#Flubot malware
Explore tagged Tumblr posts
Link
#adware#antivirus#bombaslógicas#buenasprácticasdeseguridad#caballodeTroya#ciberseguridad#copiasdeseguridad.#deteccióndevirus#ejemplosdemalware#evolucióndevirus#Flubot#gusano#gusanos#historiadelosvirus#keyloggers#malware#proteccióncontravirus#Qbot#ransomware#ransomwareRyuk#rootkits#seguridadinformática#spam#spyware#Sunburst#tiposdevirus#troyano#virusinformático#virusmáscomunes2020-2024
1 note
·
View note
Text
Five steps of Wikipedia for Sunday, 10th September 2023
Welcome, Dzień dobry, Välkommen, Willkommen 🤗 Five steps of Wikipedia from "FluBot" to "ASCII". 🪜👣

Start page 👣🏁: FluBot "FluBot is a sophisticated SMS computer virus –specifically a banking Trojan– of global reach which aims to steal private data from Android smart phones. Unlike much malware, FluBot has proven exceptionally durable, coming in waves or "campaigns" with each redesign. It masquerades as innocuous..."
Step 1️⃣ 👣: Android (operating system) "Android is a mobile operating system based on a modified version of the Linux kernel and other open-source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. Android is developed by a consortium of developers known as the Open Handset Alliance, though its..."

Image by Google LLC
Step 2️⃣ 👣: API "An application programming interface (API) is a way for two or more computer programs to communicate with each other. It is a type of software interface, offering a service to other pieces of software. A document or standard that describes how to build or use such a connection or interface is called..."

Image by NASA Open Innovation Team
Step 3️⃣ 👣: ANSI-SPARC Architecture "The ANSI-SPARC Architecture (American National Standards Institute, Standards Planning And Requirements Committee), is an abstract design standard for a database management system (DBMS), first proposed in 1975.The ANSI-SPARC model however, never became a formal standard. No mainstream DBMS systems..."

Image licensed under CC BY 2.5? by Brian Shannon
Step 4️⃣ 👣: American National Standards Institute "The American National Standards Institute (ANSI AN-see) is a private nonprofit organization that oversees the development of voluntary consensus standards for products, services, processes, systems, and personnel in the United States. The organization also coordinates U.S. standards with..."

Image
Step 5️⃣ 👣: ASCII "ASCII ( ASS-kee),: 6 abbreviated from American Standard Code for Information Interchange, is a character encoding standard for electronic communication. ASCII codes represent text in computers, telecommunications equipment, and other devices. Because of technical limitations of computer systems at..."
Image by an unknown officer or employee of the United States Government
0 notes
Text
Beware of FluBot malware — NCC alerts Nigerians
Beware of FluBot malware — NCC alerts Nigerians
The Nigerian Communications Commission (NCC) has called on Nigerians to beware of an “extremely-damaging“ malware called, FluBot. This alert was contained in a statement signed by NCC’s Director, Public Affairs, on Friday. According to the statement, the FluBot malware “targets Androids with fake security updates and App installations”. The statement read: “The Nigerian Communications…

View On WordPress
0 notes
Text
NCC alerts Nigerians of new virus that steals banking details from phones
NCC alerts Nigerians of new virus that steals banking details from phones
The Nigerian Communications Commission has alerted Nigerians of a new malware, Flubot, that “targets Androids with fake security updates and App installations.” The NCC said its findings show that Flubot “impersonates Android mobile banking applications to draw fake web view on targeted applications” and its goal transcends stealing personal data and essentially targets stealing of credit card…

View On WordPress
#Androids#DHL#Fedex#Flubot#malware#NCC#Nigeria Computer Emergency Response Team (ngCERT)#Nigerian Communications Commission#Nigerians
0 notes
Text
Cybercriminals are Targeting Victims with Dangerous Malware through Fake COVID Vaccine Information
Same malicious intent, wrapped inside new bogus content hiding #malware -- #Xanjero
Hackers have put a new spin on an old malware deployment trick by fooling people into clicking dangerous links, disguised as important COVID info… Malware is an ever-present threat. It’s virtually impossible to keep track of all these malicious campaigns. This makes it much more difficult to find new threats. But, some become so large, infecting so many devices, and victimizing so many consumers,…

View On WordPress
0 notes
Text
Malware FluBot Menyamar sebagai Update Keamanan Android
Malware FluBot Menyamar sebagai Update Keamanan Android
Pengguna smartphone Android harap berhati-hati. Baru-baru ini malware FluBot menyebar dan menginfeksi banyak smartphone bersistem operasi Android yang pada akhirnya dapat mencuri akun dan password yang dimiliki pengguna. FluBot, dalam menjalankan aksinya, berupaya mengelabui pengguna agar percaya bahwa smartphone mereka terinfeksi malware dengan menampilkan pesan peringatan keamanan palsu.…

View On WordPress
0 notes
Link

Google Play Store Google के एंड्रॉइड ऑपरेटिंग सिस्टम को चलाने वाले उपयोगकर्ताओं के लिए ऐप्स और गेम को इंस्टॉल करने का सबसे सुरक्षित तरीका है, धन्यवाद कंपनी के एंटी-मालवेयर प्रोटेक्शन के लिए जो स्टोर पर अपलोड किए गए ऐप्स को स्कैन करते हैं। कंपनी गूगल प्ले प्रोटेक्ट, मालवेयर के लिए स्कैन करने का उपकरण भी उपलब्ध कराती है, जिसमें प्ले स्टोर के बाहर स्थापित ऐप भी शामिल हैं।
Read more: व्हाट्सएप पिंक' डाउनलोड किया? मालवेयर से छुटकारा पाने और अपने डिवाइस को ठीक करने का तरीका यहां बताया गया है
हालाँकि, Google की सुरक्षा के बावजूद, खतरनाक ऐप्स कभी-कभी उपयोगकर्ताओं के डिवाइसों के माध्यम से खिसकने और संक्रमित होने का प्रबंधन करते हैं, जैसे कि नए Flubot मैलवेयर, जो उपयोगकर्ताओं के पासवर्डों को लोकप्रिय ऐप के रूप में संदेश भेजकर चुराते हैं। बीबीसी द्वारा वोडाफोन यूके के बाद वायरस की उपस्थिति की सूचना दी गई, थ्री और ईई ने अपने उपयोगकर्ताओं को इसके अस्तित्व के प्रति सचेत किया।
टेक्स्ट संदेश घोटाला एसएमएस के माध्यम से फैलता है और सोशल इंजीनियरिंग पर निर्भर करता है, जो पैकेज डिलीवरी कंपनी के संदेश के रूप में प्रच्छन्न है और उपयोगकर्ताओं को अपनी डिलीवरी को ट्रैक करने के लिए एक ऐप इंस्टॉल करने के लिए कह रहा है। चूंकि ऐप Google Play Store पर उपलब्ध नहीं है, इसलिए लिंक की गई APK (पैकेज इंस्टॉलर) फ़ाइल को मैन्युअल रूप से डाउनलोड और इंस्टॉल किया जाना चाहिए, कुछ ऐसा जो औसत से बचना चाहिए अगर वे सुरक्षा निहितार्थ को नहीं समझते हैं या एप्लिकेशन के स्रो�� पर भरोसा नहीं करते हैं।
ब्रिटेन के राष्ट्रीय साइबर सुरक्षा केंद्र (NCSC) के अनुसार, जो उपयोगकर्ता मैलवेयर से संक्रमित हैं, उन्हें अपने डेटा की सुरक्षा के लिए उचित कदम उठाने होंगे। हालांकि यह अभी भी स्पष्ट नहीं है कि पासवर्ड और क्रेडेंशियल्स सहित उपयोगकर्ता जानकारी को कैसे आसानी से निकाला जा सकता है, यह सवाल उठाता है कि ऐप को अनइंस्टॉल करने के लिए Google प्ले प्रोटेक्ट कैसे मालवेयर को ध्वजांकित करता है और उपयोगकर्ताओं को संकेत देता है।
Also read: अपने फेसबुक प्रोफाइल को सुरक्षित कैसे रखें
हालांकि जो उपयोगकर्ता मालवेयर से प्रभावित होते हैं, उन्हें अपने किसी भी अधिक डेटा को कटने से रोकने के लिए किसी नए खाते में लॉग इन नहीं करना चाहिए, NCSC का कहना है कि उन्हें जल्दी से जल्दी अपने उपकरणों को रीसेट करना होगा - क्योंकि मैलवेयर एक पूर्ण डेटा मिटा नहीं सकता है। एनसीएससी के अनुसार, फ्लूबोट वायरस को स्थापित करने के बाद उन्हें किसी भी खाते पर पासवर्ड को आदर्श रूप से बदलना चाहिए।
नवीनतम टेक समाचार और समीक्षाओं के लिए yehbhidekho का अनुसरण करें, ट्विटर, फेसबुक हमारे साथ बने रहें। हमारे नवीनतम वीडियो के लिए, हमारे YouTube चैनल को सब्सक्राइब करें।
0 notes
Text
FluBot Android Malware Spreading Rapidly Through Europe, May Hit U.S. Soon
Source: https://www.proofpoint.com/us/blog/threat-insight/flubot-android-malware-spreading-rapidly-through-europe-may-hit-us-soon
4 notes
·
View notes
Text
Druk op politie was ook in 2022 hoog - samenleving verhardt
De druk op de politie bleef het afgelopen jaar groot. Zo steeg het totaal aantal misdrijven met 7% ten opzichte van 2021. Er werden in 2022 wel meer misdrijven opgelost (32%). Naast de stijging van het aantal misdrijven waren er klimaat- en stikstofprotesten, asielprotesten en geweld van hooligans. Regelmatig verhardden de protesten en zag de politie zich genoodzaakt om te begrenzen. Tijdens de jaarlijkse bijeenkomst met de pers keken regioburgemeester Hubert Bruls, hoofdofficier van justitie Marthyne Kunst en plaatsvervangend politiechef Gert Veurink terug op het jaar 2022. Corona De afgelopen jaren zagen we het criminaliteitsbeeld ten gevolge van corona veranderen. In die periode zagen we een dalende lijn van de traditionele criminaliteit zoals woninginbraken, diefstallen en overvallen mede omdat er meer thuis werd geleefd, gewinkeld en gewerkt. Cybercrime, waar we zowel het hacken van computers als bijvoorbeeld online fraude of sextortion onder scharen, nam tijdens coronatijd juist enorm toe. Ook werd er tijdens de coronaperiode vaker melding gemaakt van overlast door jeugd. Coronabeperkingen opgeheven In 2022, het jaar waarin de coronabeperkingen werden opgeheven, zien we dat deze effecten van corona beginnen te verdwijnen. Zo stegen zowel de woninginbraken (4% t.o.v. 2021) als de straatroven (5% t.o.v. 2021) het afgelopen jaar voor het eerst weer licht. Wel is dit aantal nog steeds aanzienlijk lager dan voor de coronaperiode. Het aantal overvallen daalde met 15% ten opzichte van 2021. In 2022 daalde het aantal meldingen overlast door jeugd flink, dit ging van 23.668 in 2021 naar 16.253. Het aantal cybercrimedelicten liet voor het eerst een lichte daling zien. Wel is er nog steeds een stijgende lijn te zien ten opzichte van voor corona. Toename verkeersongevallen letsel We zien de afgelopen jaren een continue stijging van het aantal verkeersongevallen met letsel. In 2022 steeg dit weer met 21%. Hierbij waren zeker 148 dodelijke slachtoffers te betreuren (toename van 25% t.o.v. 2021). Ook het geweld tegen politieambtenaren nam dit jaar toe naar bijna 3000 incidenten (ruim 2700 in 2021). Een andere flinke stijger is diefstal van fietsen en brom/snorfietsen. Hier is sprake van een stijging met 40% in vergelijking tot 2021. Cybercriminelen spelen in op actualiteit Binnen cybercrime zien we verschillende fenomenen die regelmatig veranderen, waarbij criminelen slim inspelen op de actualiteit zoals het terugvragen van de energiecompensatie. Zowel jongeren als ouderen zijn slachtoffer. De impact op slachtoffers is vaak groot. De aanpak van cybercrime is een speerpunt voor politie en Openbaar Ministerie (OM). Zorgelijk is het gegeven dat de gemiddelde leeftijd van verdachten daalt. Het OM ziet binnen de groep verdachten van cybercrime dat het percentage jongeren tot 23 jaar tussen 2018 en 2021 gestegen is van 25 procent naar 57 procent. Daar waar mogelijk probeert het OM de schade te verhalen. Het cybercrime team van de politie boekte het afgelopen jaar een aantal mooie successen. Zo slaagde het team er in juni in de verspreiding van schadelijke software (Flubot) te stoppen. Deze software verspreidde zich razendsnel via een valse sms van bekende pakketbezorgdiensten. Met de malware konden criminelen toegang krijgen tot de gegevens van het slachtoffer. Eenmaal in een telefoon, werden de contactpersonen gebruikt om het virus verder te verspreiden. Er waren al 10.000 slachtoffers gemaakt toen de software onschadelijk werd gemaakt. In oktober had het team een belangrijk aandeel in een actie tegen de ransomware-groep Deadbolt. Met ransomware houden criminelen computerbestanden in gijzeling. Slachtoffers moeten losgeld betalen om weer toegang tot hun bestanden te krijgen. Het lukte de politie tijdens een gerichte actie meer dan 150 decryptiesleutels van deze ransomware-groep te bemachtigen door een slimmigheid met bitcoinbetalingen. Met deze sleutels konden bestanden, zoals dierbare foto’s of administratie, weer ontgrendeld worden, zonder dat het de slachtoffers geld kostte. Bestrijden ondermijning prioriteit Ook in 2022 was het effect van ondermijnende georganiseerde criminaliteit zichtbaar in de eenheid. Zo werden er 14 drugslabs aangetroffen (in 2021 waren dit er 13) op verschillende plekken in de eenheid. De labs werden vooral in het zuidelijke deel van de eenheid Oost-Nederland aangetroffen maar ook het zuidoostelijke deel van Twente valt op. De aanleiding van het aantreffen van labs is divers en komt zowel uit opsporingsonderzoeken, meldingen van burgers als veiligheidsincidenten. Het aantal geconstateerde drugsdumpingen nam iets af van 36 in 2021 naar 32 in 2022. Impactvol was verder ondermeer de liquidatie van twee mannen op klaarlichte dag midden in een vol restaurant in Zwolle in maart 2022. Deze zware georganiseerde criminaliteit tast onze democratische rechtsstaat aan en de aanpak heeft daarom ook in 2023 prioriteit. Dit doen we in nauwe samenwerking en verbinding met publieke- en private partners. Snel gedagvaard Maatschappelijke onrust, met verschillende geplande en ongeplande protestacties tot gevolg, en ook voetbalwedstrijden, legden in 2022 een fors beslag op de capaciteit van de eenheid Oost-Nederland. De parate eenheden van de eenheid kwamen zo’n 183 keer in actie waarbij gemiddeld ongeveer 31 mensen werden ingezet. Het lukte het OM verdachten die werden aangehouden tijdens de protesten tegen het stikstofbeleid, snel voor de rechter te brengen. In totaal ging het in 2022 om 33 verdachten, verspreid over elf zittingen. Ook vandaag, vrijdag 13 januari, staan nog drie verdachten terecht voor strafbare feiten tijdens een protest op 1 december jongstleden in Zwolle. Het recht op demonstreren is een groot goed, maar als er sprake is van strafbare feiten en/of gevaar voor anderen, gaat het OM over tot vervolging. Capaciteitstekort blijft beperkt Een jaar geleden waarschuwde de driehoek voor capaciteitstekorten in de basisteams die enkele jaren zouden aanhouden. In 2022 blijken de tekorten enigszins mee te zijn gevallen. Werd vorig jaar nog rekening gehouden met scenario’s waarin in de basisteams 4 tot 6 procent onderbezetting zou ontstaan, in 2022 blijkt dat de tekorten beperkt bleven tot zo’n 2%. Er zijn in 2022 een kleine 200 politiemensen de basisteams ingestroomd. Verder krijgt de eenheid Oost-Nederland vanuit het regeerakkoord en de motie Hermans de komende jaren structureel 110 nieuwe politiemensen erbij. Dit betekent nog niet dat de teams direct verlichting voelen. Zo moeten nieuwe politiemedewerkers worden opgeleid en zal de begeleiding van nieuwe instromers de komende tijd de nodige inspanning vragen. Ook worden er nog steeds collega’s landelijk ingezet voor bewaken en beveiligen. De krapte was overigens ook voelbaar in de opsporing en de hele strafrechtketen. In het afgelopen jaar is gewerkt aan versterking en dat wordt ook het komend jaar doorgezet. De kracht van de eenheid Oost-Nederland is de gewoonte om elkaar te helpen om het werk zo goed mogelijk te verdelen. De driehoek signaleert tot slot dat de politie haar werk doet in een samenleving waarin sterk uitgesproken meningen veel aandacht krijgen en gezag soms ter discussie lijkt te staan. Daarom is het, nu meer dan ooit, van belang de verbinding met alle groepen in de samenleving verder te versterken en zo te blijven bouwen aan het vertrouwen in de politie. Voor de politie is iedereen gelijkwaardig. Zij streeft ernaar dat vrijheid en veiligheid in balans zijn. Ook in 2023 wil de politie in Oost-Nederland eraan bijdragen dat alle inwoners prettig met elkaar kunnen samenleven. Bron: OM Read the full article
0 notes
Text
How to stop google download english update

HOW TO STOP GOOGLE DOWNLOAD ENGLISH UPDATE HOW TO
HOW TO STOP GOOGLE DOWNLOAD ENGLISH UPDATE INSTALL
HOW TO STOP GOOGLE DOWNLOAD ENGLISH UPDATE FOR ANDROID
HOW TO STOP GOOGLE DOWNLOAD ENGLISH UPDATE ANDROID
HOW TO STOP GOOGLE DOWNLOAD ENGLISH UPDATE WINDOWS 8
Most devices provide Netflix as a pre-installed app that you can access from the main menu, or from a Netflix button on your remote. Using Netflix on smart TVs, streaming media players, game consoles, set-top boxes, or Blu-ray players If you have a ChromeOS computer, you can download the Netflix app from the Google Play Store.
HOW TO STOP GOOGLE DOWNLOAD ENGLISH UPDATE WINDOWS 8
If you have a Windows 8 or later computer, you can also download the Netflix app for Windows. Netflix can be accessed from your internet browser by visiting and signing in or creating a new account.
HOW TO STOP GOOGLE DOWNLOAD ENGLISH UPDATE INSTALL
To install Netflix, follow the link for your device from your smartphone or tablet. Downloading Netflix on smartphones and tablets The Netflix app may come pre-installed or you may need to download it.
HOW TO STOP GOOGLE DOWNLOAD ENGLISH UPDATE ANDROID
Whether this malware makes it to North America in any significant number or not, the functionality and the devastation already caused in Europe should heighten the call to action for all Android users – to watch out for suspicious messages and to install security software in order to prevent such extremely malicious apps from ever getting on their devices.Netflix is available on many devices. In the unfortunate scenario that the malware was installed on a device and banking or other activity has taken place since the installation took place, then contact the organizations concerned immediately to block access and where necessary change passwords, remembering to make them unique and strong. If you receive an unknown or unexpected SMS message with a clickable link, refrain from clicking the link and instead remove the message.
HOW TO STOP GOOGLE DOWNLOAD ENGLISH UPDATE HOW TO
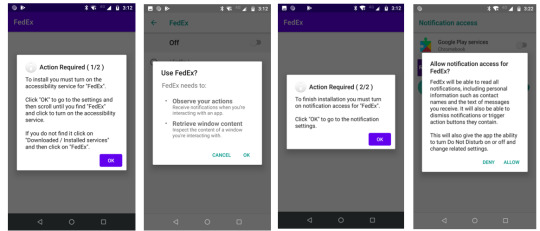
My colleague, Lukas Stefanko, has produced a short video with helpful instructions on how to remove this and any other malicious app: How to remove FluBotĪ compromised device may need to have the malware removed manually. Also, due to the extensive permissions granted, the threat actor is able to block the installation of many third-party antimalware solutions. The malicious app also disables Google Play Protect to avoid detection by the operating system’s built-in security. SMS messages and notifications from telecom carriers can be intercepted, browser pages can be opened, and overlays to capture credentials can be displayed. The contact list is exfiltrated from the device and sent to servers under the control of the bad actor, providing them with additional personal information and enabling them to unleash further attacks on other potential victims. Once installed and granted the requested permissions, FluBot unleashes a plethora of functionality, including SMS spamming, the theft of credit card numbers and banking credentials, and spyware. An example of the SMS message (in German) and the subsequent prompt to install the app can be seen below: The call to action of the message is for the user to click a link in order to download and install an app that has the same familiar branding as the SMS message but is actually malicious and has the FluBot malware embedded within it. The victim first receives an SMS message that impersonates a popular delivery logistics brand, such as FedEx, DHL, and Correos (in Spain). To avoid removal, the attacker implements mechanisms to stop the built-in protection offered by the Android OS and stops many third-party security software packages from being installed, an action many users would take to remove malicious software. This includes the potential to steal credit card numbers and access credentials to online banking accounts. If a victim is lured by the attacker into the malicious campaign, their entire Android device becomes accessible to the scammer. FluBot and TeaBot are detected by ESET products as variants of the Android/TrojanDropper.Agent family. In recent days, cybercriminals have begun to target Europeans with TeaBot (also known as Anatsa or Toddler), an Android malware family that uses exactly the same technique as FluBot to spread and to lure users into giving up their sensitive data. It’s also worth noting that this advice will help you stay safe from other Android malware strains. Here’s why you should be vigilant, how FluBot operates, and how you can remove this Android nasty from your device.
HOW TO STOP GOOGLE DOWNLOAD ENGLISH UPDATE FOR ANDROID
Why FluBot is a major threat for Android users, how to avoid falling victim, and how to get rid of the malware if your device has already been compromisedĪndroid malware known as FluBot is continuing to cause mayhem across some European countries, and there is speculation that the threat actors behind it may decide to target other geographies, including the United States.

0 notes
Text
June 2022: The Most Wanted Malware: MaliBot, New Banking, and Poses Danger to Users of Mobile Banking
The latest Global Threat Index June 2022 shows that MaliBot, a new Android banking malware, is now third in the list of most dangerous mobile malwares. It emerged after the takedown FluBot at May's end.
MaliBot pretends to be cryptocurrency mining apps under different names. It targets mobile banking users in order to steal financial data. MaliBot is similar to FluBot and uses phishing SMS messages (smishing), to lure victims to click on malicious links that will redirect them to a fake application.
Emotet, the most widespread malware overall, remains the most popular malware this month. Snake Keylogger is now in third place after an increase in activity from last month's eighth position. Snake Keylogger's primary function is to track keystrokes of users and send collected data to threat agents. Snake Keylogger was first delivered to us via PDF files in May. However, it has now been distributed through email attachments with Word attachments that are tagged as requests of quotations. Researchers also reported on a new variant of Emotet that targets Chrome browser users and has credit card theft capabilities.
Although it is always a good thing to see law enforcement succeed in taking down cybercrime groups and malwares such as FluBot, it wasn't long before a new mobile malware took its place. Cybercriminals know the importance of mobile devices in people's lives and they are constantly adapting their strategies to meet this reality. Mobile malware poses a serious threat to both enterprise and personal security. A robust mobile threat prevention solution is essential.
We also revealed this month that "Apache Log4j remote code execution" is the most exploited vulnerability. It affects 43% of all organizations globally. Web Server Exposed Git Repository information disclosure has a 42.3% global impact. With a global impact at 42.1%, "Web Servers Malicious URL Directory Traversal” is third.
Top Malware Family
*The arrows indicate the change in rank relative to the previous month.
Emotet continues to be the most widely used malware, with 14% global impact. Formbook and Snake Keylogger each have 4.4% impact on organizations around the world.
Emotet Emotet is a modular, advanced and self-propagating Trojan. Emotet was originally used to distribute banking Trojans, but it is now used to distribute other malware and malicious campaigns. Emotet uses multiple methods to maintain persistence and evade detection. It can also be spread via phishing spam email attachments and links.
– Formbook - Formbook is an Infostealer that targets the Windows OS. It was first discovered in 2016. For its strong evasion techniques, low price and high market appeal, it is called Malware-as-a-Service or MaaS (Malware-as-a-Service) in underground hacking forums. FormBook collects credentials from different web browsers, logs keystrokes, monitors and logs them, and can then download and execute files according its C&C.
Snake Keylogger - Snake is a modular .NET keylogger and credential stealer first spotted in late November 2020. It records keystrokes of users and sends the collected data to threat actors. The malware is extremely persistent and evasive, and can steal sensitive information from users.
Agent Tesla - Agent Tesla is an advanced RAT functioning as a keylogger and information stealer, which is capable of monitoring and collecting the victim's keyboard input, system keyboard, taking screenshots, and exfiltrating credentials to a variety of software installed on a victim's machine (including Google Chrome, Mozilla Firefox and the Microsoft Outlook email client).
XMRig - XMRig is open-source CPU mining software used to mine the Monero cryptocurrency. This open-source software is often used by threat actors to illegally mine victims' computers.
Remcos - Remcos is a RAT that first appeared in the wild in 2016. Remcos spreads itself via malicious Microsoft Office documents that are attached to SPAM email. It is designed to bypass Microsoft Windows UAC security to execute malware with high-level privileges.
Phorpiex - Phorpiex is a botnet (aka Trik) and has been since 2010. It controlled over a million infected hosts at its peak. It is well-known for spreading other malware families via spam attacks, as well as fueling large spam and sextortion operations.
Ramnit - Ramnit is a modular banking Trojan first discovered in 2010. Ramnit uses web session information to steal victim account credentials. This includes corporate and social network accounts as well as bank accounts. To contact the C&C server, and to download additional modules, the Trojan uses both hardcoded domains and domains generated using a DGA (Domain Generation Algorithm).
Glupteba - Glupteba is a backdoor which gradually matured into a botnet. It had a C&C address updating mechanism via public Bitcoin lists, a browser stealer capability, and a router exploiter by 2019.
NJRat - NJRat is a remote accesses Trojan, used both by Crimeware and State attackers. The Trojan was first discovered in 2012 and can capture keystrokes, view the victim's desktop, steal credentials from browsers, download and upload files, perform file manipulations and process them. NJRat spreads via phishing attacks, drive-by downloads and other means. It also has the ability to infect victims through infected USB keys and networked drives with the help of Command & Control software.
DIGITAL DEVICES LTD
Long before Apple set an average consumers mindset to replacing their handheld gadgets in two years, Digital Devices Ltd believed in Moore's law that computing will double every two years. With our heritage from the days of IBM Personal Computer XT, our founders have gone through the technology advancements of the 1990s and 2000s realizing that technology is an instrumental part of any business's success. With such a fast pace industry, an IT department can never be equipped with the tools and training needed to maintain their competitive edge. Hence, Digital Devices has put together a team of engineers and vendor partners to keep up with the latest industry trends and recommend clients on various solutions and options available to them. From forming close relationships with networking and storage vendors like Juniper, SolarWinds and VMWare to high-performance computing by HPE or AWS Cloud solutions, Digital Devices Limited offers the latest technology solutions to fit the ever-growing needs of the industry.
Our experts can guide you through the specifications and build cost efficiencies while providing high end, state-of-the-art customer services. We research and analyses market and its current demand and supply chain by offering wide range of bulk supplies of products like AKG C414 XLII, Shireen Cables DC-1021, Shireen Cables DC-2021, Dell p2419h monitor, Dell U2419H, Dell P2719H, Dell P2219H, Lenovo 62A9GAT1UK, LG 65UH5F-H and Complete IT Infrastructure products and services.
0 notes
Text
these 3 French applications are in the top 10 of victims!
these 3 French applications are in the top 10 of victims!
When you’re a pirate, you try to do things big! If we’re going to fly, we might as well do it on a large scale. All systems are good, from texting to phishing to credential theft. Flubot, Xenomorph, Sharkbot… we often warn you in our columns against these malware with frightening names. However, the important thing is never the shape, but always the substance… of your wallet! And to succeed in…

View On WordPress
0 notes
Text
Cybercriminalité : Démantèlement réussi d'un logiciel malveillant agressif visant les téléphones Android grâce à une coopération internationale avec les autorités de poursuite pénale suisses et d'autres partenaires
Cybercriminalité : Démantèlement réussi d’un logiciel malveillant agressif visant les téléphones Android grâce à une coopération internationale avec les autorités de poursuite pénale suisses et d’autres partenaires
Fin mai, une opération de grande envergure menée par Europol et la police néerlandaise, avec la participation d’autres autorités de poursuite pénale, a permis de stopper un logiciel malveillant (malware « FluBot ») qui se propageait à grande vitesse. Le maliciel, qui a infecté des téléphones mobiles équipés du système d’exploitation Android par le biais de messages textuels tels que des SMS a…

View On WordPress
0 notes
Text
Attention à vos SMS, un aperçu sur les smartphones
Attention à vos SMS, un aperçu sur les smartphones
Le malware FluBot continue son évolution et revient à la première menace des menaces les plus dangereuses pour les utilisateurs de smartphones Android. Une nouvelle campagne d’attaque est actuellement en cours. Le malware FluBot est un cheval de Troie bancaire qui émet dans votre téléphone pour voler vos identifiants de connexion et vos renseignements banques. Et ce, au profit d’une fausse…
View On WordPress
0 notes
Text
Be careful with your SMS, a scam is rampant on smartphones
Be careful with your SMS, a scam is rampant on smartphones
The FluBot malware continues its evolution and returns to the forefront of the most dangerous threats for Android smartphone users. A new attack campaign is currently underway. The FluBot malware is a banking Trojan that intrudes on your phone to steal your login credentials and banking information. And this, using a fake app that you downloaded. A life-threatening threat According to our…

View On WordPress
0 notes
Text
Police bust ‘FluBot’ cell phone scam

A mobile phone scam dubbed FluBot has been busted by the police of 11 countries that spread around the world via fake text messages, Dutch and EU police said.
Dutch cybercops led an operation in May targeting the malware, which infects Android phones using texts which pretend to be from a parcel firm or which say a person has a voicemail waiting.
Hackers would then steal bank details from infected phones, which automatically sent messages to other mobiles in the user’s contact list, passing on the scam like a flu virus.
“To date, we have disconnected ten thousand victims from the FluBot network and prevented over 6.5 million spam text messages,” Dutch police said in a statement.
The EU’s police agency Europol said FluBot was among “the fastest-spreading mobile malware to date” and was “able to spread like wildfire due to its ability to access an infected smartphone’s contacts.” Police had made the malware “inactive” but are still hunting the culprits, it said.
“This FluBot infrastructure is now under the control of law enforcement, putting a stop to the destructive spiral,” Europol said.
The countries involved in carrying out the investigation were Australia, the United States, Belgium, Finland, Hungary, Ireland, Romania, Spain, Sweden, Switzerland, and the Netherlands, coordinated by Europol’s cybercrime centre.
FluBot became one of the world’s most notorious cyberscams after it first emerged in December 2020, “wreaking havoc” around the world, Europol said.
The agency said the bug had compromised a “huge number of devices worldwide”, especially in Europe and the United States, with “major incidents” in Spain and Finland. Australian media said last year that FluBot was spreading “like a tsunami” with some users being bombarded by texts.
https://ift.tt/MlnbQB5
0 notes