#IMAP backup software
Explore tagged Tumblr posts
Text
My search for a safe IMAP backup tool ends here
I believe everything has to have a security approach. I mean to mention that safety is important if you have a huge database and you want to back up the emails. I uses Mac for my daily activity so when I created an email account it asked me about IMAP.
IMAP account is very important while you configure any email account like outlook for Mac or Windows. IMAP is Internet Message Access Protocol. You require an IMAP account to access your emails. You can check out in the below link how IMAP is linked with emails.
I am very particular about safety of data. And when it comes toIMAP backup, I am more vigilant. Because I want to ensure a safe IMAP backup mac. It is the only important factor while looking for the right IMAP backup tool. Because the conventional toolsmight deliver email archival, however it might corrupt them.
My major area of concern has always been a safe IMAP backup solution rather than only backup mac mail. Because, there is no point using a tool that set up wrong expectations and corrupts it eventually.
Let me brief you this with an example.
I was operating different mail service providers on Mac, and it was very important for me to ensure its safety. As I was aware, I was looking for a tool that enable me a safe mac email backup. It becomes important when you are using two or more mail service providers on the same system. IMAP backup and restore was my biggest task ensuring hundred percent safety with data integrity.
I achieved hundred percent safety of my data with this IMAP backup software
It was through Mail Backup X by InventPure, I could ensure a safe backup. The only tool that utilize ultra-high compression algorithm design to secure and safeguard the mail data. Even though these terms were difficult for me to understand, I actually understood the meaning while performing IMAP backup.

The best thing about this application was that it can compress and extract the files reduce required storage space. The tool also encrypts the data for security into a coded language so that it would not corrupt any further. Also, the tool support repair recovery record in case of hardware corruption so that you do not lose any important information while performing IMAP backup and restore.
It also has a feature that adds benefit to the IT team as it helps to save time on uploading and retrieving data from Network Servers or FTP.
This explanation was enough for me to select this IMAP backup tool as it uses three times storage space while compressing the data safeguarding it at the same time.
I was confident of the IMAP backup software after using the demo
I was looking for a hundred percent assurance before using this IMAP backup outlook tool. And the only way to achieve this was browsing the official website.
So, I went ahead and tried the demo version for 15 days. This was the turning point to select the tool eventually. If you really want to ensure a safe data backup then just follow the below and archive with hundred percent safety assurance www.mailbackupx.com/imap-backup-tool/.
#IMAP#IMAP backup#backup IMAP#backup IMAP folder#backup IMAP data#IMAP mail backup#IMAP backup software
1 note
·
View note
Text
What is the best IMAP backup software?
There is no disputing the fact that Mail Backup X is best IMAP backup software and there are obvious reasons why this tools rules the roost. This is a fully automatic tool that has no flaws to speak of and has mastered the art of delivering immaculate results in the most challenging of circumstances. Throw any mail volume at this tool and it will deliver the intended results without any errors. This tool is far too easy to use than even than what you can imagine because it comes equipped with a simplicity-oozing interface with a user friendly design. A technology-propelled tool that does it jobs in an immaculate manner while requiring hardly any human intervention is something we all desire and this tool fulfills this desire to the maximum extent. This tool will be worth your while because it comes jam-packed with all the functionalities we desire such as IMAP backup, archiving, migration and restore. Most users do not have a strong technical background and they do not have enough spare time to spend on training. With this ease-affording tool at your beck and call, you will never encounter the need to browse through the pages of a boredom-inducing technical manual to learn its working mechanism.

How to backup IMAP email? Get instant answers for your predicaments with this tool
We grapple with one question after the other when it comes to email management. If email backup was so simple, we would never have to look towards automatic solutions to solve this issue. Before proceeding with this task, we have to draw a clear picture in our mind as to when to backup IMAP data email, what frequency and timing to choose, etc. We want to zero in on an apt backup location or choose many backup locations simultaneously to give encouragement to formation of ideal data redundancy. There may be occasions, when full backups would mean a wastage of resources with selective backup option also at our disposal. We may also feel the need to password protect our backups. Taking all these aspects into consideration, formulating the best email management strategy can become a laborious task with manual methods or average tools. This is the reason why we must shortlist Mail Backup X as our go to solution as it has everything in its arsenal to satisfy us to the T. Equipped with a wizard based process, this tool makes applying various customizations to backups a walk in the park.
IMAP backup onto cloud based sites will reap you rich dividends
You can easily create remote backups with this IMAP mail backup tool and secure your backups from all the uncertainties that plague local backups. Local backups can be misplaced, stolen or become causality of hardware malfunction. But this does not mean that you should not create local backups as local backups are a strong means to consolidate data redundancy and completely dispel any chances of data loss. Today many viable locations for remote backups are available with Google Drive, PCloud and Dropbox being among the most prominent alternatives available to us. Maintain remote backups in tandem with cloud backups. All these options are on offer from this tool. What is more; you may also maintain portable backups alongside local and cloud backups. Everything is possible with this IMAP backup tool.
This IMAP backup application is a complete solution
Once you invest in this worthy tool, you predicaments will end once and for all. Whether you want to go for data recovery, or want to migrate mails, this tool has a perfect solution for your every problem. By investing in this tool you will be killing many flies with one blow because this is a multifunctional application that caters to all aspects of email management. This tool being compatible with both Windows and Mac will also prove to be a great money saver as you will not need different applications to deal with different email management issues. This tool is providing everything under one umbrella.
This IMAP backup application is worthy of your approval because of the following reasons
There's no reason to limit yourself as far as email management goes as this tool is compatible with both Windows and Mac.
This tool will not limit you in any manner whatsoever because you can solve multiple predicaments with this one solution that caters IMAP backup, archiving, restore and migration in one all-inclusive package.
Everyone has a different approach towards approaching a particular problem, which is the reason why this tool caters multiple backup types such as full and selective backups.
Mirror, cloud and portable backups are also available.
3X data compression that too without hampering the folder hierarchy or skipping vital email elements will allow you to enjoy an upper hand over space consumption by backups.
Smart backup and resume is another special technological offering by this tool that saves a backup session from being turned to waste by uncalled for interruptions like network failure.
This tool takes the onus upon itself to simplify and speed up email search for you via an advanced search module.
A comprehensive mail viewer will provide you a reader-friendly and systematic bird eye's view of your entire email database.
This tool is versatile yet cheap- a winning combination of benefits that will win over your approval without much ado.
PDF archiving is another praise worthy feature in the arsenal of this tool.
Round the clock user support will be at your back to resolve your issues without any delay whatsoever.
Demo
Everyone needs a test run before giving a final go to an IMAP backup tool. We are providing you test run in the form of a free 15 day demo of this tool, which will unravel the matchless features of this tool. Don't let this chance to go by unnoticed as you are about to step inside a technological plush zone where your every desire concerning email management with don the garb of reality.
#IMAP mail#IMAP email#IMAP backup#backup IMAP#IMAP mailbox backup#mail backup#backup mail#mail#email#backup software
0 notes
Text
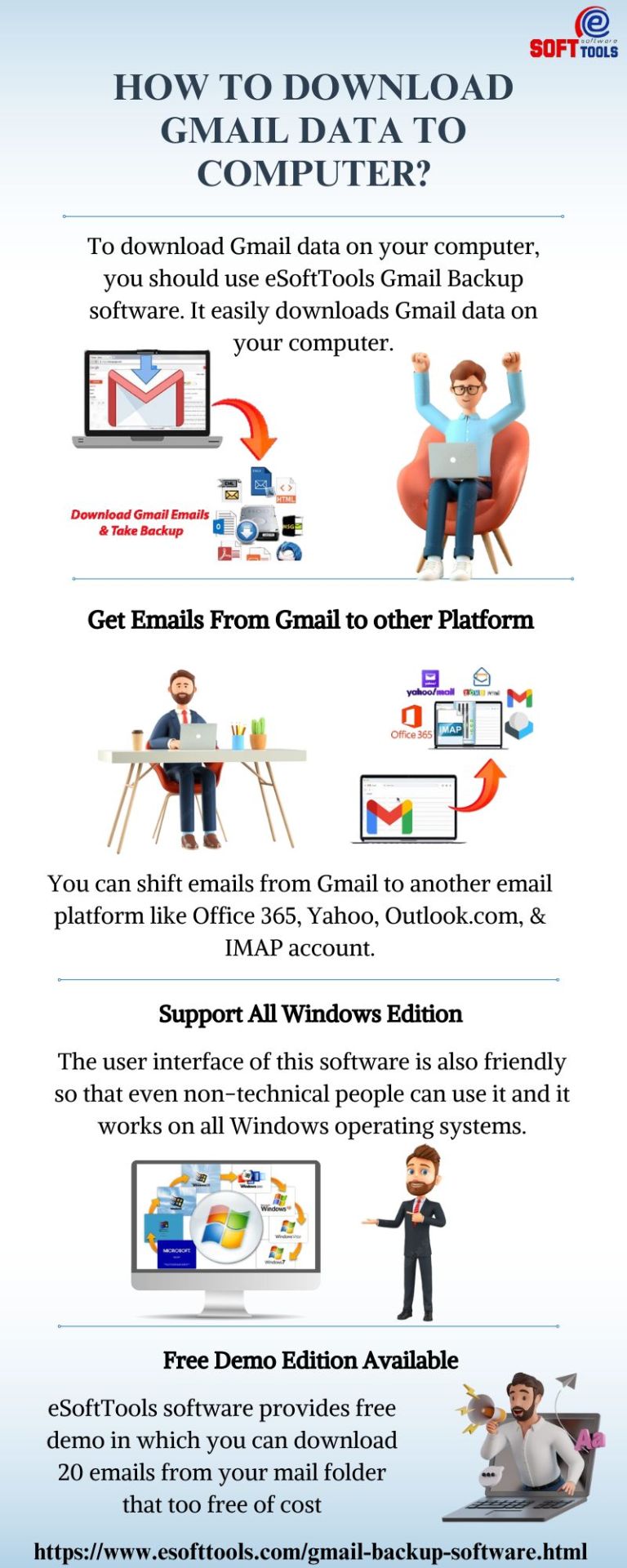
The best way to download Gmail data on computer is to use eSoftTools Gmail Backup software because this software can download Gmail data on computer in very easy steps. With the help of this software, you can shift emails from Gmail to other email platforms like Office365, Yahoo, Outlook.com, & IMAP account. The user interface of our software is also friendly, so even non-technical people can easily use this software. eSoftTools software provides free demo to all users in which users can download 20 emails from their mail folders that too free of cost.
Read more- https://www.esofttools.com/gmail-backup-software.html
0 notes
Text
If you want to import MBOX files into Gmail, it’s not directly supported by Gmail. However, you can use a few workarounds to get it done. Below are the some steps you can follow to successfully import your MBOX files into Gmail format.
Method 1: Using Thunderbird and Gmail IMAP
This is a free and effective method to transfer MBOX files to Gmail using the Thunderbird email client.
Steps:
Install Thunderbird: Download and install Thunderbird on your computer.
Set Up Gmail in Thunderbird:
Open Thunderbird and go to Account Settings.
Click Account Actions and select Add Mail Account.
Enter your Gmail login details and configure it using the IMAP protocol.
Install ImportExportTools NG Add-on:
In Thunderbird, go to the menu and click on Add-ons.
Search for ImportExportTools NG and install it.
Restart Thunderbird to activate the add-on.
Import MBOX Files:
After installing the add-on, right-click on your Gmail inbox in Thunderbird.
Select ImportExportTools NG > Import MBOX file.
Browse to your MBOX file and import it into Thunderbird.
Drag Emails to Gmail Folder:
Once the MBOX emails are imported into Thunderbird, simply drag and drop them into your Gmail folder.
Thunderbird will sync the emails to your Gmail account over IMAP.
Method 2: Using WebbyAcad MBOX to Gmail Converter
If you want a quicker and more direct method, using a dedicated tool like WebbyAcad MBOX to Gmail Converter can simplify the process. Here's how you can use it:
Steps:
Download and Install WebbyAcad MBOX to Gmail Converter: Download the software and install it on your computer.
Add MBOX Files: Launch the tool and click on Add Files to select your MBOX files.
Log in to Your Gmail Account: The converter will ask you to enter your Gmail login credentials securely.
Start Conversion: Once logged in, click on Convert and the software will automatically import the MBOX files directly into your Gmail account.
Method 3: Using Google Takeout (For Backups)
If you’re looking to restore MBOX files that were originally downloaded via Google Takeout, follow these steps:
Extract MBOX Files from Google Takeout: If you’ve backed up your Gmail using Google Takeout, extract the MBOX files from the Takeout archive.
Use Thunderbird: Follow the same steps in Method 1 to import these MBOX files back into Gmail.
Conclusion
To import MBOX files into Gmail, using Thunderbird with the Gmail IMAP setup or a dedicated tool like WebbyAcad MBOX to Gmail Converter are the most straightforward options. These methods ensure your emails are transferred safely and efficiently.
1 note
·
View note
Text
Best solution to restore Apple email
Don’t look any further for a solution to restore Apple email
Maybe you have never felt the need to restore data. But you keep hearing the experts telling you to archive email data and keep ready for restore if need be. You cannot ignore this advice as it is extremely valid and important. Archiving emails and backing up data regularly is what any wise person will do because we know how data is so prone to damage or hacking or other kind of losses. This is especially true when original messages don’t get stored in device like the case with IMAP based services. You will need to restore Apple email in a case you lose data due to any reason like hardware failure or some other. You will be able to restore only if you have backed it up or archived email folders. Else, you will not be able to do anything. You need a good backup and recovery option for this. Although we will be focusing on a method which covers all IMAP based email services like Gmail, Thunderbird, Yahoo, etc., you can read a little about Apple email to get a fair idea why we must backup emails. Here is the link- https://en.wikipedia.org/wiki/Apple_Mail
Best way to restore Apple email is with a certified software

There are a few methods available to backup as well as restore Apple mails and other on Mac. Yet, you see experts recommending only certified tools. Why is it so? Why don’t they recommend a manual method or maybe restore Apple email app which works online? There must be some factor behind it. While manual methods are never recommended for any similar task which is to be done regularly, they also pose a great challenge to novices. And when we talk of online apps, they are fraught with dangers like data loss, data stealth, corruption, etc. Along with these risks, there is almost zero support available for any doubts or mishaps. This means we shouldn’t be using these apps. We should only use a reliable certified archiving and restoring tool like Mail backup X by InventPure. This is the best one out there for end users.
Now restore Apple email account and other multiple accounts in a short, precise, and easy way
This tool makes it really easy, quick, as well as accurate to backup and restore IMAP emails on Mac. There is something else also which we need to look at. If I am in a need of a software, and I have heard good things about it, even then it would be normal for my mind to have some doubts. All users face these doubts and thus this issue must be settled. This issue is settled by bringing to users a free albeit a limited use demo of this backup tool so that their doubts are settled. They can use most of the important functions that the full restore Apple email tool comes with and once satisfied, they can purchase full version for daily data preservation in the manner they prefer https://www.mailbackupx.com/restore-apple-email/.
1 note
·
View note
Text
An easy process on how to backup apple email
I want to share my experience on apple email backup because most of the mac users are used to apple mailbox like me. There are various reason to support it however; my favourite reason is configuration of other mail clients in apple.
If you are wondering that apple mail supports other email services as well then you should definitely click below link for more information.
Many people still wonder on the subject ‘apple email backup and restore’, may be because they are confused on how to do it.
So, I thought to introduce an apple email backup tool to provide a perfect apple email backup solution.
So, just follow the easy steps of this apple email backup software.
Step 1 Launch the application of Mail Backup X by InventPure, it will display a dashboard on the screen. Select ‘Add new backup’ under Backup Setup for apple mail.
Step 2 After clicking on Add new backup, it will display a list of different IMAP accounts like Office 365, Mozilla Thunderbird, GMAIL, Postbox and so on. Select apple mail from the dialog box.
Step 3 The next step allows the tool to load data from the selected source yahoo mail. The tool will scan through the database and read the email files that are require for archival. It will take few minutesfor the tool to scan the files in your database. In few minutes, you get an actual status of the files and items being scan and procure.
Step 4 The next step is to choose apple email backup folder as the storage and click on done for completion. It allows picking the location where you want to back up the data. You can browse in your folders and choose the right place to store it. You can assign a name to the yahoo backup file to locate it later. You can also choose the option for automatic detection of changes in your database so that they can be sync to the backup. The tool offers this option as an added benefit that can be rarely found in the tool. The tool is loaded with advanced algorithms, which can detect and sync the changes made in the database.
Step 5 The next screen is the Backup confirmation screen which shows the status of the backup that has been completed. It also shows the total number of files that are back up along with a backup log. You can see how many backups being synchronized. This is the final confirmation step that makes yousure that your files have been backed up successfully and with accuracy.
Demo version of the tool eases the selection process

Even if I have produced the steps, it is important to go ahead with the registered version of the tool but not before you test it. It is advised to test the tool with a fifteen days demo version to understand more about the tool and clear your doubts. That is why, I have produced the link of the website below https://www.mailbackupx.com/how-to-backup-apple-mac-mail-mails-on-mac/.
#apple email backup#apple mail#apple mailbox#apple mailbox backup#backup apple mailbox#apple mail tool
0 notes
Text
Essential Server Buying Guide for Small Businesses

As your small business grows beyond a handful of employees, it's likely time to consider investing in a server. The term "server" can refer to hardware, software, or the functionality of both, and choosing the right server for your business can be a daunting task. This guide will help you navigate your options and make an informed decision.
Understanding Your Needs
Before diving into the specifics, ask yourself the following questions to determine your server needs:
Are you buying for file sharing?
Will it be predominantly used for email?
Does your workforce need to connect remotely?
Is it going to be used for data backup?
How much space do you have available to accommodate the server?
Server Hardware and Functionality
At a hardware level, servers are similar to standard PCs but are designed for 24/7 operation and often include additional features like ECC memory and redundant components to ensure continuous operation. Key hardware components include:
CPU: The number of cores and clock speed determine the server's ability to handle multiple tasks.
Memory (RAM): More RAM allows for better performance, especially under heavy load.
Storage: Multiple bays for hard drives and options for RAID configurations ensure data redundancy and fast access.
Choosing the Right Server Type
File Servers
File servers or Network Attached Storage (NAS) are used for storing and sharing files across a network. Look for:
Multiple hot-swappable drive bays
Configurable hardware/software RAID options
Low-power CPU for efficient operation
Domain Controllers
Domain controllers manage user authentication and access levels. They are crucial for businesses with multiple users and devices. Look for:
Virtualization-capable CPU (any 64-bit CPU)
At least 4 GB of RAM
Database Servers
Database servers handle large volumes of data and user queries. They are essential for applications and websites built on a database layer. Look for:
Hard drives rated for fast writes
Large CPUs (12- or 16-core)
Backup 'slave' servers for read-only databases
Web Servers
Web servers host websites and use HTTP to present web pages. They often work with a database server. Look for:
Hardware redundancy (especially for e-commerce sites)
Increased RAM capacity for better performance
Email Servers
Email servers, such as Microsoft Exchange, use specific protocols (SMTP, POP3, IMAP) to send and receive messages. Dedicating hardware to this task is recommended for optimal operation. Look for:
Similar specifications as a file server
Application Servers
Application servers centralize applications within their native framework (Java, PHP, .NET, various flavors of .js), improving performance and reducing maintenance costs. Look for:
Enterprise-grade storage bays (SAS hard drives)
ECC RAM
Choosing the Right Form Factor
Servers come in various physical form factors, including tower, rackmount, and blade:
Tower: Resembling desktop computers, tower servers are suitable for small businesses needing one or two servers. They don't require additional mounting hardware but take up more space as you add more servers.
Rackmount: These servers are installed in a rack chassis, which can hold multiple servers in slots. They are ideal for businesses needing several servers in a consolidated space.
Blade: Blade servers are more space-efficient than rackmount servers but require careful cooling and a larger initial investment. They are suitable for larger server rooms.
Server Operating Systems
A server operating system (OS) is more advanced and stable than a desktop OS, supporting more RAM, efficient CPU usage, and a greater number of network connections. The OS enables the server to perform various roles, such as:
Mail server
File server
Domain controller
Web server
Application server
Administrators use the server OS to authenticate users, manage applications and file storage, set up permissions, and perform other administrative tasks.
Conclusion
Choosing the right server for your small business involves understanding your specific needs, selecting appropriate hardware, and deciding on the best form factor and operating system. By carefully considering these factors, you can ensure your server investment supports your business's growth and operational efficiency.
0 notes
Text
youtube
DomainOffices.com - Secure Domain Hosting - Domain Registration - Encrypted Web Hosting
Domain Offices Oversees Security Updates

Support: 24/7/365 Technical Support via Phone, Live Online Chat, and Support Ticket
DomainOffices.com is an International Domain Name Registrar Registering all Global Domain Name Extensions, including Encrypted Web Hosting, Domain Registration, Secure Domain Hosting, Register Domain Name, Secure Web Hosting, Domain Offices, Domain Renewal, DNS System, Virtual Private Server, Semi-Dedicated Server, Dedicated Server, Shared Hosting Plan, Whois Protection, Cheap Domain Hosting, Cheap Web Hosting, Free Domain Name, Reliable Website Hosting, Cloud Web Hosting,and SSL Encryption. Domain Offices offers you the opportunity to host your web sites in one of our five first-class secure data center facilities located in 1) Chicago, USA, 2) Sydney, Australia, 3) London, England, 4) Pori, Finland, and 5) Telepoint in Sofia, Bulgaria. The Steadfast, Chicago data center offers ideal conditions for hosting web sites whose visitors reside in the United States, Canada, or Latin America, and will guarantee you the fastest web page load speed feasible. The US data center facility option is available with all our shared web hosting plans, KVM and OpenVZ-powered VPS servers, semi-dedicated hosting servers and dedicated servers. Simply pick your package and then select the US data center facility from the drop-down menu on the signup form. Domain Offices works with one of the most famous data centers in Australia - SISGroup, which is situated in the Sydney central business district. The data center offers excellent Internet connectivity and perfect conditions for hosting websites whose visitors are physically located in Australia and Oceania. The Australian data center facility will guarantee you the fastest web site load speed possible. This data center option is available with all shared web hosting packages and OpenVZ-powered VPS web hosting packages of ours. Select the plan that you want on the signup form and then select the Australian data center from the pull-down list. If your web site will be targeted at users from the United Kingdom, the rest of Europe or Africa, we offer the perfect solution for you. We partner with top-class data centers situated in 1) London England, 2) Pori Finland, and 3) Telepoint in Sofia, Bulgaria, which offer the highest level of security for your web site and which will guarantee you the fastest web page loading speed possible. You can select the desired data center from the pull-down list on the signup form. This data center option is available with all shared web hosting plans, as well as with all KVM and OpenVZ-powered virtual servers offered on our website. Domain Offices has forged strong partnerships with international data-centers in the United States, Australia, Britain, Finland, and Bulgaria, to provide our clients with secure and reliable web hosting. Shared Hosting Features: -- Free Setup -- Disk Storage: Unlimited with Data Backups -- Domains Hosted: From 1 to Unlimited (Depending on Plan) -- Full Shell/ SSH/ FTP/ SFTP Users: Unlimited -- E-mail Accounts (POP/ IMAP/ Webmail): From 100 – Unlimited (Depending on Plan) -- MySQL 5 Databases: From 5 to Unlimited (Depending on Plan) -- Custom WHOIS Details and Custom DNS Records -- Programming: Perl, PHP5, Java Servlets, Python, Contrab -- One-Click Automatic Software Installers: WordPress, PrestaShop, OpenCart, Joomla, Drupal, Moodle, vTiger, Open-Realty, phpBB, and others -- Multi-lingual Control Panel -- Account Accessibility: Domain Offices Control Panel -- Five Secured Global Data Centers - With Data Backup -- Support: 24/7/365 Technical Support via Phone, Live Online Chat, and Support Ticket -- Guarantee: 99.9% Uptime Guarantee Website: DomainOffices.com Video Link: Domain Offices - Video
DomainOffices.com is an International Domain Name Registrar Registering all Global Domain Name Extensions, including Encrypted Web Hosting, Domain Registration, Secure Domain Hosting, Register Domain Name, Secure Web Hosting, Domain Offices, Domain Renewal, DNS System, Virtual Private Server, Semi-Dedicated Server, Dedicated Server, Shared Hosting Plan, Whois Protection, Cheap Domain Hosting, Cheap Web Hosting, Free Domain Name, Reliable Website Hosting, Cloud Web Hosting, and SSL Encryption.

#Encrypted Web Hosting#Domain Registration#Secure Domain Hosting#Domain Name#Domain Name System (Protocol)#Register Domain Name#Secure Web Hosting#Domain Offices#Domain Renewal#DNS System#Virtual Private Server#Semi-Dedicated Server#Dedicated Server#Shared Hosting Plan#Whois Protection#Domain Name Registrar#Cheap Domain Hosting#Cheap Web Hosting#Free Domain Name#Reliable Website Hosting#Cloud Web Hosting#SSL Encryption#Youtube
1 note
·
View note
Text
sms backup+ still works but it takes effort
i haven't been using wireless service on a phone for years so i wasn't texting anyone. after getting a new phone and wireless service, i went to get SMS Backup+, a third-party app that forwards all SMS and MMS messages to your gmail account, and threads them properly in a readable and searchable way. The app isn't supported anymore and google changed its gmail API and security requirements, so I spent a while trying out all the other available apps and they're all complete garbage, just astoundingly terrible. I had to resort to using F-Droid as an alternative software repo and getting SMS Backup+ that way, then manually configuring IMAP for my account and the app with an app-specific password, but finally got it to work. this ought to be a basic google feature for android phones but google is google and is determined to turn everything it touches into shit.
0 notes
Text
Zoho Consulting Partner in Dubai
When it comes to choosing the right CRM solution for your business in Dubai, partnering with a reliable Zoho Consulting Partner like Icigai can make all the difference. As a leading IT services provider in Dubai, Icigai offers a range of Zoho CRM software services and support to help you streamline your business processes and boost productivity.
At Icigai, we understand that each client's needs are unique, which is why we work closely with our clients to develop customized CRM solutions that cater to their specific business needs. Our team of experienced Zoho consultants is well-equipped to handle even the most complex CRM implementation projects, from initial consultation to ongoing support.
One of our core services is Zoho Migration Support, which involves migrating your data from your current email provider to Zoho Mail. Migrating your data can be a daunting task, but with Icigai's expert assistance, the process can be seamless and hassle-free. We offer a range of migration options, but we recommend using the IMAP protocol for a smooth and efficient migration. The time it takes to migrate your data depends on factors like network speed and mailbox size, but we assure you that we will work with you to minimize any downtime.
At Icigai, we prioritize data security, so you can rest assured that your data is in safe hands. We offer backup and disaster recovery services to ensure that your data is always protected, even in the event of a disaster. Our team of experts follows industry best practices to ensure that your data remains secure at all times.
Partnering with Icigai as your Zoho Consulting Partner in Dubai can help you unlock the full potential of Zoho CRM and take your business to the next level. We offer a range of Zoho CRM software services, including customization, integration, and ongoing support, to ensure that your CRM solution is tailored to your business needs. Our team of experts is always on hand to offer advice and guidance, so you can make the most of your CRM solution.
In conclusion, partnering with a reliable Zoho Consulting Partner like Icigai can help you grow your business in Dubai. We offer a range of Zoho CRM software services and support to help you streamline your business processes, boost productivity, and ensure data security. Contact us today to learn how we can help you take your business to the next level.
0 notes
Text
An IMAP backup tool that will help you conquer every difficulty in this time-sensitive task
No one will refute the fact that IMAP backup is a time-sensitive action against unpredictable situations that may encourage data loss. Despite this understanding sinking deep into our minds, we resist the idea to backup IMAP email because of some difficulties. With tighter work schedules dictating terms and with so much going on in our personal lives, this task tends to be subconsciously avoided. There's another apparent reason why people tend to overlook this need, which is finding this procedure to be beyond their technical acumen. This stokes a feeling of fear.

We also feel at loss of answers when we are not able to find useful information detailing the nitty-gritty of email backup. This leads to a lingering resistance preventing us from creating backups. We also feel conscious of the fact that using any ominous, random tool may become a causative factor behind data loss. We also feel uncomfortable about accommodating more data in the form of backups into our limited storage space which is already being challenged by a rapid rush of miscellaneous data. We may not be equipped with technical skills required to backup IMAP email, which can become a major mental block which is hard to dissolve.
However, this does not imply that there are no easy ways to conduct email management without being engulfed in fear emanating from various factors detailed above. There's an ease affording method to backup IMAP email when you take safe refuge in the company of Mail Backup X, a tool with ease of usage and reliability written all over it. This tool has bagged unprecedented appreciation from software critics and it takes data security many levels higher with sturdy data protection techniques. The ease of usage fostered by this tool is so profound that even beginners can partake in email management, with no doubts running at the back of their minds.
Perform the time-sensitive task of IMAP backup immediately
Don't live in the false confidence that data loss always happens to someone else and you are invulnerable to threats to data security. Things can take a turn for worse quite abruptly and catch you in a totally unprepared state where you have no means at disposal to rectify the bad effects of data loss. One must be proactive and take preemptive action before things go out of hands. To perform the time-sensitive task of IMAP backup immediately you need a professional tool like Mail Backup X. This tool gets rid of all complexities in this process and boasts of flexibility which is a rarest of rare find. Unlike the services of data security experts who have to be paid a regular remuneration, this tool involves a one-time cost and satisfies your present and future email management needs without any delay.
This IMAP backup tool will roll out benefits after benefits
Mail Backup X is a numerouno tool that automates and smoothes out the process of email backup from a wide range of email services. Being a platform independent tool that does its job flawlessly on both Windows and Mac, it will offer you full value for every penny you spend on it. You can conquer any challenge in email management in the company of this ingenious tool without being made to toil hard. The platform independent nature of this tool will allow you to use both Windows and Mac interchangeably because it keeps ease of usage intact, while you work on any of them. You will not be victimized by technical complexities or face any hurdles while going the distance with this tool that caters bonus functionalities like email archiving, restore and migration. Once you are done with a short and simple installation process, you will discover that this ease-affording tool will not threaten you with any technical challenges, because ease of usage will accompany you everywhere while you transverse the versatilelandscape of this tool.
This IMAP backup tool has a lot on the cards to create an everlasting positive impression on you
To start with, this is a cost effective tool with diverse functionalities that make it an even more affordable option.
You can sever all ties with doubts as this tool delivers the goods in the area of data security.
Besides experts, users have also rated this tool as the best utility with the best lineup of features that lend completeness to email management.
You will not find anything lacking in this application that performs both IMAP backup and recovery.
This tool extends its dominion to Windows and Mac while sustaining its ease of usage on both through an interface that remains the same. This will prevent any doubts from manifesting in your mind.
This tool provides a multitude of backup options, an attribute that is highly demanded by the utility-hungry users. These backup options include full backups, partial backups, incremental backups, mirror backups, etc.
You will face no issues while actualizing data redundancy with this express paced tool that will create a milieu of heightened data security within a few minutes.
Partial backup is another novel option that enables users to augment resource efficiency.
To provide you with cost and resource efficiency, this tool employs 3x data compression that allows you to squeeze in more data into your limited storage space.
Email backup is just one side of the coin when it comes to data security. End to end encryption is the other side of the coin that is a must to secure data distributed on various storage sites. This tool facilitates both and emerges as a data friendly solution.
A nice piece of information before taking a leave
If you want to take full advantage of this enlightening web space, then you must download the free demo of this tool, which will assist you in formulating the most effective email management strategy that actualizes both discrepancies-free data retention and impenetrable data security www.mailbackupx.com/imap-backup-tool/.
1 note
·
View note
Text
Web Application Penetration Testing Checklist
Web-application penetration testing, or web pen testing, is a way for a business to test its own software by mimicking cyber attacks, find and fix vulnerabilities before the software is made public. As such, it involves more than simply shaking the doors and rattling the digital windows of your company's online applications. It uses a methodological approach employing known, commonly used threat attacks and tools to test web apps for potential vulnerabilities. In the process, it can also uncover programming mistakes and faults, assess the overall vulnerability of the application, which include buffer overflow, input validation, code Execution, Bypass Authentication, SQL-Injection, CSRF, XSS etc.
Penetration Types and Testing Stages
Penetration testing can be performed at various points during application development and by various parties including developers, hosts and clients. There are two essential types of web pen testing:
l Internal: Tests are done on the enterprise's network while the app is still relatively secure and can reveal LAN vulnerabilities and susceptibility to an attack by an employee.
l External: Testing is done outside via the Internet, more closely approximating how customers — and hackers — would encounter the app once it is live.
The earlier in the software development stage that web pen testing begins, the more efficient and cost effective it will be. Fixing problems as an application is being built, rather than after it's completed and online, will save time, money and potential damage to a company's reputation.
The web pen testing process typically includes five stages:
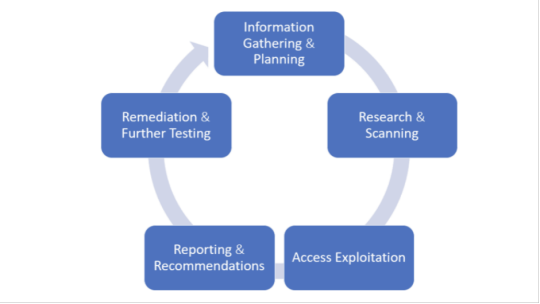
1. Information Gathering and Planning: This comprises forming goals for testing, such as what systems will be under scrutiny, and gathering further information on the systems that will be hosting the web app.
2. Research and Scanning: Before mimicking an actual attack, a lot can be learned by scanning the application's static code. This can reveal many vulnerabilities. In addition to that, a dynamic scan of the application in actual use online will reveal additional weaknesses, if it has any.
3. Access and Exploitation: Using a standard array of hacking attacks ranging from SQL injection to password cracking, this part of the test will try to exploit any vulnerabilities and use them to determine if information can be stolen from or unauthorized access can be gained to other systems.
4. Reporting and Recommendations: At this stage a thorough analysis is done to reveal the type and severity of the vulnerabilities, the kind of data that might have been exposed and whether there is a compromise in authentication and authorization.
5. Remediation and Further Testing: Before the application is launched, patches and fixes will need to be made to eliminate the detected vulnerabilities. And additional pen tests should be performed to confirm that all loopholes are closed.
Information Gathering

1. Retrieve and Analyze the robot.txt files by using a tool called GNU Wget.
2. Examine the version of the software. DB Details, the error technical component, bugs by the error codes by requesting invalid pages.
3. Implement techniques such as DNS inverse queries, DNS zone Transfers, web-based DNS Searches.
4. Perform Directory style Searching and vulnerability scanning, Probe for URLs, using tools such as NMAP and Nessus.
5. Identify the Entry point of the application using Burp Proxy, OWSAP ZAP, TemperIE, WebscarabTemper Data.
6. By using traditional Fingerprint Tool such as Nmap, Amap, perform TCP/ICMP and service Fingerprinting.
7.By Requesting Common File Extension such as.ASP,EXE, .HTML, .PHP ,Test for recognized file types/Extensions/Directories.
8. Examine the Sources code From the Accessing Pages of the Application front end.
9. Many times social media platform also helps in gathering information. Github links, DomainName search can also give more information on the target. OSINT tool is such a tool which provides lot of information on target.
Authentication Testing

1. Check if it is possible to “reuse” the session after Logout. Verify if the user session idle time.
2. Verify if any sensitive information Remain Stored in browser cache/storage.
3. Check and try to Reset the password, by social engineering crack secretive questions and guessing.
4.Verify if the “Remember my password” Mechanism is implemented by checking the HTML code of the log-in page.
5. Check if the hardware devices directly communicate and independently with authentication infrastructure using an additional communication channel.
6. Test CAPTCHA for authentication vulnerabilities.
7. Verify if any weak security questions/Answer are presented.
8. A successful SQL injection could lead to the loss of customer trust and attackers can steal PID such as phone numbers, addresses, and credit card details. Placing a web application firewall can filter out the malicious SQL queries in the traffic.
Authorization Testing

1. Test the Role and Privilege Manipulation to Access the Resources.
2.Test For Path Traversal by Performing input Vector Enumeration and analyze the input validation functions presented in the web application.
3.Test for cookie and parameter Tempering using web spider tools.
4. Test for HTTP Request Tempering and check whether to gain illegal access to reserved resources.
Configuration Management Testing
1. Check file directory , File Enumeration review server and application Documentation. check the application admin interfaces.
2. Analyze the Web server banner and Performing network scanning.
3. Verify the presence of old Documentation and Backup and referenced files such as source codes, passwords, installation paths.
4.Verify the ports associated with the SSL/TLS services using NMAP and NESSUS.
5.Review OPTIONS HTTP method using Netcat and Telnet.
6. Test for HTTP methods and XST for credentials of legitimate users.
7. Perform application configuration management test to review the information of the source code, log files and default Error Codes.
Session Management Testing
1. Check the URL’s in the Restricted area to Test for CSRF (Cross Site Request Forgery).
2.Test for Exposed Session variables by inspecting Encryption and reuse of session token, Proxies and caching.
3. Collect a sufficient number of cookie samples and analyze the cookie sample algorithm and forge a valid Cookie in order to perform an Attack.
4. Test the cookie attribute using intercept proxies such as Burp Proxy, OWASP ZAP, or traffic intercept proxies such as Temper Data.
5. Test the session Fixation, to avoid seal user session.(session Hijacking )
Data Validation Testing
1. Performing Sources code Analyze for javascript Coding Errors.
2. Perform Union Query SQL injection testing, standard SQL injection Testing, blind SQL query Testing, using tools such as sqlninja, sqldumper, sql power injector .etc.
3. Analyze the HTML Code, Test for stored XSS, leverage stored XSS, using tools such as XSS proxy, Backframe, Burp Proxy, OWASP, ZAP, XSS Assistant.
4. Perform LDAP injection testing for sensitive information about users and hosts.
5. Perform IMAP/SMTP injection Testing for Access the Backend Mail server.
6.Perform XPATH Injection Testing for Accessing the confidential information
7. Perform XML injection testing to know information about XML Structure.
8. Perform Code injection testing to identify input validation Error.
9. Perform Buffer Overflow testing for Stack and heap memory information and application control flow.
10. Test for HTTP Splitting and smuggling for cookies and HTTP redirect information.
Denial of Service Testing

1. Send Large number of Requests that perform database operations and observe any Slowdown and Error Messages. A continuous ping command also will serve the purpose. A script to open browsers in loop for indefinite no will also help in mimicking DDOS attack scenario.
2.Perform manual source code analysis and submit a range of input varying lengths to the applications
3.Test for SQL wildcard attacks for application information testing. Enterprise Networks should choose the best DDoS Attack prevention services to ensure the DDoS attack protection and prevent their network
4. Test for User specifies object allocation whether a maximum number of object that application can handle.
5. Enter Extreme Large number of the input field used by the application as a Loop counter. Protect website from future attacks Also Check your Companies DDOS Attack Downtime Cost.
6. Use a script to automatically submit an extremely long value for the server can be logged the request.
Conclusion:
Web applications present a unique and potentially vulnerable target for cyber criminals. The goal of most web apps is to make services, products accessible for customers and employees. But it's definitely critical that web applications must not make it easier for criminals to break into systems. So, making proper plan on information gathered, execute it on multiple iterations will reduce the vulnerabilities and risk to a greater extent.
1 note
·
View note
Text
A separate mac email tool for teams and individuals
Often mac users get confuse on the selection of a suitable restore mac email app for data backup. The confusion is outrage if you use the same tool for official or personal purpose. Although the propose of the tool remains the same, however it is very necessary to differentiate the tool on the basis of personal and official usage.
We deliver the right restore mac email software with two separate editions so that Mac users do not chose the incorrect tool for data backup. The requirements for individual and teams always differ and so also differs the selection of the tool for the purpose.
We have solved this problem with the help of Mail Backup X, a perfect answer to restore email mac mails for personal and official usage.
While there is more to discuss on how both the packages differ from one another, we also recommend the below two links to be browsed for more information on Apple and Mail OS.
https://en.wikipedia.org/wiki/MacOS
https://en.wikipedia.org/wiki/Apple_Mail
Since the complete exercise is about restore mac mail, it is always advantageous to study more about Apple mail and Mac operating system. It also facilitates the selection of the right tool considering different particulars for email communication.
The best way to restore mac email with team and individual edition
1. Individual edition
The tool archives emails from major mail clients like Apple Mail, Microsoft Outlook, Office 365, Microsoft Exchange, Thunderbird, PostBox, and online mail services like Gmail, Yahoo, Gmx.de any service supporting IMAP Protocol.
Quickly search emails from the archive folder using inbuilt mail viewer.
Saves more space with highly compressed archives
Import mail archives files like .pst, .ost, .mbox, .olk, .eml, .rge etc. and includes in all in one ail converter.
Set a mirror backup to cloud storage.
Encrypt your data with a private key so that the data is only visible to you.
2. Team edition
The tool executes backup of emails, contacts, & calendar for all team members.
The tool ensures to send notifications alerts in Admin dashboard if the mail backup goes offline for team members.
Archives emails from major mail clients like Apple Mail, Microsoft Outlook, Office 365, Microsoft Exchange, Thunderbird, PostBox, and online mail services like Gmail, Yahoo, Gmx.de any service supporting IMAP Protocol.
The tool uses patent-pending serverless logic as it sets cloud spaces by adding google drive, one drive, dropbox, FTP accounts. It uploads all back up data to admin specified cloud spaces.
Quickly search emails from the archive folder using inbuilt mail viewer.
The tool import or export to any mail archive archive files like .pst, .ost, .mbox, .olk, .eml, .rge.
Both versions of the tool makes sure to restore mac email addresses irrespective of the number of team members.
An easy approach to learn how to restore mac emails
The easiest way to know about restoring of mac emails is through the trial version. The trial version is easy to install and use for a period of two weeks, after which, you can switch to the licensed product.
Browse the below link for more information on the restore mac email software. https://www.mailbackupx.com/restore-mac-email/
1 note
·
View note
Text

Best IMAP Email Backup Software Users can easily Backup IMAP Mail Folder to MBOX using eSoftTools IMAP Backup and Migration software. It offers many features to export IMAP email files and also provides a smart feature to export files with specific and selected dates. The software comes with a clean graphic interface and the software offers a free demo trial, users can export 25 mails using the demo feature.
visit more -
#imap backup tool#imap migration tool#backup imap emails#imap to office 365#imap to gmail#imap downloader
1 note
·
View note
Text
Login Hotmail with Hotmail cellular utility

Outlook.Com (Hotmail) has a mobile application that you could set up for your device, be it Android or iOS. Here are the www.hotmail.com stairs to log in from the legit Outlook application.
Download the application from the corresponding store. Android app iOS app Once hooked up, get right of entry to it and press the " Introduction " button. In the " Add account " section, enter the Outlook e-mail deal with that you have registered, then press "Continue". This utility additionally supports e-mail from different carriers like Yahoo or Gmail. Enter the password on your e mail account, then press "Sign in." If you don't need to add every other account, press "Skip". Voila! You will see your Outlook inbox from the software.
Hotmail-login-mobile After including your Outlook or Hotmail account to the reliable application, it's miles recommended that you activate the notifications to be aware of all of the emails that arrive to your inbox. It is likewise feasible to open your e-mail without delay from the cellular browser, via coming into the cope with outlook.Com in your chosen browser.
Benefits of Hotmail application Free and loose get right of entry to to all Microsoft equipment Windows navigation centers Simple backup with Windows Phone Possibility to speak with friends and family immediately by e mail on the mobile telephone
Can get admission to even offline, examine and kind texts There is every other 15GB of facts upload available through Onedrive. Your messages are notified via your cell smartphone in case you enter something new within the entry field Access to the Outlook calendar to organize your contacts and to-do list Chat to speak with different users while not having to hook up with every other device
Automatic connection thru your inbox with social media A new message can be regarded even supposing there is no connection to mobile facts or wifi as it is updated at the cellular cellphone If you want to shop things on your OneDrive but you have no net at the moment simply upload it and the instant you've got a connection the down load might be entire without having to copy the operation It lets in clean verbal exchange without delay out of your account or just by using coming into without delay, right now.
Access Hotmail with 1/3-party mail provider If you need your Outlook electronic mail account on a third-birthday party consumer developer, inclusive of Thunderbird o Apple Mail? In this example, if you have issue signing in, attempt to configure the mailbox "manually", using the following IMAP parameters. Server Name: Outlook.Office365.Com IMAP Port: 993 IMAP Encryption Method: TLS Server Name: SMTP.Office365.Com Animal: 587 Encryption Method: STARTTLS For greater records, go to the Microsoft internet site.
1 note
·
View note
Text
Gmail Backup Software
Get the safe and secure backup tool to take the instant backup of all Gmail emails in your local system or hard-drive. It facilitates to import Gmail to IMAP account directly.
Explore more about this at:- https://tinyurl.com/y5vyg42q

1 note
·
View note