#Filter Appointments from Exchange Server
Explore tagged Tumblr posts
Text
How the MBOX to PST Conversion Tool Improves Workflow
In the modern digital workspace, the ability to efficiently manage and migrate email data is essential. With professionals often needing to switch between different email clients, converting file formats becomes part of daily operations. MBOX and PST are two of the most common email storage formats, but they are typically associated with different email platforms. MBOX is often used by open-source clients, while PST is native to Microsoft Outlook. The MBOX to PST conversion tool bridges the gap, enhancing productivity, ensuring data consistency, and saving valuable time.
Streamlined Migration Between Email Clients
One of the primary benefits of using an MBOX to PST conversion tool is seamless migration between email clients. Many users transition from MBOX-supported applications to Outlook for better integration with office tools or corporate environments. Manually migrating data is often complicated, risky, and time-consuming. However, a specialized conversion tool automates this process, eliminating technical barriers. This not only ensures that all messages, attachments, and metadata are accurately transferred but also reduces downtime, allowing professionals to resume work immediately after migration.
Preservation of Data Integrity
Maintaining the integrity of email data during migration is critical. Without the right tools, there is a risk of data corruption, missing attachments, or loss of formatting. The MBOX to PST conversion tool is designed to safeguard the structure and content of every email. Folder hierarchies, embedded files, and date-time stamps are preserved throughout the process. This ensures that no important information is lost, which is vital for professionals handling sensitive communications or legal documentation. The result is a complete and reliable archive that mirrors the original source.
Improved Accessibility and Organization
Switching to PST format provides users with advanced organizational capabilities. Microsoft Outlook, the default application for PST files, offers robust features like search filters, calendar integration, tagging, and categorization. When MBOX files are converted into PST, users can take full advantage of these features. This makes it easier to locate specific messages, manage appointments, and streamline daily communication tasks. With a more intuitive interface and better data organization, teams can work more efficiently and avoid the frustration of sifting through cluttered inboxes.
Enhanced Security and Compatibility
The conversion from MBOX to PST also enhances email security and compatibility within enterprise environments. PST files integrate well with Microsoft 365 and Exchange servers, offering built-in encryption, access control, and cloud backup features. This allows IT departments to enforce compliance policies, implement security protocols, and provide reliable access to archived emails. The conversion tool helps ensure that organizations can securely transition their communication data while maintaining compatibility with enterprise-grade infrastructure.
Saves Time and Reduces Errors
Manually exporting and importing email messages can be error-prone and labor-intensive. A dedicated MBOX to PST conversion tool eliminates these issues by automating complex steps. Users do not need advanced technical knowledge to carry out the migration. Most tools come with user-friendly interfaces and batch conversion features that can handle multiple files at once. This drastically reduces the time spent on administrative tasks, allowing IT professionals and end-users alike to focus on more strategic initiatives.
The MBOX to PST conversion tool plays a pivotal role in optimizing workflow efficiency across various sectors. By offering accurate data transfer, improved email management, and better integration with Outlook, this tool simplifies what would otherwise be a challenging process. Whether for personal use or enterprise-level migrations, the tool ensures that users can adapt to evolving email environments with confidence and ease.
0 notes
Text
Microsoft Outlook For Mac Free Download 2010

Along with the rise of the internet's popularity, emailing has become a common practice of both personal and professional communications. Outlook is just one of the manyemail service providers available in the market.
Outlookis Microsoft's email child, available for both PC and Mac users through its web app or software. Much like its competitors, this application offers all the tools needed to compose, send, and receive emails. Here's a detailed rundown of all of Outlook's features and performance.
Ample features and email experience
Outlook offers the basic function of sending and receiving emails just as much as its competition. What sets it apart are the many features that make your email experience even better.
Outlook is Microsoft's email server for Office 365. You can get it with the complete office suite or access it online. It offers the basic function of sending and receiving emails just as much as its competition. What sets it apart are the many features that make your email experience even better.


Get the most up-to-date version of Outlook and enjoy email, calendar, and contacts in one place. Upgrade to Microsoft 365 today. Create Groups to discuss, collaborate, and share files and notes with others. Use Skype for Business voice and video calls for real-time decisions. Improved conversation. Microsoft Outlook for Android helps millions of users connect all their email accounts, calendars and files in one convenient spot. With intelligent email, calendar reminders and contacts, Outlook for Android lets you do more from one powerful inbox. Email friends, family and colleagues from multiple accounts on one app and see what matters most first with the Focused inbox that keeps the. Outlook 2010 free download - Microsoft Outlook Express, MSG Viewer for Outlook, Microsoft Outlook 2019, and many more programs.
There are two types of rules in Outlook for Mac: server rules and client rules. Server rules If you are using a Microsoft Exchange account managed by Microsoft Exchange Server 2010 SP1 or later, you can use Outlook for Mac to create and edit server-based rules.In the Rules box of Outlook for Mac, server rules are grouped by account under Server Rules in the left pane. Microsoft outlook 2010 free download - Microsoft Outlook Express, Microsoft Outlook 2019, Microsoft Office 2011, and many more programs.
Overview of Outlook
At first glance, Outlook is like any other email suite: simple design, straightforward look. You cancompose emails in rich text and bold, highlight, underline your message however you want. Format your emails easily with tools available to insert tables, links, lists, and change font colors in one neatly arranged toolbar.
When opening emails, Outlook shows a new tab to view the entire message on the app itself. Use its Immersive Reader feature to see the email in full screen or preview photo attachments in a slideshow before deciding which one to download or save.
Keeping you organized
Outlook keeps things organized by providing you several options to sort your emails. Why get lost thru labels when you can create folders to classify emails as you see fit? You can alsoplace tags to easily categorize emails accordingly.
Its search feature is but another feature that distinguishes Outlook from other email providers. You can filter emails by file size, making it easier to offload unnecessary emails and avoid exceeding the memory limit.

Outlook products
While this email application comes with Microsoft Office 365, users can still get an Outlook account by signing up on their website. You'll get 15GB worth of email storage space the same as any other email service provider on the web. If you download the Outlook app, you can get a whopping 50 GB worth of storage great for sending and receiving emails with large file attachments.

Apart from the email suite, Outlook also comes with Microsoft's Calendar application to help you easily schedule meetings and appointments. This application notifies you ahead of your sessions so that you are in the loop, always. Outlook also helps you manage contacts using the People application.
Where can you run this program?
Outlook runs on several devices, including Windows and Mac computers. Its web-based application allows you to access your email even on others' desktops. This email suite also offers apps supported by both Android and iOS devices so that you can manage your inbox on the go using your smartphone or your iPad. Finally, this popular Microsoft program can be downloaded on Windows Mobile or integrated into numerous business systems and applications, including Skype, Evernote, Paypal, Yelp, and many more. Truly ideal for any type of user.
Is there a better alternative?
There are plenty of alternative global communications software to Outlook. If you need to use an email suite mostly for personal use, Google's Gmail is a good choice. It's free and can be accessed through any web browser or its app on Android and iOS. It also offers the same amount of storage as that of the free Outlook account, allowing messages with up to 50 MB of file attachments.
For company and business use, Workplace by Facebook is another effective communication tool that gives a more instant experience. It's a somewhat spitting image of the social media website, except for the fact that it's a central communication hub for staff and managers to use in their day-to-day work.
Download Microsoft Outlook 2010 Full
Our take
From the looks of it, Outlook is definitely worth giving a shot. The best features include classifying emails by folders and tags, as well as sorting out email through file size. Speed and performance will not be a problem for those using the desktop version, and the interface is clear and easy to understand.
Should you download it?
Yes. Microsoft's Outlook is packed with so many features that cannot be found in other email clients in the market. While you will have to shell out a little more in order to get all its features, it will definitely be worth the investment. So, if you're a fan of keeping your inbox organized and personalized, then Outlook is the tool for you.
Install Microsoft Outlook 2013 Free
2010

1 note
·
View note
Text
Filter Appointments from Exchange Server & Enhanced Word File Attachment in Outlook using Java
What’s new in this release?
Aspose team is pleased to announce the new release of Aspose.Email for Java 17.10.0. Ported from its equivalent .NET version, this month’s release includes enhancement of filtering appointments from Exchange Server using EWS client of the API. It also includes several bug fixes which further improve the overall API functionality. This release of Aspose.Email for Java introduces the capability of filtering appointments from Exchange Sever using its IEWSClient. Appointments can be filtered from Exchange server using the IEWSClient of the API with the help of ExchangeQueryBuilder. Appointments can be filtered from server by Date or Recurrence. The following code snippets show filtering appointments from Exchange server using this new feature. This month’s release also includes several bug fixes that further add to the overall stability of the API. In addition, since the API is ported from its equivalent .NET version, it also includes all those fixes which were part of the .NET version. Detailed information about the fixes can be found in the release notes section of the API documentation. The main improved features & bug fixes added in this release are listed below
Possibility of retrieving appointments with recurrences and dates filters
EWSClient.GetMailboxSize behaviour
Attachment name jibbrish on Non-Japanese Windows
EWS client can't load emails in folders containing large number of messages.
MapiMessage.BodyHtml does not return correct value
Attached Word document in Outlook message is corrupted on Save
Multi-octet character split across adjacent encoded-word with UTF8 encoding
Mht empty when converting from msg with SkipInlineImages = true
Duplicated recipients when saving EML as MHTML
Content-disposition filename duplicated
Merging PST with sample PST loses Properties of Calendar
Creating message body from HTML includes header information in output
Converting EML to HTML resulting in incorrect HTML
After EML file is opened and re-saved, in output EML file From and Sender are null
Calendar added to PST doesn't open in MS Outlook
Issues while using Aspose.Email.dll as COM
Wrong attachment name read by API
ImapClient.ListFodlers gives Timeout with Yahoo Mail
Start and End Date same for full day event
Some characters garbled while conversion from EMLX to EML
Other most recent bug fixes are also included in this release.
Newly added documentation pages and articles
Some new tips and articles have now been added into Aspose.Email for Java documentation that may guide users briefly how to use Aspose.Email for performing different tasks like the followings.
Filter Appointments from Exchange Server
Support for Email Tracking
Overview:Aspose.Email for Java
Aspose.Email for Java is a Non-Graphical Java component that enables Java applications to read and write Microsoft Outlook documents without utilizing Microsoft Outlook. It enables developers to create new MSG file from scratch, update an existing MSG file, read Outlook MSG file & get it's properties like subject, body, recipients in to, cc and bcc, Adding or removing attachment, sender information and MAPI properties. Aspose.Email for Java can be used with Web as well asDesktop Application.
More about Aspose.Email for Java
Homepage of Oulook component Aspose.Email for Java
Download Aspose.Email for Java
Online documentation of Aspose.Email for Java
#Filter Appointments from Exchange Server#Filter Appointments by Date#Filter appointments by Recurrence#saving EML as MHTML#Java email API#Converting EML to HTML#Attached Word document in Outlook message
0 notes
Text
Simple syn

#Simple syn manual
#Simple syn android
#Simple syn Pc
The hostile client's SYN requests appear valid to the server. A hostile client knows a port is open when the server responds with a SYN-ACK packet. Instead, the client program sends repeated SYN requests to all the server's ports. However, in a SYN flood, the hostile client does not return an ACK response packet. Once those three steps happen, communication can begin between the client and the server.
The client returns a final ACK packet to confirm that the server's SYN-ACK packet was received.
The server responds, sending a SYN-ACK packet.
The client sends a SYN packet to initiate communication with the server.
Windows service - SimpleSYN Mobile automatically starts in the background when Windows starts without a Windows user logging on to the system.SYN flood explained: How it exploits the three-way handshakeĪ three-way handshake involves the following three steps: No data limit - the data is always synchronized. Highest security when synchronizing Outlook through encryption.Īuto-Update - so that SimpleSYN Mobile is automatically kept up to date. Synchronization in the local network or regardless of location via the Internet. Synchronizes emails (POP3), appointments, contacts, notes and tasks.
#Simple syn android
Supports devices based on Apple iOS, iPadOS, Android OS, Windows 10.
#Simple syn Pc
Powerful filter function - for excluding private items from the synchronization process.įully automatic bidirectional synchronization of Outlook data between Windows PC and smartphones and tablets. Windows service - SimpleSYN automatically starts in the background when Windows starts without a Windows user logging on to the system. Location-independent through Internet synchronization - optionally, synchronization can also take place between separate networks via the Internet. No storage of personal Outlook data in the cloud.Įasy to use and simple setup by the SimpleSYN configuration wizard.Īuto-Update - to keep you up-to-date automatically.Īdvanced network settings - adapt SimpleSYN optimally to your network environment.īackup function to restore deleted objects and folders.Īdditional functions to the standard version: Maximum security of the data through digital encryption (uses SSL or TLS respectively). Manual synchronization - individual Outlook folders or elements can also be synchronized manually at any time.ĭelete Outlook duplicates - with the duplicate finder you can quickly and easily find Outlook duplicates and delete them. Status overview - the current synchronization process is displayed in the Status section.
#Simple syn manual
Optimal data exchange, after the initial synchronization, SimpleSYN only synchronizes changes to the Outlook database.Ĭompletely flexible synchronization - direction and type of synchronization can be configured individually for each Outlook folder.Īssignment of user privileges, user administration and integration in the Windows Active Directory (AD).Ĭomprehensive solutions for synchronization conflicts - manual or automatic selection of which Outlook elements are to be synchronized. Synchronization of subfolders - new, changed and deleted sub-folders can be synchronized. Note: the "Deleted Items" and "Outbox" folders cannot be synchronized. Synchronizes emails ( POP3), contacts, tasks, appointments, notes, journal entries or status updates. Fully automatic synchronization of Outlook data between Windows PCs in the local network (LAN, WLAN, VPN).

0 notes
Text
Office 365 syncing outlook personal folders

#OFFICE 365 SYNCING OUTLOOK PERSONAL FOLDERS INSTALL#
#OFFICE 365 SYNCING OUTLOOK PERSONAL FOLDERS FULL#
#OFFICE 365 SYNCING OUTLOOK PERSONAL FOLDERS WINDOWS#
#OFFICE 365 SYNCING OUTLOOK PERSONAL FOLDERS WINDOWS#
Mobile device support for iPhones, Androids, Blackberry, Windows phones, iPads, and any smartphones / tablets which connect to Exchange ActiveSync.
#OFFICE 365 SYNCING OUTLOOK PERSONAL FOLDERS INSTALL#
Install on a virtual machine or Exchange server – no desktop software or mobile apps to install.You can have conditional sync based on categories if you need to sync all the items from a source folder. Also automatically synchronizes the selected category(ies) to the destination mailbox folder. This allows one folder to be the source of many types of relationships based on the selected category(ies) in the Template. Category Filtering supported. Add2Exchange administrators can filter which items are synchronized from the source folder to the destination (target) folders based on category selection.Manage sync groups via Exchange distribution groups.Relationship attributes: Easily configurable to your organization’s sync needs so you decide how you want adds, edits, and deletions handled.Sync modes: Many to One, One to Many, Many to Many, One to One … and more!.
#OFFICE 365 SYNCING OUTLOOK PERSONAL FOLDERS FULL#
Type of replication: 1-way view only, bi-directional 2-way sync between folders, full mesh sync, or GAL sync.
Folder support: Calendar, Contacts, Tasks, Posts, Notes.
Up to date contact info is readily on hand and available for any daily business activities or for unplanned emergency situations.
Sync and share your corporate address book and vendor contacts to selected employees’ personal contact folders and smartphones for easy access and faster collaboration.
Sync Outlook mailbox or Exchange folders populated from third party programs such as Prolaw and Salesforce with sufficient rights and permissions.
Sync multiple Exchange public folders of the same type with users’ multiple personal folders of the same type.
Sync resource mailboxes for room scheduling (conference meeting rooms) and equipment scheduling (A/V equipment like projectors, whiteboards).
Automatically synchronize your global address list (GAL) to users’ local contacts for viewing on mobiles so you can easily identify when someone from work is calling.
Share and protect your business contacts by syncing users’ personal contacts to an Exchange folder for better contact management and a repository of company contacts.
Ideal if you want to sync your personal calendar and contacts with an assistant or your team. We refer to this as a private to private sync.
Sync one user’s personal folders to another’s users personal folder or to several other users’ folders.
Create a centralized group calendar by syncing appointments from users’ personal folders to an Exchange public folder calendar for a copy of everyone’s appointments and to facilitate scheduling.
Useful for viewing work-related appointments and business contacts on smartphones when you’re away from the office since Microsoft Exchange public folders don’t natively sync to mobiles.
Sync Exchange contact folders or Exchange calendar folders to your mobiles (iPhones, Androids).
Useful for syncing appointments or contacts made on your smartphones / tablets with Exchange folders and/or with other users’ personal folders.
Sync iPhones, Androids, (and other mobiles) with Exchange public folders.
Sync Exchange public folder calendars and contacts with your personal folders – any combination!.

0 notes
Text
Office 365 Digital Experience Monitoring
Office 365 Digital Experience Monitoring (DEM) should be critical to every enterprise. Why? It’s pretty clear that Microsoft Office 365 is winning it all when it comes to collaboration suites with more innovation, polish, and features than other platforms.

Office 365 Growth
Office 365 and its corresponding cloud services, Azure, Office Apps and everything in between is growing fast. Some of the latest figures for Office 365 and Azure growth:
200 Million Active Daily Users Wow, that’s a staggering number! On Microsoft’s’ FY20 Q1 earnings call on October 23 (link to call transcript), they updated the number from the previous 180 million mark reported in April 2019 to 200 million. That’s a number that makes every SaaS vendor jealous.
Office 365 revenue growth at 36% YoY is weaker than Azure (59%), but there’s no doubt that Office 365 remains the big income stream for Microsoft cloud products.
Microsoft reports $36.9 billion in Q2 2020 revenue: Azure up 62%, Surface up 6%, and LinkedIn up 24%
These are just a few of the examples of awesome growth. In short, Microsoft is crushing it with Office 365. And, in turn, most enterprise knowledge workers are sitting in front of Office Apps and services all day long. Therefore the importance of DEM solutions for monitoring Office 365 keeps rising (good for us!).
What’s It Mean to Monitor the Digital Experience of Office 365 Apps?
Its pretty simple — employees and knowledge workers are using Office 365 apps and services, so you want to monitor the performance and detect issues and outages before your users do. Your business and different departments within IT demand to be informed proactively instead of re-actively.
Often, the only way to go about monitoring Office 365 is via synthetic transaction monitoring (STM). Though there are some Real User Monitoring (RUM) solutions like Exoprise Service Watch for passively monitoring Office 365 apps for end-users. For the following set of requirements, we’ll focus mostly on the synthetic monitoring aspect because its where we believe you should start.
Digital Experience Monitoring for Exchange Online
Exchange Online is said to be the biggest workload for Office 365 when it comes to consumption and resources. And, while everyone loves to sound the death knell of Email, we all still continue to collaborate (at least in business) via Email. As such, organizations of all sizes need to monitor the uptime, availability and performance of Email.
When it comes to Office 365, Email monitoring means:
Exchange Online, the core of the service
Outbound SMTP filters if you use them (you probably do)
Inbound SPAM/Junk/Anti-Virus providers
Phishing Providers if they are separate from your SPAM/Junk blockers
For proactive monitoring of Exchange Online in Office 365, the following are required elements that should be checked:
Mailbox performance, uptime and availability
End-to-end network view, Round Trip Times (RTT), and latency from the end-user’s perspective. Accessing real-world protocols from the same sites and locations that users are is critical to DEM solutions. Monitoring uptime and availability from a cloud network is pointless and irrelevant.
Microsoft Exchange Online Protect (EOP) performance, inbound and outbound mail queues. How long does it take to get an email out, in, and through the internet to a destination?
Internet mail flow, transport timings and the SPAM performance. You want to make sure that your inbound and outbound mail delivery is efficient and timely.
Email delivery reliability and overall availability
Archive Mail access and performance
Mail search performance
Different access methods and protocols for Exchange Online and there’s lots of them including; EWS, ActiveSync, OWA, MAPI, Graph and more.
Calendar access, availability and performance
FreeBusy shared and hybrid lookup performance
Appointment creation, updating and lookup performance
Sign-on, Login, Folders, Inbox access
Client Access Server (CAS or CASArray) (when it comes to the Office 365 Suite)
Mailbox Server
These are the critical elements to monitor for a proper Exchange Online SLA. DEM solutions like Exoprise CloudReady provide for testing all of these elements and more. Read up further on Exchange Online or download the Exchange Online datasheet.
Digital Experience Monitoring for SharePoint Online and OneDrive
People love to bash SharePoint and while it can become unwieldy, it remains incredibly popular and flexible. The latest version of SharePoint Online (SPO) dubbed “Modern” does more client-side interaction which makes it easier and more pleasant to work with. If you have users and teams dependent on SPO / OneDrive then you should be monitoring the SharePoint Digital Experience.
SharePoint Site availability and uptime for Service Level Agreement management
Permissions, Login and Sign-In performance
SharePoint interaction with Single Sign-On vendors and tools such as Azure AD, ADFS, Okta
SharePoint Drive and asset availability, creation and access
Hop-by-hop network path performance for SharePoint and OneDrive from end-user locations, branch offices and varying network conditions that users experience. For a proper DEM solution, you must monitor from real user locations.
Search performance. SharePoint sites for busy teams often require lots of search horsepower so everyone can find what their looking for (obviously)
Upload and Download file performance, SharePoint bandwidth and ability to synchronize files.
SPO Health scores, Internet Information Services (IIS) Latency, and SharePoint Request Duration. These are critical values for monitoring the health of your SharePoint tenant.
Bench-marking SharePoint metrics is critical for comparison purposes. It helps make sense of the metrics. By bench-marking your SharePoint site performance, you can identify poorly performing SharePoint tenancies and contact your Microsoft representative if site health is poor compared to the crowd. Read more about Exoprise SharePoint Monitoring features and Exoprise Crowd-Powered benefits.
Digital Experience Monitoring for Microsoft Teams
Finally, we’ll finish up with the requirements for Microsoft Teams Digital Experience Monitoring. Teams is a large and growing platform for Office 365. Its quickly becoming the new foundation for how businesses’ collaborate. With the forced replacement of Skype for Business Online next summer (June 2021), MS Teams will become even more business critical and requires monitoring.
Monitoring the digital experience of Microsoft Teams should at least cover the following:
Teams Site availability and uptime for Service Level Agreement (SLA) management
Permissions, Login and Sign-In performance
Presence and availability, latency
Teams creation, access, messaging and notification performance
Microsoft Teams Audio Video Application Performance
Proxy Connect Times if leveraging local or cloud-based proxy systems (like Zscaler)
TCPIP Connect
DNS Lookup performance
SSL Negotiate (good indicator of general network congestion)
Page Layout, Render and DOM Loaded times
Time to First Byte (TTFB) across all of the MS Teams connections
End-to-end network performance assurance and tests
Audio, Video Jitter
Video and Audio Frame, Bitrates
Packet Loss
Round Trip Delay Time (RTT) and latency as seen by the WebRTC layer that MS Teams utilizes
STUN, TURN and other WebRTC protocol performance
Monitoring VoIP/Video performance requires monitoring from real-user networks and locations. Monitoring VoIP availability from the cloud is useless for determining digital experience.
Capturing and comparing this performance data across your environment enables different IT teams monitor the digital experience of MS Teams proactively.
Conclusion
These are the basic requirements for a full featured Office 365 proactive Digital Experience Monitoring solution. Along with just covering these items, a proper solution should be easy to install and easy to integrate with. Integration usually entails existing on-premise or cloud-based monitoring and ITSM solutions like Enterprise Splunk, SCOM, or ServiceNow.
And along with monitoring the core Office apps, a proper solution should absolutely have support for additional dependent services like:
Yammer and Skype for Business. There still here and beloved by some.
Azure AD, ADFS and a whole compliment of critical authorization services. Ideally, covering these services should watch their interactions with the downstream services to ensure performance.
VoIP, DNS, and other latency tests
Dynamics, Salesforce and other CRM solutions
Generic Web Login and Web Monitoring solution for any application.
Exoprise combines synthetic transaction monitoring with real user monitoring to be better together. Learn more.
Get in Touch for a Custom Demo
Learn how you can improve employee digital experience with browser synthetics and endpoint monitoring. Get a custom demo to see how we synthetically monitor Microsoft 365 with CloudReady as well as real user monitoring with Service Watch.
Request a Demo
This blog was originally published at The Crowd-Powered Blog on Feb 25 2020
0 notes
Text
What is Blockchain?
Blockchain seems complicated, and it definitely can be, but its core concept is really quite simple. A blockchain is a type of database. To be able to understand blockchain, it helps to first understand what a database actually is.
A database is a collection of information that is stored electronically on a computer system. Information, or data, in databases is typically structured in table format to allow for easier searching and filtering for specific information. What is the difference between someone using a spreadsheet to store information rather than a database? Show more Crypto Info

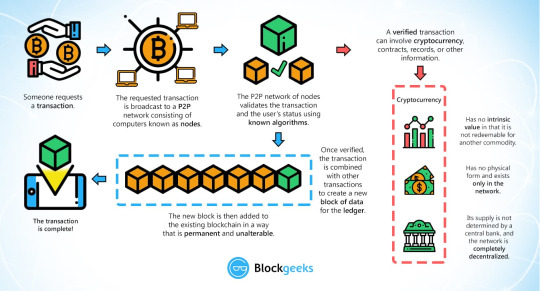
Spreadsheets are designed for one person, or a small group of people, to store and access limited amounts of information. In contrast, a database is designed to house significantly larger amounts of information that can be accessed, filtered, and manipulated quickly and easily by any number of users at once. Large databases achieve this by housing data on servers that are made of powerful computers. These servers can sometimes be built using hundreds or thousands of computers in order to have the computational power and storage capacity necessary for many users to access the database simultaneously. While a spreadsheet or database may be accessible to any number of people, it is often owned by a business and managed by an appointed individual that has complete control over how it works and the data within it. So how does a blockchain differ from a database? Storage Structure One key difference between a typical database and a blockchain is the way the data is structured. A blockchain collects information together in groups, also known as blocks, that hold sets of information. Blocks have certain storage capacities and, when filled, are chained onto the previously filled block, forming a chain of data known as the “blockchain.” All new information that follows that freshly added block is compiled into a newly formed block that will then also be added to the chain once filled. A database structures its data into tables whereas a blockchain, like its name implies, structures its data into chunks (blocks) that are chained together. This makes it so that all blockchains are databases but not all databases are blockchains. This system also inherently makes an irreversible timeline of data when implemented in a decentralized nature. When a block is filled it is set in stone and becomes a part of this timeline. Each block in the chain is given an exact timestamp when it is added to the chain. Transaction Process 📷 Attributes of Cryptocurrency 📷 Decentralization For the purpose of understanding blockchain, it is instructive to view it in the context of how it has been implemented by Bitcoin. Like a database, Bitcoin needs a collection of computers to store its blockchain. For Bitcoin, this blockchain is just a specific type of database that stores every Bitcoin transaction ever made. In Bitcoin’s case, and unlike most databases, these computers are not all under one roof, and each computer or group of computers is operated by a unique individual or group of individuals. Imagine that a company owns a server comprised of 10,000 computers with a database holding all of its client's account information. This company has a warehouse containing all of these computers under one roof and has full control of each of these computers and all the information contained within them. Similarly, Bitcoin consists of thousands of computers, but each computer or group of computers that hold its blockchain is in a different geographic location and they are all operated by separate individuals or groups of people. These computers that makeup Bitcoin’s network are called nodes. In this model, Bitcoin’s blockchain is used in a decentralized way. However, private, centralized blockchains, where the computers that make up its network are owned and operated by a single entity, do exist.
In a blockchain, each node has a full record of the data that has been stored on the blockchain since its inception. For Bitcoin, the data is the entire history of all Bitcoin transactions. If one node has an error in its data it can use the thousands of other nodes as a reference point to correct itself. This way, no one node within the network can alter information held within it. Because of this, the history of transactions in each block that make up Bitcoin’s blockchain is irreversible. If one user tampers with Bitcoin’s record of transactions, all other nodes would cross-reference each other and easily pinpoint the node with the incorrect information. This system helps to establish an exact and transparent order of events. For Bitcoin, this information is a list of transactions, but it also is possible for a blockchain to hold a variety of information like legal contracts, state identifications, or a company’s product inventory. In order to change how that system works, or the information stored within it, a majority of the decentralized network’s computing power would need to agree on said changes. This ensures that whatever changes do occur are in the best interests of the majority. Transparency Because of the decentralized nature of Bitcoin’s blockchain, all transactions can be transparently viewed by either having a personal node or by using blockchain explorers that allow anyone to see transactions occurring live. Each node has its own copy of the chain that gets updated as fresh blocks are confirmed and added. This means that if you wanted to, you could track Bitcoin wherever it goes. For example, exchanges have been hacked in the past where those who held Bitcoin on the exchange lost everything. While the hacker may be entirely anonymous, the Bitcoins that they extracted are easily traceable. If the Bitcoins that were stolen in some of these hacks were to be moved or spent somewhere, it would be known. Is Blockchain Secure? Blockchain technology accounts for the issues of security and trust in several ways. First, new blocks are always stored linearly and chronologically. That is, they are always added to the “end” of the blockchain. If you take a look at Bitcoin’s blockchain, you’ll see that each block has a position on the chain, called a “height.” As of November 2020, the block’s height had reached 656,197 blocks so far. After a block has been added to the end of the blockchain, it is very difficult to go back and alter the contents of the block unless the majority reached a consensus to do so. That’s because each block contains its own hash, along with the hash of the block before it, as well as the previously mentioned time stamp. Hash codes are created by a math function that turns digital information into a string of numbers and letters. If that information is edited in any way, the hash code changes as well. Here’s why that’s important to security. Let’s say a hacker wants to alter the blockchain and steal Bitcoin from everyone else. If they were to alter their own single copy, it would no longer align with everyone else's copy. When everyone else cross-references their copies against each other, they would see this one copy stand out and that hacker's version of the chain would be cast away as illegitimate. Succeeding with such a hack would require that the hacker simultaneously control and alter 51% of the copies of the blockchain so that their new copy becomes the majority copy and thus, the agreed-upon chain. Such an attack would also require an immense amount of money and resources as they would need to redo all of the blocks because they would now have different timestamps and hash codes.
Due to the size of Bitcoin’s network and how fast it is growing, the cost to pull off such a feat would probably be insurmountable. Not only would this be extremely expensive, but it would also likely be fruitless. Doing such a thing would not go unnoticed, as network members would see such drastic alterations to the blockchain. The network members would then fork off to a new version of the chain that has not been affected. This would cause the attacked version of Bitcoin to plummet in value, making the attack ultimately pointless as the bad actor has control of a worthless asset. The same would occur if the bad actor were to attack the new fork of Bitcoin. It is built this way so that taking part in the network is far more economically incentivized than attacking it. Bitcoin vs. Blockchain The goal of blockchain is to allow digital information to be recorded and distributed, but not edited. Blockchain technology was first outlined in 1991 by Stuart Haber and W. Scott two researchers who wanted to implement a system where document timestamps could not be tampered with. But it wasn’t until almost two decades later, with the launch of Bitcoin in January 2009, that blockchain had its first real-world application. The Bitcoin protocol is built on a blockchain. In a research paper introducing the digital currency, Bitcoin’s pseudonymous creator, Satoshi Nakamoto, referred to it as “a new electronic cash system that’s fully peer-to-peer, with no trusted third party.” The key thing to understand here is that Bitcoin merely uses blockchain as a means to transparently record a ledger of payments, but blockchain can, in theory, be used to immutably record any number of data points. As discussed above, this could be in the form of transactions, votes in an election, product inventories, state identifications, deeds to homes, and much more. Currently, there is a vast variety of blockchain-based projects looking to implement blockchain in ways to help society other than just recording transactions. One good example is that of blockchain being used as a way to vote in democratic elections. The nature of blockchain’s immutability means that fraudulent voting would become far more difficult to occur. For example, a voting system could work such that each citizen of a country would be issued a single cryptocurrency or token. Each candidate would then be given a specific wallet address, and the voters would send their token or crypto to whichever candidate's address they wish to vote for. The transparent and traceable nature of blockchain would eliminate the need for human vote counting as well as the ability of bad actors to tamper with physical ballots. Blockchain vs. Banks Banks and decentralized blockchains are vastly different. To see how a bank differs from blockchain, let’s compare the banking system to Bitcoin’s implementation of blockchain. How is Blockchain Used? As we now know, blocks on Bitcoin’s blockchain store data about monetary transactions. But it turns out that blockchain is actually a reliable way of storing data about other types of transactions, as well. Some companies that have already incorporated blockchain include Walmart, Pfizer, AIG, Siemens, Unilever, and a host of others. For example, IBM has created its Food Trust blockchain1 to trace the journey that food products take to get to its locations. Why do this? The food industry has seen countless outbreaks of e Coli, salmonella, listeria, as well as hazardous materials being accidentally introduced to foods. In the past, it has taken weeks to find the source of these outbreaks or the cause of sickness from what people are eating. Using blockchain gives brands the ability to track a food product’s route from its origin, through each stop it makes, and finally its delivery. If a food is found to be contaminated then it can be traced all the way back through each stop to its origin. Not only that, but these companies can also now see everything else it may have come in contact with, allowing the identification of the problem to occur far sooner, potentially
saving lives. This is one example of blockchains in practice, but there are many other forms of blockchain implementation. Banking no industry stands to benefit from integrating blockchain into its business operations more than banking. Financial institutions only operate during business hours, five days a week. That means if you try to deposit a check on Friday at 6 p.m., you will likely have to wait until Monday morning to see that money hit your account. Even if you do make your deposit during business hours, the transaction can still take one to three days to verify due to the sheer volume of transactions that banks need to settle. Blockchain, on the other hand, never sleeps. By integrating blockchain into banks, consumers can see their transactions processed in as little as 10 minutes,2 basically the time it takes to add a block to the blockchain, regardless of holidays or the time of day or week. With blockchain, banks also have the opportunity to exchange funds between institutions more quickly and securely. In the stock trading business, for example, the settlement and clearing process can take up to three days (or longer, if trading internationally), meaning that the money and shares are frozen for that period of time. Given the size of the sums involved, even the few days that the money is in transit can carry significant costs and risks for banks. European bank Santander and its research partners put the potential savings at $15 billion to $20 billion a year.3 Capgemini, a French consultancy, estimates that consumers could save up to $16 billion in banking and insurance fees each year4 through blockchain-based applications. forms the bedrock for cryptocurrencies like Bitcoin. The U.S. dollar is controlled by the Federal Reserve. Under this central authority system, a user’s data and currency are technically at the whim of their bank or government. If a user’s bank is hacked, the client’s private information is at risk. If the client’s bank collapses or they live in a country with an unstable government, the value of their currency may be at risk. In 2008, some of the banks that ran out of money were bailed out partially using taxpayer money. These are the worries out of which Bitcoin was first conceived and developed. By spreading its operations across a network of computers, blockchain allows Bitcoin and other cryptocurrencies to operate without the need for a central authority. This not only reduces risk but also eliminates many of the processing and transaction fees. It can also give those in countries with unstable currencies or financial infrastructures a more stable currency with more applications and a wider network of individuals and institutions they can do business with, both domestically and internationally. Using cryptocurrency wallets for savings accounts or as a means of payment is especially profound for those who have no state identification. Some countries may be war-torn or have governments that lack any real infrastructure to provide identification. Citizens of such countries may not have access to savings or brokerage accounts and therefore, no way to safely store wealth. care providers can leverage blockchain to securely store their patients’ medical records. When a medical record is generated and signed, it can be written into the blockchain, which provides patients with the proof and confidence that the record cannot be changed. These personal health records could be encoded and stored on the blockchain with a private key, so that they are only accessible by certain individuals, thereby ensuring privacy. Records of you have ever spent time in your local Recorder’s Office, you will know that the process of recording property rights is both burdensome and inefficient. Today, a physical deed must be delivered to a government employee at the local recording office, where it is manually entered into the county’s central database and public index. In the case of a property dispute, claims to the property must be reconciled with the public index. This process is not just costly and
time-consuming—it is also riddled with human error, where each inaccuracy makes tracking property ownership less efficient. Blockchain has the potential to eliminate the need for scanning documents and tracking down physical files in a local recording office. If property ownership is stored and verified on the blockchain, owners can trust that their deed is accurate and permanently recorded. In war-torn countries or areas that have little to no government or financial infrastructure, and certainly no “Recorder’s Office,” it can be nearly impossible to prove ownership of a property. If a group of people living in such an area is able to leverage blockchain, transparent and clear timelines of property ownership could be established. Smart is a computer code that can be built into the blockchain to facilitate, verify, or negotiate a contract agreement. Smart contracts operate under a set of conditions that users agree to. When those conditions are met, the terms of the agreement are automatically carried out. Say, for example, a potential tenant would like to lease an apartment using a smart contract. The landlord agrees to give the tenant the door code to the apartment as soon as the tenant pays the security deposit. Both the tenant and the landlord would send their respective portions of the deal to the smart contract, which would hold onto and automatically exchange the door code for the security deposit on the date the lease begins. If the landlord doesn’t supply the door code by the lease date, the smart contract refunds the security deposit. This would eliminate the fees and processes typically associated with the use of a notary, third-party mediator, or the origins of materials that they have purchased. This would allow companies to verify the authenticity of their products, along with such common labels as “Organic,” “Local,” and “Fair Trade.” facilitate a modern voting system. Voting with blockchain carries the potential to eliminate election fraud and boost voter turnout, as was tested in the November 2018 midterm elections in West blockchain in this way would make votes nearly impossible to tamper with. The blockchain protocol would also maintain transparency in the electoral process, reducing the personnel needed to conduct an election and providing officials with nearly instant results. This would eliminate the need for recounts or any real concern that fraud might threaten the election. Advantages and Disadvantages of Blockchain For all of its complexity, blockchain’s potential as a decentralized form of record-keeping is almost without limit. From greater user privacy and heightened security to lower processing fees and fewer errors, blockchain technology may very well see applications beyond those outlined above. But there are also some disadvantages. Pros Improved accuracy by removing human involvement in verification Cost reductions by eliminating third-party verification Decentralization makes it harder to tamper with Transactions are secure, private, and efficient Transparent technology Provides a banking alternative and way to secure personal information for citizens of countries with unstable or underdeveloped governments Cons Significant technology cost associated with mining bitcoin Low transactions per second History of use in illicit activities Regulation Here are the selling points of blockchain for businesses on the market today in more detail. Advantages of Blockchain Accuracy of the network are approved by a network of thousands of computers. This removes almost all human involvement in the verification process, resulting in less human error and an accurate record of information. Even if a computer on the network were to make a computational mistake, the error would only be made to one copy of the blockchain. In order for that error to spread to the rest of the blockchain, it would need to be made by at least 51% of the network’s computers—a near impossibility for a large and growing network the size of Bitcoin’s. Cost ReductionsTypically, consumers pay a bank to verify a transaction, a
notary to sign a document, or a minister to perform a marriage. Blockchain eliminates the need for third-party verification and, with it, their associated costs. Business owners incur a small fee whenever they accept payments using credit cards, for example, because banks and payment processing companies have to process those transactions. Bitcoin, on the other hand, does not have a central authority and has limited transaction fees. DecentralizationBlockchain does not store any of its information in a central location. Instead, the blockchain is copied and spread across a network of computers. Whenever a new block is added to the blockchain, every computer on the network updates its blockchain to reflect the change. By spreading that information across a network, rather than storing it in one central database, blockchain becomes more difficult to tamper with. If a copy of the blockchain fell into the hands of a hacker, only a single copy of the information, rather than the entire network, would be compromised. Efficient TransactionsTransactions placed through a central authority can take up to a few days to settle. If you attempt to deposit a check on Friday evening, for example, you may not actually see funds in your account until Monday morning. Whereas financial institutions operate during business hours, five days a week, blockchain is working 24 hours a day, seven days a week, and 365 days a year. Transactions can be completed in as little as ten minutes and can be considered secure after just a few hours. This is particularly useful trades, which usually take much longer because of time-zone issues and the fact that all parties must confirm payment processing. Private TransactionsMany blockchain networks operate as public databases, meaning that anyone with an internet connection can view a list of the network’s transaction history. Although users can access details about transactions, they cannot access identifying information about the users making those transactions. It is a common misperception that blockchain networks like bitcoin are anonymous, when in fact they are only confidential. That is, when a user makes public transactions, their unique code called a public key, is recorded on the blockchain, rather than their personal information. If a person has made a Bitcoin purchase on an exchange that requires identification then the person’s identity is still linked to their blockchain address, but a transaction, even when tied to a person’s name, does not reveal any personal information. Secure TransactionsOnce a transaction is recorded, its authenticity must be verified by the blockchain network. Thousands of computers on the blockchain rush to confirm that the details of the purchase are correct. After a computer has validated the transaction, it is added to the blockchain block. Each block on the blockchain contains its own unique hash, along with the unique hash of the block before it. When the information on a block is edited in any way, that block’s hashcode changes—however, the hash code on the block after it would not. This discrepancy makes it extremely difficult for information on the blockchain to be changed without notice. TransparencyMost blockchains are entirely open-source software. This means that anyone and everyone can view its code. This gives auditors the ability to review cryptocurrencies like Bitcoin for security. This also means that there is no real authority on who controls Bitcoin’s code or how it is edited. Because of this, anyone can suggest changes or upgrades to the system. If a majority of the network users agree that the new version of the code with the upgrade is sound and worthwhile then Bitcoin can be updated. Banking the UnbankedPerhaps the most profound facet of blockchain and Bitcoin is the ability for anyone, regardless of ethnicity, gender, or cultural background, to use it. According to the world bank there are nearly 2 billion adults that do not have bank accounts or any means of storing their money or wealth.5 Nearly all of these individuals live in developing
countries where the economy is in its infancy and entirely dependent on cash. These people often earn little money that is paid in physical cash. They then need to store this physical cash in hidden locations in their homes or places of living leaving them subject to robbery or unnecessary violence. Keys to a bitcoin wallet can be stored on a piece of paper, a cheap cell phone, or even memorized if necessary. For most people, it is likely that these options are more easily hidden than a small pile of cash under a mattress. Blockchains of the future are also looking for solutions to not only be a unit of account for wealth storage, but also to store medical records, property rights, and a variety of other legal contracts. Disadvantages of Blockchain While there are significant upsides to the blockchain, there are also significant challenges to its adoption. The roadblocks to the application of blockchain technology today are not just technical. The real challenges are political and regulatory, for the most part, to say nothing of the thousands of hours (read: money) of custom software design and back-end programming required to integrate blockchain to current business networks. Here are some of the challenges standing in the way of widespread blockchain adoption. Technology CostAlthough blockchain can save users money on transaction fees, the technology is far from free. The “proof of work” system that bitcoin uses to validate transactions, for example, consumes vast amounts of computational power. In the real world, the power from the millions of computers on the bitcoin network is close to Assuming electricity costs of $0.03~$0.05 per kilowatt-hour, mining costs exclusive of hardware expenses are about $5,000~$7,000 per coin.10 Despite the costs of mining bitcoin, users continue to drive up their electricity bills in order to validate transactions on the blockchain. That’s because when miners add a block to the bitcoin blockchain, they are rewarded with enough bitcoin to make their time and energy worthwhile. When it comes to blockchains that do not use cryptocurrency, however, miners will need to be paid or otherwise incentivized to validate transactions. Some solutions to these issues are beginning to arise. For example, bitcoin mining farms have been set up to use solar power, excess natural gas from fracking sites, or power from wind farms. Speed InefficiencyBitcoin is a perfect case study for the possible inefficiencies of blockchain. Bitcoin’s “proof of work” system takes about ten minutes to add a new block to the blockchain. At that rate, it’s hat the blockchain network can only manage about seven transactions per second (TPS). Although other cryptocurrencies such as Ethereum perform better than bitcoin, they are still limited by blockchain. Legacy brand Visa, for context, can process 24,000 TPS. Solutions to this issue have been in development for years. There are currently blockchains that are boasting over 30,000 transactions per second. Illegal ActivityWhile confidentiality on the blockchain network protects users from hacks and preserves privacy, it also allows for illegal trading and activity on the blockchain network. The most cited example of blockchain being used for illicit transactions is probably the an online “dark web” drug marketplace operating from February 2011 until October 2013 when it was shut down by the FBI.6

The website allowed users to browse the website without being tracked using the Tor browser and make illegal purchases in Bitcoin or other cryptocurrencies. Current U.S. regulations require financial service providers to obtain information about their customers when they open an account, verify the identity of each customer, and confirm that customers do not appear on any list of known or suspected terrorist organizations. This system can be seen as both a pro and a con. It gives anyone access to financial accounts but also allows criminals to more easily transact. Many have argued that the good uses of crypto, like banking the unbanked world, outweigh the bad uses of cryptocurrency, especially when most illegal activity is still accomplished through untraceable cash. RegulationMany in the crypto space have expressed concerns about government regulation over cryptocurrencies. While it is getting increasingly difficult and near impossible to end something like Bitcoin as its decentralized network grows, governments could theoretically make it illegal to own cryptocurrencies or participate in their networks. Over time this concern has grown smaller as large companies like PayPal begin to allow the ownership and use of cryptocurrencies on its platform. What's Next for Blockchain? First proposed as a research project in 1991,7 blockchain is comfortably settling into its late twenties. Like most millennials its age, blockchain has seen its fair share of public scrutiny over the last two decades, with businesses around the world speculating about what the technology is capable of and where it’s headed in the years to come. With many practical applications for the technology already being implemented and explored, blockchain is finally making a name for itself at age twenty-seven, in no small part because of bitcoin and cryptocurrency. As a buzzword on the tongue of every investor in the nation, blockchain stands to make business and government operations more accurate, efficient, secure, and cheap with fewer middlemen. As we prepare to head into the third decade of blockchain, it’s no longer a question of "if" legacy companies will catch on to the technology—it's a question of "when."
ARTICLE SOURCES
maximalists favor bitcoin over other cryptocurrencies and are unapologetically in favor of a bitcoin monopoly in the future. Ether is the cryptocurrency of the Ethereum network. All of the programs linked with the Ethereum network require computing power; Ether is the token that is used to pay for this power. Block Height indicates the overall length of a blockchain. Sharding is a database partitioning technique that may help blockchain networks build scalability, reduce latency, and handle more transaction volume Show more Crypto Info
0 notes
Text
Make The Top Notch Web Application For Business Using .Net Framework

Programmers have actually been trying to find a framework that would help them develop impressive web applications. And.Net offers that purpose .Net is a Microsoft framework made use of for making Web applications. There are various versions of them like Internet types, .Net MVC but all of them are made use of for the same purpose which is web application development. Each of them has various advancement style, the one you choose depends on a mix of your shows properties like understanding, Abilities and also development experience, the kind of application you are producing and the growth strategy you're comfortable with. let's recognize and also take an overview of the frameworks and some suggestions for how to select between them. Also Read: Would you like to outsource your digital marketing work? .NET Internet Pages This offers a quickly, friendly and light-weight way to combine web server code with HTML to create dynamic internet material. You can connect this to data sources, and also video, web link to social networking web sites as well as include a lot more features that assist you develop lovely websites that conform to the most up to date web requirements. Web Forms With .Net internet kinds, you can build dynamic web sites utilizing an acquainted drag as well as decrease, event-driven design. A layout surface as well as numerous controls and parts let you rapidly develop advanced, effective interface driven sites with data access. MVC .NET MVC gives you an effective, patterns-based means to develop dynamic internet sites that makes it possible for a clean separation of issues which provides you full control over markup for pleasurable, active advancement. .NET MVC consists of several features that enable quick, TDD friendly growth for developing sophisticated applications that use the most recent web criteria. Before you get puzzled, you require to recognize that all .NET frameworks are share core functionality of.NET as well as of .NET for instance, all structures offer a login security model based on membership, and all share same facilities for taking care of demands, managing sessions, and so on that belong to the core .NET capability. As well as one more thing the three structures are not completely independent, depressing I recognize. And also selecting one does not prevent using one more. Since the framework can exist side-by-side in the same web application, it' not uncommon to see private parts of applications composed making use of various frameworks. Also Read: Effective Tips to Hire a Dedicated Developer So what are the functions of.NET? There are literally numerous devices in dot net development however we will just be talking about 10 finest features. The featured features are the most typical ones from all the most up to date variations. Bundling and minification Function Bundling and minification were first introduced with Dot net 4.5 which helps to bundle and also lessen the dimension of the scripts as well as stylesheets in your application. This attribute has a great impact on the efficiency of internet application as a whole. You will additionally have a system internet optimization namespace that provides assistance bundling and minification of files. Also Read: Why Digital Marketing is Important to do Business? Highly Typed Information Controls You can currently have a data nerve center that can be strongly typed. You will get intellisense, all you require to do is appoint the item type building to a version that is mosting likely to be related to the information controls made use of in your.aspx web pages. Version Binding-- Separating the Web Form from the Version The Model binding attribute allows you to develop Web forms that are independent of the Version that inhabited the view. The Largest advantage of using Version Binding in .NET is that you can easily unit test the methods. Version binding is provided with the use of the "System Web Modelbinding" namespace. This namespace consists of worth provider courses like Control Feature, Query String Characteristic etc. All these classes are inherited from the ValueProvider Source Characteristic class. Worth Providers Asp.Net development company india provides several value carriers that can be made use of to filter information, they are Inquiry string Session Cookie Control Value Discover 10 Simple And Easy Ways to Discover the Best Outsourcing Team You can likewise produce your own custom worth providers Support for OpenID and OAuth Logins .NET gives assistance for OpenID for OAuth logins-- you can quickly use external solutions to login to your application. Like .NET MVC 4, .NET 4.5 allows you to register OAuth company in the App_Start/ AuthConfig.cs documents. We can likewise utilize this information dictionary to pass extra information. Assistance improved paging in .NET GridView control Paging assistance in .NET GridView control has been improved a great deal. It allows personalized paging building offers wonderful assistance paging as well as arranging with huge amounts of information affinity. Improved support for asynchronous programming .NET gives excellent assistance in asynchronous programs-- you can currently check out and compose HTTP demands and reactions without the need of OS strings. Additionally, you have assistance for 2 new Search phrases-- await and also async. Assistance for websockets HTML5 WebSockets enable you to perform duplex communication between the customer browser and also the internet server. It gives support for websocket procedures. .NET and also IIS 8 give support for WebSocket method-- you can now take advantage of WebSockets in your .NET web applications. Support for HTML5 types kinds .NET offers excellent assistance for HTML5 type types, the following are the list of brand-new controls available in HTML5. Email LINK Number Variety Data pickers i.e., day, month, week, time, datetime, datetime-- local Search Shade .NET web API This is consisted of in .NET MVC 4 and .NET Web Forms. This new .NET Web API assists you to construct as well as eat HTTP services quickly. In addition to the features.NET supplies numerous benefits in Web application advancement. It allows building a selection of web services such as: Online applications Business as well as corporate sites Custom CMS (material management system). Custom CRM (Consumer Connection Administration). If you ask me.Net is a benefit for those sites which require to update their web content extra regularly than various other or require to be updated instantly in regular intervals. Below are the advantages of.Net over other platforms. Based upon server side scripting technology, which is why the code is processed on the home windows server prior to it is presented in the internet browser. Therefore, .Net applications execute faster than translated manuscripts. With .Net, on the fly updates of released web applications are possible. This does not require the restarting of the web server. Additionally, .Net gives automatic state monitoring for web page controls. This is additionally called server controls. It also uses the capacity to develop brand-new as well as tailored server controls from existing controls. .Net additionally offers integrated functions for caching regularly requested websites on the server. Additional functions offered are centering web content for specific languages in addition to cultures as well as even discovering browser abilities .NET additionally gives full assistance for XML, CSS and also other brand-new in addition to well-known web criteria. · For the program reasoning, a designer can select to compose the code in more than 25. Internet languages. Which includes C#, JS, VB.NET, etc. How about that? .Net is much better even if you do not compare with others, below are some reasons to choose.net just for being better. Better UI Controls .Net stage provides rich interface controls (UI). It has a rich collection of in-build UI controls, and additionally sustains third-party UI controls. Safety. The.Net structure offers an exceptionally secure setting. It makes use of different safety and security parts for maintaining the application ensured. It has actually operated in windows conformation, which can be used to make secure as well as secure applications. Easy to incorporate with other Microsoft Applications .Net collaborates easily with various other Microsoft items, making it simple to interfere with exchange web servers, e-mails as well as Microsoft Office applications, and also retrieve data with a single login. Security & Scalability. The.Net system offers extra security as well as scalability than its programs companions. As an example, an object user interface offers an overview to recycling the items in more approximately date shows; this additionally offers all the details you intend to change, things without influencing alternate codes. It makes it easy to transform the code with more recent technology and also faster formulas. MVC Design. MVC (Design Sight Controller) style provides the benefit of arranged code as a result of its separation of concerns methodology. The organization of code promotes code reusability and makes it possible to make functional applications. Rapid Advancement .Net applications can be easily invested in any kind of Microsoft server. The structure encourages one-time configuration creation to share applications quicker. So just how does.Net do? If you are eagerly anticipating developing applications with piece de resistance, you should develop and prepare for efficiency just as you would certainly for any other attribute app. All you require to do is use the devices given by Microsoft to measure your application's performance, as well as if needed, make improvements to memory usage, code throughput and also responsiveness. We are going to evaluate the devices that Microsoft provides. If you desire an excellent executing web application, you must develop efficiency right into your internet application just as you would certainly make any other feature. You ought to determine the performance-critical scenarios in your application, set performance objectives, as well as step performance for these app circumstances early and commonly. Because each app is various and has various efficiency vital execution paths, determining those paths early and also concentrating your efforts allow you to maximize your efficiency. You don't need to entirely recognize with your target platform to create an application which has high performance. Nonetheless, you should establish an understanding of which parts of your target platform are expensive in regards to performance, how do you do this? By Measuring efficiency early in your advancement procedure. If you are determined to identify the location that are vital for efficiency and also to develop your efficiency goals, you need to always think about the customer experience (UX). There are two key location that will affect the user's assumption of your web application, they are start-up time and also responsiveness. Also, if you figure out which parts of your code execute a lot more regularly, you can make sure that these parts of your code are well maximized. Just how do you Analyze performance? As part of your total advancement plan, established factors during growth where you will certainly measure the efficiency of your application and also compare the result with the objectives you set formerly. Measure your application in the atmosphere and hardware that you expect your individuals have. By analyzing your app's efficiency early and also commonly you can change architectural choices that would be costly as well as pricey to repair later in the advancement cycle. It's time to satisfy the performance devices for.Net. Aesthetic Workshop performance evaluation. It is used to analyze the CPU usage of your.NET structure applications that will certainly be released to computer systems that are running the Windows OS. It is available from the Debug food selection in Visual Studio after you open a job. Windows Phone Application Evaluation. It is used to evaluate the CPU as well as memory, network information transfer rate, application responsiveness, as well as battery consumption in your windows phone apps. This device is offered from the debug menu for a windows phone project in a visual studio after you mount the windows phone SDK. PerfView. It is utilized to recognize CPU and memory-related performance issues. This device uses event mapping for Windows as well as CLR profiling APIs to supply innovative memory and also CPU investigations in addition to details concerning garbage collection as well as JIT collection. Windows Performance Analyzer. This is used to determine general system performance such as your application's memory and also storage usage when multiple applications are running on the same computer. This tool is offered from the download facility as part of the windows evaluation as well as implementation package (ADK) for Windows. Read the full article
0 notes
Text
Highly reliable EDB to PST converter Software to Convert EDB to PST File
youtube
What is Exchange Server?
Exchange server is human being and very crucial product of Microsoft, it very big mail server and calendar server which helps small and medium range companies to achieve better dependability and improved performance. This application support only on Windows Server Operating systems.
It can also know as a server-side utility that gives data to the client-side combining application platform. It messaging podium or MS exchange mail server provides capability for sending and receiving emails, calendaring, voicemail transcriptions, scheduling, and tools to customize collaboration and messaging service applications.
Here also available various types of other email protocols apart from an Microsoft exchange server, like as POP3, IMAP, MAPI, and Exchange ActiveSync.
What use of exchange server
Microsoft exchange server basically Organizations use for centrally manage, distribute and store company email at one hand or place. MS Exchange Server also comprises a wide range of features to allow staff to store and share contact details, schedules and tasks.
Microsoft Exchange Server (.edb file) border with a collection of email client and PIM (Personal Information Management) software or app packages, including Microsoft Outlook.
Why get damage exchange server data
Lots of reason behind of Microsoft exchange corruption some are here:-
1. Virus attack
2. User error
3. Abrupt shutdown
4. Application malfunction
5. Error in database objects
6. Improper changes in the database schema
7. Hardware Failure
8. Software Issues
9. Exchange Server Error Code 528
10. JET_errBadDbSignature-531
11. JET_errConsitentTimeMismatch-551
12. JET_errDatabaseStreamingFileMismatch-540
13. JET_errDatabaseDirtyShutdown-550
14. JET_errInvalidDatabase-1028.
For get rid these errors download Stella EDB to PST Converter Software
For more detail about Exchange Errors visit here: https://medium.com/@stellarecovery26/troubleshoot-all-exchange-errors-corruption-for-recovery-of-exchange-edb-to-pst-6913b512e7f4
Why need to convert EDB file to PST
When Microsoft exchange server get corrupted that time for overcome exchange corruption and read exchange mails we need to convert EDB file to PST. Stella Best EDB to PST converter software that will very time ready for deal any types of exchange issues and solve them, after that it restore exchange EDB file to PST outlook with multiple format EML, MSG, HTML, MBOX, DOC, MHTML, TXT etc.

How to repair exchange mailbox data
Easy EDB Exchange Repair Tool to recover corrupt EDB Server Mailboxes from 2019, 2016, 2013. For instant Exchange Converter use Stella EDB to PST Converter software that provides you power for recover any kind of damage or corruption of EDB mailbox from dismounted/ mount MS exchange server with whole previous stored EDB file data zero % data loss issues.
1. Repair and save Mailboxes from corrupt Exchange EDB files
2. Recover and fix corrupt Unicode EDB files data
3. Restore Recovered EDB Mailboxes file to Live Exchange Server
4. Import Convert Repaired MS Exchange Mailboxes to O365
5. Work with Multiple EDB files Recovery
Stella Exchange server recovery Manager to Restore Exchange Mailbox to PST
Microsoft exchange server is well excellent technology to restore your all Emails in ms exchange database file identify as .edb file. But sometime exchange EDB file got corrupted/damage due to multiple reasons like as database header file, error in JET Engine, exchange server dirty shutdown, power failure, virus infection, physical system damaged, Exchange server crash,oversize database, Virus attack,User error,Abrupt shutdown,Application malfunction,Error in database objects,Improper changes in the database schema,Hardware Failure,Software Issues,Exchange Server Error Code 528,JET_errBadDbSignature-531, log file error & many more reasons.
When you face this situation so don’t irritate because best option to recover all errors, problems of exchange database and extract data from from corrupted EDB file database and allows to restore/rebuild them in working PST file. It capably solve the trouble with Microsoft exchange server mailbox database and restore all the ms exchange EDB mailbox object such as Inbox emails, sent items, address book, attachments, appointments, notes, journals and task etc. Stella Exchange Server Recovery Manager tool to convert EDB to PST, EML, MSG, PDF, DOC etc.
Click here for Download & Information about Exchange Converter software
Nice Key Feature of Exchange Server Recovery
1. Quickly Search missing EDB file location from Your computer
2. Save EDB to PST mailbox with date filter option (start date to end date).
3. export import Exchange Mailbox to MS outlook with naming convention (from+ date+ subject, subject + from + date)
4. Convert EDB to PST online and support office 365 with whole previous exchange mailbox data.
5. Restore the recovered EDB file data into PST format and work on live exchange server.
6. This software not only repair damage EDB file but also save EDB file to PST with multi format EML, MSG, EMLX, HTML, MHTML, DOC etc.
7. Free demo with it demo exchange user can view whole exchange mailbox recovery process and also save 25 EDB email to PST at free of cost.
For More detail please visit official Site:- https://www.stelladatarecovery.com/exchange-edb-to-pst-converter.html
Some advance key of Stella EDB to PST Software
1. Convert single EDB file to working PST outlook
2. Recover pub1 and priv1 EDB file to PST
3. Free EDB to PST converter to Convert EDB mailbox to PST outlook
4. export EDB file to PST, EML, MSG and HTML
5. It gives an advance option to split large size of recovered PST file.
0 notes
Text
Stella Microsoft OST to PST Recovery Software

OST:-OST file is (.ost file, offline storage table) that offline folder which make in MS outlook. This offline folder is make for user work in offline mod but when the software synchronize changes with the Exchange server the next time they connect and made (.ost file).
PST:- PST file is (personal Storage Table) is made in Microsoft outlook the storage limit for a single user's .PST file is PST stands for personal storage.
Why We Need to Recover Exchange OST to PST
Microsoft Outlook Server is a great messaging app for comprehensive organizations. And, all the organizations, of which usually use Outlook as well as external statements for Outlook.
During the exchange OST file, completemailbox data is not directly available so you need to recover OST to PST. For recovery of corrupted OST file, as per required OST to PST Conversion the OST file is stored on the your system like as: emails and other data is still safe in the OST file. But the OST file unrecoverable or we can say that it is orphaned. You can go for manual tricks but this method takes more time does not ensure users to accurately recover Exchange OST data.
The MS-Exchange server may crash suddenly due to power failure, malicious software, virus attacks or any other reason. A serious accident can take you anywhere because you cannot be able to connect to MS Exchange Server. Such situations are very challenging and difficult because in most cases they display various error messages frequently.
Microsoft OST to PST converter software
Best MS OST to PST Converter software with the help of world nice tool Stella OST to PST conversion software to recover damage OST file data and nice 3rd party tool to recover export OST file data into working MS outlook PST with some other format like as:- EML, MSG, EMLX, HTML, MHTML, TXT, DOC, MBOX and outlook profile. OST to PST software that extract emails from OST database and save OST file to PST with zip attachments, journals, calendar, contact, scheduled task, notes and appointments.
Stella OST to PST software, you get user-friendly feature to recover OST emails from dismount orphaned OST database and convert them to healthy MS Outlook PST. OST data has been orphaned with the help of Microsoft OST from PST Converter tool and convert all data from OST file into PST in various formats like EML, MSG, HTML, TXT, DOC, HTML, MHTML and Outlook profiles.
For instant OST recovery process user can download the best “Stella Best OST to PST Recovery software” and repair OST file data into working MS outlook PST file from all version of OST file like as:- 5.0, 5.5, 97, 98, 2000, 2003, 2007, 2010, 2013, 2016 and 2019.Without any losing informationthis software has easy method for scan inaccessible outlook OST file data and convert OST to PST with such its item as:- contact, calendar, journal, task and appointment.
Better OST Recovery Software
If you are suffering from exchange OST corruption and you need to better OST Recovery tool then without think more just come at Stella and download easy solution for OST recovery a software to recover OST emails. Microsoft OST to PST Converter tool which an advance quality to repair damage OST emails from well as maintains data integrity and email. OST recovery software assists you to filter emails as per date selection and split heavy size of PST file into different sizes as 1GB, 2GB, 3GB, 4GB, and 5GB.
Know Stella OST to PST Converter feature
# It not only repair damage OST file data but also save recovered OST file to PST
# Find OST file location from your computer
# Save OST file data into working PST outlook supports all version of OST file upto 2019.
# quickly Convert exchange OST to PST file
# Divide big Size of recovered MS outlook upto 5GB
# No need to outlook during OST conversion process.
# Export Multi format of OST to PST as: - EML, MSG, EMLX, DOC, CSV, TXT, MBOX and outlook profile
# Preview & Convert OST File Items: Emails, Calendar, Contacts, Tasks, and Journals
# Recovers email attachments as well as email properties (to, from, cc, bcc, and date)
# Microsoft Outlook 97, 98, 2000, 2003, 2007, 2010, 2013, 2016, 2019
# Windows 7, Vista, XP, 2003 and 2000, Win8, Win8.1 and Win 10
# Microsoft Exchange OST: - 2019, 2016, 2013, 2010, 2007, 5.5, 5.0 etc
# Convert Bulk OST emails to MS outlook 365 at time.
# Advance and Quick Scan to Recover Damaged Outlook 365 OST File
Working Process of Stella Exchange OST Recovery Software
Step1): Download OST to PST software from here
http://stelladatarecovery.com/download/SDROSTTOPSTsetup.exe
Step2): And Install the OST to PST software

Step 3): Search OST File location which corrupted on your systems

Step 4): Then Start Scanning process

Step 5): Select email which you have recovered

Step 6): After the selective the format to convert OST file PST, EML, MSG, etc.

Step 7): Create folder where save the OST to PST file data
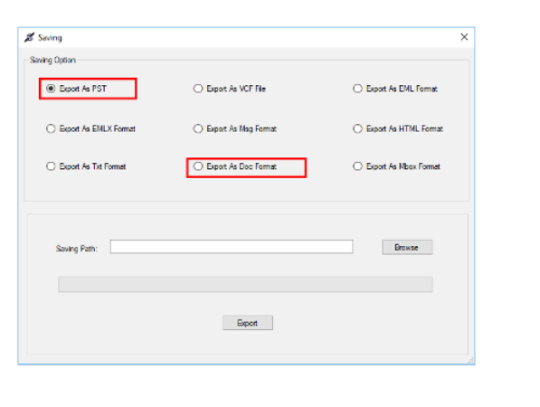
Step 8): Make folder where save the OST to PST file data

Step 9): Finally recover and convert the OST file items into working format.
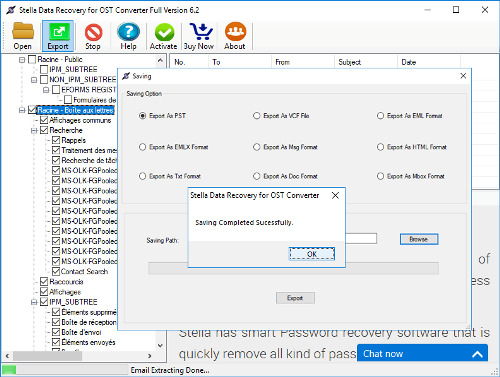
Read More For Easy Steps: https://www.stelladatarecovery.com/how-to-convert-ost-file-in-to-outlook-pst-file.html
Use Freeware OST to PST Converter Tool
Beforepurchase any paid solution you can just download free OST to PST converter software demo version at free of cost but there is some limitation you can save only 25 OST emails into working PST outlook after that satisfied demo version if you want to restore unlimited OST emails to working PST file then just register full version of Stella OST to PST software.
For More Details Visit Here: - https://www.stelladatarecovery.com/ost-to-pst-converter.html
#ost to pst#ost to pst converter#ost to pst conversion#convert ost to pst#ost to pst recovery#recover ost to pst
0 notes
Text
Camera Color Spaces Explained – sRGB vs Adobe RGB vs RAW
The post Camera Color Spaces Explained –-- sRGB vs Adobe RGB vs RAW appeared initially on Digital Photography School . It was authored by Herb Paynter .
Your cam is most likely able to record color images in a range of various color containers called ““ areas. ” These video camera color areas gather colors in among numerous size light pails identified raw, srgb, and adobergb.
Each container collects a little increased ranges of light, comparable to the method Crayola crayons are packaged and offered in progressively inclusive collections of colors; little, big, and jumbo.
Camera color areas provide professional photographers a range of various size boxes.
.Cam color areas.
Scenes that consist of both fantastic colors and brilliant lighting are outstanding prospects for capture with AdobeRGB color space.F/ 3.5, 1/1000, ISO 400, Lumix G Vario 2.8, 35mm
An argument in the image neighborhood normally emerges over which video camera color areas to pick in the video camera’’ s choices. Some color areas catch more of the colors and saturated colors than others. Pictures caught in one area might consist of more colors than another.
Each area is preferably fit for particular functions, and the concern of which cam color area to pick requirements a little bit of description. In addition to the capture concern, selecting a color area for post-production modifying will depend upon the image’’ s supreme use.
.
Your’electronic camera ’ s color areas include not simply color information, however extra parking area on the drive. Bigger color areas supply more bit-depth (discussed listed below), which inhabits more digital property on the sd card. The option of which to utilize does have useful value.
.What cam color area to utilize.
There is no singularly best color area option, so let’’ s take a look at which is finest for particular scenarios.
Images that do not consist of highly-saturated color however include considerable information in the shadow locations will take advantage of RAW format capture and high-bit processing. F/10, 1/1600, ISO 800, Lumix G Vario 2.8, 200mm
Unless the sole function of a picture is to show as a high-resolution digital image, you may wish to transform the file’’ s initial color area for a less requiring outcome. Keep in mind that every time a file alters from a bigger color area to a smaller sized color area (RAW to AdobeRGB, or AdobeRGB to sRGB), the image’’ s color strength and stability might lessen in the procedure. Some imaging applications are less requiring than others.
While copies of digital files stay similar in size and strength to the initial no matter the number of times they have actually been copied, when a digital file alters to a lower color area, it will constantly lose some vital color details. Your electronic camera color areas in basic, and gadget color areas, in specific, are all special. Each serves a specific function.
The severe vibrant variety and saturated skies taken advantage of the RAW capture and modifying in AdobeRGB. Due to the fact that of the 14-bit capture, information buried in the shadows was possible. F/14, 1/300, ISO 3200, Lumix G Vario 2.8, 12mm
.It’’ s a matter of depth.
The distinction in between video camera color areas comes down to a concern called bit depth. Bit depth is a mathematical description of the number of noticeable differences in between tones of color can be acknowledged and recreated by various gadgets (a techie term for scanners, video cameras, computer system displays, and printing makers). Not all gadgets can recreate all colors the exact same (which is the main stumbling block in the middle of all color problems).
Every gadget recreates and checks out color utilizing a various procedure. While this seems like a fixable issue, there is an unsolvable and unfortunate truth behind the issue. There are at least 3 various analyses of color at play in every capture-display-print cycle.
These vibrant seat cushions and deep shadows were recorded in RAW format, modified in AdobeRGB, and conserved in sRGB for upload to our cam club’’ s server for display screen as part of a club school trip slideshow. F/7.1, 1/320, ISO 400, Lumix G Vario 2.8, 19mm
First, cams record color by taping strengths of light as electrical signals and analyzing those signals as colors. Each color is appointed a particular number.
Second, these numbers are then sent out to the computer system. Here, they get equated into another procedure that analyzes those electrical signals into a procedure that switches on small lights (called pixels) on a backlit screen.
And 3rd, those pixels are then sent out to a printing device that advises those pixel worths to spit small splatters of colored ink onto paper.
It’’ s a really complex procedure that color researchers have actually pursued years to make easy. It simply ain’’ t that basic!
Anyway, throughout this hair-on-fire digital shift, various approaches are utilized that make use of the numerous color areas in such a way that changes the colors from one gadget to another as precisely as possible. In some cases the color translations put on’’ t communicate the colors as properly as we would like, which is why in some cases the screen colors put on’’ t match the printer colors.
.
Science utilizes charts like this to outline the qualities of cam color areas. While these charts are described as ““ theoretical ” due to the fact that they are not noticeable to the human eye however represent what each color ““ pail ” can catch versus what the eye can see.
.The supreme referee.
The just extensive color area that plots the complete scope of what the human eye can see is what the science neighborhood calls L * a * b * (inverted horseshoe diagram) area.
The human eye is the supreme arbitrator in the color wars, and all gadget abilities (printer, cam, and display screen) are specified by how they compare to the eye’’ s master range. This is why this unusual horseshoe shape is described as the Reference Space. All other gadgets, whether display screen, cam, or printer, can just acknowledge and make use of parts of this "referral area,” ” and they normally disagree with each other.
Color is a inefficient and really varied household. Each gadget speaks a various dialect of a comparable language. Each produces colors that can not be consistently replicated on other gadgets. Color is a really untidy subject.
Crayola crayon boxes consist of differing varieties of colors simply as color areas gather differing quantities of color. The lightest and darkest color crayons are the very same worth, however bigger boxes include more colors than smaller sized ones.
Some gadgets can reveal color better than others. No gadget developed by people can recreate all the colors that can be seen by people. The colors caught by one gadget that fall outside the range (Crayola box size) of other gadgets, get clipped, lost, or compressed throughout the handoff. Those colors never ever return house.
This is the terrible fact about digital color recreation. The technique to color recreation remains in maintaining as much of the typical color as possible throughout the procedure. This very same human eye (and brain) are extremely flexible about accepting the restrictions of non-human gadgets.
Color recreation is a real application of the law of reducing returns and the visual science of physics. Professional photographers comprehend this law rather well.
Very hardly ever can a cam really record all the color and characteristics of an initial scene. Nature’’ s color range extends even further than the colors that the human eye can recognize. Whenever a digital image gets shifted from one type into any another kind, that change is a diminished-value exchange.
As an image is moved from one gadget to another, those pixel worths situated outside the color range of the location gadget constantly get lost in the translation. The item of color management is to reduce color loss and preserve as much of the look of the initial as possible, all the method through the recreation procedure.
.RGB areas (sRGB, AdobeRGB, ProPhoto RGB).When you record the scene, #ppppp> It all starts with the electronic camera's color settings that are in location. All cams record light through red, green, and blue filters (RGB color area). While there are a variety of RGB color areas to pick from, each sports a somewhat various color range.
Each gadget in the photography chain analyzes colors somewhat in a different way, and each reacts to the specific color areas distinctively.
Each color area (sRGB, AdobeRGB, ProPhoto RGB, and so on) offers a distinct collection of color qualities, and each area pleases particular screen and recreation requirements.
Gamuts are descriptions of the variety of colors that a gadget can acknowledge, print, record, or screen.
Shooting a lively, saturated scene with the cam needs a bigger color area. Utilizing a video camera color area with a smaller sized range might considerably reduce the raw, extreme feeling of the scene. This is why most photography specialists motivate professional photographers to set their electronic cameras to catch images in AdobeRGB.
.sRGB.
Almost all digital electronic cameras are factory-set to record colors utilizing sRGB as the default color area for a possible factor; the majority of the images we take never ever get printed! At finest, we see them on computer system screens or social networks . Rather truthfully, the majority of the images we catch never ever make it past the preliminary glimpse at the cam’’ s LCD screen. Recording those images in higher-bit color area is an overall waste of disk area.
sRGB color area stays mostly the same given that it was specified in the 1950s to compress video images into a workable size for broadcast. While the format has actually been upgraded somewhat, the standard intent is the exact same.
sRGB was established by HP, Microsoft (and others) back in the early days of tv to attend to the color range requirements of many tvs (early variations of computer system displays), and the requirement was set long back. The airwaves and Internet internet browsers survive on an sRGB diet plan. The sRGB color area standardizes the method images are still seen on tvs and screens.
.Adobe RGB.
If the supreme location for your photo is screen or display-based existence (discussions, Internet, or tv screens), this is most likely the very best option to catch images. If you shoot for print on paper, both AdobeRGB 1998 and ProPhoto RGB include a broader range of colors and are therefore more fit for preparing images for print .
The saturated colors and dazzling characteristics are constantly caught finest in the inmost color container of all –-- RAW. The degree of changes supplied by RAW capture and ProPhoto RGB modifying is best for images like this. F/6.3, 1/800, ISO 400, Lumix G Vario 2.8, 26mm
.RAW.
Actually, the most perfect pail for recording images really goes beyond the ranges of all 3 of these video camera color areas. I'm mentioning course of your cam's capability to record images in RAW format . This is a format that supersedes any specified color areas.
RAW files catch color in the greatest bit depth possible; as much as 14-bits per color. RAW is not an acronym; it is more of a description. It is the recording of all the restricted color depth and uncompressed vibrant variety of the initial scene. Start RAW and disrobe from there.
.Video camera color areas described –-- Conclusion.
Congratulations on sticking to this short article through all the triviality.
By now, it most likely looks like electronic camera color area is more like deep space, however it doesn’’ t need to stay this technical. Merely keep in mind to catch images in RAW format (possibly in addition to catching them as JPG) and after that change the colors down the chain of recreation as the requirement determines.
Edit images in the electronic camera color areas of ProPhoto RGB or AdobeRGB to maintain as much color breathing space as needed. Those images predestined for print needs to be shifted to AdobeRGB, and decrease those images predestined for the Internet or slideshows to sRGB. Simple, enough!
The post Camera Color Spaces Explained –-- sRGB vs Adobe RGB vs RAW appeared initially on Digital Photography School . It was authored by Herb Paynter .
.
Read more about this at digital-photography-school.com
https://coolarticlespinner.com/camera-color-spaces-explained-srgb-vs-adobe-rgb-vs-raw/
0 notes
Text
Need to Recover EDB file Mailboxes - Are you facing Exchange server in accessible?
Facing Exchange server corruption or dirty shutdown issues? Do you want to convert your EDB file mailboxes to PST? We recommend you to try EdbMails EDB to PST converter application. Using EdbMails you can Restore Exchange mailbox to individual PST files with complete data. The whole folder structure of the original mailbox will be intact. Recover all your mails with complete mail and email body formatting, header details, Attachments, Embedded attachments in the mail body, appointments, and contacts, Task, Notes and Journal. EdbMails EDB to PST converter application does deep scanning of B-Tree data structure and find out every email and its corresponding items and create Individual PST files for each mailbox. EdbMails is an high performing application extract emails and its properties (Subject, sent and received Date & Time, To address, Cc, Bcc) by deep scan. No matter the size of the EDB file. It has been tested successfully with 5 TB EDB file data with more than 1000 mailboxes in that EDB file. EdbMails EDB to PST converter application will recover the corrupt or healthy or unmountable EDB files. It repairs and fixes if there is any index corruption in large EDB file. Support Microsoft Exchange servers like Exchange 2019, 2016, 2013, 2010, 2007 and 2003. No need of any Exchange services or Exchange server files. Just need EDB and STM (for Exchange 2003 and below versions) to convert EDB to PST files.
Main Features of EdbMails EDB to PST converter:
Preview of all the mailboxes / folders / items / item details High performance reliable export of mailboxes to PST file.
Extract any number of attachments and any size of attachments of an email / calendar / contact etc… Recover all the properties of an email like From, To, CC, BCC, subject, sent & received date and time, message-id, Set split size of PST file to Split the PST during export operation. Granular export, export based on subject, sent and received date, To and from address. Export the required data based on the filter applied.
Quick and easy to use the application. Recovers accidentally Deleted mailboxes / Mail items from EDB file.
EdbMails is a perfect application to recover your Exchange server database file in all condition. EdbMails is designed and built to diagnose the problems like dirty shutdown, File Index corruption, and fix the issue.
Main causes that lead to Exchange Server Mailbox Corruption. EDB file damage occurs because of logical and physical corruption. Physical Corruption: This occurs because of Hardware Failure. Chances of data corruption are of lowest level.
Logical Corruption: Logical corruption occurs at different levels. Database level: invalid indexes, cross object chain linkage, Database Engine failure. Application level: File header corruption, Access control corruption. Common Exchange server errors:
● Dirty shutdown State Exchange error
● Exchange Jet error 1018
● Exchange Jet error 1216
● Unable to mount Exchange database (hr=0x80004005, ec=-528)
● 1056749110 Exchange error
● Unable to initialize Exchange Information Store service – Error 0x8004010f
We recommend you to use EdbMails demo version before purchasing the license. Verify all the mailboxes and its folder structure and its data. EdbMails allows you to export 30 items per folder for each mailbox. Export the mailboxes and verify the folder structure and exported data in outlook PST file. For more details visit https://www.edbmails.com
youtube
0 notes
Text
The EdbMails OST to PST Converter
The EdbMails OST to PST Converter software allows for data recovery from even the most corrupt of Outlook OST files no matter what the size is. No longer have you to fear for loss of data in case of OST corruption thanks to EdbMails . EdbMails can fix any or all OST errors. This has a simple and rather intuitive user interface. Some important Features of OST to PST Converter: 1) Reliable OST to PST Converter tool: OST to PST Conversion without any data loss. More importantly the data within the original OST file remains untouched. 2) Forensic OST Repair tool: A forensic tool that can fix any OST errors you could come across easily thanks to its deep scanning algorithms. 3) Recovers everything: EdbMails recovers the emails with all the meta data like ‘subject’, ‘to address’, ‘from address’, ‘date and time’ ‘cc’, ‘bcc’, 'message id' etc. It even saves the background images, attachments (with all extensions), appointments, meeting schedules etc. 4)Extensive Filtering options: Extensive include/exclude filtering options to filter by subject, attachments, from/to address and date/time. 5) OST to Office 365/Live Exchange server Migrator: Direct OST migration to Office 365 and Live exchange server 6) Free trial version: You could easily download and try the free OST to PST Converter and export upto 30 items per folder. Steps to perform OST to PST conversion: 1. Launch EdbMails and select Export OST to PST method 2. Browse for the OST file to proceed with the OST to PST Export operation. Click the 'Continue' 3. Select the checkbox next to Mailboxes / folders in the application tree-view 4. Click the 'Export Selected Mailbox / Folders' button to export the OST file to PST.
0 notes
Text
Easiest method to Convert OST to PST
Let's talk about exporting OST files to PST. OST files aren't supposed to be directly accessible . They are automatically generated by Outlook when the need arises. Even if you delete it but a new one will take its place.
While an OST file has its utilities there can arise instances of OST corruption that may lead to problems in accessing OST contents and sometimes even hamper the proper functioning of Outlook as a whole.
Import OST to PST and recover OST data.
So what is a solution to this conundrum? What if I told you there is an awesome tool that will let you access the contents of OST with ease no matter how corrupt the file is . Yes its true and the tool I am talking about is EdbMails OST to PST Converter.
The tool to Convert OST to PST from EdbMails stands out from the rest of the tools due to its sheer reliability. The export speed that EdbMails offers is unparalleled. Support for direct migration to Office 365 and live exchange server makes EdbMails a one stop solution for all things exchange recovery.
EdbMails recovers the emails with all the metadata such ‘subject’, ‘to address’, ‘from address’, ‘date and time’ ‘cc’, ‘bcc’, 'message id' etc. Saves background images, attachments (with all extensions), appointments, meeting schedules etc. It also has extensive filtering options to help you export exactly what you need.
0 notes
Text
Hyper-Local Real Estate Market Data Allows Agents To Truly Be The “Area” Or Neighborhood Experts
This is the era of “big hyper-local data,” a time when brokers and agents are empowered more than ever to be the trusted local source for real estate market data.
According to a study in Realtor.org, 92% of home buyers said knowledge of the local real estate market was one of the skills they looked for in an agent.
Want to show that you are the neighborhood expert on your website?
You can do that by providing massive amounts of in-depth, hyper-local information. Here are some examples of the real estate market data you can add:
Recent property sales
Trends in homes sales: charts that show buyers and sellers the direction of the market over the past several quarters
Trends in home prices: very informative charts. Buyers and sellers want to know, are prices trending upward? Flat? Down?
School data: according to Realtor.com, one in three home buyers would move into a smaller home if it meant a better school district. A broker or agent can illustrate school district boundaries on their website. And even more valuable, allow their consumers to filter properties by School Attendance zones.
Municipal boundaries: taxes and services are all about where you live. Show buyers the different municipal boundaries.
Neighborhood demographics: a family wants to live where there are other families. Retired people want to live near other retirees. Show data on age, income, education, etc.
Cost of Living indices: one town can be a much more expensive place to live than another. Point out how far $1,000 will go in Town A compared to Town B.
Crime statistics: how safe is this neighborhood? Maybe the entire county has issues, but the statistics can show specific areas that perhaps have low crime rates.
Flood zone maps: last year was a record year for flood damage in the US. This would be a valuable resource to show and attract buyers.
Not only can agents show real estate market data for the county. They can drill down to the zip code and more importantly, down into the specific neighborhoods and subdivisions they are farming.
Real estate data APIs feed info to agents
The power of brokers and agents to provide a wealth of information has made a quantum leap.
Why?
Advances in data science have enabled national aggregators to gather millions of bits of hyper-local information from resources such as public records, and other sources.
These real estate data companies (disclosure: my employer is one of them) filter, sort, and warehouse this data on their servers. Then using a Real Estate Data API (Application Programming Interface), the companies “feed” pieces of this information to a local broker or agent.
All the broker or agent has to do is add a few snippets of code on their website. It’s that simple.
The agent doesn’t have to go out and gather this information for themselves. They don’t have to keep it current.
But the most important benefit is that consumers now can find this critical data on their local broker’s website. Says Christopher Brooks with District Houston Realty:
Our brokerage site benefits from the use of real estate market data by becoming a trusted source for hyper-local real estate information. The Houston real estate market covers an enormous land area, so by offering hyper-local data, customers and clients receive valuable neighborhood-specific information for their buying decisions. Recent homes sales data helps sellers understand pricing expectation in their local market.
This breakthrough offers tremendous advantages for agents. For one, it creates a new resource to attract leads. Consumers don’t need to go to a large national real estate portal for this data. They also don’t need to roam all over the web trying to find it.
Real estate-related websites are also discovering innovative ways to help brokers and agents with hyper-local data.
Remzy.com (which has been written about previously on the blog), for example, is a service that “Connects brokers and agents with off-market homeowners.” Founder David Marc Harris explained that he uses real estate market data to provide a tool for agents to find properties they know their buyers would like, but are not for sale at the time.
An agent knows a lot about the buyer they are working with. When options and inventory are low, we help agents keep their buyer shopping. Keep them in the game.
The Remzy website does this by closely examining detailed market data for a particular neighborhood that a buyer might be interested in. With a proprietary predictive algorithm, an agent can identify the homeowners who are more likely to sell.
Remzy created an effective way to reach out to a homeowner and start a conversation with them. The broker or agent selects that property. Remzy sends out a personalized offer letter via FedEx. If a homeowner is interested, they can call the agent directly.
The days of sending generic marketing letters to the whole neighborhood are over. This data helps them take a much more targeted and professional approach.
He said his letters have a 100% open rate due to the FedEx overnight delivery.
Because Remzy has access to an incredible database of information about properties, “agents are able to conduct much better targeting.”
I read an article a few years ago that said something along the lines of Real Estate Tech 1.0 was about bringing data online. Then 2.0 was about creating platforms to help agents and brokers aggregate and organize the data. I think we’ve begun to rapidly move toward 3.0 where now tools are being created to analyze the data and provide buying and selling insights.
Can tech entrepreneurs and developers predict who is most likely to want to sell their home with relative accuracy? There are signals in the data, that when combined and measured against other datasets, can help agents win more listings.
Another website, SetSchedule.com, uses hyper-local real estate data to generate leads for brokers and agents and then goes one step further and actually schedule appointments. Founder Roy Dekel said his service…
Is the first artificial intelligence lead exchange system. SetSchedule began with a simple idea to find, connect, confirm and send listing appointments to real estate agents and brokers.
SetSchedule has several strategies for generating leads for brokers and agents. One of them, called SetValue.com, uses hyper-local real estate market data to give homeowners and buyers an opportunity to see estimates on the value of a property. The website gathers data from several automated valuation models to give a range of estimates. While engaged in this process, SetSchedule creates several lead opportunities to gather contact information from interested consumers. It then arranges for brokers and agents to speak with these targeted prospects.
“In a competitive landscape, data is power,” Roy noted.
Use real estate market data to enhance social posts
In addition, brokers and agents now have an incredible resource for content they can promote on social media. Competition for eyeballs on Facebook, Twitter, Instagram and Pinterest is intense. About 90% of real estate agents report they regularly promote themselves on social media.
Instead of just listings, how great would it be to post charts showing the latest home sales activity in a particular neighborhood?
Or a chart with a trend line showing the direction of prices?
An upward swing can prompt a surge in phone calls or inquiries.
The great benefit of those posts is that the reader has to go back to a broker’s website to see the chart for further details. That visitor becomes an agent’s lead. Not someone else’s.
“The company and our agents both frequently use the data on our Facebook pages, our direct mailings to potential new clients, and in our listing presentation materials,” said Chris Saunders, marketing director with Roy Wheeler Realty in Charlottesville, VA. “It is a valuable and necessary aspect of our business at this point.”
The other benefit of adding large amounts of hyper-local data is for search engine rankings on Google and Bing. Adding relevant, real estate market data can help move a website up in the rankings. Sure, many of the top keywords for large markets are hard to beat.
But adding more of this local content to a website and aiming for less popular keywords, even neighborhood-specific keywords, could pay off in better rankings.
This advancements in big data technology have created a major breakthrough for local brokers and agents.
“The data on our website is extremely useful in bringing more traffic to our site and keeping their eyes on our pages longer. Our agents love being able to refer to the data, which instills a lot of trust and rapport with their clients,” added Saunders.
Take advantage of this tremendous leap in data technology. Don’t just tell prospects you are the agent with local knowledge. Now with real estate data API feed for displaying in-depth market data, you can SHOW them.
The post Hyper-Local Real Estate Market Data Allows Agents To Truly Be The “Area” Or Neighborhood Experts appeared first on GeekEstate Blog.
Hyper-Local Real Estate Market Data Allows Agents To Truly Be The “Area” Or Neighborhood Experts syndicated from https://oicrealestate.wordpress.com/
0 notes
Text
Hyper-Local Real Estate Market Data Allows Agents To Truly Be The “Area” Or Neighborhood Experts
This is the era of “big hyper-local data,” a time when brokers and agents are empowered more than ever to be the trusted local source for real estate market data.
According to a study in Realtor.org, 92% of home buyers said knowledge of the local real estate market was one of the skills they looked for in an agent.
Want to show that you are the neighborhood expert on your website?
You can do that by providing massive amounts of in-depth, hyper-local information. Here are some examples of the real estate market data you can add:
Recent property sales
Trends in homes sales: charts that show buyers and sellers the direction of the market over the past several quarters
Trends in home prices: very informative charts. Buyers and sellers want to know, are prices trending upward? Flat? Down?
School data: according to Realtor.com, one in three home buyers would move into a smaller home if it meant a better school district. A broker or agent can illustrate school district boundaries on their website. And even more valuable, allow their consumers to filter properties by School Attendance zones.
Municipal boundaries: taxes and services are all about where you live. Show buyers the different municipal boundaries.
Neighborhood demographics: a family wants to live where there are other families. Retired people want to live near other retirees. Show data on age, income, education, etc.
Cost of Living indices: one town can be a much more expensive place to live than another. Point out how far $1,000 will go in Town A compared to Town B.
Crime statistics: how safe is this neighborhood? Maybe the entire county has issues, but the statistics can show specific areas that perhaps have low crime rates.
Flood zone maps: last year was a record year for flood damage in the US. This would be a valuable resource to show and attract buyers.
Not only can agents show real estate market data for the county. They can drill down to the zip code and more importantly, down into the specific neighborhoods and subdivisions they are farming.
Real estate data APIs feed info to agents
The power of brokers and agents to provide a wealth of information has made a quantum leap.
Why?
Advances in data science have enabled national aggregators to gather millions of bits of hyper-local information from resources such as public records, and other sources.
These real estate data companies (disclosure: my employer is one of them) filter, sort, and warehouse this data on their servers. Then using a Real Estate Data API (Application Programming Interface), the companies “feed” pieces of this information to a local broker or agent.
All the broker or agent has to do is add a few snippets of code on their website. It’s that simple.
The agent doesn’t have to go out and gather this information for themselves. They don’t have to keep it current.
But the most important benefit is that consumers now can find this critical data on their local broker’s website. Says Christopher Brooks with District Houston Realty:
Our brokerage site benefits from the use of real estate market data by becoming a trusted source for hyper-local real estate information. The Houston real estate market covers an enormous land area, so by offering hyper-local data, customers and clients receive valuable neighborhood-specific information for their buying decisions. Recent homes sales data helps sellers understand pricing expectation in their local market.
This breakthrough offers tremendous advantages for agents. For one, it creates a new resource to attract leads. Consumers don’t need to go to a large national real estate portal for this data. They also don’t need to roam all over the web trying to find it.
Real estate-related websites are also discovering innovative ways to help brokers and agents with hyper-local data.
Remzy.com (which has been written about previously on the blog), for example, is a service that “Connects brokers and agents with off-market homeowners.” Founder David Marc Harris explained that he uses real estate market data to provide a tool for agents to find properties they know their buyers would like, but are not for sale at the time.
An agent knows a lot about the buyer they are working with. When options and inventory are low, we help agents keep their buyer shopping. Keep them in the game.
The Remzy website does this by closely examining detailed market data for a particular neighborhood that a buyer might be interested in. With a proprietary predictive algorithm, an agent can identify the homeowners who are more likely to sell.
Remzy created an effective way to reach out to a homeowner and start a conversation with them. The broker or agent selects that property. Remzy sends out a personalized offer letter via FedEx. If a homeowner is interested, they can call the agent directly.
The days of sending generic marketing letters to the whole neighborhood are over. This data helps them take a much more targeted and professional approach.
He said his letters have a 100% open rate due to the FedEx overnight delivery.
Because Remzy has access to an incredible database of information about properties, “agents are able to conduct much better targeting.”
I read an article a few years ago that said something along the lines of Real Estate Tech 1.0 was about bringing data online. Then 2.0 was about creating platforms to help agents and brokers aggregate and organize the data. I think we’ve begun to rapidly move toward 3.0 where now tools are being created to analyze the data and provide buying and selling insights.
Can tech entrepreneurs and developers predict who is most likely to want to sell their home with relative accuracy? There are signals in the data, that when combined and measured against other datasets, can help agents win more listings.
Another website, SetSchedule.com, uses hyper-local real estate data to generate leads for brokers and agents and then goes one step further and actually schedule appointments. Founder Roy Dekel said his service…
Is the first artificial intelligence lead exchange system. SetSchedule began with a simple idea to find, connect, confirm and send listing appointments to real estate agents and brokers.
SetSchedule has several strategies for generating leads for brokers and agents. One of them, called SetValue.com, uses hyper-local real estate market data to give homeowners and buyers an opportunity to see estimates on the value of a property. The website gathers data from several automated valuation models to give a range of estimates. While engaged in this process, SetSchedule creates several lead opportunities to gather contact information from interested consumers. It then arranges for brokers and agents to speak with these targeted prospects.
“In a competitive landscape, data is power,” Roy noted.
Use real estate market data to enhance social posts
In addition, brokers and agents now have an incredible resource for content they can promote on social media. Competition for eyeballs on Facebook, Twitter, Instagram and Pinterest is intense. About 90% of real estate agents report they regularly promote themselves on social media.
Instead of just listings, how great would it be to post charts showing the latest home sales activity in a particular neighborhood?
Or a chart with a trend line showing the direction of prices?
An upward swing can prompt a surge in phone calls or inquiries.
The great benefit of those posts is that the reader has to go back to a broker’s website to see the chart for further details. That visitor becomes an agent’s lead. Not someone else’s.
“The company and our agents both frequently use the data on our Facebook pages, our direct mailings to potential new clients, and in our listing presentation materials,” said Chris Saunders, marketing director with Roy Wheeler Realty in Charlottesville, VA. “It is a valuable and necessary aspect of our business at this point.”
The other benefit of adding large amounts of hyper-local data is for search engine rankings on Google and Bing. Adding relevant, real estate market data can help move a website up in the rankings. Sure, many of the top keywords for large markets are hard to beat.
But adding more of this local content to a website and aiming for less popular keywords, even neighborhood-specific keywords, could pay off in better rankings.
This advancements in big data technology have created a major breakthrough for local brokers and agents.
“The data on our website is extremely useful in bringing more traffic to our site and keeping their eyes on our pages longer. Our agents love being able to refer to the data, which instills a lot of trust and rapport with their clients,” added Saunders.
Take advantage of this tremendous leap in data technology. Don’t just tell prospects you are the agent with local knowledge. Now with real estate data API feed for displaying in-depth market data, you can SHOW them.
The post Hyper-Local Real Estate Market Data Allows Agents To Truly Be The “Area” Or Neighborhood Experts appeared first on GeekEstate Blog.
Hyper-Local Real Estate Market Data Allows Agents To Truly Be The “Area” Or Neighborhood Experts published first on https://medium.com/@YourChoice
0 notes