#Ransomware attacks in India
Explore tagged Tumblr posts
Text
Ransomware Attack Hits 300 Indian Banks: Payment Systems Down
300 Indian Banks Hit by Ransomware Attack: Payment Systems Disrupted A significant ransomware attack has temporarily crippled payment systems at nearly 300 small banks across India. The breach, targeting a key technology service provider, has disrupted banking operations nationwide. Ransomware Attack Targets C-Edge Technologies The attack struck C-Edge Technologies, a major provider of banking…
0 notes
Text
Third-Party Cyber Insurance Coverage Explained | Cyber Insurance in India

In today’s digital world, cyber risks are not just internal threats. Data breaches, identity theft, and cyberattacks can trigger lawsuits, penalties, and third-party claims, making cyber insurance in India a necessity, not a choice.
One essential part of any cyber insurance policy is Third-Party Coverage. Unlike first-party coverage (which protects your own business), this coverage shields you from claims made by others — customers, clients, vendors, or regulatory authorities.
Let’s explore:
What is cyber insurance?
What is third-party cyber liability coverage?
Why Indian companies need it
Key risks covered
Difference between first-party & third-party coverage
Benefits for corporates, SMEs, and startups
What is Cyber Insurance?
Cyber insurance, also known as cyber security insurance or cyber liability insurance, protects businesses from financial loss due to cyber threats like:
Data breaches
Malware & ransomware attacks
Hacking & phishing
Unauthorized access
Business interruption
Today, cyber insurance in India is an integral part of commercial insurance portfolios, especially for digital-first companies.
What is Third-Party Coverage in Cyber Insurance?
Third-party coverage refers to the protection provided against claims, legal actions, or regulatory penalties brought by external parties affected by a cyber incident in your organization.
For example:
If your systems are hacked and customer data is leaked, your clients may sue you.
If a business partner suffers loss due to a cyber breach on your end, they may file a claim.
If a regulator penalizes you for failing to protect personal data, you're liable.
Third-party cyber insurance pays for your legal defense, settlements, and related costs.
What Does Third-Party Cyber Insurance Cover?
Here’s a breakdown of key coverages under third-party liability in cyber insurance:
1. Legal Defense Costs
Covers attorney fees, court expenses, and legal proceedings if a third party sues your company for negligence or data loss.
2. Regulatory Fines & Penalties
Pays penalties imposed by government bodies or regulators (like CERT-In, RBI, IRDAI) for non-compliance with data protection laws.
3. Third-Party Damages
If a client or partner suffers financial loss due to your cyber incident, this coverage compensates them.
4. Media Liability
Covers claims related to defamation, copyright infringement, or libel from your digital content (especially relevant to media, tech, or advertising companies).
5. Privacy Liability
Protects against lawsuits stemming from loss or mishandling of personal identifiable information (PII) or sensitive customer data.
Third-Party vs First-Party Cyber Coverage
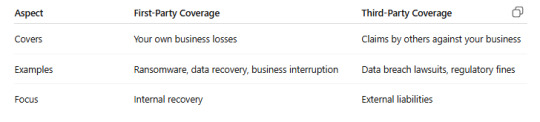
A complete cyber insurance policy should include both coverages for end-to-end protection.
Why Indian Businesses Need Third-Party Coverage
Cybersecurity threats in India are rising exponentially, especially with digital payments, cloud adoption, and remote work becoming mainstream.
Here’s why third-party coverage in cyber insurance is critical for Indian companies:
India has the second-largest number of internet users globally — more users mean more data to protect.
The DPDP Act (Digital Personal Data Protection Act) mandates strict privacy compliance.
A data breach now costs Indian companies an average of ₹18.3 crore.
Increasing legal scrutiny and class-action suits around personal data exposure.
Whether you're in e-commerce, fintech, healthcare, or education, third-party risks can impact your brand reputation, finances, and operations.
Who Should Opt for Third-Party Cyber Liability Coverage?
✅ Corporates and enterprises handling large-scale consumer or partner data ✅ Startups and SMEs operating online platforms, apps, or digital services ✅ IT and BPO companies with access to client databases or networks ✅ Healthcare and BFSI sectors governed by strict data privacy regulations ✅ Any company looking to strengthen its business insurance or company insurance coverage
How to Choose the Right Cyber Insurance Policy
When selecting a cyber insurance policy, ensure it includes:
Both first-party and third-party protection
High coverage limits for legal claims & data breaches
Coverage of legal expenses, settlements, and privacy violations
Add-ons like crime insurance and reputation damage control
Fast claims support and cyber incident response
🧩 Real-World Example
Case: Indian Fintech Startup (2023) A fintech firm faced a lawsuit after hackers breached their system and leaked customer KYC data. Customers sued the company, and regulators imposed fines. Their third-party cyber insurance covered:
₹2.5 crore in legal fees
₹1 crore in regulatory fines
₹1 crore in settlements with affected users
Without cyber coverage, these costs could have crippled the startup.
Final Thoughts
Cyber and crime insurance isn’t just about securing IT systems — it’s about protecting your business from reputational and legal ruin. Third-party coverage ensures you're prepared for legal backlash and financial liability when things go wrong.
In a digitally connected economy, having robust cyber insurance in India is no longer optional — it's essential for insurance for corporations, startups, and all modern businesses.
#cyber insurance#third-party cyber insurance#cyber insurance in India#cyber security insurance#cyber insurance policy#cyber liability insurance#business insurance#commercial insurance#cyber and crime insurance#company insurance#insurance for corporations#data breach lawsuit#regulatory fines cyber#privacy liability coverage
2 notes
·
View notes
Text
Top Cybersecurity Solutions Providers in Delhi-NCR: Wish Geeks Techserve
Cybersecurity services in India have become an essential investment for businesses looking to safeguard their digital infrastructure from rising cyber threats. With an increasing number of data breaches, phishing attacks, and malware infiltrations, organizations cannot afford to overlook the importance of strong IT security frameworks. Companies in Delhi-NCR, in particular, need to prioritize security due to the region's rapid technological growth and evolving cyber risk landscape.
Finding the top cybersecurity solutions provider in India is crucial for ensuring business continuity, regulatory compliance, and data integrity. Among the top contenders offering robust security solutions is Wish Geeks Techserve, a trusted IT security services India provider known for its innovative and customized cybersecurity strategies.
The Growing Cybersecurity Challenges in India
As the digital economy expands, businesses face a multitude of security threats ranging from ransomware attacks to sophisticated hacking attempts. The emergence of remote working models and cloud computing has further increased the vulnerability of organizations, making network security services in India a necessity rather than an option. The cyber threat landscape includes:
Phishing and Social Engineering Attacks: Cybercriminals exploit human vulnerabilities through fraudulent emails and deceptive practices to gain unauthorized access to sensitive information.
Malware and Ransomware Infections: Malicious software infiltrates systems, encrypting or corrupting critical business data, often leading to significant financial losses.
Insider Threats and Human Errors: Employees, either maliciously or unintentionally, can cause security breaches through weak passwords, mishandling of data, or lack of security awareness.
DDoS (Distributed Denial-of-Service) Attacks: Hackers overwhelm business networks with excessive traffic, leading to downtime and operational disruptions.
Cloud Security Risks: With increasing cloud adoption, businesses must ensure secure cloud storage, access management and data encryption practices to prevent unauthorized intrusions.
Why Choose Wish Geeks Techserve as the Best Cybersecurity Company in India?
Wish Geeks Techserve stands out among cybersecurity solutions providers in India, offering state-of-the-art security services tailored to businesses of all sizes. Their comprehensive approach ensures complete protection from internal and external threats. Here’s what makes them the ideal IT security services India provider:
1. Advanced Cybersecurity Solutions for End-to-End Protection
Wish Geeks Techserve provides holistic security solutions that cover all aspects of IT security. Their expertise spans across:
Threat Intelligence & Risk Assessment: Proactively identify vulnerabilities and strengthen weak points before attacks occur.
Endpoint Protection & Malware Defense: Implementing security measures that shield endpoints like computers, mobile devices and IoT systems from cyber threats.
Firewall & Intrusion Prevention Systems (IPS): Ensuring that network boundaries remain impervious to unauthorized access attempts.
Incident Response & Forensics: Swift action in the event of a cyberattack, minimizing damage and preventing future breaches.
2. Comprehensive Network Security Services in India
As a leading cybersecurity solutions provider in India, Wish Geeks Techserve specializes in network security services in India, ensuring robust defense mechanisms against cyber threats. Their network security offerings include:
Secure VPN Implementations: Allowing safe and encrypted remote access for employees working from different locations.
DDoS Protection & Mitigation: Preventing large-scale cyberattacks that aim to disrupt operations.
Zero Trust Security Frameworks: Adopting a ‘never trust, always verify’ approach to user authentication and access control.
3. 24/7 Cybersecurity Monitoring & Incident Response
Cyber threats do not operate within business hours, which is why Wish Geeks Techserve provides round-the-clock monitoring and support. Their dedicated Security Operations Center (SOC) continuously tracks anomalies, preventing attacks before they escalate.
4. Regulatory Compliance & Data Privacy Solutions
With stringent data protection regulations like GDPR and India’s upcoming Personal Data Protection Bill, businesses must comply with legal security mandates. Wish Geeks Techserve helps companies meet these requirements by implementing industry-leading compliance strategies and ensuring secure handling of customer and business data.
5. Customized Cybersecurity Strategies for Businesses
Recognizing that no two businesses have the same security needs, Wish Geeks Techserve delivers customized cybersecurity services in India based on industry-specific challenges. Whether it's securing financial transactions, protecting healthcare records, or preventing e-commerce fraud, their team crafts personalized solutions to fit organizational requirements.
How Businesses Can Benefit from Strong Cybersecurity Measures
Adopting best-in-class IT security services India offers multiple benefits beyond just data protection. Businesses that invest in top-tier security measures experience:
Improved Customer Trust: Demonstrating commitment to data privacy enhances brand credibility.
Reduced Financial Losses: Preventing cyberattacks reduces the risk of hefty ransom payments, fines and revenue losses due to downtime.
Operational Efficiency: Secure IT environments enable seamless business operations without disruptions from malware or unauthorized access.
Competitive Advantage: Businesses that prioritize cybersecurity gain an edge over competitors who fail to implement robust security strategies.
Conclusion
Cybersecurity is no longer a choice but a necessity for businesses in Delhi-NCR and across India. Choosing the right cybersecurity solutions provider in India can make all the difference in ensuring business continuity and protection against cyber threats. Wish Geeks Techserve emerges as one of the best cybersecurity companies in India, offering cutting-edge IT security services in India that cater to businesses of all sizes. Their expertise in network security services in India ensures that organizations remain resilient against evolving cyber risks.
If you’re looking for a trusted partner to fortify your cybersecurity infrastructure, Wish Geeks Techserve is the go-to provider, ensuring that your business stays secure in the ever-changing digital landscape. Invest in strong security measures today and safeguard your business’s future!
#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
4 notes
·
View notes
Text
Best Cyber Crime Lawyer in Delhi
It is crucial to hire the Best Cyber Crime Lawyer in Delhi given the rapidly changing cyber threat scenario. Discover in-depth information about their success in addressing cybercrime matters, legal acumen, and areas of experience. Count on the finest to safeguard your online rights!
The challenges of cybercrime are growing along with the digital domain. Locating the best legal assistance in Delhi is essential. This post takes you into the realm of cyber law specialists, walking you through the subtleties and knowledge of Delhi's Top Cyber Crime Attorney.

Best Cyber Crime Lawyer in Delhi: Safeguarding Your Digital World
In an era where our lives are intertwined with the digital realm, the rise of cybercrime poses a significant threat. As technology evolves, so do the tactics of cybercriminals. Delhi, being a technology hub, requires the expertise of the Best Cyber Crime Lawyer in Delhi to navigate the complex legal landscape associated with cyber offenses.
Understanding Cyber Crimes
The Evolution of Cyber Threats
Cyber threats have evolved from simple hacking attempts to sophisticated cyber-attacks, including ransomware, phishing, and identity theft. Understanding these threats is the first step toward effective legal defense.
Impact on Individuals and Businesses
Cybercrimes not only jeopardize personal information but also pose a severe risk to businesses. The Best Cyber Crime Lawyer in Delhi must comprehend the far-reaching consequences of these offenses.
Necessity of Cyber Crime Legal Experts
The digital landscape demands specialized legal knowledge. A cyber crime lawyer is equipped to interpret complex technical aspects and ensure a robust legal defense.
Qualities of the Best Cyber Crime Lawyer
Technological Acumen
The legal expert must possess a deep understanding of evolving technologies to effectively counter cyber threats. Continuous learning and adaptation are key in this dynamic field.
Analytical Skills
Analyzing digital evidence requires sharp analytical skills. The Best Cyber Crime Lawyer in Delhi excels in dissecting complex data to build a compelling case.
Our Expertise are in: -
· Fraud and financial crimes
· Cyber terrorism
· Cyberextortion
· Cyberwarfare
· Computer as a target
· Computer as a tool
· Obscene or offensive content
· Harassment
· Drug trafficking
Our Case Processing in India: -
· Supreme Court of India
· Delhi High Court
· All District Courts
Experience in Cyber Forensics
Cyber forensics is the backbone of cybercrime investigations. A seasoned lawyer employs forensic techniques to trace digital footprints and gather admissible evidence.
Legal Framework in Delhi
Cyber Laws in India
A strong foundation in Indian cyber laws is essential. The lawyer should be well-versed in acts like the Information Technology Act, providing the legal framework for cyber-related offenses.
Relevance in the Digital Age
As our lives become more digital, cyber laws gain prominence. The Best Cyber Crime Lawyer in Delhi understands the relevance of these laws in the contemporary context.
Noteworthy Cyber Crime Cases in Delhi
Highlighting past cases showcases the lawyer's experience and success in navigating the legal complexities associated with cybercrimes.
How to Choose the Right Lawyer
Assessing Specializations
Not all lawyers are equipped to handle cybercrime cases. Evaluating the lawyer's specialization ensures that they possess the specific skills required.
Checking Track Record
A proven track record in successfully handling cybercrime cases instills confidence. Past successes are indicative of the lawyer's competence.
Initial Consultation Tips
An initial consultation provides insight into the lawyer's approach. Look for effective communication, transparency, and a client-centric attitude.
Role of Cyber Crime Lawyers in Investigations
Collaboration with Law Enforcement
Cyber crime lawyers often collaborate with law enforcement agencies. This partnership is vital for gathering information and building a strong case.
Gathering Digital Evidence
Adept at digital forensics, these lawyers can extract and analyze digital evidence crucial for establishing guilt or innocence.
Courtroom Strategies
Presenting a case in court requires strategic acumen. The Best Cyber Crime Lawyer in Delhi employs effective courtroom strategies to ensure a favorable outcome.
Success Stories: Best Cyber Crime Lawyer in Delhi
Notable Cases Handled
Highlighting specific cases provides a glimpse into the lawyer's achievements and capabilities in handling diverse cybercrime scenarios.
Positive Case Outcomes
Successful resolutions and positive case outcomes demonstrate the lawyer's prowess in securing justice for their clients.
Client Testimonials
First-hand accounts from satisfied clients serve as a testament to the lawyer's commitment and effectiveness in handling cybercrime cases.
Challenges Faced by Cyber Crime Lawyers
Rapidly Changing Cyber Landscape
Adapting to the swiftly evolving cyber landscape poses a constant challenge. The best lawyers stay ahead by staying informed and updated.
Legal Loopholes and Ambiguities
Cyber laws may have loopholes or ambiguities that cyber crime lawyers must navigate skillfully. This requires a nuanced understanding of legal intricacies.
Balancing Privacy Concerns
The lawyer must strike a delicate balance between upholding privacy rights and pursuing justice, especially in cases involving sensitive information.
Best Cyber Crime Lawyer in Delhi
Overview of Services Offered
The Best Cyber Crime Lawyer in Delhi provides a comprehensive array of legal services, from case consultations to representation in court.
Client-Centric Approach
Prioritizing client needs ensures a supportive and collaborative legal process, fostering trust and confidence.
Commitment to Legal Excellence
A commitment to legal excellence is non-negotiable. The best lawyers consistently deliver high-quality legal services.

Cyber Crime Prevention Tips
Strengthening Digital Security
Providing practical tips on enhancing digital security empowers individuals and businesses to proactively protect themselves.
Educating Employees and Individuals
Awareness is the first line of defense. The article emphasizes the importance of educating individuals and employees on cybersecurity best practices.
Proactive Measures
Encouraging proactive measures ensures that readers actively engage in securing their digital presence, preventing potential cyber threats.
Collaboration with IT Experts
Importance of Technical Consultation
Collaborating with IT experts enhances the lawyer's ability to comprehend intricate technical details, strengthening the overall legal strategy.
Building Strong Legal-Technical Partnerships
A synergistic partnership between legal and technical experts ensures a holistic approach to cybercrime defense.
Key Benefits for Clients
Highlighting the benefits of collaboration assures clients that they are receiving comprehensive and effective legal support.
Industry Recognition and Awards
Acknowledgments and Accolades
Recognition from the industry and awards signal the lawyer's standing as a reputable and accomplished professional in cyber law.
Contributions to Cyber Law Development
Active contributions to the development of cyber laws showcase the lawyer's commitment to shaping a robust legal framework.
Impact on Legal Community
Positive influence within the legal community underlines the lawyer's role in fostering growth and knowledge exchange.
Best Cyber Crime Lawyer in Delhi Perspective
Insights on Cyber Crime Trends
Sharing insights on emerging cyber crime trends demonstrates the lawyer's proactive approach to staying ahead of the curve.
Future Challenges and Preparedness
Discussing future challenges and preparedness indicates the lawyer's foresight and commitment to staying relevant in the face of evolving cyber threats.
Vision for a Secure Digital Future
A lawyer with a vision for a secure digital future inspires confidence in clients and the community at large.
FAQs: Best Cyber Crime Lawyer in Delhi
Legal Fees and Consultation Charges
Legal fees vary, usually based on the complexity of the case. Consultation charges may be nominal or part of the overall legal fees.
Average Duration of Cyber Crime Cases
The duration varies, depending on the complexity of the case. Some cases may be resolved swiftly, while others may take an extended period.
Confidentiality Measures
Maintaining client confidentiality is paramount. The best cyber crime lawyers implement robust measures to safeguard client information.
Cross-Border Legal Challenges
Handling cases with international implications may pose challenges, requiring the lawyer to navigate complex legal jurisdictions.
Handling Emerging Cyber Threats
Top lawyers stay informed about emerging threats, allowing them to adapt their legal strategies to counter evolving cybercriminal tactics.
Recent Legislative Changes Impacting Cyber Law
Cyber laws evolve, and lawyers must stay updated on recent legislative changes to provide effective legal counsel.
In conclusion, the Best Cyber Crime Lawyer in Delhi plays a pivotal role in safeguarding individuals and businesses from the growing threat of cybercrime. By understanding the nuances of cyber laws, possessing technical acumen, and embracing a client-centric approach, these legal experts stand as pillars of defense in the digital world.
Read More: www.bestcybercrimelawyer.in
#best cyber crime lawyer in Delhi#cyber crime lawyer in Delhi#best cyber crime lawyer in Noida#best cyber crime advocate in Delhi
3 notes
·
View notes
Text
Cybersecurity in Power Systems: Safeguarding Transmission and Distribution Infrastructure
Introduction:
In an era dominated by technology, the power industry is undergoing a transformation, with the integration of smart grids and digital solutions becoming increasingly prevalent. However, this digital evolution brings with it a new set of challenges, particularly in the realm of cybersecurity. Power systems, including transmission and distribution infrastructure, are critical components of our modern society, making them prime targets for cyber threats. In this blog post, we will delve into the importance of cybersecurity in power systems and explore measures to safeguard transmission and distribution infrastructure.

Understanding the Landscape:
Power systems, encompassing transmission and distribution, are the backbone of any nation's infrastructure. As these systems become more interconnected and reliant on digital technologies, the vulnerability to cyber threats escalates. Transmission and distribution manufacturers in India are at the forefront of adopting innovative solutions to enhance the efficiency of power systems. However, with this increased connectivity comes the imperative need to fortify these systems against cyber attacks.
The Role of Cybersecurity in Power Systems:
Protecting Critical Infrastructure:
Cybersecurity plays a pivotal role in protecting critical infrastructure, especially in the power sector. Transmission and distribution manufacturers in India are recognizing the significance of robust cybersecurity measures to safeguard their equipment and networks.
Securing Outdoor Support Insulators:
Outdoor support insulators are crucial components in power systems, providing structural support and insulation. Cyber threats targeting these insulators could compromise the integrity of the entire power grid. Implementing cybersecurity protocols ensures the resilience of these components against potential attacks.
High Voltage Primary Bushing Outdoor Manufacturers in India:
Manufacturers producing high voltage primary bushings outdoors are well-aware of the challenges posed by cyber threats. Implementing stringent cybersecurity measures is imperative to prevent unauthorized access and manipulation of these critical components.
Addressing Vulnerabilities in Fuse Cutouts:
Fuse cutouts are essential for protecting power distribution systems from overcurrents. However, these components are susceptible to cyber threats that could disrupt their functionality. Cybersecurity measures are crucial in identifying and addressing vulnerabilities in fuse cutouts.
Cyber Threats in Power Systems:
Malware and Ransomware Attacks:
Malicious software and ransomware attacks pose a significant threat to power systems. These attacks can disrupt operations, compromise sensitive data, and demand ransom payments. Implementing robust cybersecurity measures is essential to mitigate the risk of malware and ransomware infiltrations.
Phishing and Social Engineering:
Phishing attacks and social engineering tactics target human vulnerabilities within organizations. Employees in transmission and distribution manufacturers in India must be educated on recognizing and avoiding these cyber threats to prevent unauthorized access to critical systems.
Insider Threats:
Insider threats, whether intentional or unintentional, can pose a severe risk to power systems. Establishing comprehensive access controls, monitoring systems, and conducting regular employee training can help mitigate the potential impact of insider threats.
Safeguarding Strategies:
Network Segmentation:
Implementing network segmentation is crucial to isolate and contain cyber threats. This strategy ensures that even if one part of the network is compromised, the entire system remains secure.
Regular Security Audits:
Conducting regular security audits is essential for identifying vulnerabilities and weaknesses in power systems. Transmission and distribution manufacturers in India should prioritize periodic assessments to stay ahead of evolving cyber threats.
Employee Training Programs:
Employees play a crucial role in cybersecurity. Training programs should focus on raising awareness about potential threats, recognizing phishing attempts, and promoting a security-conscious culture within the organization.
Advanced Authentication Protocols:
Implementing advanced authentication protocols, such as multi-factor authentication, adds an extra layer of security to prevent unauthorized access to critical systems.
Conclusion:
As power systems evolve with technological advancements, the need for robust cybersecurity measures becomes paramount. Transmission and distribution manufacturers in India must prioritize safeguarding their infrastructure against cyber threats to ensure the continuous and reliable delivery of power. From outdoor support insulators to high voltage primary bushings outdoors and fuse cutouts, every component plays a critical role in the functioning of power systems and requires protection from potential cyber attacks.
In the face of evolving cyber threats, a proactive approach to cybersecurity is the key to resilience. By adopting advanced cybersecurity measures and staying abreast of the latest developments in the field, Radiant Enterprises and other stakeholders in the power industry can fortify their transmission and distribution infrastructure, contributing to a secure and sustainable energy future.
#Transmission and Distribution Manufacturers in India#Outdoor Support Insulator#High Voltage Primary Bushing Outdoor Manufacturers in India#Fuse Cutouts#epoxy insulator#epoxy bushing#electricity#fuse cutouts#smart grid sensor#railway technology companies#train operating companies#locomotive#tramways#metro systems#traffic infrastructure
6 notes
·
View notes
Text
Cloud Security Market Drivers Fueling Demand Across Industries and Regions
The cloud security market is witnessing substantial growth due to the rising dependency on cloud infrastructure by organizations across various sectors. As enterprises continue to migrate their operations to the cloud, securing critical assets, applications, and data has become a top priority. This demand is catalyzed by a blend of regulatory pressure, increasing cyber threats, remote work adoption, and technological advancements in AI-driven security solutions. In this article, we explore the key drivers propelling the growth of the cloud security market and their implications for future industry developments.

Rising Cybersecurity Threats and Data Breaches
One of the primary drivers of the cloud security market is the escalating frequency and sophistication of cyberattacks. From ransomware and phishing to distributed denial-of-service (DDoS) attacks, businesses are facing complex threats that target cloud environments. As cloud infrastructures expand, so does the attack surface, making robust cloud security solutions critical for prevention and real-time response. High-profile breaches in sectors like healthcare, finance, and government have underscored the need for enhanced data protection strategies, significantly boosting market demand.
Rapid Cloud Adoption Across Enterprises
The global shift towards digital transformation has led to a rapid increase in the adoption of public, private, and hybrid cloud models. Businesses are leveraging cloud services for scalability, cost-efficiency, and agility. However, this shift has brought forth concerns about data visibility, compliance, and secure access control. As a result, cloud-native security tools that offer real-time monitoring, threat intelligence, and automated remediation are in high demand, driving growth across both developed and emerging economies.
Stringent Data Privacy Regulations
Governments around the world are implementing stringent regulations to ensure data privacy and security. Laws such as the General Data Protection Regulation (GDPR) in Europe, the California Consumer Privacy Act (CCPA), and India's Digital Personal Data Protection Act (DPDPA) mandate that organizations adhere to strict guidelines regarding the storage and processing of personal data. To comply, enterprises are turning to cloud security providers for solutions that ensure adherence to regulatory frameworks, audit readiness, and secure data handling practices.
Growing Demand for Secure Remote Work Environments
The COVID-19 pandemic accelerated the adoption of remote and hybrid work models, which continue to remain prevalent. This shift created an urgent need for secure access to enterprise resources from geographically dispersed locations. Cloud security solutions that offer secure access service edge (SASE), endpoint protection, identity and access management (IAM), and zero trust architectures have become integral to protecting remote employees and organizational data. The long-term nature of this work trend continues to drive the need for robust cloud security tools.
Advancements in Artificial Intelligence and Automation
The integration of artificial intelligence (AI) and machine learning (ML) into cloud security platforms has significantly enhanced their effectiveness. AI-enabled solutions can detect anomalous behavior, automate threat detection, and initiate rapid response protocols with minimal human intervention. These advancements help organizations proactively address vulnerabilities and ensure continuous monitoring. The demand for intelligent security tools capable of scaling with dynamic cloud environments is a major contributor to the market’s upward trajectory.
Increasing Adoption of Multi-Cloud Strategies
Many enterprises are embracing multi-cloud environments to avoid vendor lock-in and optimize performance. However, managing security across multiple cloud platforms presents complex challenges in terms of visibility, compliance, and policy enforcement. This has led to the adoption of unified cloud security platforms that provide centralized management, consistent policy enforcement, and cross-cloud analytics. The growing complexity of multi-cloud ecosystems continues to be a key driver of demand for comprehensive security solutions.
Expansion of Cloud-Native Applications
The increasing deployment of cloud-native applications, developed using containerization and microservices, is fueling the need for dynamic and scalable cloud security approaches. Traditional security models are often insufficient in protecting these decentralized architectures. As a result, solutions such as container security, API security, and DevSecOps integration are gaining traction. Businesses are investing in platforms that can secure the entire application lifecycle, from development to deployment.
Conclusion
The cloud security market is being shaped by a confluence of factors ranging from increasing cyber threats and data protection regulations to evolving work environments and technological innovations. As businesses continue their digital transformation journeys, the demand for intelligent, scalable, and compliant cloud security solutions is expected to surge. With organizations seeking to secure their cloud infrastructures while remaining agile, the market is poised for sustained growth and innovation in the coming years.
0 notes
Text
Enhancing Cybersecurity in BFSI with IT Staff Augmentation

The cybersecurity landscape constantly revolutionises, posing new and complex challenges for organisations. Building a solid cybersecurity framework is necessary with growing cyberattacks and regulatory requirements. Cybersecurity is still an evolving field in India and has immense potential. However, many organisations struggle with staffing shortages and face skill gaps within their internal cybersecurity teams, where IT staff augmentation comes into play.
Understanding IT Staff Augmentation for Cybersecurity
IT Staff augmentation involves partnering with external resources to temporarily onboard cybersecurity-specialised professionals to the existing team. These experts bring niche skills that allow organizations to bridge skill gaps, address urgent security threats, and tackle complex projects without worrying about the overhead of full-time employees.
IT Staff Augmentation vs. Outsourcing for BFSI Cybersecurity
While IT staff augmentation and outsourcing provide external cybersecurity expertise, they differ significantly.

For BFSI firms requiring hands-on cybersecurity management, IT staff augmentation offers greater flexibility, integration, and control than full outsourcing.
The Growing Cybersecurity Challenges in BFSI
Why BFSI is a Prime Target for Cyber Threats
Monetary gain is one of the biggest reasons the BFSI sector is often on target for cyber threats. Financial data is the heart of any finance sector, and hence, any attack on the system can incapacitate any business and cause customers to lose faith in the company.
More reasons why BFSI is the prime target for cyber threats are:
Sensitive and Personal Information
Business Disruption
Digital Transformation
FiTech, Cryptocurrencies, and Ransomware
Key Security Risks in Financial Services
Phishing
Phishing is a method of tricking users into divulging login credentials to gain access to internal networks. The most common form of phishing is email phishing, in which users receive an email posing as a legitimate communication.
Ransomware
Ransomware and ransomware as a service are other cyber risks to financial services. During a ransomware attack, cybercriminals lock the victims out of their computers, encrypting them with malware. The damage can only be reversed if a ransom is paid.
DDoS Attacks
In 2020, the financial sector experienced the highest number of distributed denial-of-service (DDoS) Attacks. During a DDoS attack, a victim's server is overwhelmed with fake connection requests, forcing it to turn offline. DDoS attacks are a popular cyber threat against financial services as their attack surface is diverse, comprising banking IT infrastructure, customer accounts, and payment portals.
Role of IT Staff Augmentation in Strengthening BFSI Cybersecurity
Hiring Specialized Cybersecurity Experts Through Staff Augmentation
BFSI firms often struggle to find full-time cybersecurity professionals with expertise in cloud security, threat detection, and risk management. IT Staff Augmentation provides access to:
Ethical hackers and penetration testers to identify vulnerabilities
Incident response specialists to mitigate security breaches
Regulatory compliance experts to align security protocols with PCI DSS, HIPAA, and GDPR requirements.
Benefits of Staff Augmentation in Cybersecurity Risk Management
Cost Effective Solutions
IT Staff augmentation offers a budget-friendly alternative to traditional hiring. Instead of bearing the high costs associated with full-time employment, businesses can temporarily tap into a pool of skilled professionals.
Flexible Scalability
IT Staff augmentation can quickly scale the organization's workforce up or down based on the project's needs.
Access to Specialised Talent
Access to specialized skills is essential for staying ahead of the competition. IT Staff Augmentation provides organizations with front-row seats to expert professionals in niche technologies, ensuring that projects are executed with precision and innovation.
Accelerated Project Timelines
IT Staff Augmentation allows businesses to swiftly onboard skilled professionals without the delay of the traditional hiring process. This rapid access to talent ensures that projects move forward without interruption, allowing businesses to meet tight deadlines.
How IT Staff Augmentation Companies Ensure Compliance with Security Standards
Reputable IT staff augmentation providers ensure BFSI firms maintain the following:
HIPAA and PCI DSS-compliant security frameworks to protect customer data.
Zero trust security models that limit unauthorized access.
Ongoing cybersecurity training and assessments for financial IT teams.
Key Considerations When Choosing an IT Staff Augmentation Service for Cybersecurity
Evaluating IT Staff Augmentation Companies for BFSI
Selecting the right IT staff augmentation provider is critical to BFSI's cybersecurity success. Key factors to consider:
Industry Experience – The IT staff augmentation service provider should have a proven track record in BFSI cybersecurity staffing.
Compliance Expertise – Ensure the firm offers professionals trained in PCI DSS, GDPR, and other financial regulations.
24/7 Support – Cyber threats are constant; IT Staff Augmentation service providers should provide around-the-clock monitoring and response capabilities.
Practices for Managing Augmented Cybersecurity Teams
Once BFSI firms onboard augmented security professionals, best practices include:
Clearly define security roles and responsibilities. Avoid overlap and ensure seamless collaboration with in-house teams.
Providing secure access controls – Restrict data access based on role-based permissions.
Regular performance reviews – Ensure augmented professionals meet cybersecurity objectives
By following these management strategies, BFSI firms can maximize the impact of their augmented security teams.
Future of Cybersecurity in BFSI with IT Staff Augmentation
The BFSI sector is evolving rapidly, and IT staff augmentation will play a key role in future cybersecurity strategies by enabling:
AI-Driven Threat Detection – Augmented teams will work with AI-powered security systems to automate real-time threat analysis.
Blockchain-Based Security Solutions – Experts will help BFSI firms implement blockchain for secure financial transactions.
5G and Edge Computing Security – Augmented professionals will protect financial data on next-gen networks
As cyber threats become more sophisticated, BFSI firms must adopt a proactive approach and leverage specialised cybersecurity IT staff augmentation services.

Conclusion: Is IT Staff Augmentation the Best Approach for BFSI Cybersecurity?
Given the increasing complexity of cybersecurity threats in BFSI, IT staff augmentation provides a practical, flexible, and cost-efficient solution. It allows financial institutions to:
Quickly hire specialized cybersecurity experts.
Ensure compliance with financial security regulations.
Scale security teams based on real-time threat levels.
For BFSI firms facing rapid digital transformation and evolving cyber risks, IT staff augmentation is a highly effective approach to reinforcing cybersecurity defenses while maintaining operational agility.
With over two decades of expertise in IT solutions, XLNC Technologies is a trusted partner for BFSI firms looking to fortify their cybersecurity posture while remaining agile and competitive in an increasingly digital world. By choosing XLNC, financial institutions can focus on innovation and growth, knowing their security infrastructure is in expert hands.
FAQs
How does IT staff augmentation help in improving BFSI cybersecurity?
IT staff augmentation enables BFSI firms to hire specialized cybersecurity professionals quickly to address evolving threats. It helps strengthen threat detection, incident response, and compliance management while allowing firms to scale security teams based on real-time risks without long-term hiring commitments.
What are the key differences between IT staff augmentation and outsourcing in cybersecurity?
IT Staff augmentation integrates external cybersecurity experts into in-house teams, ensuring greater control and flexibility. Conversely, outsourcing delegates complete security management to a third party, limiting internal oversight. Augmentation allows customized security strategies, while outsourcing follows a predefined service contract.
How can financial institutions ensure compliance while using IT staff augmentation services?
BFSI firms must partner with augmentation providers experienced in financial regulations like PCI DSS, GDPR, and SOC 2. They should implement zero-trust security models, role-based access controls, and ongoing compliance audits to protect sensitive financial data while maintaining regulatory adherence
What are the top cybersecurity challenges in BFSI that IT staff augmentation can solve?
IT Staff augmentation helps BFSI firms address ransomware attacks, insider threats, phishing scams, and data breaches. It provides access to cybersecurity specialists for threat monitoring, risk management, and cloud security, ensuring financial institutions stay resilient against evolving cyber risks.
How do IT staff augmentation companies help mitigate cyber risks in BFSI?
IT Staff augmentation companies offer pre-vetted cybersecurity experts who enhance real-time threat detection, incident response, and security compliance. They help BFSI firms deploy AI-driven cybersecurity solutions, implement blockchain-based security, and ensure continuous monitoring, reducing financial fraud and data breaches.
#CybersecurityInBFSI#ITStaffAugmentation#FinancialSecurity#BFSISecuritySolutions#CyberRiskManagement#ComplianceReady#TechDrivenSecurity#AugmentedCyberDefense#Ask ChatGPT
0 notes
Text
Cloud Security in India: Why Skilled Graduates Are in High Demand

In the age of digital transformation, cloud computing has become the backbone of modern businesses across India. From banks and hospitals to tech startups and e-commerce giants, nearly every sector is shifting to the cloud. However, with this rapid adoption comes an equally growing concern—cloud security.
As organizations migrate sensitive data and operations online, the demand for professionals who can secure this digital infrastructure is skyrocketing. This is where graduates of programs like the BCA in Cloud Security, are stepping into the spotlight.
☁️ The Cloud Revolution in India
India is one of the fastest-growing cloud markets in the world. According to IDC, the Indian public cloud services market is expected to reach $13 billion by 2026. Government initiatives like Digital India, the rise of remote work, and cloud-native startups have fueled this surge.
With such widespread adoption, the cloud is no longer just a storage solution—it's where businesses run their critical operations, including customer data, financial transactions, and proprietary applications.
🔐 The Rising Importance of Cloud Security
With great digital growth comes great digital risk.
From ransomware attacks on hospitals to data leaks at fintech companies, the number of cyber threats targeting cloud systems is increasing. According to a report by IBM, the average cost of a data breach in India was ₹17.9 crore in 2023, and cloud misconfigurations were among the top causes.
This makes cloud security a national priority, not just an IT issue. Businesses are now investing heavily in hiring skilled cloud security professionals to prevent data breaches, ensure regulatory compliance, and protect digital assets.
Why BCA in Cloud Security Is the Right Choice
The BCA in Cloud Security program at Edubex is designed to bridge the gap between industry needs and talent availability. It prepares students to:
Understand cloud computing models (IaaS, PaaS, SaaS)
Learn cybersecurity principles tailored for cloud platforms
Master tools like AWS, Azure, Google Cloud, and security frameworks
Perform real-time risk assessments and security audits
Get exposure to compliance standards (ISO, GDPR, etc.)
This specialization doesn’t just teach you theory—it trains you in real-world scenarios, ensuring you're job-ready from day one.
Career Opportunities in Cloud Security
Graduates with a strong foundation in cloud security are in high demand across sectors like:
IT & Software Companies
Banking and Financial Services
Healthcare & Pharma
Telecom & Media
E-Commerce & Startups
Popular job roles include:
Cloud Security Analyst
Cybersecurity Associate
DevSecOps Engineer
Information Security Consultant
Cloud Compliance Specialist
With experience and certifications, you can even grow into roles like Security Architect or Chief Information Security Officer (CISO).
A Skill for the Future
Cloud security isn’t just a trend—it’s a long-term career path. As more organizations go digital and cyber threats become more complex, the need for skilled professionals will continue to grow.
According to NASSCOM, India will face a shortage of over 1 million cybersecurity professionals by 2025. Specializing in cloud security gives you an edge in this competitive, high-growth market.
Final Thoughts: Secure Your Future Today
The demand for cloud security professionals in India has never been higher. As cyber threats evolve, businesses need smart, trained, and ethical experts who can protect their digital assets.
If you’re passionate about technology and want to play a key role in shaping the secure digital future of India, the BCA in Cloud Security program is your ideal launchpad.
0 notes
Text
How an Ethical Hacking Course Can Transform Your Career in Cybersecurity
In today’s digital era, where cyberattacks are becoming more frequent and sophisticated, the role of ethical hackers has never been more critical. Ethical hackers are the unsung heroes of the digital world, using their skills to protect systems, networks, and data from malicious attacks. If you’re looking for a career that’s both challenging and rewarding, enrolling in an ethical hacking course could be the game-changer you need. Let’s explore how this course can transform your career and why it’s worth every rupee of the ethical hacking course fees.
What is Ethical Hacking?
Ethical hacking is the practice of identifying vulnerabilities in computer systems, networks, and applications—just like a malicious hacker would, but with one crucial difference: ethical hackers use their skills to protect and defend. They work with organizations to uncover weaknesses before cybercriminals can exploit them, ensuring that sensitive data and systems remain secure.
An ethical hacking course teaches you the tools, techniques, and methodologies used by ethical hackers. From penetration testing to malware analysis, this course equips you with the skills needed to excel in the field of cybersecurity.
Why is Ethical Hacking a Lucrative Career Choice?
India is one of the most targeted countries for cyberattacks, with incidents increasing by over 300% in recent years. From ransomware attacks on hospitals to data breaches at major corporations, the stakes have never been higher. This has created a massive demand for ethical hackers who can identify vulnerabilities and prevent attacks.
Source - https://www.hackerschool.in/how-an-ethical-hacking-course-can-transform-your-career-in-cybersecurity/
0 notes
Text
India Police Arrest Kolkata Native in Crypto Scam Case
Unlock the Secrets of Ethical Hacking! Ready to dive into the world of offensive security? This course gives you the Black Hat hacker’s perspective, teaching you attack techniques to defend against malicious activity. Learn to hack Android and Windows systems, create undetectable malware and ransomware, and even master spoofing techniques. Start your first hack in just one hour! Enroll now and…
0 notes
Text
eShield IT Services — Your Trusted Partner in the Fight Against Cyber Threats
In a world that’s more digitally connected than ever, the risks are rising just as fast as the innovations. Data breaches, ransomware attacks, phishing scams — cyber threats have become more frequent, more sophisticated, and more devastating. Amid this landscape, one name stands out for its commitment to proactive protection: eShield IT Services.
Understanding the Need for Cybersecurity
Whether you're an individual freelancer or a multi-national enterprise, your digital presence is always exposed to potential risks. It's no longer just about having antivirus software or a firewall. Modern cybercriminals operate with advanced tools and target organizations through everything from unpatched applications to human error.
India, like many countries, has seen a rapid acceleration in digital adoption across sectors. With that progress comes responsibility — to secure sensitive data, comply with global regulations, and defend against evolving cyberattacks. This is where eShield IT Services brings tremendous value.
What is eShield IT Services?
eShield IT Services is a dedicated cyber security firm based in India, serving clients both locally and internationally. The company offers a wide range of cybersecurity services, designed to detect vulnerabilities, protect critical data, and help organizations meet global compliance standards.
But eShield doesn’t just offer services — it builds trust. The team is made up of experienced cybersecurity professionals who believe in ethical practices, constant learning, and client-centric solutions. Whether you’re building your first application or running an enterprise network, eShield’s mission is to help you stay secure, without the stress.
Core Services Offered by eShield IT Services
Each offering is designed to help organizations take control of their cyber hygiene and resilience:
Penetration Testing
Imagine someone trying to break into your digital infrastructure — not to steal, but to tell you how they did it. That’s exactly what eShield’s penetration testing services deliver. By simulating real-world cyberattacks, they identify system flaws before criminals can exploit them.
Web Application Security Auditing
Most businesses today rely heavily on web-based applications. eShield performs thorough audits to uncover vulnerabilities such as injection flaws, broken authentication, and cross-site scripting — ensuring that your applications remain secure and functional under pressure.
Compliance Consulting (PCI DSS, ISO 27001)
Compliance is more than just ticking boxes. With increasing regulations on data privacy and payment processing, businesses need guidance to meet standards like PCI DSS and ISO 27001. eShield offers hands-on support in designing compliant frameworks, building secure systems, and passing audits with confidence.
Managed Security Services
For companies that don’t have an in-house cyber security team, eShield acts as your outsourced security partner. From constant monitoring to threat detection and incident response, they provide a full stack of services to protect your systems around the clock.
SOC Implementation
A Security Operations Center (SOC) can be the backbone of your cybersecurity defense. eShield helps companies set up SOCs that are tailored to their size, industry, and budget — offering both on-premises and cloud-based solutions.
Why Choose eShield IT Services?
There are countless cybersecurity firms in the market. So what sets eShield apart?
Client-Focused: Every business is different, and eShield understands that. Their solutions are not one-size-fits-all but tailored specifically to your needs.
Ethical and Transparent: They believe in doing the right thing — always. Clear communication, honest risk assessments, and realistic strategies are part of their culture.
Experienced Team: With certified experts who’ve worked across multiple industries, you get advice and action based on proven strategies.
Affordable and Scalable: eShield offers pricing models that suit startups and enterprise clients alike, with scalability built into every service.
The Human Side of Cybersecurity
Often, cyber security is viewed as a purely technical field. But at its core, it's about people. It’s about protecting individuals’ identities, securing businesses’ reputations, and preserving trust in the digital systems we all rely on.
eShield IT Services blends technical know-how with a human touch. Their team works closely with clients to educate, empower, and create a culture of security awareness — because technology alone isn’t enough. Human error is the leading cause of breaches, and reducing that risk is a team effort.
Industries They Serve
From healthcare to finance, retail to government, eShield has experience across a wide range of sectors. Whether you’re managing e-commerce transactions or handling sensitive patient records, their security strategies align with your specific industry challenges.
Looking Ahead: The Future of Cybersecurity
The threat landscape is changing daily. As artificial intelligence, quantum computing, and IoT become more integrated into daily business operations, the attack surface expands. eShield IT Services continues to invest in research and upskilling to ensure that their clients remain ahead of emerging threats.
By embracing automation, predictive analytics, and threat intelligence, they’re not just reacting to attacks — they’re preventing them before they occur.
Final Thoughts
Cyber security is no longer an IT department issue. It's a business imperative, a brand protection strategy, and in many cases, a legal requirement.
eShield IT Services is not just another vendor. They are a trusted partner in your journey to secure digital transformation. By offering real solutions to real risks, they’re helping businesses across the globe thrive in an increasingly complex digital world.
If you’re ready to strengthen your cyber defense with a team that understands both technology and trust, visit www.eshielditservices.com and take the first step toward a safer future.
0 notes
Text
Top Cybersecurity Services in Noida For Penetration Testing and Managed Security Services: Wish Geeks Techserve
In an age when cyber threats are more advanced than ever, protecting your business is not optional—it’s essential. Data breaches, ransomware attacks, and phishing scams can disrupt your operations, damage your reputation, and result in significant financial losses.
That’s why forward-thinking businesses trust Wish Geeks Techserve, the Best Cybersecurity Solutions Provider in Noida, to deliver advanced protection and proactive security management tailored to their needs.
As one of the most trusted names in Cybersecurity Services India, we help companies of all sizes secure their networks, applications, and critical data with end-to-end solutions.
Why Cybersecurity Matters More Than Ever
Today, even a single security lapse can expose your entire business to cybercriminals. Small and medium-sized businesses are especially vulnerable because they often lack the in-house resources to keep pace with evolving threats.
✅ Benefits of Professional Cybersecurity Services
Protect sensitive data and customer information
Prevent costly downtime and operational disruptions
Maintain regulatory compliance and avoid penalties
Build customer trust and confidence
Enable secure remote work environments
With Cybersecurity Services in Noida by Wish Geeks Techserve, you gain peace of mind knowing your business is always protected.
Why Choose Wish Geeks Techserve?
As the Best Cybersecurity Company in India, we deliver comprehensive security services backed by deep expertise and a proactive approach. Whether you need a one-time security assessment or fully managed cybersecurity, we’re here to help.
✅ Certified Security Experts
Our team includes certified cybersecurity professionals skilled in penetration testing, threat analysis, compliance, and incident response.
✅ 24/7 Monitoring and Support
Cyber threats don’t sleep—and neither do we. Our experts monitor your environment around the clock to detect and neutralize threats.
✅ Customized Solutions
Every business has unique security challenges. We tailor our services to your industry, compliance needs, and risk profile.
✅ Advanced Tools and Technologies
From intrusion detection to endpoint protection and SIEM (Security Information and Event Management), we use best-in-class tools to keep you safe.
Our Core Cybersecurity Services
Wish Geeks Techserve offers a full suite of Cybersecurity Services Noida and across India, including:
🛡️ Managed Security Services
Proactive, ongoing protection for your networks, endpoints, and cloud infrastructure, fully managed by our security team.
🧪 Penetration Testing
Identify and fix vulnerabilities before attackers exploit them. Our ethical hackers simulate real-world attacks to test your defenses.
🔍 Vulnerability Assessments
Regular scans and assessments to uncover weaknesses across your systems and applications.
�� Network Security Services in India
Comprehensive network protection, including firewalls, intrusion prevention systems, and secure access controls.
🌐 Cloud Security Solutions
Secure your cloud workloads and SaaS applications with policies, monitoring, and encryption.
📊 Compliance and Risk Management
Stay compliant with regulations like GDPR, ISO 27001, and PCI-DSS through risk assessments and documentation.
⚠️ Incident Response and Recovery
In the event of a breach, our experts provide rapid response and help restore operations sWho We Serve
As a leading Cybersecurity Solutions Provider in India, we partner with businesses of every size and industry:
Finance and Banking
Healthcare and Pharmaceuticals
E-commerce and Retail
Manufacturing and Logistics
Education and Technology
Real Estate and Professional Services
Whether you operate locally in Noida or nationally, we deliver the expertise and tools to protect your digital assets.
Our Proven Cybersecurity Process
We follow a structured process to keep your business secure at every layer:
Assessment and Discovery: We analyze your environment, identify gaps, and understand your compliance requirements.
Strategy and Planning: Our experts develop a tailored cybersecurity roadmap aligned with your business goals.
Implementation: We deploy the necessary security solutions, configurations, and policies.
Monitoring and Management: Continuous monitoring, threat detection, and maintenance keep your systems protected.
Training and Support: We educate your team on best practices to strengthen your first line of defense.
Why We’re the Best Cybersecurity Solutions Provider in Noida
Decades of combined cybersecurity experience
Industry-leading technologies and frameworks
Proven track record protecting businesses across India
Flexible solutions for any size organization
24/7 support from certified security experts
When you choose Wish Geeks Techserve, you gain a trusted partner dedicated to safeguarding your business.
Ready to Secure Your Business?
Don’t wait for a breach to realize the importance of proactive cybersecurity. Protect your operations, data, and reputation with Wish Geeks Techserve, the Top Cybersecurity Experts in Noida.
📩 Book your free cybersecurity consultation today and discover how we can keep your business safe.
#Cybersecurity Services Noida#cybersecurity solutions in Noida#Best Cybersecurity Solutions Provider in Noida#Cybersecurity Services in Noida#Cybersecurity Services India#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Cybersecurity Solutions Provider in Noida#best Cybersecurity Solutions Provider in Noida#Network Security Services in India
0 notes
Text
10 Essential Navy Current Affairs for 2025
Naval power has long been a central pillar in the architecture of global defense and strategic influence. As we sail into 2025, the maritime landscape is undergoing significant transformations — driven by new technologies, shifting geopolitical alliances, and the need for greater environmental responsibility. This year, navies across the globe are not just preparing for warfare; they’re preparing for the future.

Here are the 10 Essential Navy Current Affairs for 2025 that highlight how modern navies are evolving and adapting:
1. Rise of AI-Powered Naval Systems
Artificial Intelligence has made a commanding entrance in the naval sphere. In 2025, AI is enhancing submarine detection, real-time threat analysis, autonomous navigation, and predictive maintenance of fleet equipment. The U.S., India, and China are all actively investing in AI-driven warships and unmanned surface vehicles (USVs), aiming to reduce response times and increase operational efficiency.
2. Indo-Pacific Strategic Shifts
The Indo-Pacific continues to be a hotspot of naval activity. With increasing assertiveness from China in the South China Sea and stronger U.S.-India naval cooperation under frameworks like QUAD, 2025 sees a heightened maritime focus on freedom of navigation operations (FONOPs) and intelligence sharing to ensure balance in the region.
3. Green Navy: A Push for Sustainability
Environmentally responsible naval operations are gaining momentum. Leading navies, including those of the UK and Japan, are committing to carbon-neutral missions. Innovations like biofuel-powered ships, electric propulsion systems, and sustainable naval bases reflect the commitment to cleaner seas and reduced emissions.
4. Expansion of the Indian Navy
India has embarked on its most ambitious naval expansion in decades. 2025 marks the commissioning of its next-generation aircraft carrier INS Vikrant-II, along with advancements in nuclear-powered submarines and stealth frigates. With its "Blue Water Navy" doctrine, India aims to project power across the Indian Ocean Region (IOR) and beyond.
5. NATO’s Enhanced Maritime Security Protocols
With renewed tensions in Eastern Europe and the Arctic, NATO has refined its maritime security strategies. 2025 sees greater joint exercises, enhanced cybersecurity frameworks for fleet networks, and a more robust presence in the Mediterranean and Baltic seas. Operation Sea Guardian, in particular, is gaining traction in deterring piracy and enforcing embargoes.
6. Drone Swarm Technology Takes Center Stage
Unmanned drone swarms capable of offensive and surveillance missions have moved from concept to combat-readiness. Navies like those of Israel and the U.S. are deploying drone clusters that can confuse enemy radar, perform reconnaissance, and conduct strike missions — a low-risk, high-impact tactic transforming naval warfare.
7. Arctic Naval Operations on the Rise
Climate change has opened new Arctic routes, and navies are racing to establish presence and control. Russia has increased its Arctic fleet deployments while the U.S. Coast Guard and Canadian Navy are collaborating on icebreaker ships and surveillance systems. 2025 emphasizes the growing importance of polar naval strategy.
8. Enhanced Maritime Cybersecurity Measures
With warships now essentially floating data centers, cyber warfare has emerged as a critical front. 2025 has seen a sharp increase in both offensive cyber operations and defensive protocols within naval commands. Naval cyber units are working to safeguard critical control systems from espionage, ransomware, and nation-state attacks.
9. Women Leading in Naval Command Roles
In a groundbreaking shift, more women are taking command positions in navies worldwide. From captaining warships to heading naval research divisions, 2025 is a landmark year for inclusivity. Navies in the UK, Australia, and India have seen significant policy shifts in gender representation and empowerment.
10. Maritime Humanitarian Missions at the Forefront
Disaster relief and humanitarian aid are now key components of naval missions. Whether it’s typhoon response in Southeast Asia or earthquake support in the Caribbean, 2025 underscores the navy’s role in non-combat operations. Amphibious ships equipped for medical and logistics support are increasingly essential in these missions.
Final Thoughts
As global navies recalibrate to face new technological, environmental, and strategic challenges, 2025 represents a crucial inflection point. From AI integration to gender inclusivity and Arctic ambitions, these 10 essential navy current affairs are not just about enhancing military power — they’re about building navies that are smarter, greener, and globally responsive.
For maritime enthusiasts, defense experts, and policymakers, understanding these dynamics is vital. The sea has always been a space of opportunity and contest — and now, more than ever, it’s a domain of innovation and transformation.
0 notes
Text
The Global Cybersecurity Analyst Salary Landscape: A Country-by-Country Breakdown
The digital age, while ushering in unprecedented connectivity and innovation, has also brought with it a surge in sophisticated cyber threats. From nation-state sponsored attacks to ransomware gangs, the landscape of cyber warfare is ever-evolving. This escalating threat environment has, in turn, fueled an immense and growing demand for skilled cybersecurity professionals, particularly cybersecurity analysts. As organizations worldwide strive to protect their critical assets and sensitive data, the value placed on these guardians of the digital realm has soared, leading to a significant rise in global cyber security salary figures. Understanding these compensation trends across different geographies is crucial for aspiring professionals and employers alike.
Country-Specific Averages and Salary Ranges
The compensation for cybersecurity analysts can vary considerably based on location, experience, and the specific demands of the local market. Below is a breakdown of average salaries and typical ranges in key global economies:
United States:
The United States consistently ranks among the highest-paying countries for cybersecurity professionals. An average Information Security Analyst salary in the US typically hovers around $111,200 annually.
Salary Range: Entry-level positions (1-3 years experience) can expect to earn around $92,500, while experienced senior-level analysts (8+ years experience) can command salaries of $127,500 or more. Some reports indicate a median salary of $105,000, with the top 10% earning up to $169,196.
United Kingdom:
In the UK, the cybersecurity sector is robust, with competitive salaries. The median annual salary for a Cybersecurity Analyst in the UK is £55,000.
Salary Range: For those just starting out, salaries might be around £37,950, while experienced professionals could see figures up to £69,450 or more, with the 75th percentile reaching £63,563.
Germany:
Germany, a technological powerhouse in Europe, offers strong compensation for cybersecurity expertise. The average cybersecurity analyst gross salary in Germany is approximately €99,264 per year.
Salary Range: An entry-level analyst (1-3 years of experience) might start at around €69,880, whereas a senior-level analyst (8+ years of experience) can expect to earn up to €123,099 annually. PayScale reports an average of €55,000 for a Cyber Security Analyst, with a range of €40,000 to €78,000.
France:
France also presents a healthy market for cybersecurity professionals. The average gross salary for a cybersecurity analyst in France is around €79,650 per year.
Salary Range: Entry-level analysts can expect approximately €56,040, while senior analysts can reach up to €98,719. Levels.fyi suggests a median total compensation of €64,955.
India:
India's rapidly expanding digital infrastructure has created a significant demand for cybersecurity talent. An experienced cybersecurity professional in India can expect to earn between ₹8 lakh to ₹20 lakh per annum or more.
Salary Range: For freshers, salaries typically range from ₹3.5 lakh to ₹6 lakh annually. Experienced professionals with 2-4 years might earn ₹6 lakh to ₹12 lakh, while senior professionals with 8+ years can command ₹20 lakh to ₹40 lakh per annum, especially in roles like Security Architects or CISOs. The average for a Cyber Security Analyst is often cited between ₹6 lakh and ₹8 lakh per year, with senior roles reaching ₹8 lakh to ₹12 lakh.
United Arab Emirates (UAE):
The UAE, with its ambitious digital transformation initiatives, offers attractive packages. The average monthly salary for a Cyber Security Analyst in the UAE is around AED 8,441, which translates to approximately AED 101,292 per year.
Salary Range: Salaries can vary from AED 2,500 to AED 20,500 per month, depending on experience. For instance, those with 6-9 years of experience can earn around AED 12,509 per month.
China:
China's massive digital economy fuels a strong demand for cybersecurity specialists. The average pay for a Cyber Security Analyst in China is approximately CNY 382,685 per year.
Salary Range: The average salary range typically falls between CNY 264,818 and CNY 466,493.
Singapore:
Singapore, a global financial and technology hub, offers highly competitive salaries for cybersecurity professionals. The average total compensation for a Cybersecurity Analyst in Singapore is around SGD 102,152 per year.
Salary Range: Salary ranges often fall between SGD 71,618 and SGD 123,862. More experienced roles in Cyber Security Operations can command S$120,000 to S$200,000 annually, with some senior roles exceeding S$350,000.
Japan:
Japan, a leader in technological innovation, also shows healthy compensation for cybersecurity roles. The average pay for a Cyber Security Analyst in Japan is approximately JPY 9,410,080 per year.
Salary Range: The salary range typically falls between JPY 6,511,775 and JPY 11,470,888. In Tokyo, an Analyst Cyber Security can see an average of JPY 13,009,500, with a range of JPY 9,002,574 to JPY 15,858,581.
Australia:
Australia's cybersecurity market is robust and well-compensated. The median yearly total compensation for a Cybersecurity Analyst in Australia is around A$141,000 to A$149,000.
Salary Range: Compensation at major companies can range from A$91,300 to A$174,000. For instance, an Analyst I at CrowdStrike might earn A$135,000 (total compensation), while top earners at Google in Australia can reach A$492,825.
Cost of Living/Purchasing Power Parity
While raw salary figures offer a glimpse into earning potential, it is important to consider the cost of living and purchasing power parity (PPP) to gain a more nuanced understanding of how far a cybersecurity salary truly stretches in each country. A higher salary in a country with a significantly higher cost of living might not translate into a better quality of life compared to a lower salary in a region with a more affordable lifestyle.
For example, countries like Switzerland and Bermuda have some of the highest cost of living indexes globally, meaning a high nominal salary might be offset by expensive housing, groceries, and services. The United States and Australia also rank relatively high on the cost of living index. In contrast, countries like India and China, while having lower average cybersecurity salaries in absolute terms, also have a considerably lower cost of living, which can lead to a comparable or even better standard of living for a local professional. The UAE, while having a moderately high cost of living, offers tax-free income, which significantly boosts net purchasing power. European nations like Germany, France, and the UK fall somewhere in between, offering a balance of strong salaries and a generally good quality of life, though major cities in these countries can be expensive. Japan and Singapore, while offering strong salaries, are also known for their high cost of living. Therefore, when evaluating a cyber security salary opportunity, factoring in the local economic context is crucial for a realistic assessment of financial well-being.
Key Takeaways
The global demand for cybersecurity professionals is undeniably strong, reflecting the critical need for digital protection across all sectors. This demand is translating into competitive and often lucrative cyber security salary packages worldwide. Regions with particularly high earning potential for cybersecurity analysts include the United States, Australia, and Singapore, which consistently offer top-tier compensation. European nations like Germany, France, and the UK also provide excellent opportunities, with strong average salaries. While countries like India and China may have lower absolute salary figures, their comparatively lower cost of living can offer a high quality of life and significant career growth opportunities within rapidly expanding digital economies. Ultimately, the most attractive location for a cybersecurity analyst will depend on a combination of salary expectations, career aspirations, and desired lifestyle.
0 notes
Text
Managed Services Market to Reach $576.7 Billion by 2032
Meticulous Research®—a leading global market research company, published a research report titled ‘Managed Services Market—Global Opportunity Analysis and Industry Forecasts (2025-2032).’ According to this latest publication from Meticulous Research®, the managed services market is expected to reach $576.7 billion by 2032, at a CAGR of 9.4% from 2025 to 2032.
The growing focus of organizations on cost optimization, the rising inclination of enterprises toward outsourced IT operations, the lack of skilled IT personnel, the rise in cyber threats & ransomware attacks on businesses, and businesses’ increasing investments in digital transformation are factors driving the growth of the managed services market. However, market growth is restrained by the lack of trust among enterprises in giving control of their systems to third-party organizations.
In addition, the rising utilization of advanced technologies and the rising adoption of cloud-based solutions are expected to generate considerable opportunities for market stakeholders. However, the market faces substantial challenges, including the low adoption of managed services by SMEs. Additionally, the proliferation of 5G technologies is a key trend in this market.
Key Players:
The managed services market is moderately competitive due to the presence of many large and small-sized global, regional, and local players. The key players operating in the managed services market include Accenture (Ireland), Tata Consultancy Services Limited (India), HCL Technologies (India), Cognizant (U.S.), IBM Corporation (U.S.), Fujitsu Limited (Japan), Kyndryl Holdings, Inc. (U.S.), Verizon Communications Inc. (U.S.), Google LLC (U.S.), Hughes Network Systems, LLC (U.S.), AT&T Inc. (U.S.), Microsoft Corporation (U.S), Cloudflare, Inc. (U.S.), Wipro Limited (India), HP Inc. (U.S.), SecureWorks Corp. (U.S.), Hitachi Vantara LLC (U.S.), Cisco Systems, Inc. (U.S.), DXC Technology Company (U.S.), and Infosys Limited (India).
The managed services market is segmented based on type, deployment mode, organization size, and end-use industry. The report also evaluates industry competitors and analyzes the managed services market at the regional and country levels.
Among the managed service types studied in this report, in 2025, the managed security services segment is anticipated to dominate the managed services market, with a share of over 39.0%. Building and maintaining an in-house security team is expensive; however, managed security services provide cost-effective access to skilled professionals, which is driving the adoption of managed security services. Managed security services provide round-the-clock monitoring and management of tools such as firewalls, intrusion detection systems, and endpoint detection & response. These benefits contribute to the segment’s large share in the managed services market.
Among the deployment modes studied in this report, in 2025, the cloud-based segment is anticipated to dominate the managed services market, with a share of over 62%. The substantial benefits of cloud-based services, including on-demand access to experienced and qualified resources, high levels of business agility and resilience, automatic upgrades, and cybersecurity, contribute to the segment’s dominant position in the managed services market.
Among the organization sizes studied in this report, in 2025, the large enterprises segment is anticipated to dominate the managed services market, with a share of over 67%. Large organizations’ rising need to manage complex IT infrastructures, their constantly changing IT needs, and increased emphasis on risk mitigation and compliance contribute to the segment’s dominant position in the managed services market.
Among the end-use industries studied in this report, in 2025, the BFSI segment is anticipated to dominate the managed services market, with a share of over 34%. The sector's increased focus on uninterpreted and enhanced customer service and the high adoption of AI/ML technology for process automation and fraud detection in the BFSI sector contribute to the segment’s dominant position in the managed services market.
Among the geographies studied in this report, in 2025, North America is anticipated to dominate the managed services market, with a share of over 40%. The presence of recognized Managed Service Providers (MSPs) in the region, the growing use of managed security services for privileged access management, the increased need to protect network infrastructure, and increased spending on IT capabilities are factors contributing to the region’s dominant position in the managed services market.
Download Sample Report Here @ https://www.meticulousresearch.com/download-sample-report/cp_id=6025
Key Questions Answered in the Report:
What is the revenue generated from the sale of managed services globally?
At what rate is the global demand for managed services projected to grow for the next five to seven years?
What is the historical market size and growth rate for the managed services market?
What are the major factors impacting the growth of this market at the global and regional levels?
What are the major opportunities for existing players and new entrants in this market?
Which type, deployment mode, organization size, and end-use industry segments are expected to create major traction for the players in this market?
What are the key geographic trends in this market? Which regions/countries are expected to offer significant growth opportunities for the organizations operating in the managed services market?
Who are the major players in the managed services market? What are their specific service offerings in this market?
What are the recent key developments in the managed services market? What are the impacts of these strategic developments?
Contact Us: Meticulous Research® Email- [email protected] Contact Sales- +1-646-781-8004 Connect with us on LinkedIn- https://www.linkedin.com/company/meticulous-research
#Managed Services Market#Managed Security Services#Managed IT Infrastructure Services#Managed Information Services#Managed Data Center Services#Managed Network
0 notes
Text
Why Every Startup Needs a Cybersecurity Strategy

In the digital-first era, start-ups are characterized by being agile, being innovative, and being willing to be technology-huggers. Cybersecurity is an aspect of app production, which often becomes overlooked in the chaos to develop applications as fast as possible, expand, and beat others to the market.
The startups are a light operation in comparison with the large companies which own their own IT departments and have million dollar budget. This is unfortunate in that they are easy prey to the cybercriminals. startups are regarded as a low hanging fruit by hackers.
What does it mean then that a cybersecurity strategy is non-negotiable to startups? Well, then, we will come to the reasons.
1. Early Startups are Easily Attackable Mostly with Cyberattacks
Most of the startup founders feel that the cybercriminals are only after big companies. That is a myth. Recent statistics show that more than 43 percent of cyber attacks are against small business entities and emerging businesses. These threats range between phishing emails and ransomware, data breaches, and identity theft, which are irreversible and can have a potential of causing severe damage.
Startups deal with confidential information about their customers, money, business strategies, and intellectual technology. When such data lands in the hands of the wrong persons, it may lead to the company losing reputation all the way to closure of business.
2. A single Attack can Disable a Startup
In contrast to bigger organizations, start-ups usually do not have enough resources to recover after a cyber event. One violation may involve fines, loss of customers, and eventual bankruptcy. This is not a bump in the road to a startup that already has thin margins.
One can only picture the failure to develop years of work on a product, just to see it ruined by a security bug that could have been avoided. And even worse, how will it affect your brand reputation when your customer information is leaked? That is why an active approach to cybersecurity is not only a technical necessity, but a company survival capability.
3. The Working Remotely Increases the Risk
The transition to remote and hybrid working has further proved to escalate the risk of cybersecurity, particularly in a post-pandemic environment. The use of personal gadgets, unsecured Wi-Fi connection and old software by employees builds an unnecessary point of entry to be exploited by any hacker.
Effective cybersecurity strategy means that remote work policies are safe, devices are secure, and people understand how to identify such risks as phishing or social engineering attacks.
4. It Is Required by Regulations
Although you may have a small startup, you are not exempted by the data protection laws. Be it GDPR, HIPAA or the DPDP Bill in India, governments are getting more stringent in terms of controls on data privacy. Large fines and a loss of company integrity could result from noncompliance.
A company with a rich cybersecurity policy will eliminate the risk of startups of being non-compliant and make them stay out of the trouble of being penalized, giving them a competitive edge with regard to both customers and investors.
5. Investors are no longer playing around with cybersecurity.
It is no longer just a technical problem in current business environment, it is also a set business metric. The standard of due diligence is changing and investors can ask startups about their data protection practices. Even before you can demonstrate that you are sincere in terms of security, you may end up losing out in terms of funding.
An effective cyber policy demonstrates that you are not only an entrepreneur who is technologically apt but also a responsible owner of the business. It brings plausibility and can even become a competitive edge.
6. Awareness and Skills are the First Step to Cybersecurity
It is not necessary to be a technological genius to apply the fundamentals of cybersecurity, but one should be aware. The upskilling in cybersecurity essentials is a wise investment needed by the founding teams or individuals.
Cybersecurity course in Kochi can be a big change in this case. Kochi has also turned out to be an evolving tech park in South India and many established institutions today provide and offer hands-on industry-related training. As a founder, developer, or head of a business, a cybersecurity course in Kochi arms you with the practical skills that will make your startup immune to digital attacks.
0 notes