#ESX Virtualization
Explore tagged Tumblr posts
Text
How Do You Secure Your Server from Malicious ESX Scripts?
Securing your server from malicious ESX scripts is essential in ensuring the safety and integrity of your data and services. ESX (Elastic Sky X) is a virtualization platform often used in server environments, enabling multiple virtual machines to run on a single host. While ESX provides great flexibility and efficiency, it can also be vulnerable to attacks, particularly through malicious scripts. These scripts, if not properly managed, can compromise the security of your server, lead to data breaches, or disrupt the smooth operation of your virtualized environment.
Here’s a detailed guide on how to secure your server from malicious esx scripts:

Keep Your System Updated
The first and most crucial step in securing your server is to keep your ESX host and all its components up to date. VMware frequently releases patches and updates to address security vulnerabilities, performance improvements, and bug fixes. Regularly check for updates and ensure that all patches are applied promptly. Neglecting these updates can leave your server open to exploitation from attackers using known vulnerabilities.
Use Secure Configurations
Another key to securing your ESX environment is ensuring that your server is configured securely. This includes configuring the ESXi firewall, disabling unnecessary services, and following VMware’s security best practices. By turning off unnecessary services, you limit the number of potential attack vectors. VMware provides a comprehensive security guide that outlines recommended configurations for hardening your ESX installation. Follow these guidelines to ensure your system is as secure as possible.
Enable ESX Host Firewall
The ESX firewall acts as a barrier between your server and any potential intrusions from malicious actors. Ensure that the firewall is configured properly to block unnecessary ports and only allow trusted traffic. Additionally, you can configure the firewall to log suspicious activity, providing valuable information in case of a security breach. Regularly review firewall logs to spot any unusual activity.
Control User Access and Privileges
One of the most common ways attackers gain access to ESX servers is through compromised user accounts or excessive privileges. Implement the principle of least privilege (POLP) by ensuring that users and administrators only have access to the resources they need. Limit access to critical system components and ensure that users cannot execute scripts unless absolutely necessary. Use role-based access controls (RBAC) to assign permissions based on job responsibilities. Moreover, regularly audit user accounts and remove any unused or inactive accounts to minimize potential vulnerabilities.
Monitor and Analyze Logs
Effective logging and monitoring are essential for identifying and responding to malicious activity quickly. Set up centralized logging for all ESX hosts and monitor these logs regularly for signs of abnormal behavior, such as unauthorized access attempts, failed login attempts, or unusual script executions. VMware vRealize Log Insight can help you manage and analyze logs efficiently, enabling you to spot malicious activity in real-time. Promptly investigate and address any suspicious log entries.
Scan for Malicious Scripts
Malicious ESX scripts are often introduced by attackers who exploit vulnerabilities in your environment. To prevent such threats, regularly scan your ESX server for suspicious scripts or files. Automated malware detection tools and anti-virus software can help detect and quarantine malicious files before they can cause damage. Ensure that any scripts running on your server are from trusted sources, and review them periodically to ensure they haven’t been tampered with.
Use Secure Boot and Trusted Execution
Secure boot is an essential security feature that prevents unauthorized firmware, bootloaders, and other malicious code from loading during the boot process. Ensure that secure boot is enabled on your ESX host, as it helps protect against rootkits and boot-time malware. Additionally, using trusted execution environments such as Intel TXT (Trusted Execution Technology) or AMD SEV (Secure Encrypted Virtualization) can further protect the integrity of your ESX server and its virtual machines from malicious scripts.
Use Virtual Machine Isolation
In environments where multiple virtual machines (VMs) are running on the same ESX host, it is essential to ensure proper isolation between VMs. This minimizes the risk of an attacker gaining access to other VMs via a compromised script. Configuring virtual machine isolation settings, such as enabling virtual machine lockdown mode and using a separate network for sensitive VMs, will significantly reduce the chance of a malicious script spreading across your environment.
Backup Regularly
Even with all the security measures in place, it’s always a good practice to have a reliable backup strategy in case of a breach. Regularly back up your ESX server and its virtual machines to secure, offsite storage. This ensures that if a malicious script causes system corruption or data loss, you can quickly restore your system to its previous state. Automate your backups and perform regular tests to ensure data integrity.
Conclusion
Securing your ESX server from malicious scripts requires a comprehensive approach that involves proactive monitoring, secure configurations, and regular updates. By following these best practices and maintaining a vigilant stance against potential threats, you can safeguard your virtualized environment from the damaging effects of malicious ESX scripts. Regular auditing, user privilege management, and the use of advanced security features like secure boot and trusted execution environments will further strengthen your defenses and help you maintain a secure, stable ESX server environment.
1 note
·
View note
Text
Virtual Machine Data Recovery Services | Fast & Secure
0 notes
Text
on Various hypervisors are available in the market with each system presenting unique features. As such, selecting an appropriate hypervisor for the desired purpose is a strenuous task. Of late two hypervisors, the Microsoft Hyper-V and VMware have outshined others in the market. However, the contemporary concern seeks to understand which software provides a better package. This scrip, hence, addresses this challenge by providing a comparative examination of the Hyper-V and VMware. An Overview In the earlier years, Microsoft has unveiled various host-staged virtualization systems; the company ventured into the hypervisor market in 2010 with the release of the Hyper-V. Similarly, VMware supplies numerous virtualization systems that are mainly host based. In the hypervisor market, the developer mainly offers two somewhat similar softwares, the ESX and ESXi (Finn & Lownds 23). The ESX is the company’s customary release and it entails the hypervisor and a developed management operation while ESXi is the firm’s latest release, and it is a hypervisor-only version. Integration structure Both the Hyper-V and ESXi do not demand an OS accompaniment since they connect directly on the hardware; however, their integration structure varies. The VMware has a direct driver structure where the application’s lines install on hardware, hence, linking the hardware and virtual gadgets servicing the server. As such, the structure incorporates the hardware drivers in the hypervisor. Similarly, the Hyper-V installs on the hardware but a structured application that propels the Window Server, directs all functions and hardware’s access. Considering this connection structure, the Hyper-V system is regarded to have an indirect driver structure (Finn & Lownds 134). Ease of management The simpler the structure of a hypervisor, the easer is its management. Management entails adopting and structuring hardware, installing virtual accompaniments, configuring the network among others. Software that incorporates and adjusts to these demands comfortably is easier to manage. The Hyper-V and the VMware incorporate and associateswith these structures in varying ways. The Hyper-V control entirely depends on a root partition plan done through a central Hyper-V manager. This plan is somewhat similar to other Microsoft management applications and demands little skills to launch. This tool, hence, controls basic virtual functions associated with the hardware. Importantly, an operator can control some hardware setups in the root partition using ordinary OS tools. Indeed, the tool is manageable remotely from a Vista system (Finn & Lownds 35). Notably, the Hyper-V manager system is capable of managing all virtual servers in the system concurrently and in an efficient manner. Tactically, using basic Microsoft devices provides the Hyper-V software with high degrees of flexibilities, hence, easing its management. The ESXi management is principally dependent on remote tools. The VI client and the Remote Command Line Interface (RCLI) are the two methods commonly used while configuring an ESXi host. The VI client is best suited for graphical configuration while remote line connection is ideal for line-based and scripted authentication. Read the full article
0 notes
Text
VM Data Recovery Services – Recover Lost Virtual Machine Data
Need to recover lost VM data? Our advanced virtual machine recovery solutions help restore deleted, corrupted, or formatted VM files efficiently.
0 notes
Text
When it comes time to deploy a platform for new projects, set up a CRM server, or build a data center fit for a standard hypervisor, every IT manager or storage administrator is faced with the question of which type of storage to use: traditional SAN appliance or virtual SAN? In this article, we'll take a look at two SAN solutions, distinguish between them, and give you an answer on which one to choose for your projects. Сontents What is the Storage Area Network (SAN)? When utilizing a typical SAN device? What are the usual costs of SAN appliances? What is a vSAN appliance? Use cases for virtual SAN (vSAN) devices When should you utilize a vSAN appliance? Cost of a virtual SAN (vSAN) device What is the difference between a regular SAN and vSAN? Which SAN to choose? Conclusion What is the Storage Area Network (SAN)? In essence, SANs are high-performance iSCSI or Fiber Channel block-mode physical datastores that may be used to host hypervisors, databases, and applications. Traditional Storage Area Network devices, which are generally available in a 4-bay tower to 36-bay rackmount configurations, offer high-performance storage space for structured applications using the iSCSI and/or Fiber Channel (FC) protocols. Structured workloads include the following: Databases: MySQL, Oracle, NoSQL, PostgreSQL, etc. Applications: SAP HANA or other major CRM or EHR software. Large deployments of standard hypervisors such as VMware ESX/ESXi, Microsoft Hyper-V, Windows Server Standard (or Datacenter) 2016/2019, KVM, Citrix (formerly XenServer), or StoneFly Persepolis For a better understanding of the difference between block storage and file storage, you can read this. When utilizing a typical SAN device? On-premises SAN systems are ideal for large deployments of critical applications with a low tolerance for delay. In addition to addressing latency problems, local SAN appliances offer you more control in terms of administration, operation, and security of physical devices, which is required by many regulating companies. With commensurate performance, SAN systems may scale from hundreds of gigabytes to petabytes of storage capacity. If your workloads have the ability to rise to this scale, on-premises SAN hardware is the superior alternative in terms of return on investment (ROI). That isn't to say that 4-bay towers or 6-bay devices aren't appropriate for SMB environments. It all comes down to the company budget, latency requirements, and the project(s) at hand. NetApp SAN, Voyager, Dell PowerVault, StoneFly ISC, and other on-premises SAN hardware are examples. What are the usual costs of SAN appliances? The level of cost of an on-premises SAN device is determined by the provider you choose, the OS you install, and, of course, the hardware specs you choose: system RAM, processor, network connections, RAID controller, hard drives, and other components are all important. Most vendors, including Dell, HPE, and NetApp, offer pre-configured products with limited customization options. As a consequence, you can find the price range on their web pages or in their catalogs. Other vendors let you customize your SAN hardware by selecting the characteristics that best meet your requirements. Before shipping you the plug-and-play appliance, they produce, test, and configure it. As a result, you could be given the qualities you desire within your budget. What is a vSAN appliance? Virtual SANs (vSANs) are iSCSI volumes that have been virtualized and installed on common hypervisors. Find out more here. The developer business VMware is responsible for popularizing the term vSAN in general. But VMware vSAN is not the only option provided. NetApp vSAN, StarWind vSAN, StoneFly vSAN, StorMagic vSAN, and others are examples of vSAN devices that are available. Use cases for virtual SAN (vSAN) devices Standard SAN and vSAN devices are similar in terms of use cases. The configuration is the sole variation between them. In other words,
vSAN equipment may be utilized for structured workloads just like classic SAN appliances (examples listed above). When should you utilize a vSAN appliance? The deployment of vSAN technology is very adaptable. A vSAN appliance can be installed locally, in the cloud, or on a distant server. This offers up a variety of applications; nevertheless, the flexible deployment has a number of drawbacks, including administration, cost, availability, latency, and so on. vSAN, depending on the vendor, promises scalable performance and a high return on investment when placed on local hyper-converged infrastructure (HCI), according to the supplier chosen (VMware vSAN is usually costly). Latency is a factor when using public clouds or distant servers. If it's in a nearby location, latency may not be an issue - as many companies who run their workloads entirely in the cloud have discovered. Furthermore, several business clients have relocated to the cloud before returning to on-premises. The causes differ from one situation to the next. Just because vSAN isn't working for someone else doesn't imply it probably wouldn't work for you. However, just because something works for others does not guarantee that it will perform for you. So, once again, your projects, finance, and performance and latency needs will determine whether or not a vSAN appliance is the best option for you. Cost of a virtual SAN (vSAN) device The cost of vSAN appliances varies depending on the manufacturer, deployment, and assigned resources such as system memory, CPU, and storage capacity. If vSAN is installed in the cloud, the price of the cloud, the frequency with which vSAN is installed, and the frequency with which it is used are all factors to consider. The budget of the infrastructure and hypervisor influences the ROI if it is put on an on-premises HCI appliance. What is the difference between a regular SAN and vSAN? Aside from the obvious difference that one product is a physical object and the other is a virtual version, there are a few other significant differences: Conventional SAN: To assign storage capacity for structured workloads, outside network-attached storage (NAS), or data storage volumes are required. If migration is required, it is often complicated and error-prone. This is permanent machinery. You can't expand processor power or system ram, but you can add storage arrays to grow storage. With an internal SAN, you won't have to worry about outbound bandwidth costs, server security, or latency issues. Virtual SAN: Provides a storage pool with accessible storage resources for virtual machines to share (VMs). When necessary, migration is relatively simple. Volumes in vSAN are adaptable. You may quickly add extra CPU, memory modules, or storage to dedicated resources. In a totally server-less setup, vSAN may be implemented in public clouds. Which SAN to choose? There is no common solution to this issue. Some operations or requirements are better served by standard SAN, whereas others are better served by vSAN. So, how can you know which is right for you? The first step is to have a better grasp of your project, performance needs, and budget. Obtaining testing results might also be beneficial. Consulting with professionals is another approach to ensure you've made the appropriate selection. Request demonstrations to learn more about the capabilities of the product you're considering and the return on your investment. Conclusion The question isn't which is superior when it comes to vSAN vs SAN. It's more about your needs and which one is ideal for your projects. Both solutions offer benefits and drawbacks. Traditional SANs are best suited for large-scale deployments, whereas vSANs offer better flexibility and deployment options, making them suitable for a wide range of use cases, enterprises, and industries.
0 notes
Link
0 notes
Text
Dell Transparent Snapshots Superior VMware VM Backup

Dell Transparent Snapshots
The size and complexity of modern virtualized environments have grown over the years, and traditional VMware virtual machine (VM) backup techniques have not been able to keep up with this. Transparent Snapshots a breakthrough in virtual machine backup and recovery were created by Dell Technologies in response to this expanding problem and are compatible with PowerProtect Data Manager.
VMware Transparent Snapshots
The Problems with Conventional VM Backup Techniques
Even if they work, traditional virtual machine backup techniques have always been problematic. ESG claims that businesses have had major challenges in upholding service-level agreements (SLAs) and performance as the number of virtual machines (VMs) has increased. These problems have been made worse by the complexity of IT environments, as many businesses now have to manage thousands of mission-critical virtual machines.
- Advertisement -
Agent-based techniques were the mainstay of virtual machine backups until the advent of VMware vSphere Storage APIs, also referred to as VMware APIs for Data Protection (VADP) and utilized for image-level protection for the previous fifteen years. The amount of data being generated and the importance of virtual machine workloads have surpassed these conventional approaches, even with this progress. As the environments became larger and more sophisticated, organizations were forced to make an unacceptable trade-off between meeting backup windows and compromising production performance.
Backup VMWare virtual machine
Transparent Snapshots: A Revolutionary Method for Virtualized Settings
Dell Technologies developed Transparent Snapshots, which are compatible with PowerProtect Data Manager, to directly address these issues. This innovation provides a no-compromise solution for virtual machine backup and recovery by utilizing an ESX VMware installable Bundle (VIB), certified by VMware by Broadcom.
Transparent Snapshots ensure uninterrupted backup performance, even for large-scale virtual machine settings, with up to 5 times faster backup times than previous methods. Additionally, recovery times can be slashed by up to 6×2, allowing businesses to promptly resume operations following an incident. Transparent Snapshots decrease the impact on virtual machine performance by collecting deltas directly within the ESX layer, resulting in a 5x reduction in VM latency.
By centralizing backup management into a single platform, PowerProtect Data Manager reduces the complexity of using various solutions and lowers infrastructure expenses. Additionally, Data Manager does away with the requirement for proxies and agents, enabling IT teams to manage virtual machines on an ESX host without being constrained by the quantity or expense of proxies they must install. The ability to automatically deploy the ESX VIB plugin frees IT teams from having to worry about manual configuration and lets them concentrate on more strategic duties.
- Advertisement -
Effect in the Real World
Transparent Snapshots also reclaim up to 10% of VMware storage, freeing up critical resources for other IT needs.” Transparent Snapshots dramatically decreased the amount of memory and storage utilized by small and medium-sized enterprises, even with 240 TB of data. In the example below, it cut the needed number of virtual machines (VMs) by 78 and the number of ESX servers by one, saving $60,000.Image credit to Dell
This can spare the resources of 12 ESX hosts, saving huge organizations with 1.5 PB of data and $720,000 in savings. These improvements result in less expensive and more environmentally friendly operations by consuming less electricity, floor space, and server hardware. You can scale your IT environment with confidence using Transparent Snapshots since you are optimizing both performance and cost.
Transparent Snapshots allow tighter SLAs, providing speedy application recovery and ensuring that data security keeps up with business needs. They can perform backups as frequently as once every hour. Granular-level recoveries are supported by the solution, enabling the restoration of individual VMs without affecting the environment as a whole.
Virtual Machine Backup
Transparent Snapshots: Virtual Machine Backup and Recovery’s Future
Transparent Snapshots significantly reduce costs associated with virtual machine backup. It recovers important resources and streamlines backup processes without sacrificing any quality.
The Broadcom integration between VMware and Dell significantly alters the way virtual machine backups are carried out. You can improve your IT operations and concentrate on fostering growth with Transparent Snapshots, secure in the knowledge that your backup solution is tailored to your requirements. This innovative technology offers unparalleled performance, streamlined operations, and substantial cost savings, making it the best option for safeguarding your virtual machines and optimizing the return on your IT investments.
Read more on govindhtech.com
#DellTransparent#SnapshotsSuperior#VMware#VMBackup#PowerProtectDataManager#data#DataManager#virtualmachines#VM#Snapshots#backupprocesses#TransparentSnapshots#technology#technews#news#govindhtech
0 notes
Text
Empowering Digital Transformation: How VMWare is Shaping the Future of IT Infrastructure

Introduction
VMWare stands as a beacon of innovation in the world of information technology. Since its inception, VMWare has revolutionized the way businesses manage their IT infrastructure, bringing virtualization to the forefront and enabling companies to operate with unparalleled efficiency and agility. This blog will explore how VMWare’s solutions are empowering businesses to transform digitally, stay ahead of the competition, and prepare for a future driven by technological advancements.
1. The Evolution of VMWare
VMWare began its journey in 1998 with a vision to simplify the complexities of IT environments through virtualization. The company’s first major breakthrough came in 1999 with the release of VMWare Workstation, a groundbreaking product that allowed multiple operating systems to run simultaneously on a single physical machine. This innovation marked the beginning of a new era in IT, where resources could be optimized and managed more effectively.
Over the years, VMWare has continued to push the boundaries of what’s possible in the IT world. In 2001, VMWare introduced ESX, a hypervisor that laid the foundation for the modern data center by enabling server consolidation and reducing hardware costs. This was followed by the launch of VMWare vSphere in 2009, a comprehensive suite of products that transformed server management and became the industry standard for virtualization.
VMWare’s ability to adapt to the evolving needs of the IT industry has been a key factor in its sustained success. As businesses increasingly moved towards cloud computing and hybrid environments, VMWare expanded its portfolio to include solutions for network virtualization, desktop virtualization, and cloud management. Today, VMWare is recognized as a leader in providing comprehensive, end-to-end solutions that drive digital transformation across various industries.
To know FAQs about VMWare, visit https://dinogeek.me/
2. Core Products and Solutions
At the heart of VMWare’s success are its core products, which have become essential tools for IT professionals around the world.
VMWare vSphere is the cornerstone of many modern data centers. As the most widely deployed virtualization platform, vSphere allows businesses to optimize their server resources, reduce downtime, and enhance security. One of the standout features of vSphere is its ability to enable live migration of virtual machines, ensuring business continuity even during maintenance periods. By centralizing and automating management tasks, vSphere frees up IT teams to focus on more strategic initiatives, making it an indispensable tool for organizations aiming to stay competitive in today’s fast-paced business environment.
VMWare NSX has redefined network security through its innovative approach to network virtualization. NSX allows businesses to create, snapshot, delete, and restore entire networks in software, effectively decoupling network services from the underlying hardware. This flexibility is a game-changer for IT departments, as it enables them to respond quickly to changing business needs. Moreover, NSX’s micro-segmentation capabilities allow for more granular security policies, reducing the attack surface and enhancing overall network security.
VMWare Horizon is another key product that has gained prominence, especially in the era of remote work. Horizon provides a secure, virtual desktop infrastructure (VDI) that enables employees to access their work environments from anywhere, on any device. This has proven to be crucial for businesses looking to maintain productivity and continuity in the face of global challenges such as the COVID-19 pandemic. Horizon’s ability to deliver a consistent and seamless user experience, regardless of the user’s location, has made it a popular choice for organizations prioritizing flexibility and security.
3. VMWare’s Role in Digital Transformation
In today’s digital age, businesses must constantly evolve to remain competitive. VMWare plays a pivotal role in this evolution by providing the tools and technologies needed to embrace digital transformation. Virtualization, the cornerstone of VMWare’s offerings, is fundamental to modern IT environments. By decoupling hardware and software, VMWare enables businesses to create flexible, scalable, and cost-effective IT infrastructures.
One of the key benefits of virtualization is its ability to support cloud computing. VMWare’s solutions are integral to the success of private, public, and hybrid cloud environments. By enabling businesses to seamlessly manage and migrate workloads between on-premises data centers and cloud platforms, VMWare facilitates a smooth transition to the cloud, ensuring that businesses can take full advantage of the scalability and cost savings it offers.
Moreover, VMWare’s solutions are designed to enhance business agility. In a rapidly changing business landscape, the ability to quickly adapt to new opportunities and challenges is critical. VMWare’s software-defined data centers (SDDC) allow businesses to rapidly deploy new applications and services, scale resources as needed, and maintain high levels of availability and security.
Real-world examples of companies that have successfully transformed their operations with VMWare’s solutions abound. From global enterprises to small businesses, organizations across various industries have leveraged VMWare to enhance their IT capabilities, reduce costs, and improve their overall business performance.
4. Innovation and Future Prospects
Innovation has always been at the core of VMWare’s strategy. As the IT landscape continues to evolve, VMWare remains committed to pushing the boundaries of what’s possible. One of the most exciting areas of innovation for VMWare is its work in artificial intelligence (AI) and machine learning (ML). By integrating AI and ML into its products, VMWare is helping businesses automate complex tasks, gain deeper insights from their data, and improve decision-making processes.
Another area where VMWare is making significant strides is edge computing. As more devices become connected to the internet, the need for real-time data processing at the edge of the network is becoming increasingly important. VMWare’s edge computing solutions enable businesses to process and analyze data closer to where it’s generated, reducing latency and improving the performance of critical applications.
Looking ahead, VMWare is well-positioned to continue leading the IT industry in innovation. With a strong focus on emerging technologies and a commitment to addressing the evolving needs of businesses, VMWare is set to play a key role in shaping the future of IT infrastructure.
5. The Impact of VMWare on Business Efficiency
One of the most significant benefits of VMWare’s solutions is the impact they have on business efficiency. By streamlining IT operations and reducing the complexity of managing infrastructure, VMWare helps businesses save time and money. For example, VMWare’s virtualization technologies enable server consolidation, reducing the need for physical hardware and lowering energy costs. Additionally, the automation capabilities built into VMWare’s products allow IT teams to automate routine tasks, freeing up time for more strategic initiatives.
Moreover, VMWare’s solutions enhance productivity by enabling seamless integration across different platforms and environments. Whether it’s connecting on-premises systems with cloud services or ensuring that applications run smoothly across different devices, VMWare provides the tools needed to create a cohesive and efficient IT environment.
Businesses that have adopted VMWare’s solutions often report significant improvements in their overall efficiency. By reducing downtime, improving resource utilization, and enabling faster deployment of new services, VMWare helps businesses operate more effectively and respond quickly to changing market conditions.
6. VMWare and Sustainability
In addition to driving business efficiency, VMWare is also committed to promoting sustainability in the IT industry. Virtualization, by its very nature, contributes to reducing the environmental impact of IT operations. By consolidating workloads onto fewer physical servers, VMWare’s solutions help businesses reduce their energy consumption and carbon footprint.
Furthermore, VMWare has implemented several initiatives aimed at promoting sustainable IT practices. The company has set ambitious goals for reducing its own environmental impact and is actively working with customers to help them achieve their sustainability objectives. Through its commitment to green IT, VMWare is playing a crucial role in helping businesses balance their need for technological advancement with their responsibility to protect the environment.
Conclusion
VMWare has established itself as a leader in the IT industry by consistently delivering innovative solutions that drive digital transformation, enhance business efficiency, and promote sustainability. As businesses continue to navigate the challenges of the digital age, VMWare’s products and services will remain indispensable tools for achieving success. Whether you’re looking to optimize your IT infrastructure, embrace cloud computing, or improve your network security, VMWare offers the solutions you need to thrive in today’s competitive landscape.
0 notes
Text
Efficient Virtual Machine Data Recovery: Tips and Tricks to Safeguard Your Virtual Environment!
0 notes
Text

#techchef#technology#data recovery services#techchef data recovery#data loss#Virtual Machine Data Recovery#Data Recovery
0 notes
Link
0 notes
Text
Expert Virtual Machine Data Recovery - Fast & Reliable
0 notes
Text
For instance, the WebSphere and the vSphere are online software hypervisors. Question 24: Yes. This is because NAS has more efficient security measures like login shares; it can be accessed by multiple operating systems. Backups are efficient and NAS has an independent file management system.Question 25: The best disaster recovery for VMware is by making use of back-up process on the servers and replication of virtual machines in the network. This can be best deployed using storage where NAS is deployed for VMs and Servers in the network (Muller 123). Question 26: vMotion works by encapsulating VMs on shared storage and then the enclustered VMs allow multiple installations on an ESX server. The memory and execution state of the VMs is transferred to high speed network. This is done by copying memory and system states of the ESX server. To allow identity of the VMs, networks used by the VMs are also virtualized by the ESX server (Wolf 84). This transfer (vMotion) takes very few seconds. Question 27: A snapshot presents a complete copy of a virtual machine at any time and all the changes made. While a clone is the exact copy of the virtual machine during the cloning process. Any changes made on the parent of the clone are not reflected in the clone. Therefore using snapshots provide better functionality than clones. Question 28: Fault Tolerance in VMware works through the use of a technique known as Record/Reply. This technique provides continuous availability to the virtual machine in case the host fails. This works whereby if a VM goes down it is restarted in another host and the secondary host now becomes the primary host while a secondary host is being looked for (Muller 98). Works CitedMuller, Al, Seburn, Wilson and Don Happe. Virtualization with VMware ESX Server. Boston, MA: Routledge, 2005. Print.Wolf, Chris and Erick Halter. Virtualization: From the Desktop to the Enterprise: Volume 1. New York, NY: John Wiley and Sons, 2008. Print. Read the full article
0 notes
Text
30 Inspirational Quotes About Virtual Laptop
Finding a really good Deal on a laptop computer For Virtualization If you're searching for information regarding how to buy a laptop for virtualization in that case , you've arrived at the correct location! In this article I'm going to present you with a lot of insight about what virtualization laptop offer you and the way in which you can get it. So, just keep checking! In this post, we're going to talk about some Virtualization Laptop Tips in addition to Virtualization Technology Overview. By the time you've completed checking out this report, I believe you will have a better idea on what kind of laptop for virtualization would be best for the needs of yours.

Therefore, what is virtualization? Virtualization primarily describes the action of running and crafting virtual machines upon a primary computer system, generally referred to as a virtual machine. The virtualization process generally requires the utilization of a program tool which makes it possible for a person to run multiple virtual environments on the same machine - and on a lot of printers if you are on a tight budget. This process allows users to operate their applications and programs in isolated locations that are specific to their needs.
These days that we have identified what virtualization is, we should discuss several of the laptop computers that are out there for it. Typically, when somebody mentions virtualization they're discussing cloud computing needs. I am sure you have heard about the power of the cloud, and many consumers are experiencing this by utilizing such computing resources like Amazon's cloud. A virtualization notebook computer is an off-the-shelf, common laptop that is fashioned with virtualization in mind.
youtube
When looking for the best laptops with virtualization abilities, it is vital that you think about the software programs your typical user will probably be consuming most. Preferably, these should be simple to operate and utilize, though the simple truth is some applications just simply run much better in a virtual environment. For example, a few internet applications merely are not in a position to function effectively in a virtual setting. And so, it's frequently a wise decision to buy the laptop with probably the most powerful processor, RAM, graphics card, hard drive, etc. In cases which are many, the ideal laptop for you is dependent upon the programs you use the foremost and there is certain to be a laptop computer available for you.
For those of you comfortable with VMWare ESX Server, you're most likely fairly familiar with the vm's function. Virtual Machines provide the foundation for virtualization: the capability to manage several os inside of the same operating system. With https://jozilla.net/best-laptop-for-virtualization/ VMWare ESX Server, you can quickly work several virtual desktops, workstations, other applications and servers across several OS levels. Lots of people are not alert to just how highly effective vms are, along with this's precisely why they often choose a virtualization based alternative over traditional VMWare solutions.
As pointed out, among the most popular uses for VMWare ESX Server is for virtualizing laptop computers. The power to utilize the exact same os on both the server and the laptop permits seamless mobility and easy to use, particularly for internet business users whose job requires them to be mobile. If you're seeking to buy a laptop computer for virtualization applications, you'll wish to find one with no less than 4GB of RAM and a separate Intel processor. Even though they differ significantly in specification, you should be able to find a notebook computer that operates seamlessly in both virtual locations and with your current operating system.
So, what about locating a laptop computer for virtualization? There are plenty of superb options, along with some of the newer and more costly portable laptops such as the HP pavilion eCP or maybe IBM's very own Personal Web Server. But, Amazon has regularly demonstrated to be a terrific company for sound technology. The hottest addition to Amazon's transportable laptop computer offerings is the HP pavilion eCP, that has received reviews that are good from both reviewers and customers. For each one of these reasons, it is easy to discover why an Amazon laptop computer for virtualization produces so much sense.
In short, there are plenty of reasons to buy a laptop for virtualization. Should you need portability but do not have the space or power essential to get a full-fledged machine, consider an Amazon laptop. In case you already have a desktop and would want to take it with you, a USB type-I card can make room having a larger laptop without in need of extra storage space. In case you want the security and reliability of your own pc but don't keep money for that, try a USB type c based virtualization solution.
1 note
·
View note
Text
Crack Fortigate Vm64

Sep 01, 2019 FortiGate VM software is available for 32-bit and 64-bit environments. Both an upgrade version for existing FortiGate VMs and a “greenfield” version are available. We will use the second solution, available as a downloadable zip archive file (the one we will use is a 64-bit version, FGTVM64-v500-build0228-FORTINET.out.ovf.zip). Crack Fortigate Vm64 Sun Type 7 Usb Keyboard With Windows 10 Wifidog Do Wrt Cable Spinet Piano Serial 419416 Mac Os 10.13 Driver For Brother Hl-1440 Hip Hop Acapellas Office 365 Forward Email To External Address Virtual Villagers Origins 2 Error02-0 License Key Reaper V5.965.
Fortigate Vm64 Crack
Crack Fortigate Vm64 Key
Crack Fortigate Vm64 3
If you have a registered Fortinet product (any one should do) and have a valid login ID on the support.fortinet.com site, you should be able to download any of the VM images (via the download link). Another option would be to fill out this online form. Oct 31, 2014 If you have a registered Fortinet product (any one should do) and have a valid login ID on the support.fortinet.com site, you should be able to download any of the VM images (via the download link). Another option would be to fill out this online form.
FortiGate virtual appliances allow you to provision Fortinet security inside a virtual environment. All the security and networking features we would expect in a hardware-based FortiGate are available in the VM too. FortiGate VM software is available for 32-bit and 64-bit environments.
Gateway drivers for windows 7. Both an upgrade version for existing FortiGate VMs and a “greenfield” version are available. We will use the second solution, available as a downloadable zip archive file (the one we will use is a 64-bit version, FGT_VM64-v500-build0228-FORTINET.out.ovf.zip). Note: it is required to have at least an access as a customer to the Fortinet support to be able to receive and use the aforementioned files.
Here we will discuss on Fortigate (Fortigen Virtual FortiOS Apliance) Necessary downloads After download, simply extract the file and open the fortigate.vmx file in VMware. Immediately after, it will be reflected on VMware window. Do not forget to change some initial setting before you fire up the Fortigate. Do a little changes here in memory settings to optimize the hardware of your PC. Set the memory requirement 512MB.
Now do some changes in Virtual Network Adapter settings as compatible to your topology. Here I made my own topology bellow and dis the post changes in VM Network Adapters. More about Virtual Netowrk and Sharing [showhide type=”post” more_text=”show more>>>” less_text=” Port-1>Internal Network>Subnet 192.168.0.0/24 Vmnet8>Port-2>Internet>Subnet 192.168.137.0/24 Now time to turn on the Fortigate VM. A cli console will come up with login prompt ( username: admin password: N/A) Now everything is ready, time to do initial configuration. Have a look at the topology once again VMnet0>Port-1>Internal Network>Subnet 192.168.0.0/24 Vmnet8>Port-2>Internet>Subnet 192.168.137.0/24 Configurations Fortigate-VM login: admin Password: Welcome! Fortigate-VM # config system interface Fortigate-VM (interface) # edit port1 Fortigate-VM (port1) # set ip 192.168.0.30 255.255.255.0 Fortigate-VM (port2) # set allowaccess http https fgmp ssh telnet ping Fortigate-VM (port1) # end Fortigate-VM # config system interface Fortigate-VM (interface) # edit port2 Fortigate-VM (port2) # set ip 192.168.137.30 255.255.255.0 Fortigate-VM (port2) # Fortigate-VM (port2) # set allowaccess http https ping Fortigate-VM (port2) # end Fortigate-VM (port2) # Now we are finished with configuration.
Time to open the Fortinet VM web console. Open the IP() is browser. A login prompt will open then, type their only username(username: admin), then login. The VM GUI console will come up then. Now time to play with Fortigate. The detailed discussions on policy, access control, NAT, load balancing on Fortigate will be posted soon. Related articles across the web • • •.
Developer: Cyberlink Release Date: February 13, 2013 Crack Type: Patch Size: 843MB PLATFORM: Windows All Install instructions: 1.Unpack & Install 2. Install update by running 'CL.2418_GM4_Patch_VDE121106-01.exe' in 'Update' folder. Power director 10 free download. Uncheck 'remind me later' box and skip registration page 3. It marries great video editing features with other powerful tools such as photo editing and sound mastering.
The following topics are included in this section:
FortiGate VM models and licensing
Registering FortiGate VM with Customer Service & Support
Downloading the FortiGate VM deployment package
Deployment package contents
Deploying the FortiGate VM appliance
FortiGate VM models and licensing
Fortinet offers the FortiGate VM in five virtual appliance models determined by license. When configuring your FortiGate VM, be sure to configure hardware settings within the ranges outlined below. Contact your Fortinet Authorized Reseller for more information.
FortiGate VM model information
Technical SpecificationFG-VM00FG-VM01FG-VM02FG-VM04FG-VM08Virtual CPUs (min / max)1 / 11 / 11 / 21 / 41 / 8Virtual Network
Interfaces (min / max)
2 / 10Virtual Memory (min / max)1GB / 1GB1GB / 2GB1GB / 4GB1GB / 6GB1GB /12GBVirtual Storage (min / max)32GB / 2TBManaged Wireless APs (tunnel mode / global)32 / 3232 / 64256 / 512256 / 5121024 / 4096Virtual Domains (default / max)1 / 110 / 1010 / 2510 / 5010 / 250
After placing an order for FortiGate VM, a license registration code is sent to the email address used on the order form. Use the registration number provided to register the FortiGate VM with Customer Service & Support and then download the license file. Once the license file is uploaded to the FortiGate VM and validated, your FortiGate VM appliance is fully functional.
10
FortiGate VM Overview Registering FortiGate VM with Customer Service & Support
The number of Virtual Network Interfaces is not solely dependent on the FortiGate VM. Some virtual environments have their own limitations on the number of interfaces allowed. As an example, if you go to https://docs.microsoft.com/en-us/azure/virtualnetwork/virtual-networks-multiple-nics, you will find that Azure has its own restrictions for VMs, depending on the type of deployment or even the size of the VM.
FortiGate VM evaluation license
FortiGate VM includes a limited embedded 15-day trial license that supports: l 1 CPU maximum l 1024 MB memory maximum
l low encryption only (no HTTPS administrative access) l all features except FortiGuard updates
You cannot upgrade the firmware, doing so will lock the Web-based Manager until a license is uploaded. Technical support is not included. The trial period begins the first time you start FortiGate VM. After the trial license expires, functionality is disabled until you upload a license file.
Registering FortiGate VM with Customer Service & Support
To obtain the FortiGate VM license file you must first register your FortiGate VM with CustomerService& Support.
To register your FortiGate VM:
Log in to the Customer Service & Support portal using an existing support account or select Sign Up to create a new account.
In the main page, under Asset, select Register/Renew.
The Registration page opens.
Enter the registration code that was emailed to you and select Register. A registration form will display.
After completing the form, a registration acknowledgement page will appear.
Select the License File Download
You will be prompted to save the license file (.lic) to your local computer. See “Upload the license file” for instructions on uploading the license file to your FortiGate VM via the Web-based Manager.
Downloading the FortiGate VM deployment package
FortiGate VM deployment packages are included with FortiGate firmware images on the CustomerService& Support site. First, see the following table to determine the appropriate VM deployment package for your VM platform.
Downloading the FortiGate VM deployment package
Selecting the correct FortiGate VM deployment package for your VM platform
VM PlatformFortiGate VM Deployment FileCitrix XenServer v5.6sp2, 6.0 and laterFGT_VM64-v500-buildnnnn-FORTINET. out.CitrixXen.zipOpenXen v3.4.3, 4.1FGT_VM64-v500-buildnnnn-FORTINET.
out.OpenXen.zip
Microsoft Hyper-V Server 2008R2 and 2012FGT_VM64-v500-buildnnnn-FORTINET. out.hyperv.zipKVM (qemu 0.12.1)FGT_VM64-v500-buildnnnn-FORTINET.
out.kvm.zip
VMware ESX 4.0, 4.1
ESXi 4.0/4.1/5.0/5.1/5.5
FGT_VM32-v500-buildnnnn-FORTINET.
out.ovf.zip (32-bit)
FGT_VM64-v500-buildnnnn-FORTINET. out.ovf.zip
For more information see the FortiGate product datasheet available on the Fortinet web site, http://www.fortinet.com/products/fortigate/virtualappliances.html.
The firmware images FTP directory is organized by firmware version, major release, and patch release. The firmware images in the directories follow a specific naming convention and each firmware image is specific to the device model. For example, the FGT_VM32-v500-build0151-FORTINET.out.ovf.zip image found in the v5.0 Patch Release 2 directory is specific to the FortiGate VM 32-bit environment.
You can also download the FortiOS Release Notes, FORTINET-FORTIGATE MIB file, FSSO images, and SSL VPN client in this directory. The Fortinet Core MIB file is located in the main FortiGate v5.00 directory.
To download the FortiGate VM deployment package:
In the main page of the Customer Service & Support site, select Download > Firmware Images.
The Firmware Images page opens.
In the Firmware Images page, select FortiGate.
Browse to the appropriate directory on the FTP site for the version that you would like to download.
Download the appropriate .zip file for your VM server platform.
You can also download the FortiGate Release Notes.
Extract the contents of the deployment package to a new file folder.
FortiGate VM Overview Deployment package contents
Deployment package contents
Citrix XenServer
The FORTINET.out.CitrixXen.zip file contains:
vhd: the FortiGate VM system hard disk in VHD format l fortios.xva: binary file containing virtual hardware configuration settings l in the ovf folder:
FortiGate-VM64.ovf: Open Virtualization Format (OVF) template file, containing virtual hardware settings for
Xen l fortios.vmdk: the FortiGate VM system hard disk in VMDK format l datadrive.vmdk: the FortiGate VM log disk in VMDK format
The ovf folder and its contents is an alternative method of installation to the .xva and VHD disk image.
OpenXEN
The FORTINET.out.OpenXen.zip file contains only fortios.qcow2, the FortiGate VM system hard disk in qcow2 format. You will need to manually:
l create a 32GB log disk l specify the virtual hardware settings
Microsoft Hyper-V
The FORTINET.out.hyperv.zip file contains:
in the Virtual Hard Disks folder:
vhd: the FortiGate VM system hard disk in VHD format l DATADRIVE.vhd: the FortiGate VM log disk in VHD format
In the Virtual Machines folder:
xml: XML file containing virtual hardware configuration settings for Hyper-V. This is compatible with Windows Server 2012.
Snapshots folder: optionally, Hyper-V stores snapshots of the FortiGate VM state here
KVM
The FORTINET.out.kvm.zip contains only fortios.qcow2, the FortiGate VM system hard disk in qcow2 format. You will need to manually:
l create a 32GB log disk l specify the virtual hardware settings
VMware ESX/ESXi
You will need to create a 32GB log disk.
Deploying the FortiGate VM appliance
The FORTINET.out.ovf.zip file contains:
vmdk: the FortiGate VM system hard disk in VMDK format l datadrive.vmdk: the FortiGate VM log disk in VMDK format l Open Virtualization Format (OVF) template files:
FortiGate-VM64.ovf: OVF template based on Intel e1000 NIC driver l FortiGate-VM64.hw04.ovf: OVF template file for older (v3.5) VMware ESX server l FortiGate-VMxx.hw07_vmxnet2.ovf: OVF template file for VMware vmxnet2 driver l FortiGate-VMxx.hw07_vmxnet3.ovf: OVF template file for VMware vmxnet3 driver
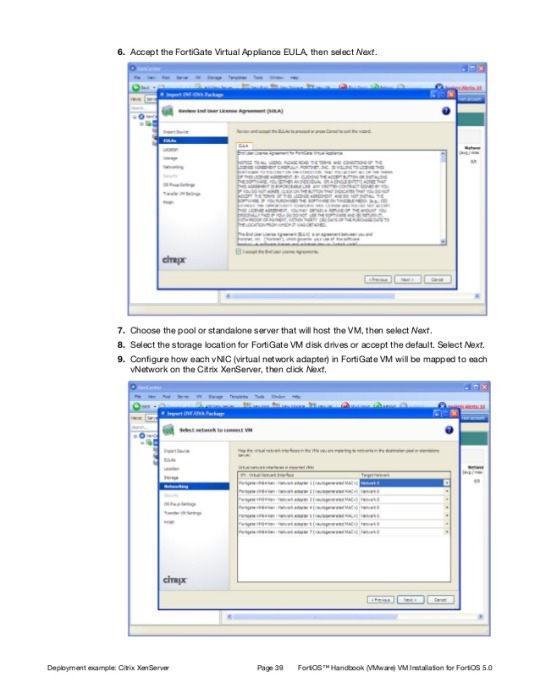
Deploying the FortiGate VM appliance
Prior to deploying the FortiGate VM appliance, the VM platform must be installed and configured so that it is ready to create virtual machines. The installation instructions for FortiGate VM assume that
You are familiar with the management software and terminology of your VM platform.
An Internet connection is available for FortiGate VM to contact FortiGuard to validate its license or, for closed environments, a FortiManager can be contacted to validate the FortiGate VM license. See “Validate the FortiGate VM license with FortiManager”.
For assistance in deploying FortiGate VM, refer to the deployment chapter in this guide that corresponds to your VMware environment. You might also need to refer to the documentation provided with your VM server. The deployment chapters are presented as examples because for any particular VM server there are multiple ways to create a virtual machine. There are command line tools, APIs, and even alternative graphical user interface tools.
Before you start your FortiGate VM appliance for the first time, you might need to adjust virtual disk sizes and networking settings. The first time you start FortiGate VM, you will have access only through the console window of your VM server environment. After you configure one FortiGate network interface with an IP address and administrative access, you can access the FortiGate VM web-based manager.
After deployment and license validation, you can upgrade your FortiGate VM appliance’s firmware by downloading either FGT_VM32-v500-buildnnnn-FORTINET.out (32-bit) or FGT_VM64-v500-buildnnnnFORTINET.out (64-bit) firmware. Firmware upgrading on a VM is very similar to upgrading firmware on a hardware FortiGate unit.
Fortigate Vm64 Crack
Having trouble configuring your Fortinet hardware or have some questions you need answered? Check Out The Fortinet Guru Youtube Channel! Want someone else to deal with it for you? Get some consulting from Fortinet GURU!
Crack Fortigate Vm64 Key
Crack Fortigate Vm64 3
Don't Forget To visit the YouTube Channel for the latest Fortinet Training Videos and Question / Answer sessions! - FortinetGuru YouTube Channel - FortiSwitch Training Videos

1 note
·
View note