#Hashtable
Explore tagged Tumblr posts
Text
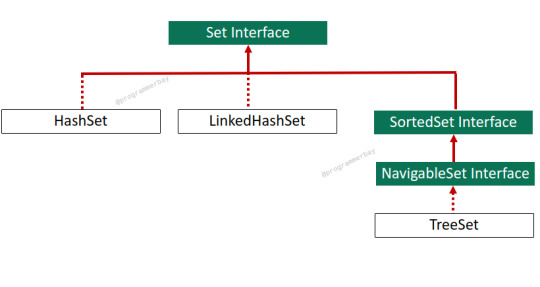
LinkedHashSet Class in Java With Program Example
LinkedHashet is an implementation class of the Set interface which also extends the HashSet class. It was introduced in Java 1.4 version. It behaves in the same manner as HashSet except that it preserves or maintains the insertion order of elements inserted in the set. In simple words, It is an implementation of the set interface that stores and manipulates an ordered collection of elements. It…
View On WordPress
#collection#collection framework#data structure#HashTable#java#java program#Linked List#LinkedHashSet
0 notes
Text
hashing is like really freeking cool ngl
#idrk how like actual cryptographic hashes work#only really messed around with FNV hash for a hashtable implementation#but like the idea that you can verify someone has a piece of data without ever seeing that data or whatever is really cool#especially for lke CSEM stuff#i think apple got heat for like checking hashes of users photos against a CSEM database but like#they're not looking at ur photos!!! its just the hashes!!!!!
0 notes
Text
Powershell syntax is not confusing
(you are just confused because posix compliant shells have corrupted your mind)
> do-action -param "string" $variable (do this first) [type]value
To declare a function:
function do-mythings {
param([int]$argument)
$argument + 5
}
> do-mythings -arg 5
10
That's all you need to get started.
Numbers are just numbers.
Inline math just works. Parentheses for order of operations.
Strings you put in quotes - double quotes allow interpolation, single quotes don't. This is the same as sh.
All variables are prefixed with $s. Even when declaring them. This makes slightly more sense than sh.
A region in {squirrelly braces} gets the [scriptblock] data type. It's like a lambda but comprehensible by mere mortals.
if (test) {success} else {fail} - the test is always executed first because (). Success and fail conditions only depending on the test. They're script blocks. No weird special syntax, if may as well be a user function.
Functions can be named anything, but the convention is Verb-PlaceThing. Not case sensitive.
Named arguments are specified with a single hyphen, like MIT Unix software (xorg for instance). If there is only one parameter the name is optional, etc. Param names can be abbreviated as long as they aren't ambiguous. This is also easy to follow with your own functions, unlike in sh (fricking hate getopt).
Types are inferred dynamically because it's easier to write scripts that way. If you need to force something (variable, expression, whatever) to have a specific type, put it in [brackets] beforehand. The type names are the same as c# and every other post-algol language. For comparison, posix shell only has one type, String.
To make an array, @(item1, item2, etc)
To make a hashtable, @{
key1 = val1
key2 = val2
}
Adding strings concatenates them together. Adding numbers adds their values. If this is not satisfactory, declare their types and it will work.
All expressions are technically objects with properties and methods. $var.property returns the value of that property. $var.invokeMethod() runs the method, which is just a function built into that data type by some poor intern 20 years ago.
Pipes (|) work similarly to sh, but transfer objects. The current object in the pipeline is always the variable $_.
As a bonus, here's a one-liner for opening Internet Explorer on Windows 11 (they lied, it's still there, they will never remove it)
(new-object -com "InternetExplorer.application").visible = $true
COM is an old windows api. Com Objects are just instances of apps. We open internet explorer as a com object.
The parentheses sets that as an expression, and its return value _is_ the exploder. It has properties like visibility, which is $false by default. This is boring so set it to $true. Now we have a real working instance of an app they've been trying to remove for years, because they can't actually remove it merely hide it away. As long as the windows api can parse HTML, this will still work.
#powershell#propaganda#i was going to write this up anyway but#you had to awaken the beast#you know who you are#mir rants#internet explorer
71 notes
·
View notes
Note
oh my god thats sick i need to do this immediately
helo mutual-in-law u seem cool hi
hello! nice to meet you
16 notes
·
View notes
Text
ugh i can't just post mcr forever i have a HashTable to write.....
2 notes
·
View notes
Text
Jeux Olympiques 2024 : de bien belles perspectives
Texte de Hashtable
Petites chroniques désabusées d'un pays en décomposition rapide… du 19 Avril 2024 que je vous invite à savourer....
(Source : https://h16free.com/2024/04/19/77292-jeux-olympiques-2024-de-bien-belles-perspectives)
À moins de 100 jours des prochains Jeux Olympiques à Paris, on sent nettement l’excitation et la joie s’emparer de tout le pays. La capitale et ses habitants se réjouissent très manifestement des festivités et jamais le mot “épreuves olympiques” n’aura trouvé une aussi belle résonance avec ce que traversent actuellement les Parisiens qui goûtent maintenant chaque minute d’anticipation de ces futurs grands moments.Futurs grands moments qu’il faut minutieusement préparer et qui ont déjà été l’occasion, notamment pour la maire de Paris, d’aller visiter les lieux des différentes épreuves dans lesquels on trouve – assez commodément – Papeete, cette petite localité qui jouxte Paris et qui accueillera notamment les épreuves de surf.
Moyennant un petit déplacement en avion (cela jouxte à 15.000 kilomètres près) dont la compensation carbone n’a pas été évoquée – mais dont on peut être sûr qu’elle a été réalisée tant Anne Hidalgo est forcément éco-consciente – et une petite facture pour le contribuable parisien de l’ordre de 60.000 euros, les installations ont pu être vérif…ah non, finalement, le voyage déclenchant des démangeaisons pour l’opposition, les contribuables parisiens, une partie de la presse et pas mal de Français en général, la maire n’aura pas poussé jusqu’au site de l’épreuve de surf.
Tout ceci nous amènera quelques mois plus tard à une petite enquête et des perquisitions pour ramasser les éléments de preuve d’une éventuelle prise illégale d’intérêts et détournement de fonds publics (oh, ça alors) dont on ne doute pas qu’elles permettront de totalement laver l’honneur de l’équipe municipale.
La préparation ne s’arrête pas là puisque, rappelons-le, elle comporte aussi le déménagement furtif des encombrants étudiants qui prennent le pain le logement des athlètes : les expulsions ont commencé. Ouf, la place est libérée, les sportifs sont soulagés, l’Olympisme respire.
De même, la déportation le déplacement discret des centaines de migrants et autres vagabonds en dehors de la ville et leur relocalisation, toujours aux frais du contribuable, un peu partout dans le reste du pays, se passe plutôt bien même si certains maires (celui d’Orléans par exemple) s’en offusquent de façon un peu verte. Ouf, la place est nettoyée, les organisateurs se détendent, l’Olympisme retrouve le sourire.
Mais que serait cette belle cérémonie sans une belle organisation et surtout une solide sécurité garantissant à tous de profiter d’un spectacle à nul autre pareil ?
Et justement, en la matière, on sait déjà que tout sera mis en oeuvre pour obtenir un niveau de sécurisation des individus. Comme jamais auparavant… ou presque, puisqu’on va finalement remettre en place ce qui fut une véritable réussite en 2021 et 2022, à savoir affubler les Parisiens et les spectateurs d’un solide petit QR code lors de leurs déplacements (l’auto-attestation ne devrait plus tarder, maintenant).
On se réjouit déjà de savoir qu’une plateforme internet sera bientôt disponible, qui laissera à tous les Parisiens concernés l’opportunité de saisir tout un tas de petites informations pertinentes sur leurs allées et venues, et on souhaite un courage olympique à tous nos seniors dont la maîtrise des outils numériques est largement suffisante pour garantir que ces petits QR codes seront correctement distribués.
Et franchement, qui ne se réjouit pas déjà d’un retour des contrôles et des patrouilles policières dans une partie de la capitale ? Voilà qui permettra d’assurer la légendaire sécurité des rues parisiennes au moins pendant la période des jeux. Les habitants concernés vont a-do-rer !
Enfin, toutes ces considérations ne seraient pas complètes sans mentionner que tout ceci se déroulera avec une maîtrise presque totale des coûts et des dépenses.
En effet, lorsqu’on lit l’article consacré aux coûts de ces Jeux Olympiques, il apparaît que le calcul du total est particulièrement pointu : entre le budget initial, le budget courant, les dépassements, les cautions de l’État, les différents postes de dépenses et de recettes, on est tout à fait rassuré sur ce qui sera inévitablement du ressort final du contribuable.
Mais si.
Il apparaît cependant que le total devrait osciller autour de 11 milliards d’euros selon différentes estimations, dont 3, 4 ou 5 milliards resteraient à la charge des moutontribuables pardon de l’État selon Moscovici, l’actuel président de la Cour des Comptes, le tout pour un budget initial de 3,8 milliards d’euros, déjà supérieur au 3,2 milliards du dossier de candidature. On ne pourra qu’admirer la précision véritablement diabolique de ces chiffres et de l’organe officiel chargé des Comptes : pour un total à 11 milliards, cela nous fait 7 milliards de petits dépassements dodus, et de 3 à 5 milliards d’euros d’argent public, ça nous fait une enveloppe qui varie allègrement de plus de 60% sur des dépassements de plus de 100%. C’est coquet.
Rassurez-vous cependant : les équipes de propag journalistiques sont déjà sur le pont pour bien nous rappeler que même avec une facture de 11 milliards d’euros (que la Nation Française tout entière peut très bien se permettre en ces temps de croissance et d’opulence macronienne), ces jeux seront probablement parmi les moins coûteux de l’histoire récente.
Mais si.
En fait, on se demande même, devant ces chiffres si modestes, pourquoi on mégote tant, à tel point même que la région Île-De-France a par exemple refusé de prendre à sa charge les déplacements de 200.000 accrédités (athlètes, officiels, journalistes…) alors qu’elle avait été courtoisement sollicitée par le comité officiel des Jeux et que ce budget ne représente qu’un peu moins de 10 petits millions d’euros.
Il n’y a pas à dire, cet événement fleure bon la précision millimétrique et la maîtrise des coûts jusqu’au plus petit poste de dépense ! Voilà qui met dans les meilleures dispositions pour imaginer ce que pourrait donner l’organisation des épreuves elles-mêmes, de la cérémonie d’ouverture et celle de clôture, et qui laisse présager d’un niveau de qualité exceptionnel pour la sécurité et l’accompagnement des joueurs, des spectateurs et de l’ensemble des corps de métiers autour de cet événement. Les supporters anglais vont a-do-rer !
Pas de doute, cela va très très bien se passer. Tout va même être olympique, pour sûr.
3 notes
·
View notes
Text
hi
import java.util.HashMap; import java.util.Map;
public class FrequencyCounter { public static void main(String[] args) { int[] nums = {2, 3, 2, 5, 3, 2}; Map<Integer, Integer> frequencyMap = new HashMap<>(); for (int num : nums) { frequencyMap.put(num, frequencyMap.getOrDefault(num, 0) + 1); } // Print the result for (Map.Entry<Integer, Integer> entry : frequencyMap.entrySet()) { System.out.println("Number " + entry.getKey() + " appears " + entry.getValue() + " times."); } }
} ////////////////////
rray = [2, 1, 5, 1, 3, 2] target = 8 We’ll find the longest subarray where the sum is ≤ 8.
We use left, right, and sum to control and track the window .int left = 0, sum = 0, max = 0;
left: starting point of our sliding window
sum: running total of the current window
count: total number of valid subarrays we find
for (int right = 0; right < array.length; right++) { Expands the window by moving the right pointer forward. sum += array[right]; while (sum > target) { sum -= array[left]; left++; } max = Math.max(max, right - left + 1); }
/// Inheritance Inheritance allows a class to inherit fields and methods from another class. It supports code reuse and method overriding.
🔹 10. Polymorphism Polymorphism lets you perform the same action in different ways. It includes compile-time (overloading) and runtime (overriding) polymorphism.
🔹 11. Encapsulation Encapsulation binds data and methods together, hiding internal details. It’s achieved using private fields and public getters/setters.
🔹 12. Abstraction Abstraction hides complex implementation details and shows only the essentials. It’s achieved using abstract classes or interfaces.
List allows duplicates, Set allows only unique elements, Map stores key-value pairs. They are part of the Java Collections Framework f
Lambdas enable functional-style code using concise syntax. They simplify the implementation of functional interfaces.
🔹 19. Functional Interfaces A functional interface has exactly one abstract method. Examples include Runnable, Callable, and Comparator.
Stream API processes collections in a functional and pipeline-based way. It supports operations like filter(), map(), and collect()
Heap stores objects and is shared, while Stack stores method calls and local variables. Stack is thread-safe; Heap is managed by the garbage collector.
Immutable objects, like String, cannot be changed once created. They are thread-safe and useful in concurrent applications.
int left = 0, right = array.length - 1; while (left < right) { if (array[left] + array[right] == target) { // Found pair } else if (array[left] + array[right] < target) { left++; } else { right--; } } //////////////////
kafka partitions
List inputList = // input data Map uniqueMap = new HashMap<>();
for (Person person : inputList) { String key = person.name + "_" + person.age;if (!uniqueMap.containsKey(key)) { uniqueMap.put(key, person); // first time seeing this name+age } else {
///
List people = Arrays.asList( new Person("Alice", 30), new Person("Bob", 25), new Person("Charlie", 35) ); // Sort by age using lambda people.sort((p1, p2) -> Integer.compare(p1.getAge(), p2.getAge()));
////////////////
public Person(String name, int age) { this.name = name; this.age = age; }@Override public boolean equals(Object o) { if (this == o) return true; if (!(o instanceof Person)) return false; Person person = (Person) o; return age == person.age && Objects.equals(name, person.name); } @Override public int hashCode() { return Objects.hash(name, age); }
}
/////////// hashCode() is used by hash-based collections like HashMap, HashSet, and Hashtable to find the bucket where the object should be placed.
bject.equals() method compares memory addresses
///
List people = Arrays.asList( new Person("Alice", 30), new Person("Bob", 25), new Person("Charlie", 35) ); // Sort by age using lambda people.sort((p1, p2) -> Integer.compare(p1.getAge(), p2.getAge())); // Print sorted list people.forEach(System.out::println); }
///
0 notes
Text
Top Java Interview Questions and Answers You Must Know in 2025

Preparing for a Java developer role? Whether you're a fresher or an experienced candidate, being well-versed with common Java interview questions can significantly boost your confidence and chances of landing the job.
In this blog, we’ll cover the most frequently asked Java interview questions along with quick answers and explanations.
📘 Looking for a complete, detailed list of Java interview questions? 👉 Check out the full guide here: Java Interview Questions – Freshy Blog
🔹 Why Java?
Before jumping into questions, let’s quickly recall why Java is such a sought-after language:
Platform independent
Strong community support
Object-oriented
Robust memory management
Used in web, mobile, and enterprise apps
🔸 Basic Java Interview Questions
What is Java? Java is a high-level, object-oriented programming language known for its platform independence via the Java Virtual Machine (JVM).
What are the main features of Java?
Object-Oriented
Secure
Portable
Robust
Multithreaded
What is the difference between JDK, JRE, and JVM?
JDK: Development kit for Java
JRE: Environment to run Java applications
JVM: Java Virtual Machine that executes code
🔸 OOPs & Core Concepts Questions
What is inheritance in Java? Inheritance allows one class to acquire properties and methods of another class using extends.
What is the difference between method overloading and overriding?
Overloading: Same method name with different parameters in the same class
Overriding: Same method signature in child and parent class
🔸 Advanced Java Interview Questions
What is a Java ClassLoader? A part of JVM that loads classes during runtime.
What is the difference between HashMap and Hashtable?
HashMap: Non-synchronized, allows one null key
Hashtable: Thread-safe, doesn’t allow null keys/values
Explain exception handling in Java. Using try-catch-finally blocks to gracefully handle run-time errors.
📚 Want More Questions with Answers?
These are just a few of the most asked Java questions. If you're preparing for interviews and want more in-depth explanations and examples:
🔗 Visit the full post here: 👉 https://www.freshyblog.com/java-interview-questions/
It includes:
Java 8 features
Multithreading questions
Collections framework
Spring Boot & JDBC-related questions
Real interview scenarios
✅ Final Tips for Java Interviews
Practice coding daily
Build sample projects
Revise OOPs and exception handling
Study frequently used Java libraries
#JavaInterviewQuestions#JavaJobs#TechInterview#JavaProgramming#JavaForFreshers#CodingInterview#FreshyBlog
0 notes
Text
C343 Project 6 - Hash Tables in Compression
1 Assignment Description This week we return to our string compression program, but replace the use of Python dictionaries with our own implementation of a hash table. 2 Your Task We have given you a complete solution for Project 5, except that we have replaced the uses of Python dictionaries with uses of the Hashtable class, defined in hashtable.py. That class has stubs for all of the methods…
0 notes
Text
How are hashCode and equals methods related?
In Java, the hashCode() and equals() methods play a critical role in determining object equality and behavior in hash-based collections like HashMap, HashSet, and Hashtable.
The equals() method is used to compare two objects for logical equality. By default, the equals() method in the Object class compares memory references. However, in most custom classes, this method is overridden to provide meaningful comparison logic—such as comparing object content (fields) rather than memory addresses.
The hashCode() method returns an integer representation of an object’s memory address by default. However, when overriding equals(), it is essential to also override hashCode() to maintain the general contract:
If two objects are equal according to the equals() method, then they must have the same hashCode() value.
Failing to do this can lead to unexpected behavior in collections. For instance, adding two logically equal objects (via equals()) to a HashSet may result in duplicates if hashCode() returns different values for them. This is because hash-based collections first use the hashCode() to find the correct bucket, and then use equals() to compare objects within the same bucket.
Example:
@Override public boolean equals(Object obj) { if (this == obj) return true; if (obj == null || getClass() != obj.getClass()) return false; MyClass other = (MyClass) obj; return this.id == other.id; } @Override public int hashCode() { return Objects.hash(id); }
In summary, always override both methods together to ensure correct object behavior in collections. A strong grasp of these concepts is crucial for building reliable applications and is a core topic in any full stack Java developer course.
0 notes
Text
What is the concept of DSA?

Meaning of DSA
In today's technology-driven world, understanding what is the concept of DSA (Data Structures and Algorithms) is crucial for anyone in computer science and software development. Whether you're a beginner or an experienced programmer, mastering DSA helps in writing efficient and optimized programs. At TCCI-Tririd Computer Coaching Institute, our experts guide students in grasping DSA concepts and enhancing their problem-solving skills.
Understand DSA: The Programming Foundation
Data Structures and Algorithms can be considered the pillar of programming. It organizes and manages data so that searching, sorting, or manipulating it becomes more accessible and more rapid.
Why is DSA Needed?
Optimized Coding: Well-structured algorithms make a program run faster.
Interview Preparation: Tech companies focus a lot on DSA in their job interviews.
Problem-Solving Efficiency: DSA improves logical and coding skills.
Competitive Programming: Good DSA knowledge helps in solving very complicated coding problems quickly.
Components of DSA
Data Structures: These are ways in which data can be organized and stored. Some critical would include:
Arrays – Data is stored in a fixed-size.
Linked Lists – Flexible storage through dynamic memory allocation.
Stacks & Queues – LIFO & FIFO data handling techniques.
Trees & Graphs – Grouping data hierarchically or based on a network.
Hashtables – Using a key-value pair for fast access to data.
Algorithms: It is a stepwise procedure for solving problems. They can be of several types, including:
Sorting Algorithms (Bubble Sort, Merge Sort, Quick Sort)
Searching Algorithms (Binary Search, Linear Search)
Graph Algorithms (Dijkstra's Algorithm, BFS, DFS)
Dynamic Programming (Fibonacci Series, Knapsack Problem)
Learn DSA with TCCI
We, the TCCI-Tririd Computer Coaching Institute, give in-depth knowledge of Data Structures and Algorithms by coding practice. Our expert faculty ensure the students get all necessary practical knowledge as well as confidence in solving real-life programmings.
Join TCCI for your first step towards DSA learning now and better your programming skills!
Let's join together and be coding pros! 🚀
Location: Bopal & Iskon-Ambli Ahmedabad, Gujarat
Call now on +91 9825618292
Get information from: https://tccicomputercoaching.wordpress.com/
0 notes
Text
Mastering Redis Data Structures: A Deep Dive into Hashtables and Sorted Sets
Introduction Mastering Redis Data Structures: A Deep Dive into Hashtables and Sorted Sets is a comprehensive tutorial that covers the fundamental concepts and techniques for working with Redis’s data structures. In this tutorial, we will delve into the world of Redis and cover the basics of Hashtables and Sorted Sets, including how to implement and utilize them in your applications. What you…
0 notes
Text
who the fuck wrote this shit??????
"I'll just finish this project I havn't touched in 3 months" said I. "How hard could it be?"
now here I sit, frantically googling gdb commands, wondering what fool thought that writing their own hashtable implementation was a good idea when the project was already working perfectly fine without it
#the last thing was just me not knowing how to use gdb lmao#my problem was that I was trying to get the label “.owo” from my hashtable#but for some fucking reason I decided to not trim the colon from the labels when inserting them#so my htget function was returning null cause the label “.owo” didn't exist and it segfaulted when I tried 2 dereference it#well really the original problem was that htget didn't have a case for items not existing which is arguably a bigger oversight tbh
8 notes
·
View notes
Text
3701_B11
Support multi-column sub-row sort; various fixes
Free up space on hashtable clear
Support dynamically constructed table cell content
Improve performance of multiple file priority changes
0 notes
Text
securing LDAP in response to Sha-512 rainbow hashtable resolution interchange in Windows Server
To secure LDAP (Lightweight Directory Access Protocol) against SHA-512 rainbow table attacks on a Windows Server, you can implement several strategies, including enforcing strong password policies, using secure connections (LDAPS), and ensuring that passwords are hashed securely. Below is a simplified example of how to configure LDAP security settings and enforce strong password policies using…
0 notes