#Kaspersky Installation Problem
Explore tagged Tumblr posts
Text
This might be the end of my Stardew Valley series
I know I recently started up a Stardew Valley laet's play. It's only a few episodes in, but recently my game has started glitching and crashing. Each of the side saves I tried crashed the game and vanished upon reopening the game. The game is up to date. There are no mods. I tried uninstalling and reinstalling it(don't worry, the save for my series is still there). I tried starting a new save just to test it and after two in game days it froze loading the next day and crashed. And when I went to open it, that save was gone.
So this might be it for the series. I'll see if I can fix it. I know another program of mine has been bugging and ClipStudio hasn't been letting me save files as ClipStudio files(although I can save them as Photoshop documents, so at least it's not a complete loss). Hopefully I can fix this, but for now the let's play is on hold.
EDIT: I decided to try unistalling Aura, since this all seemed to start after installing it. When KAspersky said they wouldn't be renewing my subscription, I started looking into other options. I decided to give Aura a shot and it seemed fine at first. BUT it was only after installing it that everything started going downhill. My laptop started freezing. ClipStudio stoppe letting me save things as CS files, and Stardew Valley had been acting up.
So I decided to uninstall it and use a different antivirus. Sure enough enough, after I removed Aura everything seems to be back to normal. I tested ClipStudio and things are saving fine. So far Stardew seems fine, I started up a new save and it made it a few days in game with no issue. So I don't know what it was about Aura, but I think it's safe to say it was the source of the problems.
4 notes
·
View notes
Note
Same anon again! Which anti virus are you using and which is the safest cra/ck without getting any problems and viruses while trying to install? Thank you again!
Honestly, you don't need a cracked version of an antivirus software. I'm using Kaspersky, which I downloaded from their official website. You need to make an account, but it's currently one of the best anti-viruses out there. I used to use Avast, but they sold out to Google and started selling people's data, so avoid that one. Apparently, another well-received antivirus software are Eset NOD32 and Norton (personally, never used those so I can't judge them myself, but they get recommended quite often)
Hell, even Windows Defender is pretty decent, but if you wanna be sure your computer is protected, then yeah, Kaspersky and Eset are pretty good for starters, and you don't need to p*rate them, their "free" versions protect your computer quite well. Personally, I'd avoid using a p*rated version of an antivirus.
3 notes
·
View notes
Text
es cierto que el vpn kaspersky afecta windows
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
es cierto que el vpn kaspersky afecta windows
Kaspersky VPN impact on Windows operating system
Kaspersky VPN is a popular virtual private network service that offers users enhanced privacy and security while browsing the internet. When it comes to its impact on Windows operating system, Kaspersky VPN plays a significant role in safeguarding users' online activities.
One of the key impacts of using Kaspersky VPN on Windows OS is the encryption of internet traffic. By rerouting your connection through secure servers and encrypting the data transmitted between your device and the internet, Kaspersky VPN helps protect your online identity and sensitive information from potential cyber threats.
Moreover, Kaspersky VPN can also help users bypass geo-restrictions and access region-locked content by masking their IP address. This feature is particularly beneficial for users who wish to stream content from different countries or access websites that may be blocked in their region.
In addition, Kaspersky VPN enhances the overall security of Windows operating system by creating a secure tunnel for data transmission, making it difficult for cybercriminals to intercept and exploit sensitive information such as login details, financial data, and personal communications.
Furthermore, Kaspersky VPN offers users peace of mind by providing anonymity and privacy while browsing the internet. By masking your IP address and encrypting your online activities, Kaspersky VPN ensures that your browsing history remains confidential and inaccessible to third parties.
Overall, the impact of using Kaspersky VPN on Windows operating system is highly positive, as it enhances security, privacy, and flexibility for users navigating the digital landscape. By incorporating Kaspersky VPN into their online routine, Windows users can enjoy a safer and more seamless browsing experience.
Windows compatibility issues with Kaspersky VPN
When using Kaspersky VPN on a Windows device, users may encounter compatibility issues that can hinder the functionality of the VPN service. Some common issues include conflicts with the Windows operating system, firewall settings, or other security software installed on the device.
One of the primary compatibility issues users face is related to the Windows operating system. Updates or changes to Windows settings can sometimes disrupt the connection between Kaspersky VPN and the device, causing it to malfunction or not work as intended. In such cases, users may need to troubleshoot the issue by adjusting the network settings or reinstalling the VPN software.
Additionally, conflicts with Windows firewall settings can also lead to compatibility issues with Kaspersky VPN. The firewall may block the VPN connection or prevent the Kaspersky software from establishing a secure connection, resulting in connectivity issues. Users can resolve this problem by configuring the firewall settings to allow Kaspersky VPN to operate without any restrictions.
Moreover, if there are other security software programs installed on the Windows device, they may interfere with Kaspersky VPN and cause compatibility issues. Incompatibility between different security programs can lead to network conflicts and disrupt the VPN connection. Users should consider disabling or uninstalling any conflicting software to ensure smooth operation of Kaspersky VPN.
In conclusion, Windows compatibility issues with Kaspersky VPN can arise due to conflicts with the operating system, firewall settings, or other security software. By troubleshooting network settings, adjusting firewall configurations, and resolving conflicts with other programs, users can overcome these compatibility issues and enjoy a secure and stable VPN connection on their Windows device.
Negative effects of Kaspersky VPN on Windows
Kaspersky VPN is generally regarded as a reliable tool for enhancing online security and privacy. However, there are certain negative effects that users may encounter when using Kaspersky VPN on Windows operating systems.
One common issue that users face is a decrease in internet speed. When the VPN is activated, all internet traffic is rerouted through Kaspersky's servers, which can result in slower connection speeds. This can be particularly frustrating when streaming videos, downloading large files, or engaging in online gaming.
Another concern is potential compatibility issues with certain applications or websites. Some users have reported difficulties accessing specific online services or experiencing errors when running certain programs while using Kaspersky VPN on Windows. This can be a significant drawback for individuals who rely on these services for work or leisure activities.
Additionally, there have been instances where Kaspersky VPN has interfered with other security software or firewalls installed on Windows systems. This can create vulnerabilities in the overall security posture of the device, as conflicting software may inadvertently expose the system to cyber threats.
In rare cases, users have also encountered stability issues with their Windows operating system after installing Kaspersky VPN. This can manifest as system crashes, freezes, or other performance disruptions that negatively impact the user experience.
While Kaspersky VPN offers valuable features for safeguarding online privacy, users should be aware of these potential drawbacks when using the application on Windows devices. It is essential to weigh the benefits against the negative effects to determine if Kaspersky VPN is the right choice for your specific needs and preferences.
VPN Kaspersky influence on Windows performance
A VPN, combined with Kaspersky security software, can have varying impacts on Windows performance. Understanding how these tools interact is crucial for optimizing your system's speed and security.
When you use a VPN, your internet traffic is encrypted and rerouted through remote servers. This can introduce a slight delay in connection speed due to the extra layer of protection. However, the impact on performance is usually minimal and may not be noticeable for everyday browsing or streaming.
Adding Kaspersky security software to the mix can further enhance your online protection. Kaspersky offers features like real-time scanning, firewall protection, and malware detection that work in the background to safeguard your system from cyber threats. While these security measures provide valuable protection, they can consume system resources and potentially affect performance.
To minimize any potential impact on Windows performance, consider adjusting the settings of both your VPN and Kaspersky software. For example, you can choose a VPN server that is closer to your physical location to reduce latency. Similarly, customize the scanning schedule of your Kaspersky software to run during off-peak hours or when the system is idle.
Ultimately, the combined use of a VPN and Kaspersky security software can significantly boost your online security without severely compromising your Windows performance. By fine-tuning the settings and balancing the trade-offs between protection and speed, you can enjoy a safe and smooth browsing experience.
Windows vulnerability due to Kaspersky VPN
Title: Windows Vulnerability Exposed by Kaspersky VPN: What You Need to Know
In the realm of cybersecurity, vulnerabilities are a constant concern, and the recent revelation regarding Kaspersky VPN and its potential impact on Windows systems has raised significant alarm bells. Kaspersky VPN, a popular virtual private network service designed to enhance online privacy and security, has inadvertently exposed Windows users to potential threats due to a vulnerability in its software.
The vulnerability stems from a flaw in the Kaspersky VPN application, which could allow malicious actors to gain unauthorized access to Windows systems. This poses a serious risk to users' sensitive data, including personal information, financial details, and confidential documents. Given the widespread use of Windows operating systems across the globe, the impact of such a vulnerability could be far-reaching and devastating.
The implications of this vulnerability are profound, as it undermines the very purpose of using a VPN – to safeguard one's online activities and protect against external threats. Instead, users find themselves exposed to potential attacks, putting their privacy and security in jeopardy.
In response to this revelation, it is imperative for Windows users who utilize Kaspersky VPN to take immediate action to mitigate the risk. This may include updating the VPN software to the latest version, implementing additional security measures, or even temporarily discontinuing the use of Kaspersky VPN until a comprehensive fix is deployed.
Furthermore, it highlights the importance of staying vigilant and proactive in safeguarding digital assets against evolving cyber threats. Regularly updating software, employing robust security protocols, and exercising caution when accessing online resources are essential practices in today's interconnected world.
Ultimately, the Windows vulnerability exposed by Kaspersky VPN serves as a stark reminder of the ever-present dangers lurking in cyberspace and the critical need for constant vigilance and proactive measures to safeguard against them.
0 notes
Link
0 notes
Text
The Ongoing Effort to Counter Zero-Day Threats This Summer
The summer season has not slowed down the release of software updates, with tech behemoths Apple, Google, and Microsoft launching numerous patches to address vulnerabilities that are being exploited in actual attacks. In July, significant bugs were also addressed by enterprise software companies SAP, Citrix, and Oracle. Here is a comprehensive rundown of the major patches rolled out during the month.
Apple’s iOS and iPadOS 16.6 In July, Apple was quite busy, releasing two separate security updates. The first update from the iPhone manufacturer was a security-only Rapid Security Response patch. This marked only the second instance of Apple issuing a Rapid Security Response, and the process was not as seamless as the first one. On July 10, Apple rolled out iOS 16.5.1 9 (a) to address a single WebKit vulnerability that was already being exploited, but the patch was quickly withdrawn after it was found to disrupt several websites for users. A few days later, Apple re-released the update as iOS 16.5.1 (c), finally resolving the WebKit issue without causing any other problems.
Later in July, Apple’s major point upgrade, iOS 16.6, was released with 25 security fixes, including the previously exploited WebKit bug that was addressed in iOS 16.5.1 (c), identified as CVE-2023-37450. Among the other bugs addressed in iOS 16.6 were 11 in the Kernel, the heart of the iOS operating system, one of which Apple said is already being exploited. The Kernel flaw is the third iOS issue identified by security firm Kaspersky as part of the zero-click “Triangulation spyware” attacks.
Apple also rolled out iOS 15.7.8 for users of older devices, along with iPadOS 16.6, Safari 16.6, macOS Ventura 13.5, macOS Monterey 12.6.8, macOS Big Sur 11.7.9, tvOS 16.6, and watchOS 9.6.
Microsoft Microsoft’s July Patch Tuesday is a crucial update to watch for, as it addresses 132 vulnerabilities, including several zero-day flaws. To begin with, one of the bugs outlined in the patch update, identified as CVE-2023-36884, has yet to be addressed. In the meantime, the technology giant has provided steps to mitigate the already exploited flaw, which is reportedly being used in attacks by a Russian cybercrime group.
Other zero-day flaws included in Microsoft’s Patch Tuesday are CVE-2023-32046, a platform elevation of privilege bug in the MSHTML core Windows component, and CVE-2023-36874, a vulnerability in the Windows Error Reporting service that could let an attacker gain admin rights. Meanwhile, CVE-2023-32049 is an already exploited vulnerability in the Windows SmartScreen feature.
It is needless to say that you should update as soon as possible while keeping an eye out for the fix for CVE-2023-36884.
Google Android Google has rolled out an update for its Android operating system, addressing numerous security vulnerabilities, including three that it says “may be under limited, targeted exploitation.”
The first of the already exploited vulnerabilities is CVE-2023-2136, a remote code execution (RCE) bug in the System with a CVSS score of 9.6. The critical security vulnerability could lead to RCE with no additional privileges needed, according to the tech firm. “User interaction is not needed for exploitation,” Google warned.
CVE-2023-26083 is an issue in Arm Mali GPU driver for Bifrost, Avalon, and Valhall chips, rated as having a moderate impact. The vulnerability was used to deliver spyware to Samsung devices in December 2022.
CVE-2021-29256 is a high-severity flaw that also impacts Bifrost and Midgard Arm Mali GPU kernel drivers.
The Android updates have already reached Google’s Pixel devices and some of Samsung’s Galaxy range. Given the severity of this month’s bugs, it’s a good idea to check whether the update is available and install it now.
Google Chrome 115 Google has released the Chrome 115 update for its popular browser, addressing 20 security vulnerabilities, four of which are rated as having a high impact. CVE-2023-3727 and CVE-2023-3728 are use-after-free bugs in WebRTC. The third flaw rated as having a high severity is CVE-2023-3730, a use-after-free. Chunk 2: A vulnerability in Tab Groups has been identified as CVE-2023-3732, which is an out-of-bounds memory access issue in Mojo. Despite none of the vulnerabilities being exploited in real-world attacks, six have been classified as medium severity. Given that Chrome is a commonly targeted platform, it’s advisable to keep your system updated.
Mozilla’s Firefox 115 was released shortly after Chrome 115, addressing several high severity flaws. Notable among these are two use-after-free bugs, identified as CVE-2023-37201 and CVE-2023-37202. Mozilla also rectified two memory safety bugs, CVE-2023-37212 and CVE-2023-37211, which were found in Firefox 114, Firefox ESR 102.12, and Thunderbird 102.12. Mozilla’s advisory noted that these bugs demonstrated evidence of memory corruption, which could potentially be exploited to run arbitrary code with sufficient effort.
Enterprise software corporation Citrix has also issued an update warning, following the rectification of multiple flaws in its NetScaler ADC (now known as Citrix ADC) and NetScaler Gateway (now Citrix Gateway) tools. One of these flaws, CVE-2023-3519, is an unauthenticated remote code execution vulnerability that has been exploited and has a CVSS score of 9.8. Citrix has observed exploits of CVE-2023-3519 on unmitigated appliances and strongly urges affected customers to install the updated versions as soon as possible. The US Cybersecurity and Infrastructure Security Agency (CISA) also issued an advisory about this bug, noting its use in attacks on a critical infrastructure organization in June.
Enterprise software company SAP has released its July Security Patch Day, which includes 16 security fixes. The most severe of these is CVE-2023-36922, an OS command injection vulnerability with a CVSS score of 9.1. Onapsis, a security firm, stated that an authenticated attacker could “inject an arbitrary operating system command into a vulnerable transaction and program.” Therefore, patching is highly recommended due to the high impact on the confidentiality, integrity, and availability of the affected SAP system.
In addition, CVE-2023-33989 is a directory traversal vulnerability in SAP NetWeaver with a CVSS score of 8.7, and CVE-2023-33987 is a request smuggling and request concatenation vulnerability in SAP Web Dispatcher with a CVSS score of 8.6.
Software firm Oracle has also released its July Critical Patch Update Advisory, which addresses 508 vulnerabilities across its products. This includes 77 new security patches for Oracle Communications, with 57 of these vulnerabilities being exploitable remotely over a network without user credentials. One of the most severe flaws is CVE-2023-20862, which has a CVSS score of 9.8. Oracle has also released 147 patches for Financial Services and 60 fixes for Fusion Middleware. The company stressed the importance of customers applying Critical Patch Update security patches promptly and remaining on actively supported versions, as it continues to receive reports of attempts to exploit vulnerabilities it has already patched. In some instances, attackers were successful because targeted customers had not applied available Oracle patches.
https://www.infradapt.com/news/the-ongoing-effort-to-counter-zero-day-threats-this-summer/
0 notes
Text
What is TDMA?
Meaning of TDMA TDMA innovation, which represents Time Division Multiple Access, is a wireless standard that has been joined into the further developed GSM standard, which is presently the world's most broadly utilized phone innovation.
TDMA is utilized in second-age (2G) mobile phone frameworks, for example, GSM. Most significant third-age (3G) mobile phone frameworks are basically founded on GSM rival CDMA. 3G takes into account quicker information speeds over 2G.

While TDMA and CDMA both accomplish a similar objective, they do so utilizing various strategies. TDMA innovation works by isolating each advanced cell channel into three-vacancies to build the measure of information conveyed.
To know more click here: How To Renew Kaspersky Antivirus
Numerous clients, in this manner, can have a similar recurrence channel without causing impedance in light of the fact that the sign is isolated into various schedule vacancies.
While every discussion is transmitted then again over short periods of time with TDMA innovation, CDMA isolates interchanges by code so numerous calls can likewise be directed into a similar channel.
The significant phone bearers in the U.S. never again use TDMA.Dash, Virgin Mobile, and Verizon Wireless use CDMA while T-Mobile and AT&T use GSM.
#How To Renew Kaspersky Antivirus#kaspersky login#my kaspersky activation code#Kaspersky Installation Problem
0 notes
Text
The Very Basics of Not Killing Your Computer
AVOID HEAT STRESS
If you have a laptop DO NOT use it on a soft surface like a pillow or on a blanket, it’ll block the vents on your computer and make it get really fucking hot inside.
If you have a desktop you gotta open it up and blow out the dust sometimes.
If you are moving your laptop in a bag turn the laptop off. Don’t put it to sleep, don’t just shut the screen, turn it off, because otherwise it’s in the bag generating heat and there’s nowhere for the heat to go in the bag. OFF. Not sleep. OFF.
DO NOT DROP
Okay I know that should be obvious but drop damage to your hard drive is bad bad news. Be as careful as you can to set your computer gently on flat surfaces; don’t leave it hanging out on a bed where it can get knocked off, don’t set it on the roof of your car. And yes, just dropping it a couple inches can kill your hard drive or totally shatter your screen.
DON’T PUT SHIT ON YOUR KEYBOARD
Look I’ve seen four people ruin their laptops because they had a pen on the keyboard and closed the laptop and it fucked up the screen and the keyboard and it sucks so much and you feel awful after it happens because it’s so avoidable just don’t put things on your keyboard and always check that your laptop is clear before you close it.
PROTECT YOUR PORTS ON YOUR LAPTOP
You’ve only got one power jack and a limited number of other inputs on your computer and if they detach from the motherboard you’re fucked. USB ports get damaged because people use them a lot and eventually it weakens the connection and then they just stop working and it sucks. You can get around this with USB ports by using a USB hub to connect things like your keyboard and mouse.
For your power plug you just gotta be careful. Avoid tripping over the cord at all costs, don’t yank the plug out of the computer. It will SUCK VERY MUCH A LOT if you have to buy a new computer because the power port lost contact with the motherboard.
Don’t move your computer with things plugged into it. Take the power cord off before you put your laptop in the bag, take out the USB mouse dongle, do not travel with little nubby bits sticking out of your computer that can easily get caught or get tweaked or snap off inside of the thing.
(I really can’t emphasize enough that most of the “it will cost more than it’s worth to fix this” laptops I see are because of USB ports and power jacks. People don’t seem to know that this isn’t something that can be fixed easily; a broken power jack is a “remove the motherboard and resoldier components” job, not a “plug a new one in in fifteen minutes” job and most computer repair shops aren’t going to solder things for you and if they DO it’s going to be very expensive)
RESTART YOUR SHIT AT LEAST ONCE A MONTH AND JUST LET THE FUCKING UPDATES RUN
You should probably restart more than once a month but whatever. This is actually something that I consider part of reducing heat stress because when your processor is straining to keep up with all the background bullshit that’s running from a program you opened three weeks ago it’s going to use up resources and get hot and look just restart it once in a while.
Also the updates are almost always okay and safe and generally running updates is a good and secure thing to do (though maybe follow a blog dedicated to the OS you run because if there IS a problem with the updates that blog will probably talk about it before the update gets forced on your computer)
ANTIVIRUS BULLSHIT
Yes you should probably be running an antivirus.
Sophos is free and it’s fine. But don’t pay for it - if you’re using Sophos use the free version.
If you’re looking for something paid and a little more comprehensive I recommend ESET - get the cheap version, renewals cost less than the initial purchase, and feel free to get a multi-year version, the credentials follow your email not the computer so if your computer dies before your license expires you can install the license on a new computer.
DO NOT INSTALL NORTON OR MCAFEE THEY ARE EXPENSIVE BULLSHIT. Kaspersky is whatever. It’s less bullshit than Norton or McAfee but not as good as ESET for about the same cost.
If you think you’ve got a virus run the free version of Malwarebytes and get your shit cleaned.
KEEP LIQUIDS THE FUCK AWAY FROM YOUR COMPUTER
Again this should be obvious and yet. But seriously, just make a rule for yourself that drinks aren’t allowed on the same table as your computer and you’ll save yourself a lot of headaches.
PLUG YOUR COMPUTER INTO A UPS
Okay I fucking hate amazon but here’s a thing you should be using, just search the rest of the internet for “surge protector/UPS” and you’ll find something that isn’t from amazon - APC is a solid brand for this.
Basically you want a fat surge protector that has a little bit of a battery backup and you want to plug your computer (desktop OR laptop) into that instead of into the wall. The benefit of this is twofold:
1) if there’s a power surge the UPS will prevent your computer’s power supply from getting fried and possibly frying parts of your motherboard
2) if there’s a power outage and you’re *at* your computer you’ll have enough time to save what you’re working on before your computer loses power (like, you’ll maybe only have a minute or two on a small UPS but that’s still time to hit CTRL+S and keep from losing work)
At a bare, bare minimum your computer should be plugged into a surge protector but NOT directly into the wall.
BACK YOUR SHIT UP
[we interrupt this yelling for me to tell you that Western Digital has apparently released their new My Passport line and I’m obligated to inform you that you can get a 2.5″ USB 3.0 backup drive with FIVE FUCKING TERABYTES OF STORAGE for $130. Or you can get 4TB for $93. Or you can get 1TB for $53. basically what I’m saying is that it is not only cheap computer season it is also cheap hard drive season.]
[also if you’re getting a backup drive get western digital not seagate seagate fucking sucks and has a much higher failure rate]
Uh, okay, anyway - Do an image backup of your computer every once in a while so that if you get infected or your hard drive dies or whatever you can just restore from backup and move on like nothing happened.
HERE’S HOW TO DO AN IMAGE BACKUP.
SAVE YOURSELF THE WEAR AND TEAR
You know what is cheap? USB Keyboards and USB mice. You know what is not cheap? Fixing the touchpad on a laptop or replacing a laptop keyboard.
Get yourself a USB hub, a USB Keyboard and a USB Mouse (wired or wireless, doesn’t matter) and if you’re using your laptop at home plug *that* into your computer.
Also if your keyboard on your laptop breaks it’s fine just to use a USB keyboard instead I promise; if the screen breaks it’s also usually cheaper and easier to get a used or inexpensive monitor than it is to replace the screen. Your laptop is basically just a very small version of whatever bullshit is going on inside a desktop, if the peripherals break but the core components are fine you can just use it like a desktop.
Unless it’s a piece of shit that doesn’t have any USB ports or video out in which case you got ripped off, friend, demand functionality in your devices I’m sorry.
/rant
114K notes
·
View notes
Text
Keygen Autocad 2013 64 Bit Windows 10

Autocad 2013 Crack Keygen Free Download 64 Bit Windows 10
Xforce Keygen Autocad 2013 64 Bit Windows 10 Download
Autocad 2013 Keygen Crack
Keygen Autocad 2013 64 Bit Windows 10 Or Later Iso File
Keygen Autocad 2013 64 Bit Windows 10 Text
May 21, 2017 Download X-Force for Autodesk 2013 All Products Universal Keygen. Date: May 21, 2017 Author: kiaben 0 Comments. X-Force for Autodesk 2013 All Products Universal Keygen, Genkey for autodesk 2013. Link Download x force 2013 (32bit + 64bit, 100% work): X-Force for Autodesk 2013. Link download autocad 2013 64bit: autocad 2013 64bit.
Xforce keygen autocad 2010 64 bit free download. Aoa Brother i want Autocad 2013 64 Bit, or 2012 64 bit patch or keygen help me guys i need Autocad 2012 32 bit xforce activator. I have also tried the 2011 keygen as somewhere it said to use the newest one that matched the latest Autocad package you had installed. Autocad 2012 product key and xforce keygen, autocad 2010 64 bit product key. 2013 Free download xforce keygen 32bits autocad. Kaspersky Internet Security 2018 Crack wit Activation Code Full Version is powerful.
Autodesk 2020 All Products Universal Keygen For Windows Free Download Latest Version for Windows. The program and all files are checked and installed manually before uploading, program is working perfectly fine without any problem. It is full offline installer standalone setup of Autodesk 2020 All Products Universal Keygen For Windows. Free Download for supported version of windows.
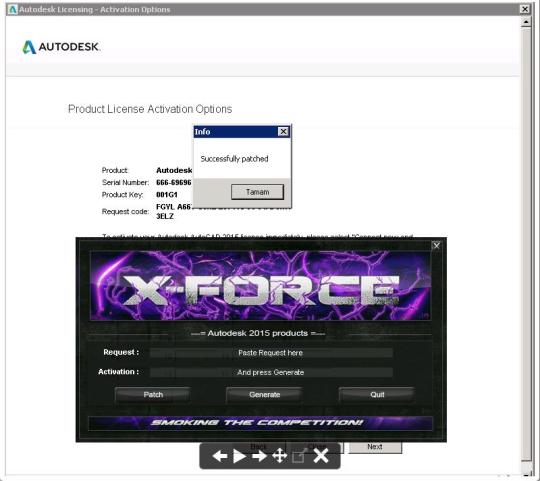
Autodesk 2020 All Products Universal Keygen x64 V2 Overview
Autodesk Products 20XX – X-FORCE, XF-ADSK was made by X-Force team for Autodesk 2006~2020 all products on Windows 32-bit and 64-bit.
Autodesk is one of the largest professional software and engineering software companies for personal computers, which today is used extensively throughout the world, with more than 200 million customers being one of the most prominent players in the field. The company’s most widely used software can be AutoCAD, Maya and 3ds Max. In this post, we plan to provide the most complete methods for activating various products of this company.
The only solution for the major activation of Autodesk products is the use of the Keygen (serial producer) of the famous X-Force group. This Keygen, which comes with new software every year, can be used to enable offline activation of most Autodesk software by turning the Request Code into Activation Code. Here are some key phrases in the Autodesk product activation process.
Serial Number : 11 digit identifier that is used solely to verify the identity of the software purchaser, and in all Autodesk software and all versions, there are usually some fixed and unchanged, for example: – 666-69696969 – 667-98989898 – 400-45454545
Product Key: A product key is used to identify a specific product, and from 2010 onwards it was mandatory to enter the correct value for installing Autodesk software. This identifier with the xxxX1 pattern is a combination of 5 characters, the first three characters of which can be either a number or a letter of the alphabet of the English language, but the fourth character (the year mark of the product) is always a fixed English word. For example:
– 001A1 (unallocated) – 001B1 (AutoCAD 2010 software) – 001C1 (AutoCAD 2011 software) – 001D1 (AutoCAD 2012 software) – 001E1 (AutoCAD 2013 software) – 001F1 (AutoCAD 2014 software) – 001G1 (AutoCAD 2015) – 001H1 (AutoCAD 2016 software) – 001I1 (AutoCAD 2017 software) – 001J1 (AutoCAD 2018 software) – 001K1 (AutoCAD 2019 software)
– 128B1 (3ds Max 2010 software) – 128G1 (3ds Max 2015) – 128J1 (3ds Max 2018 software)
– A63H1 (Alias Concept 2016 software) – A63J1 (Alias Concept 2018 software)
Autocad 2013 Crack Keygen Free Download 64 Bit Windows 10
Request Code and Activation Code : Request Code is the amount you assign to your system after installing any Autodesk software; by providing this code to the Autodesk support company, you will receive another code called Activation Code, which can be activated by importing it into the software.
Autodesk 2020 All Products Universal Keygen x64 V2 Features :
Very easy to use and simple interference
You can crack any Autodesk product easily and quickly
100 percent working and safe downloading
Activation of Autodesk products from 2012 to 2020.
Xforce Keygen Autocad 2013 64 Bit Windows 10 Download
Products that Can be Activated:
AutoCAD 2020 AutoCAD 2020 LT Autodesk AutoCAD MEP 2020 Autodesk AutoCAD Plant 3D 2020 Autodesk AutoCAD Map 3D 2020 Autodesk AutoCAD Mechanical 2020 Autodesk AutoCAD Electrical 2020 Autodesk AutoCAD Architecture 2020 Autodesk ReCap Pro 2020
ReCap Photo 2020.0.1 HotFix 64-Bit
Autodesk 3ds Max 2020 3ds Max Interactive 2020 Vault Basic Client 2020 Vault Basic Server 2020 Inventor 2020 Pro Inventor LT 2020 Autodesk Raster Design 2020 Autodesk Inventor Nastran 2020 DWG TrueView 2020 (AutoCAD DWG file viewer) SketchBook 2020 Vault Professional Server 2020 Point Layout 2020
System requirements :
OS: Windows XP, Windows Vista, Windows 7, Windows 8, Windows 8.1, Windows 10 (both 32 & 64-bit).
CPU: 1 GHz (32 bit or 64 bit) and above;
RAM: 256 MB(1028 MB Recommended);
HDD: 200 MB free space and more;
Free Download Autodesk 2020 All Products Universal Keygen x64 V2 !!
Click on the link below to start Autodesk 2020 All Products Universal Keygen x64 V2 Free Download. This is a full offline installer standalone setup for Windows Operating System. This would be compatible with both 32 bit and 64 bit windows.
Previous Versions :
Download >> Autodesk 2020 All.Products Universal Keygen x64 V2 Mirror | 933KB
Autocad 2013 Keygen Crack
Your 64bit AutoCAD 2013 was not designed to run in Windows 10 (this version of Windows is newer than AutoCAD 2013). In order for your AutoCAD 2013 to run as it did in previous versions of Windows, you need to follow these easy steps…
Install 64bit AutoCAD 2013
Make sure all previous installed versions of AutoCAD 2013 are uninstalled first.
Obtain your copy of the Longbow Converter here
Start the Converter tool
Pick the 1st tab named “AutoCAD 32bit Installer Converter“
Using your mouse, right click the tab text “AutoCAD 32bit Installer Converter” so that it changes to “AutoCAD 64bit Installer Converter“
Next, using the “…” button, select your AutoCAD installation CD and follow the instructions presented by the Converter tool user interface.
Once you have completed the AutoCAD installation process…
close the setup program then start the Converter software
Select the 3rd tab “Old AutoCAD Program Reviver”
Using the “…” button, pick the newly installed C:Program FilesAutodeskAutoCAD 2013 folder
then click “Fix Old Program“
Next install the AutoCAD 2013 sp2 from here
Now you can happily run your AutoCAD 2013 64bit on Windows 10
Troubleshooting
– If your AutoCAD crashes while interacting with the Ribbon click here

– If your AutoCAD is running really slowly, try disabling your integrated graphics card so you can run your high-performance card instead
– If you are unable to activate your product, or the activation process crashes:
Try uninstalling the July 2014 Microsoft security update
Keygen Autocad 2013 64 Bit Windows 10 Or Later Iso File
– If you have crashing problems using the File->Open or File->Save dialogs inside of AutoCAD please read this blog entry on the File->Open or File->Save Crash in AutoCAD
Keygen Autocad 2013 64 Bit Windows 10 Text
Copyright 2019 (c) Longbow Software

1 note
·
View note
Text
Download, Install and Activate Kaspersky
What are the instructions for Download, Install and Activate Kaspersky?
Steps to Download, Install and Activate Kaspersky at Usakasperskycom/Kav download:
Installing software refers to a procedure of making a device ready to run software or program. User may Install Kaspersky product KEY on the device (Windows or Mac), by following step by step procedure mentioned below:
First of all, go to the official website is usa.kaspersky.com/kavdownload
Now, choose the “My Account” option.
And then, choose the “Sign In” option from the “My Account” drop-down menu.
On the Sign-in page, type the email address & password of the Kaspersky account in the corresponding fields.
Now, hit the “Sign In” key.
In the Kaspersky account, go to the “Subscriptions” section & choose Kaspersky antivirus subscribed by users.
Now, click on the “Add Device” button displayed in front of the selected Kaspersky product.
The “Add Device” page will seem on the screen. Here, choose “Type of Device” on which users want to install subscribed Kaspersky antivirus products.
Hence, click the “Download” key displayed at the bottom of the page.
After successfully download to the device, follow the on-screen instruction to install a Kaspersky subscription to the device.
Kaspersky activation code for usa.kaspersky.com/kav download:
It is an alphanumeric characters string. I have a Kaspersky activation code that is unique for every Kaspersky user. An activation code is an array of 4 blocks of characters you need to activate the application. Each block consists of 5 characters which can be a combination of letters and numbers, which comes to a total of 20 characters: ХХХХХ-ХХХХХ-ХХХХХ-ХХХХХ.
The Download, Install and Activate Kaspersky | To activate Kaspersky read this blog step by step process:
First of all, to activate the commercial version of Kaspersky Anti-Virus 2016, use a 20-digit activation code. You can find the activation code on the Quick Start Guide if you have a boxed version or in the message sent to your e-mail if you bought the code in the online store. If you do not have an activation code, buy it at the Kaspersky Lab’s official e-Store.
So, now I expect you have an activation code. Go to my.kaspersky.com
Now click on the Signup option on this page
If you already have a Kaspersky account before click sign in
When you will sign up you need to put your email and need to create a new password for the Kaspersky account.
As a result of sign up, you will get a verification email from Kaspersky
So now go to your given email and verify to complete the Kaspersky account verification
when you will click on the verification email link, it will redirect you to your Kaspersky account.
Finally, you will get the place to add your activation code
Put your activation code here.
Now on the same page, you will find tab download, just click on that
Seems like you got your product listed right!
Just click to download
After downloading just run the product. Now you are done.
Download, Install and Activate kaspersky- Free Download
Click on the below button to start Kaspersky Internet Security 2018 Free Download. This is a complete offline installer and standalone setup for Kaspersky Internet Security 2018. This would be compatible with both 32 bit and 64-bit windows.
System Requirements For Download, Install, and Activate Kaspersky:
Before you start Kaspersky Internet Security 2018 free download, make sure your PC meets minimum system requirements.
Operating System: Windows XP/Vista/7/8/8.1/10
Memory (RAM): 1 GB of RAM required.
Hard Disk Space: 1 GB of free space required.
Processor: 512 MB of RAM required.
Tips before usa.kaspersky.com/kavdownload:
Uninstall any other antivirus from your computer if you had any before. Remove it completely and restart your computer:
Also, uninstall any Old version of Kaspersky antivirus from the computer.
Most noteworthy you must restart your computer in order to completely remove a security after uninstall.
If still, you are facing a problem you can contact our support from the given contact link or on the toll-free number.
1 note
·
View note
Text
Best Buy Renewal
kaspersky geek squad install
Kaspersky is now a world-known brand in the cybersecurity industry. Kaspersky founded in 1997 since then moving forward in innovative security solutions. The small-scale or global businesses, critical infrastructure, governments, and home consumers can also be protected from the Kaspersky. Kaspersky Geek Squad install and activation protect Windows Computer, MAC, Android as well as iOS devices by installing and activating Kaspersky on your devices. Over 400 million users are protected by Kaspersky technologies and we help 250,000 corporate clients protect what matters most to them. Learn more at Kaspersky Geek Squad Install.
If you have purchased Kaspersky through Geek Squad Best Buy and want to Install, download or renew kindly visit Kaspersky.com/geeksquad.com Kaspersky Geek Squad Renewal has stopped selling Kaspersky Lab‘s antivirus security software, and the retail giant’s Geek Squad team is ready to assist existing customers with free migrations to alternative security platforms over the next 45 days. The free offer includes existing Kaspersky subscriptions purchased from Kaspersky Geek Squad Install.
Renew Webroot Through Geek Squad
If you are looking for an option online How To Renew Webroot Through Geek Squad , chances are your webroot subscription is already ended or is going to end in a few days. When you receive a webroot from the geek squad and install it on your computer, its validity for a period of time from 6 months to 3 years. After the subscription period is over you are required to renew the subscription or else your device becomes defenseless to the cyber threats.
After you Renew Webroot Through Geek Squad your system stay fast and protected at the same time. As our competitors rely on downloading malware definitions straight to your device, Webroot store them in the cloud. This allows Webroot to maintain a small endpoint agent that installs fast, scans fast, and benefits from a more robust threat library than competitors
Webroot Geek Squad Download
Follow below process to know Webroot Geek Squad Download. You can renew Home or Business versions of Webroot. We at Webroot, we store treat definitions in the cloud. This allows Webroot to maintain a small endpoint agent that installs fast, scans fast, and benefits from a more robust threat library than competitors
Where many of Webroot competitors rely on downloading malware definitions straight to your device, Webroot store them in the cloud. This allows Webroot to maintain a small endpoint agent that installs fast, scans fast, and benefits from a more robust threat library than competitors
How to download www webroot com bestbuydownloads ?
1. Go to Official Website of Webroot.(webroot com bestbuydownloads).
2. Click on Download button.
3. Save downloaded file.
4. Run downloaded Webroot.exe file.
5. Click on Yes on User Account Control.
6. If you’re existing customer of Webroot then login to your Webroot Account through your registered email address.
7. For new customers create an account on our www webroot best buy downloads through your Email Address.
Without the renewal of webroot, your device will be defenseless against threats such as malware, ransomware, and spyware. So it is advised to renew it without any delay so that your device is always protected.
Hence, If you are also the one who is seeking webroot antivirus renewal that you received from the geek squad, you are at the right place. We help you in the process and even extend the period as an addition to renewal. we also check and diagnose if the device is completely protected after the webroot geek squad renewal is completed.
Trend Micro Geek Squad
Trend Micro Geek Squad Download services are available to provide fast assistance and on time Tech Support. This makes our customer happy and satisfied; they feel great when they are getting help whenever they are in need. We are well-known as repair, installation, and support Provider Company all over the world.
Geek Squad Tech Support started as support services for PC during its inception, and now it also handles electrical and electronics items as well. Geek squad support covers now every device which we have in our hand, kitchen or at our home.
Best Buy Renewal- Extend the Protection Plan of Your Devices
Our proficient team offers the best assistance in dealing with all the problems of devices like PC, tablets, laptops, phone, home appliances, software that include television, video games, refrigerator, cameras by extending your protection plan with Best Buy Geek Squad Renewal. With over 500 product support & extended warranty, we’ve subscribed by more than 2500 customers in a year.
You can easily know about our categories and list of different products and services to receive help for the suitable devices. It is an exhaustive list, and in case you are still confused, you can directly chat with our experts for a valid choice.
1 note
·
View note
Text
Kaspersky download and install
Kaspersky download and install procedure: To download Kaspersky, first of all, know your variant and download the exe file for that exact variant of Kaspersky as described below in the tutorial. in the tutorial, you will also get the download link or web page for all variants of Kaspersky. When you are done with the download you can double click or run the downloaded exe file to start the installation. During installation follow the positive options coming on the screen and you will be able to install your Kaspersky.

Variants of Kaspersky and how to download and install different Kaspersky variants
Down below is the list of Kaspersky variants –
Kaspersky total security
Internet security by Kaspersky
Kaspersky antivirus
Geeksquad Kaspersky
General download page for Kaspersky download – USA users
Just open a web browser on your computer.
Type usa.kaspersky.com/downloads in the URL box and hit enter key from the keyboard.
By doing this you will get a page where you will find all the Kaspersky variants listed and ready for download.
Now recognize your variant of Kasperksy from your purchase receipt or retail card.
Download the same version as mentioned on your card.
Although to complete the activation of your product. You need to create a Kaspersky account and redeem your activation code.
How to create a Kaspersky account and redeem your Kaspersky activation code?
to create a Kaspersky account open the URL https://my.kaspersky.com/ and on this page on the right top corner, you will find a sign-up button. Just click on the sign-up button.
When you will click on the sign-up button a screen will appear which will ask you for your email and a password for your upcoming Kaspersky account. Fill in the details and check the checkboxes. Also, fill in the captcha words and click on the create account button download below. Confirm your email from the email inbox as an email just arrived for confirmation. When you will click on the confirmation link login screen will appear. Put your just created credentials and login into your account.
About Kaspersky activation code which is used to download and install Kaspersky
A Kaspersky activation code is a code you get when you purchase a license to use a Kaspersky security product. It consists of 20 Latin characters and is divided into blocks in the following way: ХХХХХ-ХХХХХ-ХХХХХ-ХХХХХ. This code is required to activate the application. To install Kaspersky with an activation code you need to use this very same code.
In case you face any kind of problem you can just complete another help article for Kaspersky activation which is mentioned below.
1 note
·
View note
Text
The Best Parental Control Apps for Your Phone in 2021

If you want to monitor your children's device activity in modern times, you will need The Best Parental Control Apps/service that works well on desktop as well as mobile platforms.
Children can do all kinds of mischief on their mobile phones (or tablets), either on purpose or by accident. They may spend a lot of time staring at the screen each day Or use age-appropriate sites and apps. In any case, a good parental control app can restore your sense of control and help you keep a close eye on anything that might harm them.
Be sure to have an open and ongoing conversation with your kids about the importance of using a responsible tool, so they don't immediately plan to get rid of whatever app you install or find some smart work. Do Check out our article on What parents of connected children need to know If you do not know where to start.
How to monitor your children's mobile devices

Parental control apps can help you maintain control in a variety of ways. Some common types of monitoring include web content filtering, app blocking, time management, and location tracking.
We dive into these advanced features in more detail below. Keep in mind that some of the products we highlight are mobile solutions only, meaning they can't monitor your child's activity on a Mac or PC. If these platforms are your biggest concern, be sure to check out our Top 10 ways to earn money online.
This is how most parental control services work. You install a monitoring app on every device you want to place tabs on and manage settings and restrictions from either the web desktop or the parent-based mobile app. Changes you make to any device take effect immediately. We appreciate the services that Flexible Device Management offers.
Pricing and platform
Most parental control apps require you to pay an annual subscription based on the number of devices you monitor. Prices for monitoring one or two devices range from 10 10 to anywhere 30 anywhere, and in some cases can go up to $100 if you want 10 or more licenses.
Circle Home Plus requires a hardware device and, ultimately, a premium subscription to achieve its full potential. That said, there are some exceptions.
Some services, such as Locatigree, run on the Freemium model, despite some restrictions that do not apply to the Premium Edition. Others, such as Kaspersky Safe Kids and Norton Family, do not limit the number of devices you can monitor.
Parental control software is more powerful on Android than iOS, as Apple has locked the app's permissions and access to the device. Most parental control apps for iPhones require you to install the Mobile Device Management (MDM) Create a profile for all of these features (especially those related to app management and time constraints) to work properly.
To monitor iOS devices, consider using Apple's screen time Tools that compete with standalone competition as a pay offer. Apple's built-in (and free) solution is account-based, meaning it tracks the child's data on all Apple devices.
Apple has already added a good range of app blocking and web filtering options to its key settings in the App Restrictions section. Microsoft (Family Safety) and Google (FamilyLink) also offer first-party parental management solutions, which we cover in more detail in our guide.
Web Filtering

The key to any parental control app is to prevent children from accessing inappropriate or dangerous websites. Many apps bundle a proprietary browser, making it easier for services to manage, track and control browsing activity.
This is more sensible than trying to reverse engineer support for any perceived mobile browser. Similarly, most of these apps instruct you to stop every other browser or prevent your child from installing any kind of apps in any way.
Some parental controls do not force your child to use a proprietary browser. Rather, they take advantage of VPN technology and run Internet connections through a local app to enable content filtering.
You will see VPN Icon when such utility is enabled. The presence of this icon does not mean that the child's connection is entirely obtained through a virtual private network, nor that the device's IP address is masked.
Most of these browsers work in such a way that they block access to websites that fall into the forbidden category, including the biggest criminals, such as file sharing, gambling, pornography and violence.
No problem with the best examples HTTPS Blocking Encrypted Traffic and Access to Unknown Proxies Some apps, such as Net Nanny, allow you to create custom web filtering categories, and most allow you to add rules specific to custom domains. Others can lock secure search settings and prevent abuse. The quality of web history reporting also varies from service to service.
App monitoring, messaging and time constraints
An area where most parental control solutions are available has the potential to prevent children from using certain apps. This is beneficial for parents who can prevent their children from using social media apps, messaging services, which are difficult to monitor, or browsers that are located around certain web filters.
However, it can be difficult to track every new app your child installs. Better yet, services like Boomerang, which automatically block new apps installed by your child unless you explicitly approve them. Mobisap gives you the option to whitelist only the apps you want your child to use.
App blocking works differently on iOS. You can block access to sister apps such as Safari, Camera, and Siri if you wish. You can also disable the iTunes Store and App Store and ban app purchases. Some parent-controlled apps can completely remove app icons from the home screen at any time, so your child is unlikely to be able to access them.
One thing you won't be able to do with most parental control apps is monitor calls or SMS, MMS, and encrypted messages. You can block Secure messaging apps But Boomerang and Custodio are the only options we've tested that allow you to track SMS messages and call data.
This capability is only for Android devices and is not included in the app versions on the Google Play Store. Instead, you'll need to sideload a custom version of the app.
Time constraints are another great feature of parental control apps. Some services, such as Norton Family Premiere and Family Time, let you know how many hours (or minutes) your child can spend on a given device in a day, as well as their usage schedule.
Also tells Custodio lets you set schedules for the use of specific apps and devices, as well as allocate total time for your child, which applies to each piece of hardware that allows them to access the Internet. Use for
Location reporting
A mobile application under parental control should also monitor at least one child's current location and some historical location data. It is also important for them to control the range of information and the frequency of location reporting, so as not to bombard parents with useless data. Both the Custodio and the Norton family offer these features.
Some services, including locating, boomerang, and family time, take it a step further by letting you build a geofence around a location. For immovable, geofences are digital boundaries around a physical location that help parents when a child arrives at a designated location or leaves.
Kaspersky Safe Kids even lets you add time dimensions to geography, so you can easily make sure the child stays where they are supposed to be throughout the day. Boomerang offers a unique feature that allows you to draw custom geographies on a map.
Other apps only draw a circular radius around the point you specify. Android and iOS themselves let you track your child's location.
Talk to your children
While the range of features that parental control software supports is impressive, no system is perfect. If your children want to achieve the limits you set, they will be able to do so by using unsupervised devices or by finding ways to clear their devices from control apps.
Therefore, it is beneficial to take the time to talk to your child about why you have installed surveillance software in the first place.
However, digital safety and security are titles for everyone. It's better to approach these conversations honestly, rather than let them know for themselves and stop trusting you. For older children, in particular, it is also important to set your own rules, rather than set rules that may otherwise seem arbitrary.
Source
1 note
·
View note
Link
The events of recent weeks have proven that it’s not a safe world for masculine men out there. Now more than ever men should be looking into increasing their personal security. As an IT guy I have been thinking for a solution to the problems men face. Below are measures I can recommend one take to increase his security.
Disclaimer: this guide caters to Windows users, but others can still find value.
1. Install a VPN

VPN stands for Virtual Private Network. To understand what a VPN does, first you must understand what an IP is. IP is something like a computer passport number. Each electronic device has it’s own IP address. Websites register your IP when you use them—this makes it easy to find your location, your device, and therefore your identity. A VPN makes it so when you connect to a website you first go through the VPN server. So when you connect to a website instead of seeing your computer IP it shows the IP the VPN provides you. Roosh recently wrote on VPNs.
Example (manually changing IP):
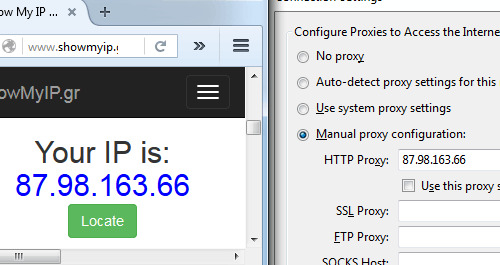
The problem here relies on the credibility of the VPN provider. Many VPN providers register your activity and can then hand it to a government organization if they so demand. Even VPNs that promised not to do this, broke their promise. There is an agreement between the Anglo-speaking countries that affects VPN users. The government can ask the provider for your data, and there is nothing your provider can do to not give it to them.
These countries are referred to as 5 eyes. Currently, similar agreements are being done with other countries, referred to as the 14 eyes: United Kingdom, United States, Australia, Canada, New Zealand, Denmark, France, the Netherlands, Norway, Germany, Belgium, Italy, Spain, Sweden
Definitely get a paid VPN. Free VPNs are not an answer, they most likely register some info on you and are slow. After some research on VPN providers I have found some VPN proviers that are outside the 14 eyes, use encryption, accept Bitcoin, support OpenVPN and have a no logging policy and an overall good reputation.
Here are my findings: blackVPN (Hong Kong, 25 servers, 100 dollars a year), Cryptostorm (Iceland, 13 servers, 52 dollars a year), HIDEme (Malaysia, 85 servers, 65 dollars a year), NordVPN (Panama, 52 servers, 48 dollars a year), Perfect Privacy (Panama, 40 servers, 150 dollars a year), Privatoria (Czech Republic, 12 servers, 23 dollars a year).
One VPN provider attracted my attention particularily, that being BolehVPN, since it is one of the only two providers that offers Tor to VPN alongside VPN to Tor (the other one being AirVPN, which is based in Italy, therefore part of 14 eyes), so if you want that particular set-up, check it out.
Make sure to check the VPN provider’s canary. It is a document that confirms that the VPN provider was not touched by the government. It should be updated every month, if it isn’t unsubscribe. Example.
How to increase VPN security
1) Pay with untraceable money
Sign up for an anonymous e-mail account using Tor and use a Bitcoin Mixer to send Bitcoins to a newly generated address in your local wallet. Alternatively, use the Bitcoin-OTC to purchase Bitcoins ‘over the counter’ from a person, rather than an exchange. Then, use a patched Bitcoin client, such as coderrr’s anonymity patch to avoid linking the newly generated address to any of your pre-existing Bitcoin addresses. —Andrew, Private Internet Access.
2) Make sure you don’t disconnect from VPN and prevent DNS leaks
Use the pro version of VPNCheck to automatically disconnect from internet when losing connection to VPN and to prevent DNS leaks. Or search for the manual way of doing it
3) Use multiple VPNs
Another measure to consider is using two or more VPNs. Basically activate one VPN first, then another one, done.
4) Resolve the PPTP IPv6 VPN flaw
Not likely to affect everyone. PPTP is the weakest VPN protocol and if you use one of the VPNs I mentioned before you will likely use a better protocol, but for those who do, there is a possible flaw that you can correct like this—for Windows Vista and above: Open cmd prompt and type: netsh interface teredo set state disabled.
5) Secure your router
Here’s a guide.
2. Install an antivirus

There are three tiers of antiviruses: antivirus sofwtare, internet suite and premium security suites. Read about them here. At minimum use Microsoft Security Essentials (free software from Microsoft), though paid antiviruses (such as Bitdefender, Kaspersky, etc.) are better.
3. Use Tor and TailsOS for safe web browsing

Many popular browsers are not highest ranked in regards to keeping your anonymity. For example, while Chrome is theoretically secure from spyware and adware, their stance on privacy can be summarized as follows:
He went on, speaking about the future of search. With your permission you give us more information about you, about your friends, and we can improve the quality of our searches. We don’t need you to type at all. We know where you are. We know where you’ve been. We can more or less know what you’re thinking about.
There are factors one must be careful of: cookies, encryption (https), tracking ads, javascript exploits, canvas fingerprinting and others. A writeup on these would take a long time so research them on your own if you wish. I will just mention browsers that avoids these issues.
USE SAFE SEARCH ENGINE
Instead of using the google search engine use disconnect.me installed into Tor (or install as extension into Firefox)
TOR BROWSER
Tor Browser is an internet browser designed for online anonymity. It is a modified version of Firefox with add-ons pre-installed. Tor works somewhat similar to the VPN concept. Before connecting to a website you go through “nodes”. Which are private stations, each with its own IP. So instead of showing your IP, it will show the IP of the last node you traveled through.
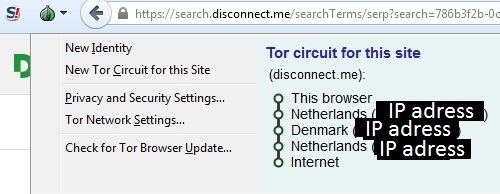
The downside of Tor is that it is slow, due to the fact that it works thanks to enthusiastic individuals. Tor is not for casual usage, but specifically for privacy needs, particularly posting online or searching the deep web.
Tor has some weaknesses you must be aware of:
First
Oftentimes when you are using a network, the network provider can’t see what you are browsing, but they can see that you are using Tor. You can use things like a bridge obfuscator, obfsproxy, or setting VPN to Tor. This is a complex issue, here is a guide on hiding tor usage from ISP (internet service provider).
Second
The trustworthiness of exit relays. When the government found out about the popularity of Tor they created their own exit nodes, that acted as honey traps. To fight this, use a TailsOS (or booted off a flash stick, DVD or SD card in a public wifi spot, like a coffee shop). That way even if the final node was a trap, it would only lead to your TailsOS profile, not your general one. Check so the public wifi spot you are using has no cameras around, so they will not be able to check camera footage of who used a laptop in that particular time frame. Don’t forget to log off when finished. Alternatively, use Tor to VPN.
Third
Often many programs, like torrents, will ignore Tor, even if you manually force them and just connect straight away, thus giving you away. The answer is to not use torrents with Tor. I REPEAT, NO FILE SHARING ON TOR.
There are of course other various vulnerabilities out there. And as a reminder, Silk Road, a large black market was cracked in the past.
COMBINING TOR WITH A VPN
Tor is good on its own but even better when combined with a VPN. There are 2 methods : Tor to VPN, VPN to Tor. Both have their weaknesses. First one allows ISPs to see you use Tor, the second does not protect from malicious end relays . VPN to Tor masks your Tor usage, Tor to VPN protects from malicious exit nodes.
I have thought of using VPN to Tor to VPN, which should theoretically accomplish both. For VPN to Tor use a secure VPN provider and add non-Tor traffic to mask usage. For Tor to VPN, pay with anonymized bitcoins and never connect to your VPN without connecting to Tor first.
VPN to Tor: The Harvard bomb hoaxer was de-anonymized because he was the only one in college using Tor. If he went through a VPN first, he would have been harder to track (assuming his VPN provider did not keep logs).
Tor to VPN: Protects from malicious exit nodes, on the other hand. TailsOS with public wifi accomplishes the same. Of course, either is better than nothing. Which you choose depends on your needs. The only two providers that offer Tor to VPN are AirVPN (based in Italy, so part of 14 eyes, but not the 5 eyes) and BolihVPN.
IF YOU DON’T WANT TO USE TOR
While using Tor is advisable, for casual usage you can set Firefox to be very secure with the help of add-ons and custom settings. Here is a guide.
WEBSITES THAT BAN VPN AND TOR
Certain websites ban Tor (e.g. Imgur). Use an alternative then (e.g. Anonmgur). Otherwise use VPN to Tor. There are VPN providers that cycle IPs, so that helps with VPN IP range bans.
TAILSOS
Windows is not very safe. There have been rumors of NSA backdoors on Windows devices. Supposedly NSA can store almost everything you do online (including Facebook, popular mail providers, and possibly things offline).
There are some good alternatives out there, TailsOs being one of them. TailOS is an operating system specifically designed for security and is Linux based. It can be ran off a USB stick. For those extra paranoid, use Tor in a public space on a laptop with TailsOS loaded of a flash drive.
Of course TailsOS is not very suitable for day to day needs, so use it for shitlord purposes. For your day to day purposes you might have to use Windows, but for the love of god, DO NOT use Windows 10, it is absolutely awful for security.
I prefer Windows 7. If you are more advanced, you can use alternative platforms like Debian or some distro of Linux or whatever. Just beware, many programs for Windows do not have alternatives on Linux based systems. If you are a casual, moving to another platform can be difficult. And if you really are a nerd, then you can look into some exotic setup like Qubes + Whonix or whatever other myriad of OS and Virtual Machines there are around.
4. Other darknet browsers

I2P network: While Tor is designed to anonymously browse the normal web and onion sites, I2P is a web of it’s own. Preferably to be browsed through Tor. It allows (slow) torrenting and great for messaging, IRC, file sharing, secret websites (.i2p)
Freenet – Freenet is a peer-to-peer platform for censorship-resistant communication.
5. Look into bitcoin and online currency
Bitcoin is virtual currency that has taken the world by storm in recent years. There are other online currencies competing against it, but Bitcoin is the most established online currency. It is the default virtual currency. Bitcoin is not for daily usage, rather online purposes. There are VPN services that accept payment with bitcoin. There are even services that will store physical gold in exchange for bitcoin.
Truly a financial revolution. Unfortunately, it’s also a big headache for tax services. Bitcoin is also infamous for being used to purchase illegal stuff on the internet black market. But you wouldn’t use it for that, would you?
To start using bitcoins just register a bitcoin wallet and you are good to go.
HOW TO INCREASE BITCOIN ANONYMITY
Bitcoins are not anonymous by default. They must be washed and anonymized. Buying through Tor + Coin mixing + anonymity patched bitcoin client. Over the counter (OTC) bitcoins are an option as well.
6. Use proper password protection
Never use the same password twice. Try to make it long and contain both characters and numerals, etc. Hint : use L33t, P@ssVV0r|)333. If you can, add non English characters even better, PåSsWøRд0, but you can’t always do it.
If you are unsure, use a safe password generator, such as Master Password To manage passwords use a password manager, such as KeePassX.
7. Use proper mail protection

Use throwaway email to register in most places. Never use your public e-mail to register anywhere controversial like Neomasculintiy affiliated websites.
SAFE MAIL PROVIDERS
For general mail needs, use a mail provider that is focused on security. I found two outside 14 eyes, in Switzerland: ProtonMail (free), NeoMailBox (50$/year, custom domain option ex : [email protected], [email protected])
Remember to still use personal safety measures, like additional encryption. Never trust 2nd parties with your protection completely.
BECOME AN EMAIL PROVIDER YOURSELF
Another interesting move is to become a provider yourself, in essence create your personal Gmail by turning your PC into a mail server. To do this, use Mail-in-a-box. They have good guide on their site https://mailinabox.email/.
USE A SAFE MAIL CLIENT
A mail client is a program that allows you to manage mail from the cloud by saving it locally, by connecting to the email host, such as Gmail. The default mail client in Windows is Microsoft Outlook (which sucks). I will focus on my preffered mail client setup.
1) Download Thunderbird
2) Install the Enigmail add-on, to allow encryption
3) Install the TorBirdy add-on, to make Thunderbird run through Tor
BEWARE THE LAW
Beware of a law that allows government officials to read any mail hosted online older than 6 months without a warrant. Use an external email client like Thunderbird or Enigmail, download your emails and store them locally. Never leave them on the server.
EMAIL ALTERNATIVES
Look into email alternatives such as : Bitmessage, I2P-Bote, Retroshare
8. Use encryption for messaging

Encryption is the process of making a message unreadable to third parties. Some programs do it for you, manually you can use a program like GPG4win or similar which uses PGP encryption.
The way it works is this :
1) You create your public key.
2) You digitally sign the information with your private key, so when the other side verifies it with their own public key, they can confirm that it is indeed YOUR public key. (WebOfTrust)
3) When someone wants to write to you he encrypts it using the public key you provided, or the other way around.
4) You then use your PRIVATE key to decrypt the message he sent you.
Here is a tutorial:
youtube
MOBILE ENCRYPTION
There are encryption possibilities for your phone as well. First, set encryption on your Android device. Second, use an app called Signal
9. Scrub EXIF data of photos you post online

When you take a photo with a particular device, often it registers what device you used to take the photo, when and where it was taken. To avoid this problem, before posting online use an EXIF scrubber. It is a piece of software that deletes all information that might incriminate you.
Some examples are BatchPurifier Lite and Exif Pilot. Also, careful with what photos you post of course, nothing that could indirectly lead to you.
10. Torrent and stream safely

Torrenting can be useful for file transferring. If you plan to torrent anything or share something with friends, look into safer peer to peer torrenting. P2P is good for small files. Generic torrent services are good for larger files.
One advice I have is avoid torrent programs known for their untrustworthiness, such as BitVomit (BitComet) and uTorrent (closed source + adBloat). qBit, Deluge, Tribler (this one’s interesting) are good options (open source and lightweight).
Beware of laws in certain countries that forbid downloading stuff online. Germany is particularly infamous for this. There are ways to combat this issues through VPNs. But DO NOT USE TOR, I REPEAT, DO NOT USE TOR FOR FILE SHARING. For even more secure anonymous file sharing look into I2P (beware avg speed: 30 kbs per sec)
As for streaming, Popcorn Time and other analogous services (such as PornTime) are used to stream new movies (and porn) respectively. They are based on BitTorrent technology. They are relatively safe services, as long as you use a VPN.
11. Encrypt the files on your PC
Use VeraCript, a piece of software designed to encrypt disk partitions or whole USB drives. It is the successor of TrueCrypt (which stopped development after feds asked them to include vulnerabilities).
https://www.youtube.com/watch?v=_fGUJ6AgOjQ
HIDE FILES IN IMAGES
Also, another interesting technique is to hide text, videos and other stuff in pictures, it’s called Steganography.
12. Look into this promising new technology for your online needs
The 3 pieces of software I am about to recommend are TOX , RetroShare and diaspora.
TOX is a Skype clone with focus on privacy.
Retroshare is a private network service. You can use it for private mailing and other purposes.
diaspora is a social network designed for privacy and decentralization https://diasporafoundation.org/
Another interesting possibility for ROK people is to use a .onion or .i2p domain or freenet for a sort of “secret” webpage, unavailable to casuals out there.
To summarize
I think this advice will benefit the ROK community for protecting their anonymity and using secret backup channels for future purposes. Here is a quick cheat sheet:
Casuals: VPN paid with shuffled bitcoin + VPNcheck Pro, Signal on Android, Firefox with add-ons for casual use, Tor for shitlordery, Encrypted mail and hard disk, password manager, ProtonMail for daily use, throwaway mail—everything else, Thunderbird with add-ons, EXIF scrubber. Download email on PC then delete off server.
Advanced: Same as above + Tor combined with VPN, I2P and Freenet, (TBitmessage I2P-Bote Retroshare) instead of mail, becoming mail provider, diaspora*
Super advanced: Same as above + Multiple VPNs, Using Tor off of TailsOS in a public space where cameras cannot film you. Alternative OS and Virtual machines. Secure you router.
Here’s a good collection of security resources.
Always remember, there is no way to remain completely anonymous, just ways to make it harder to be detected.
Read More: 5 Ways To Improve Your Online Game
1 note
·
View note
Text
How To Login My Kaspersky Antivirus? | My Kaspersky Login
You may need an activation login for your Kaspersky application not only for activation after the purchase but also for installation on a different device or in case any license problems occur. You can find the instructions on where you can find an Kaspersky login in this article. If it is not possible to find the code, you can recover it. Visit Us: Kaspersky login Call: 888-315-5450
https://avglogin.wixsite.com/avg-retail/post/how-to-login-my-kaspersky-antivirus-my-kaspersky-login
1 note
·
View note
Text
Cities under ransomware attack, 2019
*Kaspersky:
https://securelist.com/story-of-the-year-2019-cities-under-ransomware-siege/95456/
(...)
2019 has seen this plague actively shifting towards a new target – municipalities. Arguably, the most prominent and widely discussed incident was that in Baltimore, which suffered from a large-scale ransomware campaign that knocked out a number of city services and required tens of millions of dollars to restore the city’s IT networks.
Based on publicly available statistics and announcements monitored by Kaspersky experts, 2019 has seen at least 174 municipal organizations targeted by ransomware. This is an approximately 60% increase from the number of cities and towns that reported falling victim to attacks a year earlier. Whereas not everyone has confirmed the amount of extorted funds and whether a ransom was paid or not, the average demand for ransom ranged from $5,000 to $5,000,000, and on average was equal to around $1,032,460. The numbers, however, varied greatly, as the funds extorted from small town school districts, for example, were sometimes 20 times smaller than those extorted from city halls in big municipalities.
However, the actual damage caused by attacks, according to estimates by independent analysts, often differs from the sum that the criminals request. First of all, some municipal institutions and vendors are insured against cyber-incidents, which compensates the costs one way or another. Secondly, the attacks can often be neutralized by timely incident response.
Last but not the least, not all cities pay the ransom: in the Baltimore encryption case, where officials refused to pay the ransom, the city ended up spending $18 million to restore its IT infrastructure. While this sum might seem way more than the initial $114,000 requested by the criminals, paying the ransom is a short-term solution that encourages threat actors to continue their malicious practices. You need to keep in mind that once a city’s IT infrastructure has been compromised, it requires an audit and a thorough incident investigation to prevent similar incidents from occurring again, plus the additional cost of implementing robust security solutions.
Attack scenarios vary. For instance, an attack may be the result of unprotected remote access. In general, however, there are two entry points through which a municipality can be attacked: social engineering and a breach in un-updated software.
A vivid illustration of the latter problem has been observed quarterly by Kaspersky experts: the all-time leader of almost all rankings of ransomware most frequently blocked on user devices is WannaCry. Even though Microsoft released a patch for its Windows operating system that closed the relevant vulnerability months before the attacks started, WannaCry still affected hundreds of thousands of devices around the globe. And what’s more striking is the fact that it still lives and prospers.
The latest statistics gathered by Kaspersky in Q3 2019 demonstrated that two and a half years after the WannaCry epidemic ended, a fifth of all users targeted by cryptors were attacked by WannaCry. What’s more, the statistics from 2017 to mid-2019 show that WannaCry is consistently one of the most popular malware samples, accounting for 27% of all users attacked by ransomware in that time period.
An alternative scenario involves criminals exploiting human factors: this is arguably the most underestimated attack vector, as training of employees in security hygiene is nowhere near as universal as it should be. Many industries lose a tremendous amount of money due to employee errors (in some industries this is the case for half of all incidents), phishing and spam messages containing installers for dangerous malware are still circulating around the web and reaching victims. Sometimes those victims may be managing the company’s accounts and finances and not even suspect that opening a scammer email and downloading what appears to be a PDF file on their computers can result in a network being compromised.
Among the many types of municipal organizations attacked throughout 2019, some attracted more attacks than others.
The most targeted entities were undoubtedly educational organisations, such as school districts, accounting for approximately 61% of all attacks: 2019 saw operations against more than 105 school districts, with a whopping 530 schools targeted. This sector has been hit hard, yet demonstrated a resilience: while some colleges had to cancel classes, many educational institutions adopted a position of continuing studies despite a lack of technical support, claiming that computers have only recently become part of the educational process, and that staff are perfectly capable of teaching pupils without them. (((Good idea.)))
City halls and municipal centers, meanwhile, accounted for around 29% of cases. Threat actors are often aiming at the heart of processes that, if stopped, will result in an extremely problematic interruption of vital processes for the vast majority of citizens and local organizations. Unfortunately, such institutions are still often equipped with weak infrastructure and unreliable security solutions, as the workflow (especially in small, quiet towns or villages without advanced infrastructure) does not require high computing capacities. As a consequence, the locals often don’t bother updating old computers because they appear to still be functioning well. This might be related to a common mistake, whereby security updates are associated with design changes or technical developments introduced in the software, while their most vital function is in fact closing breaches found by white- or black-hat hackers and security researchers.
Another popular target was hospitals, accounting for 7% of all attacks. While some black-hat hackers and cybercriminal groups claim to have a code of conduct, in most cases attackers are motivated purely by the prospect of financial gain and go for vital services that cannot tolerate long periods of disruption, such as medical centers.
Furthermore, around 2% of all institutions subjected to an attack were municipal utility services or their subcontractors. The reason for this might be that such service providers are often used as an entry point to a whole network of devices and organizations, as they are responsible for communications in terms of billing for multiple locations and households.
In the scenario where threat actors successfully attack the service provider, they might also compromise every locality that particular vendor or institution services. In addition, the disruption of utility services may result in disruption to vital regular operations, such as providing online payment services for residents of the town or city to pay their monthly bills – this adds to the pressure the victims’ experience and pushes them towards a short-term, yet seemingly effective solution – paying the ransom.
Let’s take a closer look at the malware that has been actively used in attacks on municipalities....
3 notes
·
View notes
Text
download Kaspersky internet security 2019
download Kaspersky internet security 2019 is the URL to redeem your Kaspersky activation key. You need to go usa.kaspersky.com/downloads to redeem your Kaspersky.
How can Kaspersky Activate antivirus protect your virtual world downloaded from usa.kaspersky.com/downloads?
Kaspersky runs in the background taking minimum system space to reduce lags. Kaspersky antivirus identifies good data and hence scans are quick and safe.
It quickly scans all your incoming emails along with their attachments. Auto scans USB devices once plugged into the system for harmful files.
For all the Gamer’s, Kaspersky has a gaming mode that can suspend functions based on the user so that play is not interrupted with pop-up remainders or slow systems.
Steps to follow before installation of Kaspersky activate antivirus from usa.kaspersky.com/download:download Kaspersky internet security 2019
Redeem your retail card by visiting usa.kaspersky.com, Kaspersky retail card is necessary because it is the easiest way to download & install Kaspersky product in your PC.
This card will ensure that you have downloaded the latest version of security. Installing this security product or antivirus through an online twenty digit product key code must require. For installing this product follow some steps.
Make sure your system configuration meets the minimum system requirements.
System OS (operating system) should be updated properly so Kaspersky updates can install properly in the system.
Uninstall all the unwanted, similar and conflicting programs from the system.
Also, make sure, you remove all the temporary files from the system.
After following these steps, Download Kaspersky product by visiting usa.kaspersky.com.
Tips before Entering Kaspersky Activation Code:
Uninstall any other antivirus from your computer if you had any before. Remove it completely and restart your computer.
Also, uninstall any Old version of Kaspersky antivirus from the computer.
Most noteworthy you must restart your computer in order to completely remove a security after uninstall.
If still, you are facing a problem you can contact our support from the given contact link or on the toll-free number.
Best Features of Kaspersky Internet Security – download Kaspersky internet security 2019
After download Kaspersky Internet Security 2019 and you will get various key features.
A powerful antivirus solution for your device.
Complete protection tools.
Kaspersky Provides Internet Security, PURE and Antivirus.
Protect against phishing and other threats.
Create reports and notify the users.
malware protection
1 note
·
View note