#SiteScript
Explore tagged Tumblr posts
Text
Trigger MSFlow from SharePoint Site Design
Trigger MSFlow from SharePoint Site Design
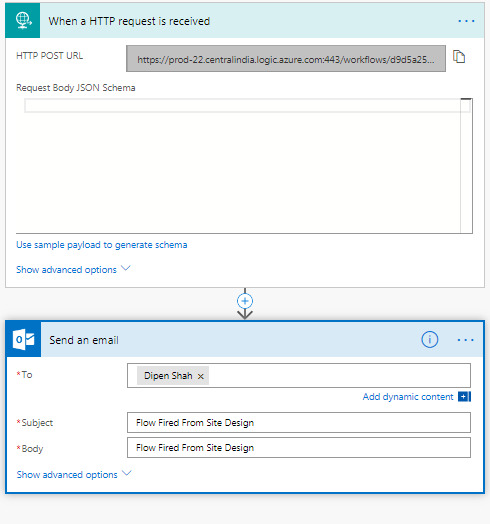
Today i am sharing knowledge how can we trigger Microsoft Flow using SharePoint site design. What is site design ? To automate provisioning new or existing modern SharePoint sites that use your own custom configurations. We need to ensure some level of consistency through out the share point modern site in organizations. For example, we may need proper branding and themeing applied to each new site.
View On WordPress
#Modern Communication Site#ModernTeamSite#MsFlow#PowerShell#SharePoint Online#SiteDesign#SiteScript#TriggerFlow
0 notes
Link
0 notes
Photo

Without a doubt, the Internet has completely revolutionized our world, and every business (either big or small) is shifting its business online.
The number of web applications is increasing, and so are the security threats. Many people don’t focus on the security of their online business, and such type of web apps allows hackers to compromise user’s data.
So it becomes vital for everyone to understand the importance of online security. There are different types of attacks the hackers can perform to compromise the security of your application and your user’s personal information. Some of the frequent attacks are –
Cross-Site Scripting (XSS)
SQL Injection
DDoS Attack
Malware
Bots
Cross-Site Request Forgery (CSRF)
Broken Authentication
Exploiting Inclusion Vulnerabilities – LFI and RFI
Read More
#Webapplicationsecurity#Webapp#Webdevelopment#VTNetzwelt#Cross-sitescripting#SQLinjection#DDoSaAttack
0 notes
Text
Yuzo Related Posts Wordpress Plugin - Major Security Flaw

Definitely a bad week for Lenin Zapata, author of the well-known Yuzo Related Post plugin for Wordpress. The plugin, installed on over 60,000 websites, was removed from the WordPress.org plug-in directory on March 30, 2019 following the public disclosure of a vulnerability in the code. The vulnerability, currently still without patches, allows the attacker to insert a script into the pages of the websites that have the plugin installed using a technique known as Cross-Site Scripting (XSS). The vulnerability present in the plugin is the result of an improper use of the is_admin() function, which has the precise purpose of verifying whether the URL accessed is in the administration section but which is mistakenly used by many Wordpress plugin developers to check if the current user has or less of administrative privileges. A "misunderstanding" far from trivial, to the point that the Wordpress Codex explicitly sees the need to refrain from such misuse: This Conditional Tag checks if the Dashboard or the administration panel is attempting to be displayed. It is a boolean function that will return true if the URL being accessed is in the admin section, or false for a front-end page. This function does not verify whether the current user has permission to view the Dashboard or the administration panel. Use current_user_can() instead. Here's the source code containing the security flaw, which is part of the assets/ilenframework/core.php file shipped with the plugin: As you can see, the code allows to issue a call to the self::ini() function to all requests directed to an administration page - thus including /wp-admin/options-general.php and /wp-admin/admin-post .php - which allows the attacker to inoculate a POST request and, consequently, arbitrarily modify the plugin options via the self::save_options() function (which is called later in the code). Among the various options of the plugin that it is possible to modify in this way there is the yuzo_related_post_css_and_style setting, which allows you to insert custom HTML code within the page: the perfect place to insert a Cross-Site Script in order to perform a series of actions not authorized, including the redirect to another site. As is now known, the attacker(s) did precisely that, causing a malicious XSS redirect of many yuzo-enabled websites to the hellofromhony.org domain, where the scripts, and then on unsafe sites like silken.ru. Here's the JavaScript code that was injected inside the yuzo_related_post_css_and_style option: The malicious script consists of a single eval() statement, a function often used by developers to execute "obfuscated" JavaScript in the form of an encoded string. The code, once decoded, can be read in this way: As you can see, this is a trivial (but far from harmless) redirect script, which allows the attacker to "hijack" each visitor's browser on a web page of his choice. A big "thank you" to Wordfence.com, the official website of the excellent Wordfence Security WP plugin, for having published the news and therefore warned the entire Wordpress community on one of the most relevant threats of recent times. Read the full article
0 notes
Link
PHP Job Script Solutions by Voizac - The Mobile responsive features make the product more adaptable. Code is fully open-source and you can customize it as per your requirements. Our software is a completely customizable solution that enables Administrators to earn revenues through their premium job seekers.The source code is completely secure and can be modified and customized according to the business needs. #voizac #jobs #jobportal #php #phpscript #solution #sitescript #hr #career #jobsolution
0 notes
Photo

OkCupid Dating App Flaws Could've Let Hackers Read Your Private Messages #ashleymadison #cross-sitescripting #databreach #datingscam #hackingnews #mobileapp #okcupid #onlinedatingapp #privacy #tinderapp #websitesecurity #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo
CUP OF CYBER - Security+ Cross Site Scripting http://ehelpdesk.tk/wp-content/uploads/2020/02/logo-header.png [ad_1] Today we look at Cross Site Scri... #awscertification #awscertifiedcloudpractitioner #awscertifieddeveloper #awscertifiedsolutionsarchitect #awscertifiedsysopsadministrator #ciscoccna #comptiaa #comptianetwork #comptiasecurity #cross-sitescripting #cupofcyber #cybersecurity #ethicalhacking #it #kubernetes #linux #microsoftaz-900 #microsoftazure #networksecurity #security #software #websecurity #websecuritytutorial #whatiscrosssitescripting #whatisxss #windowsserver #xssattack #xsstutorial #xssvulnerability
0 notes
Text
Yuzo Related Posts - Falla di sicurezza nel plugin Wordpress

Decisamente una brutta settimana per Lenin Zapata, autore del noto plugin Yuzo Related Post per Wordpress. Il plugin, installato su oltre 60.000 siti web, è stato rimosso dalla directory dei plug-in di WordPress.org il 30 marzo 2019 a seguito della divulgazione pubblica di una vulnerabilità presente all'interno del codice. La vulnerabilità, ad oggi ancora priva di patch, consente all'attacker di inserire uno script all'interno delle pagine dei siti web che hanno il plugin installato mediante una tecnica nota come Cross-Site Scripting (XSS). La vulnerabilità presente nel plugin è frutto di un utilizzo improprio della funzione is_admin(), che ha il preciso scopo di verificare se la URL a cui si accede si trova nella sezione di amministrazione ma che viene erroneamente utilizzata da molti sviluppatori di plugin Wordpress per controllare se l'utente corrente dispone o meno di privilegi amministrativi. Un "fraintendimento" tutt'altro che banale, al punto che il Wordpress Codex ravvisa in modo esplicito la necessità di astenersi da questo utilizzo errato: This Conditional Tag checks if the Dashboard or the administration panel is attempting to be displayed. It is a boolean function that will return true if the URL being accessed is in the admin section, or false for a front-end page. This function does not verify whether the current user has permission to view the Dashboard or the administration panel. Use current_user_can() instead. Di seguito il punto di codice sorgente incriminato, presente nel file assets/ilenframework/core.php e comune a tutte le versioni più recenti del plugin: Come si può vedere, il codice consente la chiamata a self::ini() a tutte le request dirette verso una pagina di amministrazione, incluse le varie /wp-admin/options-general.php e /wp-admin/admin-post.php, che consente all'attacker di inoculare una request di tipo POST e, di conseguenza, modificare arbitrariamente le opzioni del plugin sfruttando una chiamata alla funzione self::save_options() presente più avanti nel codice. Tra le varie opzioni del plugin che è possibile modificare in questo modo vi è anche la yuzo_related_post_css_and_style, che consente di inserire codice HTML personalizzato all'interno della pagina: il posto perfetto per inserire un Cross-Site Script al fine effettuare una serie di azioni non autorizzate, tra cui il redirect verso un altro sito. Come è ormai noto, la scelta dell'attacker è stata stata proprio quella, provocando un redirect coatto di tutti i siti oggetto dell'attacco prima sul dominio hellofromhony.org, dove era ospitato lo script, e successivamente su siti non sicuri come silken.ru. Questo il codice JavaScript inoculato all'interno dell'opzione yuzo_related_post_css_and_style: Come si può vedere si tratta di una istruzione eval(), un metodo utilizzato dagli sviluppatori per eseguire codice JavaScript "offuscato" sotto forma di una stringa codificata. Il codice, una volta decodificato, si può leggere in questo modo: Come si può vedere, si tratta di un banale (ma tutt'altro che innocuo) script di redirect, che consente all'attacker di "dirottare" il browser di ciascun visitatore su una pagina web a sua scelta. Un grazie a Wordfence.com, il sito ufficiale dell'ottimo plugin di sicurezza per WordPress Wordfence Security, per aver pubblicato la notizia, mettendo così in guardia l'intera comunità Wordpress su una delle minacce più rilevanti degli ultimi tempi. Read the full article
0 notes
Photo

Page Builder WordPress Plugin Bugs Could Allow Complete Site Takeover #bug #codeinjection #cross-siterequestforgery #cross-sitescripting #flaw #maliciouscodeinjection #plugin #plugins #reflectedxss #securityfix #securityflaw #vulnerabilities #vulnerability #vulnerablewordpressplugin #websitetakeover #wordpress #wordpressexploit #wordpresspatch #wordpressplugin #wordpressplugins #wordpressvulnerability #xss #xssflaw #xssvulnerability #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

XSS Vulnerability Found In Real-Time Find and Replace WordPress Plugin #bug #codeinjection #cross-siterequestforgery #cross-sitescripting #flaw #maliciouscodeinjection #plugin #plugins #securityfix #securityflaw #storedxss #vulnerabilities #vulnerability #vulnerablewordpressplugin #wordpress #wordpressexploit #wordpresspatch #wordpressplugin #wordpressplugins #wordpressvulnerability #xss #xssflaw #xssvulnerability #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

CSRF To XSS Vulnerability In Ninja Forms Risked Over 1 Million WordPress Sites #bug #codeinjection #cross-siterequestforgery #cross-sitescripting #flaw #maliciouscodeinjection #plugin #plugins #securityfix #securityflaw #storedxss #vulnerabilities #vulnerability #vulnerablewordpressplugin #wordpress #wordpressexploit #wordpresspatch #wordpressplugin #wordpressplugins #wordpressvulnerability #xss #xssflaw #xssvulnerability #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

Microsoft Patch Tuesday April Brings Fixes For 113 Vulnerabilities Including Actively Exploited Bugs #arbitrarycodeexecution #bug #cross-sitescripting #escalatewindowsprivilege #flaw #informationdisclosure #internetexplorer #memorycorruption #microsoft #microsoftbug #microsoftexploit #microsoftpatch #microsoftpatchtuesday #microsoftpatchtuesdayupdate #microsoftupdate #microsoftvulnerability #patchtuesday #privilegeescalation #rce #remotecode #remotecodeexecution #remotedesktop #spoofing #vulnerabilities #vulnerability #xssflaw #xssvulnerability #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

Find Your XSS Bug Bounty With XSS-LOADER #bugbounty #cross-sitescripting #htmltags #xssloader #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

Get XSS bug bounty with XSSfinder #cross-sitescripting #xss #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo

Multiple TikTok Vulnerabilities Could Exploit Or Delete Users’ Personal Data #checkpoint #checkpoint #cross-siterequestforgery #cross-sitescripting #csrf #csrfflaws #csrfvulnerabilities #flaws #smsspoofing #spoofing #tiktok #tiktokapp #tiktokbug #tiktokflaw #tiktokvulnerability #vulnerabilities #vulnerability #xss #xssflaw #xssvulnerability #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo
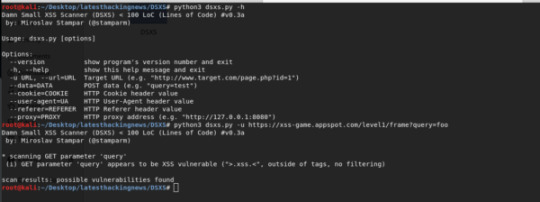
DSXS | An open source, simple and effective XSS scanner that can be easily customized #bestgithubhackingtools #cross-sitescripting #dsxs #freehackingchallenges #freehackingtools #githubhackertools #sourcecodeanalysis #vulnerability #webexploitation #xss #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes