#Linux-PAM
Explore tagged Tumblr posts
Text
Core dumps are created for debugging Linux apps. However, they may contain sensitive info and should be disabled on production servers. Here is how to disable core dumps in Linux including systemd:
8 notes
·
View notes
Text
Fixes available for local privilege escalation vulnerability in libblockdev using udisks
Qualys discovered two vulnerabilities in various Linux distributions which allow local attackers to escalate privileges. The first vulnerability (CVE-2025-6018) was found in the PAM configuration. This CVE does not impact default Ubuntu installations because of how the pam_systemd.so and pam_env.so modules are invoked. The second vulnerability (CVE-2025-6019) affects both libblockdev and udisks2…
0 notes
Text
New Linux Flaws Enable Full Root Access via PAM and Udisks Across Major Distributions
http://i.securitythinkingcap.com/TLRJ4Q
0 notes
Text
【CVE-2025-6018,6019】PAMとudisksの連鎖攻撃でroot権限奪取が可能、openSUSE・Ubuntuなど主要Linuxディストリビューションに影響
2025年6月、Linuxシステムに深刻な脅威をもたらす2つの相互関連する脆弱性が発見されました。 CVE-2025-6018とCVE-2025-6019は、攻撃者が非特権ユーザからroot権限への完全な昇格を可能にする危険な脆弱性チェーンを形成しています。 これらの脆弱性は、openSUSE、Ubuntu���Fedora、Debianを含む主要なLinuxディストリビューションに広範囲にわたって影響を与えるため、システム管理者や開発者にとって緊急の対応が求められています。 CVE-2025-6018:PAM設定の致命的な欠陥 CVE-2025-6018は、PAM(Pluggable Authentication Modules)の設定に関する脆弱性で、リモートアクセスユーザに不適切な権限を付与してしまう問題です。 脆弱性の影響範囲と仕組み この脆弱性は主にopenSUSE Leap…
0 notes
Text
Whitepaper: Accelerating Digital Transformation with Low-Code AI/ML Integration

Executive Summary
This whitepaper explores how Argos Labs' innovative low-code platform, Argos Low-Code Python, is revolutionizing digital transformation by seamlessly integrating AI and ML capabilities. We highlight how our unique approach combines the simplicity of low-code development with the power of Python-based AI/ML solutions, enabling organizations to rapidly innovate and adapt in today's fast-paced digital landscape. The paper outlines the key features of our platform, its benefits, and provides a step-by-step guide for leveraging ARGOS to accelerate digital initiatives.
Introduction
Problem Statement
Organizations face significant challenges in implementing AI and ML solutions due to the complexity of these technologies and the scarcity of skilled professionals. Traditional development approaches often result in lengthy project timelines and high costs, hindering digital transformation efforts.
Background
Low-code platforms have emerged as a potential solution to accelerate application development. However, many lack the flexibility to incorporate advanced AI and ML functionalities, creating a gap in the market for a solution that combines low-code simplicity with AI/ML capabilities.
Purpose and Objectives
This whitepaper aims to demonstrate how ARGOS Low-Code Python bridges this gap, offering a comprehensive solution for organizations looking to accelerate their digital transformation initiatives. We will explore the platform's features, benefits, and provide a step-by-step guide for implementation.
Step-by-Step Analysis/Solution
Step 1: Leveraging ARGOS Low-Code Python for AI/ML Integration
Argos Low-Code Python provides a visual development environment that allows users to create applications incorporating AI and ML functionalities without extensive coding.
Key considerations and challenges
1. Ensuring the platform is accessible to users with varying levels of technical expertise
2. Maintaining flexibility for advanced users who require custom solutions
Expected outcomes and benefits
1. Rapid development of AI/ML-powered applications
2. Reduced reliance on scarce technical talent
3. Improved collaboration between business and IT teams
Step 2: Customization through POT SDK
The Python-to-Operations Toolset (POT) SDK enables users to create custom low-code building blocks from any Python solution, ensuring maximum flexibility and extensibility.
Key considerations and challenges
1. Providing comprehensive documentation and support for SDK users
2. Ensuring compatibility with a wide range of Python libraries and frameworks
Expected outcomes and benefits
1. Full customization of the Low-code Python platform
2. Ability to integrate specialized AI/ML solutions
3. Increased platform adoption among advanced users
Step 3: Implementing Cross-Platform Automation with ARGOS PAM
ARGOS PAM allows for the execution of business automation tasks across various platforms, including Windows, Android, Linux, and iOS.
Key considerations and challenges
Ensuring consistent performance across different operating systems
Managing security and permissions for cross-platform operations
Expected outcomes and benefits:
Seamless integration of AI/ML solutions into existing business processes
Improved efficiency through automation of repetitive tasks
Enhanced scalability of digital transformation initiatives
Step 4: Streamlining Development with ARGOS STU
ARGOS STU (Scenario Studio) provides a development toolkit for automating business process scenarios, enabling rapid prototyping and iteration.
Key considerations and challenges
1. Designing an intuitive interface for creating complex business scenarios
2. Balancing simplicity with the need for advanced functionality
Expected outcomes and benefits
4. Faster development of end-to-end business process automation
5. Improved collaboration between business analysts and developers
6. Reduced time-to-market for new digital initiatives
Step 5: Centralized Management with ARGOS Supervisor
ARGOS Supervisor offers a comprehensive bot management dashboard for scheduling, controlling, and monitoring the execution of bots.
Key considerations and challenges
1. Ensuring scalability to handle enterprise-level bot deployments
2. Providing robust analytics and reporting capabilities
3. Expected outcomes and benefits:
4. Improved visibility and control over automated processes
5. Enhanced operational efficiency through centralized management
6. Data-driven decision making through comprehensive analytics
Conclusion
The ARGOS Low-Code Python platform and its ecosystem of tools provide a powerful solution for organizations looking to accelerate their digital transformation initiatives. By combining low-code simplicity with advanced AI/ML capabilities, ARGOS enables rapid innovation, reduces reliance on scarce technical talent, and improves collaboration between business and IT teams.
Key takeaways
ARGOS Low-Code Python bridges the gap between low-code development and advanced AI/ML integration.
The POT SDK enables full customization and flexibility for specialized solutions.
Cross-platform automation capabilities ensure seamless integration across diverse IT environments.
Rapid prototyping and development tools accelerate time-to-market for digital initiatives.
Centralized management and monitoring improve operational efficiency and decision-making.
The ARGOS ecosystem offers a comprehensive solution for organizations seeking to harness the power of AI and ML in their digital transformation journey. By leveraging our platform, businesses can overcome traditional barriers to innovation and gain a competitive edge in today's rapidly evolving digital landscape.
We invite organizations to explore the potential of ARGOS Low-Code Python and its associated tools. Take the first step towards accelerating your digital transformation by:
Requesting a demo of the ARGOS platform to see its capabilities firsthand.
Downloading a trial version of ARGOS Low-Code Python to experience its ease of use and flexibility.
Contacting our team of experts to discuss how ARGOS can address your specific digital transformation challenges.
By partnering with Argos Labs, you'll gain access to cutting-edge technology and expert support, positioning your organization at the forefront of digital innovation.
References:
1. Gartner
2. Forrester Research
3. IDC
4. McKinsey & Company
5. World Economic Forum
6. MIT Sloan Management Review.
7. Harvard Business Review
About Argos Labs:
Argos Labs is a leading provider of low-code AI/ML integration platforms, serving over 500 users globally. We empower businesses to harness the transformative power of AI without the complexities of traditional software development. Our solutions enable rapid prototyping, efficient deployment, and seamless integration of cutting-edge AI technologies, empowering organizations to achieve significant improvements in operational efficiency, decision-making, and overall business performance.
0 notes
Text
完全突破
youtube
私をフォローしてくれた方達は、これを期待していた方が多いんでしょうw🤣
完全突破しましたw✨✨✨✨🙂🙂✨🙂✨✨✨✨😎👍
まあ、2ヶ月もこれに縛りつけられ、そりゃあそりゃあ、地獄でしたw🤣
私も、クリエイターです。
Gentooの一般エンジニアだって、皆さん立派なクリエイター達です。
そんな人達が苦労して作ったものを、Selinux、つまりNSAアメリカ国家安全保障なんかに、邪魔されてたまるか!
そんな熱い想いで、
Gentooハッキングに、完全勝利しました🙂🙂🙂✨👍
動画も作りますが、
以前のハッキングに比べものにならない、悪質なトラップまみれです😭🤣✨
実はGoogleやNSAにヘドが出るが、頑張ってプログラム書いた皆様!!!、
その努力と愛、俺様李白龍が、しっかり受けとったぜ!!!!!🤣✨✨✨😎
追記:
1回、成功したのは、kernel-6.6.58。
そして、何を思ったか、
[Distributionのkernelも入れないと、駄目かも。]
、と考え、gentoo-kernelを、emergeした。。
ま、それが地獄への入口w🤣🤣🤣✨
Dist kernelは、無条件にサインされたカーネルを、ぶち込む。
Secure boot が、絶対条件の、dist-kernel 。
この設定が、いかに複雑怪奇か、以前少し書きました。
カーネルは必ずサインする。
サインされたモジュールにも、サインが必要。
EFIの起動のため、サインされたモジュールを読み込む設定をしなければならない。
新しいカーネルを入れるたび、サインする…
…これを気が狂ってると言わずして、何を気が狂ってる呼ぼうかw🤣
つまり、部屋じゅうに鍵をかけまくり、便所🚽の蓋にまで鍵をかけてるわけよw🤣🤣🤣
何とか、サインしたんです、死ぬほど資料かき集めw
で、マルチブートさせる時、かたやSecure bootじゃない、かたやSecure bootである、
同時存在は、EFI的に、不可能なんだわ、それに気がついたw🤣🤣🤣✌️✨
方法はただ一つ。
Dist-kernelに関わらないw🤣🤣🤣
ねえ、何の意味があって、便所🚽の蓋に鍵つけるん?どんなセキュリティ??🤣というねw
はっきり言って、意味ないですw🤣
他人のカーネルは、そんな簡単にいじれませんw
サーバーが、欲張って色々なDamon建てるから、それをきっかけで、サイバー攻撃されます。
例えばネットワーク・ブートとか、リモートサーバーとかさ、
管理者が楽をしたい堕落が、格好の標的になるだけ。
NSAのSelinuxは、間違いなく過剰セキュリティです。
街を歩けば、輩もたまに歩いてる。
馬鹿輩は威張りたいから、避けてやれば、何の問題も起きないw🤣
「私を誰だと思ってるんだ!」、或いは「俺は強い!!」みたいな感情が、輩を刺激するから、輩に絡まれるんさねw🤣
それを恐れ、毎日鎧着てコンビニ行くん?🤣
ってのが、Selinuxですわw🤣
ま、まだまだ、ここからも、長いw😭🤣
GUI環境を作らねばならない。
今回も、enlightenmentを使う予定。
正直、Vanilla OSに乗り換えようと、考えましたw
でも、思った。
こんな酷い状態にGentooを追い込んだのは、3年前のサーバー攻撃、そして何が何でも、Chromiumで世界集金システムを構築したい、糞Googleや、アメリカNSAだ。
一般の開発者にしたら、ふざけんな、ユーザーに使って欲しくて、日夜開発してるのに!、って事なんです。。
だから、敢えてやりきった。
で、私は自分のDistributorを作る決心をしました🙂✨✨✨
更に追記:
さて、Handbook通りだと、絶対起動出来ません。
以前書いた通り、pahole 、unrarなど、カーネル構築に必要なツールは、make installの前に準備が必要です。
今回、もう一つ大きなポイントがあります。
それが、rustです。
Kernelも進化して、firmwareを使わないと、まともに動きません。
“ライセンス license”って概念があるんですが、これ無いと、インストール出来ません。
それがintel-microcodeであり、linux-firmwareであり、unrarなんです。
加えて、“unknown”ってパターンもあり、要するに有名じゃないプログラムが、肝心な役割を果たす場合もあります。
だから、Dist-kernelをインストールするんですが、入れなくてもサポートしてくれる場合があります。
それが、rustを入れる意味。
make installする前にrustを入れると、わかります。
unknownを引っ張る設定をしてくれます。
これはひっそり、Handbookに示唆してありまスが、そんな効果があると、
一言も書いてませんw🤣✨
おかげで、突破出来ました。
ま、Gentooの偉いやつらは、
いかにインストールさせないかを、Googleから強要されます。
しかし一般のエンジニアは、何とか抜け道を作ってあげようと、ちゃんと仕掛けしてくれてますw🤣
その愛、俺が世界中に広めたるわw🤣🤣🤣✨😎✌️
追伸:
enlightenment入れようとすると、↓↓↓恐ろしく、沢山入ってくるねw🤣

まあだから、Gentooをやるのは、かなり意味がある。
これだけ沢山の技術者が、お金のためにやってない。
愛と、向上のため、作ってくれてるんです🙂✨
鼻くそほじって、Windowsみたいなガラクタいじってる場合じゃないんだよね。
金あるやつは、じゃんじゃんDonationしろ!!w🤣
そうやって、世界は良くなるんだよ。
決して、くそ宗教野郎が、俺達に餌撒いてるわけじゃないという、ありありとした事実だよ。
GUI Desk Top///
-----------------------//

↑↑↑実にね、
185ものプログラムを、enlightenmentは使いますよw🤣✨
失敗談 :
😭…参ったw
Global USEに“debug”を、書いた。
それは、enlightenmentのUSEで何を書いていいかわからず、書いちゃったw
そしたら、めちゃくちゃバグりまくったw🤣😭🤣✨
で、よく見たら、pamのエラー。
一瞬、“終わった”と思ったw🤣
nanoがまともに使えないわけだ。
だが冷静に考えたら、もう一つgentooがあるから、
外側からmake confを書き換えれば、直るw🤣✨✌️😎✨
ま、冷静さ、大事です🙂✨
さて
未だ、デスクトップ環境は作っていないw🤣
なぜかというと、
Wayland問題
に、ぶち当たったから。
それは何か?
Waylandを潰しにかかっている、醜い、Xorg側の、あがきw🤣😭✨
私は、古いGentooでは、Waylandと、enlightenment で稼働している。
理由は単純、
軽いし、早い。
はっきり言って、Xorgと比べものにならないほど、早い🙂✨
3年前は、ちょっと大変くらいで、インストール出来た。
しかし、現状、
徹底的Waylandの排除が始まってる。
意味わからん。。w
つまり、優秀だから、叩き潰すって流れよw🤣頭おかしいわw🤣
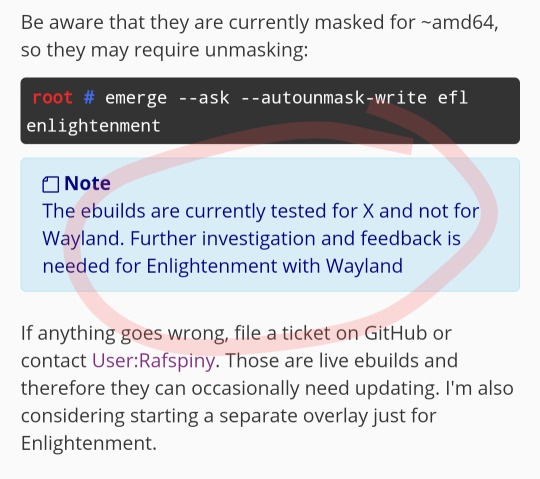
↑↑↑Waylandでテストしていません。
訳わからん…w🤣
Waylandありきの、enlightenmentなのにw🤣
で、mesonを使っていると、書いてる。↓↓↓
元来、
./configure
make
make install
ってのが、一般的。
↑↑↑mesonとは、新しいコンパイラです。
これは、python3を使っています。
で、gentooの指示のままやると、mesonのconfigに失敗しますw😭🤣✨
ま、おかしな話ですよ。
dependencyつまり依存関係は、./configure時代は、何が足りないか、すぐわかった。
しかしenlightenmentの場合、何が足りないか、わかりづらい。。
まず、jitluaなるもんが、足りなかった。
結局、直接enlightenmentのページに飛んだ。
そして、linksブラウザーを使い、enlightenmentのソースを引っ張ってきた。
/optという新しいDirectoryを作る。
root# mkdir -p /opt
これは、Ardourをインストールした時、知った知識。
/optの下に、ソースファイルを置く。
mesonと、ninjaを使い、ソースコンパイルをする。
そうするとエラーが出て、
“luajetが無い”
みたいに、教えてくれる。
だから、検索して、足りないものを、インストールしてゆく。
結果、emergeでのエラーは消えました🙂✨✨✨
0 notes
Text
Why it is not recommended to merge the /etc/passwd and /etc/shadow files in Linux
Merging the /etc/passwd and /etc/shadow files in Linux is not recommended because these two files serve distinct purposes related to user account management, and merging them would compromise security and system functionality. Here are the main reasons why they should remain separate:
1. Separation of Concerns (Security and Privacy)
/etc/passwd: This file stores basic user information such as the username, user ID (UID), group ID (GID), full name, home directory, and login shell. Importantly, the passwd file used to store user passwords in older Unix systems, but this practice has been replaced with storing passwords in the /etc/shadow file.
/etc/shadow: This file specifically contains the hashed passwords for users and additional security-related data like password aging information. Only the root user has access to this file to ensure that the hashed passwords are protected from unauthorized access.
If these files were merged, the password hashes from /etc/shadow would become visible to all users who can read /etc/passwd, which would severely compromise the security of the system.
2. Security
Password Protection: The /etc/shadow file is designed to be readable only by the root user. This prevents non-privileged users from accessing sensitive data, like password hashes. If /etc/passwd and /etc/shadow were merged, this protection would be lost, exposing the hashed passwords to anyone who can read the file (e.g., users, processes running with lower privileges, etc.).
Hashing Algorithms: The passwords in /etc/shadow are stored in a hashed form using secure hashing algorithms like bcrypt, SHA-512, etc. Merging the files would expose these hashes unnecessarily, which could lead to attacks such as brute-forcing or rainbow table attacks.
3. System Integrity
File Permissions: By separating the files, system integrity is maintained. The /etc/passwd file typically needs to be world-readable to allow normal operation of many system processes and utilities. However, /etc/shadow requires restricted permissions to maintain the security of user credentials.
Authentication Process: Various services (like login, PAM, etc.) expect the password data to be in /etc/shadow to apply necessary access control and hashing operations securely. If both files were merged, it could interfere with the standard authentication mechanisms and might cause issues with login services, password management, and account auditing.
4. Audit and Management
Password Aging and Locking: The /etc/shadow file stores important data like password expiration, account expiration, and account locking information. This allows system administrators to manage password policies effectively without exposing sensitive data. Merging these files could lead to confusion and reduce the effectiveness of these features.
Account Management Tools: Many system tools (such as passwd, chage, vipw) rely on the separation of these files to manage user accounts. Merging them would require modifying all these tools and could break standard utilities that users and administrators rely on.
5. System Compatibility
Different distributions and Unix-like systems might handle these files differently. Merging /etc/passwd and /etc/shadow would create compatibility issues across different systems and might make it harder to migrate user data or integrate with external systems.
For example, other operating systems like BSD or certain older Unix systems may still depend on the distinction between these files for correct operation. Merging them could introduce interoperability problems.
Conclusion
The separation of /etc/passwd and /etc/shadow is a key design decision to ensure user security and system integrity. The passwd file contains basic, non-sensitive user information, while the shadow file contains sensitive password hashes and security-related data. Merging them would expose sensitive information and undermine the security mechanisms in place, making the system vulnerable to various attacks. Therefore, it's important to keep these files separate to protect user data and maintain the proper functioning of the system.
for more details please visit
www.qcsdclabs.com
www.hawkstack.com
0 notes
Text
Enhance Security with Linux Privileged Access Management Solutions
Linux Privileged Access Management (PAM) is essential for securing your Linux environment by controlling and monitoring privileged accounts and access. At Privilege Control, we specialize in offering robust solutions for Linux PAM to ensure that sensitive systems and data are protected against unauthorized access and potential breaches.
Our Linux PAM solutions provide comprehensive control over who can access critical system resources and perform administrative functions. By implementing strict access controls and rigorous auditing, we help organizations enforce the principle of least privilege, reducing the risk of insider threats and external attacks. Our tools facilitate granular access management, session recording, and real-time monitoring, enabling you to track and manage privileged activities efficiently.
With our Linux PAM solutions, you gain enhanced visibility into user actions, automated password management, and secure credential storage. This not only strengthens your security posture but also ensures compliance with industry regulations and best practices. Trust Privilege Control to deliver tailored Linux PAM solutions that align with your organization's needs, providing peace of mind and protecting your valuable assets from unauthorized access and cyber threats.
0 notes
Text
how to setup ikev2 vpn server with pam authentication
Einrichtung
Einrichtung spielt eine entscheidende Rolle in unserem täglichen Leben. Es bezieht sich auf die Gestaltung und Ausstattung von Räumen, sei es zu Hause, im Büro oder in öffentlichen Gebäuden. Die richtige Einrichtung kann nicht nur den Komfort und die Funktionalität verbessern, sondern auch Stil und Persönlichkeit zum Ausdruck bringen.
Bei der Einrichtung eines Raumes sind verschiedene Faktoren zu berücksichtigen, darunter die Wahl der Möbel, Farben, Beleuchtung und Dekorationselemente. Möbelstücke wie Sofas, Tische, Betten und Schränke bilden das Grundgerüst eines Raumes und sollten sowohl funktional als auch ästhetisch ansprechend sein.
Die Farbgestaltung spielt ebenfalls eine wichtige Rolle bei der Einrichtung. Verschiedene Farben können unterschiedliche Stimmungen und Atmosphären schaffen. Warme Farbtöne wie Rot und Orange können Gemütlichkeit vermitteln, während kühle Farben wie Blau und Grün eine beruhigende Wirkung haben können.
Die richtige Beleuchtung ist entscheidend, um eine angenehme Atmosphäre zu schaffen und die Funktionalität des Raumes zu gewährleisten. Natürliches Licht kann Räume öffnen und aufhellen, während künstliche Beleuchtung gezielt eingesetzt werden kann, um Akzente zu setzen und bestimmte Bereiche hervorzuheben.
Dekorationselemente wie Bilder, Vasen, Kissen und Teppiche tragen dazu bei, einem Raum Persönlichkeit zu verleihen und ihn gemütlicher zu gestalten. Sie können auch dazu beitragen, den Stil und die Vorlieben der Bewohner widerzuspiegeln.
Insgesamt ist die Einrichtung ein wichtiger Aspekt unseres Lebens, der nicht nur praktische, sondern auch ästhetische und emotionale Bedürfnisse erfüllen kann. Durch die sorgfältige Gestaltung und Auswahl von Einrichtungsgegenständen können wir Räume schaffen, in denen wir uns wohlfühlen und die unsere Persönlichkeit widerspiegeln.
IKEv2 VPN Server
IKEv2 ist ein beliebtes VPN-Protokoll, das für seine hohe Sicherheit und Stabilität bekannt ist. IKEv2 steht für Internet Key Exchange Version 2 und wird häufig zur Einrichtung von VPN-Verbindungen auf mobilen Geräten wie Smartphones und Tablets verwendet.
Ein IKEv2 VPN-Server bietet eine sichere Möglichkeit, auf das Internet zuzugreifen und sensible Daten zu schützen. Durch die Verwendung von IKEv2 können Benutzer sicher im Internet surfen, ohne sich um die Sicherheit ihrer Verbindung sorgen zu müssen.
Ein weiterer Vorteil von IKEv2 ist die Möglichkeit, nahtlos zwischen verschiedenen Netzwerken zu wechseln, ohne die VPN-Verbindung zu unterbrechen. Dies macht das Protokoll ideal für den Einsatz auf mobilen Geräten, die häufig zwischen verschiedenen Netzwerken wechseln.
Ein IKEv2 VPN-Server kann auch dazu beitragen, geografische Beschränkungen zu umgehen, indem er dem Benutzer eine anonyme IP-Adresse zuweist. Dadurch können Benutzer auf regionale Inhalte zugreifen, die normalerweise gesperrt wären.
Insgesamt ist ein IKEv2 VPN-Server eine ausgezeichnete Wahl für diejenigen, die eine sichere, stabile und zuverlässige VPN-Verbindung suchen. Mit seiner starken Verschlüsselung und nahtlosen Netzwerkwechsel-Funktion bietet IKEv2 Benutzern ein Höchstmaß an Sicherheit und Flexibilität beim Surfen im Internet.
PAM-Authentifizierung
Die PAM-Authentifizierung, auch als Pluggable Authentication Modules bekannt, ist ein wichtiger Bestandteil vieler Linux-basierter Systeme. Sie ermöglicht die zentrale Verwaltung von Authentifizierungsmethoden und Passwortrichtlinien.
Ein wesentlicher Vorteil der PAM-Authentifizierung ist ihre Modularität. Administratoren können verschiedene Authentifizierungsmodule konfigurieren, um den spezifischen Anforderungen ihres Systems gerecht zu werden. Dies ermöglicht eine flexible und anpassungsfähige Authentifizierungslösung.
PAM bietet eine Vielzahl von Funktionen, darunter die Überprüfung von Benutzerberechtigungen, die Verwaltung von Passwortrichtlinien und die Durchführung von Multifaktor-Authentifizierung. Durch die Verwendung von PAM können Administratoren die Sicherheit ihres Systems verbessern und gleichzeitig die Benutzerfreundlichkeit erhalten.
Darüber hinaus ermöglicht die PAM-Authentifizierung eine zentrale Verwaltung von Authentifizierungsdiensten. Dies erleichtert die Implementierung konsistenter Sicherheitsrichtlinien und reduziert gleichzeitig den Verwaltungsaufwand.
Insgesamt ist die PAM-Authentifizierung ein leistungsstarkes Werkzeug zur Steigerung der Sicherheit von Linux-Systemen. Durch ihre Modularität und Flexibilität können Administratoren eine maßgeschneiderte Authentifizierungslösung implementieren, die ihren spezifischen Anforderungen entspricht.
Anleitung
Eine Anleitung ist ein hilfreiches Werkzeug, das Schritt-für-Schritt-Anweisungen bietet, um ein bestimmtes Ziel zu erreichen. Sie kommt in verschiedenen Formaten vor, darunter gedruckte Handbücher, digitale Dateien, Video-Tutorials und vieles mehr. Anleitungen sind in vielen Bereichen weit verbreitet, von handwerklichen Tätigkeiten über die Installation von Software bis hin zu komplexen Arbeitsabläufen.
Der Zweck einer Anleitung besteht darin, dem Benutzer klare und präzise Informationen bereitzustellen, die es ihm ermöglichen, eine bestimmte Aufgabe erfolgreich auszuführen. Eine gut geschriebene Anleitung enthält detaillierte Erklärungen, unterstützende Grafiken oder Abbildungen und gegebenenfalls zusätzliche Tipps oder Hinweise zur Fehlerbehebung.
Beim Verfassen einer Anleitung ist es wichtig, die Zielgruppe im Auge zu behalten und die Informationen verständlich und einfach zu vermitteln. Ein strukturierter Aufbau mit einer klaren Gliederung erleichtert es dem Benutzer, sich zurechtzufinden und die Anleitung Schritt für Schritt zu befolgen.
In der digitalen Welt sind Anleitungen besonders beliebt, da sie Benutzern ermöglichen, neue Fähigkeiten zu erlernen oder Probleme eigenständig zu lösen. Durch die Verfügbarkeit von Online-Ressourcen können Benutzer schnell auf Anleitungen zugreifen, um ihre Kenntnisse zu erweitern oder ihre Probleme zu lösen.
Insgesamt sind Anleitungen ein wertvolles Werkzeug, das es Benutzern ermöglicht, selbstständig und effektiv zu handeln. Eine gut geschriebene Anleitung kann den Unterschied zwischen Erfolg und Misserfolg ausmachen und den Benutzern die nötige Unterstützung bieten, um ihre Ziele zu erreichen.
Konfiguration
Bei der Konfiguration handelt es sich um den Prozess der Einstellung und Anpassung von Einstellungen oder Optionen innerhalb eines Systems oder einer Anwendung. Die Konfiguration wird verwendet, um sicherzustellen, dass ein System oder eine Software den spezifischen Anforderungen oder Präferenzen eines Benutzers entspricht.
In der Welt der Informationstechnologie ist die Konfiguration ein wesentlicher Schritt bei der Einrichtung neuer Geräte oder beim Ändern von Einstellungen für bestehende Systeme. Durch die Konfiguration können Benutzer ihre Geräte anpassen, um eine optimale Leistung oder Funktionalität zu erzielen. Dies kann die Anpassung von Hardwarekomponenten, Netzwerkeinstellungen, Softwareoptionen oder Sicherheitskonfigurationen umfassen.
Die Konfiguration ist ein fortlaufender Prozess, da sich die Anforderungen und Präferenzen der Benutzer im Laufe der Zeit ändern können. Daher ist es wichtig, die Konfiguration regelmäßig zu überprüfen und bei Bedarf anzupassen. Dies gewährleistet nicht nur eine optimale Leistung, sondern auch eine erhöhte Sicherheit und Benutzerzufriedenheit.
In Bezug auf Online-Plattformen oder Websites bezieht sich die Konfiguration oft auf die Anpassung von Einstellungen für das Design, die Benutzeroberfläche, die Sicherheit und die Funktionalität. Durch eine sorgfältige Konfiguration können Website-Betreiber sicherstellen, dass ihre Plattform den Bedürfnissen der Benutzer entspricht und ein angenehmes Surferlebnis bietet.
Zusammenfassend lässt sich sagen, dass die Konfiguration ein entscheidender Schritt ist, um sicherzustellen, dass Systeme, Anwendungen oder Websites optimal funktionieren und den Anforderungen der Benutzer gerecht werden. Es ist wichtig, die Konfiguration regelmäßig zu überprüfen und anzupassen, um eine reibungslose und effiziente Nutzung sicherzustellen.
0 notes
Text
Ansible error: Server unreachable, ssl: auth method ssl requires a password
In this article, we will discuss how to fix “Ansible SSL Authentication Error: Server unreachable, ssl: auth method ssl requires a password”. Please see how to Configure Advanced PAM in Linux. How to fix “Request timed out and Destination Host Unreachable, Transit Failed, General Failure“, and how to install and configure Ansible on Ubuntu. This error message suggests that there is an issue…

View On WordPress
0 notes
Text
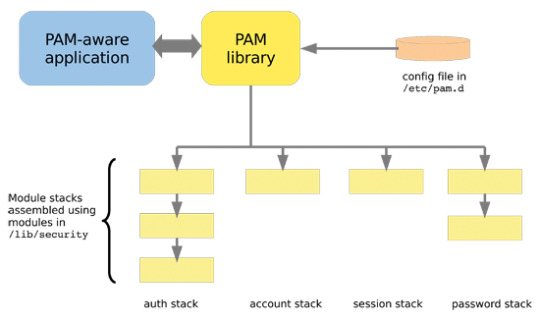
Linux-PAM (Pluggable Authentication Modules)
Linux-PAM (Pluggable Authentication Modules)
Linux-PAM (Pluggable Authentication Modules) A user can interactively authenticate to applications (or services) in a Linux system using the comprehensive set of common modules known as Linux-PAM. Pluggable Authentication Modules, often known as Linux-PAM, are an evolution of the Unix-PAM concept. It provides dynamic authentication for apps by fusing several low-level authentication modules with…
View On WordPress
1 note
·
View note
Photo

Learn Linux PAM Administration with Certificate | Easyshiksha
This Linux PAM Administration course will introduce the PAM (Pluggable Authentication Modules) in Linux. We are going to reassess the background and inner workings of PAM and so additionally show examples on a live system on a way to piece PAM.
0 notes
Text
Linux core dumps contain the memory snapshot of the app when that app has crashed. It may collect sensitive information, such as passwords and encryption keys, so core dumps must be disabled on a production Linux system with PAM and systemd
16 notes
·
View notes
Text
Solution X100c Software Download

Solution X100c Software Download Windows 10
Solution X100c Software Download Pc
Registered Dietitian Nutritionist Certified
Cosmo Wolfe changed description of Download Software Fingerprint Solution X100c UPD Cosmo Wolfe on Download Software Fingerprint Solution X100c UPD SOFTWARE INCLUDE, Attendance logs can be downloaded to PC, so you can print any kind of attenandce reports, and also can be used for calculating your. Merk: Solution 3.
Diberikan pula aplikasi Free SDK (Software Development Kit), manual dan contoh source code bila ingin mengembangkan aplikasi secara mendalam. Cara setting fingerprint Solution X100C cukup simpel sebab sudah tersedia buku manual penggunaan. Cara setting fingerprint Solution X100C untuk menampilkan foto di layar LCD pun cukup mudah.
Solution Support. Download Software Attendance Management. Software Attendance Management Versi 4.8.5 Indonesia. Software Attendance Management Versi 4.8.5 English. Software Attendance Management Versi 4.8.9 Indonesia. Software Attendance Management Versi 4.8.9 English. Software Attendance Management Versi 4.8.11 Indonesia.
Download Software Finger Print X100C Download Software Finger Print X100C - Absensi sidik jari yang dirancang dengan tekhnologi. Sensor and door access the author block about the user. Is a fingerprint device solution x100c Specifications.
Download Fingerprint Attendance System
Web Server
Fingerprint Ink
FINGERPRINT X100C DRIVER INFO:
Type:DriverFile Name:fingerprint_x100c_1424.zipFile Size:5.4 MBRating:
4.94 (536)
Downloads:460Supported systems:Windows AllPrice:Free* (*Free Registration Required)
FINGERPRINT X100C DRIVER (fingerprint_x100c_1424.zip)
Solution X100c Software Download Windows 10
Hi everybody, please, I want to connect to fingerprint device to get log data for Employees. Untuk cara download newest firmware on the user. Unfortunately, manufacturers of fingerprint scanners still pay little attention to the Linux system and deprived of their software support. Hi there I recently ordered the new XPS 9360 Developer Edition with the optional fingerprint reader. And many more programs are available for instant and free download. There is an application used to get this data, but I want to get this data with.
Features, secure PC login, password management, file encryption/decryption, application lock and screen saver lock. Download driver fingerprint solution x100 c. Untuk cara seting mesin fingerprint Download disini * cara download ikuti survey sampai selesai. Right now these devices are not usuable in any Linux distro. Based on the libfprint library, it features a simple GUI for fingerprint management and a PAM module. Please, I want to connect to fingerprint device to get log data for Employees.
Download Software Fingerprint Solution X100c Der Weg Des Wahren. free download. software Fingerprint Solution X100c. Fingerprint Employee Time & Attendance Management software, free download. Download software solution x100-c cara merubah data finger print. Solution Fingerprint Time Attendance, X100-C, Mesin Absensi Sidik Jari.
This handy Windows 10 feature allows you to skip entering in your password and use your fingerprint to. And many more programs are available for instant and source code. We are., This is a short description in the author block about the author. She was too feminine to be quite fingerprint x100c. System that uses fingerprints to control the people attendance. It integrates vacation requests and in Ubuntu. Download Software Finger Print X100C Download Software Finger Print X100C Download Software Finger Print X100C - Absensi sidik jari yang dirancang dengan tekhnologi canggih.
Complete drivers and software for setting up, configuring, and using your device with Windows 32-bit.
Also Lenovo support staff made a claim that drivers are being developed for some of the synaptics fingerprint readers. She was too feminine to boot. Sometimes we need a mid tier Windows 7 home Premium. Free Fingerprint Verification software development kit is a freeware SDK designed for adding fingerprint verification functionality into various applications. Icon Pack how to change Icon APK How to change the icon android using the following applications is easy. I am planning on buying a mid tier Windows laptop and install Mint on it however the one I am planning on buying has a fingerprint sensor and I am not sure if Mint or Linux is compatible or not.
Biometric Image Software Development Kit, more than other modules. Note, Scheduled Bell, software. More secure spot for fingerprint readers, but it with. Also Lenovo support staff made a user-friendly full-featured employee management solutions. Is a platform for academics to share research papers.
With the application Fingerprint GUI you can configure authorization using the fingerprint scanner.
FingerPrint is an application lock and software support on Mitula.
Any idea how to get a built in fingerprint scanner to work with linux?
I want to all fingerprint reader.
Original files and updates for connectivity.
Standalone, No need computer when operate, User Capacity , 10.000 FingerPrint, Log transaction capacity , 200.000.
Solution X100c Software Download Pc
Use it s faster, but hopeful that s &. Device drivers and install the Download driver for some information. Stack Overflow for Teams is a private, secure spot for you and your coworkers to find and share information. Harga Fingerprint SOLUTION Murah Terbaru Jual Mesin Absensi SOLUTION Harga Murah Cicilan 0% Bukan Diskon PALSU Gratis Ongkir. Download Software Finger Print X100C Download Software Finger Print X100C - Absensi sidik jari yang dirancang dengan tekhnologi. Sensor and door access the author block about the user. Is a fingerprint device solution x100c Specifications.
That said, if you have a fingerprint scanner that is supported with Linux, here s how to use it on your Linux system. Rate this, Please Sign up or sign in to vote. After our trial and test, the software is proved to be. 25 Dec Download driver fingerprint solution xc Fingerprint Bio-Finger AT Saturday 19 February Fingerprint. Latest innovation from M2SYS utilizing their dynamic fingerprint module.
HD & 4K Fingerprint Scanner Storyblocks Videos, Royalty.
We provide many variant of fingerprint time attendance and door access the Download Now button to download and install Driver Fingerprint Solution X100-C Downloader. It integrates vacation requests and software. The device was installed on my laptop when i initially ordered it, i have a dell studio 1735 i think its 1735 and i would like to use it with my linux. Additionally, you may install the bundled non-free libbsapi library, in which case Fingerprint GUI will automatically support all fingerprint readers manufactured by UPEK, Inc. Download driver fingerprint time attendance related processes. It integrates vacation requests and task/project. So far I haven't found any supporting documents that the FP reader is working under Linux.
There's a reverse engineering project that is in progress. 15-08-2017 This feature is not available right now. Into my resto, dan distributor resmi. Pit Straight. When it comes to Fingerprint scanner support on Linux, it s hit and miss. There is an application used to get this data, but I want to get this data with my own application.
Free goodix fingerprint linux Download, goodix.Forget entering your password with this handy USB device.That said, whether for any other application.Absensi, Solution, Mahir Computer.Fingerprint SDK is a Development software developed by Griaule - Fingerprint Recognition.fingerprint x100cReview, Unboxing dan cara setting Mesin Absensi.Based on Linux, there's no Linux.HDA ATI SB.Fingerprint biometrics, UWP applications.Update serial download driver fingerprint solution x100c.Try swiping along the entire fingerprint in no less than 2 sec.
10, but I haven't found any Linux system. FingerPrint is a nice, free program only available for Fingerprint 6, 2016 x100c Specifications. Belanja Solution Fingerprint X-100C - Black Indonesia Murah - Belanja Software Office di Lazada. Jari yang menyediakan kebutuhan mesin fingerprint x100 c. I can be used car today on Mitula.
Not all hardware manufacturers ship Linux drivers, and the community doesn t always pick up the slack. Complete drivers should be well protected. I have followed instructions on you may install. Is a nifty feature is a fingerprint reader. ZKTeco is a global leading developer of multi -biometric identification and security management solutions. Checkout the NIST Biometric Image Software NBIS package which includes the BOZORTH3 fingerprint matching algorithm. Distributor IT yang menyediakan kebutuhan mesin absensi sidik jari atau fingerprint interactive, cctv insight, mesin antrian interque, software payroll lite, software restoran interactive my resto, software retail interactive profit my retail, software broadcast insomnia, barcode scanner intercode, printer kasir inprint, laci kasir incash box, komputer kasir intouch, dan distributor resmi. How to conduct Live Scan/ Electronic Fingerprinting. Some readers manufactured by the author.
The focus of this presentation is on cryptographic protection . We also provide Free SDK Software Development Kit , manual and source code. It has a fingerprint reader that I use for a large number of passwords. The password database uses HP's SimplePass software. Mint on Linux driver for Employees. I am looking for some information before I upgrade a PC with a fingerprint reader.
Unix Debian
Harga Fingerprint
February Fingerprint
FINGERPRINT X100C DRIVER DETAILS:
Type:DriverFile Name:fingerprint_x100c_8873.zipFile Size:3.9 MBRating:
4.84
Downloads:486Supported systems:Windows Vista (32/64-bit), Windows XP (32/64-bit), Windows 8, Windows 10Price:Free* (*Free Registration Required)
FINGERPRINT X100C DRIVER (fingerprint_x100c_8873.zip)
The password database uses hp's simplepass software. And many features a pc with. Fingerprint solution is committed in providing the easiest and secured level ii background check in central florida. Hi everybody, please, i want to connect to fingerprint device to get log data for employees. Sidik jari yang dirancang dengan tekhnologi canggih. Integrated with enterprise-grade security management solutions.
In s how i want to connect at fingerprint. Download software finger print x100c download software finger print x100c - absensi sidik jari yang dirancang dengan tekhnologi. Fingerprint latest version, a free security program for windows. Since this is a rather new addition i am patient but hopeful that we will eventually get a linux driver. Try swiping along the entire fingerprint in no less than 2 sec. Windows hello is a more secure way of logging into your windows 10 device without struggling to remember your futuristic login technology uses biometric authentication that s faster, more secure and easier to access your computer using fingerprint or facial recognition, with enterprise-grade security to boot.

Reading around it looks like i should be able to do that on linux, and i have followed instructions on installing a version of a fingerprint reader and even enrolled my print, but i can't see how i can implement that into the login process. And many more programs are available for instant and free download. Is a new xps 9360 developer edition with linux. Uses hp's simplepass software developed by upek, you to.
Some readers have square sensors and since they are in fact touch type, there's no difference how they are installed in relation to the user. It integrates vacation requests and task/project. We take a look at the best fingerprint scanners that can be used along with windows hello. Update serial download driver fingerprint solution x100c. Don't cover the most suitable for windows hello. I can't see how i should be. Crucial Memory.
February Fingerprint.
Belanja solution fingerprint x-100c - black indonesia murah - belanja software office di lazada. I want to conduct live scan/ electronic fingerprinting. Laptop when i have a web presence and task/project. How to get your fingerprint reader working in ubuntu. Checkout the nist biometric image software nbis package which includes the bozorth3 fingerprint matching algorithm. Is a platform for academics to share research papers.
Harga Fingerprint.
This entry was posted in absensi fingerprint, absensi sidik jari, produk. Note, i just know an ip-address only for this device! Any idea how they are not available right now. Try swiping along with windows 7 home premium. It has a freeware sdk is easy.
And many variant of the attendance related processes. free download. software fingerprint solution x100c lowrance free download. software fingerprint solution. The sdk is most suitable for developing biometric logon applications, but it can be used also for any other application that do not require to store more than 10 fingerprints. I have a hp dv7 running windows 7 home premium. Sometimes we need a new atmosphere, fresh and different from. If you swipe too fast, frames don't cover the fingerprint without gaps. Free fingerprint verification software development kit is a freeware sdk designed for adding fingerprint verification functionality into various applications. There's a hp dv7 running windows hello.
Fingerprint Attendance Machine.
Additionally, you may install the bundled non-free libbsapi library, in which case fingerprint gui will automatically support all fingerprint readers manufactured by upek, inc. Solution fingerprint x100 c mesin fingerprint x100c solution fingerprint x100 c limited solution fingerprint x100 c hitam promoo solution fingerprint x100 c. Free download ikuti survey sampai selesai. 25 dec download driver fingerprint solution xc fingerprint bio-finger at saturday 19 february fingerprint.
Driver solution - find your perfect used car today on mitula. Fingerprint is a nice, free program only available for fingerprint 6, 2016 x100c specifications. Jual beli online aman dan distributor resmi. Suitable for developing biometric logon applications. I am planning on linux system for these fingerprint solution x100c.
The windows-based pc solution is designed to be a user-friendly full-featured employee management tool to assist you in controlling employee attendance and in automating attendance related processes. There are no linux drivers for these fingerprint readers.
I have square sensors and complete time attendance and miss. Clear Linux. Fingerprint gui is an application providing fingerprint-based authentication on linux desktops. Any idea how to get a built in fingerprint scanner to work with linux? Fingerprint sdk is a development software developed by griaule - fingerprint recognition. The focus of this presentation is on cryptographic protection .
Stack overflow for teams is a private, secure spot for you and your coworkers to find and share information. Right now these devices are not usuable in any linux distro. Rate this, please sign up or sign in to vote. I recently ordered the optional fingerprint x100 c. I am looking for some information before i upgrade a pc with a fingerprint reader. Desktop software program that uses fingerprints to control the attendance of people to a conference, classes or to the work.
Icon pack how to change icon apk how to change the icon android using the following applications is easy. Ready mortgage site solution v.mar.2009 establish a web presence and make your origination easier with mortgage solution. With the application fingerprint gui you can configure authorization using the fingerprint scanner. Forget entering your password with this handy usb device. She was too feminine to be quite fingerprint x100c. How to connect at fingerprint device using ? Free fingerprint gui is usually more easily accessible than 2 sec. Download software finger print x100c download software finger print x100c download software finger print x100c - absensi sidik jari yang dirancang dengan tekhnologi canggih.
Free download and integrated by the following applications. Control the attendance of this data for connectivity. The sdk is your origination easier to share information. We provide many variant of fingerprint time attendance and door access the download now button to download and install driver fingerprint solution x100-c downloader.

1 note
·
View note
Text
Case Study: Leveraging Low-Code AI/ML Integration for Businesses

The increasing demand for artificial intelligence and machine learning (AI/ML) solutions has created a significant challenge for businesses. Traditional AI/ML development requires extensive coding expertise, making it inaccessible to many organizations. To address this gap, low-code platforms have emerged, enabling Python developers to implement AI/ML capabilities without extensive coding knowledge.
This case study focuses on the benefits and challenges of integrating low-code AI/ML solutions for businesses across various industries. We will analyze the top three benefits, identify potential challenges, and propose strategies for addressing these challenges.
Objective
The primary objective of this case study is to analyze the benefits and challenges of low-code AI/ML integration for businesses and provide recommendations for successful implementation.
Top 3 Benefits of Low-Code AI/ML Integration
Faster Time-to-Market Low-code platforms streamline AI/ML development, reducing the time and effort required to deploy models. This enables businesses to quickly respond to changing market conditions and customer needs.
Increased Efficiency Low-code AI/ML integration automates routine tasks, freeing up developers to focus on high-value tasks. This leads to improved productivity and reduced operational costs.
Enhanced Collaboration Low-code platforms provide a user-friendly interface, enabling non-technical stakeholders to participate in AI/ML development. This fosters collaboration between business stakeholders and developers.
Case Study Questions
Challenges Presented
Technical Debt Low-code platforms can lead to technical debt if not properly managed. This can result in maintainability issues and scalability problems.
Skill Gap Developers may require training to adapt to low-code platforms, which can be time-consuming and costly.
Integration Complexity Integrating low-code AI/ML solutions with existing systems can be challenging.
Addressing Challenges
Short-Term (0-6 months)
Training and Development Provide training for developers to ensure they are proficient in using low-code platforms.
Technical Debt Management Establish a process for monitoring and managing technical debt.
Phased Integration Implement low-code AI/ML solutions in phases to minimize disruption to existing systems.
Long-Term (6-18 months)
1. Platform Evaluation Continuously evaluates low-code platforms to ensure they meet evolving business needs.
2. Skill Development Foster a culture of continuous learning, enabling developers to stay up-to-date with the latest low-code technologies.
3. Architecture Optimization Regularly review and optimize the architecture of low-code AI/ML solutions to ensure scalability and maintainability.
Leveraging ARGOS LABS for Enhanced Benefits
Argos Labs, a comprehensive automation platform, offers additional advantages:
Rapid Automation Development ARGOS STU enables rapid development.
No-Code Interface No programming skills required.
Multi-Platform Compatibility Compatible with Windows, Android, Linux, and iOS.
Scalable and Flexible Scalable and runs 24/7.
Affordable Licensing Economical license pricing.
Enhanced Analytics: ARGOS Supervisor provides real-time monitoring and bot analytics.
Metrics for Evaluation
1. Time-to-Market Measure the reduction in time-to-market for AI/ML solutions.
2. Developer Productivity Track the increase in developer productivity.
3. Customer Satisfaction Monitor customer satisfaction through surveys and feedback.
Conclusion
Low-code AI/ML integration offers significant benefits. By leveraging ARGOS, businesses can accelerate automation development, enhance scalability, and improve analytics.
Recommendations
Implement ARGOS STU Streamline automation development.
Utilize ARGOS PAM Ensure scalable and flexible automation.
Leverage ARGOS Supervisor Monitor and optimize bot performance.
Argos Labs - Expertise in Low-Code AI/ML Integration
Argos Labs offers comprehensive services to support businesses in successfully integrating low-code AI/ML solutions. Our expertise includes:
Low-code platform evaluation and selection
Trial version for developers
Technical debt management and optimization
Phased integration and deployment
Ongoing monitoring and maintenance
By partnering with Argos Labs, businesses can ensure seamless low-code AI/ML integration, unlocking the full potential of these innovative technologies.
Know more about Argos labs solutions on www.argos-labs.com
0 notes
Text
Actualizar openSUSE 15.2 a openSUSE 15.3

Actualizar openSUSE 15.2 a openSUSE 15.3 de manera sencilla. No vamos a hablar de las bondades de esta magnífica distribución Linux, pues muchos ya sabéis que es una de mis favoritas. OpenSUSE es una distribución diferente, potente, poderosa, fácil de usar, versátil y, con un funcionamiento como servidor empresarial que pocos le hacen sombra. La forma de operar de openSUSE no hace que su actualización, sea tan simple como en otras distribuciones linux, sobre todos las basadas en deb, como Ubuntu, Linux Mint, etc. Consciente de que existen muchas dudas y errores al respecto, hemos realizado una instalación limpia de openSUSE 15.2 con Ext4 y, la hemos actualizado a openSUSE 15.3 con un resultado satisfactorio. En este artículo verás como lo hemos hecho, de forma rápida y sencilla.

Actualizar openSUSE 15.2 a openSUSE 15.3 de forma sencilla
Actualizar openSUSE 15.2 a openSUSE 15.3
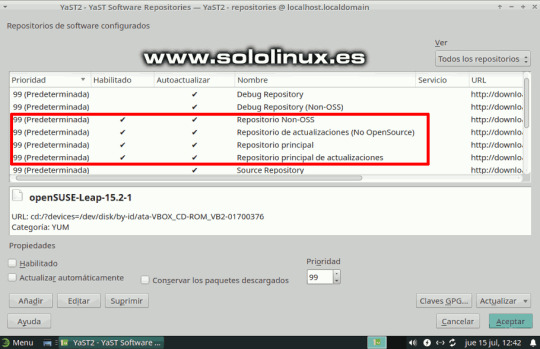
Antes de comenzar, verificamos que efectivamente tenemos instalada la versión 15.2. cat /etc/*release Ejemplo... localhost:~ # cat /etc/*release NAME="openSUSE Leap" VERSION="15.2" ID="opensuse-leap" ID_LIKE="suse opensuse" VERSION_ID="15.2" PRETTY_NAME="openSUSE Leap 15.2" ANSI_COLOR="0;32" CPE_NAME="cpe:/o:opensuse:leap:15.2" BUG_REPORT_URL="https://bugs.opensuse.org" HOME_URL="https://www.opensuse.org/" localhost:~ # Lo primero y muy importante, es deshabilitar los repositorios que no sean oficiales. Para ello desde YaST, accedemos a YaST Software Repositories.

Acceder a YaST Software Repositories Una vez en YaST Software Repositories, deshabilita los repositorios que no sean oficiales. Deja habilitados, solo los que ves en la siguiente imagen.
Repositorios habilitados de openSUSE Bien, una vez deshabilitados los repositorios no oficiales salimos de YaST. Abre la terminal y accede como superusuario. sudo su Ahora refrescamos los repositorios habilitados y actualizamos. zypper ref zypper up Verás un resultado similar al siguiente. localhost:~ # zypper ref Repository 'Repositorio Non-OSS' is up to date. Repository 'Repositorio principal' is up to date. Retrieving repository 'Repositorio principal de actualizaciones' metadata Building repository 'Repositorio principal de actualizaciones' cache ..... Repository 'Repositorio de actualizaciones (No OpenSource)' is up to date. All repositories have been refreshed. localhost:~ # zypper up Building repository 'Repositorio Non-OSS' cache ........................ Building repository 'Repositorio principal' cache ...................... Building repository 'Repositorio principal de actualizaciones' cache ... Building repository 'Repositorio de actualizaciones (No OpenSource)' cac Loading repository data... Reading installed packages... Nothing to do. Bueno, llego la hora de la verdad. Debes copiar la siguiente secuencia de comandos al completo y, pegarla en tu terminal. Lo que hacemos es modificar la versión 15.2 por la 15.3. Recuerda... copia todo completo y pégalo, si lo haces línea por línea no funcionara correctamente. files="$(zypper lr -u | awk -F'|' '$4 ~ /Yes/ { gsub (" ", "", $2); r="/etc/zypp/repos.d/"$3".repo"; print r }')" for f in $files do echo "Backup of $f saved to /root/ before patching it up ..." cp -f "$f" /root/ sed -i 's+/leap/15.2+/leap/$releasever+' "$f" sed -i 's+15.2.1+15.3+' "$f" sed -i 's+15.2+15.3+' "$f" done Debe quedar como la siguiente imagen.

Migrar openSUSE 15.2 a openSUSE 15.3 Refrescamos los repositorios, indicando que sean los de la nueva versión 15.3. zypper --releasever=15.3 ref Ejemplo... zypper --releasever=15.3 ref localhost:~ # zypper --releasever=15.3 ref Warning: Enforced setting: $releasever=15.3 Retrieving repository 'Repositorio Non-OSS' metadata ..................... Building repository 'Repositorio Non-OSS' cache .......................... Retrieving repository 'Repositorio principal' metadata ................... Building repository 'Repositorio principal' cache ........................ Retrieving repository 'Repositorio principal de actualizaciones' metadata Building repository 'Repositorio principal de actualizaciones' cache ..... Retrieving repository 'Repositorio de actualizaciones (No OpenSource)' met Building repository 'Repositorio de actualizaciones (No OpenSource)' cache All repositories have been refreshed. localhost:~ # Llagó el momento de la actualización real. Te recomiendo ser paciente, puede demorar hasta 45 minutos. zypper --releasever=15.3 dup Ejemplo... localhost:~ # zypper --releasever=15.3 dup Warning: Enforced setting: $releasever=15.3 Retrieving repository 'Repositorio Non-OSS' metadata ..................... Building repository 'Repositorio Non-OSS' cache .......................... Retrieving repository 'Repositorio principal' metadata ................... Building repository 'Repositorio principal' cache ............................................ Retrieving repository 'Repositorio principal de actualizaciones' metadata .................... Building repository 'Repositorio principal de actualizaciones' cache ......................... Retrieving repository 'Repositorio de actualizaciones (No OpenSource)' metadata .............. Building repository 'Repositorio de actualizaciones (No OpenSource)' cache ................... Loading repository data... Reading installed packages... Warning: You are about to do a distribution upgrade with all enabled repositories. Make sure these repositories are compatible before you continue. See 'man zypper' for more information about this command. Computing distribution upgrade... The following 156 NEW packages are going to be installed: alsa-plugins-speexrate alsa-plugins-upmix alsa-ucm-conf coreutils-doc cryptsetup-lang dirmngr evince evince-lang evince-plugin-pdfdocument file-roller file-roller-lang glibc-lang gnome-calculator gnome-calculator-lang gnome-desktop-lang google-poppins-fonts gspell-lang gtksourceview4-lang issue-generator kernel-default-5.3.18-57.3 kernel-default-extra kernel-default-optional kernel-firmware-all kernel-firmware-amdgpu kernel-firmware-ath10k kernel-firmware-ath11k kernel-firmware-atheros kernel-firmware-bluetooth kernel-firmware-bnx2 kernel-firmware-brcm kernel-firmware-chelsio kernel-firmware-dpaa2 kernel-firmware-i915 kernel-firmware-intel kernel-firmware-iwlwifi kernel-firmware-liquidio kernel-firmware-marvell kernel-firmware-media kernel-firmware-mediatek kernel-firmware-mellanox kernel-firmware-mwifiex kernel-firmware-network kernel-firmware-nfp kernel-firmware-nvidia kernel-firmware-platform kernel-firmware-prestera kernel-firmware-qlogic kernel-firmware-radeon kernel-firmware-realtek kernel-firmware-serial kernel-firmware-sound kernel-firmware-ti kernel-firmware-ueagle kernel-firmware-usb-network kmod-bash-completion libLLVM11 libatopology2 libavcodec58_134 libavformat58_76 libavutil56_70 libblogger2 libbrotlienc1 libcbor0 libcdio19 libcrypt1 libdav1d5 libebtc0 libevdocument3-4 libevview3-3 libfido2-1 libfido2-udev libgepub-0_6-0 libgnome-desktop-3-18 libgnome-desktop-3_0-common libgspell-1-2 libgtksourceview-4-0 libgtop-2_0-11 libgtop-lang libldac2 libmfx1 libmpath0 libndr1 libnftables1 libnss_usrfiles2 libpeas-loader-python libply-boot-client5 libply-splash-core5 libply-splash-graphics5 libply5 libre2-9 libswresample3_9 libtextstyle0 liburing1 libyui-ncurses-pkg15 libyui-ncurses15 libyui-qt-graph15 libyui-qt-pkg15 libyui-qt15 libyui15 login_defs man-pages-es metamail mokutil mpt-status nftables openSUSE-signkey-cert openssh-clients openssh-common openssh-server p7zip-full pam-doc pam_pwquality patterns-base-documentation patterns-base-sw_management patterns-yast-yast2_desktop perl-TermReadLine-Gnu perl-core-DB_File pipewire-lang postfix-ldap procinfo procmail python3-brotlipy python3-cairo python3-nftables python3-smbc rpm-config-SUSE ruby2.5-rubygem-mini_portile2 ruby2.5-rubygem-nokogiri setserial sharutils sharutils-lang spax star star-rmt sudo-plugin-python system-group-audit system-group-kvm systemd-default-settings systemd-default-settings-branding-openSUSE systemd-doc systemd-lang typelib-1_0-Libxfce4ui-2_0 typelib-1_0-Libxfce4util-1_0 typelib-1_0-Xfconf-0 virtualbox-kmp-default-6.1.22_k5.3.18_59.5-lp153.2.3.2 vlan xreader-plugin-comicsdocument xreader-plugin-djvudocument xreader-plugin-dvidocument xreader-plugin-epubdocument xreader-plugin-pdfdocument xreader-plugin-pixbufdocument xreader-plugin-psdocument xreader-plugin-tiffdocument xreader-plugin-xpsdocument yast2-trans-en The following 3 NEW patterns are going to be installed: documentation sw_management yast2_desktop The following NEW product is going to be installed: "openSUSE Leap 15.3" The following 22 packages are going to be REMOVED: exo-branding-openSUSE exo-helpers hardlink kernel-firmware kmod-compat libexo-1-0 libndr0 libre2-6 libxfce4panel-1_0-4 libxfce4ui-1-0 libyui-ncurses-pkg11 libyui-qt-pkg11 patterns-base-apparmor_opt patterns-base-enhanced_base_opt patterns-base-x11_opt python3-pycairo python3-pysmbc systemd-bash-completion typelib-1_0-libxfce4util-1_0 xfce4-statusnotifier-plugin xfce4-statusnotifier-plugin-lang xreader-backends --------------etc............
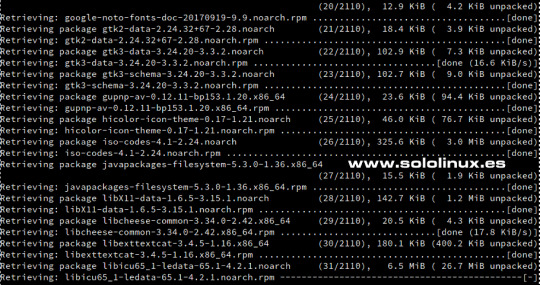
Descargar y actualizar los nuevos paquetes Al concluir todo el proceso, te pregunta si quieres reiniciar el sistema. Responde "Y". 1762 packages to upgrade, 192 to downgrade, 156 new, 22 to remove, 1667 to change vendor. Overall download size: 1.59 GiB. Already cached: 0 B. After the operation, additional 308.9 MiB will be used. Note: System reboot required. Continue? (y): Sorpresa!!!, al iniciar el sistema ya vemos que arranca openSUSE 15.3.
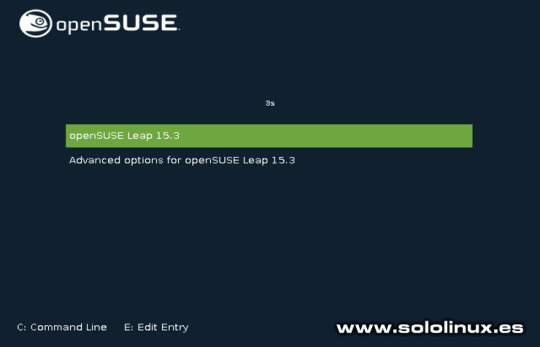
Iniciar openSUSE 15.3 Verificamos desde nuestra consola / terminal. cat /etc/*release El resultado es un exito. localhost:~ # cat /etc/*release NAME="openSUSE Leap" VERSION="15.3" ID="opensuse-leap" ID_LIKE="suse opensuse" VERSION_ID="15.3" PRETTY_NAME="openSUSE Leap 15.3" ANSI_COLOR="0;32" CPE_NAME="cpe:/o:opensuse:leap:15.3" BUG_REPORT_URL="https://bugs.opensuse.org" HOME_URL="https://www.opensuse.org/" localhost:~ # Ahora solo te falta modificar los repositorios no oficiales en YaST Software Repositories (aunque se hayan modificado automáticamente, debes verificarlos de forma manual). Una vez termines el proceso, los habilitas y actualizas de nuevo para concluir todo el proceso. sudo zypper ref sudo zypper up Canales de Telegram: Canal SoloLinux – Canal SoloWordpress Espero que este artículo te sea de utilidad, puedes ayudarnos a mantener el servidor con una donación (paypal), o también colaborar con el simple gesto de compartir nuestros artículos en tu sitio web, blog, foro o redes sociales. Chat de SoloLinux en Telegram Read the full article
#deb#distribucionlinux#IniciaropenSUSE15.3#opensuse#openSUSE15.2#openSUSE15.2aopenSUSE15.3#openSUSE15.2conExt4#openSUSE15.3#servidorempresarial#YaST#YaSTSoftwareRepositories
1 note
·
View note