#Server Routing Protocol Project Help
Explore tagged Tumblr posts
Text

Optimizing Performance in MEAN vs MERN Stack Applications
Introduction
In the world of web application development, choosing the right stack can make a significant difference in how your project performs, scales, and adapts to change. Both MEAN Stack development and MERN Stack development are popular choices, each offering its own set of tools and benefits. Whether you’re working with a MEAN Stack development company or a MERN Stack development company, understanding how these technologies behave under the hood will help you deliver faster, more reliable applications to your users.
Understanding the Core Components
At their heart, both MEAN and MERN stacks share the same four-layer architecture: a database, a server environment, an application framework, and a front-end library or framework. MEAN stands for MongoDB, Express.js, Angular, and Node.js, while MERN swaps Angular for React. MongoDB provides a flexible document-based data store, Express.js handles routing and middleware, and Node.js powers the server with its single-threaded, event-driven model. On the front end, Angular brings a full-featured framework with two-way data binding, whereas React offers a lightweight, component-based library that uses a virtual DOM for efficient updates.
Performance Characteristics of MEAN Stack Applications
MEAN Stack applications benefit from Angular’s comprehensive tooling and built-in change detection, which can help manage complex data flows out of the box. Angular’s ahead-of-time (AOT) compilation reduces runtime overhead, translating templates into optimized JavaScript before the browser ever loads them. However, because Angular is feature-rich, the initial bundle size can be larger, affecting the time it takes for users to see the first meaningful paint. With a MEAN Stack development company, you can lean on practices like lazy loading of modules and code splitting to keep the application responsive, loading only what’s necessary when it’s needed.
Performance Characteristics of MERN Stack Applications
MERN Stack development companies often praise React’s minimalistic core and the ability to pick and choose additional libraries to suit a project’s needs. React’s virtual DOM shines in scenarios where frequent UI updates occur, as it batches and diff-checks operations to minimize actual DOM manipulations. The downside? Developers need to assemble their own toolchain—state management, routing, form handling—which can introduce inconsistencies if not managed carefully. Yet, this flexibility allows for highly optimized builds: tree-shaking removes unused code, and server-side rendering (SSR) or static site generation (SSG) can be added to speed up initial page loads and improve SEO.
Shared Performance Optimization Strategies for MEAN and MERN Stacks
Regardless of whether you choose MEAN or MERN, some best practices apply across the board. Compressing assets like JavaScript and CSS using gzip or Brotli reduces payload sizes. Enabling HTTP/2 or newer protocols allows multiple resources to load over a single secure connection. Caching static assets with proper cache-control headers ensures repeat visitors experience lightning-fast page loads. On the database side, indexing frequently queried fields in MongoDB can drastically cut down response times. Finally, profiling server-side code with tools like Node’s built-in profiler highlights bottlenecks in route handlers or middleware, guiding targeted refactoring.
Frontend-Specific Optimization Techniques: Angular vs React
When optimizing an Angular-based front end, leverage change detection strategies such as OnPush to limit re-renders only to components whose inputs have truly changed. Use Angular CLI’s built-in budler to analyze bundle sizes and eliminate redundant code. In contrast, for React, employ memoization with React.memo() or useMemo to avoid unnecessary re-renders of pure functional components. Dynamic imports let you break the UI into smaller chunks, loading heavy components only when users navigate to them. Both ecosystems benefit from performance budgets: setting a size threshold for individual bundles keeps teams aware of the impact of new dependencies.
Optimizing React Performance in MERN Stack Applications
Within a MERN Stack development project, React performance can be taken further by implementing SSR or SSG through frameworks like Next.js. SSR improves time-to-first-byte by rendering HTML on the server, while SSG pre-builds pages at compile time, serving them as static files. When dynamic data is involved, incremental static regeneration combines the best of both worlds. Additionally, integrating a content delivery network (CDN) for your React assets offloads traffic from your Node.js server and brings resources closer to users worldwide. Finally, monitoring bundle sizes with tools like Webpack Bundle Analyzer ensures growth remains in check.
Backend-Level Performance Enhancements for Both Stacks
On the server side, clustering your Node.js process across multiple CPU cores ensures that incoming requests are spread evenly, increasing throughput. Utilizing connection pooling with MongoDB drivers reduces latency by reusing existing database connections. For compute-intensive tasks—image processing, encryption, or complex calculations—delegating work to a message queue (e.g., RabbitMQ or Redis streams) decouples these jobs from the request-response cycle, keeping APIs snappy. Applying rate limiting and request throttling guards against traffic spikes and malicious actors, maintaining stability under load.
Choosing Between MEAN vs MERN Based on Performance Needs
Your choice between MEAN Stack development and MERN Stack development often hinges on project requirements and team expertise. If you need a structured framework with best practices baked in and prefer convention over configuration, Angular within the MEAN stack provides a ready-made environment for large-scale applications. Conversely, if you value modularity, lightweight builds, and the freedom to select your own libraries, React in the MERN stack affords greater flexibility. A MERN Stack development company may be more agile in adopting the latest tools, while a MEAN Stack development company might excel at delivering comprehensive solutions with fewer third‑party dependencies.
Conclusion
Performance is a multi‑layered concern that touches every part of your application—from the database to the server, down to the tiniest UI component. Both MEAN and MERN stacks are capable of delivering robust, high‑speed web applications when approached thoughtfully. By understanding the strengths and trade‑offs of Angular and React, applying shared optimization techniques, and tailoring your choice to your team’s skill set and business goals, you’ll be well on your way to launching fast, responsive apps that delight users. Whether you partner with a MEAN Stack development company or engage a MERN Stack development company, prioritize ongoing performance monitoring and continuous improvement to keep your applications running at peak efficiency.
#MERN Stack development company#MERN Stack development#MEAN Stack development#MEAN Stack development company#Performance Analyzing#comparison
0 notes
Text
The Best 9 Python Frameworks for App Development in 2025
Python is the most popular and high-level, general-purpose programming language that supports multiple programming models, including structured, object-oriented, and functional programming. App developers often prefer using Python frameworks for App Development.

Developers often use Pyjnius, a Python library that allows access to Java classes. It can either launch a new Java Virtual Machine (JVM) within the process or connect to an existing JVM, such as the one already running on Android.
According to recent research from Statista, more than 48% of developers use Python frameworks for mobile app development.
What is a Python Framework?
Python frameworks are collections of pre-built modules and packages that help developers handle common tasks efficiently.
They simplify application development by providing ready-made solutions, so developers don’t have to start from scratch.
These frameworks also take care of details like thread management, sockets, and protocols, saving time and effort.
9 Best Python Frameworks for App Development in 2025
Explore here a list of Top 10 Python App Frameworks to Use in 2025:
1-Django
Django is a leading Python framework designed for building dynamic mobile and web applications with ease. It leverages a robust Object-Relational Mapping (ORM) system and follows the Model-View-Controller (MVC) pattern, ensuring clean, reusable, and easily maintainable code.
Whether you’re creating simple apps or scaling complex projects, Django’s powerful features make development faster and more efficient.
It has built-in tools like URL routing/parsing, authentication system, form validation, template engine, and caching to ensure a swift development process.
Django follows the DRY (Don’t Repeat Yourself) concept and focuses on rapid app development with a neat design.
This framework is the first choice of developers for any Python project due to its versatility, customization, scalability, deployment speed, simplicity, and compatibility with the latest Python versions.
According to a Stack Overflow survey, Django and Flask are the most popular Python software development frameworks.
Some examples popular examples of apps built with the Django framework are Instagram and Spotify.
Key Features of Django Framework:
Enables execution of automated migrations
Robust security
Enhanced web server support
Comprehensive documentation
Vast add-ins with SEO optimization
2-Flask
Flask stands out as a top-rated, open-source Python microframework known for its simplicity and efficiency. The Flask framework comes packed with features like a built-in development server, an intuitive debugger, seamless HTTP request handling, file storage capabilities, and robust client-side session support.
It has a modular and adaptable design and added compatibility with Google App Engine.
Besides Django, Flask is another popular Python framework with the Werkzeug WSGI toolkit and Jinja2 template.
Flask operates under the BSD license, ensuring simplicity and freedom for developers.
Inspired by the popular Sinatra Ruby framework, Flask combines minimalism with powerful capabilities, making it a go-to choice for building scalable and efficient web applications.
Key Features of Flask Framework:
Jinja2 templating and WSGI compliance
Unicode-based with secure cookie support
HTTP request handling capability
RESTful request dispatch handling
Built-in server development and integrated unit-testing support
Plugs into any ORM framework
3-Web2Py
Web2Py is an open-source, full-stack, and scalable Python application framework compatible with most operating systems, both mobile-based and web-based.
It is a platform-independent framework that simplifies development through an IDE that has a code editor, debugger, and single-click deployment.
Web2Py deals with data efficiently and enables swift development with MVC design but lacks configuration files on the project level.
It has a critical feature, a ticketing system that auto-generates tickets in the event of issues and enables tracking of issues and status.
Key Features of Web2py Framework:
No configuration and installation needed
Enables use of NoSQL and relational databases
Follows MVC design with consistent API for streamlining web development
Supports internationalization and role-based access control
Enable backward compatibility
Addresses security vulnerabilities and critical dangers
4-TurboGears
TurboGears is an open-source, full-stack, data-driven popular Python web app framework based on the ObjectDispatch paradigm.
It is meant to make it possible to write both small and concise applications in Minimal mode or complex applications in Full Stack mode.
TurboGears is useful for building both simple and complex apps with its features implemented as function decorators with multi-database support.
It offers high scalability and modularity with MochiKit JavaScript library integration and ToscaWidgets for seamless coordination of server deployment and front end.
Key aspects of TurboGears Framework:
MVC-style architecture
Provides command-line tools
Extensive documentation
Validation support with Form Encode
It uses pylons as a web server
Provides PasteScript templates
5-Falcon
Falcon is a reliable and secure back-end micro Python application framework used for developing highly-performing microservices, APIs, and large-scale application backends.
It is extensible and optimized with an effective code base that promotes building cleaner designs with HTTP and REST architecture.
Falcon provides effective and accurate responses for HTTP threats, vulnerabilities, and errors, unlike other Python back-end frameworks. Large firms like RackSpace, OpenStack, and LinkedIn use Falcon.
Falcon can handle most requests with similar hardware to its contemporaries and has total code coverage.
Key Features of Falcon Framework:
Intuitive routing with URL templates
Unit testing with WSGI mocks and helpers
Native HTTP error responses
Optimized and extensible code base
Upfront exception handling support
DRY request processing
Cython support for enhanced speed
6-CherryPy
CherryPy is an object-oriented, open-source, Python micro framework for rapid development with a robust configuration system. It doesn’t require an Apache server and enables the use of technologies for Cetera templating and accessing data.
CherryPy is one of the oldest Python app development frameworks mainly for web development. Applications designed with CherryPy are self-contained and operate on multi-threaded web servers. It has built-in tools for sessions, coding, and caching.
Popular examples of CherryPy apps include Hulu and Juju.
Key features of CherryPy Framework:
Runs on Android
Flexible built-in plugin system
Support for testing, profiling, and coverage
WSGI compliant
Runs on multiple HTTP servers simultaneously
Powerful configuration system
7-Tornado
It is an open-source asynchronous networking Python framework that provides URL handling, HTML support, python database application framework support, and other crucial features of every application.
Tornado is as popular as Django and Flask because of its high-performing tools and features except that it is a threaded framework instead of being WSGI-based.
It simplifies web server coding, handles thousands of open connections with concurrent users, and strongly emphasizes non-blocking I/O activities for solving C10k difficulties.
Key features of Tornado Framework:
Web templating techniques
Extensive localization and translation support
Real-time, in-the-moment services
Allows third-party authorization, authorization methods, and user authentication
Template engine built-in
HTTP client that is not blocking
8- AIOHTTP Python Frameworks for App Development
AIOHTTP is a popular asynchronous client-side Python web development framework based on the Asyncio library. It depends on Python 3.5+ features like Async and Awaits.
AIOHTTP offers support for client and server WebSockets without the need for Callback Hell and includes request objects and routers for redirecting queries to functions.
Key Highlights of AIOHTTP Python Framework:
Provides pluggable routing
Supports HTTP servers
Supports both client and WebSockets without the callback hell.
Middleware support for web servers
Effective view building
Also, there are two main cross-platform Python mobile app frameworks
9- Kivy Python Frameworks for App Development
Kivy is a popular open-source Python framework for mobile app development that offers rapid application development of cross-platform GUI apps.
With a graphics engine designed over OpenGL, Kivy can manage GPU-bound workloads when needed.
Kivy comes with a project toolkit that allows developers to port apps to Android and has a similar one for iOS. However, porting Python apps to iOS currently is possible with Python 2.7.
Features of Kivy Framework:
Enables custom style in rendering widgets to give a native-like feel
Enhanced consistency across different platforms with a swift and straightforward approach
Well-documented, comprehensive APIs and offers multi-touch functionalities
Source of Content: Python Frameworks for App Development
#topPythonframeworks#Pythonframeworksforappdevelopment#bestPythonframeworks#Pythondevelopmentframeworks#Pythonwebframeworks#top9Pythonframeworksfordevelopers#Pythonframeworksforbuildingwebapps#Pythonframeworksformobileandwebdevelopment#fullstackPythonframeworks#microframeworksinPython#Pythonappdevelopmenttools
0 notes
Text
Integration of WebRTC with FreeSwitch for Multi-Tenant IP PBX

The powerful Integration of WebRTC with FreeSwitch allows developers to design next-gen and scalable communication solutions such as PBX (Private Branch Exchange), Call Center Solutions and many more. This combination overcomes the drawbacks of traditional telephones while bringing modern web-based communication.
Using WebRTC and FreeSwitch solutions, Vindaloo Softtech has designed top-notch products such as PepperPBX and CallCentr8. Interestingly, with the integration of WebRTC with FreeSWITCH, VoIP calling has become streamlined through multi-tenant IP PBX systems.
In the absence of this integration, organizations face fragmented communication systems that require IP Phones to make calls. These complexities result in compatibility issues, additional costs, and complex setups. However, this integration has bridged the gap between IP phones and modern PBX systems.
What is PBX?
A PBX (Private Branch Exchange) is a phone system that businesses use to manage calls. It connects calls between employees, local lines, and the public phone network. Instead of giving each employee their own phone line, the PBX allows everyone to share a few external lines. This helps save money and comes with features like call conferencing, follow me, IVR, Time condition, call routing, voicemail, and managing multiple calls at once. Its main goal is to reduce the cost of needing a separate phone line for each person.
Introducing WebRTC
WebRTC (Web Real-Time Communication) is an open-source project that gives the means to real-time communication by supporting video conferencing, voice calls, and data sharing. This project facilitates RTC directly between all modern web browsers and other supported devices without requiring additional plugins or applications.
The Software Developers use the APIs written in Javascript for peer-to-peer communication, which happens directly between users’ devices without the need for an intermediary server, this way it ensures faster data exchange and reduces latency. Vindaloo Softtech, a custom VoIP application & WebRTC development company, has been offering custom WebRTC development services for years.
What is FreeSwitch?
FreeSwitch, an open-source carrier-grade telephony platform is a backbone for VoIP (Voice over Internet Protocol) software. This platform is highly scalable as business demands and can be installed on any cloud-based platform or on-premises. FreeSwitch is designed to route and interconnect communication protocols like SIP (Session Initiation Protocol), WebRTC, and others. This allows the creation of robust voice, video, and messaging systems. Hire Vindaloo Softtech for FreeSWITCH development services to reap top-notch features.
Read Also: The Future of FreeSWITCH Development – Trends to Watch Out For
Make VoIP Calls with FreeSwitch and WebRTC
FreeSwitch acts as the media server that handles routing and managing communication, while WebRTC allows real-time communication directly within web browsers. FreeSwitch natively supports Webrtc. When integrated, these two technologies enable businesses to make and manage VoIP calls through a cloud-based system that operates via the Internet.
The integration of WebRTC with FreeSWITCH allows us to build a multi-tenant IP PBX solution, a cloud-based system that manages VoIP calls from anywhere without relying on specific hardware or infrastructure. WebRTC clients use the WS/WSS protocol to communicate with FreeSWITCH via the SIP protocol, usually with SIP over WebSockets. It allows multiple clients or tenants to operate under a single PBX infrastructure while keeping their operations completely separate. It is a unified and cost-effective solution that enhances modern communication and accessibility.
What does a WebRTC Phone feature in a multi-tenant PBX system do for your business?
Using the FreeSwitch and WebRTC solution, Vindaloo Softtech, a leading VoIP software development company has designed the WebPhone feature in PepperPBX, a ready-to-deploy and secure PBX server. With the Webphone, you do not require any third-party softphone and IP or desk phones.
We have developed the below features using WebRTC and FreeSwitch for our PBX system,
Call transfer
DND support
Call Forward
Conferencing
Access Voicemails (Read & Total Count)
Call waiting
Multi Call Management
What Extra Do You Get With PepperPBX?
Total Control with Built-in Firewall: Manage your multi-tenant system with a smart dashboard and firewall. Giving you full control and security to block or allow services and ports with just a few clicks.
Robust Security: It features top-notch security with multi-factor authentication and a user-friendly interface. This system is secure and simple to manage, following trusted industry standards.
Simplified Customer Interactions: Features like IVR menus and call queuing make customer interactions seamless. It effortlessly handles inbound call centres and monitors calls.
Cloud Access: You get complete access to your system at any time from anywhere with a cloud-based platform. Through this, it ensures business continuity no matter where you are.
Specified user portal: This ensures effortless user management with direct login portals for Super Admin, Tenant Admin, and end users.
Why Should You Choose Multi-tenant PBX – PepperPBX?
Ready to Deploy
Pay Once, it’s Cost-effective
No Hidden Charges
Outstanding Scalability
Advanced Feature-packed
Secure with industry-standard protocols
User-Friendly Interface
Vindaloo Softtech, a custom VoIP development service provider, boosts features like WebRTC in a Multi-Tenant PBX System on the client’s requirement. Connect us to team up and take advantage of Custom Webrtc app development services, FreeSWITCH development solutions and a Multi-tenant PBX system.
#Custom VoIP Development#FreeSWITCH development#FreeSWITCH development services#IP PBX#Multi Tenant IP PBX Solution#pbx server#VoIP PBX systems#VoIP Software Development Company#WebRTC Development#WebRTC development services#WebRTC Solution#WebRTC solution development
0 notes
Text
Network Programming Course Online
Are you an aspiring engineer with little or no experience in network programming? Our Network Programming Course Online is designed just for you. With a focus on Linux networking, this course takes you through the essential concepts and skills needed to build real-world network applications.
In today’s tech-driven world, networking is the backbone of communication. This course starts with foundational networking concepts, helping you understand how devices communicate over a network. You’ll learn the basics of IP addressing, routing, and network protocols like TCP and UDP, which are crucial for any networked system.
The heart of the course lies in Linux network programming. You’ll dive into Linux networking APIs and master socket programming—key tools for building powerful applications. Whether you’re interested in crafting server-client models or implementing custom protocols, the course has you covered. Step-by-step lessons will guide you from simple to advanced applications, ensuring you grasp each concept thoroughly.
What makes this course unique is its blend of theory and hands-on practice. Alongside learning, you’ll work on practical assignments to apply your knowledge in real scenarios. By the end of the course, you’ll complete a capstone project where you’ll design and build a fully functional network application on Linux. This project not only strengthens your skills but also adds value to your portfolio.
No prior experience? No problem! Our course is tailored for beginners; each lesson is explained in simple, easy-to-follow language. Whether you aim to kickstart your career or sharpen your existing skills, this course provides a strong foundation for your networking and Linux programming journey.
Take the first step toward becoming a skilled network programmer. Enroll today and bring your ideas to life in the world of networking!
Network Programming course, Network Programming online, Network Programming training, online Network Programming course, online training Network Programming, online course Network Programming, Learn Network Programming Writing Network, Programs project based Training in Network, Programming project and training in Network Programming, Linux Network Programming.
#Network Programming course#Network Programming online#Network Programming training#online Network Programming course#online training Network Programming#online course Network Programming
0 notes
Text
Step-by-Step Guide: How to Build Effective Call Center Software
In today’s fast-paced digital landscape, an effective call center software system is essential for any business aiming to enhance customer service, streamline communications, and boost overall efficiency. Building call center software from scratch can seem daunting, but breaking down the process into manageable steps can make it far more approachable. If you're looking for a starting point or even considering options for call center software free, this guide will help you understand the essential elements and how to create a system that’s scalable and impactful.
Step 1: Define Your Goals and Requirements
Every successful software project begins with a clear understanding of its purpose. Start by defining the specific goals of your call center software. Do you need a solution to handle inbound customer support calls, or are you looking to enable outbound sales calls as well? Make a list of must-have features, such as:
Interactive Voice Response (IVR): An IVR system can route calls to the right agent or department.
Automatic Call Distribution (ACD): This feature distributes calls based on various factors like agent skill level and availability.
Customer Relationship Management (CRM) Integration: Syncing your call center software with CRM ensures agents have access to customer history, improving personalization.
Real-Time Analytics and Reporting: These metrics help you assess performance and make data-driven decisions.
Clearly defined goals and features will guide every step of the software development process.
Step 2: Choose Your Technology Stack
The technology stack refers to the software and programming languages needed to build your call center software. A typical call center system requires a combination of front-end (user interface) and back-end (server-side) technologies.
Front-End: JavaScript frameworks like React or Angular are commonly used to create a responsive and user-friendly interface.
Back-End: For handling calls, user data, and system configurations, popular choices are Node.js, Python, and Java.
Database: A robust database like MySQL, MongoDB, or PostgreSQL will help manage call logs, customer data, and agent information efficiently.
Voice over Internet Protocol (VoIP) Integration: For voice calls, integrate VoIP technology, which allows your software to make and receive calls over the internet.
Consider open-source options or call center software free tools for some of these components to minimize initial costs and get your software off the ground faster.
Step 3: Design User Interface and User Experience (UI/UX)
The success of any software largely depends on its usability. Design a simple, intuitive user interface that enables agents to quickly access the information they need, reducing call handling time and improving customer satisfaction. Here are some tips for an effective UI/UX design:
Prioritize Key Features: Highlight frequently used features on the main dashboard to minimize navigation time.
Use Visual Indicators: Visual cues, like color-coded call statuses, help agents easily manage calls and track their tasks.
Optimize for Speed: Avoid loading screens and unnecessary clicks to streamline workflows.
Wireframing tools such as Figma or Sketch are useful for creating visual layouts before moving into the development phase.
Step 4: Develop Core Functionalities
With your requirements defined, technology stack chosen, and UI designed, it’s time to start coding the core functionalities of the software.
IVR System: Use a VoIP provider API like Twilio to implement a customizable IVR system.
Call Routing (ACD): Build rules for automatic call routing based on agent skills, priority, and availability.
Call Recording and Monitoring: Enable call recording to ensure quality assurance and allow monitoring for real-time feedback.
CRM Integration: APIs provided by CRM software like Salesforce or HubSpot can allow seamless integration, enabling agents to access customer data directly from the call center software.
Step 5: Test and Refine
Testing is an essential part of any software development process. Conduct thorough testing to identify bugs, improve system reliability, and ensure a smooth user experience. There are several testing methods you should consider:
Unit Testing: Test individual components of the software to ensure they work as expected.
Load Testing: Simulate high call volumes to assess the system’s capacity and stability.
User Acceptance Testing (UAT): Allow a few agents to use the software and provide feedback before full-scale deployment.
Make necessary adjustments based on test results to ensure a seamless experience for both agents and customers.
Step 6: Launch and Train
Once testing is complete and the software is fine-tuned, you’re ready to deploy. However, successful implementation goes beyond just software. Agents will need training to adapt to the new system, especially if they’re moving from a more traditional call-handling approach.
Provide tutorials, guides, and live demonstrations to help them familiarize themselves with key features and functionalities. This will boost adoption rates and ensure your team uses the software to its full potential.
Step 7: Regular Maintenance and Updates
Building effective call center software doesn’t end with the launch. Regular maintenance and updates are crucial to keep up with evolving customer needs and technological advancements. Monitor system performance, gather feedback from agents and customers, and address issues promptly. Plan periodic updates to add new features and improve security, usability, and efficiency.
Final Thoughts
Developing your own call center software is a significant endeavor, but by following these steps, you can create a tailored solution that meets your organization’s specific needs. If budget is a concern, consider leveraging call center software free options for certain functionalities to minimize costs and scale over time. With the right approach and a commitment to continuous improvement, your custom-built call center software can become a powerful asset for driving customer satisfaction and operational success.
FAQ
What is Chicago Pub Cambridge known for?Chicago Pub Cambridge is famous for its welcoming atmosphere, a great selection of drinks, delicious food, and live entertainment, including karaoke and pool tables.
Where is Chicago Pub Cambridge located?Chicago Pub Cambridge is located in Cambridge, Ontario, conveniently accessible from various parts of the city.
What types of food does Chicago Pub Cambridge offer?The pub offers a variety of classic pub food options, including burgers, wings, fries, and other comfort foods, catering to various tastes.
Does Chicago Pub Cambridge have a lounge area?Yes, Chicago Pub Cambridge features a comfortable lounge area where patrons can relax, socialize, and enjoy their drinks.
Is there live entertainment at Chicago Pub Cambridge? Absolutely! Chicago Pub Cambridge hosts live entertainment events, including karaoke nights and music performances, to enhance the pub experience.
Can I host private events at Chicago Pub Cambridge? Yes, the pub offers options for private events and parties. Contact the venue for more details on availability and arrangements.
Does Chicago Pub Cambridge have pool tables?Yes, there is a pool hall area where patrons can play billiards, making it a great spot for pool enthusiasts.
Are reservations required at Chicago Pub Cambridge? Reservations are not typically required, but it’s recommended for larger groups or special occasions to ensure a spot.
What are the opening hours of Chicago Pub Cambridge?The pub’s hours may vary, so it’s best to check their website or call ahead for the most current information.
Is Chicago Pub Cambridge family-friendly? Chicago Pub Cambridge is primarily a pub and lounge, so it may be more suited for adults, though some events or times may be more family-friendly.

0 notes
Text
Intel IPU E2100-CCQDA2: Intel Infrastructure Processing Unit

What Is Intel IPU?
E2100-CCQDA2
In response to the increasing demands of contemporary data centers for enhanced security, greater performance, and complicated data processing, Intel is introducing the Intel Infrastructure Processing Unit (Intel IPU) Adaptor E2100-CCQDA2HL. This 200GbE Intel IPU E2100 PCIe adapter, which is half-length and full-height, is designed to function in a variety of PCIe-compliant servers and meet changing client needs.
The purpose of Intel’s Infrastructure Processing Unit (IPU) is to improve workloads related to data centers and cloud infrastructure. It is a specialized hardware component. It helps free up CPU time for application workloads by offloading networking and storage chores. Large-scale data centers can manage resources more effectively because to the IPU’s increased network traffic, better data processing, and increased security.
- Advertisement -
Effectiveness for the Changing Data Center
Power optimization becomes importance as artificial intelligence capabilities in data centers keeps expanding. With this new Intel IPU E2100 adaptor, full performance may be achieved without the need for additional power supply.
The Intel IPU E2100 adaptor is made with the future in mind, aiming to maximize infrastructure and spur innovation. The most recent adapter is very adaptable and supports a large number of use cases and applications.
The Intel IPU E2100 improves networking speed, storage offload, and security with AI clusters.
The IPU virtualizes network and storage services for tenant hosting, making cloud service access simple.
The IPU effectively offloads container networking and storage in Kubernetes systems.
Additionally, the IPU controls packet processing in appliances, makes accelerators-as-a-service possible, and simplifies top-of-rack operations in smart switches.
Image Credit To Intel
Intel IPU E2100 Adaptor
One particularly noteworthy feature is the availability of Falcon reliable transport in the IPU, which addresses the issues associated with lossy fibers. Falcon dependable transport is an open-source hardware-assisted transport developed by Google for demanding workloads such as storage, AI/ML, HPC, Cloud RDMA, and RPC. It builds upon the current RDMA technology in Ethernet networks to provide low latency and low jitter.Image Credit To Intel
Furthermore, without needing modifications to already-existing applications, Falcon dependable transport guarantees low-latency and high-bandwidth performance for RDMA messages and NVMe instructions in cloud-scale systems.
Built-in security and PSP, a scalable security protocol that supports cloud environments and streamlines networking administration, are features of its connection-oriented design. Falcon provides end-to-end hardware routes for both initiator and target storage applications, and it is fully backward compatible with RDMA and storage applications.
Additionally, by enabling DMTF Redfish, Intel have made IPU administration simpler. Redfish offers a standardized, effective, and safe interface for managing IPUs remotely. Redfish guarantees the continuous smooth, efficient, and safe functioning of your data center by providing users with complete control over infrastructure with the least amount of complexity.Image Credit To Intel
Join on October 15–17 at the Open Compute Project (OCP) Summit as Intel announce its newest IPU adaptor. Intel IPUs are solutions that match the demands of future data processing, not merely little hardware improvements. The Intel IPU E2100 is designed to meet the changing demands of businesses worldwide, from more cloud virtualization to advanced AI infrastructure workloads and increased power efficiency.
Intel Infrastructure Processing Unit
In the data center, the Intel Infrastructure Processing Unit (Intel IPU) Adaptor E2100-CCQDA2 provides better security features, virtual storage enablement, and infrastructure acceleration. The adapter has a 200GbE bandwidth, comprehensive packet processing pipeline, NVMe, compression, and crypto accelerators.
Features like as storage transfer, device management, telemetry, and intricate packet-processing pipelines may be executed by customer-provided software on the Arm Neoverse N1 computing complex. This Intel IPU E2100 adaptor offers the fast innovation required for the contemporary data center by employing accelerated hardware and software operating in the computing complex.
Workload separation and isolation for infrastructure
By eliminating the infrastructure overhead from conventional host-based network and storage infrastructure applications, IPUs optimize host the CPU applications, whether tenants in a cloud environment or application workloads in an edge or corporate context.
Transfer virtualized networks to the IPU so that tasks may be processed more quickly by the accelerators
Host CPUs may be employed for more revenue-generating and workload-intensive activities in an IaaS.
Use detached virtualized storage in lieu of previously required local disk storage.
The variable disk storage allocation made possible by this design reduces total expenses.
Read more on govindhtech.com
#IntelIPU#E2100CCQDA2#hardwarecomponent#IntelInfrastructureProcessingUnit#intelml#ai#cpu#artificialintelligencecapabilities#Kubernetessystems#storageapplications#detachedvirtualizedstorage#localdiskstorage#Transfervirtualizednetworks#technology#technews#news#govindhtech
1 note
·
View note
Text
Mastering the Future of IT Careers

The IT industry is rapidly expanding, offering vast career opportunities. To excel, gaining the right skills and certifications is crucial. Network Engineer Training, Cloud Network Engineer Certification, and Advanced IT Training are essential for mastering the latest technologies and practical skills. This guide highlights how such training prepares you for roles in network security, systems engineering, and more, ensuring you thrive in today’s dynamic IT sector.
Advanced IT Training: Elevate Your Career
Advanced IT Training is crucial for staying ahead of industry trends. These programs are designed to enhance your technical expertise and provide in-depth knowledge of the latest developments in IT infrastructure, network management, and cybersecurity. From Network Infrastructure Training to Mastering IT Sector Skills Development Advanced training will help you become proficient in managing complex systems.
Comprehensive Network Engineer Training
Network Engineer Training is the foundation for those aspiring to build and manage secure, efficient networks. This training covers essential skills like routing, switching, and troubleshooting network issues. You’ll gain hands-on experience with real-world scenarios, making you a valuable asset in any IT environment. Specialized training, such as NOC Engineer Training, focuses on monitoring network performance and resolving issues quickly, ensuring you can maintain high network availability.
Network Security Engineer Training: Protecting Critical Systems
With the rise in cyberattacks, Network Security Engineer Training is crucial for protecting network infrastructure. This specialized training teaches you to design, implement, and manage security protocols to safeguard data. Practical IT Skills Training provides the hands-on experience needed to effectively address cybersecurity threats.
Cloud Network Engineer Certification: Preparing for the Future of IT
Cloud computing is transforming the way businesses operate, and Cloud Network Engineer Certification positions you at the forefront of this shift. In this program, you’ll learn to design, deploy, and manage network systems within cloud environments like AWS, Azure, and Google Cloud. This certification not only enhances your knowledge of cloud technologies but also makes you a sought-after candidate in the IT job market.
Hands-On IT Training and Real-World IT Projects
Hands-On IT Training and Real-World IT Projects are crucial for skill development. These programs offer practical experience by simulating job challenges. Systems Engineer Training, for instance, includes working on real systems to build competence in managing and troubleshooting IT infrastructure.
IT Job Training with Placement: Launch Your IT Career
IT Job Training with Placement programs bridge the gap between education and employment, focusing on IT Sector Skills Development. These courses often partner with top companies to place graduates in high-demand roles in networking, security, or cloud engineering.
Industry-Relevant IT Courses: Stay Current with the Latest Technologies
Staying updated with Industry-Relevant IT Courses is crucial for success. Latest IT Technologies Training and Network Infrastructure Training keep your skills current. Continuous learning in automation, AI, and cloud computing provides a competitive edge and prepares you for future advancements.
NOC Engineer Training: Critical for Network Operations
NOC Engineer Training is vital for maintaining smooth network operations. It provides hands-on experience with monitoring tools and network management systems, preparing you to ensure uptime, resolve outages, and support mission-critical services in IT departments.
Building a Future in IT with Systems Engineer Training
Systems Engineer Training provides the skills necessary to design and manage large-scale IT systems. This training covers a wide range of technologies, including servers, storage, and virtualization. Through Hands-on IT Training, you’ll learn how to manage both hardware and software, ensuring that IT systems are efficient, scalable, and secure.
Conclusion
In a rapidly evolving industry, mastering the latest IT skills is essential for career success. Whether you’re aiming for a role as a network engineer, cloud specialist, or systems manager, Advanced IT Training offers the knowledge and experience needed to excel. Through a combination of hands-on learning, real-world projects, and industry-relevant courses, you’ll gain the expertise to thrive in the IT sector and secure your future in this exciting field.
0 notes
Text
Selecting the Ideal Tech Stack for Your VoIP Project

Software development involves various technologies and processes that are constantly evolving with new tools and frameworks. While these advancements simplify development, they also add complexity when selecting the right technologies for a project. Beyond the technical aspects, successful software development requires strong teamwork, project management and communication among diverse teams. These skills are crucial for keeping projects on track and within budget. Our blog article aims to give you a clear understanding of the crucial factors to consider when choosing the right technology stack for your software development project.
Understanding the tech stack
A tech stack is a set of tools and technologies used to build and run an application to cover everything from servers and databases to frontend and backend frameworks. Here’s a quick look at its main components:
Frontend: Handles the user interface and experience with technologies like HTML, CSS, JavaScript, and frameworks like React, Angular and Vue.js.
Backend: Manages business logic, database interactions, and server setup using languages like Python or Ruby and backend frameworks.
Databases: Store and manage application data, including relational databases like MySQL and NoSQL databases like MongoDB.
DevOps and Cloud Services: Ensure your application is integrated, scalable, and well-maintained.
VoIP Platforms
FreeSWITCH, Kamailio, OpenSIPS, and Asterisk are top platforms for creating VoIP services.
FreeSWITCH is an open-source platform that connects and routes communication protocols.
Kamailio and OpenSIPS are high-performance SIP servers for managing voice, video, and real-time communication.
Asterisk is a free framework that turns a standard computer into a powerful communication server.
Tech Stacks in Practice
Have you ever wondered what technology stacks power your favorite brands? Let's explore the tech stacks some industry leaders use and see what they rely on to deliver their services.
Uber Tech Stack:
Web Servers: NGINX, Apache
Databases: MySQL, PostgreSQL, MongoDB
Server-side Framework: Node.js
Programming Languages: Python, Java, JavaScript, Objective-C
Uber's tech stack combines robust web servers with versatile programming languages and frameworks, enabling smooth communication and data management across its platform.
Instacart Tech Stack:
Server: NGINX
Databases: PostgreSQL, Redis
Server-side Framework: Rails
Programming Languages: Ruby, Python, Objective-C
Instacart uses a streamlined stack focused on efficiency and reliability. It strongly emphasizes fast database operations and a robust server-side framework.
Reddit Tech Stack:
Server: NGINX
Databases: PostgreSQL, Redis
Server-side Framework: Node.js
Programming Languages: JavaScript, Python
Reddit's stack is optimized for handling large amounts of user-generated content. It uses powerful databases and a modern server-side framework to maintain its performance and scalability.
These examples highlight brands' different choices in building their tech stacks tailored to their specific needs and operational demands.
Choosing the Right Tech Stack for VOIP App Development
Selecting the right tech stack for app development can be overwhelming, especially for non-technical entrepreneurs. While developers often have their preferred stacks, it's wise to seek guidance from a subject-matter expert. An expert can provide valuable insights and help you avoid future issues. If you're short on resources, start with these simple steps:
Understand Your Users' Needs: Focus on what your users need. For example, if most of your users are on mobile devices, consider a "mobile-first" tech stack. If your app is "mobile-only," your tech stack will likely differ from other types of applications.
Define Your Development Needs: The complexity and scale of your app will influence your tech stack choice:
Small Projects: Well-defined stacks like Python-Django or Node.js-React are ideal for simple apps like MVPs or one-page apps.
Medium Projects: E-commerce stores or mid-market apps require more complex stacks with multiple layers of programming languages and frameworks.
Large Projects: Complex marketplaces or social apps need a robust tech stack designed to handle high-volume use and maintain performance.
Evaluate Your Resources: When choosing a tech stack, consider your available resources. Even the best tech stack won't be effective without the right developers to implement it. Many frameworks and tools are open-source and free to use, but remember to account for costs related to servers and hosting when making your decision.
Essential Components for a VoIP Software Technology Stack
Let’s understand these components.
Real-Time Communication Protocols: SIP (Session Initiation Protocol) and RTP (Real-Time Transport Protocol) are essential for managing voice, video, and messaging sessions. WebRTC enables real-time communication directly in browsers and mobile apps, making development easier.
Codecs: Codecs like G.711, G.722, G.729, and Opus compress and decompress voice data, balancing call quality and bandwidth usage.
Programming Languages: Python and Java are commonly used for their simplicity, readability, and strong support for multithreading and concurrency.
Web and Mobile Frameworks: Angular and Node.js are popular for web development, while Flutter and React Native are favored for cross-platform mobile apps.
Databases: SQL databases like MySQL and PostgreSQL handle structured data, while NoSQL databases like MongoDB offer scalability for unstructured data.
Server Technologies: Cloud services like AWS, Google Cloud, and Microsoft Azure provide scalable, secure environments with various development tools.
Testing Tools: Selenium for UI testing and Apache JMeter for load testing help ensure the software performs well and offers a good user experience.
Take Away
A tech stack is essential for a startup or business's success, so selecting the right technologies, languages, frameworks, and tools is essential.
Choosing the right technology stack for VoIP software development depends on your project's specific needs and goals. To make the best choice, follow these three rules: prototype and test, seek expert advice both within and outside your team and stay flexible. Doing so will help you build a strong and scalable product. Consulting experienced developers or software development companies can help you get tailored recommendations. With the right choice, your VoIP application will meet your current needs and be adaptable to future changes.
0 notes
Text
do i need vpn for tor project
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need vpn for tor project
VPN for Tor anonymity
Using a VPN in conjunction with Tor can enhance your online anonymity and security. Tor is an open-source browser that helps users maintain privacy and access the internet without revealing their location or browsing habits. While Tor routes your internet traffic through a series of servers to conceal your identity, combining it with a VPN adds an extra layer of protection.
VPN, or Virtual Private Network, encrypts your internet connection, making it difficult for third parties to monitor your online activities. When you connect to a VPN server before accessing Tor, your ISP, government agencies, or hackers won't be able to see that you are using Tor, further securing your privacy.
By using a VPN with Tor, you can prevent malicious entities from tracking your online behavior, enhance your protection against cyber threats, and circumvent censorship or content restrictions in certain regions. However, it's important to choose a reliable VPN provider that has a strict no-logs policy to ensure that your online activities remain private and secure.
When selecting a VPN for Tor anonymity, consider factors such as strong encryption protocols, a large server network for better connection speeds, and compatibility with Tor browser. Additionally, ensure that the VPN service is reputable and has a proven track record of safeguarding user data.
Overall, combining a VPN with Tor can significantly bolster your online privacy and security, allowing you to browse the internet anonymously and freely without compromising your sensitive information.
Tor without VPN risks
Using Tor without a VPN can expose users to certain risks that they should be aware of. Tor, short for The Onion Router, is a privacy-focused tool that provides anonymity by routing internet traffic through a series of servers operated by volunteers around the world. While Tor helps protect user privacy and data from surveillance, it does have limitations when used alone.
One of the main risks of using Tor without a VPN is the lack of end-to-end encryption. While Tor encrypts traffic between each node in the network, the final connection to the destination website may not be encrypted. This leaves user data vulnerable to interception by malicious actors, especially when accessing websites that do not use HTTPS.
Furthermore, without a VPN, your internet service provider (ISP) can still see that you are using Tor. Although they cannot see the exact contents of your traffic, ISPs may become suspicious of Tor use, potentially leading to targeted surveillance or restrictions on your internet access.
Another risk of using Tor without a VPN is the potential for malicious exit nodes. These are the final servers through which your internet traffic exits the Tor network to reach its destination. Without the additional layer of encryption provided by a VPN, malicious exit nodes could intercept and manipulate your traffic, leading to various security threats such as data theft or malware injection.
In conclusion, while Tor is a valuable tool for online privacy and anonymity, using it without a VPN exposes users to certain risks. To enhance security and mitigate these risks, it is advisable to combine Tor with a reputable VPN service that offers end-to-end encryption and additional layers of protection. By taking these precautions, users can enjoy a safer and more secure browsing experience while using Tor.
Benefits of using VPN with Tor
Combining a Virtual Private Network (VPN) with The Onion Router (Tor) can enhance your online privacy and security in numerous ways. By understanding the benefits of using both tools together, you can create a more robust defense against potential cyber threats.
One of the main advantages of using a VPN with Tor is the added layer of encryption it provides. While Tor anonymizes your internet traffic by routing it through multiple servers, a VPN encrypts your data before it even enters the Tor network. This double encryption makes it significantly harder for anyone, including Internet Service Providers (ISPs) and government agencies, to track your online activities.
Additionally, using a VPN can help bypass certain restrictions imposed by Tor exit nodes. Sometimes, exit nodes may restrict access to certain websites or services. By connecting to a VPN before accessing the Tor network, you can avoid these limitations and enjoy a more seamless browsing experience.
Furthermore, combining VPN and Tor can improve your overall browsing speed and performance. Since VPNs route your traffic through their servers, they can help reduce latency and improve connectivity. This means that by using a VPN with Tor, you may experience faster and more reliable internet connections.
Overall, the benefits of using a VPN with Tor are clear. Enhanced encryption, unrestricted access, and improved performance are just a few reasons why this combination is becoming increasingly popular among privacy-conscious individuals. By taking advantage of both tools, you can enjoy a safer and more secure online experience.
VPN vs
In today's digital age, where privacy concerns and online security breaches are on the rise, the debate between VPN (Virtual Private Network) and other forms of internet protection has become increasingly relevant. VPNs and their alternatives offer users different levels of security, privacy, and functionality, making it crucial to understand the distinctions between them.
VPN services encrypt your internet connection, ensuring that your online activities remain private and secure from prying eyes, such as hackers or government surveillance. Additionally, VPNs allow users to bypass geo-restrictions and access content that may be blocked in their region.
On the other hand, alternative methods such as proxy servers and Tor (The Onion Router) provide varying degrees of anonymity and security. Proxies work by routing your internet traffic through a third-party server, masking your IP address, while Tor routes your traffic through a series of volunteer-operated servers, encrypting it along the way.
When comparing VPNs to alternatives, it's essential to consider factors such as speed, reliability, and ease of use. While VPNs typically offer faster connection speeds and more reliable service than proxies or Tor, they may come with a subscription fee.
Furthermore, VPNs often provide additional features such as ad-blocking, malware protection, and split tunneling, which allow users to choose which traffic is routed through the VPN and which isn't.
Ultimately, the choice between VPN and its alternatives depends on your specific needs and priorities. If privacy and security are your primary concerns, a VPN may be the best option. However, if you're looking for a free solution or require maximum anonymity, alternatives like proxies or Tor could be worth exploring.
Securing Tor with a VPN
Securing Tor with a VPN
In the digital age, privacy and security have become paramount concerns for internet users worldwide. With the increasing prevalence of online surveillance and data breaches, individuals are seeking ways to safeguard their online activities from prying eyes. Two popular tools that offer enhanced privacy and security are Tor (The Onion Router) and VPNs (Virtual Private Networks). While each has its strengths, combining Tor with a VPN can provide an extra layer of protection and anonymity.
Tor is renowned for its ability to anonymize internet traffic by routing it through a series of encrypted nodes, making it difficult for anyone to trace the origin or destination of the data. However, Tor alone does not encrypt the data beyond its network, leaving it vulnerable to interception by ISPs or malicious actors.
This is where a VPN comes into play. A VPN encrypts all data passing between the user's device and the VPN server, effectively creating a secure tunnel that shields the data from prying eyes. By connecting to a VPN before accessing the Tor network, users can ensure that their internet traffic is encrypted from end to end, providing an added layer of security.
Moreover, using a VPN with Tor can help bypass restrictions imposed by ISPs or governments, as the VPN server acts as an intermediary between the user and the internet, masking the user's true location and IP address. This can be particularly useful for individuals living in countries with strict internet censorship or surveillance.
However, it's essential to choose a reputable VPN provider that respects user privacy and does not keep logs of user activity. Additionally, users should be aware that while combining Tor with a VPN can enhance privacy and security, it may also result in slower internet speeds due to the added encryption and routing processes.
In conclusion, combining Tor with a VPN can provide a robust solution for safeguarding online privacy and security. By encrypting internet traffic and anonymizing online activities, users can enjoy greater peace of mind while browsing the web.
0 notes
Text
do i need a vpn for my office
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need a vpn for my office
Office VPN necessity
Connecting to a Virtual Private Network (VPN) has become increasingly necessary in today's office environment for a variety of reasons. An office VPN provides a secure and encrypted connection between employees and the office network, ensuring that sensitive data and communications remain private and protected from potential cyber threats.
One of the main reasons why using a VPN in the office is essential is to safeguard confidential information. By encrypting data transmitted between the employee's device and the office network, a VPN prevents unauthorized parties from intercepting and accessing sensitive business data. This is particularly crucial when employees are working remotely or accessing the office network from public Wi-Fi networks, which are vulnerable to cyber attacks.
Additionally, utilizing a VPN can enhance data security and compliance with regulations such as GDPR. By implementing encryption protocols and secure tunneling mechanisms, a VPN helps prevent data breaches and ensures that the office network remains compliant with data protection laws.
Moreover, an office VPN enables employees to securely access restricted resources and applications within the office network from any location. This promotes flexibility and productivity among remote workers, as they can collaborate with colleagues, access files, and work on projects seamlessly without compromising security.
In conclusion, the use of a VPN in the office is no longer just an option but a necessity in today's digital age. By providing a secure and encrypted connection, a VPN safeguards data, enhances security, and facilitates remote work, making it an essential tool for modern businesses to protect their sensitive information and maintain operational efficiency.
VPN benefits for workplace
A Virtual Private Network (VPN) provides a range of benefits for the workplace, enhancing security, privacy, and productivity for employees and the organization as a whole. By encrypting data transmitted over the internet, VPNs protect sensitive information from potential cyber threats, such as hacking and data breaches. This is crucial for businesses handling confidential data, ensuring that proprietary information is safeguarded.
Moreover, VPNs enable employees to access company resources securely from remote locations. With the rise of remote work, VPNs have become essential tools for ensuring a secure connection to corporate networks, even when working from home or while traveling. This allows for seamless collaboration and efficient workflow, regardless of physical location.
In addition to security benefits, VPNs also offer enhanced privacy by masking the user's IP address and location. This is particularly important for businesses that operate in regions with strict censorship or surveillance laws, as a VPN can bypass these restrictions and provide unrestricted access to online content.
Furthermore, VPNs can optimize network performance by reducing latency and bandwidth congestion. By routing traffic through remote servers, VPNs can improve connection speeds and overall network efficiency, leading to better performance for employees conducting online tasks.
Overall, the advantages of employing a VPN in the workplace are manifold, ranging from heightened security and privacy to improved productivity and network optimization. By implementing a VPN solution, businesses can ensure a safe and efficient digital environment for their employees, ultimately leading to enhanced performance and success.
Security advantages of VPN in office
Title: Enhancing Office Security with VPN: Key Advantages
In the modern workplace, where digital operations dominate, ensuring the security of sensitive data is paramount. Virtual Private Networks (VPNs) have emerged as essential tools for safeguarding office networks and preserving the confidentiality, integrity, and availability of data. Here are several key security advantages of implementing a VPN in the office environment:
Data Encryption: VPNs encrypt data transmitted between the office network and remote devices, making it incomprehensible to unauthorized parties. This encryption significantly reduces the risk of data interception and eavesdropping, particularly when employees access company resources over unsecured networks, such as public Wi-Fi hotspots.
Secured Remote Access: With the rise of remote work, employees often need to access office resources from various locations. VPNs enable secure remote access by establishing encrypted connections between remote devices and the office network, regardless of the user's location. This ensures that sensitive data remains protected, even when accessed outside the office premises.
Protection Against Cyber Threats: VPNs provide an additional layer of defense against cyber threats, such as malware, phishing attacks, and man-in-the-middle attacks. By routing all network traffic through encrypted tunnels, VPNs help prevent unauthorized access to office resources and mitigate the risk of data breaches.
Anonymity and Privacy: VPNs conceal users' IP addresses and browsing activities, enhancing anonymity and privacy. This is particularly beneficial for employees who handle sensitive information or conduct research that requires discretion. By masking their online identities, VPNs help prevent surveillance and tracking by malicious actors.
Compliance with Regulations: Many industries are subject to strict regulatory requirements concerning data protection and privacy. Implementing a VPN in the office environment can help ensure compliance with these regulations by safeguarding sensitive data and preventing unauthorized access or disclosure.
In conclusion, VPNs offer numerous security advantages for offices, including data encryption, secured remote access, protection against cyber threats, anonymity, privacy, and regulatory compliance. By integrating VPN technology into their network infrastructure, organizations can fortify their defenses and mitigate the risks associated with modern cybersecurity threats.
VPN importance for office network
In the modern digital age, where cyber threats loom large, ensuring the security and privacy of confidential data within an office network is of paramount importance. This is where Virtual Private Networks (VPNs) play a crucial role. VPNs create a secure and encrypted connection when employees access the internet from within the office network, adding an extra layer of protection against potential cyber attacks.
One of the key benefits of using a VPN for an office network is the ability to encrypt data transmissions. This means that sensitive information such as financial data, client details, and confidential documents are safeguarded from unauthorized access. By establishing a secure connection between the office network and external servers, VPNs help prevent data breaches and cyber theft.
Moreover, VPNs enable employees to access company resources remotely without compromising security. Whether working from home, traveling, or using public Wi-Fi networks, employees can connect to the office network through a VPN, ensuring that sensitive data remains protected at all times. This not only enhances flexibility and productivity but also reduces the risk of data interception by cybercriminals.
Additionally, VPNs provide anonymity by masking the IP address of devices connected to the office network. This helps prevent third parties from tracking online activities and promotes a higher level of privacy for employees. By keeping communications encrypted and anonymous, VPNs contribute significantly to maintaining the integrity and confidentiality of office network operations.
In conclusion, the importance of VPNs for office networks cannot be overstated. By enhancing security, ensuring privacy, and enabling secure remote access, VPNs help create a safe and reliable digital environment for businesses to operate in the face of evolving cyber threats. It is essential for organizations to implement VPN solutions as part of their cybersecurity strategy to protect valuable assets and maintain trust with clients and partners.
Business VPN necessity
In today's interconnected digital landscape, where businesses rely heavily on the internet for various operations, the necessity of a Business VPN (Virtual Private Network) cannot be overstated. A Business VPN offers a secure and encrypted connection for remote employees, enabling them to access company resources and data from anywhere in the world without compromising sensitive information.
One of the primary reasons why a Business VPN is essential is to safeguard confidential data from cyber threats. With cybercrime on the rise, businesses face constant risks of data breaches, hacking attempts, and unauthorized access to proprietary information. A VPN creates a secure tunnel between the user's device and the company's network, effectively encrypting data transmissions and making it nearly impossible for hackers to intercept or decipher sensitive data.
Moreover, a Business VPN enhances privacy and anonymity online, crucial for maintaining competitive advantage and protecting business intelligence. By masking IP addresses and encrypting internet traffic, VPNs prevent third parties from tracking users' online activities, ensuring confidentiality in communications and transactions.
Another significant advantage of implementing a Business VPN is the ability to bypass geo-restrictions and access region-locked content or services. This is particularly valuable for companies with global operations, allowing employees to connect to localized resources or websites without restrictions imposed by geographical boundaries.
Furthermore, in an era where remote work is increasingly prevalent, a Business VPN facilitates secure remote access to corporate networks, applications, and files. This enables employees to work efficiently from remote locations while ensuring the integrity and confidentiality of company data.
In conclusion, the necessity of a Business VPN lies in its ability to provide a secure, private, and versatile network solution tailored to the needs of modern businesses. By prioritizing cybersecurity, privacy, and accessibility, businesses can mitigate risks, enhance productivity, and maintain a competitive edge in today's digital economy.
0 notes
Text
can upwork track my location when i use vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can upwork track my location when i use vpn
Upwork location tracking
Upwork is a popular platform for freelancers and clients to connect and collaborate on various projects. One concern that often arises for both parties is location tracking within the platform.
For clients, ensuring that the freelancer they hire is located in the same country or time zone can be important for communication, project timelines, and even legal or tax reasons. Upwork allows clients to set location preferences when posting a job, ensuring that they receive proposals only from freelancers in the desired location.
Freelancers, on the other hand, may be concerned about Upwork tracking their location for privacy or security reasons. Upwork does track the location of freelancers using a feature called "Work Diary," which allows clients to see screenshots of the freelancer's work-in-progress along with activity levels. This can help ensure that the freelancer is working on the project as agreed.
It is important for both clients and freelancers to understand how location tracking works on Upwork and to communicate openly about any concerns or preferences. Upwork provides tools and features to help facilitate communication and collaboration while also respecting the privacy and security of all users.
Ultimately, location tracking on Upwork can be a useful tool for ensuring transparency and accountability in remote work relationships. By being aware of how location tracking is used on the platform, both clients and freelancers can make informed decisions and collaborate effectively on projects.
VPN usage privacy
Title: Safeguarding Your Privacy: Understanding VPN Usage
In an age where online privacy is increasingly threatened, Virtual Private Networks (VPNs) have emerged as essential tools for safeguarding personal data and browsing habits. VPNs offer a secure connection between your device and the internet by encrypting your internet traffic and routing it through remote servers. This encryption ensures that even if your data is intercepted, it remains indecipherable to hackers or prying eyes.
One of the primary benefits of using a VPN is the anonymity it provides. By masking your IP address, VPNs prevent websites, advertisers, and even your internet service provider (ISP) from tracking your online activities. This means that you can browse the web without fear of being monitored or targeted with personalized ads based on your browsing history.
Moreover, VPNs are particularly useful when accessing public Wi-Fi networks, such as those found in cafes, airports, or hotels. These networks are often prime targets for cybercriminals looking to steal sensitive information. By using a VPN, you can encrypt your data and prevent hackers from intercepting your passwords, credit card numbers, or other confidential information.
Furthermore, VPNs enable users to bypass geo-restrictions and access content that may be blocked or censored in their region. Whether streaming movies and TV shows, accessing social media platforms, or engaging in online gaming, a VPN can provide unrestricted access to the global internet.
However, it's essential to choose a reputable VPN provider that prioritizes user privacy and security. Look for providers that offer a strict no-logs policy, meaning they do not store any information about your online activities. Additionally, opt for VPNs with strong encryption protocols and a wide network of servers to ensure fast and reliable connections.
In conclusion, VPNs are invaluable tools for preserving privacy and security in an increasingly interconnected world. By encrypting your internet traffic and masking your IP address, VPNs offer peace of mind and freedom online. Whether you're concerned about data privacy, bypassing geo-restrictions, or staying safe on public Wi-Fi networks, incorporating a VPN into your online routine is a smart and proactive measure.
Geo-location detection
Geo-location detection is a technology that enables websites and applications to pinpoint the geographical location of a user. This information is gathered through various methods such as GPS, IP address tracking, Wi-Fi positioning, and cell tower triangulation.
One of the primary uses of geo-location detection is to provide users with location-specific content and services. For example, an e-commerce website can show products available in the user's area, weather apps can display local forecasts, and social media platforms can suggest nearby friends or events.
Businesses can also leverage geo-location detection for targeted advertising and marketing campaigns. By knowing the user's location, companies can deliver personalized ads based on their proximity to physical stores or relevant local promotions.
In terms of security, geo-location detection can be used to verify a user's identity by matching their current location with the expected or authorized area. This technology is also helpful in preventing fraudulent activities such as fake accounts or unauthorized access from different regions.
While geo-location detection offers numerous benefits, it also raises concerns about privacy and data protection. Users must be aware of how their location information is being collected, stored, and used by websites and applications. It is crucial for businesses to implement strict security measures to safeguard this sensitive data and comply with privacy regulations.
Overall, geo-location detection plays a vital role in enhancing user experience, enabling targeted marketing strategies, improving security measures, and raising awareness about privacy issues in the digital age.
User anonymity online
User anonymity online refers to the ability of individuals to stay unidentified and untraceable while browsing the internet. With the widespread use of online platforms and the increasing concern for privacy, user anonymity has become a crucial issue in the digital age.
One of the main reasons why people seek anonymity online is to protect their privacy and sensitive information from potential threats such as hackers, trackers, and data breaches. By concealing their identity, users can prevent unwanted access to personal data and avoid being targeted by malicious entities.
Moreover, user anonymity online allows individuals to express their opinions freely without fear of retaliation or discrimination. It provides a safe space for people to share their thoughts and engage in discussions without revealing their real identity. This is particularly important in environments where censorship and surveillance are prevalent, as anonymity enables individuals to communicate without restrictions.
However, while user anonymity offers numerous benefits, it also has its drawbacks. It can be used for malicious purposes such as cyberbullying, harassment, and illegal activities. The anonymity provided by the internet can empower users to engage in harmful behaviors without facing immediate consequences, leading to potential harm to others.
In conclusion, user anonymity online plays a significant role in safeguarding privacy, enabling free expression, and protecting individuals from digital threats. It is essential for users to be aware of the risks and benefits associated with online anonymity and to use it responsibly to create a safer and more inclusive digital environment.
Internet security measures
In today's digital age, internet security measures have become more crucial than ever before. With the increasing number of cyber threats and malicious activities on the web, it is important for individuals and organizations to take proactive steps to protect their online data and privacy.
One of the fundamental internet security measures is ensuring the use of strong and unique passwords for all online accounts. A strong password should be a combination of letters, numbers, and special characters to make it difficult for hackers to crack. It is also recommended to use different passwords for each account to prevent multiple accounts from being compromised in case one password is breached.
Another important internet security measure is the use of antivirus software and firewalls to protect devices from malware, viruses, and other online threats. Antivirus software helps to detect and remove malicious programs, while firewalls act as a barrier between your device and potentially harmful websites or downloads.
Regular software updates are also essential for internet security. Software updates often include security patches that address known vulnerabilities, so by keeping your devices and applications up to date, you can reduce the risk of being targeted by cyber attackers.
Furthermore, practicing safe browsing habits such as avoiding suspicious websites, not clicking on unknown links or attachments, and being cautious when sharing personal information online can also help enhance internet security.
By implementing these internet security measures, individuals and organizations can safeguard their online presence and data from potential cyber threats, ensuring a safer and more secure digital experience.
0 notes
Text
The Roadmap to Becoming an Ethical Hacker
Ethical hacking, also known as penetration testing or white hat hacking, is a crucial field in cybersecurity. Ethical hackers play a vital role in identifying vulnerabilities, securing systems, and protecting organizations from cyber threats.
As businesses started moving to online platforms for data storage, operations, and even sales, there is an increased concern about security. The intruders are always looking for a vulnerable network where they can peek in and turn their data theft intentions into a success.
For individuals seeking to validate their proficiency in Ethical Hacking and enhance their career prospects, pursuing Ethical Hacking institute in Bangalore becomes a strategic imperative.

If you aspire to become an ethical hacker, will provide you with a roadmap to guide your journey towards achieving your goal.
Here Is a Roadmap to Help You Embark on A Journey to Become an Ethical Hacker:
Develop a Strong Foundation in Computer Science and Networking:
Start by building a solid understanding of computer networks, operating systems, and programming languages like Python, C++, or Java.
Learn about network protocols, TCP/IP, subnetting, routing, and the functioning of network devices.
2. Gain Proficiency in Operating Systems and Security Concepts:
Familiarize yourself with different operating systems, such as Windows, Linux, and macOS. Learn their command-line interfaces, administrative tools, and security features.
Study cybersecurity concepts, including cryptography, network security, and secure coding practices.
3. Learn Web Application Security:
Understand the fundamentals of web technologies like HTML, CSS, JavaScript, and server-side scripting languages (e.g., PHP, ASP.NET).
Dive into web application security and learn about common vulnerabilities such as SQL injection, cross-site scripting (XSS), and security misconfigurations.
4. Study Penetration Testing Methodologies and Tools:
Gain knowledge of various penetration testing methodologies, such as the Open Web Application Security Project (OWASP) Testing Guide and the Penetration Testing Execution Standard (PTES).
Explore popular penetration testing tools like Burp Suite, Metasploit, Nmap, Wireshark, and SQLMap.
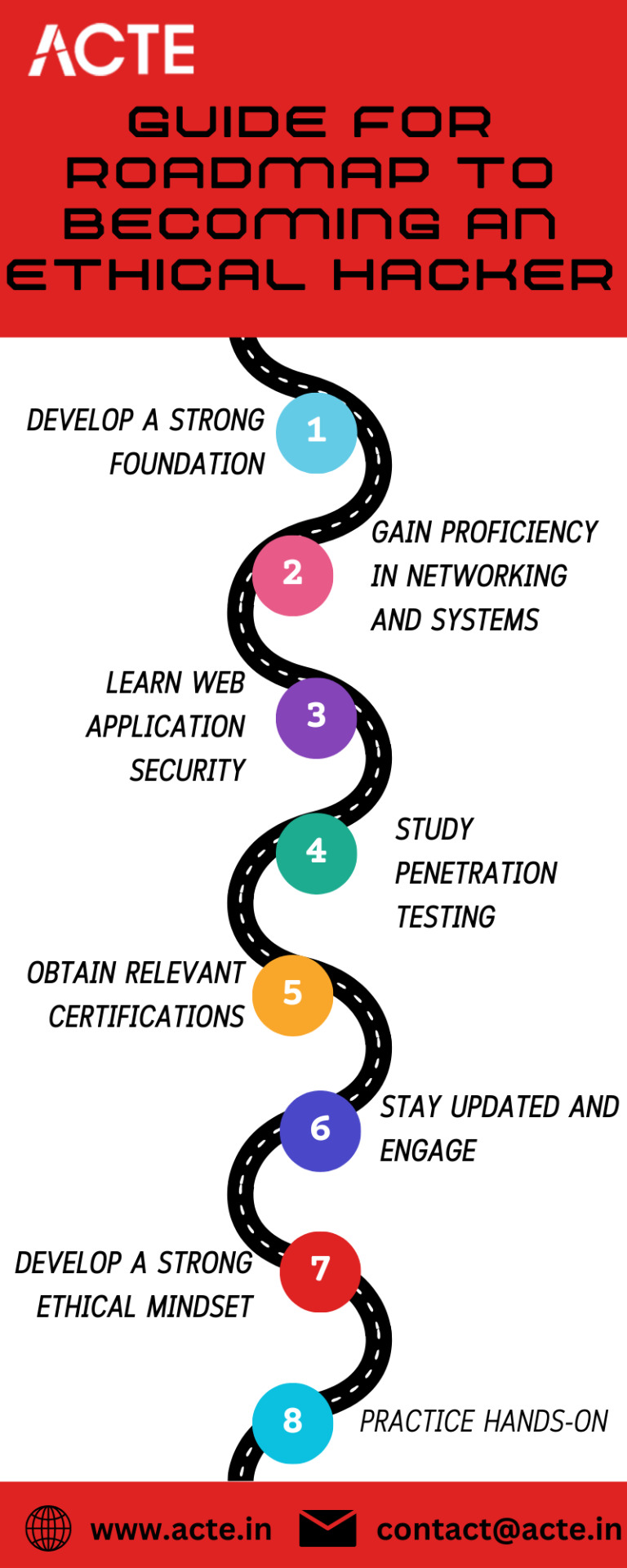
5. Pursue Relevant Certifications:
Consider obtaining industry-recognized certifications to validate your ethical hacking skills. Some notable certifications include Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and Certified Information Systems Security Professional (CISSP).
6. Engage in Hands-On Practice:
Set up a lab environment using virtualization software like VirtualBox or VMware to create virtual machines for testing purposes.
Practice ethical hacking techniques in a controlled and safe environment, ensuring you have proper authorization and permissions.
Participate in Capture The Flag (CTF) competitions and online hacking challenges to enhance your practical skills and problem-solving abilities.
7. Stay Updated with the Latest Trends and Vulnerabilities:
Follow cybersecurity blogs, forums, and news sources to stay abreast of the latest security vulnerabilities, emerging threats, and defense strategies.
Engage in continuous learning through online courses, webinars, workshops, and conferences to stay ahead in the ever-evolving field of cybersecurity.
8. Develop a Strong Ethical Mindset:
Understand and adhere to legal and ethical guidelines while performing ethical hacking activities.
Always obtain proper authorization and permissions before conducting any security assessments or penetration tests.
Respect privacy, confidentiality, and the integrity of the systems you are testing.
Becoming an ethical hacker requires a combination of technical knowledge, practical skills, and a strong ethical mindset. By following this roadmap, you can build a solid foundation in computer science and networking, specialize in web application security, gain expertise in penetration testing methodologies and tools, and stay updated with the latest trends.
Remember to approach ethical hacking with a strong ethical mindset, always ensuring you operate within legal boundaries and respect the privacy of individuals and organizations. With dedication, continuous learning, and practical experience, you can embark on a rewarding career as an ethical hacker and contribute to the security of digital systems.
Feel free to get in touch with an ACTE institution in Bangalore if you want to learn more about Ethical Hacking course because they provide certifications and possibilities for job placement. Teachers with experience can improve your learning. These services are available offline and online. Take things slowly and, if you’re interested, think about signing up for a course.
0 notes
Text
Professional Summary for PHP Developer
Using the PHP programming language, PHP developers are in charge of creating websites and computer programmers. Their responsibilities include debating customer requirements, developing code, creating and enhancing apps or website components, testing code, and ensuring projects are finished on schedule. Using the PHP programming language, PHP developers are in charge of creating websites and computer programmers. Their responsibilities include debating customer requirements, developing code, creating and enhancing apps or website components, testing code, and ensuring projects are finished on schedule.
The Qualifications for a PHP Developer It's an opening. understanding of MySQL, jQuery, and Ajax. Being a full-stack developer requires knowledge of JavaScript, CSS, and HTML. APIs, Linux/Unix, and the architecture of the MVC Framework. Identifying Cake PHP is an open-source web framework, and PHP Unit is a framework for unit testing, Photoshop or an equivalent design programme, strong communication abilities, a talent for solving problems, Critical thinking capacity. It would be wise to choose the upskilling route if you are already a developer and want to go into PHP. Your continuous professional success depends critically on your continued training and education.
Roles and responsibilities for PHP developers Working with other developers to meet data collecting requirements, quickly and effectively design, test, and launch new, creative website apps.find and fix CSS, HTML, and scripting compatibility problems, which frequently exist between a variety of different platforms and browsers. Test webpages on various browsers, and fix problems brought up by user feedback. Investigate and examine numerous architectural aspects of the system design process, such as database architecture, website performance, and web usability. Investigate and evaluate various options for adding new application functionalities.Specifications for the website, such as the product's features, price, programming languages, communication protocols, functionality, structure, and deadlines, should be described in detail.Despite the numerous discussions surrounding this technology, it is obvious that PHP does have a bright future. Yes, this tool has some outdated information, but if you are an expert in this field, you won't have any problems. You will be more productive and produce better, cleaner code if you use frameworks when developing.
Benefits of PHP The fact that PHP is open-source and cost-free is its main benefit. It is readily available for usage with events or web apps and may be downloaded from any location. Its ease of use and lack of learning curve make it more user-friendly. Anyone who is familiar with C programming can work on PHP with ease.
With the help of continuing to support different versions, it is more reliable for a few years. It facilitates the reuse of similar code and eliminates the need to create intricate and lengthy code for web application events.
It facilitates the reuse of similar code and eliminates the need to create intricate and lengthy code for web application events. An experienced web developer and software tester with a focus on increasing network-server efficiency is looking for a position in advanced programming. PHP-certified and have worked with a web development team to establish a startup company's website, which included a platform with a B2C interface that was specially designed. Self-driven, meticulous, and able to think beyond the box. competent in software testing and debugging, as well as coding and design. fluent in a number of coding languages, including JavaScript and PHP. excels in collaborative settings and leadership positions; overseen two software and web development projects.
0 notes
Text
What is IPSec and how does it work?
What is an IPSec article and how does it work? Get acquainted (gain, obtain) with present-day techniques that came from IPsec Protocols, which are used to set up encrypted connections between two or more devices. These types of protocols help keep data sent over public networks secure. You should know that IPsec is often used to set up V.P.N. VPN, which is done by encrypting IP packets and authenticating the packet source.
What is ip?
IP stands for Internet Protocol, which is the main routing protocol used in the Internet. This protocol specifies where the data should travel and which destination it should reach. But the IPSec protocol also adds encryption and authentication to the process.
Who made IpSec?
This protocol is a joint product of Microsoft and Cisco Cisco Systems works by authenticating and encrypting each data packet in a data stream.
What port does IPsec use?
The software port or network port is where the information is sent. In other words, a port is a place through which data enters or leaves a computer or server, and a number is assigned to each of these ports, which are between 0 and 65535. IPsec also typically uses port 500 to perform encryption and decryption algorithms.
What are the benefits of IPSec?
Replay attack protection: Assigns a unique number to each data packet (packet) which deletes the packet if that number is duplicate.
Confidentiality of information or encryption: VPN connection security is increased by PFS in this protocol, which is done by creating a unique key in each connection.
Information source authentication: Confirmed by the message authentication code (HMAC)
That message has not changed.
Transparency: Ipsec works at the network layer, which is actually transparent to applications and users. As a result, there is no need to change the routers and firewalls during use
Dynamic re-encryption: The security keys for decryption change at regular intervals. This prevents identity theft and hacker attacks.
Replay attack protection Any software can be compatible with this protocol Confidentiality of information (encryption) Having transport mode Having tunnel mode Authentication of the source and origin of information Layer 3 or Network Authentication.
Types of IPSec IPSec security protocols
IPsec is an open source standard and part of the IPv4 suite. IPsec can communicate between both transport mode and tunnel mode. IPsec is a global standard and can perform a variety of security processes using a set of protocols it uses, including the protocols used in IPsec. To give privacy to the data and finally Security Associations or SA to create the data used in AH and ESP.
1. IPSec AH protocol The Authentication Header (AH) protocol was developed in the early 1990s in the United States Naval Research Laboratory. This protocol ensures the security of the data source by authenticating IP packets. In this algorithm, using the sliding window method and deleting old packets and assigning a sequence number, the contents of the IPsec packet are protected against attacks such as replay attacks. In fact, with this technique, one can only be sure that the data packets have been sent from a reputable source and have not been tampered with.
In this case, both the upload and the header are encrypted. The term Tunnel is used instead of AH. All data is protected by HMAC. And only peer-to-peer points know the secret key made by HMAC and can decrypt it. And as mentioned, because headers are also encrypted and can not be changed in networks where NAT is done, the VPN service can not be used.
Integrity of submitted data Data source authentication Reject resended packages 2. IP Encapsulating Security Payload (ESP) The IP Encapsulating Security Payload (ESP) protocol was developed at the Naval Research Laboratory in 1992 as part of a DARPA-sponsored research project. The work of this protocol ensures data authentication through the source authentication algorithm, data integrity through the hash function, and confidentiality through IP packet encryption. ESP is used in settings and configurations that support either encryption only or authentication only. This is a weakness because it is unsafe to use encryption without authentication.
In this case, only the upload is encrypted and the headers remain the same without change. The term Transport is used instead of ESP. In this method, both parties must perform authentication operations and also the data is sent in encrypted form.
In fact, unlike the AH protocol, the ESP protocol in Transport mode does not provide integration and authentication for the entire IP packet. In Tunnel mode, where the entire original IP packet is located with a new packet header, ESP protects the entire internal IP packet (including the internal header) while the external header (including external IPv4 options or IPv6 extension) remains unprotected. They stay.
3. Security association IPsec protocols use a Security Association to create interconnected security features such as algorithms and keys. In fact, when the AH or ESP protocol is specified to be used, the Security Association provides a wide range of options. Before exchanging data, the two hosts agree on which algorithm to use to encrypt the IP packet. The hash function is used to ensure data integrity. These parameters are agreed in each session that has a specific life (time) and also a specific key must be specified for each session.
In how many modes can IPSec work? (Operation Modes)
IPsec AH and IPSec ESP protocols can be used in host-to-host transport mode as well as in network tunneling mode.
1. IPSec Transport Mode In transport mode, only the encrypted or verified IP packet and routing remain intact because the IP header is neither modified nor encrypted. However, when the authentication header is used, the hash value is invalidated and the IP addresses cannot be modified and translated with the Network address translation method. The Transport and Application layers are always secured with a hash, so they can not be modified in any way, even by translating port numbers.
2. Tunnel Mode or IPSec Tunnel Configuration In Tunnel mode, the entire IP packet is encrypted and authenticated. It is then categorized in a new IP packet with a new IP header. From tunnel mode to create virtual private networks for network-to-network communication (e.g. between routers to link sites), host-to-network communication (e.g. remote user access), and host-to-host communication (e.g. Private chat) is used.
Key management in IPSec protocol
IPSec is widely used in VPN technology for authentication, privacy, integrity and key management in IP-based networks.
IPSec establishes communication security within network equipment with the help of secure encryption services. For IPSec to function properly, both the sender and receiver must share a public key, which is achieved through the use of the "key management" protocol. This protocol allows the receiver to obtain a public key and authenticate the sender based on a digital signature.
2 notes
·
View notes
Text
10 Most Popular NodeJS Frameworks of 2021
Every year, we highlight the best NodeJS frameworks that make developers' jobs easier. Just as a quick reminder, Nodejs was first introduced in 2009 and is itself an open-source cross-platform framework built on Chrome's V8 JavaScript engine.
So, what are some of the best NodeJS frameworks for 2021? I'm glad you asked! Here's a quick rundown and analysis of some great features.

List of 10 Most Popular Frameworks in 2021
1. Express.js
Express.js is a Node.js web application framework that provides robust features like environment-aware smart routing and advanced response handling for developing, building, and running web apps quickly while also providing an excellent standard to most Node.JS applications today!
source:https:/www.octalsoftware.com
Express.js features and benefits:
Create handlers for requests with different HTTP verbs at different URL paths.
Integrate by inserting data into templates and setting common web application settings like port to use, location of templates used rendering responses.
Add additional request processing “middleware” any point within the handling pipeline
2. LoopBack
LoopBack is a popular node.js framework that gives developers an easy-to-use CLI and API explorer to make building their applications easier.
With Loopback, you can create great apps faster with the help of different features like dynamic links between devices or browsers as well as support for Android, iOS, and Angular SDKs out of the box!
source:https://loopback.io/
LoopBack features and benefits:
We can share models with server and client.
Saves you manual work.
It has built in ORM
It is backed by IBM
It also used in user and access role features
It give strength of full stack development
It can be used in various scenarios, including CRUD operations (accessing databases) and integrating with other infrastructures. It's incredibly easy to use as it only requires a single line of code!
3. Socket.io
Socket.io is a full-stack platform that offers developers the ability to use many programming languages and interact with virtually any service quickly, allowing them to build anything they want on it. The API provides an excellent speed in development as well as durability so businesses such as IBM trust this framework for their business needs.

source:https://blog.bitsrc.io/
Socket.io features and benefits:
The framework offers a cutting-edge feature that will keep your users connected with an auto reconnection support. If they are disconnected, the connection will quickly restore automatically until it is manually stopped by you!
Socket.io adds metadata to each packet so users can seamlessly connect with the other side of an ongoing conversation.
Socket.io uses WebSockets, which run on the top of other protocols for faster and more efficient communication between browsers and servers with metadata added to each packet
4. Sail.js
Sail is a Model-View-Controller (MVC) web application framework that facilitates the wide range of WebSocket integration features.
Socket.io provides it with its communication channel between clients and servers to facilitate real-time data exchange in both directions on browsers with no need for polling refresh or manual queries updates when data changes at server end from client side page load event trigger automatically.
source:https://sailsjs.com/
Sail.js features and benefits:
Automatic generation of Rest-APIs.
Support web socket
Hasslesfree handling of HTTPS requests.
Easy integration of Middleware
5. Koa.js
Koa.js is one of the more dominant Node.js frameworks that can make building different web services, aka APIs super fun and easy since it efficiently deals with HTTP middleware with a stack-like method!

source:https://koajs.com/
Koa.js features and benefits:
This awesome framework is a lightweight version of Express!
He is the best mechanic in town. He can handle any job, no matter how complex or easy.
Cascading middleware has made it possible for software to personalize the user experience.
6. Hapi.js
Hapi is a framework that can support the development of complicated web applications with its proxy servers, REST APIs, and other types of desktop apps. It's reliable due to both technical aspects like reliability systems as well as security measures such as SSL encryption. This makes it perfect for large teams managing multiple projects simultaneously who need an efficient process in place!

source:https://hapi.dev/
Hapi.js features and benefits:
Hapi is a powerful and reliable web server commercial-centered framework that offers enterprise level security when building applications.
It can handle large teams of programmers working simultaneously on multiple tasks while also
provide great development support for those looking to build their own proxy servers, REST APIs, or desktop apps.
7. Adonis.js
Adonis.js is an elegant, stable Node.JS framework that makes it easy to write scalable web applications from scratch using the MVC paradigm and with a modular design philosophy in mind - making this your perfect choice for writing highly-stable server-side code without sacrificing elegance or beauty!
AdonisJS is the best framework to start developing with. Don't waste your time downloading and assembling hundreds of packages together, use AdonisJS from day one!
source:https://adonisjs.com
Adonis.js features and benefits:
Multi transport mailer
Organized pattern with a folder structure
Secure and straightforward file upload.
Easier validation of user input
Facility to write custom functional test scripts
Supportive and friendly community
8. Derby.js
Derby.js is a framework that makes it easy to create mobile and web applications in both node.js and browsers.
The main feature of this tool is its synchronization across clients and servers, which allows for constant updates from one user to another without having any latency issues or lag time between messages received by different users on either side of an application's network - no matter where they are residing at the moment!
Derby.js features and benefits:
MVC Architecture for both server side & client side.
Our ShareDB platform provides you with seamless data synchronization between your server and client in a way that’s both automatic and conflict-free.
With the help of automatic timing and faster support, multiple people can use a single application simultaneously.
Many people use it for their real-time collective applications because of its speed and ease.
9. Meteor.js
Meteor.js is a paradigm-bending web development framework that allows developers to build modern, cross-platform apps using just JavaScript and Node. It's compatible with the Web, iOS, Android or desktop devices so you can develop your app without worrying about writing native code for each platform separately!

source: https://www.meteor.com/
Meteor.js features and benefits:
Full stack solution
Easy integration with other frameworks
The cross platform framework, building rapid phototyping CLI.
Less requirement of coding web and mobile application
Allow using the same code for writing boath apps
10. Nest.js
Nest.js is a new framework that combines the benefits of functional programming with those from object-oriented and reactive programming to make it easier for developers to build scalable REST APIs in JavaScript, Typescript or both.
source: https://nestjs.com/
Nest.js features and benefits:
Easy to use, learn and master
Active codebase development and maintenance
Highly scalable and easy to maintain applications.
Large community and support team
Built for large scale enterprise applications
1 note
·
View note
Text
does logitech flow work over vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does logitech flow work over vpn
Logitech Flow VPN compatibility
Logitech Flow allows users to seamlessly control and switch between multiple computers with a single mouse and keyboard. It enables a smooth workflow by eliminating the need for separate input devices for each computer. However, some users may encounter issues with Logitech Flow when using a Virtual Private Network (VPN).
VPN compatibility is essential for users who rely on VPN services to ensure their online privacy and security. When using Logitech Flow in conjunction with a VPN, users might face challenges due to the way VPNs route network traffic. VPNs create a secure connection between the user's device and the internet by encrypting data and routing it through a remote server. This encryption and rerouting process can sometimes interfere with the communication between computers in a Logitech Flow setup.
To ensure seamless compatibility between Logitech Flow and VPNs, users can try troubleshooting steps such as adjusting VPN settings, disabling split tunneling, or using a different VPN protocol. Additionally, keeping both the Logitech Flow software and the VPN client up to date can help address any compatibility issues that may arise.
While Logitech Flow VPN compatibility issues may be frustrating, taking the time to troubleshoot and find solutions can enhance the overall user experience. By ensuring that both Logitech Flow and the VPN service work harmoniously together, users can enjoy the convenience of seamless multi-computer control without compromising their online security and privacy.
Logitech Flow VPN functionality
Logitech has recently introduced an innovative feature known as Flow VPN functionality in its devices, aimed at enhancing user experience and productivity. This exciting addition allows users to seamlessly connect multiple Logitech devices through a secure virtual private network (VPN), creating a unified system that simplifies workflow and multitasking.
With Logitech Flow VPN functionality, users can enjoy the convenience of effortlessly switching between different devices, such as a computer, laptop, or tablet, without the need for complex setups or configurations. This feature is particularly beneficial for professionals who frequently work across various platforms and require a seamless transition between devices to boost efficiency and productivity.
By leveraging Logitech Flow VPN functionality, users can easily share files, documents, and even copy-paste text between connected devices with just a few clicks, eliminating the hassle of sending files via email or cloud storage services. This not only streamlines the workflow but also ensures data security and privacy through the encrypted VPN connection.
Moreover, Logitech Flow VPN functionality offers a smooth and uninterrupted user experience, allowing for a more fluid workflow and improved collaboration among team members. Whether you are a content creator, designer, or business professional, this feature provides a reliable and efficient solution for managing multiple devices simultaneously.
In conclusion, Logitech's innovative Flow VPN functionality elevates the user experience by providing a seamless connection between devices, enhancing productivity, and simplifying workflow. Stay ahead of the curve with Logitech's cutting-edge technology and experience a new level of efficiency in your daily tasks and projects.
Logitech Flow VPN integration
Logitech Flow VPN integration brings a seamless experience for users looking to enhance their privacy and security while using Logitech devices across multiple platforms. By integrating VPN (Virtual Private Network) capabilities into Logitech Flow, users can now enjoy encrypted connections and anonymous browsing while seamlessly switching between devices.
With Logitech Flow VPN integration, users can benefit from enhanced security features, such as data encryption and IP address masking, when using Logitech devices in different locations or networks. This ensures that their online activities remain private and protected from potential cyber threats.
The integration of VPN into Logitech Flow also allows for a more cohesive workflow across devices, enabling users to easily share files, copy and paste text, and control multiple devices from a single interface while maintaining a secure connection. Whether working remotely, traveling, or simply browsing the web, Logitech Flow VPN integration provides users with peace of mind knowing that their data is secure and their privacy is maintained.
Overall, Logitech Flow VPN integration offers a convenient solution for users who prioritize security and privacy in their digital interactions. By seamlessly integrating VPN capabilities into the Logitech Flow ecosystem, Logitech continues to provide innovative solutions that cater to the evolving needs of today's tech-savvy users.
Logitech Flow VPN performance
Title: Evaluating Logitech Flow VPN Performance: A Comprehensive Review
In today's interconnected world, where remote work and collaboration are the norm, Logitech Flow VPN emerges as a promising solution for seamless connectivity and enhanced productivity. With its touted ability to facilitate secure connections across multiple devices, Logitech Flow VPN aims to redefine the way users interact with their digital ecosystem. However, the efficacy of any VPN service relies heavily on its performance, particularly in terms of speed, reliability, and security.
In assessing the performance of Logitech Flow VPN, one must consider several key factors. Firstly, speed is paramount in ensuring a smooth user experience, especially during data-intensive tasks such as file transfers and video conferencing. Logitech Flow VPN impresses in this regard, boasting impressive transfer speeds and minimal latency, thanks to its optimized server infrastructure and advanced encryption protocols.
Moreover, reliability is a crucial aspect of any VPN service, as users depend on uninterrupted connectivity to stay productive. Logitech Flow VPN distinguishes itself with its robust network architecture, ensuring consistent performance across various operating systems and devices. Whether accessing corporate resources or collaborating with remote team members, users can rely on Logitech Flow VPN to maintain a stable connection at all times.
Security is another area where Logitech Flow VPN shines, offering end-to-end encryption and advanced authentication mechanisms to safeguard sensitive data from prying eyes. By leveraging industry-leading encryption standards and implementing stringent privacy policies, Logitech Flow VPN provides users with peace of mind, knowing that their online activities remain secure and confidential.
In conclusion, Logitech Flow VPN delivers on its promise of performance, offering users a reliable and secure platform for seamless connectivity and collaboration. With its impressive speed, reliability, and security features, Logitech Flow VPN emerges as a top contender in the competitive VPN market, catering to the diverse needs of modern professionals and businesses alike.
Logitech Flow VPN troubleshooting
Logitech Flow VPN troubleshooting can be a complex yet essential process for ensuring seamless connectivity and productivity across multiple devices. Logitech Flow enables users to control and transfer files between up to three computers simultaneously, enhancing workflow efficiency. However, issues may arise during the VPN setup and operation that can disrupt this seamless experience.
One common problem users may encounter is difficulty establishing a secure VPN connection between devices. To troubleshoot this, it is crucial to ensure that all devices have the latest Logitech Flow software updates installed. Additionally, checking firewall settings and network configurations to allow VPN traffic can help resolve connectivity issues.
Another issue that users may face is lag or delay when transferring files between connected devices. To address this, optimizing network speed and bandwidth allocation can improve data transfer speeds. Users can also consider using a wired connection instead of Wi-Fi to enhance stability and performance.
In some cases, users may experience compatibility issues with certain devices or operating systems while using Logitech Flow VPN. Ensuring that all devices meet the minimum system requirements and are compatible with Logitech Flow software can help avoid such challenges.
Overall, troubleshooting Logitech Flow VPN issues requires a systematic approach, including checking software updates, network settings, and device compatibility. By following these steps and seeking assistance from Logitech customer support if needed, users can resolve common problems and enjoy the benefits of seamless connectivity and file sharing across multiple devices.
0 notes