#SQLinjection
Explore tagged Tumblr posts
Text
SQLi simulation using a virtual machine
Demonstration/simulation of SQL Injection attacks (In-band, Union-based, Blind SQLi) using a Kali Linux virtual machine and a Damn Vulnerable Web Application (DVWA) on a low difficulty level
Blind SQL provided in the video can be used also for gaining other sensitive information: length of the name of the database, database name itself etc.
the common attacks are shown and described shortly in the video, but of course for better learning you can try it yourself.
more resources where you can try out exploiting SQLi vulnerability:
- Try Hack Me SQLi Lab
- W3Schools SQL Injection
- Hacksplaining SQL Injection
more advanced pokemons can try:
- Try Hack Me SQli Advanced Lab
and of course DVWA is a great tool!
5 notes
·
View notes
Text
🔒 Bahaya SQL Injection: Kenapa Website Kamu Butuh Perlindungan!
Hai teman-teman! Pernah nggak sih kepikiran kalau data di website bisa bocor cuma karena satu celah kecil? Nah, itu bisa banget terjadi kalau website kita rentan terhadap SQL Injection. Aku baru aja nyobain eksperimen simpel dan juga sebagai bagian dari tugas aku gimana bahayanya, dan aku mau sharing biar kalian juga paham dan tahu cara melindungi situs kalian. Yuk, simak!
Apa Itu SQL Injection?
Jadi begini, SQL Injection itu kayak hacker nyisipin kode jahat ke website lewat inputan yang seharusnya aman. Kalau kita nggak hati-hati, kode itu bisa bikin mereka mengakses semua data di database, bahkan mengubah atau menghapusnya! Bayangin, data pribadi, password, sampai data penting lain bisa diambil cuma karena website kita nggak aman.
Eksperimen Sederhana: Melihat Kerentanan Website
Aku buat website kecil pakai PHP dan MySQL buat coba-coba. Contohnya kayak gini:
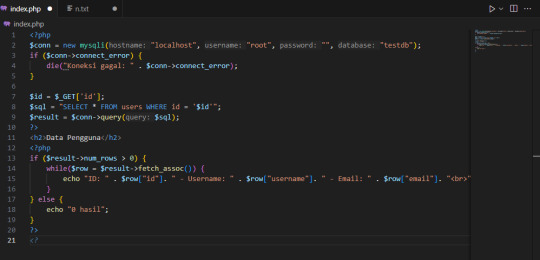
Kalau akses URL-nya kayak gini:
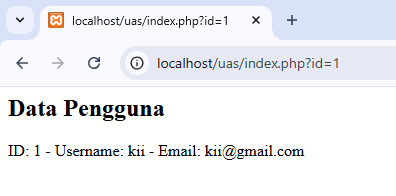
maka akan tampil data pengguna ID = 1
Tapi kalau diubah jadi: http://localhost/uas/index.php?id=1' OR '1'='1

tiba-tiba semua data pengguna muncul! Ini bahaya banget, kan? Website itu rentan banget kalau nggak diproteksi.
Kenapa Bahaya?
Serangan kayak gini bisa bikin data bocor, diubah, atau dihapus sama pihak nggak bertanggung jawab. Kalau data penting kayak password, data pelanggan, atau info rahasia lain bocor, reputasi dan kepercayaan bisa rusak parah.
Solusi Ampuh: Pakai Prepared Statements
Gampang banget, tinggal pakai prepared statements. Contohnya kayak ini:
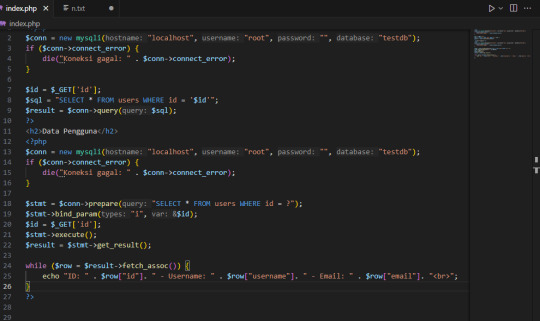
Nah, dengan cara ini, input dari pengguna dianggap sebagai data, bukan bagian dari query SQL. Jadi, serangan kayak tadi nggak bakal berhasil lagi!
Tips Tambahan buat Website Aman nihh
Validasi input: Pastikan data yang masuk sesuai format yang diharapkan.
Update software & plugin: Biarkan selalu terbaru buat nutup celah.
Batasi hak akses database: Jangan kasih hak penuh ke user database.
Backup rutin: Kalau terjadi sesuatu, data bisa dipulihkan.
Kesimpulan
Gak mau kan data kita gampang diambil orang? Pelajaran pentingnya, jangan remehkan soal keamanan. Dengan langkah simpel kayak pakai prepared statements, kita bisa jauh lebih aman dari serangan SQL Injection. Yuk, mulai perhatikan keamanan website dari sekarang! Karena data kita berharga banget, guys.
Kalau kalian suka dan mau belajar lebih jauh soal keamanan web, comment atau repost ya! Aku bakal bahas lagi soal tips dan trik lainnya. kalo ingin lebih liat lengkap caranya gimana bisa langsung ke Github-ku yaa. Cheers! ✨
Referensi
https://owasp.org/www-community/attacks/SQL_Injection
https://www.php.net/manual/en/mysqli.prepare.php
1 note
·
View note
Text
AI-Powered Security: The Future of Fraud Prevention in eCommerce
Your eCommerce business needs more than just a firewall to stay safe.
Dive into our latest blog and find out how Diginyze's AI-powered security mechanism provides multi-layered protection against fraud and secures your eCommerce business.
Check it out: https://www.diginyze.com/blog/ai-powered-security-the-future-of-fraud-prevention-in-ecommerce/

#eCommerce#AI#CyberSecurity#FraudPrevention#Bots#SQLInjection#DDoS#eCommerceSecurity#IdentityTheft#Hackers#CyberThreats#OnlineFraud#AIinEcommerce#SecurePayments#CreditCardFrauds#DataProtection#IdentityTheftProtection#PhishingProtection#CustomerExperience#SecureShopping#PCICompliance#DDoSProtection#SSL#APIs#RiskBasedAuthentication#BotProtection#DataEncryption#AIforFraudDetection
0 notes
Text

SQL Injection (SQLI) . . . for more information and tutorial https://bit.ly/3ULSU2q check the above link
#cybersecurity#mobilesecurity#DDoS#bruteforce#sqlinjection#cloudsecurity#applicationsecurity#databse#dbms#computerscience#computerengineering#javatpoint
0 notes
Text
The Hacker’s Wake-Up Call: 10 Reasons Why They Should Worry About Being Outsmarted (Part 2)
Fix Hacked Site – Malware Removal and Website Security Service. The Hacker’s Wake-Up Call: 10 Reasons Why They Should Worry About Being Outsmarted (Part 2) 10 Reasons Why Small Businesses Should Worry About Hackers Limited Resources and Expertise Hackers continuously hone their skills in the ever-evolving digital landscape and find new ways to exploit vulnerabilities. You may feel invincible as…
View On WordPress
#BrowsingCache#BruteforceAttack#CSSfiles#DDOSAttack#Firewall#HackCleanup#HackedWebsites#HiddeniFrames#HTML#JavaScript#MalwareRemoval#PerformanceOptimization#pluginerrors#SecurityOptimization#SQLInjection#SSL#StopHacks#WebsitePerformance#WebsiteSpeed#WordPressDatabase
0 notes
Text
API Errors can be costly! Errors in APIs can lead to significant issues like service outages, incorrect billing, and other service disruptions.
The average cost of an IT outage was $5,600 per minute for a telecom operator.
Our API Testing services can help address this issue.
Visit: https://www.avisysservices.com/testing-coe/

#Telco#TestingTools#PerformanceOptimization#TCoE#Testing#VulnerabilityTesting#SQLInjection#CrossSiteScripting#TelecomAPIs#QualityAssurance#AutomatedTesting#APIsecurity#Selenium#JMeter#UFT
0 notes
Video
youtube
3 Red Flags to Watch Out for in SQL Injection
#youtube#Cybersecurity SQLInjection Hacking WebSecurity Databreach Malware Protection Firewalls Awareness
1 note
·
View note
Text
SQL Injection – Mối đe dọa thường trực cần được xử lý nghiêm túc
SQL Injection – Mối đe dọa thường trực cần được xử lý nghiêm túc #SQLInjection #AnNinhMang #BaoMatThongTin #LoiHong #Cybersecurity SQL Injection (SQLi) là một kỹ thuật tấn công mạng lâu đời nhưng vẫn vô cùng nguy hiểm. Mặc dù đã được cảnh báo nhiều năm, gần đây vẫn xuất hiện nhiều trường hợp hệ thống bị tấn công thành công thông qua lỗ hổng này, đặt ra câu hỏi lớn về hiệu quả của các biện pháp…
0 notes
Text
🚨 SQL Injection : La menace que tout dev doit connaître ! 🚨 💻 Tu penses que ton site est sécurisé ? Imagine un hacker qui pourrait en quelques requêtes SQL : ⚠️ Contourner ton login et accéder à l’admin ⚠️ Exfiltrer ta base de données sans laisser de trace ⚠️ Prendre le contrôle total de ton site web ainsi que ton serveur Dans la première partie, nous avons vu les bases de l'injection SQL : contourner une authentification et repérer une vulnérabilité via les erreurs. Aujourd’hui, on passe au niveau supérieur : les attaques injection SQL avancées et comment s’en protéger ! 📌 Découvre la suite ici : Dangers de l'injection SQL – Partie 2 : https://www.patreon.com/posts/dangers-de-sql-2-125373191 💡 Pour accéder à plus de tutos exclusifs et approfondir tes connaissances en cybersécurité, rejoins-moi sur Patreon ! Ensemble, rendons le web plus sûr. 🔐 #CyberSécurité #SQLInjection #DéveloppementWeb #HackingÉthique #Patreon
0 notes
Text
SQLMutant: Advanced Tool for SQL Injection | #Pentesting #RedTeam #SQLInjection #SQLi #SQLMutant #Hacking
1 note
·
View note
Text
Remediation of SQLi
Defense Option 1: Prepared Statements (with Parameterized Queries)
Prepared statements ensure that an attacker is not able to change the intent of a query, even if SQL commands are inserted by an attacker. In the safe example below, if an attacker were to enter the userID of tom' or '1'='1, the parameterized query would not be vulnerable and would instead look for a username which literally matched the entire string tom' or '1'='1.
Defense Option 2: Stored Procedures
The difference between prepared statements and stored procedures is that the SQL code for a stored procedure is defined and stored in the database itself, and then called from the application.
Both of these techniques have the same effectiveness in preventing SQL injection so it is reasonable to choose which approach makes the most sense for you. Stored procedures are not always safe from SQL injection. However, certain standard stored procedure programming constructs have the same effect as the use of parameterized queries when implemented safely (the stored procedure does not include any unsafe dynamic SQL generation) which is the norm for most stored procedure languages.
Defense Option 3: Allow-List Input Validation
Various parts of SQL queries aren't legal locations for the use of bind variables, such as the names of tables or columns, and the sort order indicator (ASC or DESC). In such situations, input validation or query redesign is the most appropriate defense. For the names of tables or columns, ideally those values come from the code, and not from user parameters.
But if user parameter values are used to make different for table names and column names, then the parameter values should be mapped to the legal/expected table or column names to make sure unvalidated user input doesn't end up in the query. Please note, this is a symptom of poor design and a full rewrite should be considered if time allows.
Defense Option 4: Escaping All User-Supplied Input
This technique should only be used as a last resort, when none of the above are feasible. Input validation is probably a better choice as this methodology is frail compared to other defenses and we cannot guarantee it will prevent all SQL Injection in all situations.
This technique is to escape user input before putting it in a query and usually only recommended to retrofit legacy code when implementing input validation isn't cost effective.
3 notes
·
View notes
Text
Get 100% free coupon for udemy courses.
Hope you are kind enough to give me a review please.
Check your knowledge and test your skill in a professional way.
AZ-204: Developing Solutions Microsoft Practice Test 2024
#sqlserver #sqlite #SQLAB #sqldeveloper #sqlinjection #sqlimercontest #Sqlmap
1 note
·
View note
Text
☢️ SQL Injection: Web Application Vulnerabilities
In this article we will look at the essence of SQL injections, their operating principle, methods of attacking databases through SQL queries, as well as methods of protecting against such attacks.
▶️ Read the article https://redfishiaven.blogspot.com/2024/05/sql-injections-web-application.html
#redfishiaven #SQLInjection #Cybersecurity #databreach #websecurity #sqlsecurity
1 note
·
View note
Text
Top 20 Open Source Vulnerability Scanner Tools in 2023
Top 20 Open Source Vulnerability Scanner Tools in 2023 @vexpert #vmwarecommunities #100daysofhomelab #homelab #OpenSourceVulnerabilityScanners #SecurityTools #VulnerabilityAssessment #PenetrationTesting #SQLInjection #NetworkVulnerabilityTests
In the world of cybersecurity, having the right tools is more important than ever. An extremely important tool for cybersecurity professionals is the vulnerability scanners. They are designed to automatically detect vulnerabilities, security issues, and potential threats in your systems, applications, or network traffic. By carrying out network vulnerability tests and scanning web applications,…

View On WordPress
#Container Image Scanning#License Compliance#Network Vulnerability Tests#Open Source Vulnerability Scanners#Penetration Testing#Security Testing#security tools#Software Composition Analysis#SQL Injection#Vulnerability Assessment
0 notes
Text

Brute Force . . . for more information and tutorial https://bit.ly/3ULSU2q check the above link
#cybersecurity#mobilesecurity#DDoS#bruteforce#sqlinjection#cloudsecurity#applicationsecurity#databse#dbms#computerscience#computerengineering#javatpoint
0 notes
Text
The Hacker’s Wake-Up Call: 10 Reasons Why They Should Worry About Being Outsmarted
Fix Hacked Site – Malware Removal and Website Security Service. The Hacker’s Wake-Up Call: 10 Reasons Why They Should Worry About Being Outsmarted Introduction The Growing Threat of Hackers In today’s digital age, the threat of hackers is growing alarmingly. Armed with advanced technological skills and malicious intent, Hackers are constantly devising new ways to infiltrate systems, steal…
View On WordPress
#BrowsingCache#BruteforceAttack#CSSfiles#DDOSAttack#Firewall#HackCleanup#HackedWebsites#HiddeniFrames#HTML#JavaScript#MalwareRemoval#PerformanceOptimization#pluginerrors#SecurityOptimization#SQLInjection#SSL#StopHacks#WebsitePerformance#WebsiteSpeed#WordPressDatabase
0 notes