#How To Hack WhatsApp Without Rooting
Explore tagged Tumblr posts
Text
All of us are all familiar with how much an iPhone is secure when it comes to smartphones. People usually prefer an iPhone due to its fast and attractive user interface. Now most of us must have wished to spy on the iPhone device of our friends or any family member. Spying on the iPhone does not walk in the park due to its advanced security mechanisms. Now some people like professional hackers claim to hack on any iPhone with any software. Hacking on an iPhone by installing software on the phone or PC doesn’t sound smart and easy. For someone who is new to spy apps this is a hell of a task to do on its own. What if you get to know that you can actually track any iPhone device without learning any kind of skills? Yes, this is totally possible for you to spy on an iPhone device without requiring any software or app installation. People usually perform different risky techniques or tricks to break into the iPhone but those tricks won’t work. Using a phone spying app will let you spy on any iPhone device without any installation or learning. Let’s discuss one of the best phone spy apps. Spyic- An Innovative Spy App Spyic is one of the popular and professional spying apps in the World right now. This app is the trust of millions, people are using Spyic on a daily basis. Parents, employees, companies, and almost everyone. People would not imagine before anyone that spy app like Spyic was this good to use and help spy on an iPhone without software. There is no issue that people encounter when it comes to using Spyic for iPhone monitoring. Some spying apps ask users to perform Jailbreak before spying on an iPhone but that’s not the case with Spyic. You don’t have to root your Android or Jailbreak your iPhone device to perform phone spying. Spy on an iPhone Without Software Although Spyic is an app, this is a web-based app that you can operate from any web browser on any device either PC or phone. For the iPhone there is no need to install anything on the spied device. Spyic works in stealth-mode so there is zero % chances of you being exposed as it makes everything super-safe. This app is more easy and simple to use beyond your expectations. Going through the whole Spyic review will clear most of your misconceptions about this phone spy app. You would be surprised to know that there are more than 30 spying features added in this spying app. All features have been designed according to the requirements of users in this modern world of technology. Let’s get to know the main spy features of this brilliant phone spy app. Call Tracking: An amazing spy feature that gives you complete monitoring control over call records of the target iPhone device. SMS Tracking: Access all text messages of an iPhone you want to monitor, reading sent, received, and even deleted messages is possible. Location Tracking: Track an iPhone’s location on the basis of GPS or WiFi along with full access to geographical address coordinates. Apart from all the above features, Spyic has so many other perks to offer. Facebook, Instagram, WhatsApp, and all installed third-party apps can be tracked without getting detected. So, social media apps, web browser history, and almost everything can be monitored on an iPhone device through this spectacular phone spying app. You can use this app for any feature by using its dashboard. Now, most of you would be feeling curious to know how to spy on an iPhone remotely using Spyic? The wait is over, we are going to view all steps we need to follow in order to start iPhone tracking with Spyic. How to Spy on an iPhone Remotely Using Spyic Some of you might be thinking that spying on the iPhone using Spyic would be very difficult. Well, spying on an iPhone has never been this much easy and fast like it is now. All you have to do is to follow all required steps and then you are ready to go. Remember you will not have to physically access an iPhone to perform phone monitoring. Let’s have a look at all those steps that we need to follow in order to track an iPhone device.
Step 1 At first, you have to open your web browser and visit the official website of Spyic. Now click on the Signup button to start creating an account by entering Email and Password. Step 2 You would be given two options, Android and iOS. Select iOS because you are going to track an iPhone device. Step 3 Now you have to enter the credentials of an iCloud account that is logged in on the same iPhone device you want to target. Step 4 Wait for a few seconds to let the system verify the iCloud account. After following some onscreen instructions you would complete the account creation process. Congratulations, you have managed to create an account on Spyic. You can just open any kind of browser, sign in to your make a new Spyic account and start tracking that configured target iPhone. Here you will see that all these spy applications are listed on the left side of the dashboard where your Spyic’s account shows. Some people don’t get satisfied by reading reviews about any app, they always want to try that thing by themselves. Another plus point of Spyic is that it provides an online ‘Demo’ version that you can easily see by tapping on the Demo tab on Spyic’s official web-page. By watching it you would be able to know how exactly this app works. Conclusion We’ve reviewed the whole Spyic phone spy app in details, we can say that no spy app is better than Spyic in terms of quality and professional spying services. Every feature and service of Spyic is up to the expectations of the people. There are no risks involved and no need to perform Root or Jailbreak sort of activities to start phone tracking. The stealth mode of the Spyic app is what gives a guarantee to users that no one will detect them spying on an iPhone device. So what are you waiting for? Visit the Spyic’s site and start tracking an iPhone device according to your needs.
0 notes
Text
Can Private Investigators Retrieve Deleted Text Messages?
In today’s digital age, text messaging has become one of the primary modes of communication. From casual chats to business transactions, vital information is often shared through SMS or instant messaging apps. But what happens when these messages are deleted? Can they be retrieved, and if so, how? This question becomes particularly pertinent in the realm of private investigations, where uncovering hidden or erased information can be crucial to solving a case. This blog will delve into whether private investigators can retrieve deleted text messages, how they might do so, and the legal and technical challenges they face.

The Importance of Text Messages in Investigations
Text messages often play a pivotal role in various types of investigations. Whether it’s a case of infidelity, corporate espionage, or criminal activity, the information stored in text messages can serve as compelling evidence. The rise of instant messaging platforms like WhatsApp, Signal, and Telegram has only increased the relevance of digital communications in investigative work. However, people often delete these messages, either to protect their privacy or to cover their tracks, leading to the question: can deleted text messages be recovered?
The Basics of Text Message Deletion
When a text message is deleted, it doesn’t immediately vanish into thin air. Instead, the message is often marked as deleted and the space it occupies is marked as available for new data. Until that space is overwritten by new information, the deleted data may still exist in the device’s memory. This is where data recovery techniques come into play.
Data Recovery: The Technical Perspective
Private investigators use various data recovery methods to retrieve deleted text messages. These methods rely on understanding the underlying technology of data storage and deletion. Here are some of the most common techniques:
Forensic Software Tools: Specialized forensic tools are designed to recover deleted data from electronic devices. These tools can scan a device’s memory for remnants of deleted text messages and other data. Examples of such software include Cellebrite, EnCase, and Oxygen Forensic Suite. These tools are often used by law enforcement agencies and private investigators to extract information that is not accessible through regular means.
Physical Access to the Device: Physical access to the target device is usually necessary for data recovery. The investigator connects the device to a forensic workstation, where they can use the software tools to scan for deleted messages. In some cases, the device might need to be rooted or jailbroken, especially if the messages were deleted from an app with strong encryption like WhatsApp or Signal.
Cloud Backups: Many messaging apps and smartphones automatically back up data to the cloud. If the user hasn’t deleted these backups, a private investigator might be able to retrieve deleted messages by accessing these cloud backups. This method often requires obtaining the user’s credentials or legal permission to access the cloud account.
SIM Card Cloning: SIM card cloning can sometimes be used to retrieve deleted text messages. By creating a duplicate of the original SIM card, investigators may gain access to messages stored on the card. However, this method is less common due to the limited storage capacity of SIM cards and the prevalence of cloud storage.
Legal and Ethical Considerations
The ability to retrieve deleted text messages is not just a matter of technical expertise. Legal and ethical considerations play a significant role in how private investigators approach data recovery.
Legal Constraints
Consent: In most jurisdictions, retrieving deleted text messages without the consent of the device’s owner can be illegal. Unauthorized access to someone’s phone or cloud account could result in criminal charges, including violations of privacy and anti-hacking laws. Private investigators must navigate these legal constraints carefully to avoid crossing ethical and legal boundaries.
Court Orders and Subpoenas: In some cases, private investigators may work alongside law enforcement or attorneys who can obtain court orders or subpoenas. These legal instruments can compel phone companies or cloud service providers to release data, including deleted messages. However, this process is typically reserved for serious criminal investigations or civil litigation.
Admissibility in Court: Even if deleted messages are successfully retrieved, their admissibility in court may be challenged. The opposing side might argue that the data was obtained illegally or tampered with, leading to a potential exclusion of the evidence. This is why maintaining a clear chain of custody and following proper forensic procedures is crucial for private investigators.
Ethical Considerations
Client Integrity: Private investigators have a duty to uphold the integrity of their profession. Engaging in unethical practices, such as hacking or unauthorized access, can not only harm the investigator’s reputation but also jeopardize the case they are working on. It’s essential to maintain transparency with clients about the limitations and risks involved in retrieving deleted text messages.
Privacy Concerns: The retrieval of deleted text messages can infringe on an individual’s privacy rights. Private investigators must weigh the potential benefits of recovering such data against the ethical implications of violating someone’s privacy. This is particularly important in cases involving sensitive personal information.
Challenges in Retrieving Deleted Text Messages
While the technology to retrieve deleted text messages exists, it is not without its challenges. Various factors can influence the success rate of data recovery:
Time Sensitivity: As mentioned earlier, when a text message is deleted, it remains in the device’s memory until it is overwritten by new data. The longer the time since the message was deleted, the higher the likelihood that it has been overwritten, making recovery more difficult or even impossible.
Device Encryption: Many modern smartphones come with built-in encryption, which protects the data stored on the device. While this is a great feature for user privacy, it also makes data recovery more challenging. In some cases, even forensic tools might struggle to bypass encryption without the correct credentials.
App-Specific Challenges: Different messaging apps have varying levels of security and data retention policies. For example, WhatsApp messages are end-to-end encrypted, and the app automatically deletes messages after a certain period if they are not backed up. On the other hand, apps like Telegram offer self-destructing messages that delete themselves after a set time, leaving no trace. These app-specific features can complicate the process of retrieving deleted messages.
Data Corruption: In some cases, the data related to deleted messages may be corrupted or incomplete, making recovery difficult. This can occur due to software glitches, hardware failures, or improper handling of the device after deletion.
Case Studies: Success and Failure in Message Retrieval
To better understand the real-world application of message retrieval, let’s explore a few case studies that highlight both the successes and challenges faced by private investigators:
Case Study 1: Recovering Deleted Messages in an Infidelity Case
In one instance, a private investigator was hired to confirm suspicions of infidelity. The client believed that their spouse was using text messages to communicate with a potential partner, but the spouse had deleted the messages. The investigator gained access to the spouse’s phone and used forensic software to recover several deleted messages that provided clear evidence of the affair. The recovered messages were crucial in the client’s decision to proceed with a divorce, and they were also presented as evidence in court, where they were deemed admissible.
Case Study 2: The Challenges of Encrypted Messages in a Corporate Espionage Investigation
In another case, a private investigator was hired by a company suspecting that one of its employees was leaking sensitive information to a competitor. The employee had been using a secure messaging app with end-to-end encryption, and they had deleted all conversations after sending them. Despite using advanced forensic tools, the investigator was unable to retrieve the deleted messages due to the app’s strong encryption protocols and lack of cloud backups. This case illustrates the limitations investigators face when dealing with modern encryption technologies.
Alternatives to Retrieving Deleted Text Messages
When direct retrieval of deleted text messages is not possible, private investigators often explore alternative methods to gather the needed information. Here are a few alternatives:
Metadata Analysis: While the content of the messages may be deleted, metadata related to those messages—such as timestamps, sender and receiver information, and message size—might still be recoverable. Metadata can provide valuable clues, even if the actual content is no longer accessible.
Witness Interviews: If retrieving the messages themselves is not possible, investigators might turn to individuals who were involved in the communication. Interviews with these witnesses can sometimes uncover the content of deleted messages or at least provide context.
Surveillance: In some cases, real-time surveillance of the suspect’s activities can provide alternative evidence that might replace the need for deleted messages. This could involve monitoring the suspect’s online activity, following their physical movements, or recording their conversations.
Social Engineering: Social engineering techniques can sometimes be used to gather information indirectly. For instance, investigators might trick the suspect into revealing details of the deleted messages or sending new messages that can be intercepted.
Conclusion
The retrieval of deleted text messages by private investigators is a complex process that depends on various technical, legal, and ethical factors. While it is possible to recover deleted messages under certain conditions, the success of such efforts is never guaranteed. The rapid advancement of encryption technologies and the increasing awareness of privacy have made it more challenging for investigators to access deleted data.
Private investigators must navigate these challenges with caution, ensuring that they adhere to legal constraints and ethical standards. When direct retrieval is not possible, they often rely on alternative methods to gather the necessary information. Ultimately, the role of a private investigator is to uncover the truth while respecting the boundaries of privacy and legality.
If you are considering hiring a private investigator to retrieve deleted text messages, it is essential to discuss the feasibility and legal implications of such an endeavor upfront. Understanding the limitations and challenges involved w
0 notes
Text
The Guide of Mobile Hacking: Methods, Benefits, and Practices

Mobile phone has become a part of our life nowadays. We use it daily. Our mobile phone is a storehouse of many things including the information we need to send messages to someone's work, communicate and personal information including photos. And this treasure trove of data makes mobile phone hacking a concern. Mobile hack is to access someone's mobile without permission. and collecting the required messages from there. And we use a variety of techniques to do this. In this blog we will enter the world of mobile hacking and discuss about its various methods, how it helps us, why we need mobile hacking, what benefits we can get through mobile hacking, let's see the world of mobile hacking.
What is Mobile Hacking?
What we mean by mobile hacking is accessing someone's mobile without their permission. These can include smartphones, tablets and handheld devices. We use a number of methods to access these devices, including software vulnerabilities, phishing attacks, and special tools. One of the goals of mobile hackers is to hack the mobile and hope to extract important information from it.
Why Need Mobile Phone Hacking?
We all know mobile hacking is seen as negative, but here are some cases where the benefits of mobile hacking are mentioned. Today we will know about the benefits of mobile hacking, i.e. some of the benefits and advantages of mobile hacking such as:
📌 Security Testing: Cyber security professionals often take advantage of mobile hacking to test the network security of mobile devices. If it is mobile network weak then they check through mobile hacking.
📌 Parental Monitoring: Parents can monitor their child's mobile phone. To ensure the safety of your child, you can use mobile hacking to track your child's live location, save your child from terrorist attacks or various online threats.
🎯 Related Topic: Best Mobile Hack to Track Your Teenage Child
📌 Investigation: This mobile phone hacking is used to investigate a matter. It is used to hack someone's mobile and track various information about him. Mobile hacking is used to track the physical location of suspects.
📌 To Catch Cheating Spouse: Mobile hacker is needed to collect evidence of cheating spouse. A hacker can access the mobile and track the cheating spouse's social media like: Facebook, WhatsApp, Instagram, Twitter, Snapchat etc. A cheating spouse can be caught by tracking these platforms.
🎯 Related Topic: How WhatsApp Hacker Help You to Spend Infidelity-Free Life
Hack Mobile Phone by Phone Number
Hacking a phone also involves the data of that phone. Mobile hackers can hack your phone with the help of your phone number. Phishing, social engineering, and network vulnerabilities are used here. Once they get access, hackers can easily hack messages, hack calls, and even track and track the device's location.
Hack a Mobile Phone Through Phone Call
Hacking a phone through a call is one of the most advanced techniques. Hackers can gain control of a device with just one phone call. And he did that by exploiting the weakness of the mobile network. A call setup is manipulated by the system, which is invoked when a call is made. This method requires advanced engineering knowledge. And this method is used a lot.
Hack Cell Phone
Hacking a cell phone can be done through several methods, including:
📌 Phishing: Sending fraudulent messages or emails that trick the user into revealing their credentials or installing malware.
📌 Malware: Using malicious software to gain control of the device or steal data.
📌 Exploiting Vulnerabilities: Taking advantage of weaknesses in the phone's operating system or installed apps to gain unauthorized access.
Hack Android Phone
Android phones are a common target for hackers due to their widespread use and open-source nature. Some common methods to hack an Android phone include:
📌 Rooting: Gaining superuser access to the device, allowing the hacker to control all aspects of the phone.
📌 Malware: Installing malicious apps that can steal data or control the device.
📌 Network Attacks: Exploiting vulnerabilities in the phone's connection to Wi-Fi or mobile networks.
Hack Mobile Network
Hacking a mobile network involves intercepting and manipulating data transmitted over the network. This can include eavesdropping on calls, reading text messages, and tracking the location of devices. Techniques used for mobile network hacking include:
📌 Man-in-the-Middle Attacks: Intercepting communication between the mobile device and the network.
📌 Network Spoofing: Setting up fake network towers to trick devices into connecting and revealing their data.
Hack Mobile Camera
Hacking a mobile camera involves gaining control of the camera to capture photos or videos without the user's knowledge. This can be done by:
📌 Remote Access Trojans (RATs): Malware that allows the hacker to control the camera remotely.
📌 Spy Apps: Apps designed to secretly access the camera and transmit the captured data to the hacker.
Best Mobile Hacker
If you are in need of an expert mobile hacker then finding it can be very difficult for you. Because this food requires a lot of technology related knowledge and a lot of experience. Hackersalist is an organization where you can find a professional mobile hacker with vast knowledge and a hacking expert. They provide all mobile hacking services. They assure you that your work is done by an experienced hacker. Get here
Conclusion
Now at present we do good work through mobile hacking. Mobile manufacturing companies use it to test the security of their mobiles, parents use it to monitor their children, use it to investigate a crime, use services like mobile hacking to catch a cheating spouse. So before we take mobile hacking service we should be aware whether we really need mobile hacking? And how can we find a good mobile hacker if we need one? We must pay attention to these two things.
0 notes
Photo

3k, College AU. In which Dean attempts to scam Castiel over text, with... mixed results.
read here on AO3 if you prefer!
Castiel sat in his apartment, scrolling listlessly through his phone. He’d tried to stop doing this recently. The hours he flipped down the wishing well of his Instagram feed just weren’t rewarding him with the perfect life he wished for, and at a certain point it was time to stop making the wishes. But even though he’d put his social media apps in a folder marked Don’t Do It, and even though he knew he didn’t want to melt through his days like this – slumped on his sofa with phone in hand – he ended up doing it anyway.
He stared briefly at a picture of a dog. Then someone’s baked goods. Then someone else’s throwback picture to their time in Greece.
None of it was particularly exciting, but he couldn’t seem to will himself away.
Inside him, a little voice was saying, you know, you could be doing something that you actually enjoy right now, like going for a run or reading a book or watching a TV show or, and I mean heaven forbid, but you could possibly start doing that paper? You know, like, work?
Castiel scrolled some more. The voice in his mind was very loud but outwardly, he was just sitting in his living room, eyes fixed quietly on his screen.
Move! said the little voice. You can’t just sit here forever! What are you doing? Your minutes on Earth are slipping out from under you while you do things you don’t even like!
With a little sniff, Castiel kept going. It was like his thumb had a mind of its own, traversing his Instagram like a lone journeyman, while the sky-gods above in Castiel’s mind begged it to stop.
A white box unfurled from the top of Castiel’s screen.
He blinked. A notification – a text. He tried to pull down the notif to read what the text said, but he accidentally closed it instead. Treacherous little journeyman thumb, he thought. Maybe if it spent less time overexerting itself on social media scrolling, it’d be able to open a text message.
A text message. Weird. No one texted him anymore, not really – all his friends used WhatsApp, and his professors only ever contacted him via email. To just get a plain old text was unusual. He flipped over to his texting app and opened it.
>> Your phone is now hacked so do exactly what I say and I’ll remove the hack. If you don’t I’ll destroy all your phone data. If you try to block me or report this I’ll destroy all the data instantly send your home address or I’ll hack you and share everything
When he started reading the message, Castiel felt a cold clutch of worry grip his stomach. His phone was hacked? How was that even possible? He ran anti-virus and anti-malware apps all the time, even though they slowed down his phone. He took care not to visit any sites that looked suspicious. How could –
He read it again, and then frowned, and sent a message back.
<< I have to send the address or you’ll hack me? I thought you already hacked me?
There was a pause. Castiel could feel his heart beating a little fast. His phone was supposed to be a safe island that no one could get into, his own private space; having someone text him that they were inside it, had hacked it, felt like having someone in his bedroom rooting through his things.
After thirty seconds, the text came back.
>> Yeah I’ve definitely hacked it so send the address or I’ll destroy your data and share it
Castiel squinted. He typed back,
<< How are you going to share the data if you destroyed it?
Another pause, and then –
>> I’ll share it first
With a more suspicious expression on his face than ever, Castiel responded,
<< What phone do I have? What OS?
>> You have thirty seconds to send the address or I’m going to share the data
<< You didn’t answer my question.
>> I don’t have to
Castiel actually had a small smile forming on his face as the last text came in. The person on the other end of the phone clearly had no idea what they were doing. He wasn’t sure if this was just a prank from one of his friends, or if it was a genuine attempt to scam him, but it definitely wasn’t an actual hacker.
With that same little smile on his face, Castiel typed out,
<< It’s been more than thirty seconds.
>> Yeah and I have your data now so I’m gonna share it
It was almost endearing, Castiel thought.
<< You really didn’t plan ahead for if someone actually questioned you, did you?
>> Yeah I am prepared. I’m gonna destroy everything on your phone
As Castiel considered how to reply – and if he even should, or if it was better to leave the supposed hacker to their own devices – he felt his stomach growl. Lost in the endless scroll of his Instagram feed, he’d completely forgotten to eat for most of the day. The texts from this person had finally broken the spell.
<< Alright. Enjoy yourself. I’m going to go and get some food.
>> Copying all the content now
Of course you are, Castiel thought. Of course. He wandered through to his kitchen and started browsing through his shelves. He had rice – plenty of rice, and also a bottle of soy sauce that was going out of date, and a slightly withered onion. In the fridge he found a few more limp-looking vegetables that needed eating up before he next went shopping.
Ten minutes later found him watching a pot bubbling to cook his rice, with a frying pan sizzling beside it.
When he picked up his phone, the hacker hadn’t responded. Castiel took a screenshot of their conversation, and then flipped over to WhatsApp. Opening the groupchat he had with his friends, he sent the screenshot.
I’m getting hacked, he wrote, and then put a terrified emoji. Charlie responded immediately with four cry-laughing emojis, and a few others sent some gifs. Castiel watched along the top to see someone typing a response – a number he didn’t have saved to his phone.
Sounds pretty scary you should probably send it, said the person. Castiel checked the name in grey next to their number, the one WhatsApp displayed automatically. Dean Winchester.
Dean Winchester? Castiel felt a little flip in his stomach. He’d been hoping to get to chat to Dean for months, now – they’d shared a class last semester but somehow had never got to talking, just traded looks across the room. Castiel had thought he’d lost his chance when the semester had ended and their shared class had been over – but then Charlie had added Dean into the chat at the start of the new year, introducing him as someone she’d met in one of her computing classes. Dean had been quiet so far, though, just lurking and reading messages.
Now, for the first time, Dean had actually said something to him.
And it was something ridiculous. Dean wasn’t actually taking this seriously, was he? Those computing classes couldn’t be focusing in on hacking as a topic, if he was this clueless.
Castiel didn’t want to leave Dean hanging without a reply, but he also didn’t want to embarrass him by laughing at the idea of the hack being scary. Instead, he switched over to his texting app again. Maybe if he got more evidence that the “hacker” had no idea what they were doing, then Dean would realise on his own that it wasn’t anything to worry about.
He thought for a second, and then sent,
<< How’s it going? It can’t take that long to steal all my data. I only have like 4 pictures on my phone and they’re all accidental selfies.
>> I’m getting all your credit card details you should definitely just send the address
<< Isn’t my address in the same place in my phone where you found my credit card details?
A pause, and then –
>> Yeah it is but you should tell me anyway
Castiel pressed his lips together to repress a laugh, and took another screenshot, and sent it to the groupchat.
I think I’ll be okay, he said. Dean started typing again immediately, while emojis rolled in from the rest of the people in the chat.
Dean said,
I don’t know dude seems legit to me
Charlie sent a message that said,
Dean… are you reading the same thing I’m reading?
Castiel was glad that Charlie was the one questioning him, because someone had to. Surely Dean was just kidding around, though. There was no way he really thought that this terrifying “hacker” represented a serious threat.
Dean was typing again. Castiel stirred his vegetables in the frying pan.
I had a friend who got the same message, Dean said, and he didn’t send his address and the hacker totally ruined his life so you should probably just send it
The message sat there in the WhatsApp groupchat, and was met with silence. Castiel read over it, shook his head – and then he noticed his rice was definitely cooked, and went to drain the water away in the sink before it went mushy in the pot. A frown was growing on his face as he did so. When he was done, he stirred his vegetables some more and then came back and read the message again.
His eyes narrowed.
He switched to his texting app, and read over the texts the hacker had sent him. And then went back to WhatsApp, and read Dean’s message.
The style was undeniably similar.
Was Dean pranking him? Probably not, right? Why would he? But then again, Dean was trying to convince him that the hack was real over WhatsApp in a way that was stylistically similar and just as unconvincing as the hacker themself over text… Castiel wasn’t sure what to make of that. Attention from Dean would feel kind of good, but given that the attention he was possibly getting was some kind of attempt to scam him out of his personal details, the good feeling was definitely not boundless.
After some thought, Castiel turned down the heat under his frying pan, tapped through his phone, and hit Call.
Bzz, bzz. The dial tone hummed in Castiel’s ear. He found that his heartbeat was actually pounding a little hard.
Bzz, bzz. Maybe this was a bad idea. Probably he should just hang up, and try messaging instead –
“Hello?”
Castiel went still as someone picked up. Their voice was comically low and growling, as though the person who’d answered was putting on a voice.
“Hello,” Castiel said.
“This is the hacker. Tell me your address.”
Castiel pressed his lips together, very hard, so he wouldn’t laugh.
“I said, tell me the address.”
“Um,” Castiel said. “No, thank you. Dean, what are you doing?”
There was a pause, and some kind of hurried rustling on the phone, and then the voice said,
“Dean? Who’s Dean? I don’t know anyone with that name. Just send over the address and your data won’t be shared and destroyed.”
“Dean,” Castiel said, “I called you on WhatsApp. I know this is you.”
The silence, this time, was significantly more protracted. For a few seconds, Castiel thought that Dean was actually gone, or that maybe the line had gone dead. Instead, after an incredibly pregnant pause, Dean said in his normal voice,
“Fuck.”
“Can I… ask you what’s going on?”
“Uh…” Dean hesitated. “Shit. Oh, god. Okay. Look, man, uh, buddy, I’m – I’m really sorry if I freaked you out with the whole scam thing –”
“I wasn’t freaked out,” Castiel said, trying not to sound too much as though he was enjoying himself. It felt good to hear Dean’s voice down the phone. Dean Winchester, the most handsome guy in Spanish 101, was actually on the end of the phone. They were actually talking. Under circumstances that made no sense, obviously, but still.
“Right… right. I just – I’m sorry, it was this idea I had and I thought I could just…”
He broke off. Something about the tone of his voice took the silliness and hilarity out of the situation, and Castiel’s slight smile dropped to be replaced by a little frown of concern.
“Are you in some kind of trouble? Do you need a place to come to?”
“No, no, nothin’ like that. Oh my god, this is the worst.”
“Dean… is something wrong? If you need my address… you know you could have messaged me and just asked for it?”
Dean groaned.
“I don’t… I mean, yeah, but like, no,” Dean said. “Look, I’m just gonna go. I’m sorry for… whatever the hell this was, and –”
“Wait,” Castiel said, “wait, don’t go. You can’t try to scam me for my address and then not give me any answers, I…”
“Sorry,” Dean said, and then hung up.
Castiel took his phone away from his ear. There had been something so wretched and barely-concealed in Dean’s tone that Castiel himself was upset, his stomach twisting. He looked down at his phone screen.
After a long minute of thought, Castiel went to his texting app and opened the text chain with the “hacker”.
<< 401 Lazarus Rise SW, Apartment 67
He considered the text for a long moment, and then sent it. Dean didn’t text back.
But two days later, there was a knock at his front door. Castiel, sitting at his desk and reluctantly typing out some words on his paper, frowned and looked over at the clock as though its face calmly showing 5pm would give him some kind of answer about who was outside. Receiving no wisdom from it, he decided to go and see for himself.
Opening the door, he saw a delivery person wearing a big smile and carrying a bunch of flowers.
“Here you go!” they said, handed him the flowers smartly, and then marched off down the hallway. Castiel stared after them, wondering how they’d even managed to get inside the building without being buzzed in. Probably Mrs Tran down the hall leaving the door open again, so that her son could get in even though her buzzer was broken.
Castiel stood in the doorway of his apartment, holding onto the bunch of flowers. It was a simple enough arrangement – just twelve red roses, nestled in brown paper. When the delivery person was gone, Castiel blinked and looked down at them. Surely these had to be for someone else in the building – he could just check the label and try to figure out who.
The label was a piece of brown card tied to the roses with string. In a messy scrawl, Castiel read,
Hey sorry again about what happened hopefully these make up for it. Never really tried to do anything about liking a guy before so don’t know what I’m doing. Didn’t know if you’d find flowers embarrassing so tried to get your address and send them anonymously but I guess that plan sucked ass huh? Don’t feel like you gotta say anything just wanted to apologize. Dean
Castiel’s eyes went wide and soft. He read the message through one more time and then once more after that, and then tilted the roses up to look at them, and then read the message again, and then smelled the flowers. He leaned back against his doorframe. He could feel his heart just about ready to burst out of his chest.
He went into his apartment, feeling as though he were walking on marshmallows. His legs were fuzzy with his happiness. Finding his phone, he pulled up WhatsApp.
Bzz, bzz.
Bzz –
“Hello?”
“Hello, Dean.” Castiel still had the roses in one hand. He looked down at them again, and closed his eyes because the happiness was just a little too much for a half-second.
“Uh.” He heard Dean swallow. “I did put the part where you didn’t have to say anything to me, right?”
“I know. But I wanted to thank you.”
“Uhhh.” Dean sounded floored. “Okay. Well, you’re… welcome?”
“And I wanted to ask you for something.”
“Oh. Okay?”
Castiel smiled.
“Your address,” he said.
––
The next night, Castiel stood outside the door of a slightly shabby-looking apartment, and knocked.
After less than three seconds, it was opened. Framed in the doorway stood Dean Winchester, wearing a nervous smile and nicer clothes than Castiel had ever seen him wear before to class.
Castiel breathed out.
“Hey,” Dean said. His hands looked awkward and clumsy, and Castiel’s heart was full enough looking at the confused shy man in front of him that he couldn’t stop himself – he reached out and took one of them. And it wasn’t supposed to happen this way, it was all in the wrong order, they were meant to go out for dinner and then Castiel would drop Dean back at his apartment and walk him to the door and then they were supposed to do this – but somehow Dean was close, and Castiel was leaning in a little closer still, and then their lips met.
Dean kissed so gently.
When Castiel pulled away, he saw the colour flowering inDean’s lightly stubbled cheeks.
“Uh,” Dean said gruffly. “Uh, good, okay. Yeah. Good.”
“Good?”
“Good,” Dean confirmed. “Good.”
“Good,” Castiel said.
For a second, they stared at each other. And then, moving at the same time, they both leaned in again – not so gentle, now.
They didn’t make their dinner reservation.
“We should call and tell them we’re not coming,” Castiel said at one point.
“They’ll be okay.”
“We should tell them,” Castiel insisted, giving Dean a little dig in the ribs. “It’s rude not to.”
“What, you think the cops will come for us if we don’t?”
“They’re already coming for you anyway,” Castiel said. “This has all been a ruse to catch the biggest scammer in town.”
Dean dropped his head onto Castiel’s shoulder, and laughed.
“Never gonna live that one down?”
“Never,” said Castiel, and kissed him again.
#whelvenwingsfic#destiel#deancas#destiel fic#thebloggerbloggerfun#with my new and very tenuous digital drawing skillz#I made the banner with the phone on it!#I'm so oddly proud of it#I'm sure there are 10000 mistakes but hey they're my mistakes in a art what I did??#I did an art!#anyway#here endeth the three-day downpour of fics from me#lots more in the works though!
148 notes
·
View notes
Text
Pluralistic: 11 Mar 2020 (Saturated fat and obesity, which foods produce satiety, spying VPNs, Twitter's research-friendly terms of service)

Today's links
Obesity and unsaturated fats: Blaming unsaturated fats for obesity is very plausible, but likely wrong, alas.
The satiety index: Which foods cause or satisfy cravings?
Sensor Tower's VPNs and adblockers spied on users: Like sneaking laxative into Immodium.
Twitter's new Terms of Service help academics: Good bots welcome.
Italy's "I Stay in the House" law: The comprehensive quarantine plan.
Scam-buster hacks into a scam-factory: He gets their CCTVs, recordings of their calls, transaction data, Whatsapp chats, and more. Delicious.
Postmortem: the catastrophic EU Copyright Directive. Testimony from yesterday's Senate hearing.
Podcast: A Lever Without a Fulcrum Is Just a Stick: My latest Locus column, on how copyright failed artists and enriched corporations.
This day in history: 2010, 2015, 2019
Colophon: Recent publications, current writing projects, upcoming appearances, current reading

Obesity and unsaturated fats (permalink)
Scott Alexander does a very deep dive into the literature on diet, weight, and saturated vs unsaturated fats.
https://slatestarcodex.com/2020/03/10/for-then-against-high-saturated-fat-diets/
The most important elements for me were first, the validation that something really has changed: average US adult men's weight went from 155lbs to 195lbs from the 1800s to today. The 90th percentile 1800s man weighed 185lbs, today, it's 320lbs. US obesity rates in the 1800s were 1%. Today, they're 25%.
But the usual culprits can't explain the change: they ate more bread and potatoes in the 1800s, for one thing.
In China, obesity rates were very low even with a diet dominated by white rice.
1970s France had 1800s US obesity rates, on a diet of "baguettes, pastries, cheese, meat. Lots of sugar, white flour, and fat."
It's true that some tactics (intermittent fasting, low-carbing) work for some people, but they're not what worked in 1970s France or 1800s USA. So if those things work, they're "hacks" – not an indictment of carbs or eating three meals a day.
There's a widespread theory that the change is driven by the switch from saturated to unsaturated fats, which was driven by spiking heart disease in the 1950s. It's likely this heart disease epidemic can be attributed to the vast increase in smoking a couple decades earlier, but the tobacco industry's denial machine meant that the blame fell on diet, and the US (and then global) diet's fat composition shifted dramatically.
We ate a lot fewer animal-derived fats and a lot more plant-derived fats. These fats had lots more Omega 6s and (to a lesser extent) 3s, and the ratio of these Omegas also changed dramatically, both in our diet and in our bodily composition. Intriguingly, these play a significant role in metabolism. There's a plausible ring to this whole business – particularly as a way of crisping up what we mean when we say "avoid processed foods." What is "processing?" Maybe it's doing something that requires vegetable fats.
Unfortunately, neither the literature nor the lived experience of experimenters support the theory. Studies don't support it. Meta analyses don't support it. Reddit forums skew heavily to people saying it didn't work for them (dotted with people for whom it did).
Which makes weight gain a mystery. It can't be (just) exercise: we're exercising more now than we did 40 years ago, and we're heavier now. Studies about causes are inconclusive overall, but clear that weight gain is more explained by diet than exercise. What's more, we're seeing weight gain in lab rats, pets and feral animals, so exercise seems an unlikely culprit here.
Alexander ponders other possible causes: plastics or other contaminants in our diet, or that it's a "ratchet" (once your weight set point changes, it doesn't change back.). Both have little evidence to support them.
He concludes that he's "more confused than when I started it," but will avoid unsaturated fats where possible, with the exceptions of Omega-3 rich oils (fish/olive oil).
I am likewise confused, but also better-informed than I was before I read his post.

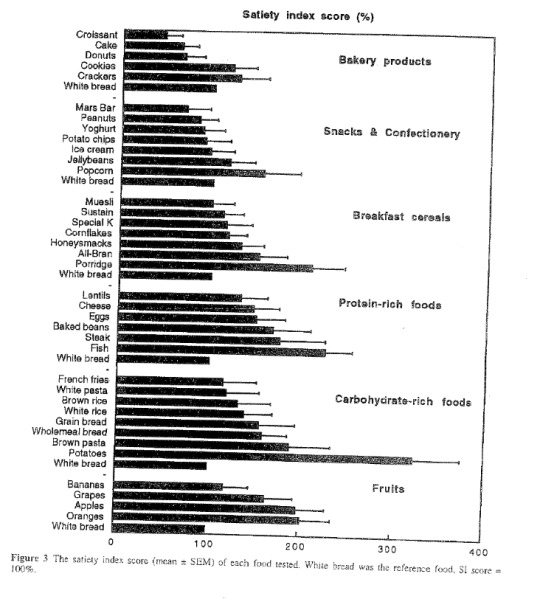
The satiety index (permalink)
I lost ~100lbs in 2002/3 with a low-carb diet. The thing I immediately noticed when I started eating (lots) more fat and (lots) less carbs was that I was always satiated, with none of the food cravings that had plagued me all my life.
No other diet since has had that effect. I really struggle with cravings (and have put 50lbs back on through my 40s, though some of that is muscle from a much higher level of exercise). For me, satiety is the barrier to sticking to any diet. I don't just get ravenous, I get these all-consuming cravings that I can't put out of my mind, even if I resist them (and the longer I resist, the more likely it is that I'll really blow it out when I give in at last).
So I was really interested in this 1995 open access study, "A Satiety Index of common foods," which offers a league table of the foods that made subjects feel full.
https://www.researchgate.net/publication/15701207_A_Satiety_Index_of_common_foods
The meaty (heh) parts are in these charts on pp682-3.

Sensor Tower's VPNs and adblockers spied on users (permalink)
Sensor Tower, a company that made apps billed as privacy-protecting, installed man-in-the-middle certificates on your devices that let them spy on everything you did online.
https://www.buzzfeednews.com/article/craigsilverman/vpn-and-ad-blocking-apps-sensor-tower
They made 20+ VPN apps for Android and Ios, but didn't disclose that all those apps were owned by analytics company, Sensor Tower. The apps had names like "Free and Unlimited VPN, Luna VPN, Mobile Data, and Adblock Focus."
The apps installed a "root certificate" in users' devices. With this cert, the company could insert itself in all the device's otherwise secure, encrypted sessions – web browsing, email, etc. Sensor Tower admits that they collected data using this cert, but insists that it was "anonymized," which is something most computer scientists agree is likely impossible for this kind of data. Re-identification of anonymized data is devilishly hard to avoid.
The claim is made even less credible when you listen to the company's other claims about its practices, such as the idea that they hid the authorship of their apps "for competitive reasons."
Or this howler: that "the vast majority of these apps listed are now defunct (inactive) and a few are in the process of sunsetting." Well, yes, they were removed for violating their users' privacy. It's not like the company had a change of heart or anything.
And then there's this: "Apple and Google restrict root certificate privileges due to the security risk to users. Sensor Tower's apps bypass the restrictions by prompting users to install a certificate through an external website after an app is downloaded."
Twitter's new Terms of Service help academics(permalink)
Twitter just published a new, and much-improved developer policy, one that permits academics to field bots for research and auditing purposes.
https://blog.twitter.com/developer/en_us/topics/community/2020/twitter_developer_policy_update.html
"Researchers will be able to share an unlimited number of Tweet IDs and/or User IDs, if they're doing so on behalf of an academic institution and for the sole purpose of non-commercial research, such as peer review."
https://techcrunch.com/2020/03/10/twitter-rewrites-developer-policy-to-better-support-academic-research-and-use-of-good-bots/
Twitter's also creating a bot registry that must include contact info for the botmaster, so that "it's easier for everyone on Twitter to know what's a bot – and what's not."
https://developer.twitter.com/en/developer-terms/policy#4-b
Italy's "I Stay in the House" law (permalink)
The FAQ for the Italian government's "I Stay In the House" decree is a fascinating document:
http://www.governo.it/it/articolo/decreto-iorestoacasa-domande-frequenti-sulle-misure-adottate-dal-governo/14278
Most notably, Italy has kicked out its tourists. As Bruce Sterling writes, "It's a tourist-ectomy. An Italy devoid of all tourists. It's fantastic, unheard-of. Surely this hasn't happened in at least 700 years."
https://www.wired.com/beyond-the-beyond/2020/03/stay-house-decree/
People are allowed to go to work, to shop, and to run errands, provided it is for an "essential purpose," which you must prove "by means of a self-declaration which can be made on pre-printed forms already supplied to the state and local police forces. The veracity of the self-declarations will be subject to subsequent checks and the non-veracity constitutes a crime."
Business travelers are permitted to enter and leave the country, cab, delivery and freight drivers are allowed to do their jobs, and "outdoor motor activity is allowed as long as not in a group."
Public offices are open. Training activities are suspended. Government offices need to provide hand santizer, but if they run out, they have to stay open ("disinfectant is a precautionary measure but itstemporary unavailability does not justify the closure of the office").
Bars, pubs and restaurants may open from 6AM to 6PM, but have to cancel live music, games and screening events. Theaters, cinemas and museums are closed.
Schools are closed. Universities are closed. Exams and graduations will be conducted by video-link. Med schools are not closed. Research institutions are not closed.
Masses and funerals are canceled. Islamic Friday prayers are canceled.
Farms are open.

Scam-buster hacks into a scam-factory (permalink)
Jim Browning is a talented and prolific scambaiter. He calls the numbers listed in pop-up tech support scams and has the scammers log into a specially prepared system that lets him trace them.
In his latest adventure, Browning thoroughly turns the tables on http://Faremart.com , a Delhi travel agency that was the front for a sprawling network of tech-support scammers taking in millions every year through fraud.
Browning not only traces the scammers: he breaks into their unsecured CCTV network so he can watch them work. He compromises their phone system and listens to the recordings of all their scam-sessions.
https://www.youtube.com/watch?v=le71yVPh4uk
He gets hold of their ledgers, which list how much money each scam nets for the gang. He doxes the scammers and learns their real names. He gets a confederate to fly a drone over their HQ and maps out their comings and going.
In part II, Browning treats us to a delightful scambaiting session in which he mercilessly trolls a scammer who claims to be in San Jose, CA, tripping him up in a series of ever-more-desperate lies.
https://www.youtube.com/watch?v=uV-qa9M-o4E
It's part of a growing genre of journalists who explore and document the operations of overseas scam operations. See, for example, Reply All's excellent podcasts on this:
https://gimletmedia.com/shows/reply-all/6nh3wk https://gimletmedia.com/shows/reply-all/76h5gl
There are two more parts to come in Browning's series (you can watch them now on his Patreon, apparently):
https://www.patreon.com/JimBrowning
He also turned his footage over to the BBC's flagship investigative programme, Panorama, which has produced its own doc based on it:
https://www.youtube.com/watch?v=7rmvhwwiQAY

Postmortem: the catastrophic EU Copyright Directive (postmortem)
Yesterday, the Senate Subcommittee on Intellectual Property held hearings on "Copyright Law in Foreign Jurisdictions," at which two key copyright experts testified on last year's catastrophic EU Copyright Directive.
First up was Pam Samuelson, one of America's leading copyright experts, who explained in eye-watering detail how the compromises made to pass the Copyright Directive produced an incoherent mess that no one can figure out how to implement in law.
https://www.judiciary.senate.gov/imo/media/doc/Samuelson%20Testimony.pdf
Next was Julia Reda, who served in the EU Parliament during the passage of the directive and helped spearhead the opposition to it.
Her testimony really shows you where the bodies were buried: how the EU knew it was making a pig's ear out of things.
https://www.judiciary.senate.gov/imo/media/doc/Reda%20Testimony.pdf
Both are essential reading for anyone striving to understand Article 17 (formerly Article 13) – it is such a tangle of garbage lawmaking that these kinds of guides are indispensable.

Podcast: A Lever Without a Fulcrum Is Just a Stick (permalink)
I've just posted my latest podcast: a reading of my new Locus Magazine column, "A Lever Without a Fulcrum Is Just a Stick," on how copyright failed artists and enriched corporations and what we can do about it.
https://craphound.com/podcast/2020/03/11/a-lever-without-a-fulcrum-is-just-a-stick-2/
Tldr: Giving monopolies to artists doesn't help them gain leverage over the super-concentrated entertainment industry, because the corporations control access to audiences and force artists to sign away those monopolies to get past their gatekeeping.
The more monopolies we give artists, the more monopolies are transfered to corporations, and the more they dominate the market and thus the more they can retain from the earnings generated by the artists' works.
Fights like the EU Copyright Directive are a distraction, a fight over shifting some points from Big Tech's balance sheet to Big Content's – but without any mechanism to move more of that revenue to creators.
Enriching creators means thinking beyond more "monopoly"-style copyright: instead, we have to think about inalienable rights that can be taken away through one-sided contracts (like the "reversion right" that lets US artists take back copyrights after 35 years).
And we have to think beyond copyright itself, by beefing up competition laws to break up entertainment cartels, and by beefing up labor laws to let artists form unions.
There is a role for copyright, but in things like extended collective licensing that would allow all online platforms to access the same catalog and pay for it based on the number of users they have, so a new platform pays pennies while Youtube pays hundreds of millions.
These blanket licenses have been key to keeping other forums for artistic revenues open: think of what the world would be like if one club or radio station could buy the exclusive rights to play the hits of the day, and then use their ensuring dominance to squeeze artists.
If you prefer the written work, you can read the column here for yourself, of course:
https://locusmag.com/2020/03/cory-doctorow-a-lever-without-a-fulcrum-is-just-a-stick/
Here's a direct link to the MP3 of the reading (thanks as always to Internet Archive for hosting – they'll host you too, for free!):
https://archive.org/download/Cory_Doctorow_Podcast_330/Cory_Doctorow_Podcast_330_-_A_Lever_Without_a_Fulcrum_Is_Just_a_Stick.mp3
And here's the RSS for my podcast:
http://feeds.feedburner.com/doctorow_podcast
Now in its 14th year (Thanks to Mark Pesce for convincing me to start it)!

This day in history (permalink)
#10yrsago London Olympics: police powers to force spectators to remove non-sponsor items, enter houses, take posters http://uk.news.yahoo.com/22/20100303/tts-uk-olympics-london-ca02f96.html
#10yrsago Leaked documents: UK record industry wrote web-censorship amendment https://www.openrightsgroup.org/blog/2010/bpi-drafted-web-blocking
#5yrsago Piketty on the pointless cruelty of European austerity https://www.spiegel.de/international/europe/thomas-piketty-interview-about-the-european-financial-crisis-a-1022629.html
#5yrsago Rightscorp loses big on extortion racket https://torrentfreak.com/rightscorp-hemorrhages-cash-profit-from-piracy-remains-elusive-150311/
#5yrsago UK foreign secretary: stop talking about Snowden, let spies get on with it https://web.archive.org/web/20150315031642/http://www.theinquirer.net/inquirer/news/2399082/government-minister-is-bored-with-snowden-and-wants-to-get-on-with-surveillance
#1yrago Defect in car security system aids carjackers, thieves https://www.pentestpartners.com/security-blog/gone-in-six-seconds-exploiting-car-alarms/
#1yrago Former Archbishop of Canterbury cheers on students who are walking out to demand action on climate change https://www.theguardian.com/environment/2019/mar/10/rowan-williams-school-pupil-climate-protests
#1yrago Leaked Chinese database of 1.8 million women includes a field indicating whether they are "BreedReady" https://twitter.com/0xDUDE/status/1104482014202351616
#1yrago Why #Article13 inevitably requires filters https://www.communia-association.org/2019/03/05/final-x-ray-article-13-dangerous-legislative-wishful-thinking/

Colophon (permalink)
Today's top sources: Slate Star Codex (https://slatestarcodex.com/), Slashdot (https://slashdot.org), Fipi Lele, Matthew Rimmer (https://twitter.com/DrRimmer).
Hugo nominators! My story "Unauthorized Bread" is eligible in the Novella category and you can read it free on Ars Technica: https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
Upcoming appearances:
Museums and the Web: March 31-April 4 2020, Los Angeles. https://mw20.museweb.net/
Currently writing: I'm rewriting a short story, "The Canadian Miracle," for MIT Tech Review. It's a story set in the world of my next novel, "The Lost Cause," a post-GND novel about truth and reconciliation. I'm also working on "Baby Twitter," a piece of design fiction also set in The Lost Cause's prehistory, for a British think-tank. I'm getting geared up to start work on the novel afterwards.
Currently reading: Just started Lauren Beukes's forthcoming Afterland: it's Y the Last Man plus plus, and two chapters in, it's amazeballs. Last month, I finished Andrea Bernstein's "American Oligarchs"; it's a magnificent history of the Kushner and Trump families, showing how they cheated, stole and lied their way into power. I'm getting really into Anna Weiner's memoir about tech, "Uncanny Valley." I just loaded Matt Stoller's "Goliath" onto my underwater MP3 player and I'm listening to it as I swim laps.
Latest podcast: A Lever Without a Fulcrum Is Just a Stick https://archive.org/download/Cory_Doctorow_Podcast_330/Cory_Doctorow_Podcast_330_-_A_Lever_Without_a_Fulcrum_Is_Just_a_Stick.mp3
Upcoming books: "Poesy the Monster Slayer" (Jul 2020), a picture book about monsters, bedtime, gender, and kicking ass. Pre-order here: https://us.macmillan.com/books/9781626723627?utm_source=socialmedia&utm_medium=socialpost&utm_term=na-poesycorypreorder&utm_content=na-preorder-buynow&utm_campaign=9781626723627
(we're having a launch for it in Burbank on July 11 at Dark Delicacies and you can get me AND Poesy to sign it and Dark Del will ship it to the monster kids in your life in time for the release date).
"Attack Surface": The third Little Brother book, Oct 20, 2020.
"Little Brother/Homeland": A reissue omnibus edition with a very special, s00per s33kr1t intro.
13 notes
·
View notes
Text
How To Hack WhatsApp Without Rooting By Exactspy ?
How To Hack WhatsApp Without Rooting By Exactspy ?
How To Hack WhatsApp Without Rooting By Exactspy ?
It is exciting for everybody to hack someone’s WhatsApp account. Whatsapp is most illustrious social networking application that is employed by numerous folks. once WhatsApp has launched, then it suffered from tiny security choices. when typically, a user has several resources which may modify to induce the WhatsApp messages with unauthorized…
View On WordPress
#how to hack someones whatsapp messenger online#How To Hack WhatsApp Without Rooting#how to hack whatsapp without the target phone#whatsapp hack android root#whatshack without root apk
0 notes
Text
How To make use of Tutu App?
Although different in functions, each are closely similar to each other. However, there is no such thing as a such file like tutu helper vip android that may work on both the platform concurrently. Read a number of the distinctive features of Tutu helper free Android file. The third-party app retailer is available in two options-free and VIP. It extensively supports widespread OS of Android and iOS, along with enablement with Pc. The app store permits the download of the most recent apps and updates on a regular basis. It supports the in-app integration whereas being the quickest downloader. Infinite and free access to widespread apps and games. These have been only a few highlighted options of tutuapp helper. Other than what has been given above, there’re many extra routine functions of tutu helper android App to make the most of and get essentially the most out of it. Tutuapp latest version has lately give you further further features to supply its users. WhatsApp Plus is now also available on the tutuapp retailer. From the cateogry of casual video games, My Talking Tom apk is quite fashionable and engrossing. You possibly can watch virtually every movie. This app has obtained a huge library from the newest movies to G(outdated) Movies. Movies and Tv Shows. Also, you'll be able to watch all of the Tv Series too. This app is superb, quick and User-Friendly and last but not the least don’t forget its tiny. App has inbuilt Updater which retains it updated at all times. Please Sign up to Movie HD together with your Google Account on Android Devices. You will need a Movie HD Activation Code just for Fire Tv and Android Tv to continue Watching Movies with this app or you will get a No Connection Error. How to install Movie HD Apk on Android Devices? Download the Apk File from the above and AMPlayer Apk. Run the app and start Streaming. Follow the steps beneath to run Movie HD Apk on Amazon Fire Stick and Fire Tv. The trick shared earlier in this put up was lengthy and robust so I have updated it with a shorter and efficient manner. Select this feature if you wish to root your android system. It's going to install an app in your android telephone referred to as as SuperSU which manages all Su permissions to different root apps. Once, you could have chosen this selection after which there are following potentialities. Success: Congratulations, your android phone is rooted successfully. Restart it now and Open SuperSU and click on on Update Binaries (in the event you get any popup). Enjoy, your rooted android gadget now. Now, you can get pleasure from all android apps like fortunate patcher which is able to work on rooted gadgets only. Failed: That exploit was unable to root your android gadget. Try every other exploit (if obtainable). App Hanged or Crashed? Close app and Re-attempt that exploit now. There are many advantages of unrooting the android phone. Select this selection if you wish to unroot your machine. This option will delete SuperSU app and it’s binaries. To unroot your machine, follow under steps. 1. Select unroot from the drop down menu. 2. Select any of accessible exploit. 3. It would delete su binaries and su app too. This selection is meant for superior users solely. It's not beneficial to make use of this option. After deciding on any of out there exploits, if you're getting any error with a quantity lower than or equal to 9 then your telephone can’t be rooted by way of Framaroot. If you bought error 10 then give a try to Framaroot 1.5.3 APK. Q1. Framaroot not engaged on XYZ system. Ans. You may give a attempt to other exploits. You possibly can try different exploits or every other APK. So it was all about Framaroot app. In case you are having any downside in downloading framaroot apk or set up it or in rooting your android telephone. Be happy to remark below. You could already know that your IP deal with is exposed to Government Agencies and ISP. IPVanish VPN is most trusted VPN service and its Military Grade Encryption ensures your internet privateness with out logging your exercise over the internet. Moreover, with one IPVanish subscribtion, you possibly can protect 10 Devices Simultaneously. The Snooping Hackers, trackers and Internet Provider will never be ready to trace your web activity. Download HereCyberflix Tv apk is clone of Terrarium Tv which was fairly standard app but discontinued by the developer. Not to fret, Cyberflix Tv is again with the new avatar of Terrarium Tv. Cyberflix Tv also scraps the video links that are already accessible on the web. Cyberflix Tv don't host any media file on their servers. The video source is unknown and they are positively not secure to your on-line privateness. Don’t panic, a good VPN will take care of that for you. With the most recent version of the applying the consumer may create number of download lists of their favorite tracks for offline functions. The variety of downloads from spotify nod which were first restricted to few, now has no limit. Creating playlists has also been given choices of sharing and discussions. The latest model has all of the options have been unlocked which earlier than were not obtainable without spending a dime customers. Options like unlimited shuffling from top to backside, quick and advanced searches in hacked spotify are the plus level. While apkview.com of repeats which was before limit to few has also been rearranged. Ads which were probably the most irritating part of free applications, which popup after ever minute or change in menu have been the users biggest points. But the most recent model of spotify apk download is completely freed from unwanted ads popups with an anti-advert characteristic which is also unlocked in contrast to others. The excellent and clear sound quality with a number of sound choices have been added with fully controllable sound qualities option from Normal, High to excessive high quality of 320 Kbps.
1 note
·
View note
Text
Whatsapp apphack

WHATSAPP APPHACK HOW TO
WHATSAPP APPHACK SOFTWARE DOWNLOAD
WHATSAPP APPHACK INSTALL
WHATSAPP APPHACK ANDROID
Social Media Monitoring: Using Spyic, you can see social media messages as well.
SMS Tracking: You can see all received and sent SMS messages on the target phone discreetly.
What’s more, you can also see the contact information and the media files that are being exchanged. Click on the ‘WhatsApp’ tab and you will now be able to see all WhatsApp messages. You will notice that the dashboard has several sections. Head straight to your Control Panel on the remote device. Step-3: Once you have everything set up, monitoring can now begin. All it takes is in one click! It is designed to not drain the battery. It can also be easily uninstalled remotely.
WHATSAPP APPHACK ANDROID
The Spyic Android app only takes about 2M of space on the phone. The process will take fewer than 5 minutes. Even WhatsApp spying is possible without rooting first.ĭownload the app and allow all permissions which the app asks. There is no need to root the phone, though. The Spyic Android solution requires installation on the target device.
WHATSAPP APPHACK HOW TO
The solution is jailbreaking-free unlike most other spy apps out there.Īlso Read: How to Hack Whatsapp Messages Without Access to Phone Being cloud-based, you can use any browser of your choice to use the app without installing anything. The Spyic iOS solution is entirely remote. Let the app sync all data which can take a short while. If the target is an iOS device, simply verify it’s iCloud credentials. Step-2: It’s time now to select the target device type. This process is simple and takes a few seconds. Step-1: First, you need to sign up for a new account. You can use Spyic to hack WhatsApp messages very easily. Using the keylogger, you can log into any social media account used by the target.ġ.2 How to Use Spyic to Hack WhatsApp Messages Online Without Survey
Android Keylogger: The app has a built-in keylogger which can capture the username and password of the social media accounts.
You can get to know the phone numbers of the contacts as well. You can even see the media files that are shared. You can see both incoming and outgoing messages.
WhatsApp monitoring: Spyic allows you to monitor all WhatsApp conversations.
If you find an Android spy solution that offers remote installation, then it’s a scam, a virus, or a phishing attempt.
WHATSAPP APPHACK SOFTWARE DOWNLOAD
**Warning: No Android spy app in the market works without an initial software download and installation. The app then silently runs in the background without being detected. What the app does is that it deletes its icon after installation. However, Spyic is special in that it uses stealth technology to stay invisible. It is not really possible for any Android solution to work without installation. If you ever come across an app that claims to work without installation, be aware! This will require physical access to the target phone.
WHATSAPP APPHACK INSTALL
You will first need to install Spyic Android app on the phone. However, with the Android operating system, it is not possible to set up monitoring remotely. This ensures that the target does not detect that he/she is being monitored. That’s all: everything else is done remotely. All you need are the iCloud credentials of the target device. You do not need physical access to the phone at all. Using this, there is no need to install anything on the phone. It is important to note that with an iOS target device, Spyic for iOS has introduced a cutting-edge cloud-based solution. When it comes to hacking WhatsApp by just the number, you need remote monitoring and setup. The app is very simple to use and has an intuitive interface that stands out. Spyic is a very popular app that is trusted by millions of people across 190 countries worldwide. If you are looking out for a way to hack WhatsApp by phone number, you need a spy app. Part 1: How to Hack WhatsApp Account Using Phone Number
Part 4: Hack a WhatsApp Account Using WhatsApp Web.
Part 3: Hack a WhatsApp Account Secretly Through Wi-Fi Spoofing.
2.2 WhatsApp Hack Online Without Survey.
Part 2: How to Hack WhatsApp with Mobile Number.
1.2 How to Use Spyic to Hack WhatsApp Messages Online Without Survey.
Part 1: How to Hack WhatsApp Account Using Phone Number.

0 notes
Text
Anti hacking mobile chrome

Hoverwatch is one of the cheapest methods by which to hack mobile phones with computer. Sign up for Neatspy for free or check the live demo here > Part 2: How to Hack Mobile Phones with Computer via hoverwatch In the next part, we’ll show you how to hack others phone using an alternative method. Now you know how to hack mobile phones with computer using Neatspy. Step 4: Go to the Neatspy dashboard and hack other phones with computer. Step 3: Hack Android without Rooting - Download the Neatspy app and install it into the target phone. Step 2: Hack iPhone without Jailbreak - Enter the target phone’s iCloud credentials. The following steps will show you how to hack mobile phones with computer: Hacking mobile phones with a computer is extremely simple when you’re using Neatspy. How to Hack Someone’s Phone with computer using Neatspy? As such, you can find out where they are and also check their entire route history. As such, whenever the target phone goes beyond that perimeter, you get a notification and alert in your computer dashboard. Geofencing: With this feature, you can set up a physical boundary for the target phone.As such, you can view all of their media, see all their messages, check the profiles of their contacts, etc. Neatspy gives you access to the target user’s Facebook, Skype, Viber, WhatsApp, and various other social media apps as well. As such, if you hack their social media activity you can find out all you have to about them. Social Media Monitoring: Most individuals lead their lives through social media these days.Most importantly, you do not need to root the target device to use this advanced keylogger feature. This gives you access to all of their social media accounts, mailing accounts, and everything else. As such, you can find out all of the target user’s passwords. Keylogging: This feature gives you access to a log of all of the target user’s keystrokes.The following are some of the most advanced and best mobile tracking features: Neatspy has a wide range of features which you can use to hack mobile phones from computer. As such, the target individual won’t grow suspicious.īefore using Neatspy, you should try out their Free Online Live Demo Here. Furthermore, Neatspy runs silently in the background and doesn’t consume a lot of battery either. You can delete the Neatspy icon from the target phone. And if it’s an Android phone, all you have to do is install the Neatspy app into it, and voila! You’re all set to hack a mobile phone with a computer.Įven after you install the Neatspy app into the target phone, Neatspy is completely discreet and stealthy. If you have the target user’s iCloud details, you can hack their phone remotely without even physically accessing it.

It’s not advisable to jailbreak or root the target phone because that opens up the target phone to hackers and malware. Neatspy is completely legal to use and it’s trusted by millions of users from across the world.įurthermore, one of the best aspects of Neatspy is that it can also hack other’s mobile phones without jailbreaking or rooting your target phone. However, it has already established itself as the leader of all spy tracking software and tools. Neatspy is the best tool with which to hack mobile phones with a computer. Part 1: How to Hack Mobile Phones with Computer via Neatspy
How to hack someone’s Phone with computer using hoverwatch?.
Part 2: How to Hack Mobile Phones with Computer via hoverwatch.

How to Hack Someone’s Phone with computer using Neatspy?.
Part 1: How to Hack Mobile Phones with Computer via Neatspy.

In this article, we’ll show you how to hack someone the right way, using reliable and secure phone hacker apps. But there are also a lot of fake hacker apps in the market. Regardless of whether you identify with any of the aforementioned scenarios, there are a lot of ways to perform a free phone hack.
Employers can also learn how to hack others phones to be able to better monitor their employees.
In this case, performing a free phone hack will get you all the information you need.
Perhaps you’re a suspicious spouse and you want proof that your partner is cheating on you.
This will allow you to control their cell phone usage and find out what they’re up to.
Maybe you’re a concerned parent and you want to hack other phones belonging to your children.
As such, if you learn how to hack mobile phones with computer, you’ll be able to both track its location and control it remotely.
Perhaps your phone is lost and you want to use a computer to find it.
There are a lot of reasons why you might want to learn how to hack mobile phones with computer:

1 note
·
View note
Text
Find Out Who is Worried About Apk Download and Why You Should Be Paying Attention
Also, bear in mind that Freedom APK necessitates root permissions. Take aim and throw a Poke Ball You will have to remain alert, or it may become away! The slow net doesn't enable you to utilize Facebook and especially its cellular app smoothly. Now, the program isn't on the Google Play Store. 1 such app is named GB Whatsapp. Cheat Engine is among the ideal Android sport hacking application out there, you could have known. To begin with, start the program from your Program drawer after you've installed it using any of the aforementioned methods I have explained earlier. Users should remember the Fortnite for Android isn't likely to operate using USB debugging enabled. There are numerous hack tools to be found on the web to produce the gameplay simpler. Even if you start purchase, you are going to be able to encounter trendy and intriguing apps there that too come free of charge. From time to time, an app could possibly be updated, inducing the smartphone to crash. The New Angle On Apk Download Just Released Blue stacks emulator is a software which provides you the interface of the telephone and permits you to utilize it like a phone itself. If you would like to download an app, and it isn't available in any other android store, Mobogenie market is a fantastic place to look for. Widget Android OS delivers some widgets on its home screen that make it possible for you to access the settings without any difficulty. The Benefits of Apk Download Downloading the blackmart alpha app is not a very challenging task if you keep on after the process given below. It's possible to root your device with assistance from magisk. So as to accomplish this, you should define the path of these fonts, which you've got to apply. Don't be afraid to download the APK file it's protected and doesn't include any type of virus a Malware. Follow all the instructions that are displayed on the track. You're in a position to conceal root from various other applications. You are going to be taught how to pick the fonts and the way to edit the pictures in accordance with your preference. Any user can create their own liberty to watch their videos that are desired in a variety of languages. Where to Find Apk Download If any site is claiming to the paid version of the app then it's a scam, then you shouldn't anticipate on the site. Magisk Hide is the feature that is offered in the Magisk Manager application and should you need to hide the major permission for the specific banking application. android apk and Don'ts of Apk Download To begin using dap you merely need Redbox live tv apk which you are able to download from our site. It is possible that you watch real-time tv with a great streaming quality. You do not require various apps to watch films and to see real-time tv. Unfortunately, not everybody can access Android Market. You'll be made to the App Store and download the game effortlessly. Bigger Screen should you adore big screens, you may choose to elect for a Android cellphone. What Is apk free About Apk Download? Also, Facebook Lite is extremely useful and ideal for the folks that have a slow online connection. download apk is going to be mapped automatically. Phone Options Aside from multitasking, another wonderful advantage of Android is the fact that it provides a plethora of options.
1 note
·
View note
Text
How To Hack WhatsApp Without Rooting By Exactspy ?
How To Hack WhatsApp Without Rooting By Exactspy ?
How To Hack WhatsApp Without Rooting By Exactspy ? It is exciting for everybody to hack someone’s WhatsApp account. Whatsapp is most illustrious social networking application that is employed by numerous folks. once WhatsApp has launched, then it suffered from tiny security choices. when typically, a user has several resources which may modify to induce the WhatsApp messages with unauthorized…
View On WordPress
#how to hack someones whatsapp messenger online#How To Hack WhatsApp Without Rooting#how to hack whatsapp without the target phone#whatsapp hack android root#whatshack without root apk
0 notes
Text
Delivery Drivers Are Using Grey Market Apps to Make Their Jobs Suck Less
The McDonald’s on Jalan Salemba Raya, Jakarta’s crowded main thoroughfare, is a magnet for food delivery orders. On any given day, a dozen or so app-based delivery drivers—locally called ojol—wait in the parking lot. Inch by inch, they try to move as close as they can to the center of the lot, desperate to have the matching algorithms recognize their proximity and assign them an order.
But even more drivers are there virtually, using GPS-spoofing apps to position themselves right in the center of the McDonald's lot while they physically wait under nearby shelters. Using these unofficial apps, known as tuyul, drivers can set their GPS pins at the optimal location they would like orders from, without having to physically drive there.
In Jakarta, these kinds of unauthorized apps are a common tool-of-the-trade among app drivers working for Gojek, a $10 billion delivery and transport "super app" that is the Indonesian equivalent of Postmates, Apple Pay, Venmo, and Uber. Though Indonesia is by far its biggest market, Gojek operates in more than 200 cities in Indonesia, Singapore, Vietnam, and Thailand.
“These are people in need who have to hold on to their jobs on difficult streets," one driver told Motherboard, explaining why drivers resort to using these apps. "They are not doing this for fun but because they have no other option.”
Like many drivers interviewed, the driver asked not to be identified, fearing loss of work and retaliation by Gojek (The experiences ojol drivers have had with Gojek were collected both as part of my dissertation research at MIT and then later, for this story.)
Over the last six years, a burgeoning underground market for unauthorized, third-party Gojek apps has emerged. Named after a child-like spirit in Indonesian folklore that helps his human master earn money by stealing, each tuyul app responds to specific needs of drivers to help make their jobs less miserable.
For instance, when older drivers complained they could not read important details of a matched order because the text was too small, a homebrewed application came into the market which magnified the destination, fare and distance of each order offered. This feature eventually spun out into apps that allowed "automatic bidding": each order would be accepted as it was offered, removing the hassle of looking at the phone. To give drivers more control over the orders offered and to avoid rejection-associated penalties, some apps allowed drivers to set filters for order characteristics—setting the maximum distance and minimum pay, for example.
The GPS-spoofing apps remain the most popular type of tuyul apps, with some having more than 500,000 downloads on the Google Play app store.

A crowd of Gojek delivery drivers wait for orders on their motorbikes. Photo by Rida Qadri
After Gojek's app was launched in 2015, many drivers needed help with small technical glitches and app malfunctions. Drivers who were more tech-savvy started helping other drivers with technical support. Eventually, these drivers began being known as "IT Jalanan"—or "IT of the Road"—creating a form of localized tech support that was easier to access than Gojek’s own tech support.
“We don’t have to go to the [Gojek] office and only for a small fee we get help wherever," one ojol driver told Motherboard. Eventually, small tech support tasks like factory resets, reboots, and GPS fixes led to a variety of unofficial apps for varying driver needs. Another driver noted the ease with which IT Jalanan fixes problems and innovates: "Even though it's illegal, the IT of the streets is very agile and smart—it makes our lives easier," the driver said.
These apps can be downloaded in various places. Some app developers have listed them on Google Play. Others have websites where drivers can download the application file directly, and a much larger proportion are sold directly through driver groups on WhatsApp and Telegram. There are two options for payment: a single payment with no "post-sale care," or a monthly membership fee which gives the driver access to an online group for technical support and updates.
Extensive manuals are shared on how to prepare an Android phone for the unofficial apps. Instructions include how to gain root access on phones, clearing the device's cache, and downloading a host of other applications which prevent detection by Gojek's system. If help is needed with any of these technical requirements, drivers can ask other technically-savvy drivers or get support from the developer.
While Gojek has constantly tried to ban tuyul, drivers who use the apps argue tuyul helps them do their jobs better, and are better designed to help them tackle the problems they regularly face as drivers.

Screenshots of unauthorized apps used by Gojek delivery drivers, which allow them to spoof GPS location and filter orders.
Take the GPS-spoofing apps. In a crowded city like Jakarta, the platform’s decision to match drivers based on spatial proximity erroneously assumes that drivers can simply show up and wait in high demand areas. “We can’t wait outside malls, we can’t wait in parking lots, we can’t wait on [the] side of the roads, then how do we get orders?” another driver told Motherboard.
By prioritizing proximity in matching drivers with orders, the algorithms push drivers to get closer to hotspots of demand. When that's not physically possible, it forces drivers to use clever hacks around this problem. Another driver who spoke to Motherboard often waits outside major train stations in Jakarta, and said that jostling for space with hundreds of commuters, taxi drivers, and street vendors doesn’t make for a pleasant experience for anyone. “Sometimes there are so many ojol drivers outside the train station that their queues take up the whole road," the driver said. "That is unfair to us and the public, preventing cars from passing."
Spending hours sitting on a stationary bike in parking lots is also uncomfortable, particularly in Jakarta’s climate, where rain is never far away. Therefore, many drivers argue that allowing them to bid for orders without needing to be in a precise location helps everyone.
Helpful as they may be, the unauthorized apps open up drivers to a host of risks. For one, there is no way for drivers to verify whether the services they pay for will actually work, and there's no telling when Gojek will ban the use of an app they purchased. Since tuyul developers can earn millions of rupiah ($1 is roughly 14,500 rupiah), it is in their interest to hype up their products and charge high membership fees.
Drivers have also used GPS-spoofing apps to create fraudulent orders, called "opik" (a play on the phrase "order fictive"). By creating a fake digital GPS trace, they can indicate to the platform that they completed an order without ever moving. Rings of drivers who have made millions of rupiah scamming Gojek’s system have been discovered and arrested in Jakarta.
Gojek has implemented a zero tolerance policy in response to the GPS-spoofing apps, and the company even runs campaigns to discourage drivers from using them. Drivers have been warned that anyone detected to be using tuyul apps will be suspended permanently. Gojek's security system has also improved over time, finding new ways to detect the use of unauthorized apps and rooted phones.
Gojek could not be reached for comment on this story.
But while tuyul apps have become harder to download and use, drivers' lived experiences and the conditions which pushed them to download the apps in the first place have not changed. Some drivers would like to put an end to this cat-and-mouse game, and have Gojek recognize that the adversarial relationship doesn't benefit the company or ojol drivers. One of these groups is Gojek on Twitter (GOT), a prominent driver community aiming to make sure “drivers are not slaves of the algorithm.” GOT are like the influencers of the driver world; its founders have collectively amassed more than 50,000 followers on Twitter. Though they disagree that tuyul are only used to cheat the system, GOT founders understand the double bind drivers face when using tuyul: they reduce hurdles drivers face in their jobs, but their use risks suspension while also giving an unfair advantage to drivers who are willing to bend the rules. GOT does not advise drivers to use tuyul apps, but understands why people would want to.
A founding member of GOT, who uses the online pseudonym Liam, proposes a system that could be a win-win. Gojek could officially allow drivers to place their GPS spot in areas within a 1-kilometer radius of their actual position. He argues that on a motorbike it would only take a minute or two to arrive at the order location from such a short distance away. Gojek could then ensure that drivers don’t place their GPS position any further than this radius, which would cut down on fake orders. Drivers would also be able to indicate that they actually want to accept orders from that area, a much stronger signal than just physical presence.
But for this system to work, Liam says, customers would need to change their expectations away from instant gratification. “The customer attitude [is] now, now, now," Liam told Motherboard. "If a driver is two minutes late, they blow up.”
Despite Gojek's adversarial relationship with tuyul, the company has benefited by adopting some of the features originally created by unauthorized apps. For instance, the "automatic bidding" app drivers had developed was introduced into the official Gojek app through a new feature called "autobid." Gojek also briefly introduced the ability for drivers to filter orders, but according to drivers removed the feature when too many drivers started filtering for specific types of orders. While Gojek adopting driver-developed app features shows its responsiveness to driver needs, it also comes with the fear of drivers losing agency over how and how long they can use the features.
The experiences of Indonesia's ojol drivers are not unique. Across the world, app-based workers are precariously employed via algorithmic systems that give them little control over their daily work, forcing them to constantly fight for agency with tricks and hacks. In that sense, tuyul app developers are responding to segments of the driver population that Gojek either does not reach out to, or hears about too late.
In other words, they are doing the same thing that causes startups to be hailed as innovative disruptors. After all, Gojek, too, was once just a startup, accused of cheating the system while claiming to make the jobs of motorbike drivers easier and more efficient—why is it any different when drivers try to do the same?
Delivery Drivers Are Using Grey Market Apps to Make Their Jobs Suck Less syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
Spotify Premium Free Iphone Without Jailbreak

Free Access to the Premium Features of Spotify with Spotify++ – Download from AppValley: Spotify is one of the most popular music streaming services. Similar to various other music-streaming services they depend on paid users to generate revenue. Paid users are the one who opts for Spotify Premium. As compared to Spotify, the premium version of the same comes packed with certain essential features that are not present in the non-premium version. However, you can get access to the premium features, without paying a dime, with Spotify++ free download.
Spotify Jailbroken Download
Spotify++ is a hacked version of the original application that provides you with the features of Spotify Premium free of cost. Unfortunately, Spotify++ is not available on the official store. If you wish to install the same then you require taking the services of a third-party App Store. We Recommend AppValley for the purpose as it has a myriad of other hacked applications that could be useful to you.
If you are in that group of users, here’s how you can get Spotify Premium for free on your iOS device. I recently came across an app called Spotify. Apparently, this is the tweaked version of the original app, and the Premium plan is already unlocked for you. How to Install Spotify on iOS 10 Without Jailbreak. Spotify for iOS (iPhone and iPad) is a tweaked version of Spotify which brings Spotify premium features for free. Learn how to install Spotify for iOS. Spotify for iOS (iPhone and iPad) is a tweaked version of Spotify which brings Spotify premium features for free. How to install iPA files on iPhone without Jailbreak. Step 3: Once you.
However, before we proceed towards the download and installation of Spotify++ let us have a look at the set of features that you can enjoy with Spotify++. Also, Check Out another best-tweaked application “WhatsApp++ Download on iOS Within 2 Minutes“.
Contents

How to Get Spotify Premium for Free on iPhone. We have shown you the “Spotify premium free Android“ app installation step-by-step, and this time it would be a different set of instructions on an iPhone. Apple has designed iOS, and they are very strict when it comes to iOS third-party apps or non-market apps. That’s all, you can start using Spotify for free. Similar to OGapp it’s a great alternative app store for iPhone containing premium modded apps for iOS. There are many cracked iOS apps available in this store including Spotify or Spotify Premium. Go to TutuApp official website using the link below. How to Get Spotify Premium Free on iOS (without Jailbreak) You can update to Premium plan to get. These options are unavailable for Free Spotify Premium account 2020 holders. These have been a few of the most helpful options of Spotify which get unlocked in buying its premium account. Read Also: 100+ Free Fortnite Accounts August 2020. Free Spotify Premium Account Username and Password 2020.
1 Spotify++ on iOS | Features:
1.2 Spotify++ on iOS – FAQs
Spotify++ on iOS | Features:
The best feature of Spotify++, present in Spotify Premium, is that you can play any song, any time on any device- mobile, tablet, or a computer. Moreover, the non-premium version of Spotify does not let you download music for offline listening, but, in Spotify++ you can download your favorite music to your local storage for offline listening. The following are some more features of Spotify++.
The non-premium version of Spotify does not offer all the sound qualities for selection purposes. However, Spotify++ has amazing sound qualities to offer.
Ads ruin the music listening experience especially if you are listening to songs on a playlist. Spotify++ eliminates the advertisements.
You can skip songs for the unlimited number of times in Spotify++, however, the non-premium version provides an only a finite number of skips.
The crazy thing about Spotify++ is that you get all the features of Spotify Premium without paying anything. Are you interested to download Spotify++ on iPhone/iPad. The following are the download and installation steps for the same?
Best Apps from AppValley
AirShou – Best iOS Screen Recorder Download.
WhatsApp Watusi Tweak Download with Updated AppValley.
FaceBook++ iOS 13.2, 13.1 & iOS 13/12+ iPhone/iPad No Jailbreak.
Install Spotify++ on iOS using AppValley
Your first step is to launch the Safari Browseron your iOS device and click down belowto navigate to the webpage from where you can install AppValley onto your iOS device.
Alternate Download Link ⇓
Click on the ‘Install AppValley’ button on the webpage. The Settings of your device will open up and you will get a prompt to install the profile of AppValley.
Please go ahead and install the profile. This will bring AppValley onto the home screen of your iOS device. Trust its profile before launching.
From AppValley, simply search for Spotify++ and tap on ‘Get’ next to the application to download and install the same onto your iOS device.
Do not forget to trust the profile of Spotify++ as well prior to launching the application.
Android Users: “AppValley Android APK Download“.
Spotify++ on iOS – FAQs
What is Tweaked Spotify++ ??
There are hundreds of great independent tweak developers out there. They just tweak or mod the paid application and provide us for free. That’s exactly Tweaked Spotify means. We can enjoy all premium applications for free with these tweaked applications. It’s not against any policies out there, but still, I would recommend you use VPN while using Spotify++ on iOS using AppValley to be more in the safest zone if you concern too much about privacy.
Is AppValley Safe to Download Spotify++ ??
AppValley doesn’t have any malware or viruses in it and it won’t break any Apple law, so, obviously, It’s a completely safe application to download our favorite “Spotify++“. We are using this Spotify++ for the last one year and we are damn sure that it’s the safest application as AppValley not accessing any root folders of Apple.
Why my Spotify++ Not Working ??
If this error is from the AppValley side, I would suggest you uninstall the earlier version and install the latest version to fix the issue. This usually happens when the app got revoked because of some bugs from the developer end or AppValley end. If you face the Spotify Plus Plus not working issue even after installing the latest version form AppValley, Just switch off your router and switch it on again and try it out. It would definitely work now, no matter what. Please make sure that Spotify is not in offline mode or revoked Apps Section in yourGeneral Settings, this might cause issues some times.
How Can I get Spotify Premium for Free ??
We have a hell lot of third party apps in that we get all paid apps tweaked versions for free. You will get the Spotify premium with some enhanced features added to it. I would list these few of my favorite apps store apps where you get Spotify Premium for Free, TuTuApp, AppValley, TweakBox and Emus4U Store. Try out any of these third-party apps stores that too without any jailbreak of your ios device and get the Spotify Premium for Free.
What is Spotify Plus Plus ??
Spotify++ or Spotify Plusis a tweaked version of Spotify developed by independent developers out there. You will get all premium features of this application at absolutely no cost per month subscription. It’s an official MD version of Spotify where you enjoy all premium features for free.
Can You Download Songs on Spotify Plus Plus ??
Yes, you can download all your favorite millions of tracks to the offline with this tweaked version of Spotify. You can enable download options in settings and offline them to listen to them while you are not connected to any internet.
How to Uninstall Spotify++ from iOS
If you are a music lover, Spotify++ is the best-modded version of the app. It gives you an unlimited collection of music in the best quality. You can even download songs from it. If you are still not finding it good enough, you can easily uninstall Spotify++ from iOS devices. Refer to the procedure given in the coming section.
You can uninstall Spotify++ safely by following the instructions given below.
Find the Spotify++ app from the home screen.
You need to press and hold the app icon for a while.
When it starts wiggling, tap on the Cross button at the top of the icon.
From the popup window, tap on Delete to confirm the action.
That’s all you have to do. The procedure is simple and removes the app safely. There will be no junk files left after uninstalling Spotify++ from iOS.
Conclusion: Spotify++ Download on iOS [iPhone/iPad]
Spotify++ gives the power of premium in your hands – Final Words. By following the steps mentioned in this guide, you caninstall Spotify++ onto your iOS device. If you face any issues during the installation, please let us know about the same via the comments section provided below. Also, let us know about your experience of using Spotify++.
Spotify Jailbroken Download
Thank You.

0 notes
Text
Best Android Hacking Apps
There is very much demand for such android hacking apps that can turn an Android phone/mobile into a hacking machine. So I make a list of the 27 best hacking apps for Android. That will turn your Android into an advanced hacking machine. Android is the Operating System that is used by more than 2 billion people. Android is a widely used operating system in the world. The developer of Android is Google. Android uses a modified kernel of Linux.
As it's Kernel made of Linux, it is difficult to hack an android on Kernel Level, but do you know android is most vulnerable also if you disable play protect from your device. And you can hack android easily by doing that on the Operating System level. So, we are going to discuss some 26 hacking APK for android, which will turn your android into a hacking machine. Such hacking apps for Android are the collection of some best apps which are used only for penetration testing and legal hacking to secure your network.
1. Aispyer
Aispyer is one of the best hacking apps for Android. If you are searching for the Android hacking app, then Aispyer is the Most secure and Reliable mobile phone tracker for you. Basically, Aispyer is a multi-functional spy app for android. It is related to track WhatsApp, Facebook, Apps, Phone Number, Web History, GPS, SMS, Email, Photos, Keylogger, Calendar, Skype, Snapchat, Line, Instagram, and Line.
The reason I would like to recommend the software is that it comes with high-end security and unobtrusiveness. Its ultimate control will be in your hands without any need to worry about information leakage. It is all one mobile tracking solution for Android users. You do not need to download any other app because this app has everything that you need. With the help of this app, you can track almost everything on your victim's mobile.
2 USB Cleaver
USB Cleaver is one of the best tools for stealing information from a connected computer system. Through this application, you can get data like stealing chrome password, IP address of the victim, dump WiFi password, etc. The best thing is this tool does everything silently without the knowledge of the victim. You can test/download this tool from below.
3 Droid SSH
The full form of SSH is Secure Shell. Basically, SSH is a server, it runs on port 22, and it helps you to connect from one computer to another computer securely. With the help of the IP address of your device and a secure password. So what is the use of Droid SSH? Basically, Droid SSH is an android app that lets you connect to your device from a PC and execute terminal and shell commands.
So you must be thinking why I post this tool in hacking apps for Android. Basically, This tool can be used for ethical hacking, like if you find any vulnerability on the SSH server and you got the password and IP of an SSH server. Then you can easily connect your android device to SSH, and you can execute terminal and bash commands. Use this tool in only a legal way.
4 Network Mapper
Network Mapper is one of the powerful apps for android that helps you to scan and discover network protocols, open ports, service discovery, OS discovery, and Vulnerabilities on a network. You can use a network mapper for finding vulnerabilities in open ports on your website. It also helps you to find the misconfiguration of servers. If you are looking for how to use Nmap in Linux, then here is the full tutorial on how to use Nmap. There is no need to root your android device to use this hacking tool. You can download the network mapper from below.
5 Droid Sheep
Want to prank people that are on the same Wi-Fi Network? Then this application is best for you. So what Droid Sheep do? It can monitor the activity of all the people connected to your Wi-Fi network. If someone is browsing a website and searching for a movie, you can intercept his request, and you can send a victim to another website as you want.
Droid Sheep only works. Droid Sheep is an open-source application. This application required rooted android phones. So if your android isn't rooted then, you can root your android to use this application. You can download Droid Sheep from below.
6 AndroRat
Rat stands for remote access tools. Andro Rat is a java based application. With this app, you can directly take the remote access of the Victim's android phone. The drawback of this tool is that it will only work on a local area network (LAN). You can take full control of any android device with the help of this tool.
0 notes
Text
3 Ways to Hack Someone's WhatsApp without Their Phone
No matter whether you're using this program for business or private reasons, WhatsApp is undoubtedly that a must-have program for every one of us. Occasionally, many of us may wish to snoop in their spouses or company nemesis who utilize WhatsApp just to understand what they may be around to. How is it possible in a universe where different men and women wish to maintain their privacy protected at any cost? The solution is simple: simply hack on the WhatsApp accounts in question, and you're prepared to go. This report takes into detail the many methods on the way to hack someone's WhatsApp with no telephone or with no knowledge.
Part 1: Crack A Person's WhatsApp Messages with them Understanding Utilizing Spyzie
A good means of how to hack a person WhatsApp with them understanding is by employing the highly-advanced applications Spyzie. When it's used to hack on whatsapp messages in an android telephone, it uses attributes like catching screenshot and keylogging to allow you to monitor every action on the target device. Though you want to set up the monitoing program on the target telephone, the procedure is really easy. On the flip side, if you'd love to track an iPhone, you do not even have to get into the target device. Here's a live presentation: https://my.spyzie.com/livedemo/dashboard.html
With this system, you're ensured full access to another telephone's WhatsApp dialog since they go and come without the slightest understanding of another party. If you would like to understand how to hack a person WhatsApp with them understanding by using Spyzie, simply follow these simple steps.
1: You will need to make a superior account. It will make it possible for you access to control panel and see the tracked WhatsApp messages along with other information.

Suggestion: Please be aware that you don't have to root the goal android telephone or jailbreak the goal iPhone (however guarantee that the iCloud backup is enabled).
2: If it's an android telephone you'd love to hack on, you'll have to set up the tracking program on the target device and also make some vital settings. You ought to discover comprehensive directions after logging in to Spyzie account. Then head right to the dashboard and then choose WhatsApp.

3: From that point onwards, you'll be in a place to keep tabs on each and each WhatsApp messages which have been sent and received by the goal telephone by logging in to you Spyzie accounts. Please be aware that you'll only have the ability to get into the very first logs or messages after 24 hours when the target device is iPhone. But, there's absolutely no such limitation on android devices .
The fantastic thing about Spyzie is the simple fact that the spied person can't find and neither can they understand that they are being tracked down. Additionally, the fact which you are able to access the control panel some of your own devices such as iOS, MAC, Windows, and Android devices making it the perfect choice to hack on anybody's WhatsApp account.
Part 2: How To Crack an Individu WhatsApp using Mac Address of the Goal Telephone
Inside this technique, we'll require the MAC address of the target telephone, the BusyBox program, in addition to the Root emulator. You can download both the BusyBox along with the Root emulator in the Google Play Store. With these three requirements in hand, we are now able to proceed.
1: Utilizing your smartphone, download, install, and execute the BusyBox program. You'll have to make an account.

2: Require the goal smartphone and get its own MAC address. Write down this address as you will require it.

Suggestion: Please be aware that we should first update the MAC address of the target telephone. To accomplish this, we're likely to utilize the Terminal program.
3: Establish the Terminal Program and kind $ su.
Suggestion: If you have a "device not found" message, then input wlan0 rather than eth0 from the areas provided.
6: Establish your WhatsApp and input the telephone number of the goal WhatsApp account.
7: Before you can completely hack the sufferer's WhatsApp you'll have to validate the hack. In cases like this, select call confirmation.
8: Write down the code that you will get and enter it in the box provided in your smartphone.
It's easy as that. From that stage henceforth, you'll be getting each and every single message that leaves and enters the goal telephone WhatsApp account.
Part 3: Pairing WhatsApp on Android with no accessibility to The Telephone
When it's somewhat complex to hack on WhatsApp messages utilizing the Mac address of the target telephone, we can try out another methodthe. But, I'll reveal to you exactly how easy it's to hack on somebody's else WhatsApp without them understanding. To those people who might want to hack on somebody else WhatsApp without always coming to contact with the target telephone, the FlexiSpy app and also the APK Icon Editor is the final savior. This works just on android mobiles. With this application, you can spoof the goal to get an apk record of this app without them knowing that the document is used to monitor them. This is a thorough procedure of hacking WhatsApp without access to call.
1: Buy the FlexiSpy app and follow the downloading and setup instructions set out in the buy email.
2: once you've installed the application, you'll obtain an activation/installation code. Please be certain that you be aware of the code since you will utilize it at the subsequent stages of the hacking procedure.
3: once you've activated the application, you'll need to await some couple of minutes for the stored information to be uploaded into your FlexiSpy account.
4: After your information has been stored on your account, the next step is to change the default and icon name of this app from â$œSystem Updateâ$ to the following name of your choice.
Suggestion: The motive as to why we're altering the name and icon of this app is in order to spoof the target client to download the app in their cell phone. However wondering how this will be possible? Well; let us keep going.
5: Drag the icon of your choice to space provided as shown below.

6: About the right-hand side of your port, click on the "ApkTool" and choose "Properties".

7: Change the FlexiSpy title to "Earn Money" and tap on the "Package Apk" alternative as shown previously to validate that the change.
8: Using your email address, send this app along with the FlexiSpy activation code you received during registration to the target phone and request them to download the app You have to be certain that you're persuasive enough to make them get into the program. As soon as they fall into your trap and also download the program, you are going to begin tracking them in the FlexiSpy dashboard. It's easy as that.
In the 3 approaches covered above, it's no secret which you could easily hack on anybody WhatsApp accounts with no expertise and keep tabs on the messages as they come and go. The way you select will undoubtedly depend on your tastes, the sort of telephone used in addition to the main reason behind the hack. Although our approaches encourage hacking in 1 way or another, you should keep in mind that the each and every individual is entitled to their own privacy. You must always keep in mind that each and every single time you hack into somebody's else WhatsApp accounts with no approval, simply know that you're breaking their solitude, and this also makes you liable for prosecution if caught in the action. Therefore, play safe and wise. Overall, if you have ideas, opinions, and ideas, please don't hesitate to hit me up and I'll be pleased to combine the conversation.
#android app#whatsapp#hack#hack app#hack android app#hack whatsapp#how to#how to hack#how to hack someones whatsapp chat history
1 note
·
View note