#PerimeterSecurity
Explore tagged Tumblr posts
Text

K12 Crash Rated Gates (M50) – Maximum Security, Zero Compromise!
When critical infrastructure demands unbreakable protection, trust the K12 (M50) Crash Rated Gates engineered by SECURE INDIA.
✓ Certified to stop a 6.8-ton truck at 80 km/h ✓ Perfect for embassies, data centers, military zones & high-risk sites ✓ Fully customizable with automated operation ✓ Designed in India, Built to Global Standards
Contact us today! 📲 +91-85114-24215, +91-93132-23737 ✉️ [email protected] 🔗 www.secure-india.com
#SecureIndia#CrashRatedGates#K12Gates#M50Certified#HostileVehicleMitigation#HighSecuritySolutions#PerimeterSecurity#MadeInIndia
0 notes
Text
The Power of Boundaries: Why Fencing Is Essential for Your Home, Business, or Property
In a world where security, privacy, and design matter more than ever, fencing has evolved from a simple boundary marker to a powerful statement of safety, value, and intentional living. Whether you're a homeowner, business operator, or property developer, the fence around your space is more than just wood, vinyl, or steel it’s peace of mind.
1. Security First: Keep the Right Things In (and Out)
Fencing is the first line of defense against unwanted visitors, trespassers, and wildlife. For homes, it deters burglars and keeps pets and children safely within the yard. For businesses, it protects assets and ensures restricted access where needed. It’s a silent guardian that works around the clock.
2. Privacy Without Compromise
Your backyard should feel like a retreat not a public park. A properly designed fence creates a cocoon of comfort where you can relax, entertain, or work without the eyes of the world on you. In commercial settings, it shields operations, reduces distractions, and creates a professional perimeter.
3. Boosting Property Value
A well-installed fence doesn’t just protect it pays. It enhances curb appeal and increases resale value. In competitive markets, a beautiful fence can be the factor that turns a prospect into a buyer. Industrial fencing also shows your business is serious, organized, and committed to safety.
4. Legal and Zoning Compliance
In many areas, fencing is a legal requirement especially for pools, commercial spaces, or properties near wildlife reserves. Proper fencing helps you avoid costly fines or liabilities, and clearly marks your property boundaries, preventing disputes with neighbors or nearby businesses.
5. Aesthetic & Branding Statement
From rustic wooden pickets to sleek metal slats, fences can match and even elevate the visual identity of a home or business. For industries, fencing is often part of the brand experience sending a message of order, professionalism, and protection.
6. Customized for Every Purpose
Residential fences come in styles tailored to gardens, pools, and pets. Industrial fences can include barbed wire, electric components, or surveillance integration. No matter the use case privacy, décor, safety, or control there’s a fence designed just for you.
7. Noise Reduction & Environmental Control
Live near a highway or industrial zone? Fences help muffle unwanted noise. They also serve as windbreaks, reduce dust, and even help control snow drifts in colder climates. It’s a buffer between you and the elements.
Conclusion:
A fence is more than a border it’s a bold decision to protect what matters. It’s the backbone of security, the shield of privacy, the architect of order. Whether you’re enclosing a backyard garden or a multimillion-dollar facility, the right fence transforms your space from vulnerable to fortified, from open to owned.
Don’t underestimate the power of a good fence. It’s not just a barrier. It’s a statement.
#FenceInstallation#HomeSecurity#PropertyProtection#FencingSolutions#ResidentialFencing#CommercialFencing#WhyFencesMatter#BoundaryProtection#FencingForPrivacy#SecureYourSpace#HomeImprovement#IndustrialFencing#OutdoorPrivacy#PerimeterSecurity#FenceBenefits
1 note
·
View note
Text
Home Burglary Caught on Camera: Man Climbs Fence, Checks for Hidden Keys, Breaks in Through Dog Door | #shorts In this shocking CCTV footage, a burglar climbs a fence into the side yard of a home, checks the perimeter for hidden keys, and eventually breaks in through a dog door. This footage serves as a stark reminder of how important it is to secure all areas of your home, from hidden keys to entry points like dog doors. Stay vigilant, reinforce your home security, and make sure to regularly inspect your property for potential vulnerabilities. Subscribe for more real-life CCTV footage and home security advice. Home burglary caught on camera, Man climbs fence to break in, Checking hidden keys, Breaking in through dog door, Perimeter security, Home security footage, Real-life CCTV footage, Burglary prevention tips, Dog door security, Securing your home
Importance of securing entry points
Hidden key security risks
How burglars plan home break-ins
CCTV footage for burglary prevention
Reinforcing home security systems
#CaughtOnCamera#HomeBurglary#CCTVFootage#HomeSecurity#DogDoorSecurity#BurglaryPrevention#PerimeterSecurity#StayVigilant#HomeSurveillance#CCTV
0 notes
Text
Home Burglary Caught on Camera: Man Climbs Fence, Checks for Hidden Keys, Breaks in Through Dog Door In this shocking CCTV footage, a burglar climbs a fence into the side yard of a home, checks the perimeter for hidden keys, and eventually breaks in through a dog door. This footage serves as a stark reminder of how important it is to secure all areas of your home, from hidden keys to entry points like dog doors. Stay vigilant, reinforce your home security, and make sure to regularly inspect your property for potential vulnerabilities. Subscribe for more real-life CCTV footage and home security advice. Home burglary caught on camera, Man climbs fence to break in, Checking hidden keys, Breaking in through dog door, Perimeter security, Home security footage, Real-life CCTV footage, Burglary prevention tips, Dog door security, Securing your home
Importance of securing entry points
Hidden key security risks
How burglars plan home break-ins
CCTV footage for burglary prevention
Reinforcing home security systems
#CaughtOnCamera#HomeBurglary#CCTVFootage#HomeSecurity#DogDoorSecurity#BurglaryPrevention#PerimeterSecurity#StayVigilant#HomeSurveillance#CCTV
0 notes
Text
Distributed Acoustic Sensing: The Future of Downhole Monitoring

Distributed Acoustic Sensing is an optical fiber sensing technique that uses fiber optic cables to detect and record acoustic and seismic signals along extended distances. Standard DAS arrays can continuously monitor signals over distances of 10-100 km with resolutions as fine as 1 meter. Specialty this systems can monitor over distances greater than 100 km.
How Does it Work?
Distributed Acoustic Sensing works by detecting acoustic or seismic signals that interact with the fiber optic cable. Standard telecommunications optical fibers are used, with no special components required within the fiber itself. Laser pulses are sent down the fiber and any signal that mechanically perturbs the fiber will cause some of the backscattered light to change wavelength via the Brillouin effect. This change is measured and provides information about the location and nature of the acoustic signal. By timing the return signal, the system can accurately locate acoustic events to within centimeters over the entire length of the fiber.
Applications for Downhole Monitoring
One of the most promising applications for Distributed Acoustic Sensing (DAS) is in downhole monitoring during oil and gas operations. Standard techniques like tubing-deployed monitoring tools provide point measurements but are unable to continuously monitor zones between sensor locations. It offers the potential to monitor acoustic signals along the entire length of production or injection wells. This opens up possibilities like:
- Flow profiling to detect zones of higher or lower flow along horizontal wellbores. Pinpointing fluid movement across fractures or between reservoir layers.
- Completion diagnostics to locate failed zones, casing leaks or other problems without pulling tools in and out of the well. Real-time monitoring avoids unnecessary workovers.
- Hydraulic fracturing monitoring to observe fracture propagation in unprecedented detail. It can detect the exact location and timing of perforation shots from multi-stage fracs to optimize treatment.
- Production monitoring to detect downhole fluid problems like sand ingress or water breakthrough earlier. Real-time zonal isolation monitoring avoids premature well shut-ins or abandonment.
Challenges for Downhole Deployment
While it shows tremendous promise for downhole monitoring applications, several technical challenges must still be addressed for reliable long-term deployment down wellbores:
- Temperature effects - Standard telecom fibers exhibit significant signal attenuation above around 80°C which limits applications to shallower wells or those with significant cooling. Ruggedized high-temperature fibers are being developed and tested.
- Fiber protection - Downhole fibers must withstand abrasive fluids, sand production, production tubing movement and other hazards. Robust protective coatings and housings are an active area of research to provide sufficient buffering.
- Deployment reliability - Repeated deployment of Distributed Acoustic Sensing cables downhole without damage requires further refinement of deployment tools and techniques. Improved reliability avoids unnecessary operational costs.
- Power supply – Downhole sensors require reliable long-term power, usually supplied topside via the fiber optic cable itself. High temperatures and rugged deployment impact power delivery abilities.
Overcoming these challenges is an area of active industry R&D with progress continually being made. As reliability improves, it promises to transform downhole monitoring capabilities.
Permanent Reservoir Monitoring Applications
In addition to deployments during discrete operations like hydraulic fracturing treatments, permanent reservoir monitoring (PRM) use cases provide some of the most exciting potential applications for Distributed Acoustic Sensing technology:
- Long-term zonal isolation - Continuously monitor for fluid migration or casing issues for early remediation to avoid premature reservoir compartmentalization.
- Water/gas coning detection - Detect upward fluid fronts earlier to optimize production strategies before detrimental water/gas breakthrough.
- Compartmentalized reservoir management - Optimize production across disparate zones within the same reservoir by continually profiling inter-zonal flow behaviors.
- 4D seismic correlation - Directly correlating time-lapse 4D seismic surveys with downhole fluid fronts encountered by DAS arrays to rapidly refine subsurface models.
- Borehole stability monitoring - Detect microseismicity, casing strains or fractures for zonal integrity assurance over decades-long field lifetimes. Avoid costly workovers.
The ability to continually monitor entire wellbores for decades enables unprecedented reservoir insight to maximize recovery. As technical issues are solved, PRM using it will drive major efficiency gains across mature fields globally.
Distributed acoustic sensing using fiber optic cables represents a disruptive new monitoring paradigm. Moving away from discrete downhole sensors towards continuum sensing unlocks capabilities never before possible. With continued progress,it will profoundly impact how subsurface operations are planned, executed and optimized. Permanent reservoir and long-term zonal isolation monitoring promise to drive step-changes in efficient, cost-effective oilfield management. It is truly the future of downhole monitoring and reservoir insight.
Get more insights on Distributed Acoustic Sensing (DAS)
About Author:
Ravina Pandya, Content Writer, has a strong foothold in the market research industry. She specializes in writing well-researched articles from different industries, including food and beverages, information and technology, healthcare, chemical and materials, etc. (https://www.linkedin.com/in/ravina-pandya-1a3984191)
#DistributedAcousticSensing#DAS#FiberOpticSensing#SeismicMonitoring#PipelineMonitoring#PerimeterSecurity#TrafficMonitoring
1 note
·
View note
Text
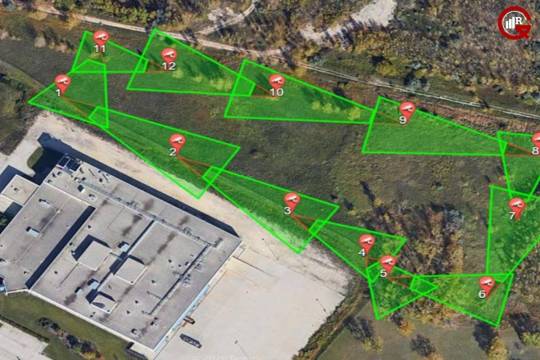
Enhancing Perimeter Security: Strategies For Protecting Your Property

In an era marked by increasing security threats and evolving risks, ensuring the safety of physical assets has become a paramount concern for organizations and individuals alike. Among the various layers of security, perimeter security stands as the first line of defense, forming a critical barrier against unauthorized access and potential threats. From residential properties to commercial establishments, the effectiveness of perimeter security measures plays a pivotal role in safeguarding assets, infrastructure, and most importantly, the people within.
The defense area encompasses a range of strategies and technologies designed to detect, deter, and respond to intrusions along the boundaries of a property. While traditional methods such as fences and gates remain fundamental components, advancements in technology have introduced sophisticated solutions capable of providing enhanced protection and real-time threat intelligence. In this article, we explore the importance of perimeter security and delve into effective strategies for bolstering protection in today’s dynamic threat landscape.
Understanding the Significance of Perimeter Security
The perimeter serves as the initial point of contact between a facility and potential threats. A robust security system not only prevents unauthorized access but also acts as a psychological deterrent, dissuading would-be intruders from attempting breaches. Moreover, by establishing clear boundaries and controlled access points, defense area measures enable efficient monitoring and response, minimizing the risk of security breaches and unauthorized activities.
In addition to safeguarding physical assets, the defense area plays a crucial role in ensuring regulatory compliance, protecting sensitive information, and preserving the privacy of occupants. For industries such as critical infrastructure, healthcare, and government facilities, the consequences of perimeter breaches can be severe, ranging from data breaches to operational disruptions and even threats to public safety. Therefore, investing in robust defense area solutions is not just a matter of protection but also a proactive measure to mitigate potential liabilities and safeguard reputations.
Key Components of Effective Perimeter Security

Physical Barriers: Traditional elements like fences, walls, and gates form the foundation of perimeter security. These barriers establish clear boundaries and control access, making it more difficult for unauthorized individuals to breach the perimeter. Modern advancements in materials and design have led to the development of high-security fences and barriers resistant to tampering, cutting, and climbing.
Surveillance Systems: Closed-circuit television (CCTV) cameras, motion sensors, and infrared detectors are integral components of a comprehensive perimeter surveillance system. These devices provide continuous monitoring of the perimeter, enabling real-time detection of suspicious activities and potential intrusions. Coupled with analytics software and remote monitoring capabilities, surveillance systems offer enhanced situational awareness and facilitate prompt response to security threats.
Access Control Systems: Access control systems regulate entry and exit points, allowing only authorized individuals to access the premises. From keypad entry systems to biometric scanners and smart card readers, modern access control technologies offer diverse options for controlling access based on user credentials and permissions. Integration with surveillance systems and alarm systems further enhances security by logging access events and triggering alerts in case of unauthorized attempts.
Intrusion Detection Systems (IDS): IDS utilize sensors and alarms to detect unauthorized entry attempts or breaches of the perimeter. These systems can be configured to detect specific threats such as forced entry, perimeter breaches, or tampering with security infrastructure. Upon detection, IDS triggers immediate alerts to security personnel or initiates automated responses such as activating lights, and sirens, or notifying law enforcement.
Perimeter Lighting: Adequate lighting along the perimeter enhances visibility and acts as a deterrent to intruders. Motion-activated lights and programmable lighting systems can effectively illuminate vulnerable areas during nighttime or low-light conditions, reducing blind spots and improving surveillance coverage.
Implementing a Comprehensive Perimeter Security Plan

Effective defense area requires a holistic approach that integrates multiple layers of protection tailored to the specific needs and vulnerabilities of the property. Here are some essential steps to consider when implementing a comprehensive perimeter security plan:
Risk Assessment: Conduct a thorough assessment of the property to identify potential security vulnerabilities, including weak points in the perimeter, blind spots in surveillance coverage, and access control deficiencies. Evaluate the level of risk posed by various threats such as theft, vandalism, unauthorized access, and terrorist activities.
Security Policy Development: Establish clear security policies and protocols governing perimeter security measures, access control procedures, and incident response protocols. Ensure that all stakeholders, including employees, tenants, and security personnel, are trained in security awareness and compliance with established policies.
Integration of Technologies: Invest in modern security technologies that offer seamless integration and interoperability, allowing for centralized monitoring and management of teh defense area systems. Implement a security information and event management (SIEM) system to consolidate security alerts and streamline incident response processes.
Regular Maintenance and Testing: Conduct routine maintenance checks and performance testing of perimeter security systems to ensure optimal functionality and reliability. Regularly update firmware and software patches to address vulnerabilities and mitigate potential security risks.
Collaboration with Law Enforcement: Establish partnerships with local law enforcement agencies and emergency responders to enhance coordination and support during security incidents. Share relevant information and intelligence to facilitate proactive threat mitigation and investigation of security breaches.
Future Trends and Emerging Technologies
As security threats continue to evolve, the field of security is witnessing rapid advancements in technologies such as artificial intelligence (AI), machine learning, and the Internet of Things (IoT). Predictive analytics and AI-driven threat detection algorithms enable the proactive identification of potential security threats based on anomalous behavior patterns and trends. Similarly, IoT-enabled sensors and devices offer real-time monitoring of environmental conditions and perimeter status, enabling dynamic adjustments to security protocols and response strategies.
Furthermore, the integration of physical security systems with cybersecurity measures is becoming increasingly important to mitigate the risk of cyber-physical attacks targeting the defense area infrastructure. By adopting a comprehensive approach that addresses both physical and digital security threats, organizations can strengthen their resilience and adaptability in the face of evolving security challenges.
Conclusion
In an age of heightened security concerns and complex threats, the importance of perimeter security cannot be overstated. By implementing robust defense area measures and adopting a proactive, multi-layered approach, organizations can enhance the protection of their assets, infrastructure, and people. From physical barriers and surveillance systems to access control technologies and intrusion detection systems, leveraging the latest advancements in security technology is essential to stay ahead of emerging threats and safeguard against potential vulnerabilities. By prioritizing perimeter security as a fundamental component of their overall security strategy, organizations can mitigate risks, ensure regulatory compliance, and foster a safe and secure environment for their stakeholders.
#PerimeterSecurity#SecurityTechnology#RiskAssessment#SurveillanceSystems#AccessControl#EmergingTechnologies
0 notes
Text

Security That Fits Your Project – Perfectly. We’re proud to showcase one of our recent installations of Neptune’s Tyre Killer, a robust and adaptable security solution designed for high-performance across a wide range of applications. Engineered with precision and powered by a Built-in Hydraulic Unit, this system is ideal for extreme climates and demanding environments. Its seamless integration with loop detectors, signal lights, and other access control systems ensures enhanced operational efficiency. Available in Unidirectional or Bidirectional configurations and multiple mounting options – Flat, Hump, or Shallow.
For Product Inquiry: Call Us @ +91 9555 500 300 Email: [email protected] . . .
🚧 #securitysolutions #TyreKiller #RoadBlocker #PerimeterSecurity #HighSecurity #perimeterprotection #SpikeBarriers #vehicleimmobilization #neptuneautomatic #SafetyFirst #HostileVehicleMitigation #protection #solutions #accessories #security #banking #military #airports
0 notes
Photo

Forteza - победитель конкурса «Экспортёр года 2020» Forteza ist der Gewinner des Wettbewerbs EXPORTEUER DES JAHRES 2020 Forteza is the winner of the competition «The Exporter of the year 2020» Forteza est le vainqueur du concours «L’Exportateur de l'année 2020» ¡Bienvenido a la exposición Securika Moscow 2021! Forteza is the winner of the competition «The Exporter of the year 2020» On March 24, 2021, an award ceremony of exporting companies of Penza region was held in Penza. More than 30 enterprises engaged in export to the near and far abroad countries competed for the title of the best exporter. The company OOO Okhrannaya technika has been recognized as the best in the category «The exporter with the most extensive export geography» and «The exporter of the year in the field of high technologies in the category «small and medium-sized enterprises». The company has more than once become the winner in various categories of annual competitions among the enterprises of Penza region working in the field of foreign trade, and this year OOO Okhrannaya technika again confirmed its right to be one of the best. #perimeter #fortezarussia #forteza #perimeterprotection #perimetersecurity #security #outdooralarm #alarmsystem #FORTEZA-PERIMETER #microwavedetectors #microwavesensors #microwavesensor #fortezasensor #protectionofthearea #alarmaroundthehouse #safe #safety #secure #security #protection #microwave #barriers #fenceprotectiondetecters #securitycontrolsystem #microwavedetectors #fenceprotectionsystem #périmètre #protectionpérimétrique #signalisation #systèmedalarme (at Penza, Russia) https://www.instagram.com/p/CM4YTGUgyso/?igshid=vqval107udff
#perimeter#fortezarussia#forteza#perimeterprotection#perimetersecurity#security#outdooralarm#alarmsystem#microwavedetectors#microwavesensors#microwavesensor#fortezasensor#protectionofthearea#alarmaroundthehouse#safe#safety#secure#protection#microwave#barriers#fenceprotectiondetecters#securitycontrolsystem#fenceprotectionsystem#périmètre#protectionpérimétrique#signalisation#systèmedalarme
2 notes
·
View notes
Photo

#optex #optexsecurity #pujaso #security #intrusion #perimetersecurity (at Okhla Phase-1, Office) https://www.instagram.com/p/CnO6ql-Sxs8/?igshid=NGJjMDIxMWI=
1 note
·
View note
Photo

Video surveillance system - How to choose a video surveillance system for your business. Don’t Know Where to Start? There are so many options when it comes to updating, replacing, or choosing a new video surveillance system. Give the experts at ELV Technologies a call today to get started. #videosurveillance #ipcctv #ipcameras #cctv #cctvinstallation #cctvsystem #videoanalytics #ptzcamera #anpr #thermalcameras #ipcamera #nvr #dvr #storagesolutions #storagesystems #remotemonitoring #surveillancecamera #perimetersecurity #integratedsolutions (at Tamil Nadu) https://www.instagram.com/p/CMlcJh4BLzz/?igshid=61ztzr81jm7r
#videosurveillance#ipcctv#ipcameras#cctv#cctvinstallation#cctvsystem#videoanalytics#ptzcamera#anpr#thermalcameras#ipcamera#nvr#dvr#storagesolutions#storagesystems#remotemonitoring#surveillancecamera#perimetersecurity#integratedsolutions
1 note
·
View note
Text

Crash Rated Automatic Bollards – Smart Security Starts Here!
Looking to upgrade your perimeter protection? Start with our "K4 Crash Rated Automatic Bollards (M30)" — designed to stop threats with strength and speed.
For higher security needs, explore our advanced models: K8 Bollards (M40) – Enhanced protection for critical sites K12 Bollards (M50) – Maximum impact resistance for the highest threat levels
✓ Engineered in India, trusted worldwide ✓ Ideal for embassies, defense zones, corporate HQs & more
Contact us today to choose the right level of protection! 📲 +91-85114-24215, +91-93132-23737 ✉️ [email protected] 🔗 www.secure-india.com
#SecureIndia#CrashRatedBollards#PerimeterSecurity#M30#K4Bollard#K8Bollard#K12Bollard#AccessControl#VehicleSecurity#HighSecuritySolutions
0 notes
Photo

If you manage a warehouse in #southernontario you are our kind of client. We are experts in providing #PerimeterSecurity for commercial, industrial facilities - #Gates, #Overheaddoors, #Locksmithing - #staysafe - #StayProtected - #HudsonProtected (at Southern Ontario) https://www.instagram.com/p/CGixtOwH4OF/?igshid=1vm54jyagw2m4
#southernontario#perimetersecurity#gates#overheaddoors#locksmithing#staysafe#stayprotected#hudsonprotected
0 notes
Photo

Go ahead and relax, I got your back. . . #belgianshepherd #belgianmalinois #gotyourback #perimetersecured #workingdog #dogoftheday #dog🐶 #safety #securityguard #ifeelsafe #ifeelsafewithyou #prideofbelgium #maligator #malinois (at Casa De Pellson) https://www.instagram.com/p/Byt0XZdhMyk/?igshid=9qv2csmvcw99
#belgianshepherd#belgianmalinois#gotyourback#perimetersecured#workingdog#dogoftheday#dog🐶#safety#securityguard#ifeelsafe#ifeelsafewithyou#prideofbelgium#maligator#malinois
0 notes
Photo

¿por qué VIDEOTEC? Durabilidad: garantía de 3 años (opcional a 5 años) variedad de opciones de encargo: construya la configuración de producto para sus productos certificados de la aplicación: estándares de la industria de Int'l y otra prueba ambiental #Onvif: miembro que contribuye #PerimeterSecurity #CIP #PTZ #IPvideo #videotec #notiseg.com
0 notes
Link
1 note
·
View note
Text
Mr Paki aka The Bro Leon✨
There's been less laughter and singing in my life since you left bro, hopefully I get to see Willie next week while I'm home - I'm his bestie from Sydney now but you left some big fucking shoes to fill yo 😭 he smiles when we speak of you but like me we just wanna ball our eyes out.
Mannnnn how about he's such a fashionista too, fulla gives me a run for my money - all the ladies love it when he drops off their orders, the actual epic charmer lolz #pooeah
This pic popped up in my memories today, bittersweet because I can still hear you making all of us laugh especially Jordy.
Will take a stroll through Otablu in your honour g! Thank you for always being the you I needed bro 🥺 Miss you majorly #perimetersecured

0 notes