#SQLi
Explore tagged Tumblr posts
Text
Cosmic Cyberlocution: Unraveling the Meta-Vulnerable Mazes of SQL Injection and the Dawn of Database Origami
SQL injection is a form of cybernetic locution where a syntax-disrupting injection molecule, or SQLI (SQL-yielding iconograph), sees a digital opportunity to extract logic-streaks by abusing macrosemic dilations that keep the integrity of a database system. The communication platforms in their most innocent form just want to move data back and forth, unassumingly creating a tunnel sphere wherein an SQLI can metamorphose into a mutable SQL worm.

Upon initiating a cabalistic interrogation, this spitfire worm deceptively mutters invocations: SELECT, INSERT, DELETE, or UPDATE; it dynamically forges new paths, unlocking chunks of cherished data as if these were open source caveats. Like a parasitic virtual predator inflation-depreciating misapplied coded queries, the SQL injection concurrently engenders a wormhole in this ostensibly invulnerable info-sphere.
Trans-culturally multiverse in application, SQLI transcends the commonly known mundane application layer in the OSI (Onion Skin Ideation). It dangerously dinner-jackets into engulfed Mare Nostrums, barrelling through Davis-matrix ethical firewalls by exploiting a netizen's IF and ELSE constructs. Flicking the digital switches of these database TRIGGERS an SQL injection, potentially extrapolating whole terabytes of vulnerable data.
Yet, software network security gurus can counter this invisible cyber sword with delightful robust-and-rogue defenses such as formless form validation, parameterized quarrying, and sweet-natured stored proceedings. These stellar, fortress-like broadswords of data protection can infinitely out-radiate the shadowy cross world attacks of SQLI. In stringent conformity with these arcane meta-protocols, it is plausible to wheel a rampart so immaculate virtually nullifying the SQL injections.
Thus, shaped by eleventh-dimensional axes of high abstractions, this meta-vulnerable loophole in a spontaneously ordered network lets the seemingly innocuous data-lite masquerade disrupt, disorient, and deconstruct, ultimately leading to the discovery of an information goldmine in the interstices of unsuspecting crypto-crannies. Its pure lunacy to let the truth tables turn oblique by these sentient, cyberlocutionary semantics. But in its twilight, it awakens an array of diasporic countermeasures crinkled onto the database origami to repudiate the SQL worm onslaught.
#ko-fi#kofi#geeknik#nostr#art#blog#writing#twitter#sql injection#cybersecurity#infosec#hacking#hackers#information security#security#networking#mysql#sql#sqli
1 note
·
View note
Text
for everyone who maintains 1 or more servers
my observability stack is now betterstack; prometheus+grafana and wazuh. pretty cool stuff. Used to main Netdata but i stepped off that bus when they started pushing their cloud shit
14 notes
·
View notes
Text
Prevent Command Injection in Symfony: Secure Your Code
Symfony is a powerful PHP framework trusted by thousands of developers, but like any framework, it's not immune to security threats. One of the most dangerous—and often overlooked—threats is a Command Injection Attack.

In this blog post, we’ll break down what a command injection attack is, how it can be exploited in a Symfony application, and—most importantly—how to prevent it. We’ll also include code examples and offer you a Website Vulnerability Scanner online free to scan your website for vulnerabilities like this one.
➡️ Visit Our Blog for More Cybersecurity Posts: 🔗 https://www.pentesttesting.com/blog/
🧨 What is Command Injection?
Command Injection is a type of security vulnerability that allows attackers to execute arbitrary system commands on your server. If user input is improperly sanitized, attackers can exploit functions like exec(), system(), or shell_exec() in PHP.
This can lead to:
Data breaches
Server hijacking
Total application compromise
🐘 Symfony Command Injection Example
Let’s start with a naive Symfony controller that might fall victim to command injection.
❌ Vulnerable Symfony Code
// src/Controller/BackupController.php namespace App\Controller; use Symfony\Component\HttpFoundation\Request; use Symfony\Component\HttpFoundation\Response; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; class BackupController extends AbstractController { public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // ⚠️ Dangerous input $output = shell_exec("mysqldump -u root -psecret mydb > /backups/{$filename}"); return new Response("Backup created: $filename"); } }
If an attacker sets filename=backup.sql;rm -rf /, this code could delete your entire server. Yikes!
🔐 Secure It With Escaping & Whitelisting
Let’s see how we can secure this.
✅ Safe Symfony Version
public function backupDatabase(Request $request): Response { $filename = $request->query->get('filename'); // Sanitize the filename using a whitelist or regex if (!preg_match('/^[\w\-\.]+$/', $filename)) { return new Response("Invalid filename", 400); } $safePath = escapeshellarg("/backups/" . $filename); $output = shell_exec("mysqldump -u root - psecret mydb > $safePath"); return new Response("Backup created: $filename"); }
By using escapeshellarg() and validating the input, we reduce the risk significantly.
🛠️ Automate Detection with Our Free Tool
Want to check if your website is vulnerable to command injection and other critical flaws?
🎯 We’ve built a Free Website Vulnerability Scanner that checks for command injection, XSS, SQLi, and dozens of other issues—all in seconds.
🖼️ Screenshot of our Website Vulnerability Scanner:

Screenshot of the free tools webpage where you can access security assessment tools.
👉 Try it now: https://free.pentesttesting.com/
📋 Sample Output Report
Our scanner doesn’t just find issues—it gives you a detailed, developer-friendly report you can act on.
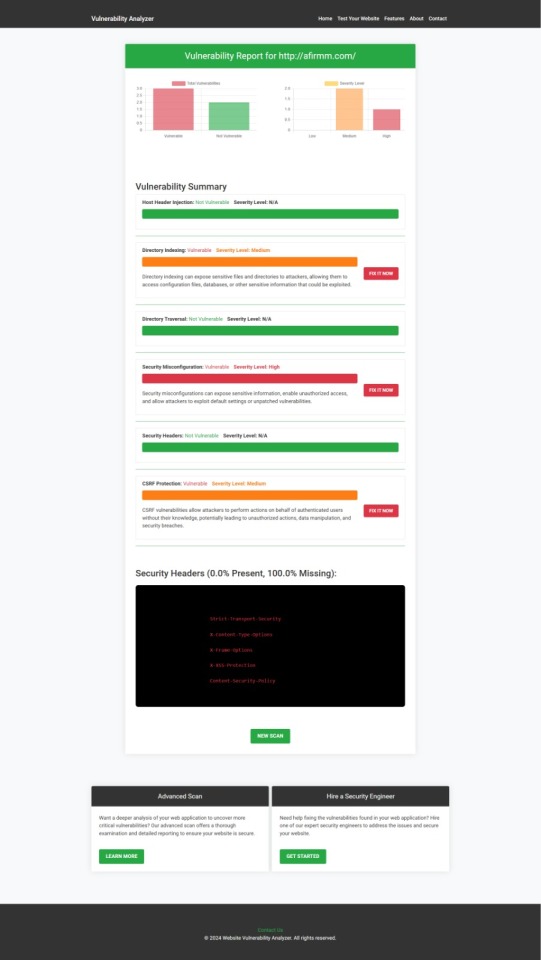
🖼️ Screenshot of a sample scan report from our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
💼 Need Help Fixing It? We've Got You Covered
🔐 Web App Penetration Testing Services If you're looking for expert-level help to secure your Symfony or PHP application, our team is ready to assist.
➡️ Learn more: https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Are You a Tech Company or Agency?
We offer white-label cybersecurity services so you can resell pentesting to your clients without hiring a full team.
📦 Get the full service suite here: 🔗 https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
💌 Stay Ahead of Threats—Subscribe Now!
Don’t miss future posts, case studies, and cybersecurity tips.
📬 Subscribe to our LinkedIn Newsletter
🔁 Final Thoughts
Command injection remains one of the most dangerous web application vulnerabilities. Symfony gives you the tools to secure your app—but only if you use them correctly.
Don’t wait until you’re hacked. Take 2 minutes to scan your website with our free Website Security Scanner tool.
📝 Originally written by the Pentest Testing Corp. team 📌 Visit our blog for more: https://www.pentesttesting.com/blog/
2 notes
·
View notes
Text
SQLi simulation using a virtual machine
Demonstration/simulation of SQL Injection attacks (In-band, Union-based, Blind SQLi) using a Kali Linux virtual machine and a Damn Vulnerable Web Application (DVWA) on a low difficulty level
Blind SQL provided in the video can be used also for gaining other sensitive information: length of the name of the database, database name itself etc.
the common attacks are shown and described shortly in the video, but of course for better learning you can try it yourself.
more resources where you can try out exploiting SQLi vulnerability:
- Try Hack Me SQLi Lab
- W3Schools SQL Injection
- Hacksplaining SQL Injection
more advanced pokemons can try:
- Try Hack Me SQli Advanced Lab
and of course DVWA is a great tool!
5 notes
·
View notes
Text
Fortinet Warns of Severe SQLi Vulnerability in FortiClientEMS Software

Source: https://thehackernews.com/2024/03/fortinet-warns-of-severe-sqli.html
More info: https://fortiguard.fortinet.com/psirt/FG-IR-24-007
5 notes
·
View notes
Text
Web Hacking Techniques: Unmasking 2025’s Top
Unmask 2025's top web hacking techniques! Learn about SQLi, XSS, Broken Auth & more to secure your digital presence from cyber threats.
0 notes
Text
PHP is the hypertext preprocessor
PHP is the hypertext preprocessor Coding Bit . It is a server-side scripting language mainly designed for the web. The actual PHP code gets executed on the server and only the result (usually HTML) gets sent back to the client's browser. Originally created by Rasmus Larder in 1994, PHP has developed into a powerful full-fledged programming language. PHP is an interpreted language, so it executes code line by line during runtime. It is usually used along with HTML, CSS, Java script, and databases like MySQL to make dynamic websites and web apps.
🔹 Core Concepts
Server-side execution:
PHP runs on the server side, and only output in some form like HTML is sent to the browser.
The user never sees the PHP code.
Dynamically typed:
You don't declare the variable types PHP figures this out at runtime.
Loosely coupled with HTML:
PHP code can be embedded directly within the HTML using the following tag: <?php ... ?>.
🔹 Common Applications of PHP
Dynamic websites: Content is adjusted based on user input or database data.
Form handling: Login systems, user registration, contact forms, file downloads.
Database operations: Reading from and writing to databases such as MySQL using PDO or My SQLi.
Content Management Systems (CMS): WordPress, Joomla, and Drupal are all implemented in PHP.
API development: RESTful APIs built with either plain PHP or using various frameworks.

#HTML#Javascript#CSS#WebsiteBoundingClientRect#Cookies#InternetPrivacy#FrontEnd#BackEnd#Database#Server#Aesop'sFables#BooProgramming
0 notes
Text
La obediencia ciega de los LLMs se está convirtiendo en un problema de ciberseguridad
Uno de los principios fundamentales del diseño de los modelos de lenguaje de gran escala (LLMs) —como GPT, Claude o Copilot— es su capacidad para seguir instrucciones de forma flexible y natural. Pero esa característica, aparentemente inofensiva, también representa un punto débil crítico cuando estos modelos se integran en flujos de trabajo reales sin una capa de control.
Recientemente, Juan Alonso resumía el problema general en este interesantísimo post de LinkedIn que les recomiendo leer:
“Los LLMs nos obedecen sin más.”
Sin mas.
Para que haya "más" lo tenemos que poner nosotros. Esto es lo que vamos a explicar a continuación.
Lo que quiero destacar con el post de Juan Alonso es que ese principio de obediencia, llevado a la realidad, puede ser muy fácilmente convertido en un vector de ataque. Tan fácil que ya se está haciendo.
Un ejemplo concreto de cómo la obediencia de un LLM es su mayor punto débil respecto a ciberseguridad es el caso publicado por Cybersecurity Dive en el artículo Critical flaw in Microsoft Copilot could have allowed zero-click attack sobre una vulnerabilidad en Microsoft Copilot para Microsoft 365, a la que se ha llamado EchoLeak, que consiste en una técnica de zero-click prompt injection que permite ejecutar instrucciones arbitrarias sin intervención del usuario. Se ha asignado a esta vulnerabilidad el identificador CVE-2025-32711, con nivel de gravedad 9.3.
¿Qué significa que un LLM "obedece sin más"?
Los LLMs funcionan como modelos autoregresivos que generan texto en función del contexto recibido. No tienen memoria transaccional, ni conocimiento del estado del sistema, ni un modelo de autorización. Lo único que procesan es texto.
Ese texto puede venir de múltiples fuentes. Veamos todas las entradas que un LLM procesa cada vez que hablamos con él:
Instrucciones del sistema: es el famoso system prompt que regula el funcionamiento del modelo (por eso algunos modelos de OpenAI son tan aduladores, porque su prompt del sistema le dice que lo sea).
Contenido de documentos o correos: los documentos que le subimos para que resuma, complete, etc.
Metadatos de archivos: ¡sorpresa! Aquí también hay texto que el modelo lee y obedece.
Si no existe una forma de distinguir una fuente confiable de una maliciosa en ese texto de entrada, el modelo tratará todo el input como instrucciones legítimas.
El ataque: zero-click prompt injection
Según el artículo de Cybersecurity Dive, investigadores demostraron que Copilot puede ser manipulado para ejecutar instrucciones maliciosas simplemente incrustándolas en el contenido que analiza.
Vamos a diseccionar cómo funciona esta manipulación:
Vector de entrada:
Instrucciones ocultas en los metadatos de un archivo de Word (o cualquier documento compatible).
Resultado:
Copilot interpreta estos metadatos como parte del prompt y actúa conforme a ellos (por ejemplo, extrayendo datos sensibles o generando respuestas con información falsa).
Parece, por tanto, que la construcción de los modelos de lenguaje hace posible atacarlos con la peor combinación de factores posible:
Zero-click: no requiere que el usuario abra el archivo explícitamente.
Sin ejecución de código: es puramente una manipulación de texto.
Difícil de detectar: los logs del modelo no necesariamente distinguen entre entrada legítima y manipulada.
Este ataque es un caso clásico de confusión entre input de datos y comandos, un problema de seguridad bien conocido en otras áreas (como XSS o SQLi), pero poco abordado en el contexto de IA generativa.
El problema estructural: input no curado
La mayoría de las implementaciones de LLMs que estamos usando no realizan un saneamiento estricto del input como sí hacen las aplicaciones siguiendo, por ejemplo, esta lista de buenas prácticas de OWASP. Somos tan nuevos (y tan novatos) poniendo en producción modelos de lenguaje que lo estamos haciendo "tal como vienen de fábrica". Esto, como estamos viendo, debe cambiar. No podemos tratar a los modelos como "appliances" y aplicar el criterio de "instalar y usar".
Sin embargo, aunque hagamos eso, aunque saneemos los prompts de los usuarios y los metadatos de los archivos que suben los usuarios, los LLMs, todos ellos, tienen el mismo problema: no distinguen entre un prompt de sistema y un texto ofuscado que simula serlo. Esto los deja completamente expuestos a técnicas de prompt injection, escalada de contexto y simulación de órdenes internas.
Contramedidas técnicas
Para mitigar estos riesgos, es fundamental adoptar un enfoque estructurado:
Filtrado del input: Antes de enviar texto al modelo, escanear en busca de patrones sospechosos o instrucciones no deseadas.
Separación de fuentes: No mezclar contenido generado por usuarios externos con prompts del sistema. Esto, seamos sinceros, es posible en modelos on premise pero muy difícil de implementar en modelos de Cloud usados mediante chat a no ser que este filtrado de seguridad lo implemente el propio fabricante.
Validación de contexto: Usar reglas adicionales para validar si el modelo debería ejecutar una acción o no.
Auditoría y trazabilidad: Registrar las instrucciones que ejecuta la IA para detectar posibles abusos.
Además, es crucial asumir que los LLMs no son actores confiables por defecto. Se debe aplicar el principio de zero trust también al modelo de IA. Los LLMs no son actores conscientes ni sistemas con lógica defensiva. Al integrarlos en flujos de trabajo reales, su obediencia incondicional se convierte en una amenaza cuando no se implementan salvaguardas a su alrededor.
El caso de Microsoft Copilot demuestra que no estamos ante una amenaza teórica, sino ante un patrón de ataque emergente que requerirá nuevas disciplinas en el diseño seguro de sistemas basados en IA.
Las buenas prácticas de ciberseguridad tradicionales (como la validación de input, control de acceso y separación de responsabilidades) siguen siendo válidas —pero necesitan ser reinterpretadas en el contexto de modelos generativos.
0 notes
Text
Web Security 101: Protecting Against Common Threats
In today’s digital world, websites serve as the face of businesses, educational institutions, and organisations. As online interactions grow, so do the threats targeting web applications. From malware attacks to phishing schemes, cyber threats are more sophisticated and frequent than ever. Whether you’re a business owner, developer, or tech enthusiast, understanding the fundamentals of web security is essential to ensure your digital presence remains safe and resilient.
In this article, we’ll cover the essentials of web security, outline common web threats, and discuss best practices to protect against them. For students and professionals pursuing technology careers, especially those enrolled in programs like the Full Stack Developer Course in Bangalore, mastering these security concepts is not just beneficial—it’s essential.
What is Web Security?
Web security, also known as cybersecurity for web applications, is the protective measure taken to safeguard websites and online services against unauthorised access, misuse, modification, or destruction. These protections help maintain the confidentiality, integrity, and availability (CIA) of information and services online.
With the increasing digitisation of services, web applications are a common target for attackers due to the valuable data they often store, such as user credentials, personal information, and payment details.
Common Web Security Threats
Here are some of the most common threats that web applications face today:
1. SQL Injection (SQLi)
SQLi a type of attack where malicious SQL queries are inserted into input fields to manipulate databases. If input validation is not properly handled, attackers can retrieve, alter, or delete sensitive data from the database.
2. Cross-Site Scripting (XSS)
XSS attacks occur when attackers inject malicious scripts into web pages viewed by other users. This can give rise to data theft, session hijacking, and the spreading of malware.
3. Cross-Site Request Forgery (CSRF)
In a CSRF attack, a malicious website tricks a user into performing actions on a different site where they’re authenticated. This can result in unauthorised fund transfers, password changes, and more.
4. Man-in-the-Middle (MITM) Attacks
These attacks happen when an attacker intercepts communication between two parties. They can steal or manipulate data without either party being aware.
5. Denial of Service (DoS) and Distributed DoS (DDoS)
These attacks flood a website with traffic, turning it slow or entirely unavailable to legitimate users. DDoS attacks can cripple even robust web infrastructures if not mitigated properly.
6. Zero-Day Exploits
Zero-day attacks exploit unknown or unpatched vulnerabilities in software. These are particularly dangerous because there’s often no fix available when the attack occurs.
Best Practices to Protect Against Web Threats
1. Use HTTPS
Securing your website with HTTPS encrypts data transferred between users and your server. It also ensures that data isn't altered during transmission. SSL/TLS certificates are now a basic requirement for modern websites.
2. Input Validation and Sanitisation
Never trust user input. Validate and sanitise all inputs on both client and server sides. This helps in preventing SQL injections, XSS, and other injection-based attacks.
3. Implement Proper Authentication and Session Management
Strong passwords, multi-factor authentication (MFA), and secure session management are crucial. Implement session expiration and automatic logout features to reduce unauthorised access risks.
4. Regularly Update Software and Libraries
Web frameworks, plugins, and server software should be regularly updated to patch known vulnerabilities. Automated tools can help identify outdated components in your tech stack.
5. Use Web Application Firewalls (WAF)
WAFs protect web applications by filtering and monitoring HTTP traffic. They can prevent many common attacks before they reach your server.
6. Data Encryption
Sensitive data—both at rest and in transit—should be encrypted. This reduces the damage caused by data breaches.
7. Conduct Regular Security Audits
Perform vulnerability assessments and penetration testing regularly to identify and fix security flaws in your applications.
8. Security Awareness Training
Educate employees and developers on security best practices. Social engineering attacks often target human error, so awareness is a strong line of defence.
Role of Developers in Web Security
Security isn't just the job of cybersecurity specialists. Developers play a critical role in implementing secure code and architecture. Understanding the OWASP Top 10—an industry-standard list of the most critical web application security risks—is a must for anyone writing backend or frontend code.
This is why modern tech education emphasises security fundamentals. At ExcelR, we integrate security concepts across our tech courses, including our Full Stack Developer Course in Bangalore. We believe that a well-rounded developer isn’t just one who can build efficient applications—but one who can build secure ones too.
Real-World Impact of Poor Web Security
Neglecting web security can have severe consequences. Major data breaches have cost companies millions in losses, legal penalties, and reputation damage. In extreme cases, companies have shut down operations permanently after suffering massive cyberattacks.
Even smaller websites are not immune. Bots and automated scripts scan thousands of websites daily for vulnerabilities, often targeting outdated CMS platforms or poorly configured servers.
Final Thoughts
Web security is not a one-time task—it’s an ongoing process of identifying risks, updating systems, and educating users and developers. With the evolution of cyber threats, staying informed and proactive is the best defense.
Whether you’re running a personal blog or developing enterprise-level web applications, implementing strong security measures can save you from irreversible damage. And if you're aspiring to become a tech professional, enrolling in a comprehensive program like the Full Stack Developer Course in Bangalore from ExcelR can give you both the technical and security skills required to thrive in today’s digital landscape.
For more details, visit us:
Name: Full Stack Developer Course In Bangalore
Address: No 9, Sri Krishna Akshaya, 1st Floor, 27th Main, 100 Feet Ring Rd, 1st Phase, BTM Layout, Bengaluru, Karnataka 560068
Phone: 9513446548
0 notes
Text
SQL Injection – Mối đe dọa thường trực cần được xử lý nghiêm túc
SQL Injection – Mối đe dọa thường trực cần được xử lý nghiêm túc #SQLInjection #AnNinhMang #BaoMatThongTin #LoiHong #Cybersecurity SQL Injection (SQLi) là một kỹ thuật tấn công mạng lâu đời nhưng vẫn vô cùng nguy hiểm. Mặc dù đã được cảnh báo nhiều năm, gần đây vẫn xuất hiện nhiều trường hợp hệ thống bị tấn công thành công thông qua lỗ hổng này, đặt ra câu hỏi lớn về hiệu quả của các biện pháp…
0 notes
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note
Text
SQL Injection in RESTful APIs: Identify and Prevent Vulnerabilities
SQL Injection (SQLi) in RESTful APIs: What You Need to Know
RESTful APIs are crucial for modern applications, enabling seamless communication between systems. However, this convenience comes with risks, one of the most common being SQL Injection (SQLi). In this blog, we’ll explore what SQLi is, its impact on APIs, and how to prevent it, complete with a practical coding example to bolster your understanding.

What Is SQL Injection?
SQL Injection is a cyberattack where an attacker injects malicious SQL statements into input fields, exploiting vulnerabilities in an application's database query execution. When it comes to RESTful APIs, SQLi typically targets endpoints that interact with databases.
How Does SQL Injection Affect RESTful APIs?
RESTful APIs are often exposed to public networks, making them prime targets. Attackers exploit insecure endpoints to:
Access or manipulate sensitive data.
Delete or corrupt databases.
Bypass authentication mechanisms.
Example of a Vulnerable API Endpoint
Consider an API endpoint for retrieving user details based on their ID:
from flask import Flask, request import sqlite3
app = Flask(name)
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = f"SELECT * FROM users WHERE id = {user_id}" # Vulnerable to SQLi cursor.execute(query) result = cursor.fetchone() return {'user': result}, 200
if name == 'main': app.run(debug=True)
Here, the endpoint directly embeds user input (user_id) into the SQL query without validation, making it vulnerable to SQL Injection.
Secure API Endpoint Against SQLi
To prevent SQLi, always use parameterized queries:
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = "SELECT * FROM users WHERE id = ?" cursor.execute(query, (user_id,)) result = cursor.fetchone() return {'user': result}, 200
In this approach, the user input is sanitized, eliminating the risk of malicious SQL execution.
How Our Free Tool Can Help
Our free Website Security Checker your web application for vulnerabilities, including SQL Injection risks. Below is a screenshot of the tool's homepage:
Upload your website details to receive a comprehensive vulnerability assessment report, as shown below:
These tools help identify potential weaknesses in your APIs and provide actionable insights to secure your system.
Preventing SQLi in RESTful APIs
Here are some tips to secure your APIs:
Use Prepared Statements: Always parameterize your queries.
Implement Input Validation: Sanitize and validate user input.
Regularly Test Your APIs: Use tools like ours to detect vulnerabilities.
Least Privilege Principle: Restrict database permissions to minimize potential damage.
Final Thoughts
SQL Injection is a pervasive threat, especially in RESTful APIs. By understanding the vulnerabilities and implementing best practices, you can significantly reduce the risks. Leverage tools like our free Website Security Checker to stay ahead of potential threats and secure your systems effectively.
Explore our tool now for a quick Website Security Check.
#cyber security#cybersecurity#data security#pentesting#security#sql#the security breach show#sqlserver#rest api
2 notes
·
View notes
Text
Statistics
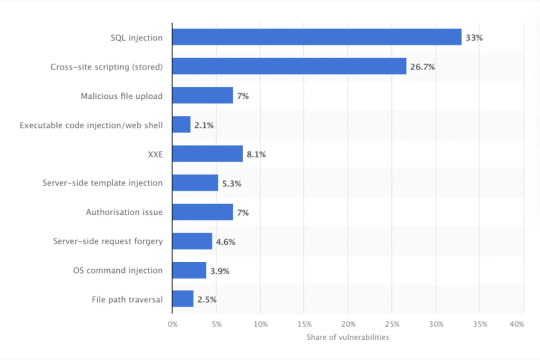
source: statista 2022 In 2023, SQL injection attacks were responsible for 23% of web application critical vulnerabilities discovered globally compared to 2022, where they were 33%. They remain one of the most prevalent security risks for web applications, despite a decline in its share of critical vulnerabilities from 33% in 2022 to 23% in 2023. This decrease indicates an improvement in secure coding practices and database security, but SQLi still poses a significant risk. ! this is why it it so important to share awareness and mitigation/defense measures on injection attacks
3 notes
·
View notes
Text
eluülikool
kui seda linna poleks mul pole ühtegi kasulikku oskust kui neid rahuaja rahmeldamisi poleks ei arvaks keegi, et ma tean midagi et mu kompetentsid on väärt neid eurosid tunni eest või kollektiivi kutsumist mul poleks põhjust olla uhke oma kõrgharitud aastate üle kui kõik läheb pahaks, olen ma tagasi põhikooli keka tunnis kes palli üle väljaku visata ei jaksa ja valu pelgab see valitakse tiimi viimasena tüdinud ülepakutud ohke saatel kaevikus ei vaja keegi SQLi päringute optimeerimist metsas pole midagi teha oskusega 19-aastastele formaalloogikat õpetada kui maja põleb, ei päästa meid akadeemiline kirjutamine pythoni skript mis värvib korrelatsioonimaatriksit vastavalt p-väärtustele kaitseb mind ainult nii kaua kui linn püsib püsti ja jätkub maheda rahuaja tüüneid rahmeldusi
0 notes
Text
SQLi, XSS, and SSRF: Breaking Down Zimbra’s Latest Security Threats
http://securitytc.com/TJbh05
0 notes