#Implications of technology on healthcare privacy and security
Text
Unveiling the Future: A Deep Dive into Emerging Technologies and Their Influence on Industries and Everyday Life
In an era of rapid technological advancement, emerging technologies like artificial intelligence (AI), the Internet of Things (IoT), and blockchain are revolutionizing industries and transforming the way we live and work. In this blog post, we will delve into these cutting-edge technologies, their potential applications, and the profound impact they have on various sectors and our daily…
View On WordPress
#Artificial intelligence (AI)#Blockchain technology#Connected vehicles#Creating new possibilities#Data security#Efficiency in manufacturing#Emerging technologies#Ethical implications#Future possibilities#Healthcare diagnostics#Improving efficiency#Innovations in industries#Internet of Things (IoT)#Potential applications#Privacy concerns#Profound impact#Real-life examples#Responsible use of data#Revolutionizing industries#Smart cities#Streamlining processes#Success stories#Supply chain traceability#Sustainable future#Tangible benefits#Transforming daily life#Trust and transparency
1 note
·
View note
Text
Angelica Purugganan
9-musgravite
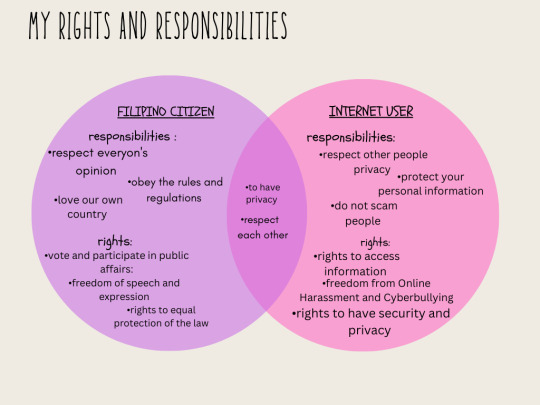
how can you observe social, ethical, and legal responsibilties in the use of technology tools and resources?
Observing social, ethical, and legal responsibilities in the use of technology tools and resources is crucial to ensure the responsible and appropriate application of technology. Here are some guidelines to help you navigate these responsibilities:
1. Social Responsibility:
- Consider the impact of technology on society: Evaluate how technology tools and resources can affect individuals, communities, and society as a whole. Anticipate and mitigate any potential negative consequences.
- Promote digital literacy: Encourage education and awareness about responsible technology use. Help bridge the digital divide by providing access to technology and teaching essential digital skills.
- Foster digital inclusion: Ensure that technology is accessible and available to all individuals, regardless of their socioeconomic background or geographical location.
- Support ethical technology initiatives: Contribute to projects and initiatives that aim to develop and utilize technology for social good, such as using technology to address environmental challenges, promote equality, or enhance healthcare.
2. Ethical Responsibility:
- Consider the ethical implications of emerging technologies: Stay informed about the latest technological advancements and assess their potential ethical implications. Examples include artificial intelligence, machine learning, genetic engineering, and virtual reality.
- Foster transparency and accountability: Advocate for transparency in the development and deployment of technology. Encourage organizations to disclose information about their algorithms, data practices, and decision-making processes.
- Encourage ethical design and development practices: Promote the integration of ethical considerations into the design, development, and deployment of technology. This includes factors such as user privacy, security, and the avoidance of bias and discrimination.
- Engage in ethical data practices: Handle data responsibly, ensuring that it is collected, processed, and stored securely. Use data for legitimate purposes and obtain explicit consent when necessary. Anonymize or de-identify data when possible to protect individual privacy.
3. Legal Responsibility:
- Comply with applicable laws and regulations: Stay updated on the legal requirements related to technology use, including data protection, cybersecurity, intellectual property, and online behavior. Ensure that your actions and use of technology are in accordance with these laws.
- Secure intellectual property rights: Respect intellectual property laws and protect your own intellectual property. Obtain proper licenses, permissions, or copyrights for any content or software you use or distribute.
- Be aware of jurisdictional differences: Recognize that technology-related laws may vary across different countries and jurisdictions. If you operate internationally, familiarize yourself with the legal requirements of the regions you engage with.
By integrating social, ethical, and legal responsibilities into your use of technology, you can contribute to a more responsible and sustainable digital ecosystem.
2 notes
·
View notes
Text
Top 10 Information Technology Advances in 2022
Technology trends are those that are expected to have an impact on business in the next decade or so. As per John Patrick Moglia, these trends will cause complete transformations in businesses. Adoption of 5G network technologies, for example, is expected to increase by 40% by 2024. Companies will use 5G networks to handle 25% of all mobile traffic. To prepare for this new technology, businesses must consider the strategies that will allow them to compete in the future.
One of the most popular technological trends in recent years has been the Internet of Things. The concept of the Internet of Things, or IOT, is that all technological devices can be connected to the internet. As a result, virtually any physical object can be linked to the digital world. This has implications for a wide range of industries, including manufacturing, energy, and utilities. IoT can provide businesses with a wealth of data that can be used to optimize marketing campaigns and improve user experience.
As a result of these trends, businesses should work to incorporate AI into their operations. They should also strive for "full stack" programmability. Companies should improve the privacy and security of their data by doing so. Companies that ignore artificial intelligence risk becoming irrelevant and obsolete. Although the first 5G-enabled devices will connect to the network in 2019, they will be far from ubiquitous. The main barriers to this expansion in previous years were inadequate infrastructure and a lack of compatible devices. These handsets are becoming more widely available.
According to John Patrick Moglia, artificial intelligence has gotten a lot of attention over the last decade and is still one of the most exciting technology trends. Artificial intelligence is already being used in navigation apps, smartphone personal assistants, and ride-sharing services. AI will eventually be used to analyze interactions and connections, predict service demand, and improve customer experience. AI has enormous potential. This technology will be widely used by 2022 and will benefit a wide range of industries.
Digital ecosystems will be a significant force in the next decade, regardless of industry. They will cover key functions in the insurance, manufacturing, semiconductor, and transportation industries. According to McKinsey, healthcare spending could exceed USD 250 billion during this period. The importance of adopting new technologies for businesses should not be underestimated. So, what are the most important technological trends? They will be the ones to shape our future.
Smart vision systems, video analytics, and additive manufacturing are just a few of the technologies that ARC Advisory Group will be keeping an eye on. These technologies have the potential to transform the modern workplace in unprecedented ways. Organizations can avoid the worst-case scenarios of disruption by understanding the implications of these emerging technologies. Artificial intelligence, robots, and machine learning are examples of these technologies. Virtualization and next-generation automation are also critical for the future of work. They are changing how we live, work, and play.
Technology trends are rapidly changing. Enterprises can gain a competitive advantage by staying up to date on the latest trends. Keeping up with new technologies will not only help their organizations remain competitive, but will also allow them to launch new products and improve customer service. It will also enable businesses to analyze large data sets using cloud-based computing resources. Finally, cloud-native insurers will be better positioned to serve as ecosystem orchestrators, connecting hubs for a wide range of stakeholders.
For many years, virtual reality has been an important component of video games. It is now likely to have a significant impact on businesses across industries. Virtual reality can be a powerful tool for engaging customers, increasing marketing efforts, and educating employees. Even educational institutions have begun to use virtual reality. If you want to learn about new technologies, it may be time to invest in VR technology. It's not surprising that businesses will begin experimenting with virtual reality.
By 2030, there will be 50 billion connected devices in use. This will result in the formation of a global network of interconnected devices. As shown by John Patrick Moglia, global spending on IoT will reach 1.1 trillion US dollars by 2022. As 5G technology becomes more widely available, this market will expand even faster. If they want to work in IoT, interested parties should start learning about AI and cybersecurity basics. Finally, this new industry has a promising future.
While big data technologies are becoming more common in business, they are also finding use in the banking and financial industries. With billions of dollars changing hands every day, financial institutions face the daunting task of processing massive amounts of data. To discover patterns and develop predictive strategies, financial analysts must first understand the data. Unstructured datasets are difficult to analyze by hand, but big data technologies are making it easier and faster than ever before. These changes are expected to have a significant impact on business operations.
2 notes
·
View notes
Text
Navigating the intersection of technology and responsibility in AI-generated video content
In the ever-evolving landscape of digital media, the rise of artificial intelligence (AI) has ushered in a new era of creativity and convenience. From generating personalized recommendations on streaming platforms to enhancing video content creation, AI has permeated various facets of our digital experiences. However, as AI continues to advance, questions surrounding its ethical implications and responsibilities emerge, particularly concerning AI-generated video content. In this blog, we delve into the intricate intersection of technology and responsibility in the realm of AI-generated video content, exploring its potential, challenges, and the imperative need for ethical guidelines.
The evolution of AI in video content creation:
The journey of AI in video content creation is nothing short of revolutionary. Gone are the days when video editing and special effects were confined to skilled professionals with expensive software. Today, AI-powered tools enable individuals with minimal technical expertise to produce captivating videos effortlessly. From deep learning algorithms capable of generating realistic human faces to AI-driven voice synthesis for dubbing, the possibilities seem endless.
One of the most notable advancements is the emergence of deepfake technology. Leveraging deep learning techniques, deepfake algorithms can seamlessly superimpose one person’s likeness onto another’s, creating hyper-realistic videos that blur the line between fact and fiction. While initially captivating for their novelty, deepfakes have raised significant concerns regarding misinformation, identity theft, and privacy infringement.
The promise and peril of AI-Generated video content:
At its core, AI-generated video content holds immense promise for various industries. From entertainment and marketing to education and healthcare, the ability to automate and enhance video production processes has the potential to revolutionize how we engage with media. For content creators, AI tools offer unprecedented efficiency, enabling them to streamline workflows and unlock new creative possibilities.
However, the proliferation of AI-generated video content also brings forth a myriad of ethical dilemmas and risks. The democratization of video manipulation tools means that malicious actors can weaponize AI to spread disinformation, manipulate public opinion, and undermine trust in media. Moreover, the uncanny realism of deepfakes poses a significant threat to individual privacy and security, as anyone can be digitally impersonated with alarming accuracy.
Addressing moral and legal concerns:
As AI-generated video content becomes increasingly prevalent, it is imperative to establish robust ethical and legal frameworks to govern its responsible use. While technological innovation should be encouraged, it must not come at the expense of ethical principles and societal well-being. Addressing the ethical considerations surrounding AI-generated video content requires a multi-faceted approach, encompassing technological, regulatory, and societal dimensions.
One crucial aspect is transparency. Content creators and platforms must be transparent about the use of AI in video production, clearly disclosing when AI-generated elements are present. This transparency not only fosters trust but also empowers consumers to make informed decisions about the content they consume. Additionally, establishing clear guidelines for the responsible creation and dissemination of AI-generated content is paramount.
From a legal perspective, the regulatory landscape surrounding AI-generated video content is still in its nascent stages. Existing laws and regulations may not adequately address the unique challenges posed by deepfakes and other AI-generated content. Policymakers must work collaboratively with industry stakeholders to develop comprehensive legislation that balances innovation with safeguards against misuse. This may include measures such as liability frameworks for AI-generated content creators and platforms, as well as enhanced privacy protections for individuals depicted in AI-generated videos.
Moreover, fostering digital literacy and critical thinking skills is essential in combating the spread of misinformation facilitated by AI-generated video content. By equipping individuals with the tools to discern fact from fiction and detect manipulative media, we can mitigate the harmful effects of disinformation campaigns and safeguard the integrity of public discourse.
The role of technology in mitigating risks:
While technology has played a significant role in enabling the creation of AI-generated video content, it also holds the key to mitigating its associated risks. Advancements in AI-driven detection and verification technologies offer promising solutions for identifying and flagging manipulated media. Machine learning algorithms can be trained to detect subtle artifacts indicative of deepfake manipulation, enabling platforms to implement proactive measures to curb their spread.
Moreover, the development of blockchain-based solutions holds promise for establishing provenance and authenticity in digital media. By leveraging blockchain technology to create immutable records of content creation and distribution, we can enhance accountability and traceability in the digital ecosystem. This can help deter malicious actors from engaging in deceptive practices while providing assurance to consumers regarding the authenticity of the content they consume.
Collaboration across stakeholders:
Addressing the complex challenges posed by AI-generated video content requires collaboration and collective action across stakeholders. Content creators, technology companies, policymakers, academia, and civil society must come together to develop holistic strategies for promoting ethical standards and responsible practices. Interdisciplinary research initiatives can drive innovation in AI detection and verification technologies, while industry partnerships can facilitate the development of best practices and standards for AI-generated content creation.
Moreover, fostering open dialogue and knowledge-sharing platforms can promote awareness and understanding of the ethical implications surrounding AI-generated video content. By engaging in transparent and inclusive discussions, we can foster a culture of responsible innovation that prioritizes ethical considerations and societal impact.
Conclusion:
As we navigate the intersection of technology and responsibility in AI-generated video content, we are faced with both unprecedented opportunities and formidable challenges. While AI holds the potential to revolutionize how we create, consume, and interact with video media, it also presents ethical dilemmas and risks that demand careful consideration. By embracing transparency, accountability, and collaboration, we can harness the power of AI while safeguarding against its potential misuse. Together, let us strive to build a future where technology serves as a force for good, enriching our lives and empowering us to navigate the digital landscape with confidence and integrity.
0 notes
Text
The Rise of Artificial Intelligence: Transforming Industries and Shaping the Future

The Impact of AI on Various Sectors and Society as a Whole
In recent years, artificial intelligence (AI) has emerged as one of the most transformative technologies of our time. From self-driving cars to virtual assistants, AI is revolutionizing industries and reshaping the way we live and work. This article delves into the various sectors that have been impacted by AI and explores the implications for society as a whole.
As AI continues to advance at an unprecedented pace, it is crucial to understand its potential and the challenges it presents. From healthcare to finance, education to manufacturing, AI is disrupting traditional processes and opening up new possibilities. However, it also raises concerns about job displacement, privacy, and ethical considerations.
By exploring the current landscape and future prospects, we can gain a deeper understanding of the rise of AI and its impact on our world.
youtube
Healthcare: Revolutionizing Diagnosis and Treatment
AI has made significant strides in the field of healthcare, revolutionizing the way diseases are diagnosed and treated. Machine learning algorithms can analyze vast amounts of medical data, enabling more accurate and timely diagnoses. For example, AI-powered systems can detect early signs of diseases such as cancer, allowing for early intervention and improved patient outcomes.
Furthermore, AI is transforming the way surgeries are performed. Robots equipped with AI capabilities can assist surgeons in complex procedures, enhancing precision and reducing the risk of human error. AI-powered chatbots are also being used to provide personalized healthcare advice and support, improving patient engagement and access to medical information.
Finance: Enhancing Efficiency and Risk Management
In the financial sector, AI is revolutionizing the way transactions are conducted and risks are managed. Machine learning algorithms can analyze large volumes of financial data in real-time, enabling more accurate predictions and faster decision-making. This has led to the development of automated trading systems that can execute trades based on complex algorithms.
AI is also being used to detect fraudulent activities and prevent financial crimes. By analyzing patterns and anomalies in financial transactions, AI-powered systems can identify potential risks and alert authorities. This not only enhances security but also reduces the financial losses associated with fraud.
Education: Personalizing Learning Experiences
In the field of education, AI is transforming the way students learn and teachers teach. Adaptive learning platforms powered by AI can personalize the learning experience, tailoring content and pace to individual student needs. This ensures that students receive the support and resources they require to succeed.
AI-powered virtual tutors and chatbots are also being used to provide instant feedback and answer student queries. This not only improves student engagement but also frees up teachers' time, allowing them to focus on more personalized instruction.
Manufacturing: Enhancing Efficiency and Automation
In the manufacturing industry, AI is driving efficiency and automation. Robots equipped with AI capabilities can perform complex tasks with precision and speed, reducing human error and increasing productivity. AI-powered systems can also analyze production data in real-time, optimizing processes and reducing downtime.
Furthermore, AI is enabling predictive maintenance, where machines can detect potential faults and schedule maintenance before breakdowns occur. This not only reduces costs but also minimizes disruptions in the production process.
Transportation: Revolutionizing Mobility and Safety
In the transportation sector, AI is revolutionizing mobility and safety. Self-driving cars powered by AI algorithms are being developed and tested, promising to reduce accidents and congestion on the roads. AI can analyze real-time traffic data, optimizing routes and reducing travel time.
AI-powered systems are also being used to enhance public transportation systems, improving efficiency and reducing carbon emissions. For example, AI can predict demand patterns and adjust public transportation schedules accordingly, ensuring optimal service for commuters.
The rise of artificial intelligence is transforming industries and shaping the future in profound ways. From healthcare to finance, education to manufacturing, AI is revolutionizing traditional processes and opening up new possibilities. However, it also raises concerns about job displacement, privacy, and ethical considerations.
As we navigate this AI-driven world, it is crucial to strike a balance between harnessing the potential of AI and addressing the challenges it presents. By understanding the impact of AI on various sectors and society as a whole, we can navigate this transformative era and shape a future that benefits all.
0 notes
Text
Top 10 Political Trends Shaping Policy in 2024
As we navigate the complexities of the political landscape in 2024, several key trends emerge that are significantly influencing policy decisions around the globe. From shifts in geopolitical dynamics to advancements in technology, here are the top 10 political trends shaping policy this year:
Global Health Security: The ongoing COVID-19 pandemic continues to reshape healthcare policies worldwide, emphasizing the importance of preparedness, vaccination strategies, and international cooperation in combating infectious diseases.
Climate Action and Sustainability: Heightened awareness of climate change has propelled governments to prioritize sustainability initiatives, with policies focusing on renewable energy adoption, carbon neutrality targets, and adaptation measures becoming increasingly prevalent.
Digital Transformation: Accelerated by the pandemic, the digital transformation of societies has prompted governments to enact policies addressing cybersecurity, data privacy, digital infrastructure, and the regulation of emerging technologies like artificial intelligence and blockchain.
Geopolitical Realignment: Shifts in global power dynamics, including the rise of China, changing alliances, and geopolitical tensions, are shaping policy responses in areas such as trade, defense, and foreign relations, influencing regional stability and security.
Social Justice and Equity: Heightened awareness of systemic inequalities has led to calls for policy reforms addressing issues such as racial justice, income inequality, gender equality, and social welfare, with a focus on fostering inclusive societies.
Demographic Shifts and Migration: Changing demographics, including aging populations and migration patterns, are driving policy discussions on healthcare systems, labor markets, immigration policies, and cultural integration, shaping societal cohesion and diversity.
Economic Recovery and Resilience: Governments are implementing policies to stimulate economic recovery following the pandemic-induced recession, emphasizing job creation, investment in infrastructure, support for small businesses, and sustainable economic growth strategies.
Digital Governance and Regulation: Policymakers are grappling with the challenges of regulating digital platforms, addressing misinformation, ensuring data protection, and balancing freedom of expression with the need to combat online harms, reshaping the digital governance landscape.
Healthcare Reform and Access: The pandemic has underscored the importance of accessible and resilient healthcare systems, prompting discussions on healthcare reform, universal healthcare coverage, pharmaceutical regulations, and the equitable distribution of medical resources.
Democratic Backsliding and Authoritarianism: Concerns about democratic erosion, including the rise of authoritarian regimes, erosion of civil liberties, and threats to democratic norms and institutions, are driving policy responses focused on defending democracy, safeguarding human rights, and promoting democratic governance.
As policymakers grapple with these pressing issues, the decisions they make in 2024 will have far-reaching implications for societies, economies, and the global community as a whole. By staying informed and engaged, we can contribute to shaping a more just, sustainable, and resilient future.
1 note
·
View note
Text
what is vpn china
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is vpn china
Chinese VPN laws
Chinese VPN laws have been a topic of debate and concern for many internet users in China and around the world. Virtual Private Networks (VPNs) are commonly used in China to bypass the country's strict internet censorship and access content that is otherwise restricted. However, the Chinese government has implemented various laws and regulations to control the use of VPNs within the country.
In 2017, China passed a controversial cybersecurity law that requires all VPN providers operating in the country to obtain a government-issued license. This law also prohibits individuals and companies from using VPNs that are not approved by the government. This has led to many popular VPN services being blocked in China, making it increasingly difficult for internet users to circumvent the Great Firewall.
Despite the restrictions, many Chinese citizens still rely on VPNs to access foreign websites and services that are blocked in the country. Some users choose to use overseas VPN services to avoid detection, while others risk using unauthorized VPNs despite the legal implications.
The Chinese government's crackdown on VPN usage is seen as part of its larger efforts to control online content and maintain its grip on internet freedom. While VPNs can offer a lifeline for users seeking unrestricted internet access, navigating the complex and ever-changing Chinese VPN laws remains a challenge for many. As technology continues to evolve, the battle between censorship and freedom of information in China is likely to persist.
Encryption in China
Encryption in China: Balancing Security and Control
Encryption technology plays a crucial role in safeguarding sensitive information in today's digital age, and China, with its rapidly growing technological landscape, is no exception. However, the Chinese government's approach to encryption reflects a delicate balance between security and control.
On one hand, encryption is recognized as a vital tool for protecting sensitive data from cyber threats and ensuring the privacy of individuals and businesses. Chinese companies, especially those operating in sectors such as finance, healthcare, and e-commerce, rely heavily on encryption to secure their communications and transactions. Moreover, encryption is essential for safeguarding state secrets and sensitive government information.
On the other hand, the Chinese government maintains strict control over encryption technologies to prevent misuse and maintain social stability. This control is evident in regulations requiring companies to register their encryption products and services with government authorities. Additionally, there are concerns about the government's ability to access encrypted data for surveillance purposes, leading to debates about the balance between security and privacy.
Despite these challenges, China has made significant strides in advancing encryption technologies. The country boasts several leading encryption firms and researchers who are at the forefront of developing innovative solutions to address cybersecurity threats. Furthermore, initiatives such as the National Encryption Management Committee demonstrate the government's commitment to promoting the responsible use of encryption while mitigating potential risks.
In conclusion, encryption plays a vital role in China's cybersecurity strategy, balancing the need for security with the government's desire for control. As technology continues to evolve, finding the right balance between these competing interests will remain a complex challenge for policymakers and industry stakeholders alike.
Great Firewall bypass
Title: Breaking Barriers: How to Bypass the Great Firewall of China
The Great Firewall of China is a formidable barrier that restricts access to many websites and online services outside the country. For individuals and businesses operating in or traveling to China, this censorship can pose significant challenges. However, there are methods available to bypass the Great Firewall and regain access to the global internet.
One commonly used technique is the use of virtual private networks (VPNs). VPNs encrypt your internet traffic and route it through servers located outside of China, effectively masking your true location and allowing you to access blocked content. There are many VPN providers available, both free and paid, offering varying levels of security and performance. It's essential to choose a reputable VPN provider with a strong track record of bypassing censorship.
Another method to bypass the Great Firewall is the use of proxy servers. Proxy servers act as intermediaries between your device and the internet, allowing you to access blocked content by routing your traffic through a server located outside of China. However, it's crucial to use proxies from trusted sources, as some may compromise your privacy or security.
Additionally, utilizing alternative DNS services can sometimes circumvent censorship. By changing your device's DNS settings to use a DNS server located outside of China, you may be able to access blocked websites and services directly, without the need for a VPN or proxy.
It's important to note that bypassing the Great Firewall may violate Chinese laws and regulations, so proceed with caution and be aware of the potential consequences. Additionally, the effectiveness of these methods may vary over time as the Chinese government updates its censorship tactics. Always stay informed and employ multiple strategies to ensure reliable access to the open internet while in China.
VPN services in China
In China, accessing the internet without encountering restrictions or censorship can be a challenging task due to the Great Firewall. However, Virtual Private Network (VPN) services offer a solution to bypass these limitations and ensure secure internet access for users within the country.
VPN services in China play a crucial role in circumventing the government-imposed restrictions on websites and online content. By encrypting internet traffic and rerouting it through servers located outside of China, VPNs enable users to access blocked websites and services such as Google, Facebook, Twitter, and various international news outlets.
One of the key considerations when choosing a VPN service in China is reliability. Since the Chinese government actively monitors and blocks VPN connections, it's essential to select a VPN provider with robust technology and infrastructure capable of evading detection and maintaining consistent access.
Additionally, privacy and security are paramount concerns when using VPNs in China. Users must opt for VPN services that offer strong encryption protocols, a strict no-logs policy, and features such as a kill switch to prevent data leaks in case of connection drops.
Furthermore, speed is a critical factor to consider, as VPNs can sometimes result in slower internet connections due to the encryption and rerouting processes. Selecting a VPN provider with a large server network and optimized servers for China can help mitigate this issue and ensure a smoother browsing experience.
In conclusion, VPN services play a vital role in providing unrestricted and secure internet access for users in China. By choosing a reliable VPN provider with robust security features and optimized servers, individuals can enjoy online freedom while protecting their privacy and data from government surveillance.
Internet censorship in China
Internet censorship in China is a prevalent and strictly enforced practice that significantly restricts the information accessible to Chinese citizens online. The Chinese government employs a combination of technological tools, legislation, and regulations to control and monitor the flow of information on the internet within the country.
The Great Firewall of China, officially known as the Golden Shield Project, is a sophisticated system of internet censorship that blocks access to foreign websites, social media platforms, and news outlets deemed politically sensitive or harmful to the Communist Party's interests. Popular websites and services like Google, Facebook, Twitter, and YouTube are inaccessible in China without the use of virtual private networks (VPNs) to bypass the firewall.
In addition to blocking foreign websites, the Chinese government also monitors domestic online content through the "50 Cent Party," internet trolls who post pro-government comments and censor critical viewpoints on social media platforms. Online surveillance and censorship are further reinforced by stringent laws and regulations that require internet companies to censor user-generated content and store data within China's borders.
Despite these strict measures, some Chinese citizens continue to circumvent censorship to access blocked content and express dissenting opinions online. However, these individuals face the risk of being monitored, arrested, or prosecuted for violating internet regulations.
Internet censorship in China raises concerns about freedom of expression, privacy rights, and access to information. As technology continues to evolve, the cat-and-mouse game between internet users and censors in China is likely to persist, highlighting the ongoing challenges of navigating the heavily controlled online landscape in the country.
0 notes
Text
what does using a vpn protect you from
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what does using a vpn protect you from
Geo-blocking evasion
Geo-blocking evasion refers to the act of bypassing restrictions set by websites or online services that limit access based on a user's geographical location. This practice has gained popularity as individuals seek to access content, products, or services that may be restricted or limited in their region. Geo-blocking is often implemented by websites or streaming platforms to comply with licensing agreements, protect copyright, or control distribution.
There are various methods that can be used to evade geo-blocking restrictions. One common way is by using Virtual Private Networks (VPNs) which allow users to mask their actual location by connecting to servers in different countries. By doing so, users can trick websites into believing they are accessing the content from an allowed location, thus gaining access to geo-blocked services.
Another method to evade geo-blocking is by using proxy servers or smart DNS services. These tools can help users reroute their internet traffic through servers located in authorized regions, effectively bypassing geo-restrictions.
It's important to note that while geo-blocking evasion may allow users to access restricted content, it may violate the terms of service of the website or platform. Users should be aware of the legal implications of bypassing geo-blocks and ensure they are not infringing on any copyrights or licensing agreements.
Overall, the practice of geo-blocking evasion has become a popular way for individuals to access global content and services, despite restrictions based on their geographical location. As technology continues to advance, users may continue to find new and innovative ways to bypass geo-blocks and access the content they desire.
Data encryption
Data encryption is a critical component of cybersecurity, serving as a safeguard for sensitive information in digital communications and storage. Encryption involves converting data into an unreadable format using algorithms, making it accessible only to those with the corresponding decryption key. This process ensures confidentiality and privacy, thwarting unauthorized access and potential breaches.
One of the primary methods of encryption is known as symmetric key encryption, where both the sender and the recipient share the same key to encode and decode messages. While effective, this approach requires a secure method for key exchange to prevent interception by malicious actors.
Another widely used encryption method is asymmetric key encryption, which employs a pair of keys: a public key for encryption and a private key for decryption. This eliminates the need for key exchange, as the public key can be freely distributed while the private key remains confidential. This method is commonly used in secure communication protocols such as SSL/TLS for encrypting internet traffic.
Data encryption plays a crucial role in various sectors, including finance, healthcare, and government, where protecting sensitive information is paramount. It helps organizations comply with regulations such as GDPR and HIPAA by ensuring data confidentiality and integrity.
However, while encryption provides robust protection against unauthorized access, it is not immune to vulnerabilities. Implementation flaws, weak algorithms, and inadequate key management can undermine encryption's effectiveness, leaving data vulnerable to exploitation.
In conclusion, data encryption is a fundamental tool in cybersecurity, safeguarding sensitive information from unauthorized access and potential breaches. By employing strong encryption methods and implementing robust key management practices, organizations can enhance their security posture and mitigate the risks associated with data compromise.
IP address masking
IP address masking is a technique used to protect a user's privacy and security while browsing the internet. When you connect to the internet, your device is assigned a unique identifier called an IP address, which can reveal your location and browsing activities. IP address masking helps to shield this information by disguising your real IP address with a different one.
There are several methods to mask your IP address, including proxy servers, virtual private networks (VPNs), and the Tor network. Proxy servers act as intermediaries between your device and the internet, masking your IP address and routing your internet traffic through different servers. VPNs encrypt your internet connection and route it through a remote server, hiding your IP address and making your online activities anonymous. The Tor network bounces your internet traffic through a series of relays, obscuring your IP address and enhancing your privacy.
IP address masking is commonly used to bypass geo-restrictions, access region-locked content, and protect against online tracking. By concealing your real IP address, you can prevent websites, advertisers, and hackers from tracking your online behavior and stealing your personal information. It also allows you to access websites and services that may be blocked in your region due to censorship or licensing restrictions.
Overall, IP address masking is a valuable tool for safeguarding your online privacy and security. Whether you are concerned about government surveillance, data breaches, or invasive tracking, masking your IP address can help you browse the internet anonymously and protect your sensitive information.
Cybersecurity threats prevention
Title: Safeguarding Your Digital Realm: Preventing Cybersecurity Threats
In today's interconnected digital landscape, cybersecurity threats loom large, posing significant risks to individuals, businesses, and governments alike. From data breaches to malware attacks, the potential vulnerabilities are manifold. However, proactive measures can be taken to fortify defenses and mitigate the risks associated with cyber threats.
One of the fundamental pillars of cybersecurity is education. Ensuring that individuals and employees are aware of common tactics used by cybercriminals, such as phishing emails and social engineering schemes, can significantly reduce the likelihood of falling victim to an attack. Regular training sessions and awareness campaigns can empower individuals to recognize and respond appropriately to potential threats.
Implementing robust security protocols and leveraging advanced technologies are also essential components of a comprehensive cybersecurity strategy. This includes utilizing firewalls, antivirus software, and intrusion detection systems to safeguard networks and sensitive information from unauthorized access. Additionally, employing encryption techniques can help protect data both in transit and at rest, further enhancing security measures.
Regularly updating software and systems is another critical aspect of cybersecurity prevention. Patching known vulnerabilities can close entry points that cybercriminals may exploit to gain access to networks and devices. Moreover, maintaining strong password practices, such as using complex combinations of characters and implementing multi-factor authentication, can add an extra layer of security against unauthorized access.
Collaboration within the cybersecurity community is paramount in staying ahead of emerging threats. Sharing information and best practices among industry peers and participating in threat intelligence networks can provide valuable insights into evolving cyber threats and effective mitigation strategies.
By adopting a proactive approach to cybersecurity, individuals and organizations can better protect themselves against the ever-evolving landscape of cyber threats. Through education, technology, and collaboration, we can collectively strengthen our defenses and safeguard the integrity of our digital realm.
Internet surveillance evasion
Internet surveillance evasion has become a pressing concern in today's digital age, with individuals and organizations increasingly seeking ways to protect their online privacy and data from prying eyes. The practice of evading internet surveillance involves taking proactive measures to prevent government agencies, hackers, or other third parties from monitoring online activities and accessing sensitive information.
One of the most common methods of evading internet surveillance is using virtual private networks (VPNs). VPNs encrypt internet traffic and mask users' IP addresses, making it difficult for anyone to track their online movements. By routing internet connections through remote servers, VPNs provide a secure and anonymous browsing experience, safeguarding users from surveillance and potential cyber threats.
Another effective way to avoid internet surveillance is through the use of anonymous browsing tools such as Tor (The Onion Router). Tor routes internet traffic through a series of volunteer-operated servers, masking users' identities and making it nearly impossible to trace their online activities. While Tor may slow down browsing speeds, it offers a high level of anonymity and security for individuals seeking to evade surveillance.
In addition to VPNs and anonymous browsing tools, individuals can also enhance their online privacy through secure messaging apps, encryption software, and regularly updating their device's security settings. By adopting a proactive stance towards internet surveillance evasion, individuals can better protect their personal data and privacy rights in an increasingly interconnected world.
0 notes
Text
does usa require vpn companies to log data
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does usa require vpn companies to log data
USA VPN regulations
In recent years, the topic of VPN regulations in the USA has garnered significant attention. VPNs, or Virtual Private Networks, have become essential tools for individuals and businesses seeking to protect their online privacy and security. However, the legality and regulation of VPNs in the USA are complex and ever-evolving.
In the USA, there is no specific federal law that explicitly bans the use of VPNs. This means that using a VPN for personal or business purposes is generally legal. However, the legality of VPN usage can vary depending on the activities conducted using the VPN. For example, using a VPN to engage in illegal activities such as online piracy or hacking is strictly prohibited under US law.
It is worth noting that while VPNs themselves are legal, the US government does have the authority to monitor and regulate VPN providers. This is done to ensure that VPN services comply with laws related to data privacy and security. In some cases, VPN providers may be required to hand over user data to the authorities as part of criminal investigations.
Overall, the use of VPN services in the USA is a legal and legitimate way to enhance online security and privacy. However, individuals and businesses should be aware of the potential legal implications of using VPNs for illegal activities. As technology continues to advance, it is crucial for both users and providers of VPN services to stay informed about the evolving regulatory landscape surrounding VPN usage in the USA.
Data logging requirements in USA
Data logging, the process of recording data over time, plays a crucial role in various industries across the United States. From ensuring compliance with regulatory standards to optimizing operational efficiency, data logging requirements in the USA are diverse and essential.
In the healthcare sector, data logging is mandated by regulations such as the Health Insurance Portability and Accountability Act (HIPAA). Healthcare providers are required to maintain accurate records of patient information, treatment procedures, and medication administration. Data logging helps ensure patient safety, facilitates effective communication among healthcare professionals, and supports clinical decision-making processes.
Similarly, in the food and beverage industry, the Food Safety Modernization Act (FSMA) imposes stringent data logging requirements to prevent foodborne illnesses and ensure product quality. Temperature monitoring, for instance, is critical during food storage and transportation to prevent bacterial growth and maintain freshness. Data logging solutions enable businesses to track temperature fluctuations, identify potential hazards, and take corrective actions promptly.
In the manufacturing sector, data logging is integral to quality control and process optimization. Regulatory bodies such as the Occupational Safety and Health Administration (OSHA) require manufacturers to monitor environmental conditions, equipment performance, and employee safety. By implementing robust data logging systems, manufacturers can detect anomalies, mitigate risks, and enhance overall productivity.
Moreover, environmental agencies like the Environmental Protection Agency (EPA) mandate data logging for monitoring air and water quality, emissions, and waste management. Accurate and timely data collection facilitates regulatory compliance, supports environmental assessments, and informs policymaking decisions.
Overall, data logging requirements in the USA are diverse, spanning across multiple industries and regulatory domains. By investing in reliable data logging solutions, organizations can ensure compliance, improve operational efficiency, and enhance overall performance.
VPN companies privacy laws
VPN companies play a crucial role in safeguarding users' online privacy and security. These companies offer encrypted connections that mask users' IP addresses, ensuring their online activities remain anonymous and protected from potential cyber threats. However, when it comes to privacy laws, not all VPN companies operate under the same jurisdiction, leading to variations in how they handle users' data.
Privacy laws governing VPN companies vary from country to country. Some countries have stringent data protection laws that require VPN companies to adhere to strict guidelines when collecting and storing users' data. In contrast, other countries may have more lenient regulations, allowing VPN companies to gather and potentially share users' information with third parties.
It is essential for users to be aware of the privacy laws governing the VPN companies they choose to use. Reading through a VPN company's privacy policy can provide insight into how they handle users' data and whether they comply with specific regulations. Opting for VPN companies based in countries with robust privacy laws can provide users with an added layer of protection and assurance that their data is being handled responsibly.
Overall, understanding the privacy laws that VPN companies operate under is crucial for users looking to safeguard their online privacy. By choosing reputable VPN providers that prioritize user privacy and comply with stringent data protection regulations, individuals can enhance their online security and enjoy a more anonymous browsing experience.
USA data retention policies
In the United States, data retention policies are a critical aspect of the country's approach to information security and privacy. These policies outline the guidelines and regulations that govern how long a company or organization must retain certain types of data before it can be deleted or disposed of.
One key aspect of data retention policies in the USA is the balance between individual privacy rights and the needs of law enforcement and national security agencies. Companies are required to retain certain types of data, such as financial records and customer information, for specific periods to comply with regulations like the Sarbanes-Oxley Act and the Health Insurance Portability and Accountability Act (HIPAA).
Additionally, the USA Patriot Act and other national security laws have implications for data retention, as they authorize the government to access private data under certain circumstances. This has led to ongoing debates about the appropriate balance between surveillance and privacy rights.
Another important consideration in the USA is the rapidly evolving nature of technology and data storage. With the growth of cloud computing and big data, companies are faced with new challenges in terms of retaining and securing vast amounts of information.
Overall, data retention policies in the USA play a crucial role in safeguarding sensitive information, ensuring regulatory compliance, and balancing privacy rights with national security interests. As technology continues to advance, it is essential for organizations to stay informed about the latest developments in data retention requirements to protect both their data and the privacy of individuals.
Logging obligations for VPN services
Logging obligations for VPN services are a critical aspect of ensuring user privacy and security. VPN providers play a pivotal role in safeguarding online activities by encrypting internet traffic and routing it through secure servers. However, the extent to which VPN services log user data varies significantly among providers, and understanding these logging obligations is paramount for users seeking anonymity and protection.
Logging refers to the practice of recording user activity and connection details, which can include timestamps, IP addresses, websites visited, and data transmitted. While some VPNs claim to have a strict no-logs policy, others may collect certain information for troubleshooting, maintenance, or even sharing with third parties. Therefore, it's essential for users to scrutinize a VPN provider's logging practices before entrusting them with their sensitive data.
When evaluating logging obligations, users should consider several factors. Firstly, transparency is key. A reputable VPN provider should clearly articulate its logging policy in its terms of service and privacy policy documents. Users should look for language that explicitly states the types of data collected, the purposes for which it's used, and whether any third parties have access to this information.
Secondly, jurisdiction plays a significant role in determining logging obligations. VPN services based in countries with strict data retention laws may be compelled to collect and store user data for extended periods, compromising user privacy. Conversely, providers operating in jurisdictions with robust privacy regulations may offer greater assurances of data protection.
Ultimately, users must weigh the benefits of using a VPN for enhanced privacy and security against the potential risks posed by logging obligations. By conducting thorough research and selecting a VPN provider that aligns with their privacy preferences, users can enjoy the benefits of encrypted internet browsing without compromising their personal data.
0 notes
Text
The Transformative Impact of Biometric Technology in Today's World

Introduction
In the digital age, where security and convenience are paramount, biometric technology stands at the forefront, offering innovative solutions that transcend traditional methods. From unlocking smartphones to securing sensitive data, the role of biometric technology is pervasive and transformative. This article delves into the multifaceted landscape of biometrics, exploring its evolution, applications, and implications for the future.
Understanding Biometric Technology
The Role of Biometric Technology
Biometric technology encompasses the identification and verification of individuals based on unique physiological or behavioral characteristics. These characteristics include fingerprints, facial features, iris patterns, voiceprints, and even gait analysis. The role of biometric technology is to provide a secure and reliable method of authentication, replacing traditional methods such as passwords or PINs.
Biometric systems capture these unique traits through specialized sensors and convert them into digital data for analysis and comparison. This process enables seamless identification and verification, enhancing security while streamlining access to various services and devices.
Evolution of Biometric Technology
The evolution of biometric technology traces back to ancient civilizations, where fingerprints were used as seals and signatures. However, modern biometrics emerged in the late 20th century with advancements in computing and sensor technologies. Today, biometric systems have become ubiquitous, with widespread adoption across industries and sectors.
Applications of Biometric Technology
Biometrics in Security
One of the primary applications of biometric technology is in security systems. From access control in high-security facilities to border control at airports, biometrics offer unparalleled accuracy and reliability. Facial recognition, in particular, has gained prominence in surveillance and law enforcement, aiding in the identification and tracking of individuals in real-time.
Biometrics in Finance
In the financial sector, biometric authentication is revolutionizing the way transactions are conducted. Banks and financial institutions are leveraging biometric identifiers such as fingerprints and voiceprints to verify the identity of customers, thwarting fraud and enhancing user experience. Mobile payment systems, equipped with biometric authentication, offer a seamless and secure way to authorize transactions.
Biometrics in Healthcare
In healthcare, biometric technology plays a vital role in patient identification and medical record management. By employing biometric identifiers, such as palm vein patterns or iris scans, healthcare providers can ensure accurate patient matching, reducing errors and improving the quality of care. Biometrics also enhance data security and privacy compliance, safeguarding sensitive medical information.
Future Trends and Challenges
Emerging Trends
The future of biometric technology holds promising advancements, driven by innovations in artificial intelligence and biometric sensor technologies. Mobile biometrics, such as fingerprint and facial recognition, will continue to proliferate, enabling secure and convenient access to devices and services. Moreover, emerging modalities, such as vein pattern recognition and DNA analysis, offer novel solutions for identity verification and authentication.
Challenges Ahead
However, with the proliferation of biometric data comes significant challenges related to privacy, security, and ethical considerations. The collection and storage of biometric information raise concerns about data breaches and identity theft. Moreover, the potential misuse of biometrics for surveillance and mass monitoring underscores the need for robust regulations and ethical frameworks to govern their usage.
Frequently Asked Questions (FAQs)
How secure is biometric authentication? Biometric authentication offers a high level of security, as it relies on unique physiological or behavioral characteristics that are difficult to replicate. However, like any security measure, it is not foolproof and may be susceptible to spoofing attacks.
Can biometric data be stolen or hacked? While biometric data is more secure than traditional passwords or PINs, it is not immune to theft or hacking. Biometric templates stored in databases can be vulnerable to breaches, highlighting the importance of robust encryption and security measures.
Are biometric systems reliable for authentication? Biometric systems are generally reliable for authentication, with low false acceptance and false rejection rates. However, the accuracy of biometric systems may vary depending on factors such as sensor quality, environmental conditions, and the quality of the biometric sample.
What are the privacy concerns associated with biometric technology? Privacy concerns related to biometric technology stem from the collection, storage, and potential misuse of biometric data. There are concerns about surveillance, profiling, and the erosion of individual privacy rights in the digital age.
How is biometric technology regulated? Biometric technology is subject to various regulations and standards aimed at protecting privacy, security, and ethical considerations. Regulatory bodies such as the GDPR in Europe and the Biometric Information Privacy Act in the United States govern the collection, storage, and usage of biometric data.
What are the future prospects of biometric technology? The future of biometric technology holds immense potential for innovation and advancement. Emerging modalities, such as DNA analysis and brainwave authentication, offer novel solutions for identity verification and authentication, paving the way for a more secure and seamless digital future.
Conclusion
In conclusion, the role of biometric technology in today's world is undeniable, with far-reaching implications for security, convenience, and innovation. From securing financial transactions to enhancing healthcare delivery, biometrics offer a myriad of benefits that promise to shape the future of authentication and identification. However, as biometric technology continues to evolve, it is imperative to address the associated challenges and ethical considerations to ensure its responsible and ethical usage.
0 notes
Text
Data Security: Impact of CD DVD Medical DICOM Publishing Systems

Data security is paramount, especially in the healthcare sector where sensitive patient information is constantly being generated and shared. Medical imaging, in particular, generates large amounts of data that need to be securely stored, accessed, and shared.
DICOM (Digital Imaging and Communications in Medicine) has become the standard for managing medical imaging data, and the DICOM publishing system plays an important role in ensuring the security and integrity of this data.
DICOM publishing systems include a range of technologies and tools designed to publish medical images on CD or DVD for storage, sharing and distribution.
These systems typically include DICOM CD/DVD burners, disc publishers, and robotic systems that automate the burning and labelling of discs. Although these technologies provide convenience and efficiency, they also present unique challenges and considerations when it comes to data security.
Understanding DICOM Medical Services
DICOM medical services refers to the suite of protocols, standards, and technologies used to manage, store, and disseminate medical imaging data. These services enable healthcare providers to capture, store, and share medical images such as X-rays, MRIs, CT scans, and ultrasounds in a standardized format. By following DICOM standards, healthcare organizations ensure interoperability and compatibility across different imaging devices and systems.
Role of DICOM Publishers
DICOM publishers play a vital role in the workflow of medical imaging departments and healthcare organizations. These systems allow medical professionals to create CDs or DVDs containing DICOM images for patients, referring physicians, or for archival purposes. DICOM publishers often feature advanced capabilities such as automatic disc burning, printing of patient information and labels, and integration with PACS (Picture Archiving and Communication Systems) for seamless data transfer.
Security Challenges and Considerations
While DICOM publishing systems provide convenience and efficiency, they also present security challenges that must be addressed. Here are some key ideas:
Data Encryption: DICOM images contain sensitive patient information and must be encrypted to prevent unauthorized access. DICOM publishing systems must support encryption standards such as AES (Advanced Encryption Standard) to ensure data security during storage and transmission.
Access Control: Access to DICOM publishing systems should be limited to authorized personnel only. Role-based access control mechanisms should be implemented to limit user privileges and prevent unauthorized users from tampering with sensitive data.
Audit Trails: DICOM publishers must maintain detailed audit trails of all disc creation and distribution activities. These audit trails provide a record of who accessed the system, what actions were taken, and when they occurred, facilitating accountability and compliance with regulatory requirements.
Safe Disposal: Proper disposal of DICOM discs is essential to prevent data breaches. DICOM publishing systems must support secure disc erasure methods that ensure that data cannot be recovered when the disc is no longer needed.
Integration with PACS: Integration between DICOM publishing systems and PACS is essential for seamless data transfer and workflow automation. However, the security implications must be carefully considered, ensuring that data transmitted between systems is encrypted and protected from unauthorized access.
Compliance and Regulatory Requirements
Healthcare organizations must adhere to various compliance and regulatory requirements governing the security and privacy of patient data. Regulations such as HIPAA (Health Insurance Portability and Accountability Act) in the United States and GDPR (General Data Protection Regulation) in the European Union impose strict requirements for the protection of medical information. DICOM publishing systems must follow these rules to avoid legal consequences and protect patient confidence.
Best Practices for Secure DICOM Publishing
To reduce the security risks associated with DICOM publishing systems, healthcare organizations should implement the following best practices:
Regular Security Assessments: Perform regular security assessments and audits of DICOM publishing systems to identify weaknesses and vulnerabilities. Resolve any identified issues immediately to maintain data security.
Employee Training: Provide comprehensive training to employees using DICOM publishing systems to ensure they understand security protocols and best practices for handling sensitive data.
Encryption and Authentication: Implement strong encryption and authentication mechanisms to protect DICOM images from unauthorized access. Use multi-factor authentication where possible to increase security.
Vendor Selection: Choose DICOM publishing system vendors with a proven track record of prioritizing data security and compliance. Make sure the vendor provides regular updates and support to address emerging security threats.
Data Backup and Disaster Recovery: Implement robust data backup and disaster recovery strategies to ensure continuity of operations in the event of a security incident or system failure.
Conclusion
DICOM publishing systems play a vital role in the management and distribution of medical imaging data, but they also present unique challenges and considerations for data security.
By understanding these challenges and implementing best practices for secure DICOM publishing, healthcare organizations can protect sensitive patient information and maintain compliance with regulatory requirements. As technology continues to evolve, healthcare providers need to remain vigilant and proactive in protecting patient data from emerging threats.
0 notes
Text
The Innovation Journey of Partisia Blockchain: Unveiling its Evolution and Impact
In the rapidly evolving world of blockchain technology, Partisia Blockchain stands out as a leader of innovation, transforming the way data is handled and transactions are conducted within decentralized networks. With its pioneering Multi-Party Computation (MPC) technology at the forefront, Partisia sets a new standard for privacy, security, and collaboration in the digital era. This in-depth exploration examines the fundamental features and advantages of the Partisia Blockchain, shedding light on its transformative potential and the future of blockchain technology.
For more information click the link below 👇

Introduction
Partisia Blockchain leads a paradigm shift in the blockchain landscape, introducing revolutionary concepts and technologies that redefine how we interact with decentralized systems. This comprehensive analysis delves deep into the core principles and components that underpin the Partisia ecosystem, highlighting its innovative solutions and their implications for the future of blockchain technology.
Multi-Party Computation (MPC) Technology
At the heart of Partisia Blockchain's architecture is its Multi-Party Computation (MPC) technology, a groundbreaking approach that enables multiple parties to collaboratively perform computations on encrypted data without compromising confidentiality. By leveraging cryptographic protocols, MPC ensures each participant retains control over their inputs while collectively deriving valuable insights. This technology opens up new possibilities for secure and confidential transactions, computations, and data sharing across various industries such as finance, healthcare, and logistics.
How MPC Works
In an MPC environment, data is encrypted, and different parties can execute computations on the encrypted data without having access to the underlying data. This cryptographic technique allows for secure collaboration on sensitive data, ensuring privacy and security while enabling parties to gain insights from the data.
MPC Applications
MPC has diverse applications across industries. In finance, MPC can enable secure sharing of data between institutions, allowing for accurate risk assessment without disclosing sensitive customer information. In healthcare, MPC can facilitate collaboration between hospitals and researchers, allowing them to analyze patient data securely for medical research and drug development.
The $MPC Token
The $MPC token serves as the backbone of the Partisia ecosystem, facilitating transactions and incentivizing network participants. Beyond its role as a medium of exchange, the $MPC token plays a crucial role in governance and community engagement. Token holders are empowered to shape the platform's future trajectory through voting and participation in decision-making processes. The token's finite supply and growing demand embody scarcity and utility, driving adoption and liquidity across diverse ecosystems.
Governance and Community Engagement
The $MPC token enables token holders to participate in governance processes, influencing decisions related to network upgrades, protocol changes, and other key developments. This democratic approach fosters a sense of ownership and accountability within the community.
MOCCA (On-Chain Custody Advanced Solution)
MOCCA is an advanced on-chain custody solution that offers enhanced security and flexibility for digital asset management. Utilizing smart contracts and cryptographic techniques, MOCCA allows users to securely store and manage their assets on the blockchain while retaining full control and ownership. This innovative custody solution mitigates risks associated with centralized custodianship, providing users with peace of mind and confidence in their digital holdings.
Benefits of MOCCA
MOCCA's decentralized approach to custody offers several benefits, including increased security and reduced counterparty risk. Users maintain control over their assets and are less vulnerable to hacks and other forms of attack commonly associated with centralized custodians.
Bring Your Own Coin (BYOC) Bridge
Partisia introduces the Bring Your Own Coin (BYOC) Bridge, an interoperability solution that bridges the gap between different cryptocurrency ecosystems. With the BYOC Bridge, users can seamlessly integrate their preferred cryptocurrencies into the Partisia ecosystem, accessing a diverse range of services and applications. Whether it's ETH, USDC, or BTC, users can leverage their existing holdings to participate in the Partisia ecosystem, maximizing the utility of their cryptocurrency holdings while exploring new opportunities in the decentralized landscape.
Promoting Inclusivity and Adoption
The BYOC Bridge promotes inclusivity by allowing users to participate in the Partisia ecosystem using their existing crypto holdings. This interoperability not only encourages adoption but also fosters a more connected and versatile blockchain ecosystem.
Complete Sharding Implementation
Partisia's Complete Sharding implementation marks a significant advancement in blockchain scalability and efficiency. By partitioning the blockchain network into smaller, independent shards, Complete Sharding enables parallel transaction processing, increasing throughput and reducing latency. This scalable architecture ensures optimal performance even during peak transaction volumes, offering users a seamless and responsive experience across various applications.
Addressing Scalability Concerns
Sharding addresses scalability concerns by distributing the network's workload across multiple shards. This approach enhances performance and efficiency, laying the foundation for mass adoption and supporting a wide range of applications.
Transparency
Transparency is a core value within the ethos of Partisia Blockchain, permeating every aspect of its ecosystem. It encompasses openness, honesty, and accessibility in information sharing and decision-making processes, fostering trust and collaboration among stakeholders. Through transparent governance mechanisms and publicly accessible information, Partisia ensures that all participants have a voice and visibility into the platform's operations.
Trust and Confidence
Transparency extends to the inner workings of the blockchain itself, employing transparent protocols and cryptographic techniques. Users can verify the validity of transactions and computations with ease, promoting trust and confidence in the platform's reliability. This openness ensures that users can audit and validate the integrity of the blockchain, further enhancing trust in its operations.
Conclusion
In summary, Partisia Blockchain represents a transformative force in the digital age, pushing the boundaries of innovation and revolutionizing how we interact with decentralized networks. Through its pioneering technologies such as MPC, the $MPC token, MOCCA custody solution, BYOC Bridge, and Complete Sharding implementation, Partisia empowers users to embrace a new era of decentralized finance, security, and collaboration.
As the blockchain landscape continues to evolve, Partisia remains committed to driving progress and exploring new possibilities within decentralized networks. With its visionary approach and dedication to excellence, Partisia paves the way for a future where blockchain technology transcends barriers and empowers individuals and communities worldwide.
1 note
·
View note
Text
The Imperative in ISO 27001 Certification in Malta
/ Uncategorized / By Factocert Mysore

The Imperative in ISO 27001 Certification in Malta
ISO 27001 Certification in Malta a generation of virtual conversion and interconnectedness, protecting sensitive facts and mitigating cyber threats have emerged as crucial imperatives for worldwide organizations. ISO 27001certification in Malta is a cornerstone of statistics safety management, imparting a scientific framework for identifying, assessing, and mitigating facts and protection dangers.
For corporations strolling in Malta, a thriving financial tool on the crossroads of Europe and North Africa, undertaking ISO 27001 certification in Malta isn’t always a great regulatory requirement; it’s far more strategically important. This manual explores the importance of ISO 27001 certification in Malta, its advantages, the certification technique, and its broader implications for companies within the Maltese information safety panorama.
Apprehending ISO 27001 Certification in Malta
ISO 27001 is a globally recognized standard, a useful and beneficial aid from the International Organization for Standardization (ISO) that specifies the requirements for installing, enforcing, retaining, and continuously improving a records protection control device (ISMS). The benchmark gives a systematic technique for managing and protecting sensitive statistics, securing their confidentiality, integrity, and availability.
Consequence in Malta’s Information Security Landscape
Malta’s financial tool has experienced a fast increase and diversification in recent years, driven by the beneficial resources of its strategic geographical location, professional personnel, and beneficial corporate industrial enterprise company agency surroundings. As Malta emerges as a hub for the technology, finance, and gaming industries, the significance of statistics and facts safety can’t be overstated.
ISO 27001 certification in Malta is highly relevant for corporations in Malta in several sectors, along with financial offerings, healthcare, e-change, and gaming. It offers an unquestioned framework for handling records safety risks, complying with regulatory requirements, and safeguarding vital belongings and sensitive facts.
By implementing the General Data Protection Regulation (GDPR) and precise records safety jail guidelines, ISO 27001 certification in Malta gives organizations in Malta a proactive technique of demonstrating compliance and constructing bypass-through in thoughts among clients, companions, and stakeholders.
Benefits of ISO 27001 Certification
Enhanced Information Security:
ISO 27001 certification in Malta lets corporations record safety dangers, ensuring data confidentiality, integrity, and availability. By imposing robust protection controls and practices, businesses can shield themselves from opposition to unauthorized rights of proper admission facts breaches and unique cyber threats.
Regulatory Compliance:
ISO 27001 certification in Malta provides a framework for complying with numerous regulatory requirements associated with records protection, privacy, and protection. Certification demonstrates a power of will to fulfill jail duties and business enterprise commercial enterprise organization corporation corporation corporation corporation corporation company necessities, reducing the risk of regulatory consequences and fines.
Improved Business Resilience:
Organizations can improve their resilience to cyber threats and disruptions by proactively analyzing facts of safety risks. The ISO 27001 certification in Malta permits agencies to build incident response plans, organizational continuity techniques, and catastrophe healing techniques to mitigate the effects of protection incidents and ensure continuity in their industrial and business organization groups.
Enhanced Customer Trust:
ISO 27001 certification in Malta serves as a badge of credibility and is acquired as actual. It assures customers, companions, and stakeholders that a commercial organization corporation, company business enterprise, enterprise business enterprise, or commercial agency significantly takes facts safety. Certification can differentiate market agencies, grow patron self-notions, and beautify relationships with clients and partners.
Cost Savings:
Implementing ISO 27001 certification in Malta requirements can result in monetary, financial, and financial savings by reducing the hazard of protection incidents, records breaches, and regulatory non-compliance. By making funding for preventative measures and safety controls, groups can mitigate functionality, financial losses and reputational damage associated with protection breaches.
Competitive Advantage:
In an increasingly competitive marketplace, ISO 27001 certification in Malta can offer a competitive advantage by using the power of will to protect records and manipulate chance. It can also be a call for a commercial agency with high-quality clients or companions, giving certified companies a strategic detail over the non-licensed competition.
The Certification Process Achieving ISO 27001 certification consists of numerous key steps, among topics:
Gap Analysis:
Conduct a comprehensive evaluation of present data, protection practices, hints, and techniques to identify gaps and areas for improvement regarding ISO 27001 requirements.
ISMS Development:
Develop and place into impact a statistics safety manipulation tool (ISMS) that aligns with ISO 27001 certification in Malta necessities. This consists of defining safety goals, project threat checks, and enforcing safety controls to mitigate recognized risks.
Training and Awareness:
Provide employees with education and famous packages on information safety tips, techniques, and first-rate practices. Ensuring personnel recognize their roles and responsibilities is crucial for successfully implementing the ISMS.
Internal Audits:
Conduct ordinary internal audits to evaluate the effectiveness of the ISMS, apprehend non-conformities, and implement corrective moves to cope with improvement regions.
Management Review:
Engage senior manipulate in periodic opinions of the ISMS to evaluate its common commonplace, common standard performance, suitability, and effectiveness in wearing out information protection dreams.
Certification Audit:
Select an excellent certification body for modern ISO 27001 certification in Malta and conduct a proper certification audit. The audit consists of an in-depth examination of the commercial employer enterprise’s ISMS documentation, techniques, and compliance with ISO 27001 necessities.
Continuous Improvement:
Establish a manner of life of non-preventive improvement through monitoring key primary conventional right-sized normal common regular overall performance symptoms and signs task everyday evaluations, and implementing corrective and preventive actions to improve the effectiveness of the ISMS.
Conclusion:
ISO 27001 certification in Malta is vital to Malta’s records safety panorama, providing businesses with a systematic approach to defensively protecting sensitive records. In the face of growing cyber threats and regulatory scrutiny, Certification offers agencies a proactive method to safeguard important belongings, ensure regulatory compliance, and build protective minds among customers and stakeholders.
By carrying out ISO 27001 certification in Malta, organizations in Malta can enhance their resilience to cyber threats, beautify their competitive feature within the market, and show a power of mind for information protection excellence. As Malta keeps to encompass digital innovation and financial boom, ISO 27001 certification in Malta will play a vital function in defensive touchy data, preserving enterprise enterprise enterprise business commercial employer enterprise enterprise enterprise agency commercial employer enterprise company enterprise enterprise organization business agency organization enterprise employer business enterprise organization business industrial organization business organization enterprise organization continuity, and fostering go with the flow-thru in thoughts in an interconnected global.
For more information visit: ISO 27001 Certification in Malta
Related Links:
ISO 14001 Certification in Malta
ISO 9001 Certification in Malta
ISO 45001 Certification in Malta
ISO 22000 Certification in Malta
ISO 13485 Certification in Malta
0 notes
Text
Undress AI Unmasked: Separating Fact from Fiction in the World of Image Manipulation

In the realm of image manipulation, Undress AI has emerged as a contentious technology, sparking debates and controversies about its capabilities and implications. This article aims to peel back the layers and uncover the truth behind Undress AI, separating fact from fiction to provide a clearer understanding of its potential and limitations.
Undress AI, also known as clothing removal AI, has garnered attention for its ability to digitally remove clothing from images using advanced algorithms and machine learning techniques. While its proponents tout its potential applications in fields such as fashion design and virtual fitting rooms, critics raise concerns about its potential misuse for non-consensual pornography and invasion of privacy.
One of the primary misconceptions surrounding Undress AI is the belief that it is capable of accurately and reliably removing clothing from any image. In reality, the effectiveness of Undress AI depends on a variety of factors, including the quality of its training data, the sophistication of its algorithms, and the complexity of the image being processed.
While Undress AI may be able to remove clothing from images under ideal conditions, such as well-lit and clear photographs, its performance may degrade when faced with more challenging scenarios, such as low-quality images or complex clothing styles. Additionally, the technology may struggle to accurately identify and manipulate certain types of clothing, such as sheer fabrics or intricate patterns.
Another common misconception about Undress AI is the belief that it is inherently malicious or unethical. While it is true that Undress AI raises ethical concerns about consent and privacy, it is important to recognize that the technology itself is neutral. Like any tool, its impact depends on how it is used and the context in which it is deployed.
For example, while Undress AI could potentially be misused for creating fake nude images or harassing individuals, it also has legitimate applications in fields such as fashion design, healthcare, and entertainment. By allowing designers to visualize garment designs on virtual models or aiding medical professionals in teaching anatomy, Undress AI has the potential to drive innovation and positive change.
Furthermore, it is essential to recognize that Undress AI is not a silver bullet solution for image manipulation. While it may be able to remove clothing from images, it cannot create entirely realistic or convincing results on its own. In many cases, human intervention and expertise are still necessary to achieve desired outcomes.
Addressing the misconceptions surrounding Undress AI requires a nuanced approach that acknowledges both its potential and its limitations. Rather than demonizing or glorifying the technology, we must strive to understand its capabilities and implications within the broader context of digital ethics and responsible innovation. Check my blog Undress AI Remove Clothes From Images Online
From a regulatory standpoint, policymakers must work to establish clear guidelines and safeguards for the development and use of Undress AI. This may include implementing restrictions on the types of images that can be processed, as well as penalties for those who misuse the technology for harmful purposes.
Additionally, raising awareness among the general public about the realities of Undress AI is crucial. By providing accurate information and fostering critical thinking skills, we can empower individuals to make informed decisions about how they engage with technology and protect their privacy and security online.
Ultimately, separating fact from fiction in the world of Undress AI requires a balanced and informed approach that considers both its potential benefits and risks. By promoting transparency, accountability, and ethical use, we can harness the power of Undress AI to drive positive change while safeguarding the rights and dignity of individuals.
1 note
·
View note