#Schools remain key targets for hackers
Text
Last week, WIRED published a deep-dive investigation into Trickbot, the prolific Russian ransomware gang. This week, US and UK authorities sanctioned 11 alleged members of Trickbot and its related group, Conti, including Maksim Galochkin, aka Bentley, one of the alleged members whose real-world identity we confirmed through our investigation. Coincidence? Maybe. Either way, it's a big deal.
In addition to the US and UK sanctions, the US Justice Department also unsealed indictments filed in three US federal courts against Galochkin and eight other alleged Trickbot members for ransomware attacks against entities in Ohio, Tennessee, and California. Because everyone charged is a Russian national, however, it is unlikely they will ever be arrested or face trial.
While Russian cybercriminals typically enjoy immunity, the same may not remain true for the country’s military hackers. The lead prosecutor of the International Criminal Court (ICC) says the ICC will begin pursuing charges for cyber war crimes. The prosecutor, Karim Khan, did not name Russia, but the move follows a formal petition from the Human Rights Center at UC Berkeley’s School of Law asking the ICC to prosecute Russia’s Sandworm hackers for war crimes. Part of Russia’s GRU military intelligence agency, Sandworm is responsible for causing blackouts in Ukraine, the only known instances of cyberattacks shutting down an electrical grid. Sandworm also released the NotPetya malware against Ukraine, which ultimately spread globally and caused an unprecedented $10 billion in damages worldwide.
Russia is far from the only country that engages in offensive cyberwar tactics. China-backed hackers have repeatedly targeted the US and other countries, and they may be getting some help finding unpatched vulnerabilities. A Chinese law passed in 2022 demands that any network technology company operating in the country share details about vulnerabilities in its products with the Chinese government within two days of their discovery. Information about these vulnerabilities may then be shared with China’s hackers. It’s unclear how many Western companies comply with the law or provide enough information to allow Chinese hackers to exploit the products’ flaws.
Speaking of Chinese hackers, Microsoft this week finally explained how China’s state-sponsored hackers managed to steal a cryptographic key that allowed the attackers to successfully access the Outlook email accounts of at least 25 organizations, including US government agencies. According to Microsoft, the hackers broke into the account of a company engineer using token-stealing malware. They then used that account to access a cache of crash data that accidentally contained the signing key they then stole and used to go on an Outlook hacking spree. None of this was supposed to be possible, and Microsoft says it has corrected several flaws in its systems that allowed the attack to happen.
Before he died in a mysterious plane crash last month following an attempted coup against Russian president Vladimir Putin, Yevgeny Prigozhin wasn’t just the leader of the Wagner Group mercenaries. He was also the head of the notorious Internet Research Agency (IRA), a Russian outfit responsible for widespread disinformation campaigns. While the IRA was reportedly shut down, new research shows that pro-Prigozhin trolls continue to push his agenda. Many of the accounts spreading disinformation on X (formerly Twitter) have been banned. But since when has that stopped them?
Elsewhere, we explained how prompt injection attacks against generative AI chatbots like ChatGPT take advantage of a flaw that’s difficult to fix. We detailed how hard it is to opt out of allowing Facebook to use your data to train its AI. We have a rundown on Proton Sentinel, a suite of tools that are similar to Google’s offerings but with a strong emphasis on privacy and security. We also co-published a story with The Markup into Axon’s quest to build Taser-armed drones. And we got the inside scoop on a meeting between top US spies and civil liberties groups over Section 702 of the Foreign Surveillance Intelligence Act, which is set to expire at the end of the year.
But that’s not all. Each week, we round up the security and privacy news we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
Your New Car Is a Privacy Nightmare
Car companies are collecting and selling extremely detailed personal data from drivers who have no real way to opt out, a new report from the Mozilla Foundation found. Researchers spent hundreds of hours studying 25 privacy policies for major car brands and found that none of them met the foundation’s minimum standards around privacy and security.
According to the report, modern cars, stuffed to the roof with sensors, collect more information about you than just about any other product in your life. They know where you go, what you say, and how you move your body. Nissan’s privacy policy, for example, allows the company to collect and share drivers’ sexual activity, health diagnosis data, and genetic information, according to the report.
Eighty-four percent of the brands that researchers studied share or sell this kind of personal data, and only two of them allow drivers to have their data deleted. While it is unclear exactly who these companies share or sell data to, the report points out that there is a huge market for driver data. An automotive data broker called High Mobility cited in the report has a partnership with nine of the car brands Mozilla studied. On its website, it advertises a wide range of data products—including precise location data.
This isn’t just a privacy nightmare but a security one. Volkswagen, Toyota, and Mercedes-Benz have all recently suffered data leaks or breaches that affected millions of customers. According to Mozilla, cars are the worst category of products for privacy that they have ever reviewed.
Update Your iPhone: Apple Fixes No-Click Zero-Days
Apple has just released a security update to iOS after researchers at Citizen Lab discovered a zero-click vulnerability being used to deliver Pegasus spyware. Citizen Lab, which is part of the University of Toronto, is calling the newly discovered exploit chain Blastpass. Researchers say it is capable of compromising iPhones running the latest version of iOS (16.6) without the target even touching their device. According to researchers, Blastpass is delivered to a victim’s phone through an iMessage with an Apple Wallet attachment containing a malicious image.
The Pegasus spyware, developed by NSO Group, enables an attacker to read a target’s text messages, view their photos, and listen to calls. It has been used to track journalists, political dissidents, and human rights activists around the world.
Apple says customers should update their phones to the newly released iOS 16.6.1. The exploit can also attack certain models of iPads. You can see details of the affected models here. Citizen Lab urges at-risk users to enable Lockdown Mode.
North Korean Hackers Target Security Researchers Again
North Korea-backed hackers are targeting cybersecurity researchers in a new campaign that is exploiting at least one zero-day vulnerability, Google’s Threat Analysis Group (TAG) warned in a report released Thursday. The group did not provide details about the vulnerability since it is currently unpatched. However, the company says it is part of a popular software package used by security researchers.
According to TAG, the current attack mirrors a January 2021 campaign that similarly targeted security researchers working on vulnerability research and development. Like the previous campaign, North Korean threat actors send researchers malicious files after first spending weeks establishing a relationship with their target. According to the report, the malicious file will execute “a series of anti-virtual machine checks” and send collected information—along with a screenshot—back to the attacker.
Georgia DA in Trump RICO Case Gets Doxxed
In order to shield prospective jurors from harassment, District Attorney Fani Willis asked the judge in Donald Trump’s racketeering trial to prevent people from capturing or distributing any sort of image or identifying information about them. The motion, filed in Fulton County Superior Court on Wednesday, revealed that immediately after the indictment was filed, anonymous individuals on “conspiracy theory websites" had shared the full names, ages, and addresses of 23 grand jurors with “the intent to harass and intimidate them.”
Willis also revealed that she had been the victim of doxxing when the personal information of her and her family—including their physical addresses and “GPS coordinates”—was posted on an unnamed website hosted by a Russian company. Willis, who is Black, had previously disclosed that she faced racist and violent threats after the announcement of her investigation into the former president.
18 notes
·
View notes
Text
Schools remain key targets for hackers, US intelligence officials say
Schools remain key targets for hackers, US intelligence officials say
In a joint cyber security bulletin issued Thursday by the FBI, DHS and a consortium that monitors nationwide online threats, officials said hackers are “targeting kindergarten through twelfth grade (K-12) educational institutions, leading to ransomware attacks, the theft of data, and the disruption of distance learning services.”
The bulletin noted that hackers targeting schools have disrupted…

View On WordPress
0 notes
Text
Wednesday, May 12, 2021
WHO Announces Virus “Plateau”
(Foreign Policy) Countries across Europe are beginning to reopen after months of restrictions. U.S. President Joe Biden has endorsed a proposal to waive patents on COVID-19 vaccines, paving the way for accelerated production. But rather than achieving herd immunity, the world appears to be entering a new phase of the coronavirus pandemic, with more contagious variants spreading rapidly in places without stringent regulations or sufficient vaccines. In a Monday briefing, the World Health Organization (WHO) said the world had reached a plateau in new cases and deaths from the coronavirus, with numbers declining overall in most regions. WHO Director-General Tedros Adhanom Ghebreyesus acknowledged that the plateau was “unacceptably high.” Nearly 90,000 COVID-19 deaths were recorded worldwide last week. Thousands of those deaths occurred in India, where new cases and deaths have remained near record daily highs for days—and are still likely undercounted. Meanwhile, Malaysia announced a new lockdown on Monday amid a third wave driven in part by more infectious variants. Cases are rising elsewhere in South and Southeast Asia, as well as in Latin America—with potential consequences for political leaders.
Election reform controversy
(Reuters) Democrats in the U.S. Senate hope today to advance sweeping election reform legislation making it easier for Americans to cast ballots, despite intense opposition from Republicans, many of whom support new restrictive voting rules at the state level. The 886-page bill would expand mail-in voting that was used widely in last year’s presidential election because of the coronavirus pandemic and would lengthen the hours of in-person balloting.
California expands drought emergency to large swath of state
(AP) California Gov. Gavin Newsom on Monday expanded a drought emergency to a large swath of the nation’s most populous state while seeking more than $6 billion in multiyear water spending as one of the warmest, driest springs on record threatens another severe wildfire season across the American West. His emergency declaration now includes 41 of 58 counties, covering 30% of California’s nearly 40 million people, and he said a further expansion is likely as conditions worsen. The U.S. Drought Monitor shows most of the state and the American West is in extensive drought just a few years after California emerged from the last punishing multiyear dry spell. “We’re staring down at what could be disastrous summer and fall, with the potential of communities running out water, and fires,” said Democratic U.S. Rep. Jim Costa.
DarkSide Admits Hack
(1440) Officials from the FBI confirmed yesterday a cyberattack that shut down one of the nation’s biggest gas pipelines was carried out by a cybercriminal outfit known as DarkSide. The group, based in Eastern Europe, is believed to develop, use, and sell ransomware—malicious software capable of locking IT systems until payment is made. Colonial Pipeline, which supplies an estimated 45% of the East Coast’s gasoline, shut down its network as a proactive measure after being hit with the attack late last week. In a twist, DarkSide representatives said they didn’t mean to create problems, but rather to simply “make some money.” The group, which claims to have an ethical code, represents an emerging phenomenon of hackers operating as enterprises—DarkSide even reportedly has a call-in number and help desk for its victims. It’s unclear whether the company paid the ransom; service is expected to be restored by next week. (AP) Meanwhile, more than 1,000 gas stations in the Southeast reported running out of fuel, primarily because of what analysts say is unwarranted panic-buying among drivers, as the shutdown of a major pipeline by a gang of hackers entered its fifth day Tuesday.
Central American leaders resisting Biden’s anti-corruption efforts
(Washington Post) In a rebuff to the Biden administration, political leaders in El Salvador and Guatemala have forced out several senior judges known for their independence and anti-corruption zeal, underscoring the difficulties facing Washington’s new Central America policy. President Biden has put the fight against corruption at the heart of that policy. U.S. officials argue that graft is stunting Central American economies and driving citizens to attempt to migrate to the United States. The sidelining of the judges has raised concerns at the highest levels of the U.S. government. The administration is readying measures to increase pressure on El Salvador, Guatemala and Honduras, known as the Northern Triangle countries—including a name-and-shame list of corrupt politicians who would be denied U.S. visas. The efforts come as human rights groups warn of democratic backsliding in Central America, where the judiciary had emerged as a key check on presidential power.
Paris Teenager’s New Gig: Would-Be Queen of Italy. A Nation Shrugs.
(NYT) Vittorio Emanuele di Savoia, the son of the last king of Italy, gave his granddaughter a big 16th birthday present. In a formal 2019 decree, the “Duke of Savoy, Prince of Naples and by the grace of God direct heir to Head of the Royal House of Savoy,” amended a medieval law that for centuries had restricted succession in his royal line to male heirs. He bumped “our beloved granddaughter” Vittoria Cristina Chiara Adelaide Maria up the royal food chain, making her the first woman in 1,000 years to be invested with the authority to eventually lead the family and stake a claim to the defunct monarchy. “It was the best gift he could give me,” Vittoria, now 17 and a burgeoning Instagram influencer, said from her Paris home. But the gift didn’t include a crown. Italy is a republic, having abolished the monarchy 75 years ago for its disastrous support of Mussolini, and Italians have approximately zero interest in a royal restoration. “Never say never,” said Vittoria’s father, Emanuele Filiberto, an Italian television personality who claims the title Prince of Venice, which is also the name of his Los Angeles restaurant and former food truck. (“We do a lot of film premieres. We did Jumanji,” he said.) Obviously, he said, the monarchy wasn’t returning “tomorrow,” but he had no sons and the family needed a head of the royal household to run its historic orders.
Russian governor: School shooting in Kazan kills 7 students
(AP) A school shooting erupted Tuesday morning in the Russian city of Kazan, killing seven students and leaving 16 other people hospitalized with wounds, a Russian governor reported. Rustam Minnikhanov, governor of the Tatarstan republic which has Kazan as its capital, said Tuesday that four male and three female eighth-grade students have died in the shooting. Twelve more children and four adults were hospitalized in the attack, Minnikhanov said. The shooter was 19. Kazan is roughly 700 kilometers (430 miles) east of Moscow.
Deadly ‘black fungus’ cases add to India’s covid crisis
(Washington Post) As coronavirus cases and deaths soared in India recently, doctors began to notice another disturbing trend. Some covid-19 patients who had been released from hospitals were coming back with different symptoms, including sinus pain, blurred vision, black and bloody nasal discharge and a dark discoloration around the nose. The culprit was a deadly fungal infection called mucormycosis that physicians say is increasingly preying on people with immune systems weakened by covid-19 and the steroids used to treat it. Though cases of the black fungus remain rare, its lethality and increasing prevalence have prompted government warnings, put doctors on high alert and added to the country’s health crisis. “The death rate from mucormycosis is 50 percent,” said Amarinder Singh Malhi from All India Institute Of Medical Science, a public hospital in New Delhi. “The death rate from covid is 2.5 percent. So we have to use these steroids very cautiously.”
100 days in power, Myanmar junta holds pretense of control
(AP) After Myanmar’s military seized power by ousting the elected government of Aung San Suu Kyi, they couldn’t even make the trains run on time: State railway workers were among the earliest organized opponents of the February takeover, and they went on strike. Health workers who founded the civil disobedience movement against military rule stopped staffing government medical facilities. Many civil servants were no-shows at work, along with employees of government and private banks. Universities became hotbeds of resistance, and in recent weeks, education at the primary and secondary levels has begun to collapse as teachers, students and parents boycott state schools. One hundred days after their takeover, Myanmar’s ruling generals maintain just the pretense of control. The illusion is sustained mainly by its partially successful efforts to shut down independent media and to keep the streets clear of large demonstrations by employing lethal force. More than 750 protesters and bystanders have been killed by security forces, according to detailed independent tallies. Meanwhile, the junta also faces a growing military challenge in the always restive border regions where ethnic minority groups exercise political power and maintain guerrilla armies. Two of the more battle-hardened groups, the Kachin in the north and the Karen in the east, have declared their support for the protest movement and stepped up their fighting, despite the government military, known as the Tatmadaw, hitting back with greater firepower, including airstrikes.
China Targets Muslim Women in Push to Suppress Births in Xinjiang
(NYT) When China’s government ordered women in her mostly Muslim community in the region of Xinjiang to be fitted with contraceptive devices, Qelbinur Sedik pleaded for an exemption. She was nearly 50 years old, she told officials. She had obeyed the government’s birth limits and had only one child. It was no use. The workers threatened to take her to the police if she continued resisting, she said. She gave in and went to a government clinic where a doctor, using metal forceps, inserted an intrauterine device to prevent pregnancy. She wept through the procedure. Across much of China, the authorities are encouraging women to have more children, as they try to stave off a demographic crisis from a declining birthrate. But in the Xinjiang region, China is forcing them to have fewer, tightening its grip on Muslim ethnic minorities and trying to orchestrate a demographic shift that will diminish their population growth. It is part of a vast and repressive social re-engineering campaign by a Communist Party determined to eliminate any perceived challenge to its rule, in this case, ethnic separatism.
35 killed in Gaza, 3 in Israel, as violence escalates
(Reuters) Hostilities between Israel and Hamas escalated overnight, with 35 Palestinians killed in Gaza and three in Israel in the most intensive aerial exchanges for years. Israel carried out hundreds of air strikes in Gaza into the early hours of Wednesday, as the Islamist group and other Palestinian militant groups fired multiple rocket barrages at Tel Aviv and Beersheba. One multi-story residential building in Gaza collapsed and another was heavily damaged after they were repeatedly hit by Israeli air strikes. It was the heaviest offensive between Israel and Hamas since a 2014 war in Gaza, and prompted international concern that the situation could spiral out of control. U.N. Middle East peace envoy Tor Wennesland tweeted: “Stop the fire immediately. We’re escalating towards a full scale war. Leaders on all sides have to take the responsibility of de-escalation. The cost of war in Gaza is devastating & is being paid by ordinary people. UN is working w/ all sides to restore calm. Stop the violence now,” he wrote.
Israelis, Palestinians and Their Neighbors Worry
(NYT) Let’s see, what happens when TikTok meets Palestinian grievances about right-wing Israeli land grabs in Arab neighborhoods in Jerusalem? And then you add the holiest Muslim night of prayer in Jerusalem into the mix? Then toss in the most emotional Israeli holiday in Jerusalem? And a power play by Hamas to assume leadership of the Palestinian cause? And, finally, a political vacuum in which the Palestinian Authority is incapable of holding new elections and Israel is so divided it can’t stop having elections? What happens is the explosion of violence around Jerusalem on Monday that quickly spread to the Gaza front, and has people asking: Is this the big one? Is this the start of the next Palestinian uprising? The Israeli government, the surrounding Arab nations and the Palestinian Authority all desperately want the answer to be “no”—Israel because it would find little support from a left-leaning White House, let alone the rest of the world, for a big crackdown on Palestinians; the Arab governments because most of them want to do business with Israeli tech-makers, not get mired defending Palestinian rock-throwers; and the Palestinian leadership because it would expose just how little it controls the Palestinian street anymore. But unlike the Intifadas that began in 1987 and 2000, when Israel had someone to call to try to turn it off, there is no Palestinian on the other end of the phone this time—or, if there is, he’s a 15-year-old on his smartphone, swiping orders and inspiration from TikTok, the video app often used by young Palestinians to challenge and encourage one another to confront Israelis.
At least 1m people facing starvation as Madagascar’s drought worsens
(Guardian) Madagascar’s worst drought in 40 years has left more than a million people facing a year of desperate food shortages. The south saw 50% of its usual rains during the October planting season, in a fourth year of drought. According to the Famine Early Warning System Network, most poor families have to rely on foraging for wild foods and leaves that are difficult to eat and can be dangerous for children and pregnant women. Aid agencies have reported people eating termites and mixing clay with tamarind.
1 note
·
View note
Link
In times like these it becomes all the more important to remember that tools like Zoom, Slack, and Facebook Messenger are not benign public services, and while the sentiment they've expressed to the global community in responding to the crisis may be sincere, it hasn't addressed the fundamental ethical issues with any piece of proprietary software.
After taking the LibrePlanet 2020 conference online, we received a number of requests asking us to document our streaming setup. As the pandemic grew worse, this gave way to more curiosity about how the Free Software Foundation (FSF) uses free tools and free communication platforms to conduct our everyday business. And while the stereotype of hackers hunched over a white on black terminal session applies to us in some ways, many of the tools we use are available in any environment, even for people who do not have a lot of technical experience. We've started documenting ethical solutions on the LibrePlanet wiki, in addition to starting a remote communication mailing list to help each other advocate for their use.
In the suggestions that follow, a few of the tools we will recommend depend upon some "self-reliance," that is, steering clear of proprietary network services by hosting free software solutions yourself, or asking a technical friend to do it for you. It's a difficult step, and the benefits may not be immediately obvious, but it's a key part of preserving your autonomy in an age of ubiquitous digital control.
To those who have the technical expertise and available infrastructure, we urge you to consider hosting instances of free communication platforms for your friends, family, and your community at large. For example, with a modest server and some GNU/Linux knowledge, you could help local students learn in freedom by volunteering to administer an instance of one of the programs we'll be recommending below.
The need to self-host can be an uncomfortable reminder of our dependence on the "cloud" -- the network of someone else's computers -- but acknowledging our current reliance on these providers is the first step in making new, dependable systems for ourselves. During dangerous and stressful times, it's tempting to sideline our ethical commitments for easier or more convenient ways to get things done, and software freedom is no exception. We hope these suggestions will inspire you to inform others about the importance of their freedom, privacy, and security.
Chat
When we can no longer communicate face-to-face, tools for voice and video calling often come to mind as the next best thing. But as evidenced by the size and success of the proprietary software companies that sponsor these tools, their development isn't easy. Promoting real-time voice and video chat clients remains a High Priority Project of ours. Though we may still be waiting for a truly perfect solution, there are some projects that are far enough along in their development that we can recommend them to others.
Audio calls
Mumble: Mumble is a real-time, low latency program for hosting and joining audio conversations. Clients are available for every major operating system, and even large rooms tend not to put too much stress on the network. When it was time for us to go fully remote, the FSF staff turned to Mumble as a way to have that "in-office" feel, staying in touch in rooms dedicated to each of our teams and a general purpose "water cooler" room.
Asterisk/SIP: When we give tours of the FSF office, people often think we're joking when we mention that even the FSF's conference phones run free software. But through Asterisk and our use of the SIP protocol, it's entirely true. Although it can be difficult to set up, it's worth mentioning that free software can manage your traditional phone lines. At the FSF, we transfer calls to digital extensions seamlessly with tools like Jami and Linphone.
Video calls and presentations
Jitsi: Jitsi was a key part of LibrePlanet 2020's success. Providing video and voice calls through the browser via WebRTC, it also allows for presenters to share their screen in a similar way to Zoom. And unlike Zoom, it doesn't come with serious privacy violations or threats to user freedom. The connection between callers is direct and intuitive, but a central server is still required to coordinate callers and rooms. Some of these, like the Jitsi project's own "Jitsi Meet" server, recommend proprietary browser extensions and document sharing tools. If you're able, hosting your own instance is the most free and reliable method.
Jami: While it's used at the FSF primarily for its SIP support, Jami (previously GNU Ring) is a solid communication client in its own right, allowing for distributed video calls, text chat, and screen sharing.
OBS: Another much-used software program this LibrePlanet was OBS Studio. Illness, different timezones, or unforeseen travel were no match for the solutions that OBS Studio offered. It's a flexible tool for streaming video from multiple inputs to a Web source, whether that's combining your webcam with conference slides, or even your favorite free software game. At LibrePlanet, OBS allowed our remote speakers to record their presentations while speaking in one screen, and sharing audiovisual materials in a second window.
Text chat
XMPP: If you've ever used "Jabber," older iterations of Google Talk or Facebook Messenger, then you've used XMPP. XMPP is a flexible and extensible instant messaging protocol that's lately seen a resurgence from clients like Conversations.im and encryption schema like OMEMO. XMPP is the instant messaging method we prefer at the FSF when we need to discuss something privately, or in a secure group chat, as everything is sent through servers we control and encrypted against individual staff members' private key. Also, access to the FSF XMPP server is one of the many benefits of our associate membership program.
IRC: Messaging services have become all the rage in office atmospheres, but nothing about Messenger or Slack is new. In fact, Slack (and its counterpart for video games, Discord) takes more than a few cues from the venerable Internet Relay Chat (IRC). IRC remains an enduring way to have a text-based chat in real-time, and as evidenced by Web clients like The Lounge, or desktop clients like Pidgin, it can be as stripped down or feature-rich as you like. For a true hacker experience, you can also log into IRC using Emacs.
Long-form discussion
Encrypted email: While it's asynchronous and maybe the most "old school" item on our list, GPG-encrypted email is a core part of the FSF workflow, and helps guard against prying eyes, whether they're one room over or in an NSA compound across the country. The initial setup can sometimes be a challenge, which is why we provide the Email Self-Defense Guide to get you up and running.
Discourse: Discourse is the message board software that powers the FSF associate member forum, and we couldn't be happier to recommend it. While the concept may seem a little antiquated, message boards remain a good way to coordinate discussions on a particular topic. Discourse's moderation tools are intuitive and easy to use, and it even includes achievements for users to earn!
Document Sharing
If you're unused to working remotely, finding ways to collaborate with others on a document or presentation can be a challenge. At the FSF, Etherpad is the main tool that we use to keep live meeting notes and work together on other documents. It provides all the features you need for quick collaboration, including comments, revision tracking, and exports to a variety of formats. You can host your own instance, or you can select an instance made available by others and start sharing.
File Sharing
At the FSF office, we have a common server to store our files. Not everyone has the luxury of a setup like that, and especially not due to the fast changeover from office to home. To avoid using proprietary "solutions" and disservices like Dropbox, you can turn to the widely popular Nextcloud to synchronize your text and email messages, share calendars with coworkers, and exchange files privately with your friends.
If you need something temporary, there's always Up1. Up1 is a temporary, encrypted text and image sharing program you can host locally, making sure those files you need to exchange are only there for just as long as it takes for your friend to download them. And while we don't use it ourselves, we've heard good things about the Riseup network's instance of Up1, and will occasionally suggest it to those wanting a quick and easy way to share files while retaining their freedom.
Conclusion
This is just a small selection of the huge amount of free software out there, all ready to be used, shared, and improved by the community. For more suggestions on both local and Web-based programs, visit the FSF's Free Software Directory, our volunteer-run wiki which aims to be a comprehensive list of the thousands of free programs available for everyday use.
As always, free software is a moving target. We reap as much as the community puts into it, and as more and more attention shifts to the crisis caused by the novel coronavirus, the tools themselves are likely to see an increased amount of development. Please collaborate with us on the LibrePlanet wiki's entry on remote communication to help people find ways of communicating that put user freedom as a priority.
2 notes
·
View notes
Text
You have the right to remain encrypted

“You have the right to remain silent.” We’ve heard the Miranda warning countless times on TV, but what good is the right to remain silent if our own cellphones testify against us? Imagine every incriminating and embarrassing secret our devices hold in the hands of prosecutors, simply because you’ve been accused of a minor crime. This is the brave new world that Attorney General Bill Barr advocated when he recently addressed the International Conference on Cyber Security and called for an end to encryption as we know it.
Encryption is indispensable to modern privacy. Without it, every message might be read by a third party, and every phone and laptop easily copied by an intruder. Encryption is the digital lock which gives us the security to trust our financial data and inner-most thoughts to the cloud, and without which everything, and I mean everything, in our digital lives might be exposed. Without strong encryption, police officers can potentially transform our cellphones and computers into a de facto government tracking device.
It’s odd hearing this call for surveillance coming from Barr of all people. As general counsel at Verizon, he preached about the “freedom to innovate”, opposing net neutrality rules that would block internet service providers from shaking down websites and apps to get faster speeds and better access to potential users. What could more stifle the innovation of every single American than the knowledge that anything we say or do on our devices can be monitored at the request of the police?
Barr described basic cryptography as a law-free zone, “insulated from legitimate scrutiny.” But just how legitimate has law enforcement’s scrutiny been in the past? Here, in New York City, the answer is pretty damning. For years, the sprawling NYPD surveillance apparatus has operated with little oversight or transparency.
Officers have used emerging tools like “stingrays”, fake cell towers that can track all the cellphone usage in a neighborhood. For years, the NYPD used these dystopian data-collection devices to track New Yorkers without ever establishing public privacy guidelines on how the tools can be used or when the data they collect can be retained. Even more alarming, this sort of surveillance had been riddled with bias.
An OIG-NYPD report found that over 95% of NYPD investigations targeted Muslim New Yorkers and their allies, despite the fact that the majority of terrorist plots in the US come from right wing extremists and white supremacists. Throughout the 2000s, the NYPD’s “stop-and-frisk” program targeted hundreds of thousands of New Yorkers, almost all of whom were New Yorkers of color. And the NYPD’s gang database is comprised of over 99% New Yorkers of color.
If Bill Bar gets his way and we equip local police with the ability to hack our phones on demand, we know that they won’t target everyone. No, instead, they will go after the exact same communities that have been over-policed and under suspicion for decades.
It would be bad enough if Barr’s plan empowered digitized stop-and-frisk, but it’s far worse: it’ll break the internet. We talk about encryption as if it’s a lock, but it’s not, it’s math. Incredibly complicated and, at times, fragile math. When we talk about building-in “back doors” and “master keys” what we’re really talking about is compromising the fundamental strength of the cryptography upon which we all depend.
Encryption back doors are simply another way of saying “bad encryption.” By their very nature, these sorts of exploits introduced vulnerabilities that can be used by third parties to compromise our data. Barr has talked about “Exceptional Access Keys” and “Layered Cryptographic Envelopes’, but the truth is that when you look past the jargon, there isn’t a single solution that experts would universally agree is just as secure as un-diluted encryption.
Even if a “back door” were cryptographically sound, and it’s not, we would still be creating a single point of failure. If you create a government repository of encryption keys, guess what the biggest target for global hackers and foreign governments will be? And its not like the US has a great record on keeping our own data safe. The DHS, NSA, DOD, all of the government agencies that we trust to safeguard our secrets have been hacked.
And to make matters worse (yes, it can actually get worse), the law wouldn’t even reach the people Barr really wants to target. A federal law that breaks crypto for Americans will be a paper tiger for those operating outside the U.S. Imagine a someone is sitting on a beach in India, Namibia, or the French Southern Territories (countries picked at random to avoid picking on the usual suspects). How much will they care about what Bill Barr says about encryption? Not one bit. They’ll just care about what the rest of us should focus on: does this product or service keep my data safe. If Barr blocks American firms from providing secure communications and data storage, competitors around the world will quickly fill the space.
The answer is clear. We don’t need a new encryption standard. We don’t need a new legal requirement for app developers. We need privacy. As things stand, the government already has an unprecedented ability to monitor what each and every American does in digital and physical space. This isn’t the moment to break down one of the few privacy protections we have, this is the chance to build on existing encryption to make sure that when we invoke our right to remain silent, we don’t have our own devices speaking against us.
Cahn is the executive director of The Surveillance Technology Oversight Project at the Urban Justice Center, a New York-based civil rights and police accountability organization. On Twitter @cahnlawny.
Zubair is a rising 2L at the University of California, Berkeley School of Law and a civil rights intern at The Surveillance Technology Oversight Project. On Twitter @AyyanicBond
https://boingboing.net/2019/08/02/you-have-the-right-to-remain-e.html
22 notes
·
View notes
Note
hii!!!! can i please request an angsty hc with rfa and their reaction to where the bomb in rika's apartment actually goes off cuz some burglar tries to break in and they only found out about it thru ur goodbye messages in the chatroom before u die?? thx thx and hope youre having a night day or night!! :D
yikes apparently you want to see me cry, okay i see how it is lolol
lets do this;;;;
p.s this is v long (rest under the cut) and anything [in square brackets] is a text.
NOTE: OMG IM SO SORRY YOU ASKED FOR HDC BUT I MADE A SCENARIO INSTEAD IM AWFUL PLEASE TELL ME IF YOU’D LIKE THIS CHANGED INTO HDCS I FEEL TERRIBLE.
tw: bomb, guns, death.
PLEASE READ AT YOUR OWN RISK.
It was cold. The clock had just hit 2:30 am. The faint sounds of the city filled the silence of the apartment. You sat at your desk, polishing up some minor details for the party. Only a few more days until you got to meet everyone and you were incredibly excited. While you were still concerned about the bomb and the hacker, you trusted Seven and V to deal with it - and if they couldn’t do it, Jumin was incredibly reliable. So you put your worries to rest and all of your efforts went into the RFA party.
Besides, if anything did go wrong (which you doubted would happen) you had a will and letters to go to all of your loved ones, both of which were safely kept in your own home. But everything would be fine anyway, so they really weren’t necessary.
You quickly emailed the rest of the details to Jaehee, answered some guests and bid goodnight to Yoosung who was complaining about LOLOL server maintenance. Shutting your laptop, you stood up to brush your teeth and prepare for bed. Eventually, you turned off the lights and crawled under the warm covers, listening to the bustling city with excitement as you drifted off.
Something isn’t right.
The red LEDs of your alarm clock read 4:41 am as you startled awake. It’s too cold. Slipping out of your bed, you grabbed your phone from the nightstand and unlocked it, opening the RFA chat. No one’s online.
[Guys, something’s off.]
You had just hit send when a voice rang out.
“A stranger has been located.”
Your heart leapt into your throat. Scared for your life, you frantically texted the chat, your thoughts as chaotic as your messages.
[SVENE]
[HLEP]
[ETHERES SOMETHING HRRIBLY WRONOG]
[SOEMONES HERW]
“Sensed location of stranger… adjusting target…”
[THE SYSDYEMS BEEN AC TIVATESD]
You desperately tried to phone Seven- anyone. No one was picking up. Your chest heaved. I can’t breathe. Panic spread like wildfire and you sprinted out of your room to try and escape the apartment-
Your heart stopped beating and your feet froze in fear. A shining, silver barrel was pointed straight at your heart.
It’s freezing.
“Don’t. Move. A muscle.” Whoever was behind responsible for breaking into your apartment, well, he clearly had a death wish. “What is that?!”
“Backing up all information… After the back up is complete, the bomb will be activated. 20 seconds backup remaining.”
“What is going on?!” He screamed, lowering his gun for just a second. He had a weak point, in your range. You had to make a decision; would you let him steal not only the information but your life or would you save something?
…I can’t let him get his hands on that information.
“15 seconds backup remaining…”
You took your chance. Adrenaline rushed through you as you hit the gun out of his hand. “Wh- HEY!” You punched his side with all your strength. Then, bringing your knee up, you kicked him in the groin as hard as you could, sending him crumpling to the floor. “You bitch!”
No one will come.
“10 seconds backup remaining…”
You lunged for the abandoned gun, your fingers, slick with sweat, failing to pick it up. “Oh no, you don’t!” The intruder seized your ankle, pulling you down to the floor. You yelped in shock.
“Let me go!” I’m scared.
“5 seconds backup remaining…”
Your tears overflowed as he began to stand. With the remainder of your energy, you kicked him off you, finally picking up the gun. Pushing yourself off the floor, you rushed into your room, slamming the door behind you.
I can’t think straight.
“Backup complete. Relocating target.”
You fumbled with your phone, texting whoever you could. Your family, your friends, and of course, the RFA. Three simple words; usually said to fiances, parents or children. Never in your life would you have believed they’d be said in this circumstance - especially not by you.
“Bomb will detonate in T minus 5…”
Outside your room, you heard the robber curse. Your heartbeat crushed your chest and your tears streamed down your face.
The information is safe. Ĭ̶̗ ̴̢͌͂ä̶͖́m̷̠͒ ̶̜͠g̴̛̜̯̐̓ồ̷̱̽i̶̯̤̮͐n̵̬̝̑g̸̦̺̈̂͂ ̷̘̒̅̉��̻t̴̛͔̖̣͆̆ọ̵͝ ̸̘̆̿d̴̺͗͜i̶̖͐e̶̬͇̦͑.
“4…”
Your lungs were on fire.
I’m sorry I couldn’t do more for you. E̵͈̒̃̾v̸͎̗̠̍̓̉e̵̡͖͗r̵͍̗̼͝͝y̷̜͓͍͗͌̒t̵̙̪͕͝h̸̥͆͜͝i̵͕̱͚͊̃͂n̸̜͈̥̏g̸̮͐̐̿'̸̛̰̖͎͌̽s̶̪̦̉̋ ̶̯̋̔ẉ̷̦͌r̷̦̜̉o̴̼̔̚n̸̝̒͌ǵ̴̖͇͌.
“3…”
Your head was light.
Please don’t blame yourselves.I̵͉̹̎̀ ̷͓̈́a̸̢͎͒m̴̭̋̏ ̷̤͕̾̓̅s̷͚͔͚̔ǫ̷̖͖̎͆̇ ̷̼̂â̷̘̜̝̎l̸̦̦͚̉o̸͔̒̅n̸͇̑̔̃e̴͚̒͋.
“2…”
You braced for impact.
I love you all. I̵̥͙̺̓̉t̶͓̣͒͠'̷̥͐̃͒s̷͙̺̉̂ ̵̩͔̀̌͋s̷̨̲̙̃o̵̧̗̗͛ ̵͒͜c̵͓̥̍ỏ̵͙͓̪͂̉l̸͎̖̱̾͝d̵̡͇̉.
“1…”
Thank you for everything. H̵͍̙͉͐e̴͉͖̔̔͂l̵̬̥̰͐̚p̴͔̣̓̎͆ ̶̨̍̐̈́m̶̙̤͕͊̍̋e̷̡̪̺͐̂.̸̱̟̈́̓
“Detonating.”
You screamed.
They didn’t learn about it until the morning. The whole country knew. Soon, the whole world.
The apartment building had exploded in a fiery haze, collapsing one half of the building into the inferno. It was attended by every fire station in the city. There were four dead, twelve injured and two in critical condition, at that moment. The source of the blast was floor fourteen. Your apartment. That’s what they knew. That’s what was reported by every news broadcaster in the city.
You were dead.
That’s what they knew.
Seven found out first. The alarms rang out during the countdowns. His fingers flew across the keys at a speed he didn’t know he could reach. It was too late. The continuous clicking came to an abrupt halt. He wasn’t fast enough. His heart pounded in his ears and he felt faint. His mouth was dry. He couldn’t think, he couldn’t move. He couldn’t breathe. Pain welled up in his throat and tears drenched his skin. Seven couldn’t do anything. He had made that bomb. He wasn’t skilled enough to turn it off. He couldn’t save you. He couldn’t save you. He couldn’t save you. He couldn’t save- he couldn’t- he- save- you…
V was there. Seven had called him as the first countdown began. V, in the area at the time, rushed there only to arrive and watch everything collapse. He watched the fire erupt from the rubble, felt the heat on his entire body. He suffered the shockwave in his chest. The blaze of failure rivalled that of the flames before him. His heart clenched. He had failed yet another person he held dear. V froze in front of the mayhem.
The police asked him many questions; Where was he before the explosion? Did he know how it happened? Did he know anyone in the building? Did he live there? Did he have anywhere to go, anyone to call? V let them check his emergency contacts. Jumin was called.
Jumin arrived on the scene not even twenty minutes later to pick up V. He stepped out of the car, emotionless. The police filled him in. There was no body to be found, however, earwitnesses had overheard a scuffle and shouting moments prior, indicating there was someone else in the apartment. That’s what they knew. Jumin couldn’t feel anything. He comforted V regardless of the growing ache in his chest. He stepped to the side to call Jaehee. He could only manage the address and the words: “It’s MC, come immediately.” In too much shock, Jumin only found himself hugging V tighter.
She pulled up very soon after. “Mr Han…” She didn’t even have to ask. The flames had subsided and were replaced by a heavy sorrow hung which in the air. The sun peaked over the buildings, covered substantially by smoke. Above that, the pink sky glittered with the last remaining stars. Jaehee glanced up. She didn’t know what came over her but she found herself scowling at the sky. You’d loved it. You’d loved the feeling of freedom it gave. You’d loved the colours, how they spread across the sky as though it was a canvas and the sun was the artist. Now it glimmered with a hope that she didn’t know if she would ever get to experience again. Jaehee shook her head and looked back down. She had to make you proud. She had so much work to do.
Zen overheard it only after he’d left his house. It was in shop TVs, the people in the park were whispering about it, even his fellow actors. People he passed gave him pitiful looks and he hated it. Zen couldn’t bear to log into the messenger. He didn’t want to know that he could’ve helped you; that he could’ve made sure you weren’t alone. He didn’t want to think about it. It was too quiet during his rehearsals. His director sent him home early. As he rode home, the wind tore at his jacket and tugged on his hair. It was too cold. Yoosung called him soon after he made it home, in hysterics. Zen agreed to meet up.
They met at Yoosung’s place. Zen knew Yoosung wouldn’t be able to go anywhere else. He was distraught. His tears stained through his shirt. His friends were telling the school that he wouldn’t be in. Yoosung felt so, so, so very alone. You two were close for the fleeting moments you knew each other. First Rika, now you? His heart couldn’t take it. His mind was racing. Was it him? Was he a bad-luck charm? Was it his fault? Why did you have to leave him? Why now? Why? Why?! His thoughts cluttered, his emotions in pandemonium. He could do nothing but cry and hold onto Zen. Yoosung didn’t want to be alone. You made him feel less lonely.
You made them all feel cherished. Feel wanted, feel heard, feel loved. But you were gone.
That’s what they knew.
Whoo boy did i make myself sad or what
I promise I’ll write more. And I’m not just saying that this time. I promise.
anyway, hope this is what you want! Just tell me if you’re unsatisfied and ill rewrite!
bye bye! *poof*
#wow who keeps forgetting tags this girl#mystic messenger#mysmes#mm#v mystic messenger#mystic messenger 707#mc mystic messenger#707 mystic messenger#mystic messenger zen#mystic messenger imagines#mystic messeger scenario#minific#puffle writes#imagine#scenario#mys mes#mysme jaehee#jaehee kang#jumin han#mysme jumin#mysme#mysme zen#hyun#hyun ryu#v#jihyun kim#mysme jihyun#yoosung#yoosung kim#mysme yoosung
165 notes
·
View notes
Text
Essay III – Unfriended – Contemporary Cyber Horror
The newer generation has been so obsessed with social media and their reputation on the internet that they would do anything for a ‘like’ on their selfie or wall posts. When the internet gained popularity in the early 2000’s with AOL Instant Messenger and the Chat Rooms, we were worried about pedophiles and seeing our neighbor on Dateline NBC with Chris Hanse in To Catch a Predator. There was a sick obsession with the predators that lurk the internet, seeking out innocent children and young teens in the chat room to lure them into crude acts and god knows what. In 2005 the Cyber Horror movie released called Hard Candy with Ellen Page, followed the vigilante in seeking out a pedophile online. She had lured him into a trap for a taste of his own medicine. He admitted to being involved in a heinous rape murder scenario of a girl him and a partner targeted online. She drugged him and planned an elaborate set up to pretend to castrate him (which was all fake to get him to confess to the murder) and eventually got him to commit suicide, as she later revealed she has done the same to his partner from said crime. This film was a sit-on-the-edge-of-your-seat thriller flick and took it to the extreme fantasy scenario of what we would imagine to do if we ever encountered a twisted pedophile in real life. As Stephen King says in Why We Crave Horror Movies, “we’re all mentally ill; those of us outside the asylums only hide it a little better” (King). We find enjoyment in these films as we all are a little twisted and have a bit of a dark side. Buying tickets to the movie theater to watch these sort of films on the big screen prove his claim. We are fascinated with the nightmares, the guts and the gore.

In the 2014 American film, Unfriended, the director explores different genres of horror including Found Footage, POV, Cyber and even Supernatural. Unfriended is based on our collective fears of the dark side of social media and cyberbullying. The film is mainly shot through a MacBook screen of a high school student who finds themselves haunted and terrorized by an anonymous source. As categorized mainly as a Cyber horror, a film which either has its narrative told through a computer or any other form of technology, or that utilizes technology as a key plot element, Unfriended fits every aspect of the genre. It all begins with Blair logging onto her laptop to view a video on live leak to watch a video of her best friend, Laura Burns, a year prior, committing suicide after being cyber bullied due to a series of humiliating events at an unsupervised party.

Blaire is showed video chatting moments later with her boyfriend and their friends joined the conversation along with an anonymous user who they believed answered the video call, eerily would not allow them to skype with their friends without the unknown user being attached. They all then received Facebook messages from Laura, believing she was hacked they were worried how someone could be so cruel with a prank like that. Then their other friends page was hacked, posting embarrassing pictures of the accused hacker. That’s where things got intense and the actual hacker identifies herself as the dead friend on skype. The ghost behind the account began typing rude comments in the skype chat, turning everyone against each other, revealing that Val was the one who pushed Laura over the edge to kill herself. She is shown on the video chat almost frozen, then fell over, police arrive confirming her death as a suicide. The ghost user shows all of the friends’ dirty little secrets as the film progresses.
One by one they commit suicide over skype and are forced to play mind games created by Laura to reveal that Blaire, who was supposed to be her best friend, posted a humiliating video of her in the first place which caused the initial cyberbullying and ultimately lead to her suicide. After everyone has died, the door cracked in Blaire’s room, a pair of hands slammed the laptop shut and the ghost of Laura lunged violently at her and the screen went black.
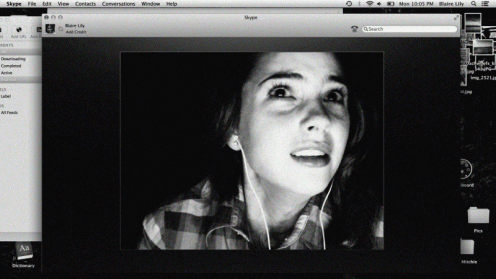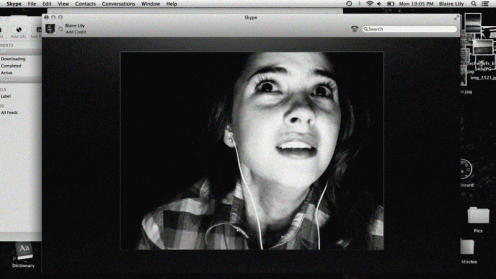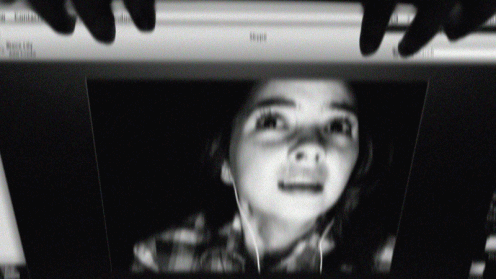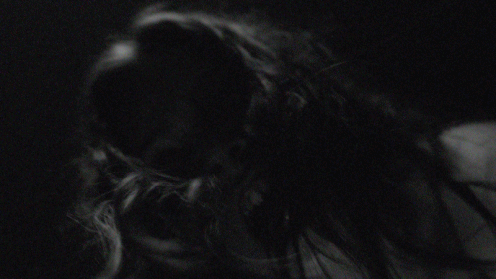
Going back to Hard Candy, that cyber horror film played off our fears of child molesters and the dangers that they could find within the chatrooms. It got your heart racing and confirmed our trepidation that people like that exist and are a huge danger to our children… as time went on our fears of the internet evolved to something much more. Children were now the predators upon each other. Using social media as a tool to humiliate one another and get under each other’s skin on a larger scale than the playground. As Sigmund Freud puts it, “The uncanny is something familiar that has been repressed and then reappears,” (Freud 152). The obsession with the eerie ability that the internet has to ruin someone’s life in a split second grows with every new advancement in technology. We are now in a world that bullies thrive behind a keyboard and it is very easy to manipulate our peers through social status and our online appearance. We lived in such a private society before Myspace, Facebook and Instagram came about… “everything that was meant to remain a secret and hidden but has come into the open,” (Freud 132). The ghost exposed all of the dark secrets of each teen in this film and brought it to the open. Moments before Blaire was attacked by the ghost, the video that led to the death of Laura was posted on her Facebook wall, putting out one last secret out into the open for everyone to turn against her.

In Ghostland: An American History in Haunted Places, Dickey investigated several historical accounts of hauntings across the country but one chapter stuck out to me while watching Unfriended. The Rathole Revelation discussed the background of spiritualism and how America’s fascination with spirits became popular during the 1850’s. He wrote an account of the Fox sisters and how they were breaking the glass ceiling of spiritualism by being female and able to communicate to the dead. In Unfriended, the main character was a female and her friend who had committed suicide was a female as well, so by her reaching out from the other side in a frightening manner was interesting when looking at it in a gender role perspective. On the anniversary of her death, Laura reached out one last time to her so-called friends for closure of her suicide. “Spiritualism’s appeal lay in its social aspect: it was a means of bringing together a community over a shared grief or curiosity, in an intimate and emotionally intense setting” (Dickey). She used her haunting ability as a way of getting her revenge on those who cyberbullied her to her death. She made them curious with the anonymous skype user, the humiliating photos on Facebook, the chat log of Val telling her to kill herself, etc. The intimate and emotionally intense setting of the video chat and mind games was her way of getting what she wanted.
The anxious feeling one might get watching these films is uncanny, some might say it is normal to have that sensation as the plot thickens. Our emotions rise and begin to relate these occurrences real life and how this can possibly happen to my children one day, maybe not the supernatural part, but the cyberbullying definitely.
Dickey, Colin. Ghostland: An American History in Haunted Places. Penguin Books, 2017.
Freud, Sigmund. (2003). The Uncanny. London: Penguin Books.
King, Stephen. (1981). “Why We Crave Horror Movies.”
7 notes
·
View notes
Text
New Post has been published on All about business online
New Post has been published on http://yaroreviews.info/2021/05/key-u-s-energy-pipeline-closes-after-cyberattack
Key U.S. Energy Pipeline Closes After Cyberattack

The main pipeline carrying gasoline and diesel fuel to the U.S. East Coast was shut down by its operator after being hit with a cyberattack.
Colonial Pipeline Co. operates the 5,500-mile Colonial Pipeline system taking fuel from the refineries of the Gulf Coast to the New York metro area. It said it learned Friday that it was the victim of the attack and “took certain systems offline to contain the threat, which has temporarily halted all pipeline operations.”
The 5,500-mile Colonial Pipeline system carries roughly 45% of gasoline and diesel fuel consumed on the East Coast

Greensboro
Birmingham
Baton Rouge

Greensboro
Birmingham
Baton Rouge

Greensboro
Birmingham
Baton Rouge

Greensboro
Birmingham
Baton Rouge
The outage isn’t expected to have a significant impact on fuel markets unless the pipeline remains shut down for several days, analysts said.
In an update Saturday afternoon, the company said it has found that the cyberattack on Colonial involved ransomware, a type of code that attempts to seize computer systems and demand payment from the victim to have them unlocked.
Two people briefed on the probe said the attack appeared to be limited to information systems and hadn’t infiltrated operational control systems, but cautioned that the investigation was in its early stages.
The company said it had engaged a third-party cybersecurity firm to help with the issue, which affected some of its IT systems, and had contacted federal agencies and law enforcement.
FireEye Inc., a U.S.-based cybersecurity firm, is investigating the attack, according to people familiar with the matter. A FireEye spokesman declined to comment.
The Federal Bureau of Investigation and the Cybersecurity and Infrastructure Security Agency, which works with critical infrastructure companies on cyber defense, didn’t immediately respond to requests for comment.
It wasn’t clear whether the attack was perpetrated by a nation-state actor or criminal actor. Attributing cyberattacks is difficult and can often take months or longer.

Colonial Pipeline Co. says that ‘our primary focus is the safe and efficient restoration of our service.’
Photo: Luke Sharrett/Bloomberg News
The Colonial Pipeline is the largest refined-products pipeline in the U.S., transporting more than 100 million gallons a day, or roughly 45% of fuel consumed on the East Coast, according to the company’s website. It delivers fuels including gasoline, diesel, jet fuel and heating oil and serves U.S. military facilities.
“At this time, our primary focus is the safe and efficient restoration of our service and our efforts to return to normal operation,” the company said in a statement. “This process is already under way, and we are working diligently to address this matter and to minimize disruption to our customers.”
Colonial spokeswoman Kelsey Tweed said the company didn’t have further details to provide at this time.
Privately held Colonial is owned by several entities, including units of investment firm IFM Investors, Koch Industries Inc., KKR & Co. KKR 1.80% Inc. and Royal Dutch Shell RDS.A 1.89% PLC. KKR declined to comment. IFM, Shell and Koch didn’t immediately respond to requests for comment.
Inventories of gasoline have been readied for the summer driving season and usually get replenished every five to six days. But if the pipeline remains offline for days, shortages at terminals that receive fuel in the southeastern U.S. and Atlantic Coast markets could begin to affect retail stations and consumers, said Andy Lipow, president of consulting firm Lipow Oil Associates in Houston.
“It’s similar to a hurricane event where the pipeline gets shut down, so if it’s for a day or two then the impact will be mitigated,” Mr. Lipow said.
The fuel artery is critical to supplying the northeastern U.S. and other markets, and extended shutdowns of the pipeline have caused fuel prices to jump.
More on Cyberattacks Targeting the U.S.
Fuel prices rose in 2016 following a Colonial pipeline leak in Alabama that closed the conduit, as they did in 2008 when Hurricane Ike smashed into the Gulf Coast.
It is also among the many aging U.S. pipelines that were built before 1970, having started full operations in 1964.
An outage lasting more than five days could have sharp consequences for fuel supplies, particularly in the southeast U.S., as inventory levels there are fairly tight, said Tom Kloza, global head of energy analysis for Oil Price Information Services, or OPIS, an IHS Markit company.
“If you were looking at the top 20 public targets that you could really wreak havoc with by screwing with the software, the Colonial Pipeline is in that group,” Mr. Kloza said. “It’s a big deal.”
Still, areas along the northern Atlantic Coast have ample fuel supplies amid a rise in foreign imports, particularly from Europe, he said.
Cyberattacks targeting critical infrastructure or key companies, some by suspected foreign actors, have become a growing area of concern for the U.S. national security officials.
Russian hackers, for example, have been blamed by Western intelligence agencies for temporarily downing parts of Ukraine’s power grid in the winter. Pipelines have long been viewed as an area of concern for these kinds of attacks, in part because halting their operations can have immediate impact.
President Biden in April announced punitive measures against Russia, blaming suspected Russian agents for a month-long hack of the U.S. government and some of America’s biggest corporations.
Newsletter Sign-up
WSJ Pro Cybersecurity
Cybersecurity news, analysis and insights from WSJ’s global team of reporters and editors.
That attack involved , a network-management technology firm whose software was one of the primary entry-points for the hackers, but extended beyond its software. It has been described as one of the worst instances of cyber espionage in U.S. history.
U.S. officials in recent months have ramped up warnings about such hacks. The number of ransomware incidents has risen dramatically during the coronavirus pandemic, cybersecurity experts say, targeting schools, hospitals and companies.
On Wednesday, Homeland Security Secretary Alejandro Mayorkas said his agency is dedicating more resources to counter ransomware aimed at locking up government and private-sector computer networks. And the Justice Department last month announced a new task force dedicated to ransomware.
“The threat is real. The threat is upon us. The risk is to all of us,” Mr. Mayorkas said.
Mike Chapple, a cybersecurity expert at the University of Notre Dame and former National Security Agency official, said the Colonial Pipeline attack appeared to show the hackers were “extremely sophisticated” or that the systems weren’t properly secured.
“This pipeline shutdown sends the message that core elements of our national infrastructure continue to be vulnerable to cyberattack,” Mr. Chapple said.
If the attack originated from malware or ransomware that infected systems, potentially inadvertently, then network issues could be fixed in a matter of days or weeks, depending on how well prepared Colonial was to respond to an attack, said Grant Geyer, chief product officer of software firm Claroty, which specializes in industrial cybersecurity.
But if a nation-state directed the attack, it would require an extensive cybersecurity response to fix vulnerabilities that could serve as a “backdoor” for infections later.
“A lot of the systems that control industrial environments are managed by, in some cases, antiquated Windows systems that are rife with vulnerabilities,” Mr. Geyer said, adding the problem is particularly acute in the energy industry.
—Miguel Bustillo and David Uberti contributed to this article.
Write to Collin Eaton at [email protected] and Dustin Volz at [email protected]
Copyright ©2020 Dow Jones & Company, Inc. All Rights Reserved. 87990cbe856818d5eddac44c7b1cdeb8
0 notes
Text
Schools remain key targets for hackers, US intelligence officials say
Schools remain key targets for hackers, US intelligence officials say
By Josh Campbell, CNN
Updated 12:30 PM ET, Fri December 11, 2020

View On WordPress
0 notes
Text
Final Project
Students in Toronto who are in the last few years of high school. They are accustomed to using social media, but they do not know how to get the most out of it, nor do they know about many of the challenges or security issues that we have learned about in class.
The Power of Hashtags
People use hashtags as a way of connecting relevant content and information together. For example, if I created a social media post on twitter and used the hashtag #Raptors, now anyone who searches #Raptors will also be able to see this post in real time. As an influencer or company who uses hashtags to sell products or services, they use relevant hashtags to essentially group things together. For example, a gardening company may hashtag a few gardening tools and sprays on a single picture, with the hope of attracting more people to at least one of the hashtags revolving around a similar topic.
It is important to use hashtags to filter out your content and posts. What this means is you want to narrow your audience. It would also be very effective to measure your KPI such as traffic and views on specific hashtags to see what works and what doesn’t. By focusing on this, you will be able to attract more traffic to your posts by using the right and relevant hashtags.

2. Social Media Conversions
Social media are such powerful platforms that give you the opportunity to measure your success. A social media platform like Facebook, where you can now advertise your business and purchase items directly from the advertisement page have multiple different conversion metrics you can use to measure the success of your ads. Some conversion metrics you are able to measure are things like newsletter subscriptions, clicks, spending amount, conversion rates and bounce rate to name a few. As students continue to use social media for their entertainment, it is important for them to understand that those platforms can create opportunities for them as they head into post secondary or into the workplace. For example, an entrepreneur, these platforms provide them the ability to consistently check their metrics, make adjustments and monitor the results. In large companies as well, many now use online social media and advertisement tactics to gain customer information. Companies then use that data to tweak their tactics in hopes of receiving higher returns. Understanding how to use these metrics will give you a large advantage when you are able to manage these aspects of a company.
In my opinion, as young students, mastering how to use these metrics as a young age gives you tremendous advantage over many others who are not proactively learning and understanding conversions. You will be more advanced for employment and with today’s unprecedented times, the world is only going to become more reliable with online instruments. Data will continue to be received more and more online and slowly move away from the old school paper and mail surveys to receive customer data.

3. Cybersecurity
In this day and age, quadrillions of information is being uploaded online including our very own profiles. The difficult issue here is that with the expanding amount of information that is being shared online, we are exposed to the risks of cybercrime. Cybercrime is usually apparent through hackers who send viruses to our computers and steal our personal information such as passwords, SIN, addresses, credit card numbers and more. These kind of hackers who gain our information for personal gain are on the extreme spectrum of cybercrime, while on the other hand there are businesses who hire experts to collect information from us through our very own devices. One of the ways this is done is through the implementation of cookies. Cookies are code embedded on your computers and laptops that occurs when you visit websites. These cookies help the companies identify you as a unique visitor and records your interaction with the website (Module 4). Advertising companies then display advertisements on any site you visit. You may notice if you shop for a specific brand of clothing and you move on to a completely different website, you will see an ad generate based on the last thing you were searching for and this is all due to cookies. The “third party” data is stored in profiles by groups called “data brokers”. These brokers then segment us into groups based on categories. This is why your online identity is important. “Think twice, click once” is a great saying because the more you browse on your social media, the more data of you is actually being stored. It’s important to keep cautious of this because information can get hacked or leaked.
4. The Benefits of Apps
In the millennial generation, the most popular devices used by consumers are smart devices . In fact, over 3 billion people in the world are proven to be smartphone users due to its many smart device innovative features, including it’s variety of apps! Apps are one or more programs that are designed for end-users. For businesses, apps are important because they can help you target broader audiences and potential consumers because most people use their phones every day, and putting your content software on their devices is an easy way to reach them (Module 7). Apps create colour and variety for smart devices as they act as a platform to create and consume an endless amount of activities such as a game console (PS5), Smartphone (iPhone), web browser and more. More commonly, many apps are accessed through smart devices such as smartphones and tablets. As mobile devices were drastically innovated over the years, along with it came the famous “Mobile App” in which we use such platforms to make our daily life more convenient. The evolution of apps has impacted our lives in many ways: If you’re looking for something in the dark, you can turn the flash on your phone and use it as a flashlight, and use it as a flashlight. When we need to calculate how much we should tip a service provider, we automatically pull out our phone calculator! When we want to connect with someone overseas, we can easily message or call them- you get the gist of it. For businesses, you can use apps to learn about your consumers and improve your marketing tactics. It can also be used as a platform to condense large amounts of information into an easy communication channel for users and employees.

“apps” by Sean MacEntee is licensed under CC BY 2.0
5. Why Websites are Key for Businesses
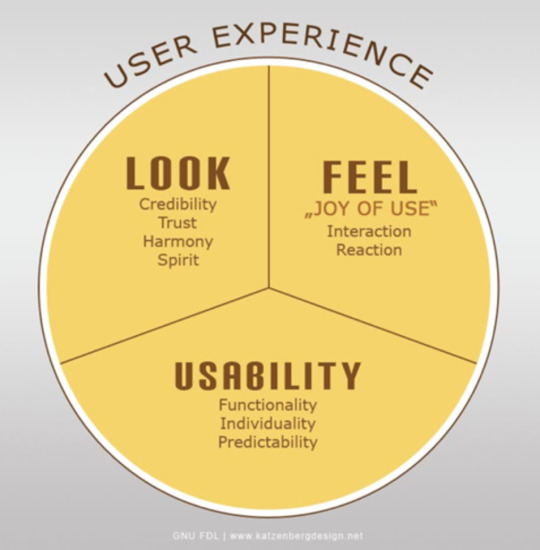
The importance of incorporating a website for your business. A website is a platform that may include both hardware and software in order to operate. Some of the world’s most famous websites include: Youtube, Wikipedia, Twitter, Facebook and Amazon. People rely on websites for reasons such as daily entertainment, online shopping, acquiring resources through search engines and many more. What all of these great websites have in common is that they are all able to optimize their website by remaining responsive but also adapting to different platforms, by delivering the same uniform experience for users. Another good way to measure how well a website was created is by observing the user experience it provides. More specifically, what we can use as a benchmark to test the value of the website is through the look, feel and usability it provides. Does the website look like a platform you can trust? Does browsing through the website give you any feelings such as joy? Is it easy to navigate through the website? Does the website load quickly? All of these issues are highly important and must be accounted for when creating a good website. The interplay of visuals, colour, ergonomics, and more, all play a specific role in the overall experience a website can provide (Module 7). To create a website, there are a number of different platforms that provide a variety of templates such as Wordpress, GoDaddy, Shopify and many more. These websites often include the three main categories: media queries, fluid grids and flexible images. Each category has a specific role on the website as they affect the look and feel of the website.
Source: Wikimedia Commons (2009)
Sources
“Marketing Dashboards and Reports.” Funnel, 5 Apr. 2020, funnel.io/dashboards-and-reports?utm_source=google&utm_medium=cpc&utm_campaign=bb-search-generics-us-1-bmm&utm_term=social%2Bmedia%2Bdata%2Banalytics%2B-%2Bbmm%2B-%2Bus%2B&gclid=EAIaIQobChMIgM6K9Nzy6gIVDJyzCh1dvAr8EAAYAS
Figure 2f from: Irimia R, Gottschling M (2016) Taxonomic revision of Rochefortia Sw. (Ehretiaceae, Boraginales). Biodiversity Data Journal 4: E7720. https://doi.org/10.3897/BDJ.4.e7720. (n.d.). doi:10.3897/bdj.4.e7720.figure2f
O'Dea, P. B., & 28, F. (2020, February 28). Smartphone users worldwide 2020. Retrieved from https://www.statista.com/statistics/330695/number-of-smartphone-users-worldwide/
0 notes
Text
Final Project
Students in Toronto who are in the last few years of high school. They are accustomed to using social media, but they do not know how to get the most out of it, nor do they know about many of the challenges or security issues that we have learned about in class.
The Power of Hashtags
People use hashtags as a way of connecting relevant content and information together. For example, if I created a social media post on twitter and used the hashtag #Raptors, now anyone who searches #Raptors will also be able to see this post in real time. As an influencer or company who uses hashtags to sell products or services, they use relevant hashtags to essentially group things together. For example, a gardening company may hashtag a few gardening tools and sprays on a single picture, with the hope of attracting more people to at least one of the hashtags revolving around a similar topic.
It is important to use hashtags to filter out your content and posts. What this means is you want to narrow your audience. It would also be very effective to measure your KPI such as traffic and views on specific hashtags to see what works and what doesn’t. By focusing on this, you will be able to attract more traffic to your posts by using the right and relevant hashtags.

2. Social Media Conversions
Social media are such powerful platforms that give you the opportunity to measure your success. A social media platform like Facebook, where you can now advertise your business and purchase items directly from the advertisement page have multiple different conversion metrics you can use to measure the success of your ads. Some conversion metrics you are able to measure are things like newsletter subscriptions, clicks, spending amount, conversion rates and bounce rate to name a few. As students continue to use social media for their entertainment, it is important for them to understand that those platforms can create opportunities for them as they head into post secondary or into the workplace. For example, an entrepreneur, these platforms provide them the ability to consistently check their metrics, make adjustments and monitor the results. In large companies as well, many now use online social media and advertisement tactics to gain customer information. Companies then use that data to tweak their tactics in hopes of receiving higher returns. Understanding how to use these metrics will give you a large advantage when you are able to manage these aspects of a company.
In my opinion, as young students, mastering how to use these metrics as a young age gives you tremendous advantage over many others who are not proactively learning and understanding conversions. You will be more advanced for employment and with today’s unprecedented times, the world is only going to become more reliable with online instruments. Data will continue to be received more and more online and slowly move away from the old school paper and mail surveys to receive customer data.

3. Cybersecurity
In this day and age, quadrillions of information is being uploaded online including our very own profiles. The difficult issue here is that with the expanding amount of information that is being shared online, we are exposed to the risks of cybercrime. Cybercrime is usually apparent through hackers who send viruses to our computers and steal our personal information such as passwords, SIN, addresses, credit card numbers and more. These kind of hackers who gain our information for personal gain are on the extreme spectrum of cybercrime, while on the other hand there are businesses who hire experts to collect information from us through our very own devices. One of the ways this is done is through the implementation of cookies. Cookies are code embedded on your computers and laptops that occurs when you visit websites. These cookies help the companies identify you as a unique visitor and records your interaction with the website (Module 4). Advertising companies then display advertisements on any site you visit. You may notice if you shop for a specific brand of clothing and you move on to a completely different website, you will see an ad generate based on the last thing you were searching for and this is all due to cookies. The “third party” data is stored in profiles by groups called “data brokers”. These brokers then segment us into groups based on categories. This is why your online identity is important. “Think twice, click once” is a great saying because the more you browse on your social media, the more data of you is actually being stored. It’s important to keep cautious of this because information can get hacked or leaked.
4. The Benefits of Apps
In the millennial generation, the most popular devices used by consumers are smart devices . In fact, over 3 billion people in the world are proven to be smartphone users due to its many smart device innovative features, including it’s variety of apps! Apps are one or more programs that are designed for end-users. For businesses, apps are important because they can help you target broader audiences and potential consumers because most people use their phones every day, and putting your content software on their devices is an easy way to reach them (Module 7). Apps create colour and variety for smart devices as they act as a platform to create and consume an endless amount of activities such as a game console (PS5), Smartphone (iPhone), web browser and more. More commonly, many apps are accessed through smart devices such as smartphones and tablets. As mobile devices were drastically innovated over the years, along with it came the famous “Mobile App” in which we use such platforms to make our daily life more convenient. The evolution of apps has impacted our lives in many ways: If you’re looking for something in the dark, you can turn the flash on your phone and use it as a flashlight, and use it as a flashlight. When we need to calculate how much we should tip a service provider, we automatically pull out our phone calculator! When we want to connect with someone overseas, we can easily message or call them- you get the gist of it. For businesses, you can use apps to learn about your consumers and improve your marketing tactics. It can also be used as a platform to condense large amounts of information into an easy communication channel for users and employees.

"apps" by Sean MacEntee is licensed under CC BY 2.0
5. Why Websites are Key for Businesses
The importance of incorporating a website for your business. A website is a platform that may include both hardware and software in order to operate. Some of the world's most famous websites include: Youtube, Wikipedia, Twitter, Facebook and Amazon. People rely on websites for reasons such as daily entertainment, online shopping, acquiring resources through search engines and many more. What all of these great websites have in common is that they are all able to optimize their website by remaining responsive but also adapting to different platforms, by delivering the same uniform experience for users. Another good way to measure how well a website was created is by observing the user experience it provides. More specifically, what we can use as a benchmark to test the value of the website is through the look, feel and usability it provides. Does the website look like a platform you can trust? Does browsing through the website give you any feelings such as joy? Is it easy to navigate through the website? Does the website load quickly? All of these issues are highly important and must be accounted for when creating a good website. The interplay of visuals, colour, ergonomics, and more, all play a specific role in the overall experience a website can provide (Module 7). To create a website, there are a number of different platforms that provide a variety of templates such as Wordpress, GoDaddy, Shopify and many more. These websites often include the three main categories: media queries, fluid grids and flexible images. Each category has a specific role on the website as they affect the look and feel of the website.

Source: Wikimedia Commons (2009)
Sources
“Marketing Dashboards and Reports.” Funnel, 5 Apr. 2020, funnel.io/dashboards-and-reports?utm_source=google&utm_medium=cpc&utm_campaign=bb-search-generics-us-1-bmm&utm_term=social%2Bmedia%2Bdata%2Banalytics%2B-%2Bbmm%2B-%2Bus%2B&gclid=EAIaIQobChMIgM6K9Nzy6gIVDJyzCh1dvAr8EAAYAS
Figure 2f from: Irimia R, Gottschling M (2016) Taxonomic revision of Rochefortia Sw. (Ehretiaceae, Boraginales). Biodiversity Data Journal 4: E7720. https://doi.org/10.3897/BDJ.4.e7720. (n.d.). doi:10.3897/bdj.4.e7720.figure2f
O'Dea, P. B., & 28, F. (2020, February 28). Smartphone users worldwide 2020. Retrieved from https://www.statista.com/statistics/330695/number-of-smartphone-users-worldwide/
0 notes
Text
Coronavirus live news: US Democrats told to avoid convention; Brazil cases pass 2m | World news
8.48pm EDT
20:48

Patrick Wintour
The west’s shortsighted response to the impact of Covid-19 could result in 640 million people being infected and 1.7 million killed in the world’s poorest countries, the UN warned.
The direct medical costs of treating 2.2 million patients in hospital critical care beds could amount to an estimated $16.28bn, while the focus on coronavirus could also lead to a diversion of scarce health resources, leading to a further 1.7 million preventable deaths from HIV, TB and malaria.
The findings – prepared for the UN by the economics department at Oxford – are designed as a call to arms as G20 finance ministers prepare to meet this weekend.
UN officials are deeply concerned that as the pandemic recedes in Europe, the impacts of the virus and of the global recession on the world’s poorest are already being forgotten.
8.38pm EDT
20:38
White House: ‘The science should not stand in the way’ of reopening schools
Earlier on Thursday, White House press secretary Kayleigh McEnany defended President Trump’s push to reopen schools, despite concerns about the spread of coronavirus in the classroom.
“And when he says open, he means open and full, kids being able to attend each and every day at their school,” McEnany noted furing her White House briefing.
“The science should not stand in the way of this,” McEnany said, adding moments later, “The science is on our side here.”
However, a number of school officials have expressed concern about students and staff members potentially contracting the virus once in-person instruction resumes.
In response to those concerns, many school districts have announced plans to hold virtual classes this fall. Trump and some of his allies have pointed to evidence that children are very unlikely to become severely ill from coronavirus to justify their push to reopen schools. However, many public health experts have said there has not yet been enough research conducted on how children react to the virus.
8.27pm EDT
20:27
US daily cases surge at around 60,000 for more than a week
According to data from the Johns Hopkins University coronavirus tracker, which relies on official government figures for coronavirus cases and deaths, the US has recorded over 60,000 cases – and on one occasion almost 70,000 cases – for six of the nine days leading up to 15 July, which is the most recent date for which a daily case figure is confirmed.
Table showing US daily case rises. Photograph: Johns Hopkins University
In the US, there are currently 3,559,899 confirmed cases, the highest in the world, and 138,201 deaths.
10 July marked a global record increase of 67,800 cases. Here are the dates and the case numbers confirmed each day, since 7 July, which was the first day that US daily cases increased by 60,000:
7 July: 60,000
8 July: 58,600
9 July: 63,200
10 July: 67,800
11 July: 60,200
12 July: 59,000
13 July: 59,200
14 July: 67,400
15 July: 67,300
Updated
at 8.33pm EDT
7.55pm EDT
19:55
Democrat officials instruct senators, Congress members to skip national convention
The New York Times reports that Democrats are urging elected leaders and party delegates to skip the national convention in August as coronavirus cases surge, in what the Times says is “a sign of the ever-shrinking aspirations for their big campaign event in the face of the spreading virus.”
The Times reports:
The directive ensures that little will happen at the physical convention site beyond keynote speeches from former Vice President Joseph R. Biden Jr., his vice-presidential nominee and a handful of other top party leaders. The remainder of the event — state delegation meetings, parties and schmoozing, voting on the party platform and Mr. Biden’s nomination — will happen virtually or not at all.
Over the past several months, Democrats have scaled back their plans, moving the convention across downtown Milwaukee from the Fiserv Forum, the city’s professional basketball arena, to the Wisconsin Center, a modest convention center that typically hosts events like the city’s car show. The last national political event to take place there was the 2004 Green Party convention. Party officials have been consulting regularly with doctors and epidemiologists and say they are following the recommendations of the medical establishment.
Updated
at 8.11pm EDT
7.51pm EDT
19:51
Mexico to impose local restrictions
The spread of the coronavirus has spurred Mexican authorities to impose local restrictions on mobility, commerce, and leisure, particularly in popular tourist destinations, even as the government seeks to revive the battered economy, Reuters reports.
On Wednesday, authorities in the Caribbean beach resort of Tulum threatened to fine or arrest people for disobeying rules on wearing face masks, the latest in a series of local and state-level curbs against the spread of the virus.

A worker in Mexico wears protective mask in Mexico City, 16 Jul 2020. Photograph: Carlos Tischler/REX/Shutterstock
Eager to lift an economy that is forecast to shrink as much as 10% this year, Mexican President Andres Manuel Lopez Obrador has encouraged people to get out, and has resisted reimposing more stringent nationwide restrictions.
But some local authorities worry if they do not take precautions, the hit to their livelihoods will be worse.
“We can’t play with the health of the citizens,” Tulum’s mayor, Victor Mas Tah, said in comments reported by local media.
Updated
at 8.17pm EDT
7.28pm EDT
19:28
Brazil cases pass 2m
Brazil on Thursday passed the 2 million confirmed coronavirus cases mark, with little sign that the rate of increase is slowing as anger grows over President Jair Bolsonaro’s handling of the outbreak, Reuters reports.
In recent weeks, there have been nearly 40,000 confirmed new cases per day, according to government figures. On Thursday, confirmed cases in Brazil totalled 2,012,151, while deaths numbered 76,688.

Brazil’s President Jair Bolsonaro observes a ceremony in Brasilia, Brazil, 15 July 2020. Photograph: Ueslei Marcelino/Reuters
Despite the rapid spread of the virus, Bolsonaro, a far-right former army captain, has pressured local governments to lift lockdown restrictions.
Bolsonaro, who tested positive for the virus last week, has played down its health risks and fought against social distancing orders, calling their economic effects worse than the disease itself. Under pressure, many governors and mayors have loosened restrictions in recent weeks, fueling bigger outbreaks.
Polls show Bolsonaro’s popularity has been sinking during the pandemic. The share of Brazilians that see his government as bad or terrible has risen to 44%, according to a late June survey by pollster Datafolha. That was up from 38% in April and 36% in December.
Updated
at 8.17pm EDT
7.23pm EDT
19:23
Summary
Hello and welcome to today’s live coverage of the coronavirus pandemic.
My name is Helen Sullivan and I’ll be bringing you the latest from around the world for the next few hours.
As always, you can get in touch on Twitter or via email:
Twitter: @helenrsullivan
Email: [email protected]
Brazil, the second-worst-affected country worldwide in terms of number of confirmed cases and deaths, passed 2 million infections late on Thursday, according to the health ministry.
The country’s cases have doubled in just under a month, nearly 40,000 confirmed new cases per day in recent weeks, according to government figures.
Here are the other key developments from the last few hours:
There are 13,683,631 known coronavirus cases worldwide. The number of deaths stands at 586,752, according to Johns Hopkins University’s tracker.
Puerto Rico’s governor has announced major rollbacks including the closure of bars, gyms, marinas, theaters and casinos and restricted the use of beaches as the U.S. territory is hit by a spike in Covid-19 cases in recent weeks.Governor Wanda Vázquez said the changes and an ongoing curfew from 10 p.m. to 5 a.m. will remain in place until 31 July.
White House: ‘The science should not stand in the way’ of reopening schools. White House press secretary Kayleigh McEnany defended President Trump’s push to reopen schools, despite concerns about the spread of coronavirus in the classroom.“And when he says open, he means open and full, kids being able to attend each and every day at their school,” McEnany noted furing her White House briefing.
A new report from the Centers for Disease Control and Prevention says President Trump’s European travel ban was enacted too late to protect New York residents. “Although travel restrictions are an important mitigation strategy, by the time the European restrictions were implemented, importation and community transmission of Sars-CoV-2 had already occurred in NYC,” the report said.
Spain has reported its steepest daily rise in coronavirus infections in more than two months, with 580 new cases, after a rise of 390 cases on Wednesday. The regions of Aragon and Catalonia lead the increase, Reuters reports.Authorities have reimposed restrictions in some areas of Catalonia, including home confinement in the Lleida area affecting about 160,000 people, and health officials there said measures would have to be taken in the capital, Barcelona, but gave no further details.
Russian state-sponsored hackers are targeting UK, US and Canadian organisations involved in developing a coronavirus vaccine, according to British security officials. The UK’s National Cyber Security Centre (NCSC) said drug companies and research groups were being targeted by a group known as APT29, which was “almost certainly” part of the Kremlin’s intelligence services.
In the US, Florida has again broken its single-day record of coronavirus deaths, as the state struggles to get the virus under control. Florida health officials announced 156 residents died of coronavirus yesterday, breaking the record of 132 deaths reported on Tuesday morning. The new figure brings the total number of coronavirus deaths in the state to 4,677, with more than 315,000 cases confirmed.
The Israeli government is reported to be considering a full national lockdown during weekends and plans to shut all kindergartens. The expectation of a move comes as the cabinet is holding an emergency meeting following a surge in infections.
The team behind the development of a Covid-19 vaccine at Oxford University in the UK hope to begin tests on volunteers who will be intentionally exposed to the virus in a “challenge trial”, a move seen as controversial since there is no proven cure for the illness. Although challenge trials, in which healthy volunteers are given a pathogen, are routine in vaccine development, taking the approach for Covid-19, where there is no fail-safe treatment if a volunteer becomes severely ill, has been questioned.
Coronavirus has been the direct cause of death of nine out of 10 Italian victims, a study released on Thursday said, shedding new light on the pandemic which mainly struck the country’s northern regions. Since discovering its first infections in February, Italy has reported about 35,000 Covid-19 fatalities. However, health authorities said many of those who died were also affected by other ailments and this provoked a fierce debate on whether the virus was the actual cause of death.
The post Coronavirus live news: US Democrats told to avoid convention; Brazil cases pass 2m | World news appeared first on Shri Times.
via Blogger https://ift.tt/3eB04Rb
0 notes
Text
2020 VISIONS Six security risks across retail and ecommerce for the year ahead

Retail is going to face a range of rapidly changing and evolving technologies and customer habits in the year ahead. Here Malcolm Murphy, Technical Director, EMEA at Infoblox takes a look at some of the hot buttons you may need to press come January.
Retailers, ecommerce pure-plays and most customer facing businesses and brands have been faced with a decade of rapidly changing technologies and, as a result, huge shifts in consumer behaviour. 2020 isn’t going to see that slow down… so what are you going to be up against in the year ahead?
1: Embedded video in connected devices will take security threats to another level
As technology advances, the threat landscape is only going to grow in both volume and complexity. The rate at which badly-behaved devices are connecting to networks is going to be the biggest problem. Research from IHS Markit projects there will be as many as 30.7 billion IoT devices in use in 2020, which is expected to more than double to 75 billion by 2025 - this explosion of smart devices on the network only widens attack surfaces.
I strongly suspect that video cameras in IoT connected devices, such as video doorbells and embedded cameras in smart speakers, will be the next big threat to the network due to the richer information sets they hold. Since these devices are collecting more and more data, they are becoming increasingly interesting targets for hackers, so that data is at a higher risk of being compromised. Despite this risk, security is still not being prioritised by manufacturers in the design of smart products, so until this is addressed, we’ll continue to see breach levels rise.
2: ‘Zero Trust’ still won’t be a reality
Despite the hype, no one is actually doing “Zero Trust” yet. Putting the infrastructure in place to enable organisations to verify anything and everything trying to connect to its systems before granting access is a really hard thing to do, as we can’t easily layer it onto existing technology at scale
As it stands, we’re nowhere near being able to implement the Zero Trust concept at a cost-effective level, and this is unlikely to change in 2020. This approach will remain difficult, expensive and inconvenient. I think it will take a catastrophic event or new regulation to make organisations invest in Zero Trust, it won’t happen on its own.
3: We can no longer assume everyone is coming through the drawbridge, and need to secure the castle accordingly
Compared to the midyear of 2018, the number of reported breaches was up 54% in 2019 and the number of exposed records was up 52%, according to a report published by Risk Based Security. Networking is changing, and security has to change with it. As new ways of networking come to light, so do new points of vulnerability. For example, an organisation may have assumed it was routing everyone through a drawbridge, now it’s added several windows, doors and bridges. Assuming that everyone still come through the front door, despite all of these new points of access, makes you vulnerable.
It’s easy to go down one security path but not step back and consider the wider, changing needs. In 2020, organisations will need to stop and re-think their approach to network security based on the changes they have made to their infrastructure over time.
4: Smarter stores will create friction for retailers
A big driver of network security for retailers is smarter stores, which leverage in-store tech and networking through interactive screens, electronic shelf labels and more to improve in-store customer experience. Retail is, however, as hostile and unsophisticated an environment for IT as you can imagine, thanks to low budgets and outdated, legacy systems.
Retailers are used to assets having an incredibly long lifetime; point of sale systems, for example, are a big investment made to last years. This mentality will create friction between legacy technology and the push for smarter stores, and security investments are likely to fall to the bottom of the list. This conflict in mentality, alongside lower footfall as more consumers’ favour shopping online, is going to be an issue for retailers trying to improve in-store customer experience in 2020.”
5: CSOs are playing a rigged game
Many CSOs will lie awake at night worrying about their organisations security. The fact is, it’s unlikely to be a question of “if”, but a question of “how”. While CSOs are fighting a constant battle against the breach, it’s almost as though they’re playing a game that is rigged against them.
It’s hard to maintain a proactive mindset knowing that the likelihood of a breach is high. To minimise the burden, CSOs need to get buy in from the wider leadership team from the offset, and manage expectation that even with the best will in the world, hacks can’t always be prevented.
According to IBM’s 2019 Cost of a Data Breach Report, data breaches cost organisations a staggering $3.92m (£3.04m)on average. I expect that, as we move into 2020, more business leaders will come to recognise that earlier involvement of cyber security experts can help avoid a major data breach, which could derail plans, cripple production operations, or worse, cause a total loss of trust in the brand.
6: All the latest technology won’t save you if you leave the front door unlocked
When it comes to security, more isn’t always better. Even with state of the art security, hackers are still one step ahead. Old-fashioned ransomware still wreaked havoc in 2019, which old school protection could’ve prevented. For those using technology for good, it’s not necessarily the tech you deploy, it’s how you deploy it.
Those that continue to be pre-occupied with the latest shiny and new technology in 2020 will put themselves in the firing line for security breaches. Before you look at purchasing the latest upgrade, think about getting the most out of what you’ve got and ensuring the basics are done right first.
Threat hunting is a proactive way to help you get the most out of your existing systems and understand which areas are vulnerable. Looking at how you share and enrich this threat data and context across multiple technologies and how this data informs other security tools is also key. If you have two security tools working well, they will almost certainly work better if they are integrated and share data.
from InternetRetailing https://ift.tt/2S5iW3c
via IFTTT
0 notes
Text
At Cannabis Shops, Face Recognition Is Already a Thing
Mason Marks is a law professor at Gonzaga University and a Research Scholar at NYU Law School’s Information Law Institute. Find him on Twitter @MasonMarksMD
Imagine you are a medical marijuana patient driving to a cannabis dispensary. As you pull into the parking lot, surveillance cameras record your license plate number. You step out of the car, and walk toward the entrance.
A sign above the door reads “please look up for entry.” You crane your neck and gaze into a camera paired with artificial intelligence that analyzes your face. A red light suddenly turns green, and the door slides open. You enter the store and bypass a line of customers waiting at the register, opting instead for a self-service kiosk.
As you approach the machine, in-store cameras feed images to algorithms that analyze your appearance to determine if you might be carrying a weapon, and compare your face to millions of photos in a law enforcement database. When you finally reach the kiosk, it scans your face, identifies you as a returning customer, and greets you with a coupon for your favorite cannabis product.
This may sound like a scene from a sci-fi movie, but these tools are employed in cannabis dispensaries today. The cannabis industry is embracing new technologies like facial recognition and advanced video analytics throughout the supply chain—from grow rooms and processing facilities to distribution centers and retail dispensaries. The companies behind the technology say it benefits cannabis businesses, employees, and consumers. But in an industry marred by decades of mass-incarceration that has discriminated against communities of color, face surveillance poses serious privacy risks, and can easily be used for targeted harassment.
“It is hard, if not impossible, to find an example of a surveillance technology that has not been turned against groups that are already vulnerable in our structurally inequitable system,” said Shankar Narayan, Director of the Technology and Liberty Project at the ACLU of Washington, in an interview with Motherboard. Although legal for medical or recreational use in 33 states, cannabis remains illegal under federal law. Because it occupies a legal grey area, banks are hesitant to touch the industry, making it primarily an all-cash business and an attractive target for thieves. In Denver, Colorado, alone, there were 34 reported dispensary robberies in the first half of 2019.
Some tech companies see the risk of theft as an opportunity to sell facial recognition systems. Don Deason, VP of Sales for Blue Line Technology, claims his company’s platform has significantly reduced cannabis robberies. It works like this: When customers approach the front door of a dispensary, audiovisual cues prompt them to look up at a camera. If they comply, the system records an image of their faces, and the front door opens. If they decline or their faces are obscured, by a mask for example, then access is denied.
The system is also used to deter robberies and mass shootings in convenience stores, schools, and office buildings.

A facial recognition system from Blue Line Technology hangs above the entrance to a convenience store. Courtesy of Blue Line Technology
Deason told Motherboard that as long as customers don’t shoplift or cause a disturbance, “their information is deleted after 48 hours.” However, if a store’s management believes customers are misbehaving, they can tag each face with a unique number, and the system retains that information indefinitely. If tagged customers later return to the store, the system recognizes them and alerts employees of their arrival by email or text message. Deason said Blue Line encourages dispensaries not to confront tagged customers, but ultimately “store owners set the store security policy and procedures,” and, “the security response varies based upon store policy.”
Blue Line’s platform also controls access to restricted areas of cannabis businesses such as grow houses, cutting rooms, and safes, serving as a replacement for keys and access cards. When paired with other devices such as RFID tags, which are affixed to cannabis products, face recognition systems can track cannabis as it changes hands from one employee to the next.
“Many cannabis robberies are inside jobs,” said Matthew Heyl of Helix Security, a Denver company that provides surveillance products and services to cannabis businesses. He claimed video analytics and biometric access controls establish a chain-of-custody and deter diversion of legal cannabis to illicit markets.
For those reasons, government agencies that enforce cannabis laws are interested in facial recognition, said Steve Owens, the CEO of Adherence Compliance, a Denver consulting firm that has partnered with Blue Line. “This topic is really resonating with the regulators,” Owens told Motherboard. “When we mention it to Alameda County, they get it right away, because it helps them with their investigations.”
In addition to tracking employees and controlling access, facial recognition is used in dispensaries at the point of sale for age-verification. A Las Vegas based company called 420 Cyber markets its Badass Budtender kiosk as a replacement for human “budtenders” who check ID at the register. The kiosks can be equipped with facial recognition to ensure customers are of legal age.
Inside dispensaries, facial recognition can do far more. 420 Cyber markets what it calls “Video Active Security Monitoring” (VASM), which it says can determine whether customers carry concealed weapons, if there are warrants for their arrest, and whether their appearance matches “be on the lookout” (BOLO) alerts issued by police. It can reportedly recognize A-list celebrities if they happen to visit your store.
Consumers using 420 Cyber’s kiosks can also opt-in to personalization services: The units can scan and identify people’s faces, interpret their emotional responses to products, and help dispensaries learn which brands they prefer. 420 Cyber’s website says this data can be used to deliver targeted content “designed for individual viewing based on age, race, gender, location and daypart [the time of day a customer visits the store].”
Despite what vendors say, face recognition technology remains problematic and controversial. Algorithmic systems naturally adopt the objectives and values of their creators, and research shows that systems trained on insufficiently diverse datasets are often inaccurate and sometimes discriminate against women, racial minorities, and members of the LGBTQ community.
Even if the system is working as designed, face recognition can easily be adapted to target immigrants, activists, and other marginalized groups with little or no oversight. Citing those risks, at least three cities including San Francisco, Oakland, and Somerville, Massachusetts have banned municipal use of the technology. In June, the leading supplier of police body cameras, Axon, removed facial recognition from its services after an ethics board concluded it was “not yet reliable enough to justify its use.”
“Despite what developers may say, facial recognition technology has the potential to reinforce the racist and classist policies of prohibition”
“Technology makes a lot of promises, but there’s no guarantee they can deliver,” wrote Kamani Jefferson and Tyler McFadden in an email interview with Motherboard. The pair founded North Star Liberty Group, a DC-based government relations firm that advocates for ending cannabis prohibition while promoting racial and economic equality.
Jefferson previously served as President of the Massachusetts Recreational Consumer Council, where he helped push for a state-run social equity program that helps groups disproportionately impacted by the War on Drugs participate in the cannabis industry through professional training and mentoring. In July, Michigan announced its own social equity initiative. California created one last year, and San Francisco, Sacramento, and Los Angeles have local programs.
“Despite what developers may say, facial recognition technology has the potential to reinforce the racist and classist policies of prohibition,” Jefferson said. “It’s a classic case of a slippery slope, and until there’s a guarantee that not one innocent person will be thrown in jail due to the faults of this technology, I wouldn’t recommend cannabis facilities waste their money.”
Grayce Bentley is the Social Equity Coordinator for Cannabis Advising Partners in Long Beach, CA. In a phone interview, she told Motherboard: “I don’t think this is right at all, especially if facial recognition has been shown to be biased based on race, gender, et cetera.” Moreover, Bentley said most dispensaries serve a clientele consisting of both medical and recreational cannabis consumers, and “facial recognition should not be used in businesses where medical patients could be present.” She argued that collecting face data could violate federal health privacy laws such as the Health Information Portability and Accountability Act (HIPAA).
Data breaches will likely be a growing problem for the cannabis industry as well. In 2017, a company called MJ Freeway, a major provider of software to cannabis businesses, suffered multiple hacking attempts. In one incident, hackers obtained consumers’ date of birth, contact information, and other unspecified data. If the company had also kept images of customers’ faces, the breach could have been more disastrous.
All the companies Motherboard spoke with said they make efforts to protect face recognition data through encryption. “But encryption is not a panacea,” said Ido Kilovaty, a law professor at the University of Tulsa who specializes in cybersecurity. “Hackers can launch brute-force attacks or look for other vulnerabilities, and there is always a risk of insider threats.”
“It doesn’t matter if the developers ‘don’t see race’ when their algorithm and security staff undoubtedly do.”
Even if impenetrable cybersecurity was achievable, it wouldn’t protect consumers from discrimination based on facial recognition. In recent years, there has been a rash of troubling AI systems that attempt to make assumptions about peoples’ sexuality and potential criminality based solely on their facial features. Tech ethicists have warned that the trend threatens to revive long-disproven pseudoscience practices like physiognomy, which have historically been used to justify racism and discrimination.
Shankar Narayan said he’s concerned about mission creep—when technologies implemented for a specific purpose are shifted to another application. A cannabis business might start out using facial recognition to analyze people’s emotional responses to different products, “but you can take that further, and start analyzing people’s propensity for violence,” said Narayan. Since facial recognition may be biased against vulnerable communities, it could disproportionately mischaracterize members of those groups as dangerous.
Narayan also noted that private surveillance systems can easily be repurposed for use by law enforcement and federal agencies. One example is police use of Amazon’s Ring doorbell cameras, which was recently reported on by Motherboard. “While being operated by an individual entity, it’s a private camera, and it need not conform to any rules around surveillance that apply to government cameras. But the company may turn the data over to the government,” Narayan said. “And then for all intents and purposes, it’s functioning as a government camera.”
Some companies marketing facial recognition to the cannabis industry have deep ties to law enforcement. Blue Line was founded by Joseph Spiess, Tom Sawyer, and Marcos Silva. Spiess is Chief of Police for the St. Louis suburb of Brentwood, Missouri. Sawyer, a retired St. Louis detective and DEA agent, built his career investigating drug crimes. Silva, an Army veteran who served in the Iraq War, is a St. Louis police detective who designed, implemented, and oversees the city’s real-time crime center (RTCC).
Michael Kwet, a fellow at Yale Law School’s Information Society Project who researches surveillance technology, expressed concerns: “For years, these officers locked people away for possession and sale of marijuana, with devastating effects on communities of color. Now they’re cashing in to protect the legal marijuana industry with facial recognition, while people previously persecuted languish behind bars.”
According to its website, the RTCC operated by Blue Line’s Silva “is focused on monitoring, deterring and evaluating criminal activity in real-time with the help of the advanced technology in the center,” which includes license plate readers, gunshot spotters, and crime analysis software. In 2015, former Police Chief Sam Dotson told St. Louis Public Radio the RTCC would tap into surveillance cameras owned by private companies and use “new software that would allow the analysts to better predict crime.”
Blue Line told Motherboard it does not have access to the face recognition databases of the cannabis businesses it serves, and therefore, it cannot share that data with law enforcement. However, because its clients set their own security policies and responses, store owners are free to turn facial recognition data over to police. Through this kind of sharing between private and public surveillance networks, police could gain access to face data stored by dispensaries even in cities where facial recognition is banned for government use.
Prior to his current role at the ACLU of Washington, Shankar Narayan was the organization’s Legislative Director, and he worked on Initiative 502, Washington State’s recreational marijuana bill. Before that, he worked on medical marijuana legislation.
“In the context of that medical marijuana law, we went through a lot of these same issues, and there was intense concern over patient privacy. Coming off of that very intense discussion, there’s some deep irony that in the name of security, entities that sell cannabis are now installing these highly invasive surveillance mechanisms. That is really the opposite of the spirit in which we had the discussions around medical marijuana dispensaries, and I think we should be deeply concerned about privacy in that context.”
Addressing concerns about bias, Don Deason told Motherboard that Blue Line’s face recognition system “recognizes everyone equally,” and that the company is “not tracking age, gender, race, or what products people buy.” He said the system sorts faces into only three categories: “known, unknown, or threat,” and people are categorized as threats based solely on their behavior inside a cannabis business, not on their physical traits or facial expressions.
Os Keyes, a doctoral researcher at the University of Washington who studies human-computer interaction, told Motherboard that Blue Line “has an incredibly shallow understanding of the concerns about bias in facial recognition.” They noted that whether security guards or police stop and search customers or accuse them of shoplifting may be influenced by personal prejudices.
“Whether someone is accurately matched by facial recognition is, similarly, something that we know has racial and gender biases,” said Keyes. “It doesn’t matter if the developers ‘don’t see race’ when their algorithm and security staff undoubtedly do.”
Despite tech company efforts to protect face recognition data and reduce bias, many cannabis industry experts remain uncomfortable with the technology.
Kamani Jefferson and Tyler McFadden implied it is unnecessary. They referenced statistics suggesting crime has decreased in states and neighborhoods with licensed cannabis dispensaries.
“There’s no reason to believe that trend won’t continue,” they added.
Griffen Thorne, an attorney with the law firm Harris Bricken, expressed doubt that adopting facial recognition technology would help businesses comply with state and local cannabis laws. “In California, cannabis businesses must have a security plan. They must have video recording, and doors that lock,” he said. “Beyond those basics, you don’t need to use fingerprint scanners or facial recognition technology.”
Shankar Narayan asked, “How can we be a free society with this level of surveillance? It kills free speech, it chills constitutional activity, it disproportionately impacts communities of color, it’s subject to abuse, [and] there’s not a lot of checks and balances here.”
One thing seems certain: legislators, government agencies, and the cannabis industry itself, should involve potentially affected communities in deciding how facial recognition should be implemented in the industry, and whether it should be used at all.
At Cannabis Shops, Face Recognition Is Already a Thing syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
The Russian Timeline
I pulled this together from the various news outlets and (I believe) it is the most comprehensive timeline out there detailing past and present developments surrounding the Russian involvement in the elections and potential connections to Trump. Please feel free to share as widely as you like.
April 18, 2012
In a joint announcement by Exxon/Mobil’s CEO Rex Tilerson and Rosneft Executive Chairman Igor Sechin, Exxon and state-owned Russian oil company Rosneft unveil an offshore exploration partnership that could invest upward of $500 billion in developing Russia's vast energy reserves in the Arctic and Black Sea. Sechin, a close ally of Russian Prime Minister and President-elect Vladimir Putin, hailed the partnership, saying it had already added $7 billion to Exxon and Rosneft's combined market capitalization since it was announced.
June 21, 2013
Vladimir Putin awards Rex Tillerson the Order of Friendship.The Order of Friendship is awarded to Russian and foreign nationals for special merit in strengthening peace, friendship, cooperation and understanding between nations.
November 19, 2013
Trump holds Miss Universe pageant in Moscow. During this trip, later intelligence reports would suggest the KGB/FSB filmed Trump watching Russian prostitutes perform "golden showers" in his hotel room and begin compiling compromising financial and personal information on Trump.
February 22, 2014
Ukrainian President Viktor Yanukovych flees Kiev during a series of violent protests. Later, Vladimir Putin admits to helping Yanukovych escape Ukraine to Russia.
February 28-March 18, 2014
Russia invades the Ukraine and annexes Crimea and Sebastopol.
March 17, 2014
The US, the EU and Canada introduce the first round of specifically targeted sanctions against Russian the day after the Crimean referendum and a few hours before the Russian president Vladimir Putin, by signing a decree recognizing Crimea as an independent state, laid the groundwork for its annexation by Russia. The sanctions lead to the Russian financial crisis with losses estimated at $100 Billion Euros.
March 24, 2014
In an interview with Fox and NBC News Trump suggests imposing sanctions to hurt Russia economically and then later says he supports such sanctions. Trump also says (about Mitt Romeny) "Well, Mitt was right, and he was also right when he mentioned in one of the debates about Russia, and he said, 'Russia's our biggest problem, and Russia is, you know, really something."
April 28, 2014
The United States imposes a ban on business transactions within its territory on seven Russian officials, including Igor Sechin, executive chairman of the Russian state oil company Rosneft, and seventeen Russian companies. The result includes a block of the formerly announced partnership between Exxon and Rosneft.
June 16, 2015
Donald Trump announces he will run for president of the United States.
July 2015
A hacking group possibly linked to the FSB, the main successor to the K.G.B., entered Democratic National Committee servers undetected for nearly a year, security researchers said. The group was nicknamed Cozy Bear, the Dukes or A.P.T. 29 for “advanced persistent threat.”
December 17, 2015
Putin is quoted as saying (about Trump), "He’s a really brilliant and talented person, without any doubt,” Putin told reporters, according to a translation by Interfax. "It’s not our job to judge his qualities, that’s a job for American voters, but he’s the absolute leader in the presidential race.”
March 2016
Investigators believe that the G.R.U., or a hacking group known as Fancy Bear or A.P.T. 28, was the second group to break into the D.N.C., but it played a bigger role in releasing the committee’s emails.
March 21, 2016
Trump names Carter Page one of his foreign policy advisors. Page, Managing Partner of Global Energy Capital, is known for brokering energy deals in Russia and has been an advisor to (and investor in) Gazprom, the Russian state-controlled natural gas company.
May, 2016
Trump promotes Paul Manafort to campaign chair and chief strategist. Manafort worked as a political consultant for the Ukraine’s ruling party from 2006-2012, and specifically for then-Ukrainian Prime Minister, Viktor Yanukovych. During that time, Manafort persuaded the Ukrainian government to change its grain policies in a way that benefited a U.S. agribusiness giant, and to consider deals with Exxon and Chevron for oil exploration.
June 14, 2016
Russian government hackers penetrate the computer network of the DNC and gain access to the entire database of opposition research on Donald Trump.
June 15, 2016
American cyber-technology firm Crowdstrike releases a detailed statement about Russian hacking of the DNC.
Trump’s team issues a statement: “We believe it was the DNC that did the ‘hacking’ as a way to distract from the many issues facing their deeply flawed candidate and failed party leader.”
A hacker calling himself Guccifer 2.0 says he’s given the hacked emails to WikiLeaks, and also publishes them himself, complete with telltale Russian-language formatting errors.
July 2016
A January 27, 2017 Business Insider article details a dossier with unverified claims about President Donald Trump's ties to Russia contained allegations that Igor Sechin, Executive Chairman of Rosneft (and former deputy prime minister), offered former Trump foreign policy advisor Carter Page and his associates the brokerage of a 19% stake in the company in exchange for the lifting of US sanctions on Russia.
The dossier says the offer was made in July, when Page was in Moscow giving a speech at the Higher Economic School and just prior to the Republican National Convention. The claim was sourced to "a trusted compatriot and close associate" of Sechin, according to the dossier's author, former British spy Christopher Steele.
Yahoo News (September 23) reports that on that same Page trip, U.S. intelligence agencies received reports that Page met with another top Putin aide while in Moscow — Igor Diveykin. A former Russian security official, Diveykin now serves as deputy chief for internal policy and is believed by U.S. officials to have responsibility for intelligence collected by Russian agencies about the U.S. election.
July 22, 2016
WikiLeaks publishes the first in a series of hacked emails taken from the DNC.
It releases a statement on Twitter reading, "Today, Friday 22 July 2016 at 10:30am EDT, WikiLeaks releases 19,252 emails and 8,034 attachments from the top of the US Democratic National Committee -- part one of our new Hillary Leaks series," the introduction says.
"The leaks come from the accounts of seven key figures in the DNC," including Communications Director Luis Miranda (10,770 emails), National Finance Director Jordon Kaplan (3,797 emails), Finance Chief of Staff Scott Comer and others. The newly released emails cover the period from January 2015 through May 25, 2016.
July 24, 2016
Debbie Wasserman Schultz resigns from her position as DNC Chair amid email revelations that party officials were trying to undermine the candidacy of Sen. Bernie Sanders.
Clinton campaign manager Robby Mook tells ABC News' "This Week" that their researchers (Crowdstrike) believe the Russians are responsible for the attack.
July 25, 2016
The FBI announces it's investigating the hack.
The DNC apologizes to Sen. Sanders.
Trump: "The new joke in town is that Russia leaked the disastrous DNC e-mails, which should never have been written (stupid), because Putin likes me."
July 27, 2016
In a news conference, Trump tells reporters that if Russia is behind the DNC hack that they most likely accessed her deleted emails from her tenure as secretary of state."By the way, if they hacked, they probably have her 33,000 emails. I hope they do," Trump said. "They probably have her 33,000 emails that she lost and deleted.” He then says, directly facing toward the cameras: "Russia, if you're listening, I hope you're able to find the 30,000 emails that are missing."
July 28, 2016
Donald Trump, in an interview with Fox News' "Fox & Friends," clarifies that "of course" he was being "sarcastic" with his comments about Russia hacking into Clinton's deleted emails.
August 2016
Harry Reid (R-Nev) writes to FBI Director James B. Comey asking him to initiate an investigation into Page’s Moscow visit stating the FBI should investigate his meetings as part of a larger look into whether the Trump campaign was conspiring with the Russian government to tamper with the U.S. presidential election.
A New York Times investigation conducted with the help of Ukrainian National Anti-Corruption Bureau shows that Donald Trump’s campaign chairman Paul Manafort received $12.7 million in cash from the former president of Ukraine, Victor Yanukovych. The investigation causes Manafort to step down from his post. Steve Bannon replaces Manafort as Chief Strategist and Kellyanne Conway replaces Manafort as Trump’s campaign manager.
September 13, 2016
UN ambassador Vitaly Churkin lodges a formal complaint with the United Nations over a top U.N. official's condemnations of Donald Trump and some European politicians. Eight days before, Zeid went after Trump in a speech in The Hague, Netherlands, lumping the billionaire businessman with several populist leaders in Europe. "All seek in varying degrees to recover a past, halcyon and so pure in form, where sunlit fields are settled by peoples united by ethnicity or religion," Zeid said, calling it a sentiment they share with the Islamic State. "This is not only strange — it's scary," senior policy adviser Jake Sullivan said. "A major-party candidate for the presidency of the United States is being protected by the Kremlin. Wow."
September 23, 2016
Yahoo news reports that although Trump first mentioned Carter Page’s name when asked to identify his “foreign policy team” during an interview with the Washington Post editorial team, his precise role in the campaign remains unclear; Trump spokeswoman Hope Hicks last month called him an “informal foreign adviser” who “does not speak for Mr. Trump or the campaign.” When Trump campaign spokesman Jason Miller was asked about Page he responded Page “has no role” and added: “We are not aware of any of his activities, past or present.” Miller did not respond when asked why Trump had previously described Page as one of his advisers.
September 26, 2016
Carter Page announces he is taking a leave of absence from his work with the Trump campaign due to the controversy over Rosneft.
At the first presidential debate, Trump states “I don’t think anybody knows it was Russia that broke into the DNC. [Clinton’s] saying Russia, Russia, Russia, but I don’t—maybe it was. I mean, it could be Russia, but it could also be China. It could also be lots of other people. It also could be somebody sitting on their bed that weighs 400 pounds, OK?”
October 6, 2016
DC Leaks publishes some hacked DNC emails.
October 7, 2016
Beginning on Oct. 7, WikiLeaks publishes the first in a series of 50,000 emails belonging to Clinton campaign chairman John Podesta.
The Department of Homeland Security and the Office of the Director of the National Intelligence issue a joint statement concluding: “The U.S. Intelligence Community (USIC) is confident that the Russian Government directed the recent compromises of e-mails from US persons and institutions, including from US political organizations. The recent disclosures of alleged hacked e-mails on sites like DCLeaks.com and WikiLeaks and by the Guccifer 2.0 online persona are consistent with the methods and motivations of Russian-directed efforts. These thefts and disclosures are intended to interfere with the US election process.”
October 9, 2016
2nd debate: Trump questions whether Russia is behind the hacks and suggests "maybe there is no hacking."
“I notice any time anything wrong happens, they like to say ‘The Russians!’ She doesn't know if it's the Russians doing the hacking," Trump said of his rival Hillary Clinton. "Maybe there is no hacking. But they always blame Russia and the reason they blame Russia is because they think they are trying to tarnish me with Russia.”
October 20, 2016
3rd debate:
Trump: [Clinton] has no idea whether it is Russia, China or anybody else.
Clinton: I am not quoting myself.
Trump: You have no idea.
Clinton: I am quoting seventeen, seventeen [US intelligence agencies.] Do you doubt…
Trump: Our country has no idea.
October 30, 2016
FBI Director James Comey announces an investigation and possible link between Clinton email server and emails from Anthony Weiner.
November 6, 2016
FBI Director Jamey Comey affirms the FBI’s July decision not to charge Clinton after review of Weiner emails.
November 7, 2016
WikiLeaks releases second batch of thousands of DNC emails.
November 8, 2016
Donald Trump wins the US presidential election.
November 10, 2016
Deputy Foreign Minister Sergei Ryabkov states that Russian government officials conferred with members of Donald Trump’s campaign team in an interview with the Interfax news agency.
November 17, 2016
House Minority Leader Nancy Pelosi, D-California, tells reporters she believes there should be a federal investigation into the hacking and that her team's own investigations alongside the DNC and other Democratic groups had led them to believe it was the Russians.
December 5/6, 2016
Sergei Mikhailov, a senior officer of the Federal Security Service, or F.S.B. (formerly the K.G.B.) in their cyber security department was attending a routine staff meeting when several armed police officers burst in, threw a hood over his head, and dragged him from the room. That is the last anyone has seen of him. Following that day, the Russian State charged him with treason.
Later, Russian media broke the story that another high ranking intelligence official Russian Stoyanov), at Kaspersky Labs, a leading private sector cybersecurity firm, had been detained. There was sketchy information as to whether or not the official had also been imprisoned and charged. Kaspersky Labs, maker of anti-virus software, has long been rumored to be associated with the Russian government.
If true, the actions could be an attempt by the Russian government to remove leaks that would link them to the Russian election hacking.
December 7, 2016
Russia makes surprising announcement it has sold 19.5% of Rosneft, the state-controlled oil company. Reports on the investors are hazy, but include Glencore and Qatar. Although Rosneft is valued at $59 Billion, total investment by Glencore and Qatar is $3B Euros and additional funding may have occurred of up to $2.5Billion by Russian and Cayman Island banks and a series of shell companies.The deal defies expectations that no investor would dare buy a share in the Russian asset, given Western sanctions against the government of President Vladimir V. Putin.
December 9, 2016
President Obama’s counter-terrorism adviser Lisa Monaco announces that the intelligence community’s review of the Russian hacking incident will be completed before the inauguration and presented to Congress.
The Washington Post reports that the CIA says the hack was done to help Trump get elected.
The New York Times matches the Post's reporting and says the Republican National Committee was also hacked but information wasn’t shared.
Trump's transition team says of the intelligence community: "These are the same people that said Saddam Hussein had weapons of mass destruction. The election ended a long time ago in one of the biggest Electoral College victories in history. It’s now time to move on and 'Make America Great Again.'"
December 11, 2016
RNC Chairman, and Trump's incoming White House Chief of Staff, Reince Priebus and Trump deny the RNC was hacked and separately deny that Russia was trying to interfere in the election, counter to the DHS and DNI's October statement.
Trump tells "Fox News Sunday" that the reports of Russia hacking are "ridiculous" and “Nobody really knows, and hacking is very interesting. Once they hack, if you don’t catch them in the act you’re not going to catch them.” Trump also argues that U.S. intelligence has "no idea" if Russia or China are behind the hackings.
Breach remediation firm Crowdstrike points out that it did in fact catch the hackers “in the act,” monitoring their activities inside the DNC network for weeks.
Sen. John McCain (R-AZ) calls for a select committee to investigate the Russian hacking, saying "it’s clear the Russians interfered."
December 12, 2016
Republican lawmakers announce that congressional committees will also investigate the allegations made by the CIA.
December 13, 2016
Trump names Rex Tillerson his nominee for Secretary of State. Tillerson, CEO of Exxon Mobil, received the Russian Order of Friendship from Putin in 2011 following negotiation of a partnership to drill in the Arctic. The partnership was delayed due to US sanctions against Russia for its annexation of Crimea. Tillerson has had a close and personal relationship with Igor Sechin, head of the Russian oil giant Rosneft, for over a decade.
December 14, 2016
Rep. Devin Nunes, R-California, who chairs the House Permanent Select Committee on Intelligence, releases a statement, calling it "unacceptable" that intelligence community directors declined the House Intelligence Committee's request to be briefed on the hacking.
"The Committee is vigorously looking into reports of cyber-attacks during the election campaign, and in particular we want to clarify press reports that the CIA has a new assessment that it has not shared with us," Nunes added in the statement. "The Committee is deeply concerned that intransigence in sharing intelligence with Congress can enable the manipulation of intelligence for political purposes."
December 16, 2016
In a press conference, Obama says that the hacks were initiated by the “highest levels of the Russian government.” Obama suggests he will retaliate but doesn’t specify how.
December 26, 2016
The Telegraph is reporting (1/28/17) an ex-KGB chief suspected of helping the former MI6 spy Christopher Steele to compile his dossier on Donald Trump may have been murdered by the Kremlin and his death covered up. it has been claimed.
Oleg Erovinkin, a former general in the KGB and its successor the FSB, was found dead in the back of his car in Moscow on Boxing Day in mysterious circumstances.
Erovinkin was a key aide to Igor Sechin, a former deputy prime minister and now head of Rosneft, the state-owned oil company, who is repeatedly named in the dossier.
December 28, 2016
On reports of impending sanctions,Trump tells reporters, "I think we ought to get on with our lives.”
December 29, 2016
Obama announces sanctions against Russian officials, including expulsion of 35 Russian diplomats and the closing of Russian compounds in Maryland and New York on suspicion they were used for intelligence gathering.
Trump: "It's time for our country to move on to bigger and better things. Nevertheless, in the interest of our country and its great people, I will meet with leaders of the intelligence community next week in order to be updated on the facts of this situation."
The Russian government vows retaliation.
December 30, 2016
Putin makes the surprise announcement that he won’t kick U.S. diplomats out of Russia.
"We will not create problems for U.S. diplomats," Putin says in a statement. "We will not expel anybody.”
Trump: "Great move on delay (by V. Putin) - I always knew he was very smart!"
December 31, 2016
Trump: “I know a lot about hacking. And hacking is a very hard thing to prove. So it could be somebody else. And I also know things that other people don’t know, and so they cannot be sure of the situation.”
January 3, 2017
Trump tweets that his intelligence briefing on the Russian hacking evidence has been postponed.
January 5, 2017
Trump: "So how and why are they so sure about hacking if they never even requested an examination of the computer servers? What is going on?"
NBC News reports that the FBI said they had already captured the necessary forensic data via “upstream” intelligence, a term that refers to capturing data in transit.
January 6, 2017
Classified documents are presented to President Obama and President-elect Trump by four of the senior-most US intelligence chiefs -- Director of National Intelligence James Clapper, FBI Director James Comey, CIA Director John Brennan, and NSA Director Admiral Mike Rogers. These documents include allegations that Russian operatives claim to have compromising personal and financial information about Mr. Trump multiple US officials with direct knowledge of the briefings tell CNN.
January 10, 2017
The Daily Beast (1/11/17) reports a leaked dossier says that Diveykin (the report identifies him as “Devykin”) had warned Page at their meeting in July about the Kremlin preparing an ugly “kompromat” or compromising materials on Trump that involved the golden shower video.
January 11, 2017
Trump: “Intelligence agencies should never have allowed this fake news to ‘leak’ into the public,” Trump wrote on Twitter. “One last shot at me. Are we living in Nazi Germany?”
Trump admits to Russia hacking but denies the attacks were meant to boost him.
January 17, 2017
In a WSJ interview Trump suggested he would be open to lifting sanctions on Russia.
January 22, 2017
Rex Tillerson’s nomination for Secretary of State receives the endorsement of the Senate Panel.
January 23, 2017
Trump announces James Comey will remain FBI Director
13 notes
·
View notes
Text
Monday, June 7, 2021
Employers and the need for workers
(NYT) For the first time in a generation, workers are gaining the upper hand. Companies are becoming more willing to pay a little more to train workers, to take chances on people without traditional qualifications and to show greater flexibility in where and how people work, our senior economics correspondent writes. The share of job postings that say “no experience necessary” is up two-thirds over 2019 levels, according to one firm. The shift builds on changes already underway in the tight labor market before the pandemic, when the unemployment rate was 4 percent or lower for two straight years.
Ransomware attacks are closing schools, delaying chemotherapy and derailing everyday life
(Washington Post) It can feel abstract: A group of organized but faceless criminals hijacking corporate computer systems and demanding millions of dollars in exchange for their safe return. But the impact of these ransomware attacks is increasingly, unavoidably, real for everyday people. These crimes have resulted in missed chemotherapy appointments and delayed ambulances, lost school days, and transportation problems. A ransomware attack on Colonial Pipeline in May led to gas shortages and even dangerous situations caused by panic buying. This past week, hackers compromised the JBS meat processing company, leading to worries about meat shortages or other key food providers being at risk. Last fall, the Baltimore County Public Schools system was hit with ransomware and forced to halt classes for two days, which were being held virtually. As recently as Wednesday, ransomware attacks were causing problems across the country. In Martha’s Vineyard, the ferry service transporting people to and from the Massachusetts island said it had been hit by a ransomware attack that disrupted its ticketing and reservation process. “It’s not only that it’s getting worse, but it’s the worst possible time for it to happen,” said Robert Lee, chief executive of Dragos, an industrial cybersecurity firm. He says on average, there are likely 20 to 30 big ransomware cases happening behind the scenes in addition to the ones making headlines.
Drought and rain
(NYT) A severe drought of historic proportions has much of the Western half of the U.S. in its grip. Nearly all of California, Oregon, Nevada, Arizona, New Mexico, Utah and North Dakota are in drought, and in large areas of those states conditions are “severe” or “exceptional.” Wildfires of a size normally seen in summers have already occurred in California, Arizona and New Mexico. Experts are concerned that this summer’s wildfires will be severe and widespread. Reservoirs in California hold about half as much water as usual for this time of year. On the other side of the Pacific, the annual summer monsoon in South Asia begins this month. Years of data suggests global warming is likely to make monsoons worse.
Mexicans vote in midterm elections seen as referendum on president
(Reuters) Mexicans headed to the polls on Sunday to vote for a new lower house of Congress, state governors and local lawmakers, in a race seen as a referendum on President Andres Manuel Lopez Obrador’s policies and efforts to shake up Mexico’s institutions. All 500 seats in the lower house, 15 state governorships and thousands of local leadership positions are up for grabs, with some 93.5 million Mexicans eligible to vote. Since taking office in 2018 after a landslide victory, Lopez Obrador has expanded the role of the state in the energy industry and radically cut back on the cost of government to channel resources to the poor and his priority infrastructure projects. Though voters tend to criticize his government’s record on job creation and fighting crime, they are more skeptical of Mexico’s former rulers, now in opposition. Lopez Obrador has also benefited from the vaccine rollout.
Peruvian voters face choice between 2 polarizing populists
(AP) Peruvian voters will choose between two polarizing populist candidates Sunday in a presidential runoff held as the coronavirus pandemic continues to batter the Andean country and festering anger has led to fears of more political stability. Political novice Pedro Castillo and Keiko Fujimori, making her third run for the presidency, have both promised COVID-19 vaccines for all and other strategies to alleviate the health emergency that has killed more than 180,000 people and pushed millions into poverty. The pandemic not only has collapsed Peru’s medical and cemetery infrastructure, left millions unemployed and highlighted longstanding inequalities in the country, it has also deepened people’s mistrust of government as it mismanaged the COVID-19 response and a secret vaccination drive for the well-connected erupted into a national scandal. Amid protests and corruption allegations, the South American country cycled through three presidents in November. Now, analysts warn this election could be another tipping point for people’s simmering frustrations and bring more political instability. “I think in both situations the risk of social unrest is high. It’s a time bomb,” said Claudia Navas, an analyst with the global firm Control Risks. “I think if Castillo wins, people who support Fujimori or support the continuation to some extent of the economic model may protest.” But Navas said “a more complex scenario will evolve if Fujimori wins because Castillo has been able to create a discourse that has played well in some rural communities with regards to the social divide and saying that political and economic elites have orchestrated things to remain in power and maintain the social inequalities.”
Normandy commemorates D-Day
(AP) When the sun rises over Omaha Beach, revealing vast stretches of wet sand extending toward distant cliffs, one starts to grasp the immensity of the task faced by Allied soldiers on June 6, 1944, landing on the Nazi-occupied Normandy shore. On D-Day, more than 150,000 Allied troops landed on the beaches code-named Omaha, Utah, Juno, Sword and Gold, carried by 7,000 boats. This year on June 6, the beaches stood vast and empty as the sun rose, exactly 77 years since the dawn invasion. On D-Day, 4,414 Allied troops lost their lives, 2,501 of them Americans. More than 5,000 were wounded. On the German side, several thousand were killed or wounded. Normandy has more than 20 military cemeteries holding mostly Americans, Germans, French, British, Canadians and Polish troops who took part in the historic battle.
Amsterdam is crumbling
(NYT) Amsterdam, with its scenic canals lined with picturesque, 17th- and 18th-century buildings, a major European tourist destination, is slowly crumbling. Sinkholes are appearing in its small streets, and nearly half its 1,700 bridges are rickety and need repairs, frequently requiring trams to cross at a snail’s pace. As a huge project to shore up the canal walls gets underway, the city is beginning to look like one gigantic construction site. The fundamental problem is the state of the walls: About 125 miles of them are so dilapidated that they are in danger of collapsing into the canals, potentially taking buildings and people with them. Like much of the Netherlands, Amsterdam lies below sea level. Built on a swamp and heavily expanded in the 17th century, the city sits atop millions of wood pilings that serve as foundations. The Royal Palace on the Dam, for example, rests on 13,659 of them. Virtually everything in central Amsterdam is supported by these pilings. “At the time these were built to carry the weight of horses and carriages, not of 40-ton cement trucks and other heavy equipment,” said Egbert de Vries, the alderman in charge of what promises to be an enormous rebuilding project. As modern life changed the city, many houses were fortified with cement and concrete, but the underpinnings of streets and canal walls were ignored.
Young Chinese take a stand against pressures of modern life—by lying down
(Washington Post) Young Chinese are rebelling against society through a simple act of resistance: lying down. Examples of the tangping, or “lying flat,” way of life include not getting married, not having children, not buying a house or a car and refusing to work extra hours or to hold a job at all. “I stay at home and sleep and watch television series. Sometimes I go out for walks, read books and just think a lot,” said Daisy Zhang, 28, who described herself as “lying flat” for the last two weeks after leaving her job in the film industry in Wuxi in China’s Jiangsu province. Tangping has emerged over the last few months as the rallying call of Chinese millennials who have had enough of the rat race. Some compare them to the 1950s Beat Generation in the United States. Others call their behavior a form of nonviolent resistance or “ideological emancipation” from consumerism. Supporters portray it as a rejection of struggle and endless striving. Critics say it is defeatist. Ultimately, observers say, tangping is a reflection of China’s disenchanted middle class, faced with stagnant wages in increasingly expensive and competitive cities. “People realize there is no upward mobility,” said Yicheng Wang, a PhD student in political science at Boston University who studies propaganda and popular discourse. “It’s a negative acceptance. My life is like this. It will always be like this.”
After unending conflicts, Gazans wrestle with rebuilding—and whether it’s worth it
(Washington Post) For the 2 million residents of Gaza, last month’s hostilities were just the latest in an endless cycle of war, the fourth to convulse the Palestinian enclave along the Mediterranean in just 13 years. The latest fighting was impossible to escape as Israel struck more than 1,500 targets in the Gaza Strip. Hamas and other Gaza-based militants fired more than 4,300 rockets, wreaking terror on the other side of the border. More than two weeks after the cease-fire, life has returned; even beach cafes have reopened. But existence remains shaped by destruction and reconstruction. Families are being forced once more to rebuild and repair their homes, their businesses and what they can of their lives—their suffering compounded by losses on top of losses, trauma on top of trauma. After significant damage to family property in three of Gaza’s four conflicts since 2008, Kayan Abu Safiya is not sure it is worth rebuilding. “Everything you build here will be destroyed,” he said as he surveyed the pile of rubble that had been an apartment building he erected to house his many offspring as they grew up and got married. “Working, investing, getting money to help my children, and it all goes in one second.”
1 note
·
View note