#Router Password Recovery
Explore tagged Tumblr posts
Text
How Secure Is Your Clinic Data? Best Practices for EMR/EHR Security
Why EMR/EHR Security Matters in a Clinic Management System
1. Protecting Patient Privacy
All sensitive patient information is kept in a clinic's EMR/EHR system. This includes medical history, treatment history, and billing information. Any breach can lead to identity theft, insurance fraud, or private information being disclosed.
2. Compliance with Healthcare Standards
Regulatory bodies impose strict data protection legislation to keep a patient's confidentiality intact. These should be monitored according to:
HIPAA (Health Insurance Portability Act).
GDPR (General Data Protection Regulation).
PIPEDA (Personal Information Protection and Electronic Documents Act).
3. Prevention of Cyber Threats and Data Breaches
Cyber criminals steal healthcare data for its high value. The common cyber threats facing organizations include:
Ransomware Attacks-Encrypted patient data until ransom is given
Phishing Scams-Un8990havior of a staff member by means of a staff fake email
An insider threat- Employees misuse access to private records.
4. System Reliability and Continuity of Operations
A breach or data loss can result in halting the operations of a clinic, which could delay possible treatment or affect care to patients. A very secure clinic management should have backup support and failover systems to mitigate any possible downtime.
EMR/EHR Security Best Practices for Clinic Management Systems
Implement Strong Access Controls
Limiting access to EMR/EHR data means granting access to viewing or modifying patient records for a lesser number of people, namely the authorized personnel only.
Best Practices in Access Control
✅ Role-Based Access Control (RBAC) – Roles (e.g. doctors, nurses, admin staff) have specific permissions assigned.:
✅Multi-Factor Authentication (MFA) –Requires the users to verify their identity through two or more authentication factors.
-Unique User IDs: Prevents password sharing by providing individual login credentials.
Encrypt Patient Data
Encryption is a method that safeguards any sensitive information and converts that information into a code, which cannot be read without the proper decryption key.
Encrypted Strategies for EMR/EHR Systems:
🔐 End to End Encryption (E2EE) - Data is kept encrypted even in the course of transmission and storage.
🔐 AES-256 Encryption - The international gold standard for encrypting health care data.
🔐Encrypted Backups - Protect the data against attacks.
Regular Security Audits and Risk Assessments
Security audits can detect vulnerabilities in time before a cybercriminal exploits them.
Audit and Risk Management Steps:
📋Conduct periodic security audits - Penetration testing to know where weak points exist.
📋System Monitoring- Trace unusual login activities or unauthorized access attempts.
📋Risk assessment plans- Assess threats and change security measures accordingly.
Secure Network and Firewall Protection
A strong network security makes it possible that hackers cannot penetrate into the clinic database.
Best Practical Network Security:
Use firewalls and intrusion detection systems (IDS) to block malicious traffic
Establish VPN (Virtual Private Network) for the security of remote access
Update routers and network devices on a regular basis so that vulnerabilities do not appear.
Staff Training in Cybersecurity Awareness
A human mistake remains one of the most significant threats to the security of medical EMR/EHR. Clinic management systems, will only be as secure as their end users.
Cyber Security Training for Healthcare Workers:
Phishing Awareness: Recognize suspicious emails and links.
Strong Password Policies: Creating complex passwords and using password managers.
Incident Response Protocols: Education to staff about the course of action taken in case of security breach.
Implement Data Backup and Disaster Recovery Plans
Cyber disasters, as well as hardware failures, often lead to unpleasant clinic operational disruptions. Such disruptions have severe business consequences, which are important reasons why you take your time to prepare disaster recovery plans.
Core Elements of the Back-Up Strategy:
💾 Automated Daily Backups – Securely store data copies off-site or in the cloud
💾 Redundant Storage Systems – Store the data at several backup locations
💾 Regular Data Recovery Testing – Make sure the backup data can be restored
Conclusion
Protecting his EMR/EHR system does not only mean protecting the patient, but also building trust, legislation, and continuity of operation of the clinic. Implementation of access controls, encryption, network security, and staff training may drastically reduce these threats. To a clinic that wants a secured as well as reliable clinic management system, Clinthora is among the options available and shows good specifications in security features, including encryption of data, role-based access, cloud storage, and compliance support.
FAQ
What are the commonest forms of cyber attack against EMR/EHR systems?
Among the common attacks are phishing, ransomware, the insider threat, and data breaches through simple passwords and insecure networks.
Is it completely safe for clinics to use it under a cloud-based EMR-EHR program software?
Yes, cloud EMR/EHRs, with end-to-end encryption, multi factor authentication, and compliance to certain standards (HIPAA, ISO27001), provide very secure applications to clinics.
When should a clinic have a security audit done?
Clinics should have their systems audited and monitored regularly to comply with the requirement at least once every quarter.
What is the basis of EMR-EHR Security training?
Training enhances awareness of human error-unfriendly cyber threats, password security, and incident response to breaches avoidance.
How does Clinthora enhance data security in Clinics?
Clinthora provides secure patient data storage with encrypted backup and role-based access control against cyber threats in real time.
0 notes
Text
MSN Butterfly Support: Everything You Need to Know
MSN which is a short form for Microsoft Network is an integral part of Microsoft's online offerings since the beginning of 1995. Through the years, MSN has evolved, with a wide range of offerings such as information, email, entertainment, news as well as other. A few of the well-known icons of MSN's services online is " MSN Butterfly Support" The iconic butterfly symbolizes the unified access, connectivity as well as the reliability MSN is aiming to give its customers. In this post we'll look at MSN Butterfly Support, its important role, its common issues solutions, troubleshooting methods, and ways to contact MSN Support for help.
What is MSN Butterfly?
The MSN Butterfly first came into existence as part of the MSN branding in order to signify its Internet services. As time passed, it came to be synonymous with MSN Messenger, Hotmail, and other Microsoft internet-based services. The butterfly symbolised rapidity, convenience of communication and the ease of communication within the world of technology.
Although MSN Messenger was discontinued in 2013, the butterfly has remained the most iconic image in Microsoft's history in the digital realm. Even today, people search on the internet for "MSN Butterfly Support" when they need assistance with various Microsoft Services.
Importance of MSN Butterfly Support
MSN Butterfly support is vital for those who depend on Microsoft's services for communications information, news, private or corporate email. Microsoft offers various levels of support based on the service being used, that includes:
MSN Email Support (formerly Hotmail, now Outlook)
MSN News and Entertainment Support
MSN Browser and Home Page Support
Technical Assistance for MSN Premium Subscribers
When users experience problems in any of these solutions, MSN Butterfly Support can aid them to resolve their issues immediately.
Common Issues Resolved by MSN Butterfly Support
MSN services are typically trustworthy, however some users might have occasional issues. The most frequent problems solved through the MSN Butterfly Service are:
1. Login Issues
Forgotten passwords
Account closed due to unusual account activity
Two-factor authentication problems
2. Email Problems
Not able to receive or send emails
Problems with Spam filtering
Lost or missing emails
Help with account recovery
3. MSN Homepage & Browser Problems
MSN homepages not loading correctly
Probleme have been reported with MSN for the primary homepage
Problems with compatibility of the browser
4. Subscription and Billing Issues
MSN Subscription renewals for Premium issues
Billing errors
Canceling MSN Premium services
5. Security and Privacy Concerns
Phishing scams in email
An account that has been accessed without authorization
Security settings are updated
How to Troubleshoot MSN Issues?
Prior to contacting the MSN Butterfly Customer Support Users can test the following basic troubleshooting techniques:
Step 1: Check Internet Connection
Check that your internet connection functioning correctly. If you find that your MSN services do not load Try restarting your router or modem.
Step 2: Reset Password
If you're unable to access your MSN account or email you can reset your password on the official Microsoft account reset page.
Step 3: Clear Cache and Cookies
To resolve browser-related issues clearing your cache or cookies could resolve problems with loading.
Step 4: Check Microsoft Service Status
Microsoft offers a status page that allows users to verify the status of their service to determine if MSN or any other Microsoft services are not functioning properly.
Step 5: Update Your Browser
Make sure you're using the most recent Version that is compatible with Google Chrome, Microsoft Edge as well as Mozilla Firefox, as outdated browsers can cause problems.
Step 6: Disable Browser Extensions
A few browser extensions could affect MSN services. Disable them, then reload the site.
How to Contact MSN Butterfly Support?
If troubleshooting doesn't fix the issue If the issue persists, customers can call MSN Butterfly Support through the below options:
1. Microsoft Support Website
Microsoft offers a support site that is official and that provides users with documents, FAQs as well as contact options for MSN related questions.
2. Live Chat Support
Customers can reach Microsoft agents via live chat, which can provide faster assistance.
3. Phone Support
Microsoft has toll-free customer support numbers across different areas for immediate support.
4. MSN Help Forums
Members can ask questions on MSN or Microsoft community forums. MSN as well as Microsoft community forums, where experts as well as other users offer solutions.
Conclusion
MSN Butterfly Support remains an important resource for those who depend upon MSN services. If you require assistance in navigating issues with your MSN mail, home page or subscriptions, Microsoft provides multiple support ways to help users with. If you follow the troubleshooting procedures and then contacting the correct assistance team, you will be able to get the most out of MSN issues quickly.
If you encounter any issues don't delay in contacting MSN Butterfly Support to ensure you have a smooth web-based experience.
0 notes
Text
Instagram is one of the most popular social media platforms, but like any app, it can experience issues. Whether your Instagram is crashing, not loading, or showing errors, these problems can be frustrating. In this guide, we’ll explore common reasons Instagram might not be working and provide simple steps to fix them. Common Reasons Instagram Might Not Be Working Internet Connection Issues A weak or unstable Wi-Fi or mobile data connection can prevent Instagram from loading properly. Server Outages Instagram’s servers occasionally experience downtime, causing widespread disruptions. Outdated App Version Running an outdated version of Instagram can lead to compatibility issues or bugs. Device or Software Problems Your smartphone’s settings, operating system, or cache can interfere with Instagram’s functionality. Account or Login Issues Problems with your account, such as temporary bans or incorrect login details, may prevent access. Step 1: Check Your Internet Connection A stable internet connection is crucial for Instagram to work correctly. Steps to Fix: Switch between Wi-Fi and mobile data to see if one works better. Restart your router if you’re using Wi-Fi. Test your connection by opening a website or another app to ensure the issue isn’t specific to Instagram. Step 2: Verify Instagram’s Server Status Sometimes, Instagram’s servers may be down, affecting users worldwide. Steps to Check: Visit a website like DownDetector to see if others are reporting Instagram outages. Check Instagram’s official Twitter account for updates on server issues. What to Do: If Instagram’s servers are down, you’ll need to wait until the issue is resolved. Step 3: Update or Reinstall the Instagram App An outdated app version can cause Instagram to stop working properly. Steps to Update: Go to the App Store (iPhone) or Google Play Store (Android). Search for Instagram and check if an update is available. Tap Update if prompted. Steps to Reinstall: Uninstall the Instagram app from your device. Reinstall it from the App Store or Google Play Store. Log back into your account. Step 4: Clear Cache and Data (Android Users) Clearing Instagram’s cache can fix loading errors or app crashes. Steps to Clear Cache: Go to your phone’s Settings > Apps > Instagram. Tap Storage > Clear Cache. If the issue persists, tap Clear Data (this will log you out of the app). Note for iPhone Users: iOS doesn’t have a cache-clearing option. You’ll need to reinstall the app. Step 5: Restart Your Device Restarting your smartphone can resolve temporary glitches. Steps to Restart: Power off your device completely. Wait a few seconds, then turn it back on. Open Instagram and check if it’s working. Step 6: Check for Account or Login Issues If Instagram shows errors related to your account, you may need to address account-specific problems. Common Account Issues: Incorrect Login Details: Double-check your username and password. Temporary Bans: If you’ve violated Instagram’s guidelines, your account might be restricted. Hacked Account: Secure your account by resetting your password. What to Do: Visit the Instagram Help Center for account recovery options. Contact Instagram support if you believe your account has been unfairly restricted. Step 7: Check Device Settings Your phone’s settings can sometimes interfere with Instagram’s functionality. Steps to Fix: Ensure your phone’s operating system is up to date. Disable Low Power Mode or Battery Saver to ensure background activity isn’t restricted. Adjust app permissions: Go to Settings > Apps > Instagram > Permissions. Enable necessary permissions like Camera, Microphone, and Storage. Step 8: Contact Instagram Support If none of the above solutions work, you can reach out to Instagram for assistance.
Steps to Contact Support: Open the Instagram app. Go to Settings > Help > Report a Problem. Describe the issue and submit your report. Conclusion Instagram not working can be caused by anything from internet issues to server outages. By following these troubleshooting steps, you can quickly identify and fix the problem, ensuring you’re back to scrolling, posting, and connecting in no time. If the issue persists after trying all the solutions, it might be time to contact Instagram’s support team or consider switching devices to see if the problem is device-specific.
0 notes
Text
Goa Games Login Problems? Here’s How to Solve Them

Navigating through the world of online gaming should be an exciting and seamless experience, but sometimes, issues with logging into platforms like Goa Games can hinder your progress. Fortunately, most login problems can be easily solved with a few simple steps. If you've encountered difficulties with Goa Games login, don't worry; this guide will help you resolve them and get you back into the game in no time.
One of the most common issues players face when trying to log in to Goa Games is entering incorrect login details. It’s easy to forget your username or password, especially if you haven’t logged in for a while. The first step is to double-check the accuracy of your credentials. Ensure that your username and password are entered correctly, paying attention to any capitalization or special characters. If you’re unsure about your login details, Goa Games provides a simple password recovery option. By clicking on the “Forgot Password” link, you can reset your password and regain access to your account.
Another potential issue that may affect the Goa Games login process is a weak or unstable internet connection. Online gaming platforms require a stable internet connection for optimal performance. If you’re experiencing difficulties logging in, check your network connection to ensure it’s strong and reliable. You can try restarting your router or switching to a different network to see if the problem persists. Additionally, clearing your browser’s cache and cookies can often resolve any glitches that may prevent you from logging in smoothly.
Sometimes, issues with Goa Games login may arise from browser compatibility. Different web browsers may have varying levels of support for online platforms. If you’re unable to log in using your preferred browser, try switching to another one. Google Chrome, Mozilla Firefox, and Microsoft Edge are all widely compatible with Goa Games, so consider using one of these to see if it resolves the issue. Additionally, updating your browser to the latest version can help address any bugs or performance issues that may be affecting the login process.
If you’ve confirmed that your login credentials are correct, your internet connection is stable, and you’re using a compatible browser, but you’re still facing issues, it could be a problem with the Goa Games server. Like any online platform, Goa Games occasionally undergoes maintenance or experiences temporary outages. In such cases, the best thing to do is wait for the issue to be resolved. Goa Games often communicates such maintenance periods via their website or social media channels, so it’s worth checking for any official updates.
Lastly, if none of these solutions work, you may want to reach out to Goa Games’ customer support team for assistance. They have a dedicated team of professionals who are ready to help troubleshoot any login issues you may be facing. Whether you need help resetting your password or identifying potential technical issues, the support team is there to provide you with the necessary guidance.
In conclusion, while experiencing login problems on Goa Games can be frustrating, most issues can be easily resolved with a few troubleshooting steps. Whether it's double-checking your credentials, ensuring a stable internet connection, or switching browsers, these solutions should help you regain access to your account. Remember, if you’re still having trouble, the Goa Games customer support team is always available to assist. By following these steps, you can quickly get back to enjoying all the exciting games and features that Goa Games has to offer.
0 notes
Text
Computer Repair Group
WEBSITE: https://www.computerrepairgroup.com.au/
Address: 32 Edgewater Drive Bella Vista NSW 2153
PHONE: 04 3111 1111
Computer / Technology

Computer Repair Group is one of the leading Computer Repair Service Centres in Sydney, Australia. We are a gold certified Microsoft Partner and offer data recovery, software solutions, network setup, onsite installations, fault finding, upgrades and new or replacement parts to all of our clients. Our mobile vans also carry a huge range of new PC’s and peripherals such as switches, modems, routers, printers, laptops, video cards, memory, dvd-roms and much more. We have built a reputation of customer satisfaction through technical excellence and friendly staff.
Keywords: Data Recovery, Password Recovery, Desktop Fault Finding, Laptop Fault Finding, Desktop Repairs, Laptop Repairs, Ethernet Printer installations, Wireless Printer installations, Network Upgrades, Wireless Installations, Backup solutions, Mobile Services
EMAIL: [email protected]
1 note
·
View note
Text
Boost your Knowledge about basic of computer

To boost your knowledge about the basics of computers, consider focusing on the following areas:
**Hardware Fundamentals**:
- **Components**: Learn about key hardware components such as the CPU, RAM, hard drive, motherboard, and peripherals (keyboard, mouse, monitor).
- **Functionality**: Understand how each component works and how they interact to perform computing tasks.
**Software Basics**:
- **Operating Systems**: Gain knowledge of different operating systems (Windows, macOS, Linux) and their basic functions.
- **Applications**: Learn about common software applications like word processors, spreadsheets, and web browsers, and how to use them effectively.
**Computer Networks**:
- **Networking Basics**: Understand concepts like IP addresses, routers, switches, and the internet.
- **Connectivity**: Learn about wired and wireless connections, including Wi-Fi and Ethernet.
**File Management**:
- **Organizing Files**: Learn how to create, move, copy, and delete files and folders.
- **File Formats**: Understand different file formats and their uses (e.g., .txt, .jpg, .pdf).
**Basic Troubleshooting**:
- **Common Issues**: Familiarize yourself with common computer problems and their solutions.
- **Diagnostic Tools**: Learn to use basic diagnostic tools and utilities to identify and fix issues.
**Digital Literacy**:
- **Internet Usage**: Understand how to use search engines, email, and social media safely and effectively.
- **Online Security**: Learn about online safety practices, such as recognizing phishing scams and using strong passwords.
**Programming Fundamentals**:
- **Basic Coding**: Explore introductory programming concepts using languages like Python or JavaScript.
- **Logic and Algorithms**: Understand basic programming logic, algorithms, and problem-solving techniques.
**Data Storage and Management**:
- **Types of Storage**: Learn about different types of storage devices (HDDs, SSDs, cloud storage).
- **Backup and Recovery**: Understand the importance of data backup and basic recovery procedures.
**Computer Maintenance**:
- **Regular Updates**: Keep your system and software up to date to ensure security and performance.
- **Cleaning**: Regularly clean your computer’s physical components to prevent dust buildup.
**Learning Resources**:
- **Online Courses**: Platforms like Coursera, Udemy, or Khan Academy offer courses on computer basics.
- **Books and Tutorials**: Find beginner-friendly books and online tutorials to reinforce your learning.
By focusing on these areas, you can build a strong foundation in computer basics and enhance your overall understanding of technology.
TCCI Computer classes provide the best training in online computer courses through different learning methods/media located in Bopal Ahmedabad and ISCON Ambli Road in Ahmedabad.
For More Information:
Call us @ +91 98256 18292
Visit us @ http://tccicomputercoaching.com/
#best computer class in bopal-Ahmedabad#best computer class in Iscon Ambli Road-Ahmedabad#best MS-Office learning institute in bopal-Ahmedabad#best MS-Office institute in Iscon Ambli Road-Ahmedabad#Excel learning class in bopal-Ahmedabad
0 notes
Text
Cybersecurity for Local Business: 10 Necessary Steps to Begin

In today's digital landscape, local businesses face an ever-evolving hazard landscape when it pertains to cybersecurity. The dangers are genuine, from phishing attacks to data violations, and the repercussions can be ruining. Nonetheless, small businesses can secure themselves and protect their essential possessions with the appropriate technique.
In this comprehensive overview, we'll discover ten vital actions small companies can take to strengthen their cybersecurity defenses and stay ahead of the curve.
Conduct a Thorough Threat Assessment.
The initial step in building a robust cybersecurity method is recognizing your organization's possible dangers. Conduct a thorough threat analysis to identify vulnerabilities, examine the possibility and effect of potential attacks, and prioritize your safety initiatives as necessary.
When performing a threat evaluation, consider factors such as the data you handle, the gadgets and systems you utilize, the accessibility indicate your network, and the security measures currently in position. Engage with your cloud storage space company or IT service provider to assist you in recognizing and examining the dangers specific to your company.
Carry Out Strong Gain Access To Controls and Verification.
Carrying out durable accessibility controls and verification steps is one of the most effective ways to stop unauthorized access to your systems and data. This consists of:
Implementing solid password plans: Require employees to use complex, one-of-a-kind passwords that are transformed consistently.
Applying multi-factor authentication (MFA): Add a layer of protection by requiring customers to provide extra verification, such as a one-time code or biometric data, to access your systems.
Limiting gain access to benefits: Grant workers the minimal level of gain access to essentials to execute their job responsibilities and consistently evaluation and update gain access to authorizations.
By making it more difficult for assailants to acquire access to your systems, you can substantially decrease the risk of data violations and other cyber incidents.
Keep Software Applications and Equipment Up to Date.
Cyberpunks often exploit vulnerabilities in out-of-date software programs and systems to gain unauthorized access to your network. Make sure that all your company software, including running systems, applications, and firmware, is regularly updated with the most recent safety patches and pest fixes.
Establish automated updates whenever feasible, and make it a habit to manually check for and install updates regularly. Don't neglect to upgrade gadgets like routers, printers, and various other linked tools, as they can likewise be access points for attackers.
Implement Robust Backup and Calamity Recovery Techniques.
In an effective cyber strike, such as a ransomware incident, having a reputable backup and disaster recuperation plan in place can distinguish between a minor aggravation and a catastrophic company interruption.
Frequently back up your crucial information on-site and in the cloud, and check your backup and reconstruction processes to guarantee they work as anticipated. Consider executing a 3-2-1 backup approach, which involves maintaining three duplicates of your information, with two stored on different media and one saved offsite.
Educate and Train Your Staff members.
Workers are frequently the weakest link in a company's cybersecurity defenses. They can accidentally reveal your company to dangers via phishing scams, weak passwords, or other security gaps. Purchase regular cybersecurity training for your team to help them identify and respond to potential hazards.
Cover topics such as determining phishing attempts, producing strong passwords, safely dealing with delicate info, and reporting questionable activity. Encourage a safety and security recognition culture and equip your employees to be energetic in protecting your service.
Execute Endpoint Security and Antivirus Software Application.
Secure your tools with durable endpoint defense and anti-virus software applications, including desktops, laptop computers, and smartphones. These tools can discover, protect against, and eliminate malware, ransomware, and other cyber hazards that might attempt to infiltrate your systems.
Ensure that your antivirus software application is upgraded and configured to scan for and attend to any detected threats instantly. Consider releasing a central endpoint monitoring service to improve the implementation and management of safety controls across your network.
Establish a Comprehensive Case Action Strategy.
Despite your best efforts, your service might still be a victim of a cyber attack. On such an occasion, a well-defined incident response plan can help minimize the impact and swiftly recover your operations.
Your incident feedback strategy should outline the steps to be taken throughout a safety and security breach, consisting of procedures for containing the occurrence, checking out the origin, alerting pertinent celebrations, and restoring typical organization operations. Frequently evaluate and upgrade the plan to guarantee it remains effective despite advancing threats.
Carry Out Network Segmentation and Firewalls.
Split your network into smaller, separated segments to limit the spread of potential risks and include damage in case of a violation. This can be attained via firewall software, virtual local area networks (VLANs), and various other network segmentation technologies.
Firewall software is a gatekeeper, tracking and managing traffic circulation between your network and the Internet. Ensure your firewall programs are appropriately configured and current to block unauthorized access and detect suspicious activity.
Utilize Cloud-Based Safety And Security Solutions.
As even more small companies adopt cloud-based modern technologies for their procedures, the safety and security ramifications of these solutions must be considered. Leverage cloud-based safety remedies, such as anti-viruses, e-mail security, and internet filtering systems, to boost your total cybersecurity posture.
These cloud-based solutions often provide advanced risk detection, automatic updates, and systematized management, making it less complicated for small companies to keep durable safety and security facilities without needing considerable in-house IT resources.
Companion with a Cybersecurity Provider.
If your local business does not have the internal expertise or resources to handle its cybersecurity effectively, consider partnering with a reputable cybersecurity provider. These professionals can offer different services, including susceptibility assessments, infiltration screening, safety and security surveillance, and occurrence action, to assist you in reinforcing your defenses and staying ahead of arising risks.
Please search for a service provider that concentrates on serving small and medium-sized companies and ensures that it has a proven performance history of providing effective cybersecurity remedies. By applying these ten crucial actions, small businesses can substantially boost their cybersecurity stance and protect themselves from the growing risk of cyber attacks. Remember, cybersecurity is a continuous procedure, and it's vital to regularly assess and upgrade your approaches to equal the progressing threat landscape.
Cybersecurity Resources for Small Companies.
Still feeling overwhelmed by the intricacies of cybersecurity? You're not the only one. The good news is that numerous resources are readily available to assist businesses browsing this landscape and reinforce their defenses:
Global Cyber Partnership's (GCA) Cybersecurity Toolkit for Local Business: This comprehensive toolkit offers free resources, including overviews, lists, and tools, to assist local businesses in enhancing their cybersecurity methods.
National Institute of Requirements and Innovation (NIST) Cybersecurity Structure: NIST uses a commonly identified structure that gives guidelines and the finest techniques for improving an organization's cybersecurity.
Microsoft Cybersecurity Resource Center: Microsoft's resource facility provides a riches of pointers, write-ups, and technology remedies to help small companies boost their cybersecurity..
Federal Trade Commission (FTC) Cybersecurity for Small Business: The FTC supplies a detailed collection of magazines, videos, and write-ups covering various cybersecurity topics, particularly for small businesses.
Cybersecurity & Infrastructure Security Company (CISA) Resources: CISA provides a selection of overviews, lists, and training materials to aid small businesses boost their cybersecurity methods.
Small Business Administration (SBA) Cybersecurity Resources: The SBA provides numerous cybersecurity sources and support for small businesses.
Remember, cybersecurity is not a one-time initiative but a recurring procedure that calls for vigilance and continual improvement. By leveraging these sources and implementing the ten crucial steps outlined in this overview, local businesses can take aggressive measures to safeguard their operations and essential possessions from the ever-evolving danger of cyber strikes.
0 notes
Text
can't log into vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can't log into vpn
VPN login issues troubleshooting
Dealing with VPN login issues can be frustrating, especially when you're trying to secure your connection or access restricted content. However, understanding common troubleshooting steps can help resolve these issues efficiently.
Firstly, ensure you're using the correct credentials. Double-check your username and password for typos, and consider resetting your password if necessary. Sometimes, expired passwords or account restrictions can prevent successful logins.
Next, verify your internet connection. A stable and reliable internet connection is essential for VPN functionality. If you're experiencing connectivity issues, troubleshoot your network connection by restarting your router or switching to a different network.
Additionally, confirm that the VPN service is operational. Check the status of the VPN server you're trying to connect to, as server maintenance or downtime can affect login capabilities. You can usually find this information on the VPN provider's website or through customer support channels.
Another common culprit for VPN login problems is software conflicts or outdated applications. Ensure your VPN client is up to date and compatible with your operating system. If you're using third-party security software or firewalls, temporarily disable them to see if they're causing the login issues.
If you're still unable to log in, try using a different VPN server location. Sometimes, specific servers may be experiencing high traffic or technical difficulties, preventing successful connections.
Lastly, reach out to your VPN provider's customer support for assistance. They can offer personalized troubleshooting steps based on your specific issue and provide insights into any ongoing service disruptions.
By following these troubleshooting tips, you can overcome VPN login issues and enjoy a secure and seamless online experience.
Forgot VPN credentials
When you use a Virtual Private Network (VPN) to protect your online activity and ensure your privacy, it's crucial to remember your login credentials. However, it's not uncommon to forget your VPN username or password, especially if you use multiple VPN services or have complex login details.
If you find yourself in a situation where you have forgotten your VPN credentials, there are several steps you can take to regain access to your VPN service. The first step is to check if the VPN provider offers a password recovery option on their website. Many VPN services have a "Forgot Password" link that allows you to reset your password by verifying your identity through email or security questions.
If the password recovery option is not available or you are unable to access it for any reason, your next course of action should be to contact the VPN provider's customer support. Most VPN companies have dedicated support teams that can assist you in recovering your login credentials or provide you with alternative solutions to regain access to your VPN account.
In some cases, you may need to provide proof of purchase or other identifying information to verify your ownership of the account before the customer support team can help you reset your password or retrieve your username. It's essential to be patient and cooperative during this process to ensure a smooth and efficient resolution.
To prevent future incidents of forgetting your VPN credentials, consider using a password manager to securely store and manage your login details. Additionally, creating a backup of your VPN credentials in a secure location can help you avoid being locked out of your VPN account in case you forget your login information again.
VPN authentication problems
VPN authentication problems can be frustrating and can hinder your ability to connect securely to a private network. Authentication is a critical step in the VPN connection process as it verifies the identity of the user before granting access. There are several common VPN authentication issues that users may encounter:
Incorrect credentials: One of the most common reasons for authentication problems is entering incorrect login credentials. This could be due to a simple typing error or forgetting the correct username or password.
Expired credentials: If your VPN account credentials have expired or have been updated by the network administrator, you may experience authentication failures when trying to connect.
Connectivity issues: Poor internet connection or network disruptions can also lead to authentication problems when establishing a VPN connection. It is essential to have a stable internet connection to authenticate successfully.
VPN server issues: Sometimes, the VPN server itself may be experiencing technical difficulties, leading to authentication failures for all users trying to connect.
To troubleshoot VPN authentication problems, users can start by double-checking their login credentials, ensuring that their account is active, and verifying their internet connection stability. If issues persist, contacting the network administrator or VPN service provider for assistance may be necessary to resolve the problem effectively. By addressing these common authentication issues, users can enjoy a secure and uninterrupted VPN connection experience.
VPN connection errors
VPN Connection Errors: Common Issues and Solutions
VPN, or Virtual Private Network, is a crucial tool for ensuring online security and privacy. However, like any technology, VPN connections are not immune to errors. Understanding common VPN connection errors can help you troubleshoot and resolve issues quickly.
One of the most common VPN connection errors is the "VPN connection failed" message. This error often occurs due to incorrect login credentials, server connectivity issues, or outdated VPN software. To fix this error, double-check your username and password, ensure your internet connection is stable, and update your VPN client to the latest version.
Another frequent issue is the "VPN server not responding" error. This error can be caused by server overload, firewall settings blocking the VPN connection, or network configuration issues. To resolve this error, try connecting to a different VPN server, disable any firewalls or antivirus programs temporarily, and verify that your network settings are configured correctly.
Additionally, the "VPN authentication failed" error may occur when the encryption protocols used by the VPN client and server do not match. To fix this error, adjust the encryption settings on both the client and server sides to ensure compatibility.
Lastly, if you encounter the "VPN connection timed out" error, it could be due to network congestion, server downtime, or misconfigured settings. Troubleshoot this error by switching to a different network, restarting your router, or adjusting the VPN connection settings.
In conclusion, understanding common VPN connection errors and their solutions is essential for maintaining a secure and stable connection. By following these troubleshooting tips, you can resolve VPN errors efficiently and enjoy a seamless browsing experience.
VPN login troubleshooting guide
In the digital age, VPNs have become an indispensable tool for ensuring online security and privacy. However, even the most reliable VPN services may encounter login issues from time to time. If you are facing VPN login problems, this troubleshooting guide will help you resolve them efficiently.
Firstly, ensure that you are entering the correct login credentials. Check for any typos in your username or password, and make sure that the Caps Lock key is turned off. If you have forgotten your password, follow the service provider's password recovery process to regain access to your account.
If your login credentials are correct but you still can't log in, try switching to a different VPN server. Sometimes, server congestion or technical issues can prevent successful logins. By choosing a different server location, you may be able to bypass the problem and connect to the VPN successfully.
Another common solution to VPN login problems is to clear your browser's cache and cookies. This can help eliminate any stored data that may be causing conflicts with the VPN login process. Additionally, restarting your device or reinstalling the VPN application can also resolve login issues by refreshing the connection.
If all else fails, reach out to your VPN service provider's customer support team for assistance. They can offer tailored solutions to your specific login problems and guide you through troubleshooting steps to get your VPN up and running smoothly again.
By following these troubleshooting tips, you can quickly overcome VPN login issues and enjoy a secure and private online browsing experience. Remember to stay patient and persistent, as most login problems can be resolved with a few simple fixes.
0 notes
Text
does a vpn mess with logins to sites
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn mess with logins to sites
VPN Login Compatibility
When it comes to VPN services, ensuring compatibility with various devices for seamless login experiences is crucial. VPN login compatibility plays a significant role in user satisfaction and accessibility.
Most VPN providers offer login compatibility across a wide range of operating systems, including Windows, macOS, iOS, Android, and Linux. This versatility allows users to access the VPN service from their preferred devices, regardless of the platform they are using. Whether you are logging in from your laptop, smartphone, or tablet, a VPN service that supports multiple operating systems ensures a smooth and consistent user experience.
In addition to offering compatibility across different operating systems, VPN services also cater to various browsers, such as Chrome, Firefox, Safari, and Edge. This ensures that users can log in to their VPN accounts using their preferred web browser, making the process more convenient and user-friendly.
Furthermore, some VPN providers also offer dedicated apps for specific devices, such as smart TVs, routers, and gaming consoles. This level of customization ensures that users can easily log in to their VPN accounts from any device they choose, ensuring privacy and security across all their online activities.
In conclusion, VPN login compatibility is an essential factor to consider when choosing a VPN service. By selecting a provider that offers compatibility across multiple devices and platforms, users can enjoy a seamless and secure online experience, regardless of the device they are using.
VPN Authentication Issues
VPN authentication issues can be a frustrating hurdle for users seeking secure access to their network resources. Authentication problems can arise from various factors, ranging from incorrect login credentials to technical glitches within the VPN infrastructure.
One common issue is the input of incorrect login credentials. Users may mistype their username or password, leading to authentication failures. This can be particularly problematic if the VPN client does not provide clear error messages, leaving users uncertain about the cause of the problem.
Another challenge arises when users forget their passwords or usernames, leading to authentication failures. In such cases, organizations may need to implement password recovery mechanisms or provide support for resetting credentials to help users regain access.
Technical issues within the VPN infrastructure can also cause authentication problems. This may include misconfigurations on the VPN server, expired user accounts, or connectivity issues between the client and server. Diagnosing these issues often requires collaboration between network administrators and IT support teams to identify and resolve the underlying cause.
Additionally, security measures such as two-factor authentication (2FA) can introduce complexities that users may struggle to navigate. Issues with receiving or entering verification codes can hinder the authentication process, requiring additional troubleshooting steps to ensure successful login.
To mitigate VPN authentication issues, organizations should prioritize user education and provide clear guidance on the login process. Implementing robust password policies, offering self-service password reset options, and regularly auditing VPN configurations can also help prevent and address authentication challenges effectively. By proactively managing authentication issues, organizations can ensure smooth and secure access to their network resources for users.
Site Access with VPN
Site Access with VPN
VPN, which stands for Virtual Private Network, is a technology that enables users to create a secure connection to another network over the internet. One of the most common use cases for VPN is to access websites and online services safely and privately.
When you access a website using a VPN, your internet traffic is encrypted and routed through a remote server before reaching the website. This process helps mask your IP address and location, making it difficult for websites to track your online activities. As a result, VPN users can enjoy increased privacy and security while browsing the web.
In addition to enhancing privacy and security, VPNs also allow users to bypass geo-restrictions. For example, if a website or online service is not available in your region, you can use a VPN to connect to a server in a different location where the content is accessible. This functionality is particularly useful for accessing streaming services, social media platforms, and other region-locked websites.
Furthermore, VPNs can help protect users' data from potential cyber threats, such as hacking, surveillance, and data theft. By encrypting internet traffic and masking IP addresses, VPNs create a secure tunnel through which users can safely transmit sensitive information without fear of interception.
In conclusion, VPNs play a crucial role in enabling secure and private site access for users around the world. Whether you're concerned about online privacy, want to bypass geo-blocks, or safeguard your data while browsing the web, using a VPN is a practical solution to enhance your online experience.
VPN Impact on Website Logins
A VPN (Virtual Private Network) can have a significant impact on website logins in various ways. One of the main benefits of using a VPN for website logins is the enhanced security it provides. By encrypting your internet connection and masking your IP address, a VPN can help protect your login credentials from potential hackers and cybercriminals. This is especially important when accessing sensitive accounts such as online banking or email.
Moreover, a VPN can also help bypass geo-restrictions that may prevent you from logging into certain websites based on your location. By connecting to a server in a different country, you can access websites and online services that may not be available in your region.
Another advantage of using a VPN for website logins is privacy protection. Your internet service provider (ISP) won't be able to track your online activities, including the websites you log into, when you use a VPN. This ensures that your login information remains confidential and secure.
However, it's essential to choose a reliable and trustworthy VPN provider to ensure the security and privacy of your website logins. Opt for a VPN service that offers strong encryption protocols, a strict no-logs policy, and a wide range of server locations to enhance your online security and browsing experience.
In conclusion, using a VPN for website logins can enhance security, privacy, and accessibility while protecting your sensitive login information from potential threats. Consider incorporating a VPN into your online routine to enjoy a safer and more secure browsing experience.
VPN Login Challenges
Facing challenges when logging into your VPN service can be frustrating and disruptive, but understanding the common issues can help you troubleshoot and resolve them quickly. One of the primary challenges users encounter when logging into a VPN is entering incorrect login credentials. Double-checking your username and password for accuracy is crucial, as even small typos can prevent successful authentication.
Another common VPN login challenge is related to authentication problems. This issue can arise due to expired credentials, changed passwords, or server-side errors. In such cases, resetting your password or contacting your VPN service provider for assistance can help resolve the problem.
Furthermore, network connectivity issues can also impact your ability to log into your VPN successfully. Poor internet connection, firewall restrictions, or server maintenance can all contribute to login failures. Restarting your router, disabling firewall settings temporarily, or waiting for server maintenance to complete can potentially resolve connectivity-related login challenges.
Additionally, software compatibility issues or outdated VPN clients can pose obstacles during login attempts. Ensuring that your VPN client is up to date and compatible with your operating system can prevent login difficulties due to software glitches.
By being aware of these common VPN login challenges and their potential solutions, you can troubleshoot effectively and enjoy a seamless and secure VPN experience. Remember to keep your login credentials secure, maintain updated software, and address connectivity issues promptly to access your VPN without any hassles.
0 notes
Text
Explore What's In Our Fully Managed IT Support Services with TLS-IT in Dubai
Businesses in Dubai rely on IT solutions from TLS-IT as an indispensable partner, to streamline operations, enhance security and stay ahead in an increasingly competitive marketplace. TLS-IT stands out among UAE IT Solution Partners as being one of the largest Managed IT Service Providers.
TLS-IT Services:
Fully Managed IT Services Overview:
Introduction: TLS-IT, recognized as one of the best IT Solutions Partners in the UAE, takes pride in being a leading Managed IT Services Provider in Dubai.
Key Services:
Data Backup & Recovery
IT Consultancy
Complete IT Audit
Office IT Setup
Network Security & Solutions
Structured Cabling
IP Telephony & PABX
Managed End-User Support
Features of Our Fully Managed IT Services:
IT Strategy, Consulting & Reporting:
Strategic Approach: Our IT strategy consulting involves a thorough examination of your IT department, considering business processes, IT administration, and application landscape.
Execution: Implementing process improvements for enhanced efficiency and alignment with organizational goals.
Active IT Management & Support:
Beyond Operations: Modernized strategy utilizing cutting-edge technologies to set clients apart from competitors.
Comprehensive Approach: It goes beyond keeping servers and software operational, focusing on proactive measures to prevent technical malfunctions.
Business Resilience and IT Security:
Backup Planning: Ensuring a backup plan is in place to safeguard against data loss due to technical failures or cyber threats.
Security Measures: Network support solutions designed to create a secure environment, protecting vital data and passwords.
Specialist Expertise:
Help Desk Support: An extension of our RMM program, allowing you and your staff to communicate with certified experts through calls, chats, or emails.
Focus on Growth: Providing technical support so that businesses can concentrate on growth without IT-related concerns.
Fully Managed IT Solution: A Comprehensive Package for SMEs
Service Inclusions:
End-to-End Proactive IT Management Delivered by Experts
24 X 7 Unlimited Remote IT Support
24 X 7 Unlimited Onsite IT Support
Projects and Consultancy
Telephony and Connectivity
Hardware Maintenance & Support
Network Security
Data Protection
Remote Monitoring and Management
Cloud Services
Network Security Services: Safeguarding Your Business
Security Measures:
Managed switches setup
Wireless access points installation
Routers and firewalls configuration
Data and voice network cabling installation
Extensive security testing and hardening for data and user privacy
Data Protection: Ensuring Data Integrity
Backup Strategies:
On-site and off-site data backup solutions
Regular testing of backups
Expert assistance in designing and implementing an ideal backup system
Monitoring, notifications, and issue resolution
Remote Monitoring and Management: Proactive IT Support
Services Highlights:
24/7 system monitoring
Patch management
Virus protection
Backup verification
Preventing minor issues from escalating
Cloud Services: Secure and Accessible Data
Data Migration Support:
Assisting in migrating databases and applications to a cloud-based environment
Expert guidance before, during, and after cloud data migration
Ensuring data safety and constant accessibility
Domain & Email Security: Comprehensive Protection
Security Measures:
Ensuring the security of domains and emails
Protection against phishing attacks and data breaches
Why Choose TLS-IT for Fully Managed IT Services in Dubai?
Flexible IT Solutions:
Tailored solutions to meet the unique needs of each organization.
Cost-Effective Solutions:
Maximizing IT investment returns without disrupting business operations.
Complete Support:
Comprehensive technical assistance for seamless project execution.
Highly Experienced Team:
A team of qualified experts covering all aspects of IT.
In conclusion, TLS-IT's Fully Managed IT Services in Dubai provide a comprehensive and reliable solution for SMEs, ensuring a seamless IT experience for businesses looking to outsource or change their IT provider. Visit tls-it.com or contact us at +971-4-3955-877 to explore how TLS-IT can empower your business through advanced IT solutions.
0 notes
Text
Troubleshoot Google login in Error
Welcome to our complete guide on how to fix Google sign-in issues. If you've ever had trouble signing in to your Google Account, whether due to errors, account suspensions, or issues with third-party accounts, we have the solutions you need. In this article, we will provide expert advice and effective solutions to help you solve these problems. This guide is intended for users registered with Google SSO. As a district administrator, follow the troubleshooting steps below before completing a support ticket. Teachers, follow the login flow and common errors before completing a support ticket.
October 2023: Google Workspace for Education update Starting October 23, 2023, Google Workspace for Education rolled out an update that requires an organization's administrators to review and confirm access settings for configured third-party apps, including Great Minds. If you do not confirm this setting, users designated as under 18 will not be able to launch Great Minds through Google SSO.
This article from Google explains its recent update and provides a video tutorial on how to review and confirm third-party app settings: Improvements to third-party app access for Google Workspace for Education
When reviewing your app settings, you'll want to designate Great Minds as a "trusted" app. If you have any problems configuring these access settings, please contact our support team for assistance.
Sign in to your Google account To use Sign in with Google, you must sign in to your Google account. If you are having trouble signing in to your Google Account login error, you can follow the steps provided in this section to fix sign-in issues. This section also includes instructions on how to determine if your account is suspended or disabled.
Troubleshooting Google account sign-in issues If you're having trouble signing in to your Google Account, follow these steps to resolve the issue:
Check your Internet connection: Make sure you have a stable Internet connection before trying to log in. If your connection is unstable, try restarting your router or connecting to a different network. Check your username and password: Double-check that you are entering your username and password correctly. Pay attention to capitalization and special characters. If you forgot your password, you can use the account recovery options provided by Google. Clear your browser cache: Cached data can sometimes interfere with the login process. Clear your browser cache and try to log in again. Disable browser extensions: Certain browser extensions or add-ons may conflict with your Google Account sign-in. Temporarily disable any extension that may be causing the problem and try signing in again. Try using incognito mode: Open a new private browsing or incognito window and try to sign in to your Google account. This will disable any extensions or cookies that may be causing the problem.

1 note
·
View note
Text
Disaster-Proof Your Data: 5 Essential IT Recovery Tips
In today's digital landscape, protecting your data from potential disasters is crucial. Whether it's natural calamities or cyber threats, various risks can disrupt your IT infrastructure and compromise valuable information.
That's where disaster recovery strategies come in. In this article, we will explore five essential IT recovery tips, discussing:
Data backup and storage best practices
The importance of a robust disaster recovery plan
The role of cloud computing in preserving your data
Regular testing and monitoring
By following these IT recovery tips, downtime can be minimized, data can be protected, and business continuity can be maintained in the face of any disaster.
Key Takeaways
Understand the importance of planning, testing, and implementing measures to minimize downtime and data loss in IT disaster recovery.
Assess data vulnerabilities by evaluating the security of data storage systems and network infrastructure.
Develop a robust backup strategy by creating multiple copies of data and storing them in different locations.
Implement disaster recovery procedures by conducting risk assessments, regularly backing up critical data, and defining recovery time objectives and recovery point objectives.
Understanding IT Disaster Recov
In order to comprehend the intricacies of IT disaster recovery, it is essential to delve into the technical aspects and processes involved. IT disaster recovery refers to the set of strategies and procedures that organizations implement to ensure the restoration of their IT systems and data in the event of a disaster.
This includes planning, testing, and implementing measures to minimize downtime and data loss. To gain a comprehensive understanding, one must familiarize oneself with concepts such as backup and recovery, business continuity, and risk assessment.
Additionally, knowledge of various technologies, such as cloud computing and virtualization, is crucial in developing a resilient disaster recovery plan. By acquiring this knowledge and understanding the underlying principles, organizations can effectively mitigate the impact of disasters on their IT infrastructure and ensure business continuity.

Assessing Your Data Vulnerabilities
To ensure the effectiveness of your IT disaster recovery plan, it is crucial to assess the vulnerabilities of your data. Understanding the weaknesses in your data infrastructure allows you to implement appropriate safeguards and protection measures.
Here are three key areas to consider when assessing your data vulnerabilities:
1. Data storage: Evaluate the security of your data storage systems, including servers, cloud platforms, and backup devices. Ensure that access controls, encryption, and regular backups are in place to protect against data loss or unauthorized access.
2. Network security: Assess the security of your network infrastructure, including firewalls, routers, and network protocols. Regularly update and patch your systems to prevent vulnerabilities from being exploited by hackers or malware.
3. Employee training and awareness: Educate your employees on best practices for data security, such as creating strong passwords, recognizing phishing attempts, and securely handling sensitive information. Regularly conduct training sessions to reinforce these practices and keep your workforce informed about emerging threats.
Creating a Robust Backup Strategy
Continuing the discussion on assessing data vulnerabilities, it is essential to develop a robust backup strategy to ensure the protection and availability of your data.
A robust backup strategy involves the creation of multiple copies of your data and storing them in different locations. This ensures that even if one copy becomes inaccessible or corrupted, you can still retrieve your data from another source.
It is crucial to regularly back up your data to minimize the risk of data loss. Additionally, consider using a combination of onsite and offsite backups for added security. Onsite backups provide quick access to data, while offsite backups protect against physical damage or theft.
Implementing Disaster Recovery Procedures
To ensure the highest level of data protection and recovery, it is imperative to implement effective disaster recovery procedures. These procedures are essential in minimizing downtime and ensuring business continuity in the event of a disaster.
Here are three key steps to consider when implementing disaster recovery procedures:
1. Conduct a thorough risk assessment: Identify potential risks and vulnerabilities that could impact your IT infrastructure and data. This includes natural disasters, cyberattacks, and hardware failures. By understanding the risks, you can develop a comprehensive disaster recovery plan.
2. Develop a robust backup strategy: Regularly backup your critical data and systems to offsite locations or cloud storage. Implementing a combination of onsite and offsite backups will provide an additional layer of protection. Regularly test and validate your backups to ensure they are usable in the event of a disaster.
3. Establish clear recovery objectives: Define recovery time objectives (RTOs) and recovery point objectives (RPOs) to determine how quickly you need to restore your systems and how much data loss is acceptable. This will help prioritize your recovery efforts and allocate resources effectively.
Testing and Updating Your Recovery Plan
Testing and updating your recovery plan is crucial for maintaining the effectiveness and reliability of your disaster recovery procedures. In the ever-evolving world of technology, it is essential to regularly assess and refine your recovery plan to ensure its ability to handle unforeseen events.
Testing allows you to identify any gaps or weaknesses in your plan, enabling you to make necessary adjustments and improvements. By conducting regular tests, you can validate the functionality of your recovery procedures and verify that all systems and processes are working as intended. This proactive approach helps to minimize downtime and maximize data protection.
Additionally, updating your recovery plan ensures that it remains aligned with your organization's changing IT infrastructure and business requirements. By staying current with technological advancements and industry best practices, you can enhance the resilience and efficiency of your disaster recovery capabilities.
Conclusion
In conclusion, implementing effective IT disaster recovery strategies is crucial for businesses to protect their valuable data from potential disasters.
By assessing vulnerabilities, creating a robust backup strategy, implementing disaster recovery procedures, and regularly testing and updating the recovery plan, businesses can ensure the availability of their data even in the face of unforeseen events.
Following these essential IT recovery tips will minimize downtime, safeguard data, and maintain business continuity.
1 note
·
View note
Text
Ok here's what you do in this case.
Most networks will have the wifi password on the back of the router.
While on your main network, the one she turns off, you're going to go to your preferred web browser, and open an incognito tab.
The way you do this:
For Chrome in the very top right corner, there are 3 dots next to where your account is.
You're going to click the dots, and it will open a long menu. The 3rd or 4th option down says "New Incognito window". Press that button.
For Firefox it's in a similar place, only it's 3 lines stacked together.
Click those lines, and the 3rd or 4th option will say, "Open private window". Click that.
You are now going to make a Proton email. The site lets you create an email without 2FA (2 factor authentication) meaning you do not need to verify your identity with a backup email, phone number, etc. so that if this following method is discovered, there are fewer traces to find how you did it. Make sure you have a secure place to record your Proton email and password because if the password is lost then you lose the email!!
THE SITE HAS FREE OPTIONS!! KEEP SELECTING THE PROMPTS FOR THE FREE EMAIL!!! DO NOT PAY!!!
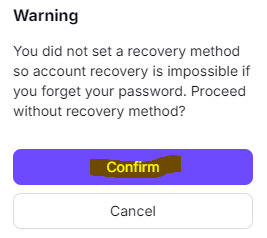
Proton email will ask you if you'd like to add a backup/recovery method. SELECT "MAYBE LATER"!!

It will ask you to confirm your choice to not have a backup. Select "confirm"!!
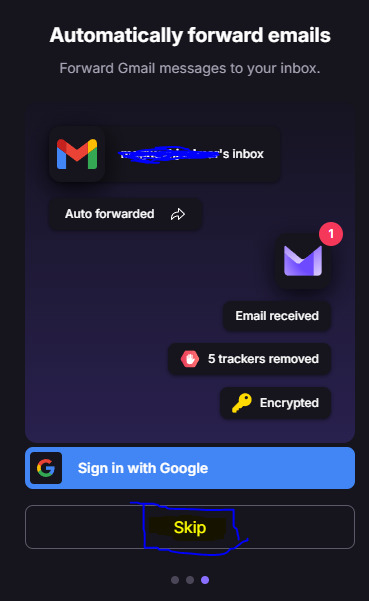
It will ask again if you would like to attach a Gmail account or otherwise. Select "skip".
Now you have your private and secure email, no strings attached. You're ready for part 2!
From here, still in the incognito tab, you're going to visit Proton VPN and install the VPN for your type of computer (Windows, Mac, Linux). DO NOT RUN IT YET!!
CREATE THE FREE PROTON VPN ACCOUNT!! AGAIN, DO NOT PAY FOR IT!! THEY HAVE THE OPTIONS TO DENY PAYMENT AND USE THEIR PROGRAM FOR FREE!!
Once the FREE account is made, it's onto the next step.
Now for the hardest part. Disregard if you know the wifi router name and password, and skip the next 2 paragraphs. If not, deep breaths. It's going to be intimidating, but you've got this.
WAIT UNTIL YOUR MOTHER IS ASLEEP OR GONE FOR A REASONABLE AMOUNT OF TIME!!! Essentially, learn her sleep and exit patterns to know if she will wake after an hour, two hours, three, etc. And if she does, then does she leave her bedroom? If she leaves the house, does she return within any amount of time?
You're going to pattern your timing here, and make sure you know where the router she uses and you do not, is located. Bring something to record the wifi network name and password. Whether this is a phone camera, a scrap of paper and a pen/pencil, make sure you can collect that name and password quickly.
Get the info ASAP and go back to your computer. Now, you're going to disconnect from the network your mother turns off.
The way you do this on Windows 10 is you go to your wifi settings.
When you select this, at the top, it will list the network you're currently connected to. You're going to know your computer is connected when it says, "You're connected to the Internet."

On the leftmost side, in the options, select, "Wi-Fi".

Now you'll see at the top of this page, there is the small blue toggle that says, "On."

Select this toggle so it turns gray.
Run Proton VPN now.
Tell it to connect to a network from any available in the list by clicking "Quick Connect".
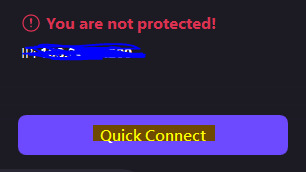
It will not be able to connect yet because you're disconnected from any network, but let it keep trying to connect regardless.
From here, you're going to go back to your computer's internet settings, and look for the network your mother uses.
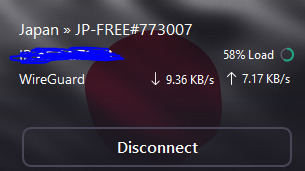
To do this, go to your Windows wifi settings again, and under the Wi-Fi tab, just beneath the toggle you selected before to make it gray, you're going to select the toggle again so it turns blue. This turns the wifi back on, and the VPN will connect. YOU WILL KNOW THE VPN IS CONNECTED WHEN IT SHOWS A FLAG FOR ANOTHER COUNTRY AND THE OPTION "DISCONNECT"!!
Now, back to the Windows wifi settings yet again. You'll notice just beneath this toggle, there's the option "Show available networks".
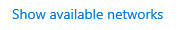
This will open in the bottom right of your screen, the list of available wifi networks. Search for the one your mother uses, the one with the same router name that you wrote down. Click on it, enter the password you collected.
Now you're connected to her network, and it's nearly impossible to kick you off unless she shuts the router down as a whole!
Should the router go down, Proton VPN will say so. If your IP gets blocked, or it changes, Proton VPN will say so.
Now! Go ahead and do everything in the above original post I made SPECIFICALLY FOR THIS ROUTER, THE ONE YOUR MOTHER USES AND WHICH YOU JUST CONNECTED TO, and you'll be able to protect your IP even more!
Make sure to hide your Proton email and VPN account information in a secure place, and be safe on the internet!!
And, if you want to hide Proton VPN as a whole on your computer, let me know. I can show you how to change the icon so it's less suspicious!
An important life tip for parents who block your wifi on PC/laptop (Windows 10)
I found a workaround that's suiting me so far. How it works is, wifi is blocked through the router by detecting your computer's IP address, and blocking said address. Now, it seems complicated because there are tons of methods to use for changing your IP. But so you don't have to go through the same steps every time, do this:
Make sure you're connected to a wifi network that you're blocked on. You can check by going to the Windows search bar, type "settings", hit enter, and select "Network & Internet".
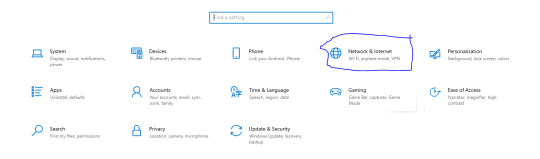
It will show you the network you're currently connected to. If it says "connected, no internet" or something along those lines, you're good for the next step.
Next, go to the tab on the left labeled "WiFi". There, you will see a setting labeled "Random hardware address", and a slider beneath it that is most likely greyed out. Select it, making sure it turns blue.

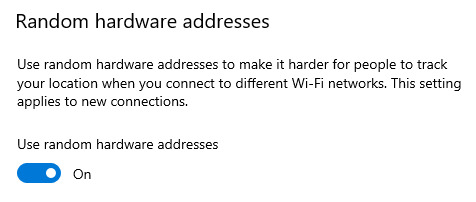
Then, you're going to hit the tab on the left labeled "Status". From there, just beneath where it says you're connected to a router without internet, click the grey button labeled "properties".
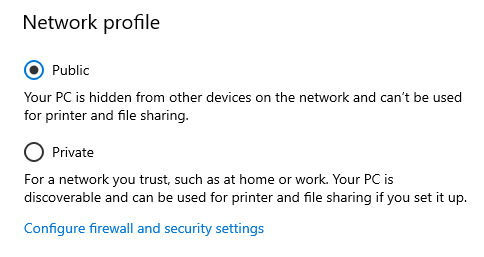
Where it says "Network profile", click the "Public" setting, so that other devices in the house cannot discover your computer or connect to it, and therefore reach its files and settings.
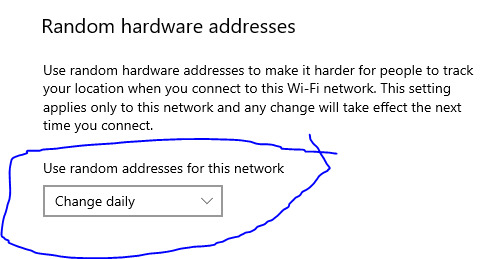
And lastly, scroll down to the section labeled "Random hardware address". There is a drop down menu. Open the menu, and select "Change daily". This will change your IP address on a daily basis, meaning your computer will be unblocked until the IP is discovered, but once the next day arrives, it will change again and unblock it.
Hope this helps y'all as it helped me. Do not let fucking shit block you from the most essential resource in the modern world. Internet connects you to every necessary thing in existence. It's a basic necessity at this point, by ethical standards. Regain access to it however you can, wherever you can, whenever you can.
461 notes
·
View notes
Text
Cybersecurity Challenges in the Era of Remote Work and BYOD

The rapid shift to remote work and the widespread use of Bring Your Own Device (BYOD) policies have introduced new cybersecurity challenges for organizations. The expanded attack surface, increased reliance on personal devices, and remote network access create vulnerabilities that cybercriminals can exploit. Understanding and addressing these challenges is crucial for maintaining a secure remote work environment. Let’s explore some of the key cybersecurity challenges in the era of remote work and BYOD.
1. Endpoint Security: With remote work and BYOD, employees connect to corporate networks using various devices, including personal laptops, smartphones, and tablets. Ensuring the security of these endpoints becomes critical. Organizations must implement strong endpoint protection measures such as antivirus software, firewalls, and encryption to mitigate the risk of malware infections and unauthorized access.
2. Secure Remote Access: Remote work necessitates secure remote access to corporate resources. VPNs, multi-factor authentication (MFA), and secure remote desktop protocols are essential for encrypting connections and verifying user identities. Organizations should enforce strict access controls and monitor remote access activities to detect any suspicious behavior or unauthorized access attempts.
3. Data Protection and Privacy: The remote work environment increases the risk of data breaches and privacy violations. Sensitive data may be stored and transmitted outside the corporate network, making it more susceptible to unauthorized access. Implementing data protection measures such as encryption, data loss prevention (DLP), and data classification policies is crucial to safeguard sensitive information.
4. Phishing and Social Engineering: Cybercriminals exploit the vulnerabilities of remote workers through phishing attacks and social engineering tactics. Employees working outside the corporate network may be more susceptible to malicious emails, fake websites, and social engineering scams. Regular employee training and awareness programs can help mitigate these risks by educating employees about common attack vectors and best practices for identifying and reporting suspicious activities.
5. Home Network Security: Home networks may lack the robust security measures implemented in corporate environments. Weak passwords, unpatched routers, and outdated firmware can create vulnerabilities that cybercriminals can exploit. Educating employees about home network security best practices and providing guidelines for securing their home networks can help mitigate these risks.
6. Data Backup and Recovery: With remote work, the risk of data loss due to device theft, hardware failure, or human error increases. Regular data backups, both locally and in the cloud, are essential to prevent data loss and enable quick recovery in case of incidents. Organizations should establish clear data backup policies and ensure employees adhere to them.
7. Shadow IT: The use of unauthorized applications and services (Shadow IT) can introduce security risks. Employees may adopt unsanctioned cloud services or collaboration tools without proper security controls. Organizations should provide secure alternatives and educate employees about the risks associated with using unauthorized applications.
8. Compliance and Regulatory Considerations: Remote work may introduce compliance challenges, particularly with data protection and privacy regulations. Organizations must ensure that remote work practices align with regulatory requirements, including data handling, storage, and cross-border data transfer. Regular audits and assessments can help identify compliance gaps and ensure adherence to relevant regulations.
Addressing the cybersecurity challenges in the era of remote work and BYOD requires a multi-layered approach. Organizations should implement robust security measures, provide ongoing cybersecurity awareness training, enforce policies and best practices, and regularly assess the effectiveness of their security controls. By prioritizing cybersecurity and staying vigilant, organizations can maintain a secure remote work environment and protect sensitive data from evolving threats.
If you need assistance in implementing secure remote work solutions, strengthening your cybersecurity posture, or have any other technology-related questions, visit us at www.infradapt.com or call us at 484-546-2000. Our team of experts can provide guidance, support, and tailored solutions to address your specific cybersecurity challenges.
https://www.infradapt.com/news/cybersecurity-challenges-remote-work-and-byod/
0 notes
Text
Data Privacy-Protection Tools to Keep Your PC Safe

The importance of data privacy-protection tools to keep personal and sensitive data safe cannot be overstated. With the growing number of cyber threats and the increasing amount of personal data shared and stored online, it is crucial to use effective data privacy-protection tools such as VPNs, antivirus software, password managers, and encryption tools to prevent unauthorized access and data breaches.
Compliance with data privacy laws and regulations is also essential to avoid legal consequences and financial impact.
In today's digital age, it's essential to keep your personal data safe from cyber threats. Data privacy-protection tools are essential to keep your PC safe from cyber threats and protect your personal information from being compromised.
Data protection refers to a collection of techniques and procedures for ensuring the privacy, availability, and integrity of your information. Any organization that gathers, processes, or keeps sensitive data must have a data protection plan.
A good plan may aid in the prevention of data loss, theft, or corruption, as well as the mitigation of harm caused by a breach or disaster. So, if you're worried about how to keep your data safe, here's a quick primer to some options.
Data Privacy- Protection Tools to Keep Your PC Safe
Firewall
Because it divides one network from another, a firewall is one of the finest network defenses. To prevent unwanted traffic from entering the network, firewalls are used. Furthermore, you may only open ports, giving hackers less freedom to move to get access to or steal your data.
The firewall may entirely reject some or all traffic, or it may perform verification on some or all traffic, depending on the organization's firewall policy. Firewalls can be freestanding or integrated into other infrastructure devices like routers and servers. Firewall solutions are available in both hardware and software formats.
Backup & Recovery
Backup and recovery refer to the process of backing up data in the event of a loss and establishing systems that enable data recovery in the event of a loss. A backup and recovery solution helps businesses protect themselves if data is lost or corrupted.
Data from a previous time can only be restored if it has been backed up. All key business assets should be replicated regularly to ensure redundancy so that you can swiftly recover your data in the event of a server failure, inadvertent loss, or malicious harm from ransomware or other assaults.
Antivirus
Antivirus is one of the most extensively used security technologies in both personal and business environments. Although there are several antivirus software companies on the market, they all utilize the same approaches to identify dangerous code, mainly signatures and heuristics. Antivirus software can help you detect and remove trojans, rootkits, and viruses that can steal, change or harm your personal information.
Intrusion Detection & Prevention Systems
Intrusion detection systems, often known as IDS and intrusion prevention systems, or IPS, examine network traffic in detail and log possibly hostile behavior. An IDS may be set up to examine system event logs, monitor suspected network activity, and send out warnings when sessions appear to breach security parameters.
An IPS can not only identify harmful sessions, but it can also terminate them, albeit this is generally confined to particularly crude and apparent assaults like DDoS.
Between alert and action, security administrators usually perform an analysis to determine whether the alert represents danger and whether the threat is relevant to them.
These solutions need excellent calibration and research before making a session drop decision on an incoming alert, but they can help with data protection by preventing a hacker from gaining into your file servers using vulnerabilities and malware.
Security Information & Event Management
SIEM systems, or security information and event management, allow real-time analysis of security logs generated by network devices, servers, and software applications. SIEM solutions can not only collect and correlate events, but they can also do event deduplication, which involves deleting numerous reports from the same instance and then acting on alert and trigger criteria.
It also frequently includes an analytics toolbox to assist you to identify exactly the events you need right now, such as data security events. For data security investigations, SIEM systems are essential.
Data Loss Prevention
DLP systems, also known as data loss prevention systems, keep an eye on workstations, servers, and networks to ensure that sensitive data isn't destroyed, relocated, or duplicated. DLP is a combination of tactics and technologies that you may use to ensure that your data is properly protected.
Several technologies to defend against and recover from data loss are frequently included in data loss prevention systems. They also keep track of who is accessing and transferring data to detect unlawful activity.data privacy protection tools
Access Control
Users should not be permitted to copy or save sensitive data locally in most instances. Furthermore, critical information should never be saved on a portable machine. All systems should need some sort of login, and criteria should be in place to lock the system down if it is used inappropriately. Only authorized people should have access to sensitive files
Read This Full ARTICLE, Click Here
0 notes
Text
Cybersecurity in the Age of Remote Work: Challenges and Best Practices for Indonesian Organizations
In the age of remote work, cybersecurity has become a critical concern for organizations worldwide, including those in Indonesia. The shift to remote work brings about several unique challenges that organizations must address to ensure the security of their systems, data, and employees. In this response, I will outline some of the key challenges faced by Indonesian organizations in terms of cybersecurity during remote work and provide best practices to mitigate these challenges.
Challenges in Cybersecurity for Indonesian Organizations:
Increased Attack Surface: With employees working remotely, the attack surface expands as corporate systems and data are accessed from various devices and networks outside the organization's control. This increases the risk of unauthorized access, data breaches, and other cyber threats.
Insecure Home Networks: Employees working from home often rely on their personal networks and devices, which may lack proper security measures. Weak or unpatched routers, outdated operating systems, and misconfigured devices can become potential entry points for attackers.
Phishing and Social Engineering: Remote work environments may make employees more susceptible to phishing attacks and social engineering attempts. Attackers may exploit the lack of face-to-face communication and impersonate colleagues or authorities to trick employees into sharing sensitive information or clicking on malicious links.
Inadequate Endpoint Security: Endpoint devices such as laptops, smartphones, and tablets used for remote work may not have the same level of security controls as office devices. This can make them more vulnerable to malware, ransomware, or other malicious activities.
Data Loss and Leakage: Sharing and storing sensitive data remotely can increase the risk of data loss or leakage. Insecure file-sharing practices, weak passwords, or accidental sharing of confidential information can lead to unauthorized access or data breaches.
Best Practices for Indonesian Organizations:
Employee Education and Awareness: Conduct regular cybersecurity awareness training for employees to educate them about common cyber threats, safe online practices, and the importance of data security. This should include guidance on identifying phishing emails, using strong passwords, and recognizing potential security risks.
Secure Remote Access: Implement secure virtual private networks (VPNs) to encrypt communication between remote employees and corporate networks. Require multi-factor authentication (MFA) for all remote access to add an extra layer of security.
Strong Endpoint Security: Ensure that all remote devices have up-to-date antivirus and anti-malware software installed. Implement centralized device management and enforce security policies, including regular patching and software updates.
Data Protection and Encryption: Encourage employees to use secure file-sharing platforms that encrypt data in transit and at rest. Implement data loss prevention (DLP) solutions to monitor and prevent unauthorized data transfers or leakage.
Regular Security Audits and Monitoring: Conduct periodic security audits to identify vulnerabilities in systems, networks, and applications. Implement continuous monitoring solutions to detect and respond to potential security incidents in real-time.
Incident Response Plan: Develop an incident response plan that outlines the steps to be taken in the event of a cybersecurity incident. This should include procedures for reporting incidents, isolating affected systems, and restoring operations.
Regular Backup and Recovery: Implement regular data backups to ensure that critical data can be restored in case of data loss or ransomware attacks. Test the backup and recovery processes periodically to verify their effectiveness.
Compliance with Regulations: Stay updated with relevant cybersecurity regulations and standards in Indonesia, such as the Government Regulation No. 82/2012 on the Protection of Personal Data in Electronic Systems. Ensure that remote work practices align with these requirements.
Secure Collaboration Tools: Implement secure collaboration and communication tools that support encryption and access controls. Use platforms with built-in security features to protect sensitive information shared among remote employees.
B2b events and conferences
Business events in Bangalore
B2b events
Tech summit
Business events in India
corporate events in India
Business Event
0 notes