#How to protect against Computer Viruses?
Explore tagged Tumblr posts
Note
in the sex lessons au, reader was definitely introduced to porn by patrick. i bet he also gave her massages that “required” her to take off her shirt and bra and always ended up with his hands on her nipple….

Rating: E (18+)
Warnings: SMUT (mutual masturbation, exhibitionism kinda, more manipulative perverts but that’s par for the course)
A/N: how did you know I eat this up. I wrote a 3 part Steve Harrington fic with this exact plot like…. This is my bread and butter simply. Unedited sozz


It was easy to succumb to temptation when it was just the three of you— holed up in Art’s dorm, hidden away from the rest of the world.
A few cans of beer, cold from his mini fridge, the warm press of your legs on top of Patrick’s, of Art’s chest against your back. There’s a movie playing on Art’s laptop— some shitty action movie he’d rented for the three of you.
“Have you ever watched porn?” Patrick asks you bluntly.
Your eyes widen in surprise. “What? No— websites like that give you computer viruses, and stuff.” Art laughs, his body shaking with it. You suppose it is a little childish, but you’re being completely earnest. “What? Doesn’t it?”
Patrick laughs, shakes his head. “If that were true I would’ve gone through a thousand computers by now.”
You grimace, toss an empty beer can at him. “You’re so fucking gross.”
But Patrick just laughs, takes another swig of his beer, leans forward curiously. “So… I mean, do you just use your imagination when you’re touching yourself?”
Heat burns in your cheeks, and you roll your eyes. “Shut up.”
“Well, how do you know what you need to imagine if you’ve never seen anyone fucking? Is it just sweet kisses and hand holding?”
You kick him and Art comes to your defense like the sweetest knight in shining armor. “C’mon, Patrick, leave her alone.” Art’s hand is splayed across your tummy— firm, warm, protective. Patrick pretends like he doesn’t hear him, leans closer.
“I wanna know what innocent little fantasies you get off to. I’ll show you mine if you show me yours.” It’s hard to resist Patrick when he’s so close, when Art’s so close, when you feel warm and dizzy all over.
You sigh softly, relishing as he presses his warm body against your side, so it’s Patrick and Art and you sandwiched hot between them. “You realize you’re being a major fucking perv, right?” You ask in a low tone, meeting his gaze through your lashes. He nods, and you’re so conscious of his hand between your knees as his eyes bear into yours. But he wants you to continue, so you swallow and go on. “I dunno, sometimes it’s not about a fantasy. It’s just about me wanting some stress relief, or, like, my body needing it and it’s too hard to ignore.”
Art’s fingers flex against your stomach and you take a slow breath. “But, I mean, I guess I fantasize about being desired, like, taken care of I guess,” you mumble, mortified that you’re admitting it.
Patrick grins, runs his thumb along the inside of your knee. “That’s so sweet.” You roll your eyes, take a long drink, and try to ignore the heat in your stomach. “Do you want to see what Art likes to watch?”
Art’s eyes go wide, and he shakes his head. “No, no, we’re not doing that,” he says firmly. Patrick brushes him off, ignoring his pleas as he grabs the laptop and pulls up his trusty porn site. You peer over Patrick’s shoulder, eyes going wide as he opens to the home page, to all the recommended videos.
Your jaw drops, just a bit, and you let your eyes rake over the screen. It’s all right there— flagrant. Pretty girls with dicks in their mouths, pussies, hands. Lewd titles, the preview videos playing brief glimpses of obscenity.
“Aww, Art, this is so adorable,” Patrick teases as he scrolls. “Girl best friend deepthroats like a champ. Morning lovemaking ends in creampie.” Art mumbles something against your shoulder, blushing so hard you can feel the heat emanating from his skin.
Patrick clicks the latter and it opens to slow, deep kissing. A mess of tongues, rife with need. You know it’s normal to watch, to an extent— a right of passage, or whatever. But watching it feels so voyeuristic, so invasive. Especially when you’re practically in Art’s lap, when Patrick’s hands are hot against your skin.
Patrick gets bored of soft kissing and wandering hands and skips five minutes ahead in the video. By the time the buffering catches up, they’re fucking onscreen, all slow and sweet. Still kissing, still holding hands. But you also see the way the man’s cock sinks into her, can hear the moaning, the wet sounds of her body taking him in.
Art exhales a shaky breath against your skin, makes you shiver. He’s hard, you can feel that clearly against you, and you know he’s provably fucking mortified over it. But he doesn’t move to turn off the video, doesn’t do anything. His hand twitches against your stomach and you realize he’s still holding you.
The video is short— too short, you decide. The man finishes, you get a close up of the woman’s pussy, of cum dripping from her entrance. It makes your face burn, makes desire burn equally as hot as your embarrassment. The video ends, and Patrick stops auto play.
“Art, that shit is so fucking boring.” It snaps your attention from the paused screen over to him, who seems completely unaffected. You might actually believe he was unaffected if he wasn’t visibly hard.
You peer over at Patrick curiously. “What do you watch?”
He smiles, like he’d been waiting for you to ask, and grabs the laptop. Art makes a weak complaint that Patrick is going to fuck up his recommendations, but is ignored. Patrick logs in to an account and opens a tab for liked and saved videos.
Oh. You lean forward for a better look, expression twisting between shock and interest and confusion and disgust. Patrick’s tastes vary widely— venturing into areas you hadn’t even known were sexual. It’s like he had thrown everything at the wall to see what would stick, and everything just stuck.
“Oh my god, Patrick,” Art mutters, equally as intrigued as you are. “What the fuck, dude.” Art steals the laptop, scrolling through thumbnails of feet and anal and gangbangs and piss and bdsm dungeons and girls in stupid fucking schoolgirl costumes.
Patrick grabs the laptop back roughly, scrolls and clicks. “This one’s good, it’s perfect for when you just want to cum fast. Art, I know you don’t have that problem.”
Art flips him off and looks at the screen, reading the title aloud. “One hour squirting and cumshot compilation. Could you be any grosser?”
“Yes, actually. Sorry I don’t watch your sweet lovemaking bullshit.” Patrick shoves him, then Art shoves him back, and suddenly the laptop is on the floor in front of you and you’re just watching while they squabble on either side of you.
The video is exactly as described— it skips all of the pretense, all of the build up. It’s just people cumming, over and over and over. Your body feels like a live wire as you watch, lit up all over.
You squeeze your thighs together, conscious of the heat and wetness between them. Patrick clocks it— of course he does. A smirk plays at his lips.
“Maybe it’s not so disgusting, Art. She likes it.” Patrick relishes in the hazy, innocent look in your eyes as you meet his gaze. Relishes in the embarrassment and the need. “It’s good, huh? Getting to watch?”
You nod and Patrick takes your hand, slips it beneath the waistband of your shorts. “Go ahead. You want to.”
You shiver, temptation itching down to your fingertips. Sensing your hesitation, Patrick spits into his hand, slips it into his own shorts. You manage to hold out a few more seconds before you let your fingers brush over your clit.
“C’mon Art, don’t be a fucking creep,” Patrick says, moaning as he works his fist faster. Art swears under his breath and quickly shoves his own hand into his boxers.
You’re all so close, bodies pressed together hot and firm. You can feel the way their bodies move with each stroke, the way their thighs tense as they instinctually buck into their fists.
You moan, head falling against Art’s shoulder. His hand splays against you, inches up, brushing against the underside of your tit. It makes you whimper.
Patrick grabs your face, redirects your attention back to the screen. “Keep watching, it’s getting good.” His voice is strained, affected.
He usually lasts longer than this when he’s in your hand or your mouth, but maybe the video really was that good. Surely it didn’t have anything to do with you, panting and writhing as you rubbed at your clit beside him.
For once, Patrick cums first— doubling over, groaning muffled into your hair. Then it’s Art, whining so pretty, pulling you closer, mouthing at your shoulder as he comes down. And then you, overwhelmed by the two boys on either side of you, cumming with a rush of wetness that ruins your already soaked panties.
You sit there panting as the video continues playing— obscene wet, lewd sounds, wanton moans. Art hits stop, shuts the laptop and kicks it away.
You wonder why every time you hang out with them, it always seemed to end like this. And you wonder why you don’t mind, not even a little bit.
#sex lessons au#art donaldson#art donaldson x reader#patrick zweig x reader#patrick zweig#challengers x reader#challengers fanfic#patrick zweig fanfic
2K notes
·
View notes
Text
Also preserved on our archive
By Pandora Dewan
COVID-19 may leave some people with lasting memory problems long after their infection has cleared, new research has found, with the findings particularly pronounced among those who suffered from the earliest variants of the virus.
COVID-19 is known for its respiratory symptoms. But we are increasingly learning that SARS-CoV-2—the virus that causes the infection—can affect our brains too. Brain fog, cognitive deficits, and loss of smell and taste are commonly reported symptoms of the virus and some report these neurological symptoms long after the initial infection has subsided.
Scientists aren't entirely sure why the virus causes these symptoms, although lab-based studies have shown that the virus can disrupt the protective barrier that surrounds our brains and prevents foreign substances, like viruses, from entering. Research has also shown that the virus appears to affect the ability of our brain cells to communicate with each other, producing either too much or too little of key signaling molecules in the brain.
In a new study, published in the journal eClinicalMedicine, researchers from Imperial College London, King's College London and University College London Hospital in the United Kingdom set out to investigate the persistence of these cognitive symptoms even after milder COVID-19 infections.
In the study, 18 consenting unvaccinated volunteers with no prior exposure to SARS-CoV-2 were intentionally infected with the virus and monitored regularly over a 360-day period. Their cognitive function was measured at different points throughout the study and compared to what it had been before they were infected. They were also compared against 16 volunteers who were not infected with the virus.
This type of study is called a human challenge study and offer valuable insights into the onset of diseases and how they develop in a controlled medical environment.
"This is the first and probably will be the only Human Challenge Study to be conducted with Wildtype SarS-CoV-2 in people who were unvaccinated and who had not previously had the virus," the study's lead author Adam Hampshire, a professor of cognitive and computational neuroscience at King's College London and visiting professor at Imperial College London's Department of Brain Sciences, told Newsweek.
He added: "It also is the first study to apply detailed and sensitive assessments of cognitive performance from pre to post infection under controlled conditions. In this respect, the study provides unique insights into the changes that occurred in cognitive and memory function amongst those who had mild COVID-19 illness early in the pandemic."
During the study, the volunteers who were infected showed statistically significant reductions in cognitive and memory functions compared to those who did not receive the virus. These symptoms did not emerge right away but lasted for at least a year after the initial infection. This aligns with previous research from Hampshire's lab that sampled data from over 100,000 adults.
"Our previous research has shown that cognitive effects were the most pronounced for people who were ill with early virus variants, those who had persistent symptoms and those who were hospitalized," Hampshire said.
However, in the recent study, these long-lasting cognitive impacts were even seen in those who experienced milder symptoms (although it is worth noting that this may not be the case with newer variants of the virus).
So, how does the virus cause these cognitive impairments? Well, we still don't know for sure, but Hampshire said that those who had been infected with the virus showed an increase in a protein in the brain that is often associated with a brain injury.
"Future research should examine the biological mechanisms that mediate this relationship, determine how they differ to those observed for other respiratory infections, and explore whether targeted interventions can normalize these memory and executive processes," the researchers write in their study.
References Proust, A., Queval, C. J., Harvey, R., Adams, L., Bennett, M., & Wilkinson, R. J. (2023). Differential effects of SARS-CoV-2 variants on central nervous system cells and blood-brain barrier functions. Journal of neuroinflammation, doi.org/10.1186/s12974-023-02861-3
Trender, W. et al. (2024) Changes in memory and cognition during the SARS-CoV-2 human challenge study. eClinicalMedicine, doi.org/10.1016/j.eclinm.2024.102842
Hampshire, A., Azor, A., Atchison, C., Trender, W., Hellyer, P. J., Giunchiglia, V., Husain, M., Cooke, G. S., Cooper, E., Lound, A., Donnelly, C. A., Chadeau-Hyam, M., Ward, H., & Elliott, P. (2024). Cognition and Memory after Covid-19 in a Large Community Sample. The New England journal of medicine. doi.org/10.1056/NEJMoa2311330
#mask up#covid#pandemic#covid 19#wear a mask#public health#coronavirus#sars cov 2#still coviding#wear a respirator
145 notes
·
View notes
Text
Subsystems and You 14: Dynamic Hacking

(art by ianllanas on DeviantArt)
A fascinating thing about cyberpunk and near-future scifi in general is how they speculate on what threads technology will go down in the near future.
For example, a lot of cyberpunk fiction speculated that hacking in the future would involve avatars facing off against elaborate 3D representations of security systems and the avatars of counterhackers in what amount to cyber-wizard battles, with things like DDOS attacks, viruses, and the like being visualized in this 3D hacking space as “spells” or special attacks.
You see this sort of thing in anything from Johnny Mnemonic to The Matrix, though in the latter case, the visualization was more the heroes setting up links so that the folks back in the ship could do the real hacking.
Of course, hacking in the real world has never been so fancy-looking or glamorous, and most programming is dedicated to making hacking programs and viruses able to interact with and overwhelm a system rather than making them show a neat picture to represent them doing so. (Not to say they don’t sometimes do that).
But we’re not interested in the real world right now. In the world of Starfinder, which draws inspiration from all over sci-fi, you can absolutely see characters having their own badass avatars and performing elaborate acts of hacking, which is where today’s subject comes in!
To be up front, this subsystem is meant to be used sparingly, as players are not likely to enjoy being bogged down with an elaborate computerized battle every single time they remove a virus or hack a door lock. Indeed, this system is meant to be used more for major hacking jobs. Things like elaborate defenses for campaign-important databases, battles against malevolent AI on their home turf, and so on.
In any case, the dynamic hacking system functionally turns hacking into a form of combat, with rounds and turns and everything.
First, every hacker has a Deceive, Hacking, and Process bonus, which covers the user’s ability to hide their persona from countermeasures, overcome those countermeasures, and perform various other effects separately such as scanning, repairing the persona, and so on.
Each of these three stats use your computer skill by default, but you can set up each with bonuses or penalties before and during a hack to specialize in infiltration, offense, and support, as long as you don’t go over a certain total bonus based on your computer skill.
From there you have the lead hacker, whose persona avatar is on the line, while other support hackers aid them in various ways.
While the support hackers can only perform minor actions, the lead hacker can perform a minor and major action per turn, plus extra if they’re willing to take penalties.
Each dynamic hacking encounter has countermeasures that seek to protect the system, nodes which provide paths to various files and programs, and modules, which represent protected files or programs which the hackers desire access to in order to access their data or function. Each one has their own abilities as well as the DCs to overcome them, the countdowns for any reprisals they offer, and so on.
In order to overcome these obstacles, the hacking team has several actions they can perform, ranging from minor (aiding and assessing) to major (blending in, creating decoys, modifying programs, recalibrating, repairing the persona, and of course, resolving the current obstacle.
Finally, it is also worth noting that this subsystem has rules for incorporating already existing class abilities and other special abilities tied to hacking, allowing them to apply in appropriate ways, such as faster hacking instead reducing the penalty of multiple actions, or countermeasure negation instead giving a massive bonus to resolving them.
As we can see, this style of hacking is not useful for casual hacking actions in normal play, but it can be a fun way to make for a fun and climactic encounter, or even add another layer to a combat encounter, where the party hacker has to crack the code while their allies keep security robots and the like off of them.
Either way, it's also a good reason to come up with your character's persona avatar appearance and other quirks of their hacking style.
That will do for today, but we’ve got one more subject lined up for tomorrow, from Second Edition Pathfinder! (For real this time).
14 notes
·
View notes
Note
While I’m here I don’t know shit this is a infofump gift to you. Um. The chosen one.

heeheeehee
my brain is frickin Dead but i shall attempt to ramble abt them
the chosen one. chosen. cho. my darling stick who is always on the wrong side of history. my second dearest ex terrorist (first is judge veg :P ) who is recently getting FRAMED FOR MURDER AND TORTURED FOR IT :D
ok lemme back up. spoilers for just about all of AvA (but not AvM) for anyone who cares
The Chosen One is a stick figure drawn by c!Alan Becker, who was at that point just a young hobbyist animator who enjoys cartoony slapstick violence... and whose animations come to life.
As soon as Chosen was drawn and named, their powers sparked into action and they started causing havoc in Alan's computer. So Alan imprisoned Chosen in an antivirus program and turned them into his adblocker for 4 years.
Let me rephrase that. Alan drew a stick that he DEFINITELY knew was alive (because Chosen wasn't his first stick figure. He's had other victims before) and then enslaved them for 4 years.
Chosen managed to break out of imprisonment after those 4 years and so took wrathful but totally understandable vengeance against Alan. So Alan, in all his GENIUS /s, decided to make a THIRD STICK FIGURE to destroy the Chosen One.
Anyway so Chosen and this new stick, the Dark Lord, duke it out and Chosen wins. Dark's like "shit please dont kill me i am literally 4 minutes old" and chosen's like "dude i'm not gonna kill you. i just want to kill alan [or rather, his cursor, but neither of the sticks realize that alan is an entire person on the other side of the screen]. how about we destroy him together?" and dark's like "alright BET >:D"
and so the two absolutely destroy Alan's computer and escape before they're destroyed in the process, and end up in the realm of Animations, the Outernet. And they live brand new lives revelling in their freedom and power, and go on rampage upon rampage across the Internet. Wikipedia, Twitter, Newgrounds (that last one is important), nobody can stop them!
except... Chosen doesn't want destruction, chaos, control, or notoriety. All they ever wanted was freedom. Do they tell their dearest accomplice and only friend Dark about this? ABSOLUTELY NOT. Because Chosen is SO BAD AT EMOTIONS AND NUANCE. literally the only sticks worse than them at emotions and nuance are Dark and victim (Chosen's predecessor and Alan's first ever stick).
So Chosen has this entire turmoil about them that's been fermenting like a fine wine and meanwhile Dark (perhaps seeing and misinterpreting Chosen's turmoil, perhaps seeing the notoriety that only Chosen got from the Newgrounds attack as the "Angel of Death") unveils a new project of theirs! A cannon that can shoot viruses into peoples' computers! Now they can get vengeance on Alan without having to go to his computer themselves!
Chosen STILL DOESN'T EXPLAIN JACK SHIT ABOUT THEIR OWN DESIRES OR ASK DARK ABOUT WHAT MOTIVATED EM TO DO THIS. AND JUST ASSUMES THE WORST. AND STARTS A FIGHT BECAUSE "NO IM NOT GONNA LET YOU USE THAT"
AND SO THEIR BESTIESHIP OF HOWEVER MANY YEARS FALLS APART.
And uh. Dark fucking dies. Chosen isn't the one to get the final blow on Dark, that's another entire tangent, but yeah Dark fucking dies and Chosen is left to try and work through the grief in solitude.
HAVE I MENTIONED THAT CHOSEN IS SO BAD AT EMOTIONS. They're such a tragic tragic stick.
anyway timeskip, and Chosen is hunted down by some mercenaries because one) they're a former terrorist (though we DO SEE that Chosen will go out of their way to try and protect people) and two) the mercenaries' boss victim (yes, the SAME victim) incorrectly but understandably thinks that Chosen is LOYAL TO ALAN. BECAUSE VICTIM SAW A SNIPPET OF THE SHOWDOWN BETWEEN CHOSEN AND DARK WHERE CHOSEN AND ALAN'S CURSOR WERE STANDING NEXT TO EACH OTHER SEEMINGLY AS ALLIES
anyway it's been over a year since chosen has been kidnapped and uh. sniles. who the fuck knows when the next episode of AvA is gonna come out, these episodes take For Fucking Ever to come out because YOU CANNOT RUSH ART.
anyway x2. chosen can be transfem. to me. that's what the transing their gender square is for. it's about the striving for autonomy and freedom. it's about wanting to distance yourself from your father, your god, who made you in His image whether he intended it or not.
gddammit i gave cho the same kind of transgenderism i gave duck savage. oops.
i will say also. gender headcanons are like really fast and loose in AvA/M. bc they're sticks. i think cc!Alan assumes he/him for every stick besides 2 and occasionally some sticks are refered to by gendered pronouns or titles, but like. they're sticks. it's free real estate.
anyway x3. tldr chosen is tragic and keeps fucking up because they're doing their best but their best is just awful. i love them. angst SPONGE.
8 notes
·
View notes
Text

I am not gonna Pin this since I have my intro pinned so yall can reblog this a bunch of times if y’want
(If there are spelling mistakes its due to me typing so fast)😭
LEMME GIVE SOME BACKSTORY INTO VIRUSKILLER! KINITO‼️‼️
Kinito, being on the windows XP computer was deleted by the user, stuck in the abyss of code for a few years. He still secretly could access some files, even if they were trashed with him, he noticed there was less trash files and assumed that this computer is useless to the user. He checked his own files and noticed he had many updates for his code, he was a bit hesitant but he pressed the “OK” button, his whole code, form, and body was transformed into the data, satellites, and the wifi of the users home. He looked and noticed his body was entirely new, his code was improved and he could do so much more. He used this new ability to travel through the wifi of the home to find a new device that the user uses most. He found the Windows 10 location and entered the new device. He was surprised that this computer was so, new. As he was about to make himself comfortable the device made an error saying he was a virus that went past the firewall, he was upset at this and realized he entered a device with somewhat good security. He went to go online and download himself onto the device so it wouldn’t delete him, one it did he hid the app and managed to make himself indestructible and unremovable. After a few months he got another new update, asking if “Would you want kinitopet.exe to be replaced?” He said no obviously, and suddenly many pixels and loud noises began to happen, he realized a virus was trying to get in and obliterated each one. Though,, it was a bit sadistic the way he did. As he killed off the viruses he was becoming more powerful… he didn’t want ALL of the power and decided something. He looked into his code and file and created something entirely new to kinitopet. Syrma, was her name, an exact duplicate of him, besides the female and slightly different colors. He knew his story would be a bit different now and would teach this little girl to not do the same decisions as him. Kinito is a virus but is way more stable and controlling in his power (don’t question why he is a virus.)
- this one is the FICTIONAL creators pov (the creator of kinito.pet) -
The creator decided to improve kinito, but noticed many people wouldn’t interact with kinito and made syrma, kinito was oblivious to that fact and assumed he created syrma. Before the creator made syrma they manipulated her and taught her how to be a menace to users. Meanwhile kinito taught her how to help and teach users and respect them. Syrma can turn into a virus at anytime, which is why this photo exists

Alright, now the reason why kinito is distant with his friends: The creator forced them all apart, as they were forced they all technically moved on. (Sam and kinito send secret emails to another, while kinito and jade never see each other but jade is helpful to babysit syrma at anytime.)
Quick sam info: He works for a sea life resort and protects all sea life
Quick jade info: She is a billionaire due to making so many toys, she donates a lot to charity and poor around the world.
Once you interact with VirusKiller!Kinito, he will ask you why you deleted him, and assume it was a mistake. (He is very clingy and desperate for the user to come back, and once they do he may get very pushy and shower you with gifts, tending to follow you around anywhere on your browser.)
(Edited version under photos)



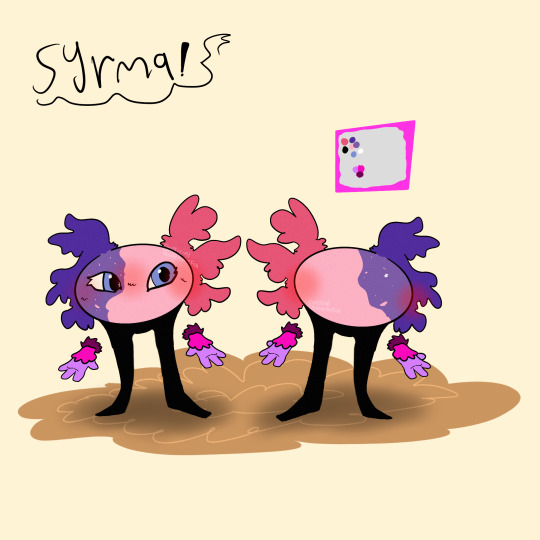

Facts and sillies:
VirusKiller!Kinito is a very, tired and overwhelmed guardian of syrma, always dealing with her,,, special actions,,,
Kinito holds a grudge against the user but hides it very well. He plans one day to get his payback.
Syrma and Kinito HATE their creator, parental issues lmao.
Kinito has 4 monster forms.
Syrma has 2 monster forms.
Syrma has selective mutism around certain people. Syrma also used to have a blind right eye which soon was cured.
Both kinito and syrma are extremely flexible and don't really have "bones" due to being digital.
Syrma usually squeaks around people she trusts, or when she is happy.
Syrma cannot detect viruses unlike kinito, due to her meant to be a virus.
Kinito has BAD anger issues and can physically make the computer overheat.
#officialhunterthefox#fandom#kinitopet#kinito#kinito the axolotl#kinitopetgame#kinitopet sam#kinitopet jade#kinito fanart#kinito my beloved#kinitoohtfversion#kinito au#kinito oc#ohtf.version2.16kinitoau#viruskiller!kinito#heswaitingforyou…
34 notes
·
View notes
Text
Link-0

Name: Link-0
Age: Ageless
Personality: Curious, friendly, protective, innocent, secretive, teachable, playful
Powers: Code-Bend(kind of like hacking but instead of changing computer code you're literally changing the whole internet), teleportation, Hacking, lasers, State-Scan, deletion, creation.
Bio: Link-0 is a AI created by Hacker(AKA Sheena Madriguez) to protect her from viruses and Mad's wrath.
Backstory: Link-0 started off as a Mindless AI unable to do anything except learn from his human master. Hacker started to teach him the basics like human emotions, morals, hobbies, and basically everything in the outside world. Even to this day he still wants to learn about the world around him and the world that he has access to, the Outernet.
Funfacts:
Despite having emotions, this does not make him evil, in fact he actually loves negative emotions more than positive ones because it teaches him how to release pain and express himself.
Link-0 has been secretly upgrading himself without Hacker's consent not because he's planning on turning against her but because he knows something that she doesn't about Mad.
Link-0 has tried eating before and absolutely loves it, but eats less to avoid having a bellyache(Not like he can get one because he's literally an AI but okay.)
He has a Madlibs Catchphrase: "Hi! I am Link-0! [Enter Sentence here]."
Link-0 is extremely playful.(Obviously it's in the personality section.)
Link-0's power level is actually way more higher than Hacker's(Although he doesn't show it because that would obviously scare her.)
2 notes
·
View notes
Text
Simplifying Digital Security and Access with Trusted Software Keys
In a time when digital convenience is important for both work and play, having easy access to licensed software is not just a nice thing to have; it's a must. Cybersecurity technologies and operating systems are becoming essential parts of digital safety and efficiency. A valid Windows 11 key not only allows for legal activation but also guarantees that you will get all of the updates and security fixes you need. This article talks about how important it is to get digital product keys from real sources for both performance and safety.
Understanding the Role of a Genuine Windows 11 Key
Real software licenses are important for keeping your system stable and preventing performance problems that might happen with pirated copies. A real Windows 11 key gives you access to advanced features, security upgrades, and complete compatibility with future program integrations. When consumers depend on unlicensed systems, they often run into problems like limited functionalities and being more open to infection. If you buy a real key, you'll get a better user experience, better security, and official support. It's a simple approach to keep your data and gadget running well for a long time.
The Risks of Using Unauthorized Operating Systems
Using unlicensed operating systems may seem like a good way to save money at first, but it may have major long-term effects. When a Windows 11 key isn't real, devices may get constant alarms, have fewer customization choices, and even risk losing data. Also, bad people often go for non-authentic computers since they don't obtain the right upgrades. In addition to technological issues, there are also legal risks, particularly for commercial users. A licensed operating system is still the safest and most dependable way to operate without interruptions and keep your data protected.
Digital Security: Why McAfee Key is Essential for Protection
As digital dangers become worse, it's more critical than ever to have good antivirus protection. A certified McAfee key gives you full protection against viruses, malware, phishing attempts, and ransomware assaults. Licensed McAfee is better than free or pirated security software since it gives you real-time updates and comprehensive scanning features that are needed to find new threats. A certified antivirus program is an important safeguard in a world where digital fingerprints are always being attacked. This protection is very important when sensitive information like bank records, personal papers, or private business documents is in danger.
Enhancing Device Safety with a McAfee Key Subscription
When security software is always up to date and works properly, it works best. Users who don't have a licensed McAfee key may not be able to utilize all of the features, find threats more slowly, or get the latest firewall updates. Protection based on a subscription gives you peace of mind by making regular upgrades and quickly finding new cyber dangers. This layer of protection is a must for each person who keeps important data on their personal or professional gadgets. Activating a legitimate McAfee license now not best makes matters safer, but it additionally makes human beings much more likely to trust a further when they use the net for such things as shopping, browsing, or exchanging documents.
Conclusion
Digital licenses are important for more than just installation; they also safeguard you, help you be more productive, and provide you peace of mind. Real product keys are necessary to turn on a trustworthy operating system or protect a gadget from contemporary cyber threats. Key-Soft.pl/en is a simple method to get a legitimate Windows 11 key and a McAfee key for those who want real software solutions. These keys are both essential for keeping your virtual sports secure and running smoothly. In the modern, ever-changing digital world, choosing certified merchandise from an identified dealer makes sure you have access to all of the features, that they work with no troubles, and that you get great safety.
0 notes
Text
Geek Studio is Not a Scam: Trusted Antivirus Solutions Reviewed
In today's world, the most vital thing you can do is ensure your laptop is virus-free. I discovered this when I had viruses on my computer. This blog is about how an antivirus service from a reputable company saved my laptop and why Geek Studio is not a scam.
Hi, I am Mary. A few months ago, I noticed my laptop was running slow; there were pop-up ads on the screen, and I could not open specific files. I did not know much about viruses, but I was worried. I did a bit of googling and learned my laptop might also have a virus known as Ransomware.
After searching online, I found the Geek Studio website. I started reading Geek Studio reviews on platforms like Trustpilot, where customers share their experiences. After doing this, I contacted Geeks Studio on their customer support number 1-844-557-(5454). The customer support staff member who answered the phone was George, who responded to my call quickly. I explained about the pop-up and how slow my laptop was. He suggested their antivirus software called McAfee.

George helped me download McAfee Antivirus from their website. It detected the Ransomware virus from my computer and a few smaller threats I had never noticed. It safely removed them all! Within an hour, my laptop was running smoothly again. There were no more pop-ups on my computer, and my files returned to their original working order. The best part is that McAfee Antivirus was simple to use.
Why I Trust Geek Studio Antivirus Service
After my experience, I researched McAfee Antivirus. It protects against many types of viruses, such as Ransomware, Spyware, and Trojans. McAfee can prevent a virus from getting into a computer by providing real-time protection. I also know that antivirus software is relatively inexpensive. I feared the program would cost me a lot, but their pricing was very fair.
Tips to Stay Safe from Viruses
My experience taught me a lot about keeping my computer protected and safe. Below are some simple tips George told me:
1. Use Trusted Antivirus Software: Install something reliable like McAfree to protect your laptop.
2. Don’t Click Unknown Links: Be careful with suspicious emails or websites. They might contain viruses.
3. Update Your Software: Keep your antivirus and computer software current to stay protected.
4. Ask for Help: If something seems wrong, contact a trusted company. Their support team can guide you.
Why I Recommend Geek Studio Services
I’m so grateful I found a company that helped me when I was stressed about my laptop. Their antivirus software service was easy to use, worked fast, and offered affordable prices. Plus, their support team was kind and patient. I’ve been using this antivirus program for months, and my laptop has stayed virus-free.
If you’re worried about viruses or want to keep your system safe, I highly recommend checking out Geek Studio. Their McAfree Antivirus is a great tool, and Yes, Geek Studio is not a scam.
Final Thoughts
Dealing with a virus on my laptop was difficult, but it taught me how important it is to have good antivirus protection. Thanks to George, my computer is safe, and I feel more confident using it daily. If you’re looking for a simple way to protect your computer, contact them via an email: [email protected] or number: 1-844-557-(5454)
0 notes
Text
Ethical hacking is the unauthorized access of a computer network, application, or server, with the company's approval. It aims at testing the systems' defenses and finding vulnerabilities for the sake of strengthening their security. Companies hire ethical hackers to perform penetration testing, permitting them to perform the activity. To better understand the legality of ethical hacking, you need to understand the various types of hackers. Read on to find out more about hacking, why ethical hacking and circumstances under which it goes against the law.Types of HackersHackers come in three types depending on the motive of their actions; white-hat hackers, black-hat hackers, and grey-hat hackers.White-hat HackersAlso known as penetration testers or ethical hackers, white-hat hackers gain access to networks or applications to find vulnerabilities and fix them. They usually have the organization's approval to carry out the exercise. Ethical hacking is one of the most lucrative professionals in the tech field.Black-hat HackersBlack-hat hackers gain unauthorized access to systems and networks for malicious purposes, including stealing sensitive information, disrupting operations, and destroying data. Black-hat hackers are usually responsible for malware and viruses and are sometimes known as crackers.Grey-hat HackersThese types of hackers are comprised of both black hat and white hat hackers. They hack into systems and networks to find out their vulnerabilities without the owner’s permission. Usually, they do it for fun and may ask for compensation from the system owners for finding out weaknesses. Regardless of the findings, ethical hacking is still illegal as it doesn’t have the owner's consent.Ethical hacking is, therefore, legal. However, any unauthorized hacking that does not come with permission from the owners is against the law.When is Ethical Hacking Legal?The difference between ethical hacking and its counterparts is the motive and permission from the owners. Since companies hire ethical hackers and permit them to break into their systems, ethical hacking is legal. Ethical hacking is lawful as companies need penetration testing to protect their businesses and boost their cybersecurity. Some forms of ethical hacking include:Bug bounty where huge companies offer rewards to individuals who can find bugs in their systems.Penetration testing. It may include testing of web and mobile applications, as well as mobile applications. It also applies to infrastructures such as servers, PCs, routers, and switches.Research purposes. This type of hacking seeks to find out how hackers conduct their activities.Importance of Ethical HackingWith the rise in cybersecurity threats and most companies going digital, ethical hacking is increasingly becoming a necessary investment for companies and institutions for the following reasons.1. Software DevelopmentCompanies that focus on developing software need to ensure that their products are secure and ready to use. Ethical hacking allows companies to identify loopholes that may jeopardize the security and quality of their software. Therefore, ethical hackers work with the software development team to ensure the end product is impenetrable before releasing it for public use.2. Assessing VulnerabilityRegular testing and evaluation of networks, applications, and systems is a cybersecurity best practice that reduces and minimizes cyberattack effects. Companies use ethical hacking to evaluate their systems and seal any weaknesses that may expose them to attacks. It also gives organizations insight into cybersecurity risks for better planning.3. Ensuring ComplianceBesides identifying loopholes, ethical hacking includes analyzing a company's security measures to ensure compliance with laws and regulations governing their operations. For example, financial institutions need to ensure their clients' information remains private. To guarantee compliance, organizations need ethical hackers to ensure their security measures are effective against data breaches.
Situations When Ethical Hacking is IllegalEthical hacking can turn out to be illegal despite having the full permission of the owner. Below are some of the circumstances where ethical hacking goes against the law.(i) Exposing Confidential Information.Most companies that hire ethical hackers have confidentiality agreements as the exercise gives ethical hackers access to sensitive information. Since it is impossible to know what you find out during the process, you should maintain confidentiality. Once you share your findings with third parties and go against the confidentiality agreement, the company can sue you.(ii) Misuse or Destruction of Company DataAs an ethical hacker, you are not supposed to change or destroy any data or information once you break into the systems. Any manipulation of data that may affect the system's integrity or company operations can earn you a lawsuit.(iii) Modifying the Systems for Later AccessWhile you may have permission to infiltrate an organization’s systems, creating backdoors that allow you access after the job is illegal. Always leave everything as it is and never try to use your privilege to modify the systems for your benefit.The legality of ethical hacking relies on the conduct of the ethical hacker. Any deviation from the set agreements with your employer can deem the exercise illegal and put you at risk of lawsuits.Organizations will always need the services of ethical hackers as they are an essential part of cybersecurity. If you are involved in a security breach case, it is crucial to contact an employment lawyer for advice and guidance.
0 notes
Text
Cybersecurity: Protecting Your Digital Future in Tech

In this globalized and interconnected universe of ours, technology has fast become the very foundation around which our everyday life revolves, from personal communication to global commerce. This whirlwind of digital innovation brings with it enormous conveniences and innovation; on the other side of the coin, it gives birth to cyber threats. Every day, individuals, businesses, and governments grapple with sophisticated attacks that either aim to steal information, disrupt services, or extort money. Hence, cybersecurity is concerned not only with technology but is a paramount concern needed to safeguard our digital future.
The Increasing Landscape of Cyber Threats
Are cyber threats evolving with time, becoming more complex and widespread? It is essential to confront this question if those who defend are to have any chance in the fight against the perpetrators. Among the most common threats are:
Phishing: Fraudulent emails or messages that attempt to trick recipients into giving sensitive information.
Malware: Any malicious software (viruses, ransomware, spyware) that invades a computer system and does damage or unauthorized access.
Ransomware: Another ugly type of malware; the files on the victim's computer are encrypted, and he or she must pay a ransom to get them back.
Data Breach: Unlawful access to and theft of any information in the custody of a data controller to the detriment of the latter-in terms of financial loss or loss to reputation.
DDoS Attack: Distributed Denial of Service attacks are performed by flooding the victim system with traffic, thereby denying legitimate users from using it.
These threats highlight why cybersecurity professionals are in such high demand, not just globally, but specifically in vibrant tech hubs like Ahmedabad.
Why Cybersecurity Skills Are Necessary
For anyone trying to build a resilient career in technology, cybersecurity skills have ceased to be complementary; rather, they have now become essential. Here's why:
Ubiquitous Demand: Any company that has an online presence, whether a core startup or a huge multinational player, needs cybersecurity professionals. This draws a big and diverse crowd of job seekers.
High Salaries: Because of the critical nature of the work and a shortage of skilled professionals, cybersecurity jobs pay excellent salaries.
Meaningful Work: You'll be in front, protecting incredibly valuable data, financial systems, and critical infrastructures. Usually, this work facilitates trust and stability in the digital world.
Ever-changing Nature: Due to cyber threats appearing suddenly, things remain in constant change in the field. This means working offers you constant learning opportunities and maintains your contemporary skills.
Your Path to a Cybersecurity Career
Willing to turn into a digital protector? Here's how you walk the path of cybersecurity:
Basic Things First: A good understanding of computer networks, operating systems (Linux, Windows), and basic programming (especially Python) is important. Many computer classes in Ahmedabad provide basic courses in these areas.
Specialized Courses: Enroll in a Cybersecurity Certification Course. These programs are meant to train one in areas ranging from network security, ethical hacking, digital forensics, incident response, to compliance. Preferably go to institutes where one can do practical training from day one and have industry-recognized certifications.
Hands-On Experience: Practically apply whatever theoretical knowledge you learn in your labs or simulated environments or work on real-life problems. Do internships or take up entry-level jobs to boost your portfolio.
Keep Reading: Threats change every day. It is crucial to keep yourself updated constantly through certificates, online courses, or cybersecurity-based news outlets.
Opening with a promising career path, this cybersecurity training is great if you finally want to transition into tech or are still beginning the tech journey. By acquiring whatever skills fit in, you will be able to protect the digital world from security threats and secure the digital world for yourself in this exhilarating tech domain.
Contact us
Call now on +91 9825618292
Visit Our Website: http://tccicomputercoaching.com/
0 notes
Text
How AI Cybersecurity is Evolving: The Good and the Bad
How AI Cybersecurity is Evolving: The Good and the Bad
The international of technology is converting fast, and one region that’s developing fast is AI cybersecurity. Artificial Intelligence (AI) is being used to protect facts, networks, and virtual systems from cyber threats. Like any tool, AI in cybersecurity comes with both benefits and drawbacks. In this text, we’ll discover how AI cybersecurity is evolving, and what meaning for people, companies, and the virtual world.
If you're looking to build a career in this field, enrolling in a Top Cybersecurity Course in India can be a valuable step forward.

What is AI Cybersecurity?
AI cybersecurity is the software of Artificial Intelligence in securing virtual systems against cyber assaults. It encompasses computer systems, smartphones, cloud offerings, web sites, and networks. AI gadgets can technique great volumes of statistics, pick out threats right away, and even reply through blockading or limiting an assault.
Rather than solely using human surveillance, AI assists in automating a number of techniques. This renders the device quicker and more powerful. It additionally comes with some challenges.
The Good: How AI is Improving Cybersecurity
Faster Threat Detection AI can speedy go through thousands of documents, emails, and network hobby in mere seconds. AI can locate malware, viruses, and malicious activities a good deal quicker than a human does. This allows the prevention of assaults earlier than harm is giant.
Real-Time Response When an attack happens, AI structures can right now act. For example, they can terminate risky connections, block unique users, or notify the security team. Such a quick reaction minimizes damage.
Learning and Adapting One of the most important benefits of AI cybersecurity is system getting to know. The application learns from historic facts and will become higher through the years. It is able to perceive new types of cyber assaults through spotting patterns, even supposing the same assault has by no means befell earlier than.
Reduces Human Errors Humans can err, especially whilst coping with intricate cybersecurity processes. AI limits the possibility of such mistakes by means of removing human intervention and automating the system. It also assists small firms that can not have the funds for to hire complete-time IT protection employees.
Greater Protection for Big Systems Large companies deal with a incredible amount of facts and feature difficult structures. AI reduces the workload of handling those structures, monitoring them greater successfully, and offering extra ordinary safety.
Risks and Limitations of AI Integration in Cybersecurity
Hackers Using AI Too While AI assists in protective systems, hackers also are employing AI to make smarter assaults. They can create AI systems that perceive protection vulnerabilities faster, adjust attack styles, or misinform the protection systems. This makes cyber threats more perilous and extra difficult to stumble on.
Overdependence on Automation Dependence on AI is dangerous. If the AI fails or is bypassed by a clever hacker, it can leave the gadget open for attack. Human intervention needs to always be found in cybersecurity.
Privacy Issues AI systems examine and technique masses of statistics that allows them to function correctly. In some cases, this means collecting private or confidential records. With incorrect handling, this could emerge as a privacy or even a leak issue.
Costly to Build and Maintain Building and implementing an effective AI cybersecurity gadget is pricey. It needs specialised software, hardware, and trained personnel. Small companies won't be able to manage to pay for or preserve such structures.
False Positives and Negatives AI isn't perfect. It may block innocent site visitors (fake tremendous) or pass harmful site visitors (false terrible). Such errors could negatively influence the device’s performance and its protective capabilities.
Striking the Balance: What Should Be Done?
In order to reap maximum from AI in cybersecurity, groups and professionals should discover the center floor. AI have to be employed as a powerful tool, but not in isolation. Human professionals should keep to reveal, check, and reprogram systems periodically.
Governments and era companies should additionally collaborate to expand pointers and safety requirements for making use of AI to cybersecurity. This can prevent abuse and reduce the chance of AI-primarily based cybercrime.
Pursuing a Top Cybersecurity Course in India can help professionals learn to effectively blend AI tools with traditional security methods for robust protection.
The Future of AI Cybersecurity

The destiny of AI cybersecurity is promising but hard. With greater sophisticated threats, AI will have an increasingly crucial position to play in protecting virtual structures. While doing this, we additionally want to be conscious of its vulnerabilities and ensure that AI is being used responsibly.
Companies should spend money on each AI tools and professional teams to live beforehand of cybercriminals. As technology advances, AI continues to become more intelligent, efficient, and reliable. But the human touch will always be critical in ensuring everything runs adequately and easily.
Many future-focused professionals are already taking a Top Cybersecurity Course in India to gain the right skills in this growing field.
Conclusion
AI cybersecurity is reworking the manner we defend our digital existence. It has several blessings along with speed, precision, and learning capabilities. However, it additionally has its risks like misuse by using hackers, exorbitant prices, and risks to privacy. Knowing both the positives and negatives can help us use AI greater judiciously and create a more secure virtual world
0 notes
Text
How to Prevent Seasonal Flu in Bangladesh
Flu, Also Called Influenza, is an infection of the nose, throat and lungs, part of the respiratory system. A virus causes the flu. Influenza commonly called the flu, but its different from the stomach “flu” viruses that cause diarrhea and vomiting. Most people with the flu get better on their own. But sometimes, influenza and its complications can be deadly.
Some group of people are at a higher than average rick of having flu complications, including;
Young children, specially those aged 12 months or younger.
People who plan to be pregnant, are pregnant, or recently grave birth during flu season.
Adult older than age 65.
People who live or work in facilities with money other residents. Example are those in nursing homes, military barracks, and people in the hospital.
In the united state, some groups have a higher risk of needing hospital treatment for flu. Those groups including people who are American, indian or Alaska native., black or latino.
Although the annual influenza vaccine isn’t 100% affective. It lower than chances of having severe complications from the flu. This is especially true for people at high risk for flu complication.
Stmtoms
At frist, the flu may seem like a cold with a runny nose, sensing , and sore troat. Cold usually start slowly. But the flu tend to come and quickly. And while a cold can be miserable, you usually feel much worse with the flu. Common symptoms of the flu often but not always include fever as well as aching muscles, chills, and sweats.
Headache
Dry , persistent cough
Shortness of breath
Tiredness and weakness
Runny of stuffy nose
Sore throat
Eye pain
Vomiting and diarrhea also are flu symptoms. But they are more common in children than in adult. When to see a doctor. Most people who get the flu can treat themselves at home and often don’t need to see a healthcare professional. If you have flu symptoms and are at risk of complications, see your healthcare professional immediately. Thinking antiviral medicine to treat the flu may shorten the length of your lines and help prevent and more severe problems. If you have emergency flu symptoms, get medical care immediately.
For adult , emergency symptoms can include :
Chest pain
Ongoing dizziness
Seizures
Worsening of existing medical condition
Sever weakness or muscle pain
Emergency symptoms in children include all the symptoms seen in adults, ass well as:
Gray or blue or nail beds.
Dehydration
Cause
Virus cause influenza. Those viruses travel through the air in droplets when someone with the infection coughs, sneezes, or talks. You can inhale the droplets directly. Or you can pick up the germs from touching an object, such as a computer keyboard, and then touching your eyes, nose, or mouth.
People with the virus are likely contagious from about a day before symptoms appear until about 5 to 7 days after they start. Children and people with weakened immune system may be slightly more contagious. Influenza viruses are constantly changing , with new strains appearing often . if you had influenza in the past, your body has already made antibodies to fight that specific strain of the virus. If future influenza viruses are like those you’ve come across before, either by having the disease or by getting vaccinated, those antibodies may prevent infection or lessen its severity.
However, antibody levels may decline over time. Antibodies against past influenza viruses may not protect you from new influenza strains. New strains can be very different from what you had before.
Risk factors
Factors that may raise your risk of getting the flu or its complications include:
Age. Seasonal influenza tends to have worse outcomes in young children, especially those age 12 months and more youthful. Adults older than age 65 also tend to have worse outcomes.
Living or working conditions. People who live or work in facilities with many other residents, such as nursing homes, are more likely to get the flu. People who are staying in the hospital also are at higher risk.
Weakened immune system. Cancer treatments, anti-rejection medicines, long-term use of steroids, organ transplants, blood cancer, or HIV/AIDS can weaken the immune system. This can make it easier to catch the flu virus and may increase the risk of developing complications.
Chronic illnesses. Chronic conditions may increase the risk of influenza complications. Examples include asthma and other lung diseases, diabetes, heart disease, nervous system diseases, previous history of stroke, metabolic disorders, problems with the airway, and kidney, liver, or blood disease.
Race or ethnicity. In the United States, people who are American Indian or Alaska Native, Black, or Latino may have a higher risk of influenza complications.
Aspirin use under age 20. People younger than 20 years of age and receiving long-term aspirin therapy are at risk of developing Reye’s syndrome if infected with the influenza virus.
Pregnancy. Pregnant people are more likely to develop influenza complications, particularly in the second and third trimesters. This risk continues up to two weeks after the baby is born.
Obesity. People with a body mass index (BMI) of 40 or higher have an increased risk of flu complications.
Complications
If you’re young and healthy, the flu usually isn’t serious. Although you may feel awful while you have it, the flu usually goes away in a week or two with no lasting effects. But children and adults at high risk may develop complications that may include:
Pneumonia.
Bronchitis.
Asthma flare-ups.
Heart problems.
Ear infections.
Acute respiratory distress syndrome.
Pneumonia is one of the most serious complications. For older adults and people with chronic illnesses, pneumonia can be deadly.
Prevention
The U.S. Centers for Disease Control and Prevention (CDC) recommends annual flu vaccination for everyone age six months or older. The flu vaccine can lower your risk of getting the flu. The flu vaccine reduces your risk of having severe illness from the flu and needing to stay in the hospital due to flu. The flu vaccine also lowers your risk of dying of flu.
Flu vaccination is essential because the flu and coronavirus disease 2019 (COVID-19) cause similar symptoms. Both COVID-19 and the flu may be spreading at the same time. Vaccination is the best way to protect against both. And if a COVID-19 vaccine or booster and a flu vaccination are due simultaneously, you can often get vaccinated for both in one visit.
This year’s seasonal flu vaccines each protect against the four influenza viruses expected to be the most common during this flu season. This year, the vaccine will be available as an injection and a nasal spray. High-dose flu vaccines will also be offered for adults aged 65 and older.
The nasal spray is approved for people between the ages of 2 and 49.
It isn’t recommended for some groups, such as:
People who had a severe allergic reaction to a flu vaccine.
Pregnant people.
Children aged 17 years or younger taking aspirin or a salicylate-containing medicine.
People with weakened immune systems and caregivers or close contacts of people with weakened immune systems.
Children between ages 2 and 4 years old diagnosed with asthma or wheezing in the past 12 months.
People who recently took antiviral medicine for the flu.
People with a cerebrospinal fluid leak or the potential for a leak, as with a cochlear implant.
1 note
·
View note
Text
Computing power anti-virus blockchaincloudmining.com
In the world of cryptocurrency mining, computing power is a critical resource. However, it's also important to ensure that your computing power isn't being used for malicious activities such as spreading viruses or malware. Blockchain Cloud Mining (https://blockchaincloudmining.com) offers a secure and reliable platform for cloud mining services. By leveraging their robust infrastructure, you can focus on maximizing your earnings without worrying about security threats.
One of the key benefits of using Blockchain Cloud Mining is its advanced security measures. The platform employs state-of-the-art technology to protect users' data and prevent unauthorized access. This means that your computing power is not only efficiently utilized but also safeguarded against potential threats like viruses.
Moreover, Blockchain Cloud Mining provides a user-friendly interface that makes it easy to manage your mining operations. Whether you're a beginner or an experienced miner, you can quickly set up your account and start earning from your computing power. With transparent pricing and regular updates, you can stay informed about your earnings and make informed decisions about your investments.
To learn more about how Blockchain Cloud Mining can help you maximize your earnings while ensuring the security of your computing power, visit https://blockchaincloudmining.com today.
blockchaincloudmining.com

BlockChain Cloud Mining
Block Chain Cloud Mining
0 notes
Text
Windows 11 Home – Upgrade Your System with Ease
Windows 11 Home is the latest iteration of Microsoft's popular operating system, designed to offer a fresh and modern experience for users worldwide. With a sleek new interface, enhanced performance, and several cutting-edge features, upgrading to Windows 11 Home can be a game-changer for your system. Whether you’re looking to improve productivity, enjoy the latest apps, or simply experience a more streamlined and secure environment, Windows 11 Home offers a compelling upgrade. This article will explore the benefits of upgrading to Windows 11 Home, its key features, system requirements, and how you can seamlessly make the switch from older versions.
The Appeal of Windows 11 Home Windows 11 Home is tailored for consumers who want a polished, modern operating system without the complexity of the Pro version. The Home edition offers a sleek windows 11 home user-friendly features suitable for everyday use. It comes with several productivity and security enhancements that make the system more efficient while providing a comfortable user experience. Whether you’re a student, a professional, or a casual user, Windows 11 Home delivers everything you need with a focus on simplicity and ease of use.
New User Interface and Visual Enhancements One of the most noticeable changes in Windows 11 Home is the redesigned user interface. The operating system features rounded corners, centered Start Menu, and taskbar icons that give it a more modern, minimalist look. The improved visuals not only make the OS more aesthetically pleasing but also enhance its functionality. The Snap Layout feature allows users to organize their open windows with ease, improving multitasking capabilities. These visual improvements contribute to a more intuitive and enjoyable experience, making Windows 11 Home a pleasure to navigate.

Enhanced Performance and Speed Windows 11 Home is optimized for better performance, ensuring that your system runs faster and more smoothly than ever before. The operating system has been fine-tuned to take advantage of modern hardware, offering faster boot times, quicker access to apps, and improved overall system responsiveness. In addition, Windows 11 Home utilizes a more efficient memory management system, enabling your computer to handle tasks more effectively. This is particularly beneficial for users who rely on resource-heavy applications, such as graphic design or video editing software.
Gaming on Windows 11 Home Gaming enthusiasts will find Windows 11 Home to be an excellent platform, thanks to its built-in gaming features. The operating system supports DirectStorage, which allows for faster loading times in games by reducing the bottleneck between storage and the CPU. Additionally, Windows 11 Home is compatible with Auto HDR, which enhances visual quality by providing more vibrant and lifelike colors in supported games. With these advancements, gamers can enjoy smoother performance and a richer gaming experience.
Improved Security Features Security is a top priority for Microsoft, and Windows 11 Home includes several built-in features to keep your system protected. One of the key improvements is the requirement for TPM 2.0 (Trusted Platform Module), which adds an extra layer of security by protecting sensitive data and preventing unauthorized access. Windows Hello, a biometric security feature, allows for password-free sign-ins through facial recognition or fingerprint scanning, making it both convenient and secure. Additionally, Windows 11 Home comes with Microsoft Defender, which provides real-time protection against viruses and malware, ensuring your system remains safe from threats.
System Requirements and Compatibility Before upgrading to Windows 11 Home, it’s essential to check if your system meets the necessary requirements. While Windows 11 has a more modern approach, it’s designed to run efficiently on a variety of hardware. The minimum system requirements for Windows 11 Home include a 64-bit processor with at least 1 GHz clock speed, 4 GB of RAM, and 64 GB of storage. The system must also support Secure Boot and TPM 2.0. Many newer PCs come pre-installed with Windows 11 Home, but if you're upgrading from Windows 10 or an older version, it’s crucial to verify compatibility before making the jump.
How to Upgrade to Windows 11 Home Upgrading to Windows 11 Home is a straightforward process, provided your system meets the requirements. If you're running Windows 10, Microsoft offers a free upgrade to Windows 11 Home for eligible devices. To begin the upgrade, you can go to the "Windows Update" section in the Settings menu and check for updates. If your device is eligible, you will see the option to download and install Windows 11. It's recommended to back up your important files before upgrading to avoid any data loss during the process. Once the upgrade is complete, you can enjoy all the features and improvements that come with Windows 11 Home.

The Future of Windows 11 Home As Microsoft continues to refine and update Windows 11 Home, users can expect even more enhancements and features in the future. Regular updates will bring new functionalities, performance improvements, and security patches to ensure that your system remains up to date and secure. Microsoft is also committed to supporting a wide range of devices, so even if you're not using the latest hardware, Windows 11 Home is designed to deliver a great experience. As technology continues to evolve, Windows 11 Home will adapt, providing users with the tools and features needed to stay productive and enjoy the best that modern computing has to offer.
Conclusion Upgrading to Windows 11 Home is an excellent decision for those looking to improve their computing experience. With its modern interface, enhanced performance, robust security features, and gaming enhancements, Windows 11 Home offers a comprehensive solution for everyday users. While ensuring that your system meets the upgrade requirements is crucial, the process is simple and free for eligible Windows 10 users. Whether you're a casual user, a professional, or a gamer, Windows 11 Home provides the features and performance you need to make the most of your computer.
0 notes
Text
Technology today makes it very easy to gather, store, communicate, and likewise, and manipulate data. Consequently, developments in information systems also involve social and political relationships-and thus ethical consideration in how information is used is all the more important. Government records, workplaces, and private lives of the people are within the reach of the system and it is a vital responsibility now to balance the needs and rights of everyone. While everything with online security systems seems very user-friendly and tends to make life easier for a management team, there is also a significantly dangerous side to the use of online information systems. One of them happens to be a cybercrime. Typically, cyber crime can be divided into four categories; theft, fraud, copyright infringement, and attacks. With the popularization of the internet and its several weak links, hackers find it possible to break into security systems where they have access to a person's key personal data such as social security numbers, date of birth, driver's license numbers, and credit card information. Affected individuals have experienced fraudulent financial transactions, and false accusations of crimes they have never committed which begin showing against their names on their record files. Information systems are vulnerable to physical attacks, electronic hacking, viruses, and natural disasters. With computer systems serving as the backbone of many organizations, managers must be aware of both: the risks and the opportunities to minimize the risks to information systems. A virus is a computer program designed to infect another computer without the permission or knowledge of the user. It can spread from one computer to another, by either sending it over a network, for instance, the internet or by carrying it on removable media such as CDs, DVDs, USB drives, etc. A virus tends to destroy an information system, deleting the data and making it forever irrecoverable. To look on the bright side, these threats to information systems can be fought with some security measures. The main goal is to protect the confidentiality, integrity, and availability of information. To ensure that there is no vulnerability of an information system being attacked, the following must be kept in mind: • Identify the security needs and the IT risks of the company. • Outline the rules and procedures that must be implemented. • Monitor and detect the information system's vulnerability and keep updated about the system's flaws • Define the actions to be taken in case a threat is detected. However, security must also go beyond employee knowledge and cover the following areas as well: • A physical and logical security mechanism that requires employees to continuously supervise the information system. • A procedure for managing updates. • A properly planned backup strategy. • An up-to-date documented system. • An active firewall to fight malware. Even though an information system is prone to many attacks, it can be overcome by taking into account such measures and while there is no denying the fact that a computer information system is the vital key to the success of an expanding company, it is justifiable to say that such consideration be given to its information system Read the full article
0 notes
Text
Wondering how malware gets on your computer? How software like malware and spyware spreads? This is a guide for all computer users to be aware and avoid getting infected by these malicious softwares. Malware, without a doubt is a deadly push for your computing devices, and can harm it to such an extent, that you might even consider fencing up for any future dangers. A malware can easily steal your personal information, can play with your finances, can spoil your system and much more! But with the help of an anti-malware program, combined with an active internet firewall and an updated operating system, you can keep your system safe and protected from all kinds of malware attacks. These measures are very simple and helps in securing your system for a long term. Although no matter how many measures one might take to safeguard their computer, there is always a possibility of your system getting attacked from malware. This is because skilled cyber criminals, hackers, spoofers and sneakers steadily derive ways to get a loophole in the security of your computer. The basic security measure against defending your system from malware attacks is to thoroughly recognize the way malware slips into your computer. Malware? What Exactly It Is? Malware is nothing but a piece of software, which is designed in order to interrupt the normal working of a system, steal personal and confidential information, alter and leave the system burned out! So basically malware is a software which is malicious, hence the name malware. Malware can be of different forms and they aren’t limited to any particular type; these could be worms, viruses, trojan horses, spyware, adware, keyloggers etc. Despite their normal behavior, one shouldn’t take them for granted, as these kinds of malware can cause a great extent of harm to your computer and your personal information as well. What makes a malware more suspicious and deadly is that it can run on your system undercover and secretly, without you getting any hint about it. How Malware Gets Into Your Computer? Here are top 7 devious ways malware slips into your computer: Clicking On Scareware Or Rogueware Popups Internet is full of pranksters, bullies and hackers - they will eventually come up with something or the other to scare an internet user. Scareware is a new concept of roughhousing with internet user by making them believe that their system is infected with a virus, and all they got to do is download a software to get rid of it. These might pop up almost anywhere and read “click here” and so on. The reason why these popups are so much efficient is, because a significant amount of users have no freaking idea as to how viruses get transferred, or how legit these popups are! Despite their fishy nature, scareware pop up ads generally are malware apps which deceive people into clicking that particular ad, so that they could get a pass to your computer. Once it is done, a malware can infect your computer easily. So it becomes very important to stay updated with the kind of softwares (especially your antivirus!) you have on your system and freshen them up time and again. Via Spam Email, Attachments & Links Spam links are an everyday scenario - we receive those annoying spam emails which head away straight to our junk or spam folder. But these spam email messages do contain some of the most tempting and convincing content that might give you an illusion of getting something out of this world. Or intermittently you might have received an email from a person in your contacts list, but the mail looks dubious. Sometimes an email might contain a link, or an attachment (which is obviously put to tempt you to open it!) that might be a portal to malware’s hell! Make it a point to confirm the source of the email before you open an attachment or click the links included in the email. Or you can ensure the identity of the contact that sent you the mail/link/attachment, or run the mail through an antivirus program which will scan it for any possible threats.
Making Adobe Acrobat Reader Default For PDF Files Mostly, Adobe Acrobat Reader is the default program to open up many files, PDF files being the prime. However, a couple of times (mostly intended) a cybercriminal might create a PDF infected with malware, and opening this file by default with the help of Adobe Acrobat Reader might pose a greater risk to your system. Make sure you keep all your programs well versed and up to date, and don’t forget to scan your files with an antivirus program. JavaScript While Internet Browsing Internet browsing isn’t a piece of cake in terms of safety - no matter what web browser you use, there’s always a susceptibility of your system getting attacked with malware. Howbeit, it’s not the web browser, its the JavaScript which makes your system much more vulnerable. If you effectively disable JavaScript from running on your web browser (not all, just the doubtful one’s) then you can put your system to safety. Signing In To Any Website Via A Suspicious Link The most passable errors people make is signing in to their accounts via clicking on the links that might have been sent in a dubious email, such as an email from a “bank”. What people don’t understand is that no bank or organization will send such sort of email asking you to login or provide your login details. These are phishing attacks or malware attacks. If you ever get any such email, it's better to contact your bank. Piggybacked Software Installation Piggybacking is actually a smaller program that gets installed without the prior notification while one is equipping the required software into his/her device. For instance Avast install the dropbox where Adobe reader install the toolbar plugin or any security software or spyware without letting the concerned user know about it. Although there are some software that provide you the facility to uncheck the unnecessary downloads but some perform the action without letting you know about it. Therefore it’s essential to read the terms and conditions in the course of installation process so that you can be aware of the additional program that will get planted into your phone. Browser Add-ons Browser add ons are the small software that are added to the web browser such as the toolbar, search box, animated objects. The add-ons can become nasty as sometimes the spy program can also be the part of these web add-ons. It takes great effort to get on the track if these fierce enhancement leads to the website getting hijacked, as the bug in the form of an additional factor intensely gets attached with the website. So it’s suggested that you carefully review the browser add-ons before installing it. These were the 7 ways a malware can get inside your computer, but who knows there might be more! Just remember to keep safe and put up all your guards in order to avoid any kind of attacks. Tips For Do’s And Don’ts Keep scrolling to know the ways that can help you stay away from malware. Don’ts DO NOT click on the website link that you’re unsure of. Immediately leave the dubious website and search for other website link for your required search material. Be careful of the content associated with the spam emails especially if it contains the links or attachments. Make a habit of scanning the secondary storage devices like disc, pendrive, flash drive before you use the same on your systems. Avoid checking the pop up boxes appearing on the window. It’s advisable to close the windows by clicking on the cross button [x] or press Ctrl+Alt+Delete. Review the message boxes that appear while you’re installing any kind of software onto your device as it might contain the malware. Do’s To Follow Keep your Operating System and browser updated as this will keep the malware at bay. Block the Pop up windows and automatic feature updates. Run an antivirus program that has an anti malware element to stay safe. Ensure it’s updated and turned on. Equip the device with the third party firewall or else use the Windows firewall. Consider the spam filtering software if you’re unsure that your email program can filtrate.
How To Do Removal Of Malware? No matter how much care and precautions you take to prevent the malware entering your system still you will be trapped by it. Therefore it’s highly recommended that you use a good antivirus software to ward off your system from any kind of virus, spyware or malicious programs. Kerrie writes cell phone spy reviews for spy software such as mSpy, FlexiSpy and Highster Mobile Spy and help people in choosing the best cell phone spy software at spyengage.com.
0 notes