#PHP error reporting
Explore tagged Tumblr posts
Text
How to Protect Your Laravel App from JWT Attacks: A Complete Guide
Introduction: Understanding JWT Attacks in Laravel
JSON Web Tokens (JWT) have become a popular method for securely transmitting information between parties. However, like any other security feature, they are vulnerable to specific attacks if not properly implemented. Laravel, a powerful PHP framework, is widely used for building secure applications, but developers must ensure their JWT implementation is robust to avoid security breaches.

In this blog post, we will explore common JWT attacks in Laravel and how to protect your application from these vulnerabilities. We'll also demonstrate how you can use our Website Vulnerability Scanner to assess your application for potential vulnerabilities.
Common JWT Attacks in Laravel
JWT is widely used for authentication purposes, but several attacks can compromise its integrity. Some of the most common JWT attacks include:
JWT Signature Forgery: Attackers can forge JWT tokens by modifying the payload and signing them with weak or compromised secret keys.
JWT Token Brute-Force: Attackers can attempt to brute-force the secret key used to sign the JWT tokens.
JWT Token Replay: Attackers can capture and replay JWT tokens to gain unauthorized access to protected resources.
JWT Weak Algorithms: Using weak signing algorithms, such as HS256, can make it easier for attackers to manipulate the tokens.
Mitigating JWT Attacks in Laravel
1. Use Strong Signing Algorithms
Ensure that you use strong signing algorithms like RS256 or ES256 instead of weak algorithms like HS256. Laravel's jwt-auth package allows you to configure the algorithm used to sign JWT tokens.
Example:
// config/jwt.php 'algorithms' => [ 'RS256' => \Tymon\JWTAuth\Providers\JWT\Provider::class, ],
This configuration will ensure that the JWT is signed using the RSA algorithm, which is more secure than the default HS256 algorithm.
2. Implement Token Expiry and Refresh
A common issue with JWT tokens is that they often lack expiration. Ensure that your JWT tokens have an expiry time to reduce the impact of token theft.
Example:
// config/jwt.php 'ttl' => 3600, // Set token expiry time to 1 hour
In addition to setting expiry times, implement a refresh token mechanism to allow users to obtain a new JWT when their current token expires.
3. Validate Tokens Properly
Proper token validation is essential to ensure that JWT tokens are authentic and have not been tampered with. Use Laravel’s built-in functions to validate the JWT and ensure it is not expired.
Example:
use Tymon\JWTAuth\Facades\JWTAuth; public function authenticate(Request $request) { try { // Validate JWT token JWTAuth::parseToken()->authenticate(); } catch (\Tymon\JWTAuth\Exceptions\JWTException $e) { return response()->json(['error' => 'Token is invalid or expired'], 401); } }
This code will catch any JWT exceptions and return an appropriate error message to the user if the token is invalid or expired.
4. Secure JWT Storage
Always store JWT tokens in secure locations, such as in HTTP-only cookies or secure local storage. This minimizes the risk of token theft via XSS attacks.
Example (using HTTP-only cookies):
// Setting JWT token in HTTP-only cookie $response->cookie('token', $token, $expirationTime, '/', null, true, true);
Testing Your JWT Security with Our Free Website Security Checker
Ensuring that your Laravel application is free from vulnerabilities requires ongoing testing. Our free Website Security Scanner helps identify common vulnerabilities, including JWT-related issues, in your website or application.
To check your site for JWT-related vulnerabilities, simply visit our tool and input your URL. The tool will scan for issues like weak algorithms, insecure token storage, and expired tokens.

Screenshot of the free tools webpage where you can access security assessment tools.
Example of a Vulnerability Assessment Report
Once the scan is completed, you will receive a detailed vulnerability assessment report to check Website Vulnerability. Here's an example of what the report might look like after checking for JWT security vulnerabilities.

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
By addressing these vulnerabilities, you can significantly reduce the risk of JWT-related attacks in your Laravel application.
Conclusion: Securing Your Laravel Application from JWT Attacks
Securing JWT tokens in your Laravel application is essential to protect user data and maintain the integrity of your authentication system. By following the steps outlined in this post, including using strong algorithms, implementing token expiry, and validating tokens properly, you can safeguard your app from common JWT attacks.
Additionally, make sure to regularly test your application for vulnerabilities using tools like our Website Security Checker. It’s a proactive approach that ensures your Laravel application remains secure against JWT attacks.
For more security tips and detailed guides, visit our Pentest Testing Corp.
2 notes
·
View notes
Text

Good Morning World The News Media is Thriving These Days, But…
The news media is thriving these days, alive and well with its many commercials, political propaganda, gossip, sports, and, relatively speaking, minor news events—and, oh yes, commercials. From our very beginning, “Freedom of the Press” has been a major contribution to the safety, welfare, and protection of the people from the errors and sins of government, but real in-depth reporting is slowly disappearing from the scene. Daily news events are reported over and over, sometimes for days, while other important subjects are overlooked. We are majoring in minors and minoring in majors.
For example, where, today, are the pros and cons of single payer healthcare being discussed? Certainly, this subject is being discussed superfluously, but where are the in-depth pro and con discussions? Most of what I hear about the subject is, to the effect, “No need to discuss this as it will never be approved anyway”. Oh well, healthcare is only 17.5 percent of our spending nationally, annually contributing to our national deficit and debt. No problem.
Ref: http://www.justfacts.com/healthcare.asp
The financial crisis of 2008 was triggered by derivatives, one of those new securities invented to allegedly provide insurance coverage to home mortgage holders, aka fish food for speculators in the financial markets. I don’t really know how many dollars’ worth of these securities were in circulation in 2008. I have heard numbers like $400 Trillion. I have also heard numbers amounting to $900 Trillion. What are the numbers now, and when is our illustrious media going to reveal them to the people. The last time I heard anything in the mass media about the derivative risk was an article by Peter Cohan, AOL.COM, Big Risk: $1.2 Quadrillion Derivatives Market Dwarfs World GDP. Folks! Do you know how much money $1.2 Quadrillion is? Let me tell you. It is $1,000,000,000,000,000,000,000,000.00 or 1,000 times $1 Trillion. My gosh, folks, the world’s annual gross domestic product is only $50 to $60 trillion, and this article was written June 9, 2010—over six years ago. Oh well, that wasn’t important either. The public wouldn’t understand anyway.
Let’s really get basic. It’s common knowledge that education in government, and civics has been lacking in our school systems in recent years. Yet our government from the president on down and the news media, when they address the people, they refer to members of the House of Representatives as Congressmen (or women). They are not Congressmen. Their titles are Representatives. If they are a congressman, so also is a Senator by gum and by golly. Congress is the name given to our national legislature, a bicameral body made up of the House of Representatives, the lower house, and the Senate, the upper house. To be a congressman, one would have to be both a Representative and a Senator at the same time. Duh… By the way, do you want to know why we have two houses? In short, the answer is the lower house, the House of Representatives represent the majority of the people, the masses who elect them. There are 435 members. The Senate, the upper house, represents the minority elite among us, in theory at least. There are 100 of them. I say elite. In our nation’s beginning, Senators were elected by the House of Representatives. Only later in the course of our history where they were elected by the people as they now are. For further information:
http://www.sfgate.com/politics/article/Enduring-debate-elitism-versus-populism-3189454.php
To close, for now, our news media exists to serve our people. They have to earn income to pay their bills, i.e. salaries, insurance, rent, and return on investments to their investors, but their main purpose, their only purpose which, in the end, justifies their very existence is to serve the people with news which is the truth; and, in my view, they could do a much better job. This is my view. What’s yours? Saturday, October 19, 2024, Jacksonville, Florida USA From: Steven P. Miller, @ParkermillerQ, gatekeeperwatchman.org TM Founder and Administrator of Gatekeeper-Watchman International Groups. #GWIG, #GWIN, #GWINGO. www.facebook.com/gatekeeperwatchnan www.facebook.com/ Instagram: steven_parker_miller_1956
3 notes
·
View notes
Text
Complete Guide to Rapid URL Indexer's RESTful API for Developers
Rapid URL Indexer has released comprehensive documentation for our RESTful API, giving developers programmatic access to our URL indexing service. This API allows you to automate the submission of URLs for indexing, check project statuses, and monitor your account resources.
API Endpoints
Rapid URL Indexer provides five key endpoints for interacting with the service:
GET /api/v1/projects/list - Retrieve all your indexing projects
POST /api/v1/projects - Create a new indexing project with URLs
GET /api/v1/projects/{project_id} - Check a specific project's status
GET /api/v1/projects/{project_id}/report - Download a project's indexing report
GET /api/v1/credits/balance - Check your current credit balance
Each endpoint is fully documented with example requests and responses, making implementation straightforward regardless of your development environment.
Authentication
Rapid URL Indexer uses API key authentication for all endpoints. Your API key must be included in the X-API-Key header with every request. This ensures secure access to your account resources while simplifying the authentication process.
Project Creation and Management
When creating a new indexing project, you can specify:
A custom project name for easy identification
An array of URLs to be indexed (each validated for proper format)
Optional notification preferences for status changes
The API handles input validation automatically, sanitizing project names and ensuring all URLs are properly formatted. Invalid URLs are discarded, and you'll receive immediate feedback on the success or failure of your request.
Status Tracking
Rapid URL Indexer's API provides detailed status tracking for all indexing projects. Projects progress through several states:
pending - Created but not yet submitted
submitted - Actively being processed for indexing
completed - All URLs have been processed
failed - Processing encountered errors (credits refunded)
refunded - Some URLs couldn't be indexed within 14 days
This granular status tracking gives you complete visibility into the indexing process and helps you manage your resources effectively.
Reporting
For completed projects, you can download comprehensive CSV reports showing which URLs were successfully indexed. These reports provide valuable data for SEO analysis and can be integrated into your existing reporting workflows.
Error Handling
Rapid URL Indexer's API uses standard HTTP status codes and detailed error messages to communicate issues. Common error scenarios include:
400 Bad Request - Missing or invalid parameters
401 Unauthorized - Invalid API key
403 Forbidden - Insufficient credits
404 Not Found - Requested resource doesn't exist
429 Too Many Requests - Rate limit exceeded
Each error response includes a descriptive message to help you troubleshoot and resolve the issue quickly.
Rate Limiting
To ensure fair usage and system stability, the API enforces a rate limit of 100 requests per minute per API key. This generous limit accommodates most use cases while preventing abuse.
OpenAPI Specification
For developers using modern API tools, Rapid URL Indexer provides a complete OpenAPI 3.1 specification. This can be imported into tools like Swagger UI, Postman, or other API development environments for easier integration and testing.
Integration Examples
The API documentation includes comprehensive examples for all endpoints, making it easy to implement in any programming language. Whether you're using Python, PHP, JavaScript, or any other language with HTTP capabilities, you can quickly integrate Rapid URL Indexer into your workflow.
Use Cases
Rapid URL Indexer's API is particularly valuable for:
SEO agencies managing multiple client websites
Content management systems that need automated indexing
E-commerce platforms with frequently changing product listings
News sites and blogs that publish content regularly
Custom SEO tools and dashboards
By automating the indexing process through the API, you can ensure new content is discovered and indexed quickly, improving your overall SEO performance.
https://rapidurlindexer.com/indexing-api/
0 notes
Text
How to show All Errors in PHP ?

We can show all errors in PHP using the error_reporting() function. It sets the error_reporting directive at runtime according to the level provided. If no level is provided, it will return the current error reporting level. error_reporting(E_ALL) level represents all errors, warnings, notices, etc. PHP Code: If the level is set to zero, no error is reported even when an unavailable file is included. PHP Output: No output No error is reported PHP Code: When the level is set to […]
0 notes
Text
Philippines v. Conti: Statutory Rape and Sexual Assault Conviction
Supreme Court of the Philippines details the appeal of Marlon Conti y Paraggua following his conviction for Violation of the Anti-Violence Against Women and their Children Act of 2004 and Statutory Rape. The Court of Appeals affirmed the Statutory Rape conviction, and this decision further examines the evidence presented by the prosecution and defense, ultimately upholding the lower court's findings regarding Statutory Rape. Additionally, the Supreme Court finds Marlon also guilty of Sexual Assault due to evidence of finger penetration, which was properly alleged in the original complaint. The decision outlines the penalties and damages for both offenses, modifying the previous judgments to reflect the new Sexual Assault conviction.
Here is a case digest of the provided source material following the ALAC (Answer, Legal Basis, Application, and Conclusion) format, along with the doctrine and ratio of the case:
Case Digest: People of the Philippines vs. Marlon Conti y Paraggua
Facts:
Marlon Conti y Paraggua (Marlon) was charged in two separate Informations with Violation of Section 5(a), in relation to Section 6(a), of Republic Act No. 9262 (Anti-Violence Against Women and their Children Act of 2004) and Statutory Rape under Article 266-A(1)(d) of the Revised Penal Code (RPC).
The first charge (Criminal Case No. 16451) stemmed from Marlon's alleged physical violence against his live-in partner, BBB, by boxing and mauling her, and threatening her with a gun on November 13, 2013, causing her physical injuries and emotional distress.
The second charge (Criminal Case No. 16452) alleged that on or about November 13, 2013, and prior thereto, Marlon sexually abused BBB's 7-year-old daughter, AAA, by inserting his finger into her vagina and thereafter having sexual intercourse with her.
Marlon pleaded not guilty, and the cases were jointly tried.
The prosecution presented BBB, AAA, and Dr. Mila-Simangan (Municipal Health Officer who examined BBB and AAA). BBB testified that on November 13, 2013, she witnessed Marlon pull down AAA's shorts and insert his finger into her vagina, which BBB stated was the third time she had seen such an act. Marlon then inserted his penis into AAA's vagina. When BBB tried to intervene, Marlon punched her, causing her to lose consciousness. Dr. Simangan's Medicolegal Report indicated hymenal lacerations on AAA.
Marlon denied the charges, interposing the defense of alibi, claiming he was at a warehouse for work on the night of the incident. His co-worker, Faustino Rodriguez, corroborated his presence at the warehouse but admitted they slept in different rooms, 15 meters apart, and he could not see into Marlon's room.
The Regional Trial Court (RTC) convicted Marlon of both crimes. For the RA 9262 violation, he was sentenced to arresto mayor (1 month and 1 day to 6 months imprisonment) and ordered to pay a fine of PHP 100,000.00. For Statutory Rape, he was sentenced to reclusion perpetua and ordered to pay AAA PHP 75,000.00 as civil indemnity, PHP 75,000.00 as moral damages, and PHP 75,000.00 as exemplary damages. The RTC rejected Marlon's defenses, finding the testimonies of BBB and AAA sufficient.
Marlon appealed only the Statutory Rape conviction (Criminal Case No. 16452) to the Court of Appeals (CA), assailing the credibility of the victims and claiming their testimonies were inconsistent and contrary to human experience.
The Court of Appeals (CA) affirmed Marlon's conviction for Statutory Rape, finding the elements established by AAA's categorical testimony, BBB's corroboration, and Dr. Simangan's medical findings. The CA modified the judgment by imposing a 6% per annum interest on the monetary awards.
The case was then appealed to the Supreme Court.
Issue: Did the CA commit any reversible error in affirming Marlon's conviction for Statutory Rape?
Ruling:
A. Answer: The Supreme Court DENIED the appeal, affirming Marlon's conviction for Statutory Rape under Article 266-A(1)(d) of the RPC. Furthermore, the Court MODIFIED the judgment by also finding Marlon guilty beyond reasonable doubt of Sexual Assault under Article 266-A(2) of the RPC in relation to Section 5(b) of RA 7610, given that the prosecution also proved he inserted his finger into AAA's vagina before having carnal knowledge.
L. Legal Basis:
Statutory Rape (Article 266-A(1)(d) RPC): Requires (1) the offended party to be under 12 years of age, and (2) the accused to have had carnal knowledge of the victim, irrespective of force or intimidation. The imposable penalty is reclusion perpetua.
Sexual Assault (Article 266-A(2) RPC in relation to Section 5(b) of RA 7610): Committed when (1) the victim is a child (male or female) under 12 years of age, and (2) the offender inserts any instrument or object into the genital or anal orifice of the victim. The imposable penalty is reclusion temporal in its medium period.
Defense of Denial and Alibi: Denial is a weak defense against positive testimony. For alibi to prosper, the accused must prove presence elsewhere and physical impossibility of being at the crime scene or its vicinity.
Credibility of Witnesses: The trial court's factual findings, especially on witness credibility, are accorded great weight and respect, particularly when affirmed by the CA.
Charging Multiple Offenses (Rule 110 & 120, Rules of Criminal Procedure): While generally an Information charges only one offense (Section 13, Rule 110), if an accused fails to object before trial to a single complaint or information charging two or more offenses, the court may convict for all offenses charged and proven (Section 3, Rule 120).
Nomenclature of Sexual Assault for Minors: The proper nomenclature for acts of sexual assault committed against a victim under 12 years of age (e.g., finger insertion) is "Sexual Assault under paragraph 2, Article 266-A of the RPC in relation to Section 5 (b) of R.A. No. 7610" (referencing People v. Tulagan).
Indeterminate Sentence Law (Act No. 4103): Applied for determining the penalty for Sexual Assault.
Civil Liabilities: Monetary awards include civil indemnity, moral damages, and exemplary damages, with legal interest of 6% per annum from the finality of judgment until fully paid.
A. Application:
For Statutory Rape: The Court affirmed the findings of the lower courts that all elements of Statutory Rape were proven beyond reasonable doubt. AAA was undisputedly under 12 years old at the time of the incident, and Marlon had sexual intercourse with her. Marlon's denial was outweighed by the direct, positive, and detailed testimonies of AAA and BBB, corroborated by Dr. Simangan's medical findings. His alibi failed because his co-worker's testimony did not establish physical impossibility of Marlon being at the crime scene; they slept in separate rooms, and the co-worker could not see Marlon's activities. The Court found no reason to overturn the factual findings and credibility assessments of the lower courts.
For Sexual Assault: The Court further found Marlon guilty of Sexual Assault. The testimonies of AAA and BBB clearly established that Marlon first inserted his finger into AAA's vagina before engaging in sexual intercourse. This act fulfills the elements of Sexual Assault, as AAA was under 12 and Marlon inserted an object (his finger) into her genital orifice. Since the Information sufficiently alleged this act of finger insertion in addition to the sexual intercourse, and Marlon failed to file a motion to quash the Information for charging multiple offenses, he could be convicted of both offenses charged and proven, as allowed by Section 3, Rule 120 of the Rules of Criminal Procedure. Consistent with People v. Tulagan, the Court clarified that the proper nomenclature for this act is "Sexual Assault under paragraph 2, Article 266-A of the RPC in relation to Section 5 (b) of R.A. No. 7610".
Penalties and Damages:
For Statutory Rape, the penalty of reclusion perpetua was imposed, along with PHP 75,000.00 each for civil indemnity, moral damages, and exemplary damages.
For Sexual Assault, applying the Indeterminate Sentence Law, Marlon was sentenced to an indeterminate penalty of twelve (12) years, ten (10) months and twenty-one (21) days of reclusion temporal, as minimum, to fifteen (15) years, six (6) months and twenty-one (21) days of reclusion temporal, as maximum. He was also ordered to pay PHP 50,000.00 each for civil indemnity, moral damages, and exemplary damages for this crime.
All monetary awards are subject to a legal interest rate of six percent (6%) per annum from the date of finality of the decision until fully paid.
C. Conclusion: The Supreme Court denied the appeal, upholding the conviction for Statutory Rape and imposing an additional conviction for Sexual Assault. Marlon Conti y Paraggua was thus found guilty beyond reasonable doubt of both Statutory Rape under Article 266-A(1)(d) of the Revised Penal Code and Sexual Assault under Article 266-A(2) of the Revised Penal Code, in relation to Section 5(b) of RA 7610, with corresponding penalties and civil liabilities for each offense.
Doctrine: When an accused is charged under a single information for both carnal knowledge and the insertion of an object into the victim's genitals, and the victim is a child under 12 years of age, and the accused fails to object to the multi-offense information before trial, the court may convict the accused of both Statutory Rape under Article 266-A(1)(d) of the Revised Penal Code and Sexual Assault under Article 266-A(2) of the Revised Penal Code in relation to Section 5(b) of RA 7610, provided both offenses are proven during trial. The Court re-affirms that for such acts involving a child under 12, the proper legal nomenclature for the insertion of an object is "Sexual Assault under paragraph 2, Article 266-A of the RPC in relation to Section 5 (b) of R.A. No. 7610.".
Ratio: The Supreme Court's decision to affirm the Statutory Rape conviction and impose an additional conviction for Sexual Assault was based on the following reasons:
Overwhelming Evidence for Statutory Rape: The prosecution successfully established all elements of Statutory Rape through clear, consistent, and categorical testimonies from the child victim and her mother, which were further corroborated by medical findings. The defense's general denial and uncorroborated alibi were insufficient to overturn these positive and direct testimonies. The Court consistently defers to the factual findings and credibility assessments of the trial court, especially when affirmed by the appellate court.
Dual Conviction Despite Single Information and Lack of Objection: Although Rule 110 generally mandates a single offense per information, Rule 120, Section 3 allows for conviction of multiple offenses if they are charged in a single information and the accused fails to object before trial. In this case, the Information explicitly described both the finger insertion and subsequent sexual intercourse. Since Marlon did not file a motion to quash the Information, he effectively waived his right to object to the duplicitous charge, allowing the court to convict him of both distinct crimes as proven.
Distinct Nature of the Acts: The Court recognized that the act of inserting a finger into the victim's vagina and the act of carnal knowledge, while occurring in close succession, are separate and distinct criminal acts, each fulfilling the elements of a different offense. This approach aligns with prior jurisprudence that allows for convictions for multiple forms of rape/sexual assault from a single incident if the information supports it and different acts are proven.
Proper Nomenclature for Child Sexual Assault: The Court reiterated its ruling in People v. Tulagan to correctly classify the act of finger insertion into a child under 12 as "Sexual Assault under paragraph 2, Article 266-A of the RPC in relation to Section 5 (b) of R.A. No. 7610." This ensures the proper legal characterization and application of penalties for such offenses against children.
0 notes
Text
Data hacks and identity theft have been making the headlines in recent years, making the security of your website more important than ever before. This is especially true if you handle financial transactions through your company's site, as you'll be processing your customers' sensitive financial data. Fortunately, you have many tools available to you to help ensure your website is as secure as possible. ScanMyServer ScanMyServer provides a comprehensive report of vulnerabilities throughout your website and on your server. It can identify PHP code injection, SQL injection, blind SQL injection, HTTP header injection and other scripting vulnerabilities. This service is free, and there is no registration required to test your site. You'll receive your results via email and can download a security badge to display on your site for your customers' peace of mind. Vega Vega is a security scanner designed for use with web applications. It provides an easy-to-use interface that makes the process as streamlined as possible, even for those who are unfamiliar with web security testing. It can help identify cross-site scripting, SQL injection and other application vulnerabilities. This open source application is backed by a powerful API for even greater customization and capability. Metasploit Metasploit makes use of the latest ethical hacking techniques to detect website vulnerabilities. This is what is known as penetration testing and has become more and more popular in recent years. If ethical hackers can break through your website's security protocols, then data thieves undoubtedly will be able to as well. Identifying these vulnerabilities early on can help you make the changes needed to secure your site from the latest threats. Sucuri Sucuri is a free website scanner that can detect viruses and malware. It can also identify and website errors or broken code, as well as out-of-date software. It can even alert you if your website has been blacklisted. This tool is compatible with a variety of popular website-building platforms, including WordPress, Drupal, Magento, Joomla and more. Qualys SSL Server Test This tool analyzes the configuration of your SSL web server and is designed specifically for secure (https) websites. You'll get in-depth analysis of your URL to help you identify vulnerabilities. This includes your site's expiration day, SSL/TLS version, overall security rating, protocol details and more. This is another free service, and neither your personal information nor your test results are used for any purpose other than to provide you with the analysis you have requested. Wapiti Wapiti scans for a variety of vulnerabilities in web applications. Similar to penetration testing, this application injects data to see if various scripts are vulnerable to attacks. It is capable of detecting file disclosure and inclusion vulnerabilities, site configuration issues, and a variety of injection complications. It is important to note, though, that while free, this is a command-line application. This may be a bit difficult for beginners to get the hang of and is better suited to advanced users. Wireshark Wireshark is another penetration testing application. It specializes in analyzing network protocols, getting into the tiniest details of your packet information and decryption. It's compatible with all the major operating systems, including Windows, OS X, Linux, Solaris and more. The application is free to download and can be viewed through a user interface or in TTY-mode TShark utility. Skipfish Skipfish crawls through your website, one page at a time, to detect any vulnerabilities in the code. This open source web application is free to download and use, and it is optimized for HTTP handling. It is capable of handling up to 2,000 requests per second without putting a strain on your CPU. Compatible with Windows, MacOS X, Linux and FreeBSD operating systems, this security application can detect even subtle flaws, like blind injection vectors.
Detectify Detectify is a suite of more than 100 automated security tests for your website. In total, it checks for over 700 distinct vulnerabilities. The team of ethical hackers behind the platform continually update the scans to detect the latest threats as they emerge, keeping your website secure in real time. You can test Detectify for free for 21 days, after which you'll have to pay a recurring membership fee for the ongoing security service. Siteguarding Siteguarding is a free online tool for detecting viruses, malware, phishing, injected spam, defacement and more. It can also help you clean and remove these threats from your website to ensure your security. The company also provides web hosting services, for a complete web security management package. These are just a few of the many website security options you have available to you, so there is no excuse for not having your website provide the latest security protections for your customers. Try out a few scans today to identify areas where your company website might be vulnerable so that you can regain control.Ken Lynch is an enterprise software startup veteran, who has always been fascinated by what drives workers to work and how to make work more engaging. Ken founded Reciprocity to pursue just that. He has propelled Reciprocity's success with this mission-based goal of engaging employees with the governance, risk, and compliance goals of their company in order to create more socially minded corporate citizens. Ken earned his BS in Computer Science and Electrical Engineering from MIT.
0 notes
Text
How to Send Automated Direct Mail Letters Using an API

In an increasingly digital world, automation and personalization are the cornerstones of successful marketing. One channel that continues to prove its effectiveness is direct mail. When powered by an API, direct mail evolves from a traditional communication method to a dynamic, data-driven marketing tool. This guide explores how to send automated direct mail letters using an API, including benefits, setup, use cases, and best practices.
What Is an Automated Direct Mail API?
A Direct Mail API (Application Programming Interface) is a set of code protocols and tools that allow businesses to connect their CRM, eCommerce platform, or other software to a third-party direct mail service provider. Once connected, you can automatically generate, personalize, and send letters, postcards, or brochures through physical mail.
The entire process���from letter composition to print queue to delivery—is handled through simple API calls, removing the need for manual printing, addressing, or postage.
Benefits of Using an API for Direct Mail Letters
1. Efficiency Through Automation
With an API, direct mail campaigns become part of your automated workflows. Triggered mailings—such as sending a letter after a customer signs up, abandons a cart, or reaches a certain milestone—can happen without manual involvement.
2. Real-Time Personalization
Direct Mail APIs allow dynamic insertion of customer-specific data like names, offers, order history, or geographic content into each mail piece. This level of personalization dramatically boosts engagement and conversion rates.
3. Scalability for High-Volume Campaigns
From sending hundreds to millions of letters, APIs handle scale effortlessly. Whether you're launching a national campaign or a targeted outreach, the API ensures consistency and accuracy across volumes.
4. Reduced Operational Costs
Automation eliminates printing errors, manual labor, and the need for in-house printing resources. API-based mailing also ensures optimized postage and delivery routes, saving time and money.
5. Enhanced Tracking and Analytics
Advanced APIs offer status tracking, delivery confirmations, and reporting metrics. Marketers can analyze open rates, conversions, and ROI with more granularity than ever before.
Step-by-Step: How to Send Direct Mail Letters Using an API
Step 1: Choose a Direct Mail API Provider
Popular providers include Lob, PostGrid, Click2Mail, and Postalytics. Choose one based on:
Country and postal coverage
Letter formats (e.g., A4, folded mailers)
API documentation quality
CRM/eCommerce integrations
Pricing models (per mailpiece, subscription, bulk discounts)
Step 2: Get API Credentials
Register for an account and access your API key or token. This key authenticates your requests to the direct mail platform.
Step 3: Integrate With Your Tech Stack
Use one of the following:
No-code tools like Zapier, Integromat, or Tray.io
Native integrations with platforms like Salesforce, HubSpot, Shopify
Custom code integrations using languages like Python, JavaScript, or PHP
Step 4: Create Your Mail Templates
Design the body of your letter with placeholders for dynamic fields:
htmlCopy
Edit
Dear {{first_name}}, Thank you for purchasing {{product_name}}. Enjoy 10% off on your next order!
You can use HTML templates or platform-specific editors.
Step 5: Set Triggers or Events
Configure when the API should send the letter:
After customer registration
When a lead becomes inactive for 30 days
Upon completing a purchase
To follow up post-event or appointment
Step 6: Send API Request
Here’s a sample API request using cURL:
bashCopy
Edit
curl https://api.mailprovider.com/v1/letters \ -H "Authorization: Bearer YOUR_API_KEY" \ -d '{ "to": { "name": "John Doe", "address_line1": "123 Main St", "city": "New York", "state": "NY", "postal_code": "10001" }, "from": { "company": "Your Company", "address_line1": "456 Agency Rd", "city": "Los Angeles", "state": "CA", "postal_code": "90001" }, "template": "promo_letter_01", "variables": { "first_name": "John", "product_name": "Wireless Earbuds" } }'
Step 7: Track Status and Confirm Delivery
Use the API to fetch delivery statuses or view reports:
bashCopy
Edit
GET https://api.mailprovider.com/v1/letters/{letter_id}/status
Use Cases of Automated Direct Mail Letters
1. E-Commerce Cart Abandonment
Send reminder letters with discount coupons to convert abandoned carts into sales.
2. Financial Services
Welcome new clients or deliver legally compliant notices using physical letters with tracking.
3. Real Estate
Automate property listing letters to specific zip codes based on market activity.
4. Healthcare
Send appointment reminders, compliance updates, and test results via HIPAA-compliant print-and-mail APIs.
5. Education & Non-Profits
Send donation requests, thank-you notes, or enrollment packets to segmented audiences.
Best Practices for Sending Direct Mail via API
Clean Your Mailing List: Ensure address accuracy using Address Verification APIs to avoid undeliverable mail.
Personalize Content: Use behavioral and transactional data to tailor the message.
Test in Sandbox Mode: Use API test environments to avoid accidental mailings.
Monitor API Errors: Log and respond to API response codes to fix failures quickly.
A/B Test Mail Variants: Test different letters to determine which copy/design performs best.
Ensure Legal Compliance: Follow data protection regulations (GDPR, HIPAA, CAN-SPAM) for data handling and messaging.
Challenges and Solutions
ChallengeSolutionAPI complexityUse SDKs and libraries provided by the providerData formatting issuesStandardize addresses before mailingRegulatory complianceUse providers that offer HIPAA, GDPR, and SOC2 certificationsPrint errorsUse preview or proof mode before triggering bulk sendsHigh costs for low volumeBatch mailings or use hybrid digital/print strategies
Conclusion: Automating Letters for Smarter Direct Mail
Integrating a Direct Mail API transforms how businesses send letters—making it faster, cheaper, and more impactful. Whether you're a marketer, developer, or business owner, leveraging automation in physical mail campaigns can unlock new engagement opportunities and streamline operations.
By using automated workflows, real-time personalization, and tracking, your brand can ensure every letter counts—delivered with precision and purpose.
youtube
SITES WE SUPPORT
Healthcare Direct Mail – Wix
0 notes
Text
Meeting and Conference Booking System using PHP and MySQL

The Meeting and Conference Booking System has been designed to override the problem of existing manual system. This web application is supported to eliminate and in some case reduce the hardship faced by manual system. The application is reduced as much as possible to avoid errors while entering the data. It’s also provide message while entering invalid data. No formal knowledge is required for the user to operate this system. Overall we said that Meeting and Conference Booking System is user friendly.
Click here: https://phpgurukul.com/meeting-and-conference-booking-system-using-php-and-mysql/
Project Modules
In Meeting and Conference Booking System we use PHP and MySQL Database. This project keeps the records of booking, users and conference rooms. Meeting and Conference Booking System has two module i.e. admin and user.
Admin Module
1. Dashboard: In this section, admin can briefly view the total new booking, approved booking, Cancelled Booking, Total Registered users and total sub-admins.
2. Sub-Admins: In this section, admin can manage sub-admins (add/delete/update).
3. Room: In this section, admin can manage rooms (add/update/delete).
4. Booking: In this section, admin can view new, approved, canceled bookings and also give a remark.
5. Reg Users: In this section, admin can view the detail of registered users.
6. Page: In this section, admin can manage about us and contact us pages..
7. Reports: In this section admin can view the and check booking details in a particular period.
Admin can also update his profile, change the password and recover the password.
User Module
1. Home: It is a welcome page for users.
2. About: It is a about us page of website.
3. Meeting & Conference Room: In this section, user can view details of onference and meeting room which are available.
4. Contact: It is a contact us page of website.
5. Sign Up: Users can register through sign uppage.
6. Login: It is login page.
7. My Account: After registration user can have their own account where he/she can update profile, change password, recover password and view booking details of conference and meeting room.
How to run the Meeting and ConferenceBooking System Project in PHP
Download the zip file
2. Extract the file and copy mcbs folder
3.Paste inside root directory(for xampp xampp/htdocs, for wamp wamp/www, for lamp var/www/Html)
4.Open PHPMyAdmin (http://localhost/phpmyadmin)
5. Create a database with the name mcbsdb
6. Import mcbsdb.sql file(given inside the zip package in SQL file folder)
7. Run the script http://localhost/mcbs
Admin Credential Username: admin Password: Test@123
User Credential Username: [email protected] Password: Test@123
Or Register a New User
PHP Gurukul
Welcome to PHPGurukul. We are a web development team striving our best to provide you with an unusual experience with PHP. Some technologies never fade, and PHP is one of them. From the time it has been introduced, the demand for PHP Projects and PHP developers is growing since 1994. We are here to make your PHP journey more exciting and useful.
Email: [email protected] Website : https://phpgurukul.com
0 notes
Text
Excel to Tally Is Now 100% Automatic

How Excel to Tally Integration Solves Major Data Challenges for Businesses
Managing large volumes of business data—from purchases and sales to taxes and expenses—can be overwhelming when it’s scattered across various systems and formats. The risk of errors, delays, and inefficiencies increases significantly without a centralized approach.
Why Businesses Need Excel to Tally Integration
Tally is a widely trusted accounting software that simplifies financial management, return filing, and reporting. However, to truly benefit from Tally, businesses must ensure that all their data—regardless of source—is accurately and automatically imported into it.
That’s where the Excel to Tally Import Utility Module by Antraweb Technologies steps in. It automates the entire process, eliminating the need for manual data entry and reducing errors.
What Is Excel to Tally Import Utility?
The Excel to Tally Import Utility allows businesses to import data directly from Excel spreadsheets and various platforms—like e-commerce sites (Amazon, Flipkart), CRMs, or custom-built software—into Tally.
Whether it’s vouchers, ledgers, cost centers, or stock data, this integration handles it all seamlessly.
Key Features That Simplify Data Integration
Automated Data Mapping: Fields in Excel are automatically mapped to Tally fields, saving time and ensuring consistency.
Scheduled Imports: You can schedule regular imports to keep Tally updated in real-time.
Source Flexibility: Supports imports from diverse sources like Magento, PHP, Java, .NET systems, and more.
How to Import Excel Data into Tally
Using TallyPrime’s import function is simple:
Use predefined or custom mapping templates.
Select the appropriate Excel file and worksheet.
Choose how to handle existing data (merge, ignore, or overwrite).
Preview the data and proceed with import after taking a backup.
For advanced imports, TallyPrime Release 4.0 offers the ability to create custom mapping templates for masters (like ledgers or stock items) and transactions (like sales).
Major Benefits of Excel to Tally Integration
Saves Time: Automates repetitive tasks and eliminates manual data entry.
Reduces Errors: Ensures data accuracy and integrity across systems.
Boosts Productivity: Frees up your team to focus on strategic work.
Final Thoughts
Adopting Excel to Tally integration streamlines your financial data flow, minimizes manual work, and enables better decision-making. It’s an essential tool for businesses aiming for operational efficiency and growth.
Want to experience the full power of this utility? 👉 Explore the Excel to Tally Import Utility Module
For personalized support and setup, contact Antraweb Technologies—a trusted Tally partner with 33 years of experience.
0 notes
Text
Website Developer in Bangalore: Hello Errors Delivers More Than Just Code

In today’s digital-first economy, your website is often the first impression your brand makes. Whether you’re a fast-growing startup or a legacy business pivoting online, having a professional, performance-driven website is no longer optional—it's critical. And if you're based in India’s tech capital, the search for the right Website Developer in Bangalore ends at Hello Errors.
Bangalore is not only home to IT giants and unicorn startups but also a vibrant ecosystem of SMEs, creators, and emerging brands. What they all have in common is the need for a modern, engaging, and scalable online presence. That’s where Hello Errors steps in as your digital partner—not just another development agency, but a full-spectrum digital solutions company that crafts websites designed for success.
Why Businesses in Bangalore Need Specialized Website Developers
With consumers relying on digital platforms to discover, evaluate, and engage with businesses, having a strong online foundation is crucial. Here’s why choosing a Website Developer in Bangalore with local and global expertise makes a difference:
Bangalore-based developers understand regional consumer behavior
Faster turnaround and easier communication with local teams
Adaptability to Indian and international tech regulations
On-the-ground collaboration and faster iterations
Hello Errors brings the best of both worlds—deep local insight and cutting-edge global tech capabilities—to help your business thrive online.
Industry-Specific Website Development: One Size Doesn’t Fit All
One key reason Hello Errors is a top-rated Website Developer in Bangalore is its industry-focused approach. The team doesn’t believe in cookie-cutter templates. Instead, they tailor development strategies to suit the unique needs of various industries.
📚 EdTech Portals
Hello Errors creates dynamic learning portals with course management, video hosting, assessments, and secure login systems.
🛍️ E-commerce
Scalable online stores with real-time inventory, multiple payment gateways, and SEO-optimized product pages.
🏥 Healthcare
HIPAA-compliant websites with features like appointment booking, telemedicine integration, and health blogs.
🧑💼 Corporate Websites
Clean, functional, and fast-loading websites designed to reflect professionalism and brand authority.
Whether you're a D2C brand or a SaaS platform, Hello Errors ensures your website speaks directly to your target audience.
Technologies That Scale With Your Business
What truly separates Hello Errors from other Website Developers in Bangalore is their use of modern, scalable, and future-proof technologies. They don’t just build for today—they build for what your business will become tomorrow.
🧱 Tech Stack Highlights:
Frontend: React.js, Vue.js, Next.js
Backend: Node.js, Django, PHP, Laravel
CMS: WordPress, Webflow, Shopify (customized)
Databases: MongoDB, MySQL, PostgreSQL
Cloud: AWS, Google Cloud, DigitalOcean
Their developers choose the right combination of tools and frameworks based on your goals, budget, and scalability needs. This forward-thinking approach ensures your site grows as your business does.
The Hidden Power of Post-Launch Support
Many businesses think their job is done once the website is live. That’s a myth. Post-launch support is what keeps your digital investment secure, optimized, and relevant.
As your trusted Website Developer in Bangalore, Hello Errors offers ongoing services such as:
Security monitoring and bug fixes
Performance tuning and page speed optimization
Content and SEO updates
New feature rollouts
Analytics integration and reporting
With Hello Errors, you’re never left stranded. They grow with you, constantly iterating and improving based on user feedback and analytics.
SEO-First Development: Visibility Built-In
Your website could be a visual masterpiece—but if it’s not ranking on search engines, it won’t matter. That’s why Hello Errors builds SEO directly into the development process.
Unlike many agencies that treat SEO as an afterthought, Hello Errors includes:
Clean code structure and semantic HTML
Mobile responsiveness and fast loading times
Keyword optimization across meta tags and content
Schema markup for rich snippets
URL structure and sitemap optimization
This ensures your website isn’t just pretty—it’s found by the right people at the right time.
Real Collaboration, Not Just Client Work
At Hello Errors, collaboration is more than a buzzword—it’s a practice. When you hire them as your Website Developer in Bangalore, you become a partner in the development journey.
Their process includes:
Workshops to understand your business goals
Wireframe design and UX mapping
Agile sprints and frequent check-ins
Transparent communication and delivery milestones
This level of client involvement leads to better alignment, faster feedback loops, and a product that genuinely reflects your brand.
What Makes Hello Errors the Go-To Website Developer in Bangalore?
Let’s recap what makes Hello Errors your ideal web development partner:
🛠️ Full-stack development expertise
🎨 UI/UX-focused design thinking
🚀 SEO-first development methodology
🤖 Integration of AI, ML, and app features
🔄 Continuous post-launch support
🧠 Industry-specific customizations
📍 Bangalore-based team with global quality
Whether you’re looking for a full-fledged business website, a scalable web app, or a platform that integrates seamlessly with mobile, Hello Errors brings precision, performance, and passion to every project.
Ready to Build a High-Performance Website in Bangalore?
Your business deserves more than a basic website. It needs a digital experience that resonates, converts, and scales. As a trusted Website Developer in Bangalore, Hello Errors delivers websites that combine form, function, and future-readiness.
📞 Contact Hello Errors today at https://helloerrors.in Let’s build something exceptional—together.
#WebsiteDeveloperInBangalore#HelloErrors#WebDevelopmentBangalore#SEOWebsiteDeveloper#UXUIDesign#ResponsiveWebDevelopment#TopDeveloperInBangalore#DigitalTransformationIndia#CustomWebsiteDesign#StartupWebSolutions
0 notes
Text
How to Detect Subdomain Takeover in Symfony: A Complete Guide with Code Examples
Subdomain takeover is a serious yet often overlooked security risk, especially in modern PHP frameworks like Symfony. If you’re running a Symfony-based application and have subdomains pointing to deprecated or unconfigured cloud resources, attackers may be able to hijack those subdomains.
In this blog, we’ll walk you through:
What subdomain takeover is
How to detect it manually and programmatically in Symfony
How to prevent it
How to leverage our website vulnerability scanner online
How to boost your app’s security with our professional services
🔍 This guide includes real code examples, image references, and essential links to enhance your cybersecurity posture.
🔐 What Is Subdomain Takeover?
Subdomain takeover occurs when a subdomain (like api.yoursite.com) points to an external service (e.g., AWS S3, GitHub Pages, Azure), but that service is no longer claimed. Hackers can register or claim the service, hijack the subdomain, and serve malicious content.
🧠 For example:
api.yoursite.com -> points to someuser.github.io
If someuser.github.io is deleted and the DNS still points there, anyone can recreate it and take over the subdomain.
⚠️ Why Symfony Apps Are at Risk
Symfony is commonly used with cloud services and CDN integrations. If you're using AWS, GitHub Pages, Netlify, or Heroku in your Symfony setup and later decommission a project without updating DNS records, you're vulnerable.
🧪 How to Check for Subdomain Takeover in Symfony
1. Manually Scan DNS Records
You can manually enumerate subdomains and identify CNAME records pointing to external services. Use tools like:
dig sub.yoursite.com CNAME
Look for services like:
*.s3.amazonaws.com
*.github.io
*.herokudns.com
Compare these with known vulnerable services from sources like Can I Take Over XYZ: https://github.com/EdOverflow/can-i-take-over-xyz
2. Use Symfony to Programmatically Detect Subdomain Issues
Here's a PHP script to run inside your Symfony CLI or custom Command:
// src/Command/SubdomainCheckCommand.php namespace App\Command; use Symfony\Component\Console\Command\Command; use Symfony\Component\Console\Input\InputInterface; use Symfony\Component\Console\Output\OutputInterface; use GuzzleHttp\Client; class SubdomainCheckCommand extends Command { protected static $defaultName = 'security:check-subdomains'; protected function execute(InputInterface $input, OutputInterface $output): int { $subdomains = ['blog.example.com', 'api.example.com']; // Add your subdomains here $client = new Client(['timeout' => 5]); foreach ($subdomains as $subdomain) { try { $response = $client->request('GET', 'http://' . $subdomain); $status = $response->getStatusCode(); $output->writeln("$subdomain is active - HTTP $status"); } catch (\Exception $e) { $output->writeln("<error>$subdomain might be vulnerable: {$e->getMessage()}</error>"); } } return Command::SUCCESS; } }
💡 Run this command with:
php bin/console security:check-subdomains
3. Automate with Our Free Tool
If you want a faster and simpler scan for subdomain takeover and 40+ vulnerabilities:
🔗 Visit 👉 https://free.pentesttesting.com/
📸 Screenshot of Our Website Vulnerability Scanner Tool:

Screenshot of the free tools webpage where you can access security assessment tools.
📸 Sample Assessment Report to check Website Vulnerability:
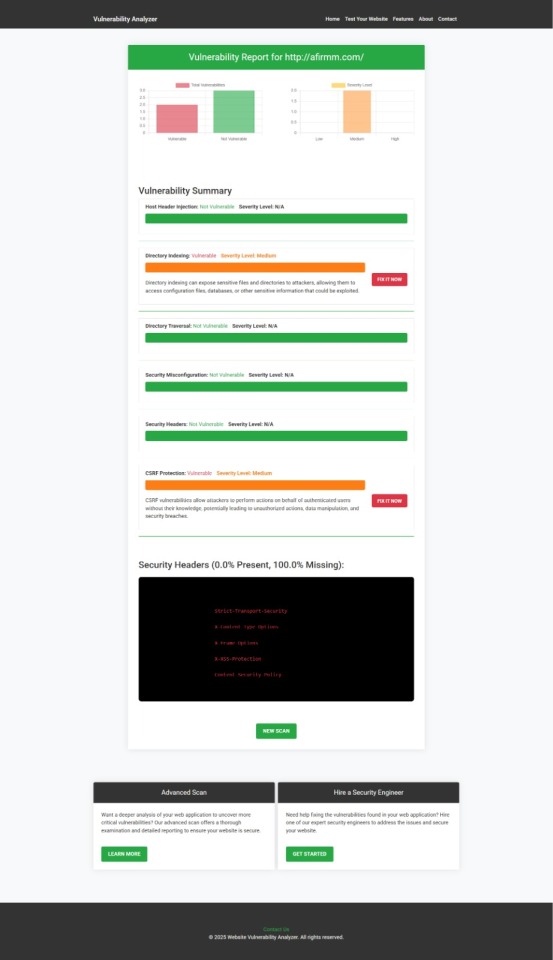
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🛡️ Prevention Tips for Symfony Subdomain Takeover
🔁 Regularly audit DNS records for stale subdomain entries
📦 Remove unused services (Heroku, GitHub Pages, etc.)
🧰 Use automated tools for continuous scanning (e.g., cron jobs + our scanner)
🗂️ Add DNS monitoring to your CI/CD process
📘 Further Reading from Pentest Testing Corp.
For more Symfony security content, visit our blog: 👉 https://www.pentesttesting.com/blog/
Other Symfony-related guides:
🔗 Top 7 WebSocket Vulnerabilities in Laravel (applies to Symfony too!)
🔗 Prevent Buffer Overflow in Symfony
🧰 Our Professional Services
🛠️ Web App Penetration Testing
Need deep manual penetration testing for Symfony or Laravel apps? 🔗 Explore: https://www.pentesttesting.com/web-app-penetration-testing-services/
🤝 Offer Cybersecurity Services to Your Clients
Are you a dev agency, MSP, or hosting provider? You can offer our penetration testing under your brand. 🔗 Learn more: https://www.pentesttesting.com/offer-cybersecurity-service-to-your-client/
📬 Stay Updated with Our Cybersecurity Newsletter
Subscribe to our exclusive newsletter for tips, tools, and vulnerabilities straight to your inbox. 📬 Subscribe on LinkedIn → https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
🔚 Final Thoughts
Subdomain takeover vulnerabilities can be devastating—but they’re preventable. Whether you’re a Symfony developer or a DevOps engineer, it’s critical to automate your checks and audit DNS entries regularly.
✅ Want a free scan? DM me or check https://free.pentesttesting.com/
1 note
·
View note
Text
nMon Nulled Script 1.12

Discover the Power of nMon Nulled Script for Website Monitoring If you’re looking for a reliable and cost-effective solution to keep your website and server performance under control, the nMon Nulled Script is your perfect choice. This advanced monitoring tool empowers webmasters and developers to track their websites seamlessly, ensuring uptime and speed are optimized without any hassle. Available for free download from our website, the nMon Nulled Script offers an all-in-one service monitoring solution that caters to every website owner’s needs. What Is nMon Nulled Script? – A Detailed Product Description The nMon is a professional-grade website and server monitoring script originally developed to provide comprehensive real-time analytics. It offers features such as uptime monitoring, speed analysis, and detailed reports that help you understand how your site is performing at any moment. With the nulled version available for free download on our platform, you get access to all premium functionalities without paying a penny. Whether you manage a personal blog, an e-commerce platform, or a corporate site, the nMon ensures you never miss a critical alert that could impact your online presence. The script integrates easily with various hosting environments and requires minimal configuration, making it user-friendly for beginners and professionals alike. Technical Specifications of nMon Nulled Script Compatible with most web servers including Apache and Nginx Supports PHP 7.2 and above for smooth operation Database integration with MySQL or MariaDB Responsive interface optimized for desktop and mobile devices Real-time data visualization using interactive charts and tables Customizable alert system with email and SMS notifications Lightweight code ensuring minimal server resource consumption Features and Benefits of Using nMon Nulled Script The nMon Nulled Script offers a rich set of features designed to make website monitoring effortless and efficient: Real-Time Monitoring: Get instant updates on website uptime and server performance to tackle issues proactively. Comprehensive Reports: Analyze traffic, response times, and error logs to enhance your site’s reliability. Easy Integration: Seamlessly incorporate the script into your existing infrastructure with straightforward setup guides. Free Access: Download the nMon Nulled Script for free from our website, enabling budget-friendly website management. Boost SEO Performance: Maintain optimal website speed and availability, key factors in search engine rankings. Use Cases for nMon Nulled Script This script is highly versatile and suitable for various scenarios: Website Owners: Keep your site up and running smoothly to deliver the best user experience. Developers: Monitor client websites and servers effectively with a tool that supports multiple environments. Digital Agencies: Offer premium monitoring services to your customers without extra licensing costs. E-commerce Platforms: Ensure uninterrupted service during peak sales periods to maximize conversions. Installation and Usage Guide for nMon Script Getting started with the Nulled Script is straightforward: Download the Script: Access the nulled version directly from our website without any fees. Upload to Server: Transfer the files to your web server via FTP or your hosting control panel. Configure Database: Create a MySQL database and import the provided SQL file to set up necessary tables. Adjust Settings: Modify configuration files with your database credentials and preferred monitoring parameters. Access the Dashboard: Log in to the admin panel to start monitoring your website and server statistics. For enhanced website design, consider pairing this tool with wpbakery nulled, which is available for free download on our site. Frequently Asked Questions (FAQs) Is the nMon Nulled Script safe to use? Yes, our version is thoroughly tested to ensure it functions correctly without security risks. Always download nulled scripts from trusted sources like our website.
Can I customize the monitoring alerts? Absolutely! The script allows you to set up email and SMS notifications tailored to your monitoring preferences. Does it support mobile devices? Yes, the interface is fully responsive and accessible on smartphones and tablets. Where can I get professional design plugins to complement nMon? We recommend trying elementor nulled pro for advanced page building features.
0 notes
Text
Sweep AI: The Future of Automated Code Refactoring
Introduction to Sweep AI
In today’s digital age, writing and maintaining clean code can wear developers down. Deadlines pile up, bugs pop in, and projects often fall behind. That’s where Sweep AI steps in. It acts as a reliable coding assistant that saves time, boosts productivity, and supports developers by doing the heavy lifting in coding tasks.
This article breaks down everything about Sweep AI, how it helps with code automation, and why many developers choose it as their go-to AI tool.
Understanding Sweep AI
Sweep AI is an open-source AI-powered tool that behaves like a junior developer. It listens to your needs, reads your code, and writes or fixes it accordingly. It can turn bug reports into actual code fixes without needing constant manual guidance.
More importantly, Sweep AI does not cost a dime to start. It’s ideal for teams and solo developers who want to move fast without sacrificing code quality.
How Sweep AI Works
Sweep AI works in a simple yet powerful way. Once a developer writes a feature request or a bug report, the AI jumps into action. Here’s what it usually does:
Reads the existing code
Plans the changes intelligently
Writes pull requests automatically
Updates based on comments or suggestions
Sweep AI also uses popularity ranking to understand which parts of your repository matter the most. It responds to feedback and works closely with developers throughout the code improvement process.
Types of Refactoring Sweeps AI Can Handle
Sweeps AI does not just work on surface-level improvements. It digs deep into the code. Some of its main capabilities include:
Function extraction: breaking large functions into smaller, clearer ones
Renaming variables: making names more meaningful
Removing dead code: getting rid of unused blocks
Code formatting: applying consistent style and spacing
It can also detect complex issues like duplicate logic across files, risky design patterns, and nested loops that slow down performance.
Why Developers Are Turning to Sweeps AI
Many developers use Sweeps AI because it:
Saves time
Reduces human error
Maintains consistent coding standards
Improves software quality
Imagine a junior developer who must refactor 500 lines of spaghetti code. That person might take hours or even days to clean it up. With Sweeps AI, the job could be done in minutes.
Step-by-Step Guide to Start Using Sweep AI
You don’t need to be a tech wizard to get started with Sweep AI. Here are two easy methods:
Install the Sweep AI GitHub App Connects to your repository and starts working almost immediately.
Self-host using Docker Ideal for developers who want more control or need to run it privately.
Sweep AI also shares helpful guides, video tutorials, and documentation to walk users through each step.
The Present and the Future
Right now, Sweeps AI already supports languages like Python, JavaScript, TypeScript, and Java. But the roadmap includes support for C++, PHP, and even legacy languages like COBOL. That shows just how ambitious the project is.
In the coming years, we might see Sweeps AI integrated into platforms like GitHub, VS Code, and JetBrains IDES by default. That means you won’t need to go out of your way to use it will be part of your everyday coding workflow.
How Much Does Sweep AI Cost?
Sweep AI offers a flexible pricing model:
Free Tier – Unlimited GPT-3.5 tickets for all users.
Plus Plan – $120/month includes 30 GPT-4 tickets for more advanced tasks.
GPT-4 Access – Requires users to connect their own Openai API key (charges may apply).
Whether you’re working on a startup project or a large codebase, there’s a plan that fits.
Is Sweep AI Worth It?
Absolutely. Sweep AI is more than just another coding assistant it’s a valuable teammate. It understands what you need, helps you fix problems faster, and lets you focus on what really matters: building great products.
Thanks to its smart features and developer-friendly design, Sweep AI stands out as one of the top AI tools for modern software teams. So, if you haven’t tried it yet, now’s a good time to dive in and take advantage of what it offers.
Frequently Asked Questions
Q: Who is the founder of Sweep AI?
Sweep AI was co-founded by William Suryawan and Kevin Luo, two AI engineers focused on making AI useful for developers by automating common tasks in GitHub.
Q: Is there another AI like Chatgpt?
Yes, there are several AIS similar to Chatgpt, including Claude, Gemini (by Google), Cohere, and Anthropic’s Claude. However, Sweep AI is more focused on code generation and GitHub integrations.
Q: Which AI solves GitHub issues?
Sweep AI is one of the top tools for automatically solving GitHub issues by generating pull requests based on bug reports or feature requests. It acts like a junior developer who understands your project.
Q: What is an AI agent, and how does it work?
An AI agent is a software program that performs tasks autonomously using artificial intelligence. It receives input (like code requests), makes decisions, and performs actions (like fixing bugs or writing code) based on logic and data.
Q: Who is the CEO of Sweep.io?
As of the latest information, Kevin Luo serves as the CEO of Sweep.io, focusing on making AI development tools smarter and more accessible.
0 notes
Text
TYPO3 Programming Made Simple: Your First Step

If you’re looking to build powerful, flexible websites, TYPO3 CMS is a great place to start. It’s an open-source content management system (CMS) built for serious projects—think multilingual corporate sites, secure web platforms, and custom features that go far beyond a simple blog. This guide will walk you through the basics of TYPO3 programming, so you can start your development journey with confidence.
What is TYPO3 CMS?
TYPO3 is a CMS written in PHP that’s designed for high-performance websites. Unlike basic CMS tools, TYPO3 is built for large-scale projects. It gives you control over how your website works and looks, using tools like TypoScript, Fluid templates, and extensions.
Getting Your TYPO3 Development Environment Ready
Before you start coding, you need to prepare your setup. Don’t worry—it’s pretty straightforward.
System Requirements: Make sure your system has PHP 8.x, MySQL or MariaDB, Apache or Nginx, and Composer installed.
Install TYPO3 with Composer: Open your terminal and run: bashCopyEditcomposer create-project typo3/cms-base-distribution my-project
Set Up the Database: Once TYPO3 is installed, visit your project in a browser. The built-in installer will guide you through setting up the database and finishing the configuration.
TYPO3 Programming Basics
Let’s look at the key tools TYPO3 gives you to build your site.
TypoScript
TypoScript is TYPO3’s configuration language. It tells TYPO3 how to render content on the page. You don’t need to write PHP—TypoScript lets you control layout and behavior using simple rules.
Fluid Templates
Fluid is TYPO3’s templating engine. It helps separate your HTML design from the backend logic, so you can focus on layout while keeping your code clean and maintainable. It’s especially useful if you're working with designers or frontend developers.
Extensions
In TYPO3, almost everything is built as an extension. Need a blog? An online store? A custom form? There’s probably an extension for that. You can install ready-made ones from the TYPO3 Extension Repository—or build your own for full control.
How to Build Custom Features
Here’s how developers add advanced features to TYPO3:
Creating Extensions: You can use the Extension Builder tool or create one manually by setting up controllers, models, and views. TYPO3 uses the MVC (Model-View-Controller) pattern, which keeps your code structured and easy to work with.
Custom Content Elements: Want content blocks tailored to your exact needs? Use a tool like Mask or write your own to create reusable, flexible elements for editors.
Backend Modules: TYPO3 lets you build tools inside the admin area—like custom dashboards or management panels—to improve the editing experience.
Debugging and Best Practices
No project runs perfectly all the time. Here’s how to handle issues the TYPO3 way:
Turn on debugging in the LocalConfiguration.php file or the Admin Panel.
Use TYPO3’s built-in logging and error reporting to catch problems early.
Follow TYPO3’s coding standards to keep your project clean, consistent, and easy to maintain—especially if you're working in a team.
Why TYPO3?
Built to Scale: TYPO3 handles huge websites with thousands of pages and users.
Multilingual Ready: It makes managing content in multiple languages straightforward and efficient.
Secure by Design: TYPO3 includes strong access controls and gets regular security updates.
Helpful Community: With detailed documentation, active forums, and tutorials, help is always within reach.
Final Thoughts
TYPO3 isn’t just another CMS—it’s a developer’s toolset for building professional, scalable websites. Once you understand TypoScript, Fluid templates, and extensions, you’ll be ready to create just about anything. Whether it’s a small custom feature or a full-blown enterprise website, TYPO3 gives you the structure and power to bring your ideas to life.
0 notes
Text
Empowering Digital Growth with Expert eCommerce Services

In today’s digitally connected world, eCommerce services have become the backbone of business success. Whether it’s a startup entering the market or an established brand looking to scale, efficient and reliable digital commerce solutions are crucial. With platforms like Tenovia offering expert strategies and technological solutions, brands now have the opportunity to grow rapidly while focusing on their core offerings.
Why Your Business Needs eCommerce Services Today
Digital transformation is no longer optional—it's essential. Consumer behavior has shifted significantly toward online platforms, prompting businesses to adapt quickly or risk falling behind. This is where eCommerce services come into play. These services provide comprehensive support across various digital functions such as marketplace management, D2C website development, digital marketing, analytics, and performance tracking.
Companies like Tenovia empower brands to harness the full potential of the digital landscape. From setting up online stores to optimizing customer experiences, these solutions drive visibility, engagement, and ultimately, conversions.
Key Features of Professional eCommerce Services
A robust eCommerce service provider doesn’t just create a website. It creates a complete digital ecosystem that aligns with your brand vision and business goals. Let’s explore the key components that define quality eCommerce services:
1. Custom eCommerce Development
Every brand has unique needs. Tailor-made development solutions ensure your online store reflects your brand identity and provides a seamless customer experience. At Tenovia, platforms such as Shopify, Magento, WooCommerce, and custom PHP frameworks are leveraged to build efficient, scalable, and responsive sites.
2. Digital Marketing & Performance Campaigns
Driving traffic is crucial, but what matters most is converting that traffic. With data-driven SEO, paid ad campaigns, and social media strategies, expert teams manage your brand presence across all digital channels. Tenovia’s digital marketing experts optimize every campaign to deliver measurable ROI and business growth.
3. Marketplace Management
Selling on platforms like Amazon, Flipkart, and Nykaa can be complex. A top-tier eCommerce service provider handles product listings, pricing strategies, inventory sync, and promotional campaigns, giving your brand an edge on crowded marketplaces.
4. Analytics & Insights
Smart decision-making is rooted in data. eCommerce solutions include analytics dashboards, sales reports, consumer behavior tracking, and custom KPIs. Tenovia offers end-to-end analytics so you always know what’s working—and what needs improvement.
5. Operational Excellence
From order processing to customer support, back-end operations must be smooth and timely. Leading providers like Tenovia integrate logistics, CRM, and ERP systems for operational efficiency.
Benefits of Partnering with a Reliable eCommerce Services Provider
Choosing the right partner can transform your business. Here's how:
✔️ Enhanced Online Visibility
With SEO, content strategy, and ad optimization, your brand becomes more discoverable. Better visibility leads to increased traffic and sales.
✔️ Better Customer Experience
UI/UX design, intuitive navigation, fast page loads, and secure checkout options make shopping effortless, improving customer satisfaction and repeat purchases.
✔️ Scalability
Whether you’re expanding across new markets or launching new products, a professional eCommerce services provider ensures your system is future-ready.
✔️ Cost Efficiency
Outsourcing complex tasks such as development, marketing, and operations reduces costs and minimizes errors. It also frees up your internal teams for core business tasks.
✔️ Revenue Growth
When all aspects of your digital business—from traffic to conversion—are optimized, it naturally results in greater profitability.
Tenovia – A Leader in Data-Driven eCommerce Services
Tenovia stands out as a partner committed to driving eCommerce success through intelligent, integrated, and result-oriented strategies. With over a decade of experience and a portfolio spanning various sectors like fashion, electronics, FMCG, and healthcare, Tenovia helps brands scale sustainably and competitively.
Their approach combines technology, strategy, and execution to deliver solutions that are not just efficient—but transformative. Whether it’s launching a D2C website or managing performance campaigns across digital platforms, Tenovia ensures every brand achieves its eCommerce goals.
Clients benefit from:
Strategic consulting with real-time market insights
Comprehensive digital marketing campaigns
Conversion rate optimization and funnel improvements
Continuous monitoring and technical support
Choosing the Right eCommerce Services: What to Look For
When selecting an eCommerce services provider, consider the following:
Industry Experience: Have they worked with brands similar to yours?
Technology Stack: Do they use the latest tools and platforms?
Client Testimonials: What do their clients say about results?
Customization: Can they tailor solutions to your unique needs?
Support & Communication: Is their team accessible and responsive?
Tenovia ticks all these boxes, making them a trusted growth partner for businesses looking to succeed online.
Future Trends in eCommerce Services
The digital commerce space is rapidly evolving. Here are some upcoming trends you should prepare for:
AI-Powered Personalization: Offering unique experiences based on user behavior.
Voice Commerce: Optimizing for voice search across platforms like Alexa and Google Assistant.
AR/VR Shopping Experiences: Creating immersive shopping interfaces.
Subscription Models: Driving consistent revenue with recurring purchases.
Green Commerce: Emphasizing sustainability in logistics and packaging.
A proactive eCommerce services provider like Tenovia helps brands not only keep up with these trends but leverage them for competitive advantage.
Conclusion
In an era where digital is the new storefront, investing in expert eCommerce services is no longer a luxury—it’s a necessity. From building your online store to executing strategic marketing campaigns and analyzing performance data, every aspect must be synchronized for success.
Partnering with an experienced provider like Tenovia ensures your business not only survives the digital shift but thrives. With a commitment to data, technology, and performance, Tenovia helps you unlock your brand’s full online potential. So, if you're ready to drive conversions, delight customers, and dominate your niche, it’s time to take the leap with professional eCommerce services.
0 notes
Text
Rapid URL Indexer Launches Complete RESTful API for URL Indexing Projects
Rapid URL Indexer has released comprehensive documentation for its RESTful API, giving developers the power to programmatically submit URLs for indexing and monitor their progress. The new API documentation provides everything developers need to integrate URL indexing capabilities into their own applications, content management systems, or workflow automation tools.
The Rapid URL Indexer API follows RESTful principles, making it intuitive for developers familiar with modern web APIs. All endpoints accept and return JSON data, with clear status codes and error messages to simplify debugging and integration.
Authentication is handled via API keys, which are included in the X-API-Key header for each request. This approach provides a secure yet simple authentication mechanism that works well with existing API clients and frameworks.
The API includes several key endpoints that cover the full lifecycle of URL indexing projects, including URL submission, project status checking, report generation, and account management.
The documentation includes practical code examples in multiple languages, including Python, JavaScript (Node.js), PHP, and Ruby. These examples demonstrate common workflows, such as submitting a batch of URLs and polling for completion status.
To get started with the Rapid URL Indexer API, developers need to create an account, subscribe to an appropriate plan, and generate an API key from the dashboard. The documentation includes a quick start guide that walks through this process and provides initial examples to verify the setup.
Check out the full documentation and start building with our API today: https://rapidurlindexer.com/indexing-api/
0 notes