar.
2. Once theTrend Micro website loads, click on the "Install Now" button located in the middle of the page.
3. On the next page, select your operating system from the drop-down menu and then click on the "Download" button.
4. Once the download is complete, double-click on the installer file to begin installation.
5. Follow the prompts to complete installation and then restart your computer when prompted.
How to update the micro install on your new computer?
If you've just purchased a new computer, you'll need to update your Trend Micro security software. This can be done easily by following these steps:
1. Open your Trend Micro security software
2. Click on "Update"
3. Select "Check for updates now"
4.Click "Install"
5. Restart your computer
That's it! You've now successfully updated your Trend Micro security software on your new computer.
How to uninstall and reinstall the micro install on your old computer?
If your old computer is running slowly, you may want to uninstall and reinstall the micro install. This can help speed up your computer and help it run more smoothly.
To uninstall the micro install, follow these steps:
1. Click on the Start menu and select Control Panel.
2. Click on Add or Remove Programs.
3. Find the entry for Micro Install and click on it.
4. Click on the Remove button.
5. Follow the prompts to remove the program from your computer.
6 After the program has been uninstalled, restart your computer.
7 Once your computer has restarted, you can then reinstall the program by following these steps: 8 Download the latest version of Micro Install from their website 9 Once the download is complete, double-click on the installer file to begin 10 Follow the prompts to install Micro Install onto your computer 11 Upon completion, restart your machine again 12 You should now have a clean installation of Micro Install onto your old computer!
Conclusion
If you're looking to install Trend Micro on your new computer, there's no need to worry. The process is actually quite simple and can be done in just a few minutes. All you'll need is your Trend Micro activation code and an internet connection. Once you have those two things, just follow the steps below and you'll be up and running in no time.
0 notes
Text
activate trend micro with activation code
GETSTARTED BY TRENDMICRO
Effectively Download, Introduce and Initiate Trend Micro Geek Squad
While purchasing any Trend Micro Geek Squad item, a 20-digit alphanumeric keycode will presumably be shipped off a composed or email on the retail location.
The successive mystery will be utilized to initiate the antivirus application.
The strategy to download and introduce is quite simple; follow the activities recorded underneath.
Survey Framework Necessities of Trend Micro Geek Squad
Windows PC
Operating system Win 7 (32-digit/64-bit), Win 8.1(32-cycle/64-bit) and Grow 10 (32-bit/64-bit)
Processor-Inch GHz technique;
Smash 1 GB Slam (2GB suggested);
Space Accessible 1.3 GB Hard Drive space (1.5 GB suggested)
Macintosh PC
Operating system Apple Macintosh operating system 10.13 into 10.14 or more noteworthy, Macintosh operating system X variation 10.15"Catalina" (10.15 or more prominent )
Processor-Intel Center - base Mac PC;
Slam 2GB Smash;
Space Accessible 1.5GB of accessible Hard Drive space
Moves toward Download, Introduce and Actuate Trend Micro Geek Squad
Download Trend Micro Installer report from Trend Micro Geek Squad download website page.
Whenever you are about the website page, the archive will consequently start downloading. In any case, click Download Today to store the record.
Following the downloading gets done, make a beeline for the report area. Doubleclick .exe or .dmg report to execute it.
The establishment window will show up, click the Introduce Program.
It'll lead something grasp test. Once finished, click the Paid variation.
Input the 20-digit actuation successive number and afterward click Straightaway.
Practice the onscreen training, pick the hopeful choices and finish the establishment method.
After you complete the methodology, Trend Micro Geek Squad is going to without a doubt probably most likely before long be introduced and enacted on your own framework.
Advance Malware and Journal Assurance
It's supported by imaginative man-made intelligence and cloud-based assurance, which give realtime malware along other risk insurance.
You might stay safeguarded against some other malware, ransomware, rootkit as well as various vindictive infections.
Antitheft and Antiscam
Our delicate and personality records are extremely fundamental, and programmers might begin searching for the opportunity to slip it by sending messages, joins or through web destinations.
This element will hinder and furthermore avoid some trick or malware undertakings until they abuse you.
Parental Control
Since you watch your self, it's fundamental for give security to your young ones on the web.
Using this component, it is feasible to remotely control those assignments on the web and channel any material harming to the youngsters.
Online entertainment Security Assurance
For the people who have accounts in pretty much any online entertainment, recollect your protection isn't ensured. There are programmers out there to take private subtleties.
Digital hoodlums can disregard isolation assurance. With the help with the element, your cultural sites isolation stays classified and secured.
Framework Streamlining and Fixes
A few times at whatever point your PC works gradually, it needs to patch and encouraged.
Geek Squad Trend Micro will lift, fixes and fix blemishes on your own body to permit it to easily run.
Web based shopping and Banking Insurance
In the occasion, you do monetary exchanges and web shopping routinely, ensuring a safe atmosphere is basic.
Using this component, you will not need to be stressed as the web climate is obtained. Furthermore, give extra security to an own secret phrase utilizing Secret key Manager.
Ward off trouble makers a long way from slipping your monetary points of interest.
Multi-Gadget Administration
You can safeguard gadgets like PC, Macintosh notwithstanding cell mechanical assembly. Ensure that all of your mechanical assembly stay safeguarded.
1 note
·
View note
Text
activate trend micro for windows
An extremely straightforward and simple cycle to Trend Micro greatest Security Initiation. The latest most extreme security requires no circles
You can track down the moves toward introduce it in the data area. You can get the proof segment underneath on this page. Begin to begin the moment establishment system with us.
Trend Micro Web Security Actuation Help
Trend Micro offers a paid version of web security for PCs. www.trendmicro.com/bestbuy is the right page to introduce, download and enact your trend micro security program for your gadget. Subsequently, you can arrive at this page every minute of every day to get master help too.
Download Trend Micro with key and Download Trend Micro with Item Key
There is no question that trend micro item key programming is a top of the line web security program viable with various working frameworks, including Windows computers, Macintoshes, Android, and iOS gadgets. For security against various sorts of infections, Trend Micro can be utilized as infection safeguard programming. It comprises of information robberies, ransomware, infections, perilous destinations, and numerous other obscure dangers. Moreover, Trend Micro Security 2018 is a genuinely very much checked on web security program too. To attempt Trend Micro's free preliminary items, including Antivirus, Web Security and more, kindly visit their download focus.
Trend Micro Greatest Security Download with Item Key
Trend Micro gives moderate web-based insurance to your gadget with its Web Security Antivirus Programming. It is accessible with a 30 days preliminary version by downloading the free online installer of this program, it is likewise reasonable for both 32Bit and 64Bit
1 note
·
View note
Text
install trend micro security for best buy
At the point when you buy any antivirus item from this american brand, you can set up the indistinguishable from your gadget essentially. It is very helpful to place in any of the security programs from trend micro with a couple of straightforward advances which you need to consent with.1. In the first place, you will should download the antivirus programming to be had at trend micro. This might be finished with a strong net association without a compact disc or dvd. You could likewise attempt this with the help of a retail card.2. Following stage is gaining admittance to the specific 20 man or lady alpha-numeric code (xxxx xxxx-xxxx) that is your item key. In the event that you purchase a retail card, you might find this specific code at the posterior of the cardboard which you need to enter when you made your record and log in.Three. You can now convey trend micro with this item key with the guide of coming into this specific item key. The establishment technique is currently entire and you could tap on the 'post' button.The trendmicro.Com/arrangement item key makes it simple and advantageous for all clients to introduce antivirus with out a truckload help. Be that as it may, in the event that you run into any difficulty all through the set up strategy, then here are a few pointers for assist.Take a gander at your web association if the computerized download falls flat. Deficient net speed frequently hampers a smooth download of antivirus files.In case you have a current antivirus to your contraption, you will initially should uninstall it sooner than you establishment trend micro com safe.Make sure that your running framework has the trendy updates all together that it's far similar with the trend micro antivirus which you are placing in.
Needed to place in trend micro in PC (home windows)? Entire manual for introduce trend micro secure to your PC or computer:To introduce trend micro secure on PC or PC clients need to initially join on www.trend micro.Com/protected with their electronic mail and trend micro safe key code. Assuming currently enlisted sincerely sign in to trend micro secure account.When you signed in to trend micro record click on transfer laptop.Store trend micro wsainstall exe and run this report to introduce trend micro safe.
Looking to down stack trend micro in macintosh pc (apple)?
Check under orders to down load and establishment trend micro on your mac:For a smooth introduce, macintosh clients need to open www.trendmicro.Com/on a browser(safari) and down load trend micro loose anyplace installer.Get passage to the trend micro installer report through double tap on trend micro utility and drag it to the application folder.Subsequent step is to enact trend micro for that clients need to double tap on trend micro secure anyplace application and hit set off subsequent to setting key code in.As macintosh individual realize that they need to put pc secret key for any changes. trendmicro.Com/will request secret key permit the product to introduce and you're prepared."Trend Micro Best Purchase"
1 note
·
View note
Text
best buy install trend micro purchased
Trend Micro Help specialists can loan their hand to download, introduce and refresh Trend Micro Government agent Sweeper Antivirus on your framework. We can likewise fix all mistakes that might manifest while introducing and arranging Trend Micro Antivirus on your PC. We can help you recognize and eliminate malignant dangers, malware and spyware by playing out a fast sweep on all records and organizers. With our powerful innovation, we can annihilate dubious projects and contaminated documents from your framework. Our antivirus specialists can clean all web-based dangers, including Trojan, root units, key lumberjacks, and worms in single range. We can advance your PC's speed and proficiency and furthermore shield it from being languid.
Where to search out Trend Micro Permit Code?
The Trend Micro security bundle is easy to arrangement and introduce at trendmicro.com/enactment. Basically find 20-character alpha-numeric code that is composed on the rear of the retail card. Here might be an example Item Key to let you understand:xxxx xxxx xxxx
Trendmicro Antivirus Establishment Guide
Antivirus and digital protection items from this brand are not difficult to utilize and introduce and should be possible in a straightforward way by following a couple of steps. The security bundle presented by this brand is inconceivably simple to arrangement and introduce. You can undoubtedly introduce and overhaul any of the Trendmicro Antivirus items that assist you with taking care of network safety in the most ideal way.
This is the way you can do it in three basic advances:
Begin with arrangement and introduce at trendmicro.com/bestbuy by downloading the product that you can manage without a Cd or DVD. All you want is a decent web association for the reason.
You will track down a 20 person alpha-numeric code (xxxx xxxx-xxxx) which is your item key. Assuming you purchase retail card, you will find this exceptional code on the posterior of the card that you want to enter.
Introduce trendmicro with this Item Key by entering this extraordinary item key to finish the establishment cycle and tapping on the 'Submit' button.
With the trendmicro.com/bestbuy Item Key, you can finish the establishment interaction without help from anyone else. The following are a couple investigating tips for a smooth Trendmicro establishment.
Assuming that the programmed download fizzles, you can call the helpline for help. Slow web associations can prompt issues in downloading.
Assuming you as of now have an enemy of infection introduced on your gadget, you should uninstall that first and eliminate it totally from your framework.
1 note
·
View note
Text
activate trend micro internet security
An extremely basic and simple interaction to Trend Micro greatest Security Activation. The furthest down the line most extreme security requires no plates
You can track down the moves toward install it in the data segment. You can get the proof area underneath on this page. Begin to begin the moment installation strategy with us.
Trend Micro Internet Security Activation Help
Trend Micro offers a paid rendition of internet security for PCs. www.trendmicro.com/bestbuy is the right website page to install, download and enact your trend micro security program for your gadget. Thus, you can arrive at this page every minute of every day to get master help too. The complementary number is +61-872-000-111.
Download Trend Micro with key and Download Trend Micro with Item Key
There is no question that trend micro item key programming is a top of the line internet security program viable with various working frameworks, including Windows computers, Macintoshes, Android, and iOS gadgets. For insurance against various sorts of infections, Trend Micro can be utilized as infection guard programming. It comprises of information robberies, ransomware, infections, perilous locales, and numerous other obscure dangers. Moreover, Trend Micro Security 2018 is a genuinely very much explored internet security program too. To attempt Trend Micro's free preliminary items, including Antivirus, Internet Security and more, if it's not too much trouble, visit their download focus.
Trend Micro Most extreme Security Download with Item Key
Trend Micro gives moderate web-based insurance to your gadget with its Internet Security Antivirus Programming. It is accessible with a 30 days preliminary variant by downloading the free online installer of this program, it is likewise reasonable for both 32Bit and 64Bit
1 note
·
View note
Text
trend micro home install download
Trend Micro, a Japanese Global Network protection and security firm sent off in La, California involving its own worldwide central command in Tokyo, Japan, a Research and development focus in Taipei, Taiwan, alongside territorial base camp in Asia, Europe, and furthermore in areas of America. The business extends security applications for servers, distributed computing environmental factors, little, medium and undertaking organizations along with individuals.
How To Install www.trendmicro.com/bestbuypc?
Indeed, even as we begin with Trend Micro Install an individual should survey and recognize Trend Micro Activation code. Investigate the Trend Micro Re-Tail card, since you can find 20 examples alpha-numeric Activation code Test (XXXX XXXX-XXXX).
Trend Micro matches various wellbeing items for Home Clients see the posting underneath:
Thorough risk Assurance
Internet Security
Against Infection for Macintosh
Portable Security for both Android and I-operating system
Secret phrase Supervisor
Greatest Security
Essential Macintosh Security
Antivirus + Security
Internet Security for Tab
Portable Security for both Android and I-operating system
Suppose You Might want to Install Trend Micro Versatile Security for both Android and I-operating system see www.trendmicro.com/activation. Beneath you'll find a full-page in regards to your Activation code. By the posting of results select one that claims"Enter Activation Code | Trend Micro"
Beat on Near move.
Essential Macintosh Security www.trendmicro.com/bestbuypc.
Further, even if you might want to Install Trend Micro Essential Macintosh Security start a brand new site page of Safari program and afterward click over the location bar www.trendmicro.com/bestbuypc. This you will see a green button Snap here to start your download. All things considered, in the event that you find a critical assortment of web crawler results attract to your name"antivirus for Macintosh | Trend Micro".
Trend Micro AntiVirus Best buy.
BestBuy is the primary store of Gadgets device and pc programming. New PC and Scratch pad clients for the most part favor antivirus security from same-store to Install Trend Micro most valuable purchase. As the shopper expects to continue www.trendmicro.com/bestbuypc. All things considered, simply in the occasion you're utilizing a web crawler like Bing, then Google and Hurray attempt to find"Geek Crew | Trend Micro" or even "www.trendmicro.com".
Start the internet website on the grounds that the installer record starts downloading Run Trend Micro Installer report to install to your own PC.
1 note
·
View note
Text
download purchased trend micro
Trend Micro Security utilizes progressed man-made brainpower innovation to give strong, multi-gadget protection.It is viable with different gadgets like PC, Macintosh, Cell phones, windows, and PC. With its definitive elements trend micro download and install process is secure that shields your gadgets and internet from emancipate, malware, spyware, infection, and different dangers. Inspect purchasing Trend micro from Trend Micro on the off chance that you will purchase another gadget for your home, official or business use. Trend micro nerd crew is a 100 percent security supplier antivirus that eliminates a wide range of dangers from your gadgets as well as from the network.Trend Micro Security looks at your PC to guarantee it meets the essential structure necessities; checks it for existing contaminations or programming you need to uninstall first, and after that profits to support you during the license study and foundation process. In the event that you're presenting the 30-day Preliminary execution you will not need a successive number. If you've paid for the security, you will be exhibited where to enter the consecutive number. In case you at this point have a more prepared arrival of Trend Micro Security programming presented on your PC, the installer makes you uninstall it, prompts you to reboot, and the foundation subsequently proceeds. Right when the foundation is done, you've helped the activation methodology, trapped with your Trend Micro record (in case you at this point have one), or supported through the development of one more record if you don't. At the point when inception is done, you can genuinely invigorate your disease protection for the latest portions or essentially let Trend Micro Security update itself for you. Ordering the Trend Micro Toolbar in your program of choice is the last development. By then, you'll be all around safeguarded from web risks in filed records, on relational associations, or from associations in phishing messages that should accept you to terrible destinations or convince you to download detestable records. The overview of protections given by Trend Micro Security is long.Keep Your internet Exchanges Secure with Trend Micro Security's Compensation Watchman BrowserThese days, online trades are regularly under risk from malware and program imbuements that would take your character data or your money as you sign in to your favored banking, monetary, or business accounts. Trend Micro new Compensation Watchman Program, open with every one of the three 2019 PC arrivals of Trend Micro Security, is expressly planned to confirm and keep your data hidden by means of normally giving a "set program" for all your internet based trades. Pay Gatekeeper works by clearing out any weaknesses or untouchable developments in your default PC program — whether or not Chrome, Firefox or Internet Pioneer. It by then applies Trend Micro's famous Trend Micro Toolbar to enhance your security from cybercriminals who need to take your capabilities. Clients can then similarly convey Trend Micro Secret word Administrator in Pay Watchman Program to additional assurance that you simply use strong, mixed passwords while driving trades in your web-based records.
1 note
·
View note