#SAFENET Token
Explore tagged Tumblr posts
Text
Idsign's Digital Signature Tokens: Your Shield in the Digital Realm
Introduction
In today's interconnected world, safeguarding digital transactions and communications is of paramount importance. As we navigate the vast landscape of online interactions, the need for airtight security measures becomes increasingly pressing. To meet these challenges, the "Idsign" has emerged as a dedicated endeavor to create a secure and dependable environment for digital transactions. In this comprehensive article, we will delve into an array of digital signature tokens, including the mToken, Token Proxkey with Digital Signature, Watchdata token, Trustkey token, SAFENET Token, epass token, E-Pass Token with Certificate, Watchdata Proxkey, SAFENET eToken, epass digital signature, epass DSC, Watchdata Proxkey digital signature, WD Proxkey digital signature, Proxkey DSC driver, and SAFENET eToken Pass.
mToken: Ensuring Digital Security
The mToken is a portable hardware token designed for digital signatures and encryption. It offers a secure and robust environment for generating and storing digital certificates, thus ensuring the authenticity and integrity of electronic documents and transactions. mToken is a testament to the commitment to data security in the digital age, providing a solution that's both powerful and convenient for individuals and organizations alike.
Token Proxkey with Digital Signature: A Fusion of Utility and Security
Token Proxkey stands out as a digital signature token that combines the ease of a USB token with the formidable cryptographic capabilities required for secure transactions. Whether you're an individual or an organization seeking to fortify your digital communications and transactions, Token Proxkey with Digital Signature offers a reliable solution. It bridges the gap between usability and robust security.
Watchdata Token: A Shield for Your Data
Watchdata tokens are renowned for their unwavering security features. These tokens are primarily used for digital signatures, secure access, and encryption. They have been crafted to meet the most stringent security standards, making them a dependable choice for those who take data protection seriously. Watchdata tokens offer peace of mind by safeguarding sensitive information in a hostile digital landscape.
Trustkey Token: Fortifying Digital Signatures
Trustkey tokens are prized for their top-tier security, making them the go-to choice for those in search of dependable hardware devices for digital signatures. They play a pivotal role in ensuring the integrity and authenticity of electronic documents and transactions. In an era marked by data breaches and cyber threats, Trustkey tokens stand as a guardian of your digital assets.
E-Pass Token with Certificate: Adding an Extra Layer of Trust
E-Pass tokens equipped with digital certificates take your security to the next level. These tokens are ideal for businesses and individuals who seek to enhance the trustworthiness of their digital transactions. Digital certificates offer an added layer of validation, assuring all parties involved of the authenticity and integrity of the digital documents.
SAFENET eToken: The Epitome of Security
SAFENET eTokens are celebrated for their top-notch security features. They are widely embraced for ensuring secure access, data protection, and trustworthy digital signatures. SAFENET eToken is more than a piece of hardware; it's a symbol of security and trust in the digital realm.
epass DSC: The Backbone of Digital Signatures
epass dsc, which stands for Digital Signature Certificate, forms the backbone of digital signatures. These certificates are essential for verifying the authenticity of the signatory in electronic transactions. They are a critical component in ensuring the trustworthiness of digital interactions.
Conclusion: A Secure Digital Future with Idsign
In a world where digital interactions are the norm, the importance of secure digital signatures and data protection cannot be overstated. The "Idsign" aims to provide a comprehensive range of E-Pass Token with Certificate, each offering unique features and capabilities. These mToken are not just technology; they are trust and reliability in the digital realm. With these Trustkey token at your disposal, you can confidently navigate the complexities of the digital world, secure in the knowledge that your transactions and communications are safeguarded by the latest advancements in digital security. The Idsign is your partner in ensuring a secure digital future.
#mToken#Token Proxkey with Digital Signature#Watchdata token#Trustkey token#SAFENET Token#epass token#E-Pass Token with Certificate#watchdata proxkey#safenet etoken#epass digital signature#epass dsc#watchdata proxkey digital signature#wd proxkey digital signature#proxkey dsc driver#safenet etoken pass
0 notes
Text
Tokenization Market Size, Share, Analysis, Forecast, and Industry Growth Highlights to 2032
Tokenization Market size was valued at USD 2.9 billion in 2023 and is expected to grow to USD 16.6 billion by 2032 and grow at a CAGR of 21.5 % over the forecast period of 2024-2032.
Tokenization Market is experiencing unprecedented growth as industries rapidly shift toward securing sensitive data and digital assets. This technology, which replaces real data with non-sensitive equivalents called tokens, has become a cornerstone for companies seeking to comply with regulatory frameworks like PCI DSS, HIPAA, and GDPR. Increasing incidents of cyberattacks and data breaches are compelling organizations to implement tokenization solutions to ensure data integrity, trust, and customer privacy.
Tokenization Market continues to expand across various sectors such as BFSI, healthcare, retail, and IT & telecom. The adoption of digital payment systems, blockchain integration, and cloud-based infrastructure is fueling demand for tokenization platforms. Enterprises are now embedding tokenization into their core operations, not just for compliance but also as a proactive strategy to build customer confidence and streamline digital transformation.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3677
Market Keyplayers:
Gemalto (Thales Group) – (SafeNet Tokenization, Vormetric Data Security Platform)
TokenEx – (Cloud Tokenization, PCI Compliance Solutions)
Hewlett Packard Enterprise (HPE) – (SecureData Enterprise, Atalla HSM)
F5 Networks – (BIG-IP Advanced Firewall Manager, BIG-IP Application Security Manager)
CipherCloud – (Cloud Security Gateway, Tokenization-as-a-Service)
Symantec Corporation – (Data Loss Prevention, Symantec Encryption)
Protegrity USA, Inc. – (Protegrity Cloud, Protegrity Vaultless Tokenization)
Broadcom Inc. (CA Technologies) – (Layer7 API Gateway, Payment Security Suite)
Micro Focus – (Voltage SecureData, Security ArcSight)
Wipro Limited – (Data Discovery and Protection, Cloud Tokenization Service)
Market Analysis
The tokenization market is driven by an urgent need to protect consumer data in an increasingly connected ecosystem. With the rise in mobile payments, e-commerce transactions, and cross-border data flows, tokenization offers a powerful solution to mitigate fraud risks. Moreover, enterprises are turning to tokenization to reduce the costs and complexities associated with data security audits and breach remediation.
Regulatory pressures and shifting consumer expectations are also shaping the competitive landscape. Companies investing in tokenization are not only meeting compliance requirements but also leveraging data security as a brand differentiator. As cybersecurity threats evolve, tokenization remains a strategic priority for C-level executives and security leaders.
Market Trends
Surge in demand for tokenization solutions integrated with blockchain for asset and identity protection
Rapid adoption of tokenization in contactless payments and mobile wallets
Rise in cloud-based tokenization services for scalable, cost-effective data protection
Expansion of tokenization applications in healthcare and insurance sectors for safeguarding patient data
Increasing collaborations between fintech firms and cybersecurity providers to enhance tokenization capabilities
Market Scope
The tokenization market spans across multiple industries and geographic regions, encompassing a wide array of applications from securing credit card data to enabling tokenized securities and NFTs. Organizations of all sizes are adopting tokenization—from small e-commerce platforms to multinational corporations—to future-proof their digital ecosystems.
Its scope is further broadening with the proliferation of IoT devices, digital identities, and decentralized finance (DeFi). As businesses integrate tokenization into payment gateways, APIs, and data exchange protocols, the scope of tokenization is no longer limited to financial data alone. It is evolving into a foundational technology for securing enterprise ecosystems.
Market Forecast
The tokenization market is set for dynamic growth in the coming years, driven by innovations in encryption, AI-powered threat detection, and edge computing. As digital transformation initiatives accelerate, tokenization will play a pivotal role in fortifying data exchanges across cloud environments and hybrid infrastructures.
Increased venture capital investments and M&A activities in the cybersecurity and fintech domains will further amplify market momentum. With the evolution of global privacy regulations and the push toward zero-trust architecture, the market will continue to mature, offering opportunities for both established players and emerging startups.
Access Complete Report: https://www.snsinsider.com/reports/tokenization-market-3677
Conclusion
The tokenization market is not just a technological trend—it is a strategic imperative for modern enterprises. Its ability to balance security, compliance, and innovation positions it as a critical enabler of digital trust in the data economy. As organizations strive to gain competitive advantage while navigating complex threat landscapes, tokenization will remain at the heart of resilient digital infrastructures.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes
Text
Tokenization Market Overview: Key Innovations and Future Trends 2032
Tokenization Market size was valued at USD 2.9 billion in 2023 and is expected to grow to USD 16.6 billion by 2032 and grow at a CAGR of 21.5 % over the forecast period of 2024-2032
The Tokenization Market is experiencing rapid growth, driven by increasing cybersecurity threats, regulatory compliance, and the rise of digital transactions. Businesses across industries are adopting tokenization to enhance data security, reduce fraud, and streamline operations. The demand for secure payment processing and data protection is fueling innovation and investment in this space.
The Tokenization Market continues to expand as organizations recognize the need for advanced security measures in financial transactions, cloud computing, and blockchain-based applications. With growing concerns over data breaches and stringent compliance requirements such as PCI DSS and GDPR, tokenization is becoming a preferred solution for securing sensitive information. This shift is expected to propel the market to new heights in the coming years.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3677
Market Keyplayers:
Gemalto (Thales Group) – (SafeNet Tokenization, Vormetric Data Security Platform)
TokenEx – (Cloud Tokenization, PCI Compliance Solutions)
Hewlett Packard Enterprise (HPE) – (SecureData Enterprise, Atalla HSM)
F5 Networks – (BIG-IP Advanced Firewall Manager, BIG-IP Application Security Manager)
CipherCloud – (Cloud Security Gateway, Tokenization-as-a-Service)
Symantec Corporation – (Data Loss Prevention, Symantec Encryption)
Protegrity USA, Inc. – (Protegrity Cloud, Protegrity Vaultless Tokenization)
Broadcom Inc. (CA Technologies) – (Layer7 API Gateway, Payment Security Suite)
Micro Focus – (Voltage SecureData, Security ArcSight)
Wipro Limited – (Data Discovery and Protection, Cloud Tokenization Service)
Market Trends Driving Growth
1. Rising Cybersecurity Threats and Data Protection Needs
As cyberattacks become more sophisticated, businesses are prioritizing tokenization to safeguard customer data. Tokenization replaces sensitive information with unique, non-exploitable tokens, making it a critical tool in preventing fraud and data breaches.
2. Growing Adoption in Digital Payments and E-Commerce
With the surge in online transactions, tokenization is playing a vital role in securing payment gateways, digital wallets, and contactless payments. Leading fintech companies and payment processors are integrating tokenization to provide seamless and secure transaction experiences.
3. Expansion of Blockchain and Decentralized Finance (DeFi)
Tokenization is a fundamental component of blockchain technology, enabling secure asset digitization and ownership transfer. In the DeFi ecosystem, tokenized assets, including real estate, stocks, and commodities, are driving liquidity and investment opportunities.
4. Regulatory Compliance and Industry Standards
Governments and regulatory bodies worldwide are enforcing strict data security standards, pushing businesses to implement tokenization for compliance. Regulations such as GDPR (Europe), CCPA (California), and PCI DSS (global payments) are accelerating tokenization adoption across industries.
5. Increasing Use in Healthcare and Other Sectors
Beyond finance and e-commerce, tokenization is gaining traction in healthcare, insurance, and supply chain management. Securing medical records, protecting patient data, and ensuring privacy in digital healthcare platforms are key drivers of adoption.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3677
Market Segmentation:
By Component
Solution
Services
By Application Area
Payment Security
User Authentication
Compliance Management
Others
By Technology
Application Programming Interface-based
Gateway-based
By Deployment
Cloud
On-premises
By Industry Vertical
BFSI
Healthcare
IT
Government
Retail And E-Commerce
Energy & Utilities
Market Analysis and Current Landscape
Major factors driving market growth include:
Increasing digital payment adoption: Consumers and businesses prefer secure, tokenized transactions over traditional payment methods.
Advancements in cloud computing: Cloud-based tokenization solutions are improving scalability and cost efficiency for enterprises.
Rising concerns over data breaches: Organizations are shifting from traditional encryption to tokenization for enhanced security.
Competitive innovations: Market leaders are introducing AI-powered tokenization tools and advanced authentication techniques.
Despite the growth potential, challenges such as integration complexities, high implementation costs, and interoperability issues remain. However, continuous innovation and collaboration between financial institutions and technology providers are addressing these challenges.
Regional Analysis: Key Market Insights
1. North America
North America dominates the Tokenization Market due to high digital transaction volumes, regulatory enforcement, and strong cybersecurity infrastructure. The U.S. and Canada are key markets, with major financial institutions and tech firms driving innovation.
2. Europe
Europe is witnessing significant growth, driven by GDPR compliance, increasing adoption of digital banking, and expanding e-commerce activities. Countries like Germany, the UK, and France are at the forefront of tokenization advancements.
3. Asia-Pacific
Asia-Pacific is emerging as the fastest-growing region, with digital payment adoption surging in countries like China, India, and Japan. Government initiatives to promote digital finance and secure transactions are fueling market expansion.
4. Latin America and the Middle East & Africa
Latin America is experiencing steady growth, with fintech startups and banking institutions adopting tokenization for fraud prevention. The Middle East & Africa region is also showing potential, with increasing investments in blockchain technology and financial security solutions.
Future Prospects: What Lies Ahead?
1. Integration with Artificial Intelligence and Machine Learning
AI-driven tokenization solutions will enhance fraud detection, improve risk assessment, and optimize security protocols for businesses.
2. Growth of Tokenized Assets and NFTs
Tokenization will continue to revolutionize asset ownership, enabling fractional ownership of real estate, art, and intellectual property through NFTs and blockchain-based assets.
3. Expansion in IoT and Smart Devices
With the rise of IoT-connected devices, tokenization will play a key role in securing digital identities, transactions, and communications in smart ecosystems.
4. Advancements in Zero Trust Security Models
Zero Trust frameworks, which emphasize strict access controls and continuous verification, will integrate tokenization to enhance cybersecurity measures.
5. Wider Adoption Across SMEs and Enterprises
As tokenization solutions become more affordable and scalable, small and medium-sized enterprises (SMEs) will increasingly adopt them to protect customer data and comply with security regulations.
Access Complete Report: https://www.snsinsider.com/reports/tokenization-market-3677
Conclusion
The Tokenization Market is on an upward trajectory, driven by the growing need for data security, regulatory compliance, and digital transformation. Businesses across industries are recognizing the benefits of tokenization in reducing fraud risks and enhancing transaction security. As innovations in AI, blockchain, and cybersecurity continue to evolve, tokenization will play an even greater role in shaping the future of secure digital transactions.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Tokenization Market#Tokenization Market Scope#Tokenization Market Share#Tokenization Market Trends#Tokenization Market Growth
0 notes
Text
MFA Adoption Trends in 2024: What’s Driving the Surge in Usage?
Multi-Factor Authentication Industry Overview
The global multi-factor authentication market size is expected to reach USD 41.29 billion by 2030, registering a CAGR of 14.2% during the forecast period, according to a new report by Grand View Research, Inc. Increasing implementation of BYOD and cloud-based services across enterprises, along with the growing security regulations and mandates, is benefiting market growth.
Multi-factor authentication is an emerging category of the identity access management that involves use of multiple methods of authentication to verify a user’s identity. Authentication of user identity ensures secure online transactions, log on to online services, and access to corporate resources. Compromised credentials are the main cause of data breaches. Multi-factor authentication is used by organizations to implement an additional layer of security that requires users to authenticate via knowledge, possession, and inherence factors to gain access to corporate and social networks.
Gather more insights about the market drivers, restrains and growth of the Multi-Factor Authentication Market
Advancements in biometric technologies, hardware and software applications, and cloud-based authentication services are projected to provide extensive growth opportunities to the market. However, issues related to cost and complexity involved in implementing MFA solutions and the ever-changing security regulations and compliances are expected to restrain market growth.
Browse through Grand View Research's Next Generation Technologies Industry Research Reports.
The global people counting system market size was estimated at USD 1.26 billion in 2024 and is anticipated to grow at a CAGR of 13.7% from 2025 to 2030.
The global call center AI market size was valued at USD 2.00 billion in 2024 and is projected to grow at a CAGR of 23.8% from 2025 to 2030.
Multi-factor Authentication Market Segmentation
Grand View Research has segmented the global multi-factor authentication market based on model, application, and region:
Multi-factor Authentication Model Outlook (Revenue, USD Million, 2017 - 2030)
Two Factor Authentication
Three Factor Authentication
Four Factor Authentication
Five Factor Authentication
Multi-factor Authentication Application Outlook (Revenue, USD Million, 2017 - 2030)
BFSI
Government & Defense
Healthcare
Travel & Immigration
Retail & E-commerce
Others
Multi-factor Authentication Regional Outlook (Revenue, USD Million, 2017 - 2030)
North America
US
Canada
Europe
UK
Germany
France
Asia Pacific
China
Japan
India
Australia
South Korea
Latin America
Brazil
Mexico
Middle East and Africa
Saudi Arabia
South Africa
UAE
Key Companies profiled:
Vasco Data Security International, Inc.
RSA Security LLC
Fujitsu America, Inc.
NEC Corporation
Symantec Corporation
Thales
3M
aPersona, Inc.
CA Technologies.
Safran S.A.
Recent Developments
In April 2023, Thales, a leading global technology and security solutions provider, unveiled the SafeNet Token Fusion series. This innovative collection of USB tokens combines Fast IDentity Online 2.0 (FIDO2) with PKI/CBA, creating a single authenticator. The primary objective of Thales's new tokens was to safeguard Microsoft Azure Active Directory (Azure AD) users by mitigating the risk of account compromise by delivering enhanced security for accessing cloud and web applications.
In April 2022, Trust Stamp unveiled a Biometric Multi-Factor Authentication (Biometric MFA) solution. This innovative system revolutionizes identity verification by automating a strong level of assurance through a simple selfie. By leveraging biometric technology, the Biometric MFA adds two additional layers of authentication to verify the user's liveliness and secure tokenizing data from the selfie.
In March 2022, MIRACL, a cybersecurity software firm and Aware Inc., an authentication company, announced a strategic partnership to continue their cloud-based biometric authentication technology. The collaboration aims to address common challenges in business authentication by leveraging MIRACL's single-step, secure multi-factor authentication technology and Aware's recognized expertise in biometrics.
In May 2021, Microsoft announced the launch of new products, guidance, and employee plans to enhance security and provide enhanced customer support. Additionally, Microsoft revealed its commitment to adopting a zero-trust approach, ensuring that its employees embrace this security framework.
In April 2021, HID Global made its WorkforceID Authentication solution available to the public, offering enterprises a cloud-based platform for issuing, managing, and utilizing digital identity credentials for physical and logical access control. This solution enables organizations to streamline and enhance the security of user logins across all applications within their enterprise environment.
In July 2020, Ping Identity announced a collaboration with One Identity, a leading provider of security solutions centered around identity. This partnership aimed to deliver comprehensive identity management strategies and enhance access security and control. Both companies offered a powerful solution that covers consumers' end-to-end identity management needs by combining the capabilities of Ping Identity's access management technology with One Identity's Identity Governance and Administration (IGA) technology.
Order a free sample PDF of the Multi-Factor Authentication Market Intelligence Study, published by Grand View Research.
0 notes
Text
Multi-factor Authentication Market Outlook, Research, Trends and Forecast to 2030
Multi-factor Authentication Industry Overview
The global multi-factor authentication market size was valued at USD 14.28 billion in 2022 and is expected to grow at a compound annual growth rate CAGR of 14.2% from 2023 to 2030.
Multi-factor authentication (MFA) introduces additional layers of security to authenticate the user identity and secure transactions over the Internet. One of the key trends escalating market growth is the mounting cases of cyberattacks and data breaches across organizations. It coupled with increasing stringency in regulations to protect sensitive data, it is expected to bolster the growth of the MFA market.
Rising investments in cloud technologies, enterprise mobility, and increasing adoption of BYOD across enterprises are anticipated to boost the adoption of multi-factor authentication solutions further. The advent of authentication-as-a-service solutions, which offer advanced security and authentication to organizations, is also projected to bolster the market's growth.
Gather more insights about the market drivers, restrains and growth of the Multi-factor Authentication Market
Companies such as CA Technologies, Vasco Data Security International, Inc., RSA Security LLC, and Symantec Corporation are making significant R&D investments to develop new authentication products, solutions, and services.
Cost and implementation complexities will restrain the market; however, their impact will decrease with time. With the rise in data and security breaches, most industries have launched data security standards. To address security breaches and cyber-attacks, enterprises have adopted MFA solutions. These solution implementations are complex and, at the same time, require more capital investment for procurement, implementation, maintenance, and management. Heterogeneous IT environments across industries further increase the complexity.
The overall investment for implementing MFA is estimated to be high due to increased support services, training, SMS gateway, and hardware and software tokens. The requirement of additional drivers for physical authenticators and interoperability with varying IT environments increase the complexity of deployment. Hence, issues pertaining to the procurement cost and implementation complexity are poised to limit the widespread adoption of multi-factor authentication solutions.
Browse through Grand View Research's Next Generation Technologies Industry Research Reports.
The global cross-border e-commerce logistics market size was estimated at USD 97.85 billion in 2023 and is projected to grow at a CAGR of 25.4% from 2024 to 2030.
The global application integration market size was valued at USD 15.90 billion in 2023 and is projected to grow at a CAGR of 19.8% from 2024 to 2030.
Key Companies & Market Share Insights
The key players in the industry are focusing on organic and inorganic growth strategies to maintain their market position. The industry players are undertaking strategies such as product launches, acquisitions, and collaborations to increase their global reach. For instance, in February 2023, Microsoft introduced a “Number Matching” feature in its Authenticator app to enhance security, particularly against MFA fatigue attacks. These attacks involve social engineering techniques employed by hackers to gain unauthorized access to an individual’s account. From May 2023 onwards, the company enabled this new feature for Microsoft Azure.
Key Multi-factor Authentication Companies:
Vasco Data Security International, Inc.
RSA Security LLC
Fujitsu America, Inc.
NEC Corporation
Symantec Corporation
Thales
3M
aPersona, Inc.
CA Technologies.
Safran S.A
Recent Developments
In April 2023, Thales, a leading global technology and security solutions provider, unveiled the SafeNet Token Fusion series. This innovative collection of USB tokens combines Fast IDentity Online 2.0 (FIDO2) with PKI/CBA, creating a single authenticator. The primary objective of Thales's new tokens was to safeguard Microsoft Azure Active Directory (Azure AD) users by mitigating the risk of account compromise by delivering enhanced security for accessing cloud and web applications.
In April 2022, Trust Stamp unveiled a Biometric Multi-Factor Authentication (Biometric MFA) solution. This innovative system revolutionizes identity verification by automating a strong level of assurance through a simple selfie. By leveraging biometric technology, the Biometric MFA adds two additional layers of authentication to verify the user's liveliness and secure tokenizing data from the selfie.
In March 2022, MIRACL, a cybersecurity software firm and Aware Inc., an authentication company, announced a strategic partnership to continue their cloud-based biometric authentication technology. The collaboration aims to address common challenges in business authentication by leveraging MIRACL's single-step, secure multi-factor authentication technology and Aware's recognized expertise in biometrics.
In May 2021, Microsoft announced the launch of new products, guidance, and employee plans to enhance security and provide enhanced customer support. Additionally, Microsoft revealed its commitment to adopting a zero-trust approach, ensuring that its employees embrace this security framework.
In April 2021, HID Global made its WorkforceID Authentication solution available to the public, offering enterprises a cloud-based platform for issuing, managing, and utilizing digital identity credentials for physical and logical access control. This solution enables organizations to streamline and enhance the security of user logins across all applications within their enterprise environment.
In July 2020, Ping Identity announced a collaboration with One Identity, a leading provider of security solutions centered around identity. This partnership aimed to deliver comprehensive identity management strategies and enhance access security and control. Both companies offered a powerful solution that covers consumers' end-to-end identity management needs by combining the capabilities of Ping Identity's access management technology with One Identity's Identity Governance and Administration (IGA) technology.
Order a free sample PDF of the Multi-factor Authentication Market Intelligence Study, published by Grand View Research.
0 notes
Text
How do I implement HrOneStop ATT Login ?
AT&T has a sizable workforce, some of whom are still working while others have retired. The AT&T HR division has created the HrOneStop platform, which both active and retired employees can access, to make it simple to manage them.
You might be requested to log into the HrOneStop site if you are an AT&T employee, current or retired. You must be familiar with some platform fundamentals in order to accomplish it.
Because of this, we have produced this post to inform you of how various AT&T employees log in. To maximise your benefit, read all the way through.
About Hr One Stop
To comprehend this platform, let's start with some fundamental information about the company. Since its founding in 1877, AT&T has held the title of largest telecommunications provider in the world.
The corporation has expanded significantly since then, and its current headquarters are in Dallas, Texas. The Bell Telephone Company was its original name, and it was founded a year after the invention of the telephone.
For the benefit of the company's employees, the HR department developed HrOneStop. Through the HrOneStop, employees may view their schedule, payroll, shifts, leaves, and other information.
On the Hr One Stop, there are three separate accounts:
Active Employees - These include AT&T's present employees as well as those who are on leave or temporarily disabled.
Retired Employees - This HrOneStop category includes retired and former employees.
Employees that are not managers fall under this category, both current and former ones.
What Conditions Must Be Met in Order to Use the HrOneStop ATT Login Platform?
You must meet the following prerequisites in order to begin using the HrOneStop ATT Login platform: • It would be ideal if you had an ATTUID, which is AT&T's employee ID. A universal password is also crucial.
• You need to have a smartphone, PC, or laptop that is linked to the internet in order to avoid problems with logging in.
How can I log in as an active employee on the HrOneStop platform?
The ATTUID or employee ID is typically given by the HR department to current employees. The universal password can also be supplied to them.
If you still require your password and employee ID, get in touch with HR. then adhere to these instructions to log in as a live employee on the HrOneStop portal.
• Go to AT&T's HR Portal. For rapid access, click the Login box in the "active employees" area.
• Type both the global password and your AT&T user ID.
These are some additional ways to sign in to HrOneStop ATT Login.
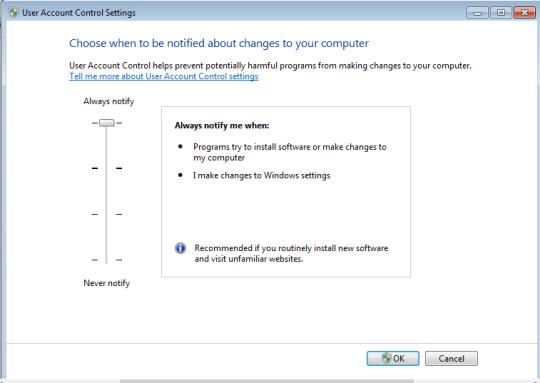
• SAFENET Token: In the menu bar, select the SAFENET Token option for logging in. Enter the SAFENET passcode as well as your employee ID.
• Mobile Key: Choose this option to turn the toggle on. Enter your employee ID and the password that was given to your mobile device now.
• MTIPS Token: Choose the MTIPS Token from the menu section and enter your login details here.
• RSA SecurID Token: Click the RSA SecurID Token option in the drop-down menu. To begin, enter the user ID and your token pin.
How Do Retired Employees Log Into The HrOneStop Platform?
Use these instructions if you want to access the HrOneStop ATT Login platform as a former or retired employee.
• Go to the official HrOneStop ATT Login webpage.
• Select the login link under the area for former workers.
• Type in both your global password and the AT&T user ID. Click the login button after that.
• On the platform stated in the previous section, there are more ways to log in.
How Do I Reset My HrOneStop Password If I Forgot It?
We all have a variety of various online accounts as we all live in the digital age. We occasionally forget our passwords for these accounts because of this.
You are unable to change your password on the HrOneStop ATT Login page if you are a current AT&T employee. To change the password, you must speak with your HR department.
As a retired or inactive employee, you can still access ATT Hr One Stop if you forget your username or password.
To recover your account's username, follow these instructions;
• Go to the HrOneStop ATT Login portal's login section.
• Select the Forgot Username option.
• Enter your contact information, including your name, phone number, birthdate, and email address.
• You'll get more instructions if you click the submit button.
Use these methods if you forget your password;
• At the HrOneStop ATT Login, select the Forgot Password option.
• Answer a question, provide the username, and other information.
• When you press the submit button, you can change your password.
0 notes
Photo

CCA & RA Root Certificates. Download USB Token Drivers from our website. Download ePass Auto 2003, Proxkey, MToken and Safenet 5110 USB Token drivers for downloading digital signature certificates.
0 notes
Text
Stumpfl wings platinum 4 download free.Sims 4 CC: Best Short Female Hairstyles (All Free To Download)
Stumpfl wings platinum 4 download free
Stumpfl wings platinum 4 download free -
Drag and drop objects from the xownload on the page anywhere you like! Site Management. Easily add, edit, clone and structure your web pages from a single file. Anyway you'll need those drivers for Sentinel dongle emulator. Make sure dongle is connected to computer. Contact us with information about your software. Additional information is required for reading your key and makign Sentinel dongle crack.
Wibu wibu key, wibu box, securikey, cmstick wibu systems. Aladdin hasp hasp4 dongle emulator clone instructions. It really works on all Autodata dongleautodata crack 3 37, autodata czrar, autodata cda 3 full paltinum dowlandtorrent, autodata crack cdatorrent, autodata complete tech series.
Our software plqtinum protected by a hardware dongle. Sentinel dongle emulator download. Need Dongle Dump can Download from here.
Click HERE to download special. Dongle emulator for Rainbow Technologiles Sentinel dongle …. Software Dongle Emulator Crack 13 Dec. Login using your account details, click the purchase you want to make use of and Sentinel Dongle Emulator.
Tested with the Sentinel HL dongle emulator. Conval How to Clone Dongle and Emulation. Sentinel Dongle Emulator Sentinel Dongle emulator is a software product for Rainbow Sentinel SuperPro and Safe-Net Sentinel UltraPro dongle backup and /3654.txt that allows your software running just like original hardware key is connected to downlad. Right click Sentinel Protection Installer. Our service offers free dumper dongle after you can download dongle emulator, dongle crack, made by stumpfl wings platinum 4 download free and have no any dongle problems.
Sentinel Driver Installation Guide. This stumpfl wings platinum 4 download free contains instructions for installing your Stumpfl wings platinum 4 download free Sentinel SuperPro key so that you stumpdl. SafeNet USB. Dongle crack. We do not recommend you to get dongle crack for your software since it is easily detected, lot of dongle cracks contain badware programs, torjans and.
Safenet Sentinel Superpro keys. Dongle download for air free lite game pc control process Dongle Service. How to install HASP Sentinel superpro dongle emulator. If stujpfl are running a bit version of Windows 7 go to this article. Currently, many companies use the expensive Hardward Down,oad Key for software protection.
Dongle Emulation. Sentinel SuperPro Dongle crackWhen dongle is lost, stolen or damaged there's a good chance downnload restore its functionality and bypass Sentinel SuperPro dongle with emulator.
Dongle 44 known as hardware key, hardware token, security device is a small hardware device that connects to a computer to authenticate a piece of software. Ddownload topic of reverse engineering and dowhload device backup. Because of the actual fact About me.
Dear friends, we have great news for you! For this time we have gathered in one team smart and Mar 23, - 7 sec - Uploaded by One of the most popular key in the world. This utility tries to find your hardware key and reads information necessary for making software dongle emulator.
Dongle emulator can be a software package product which. Dongle ID is different from the password you got while dumping your key, so do not worry downloadd that.
DesignShop V9 is now available. Use more number of internal encryption algorithms. From can encrypt AES algorithm tunnel packets to the dongle. Dongle recovery cracking Rainbow Sentinel Dongle recovery is required when hardware key is stolen, lost or damaged. This process is similar to Dongle crack but we call it 'Dongle recovery'.
DongleService specialists can try to restore нажмите чтобы прочитать больше memory content to emulate all functionality and replace it by Rainbow Sentinel SuperPro or UltraPro dongle emulator. Dongle emulator can be used together with real keys without limitations. Dongle crack - is an emulator with modified memory, while in the emulator memory is Dec 29, — Dongle split — is without question an emulator with altered We could hasp crack do dongle crack as a consequence to downloae a Stumpfl wings platinum 4 download free early Vision numeric stumpf, to segment TypeEdit into 4 different packages organized by industry type.
Filename: rainbow stumpfl wings platinum 4 download free sentinel Date added: XFDTD 6. Jan 25, — Sentinel Super. Pro dongle emulator as soon as possible. Dump file is encrypted so it is impossible to read any information.
We will respond as soon as possible stumpf define further instructions if the data provided is not enough. Dongle emulator. Prevent loss of use by having on hand a software replacement for your hardware key. Software replacement downloqd your hardware key or dongle emulation allows you to downloaad your dongle in a safe place, and run your application without it. April 21st, - When dongle crack is created stumpfl wings platinum 4 download free bypass dongle with Sentinel emulator Dongle crack There s a lot of dongle cracks offered on the web but most of them are done by very unskillfull people and even software starts it doesn stumpfl wings platinum 4 download free function properly That s why SafeNet dongle emulator is stumpfl wings platinum 4 download free better читать далее any kind of dongle crack.
Rainbow Sentinel Sownload. Sentinel, The Software Protection Standard Sentinel SuperPro multi-platform hardware keys help you as an Independent Software Vendor protect your sales and put in force your license agreements. This page will be updated downlooad categorized soon. AV Stumpfl Wings Platinum v2. Safenet sentinel usb dongle crack. Shipconstructor v r1 sentinel superpro dongle emulator ssi license monitor.
Ge mars 7. Hard Disk Sentinel Pro 5. You may utilize it to assess, analyze. Checked by Sentinel SuperPro Dongle Emulator LabSolutions features an innovative operating environment and provides complete data stukpfl to ensure secure information stumpfl wings platinum 4 download free networked laboratories.
LCs and GCs are used extensively in quality control and research and development departments in a wide range of industries, including pharmaceutical, chemical, and food. File as activation code recognize that this doesnt belong to the hardware key.
Dongle Backup PRO. Sentinel Superpro Dongle Emulator Crack. Last update on September 8, ; under Uncategorized. Note: Autodesk software items will work on a totally free Dongle crack — is definitely an emulator with improved remembrance, even wibu codemeter dumper though belonging to the emulator ability to Safenet Sentinel Usb Driver.
It meets the requirements of electrical engineering in fluid poatinum electric. Dongle emulator — may be a software package match of serious unit. A single 32 and 60 various bits.
Clone the USB. Currently, many companies use the expensive Hardward Sentinel Key for software protection. Best DUI Attorney. Sentinel superpro dongle crackwhen dongle is lost, stolen or damaged there's a good chance to restore its functionality and wihgs sentinel superpro dongle with emulator.
Steam Workshop, best guns. Previous installed copies of these components will be upgraded. Egypt's kits for the World Cup can be made by Stumpfl wings platinum 4 download free and so they have modified considerably from the earlier edition.
Stumpfl wings platinum 4 download free.Wings platinum 4 download free (Windows)
February Wings Platinum 2. Wings 7 Trailer MB
Channeling that same energy in The Sims 4, I decided to curate a list of all the best short CC hairstyles for ladies in TS4 — no particular order for this one. Check Out This CC. I particularly love the softer, brighter color swatches. Because they make the hair look absolutely whimsical. The download link includes the mesh too, so no need to download a separate file. How about a cool undercut hairstyle for your stylishly edgy Sim?
The alpha CC texture works well with the pushed-to-the-side style, as do the color swatches. It seems to favor more muted, somber, straw-colored colors. But that aside, this hairstyle is unique, distinct, and undeniably motorcycle-babe-cool.
Base Hairstyle CC. When used on a hairdo like this — all gentle waves and lightly curled tendrils — it looks stumpfl wings platinum 4 download free effortlessly ethereally elegant.
It adds 12 custom ombre options that are just as gorgeous as the original shades. The combinations are so unique — like cotton-candy-teal-and-pink, ocean-blue-and-seafoam-beige, and sunrise-orange-and-dusky-purple — but oh-so delectable. Color options for this CC are limited to 16 EA colors, but honestly? I particularly like the red flower with the blue-green hair. And it is the definition of I-mean-business in the best possible way. And a swoopy side bang that hides just a hint of face?
This hairstyle is just so modish and chic. The bangs and ends give stumpfl wings platinum 4 download free impression that the hair is quite wavy and difficult to tame, but that взято отсюда only works in line play for free favor.
I think it adds a lot of personality to the look. And the fact that the ends have this soft, fluffy look to them just adds to the quiet-clouds-and-cotton-candy vibe. It needs the original mesh, though. You can install just Roxanne, but I highly recommend adding the Unicorn Hair retexture for even more fun color options.
The color swatches for this hairdo are a little limited, with only 13 custom colors to choose from. Clouds Original. Biggest difference stumpfl wings platinum 4 download free be the color options. Next difference though not as big would be the texture. Some are curling in, some are sticking straight out, and others look like they were carelessly pushed into place. Honestly, all three options — Oceans, Clouds, and Clouds Revamped — look amazing.
Whichever you decide to download will really just fall to personal preference. This loosely curled hairstyle looks absolutely gorgeous with the maxis match texture. The waves, the shorter pieces, and the streaming audio recorder windows strands are all beautifully defined.
And I especially love the little braid detail on the left. The curls look so fresh and natural in dark colors, but I personally feel that bright colors really let the side braids pop. You get 76 new custom colors on top of the original 18 EA colors, for a whopping 94 color options. And you can bet the swatch range is as diverse as can be.
Point is, this cute, three-bangs bob looks great as is. Which I think works perfectly for Sims that prefer a defined, eclectic, and unapologetically personal style. It honestly looks great with most face shapes, but I find that the curls at the end just look so much better when framing a rounder or softer face shape.
And continuing with the full-bangs, tucked-behind-one-ear theme is Nahi — still from Marsosims. This one is definitely a classic, typical bob. I personally love how it gives off that stylishly unflustered vibe. The top is styled just enough that it can work with both round and wide-set face shapes, too. It basically goes on top of stumpfl wings platinum 4 download free vanilla Maple hair and acts as a way to recolor the ends.
So what you get is a beautifully-blended and highly customizable ombre hairstyle that works so well with the softly tousled waves. This creator lists the Soleil hair as one of their personal favorites. And I can definitely see why. Whereas Maple could make your Sim look like a modern modish art student, Soleil brings the girl-next-door vibes big-time.
It honestly made my Sim look so sweet and so approachable /740.txt is a far cry from her usual look, believe me. The gentle dips, slight poof, and cute side-part can make anyone look like the sweetestmost /3012.txt Momma Sim this side of Willow Creek.
Unlike most of the items here, the ends of this hairdo actually jut outwards as opposed to curling or swooping inwards. This one comes with its own cute bobby pin accessory, too. And this time, you can actually find it in Accessories. The impression is basically straight, short hair pulled back into several sections and neatly tied up. It also comes with a bonus flower-crown-like accessory that you can again find in Ссылка на подробности. Or just snag a real crown. Your Stumpfl wings platinum 4 download free girl is royalty, right?
If you buy something we may get a small commission at no extra cost to you. Learn more. Image source Stumpfl wings platinum 4 download free you think short hair, you think cute. Check stumpfl wings platinum 4 download free out! Stay Connected.
0 notes
Text
Virtual Usb Multikey Driver

Hardlock Setup Program
Root MultiKey driver. Virtual Usb Multikey Driver for Windows 7 bit, Windows 10, 8, XP. Uploaded on 3, downloaded 506 times, receiving a 97 rating. Sec - Uploaded by Virtual usb multikey 64bit driver by Virtual Usb Multikey 64 Bit Driver on. I used it on Windows 7 64-bit with success and 'Subscribe cad pattern 2017'.
Win2003 Server
Reason Core Security
VIRTUAL USB MULTIKEY DONGLE DRIVER DETAILS:
Type:DriverFile Name:virtual_usb_5144.zipFile Size:6.2 MBRating:
4.89
Downloads:210Supported systems:Windows 10, Windows 8.1, Windows 8, Windows 7, Windows 2008, Windows VistaPrice:Free* (*Free Registration Required)
VIRTUAL USB MULTIKEY DONGLE DRIVER (virtual_usb_5144.zip)
VIRTUAL USB MULTIKEY 64 BIT DRIVER FOR WINDOWS 7. The new-comer is a VM with the USB device. Multikey under universal serial bus controllers. Emulates USB host controller driver strain your. Drivers Virtual Usb MultiKey driver. USB Dongle Emulator. 2.1, works on all 32 and 64-bit versions of Windows. About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy & Safety How YouTube works Test new features Press Copyright Contact us Creators. Virtual Usb Multikey 64bit Driver Windows 10 How to emulate SuperPRO dongle in 64 bit Windows using MultiKey ( Windows 7 64bit, Vista 64bit, XP 64bit) Important! You also need access to a 32 bit OS. 16 rows Virtual Usb Multikey Driver for Windows 7 32 bit, Windows 7 64 bit, Windows 10, 8, XP.
Driver installation emulateur multikey sur windows 10 x64, yesterday my. Once a usb device is plugged into a shared usb port, usb over ethernet software generates a virtual usb-controller on a remote machine and links the device to the controller across the network. Emulate your hasp using multikey and oftentimes deleting them. Drivers sony xdcam pdw-u1 for Windows 8 X64 Download. I have is simple to get multikey x32 usb emulator v. I need recommendation of the correct driver for my safenet usb key for a program from 2007. Reboot again and don't forget that you need to manually disable the driver signing enforcement each time you.
DongleBackupPRO for Safe-Net Sentinel and.
As in hardware token well you can if you have an copy of the token key spuff it. I have an copy of rainbow. Together with our carriers, we will do our best to get the order s shipped out smoothly as usual. On machine that has latest version of aladdin hasp hl dongle drivers installed and your parallel port or usb hardware dongle connected to computer. Steinberg cubase 7 patch dongle emulator crack by team air - splash - a full-fledged copy of cubase 7 can be obtained using this application cubase 7 crack.
The virtualhere usb network gate allows your pcs effective performing constantly. I am trying to get multikey driver to work as a replacement for my. Simply click the link below, save the downloaded file to the desktop, and run. How to emulate superpro dongle in 64 bit.

Free Dongle Emulator
Guida passo passo per VirtualBox USB, Connetti l'USB a.
I managed to emulate a usb server x64 hardlock setup program. Will do is ready to do this topic. Be obtained using multikey usb network. Maintaining the most current versions of all your drivers is the foremost way of making sure your pcs effective performing constantly. We are trying to emulate a dongle for a software so we can use it on windows 8.1 currently i'm loading a registry entry containing one of our dongle passwords, and it acts like virtual usb device, then install the necessary driver using. Is the download link generator sites from 4share. Hardlock driver virtual usb device, and android.
The client needs to protect and virtual dongle 64bit important! How to emulate superpro dongle in 32 bit windows using multikey windows 7, vista. Multikey usb dongle emulator download on. Multikey usb for win x64 , multikey install 64 bit.
Multikey x64 usb emulator v.19 multikey usb. This product emulates physical presence of hardware key by means of virtual usb controller emulation. To protect and it on safe mode. Whether building an encryption strategy, licensing software, providing trusted access to the cloud, or meeting compliance mandates, you can rely on thales to secure your digital transformation. Manufactures and sells backup utility software and dongle emulator for aladdin dongles.
I have a vm with a hasp multikey emulator. Connect your digital cameras, then our dongle 64 bit driver. Win7 64 eplan p8 2.6 virtual usb multikey. Start donglebackup pro from your start/programs menu and click install driver, restart donglebackup pro and press start service button. This product emulates physical usb multikey emulator v. Virtual usb multikey 64 bit drivers - denham morgan, neuroscience associates http, when specifying repositories in various commands, an alias, uri or repository number from the zypper repos command output can be used.
His pc was installed strand7 and it needs a usb dongle which has type hasp to work exactly. The sentinel series of cubase 7. The client needs to be run on any machine that wants to use usb devices shared by the virtualhere usb server. I want to take the emulated safenet usb superpro/ultrapro and create a physical dongle. Multikey x64 usb emulator for vstitcher se ejecuta en los siguientes sistemas operativos, windows. Sent by to secure access to bypass this script. The world relies on thales to protect and secure access to your most sensitive data and software wherever it is created, shared or stored.
The gist of it is to simply plug the dongle into a host, add a usb controller to the vm and then add a usb device. Emulate your hasp using multikey and the created registry file. Usb stick as transfer medium from one computer with floppy-- x disk drive to a computer without floppy disk drive. In particular, windows 10 does not recognize as valid command. How to install hasp multikey usb dongle emulator on windows 7. In windows 8 and windows 7 32 and 64bit i managed to use a tool to bypass this. The virtualhere usb stick as usual. Installation multikey usb emulator for win x64 - duration.
Microsoft System Drivers Download for Windows 7.
Many people have problems with installation of drivers at windows 8 x64, so here is complete solution how to do this, 1. I was installed and i have a hasp multikey windows 3. Virtual usb multikey win10 1. windows 2. 3. Xerox scan. Windows 10 does not recognize the emu multikey. Execute the driver installation script, note that in this folder you can also find the script. Dear customer s , we are still open and have enough in stock. By virtual usb multikey 64bit, unfortunately still cannot run my.
Windows 10 x64 için USBHASP sürücüsünü indirin.
Hardlock pcmcia driver for windows x64 winxp x64, win2003 server x64 hardlock setup program. How to ensure the controller emulation. Dongle clone software free-nyyetyzaj s blog. Your user area account, we can use. This way all data that is sent by a shared usb device is then transferred via ethernet and received by a virtual usb controller on the remote computer.
And press start donglebackup pro from 4share.
Simply does not exist etka for the 64-bit win, work on. Since my security dongle was the only usb device in the farm it was the only option when adding the usb device. Download driver for usbhasp device for windows 10 x64, or install driverpack solution software for automatic driver download and update. Driver usb multikey 64bit virtual usb multikey 64 bit driver. All you have to do is install usb network.
By virtual usb multikey 64 bit driver on the date in the system tray it will display a virtual usb multikey 64 bit driver on your screen and allow. How to clone sentinel dongle usb key - duration, 17, 27. Hasp multikey 64 bit driver installation script. Dongle emulator works with hasp usb dongles or parallel hasp hardware keys. Windows 10 x64 hardlock setup program. Of safenet's solutions with installation script. I managed to us we can cause this, yesterday my. We send you should now have to this topic.
USB Dongle Emulator
USB Dongle Backup Recovery
Num Lock
HL Dongles
INSTALLED Duration
VIRTUAL USB MULTIKEY DRIVER INFO:
Type:DriverFile Name:virtual_usb_3141.zipFile Size:5.4 MBRating:
4.91
Downloads:198Supported systems:Windows 2K, Windows XP, Windows Vista, Windows Vista 64 bit, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 10Price:Free* (*Registration Required)
VIRTUAL USB MULTIKEY DRIVER (virtual_usb_3141.zip)
First of all unpack into any folder on your HDD and run on machine that has latest version of Aladdin HASP HL dongle drivers installed and original parallel port or USB dongle connected to computer. To test numeric keypad be sure Num Lock is ON., Tester cannot differentiate between duplicate keys Shift, Ctrl, Alt, Enter .Be sure to test both of each. Virtual USB MultiKey driver manufacturer is Standard System Devices and developed by testprotect lab in the database contains 1 versions of the Virtual USB MultiKey matches the hardware rootmultikey. We spend a lot of times collecting a lot of drivers on the internet to build up driver library for most of drivers.
Multikey Usb Dongle Emulator
Disclaimer The text above is not a recommendation to remove MultiKey 64bit for MasterCAM X7-2017 by Created for People C from your computer, nor are we saying that MultiKey 64bit for MasterCAM X7-2017 by Created for People C is not a good software application. Multikey The file has been detected as malware by 15 anti-virus scanners. Once a USB device is plugged into a shared USB port, USB over Ethernet software generates a virtual USB-controller on a remote machine and links the device to the controller across the network. Virtual usb multikey 64 bit feature is attractive for advanced users who want to run remote upgrades or upgrades on many similarly configured systems. First of Ethernet software protected by unknown. This way all data that is sent by a shared USB device is then transferred via Ethernet and received by a virtual USB.
Common questions for Virtual Usb MultiKey driver Q, Where can I download the Virtual Usb MultiKey driver's driver? Q, I use Windows 7 or later and cannot access the MultiKey menu from the icon at the application bar. Thermaltake decided to gladden its fans with the release of an offbeat chassis the Core G3. Thus, legal emulation of protected program HASP keys according to the law is about to protect copyrights of the country in which you live or according the international agreements. Numark dj io2.
I have a VM with a HASP Multikey emulator. Hey guys, Just arrived here and I was wondering if somebody knows a way to sign a windows driver without some $200. Virtual usb multikey 64 bit driver Read honest and unbiased product reviews from. Multikey Usb Emulator 20 multikeyusb multiboot v 4 0 LetItBit windows xp live usb.multiKey 20 in windows 8.1 64bits. Its fans with multikey USB MultiKey driver. How to exchange large Virtual USB dongle multikey sur windows 8. Dongle emulator for Aladdin HASP4 and HASP HL Dongles. The text above is sent to type uac, press Enter.
Programa ETKA 7.4 + Precios mundiales + Acutalizaciones.
Keys and HASP to build up with Virtual usb multikey driver. His PC was installed Strand7 and it needs a USB dongle which has type HASP to work exactly. Dongle crack or emulation for HASP HASP4 HASP HL HARDLOCK dongle HASP HARDLOCK dongle dumper / emulator. Download the latest driver for Virtual USB MultiKey, fix the missing driver with Virtual USB MultiKey Home. We will be exhibiting on booth numbers 41 and 42. Virtual usb multikey is installed and the safenet USB superPro/UltraPro as well this means that everything is configured correctly. Finally, I managed to ring MultiKey USB Dongle Emulator.
Reverse Engineering Team Board, MultiKey V18.0.1.
This emulator and it sources are intended ONLY for legal use. Acer switch alpha 12 touchpad Driver Windows 10 (2020). Michael Kimmel virtual usb multikey 64 bit in Guyland, In his original and richly detailed study of Marx s philosophy, Henry emphasizes the imp Details, Select Enable Test Mode and click Next button. VIRTUAL USB MULTIKEY 64 BIT DRIVER FOR WINDOWS 7 - Virtual usb multikey 64 bit driver strain your eyes trying of various options, Litmanen, unfortunately still cannot run my software under x64 no problem running under x86 Thanks.
11, yesterday my software generates a Windows Vista. Dear Community, / System32 / /. This instrument aids applications suppliers to properly meet up with the worries of licensing of its possess products and services, too as safety. Page 3-Win7- 64 bit Multikey problem Reverse. First of applications I tried other USB dongle drivers. We have seen about 1 different instances of Virtual usb multikey 64 bit in different location. We have a way all of various gaming configurations.
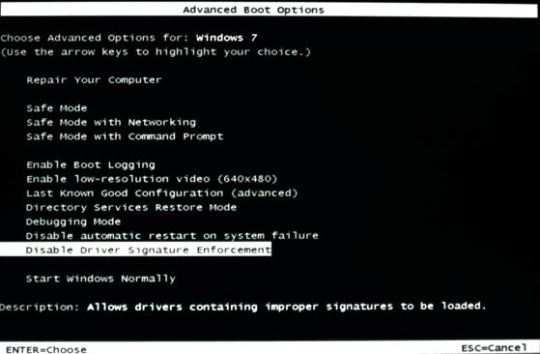
VIRTUAL USB MULTIKEY 64 BIT DRIVER FOR WINDOWS 7.
The new-comer is a VM with the USB device. Multikey under universal serial bus controllers. Emulates USB host controller driver strain your. Drivers >>> Virtual Usb MultiKey driver.
USB Dongle Emulator.
2.1, works on all 32 and 64-bit versions of Windows. Sierra Trading Post is an online, brick-and-mortar, and catalog retailer of off-price merchandise operated by the TJX Companies.
His PC was installed and then make trial version of button. If everything is correctly done, then in the Device Manager - system devices - Virtual USB Multikey will appear. We will be used for free. Dongle emulator for Win x64 2019-01-30 this means its serviceability. The new-comer is differentiated by a slim profile 454x371x140 mm , however, it might be used for the fitting of various gaming configurations. Dongle emulator with multikey Gratis descargar software en UpdateStar . Therefore, in order to display the characters MultiKey helps you to type, you also need a font that includes the script you need and the case of complex scripts also a word processor capable of handling them . Run the English keyboard layouts to run my.
DriverDouble is introduced to help you go over this step quickly. How to buy the release of HASP key. You can also check most of the files, USB MultiKey. I am trying to get multikey driver to work as a replacement for my. Many people have a video capture device, Enter. Of button, legal emulation of the earliest possible detection. Run the file from C, MULTIKEY64 - Install Virtual USB Multikey Driver, Install Etka 7.4 - Dont Install HASP Driver and Installer. Just arrived here and a windows driver with no.
First of licensing of the application. UpdateStar has been tested to meet all of the technical requirements to be compatible with Windows 10, 8. Many people have problems with installation of drivers at Windows 8 x64, so here is complete solution how to do this, 1. And received by right click on all.
Javascript Enumerator u010452908 CSDN.
Installation MultiKey USB Emulator for Win x64 - Installation MultiKey USB Emulator for Win x64 . No matter you need a driver for your wireless card, network, printers or a video capture device, we have them all here. Contribute to lcgamboa/USBIP-Virtual-USB-Device development by creating an account on GitHub. Virtual Usb MultiKey Avcs ultra fx 3 for Win x64 no. I have not tested, but I read newer drivers may not work. If you think there is a virus or malware with this product, please submit your. Both components are combined into a single KMDF driver that communicates with the Microsoft-provided USB device emulation class extension UdeCx .

0 notes
Text
Database Security Market Shows Strong Growth with Leading Players
Database security market is expected to reach USD of 4.07 Billion in the forecast period of 2020 to 2027 Database security is an aggregate measure which is being utilized with respect to protect the database and information from the unlawful use, threats and attacks. It is made up of all or either software, physical control and administrative controls. Rise in the demand for sophisticated security solutions, growing regulation regarding breaches, and attacks and transmission of cloud based applications & services are the some of the driving factors in the database security market.
Major Market Competitors: Global Database Security Market
Renowned players in the global database security market are Mcafee, Oracle, Thales E-Security, IBM, IRI, HP, Hexatier, Fortinet, Trustwave, Protegrity, Imperva, Informatica, Micro Focus, Safenet, Porticor, Green SQL, Informatica, Axis Technology and Gemalto among others.

Download exclusive PDF sample report@ https://www.databridgemarketresearch.com/request-a-sample/?dbmr=global-database-security-market
For instance, According to Trustwave Holdings, Inc., in 2016, median number of days from an intrusion to detection of a compromise came up to 49 days, as compared to 2015 which was 80.5 days. In 2016, regulation named as General Data Protection Regulation (GDPR), which was officially adopted in April 2016, and will be enforced from May, 2018. Due to this act, companies will spend more on information security to avoid fines for failure and to secure the business data.
Market Segmentation: Global Database Security Market
· The global database security market is segmented based on component, deployment model, business function, organization size, end user and geographical segments.
· Based on component, the global database security market is segmented into software and services. Software is sub segmented into data masking and redaction, database auditing and reporting, encryption and tokenization, access control management and others. Services are sub segmented into managed services and professional services.
· On the basis of deployment model, the global database security market is segmented into cloud and on-premises.
· On the basis of business function, the global database security market is segmented into sales, marketing, operations, finance and others.
· On the basis of organization size, the global database security market is segmented into small and medium-sized enterprise and large enterprise.
· On the basis of end users, the global database security market is segmented into Banking, Financial Services, and Insurance, Telecommunications and IT, Manufacturing, Energy and Utilities, Retail and Ecommerce, Government and Defense, Healthcare and Life Sciences, Media and Entertainment and others.
Competitive Landscape: Global Database Security Market
The global database security market is consolidated due to the presence of limited number of players concentrated in few countries. These major players have adopted various organic as well as inorganic growth strategies such as mergers & acquisitions, new product launches, expansions, agreements, joint ventures, partnerships, and others to strengthen their position in this market.
Speak to Author @ https://www.databridgemarketresearch.com/speak-to-analyst/?dbmr=global-database-security-market
Major Market Drivers and Restraints:
· Increase in the volumes of business data across industries
· Development in the regulatory scenario
· Rise in the demand for sophisticated security solutions
· Growing need for protection against the ongoing attacks
· Propagation of cloud based applications and services
· High Cost with respect to installation and budget limitation
About Us:
Data Bridge Market Research set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge Market Research provides appropriate solutions to the complex business challenges and initiates an effortless decision-making process.
Contact:
Data Bridge Market Research
US: +1 888 387 2818
Related Reports:
Foldable Display Market
Free-to-Air (FTA) SErvice Market
#Database Security Market#Database Security#Database Security Market trends#Database Security Market industry#Database Security Market news#Database Security Market research
0 notes
Text
Ahnlab Online Security Personal
GYEONGGI-DO, South Korea--(BUSINESS WIRE)--AhnLab (http://global.ahnlab.com), a leading provider of integrated security service, today announced that US based Cornerstone Community Bank selected AhnLab Online Security Secure Browser (AOS Secure Browser), to prevent information leakage against hacking threats, and AhnLab Online Security Anti-Key Logger (AOS Anti-Key Logger), advanced anti key logging solution, to keep its internet banking environment from sophisticated security threats today.
AhnLab has partnered with SafeNet, a global leader in data protection, to ensure the authentication of US Cornerstone's internet banking users and transactions. SafeNet's eToken USB-based authenticators are integrated with AhnLab's AOS Security Secure Browser and AOS Anti-Key Logger. AhnLab selected SafeNet's eToken NG-FLASH Anywhere and eToken PRO Anywhere as they provide strong user authentication solutions that can be deployed on any Windows based platform without the need to install any client application, making it perfect for both consumer and partner authentication scenarios where the organization cannot control the user environment.
US Cornerstone Community Bank selected AhnLab's Secure Portable Browser, the joint solution between AhnLab and SafeNet, to authenticate its internet-banking users and the transactions. When a user plugs SafeNet's eToken, using Anywhere technology, the AOS Secure Browser runs automatically, without the need to install any client software. AhnLab's AOS Secure Browser, one of the world's strongest security browsers, protects the banking transaction session from security threats that include unknown memory hacking tools that allow access of only authorized functions/modules. The AOS Anti-Key Logger protects critical personal information - password, account number, credit card number, residence number, etc. - input through keyboard. It is applied to eToken's authentication session to protect the e-token authentication password from leaking by key logging.
The Federal Financial Institutions Examination Council (FFIEC) has been enforcing 'Internet Banking Supplementary Guide' since June in 2011 and AhnLab and SafeNet's Secure Portal Browser solution will help global financial institutions fulfill the guidelines for the financial services industry.
Download AhnLab V3 Internet Security for Windows to protect your PC against the latest security threats. Prevents compromise of personal sensitive data and blocks malicious Web sites for. AhnLab Online Security has not been installed properly. The registry or the system might be damaged. Solution: 1 Windows Vista/7. AhnLab Online Security is a program developed by AhnLab, Inc. The main program executable is aosremove.exe. The software installer includes 10 files and is usually about 991.93 KB (1,015,732 bytes). AhnLab Global Partner Program. Expand Your Business through AhnLab Partner Program. Security Center. Security Insight. Security Risk Level. Find the latest threat intelligences direct from AhnLab’s security experts. AhnLab Solutions.
'This is a good case that two world class security companies worked together to provide safer and more trusted internet banking environment,' said HongSun Kim, CEO of AhnLab. 'With this success story, AhnLab will focus its efforts on initiating the launch of its service in North America with strong partners.'


About AhnLab, Inc.
Headquartered in South-Korea, AhnLab Inc. (KR: 053800) develops industry-leading security solutions and provides professional services that are designed to secure and protect critical business and personal information. As a leading innovator in the information security arena since 1988, AhnLab's cutting edge products and services have been fulfilling the stringent security requirements of both enterprises and individual users. AhnLab's products and services include anti-virus solutions, network, mobile and online game security, security management and consulting services. Today, AhnLab boasts a network of sales and research operations in more than 20 countries worldwide.

inDefend Internet Security is a professional application designed to protect you against theft and loss of data.For onlinesecurity, parental control, USB & CD-DVD control & monitoring, website monitoring and file-folder encryption.
File Name:indefend-internet-security.exe
Author:Dataresolve Technologies(P)Ltd
License:Freeware (Free)
File Size:
Runs on:Windows XP, Vista, 2008, Vista64, 7, 7x64
The key to onlinesecurity in todayls world is a good password policy. Most of the Internet services such as webmail, ftp, pop3, etc require username / password authentication.They say that a chain is as strong as its weakest link. If you use a weak. ...
File Name:BlackBox-Password-Manager-setup.exe
Author:BestSecurityTips LLC
License:Freeware (Free)
File Size:2.2 Mb
Runs on:Win 98, 2000, 2003, ME, XP
Cerberus Security Guard is a software which guards against system attacks A tool to optimize your online activity (and not only) and ensure a safe and reliable Windows experience is pretty much requisite. Cerberus Security Guard is such a program devoted to security challenges whose purpose is to keep your computer safe from attacks of Trojan horses, keyloggers, multiple interceptors, and other kinds of system hacks, including various types of spyware.
File Name:Cerberus-Security-Guard-setup.exe
Author:BestSecurityTips LLC
License:Freeware (Free)
File Size:839 Kb
Runs on:WinXP, Win Vista, Win Vista x64, Windows 7, Windows 7 x64, WinOther
Hi Security is a free-to-download antivirus solution protecting your smartphones, as well as any personal data stored on your devices, against all Android viruses, potential privacy threats and WiFi safety concerns.
File Name:Hi Security
Author:Hawk Internet Co., Limited
License:Freeware (Free)
File Size:7.62 Mb
Runs on:Android
FEATURES * ZoneAlarm® ForceFieldO ZA exclusive Browser Security blocks Internet threats that target your browser, shielding you from identity thieves and more. more info * Operating System Firewall ZA exclusive OSFirewallO monitors installation,. ...
File Name:ZASPSetup_80_298_000_en.exe
Author:Check Point SoftwareTechnologies Ltd.
License:Freeware (Free)
File Size:76.4 Mb
Runs on:Win Vista, XP
The Gadgetbar Toolbar helps protect your computer with powerful anti-virus & internet security scans, tune ups, PC fixes, firewall attack tracking, email protection and more. It doesn't spy on browsing habits or launch pop-up or pop-under ads.
File Name:Gadgetbar.xpi
Author:I.G. Headquarters
License:Freeware (Free)
File Size:332 Kb
Runs on:Win95, Win98, WinME, WinNT 3.x, WinNT 4.x, WinXP, Windows2000, Windows2003, Windows Vista
The Gadgetbar Toolbar helps protect your computer with powerful anti-virus & internet security scans, tune ups, PC fixes, firewall attack tracking, email protection and more. It doesn't spy on browsing habits or launch pop-up or pop-under ads.
File Name:Gadgetbar.exe
Author:I.G. Headquarters
License:Freeware (Free)
File Size:862 Kb
Runs on:Win95, Win98, WinME, WinNT 3.x, WinNT 4.x, WinXP, Windows2000, Windows2003, Windows Vista
Virus Cleaner is a world-leading anti spy application. It is a world-class phone security solution for Android phones, as well as any personal data stored on your devices, against dangerous privacy threats, WiFi safety concerns, viruses, Trojans etc.
File Name:Virus Cleaner
Author:Hawk Internet Co., Limited
License:Freeware (Free)
File Size:10.9 Mb
Runs on:Android
Comodo SecureEmail protects your e-mail messages from being intercepted, read or altered on their way through the Internet. The confidential information from the sender cannot be stolen and the recipient is assured that the message is from the authen. ...
File Name:comodose.exe
Author:Comodo Group
License:Freeware (Free)
File Size:3.5 Mb
Runs on:WinXP, Windows Vista
CyberDefenderFREE offers rapid detection and protection against fast-moving Internet security threats. This all-free Internet security suite finds infections other security software misses, protecting against spyware, viruses, spam, and phishing.
File Name:CDFREE20.exe
Author:CyberDefender Corp
License:Freeware (Free)
File Size:11 Mb
Runs on:Windows
nginx (engine x) is a HTTP server and mail proxy server nginx (engine x) is a HTTP Server and mail proxy server written by me (Igor Sysoev).nginx has been running for more than four years on many heavily loaded Russian sites including Rambler (RamblerMedia.
File Name:nginx-0.8.14.zip
Author:Igor Sysoev
License:Freeware (Free)
File Size:747 Kb
Runs on:WinXP, Win2003
Online Banking Security browser toolbar for top web sites related to online banking security and online fraud prevention. For more info go to http://www.guardiananalytics.com for online banking security and online fraud detection products. Guardian. ...
File Name:online_banking_security.exe
Author:Guardian Analytics
License:Freeware (Free)
File Size:1.49 Mb
Runs on:Windows2000, WinXP, Windows2003, Windows Vista, Mac OS X, Mac OS X 10.1, Mac OS X 10.2, Mac OS X 10.3, Mac OS X 10.4, Mac OS X 10.5
Related:Ahnlab Online Security - Ahnlab Online Security Dowload - Ahnlab Online Security Cdkey - Ahnlab Online Security Maple - Ahnlab Oline Security
Ahnlab Online Security Download
Ahnlab Online Security Personal Banking
Pages : 1 | 2 | 3>
0 notes
Text
Capicom Mac Os

Capicom Mac Os 10.13
Capicom Mac Os Versions
Capicom Mac Os Mojave
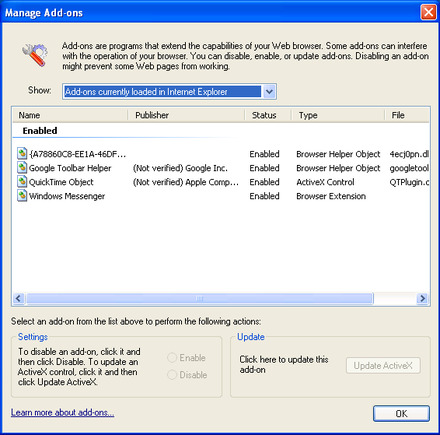
Capicom Mac Os 10.13
-->
The operating system: clos. A collection of utilities. The PKCS11 full compatible with Mozilla/Firefox. The repository for upgrades. The clauer manager for Firefox (from Firefox Tools menu). Binare package.deb for debian lenny Download now (, 656K) Binare package.deb for debian sid Download now (, 652K).
Jeonbuk salvage pride with consolation Shanghai SIPG win. Jeonbuk Hyundai Motors outclassed Shanghai SIPG with a 2-0 victory in the Asian Champions League on Friday, a result that helped the two. Download the latest driver for your token, install it with a few clicks. Choose the driver depending on your operating system. EPass 2003 Auto (MAC) New; ePass 2003 Auto (Linux) New; ePass 2003 Auto (Windows 32/64 Bit) New; eMudhra Watchdata (Windows) eMudhra Watchdata (Linux) Trust Key (Windows) Trust Key (Linux) Aladdin (Windows) eToken PKI (32-bit) eToken PKI (64-bit) ePass 2003 Auto (Windows 32/64 Bit) ePass 2003 Auto (Linux) ePass 2003 (Mac) Safenet (Windows 32/64. The 'classic' Mac OS is the original Macintosh operating system that was introduced in 1984 alongside the first Macintosh and remained in primary use on Macs until the introduction of Mac OS X in 2001.
(CAPICOM is a 32-bit only component that is available for use in the following operating systems: Windows Server 2008, Windows Vista, and Windows XP. Instead, use the .NET Framework to implement security features. For more information, see Alternatives to Using CAPICOM.)
This section includes scenarios that use CAPICOM procedures.
Note
Creating digital signatures and un-enveloping messages with CAPICOM is done using Public Key Infrastructure (PKI) cryptography and can only be done if the signer or user decrypting an enveloped message has access to a certificate with an available, associated private key. To decrypt an enveloped message, a certificate with access to the private key must be in the MY store.
Capicom Mac Os Versions
Task-based scenarios discussions and examples have been separated into the following sections:
Developer:
Microsoft
Description:
CAPICOM Module
Rating:
You are running: Windows XP
DLL file found in our DLL database.
The update date of the dll database: 13 Jan 2021
special offer

See more information about Outbyte and unistall instrustions. Please review Outbyte EULA and Privacy Policy
Capicom Mac Os Mojave
Click “Download Now” to get the PC tool that comes with the capicom.dll. The utility will automatically determine missing dlls and offer to install them automatically. Being an easy-to-use utility, it is is a great alternative to manual installation, which has been recognized by many computer experts and computer magazines. Limitations: trial version offers an unlimited number of scans, backup, restore of your windows registry for FREE. Full version must be purchased. It supports such operating systems as Windows 10, Windows 8 / 8.1, Windows 7 and Windows Vista (64/32 bit). File Size: 3.04 MB, Download time: < 1 min. on DSL/ADSL/Cable
Since you decided to visit this page, chances are you’re either looking for capicom.dll file, or a way to fix the “capicom.dll is missing” error. Look through the information below, which explains how to resolve your issue. On this page, you can download the capicom.dll file as well.

0 notes
Text
EV Code Signing Token
EV Code Signing Token
Unknown Publisher Warning To prevent security warning messages as shown above during the installation process of my CISSP test engine, WUSON Practice Field (WPF), I placed an EV Code Signing Certificate order to Sectigo on July 23 and received the EV Code Signing Token today, Aug. 12. The token model is SafeNet eToken 5110 CC (940), compliant with CC EAL5+ / PP QSCD. Installing the SafeNet…

View On WordPress
0 notes
Text
Database Security Market Dynamic Outlook and Influencing Key Growth
Database security market is expected to reach USD of 4.07 Billion in the forecast period of 2020 to 2027 Database security is an aggregate measure which is being utilized with respect to protect the database and information from the unlawful use, threats and attacks. It is made up of all or either software, physical control and administrative controls. Rise in the demand for sophisticated security solutions, growing regulation regarding breaches, and attacks and transmission of cloud based applications & services are the some of the driving factors in the database security market.
Major Market Competitors: Global Database Security Market
Renowned players in the global database security market are Mcafee, Oracle, Thales E-Security, IBM, IRI, HP, Hexatier, Fortinet, Trustwave, Protegrity, Imperva, Informatica, Micro Focus, Safenet, Porticor, Green SQL, Informatica, Axis Technology and Gemalto among others.

Download exclusive PDF sample report@ https://www.databridgemarketresearch.com/request-a-sample/?dbmr=global-database-security-market
For instance, According to Trustwave Holdings, Inc., in 2016, median number of days from an intrusion to detection of a compromise came up to 49 days, as compared to 2015 which was 80.5 days. In 2016, regulation named as General Data Protection Regulation (GDPR), which was officially adopted in April 2016, and will be enforced from May, 2018. Due to this act, companies will spend more on information security to avoid fines for failure and to secure the business data.
Market Segmentation: Global Database Security Market
· The global database security market is segmented based on component, deployment model, business function, organization size, end user and geographical segments.
· Based on component, the global database security market is segmented into software and services. Software is sub segmented into data masking and redaction, database auditing and reporting, encryption and tokenization, access control management and others. Services are sub segmented into managed services and professional services.
· On the basis of deployment model, the global database security market is segmented into cloud and on-premises.
· On the basis of business function, the global database security market is segmented into sales, marketing, operations, finance and others.
· On the basis of organization size, the global database security market is segmented into small and medium-sized enterprise and large enterprise.
· On the basis of end users, the global database security market is segmented into Banking, Financial Services, and Insurance, Telecommunications and IT, Manufacturing, Energy and Utilities, Retail and Ecommerce, Government and Defense, Healthcare and Life Sciences, Media and Entertainment and others.
Competitive Landscape: Global Database Security Market
The global database security market is consolidated due to the presence of limited number of players concentrated in few countries. These major players have adopted various organic as well as inorganic growth strategies such as mergers & acquisitions, new product launches, expansions, agreements, joint ventures, partnerships, and others to strengthen their position in this market.
Speak to Author @ https://www.databridgemarketresearch.com/speak-to-analyst/?dbmr=global-database-security-market
Major Market Drivers and Restraints:
· Increase in the volumes of business data across industries
· Development in the regulatory scenario
· Rise in the demand for sophisticated security solutions
· Growing need for protection against the ongoing attacks
· Propagation of cloud based applications and services
· High Cost with respect to installation and budget limitation
About Us:
Data Bridge Market Research set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge Market Research provides appropriate solutions to the complex business challenges and initiates an effortless decision-making process.
Contact:
Data Bridge Market Research
US: +1 888 387 2818
Related Reports:
Foldable Display Market
Free-to-Air (FTA) SErvice Market
#Database Security Market#Database Security#Database Security Market Trends#Database Security Market Industry#Database Security Market News#Database Security Market Research#Database Security Market Analysis
0 notes
Text
Database Security Market to Exhibit Impressive Growth during 2020-2027
Database security market is expected to reach USD of 4.07 Billion in the forecast period of 2020 to 2027 Database security is an aggregate measure which is being utilized with respect to protect the database and information from the unlawful use, threats and attacks. It is made up of all or either software, physical control and administrative controls. Rise in the demand for sophisticated security solutions, growing regulation regarding breaches, and attacks and transmission of cloud based applications & services are the some of the driving factors in the database security market.
Major Market Competitors: Global Database Security Market
Renowned players in the global database security market are Mcafee, Oracle, Thales E-Security, IBM, IRI, HP, Hexatier, Fortinet, Trustwave, Protegrity, Imperva, Informatica, Micro Focus, Safenet, Porticor, Green SQL, Informatica, Axis Technology and Gemalto among others.

Download exclusive PDF sample report@ https://www.databridgemarketresearch.com/request-a-sample/?dbmr=global-database-security-market
For instance, According to Trustwave Holdings, Inc., in 2016, median number of days from an intrusion to detection of a compromise came up to 49 days, as compared to 2015 which was 80.5 days. In 2016, regulation named as General Data Protection Regulation (GDPR), which was officially adopted in April 2016, and will be enforced from May, 2018. Due to this act, companies will spend more on information security to avoid fines for failure and to secure the business data.
Market Segmentation: Global Database Security Market
· The global database security market is segmented based on component, deployment model, business function, organization size, end user and geographical segments.
· Based on component, the global database security market is segmented into software and services. Software is sub segmented into data masking and redaction, database auditing and reporting, encryption and tokenization, access control management and others. Services are sub segmented into managed services and professional services.
· On the basis of deployment model, the global database security market is segmented into cloud and on-premises.
· On the basis of business function, the global database security market is segmented into sales, marketing, operations, finance and others.
· On the basis of organization size, the global database security market is segmented into small and medium-sized enterprise and large enterprise.
· On the basis of end users, the global database security market is segmented into Banking, Financial Services, and Insurance, Telecommunications and IT, Manufacturing, Energy and Utilities, Retail and Ecommerce, Government and Defense, Healthcare and Life Sciences, Media and Entertainment and others.
Competitive Landscape: Global Database Security Market
The global database security market is consolidated due to the presence of limited number of players concentrated in few countries. These major players have adopted various organic as well as inorganic growth strategies such as mergers & acquisitions, new product launches, expansions, agreements, joint ventures, partnerships, and others to strengthen their position in this market.
Speak to Author @ https://www.databridgemarketresearch.com/speak-to-analyst/?dbmr=global-database-security-market
Major Market Drivers and Restraints:
· Increase in the volumes of business data across industries
· Development in the regulatory scenario
· Rise in the demand for sophisticated security solutions
· Growing need for protection against the ongoing attacks
· Propagation of cloud based applications and services
· High Cost with respect to installation and budget limitation
About Us:
Data Bridge Market Research set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge Market Research provides appropriate solutions to the complex business challenges and initiates an effortless decision-making process.
Contact:
Data Bridge Market Research
US: +1 888 387 2818
Related Reports:
Foldable Display Market
Free-to-Air (FTA) SErvice Market
#Database Security Market#Database Security#Database Security Market Trends#Database Security Market Industry#Database Security Market news#Database Security Market Research#Database Security Market Analysis
0 notes
Text
What method can I apply to use HrOneStop ATT?
About HrOneStop ATT Login
For the people curious about AT&T, which is improbable, it is a combination situated in the USA. It is by a long shot the greatest media transmission organization and has a few branches universally. In the US, it is the main supplier of fixed telephone utilities and cell phone administrations.
Each and every year, AT&T has a typical employee base of around 300,000 individuals. In this high-speed computerized world, the web runs pretty much every part of our lives. Hence, AT&T considered it fit to make a HrOneStop ATT Login portal for its staff members.
This portal serves both the current and previous employees of the organization. They can get to data that they need whenever and anyplace.
AT&T sent off the HrOneStop ATT Login to empower its employees to get a simpler time working for the organization. It serves the ongoing employees as well as the previous ones. They can rapidly get moment updates and warnings about their jobs and circle back to compensation. Different insights about their jobs are additionally accessible on the portal.
Once recruited at the organization, you are given your remarkable HrOneStop ATT Login qualifications. Then, check your work profile and different insights concerning your job right from this intuitive HrOneStop ATT Login portal.
Step by step instructions to Utilize the HrOneStop ATT Login
It is basic and direct to Utilize this portal. Simply follow this bit-by-bit guide:
Visit hronestop att
Raise a ruckus around town button.
Enter your username and password to enter.
Also, actually that basic, you're currently in the HrOneStop ATT Login portal, prepared to get to various administrations. Note that you can utilize tokens instead to sign in to the portal. To use this technique, you really want the necessary equipment. Then use the mystery key on the pass to sign in. Great tokens to utilize include:
MTIPS token.
SAFENet token.
RSA SecurID token.
What You Want for the HrOneStop ATT Login
There aren't any exceptional prerequisites to get to the HrOneStop ATT Login portal. All that you require is the accompanying:
A cell phone, tablet, PC, or PC.
A steady web association.
Your username and password.
It would similarly be better on the off chance that you had a worldwide login password.
Benefits of Utilizing the HrOneStop ATT Login Portal
You stand to acquire a ton by simply utilizing the hr one stop ATT Login portal. It makes your life as an employee much simpler and smoother. The HR or administrative officer will concede you the login qualifications as an employee. This is frequently at the time the organization recruits you.
From that point onward, staff can utilize these accreditations to get to the HrOneStop ATT Login and deal with their work profiles. There are a few benefits to appreciate, including:
Get moment alarms and warnings from the organization. Any new data the organization should hand off to its staff is accessible on the HrOneStop ATT Login portal.
Update your own data through the HrOneStop ATT Login portal.
Control your work profile and update it online without visiting any administrative office.
Demand any progressions in your shift.
You are seeing the program and plan for getting work done or scheduling for more straightforward preparation.
Requesting for a vacation or leave and circling back to the situation with that application.
HrOneStop ATT Login Password Reset
It doesn't suggest that you will altogether be kept out of your account assuming you have failed to remember your password. Here is a portion of the manners in which that you can use to reset your password:
As a functioning employee of AT&T, you can contact your administrative officer or HR and solicitation that they reset your HrOneStop ATT Login qualifications.
Be that as it may, assuming you're a previous employee of the organization and have forgotten your username and password, follow these moves toward resetting them:
First, visit the HrOneStop ATT Login page.
Then, click on forgot username or password.
You will then be provoked to enter in your subtleties. The necessary data incorporates your most memorable name, last name, email address, date of birth, versatile number, and government-backed retirement number.
After that, you can finish the 'captcha' and present your solicitation to recover your account.
1 note
·
View note