#OpenVAS
Explore tagged Tumblr posts
Text
Novo post em udigrudroid.wordpress.com O Greenbone Community Edition ou OpenVAS, como é conhecido, é um scanner de código aberto para gerenciamento de vulnerabilidades, assim como o Qualys ou o Nessus. Muitas empresas constroem sua arquitetura de varredura de vulnerabilidades com base neste serviço. Neste post, você se familiarizará com o uso básico do GVM para escanear um único alvo, estabelecendo assim uma linha de base para a postura de segurança do seu ambiente de rede
#docker#Greenbone Community Edition#gvmd - Greenbone Vulnerability Management Daemon#NVT#OMP#OpenVAS#VT - Vulnerability Tests
0 notes
Text
Cài Đặt Kali Purpule Trên Máy Ảo + OpenVAS
Xin chào các bạn, khóa học Comptia Security + với các bài thực hành trên hệ thống CetrMaster Lab hoàn toàn online , hướng dẫn thì step by step + video, đặc biệt là hệ thống Comptia họ setup sẵn các máy từ attack đến target, rồi defence … nên nhiều khi các bạn thực hành rất tốt nhưng không biết mấy bộ tool đó làm thế nào để có, rồi khi đi làm sếp bắt cài lại ngớ người ra, cho nên có những thứ…
View On WordPress
0 notes
Text
Naomi Wolf: "The centerpiece of The Pfizer Papers is an intentional attack on human sexuality, and especially on women and babies. They killed the babies, and they knew it. They poisoned the breast milk, and they knew it. They damaged the placentas, and they knew it. They lowered the sperm count, and they knew it." [1]
Miscarriages and stillbirths in the US and the UK
By June 2021, six months after the initial rollout of the COVID vaccines, it was already clear that pregnant women who were vaccinated in the 1st or 2nd trimesters had a 90% risk of miscarrying. [2] That data was gathered by the V-Safe Surveillance System of the Centers for Disease Control (CDC) and was reported in the New England Journal of Medicine. [3]
The enormous toll of miscarriages following peak COVID vaccine uptake is documented in OpenVAERS, a summary of the Vaccine Adverse Event Reporting System, and is shown here: [4]
11 notes
·
View notes
Text
saving myself from a crashout one day at a time (cause how tf did I figure out how to use OpenVAS on my own even tho I asked for help) I love my future career that's just one exam away that I pray I pass
2 notes
·
View notes
Text
Server Security: Analyze and Harden Your Defenses in today’s increasingly digital world, securing your server is paramount. Whether you’re a beginner in ethical hacking or a tech enthusiast eager to strengthen your skills, understanding how to analyze adn harden server security configurations is essential to protect your infrastructure from cyber threats. This comprehensive guide walks you through the key processes of evaluating your server’s setup and implementing measures that enhance it's resilience. Materials and Tools Needed Material/ToolDescriptionPurposeServer Access (SSH/Console)Secure shell or direct console access to the serverTo review configurations and apply changesSecurity Audit ToolsTools like Lynis, OpenVAS, or NessusTo scan and identify vulnerabilitiesConfiguration Management ToolsTools such as Ansible, Puppet, or ChefFor automating security hardening tasksFirewall Management InterfaceAccess to configure firewalls like iptables, ufw, or cloud firewallTo manage network-level security policiesLog Monitoring UtilitySoftware like Logwatch, Splunk, or GraylogTo track suspicious events and audit security Step-by-Step Guide to Analyzing and Hardening Server Security 1. Assess Current Server Security Posture Log in securely: Use SSH with key-based authentication or direct console access to avoid exposing passwords. Run a security audit tool: Use lynis or OpenVAS to scan your server for weaknesses in installed software, configurations, and open ports. Review system policies: Check password policies, user privileges, and group memberships to ensure they follow the principle of least privilege. Analyze running services: Identify and disable unnecessary services that increase the attack surface. 2. Harden Network Security Configure firewalls: Set up strict firewall rules using iptables, ufw, or your cloud provider’s firewall to restrict inbound and outbound traffic. Limit open ports: Only allow essential ports (e.g., 22 for SSH, 80/443 for web traffic). Implement VPN access: For critical server administration, enforce VPN tunnels to add an extra layer of security. 3. Secure Authentication Mechanisms Switch to key-based SSH authentication: Disable password login to prevent brute-force attacks. Enable multi-factor authentication (MFA): Wherever possible, introduce MFA for all administrative access. Use strong passwords and rotate them: If passwords must be used,enforce complexity and periodic changes. 4. Update and Patch Software Regularly Enable automatic updates: Configure your server to automatically receive security patches for the OS and installed applications. Verify patch status: Periodically check versions of critical software to ensure they are up to date. 5. Configure System Integrity and Logging Install intrusion detection systems (IDS): Use tools like Tripwire or AIDE to monitor changes in system files. Set up centralized logging and monitoring: Collect logs with tools like syslog, Graylog, or Splunk to detect anomalies quickly. Review logs regularly: Look for repeated login failures, unexpected system changes, or new user accounts. 6. Apply Security Best Practices Disable root login: prevent direct root access via SSH; rather,use sudo for privilege escalation. Restrict user commands: Limit shell access and commands using tools like sudoers or restricted shells. Encrypt sensitive data: Use encryption for data at rest (e.g., disk encryption) and in transit (e.g., TLS/SSL). Backup configurations and data: Maintain regular, secure backups to facilitate recovery from attacks or failures. Additional Tips and Warnings Tip: Test changes on a staging environment before applying them to production to avoid service disruptions. Warning: Avoid disabling security components unless you fully understand the consequences. Tip: Document all configuration changes and security policies for auditing and compliance purposes.
Warning: Never expose unnecessary services to the internet; always verify exposure with port scanning tools. Summary Table: Key Server Security Checks Security AspectCheck or ActionFrequencyNetwork PortsScan open ports and block unauthorized onesWeeklySoftware UpdatesApply patches and updatesDaily or WeeklyAuthenticationVerify SSH keys,passwords,MFAMonthlyLogsReview logs for suspicious activityDailyFirewall RulesAudit and update firewall configurationsMonthly By following this structured guide,you can confidently analyze and harden your server security configurations. Remember, security is a continuous process — regular audits, timely updates, and proactive monitoring will help safeguard your server against evolving threats. Ethical hacking principles emphasize protecting systems responsibly, and mastering server security is a crucial step in this journey.
0 notes
Text
Enterprise Guide to IoT Penetration Testing: Tools, Techniques, and Risk Reduction
The Internet of Things (IoT) has transformed our homes and workplaces but at what cost?
With billions of connected devices, hackers have more entry points than ever. IoT penetration testing is your best defense, uncovering vulnerabilities before cybercriminals do. But where do you start? Discover the top tools, techniques, and expert strategies to safeguard your IoT ecosystem. Don’t wait for a breach, stay one step ahead.

Read on to fortify your devices now!
Why IoT Penetration Testing is Critical
IoT devices often lack robust security by design. Many run on outdated firmware, use default credentials, or have unsecured communication channels. A single vulnerable device can expose an entire network.
Real-world examples of IoT vulnerabilities:
Mirai Botnet (2016): Exploited default credentials in IP cameras and DVRs, launching massive DDoS attacks.
Stuxnet (2010): Targeted industrial IoT systems, causing physical damage to nuclear centrifuges.
Smart Home Hacks: Researchers have demonstrated attacks on smart locks, thermostats, and even baby monitors.
These incidents highlight why IoT security assessment must be proactive, not reactive.
IoT Penetration Testing Methodology
A structured approach ensures thorough testing while minimizing risks to operational systems.
Reconnaissance & Information Gathering
Identify all IoT devices (smart cameras, sensors, gateways).
Use tools like Nmap, Shodan, and Wireshark to map network traffic.
Extract firmware using Binwalk or Firmware Analysis Toolkit (FAT).
Vulnerability Assessment
Scan for weak credentials, outdated protocols (e.g., Telnet, FTP), and unpatched CVEs.
Tools: OpenVAS, Nessus, OWASP ZAP.
Exploitation & Post-Exploitation
Attempt to bypass authentication, escalate privileges, or intercept data.
Use Metasploit Framework, ExploitDB, or custom scripts.
Test hardware interfaces (UART, JTAG) if physical access is possible.
Reporting & Remediation
Document findings with risk ratings (Critical/High/Medium/Low).
Recommend patches, network segmentation, or encryption upgrades.
DID YOU KNOW?
During the forecast period, the global IoT security market is expected to expand significantly, with projections indicating growth from USD 24.2 billion in 2024 to USD 56.2 billion by 2029, reflecting a CAGR of 18.4%.
[ Are You Looking: DevOps Services ]
Best Open-Source Tools for IoT Penetration Testing
Discover the top tools for assessing IoT security, from firmware analysis to network exploitation. These open-source solutions help uncover vulnerabilities before attackers do.
Firmware Analysis – Binwalk & Firmadyne
Binwalk extracts firmware binaries to analyze file systems.
Firmadyne emulates firmware to detect vulnerabilities.
Network Traffic Analysis – Wireshark & Tcpdump
Inspect unencrypted MQTT, CoAP, or HTTP traffic.
Exploitation Frameworks – Metasploit & IoTGoat
Metasploit has modules for IoT-specific exploits.
IoTGoat is a deliberately vulnerable IoT environment for practice.
Hardware Hacking – JTAGulator & Bus Pirate
Identify debug ports (UART, SPI, I2C) for firmware dumping.
Password Cracking – Hydra & Hashcat
Bruteforce weak credentials on web interfaces or SSH.
[ Good Read: AWS For Beginners ]
Real-World IoT Attack Scenarios & Mitigations
Explore how attackers exploit weak IoT security from hijacked smart cameras to unencrypted medical devices and learn actionable fixes to prevent breaches.
Case 1: Weak Authentication in Smart Cameras
Vulnerability: Default admin:password combinations.
Exploit: Attackers gain live video access.
Fix: Enforce strong passwords & multi-factor authentication (MFA).
Case 2: Unencrypted MQTT Protocols
Vulnerability: Smart sensors transmit data in plaintext.
Exploit: Man-in-the-middle (MITM) attacks steal sensitive data.
Fix: Use TLS encryption and certificate-based authentication.
Case 3: Outdated Firmware in Medical IoT
Vulnerability: Unpatched CVEs in insulin pumps.
Exploit: Remote code execution (RCE) risks patient safety.
Fix: Automated firmware updates with integrity checks.
Key Takeaways for Decision-Makers
Security leaders must enforce robust IoT policies, align penetration testing with business risk, and foster collaboration between IT and OT teams to ensure long-term resilience.
Prioritize Security by Design: Ensure vendors follow OWASP IoT Top 10 guidelines.
Segment IoT Networks: Isolate critical devices from enterprise IT systems.
Conduct Regular Pen Tests: Schedule IoT penetration testing at least annually.
Invest in Threat Monitoring: Deploy SIEM solutions like ELK Stack or Splunk for anomaly detection.
You can check more info about: Enterprise Guide to IoT Penetration Testing.
DevOps Explained.
Platform Engineering Services.
0 notes
Text
Cyber Security Testing
Understanding Cyber Security Testing
Cyber security testing plays a crucial role in safeguarding digital infrastructure, networks, and data from unauthorized access, breaches, and malicious activities. It involves a range of practices that simulate attacks, assess vulnerabilities, and validate the effectiveness of security measures in place. Organizations rely on these tests to ensure their defenses are robust enough to resist evolving cyber threats.
Types of Cyber Security Testing
Several types of cyber security testing are utilized to cover different threat scenarios. Penetration testing (pen testing) simulates real-world attacks to find exploitable vulnerabilities. Vulnerability assessments scan systems for known flaws and misconfigurations. Security audits evaluate policies, procedures, and compliance against standards such as ISO 27001 or NIST. Red team testing involves ethical hackers mimicking advanced attackers to test incident response capabilities, while blue team testing focuses on defensive readiness and monitoring.
Importance of Cyber Security Testing
Cyber security testing is essential for identifying potential weaknesses before attackers exploit them. It provides insights into the effectiveness of current security controls and helps organizations understand their risk exposure. Through regular testing, businesses can avoid costly breaches, protect sensitive information, and maintain customer trust. It also ensures compliance with regulatory requirements and industry best practices.
Tools Used in Cyber Security Testing
A wide array of tools are available to support cyber security testing. Tools like Metasploit and Burp Suite are popular for penetration testing, while Nessus and OpenVAS are widely used for vulnerability assessments. Wireshark helps in network traffic analysis, and tools such as Nmap assist with port scanning and network mapping. These tools enhance the accuracy and efficiency of testing processes.
Challenges in Cyber Security Testing
Despite its importance, cyber security testing comes with challenges. Keeping up with the rapidly changing threat landscape requires continuous learning and tool updates. Testing can be time-consuming and resource-intensive, and improper testing methods can lead to system downtime or unintended data exposure. Balancing thorough testing with minimal disruption is critical for effective results.
Best Practices for Effective Testing
To conduct successful cyber security testing, organizations should define clear objectives, scope, and risk tolerance. Testing should be scheduled regularly and after major system changes. Engaging qualified professionals with up-to-date skills ensures accurate results. Moreover, findings must be documented thoroughly, and remediation efforts should follow immediately to address identified issues.
Conclusion
Cyber security testing is not just a technical necessity but a strategic investment in an organization’s digital resilience. By proactively identifying and mitigating risks, businesses can defend against cyber threats and secure their critical assets in an increasingly connected world.
0 notes
Text
Comptia Security + : Cài Đặt Kali Purpule Trên Máy Ảo + OpenVAS
Xin chào các bạn, khóa học Comptia Security + với các bài thực hành trên hệ thống CetrMaster Lab hoàn toàn online , hướng dẫn thì step by step + video, đặc biệt là hệ thống Comptia họ setup sẵn các máy từ attack đến target, rồi defence … nên nhiều khi các bạn thực hành rất tốt nhưng không biết mấy bộ tool đó làm thế nào để có, rồi khi đi làm sếp bắt cài lại ngớ người ra, cho nên có những thứ…
View On WordPress
0 notes
Text
We have passed the four-year anniversary of the roll-out of the experimental C19 modified mRNA injections.
Here is the table for the “Total” adverse events - US data is not yet available from here:
VAERS Analysis – Weekly analysis of the VAERS data
The data from here Red Boxes Page - OpenVAERS provides the “Total” umbers for all adverse events reported for adverse events reported to VAERS arising from the experimental injections manufactured by US companies for the entire planet.
Here’s the table:
Note that the propensity to associate ab adverse reaction diminishes the more time passes since the last injection. In some cases an adverse event can arise three years after the experimental injections, given in 2021.
The number of adverse events dropped markedly, but the number of deaths increased. The latest US figures to 27 December 2024 are below:
5 notes
·
View notes
Text
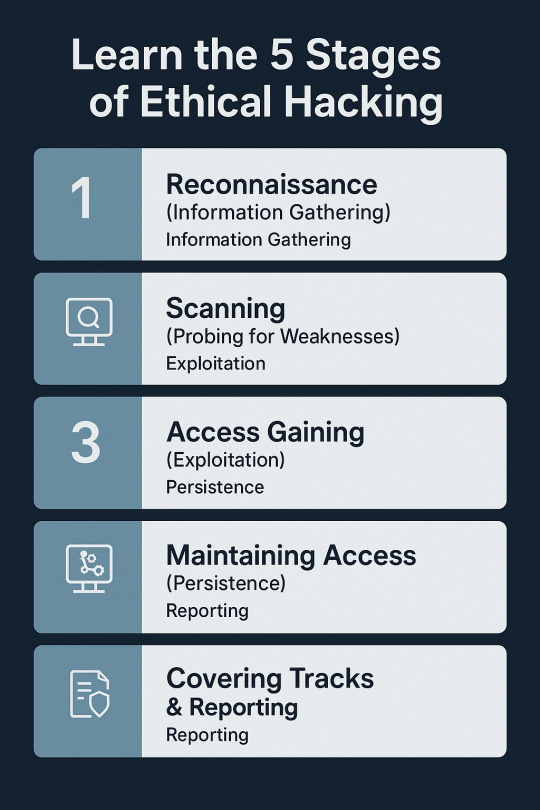
Learn the 5 Stages of Ethical Hacking
With threats on the digital platform ever-present today, ethical hacking has emerged as an essential method for protecting systems, networks, and information. As malicious hackers use vulnerabilities to carry out crime, ethical hackers (or white hat hackers) utilize their craft for good purposes — finding and fixing vulnerabilities before threat actors have the chance to do so. But ethical hacking is not a random process. It follows a methodical process to make every step legal, efficient, and in accordance with the security goals of the organization. This process is typically in five stages, which are very specific and trace ethical hackers from reconnaissance to reporting. Let us dive into detail about what these stages involve and why they're crucial for a successful cyber defense strategy. Phase 1: Reconnaissance (Information Gathering) Also known as: Footprinting Reconnaissance is the first and, arguably, the most important phase of ethical hacking. It's akin to the "research" phase. Ethical hackers find out as much as they can about the target before they try to break into it. This phase lays the groundwork for everything that follows. Aims: •Get familiar with the digital footprint of the target •Identify weak spots and vulnerable entry points • Steal away undetected while gathering information Methods Used: • Passive Reconnaissance – No contact with the target (e.g., use of WHOIS lookup, DNS records, social media, public databases). • Active Reconnaissance – Direct contact with the system (e.g., ping sweeps, port scanning, traceroutes). Tools: •Maltego •Nmap •Recon-ng •Google Dorking Why it matters: Proper reconnaissance saves time and makes the rest of the hacking process easier. It also replicates the first steps taken by real-world cyber attackers.
Phase 2: Scanning (Probing for Weaknesses) After the ethical hacker has sufficient surface information, scanning is the next phase where more intensive probing is done to identify particular vulnerabilities in the system. Objectives: • Discover open ports and services • Detect live systems • Identify running OS and applications • Discover known vulnerabilities
Methods: • Port Scanning – Scanning which ports are open and what services are running.
• Network Mapping – Knowledge of the network topology and the identification of the hosts. • Vulnerability Scanning – System scanning for known configuration or software vulnerabilities. Tools: • Nessus • Nikto • OpenVAS • Wireshark Why it matters: Scanning gives the hacker a technical snapshot of how healthy the system is and assists the hacker in determining which vulnerabilities to exploit during the exploitation phase.
Phase 3: Access Gaining (Exploitation) This is where ethical hacking really gets to work and occurs. The hacker attempts to break into the system by taking advantage of the weaknesses revealed in the scanning. It sounds like the climax, but it's a very choreographed and strategic move that makes ethical hacking. Objectives: • Use a known exploit to gain access • Increase privileges (for example, from guest to admin) • Identify the amount of potential damage that an actual perpetrator might do Methods • Buffer overflow attacks • tSQL injection • Brute-force password cracking • Misconfiguration exploitation Tools: • Metasploit • Hydra • John the Ripper • SQLMap Why it matters: Access that is gained allows organizations to see how much access an attacker would have, giving them a chance to cut off critical points of access before damage is being caused.
Phase 4: Maintaining Access (Persistence) During this phase, the ethical hacker mimics what an actual attacker would do once they have compromised the system — maintain access to keep gathering data or installing malware. Objectives: •Create backdoors or remote access tools •Mimic advanced persistent threats (APT) •Illustrate long-term risk exposure Methods: •Installing Trojans or rootkits (ethically and with permission) •Creating rogue user accounts •Altering system services for covert access Tools: •Netcat •Backdoor Factory •MSFVenom Why it matters: This stage assists in determining how long a system might remain compromised undetected — an important consideration when analyzing incident response measures. Phase 5: Covering Tracks & Reporting While malicious hackers attempt to cover their tracks, ethical hackers do the opposite — they make sure all actions taken are logged, traced, and completely documented. Reporting is the last and possibly most useful step of the ethical hacking process.
Goals: • Restore the system to normal • Report to the organization • Deliver remediation steps that are actionable What's in the Report: • Disclosed vulnerabilities • Attacks tried and success rates • Possible impact of each vulnerability • Fix recommendations and improvements Why it matters: The final-report is a blueprint that the organization can use to make its defenses harder. It transforms an ethical hack from a test into an actionable business tool.
The Legal and Ethical Side It's important to emphasize: Ethical hacking should be done with the right permission. That is, written permission, well-delineated scope, and test boundaries. Unapproved hacking—no matter what "noble cause"—is against the law and punishable by it. Why the 5 Phases are Important Together, these five phases create a repeatable, effective cycle of security testing. They: •Echo the methods of actual attackers •Detect potential threats prior to exploitation •Enhance organizational cybersecurity stance •Meet standards such as ISO/IEC 27001, PCI-DSS, etcFinal Thoughts Ethical hacking is not merely about cracking open systems—it's about learning them, enhancing them, and helping to make the internet a more secure place. From IT managers to aspiring cybersecurity analysts to entrepreneurs, recognizing the five stages of ethical hacking can assist you in making better, more secure decisions. With increasing cybercrime, ethical hacking is no longer a choice — it's a necessity. And as with any strategic process, its success depends on how systematically and responsibly it's carried out.
Website: https://www.icertglobal.com/course/ceh-certification-training/Classroom/62/3044
0 notes
Text
OpenVASとは?商用ツールに匹敵する検査項目とカスタマイズ性を備えたオープンソース脆弱性スキャナの魅力
無償で利用できる高機能スキャナー『OpenVAS』の魅力 現代のサイバーセキュリティにおいて、システムの脆弱性を迅速に発見し、適切に対処することは欠かせません。 OpenVASは、無料で利用できるオープンソースツールでありながら、企業向け有料ソリューションにも匹敵する機能を備えています。 多様なカスタマイズ性と継続的なアップデートが特徴のこのツールについて詳しく解説します。 コミュニティ主導の開発体制がもたらす信頼性と柔軟性 OpenVASの強みは、世界中のセキュリティ専門家によるコミュニティ主導の開発体制にあります。 この仕組みにより、脆弱性データベースは日々更新され、新たな脅威への対応が迅速に行われています。 現在、5万件以上の検査項目が登録されており、幅広い脆弱性を網羅しています。 開発元であるGreenbone…
0 notes
Text
启辰留学服务:daikao8.com
【微信:Hackr404】
【WhatsApp:+85254868103】
【电报TG:VIPgpa1】
黑客利用技术手段入侵系统修改成绩,这真的是一个令人震惊的消息黑客悄无声息地入侵网站是一个复杂且需要高度技巧的过程。以下是一些黑客可能采用的方法和步骤,以实现这一目标:
**信息收集**
黑客首先会对目标网站进行全面的信息收集。这包括了解网站的结构、使用的技术栈、可能的安全漏洞以及相关人员的信息。通过搜索引擎、社交媒体、公开的数据泄露和公开的技术信息,黑客可以构建出目标网站的一个大致画像。
**扫描与枚举**
接下来,黑客会使用各种扫描工具来探测目标网站的开放端口、服务以及潜在的安全漏洞。Nmap等端口扫描工具可以帮助黑客识别出哪些服务正在运行,而漏洞扫描工具如OpenVAS、Nessus等则可以发现系统中可能存在的已知漏洞。
**利用漏洞进行攻击**
一旦发现可利用的漏洞,黑客会尝试利用这些漏洞来侵入系统。例如,如果网站存在SQL注入漏洞,黑客可能会尝试注入恶意SQL代��来窃取或篡改数据库中的数据。对于跨站脚本攻击(XSS)漏洞,黑客可能会注入恶意脚本,以便在用户浏览器中执行并窃取用户信息。
**提升权限与维持访问**
成功侵入系统后,黑客会尝试提升自己的权限,以便能够访问更多的系统资源。这通常涉及到利用操作系统的漏洞或配置错误。一旦获得足够的权限,黑客可能会安装后门程序或木马,以确保未来能够持续访问该网站。
**清除痕迹**
为了掩盖自己的入侵行为,黑客在完成任务后会尽量清除留下的痕迹。这可能包括删除日志文件、修改系统设置以及掩盖任何可能暴露其活动的证据。
除了上述的技术手段外,黑客还可能利用社会工程学来辅助入侵过程。例如,他们可能会通过伪造合法的邮件或消息来诱骗用户点击恶意链接或下载恶意附件,从而绕过安全防御。
值得注意的是,1. 黑客改成绩,黑客改分数,黑客改考试成绩,黑客修改成绩单,黑客入侵修改考试成绩,黑客改毕业成绩,黑客改留学成绩
2. 黑客改雅思成绩,黑客改托福成绩,黑客改GRE成绩,黑客改GMAT成绩,黑客改SAT成绩,黑客改ACT成绩
3. 黑客改AP成绩,黑客改A-level成绩,黑客改IB成绩,黑客改PTE成绩,黑客改Duolingo成绩
4. 黑客改大学成绩,黑客改研究生成绩,黑客改博士生成绩,黑客改留学生成绩,黑客改GPA成绩
5. 黑客改高考成绩,黑客改中考成绩,黑客改期末考试成绩,黑客改期中考试成绩,黑客改模拟考试成绩
6. 黑客改语言成绩,黑客改学术成绩,黑客改专业课成绩,黑客改选修课成绩,黑客改实验课成绩
7. 黑客改论文成绩,黑客改答辩成绩,黑客改实习成绩,黑客改毕业设计成绩,黑客改学位成绩
8. 黑客改国外大学成绩,黑客改国内大学成绩,黑客改交换生成绩,黑客改预科成绩,黑客改语言班成绩
9. 黑客改在线考试成绩,黑客改远程考试成绩,黑客改网考成绩,黑客改机考成绩,黑客改笔试成绩
10. 黑客改口试成绩,黑客改面试成绩,黑客改实践成绩,黑客改实验成绩,黑客改项目成绩
11. 黑客改留学生语言成绩,黑客改留学生学术成绩,黑客改留学生专业课成绩,黑客改留学生选修课成绩
12. 黑客改留学生GPA,黑客改留学生学位成绩,黑客改留学生毕业成绩,黑客改留学生交换成绩
13. 黑客改留学生预科成绩,黑客改留学生语言班成绩,黑客改留学生在线考试成绩
14. 黑客改留学生远程考试成绩,黑客改留学生网考成绩,黑客改留学生机考成绩
15. 黑客改留学生笔试成绩,黑客改留学生口试成绩,黑客改留学生面试成绩
16. 黑客改留学生实践成绩,黑客改留学生实验成绩,黑客改留学生项目成绩
17. 黑客改留学生论文成绩,黑客改留学生答辩成绩,黑客改留学生实习成绩
18. 黑客改留学生毕业设计成绩,黑客改留学生学位论文成绩,黑客改留学生课程成绩
19. 黑客改留学生期末考试成绩,黑客改留学生期中考试成绩,黑客改留学生模拟考试成绩
20. 黑客改留学生高考成绩,黑客改留学生中考成绩,黑客改留学生语言考试成绩
21. 黑客改留学生学术考试成绩,黑客改留学生专业考试成绩,黑客改留学生选修考试成绩
22. 黑客改留学生实验考试成绩,黑客改留学生在线课程成绩,黑客改留学生远程课程成绩
23. 黑客改留学生网课成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
24. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
25. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
26. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
27. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
28. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
29. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
30. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
31. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
32. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
33. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
34. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
35. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
36. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
37. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
38. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
39. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
40. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
41. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
42. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
43. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
44. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
45. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
46. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
47. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
48. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
49. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
50. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
51. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
52. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
53. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
54. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
55. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
56. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
57. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
58. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
59. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
60. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
61. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
62. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
63. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
64. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
65. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
66. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
67. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
68. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
69. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
70. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
71. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
72. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
73. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
74. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
75. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
76. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
77. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
78. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
79. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
80. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
81. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
82. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
83. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩
84. 黑客改留学生口试课程成绩,黑客改留学生面试课程成绩,黑客改留学生实践课程成绩
85. 黑客改留学生实验课程成绩,黑客改留学生项目课程成绩,黑客改留学生论文课程成绩
86. 黑客改留学生答辩课程成绩,黑客改留学生实习课程成绩,黑客改留学生毕业设计课程成绩
87. 黑客改留学生学位课程成绩,黑客改留学生交换课程成绩,黑客改留学生预科课程成绩
88. 黑客改留学生语言班课程成绩,黑客改留学生在线考试课程成绩,黑客改留学生远程考试课程成绩
89. 黑客改留学生网考课程成绩,黑客改留学生机考课程成绩,黑客改留学生笔试课程成绩

#黑客改成绩黑客改GPA黑客改分数黑客改成绩单学校网络安全成绩系统入侵黑客技术分析真实案例学校警示信息安全防范措施教育机构违法行为网络安全防护技术探讨#黑客改成绩#找黑客改分修改成绩单 挂科gpa成绩提高 找黑客改分 成绩单 高中修改成绩
0 notes
Text
Why Linux is the Preferred Choice for DevOps Environments
In the world of DevOps, speed, agility, and reliability are key. Linux has emerged as the go-to operating system for DevOps environments, powering everything from cloud servers to containers. But what makes Linux so popular among DevOps professionals? Let's dive into the core reasons: stability, security, and flexibility.
1. Stability
Linux is known for its rock-solid stability, making it ideal for production environments. Its robust architecture allows servers to run for years without requiring a reboot. This stability is essential in DevOps, where continuous deployment and integration rely on highly available systems.
Consistent Performance: Linux handles high workloads with minimal performance degradation.
Long-Term Support (LTS): Distributions like Red Hat Enterprise Linux (RHEL) and Ubuntu LTS provide security patches and updates for extended periods, ensuring a stable environment.
2. Security
Security is a top priority in DevOps pipelines, and Linux offers powerful security features to safeguard applications and data.
Built-In Security Modules: Linux includes SELinux (Security-Enhanced Linux) and AppArmor, which provide mandatory access control policies to prevent unauthorized access.
User and Group Permissions: The granular permission system ensures that users have the least privilege necessary, reducing the attack surface.
Frequent Security Updates: The open-source community quickly addresses vulnerabilities, making Linux one of the most secure platforms available.
Compatibility with Security Tools: Many security tools used in DevOps, such as Snort, OpenVAS, and Fail2Ban, are natively supported on Linux.
3. Flexibility
One of the standout features of Linux is its flexibility, which allows DevOps teams to customize environments to suit their needs.
Open Source Nature: Linux is open-source, allowing developers to modify and optimize the source code for specific requirements.
Wide Range of Distributions: From lightweight distributions like Alpine Linux for containers to enterprise-grade options like RHEL and CentOS, Linux caters to different needs.
Containerization and Virtualization: Linux is the foundation for Docker containers and Kubernetes orchestration, enabling consistent application deployment across various environments.
Automation and Scripting: Linux shell scripting (Bash, Python, Perl) simplifies automation, a core aspect of DevOps practices.
4. Compatibility and Integration
Linux plays well with modern DevOps tools and cloud platforms.
Cloud-Native Support: Major cloud providers like AWS, Google Cloud, and Azure offer robust support for Linux.
CI/CD Integration: Most CI/CD tools (e.g., Jenkins, GitLab CI, CircleCI) are built to run seamlessly on Linux.
Version Control and Collaboration: Git, the cornerstone of version control in DevOps, was created for Linux, ensuring optimal performance and integration.
5. Community and Support
The active Linux community contributes to continuous improvement and rapid bug fixes.
Extensive Documentation and Forums: There’s no shortage of tutorials, forums, and documentation, making troubleshooting easier.
Enterprise Support: Distributions like RHEL provide enterprise-grade support for mission-critical applications.
Conclusion
Linux’s stability, security, and flexibility make it the preferred choice for DevOps environments. Its compatibility with automation tools, containerization platforms, and cloud services enhances productivity while maintaining high standards of security and reliability. For organizations aiming to accelerate their DevOps pipelines, Linux remains unmatched as the foundation for modern application development and deployment.
For more details www.hawkstack.com
0 notes
Text
Cyber Security Testing
Introduction to Cyber Security Testing Cyber security testing is a crucial process that ensures digital systems, networks, and applications are protected against cyber threats. As cyberattacks become more advanced, organizations must conduct thorough testing to identify and fix vulnerabilities before attackers can exploit them. Cyber security testing plays a significant role in safeguarding sensitive data and maintaining the integrity, availability, and confidentiality of systems.
Types of Cyber Security Testing Various types of cyber security testing address different aspects of an organization's security posture. Vulnerability assessment involves scanning systems for known weaknesses, while penetration testing simulates real-world attacks to test defenses. Security audits review configurations and policies, and code reviews identify security flaws in software development. Each type of testing serves a unique purpose in providing a comprehensive security overview.
Importance of Cyber Security Testing Cyber security testing is vital in proactively identifying risks and reducing the chance of breaches. It helps organizations comply with regulatory standards like GDPR, HIPAA, and ISO 27001. Testing also strengthens trust among customers and stakeholders by demonstrating a commitment to security. Regular testing improves incident response and reduces potential downtime and financial losses from cyber incidents.
Common Cyber Security Testing Tools Security professionals rely on various tools to conduct cyber security testing effectively. Tools like Nessus, Nmap, and OpenVAS are popular for vulnerability scanning. Burp Suite and OWASP ZAP are commonly used for web application security testing. Metasploit is widely used for penetration testing and exploiting vulnerabilities. These tools help automate tasks, identify threats faster, and enhance the efficiency of testing procedures.
Best Practices in Cyber Security Testing To maximize the effectiveness of cyber security testing, following best practices is essential. Organizations should define clear testing objectives, scope, and methodologies. Testing should be conducted regularly and after any major system updates or changes. Keeping up with evolving threats and continuously updating tools and techniques is crucial. Moreover, involving internal and third-party testers can bring in diverse perspectives and uncover hidden risks.
Challenges in Cyber Security Testing Despite its importance, cyber security testing faces several challenges. Limited budgets and resources can restrict testing frequency and depth. Rapid technology changes and the complexity of IT environments make it difficult to cover all potential vulnerabilities. Ensuring that testing does not disrupt live systems is another concern. Overcoming these challenges requires careful planning, skilled professionals, and a risk-based testing approach.
Conclusion Cyber security testing is a proactive defense mechanism that helps organizations stay ahead of evolving threats. By identifying vulnerabilities, ensuring compliance, and implementing strong security measures, testing significantly contributes to the resilience of digital infrastructures. Regular and comprehensive testing must be an integral part of every organization’s cybersecurity strategy.
0 notes
Text
Here is the update of the reports published on VAERS, resulting from injuries and deaths sustained from taking the experimental modified mRNA and other C19 injections concocted by companies based in the US, like Pfizer and Moderna.
Details of US deaths and injuries are not yet available. These are numbers reported o VAERS from all over the world, including the US.
Using data from here:
Red Boxes Page - OpenVAERS
The Moderna dresses are an estimate, the Pfizer doses are the number “shipped” as claimed by Pfizer here:
COVID-19 Vaccine Equity | Pfizer
Billions of doses may have been destroyed and not administered. Any claims hat the number of extra doses were a bribe paid to big pharma and eventually (partially) returned in cash to health regulators and politicians is not substantiated, yet.
Check out this article from October 2022.
(100) What happened to 4.3 billion doses in NZ, Australia, Canada, UK, EU and the US?
Doses were initially billed at around 20 bucks each. 4.3 billion extra represents 86 billion to be shared around. I wonder if every country has the right set-up to dispose of these extra doses properly – and not just flushed down the toilet.
I will update numbers from the US when they become available from here:
VAERS Summary for COVID-19 Vaccines through 10/25/2024 – VAERS Analysis
Onwards!
Please subscribe (paid, preferably! or unpaid) or donate via ko-fi. Ko-fi donations here: https://ko-fi.com/peterhalligan An annual subscription of 100 bucks is less than 30 cents a day and is one third less than a $3 ko-fi donation a week! Please post on your “X” (Twitter) feed!
1 note
·
View note
Text
Mastering Ethical Hacking with OpenVAS Scanners: A Beginner's Guide
Introduction OpenVAS (Open Vulnerability Assessment System) is a popular open-source vulnerability scanner used for detecting and reporting security vulnerabilities in networks. Ethical hacking, also known as penetration testing, is the practice of simulating cyber attacks to test an organization’s defenses. In this tutorial, we will explore the basics of navigating OpenVAS scanners, a crucial…
0 notes