#Fortinet FortiGuard Firewall
Explore tagged Tumblr posts
Text
Comprehensive Guide to Fortinet FortiGuard Firewall Security
Discover the key features and benefits of Fortinet FortiGuard Firewall Security and how it protects your business from cyber threats.

0 notes
Text

Fortinet FortiGate 70F Hardware plus FortiCare Premium and FortiGuard Unified Threat Protection (UTP) - 1 Year Subscription - FG-70F-BDL-950-12
The FortiGate 70F series integrate firewalling, SDWAN, and security in one appliance, making them perfect for building secure networks at distributed enterprise sites and transforming WAN architecture at any scale
For more information, Visit: https://newtrend.ae/product-category/fortinet/ Live chat: +971 507542792
#Fortinet#FortiGate70F#Firewall#SDWAN#Security#UTP#EnterpriseNetworking#WANTransformation#FortiCare#FortiGuard#CyberSecurity#SecureNetworks#FortinetUAE#TechSolutions#NetworkSecurity#DistributedSites#WANSecurity#FortinetPartners#FortinetProducts
0 notes
Text
Web Content Filtering Market Size, Share, Analysis, Forecast, and Growth Trends to 2032: North America and Asia-Pacific Show Explosive Growth

The Web Content Filtering Market size was valued at USD 4.62 Billion in 2023 and is expected to reach USD 13.11 Billion by 2032 and grow at a CAGR of 12.29% over the forecast period 2024-2032.
The Web Content Filtering Market is rapidly evolving as organizations worldwide place increased emphasis on cybersecurity, employee productivity, and data protection. As digital connectivity expands, enterprises, educational institutions, and government agencies are investing heavily in content filtering solutions to manage access to inappropriate, malicious, or distracting web content. The shift to hybrid work environments and rising cloud adoption have further accelerated demand for advanced filtering technologies integrated with AI, machine learning, and real-time threat intelligence.
The Web Content Filtering Market is also being driven by growing regulatory requirements, especially concerning data security and online safety. Companies are now seeking robust, customizable filtering tools that provide granular control over web access while ensuring compliance with industry standards. As more internet-enabled devices are integrated into corporate networks, content filtering is becoming a foundational component of enterprise cybersecurity strategy.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/4060
Market Keyplayers:
McAfee Inc. (McAfee Web Gateway, Cloud Secure Web Gateway)
Blue Coat Systems Inc. (Blue Coat WebFilter, ProxySG)
Palo Alto Networks Inc. (URL Filtering, PAN-DB)
Cisco Systems Inc. (Cisco Umbrella, Web Security Appliance)
Barracuda Networks Inc. (Barracuda Web Security Gateway, Web Application Firewall)
ContentKeeper Technologies (ContentKeeper Secure Internet Gateway)
Bloxx, Ltd. (Bloxx Web Filtering)
Fortinet (FortiGuard Web Filtering, FortiGate)
Interoute (Interoute Secure Web Gateway)
TitanHQ (WebTitan Cloud, WebTitan Gateway)
Clearswift (Clearswift Secure Web Gateway)
Cyren (Cyren Web Security)
Trend Micro (Trend Micro InterScan Web Security, Cloud App Security)
Untangle (NG Firewall Web Filter, Command Center)
Symantec Corporation (Symantec WebFilter, ProxySG)
Kaspersky Lab (Kaspersky Web Traffic Security, Endpoint Security)
Zscaler Inc. (Zscaler Internet Access, Zscaler Secure Web Gateway)
Sophos (Sophos XG Firewall, Web Gateway)
Forcepoint LLC (Forcepoint Web Security Cloud, NGFW)
WatchGuard Technologies Inc. (WatchGuard WebBlocker, Firebox Security Suite)
Market Analysis
The global web content filtering landscape has matured from simple URL blocking systems to comprehensive, policy-driven platforms. Vendors now offer dynamic filtering based on real-time behavior analysis, keyword inspection, SSL inspection, and user identity. Increased use of BYOD (Bring Your Own Device) policies and remote access have widened the scope of deployment across mobile platforms. Key industry verticals such as healthcare, finance, and education are at the forefront of adoption due to their high compliance needs and data sensitivity. Market consolidation is underway, with major cybersecurity companies acquiring smaller niche players to strengthen their filtering capabilities and expand their customer base.
Market Trends
Integration of AI and ML for smarter, predictive filtering
Rise in demand for cloud-based content filtering solutions
Increasing focus on secure web gateways (SWG) and zero trust architecture
Growth in mobile content filtering for remote and hybrid workforces
Enhanced filtering tools tailored for educational institutions
Compliance-driven adoption in finance, healthcare, and government sectors
Multi-language and contextual content filtering capabilities
Market Scope
Expanding Beyond Enterprises: Growing adoption in K–12 schools, universities, and libraries for student protection and content control
Smart Content Classification: Solutions now offer deep content analysis rather than relying solely on URL blacklists
Global Reach, Local Sensitivity: Vendors focusing on region-specific compliance and cultural content parameters
Customization is Key: Demand for flexible user policies, real-time reporting, and admin dashboards
IoT & Edge Filtering: Filtering expanding to IoT and edge environments with minimal latency
As the internet continues to evolve, the scope of web content filtering expands from being a basic IT tool to a strategic defense mechanism. It now plays a vital role in business continuity, brand integrity, and legal compliance.
Market Forecast
The future of the web content filtering market is not just growth—it's transformation. Driven by next-gen technology and complex threat landscapes, the market is expected to evolve into a more intelligent and adaptive ecosystem. The integration of filtering capabilities into broader cybersecurity platforms will shape how enterprises secure their digital perimeters. With emerging tech like 5G, edge computing, and AI-driven analytics, content filtering will move closer to real-time, contextual decision-making, empowering organizations to proactively mitigate risks before they escalate.
Access Complete Report: https://www.snsinsider.com/reports/web-content-filtering-market-4060
Conclusion
In a world where online interactions define workplace productivity, learning environments, and consumer engagement, the Web Content Filtering Market is no longer a backend IT concern—it's a frontline strategy. As organizations prioritize safe, efficient, and compliant web access, the demand for smart, scalable filtering solutions will only intensify. For vendors and stakeholders, this market represents not just a technological opportunity, but a societal mandate to safeguard digital experiences in an increasingly connected age.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Web Content Filtering Market#Web Content Filtering Market Scope#Web Content Filtering Market Share#Web Content Filtering Market Trends
0 notes
Text
Web Content Filtering Market Size, Share, Scope, Opportunities, Analysis, Forecast, Growth, and Industry Report 2032
The Web Content Filtering Market size was valued at USD 4.62 Billion in 2023 and is expected to reach USD 13.11 Billion by 2032 and grow at a CAGR of 12.29% over the forecast period 2024-2032.
Web Content Filtering Market is experiencing significant growth due to rising concerns over cybersecurity, data privacy, and regulatory compliance. Businesses, educational institutions, and government agencies are adopting advanced content filtering solutions to safeguard their networks and users. The increasing use of cloud-based security solutions and AI-driven filtering technologies is further driving market expansion.
Web Content Filtering Market continues to evolve as digital threats become more sophisticated. With the growing reliance on the internet for communication, work, and learning, organizations are prioritizing web filtering solutions to prevent malware, phishing attacks, and access to harmful or inappropriate content. The demand for real-time, AI-powered filtering tools is expected to surge, ensuring safe and secure browsing experiences across industries.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/4060
Market Keyplayers:
McAfee Inc. (McAfee Web Gateway, Cloud Secure Web Gateway)
Blue Coat Systems Inc. (Blue Coat WebFilter, ProxySG)
Palo Alto Networks Inc. (URL Filtering, PAN-DB)
Cisco Systems Inc. (Cisco Umbrella, Web Security Appliance)
Barracuda Networks Inc. (Barracuda Web Security Gateway, Web Application Firewall)
ContentKeeper Technologies (ContentKeeper Secure Internet Gateway)
Bloxx, Ltd. (Bloxx Web Filtering)
Fortinet (FortiGuard Web Filtering, FortiGate)
Interoute (Interoute Secure Web Gateway)
TitanHQ (WebTitan Cloud, WebTitan Gateway)
Clearswift (Clearswift Secure Web Gateway)
Cyren (Cyren Web Security)
Trend Micro (Trend Micro InterScan Web Security, Cloud App Security)
Untangle (NG Firewall Web Filter, Command Center)
Symantec Corporation (Symantec WebFilter, ProxySG)
Kaspersky Lab (Kaspersky Web Traffic Security, Endpoint Security)
Zscaler Inc. (Zscaler Internet Access, Zscaler Secure Web Gateway)
Sophos (Sophos XG Firewall, Web Gateway)
Forcepoint LLC (Forcepoint Web Security Cloud, NGFW)
WatchGuard Technologies Inc. (WatchGuard WebBlocker, Firebox Security Suite)
Market Trends
AI and Machine Learning Integration – AI-driven filtering tools are improving threat detection and content categorization in real time.
Cloud-Based Security Solutions – Cloud adoption is increasing, enabling businesses to implement scalable and flexible content filtering mechanisms.
BYOD and Remote Work Challenges – The rise of remote work and Bring Your Own Device (BYOD) policies is driving the need for robust web filtering solutions.
Stringent Compliance Regulations – Industries such as healthcare, finance, and education must adhere to strict regulatory requirements, boosting market demand.
Enquiry of This Report: https://www.snsinsider.com/enquiry/4060
Market Segmentation:
By Component
Solutions
Services
By Deployment
On-premises
Cloud-based
By End User
Enterprises
Educational Institutions
Government
Healthcare
Market Analysis
Key Industry Players: Major companies such as Cisco, Symantec, McAfee, and Palo Alto Networks are investing in AI-driven filtering solutions.
Enterprise Adoption: Large organizations and SMEs are integrating web filtering tools into their cybersecurity strategies to protect sensitive data.
Regional Expansion: North America leads the market, while Asia-Pacific is emerging as a key growth region due to increasing digitalization and cybersecurity awareness.
Future Prospects
Next-Gen AI and Behavioral Analytics: AI-powered content filtering will evolve to detect new threats and prevent cyberattacks more effectively.
5G and IoT Security Enhancements: With the expansion of 5G networks and IoT adoption, web filtering solutions will play a crucial role in securing connected devices.
Personalized Filtering for Individuals: Consumer-focused web filtering applications will gain traction, providing safer browsing for families and individuals.
Government and Enterprise Collaborations: Increased partnerships between governments and cybersecurity firms will drive advancements in web filtering technologies.
Access Complete Report: https://www.snsinsider.com/reports/web-content-filtering-market-4060
Conclusion
The Web Content Filtering Market is set for continuous growth as organizations prioritize cybersecurity and regulatory compliance. Advancements in AI, cloud computing, and real-time filtering will shape the future of web security. As digital threats evolve, businesses and individuals alike will increasingly rely on robust content filtering solutions to ensure safe and secure online experiences.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes
Photo

FIREWALL FORTINET FORTIGATE 60F, ALÁMBRICO, 10GBIT/S, 10X RJ-45, INCLUYE GARANTÍA FORTICARE Y LICENCIA FORTIGUARD 24X7 UTP 1 AÑO, FG-60F-BDL-950-12
0 notes
Text
Shop for the best quality firewalls in Dubai UAE

Fortinet fg 80f firewall uniquely meets the performance needs of hyper-scale and hybrid IT architectures, enabling organizations to deliver optimal user experience and manage security risks for better business continuity with reduced cost and complexity.
Protect your network with IPS and advanced Malware plus Email and web Protection with the Unified Threat Protection Bundle. The recommended use case for UTP is for NGFW and Secure Web Gateway.
Protects against malware, exploits, & malicious websites in both encrypted & non-encrypted traffic, prevents and detects known attacks using threat intelligence from FortiGuard Labs security services. Engineered for Innovation using security processors (SPU) to deliver the industry’s best threat protection performance and ultra-low latency, provides industry-leading performance and protection for SSL encrypted traffic including the first firewall vendor to provide TLS 1.3 deep inspection
#costtocost#dubai#uae#business#it services#it support#firewalls in dubai#firewall#fortinet firewall#fortigate 100f#fortigate 80f#fortigate 60f#best electronics and it retailer#electronics and it supplier in uae#it networking
0 notes
Text
Tính năng Web filter dựa trên Category của Fortinet: Dịch vụ này tận dụng tối đa các thông tin tình báo về mối đe dọa hàng đầu trong ngành từ FortiGuard Labs. 66 triệu URL độc hại/lừa đảo/spam bị chặn bởi FortiGuard Labs, thông qua khoảng 307 triệu URL được phân loại. Web Filter của FortiGuard khai thác cơ sở dữ liệu bao gồm hàng trăm triệu URL được phân loại thành hơn 90 danh mục để trao quyền kiểm soát và báo cáo web chi tiết cho người dùng.
Xem tại: https://viettuans.vn/so-sanh-firewall-fortinet-fg-60f-va-fg-70f

0 notes
Text
Chinese state hackers infect critical infrastructure throughout the US and Guam

peterschreiber.media | Getty Images
A Chinese government hacking group has acquired a significant foothold inside critical infrastructure environments throughout the US and Guam and is stealing network credentials and sensitive data while remaining largely undetectable, Microsoft and governments from the US and four other countries said on Wednesday.
The group, tracked by Microsoft under the name Volt Typhoon, has been active for at least two years with a focus on espionage and information gathering for the People’s Republic of China, Microsoft said. To remain stealthy, the hackers use tools already installed or built into infected devices that are manually controlled by the attackers rather than being automated, a technique known as "living off the land." In addition to being revealed by Microsoft, the campaign was also documented in an advisory jointly published by:
• US Cybersecurity and Infrastructure Security Agency (CISA) • US Federal Bureau of Investigation (FBI) • Australian Cyber Security Centre (ACSC) • Canadian Centre for Cyber Security (CCCS) • New Zealand National Cyber Security Centre (NCSC-NZ) • United Kingdom National Cyber Security Centre (NCSC-UK)
Besides the living-off-the-land technique, the hackers further obscured their activity by using compromised home and small office routers as intermediate infrastructure that allows communications with infected computers to emanate from ISPs that are local to the geographic area. In Microsoft’s advisory, researchers wrote:
To achieve their objective, the threat actor puts strong emphasis on stealth in this campaign, relying almost exclusively on living-off-the-land techniques and hands-on-keyboard activity. They issue commands via the command line to (1) collect data, including credentials from local and network systems, (2) put the data into an archive file to stage it for exfiltration, and then (3) use the stolen valid credentials to maintain persistence. In addition, Volt Typhoon tries to blend into normal network activity by routing traffic through compromised small office and home office (SOHO) network equipment, including routers, firewalls, and VPN hardware. They have also been observed using custom versions of open-source tools to establish a command and control (C2) channel over proxy to further stay under the radar.
The Microsoft researchers said that the campaign is likely designed to develop capabilities for “disrupting critical communications infrastructure between the United States and Asia region during future crises.” Guam is an important US military because of its Pacific ports and the air base it provides. As tensions over Taiwan have simmered, the strategic importance of Guam has become a focal point.
The initial entry point for the Volt Typhoon compromises is through Internet-facing Fortinet FortiGuard devices, which in recent years have proved to be a major beachhead for infecting networks. By exploiting vulnerabilities in FortiGuard devices that admins have neglected to patch, the hackers extract credentials to a network’s Active Directory, which stores usernames, password hashes, and other sensitive information for all other accounts. The hackers then use that data to infect other devices on the network.
“Volt Typhoon proxies all its network traffic to its targets through compromised SOHO network edge devices (including routers),” Microsoft researchers wrote. “Microsoft has confirmed that many of the devices, which include those manufactured by ASUS, Cisco, D-Link, NETGEAR, and Zyxel, allow the owner to expose HTTP or SSH management interfaces to the Internet.”
The remainder of the advisory mostly outlines indicators of compromise that admins can use to determine if their networks have been infected.
Microsoft researchers wrote:
In most cases, Volt Typhoon accesses compromised systems by signing in with valid credentials, the same way authorized users do. However, in a small number of cases, Microsoft has observed Volt Typhoon operators creating proxies on compromised systems to facilitate access. They accomplish this with the built-in netsh portproxy command.
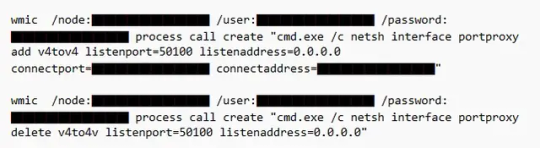
Volt Typhoon commands creating and later deleting a port proxy on a compromised system
In rare cases, they also use custom versions of open-source tools Impacket and Fast Reverse Proxy (FRP) to establish a C2 channel over proxy.
Compromised organizations will observe C2 access in the form of successful sign-ins from unusual IP addresses. The same user account used for these sign-ins may be linked to command-line activity conducting further credential access. Microsoft will continue to monitor Volt Typhoon and track changes in their activity and tooling.
Among the industries affected are communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education. The advisories provide guidance for disinfecting any networks that have been compromised.
0 notes
Text
Mastering Fortinet Firewall Management for Cyber Defense

Introduction In this article, we will discuss the best practices for mastering Fortinet firewall management. In today's digital age, cybersecurity has become a top priority for businesses of all sizes. With the increasing number of cyber threats, it is essential to have a robust firewall in place to protect your network and data. Fortinet is a leading provider of cybersecurity solutions, and their firewall is one of the most popular in the market. However, having a Fortinet firewall is not enough; you need to know how to manage it effectively to ensure unbeatable cyber defense 1. Keep Your Firewall Up-to-Date2. Configure Your Firewall Properly3. Monitor Your Firewall Regularly4. Implement Multi-Factor Authentication5. Use VPN for Remote Access6. Conduct Regular Security AuditsCase Study 1: Healthcare ProviderCase Study 2: Financial Institution Understanding Fortinet Firewall Fortinet firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It is designed to protect your network from unauthorized access, malware, and other cyber threats. Fortinet firewall uses a combination of hardware and software to provide comprehensive security features, including intrusion prevention, antivirus, web filtering, and application control. An example of Fortinet firewall in action could be a company that uses it to protect their internal network and data from cyber threats. The firewall would monitor all incoming and outgoing traffic on the network, and based on predetermined security rules, it would allow or deny access to certain resources. For example, if an employee tries to access a suspicious website or download a potentially harmful file, the Fortinet firewall would block that traffic to prevent it from infecting the network with malware. Additionally, the firewall could be configured to block unauthorized access attempts from outside the company, such as hackers or cybercriminals. This would help to keep the company's data safe and secure, and prevent any data breaches or cyber attacks from occurring. Best Practices for Fortinet Firewall Management To ensure unbeatable cyber defense, you need to follow these best practices for managing your Fortinet firewall: 1. Keep Your Firewall Up-to-Date Fortinet regularly releases firmware updates to address security vulnerabilities and improve performance. It is essential to keep your firewall up-to-date with the latest firmware to ensure optimal security. You can check for firmware updates through the Fortinet support portal or the FortiGuard service. 2. Configure Your Firewall Properly Configuring your firewall properly is crucial to ensure that it provides the necessary protection for your network. You need to define security policies that specify which traffic is allowed or blocked based on the source, destination, and type of traffic. You should also configure your firewall to log all traffic to detect any suspicious activity. 3. Monitor Your Firewall Regularly Monitoring your firewall regularly is essential to detect any security threats and ensure that it is functioning correctly. You should review the firewall logs daily to identify any suspicious activity and take appropriate action. You can also use Fortinet's FortiAnalyzer to analyze firewall logs and generate reports. 4. Implement Multi-Factor Authentication Multi-factor authentication adds an extra layer of security to your network by requiring users to provide additional authentication factors, such as a password and a token. Fortinet supports multi-factor authentication, and you should implement it to prevent unauthorized access to your network. 5. Use VPN for Remote Access Virtual Private Network (VPN) provides a secure connection between remote users and your network. Fortinet supports VPN, and you should use it for remote access to ensure that your network is protected from unauthorized access. 6. Conduct Regular Security Audits Regular security audits are essential to identify any security vulnerabilities and ensure that your firewall is providing the necessary protection. You should conduct security audits at least once a year to identify any weaknesses and take appropriate action. Case Studies Here are some case studies that demonstrate the effectiveness of Fortinet firewall in providing unbeatable cyber defense: Case Study 1: Healthcare Provider A healthcare provider was experiencing frequent cyber attacks, which resulted in data breaches and downtime. They implemented Fortinet firewall and configured it properly to block unauthorized access and detect any suspicious activity. They also implemented multi-factor authentication and VPN for remote access. As a result, they were able to reduce cyber attacks by 90% and improve their network performance. Case Study 2: Financial Institution A financial institution was facing a significant threat from cyber attacks, which resulted in financial losses and reputational damage. They implemented Fortinet firewall and configured it to block unauthorized access and detect any suspicious activity. They also conducted regular security audits to identify any weaknesses and take appropriate action. As a result, they were able to reduce cyber attacks by 95% and improve their overall security posture. Fortinet firewall is an essential component of your cybersecurity strategy, and mastering its management is crucial to ensure unbeatable cyber defense. By following the best practices discussed in this article, you can configure your firewall properly, monitor it regularly, and implement additional security measures to protect your network and data. Remember to keep your firewall up-to-date, configure it properly, monitor it regularly, implement multi-factor authentication and VPN, and conduct regular security audits. By doing so, you can ensure that your network is protected from cyber threats and maintain your business's reputation and profitability. Read the full article
0 notes
Text
Cyber Security Insurance Products
New Post has been published on https://www.aheliotech.com/blog/cyber-security-insurance-products/
Cyber Security Insurance Products
As your trusted Network Service Provider, AhelioTech is here to help you understand the direction we see Cyber Security and Technology Liability Insurance moving. You may have already implemented some of these practices but as Cyber Security needs advance, AhelioTech continues to provide topics of discussion for your security posture. We have included some areas which customers like you are asking to discuss.
Multi-Factor Authentication
Multi-factor authentication (MFA) is a security product that is used to verify a user’s identity at login. It adds two or more identity verification steps to user logins by utilizing secure authentication tools. This is an additional layer of defense to prevent a breach on multiple local and/or mobile devices that may be difficult to secure otherwise.
AhelioTech recommends Duo Mobile for MFA to protect your local computer logins, Microsoft 365 logins, VPN and network remote access, along with many other applications. Securing your data at all levels and endpoints is made easier with MFA.
Phishing and Cyber Security User Training and Awareness
Approximately 90% of Cyber Security attacks and breaches occur due to phishing. The AhelioTech Phishing and Cyber Security User Training and Awareness Platform powered by Huntress Curricula addresses the boring ‘Death by PowerPoint’ information security awareness training that drives employees to resent security instead of embracing it. Our behavioral science approach trains employees using short, memorable stories based on real-world cyber-attacks.
It is a fact that user error is the weakest link in Technology and Cyber Security. AhelioTech helps educate your users of these potential pitfalls. Contact AhelioTech today to discuss training options.
EDR & MDR
EDR is the baseline monitoring and threat detection tool for endpoints and the foundation for every Cyber Security strategy. MDR rapidly identifies and limits the impact of threats without the need for constant human monitoring.
AhelioTech recommends Huntress to both manage Microsoft Defender and provide enhanced security layers via persistent foothold and ransomware canary monitoring, external recon, process insights and a threat ops team for active threat hunting.
Next-Generation Firewalls
Next Gen Firewalls (NGFWs) are deep-packet inspection firewalls that move beyond port/protocol inspection and blocking to add application-level inspection, intrusion prevention, and bring intelligence from outside the firewall.
AhelioTech recommends Fortinet firewalls to address the need for a NGFW. These firewalls can be licensed for many levels of protection, including the most common of protection levels – the UTP bundle, which includes FortiGuard IPS Service, FortiGuard Anti-Malware Protection (AMP) — Antivirus, Mobile Malware, Botnet, CDR, Virus Outbreak Protection and FortiSandbox Cloud Service, FortiGuard Web Security — URL and web content, Video and Secure DNS Filtering, FortiGuard Anti-Spam. Our trained professionals are here to help you determine what this means for your network security.
DKIM & DMARC
Domain Keys Identified Mail (DKIM) is an email authentication technique that allows the recipient to confirm that an email was sent and authorized by the owner of that domain by giving the email a digital signature.
Once the recipient determines that an email is signed with a valid DKIM signature and confirms that the body of the message and attachments have not been modified, it allows the email to be delivered. DKIM signatures are hidden from end-users and validation is done on a server level preventing potential user error of opening malicious emails.
Domain-based Message Authentication, Reporting and Conformance (DMARC) is an email authentication protocol. It gives email domain owners the ability to protect their domain from unauthorized use, commonly known as Email Spoofing. The purpose of implementing DMARC is to protect a domain from being used in email attacks.
AhelioTech has trained experts to assess your organization and determine the needed DKIM and DMARC protections.
Internal and External Security Scanning
AhelioTech Network Scanning and Threat Detection, powered by Nessus Professional vulnerability, scanning provides a point-in-time vulnerability scan for all network assets. Performing these scans allows for tracking and remediation of any identified security issues, as well as satisfies scanning requirements for many Cyber Security and Cyber Liability Insurance requirements.
AhelioTech is Your Technology and Cyber Security Tool
Cyber Liability Insurance requirements vary depending on a multitude of factors including your industry and your overall network structure. AhelioTech is here to help you navigate those requirements and protect your organization.
Contact AhelioTech Today for More Information.
0 notes
Text
Fortinet FortiGuard Firewall: Security Solutions for Financial Institutions
Learn how Fortinet FortiGuard Firewall enhances cybersecurity and regulatory compliance for financial institutions.
0 notes
Text
Advantages of Fortinet labs
Using the use of a URL filter, fortinet labs created FortiGuard Web Filtering, online filtering software that is used by businesses and schools to limit access to various websites. Administrators of a school or company could want to filter out improper, offensive, or unlawful content or stop media streaming sites from hogging too much bandwidth and sluggish the network.
FortiGuard's ability to block content using both hardware and software controls makes it exceptionally effective. In particular, it works well to stop malware downloads from rogue or compromised websites. Regrettably, FortiGuard may also unintentionally block websites that offer reputable and helpful content.
Open FortiGuard likely so you can continue to be productive. Also, IT managers don't want you to infect their computers with malware that you unintentionally downloaded. As a result, it shouldn't come as a surprise that networks employ website-blocking software like FortiGuard Web Filtering.
Also, networks utilize FortiGuard Web Filtering for good reason: to stop malicious files and offensive information from getting onto your network! You'll be relieved to learn that it's not particularly difficult to get around FortiGuard Web Filtering if you really must.
How Does Web Filtering by Fortinet Operate?
There are many ways to do this, including adding the IP address of the website in firewall's block list or preventing routers from accessing the IP address of the server that hosts the website.
In order to determine whether to ban or reroute websites, FortiGuard Web Filtering uses DNS web filtering, which involves using DNS lookups to obtain webpage ratings. The procedure can be controlled with DNS filtering services.

The eve ng windows 7 prohibit users from accessing content that can impair productivity or offend, block access to dangerous and risky websites, and prevents malware from being downloaded. This method uses straightforward techniques to get around blocks, such as supplying a website's IP address rather than its URL.
The user will get a notification from Fortinet informing them that access has been blocked whenever they try to access a blocked site on a block list. All-access attempts are recorded in log files created by the Fortinet application.
Can I still access websites blocked by Fortinet?
Web filtering by Fortinet will prevent access to specific websites. You have a variety of methods available to you if you want to unblock them. Simply request that the Fortinet Web Filtering tool administrator provide you access to the particular websites you require. This is the most simple method, but it may not be possible to open the filtering such that risky websites are also made available.
Access the website using mobile data. Although this method is the fastest and possibly most convenient, keep in mind that you will use some of your data allotments.
If there is a duplicate of the website you're looking for, use an alternative domain name to access it. To see if another domain name is available, you'll need to conduct an online search.
0 notes
Text
Fortinet FortiGate FG-40F
The new generation FortiGate Firewall 40F (FG-40F) series is ideal for building security-driven networks in the distributed enterprise sites and WAN architecture transformation at any scale. With FortiGuard's rich suite of AI/ML-based security services and our integrated Security Fabric platform, the FortiGate FortiWiFi 40F series delivers coordinated, automated, end-to-end threat protection in all use cases. FortiGate has the first integrated SD-WAN and zero-trust network access (ZTNA) inforcement within the NGFW solution and is powered by a single OS. FortiGate 60F automatically controls, validates, and facilitates user access to applications and ensures consistency with a seamless and optimized user experience.
FortiOS everywhere
FortiOS, Fortinet's advanced operating system
FortiOS enables the convergence of high-performance networking and security across servers Fortinet Security Fabric. Because it can be deployed anywhere, it provides a consistent and Contextual security posture in network, endpoint and multi-cloud environments. FortiOS powers all FortiGate deployments, whether physical or virtual devices such as container or as a cloud service. This universal deployment model enables consolidation from multiple technologies and use cases into organically assembled best-in-class capabilities, unified operating system and ultra-scalability. The solution enables organizations to protect all edges, simplify operations and run your business without compromising performance or security. FortiOS dramatically expands the Fortinet Security Fabric's ability to provide advanced AI/ML-based services, inline advanced sandbox detection, integrated ZTNA enforcement, and more. Provides protection across hybrid deployment models for hardware, software and Software-as-a-Service with SASE. FortiOS extends visibility and control, ensuring consistent deployment and enforcement a simplified unified policy and governance framework. Its (FG-40F) security policy allows centralized management across large networks with the following key attributes:
• Interactive expansion and topology viewers that display real-time status
• Click-to-click remediation that provides accurate and fast protection against threats and exploits
• Unique threat score system correlates weighted threats with users and prioritizes investigations.
FortiConverter service
The FortiConverter service provides a seamless migration that helps organizations transition from a wide range of legacy firewalls to FortiGate Firewalls of the next generation quickly and easily. The service eliminates errors and redundancy by using best practices with advanced methodologies and automated processes. Organizations can accelerate the protection of their network with the latest FortiOS technology.
FortiGuard Services FortiGuard AI security
FortiGuard's rich suite of security services counters threats in real-time using AI, coordinated protection designed by FortiGuard Labs researchers, engineers and security threat researchers, and forensic specialists.
0 notes
Text
BEST NETWORK SECURITY PRODUCT: FG-60F-BDL-950-12
Secure SD-WAN ASIC SOC4
• Combines a RISC-based CPU with Fortinet's proprietary Security Processing Unit (SPU).
content and network processors for unmatched performance
• Provides the fastest application identification and management for efficient business
operation
• Accelerates IPsec VPN FG-60F-BDL-950-12 performance for the best user experience with direct Internet access
• Enables the best NGFW security and deep SSL inspection with high performance
• Extends security to the access layer and enables SD branch transformation with accelerated a
integrated switch and access point connectivity.
FortiCare FG-60F-BDL-950-12
Fortinet is dedicated to helping our customers succeed with FortiCare every year
to help thousands of organizations get the most out of our Fortinet Security Fabric solution. Our
The lifecycle portfolio offers Design, Deploy, Operate, Optimize and Evolve services. Work
services offer device-level FortiCare Elite with extended SLAs to meet our customers' requirements
operational and availability needs. In addition, we provide our customized services at the account level
rapid incident resolution and proactive care offering to maximize security and performance
deploying Fortinet.
Use cases
Next-Generation Firewall (NGFW)
• FortiGuard Labs' suite of AI-powered security services – natively integrated with yours
NGFW – secures the web, content, and devices and protects networks from ransomware and
sophisticated cyber attacks
• Real-time SSL inspection (including TLS 1.3) provides complete visibility into users, devices and
applications through the attack surface
• Fortinet's patented SPU (Security Processing Unit) technology provides industry-leading performance
high-performance protection.
Secure SD-WAN
• FortiGate WAN Edge powered by a single OS and unified security and management framework
and systems transform and secure WAN networks
• Provides a superior quality of experience and an effective security position to work from anywhere
where models, SD-Branch and cloud-first WAN FG-60F-BDL-950-12 use cases
• Achieve operational efficiencies at any scale through automation, deep analytics and
self-healing.
Universal ZTNA
• Control access to applications regardless of the user's location and location
the application is hosted for the universal application of access policies
• Provide extensive validation, review, and policy enforcement before a request is granted
approach - every time
• Agent-based access with FortiClient or agent-less access via a guest or BYOD proxy portal.
FortiGuard packages
FortiGuard Labs delivers a range of security intelligence services to augment the FortiGate firewall platform.
With one of these FortiGuard packages, you can easily optimize the protection capabilities of your FortiGate.
FG-60F-BDL-950-12
FortiCare Elite services offer extended service level agreements (SLAs) and accelerated problem resolution. This
advanced support offer provides access to a dedicated support team. One-touch ticketing
an expert technical team simplifies the solution. This option also provides extended end-of-engineering support
(EoEs) for 18 months for more flexibility and access to the new FortiCare Elite portal. This intuitive portal
provides a unified view of device health and security.
0 notes
Text
Fortinet NSE7_EFW-7.0 Practice Test Questions
You can get the latest NSE7_EFW-7.0 Practice Test Questions to pass your Fortinet NSE 7 - Enterprise Firewall 7.0 exam. PassQuestion provides you the best NSE7_EFW-7.0 Practice Test Questions which can help you to prepare Fortinet NSE7_EFW-7.0 Exam smoothly and efficiently. You can use the latest and up-to-date NSE7_EFW-7.0 real questions and answers for the Fortinet NSE 7 - Enterprise Firewall 7.0 Exam. If you want to have an understanding of different topics, then you need to use the best available NSE7_EFW-7.0 Practice Test Questions and this can help you pass the Fortinet NSE 7 - Enterprise Firewall 7.0 NSE7_EFW-7.0 Exam with ease.
NSE7_EFW-7.0 Exam Overview - Fortinet NSE 7 - Enterprise Firewall 7.0
The Fortinet NSE 7—Enterprise Firewall 7.0 exam is part of the NSE 7 Network Security Architect program, and recognizes the successful candidate's knowledge and expertise with Fortinet solutions in enterprise security infrastructure environments. The exam tests applied knowledge of the integration, administration, troubleshooting, and central management of an enterprise firewall solution composed of FortiOS 7.0.1, FortiManager 7.0.1, and FortiAnalyzer 7.0.1.
The Fortinet NSE 7—Enterprise Firewall 7.0 exam is intended for network and security professionals who are responsible for the design, administration, and support of an enterprise security infrastructure composed of many FortiGate devices.
Exam Information
Exam name Fortinet NSE 7—Enterprise Firewall 7.0 Exam series NSE7_EFW-7.0 Time allowed 60 minutes Exam questions 35 multiple-choice questions Scoring Pass or fail, a score report is available from your Pearson VUE account Language English and Japanese Product version FortiOS 7.0.1, FortiManager 7.0.1, FortiAnalyzer 7.0.1
Exam Objectives
Successful candidates have applied knowledge and skills in the following areas and tasks:
System and session troubleshooting
Implement the Fortinet Security Fabric
Diagnose and troubleshoot resource problems using built-in tools
Diagnose and troubleshoot connectivity problems using built-in tools
Troubleshoot different operation modes for a FGCP HA cluster
Central management
Troubleshoot central management issues
Content inspection
Troubleshoot FortiGuard issues
Troubleshoot web filtering issues
Troubleshoot the Intrusion Prevention System (IPS)
Routing
Troubleshoot routing packets using static routes
Troubleshoot Border Gateway Protocol (BGP) routing for enterprise traffic
Troubleshoot OSPF routing for enterprise traffic
VPN
Implement a meshed or partially redundant IPsec VPN
Troubleshoot Autodiscovery VPN (ADVPN) to enable on-demand VPN tunnels between sites
0 notes
Photo

FortiGate NGFWs deliver industry-leading enterprise security for any edge at any scale with full visibility and threat protection. Organizations can weave security deep into the hybrid IT architecture and build security-driven networks to achieve:
Ultra-fast security
Consistent real-time defense with FortiGuard Services
User experience with security processing units
Operational efficiency and automated workflows
Contact Networkise for Fortinet Firewall in Dubai.
#fortinet#fortinet firewall in dubai#fortinet firewall#fortinet distributors in Dubai#firewall solutions dubai#fortinet authorised dealer#fortinet partner in dubai#fortinet suppliers in uae#fortinet distributors in uae#FG-60F uae#Fortinet renewal in uae#Fortinet license in uae#Fortigate in dubai#Fortigate bundle uae
1 note
·
View note