#Steps to run java program in cmd
Explore tagged Tumblr posts
Text
A Guide to Creating APIs for Web Applications
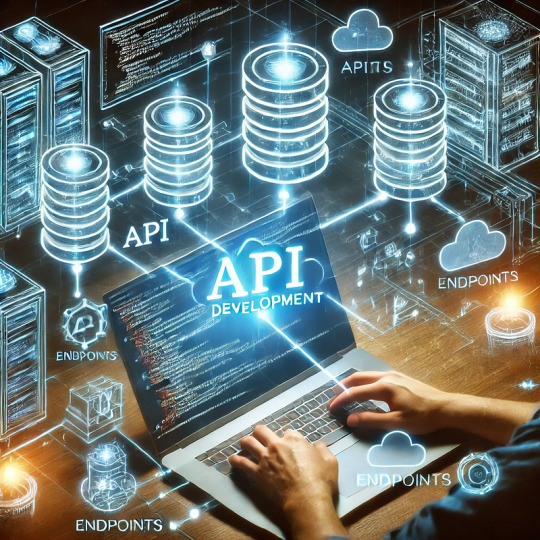
APIs (Application Programming Interfaces) are the backbone of modern web applications, enabling communication between frontend and backend systems, third-party services, and databases. In this guide, we’ll explore how to create APIs, best practices, and tools to use.
1. Understanding APIs in Web Applications
An API allows different software applications to communicate using defined rules. Web APIs specifically enable interaction between a client (frontend) and a server (backend) using protocols like REST, GraphQL, or gRPC.
Types of APIs
RESTful APIs — Uses HTTP methods (GET, POST, PUT, DELETE) to perform operations on resources.
GraphQL APIs — Allows clients to request only the data they need, reducing over-fetching.
gRPC APIs — Uses protocol buffers for high-performance communication, suitable for microservices.
2. Setting Up a REST API: Step-by-Step
Step 1: Choose a Framework
Node.js (Express.js) — Lightweight and popular for JavaScript applications.
Python (Flask/Django) — Flask is simple, while Django provides built-in features.
Java (Spring Boot) — Enterprise-level framework for Java-based APIs.
Step 2: Create a Basic API
Here’s an example of a simple REST API using Express.js (Node.js):javascriptconst express = require('express'); const app = express(); app.use(express.json());let users = [{ id: 1, name: "John Doe" }];app.get('/users', (req, res) => { res.json(users); });app.post('/users', (req, res) => { const user = { id: users.length + 1, name: req.body.name }; users.push(user); res.status(201).json(user); });app.listen(3000, () => console.log('API running on port 3000'));
Step 3: Connect to a Database
APIs often need a database to store and retrieve data. Popular databases include:
SQL Databases (PostgreSQL, MySQL) — Structured data storage.
NoSQL Databases (MongoDB, Firebase) — Unstructured or flexible data storage.
Example of integrating MongoDB using Mongoose in Node.js:javascriptconst mongoose = require('mongoose'); mongoose.connect('mongodb://localhost:27017/mydb', { useNewUrlParser: true, useUnifiedTopology: true });const UserSchema = new mongoose.Schema({ name: String }); const User = mongoose.model('User', UserSchema);app.post('/users', async (req, res) => { const user = new User({ name: req.body.name }); await user.save(); res.status(201).json(user); });
3. Best Practices for API Development
🔹 Use Proper HTTP Methods:
GET – Retrieve data
POST – Create new data
PUT/PATCH – Update existing data
DELETE – Remove data
🔹 Implement Authentication & Authorization
Use JWT (JSON Web Token) or OAuth for securing APIs.
Example of JWT authentication in Express.js:
javascript
const jwt = require('jsonwebtoken'); const token = jwt.sign({ userId: 1 }, 'secretKey', { expiresIn: '1h' });
🔹 Handle Errors Gracefully
Return appropriate status codes (400 for bad requests, 404 for not found, 500 for server errors).
Example:
javascript
app.use((err, req, res, next) => { res.status(500).json({ error: err.message }); });
🔹 Use API Documentation Tools
Swagger or Postman to document and test APIs.
4. Deploying Your API
Once your API is built, deploy it using:
Cloud Platforms: AWS (Lambda, EC2), Google Cloud, Azure.
Serverless Functions: AWS Lambda, Vercel, Firebase Functions.
Containerization: Deploy APIs using Docker and Kubernetes.
Example: Deploying with DockerdockerfileFROM node:14 WORKDIR /app COPY package.json ./ RUN npm install COPY . . CMD ["node", "server.js"] EXPOSE 3000
5. API Testing and Monitoring
Use Postman or Insomnia for testing API requests.
Monitor API Performance with tools like Prometheus, New Relic, or Datadog.
Final Thoughts
Creating APIs for web applications involves careful planning, development, and deployment. Following best practices ensures security, scalability, and efficiency.
WEBSITE: https://www.ficusoft.in/python-training-in-chennai/
0 notes
Text
Complete Salesforce Deployment using Ant Migration Tool ..
Apache ANT: Apache Ant is a Java library. The main known usage of Ant is the build of Java applications, also it can be used effectively to build non Java applications. Ant can be used to pilot any type of process which can be described in terms of targets and tasks. Ant is extremely flexible and does not impose coding conventions or directory layouts to the Java projects which adopt it as a build tool. Ant UI as provided in Eclipse comes with a first-class Ant build-file editor, including syntax highlighting, Content Assist, templates, and content formatting. The Ant UI also has a wizard for running Ant scripts and a toolbar button for repeating previous builds.
Apache ANT – A Tool? Configuring A Java build process typically includes:
The compilation of the Java source code into Java byte-code
Creation of the .jar file for the distribution of the code
Creation of the Java doc. documentation
Installation of Java: Recommended Java latest version It is recommended to use last least the latest long-term release version of Java. To run Java programs, you:
Must have the Java run-time environment (JRE) installed
The Java executable must be available in your path environment
You can test if the JRE is correctly installed via a console. To open a console on Windows: Win+R, enter cmd and press Enter.
Now type in the following command: java -version
If the JRE is correctly installed, this commands prints information about your Java installation.
If you don’t have java install…. you need to follow steps to install Java. You must have Platform:
Windows 2008 Server
Windows 7
Windows 8
Windows XP
Windows Server 2012
Windows Vista
Windows 10
Java version: Recommended Latest
Before proceed with online installation you may need to disable Internet firewall. Due to auto firewall settings they may be reject online or auto installation.
Steps to follow: Installation process Online
Go to the Manual download page
Click on Windows Online
The Downloading box appears to run or save file into your machine
When downloading finishes, you need to run the installer
Click on Run
Note:
Save file to known location on your computer
To start quick installation you need to Double-click on saved file
When installation process starts…click the Install button to accept the license terms and to continue with the installation
In last steps of installation process, click “CLOSE”. This will complete Java installation process.
Deployment using ANT Migration Tool Lot of tool available to develop in Salesforce, when we comes to deployment we have few opt to adopt. The easiest way to do Salesforce deployment, but certain components cannot be deployed through change-set, then after we need to apply or deploy certain components.
Why we use ANT Tool?
Deploying Metadata from an organization to another using Salesforce migration ANT tool, it retrieves metadata locally
It provides extra tools which can be used and an added advantage is to get metadata in form of XML from servers and can be download directly into our machine
When metadata can de downloaded directly into machine from local server, you can make changes easily in your XML files
The Components which can’t migrated using change-sets in Salesforce(dot)com , we can easily migrate using Salesforce migration ANT Tool
Steps need to follow while doing data migration for one SF org to another org
First we have to ensure that you have Ant relocation device in your system
We require to give subtleties of the qualifications and the sort of metadata you need to move
We need Java and Apache Ant introduced on your framework
Next step is to stack the accreditation’s of both the Salesforce organization in the document called ‘build.properties’
The certifications that gives is that it goes to the record ‘build.xml’. When the information is being moved, the build.xml document is what is utilized? At that point we can give subtleties of the metadata that we need to move to the org. It could be anything i.e classes, custom and standard items, custom fields etc
We can give these subtleties in the document ‘package.xml’
In wake of giving every one of subtleties, we can initially recover the information from Salesforce org & utilize order of ‘insect retrieveUnpackaged’ and pursued by ‘subterranean insect deployUnpackaged’ after the recovering has been effectively done by the process.
Before doing above, we need to ensure everything that path has been set up to the directory of the ‘unpackaged’ folder.
If you found this post is important for you, you can touch-base with us & for more tips, tricks and strategies to uncover information from your queries and concerns or if you need for more hands-on and live involvement with our experts, you can write us. Our online training is a mixture of study materials, real-world scenario , Salesforce use cases and hands-on experience and a real time project, so that you can easily prepare yourself for any interview and examinations, we have recommend our experienced experts and real time professionals for the certification training and their guidance out there, as well as they shares real time experience with candidates.
1 note
·
View note
Text
Java se development kit 10 install fails

Java se development kit 10 install fails how to#
Java se development kit 10 install fails install#
Java se development kit 10 install fails update#
Java se development kit 10 install fails 32 bit#
Java se development kit 10 install fails full#
OS: Win11 Pro, Win10 Pro N, Win10 Home, Windows 8.1 Pro, Ubuntu System Manufacturer/Model Number: ۞ΞЖ†ԘΜΞ۞ Java - What is the difference between JDK and JRE? - Stack Overflow Why would you need JDK then? Because application server will convert JSP into Servlets and use JDK to compile the servlets. For example, if you are deploying a WebApp with JSP, you are technically just running Java Programs inside the application server. Sometimes, even though you are not planning to do any Java Development on a computer, you still need the JDK installed. On the other hand, if you are planning to do some Java programming, you will also need JDK.
Java se development kit 10 install fails install#
Usually, when you only care about running Java programs on your browser or computer you will only install JRE.
Java se development kit 10 install fails full#
JDK: It's the full featured Software Development Kit for Java, including JRE, and the compilers and tools (like JavaDoc, and Java Debugger) to create and compile programs. It also includes browser plugins for Applet execution. It is basically the Java Virtual Machine where your Java programs run on.
Java se development kit 10 install fails how to#
How to open or run a JAR file on Windows.JRE: Java Runtime Environment.
Java Virtual Machine Launcher, Could not create the Java Virtual Machine.
Most modern computers will be able to run Java JRE perfectly without any hassle. So, as you can see that specs are not an option.
Browsers: Internet Explorer versions 9 and higher, Mozilla Firefox.
Processor: Intel Pentium II 266 MHz CPU or above.
Java se development kit 10 install fails update#
Space: 124 MB or more for JRE (Java Runtime Environment) + 2 MB for Java Update.
Operating system: Windows 7 or above, Server 2008, Server 2012 (including R2).
Your computer just needs to meet the following requirements and you will be good to go. Java is a programming language and to install it you don’t need tons of bells and whistles, and we are going to prove it. What are the system requirements for Java? If you are using a 64-bit variant, then it gives you information about the Java installed on your system. Then this means that you are using a 32-bit variant. If it says something like the following error message.Įrror: This Java instance does not support a 64-bit JVM. It is an easy step, just open CMD with administrative privileges. You can use the Command Prompt to check if you are using Java 32-bit or 64-bit.
Java se development kit 10 install fails 32 bit#
How do you check my Java is 32 bit or 64 bit? Read: Java security – Tips for using Java securely on Windows. Then restart your computer and you will be good to go. Windows 11: Click on the three vertical dots and select Uninstall. Windows 10: Select Java and click Uninstall.If you don’t want to install anything then you need to use Windows Settings to remove Java from your system. After uninstalling the language it is advisable to restart your computer. You can easily install Java Uninstall Tool from and then use it to remove Java from your computer. Let us start with a utility provided by Java, i.e Uninstall Tool. But you need to make sure that you are removing them completely and in this section, we are going to see how to do the same. There are two ways by which you can remove Java completely from Windows PC. Sometimes, it is required to remove all the older versions of Java. Then follow the on-screen instructions to install it on your computer. If you are a developer and want to install Java SE Development Kit then go to and download the one for your Operating System. Now, follow the on-screen instructions to install Java JRE on your computer.Click Agree and Start freeload and your download will begin.Visit and then click on the Download tab.To download Java 64-bit and 32-bit on your computer, you need to follow the given steps. Download Java 64-bit and 32-bit for Windows 11/10 Do note that Java is not to be confused with JavaScript. It is not only important for developers but also for someone who wants to run apps and websites built with the help of this language. It is one of the world’s leading software development tools used by many programmers to create software, games, and other projects. Java is an Objected Oriented Programming Language, allows users to build and run their game in its environment. That’s why we are here to answer from where to download Java 64-bit and 32-bit for Windows 11/10? Not only that, there are a lot of games, websites, and apps that won’t run on your system if you don’t have Java installed on it. So, if you want to ride the bandwagon and use the language, you must download it on your system. Java is one of those OOPs based languages, along with Python and C++, that’s in demand right now.

0 notes
Text
Installed new jdk on mac but

Installed new jdk on mac but how to#
Installed new jdk on mac but archive#
Installed new jdk on mac but windows 10#
Installed new jdk on mac but license#
Installed new jdk on mac but windows 10#
Now pat yourself in the back cause you’ve successfully installed JDK in windows 10 all by yourself🤗🤗. A small window will appear to click on yes and the installation will begin.ĥ) Once the installation gets finished a new installation wizard for Java will appear, here click next.Ħ) After that you’ll be asked to choose the installation folder, here we will go with the default installation folder so click on next.ħ) A progress bar will appear showing the installation progress, once it gets completed “ Java(TM) SE Development Kit successfully installed” will appear on the screen and after that click on the close button.Ĭongrats 👏👏, by this time you’ve successfully installed JDK in your windows 10 machine.ġ) To check if JDK is installed properly or not, open up your command prompt by pressing the Windows button, type “ cmd” and press enter.Ģ) In the command prompt type, “ java –version” and press enter to check the installed version of JDK.ģ) After that type “ javac –version” and press enter to check the installed version of the java compiler. Depending on your internet connection the JDK file will get downloaded accordingly.Ĥ) Now go to the folder where the downloaded exe file is available, right-click on the file and run it as administrator.
Installed new jdk on mac but license#
Click on that link to download the installer for windows 10.ģ) A popup screen will appear here, check the license agreement box and click on the long green download button. Now scroll down and there you’ll see a “ windows X64 Installer” row and next to that a download link is given. Once you’re on that page click on the “ JDK Download” button.Ģ) After that, you’ll be redirected to the “ Java SE Development Kit Downloads” page. From there you’ll be redirected to the official JDK download page. Step 1: Download the latest version of JDK (Java Development Kit)ġ) First things first you’ll need to download a jdk.exe and to download that you’ll have to click on the download link we’ve provided below. If you’re still finding it hard installing JDK on your Windows 10 machine then you can refer to the below video for a complete guide.
Installed new jdk on mac but how to#
Video Tutorial: How to Install Java JDK JRE on Windows 10 So today let’s download and Install Java JDK JRE in your windows 10. However, the process of downloading and installing JDK is not that hard. If you want, assign a new name to the JDK. Select the Home directory, and click Next. The directory chooser should show Home and MacOS, and Home should have an icon on it indicating it is a Java home directory. If successful, mvn -version will return info on what was just installed.To run any Java program you need JDK installed on your windows machine. Type '/Library/Java/JavaVirtualMachines/1.7.0.jdk/Contents' in the File field. bash_profile to refresh it and then run mvn -version. Once done, quit the Terminal window, reopen a new one and type the following command to check if the system variable has been. If you're using the same terminal, go ahead and clear it with CMD + K. The latest version as of 08/26/20 is 3.6.3.Įxport M2_HOME=/Applications/apache-maven-3.6.3 Version number will vary based on when you're reading this. bash_profile again and add these two variables. Once it's downloaded, move it into your Applications folder and unzip it ( unzip apache-maven-3.6.3-bin.zip).
Installed new jdk on mac but archive#
This tutorial follows downloading the binary zip archive file. The problem is that this tool has a dependency on Java 8, however, my installed JDK is 7, and I have to keep it for all existing Java projects.
Add export JAVA_HOME=$(/usr/libexec/java_home) to the file and save it.
bash_profile, go ahead and create one with touch. If you run echo $JAVA_HOME and it returns blank, it means you haven't set the variable yet. bash_profile, you can skip the next step).
Next, you'll need to add the $JAVA_HOME variable in your.
In your terminal, if you run java -version again now, it should return details of the installed JDK.
You can check the installed Java path by going to your Mac's Settings > Java > Java (within the Java Control Panel) > Path.
If you don't have a JDK installed, you can download it here.
Open a new terminal and run java -version.
You can skip the first half if you already have Java JDK installed. I've needed to set up Java and Maven enough times that I figured I should write about it so that it's an easier setup for at least one other person.

0 notes
Text
How to play Minecraft on LAN [TLauncher]

How to play Minecraft on LAN [TLauncher]
The recreation has long brought the option to create a nearby server for your very own world, and all who are on your neighborhood network may be able to hook up with how to play minecraft java with friends your server. In fashionable, everything is simple, but there are many barriers, in this newsletter all is described in element. Select the desired configuration type from the contents and observe the steps defined.
Contents:
Server Configuration When You Are on the Same Wi-Fi or LAN Network with Another PlayerServer Configuration When Playing over the Internet with Another Player Using Hamachi Setting up a Local Minecraft Server with Mods Possible Problems and Solutions
Server Configuration When You Are on the Same Wi-Fi or LAN Network with Another Player If numerous PCs aren't far from every other and are on the identical Wi-Fi or LAN network (related through cable), then this putting will in shape your case.
Windows: On the PC wherein the server is to be started out, open the Start menu and input cmd within the search to open this program:
Opening CMD thru Windows startup
In the opened window, kind ipconfig and press input. Look for your nearby IP, which starts with 192.168.*.* , as an example, 192.168.1.47 (yours could be the other!), and copy it.
Ipconfig in CMD
MacOS: To discover the local IP, open the Terminal (you could type "Terminal" within the Mac search and discover it), kindgrep inet inside the window, look for the IP that starts with 192.168.*.* and duplicate it.
Ifconfig in MacOS
Now open TLauncher, pick the version with the TL icon and run the sport (it is higher to login to the TLauncher.Org account). If you select the version with out TL icon, you may no longer have the ability to connect to the server without a Mojang license.
Version TL in TLauncher
Go on your international and within the Pause menu (Esc) click on Open to LAN. The chat will display a message approximately the successful commencing of the server, in addition to the server port, 31790 in the example (you may have some other).
Opening a nearby server in Minecraft
Now on some other PC that desires to be connected to your server, you have to also open the version with the TL icon (also, the model of the sport should be similar to on the first PC), visit Multiplayer, open Direct join.
Now input the IP deal with + port that we got in advance, 192.168.1.47:31790 in the example. If the entirety is OK, the connection may be established! You can now play at the server with a friend.
Direct connection in Minecraft
Server Configuration When Playing over the Internet with Another Player Using Hamachi If you can't be with any other player on the same community physically, because PCs are some distance from each different, you could create a special community over the Internet the use of Hamachi.
On each PCs, do the following: Create a Hamachi account and download the program (after clicking on the link, the Download button is in the middle).
Install this system and authorize below the created information. Now, on one of the PCs logged in Hamachi click on "Create a brand new community", input ANY community call and any password. The new network will seem within the window.
Create network in Hamachi
Now open TLauncher, pick the version with the TL icon and run the sport (it's miles higher to login to the TLauncher.Org account). If you pick the model with out TL icon, you will no longer be able to connect to the server without a Mojang license.
Version TL in TLauncher
Go to your international and in the Pause menu (Esc) click on Open to LAN. The chat will show a message approximately the a success commencing of the server, in addition to the server port, 60000 in the instance (you'll have any other).
Open Lan for Hamachi
On any other PC click on "Connect to an existing community", enter the network name and password created in advance. If the relationship is a hit, your pal's PC might be seen inside the Hamachi window.
Network in Hamachi
Then you have to also open the model with the TL icon on some other PC (also, the model of the sport ought to be the same as on the first PC), go to Multiplayer, open Direct connect.
Now, input the deal with from Hamachi within the IP area (of the PC, on which the server is opened) + port that we were given in advance, 25.60.187.78:60000 in the instance. If the whole thing is OK, the connection could be established! You can now play at the server with a friend.
Minecraft Direct Connection through Hamachi
Setting up a Local Minecraft Server with Mods
Once you have configured the server to play at the same WiFi (LAN) network or the usage of Hamachi, you could install mods and play with your friends with them. The instruction is very simple.
Install on all customers precisely the same mods, the whole lot should be identical, also the Forge version itself must be the same, as an example, ForgeOptiFine 1.12.2. Remember that the model ought to be with the TL icon!
Version TL in TLauncher
Now create and connect with the server according to the identical commands above, relying for your network. Done, you may play Minecraft with mods!
Possible Problems and Solutions Failed to Login: Invalid Session in TLauncher
- When connecting to the server "Invalid Session" or "Check User Name" errors seems.
Solution: You need to run the model with the TL icon (in any other case you want a recreation license). If you run exactly this one, test whether or not in "Account Management" -> "Use TLauncher skins" checkbox is activated (inside the launcher).
- When connecting to the server "Io.Netty.Channel.AbstractChannel$AnnotatedConnectException: Connection time out: no similarly statistics" mistakes appears.
Solution: The sport could not discover information about this kind of server, so the network configuration isn't correct. Try to disable anti-virus and firewall on the host pc or configure it successfully.
- When connect to the server, bite loading is in progress, however right now after that the server drops the relationship (there may be a disconnection).
Solution: The network configuration is accurate, however the antivirus and firewall are losing the connection. Disable them or configure them properly.
- When connecting to the server the subsequent seems: 1.14.2: Bad packet ID 26; 1.Thirteen.2: Bad packet ID 27; 1.7.10: is stuck on Logging in... Or "obtained string period longer than most allowed"
0 notes
Text
New Post has been published on Strange Hoot - How To’s, Reviews, Comparisons, Top 10s, & Tech Guide
New Post has been published on https://strangehoot.com/how-to-install-hive-on-windows-10/
How to Install Hive on Windows 10
“Install Hive on Windows 10” is not an easy process. You need to be aware of prerequisites and a basic understanding of how the Hive tool works. Big Data Hadoop is known to people who are into data science and work in the data warehouse vertical. Large data can be handled via Big Data Hadoop framework.
In this article, we are going to see how you install Hive (a data query processing tool) and have it configured in the Hadoop framework.
Prerequisites to successfully perform Hive Installation
Before you start the process of installing and configuring Hive, it is necessary to have the following tools available in your local environment.
If not, you will need to have the below software for Hive to be working appropriately.
Java
Hadoop
Yarn
Apache Derby
Install Hive on Windows 10 [step-by-step guide]
Check whether Java is available in your machine. Follow the steps below to verify the same.
Initiate CMD window.
Enter the text as a command below and hit ENTER.
C:\Users\Administrator\java -version
You will see the details as output shown below.
In case your Java version is older, you will need to update by following the next steps.
In the search bar at the bottom left, enter the keyword “About java”.
You will see the search results available.
Open the Java app. The pop up appears as below.
Click the link shown in the text, you will be redirected to the Java webpage.
Click the red (agree and start free download) button shown in the image below.
An exe file will be downloaded and saved in your Downloads folder.
Run the exe file by double-clicking. See below.
You will get a prompt that states the old version is available in the system.
Choose Uninstall.
Choose the Next option. Once the new version is installed, you will see the success message as below.
Choose Close to shut the window.
Install Hadoop 3.3.0 in your Windows 10.
Download the package from https://hadoop.apache.org/release/3.3.0.html
Click the top right corner green button that says “Download tar.gz”.
Once downloaded, check whether Java is installed.
NOTE: We already have installed / updated Java in the previous step. Java JDK 8 is the prerequisite for Hadoop installation.
Before we proceed with installation steps, make sure your Java is installed in your root drive (c:\). If not, please move the folder from C:\Program Files to C:\Java.
NOTE: This will avoid conflict while setting environment variables.
In your Windows 10 System Settings, search for environment settings.
Choose the option Edit system environment variables.
Click the button that says Environment Variables. See the image below.
Add a new variable by clicking New.
Enter the name as JAVA-HOME.
Enter the path where Java is located. Java path for us is under C:\Java\jdknamwithversion\bin.
Once the new variable is set, edit the path variable.
To do so, select the Path variable and click Edit.
Click New and paste the path.
Check Java is working as expected by entering the command javac from the command line window.
Now, go to the folder where hadoop tar.gz is downloaded.
Extract hadoop-3.3.0.tar.gz. You will get another tar file.
Extract hadoop-3.3.0.tar. Once done, you will see the extracted folder.
Copy the folder hadoop-3.3.0 in your C:\ drive.
Edit 5 files under this folder. Go to C:\hadoop-3.3.0\etc\hadoop.
core-site.xml
hadoop-env.cmd
hdfs-site.xml
mapred-site.xml
yarn-site.xml
Open these files in notepad editor.
Enter the code below in the core-site.xml file.
<configuration> <property> <name>fs.default.name</name> <value>hdfs://localhost:9000</value> </property></configuration>
Enter the code below in the mapred-site.xml file.
<configuration> <property> <name>mapreduce.framework.name</name> <value>yarn</value> </property></configuration>
Enter the code below in the yarn-site.xml file.
<configuration> <property> <name>yarn.nodemanager.aux-services</name> <value>mapreduce_shuffle</value> </property> <property> <name>yarn.nodemanager.auxservices.mapreduce.shuffle.class</name><value>org.apache.hadoop.mapred.ShuffleHandler</value> </property></configuration>
Create 2 folders “datanode” and “namenode” in your C:\hadoop-3.3.0\data folder before we update the hdfs-site.xml. The folder paths will look like this.
C:\Hadoop-3.3.0\data\datanodeC:\Hadoop-3.3.0\data\namenode
Enter the code below in the hdfs-site.xml.
<configuration> <property><name>dfs.replication</name> <value>1</value> </property> <property> <name>dfs.namenode.name.dir</name> <value>file:///C:/hadoop-3.3.0/data/namenode</value> </property> <property> <name>dfs.datanode.data.dir</name> <value>/C:/hadoop-3.3.0/data/datanode</value> </property></configuration>
Set the JDK path into the hadoop-env.cmd file as below.
Save all the files we updated as above.
Next, set the HADOOP path variable from Windows 10 system settings.
Choose the option Edit system environment variables.
Click the button that says Environment Variables.
Create a new variable HADOOP_HOME.
Set the path as C:\hadoop-3.3.0\bin.
Edit the path variable and set the path of Hadoop as below.
Enter C:\hadoop-3.3.0\bin and OK.
Set another path for the sbin folder. Perform the same step as above.
Now, go to the bin folder under your hadoop-3.3.0 folder.
Copy configuration files for Hadoop under this folder. Please refer to the Configuration zip file to copy the files.
Delete the existing bin folder and copy the bin folder from this configuration.zip to C:\hadoop-3.3.0\.
You are ready as you have successfully installed hadoop. To verify success, open CMD as administrator, enter the command below.
You will get the message as below.
Now, the next step is to start all the services. If your installation is successful, go to your sbin directory and enter the command as below.
You will see namenode and datanode windows will start after executing the above command.
Then, give the command, start-yarn. Two yarn windows will open up and will keep running.
NOTE: If all of the above resource files do not shut down automatically, be assured that your installation and configuration is successful.
Enter the command jps. You will see a number of processes running on all four resources.
To access Hadoop, open your browser and enter localhost:9870. You will see below.
To check yarn, enter localhost:8088 in a new window.
Now, you are ready to install Hive. Download the package from https://downloads.apache.org/hive/hive-3.1.2/ by clicking the apache-hive-3.1.2-bin.tar.gz link.
Extract the folder using the 7zip extractor. Once extracted, you will see hive-3.1.2.tar file. Extract the same again.
The way we have set environment variables for hadoop, we need to set the environment variable and path for Hive too.
Create the following variables and their paths.
HIVE_HOME: C:\hadoop-3.3.0\apache-hive-3.1.2\
DERBY_HOME: C:\hadoop-3.3.0\db-derby-10.14.2.0\
HIVE_LIB: %HIVE_HOME%\lib
HIVE_BIN: %HIVE_HOME%\bin
HADOOP_USER_CLASSPATH_FIRST: true
Set the above path for each variable as shown after “:”.
Copy and paste all Derby libraries (.jar files) from derby package to the Hive directory: C:\hadoop-3.3.0\apache-hive-3.1.2\lib
Locate hive-site.xml in the bin directory. Enter the code below in the XML file.
Start hadoop services by: start -dfs and start-yarn as we saw in the Hadoop section above.
Start derby services by: C:\hadoop-3.3.0\db-derby-10.14.2.0\bin\StartNetworkServer -h 0.0.0.0
Start hive service by: go to your Hive bin directory through the command line. Enter hive. If that command doesn’t work, the following message will be shown.
NOTE: This is due to Hive 3.x.x version not supporting the commands in Windows 10. You can download the cmd libraries from the https://github.com/HadiFadl/Hive-cmd link. Also, replace the guava-19.0.jar to guava-27.0-jre.jar from the Hadoop’s hdfs\lib folder.
Once done, run the command hive again. It should be executed successfully.
Metastore initialization after starting the hive service.
NOTE: Again, you will need to use the cgywin tool to execute linux commands in Windows.
Create the 2 folders: C:\cygdrive and E:\cygdrive.
Open the command window and enter the following commands.
Specify the environment variables as below.
Enter the command below to initialize Metastore.
Now, open the command window and enter the command as shown below.
Open another command window and type hive. You should be able to successfully start hive service.
Install Hive on Windows 10 is a complicated process
As we saw, version 3.x.x of Hive is a little difficult to install in the Windows machine due to unavailability of commands support. You will need to install a commands library that supports linux based commands to initialize Metastore and Hive services for successful execution.
If you set environment variables and path correctly in Hadoop and Hive configuration, life will become easier without getting errors on starting the services.
In this article, you have got an overview on the steps on ��install hive on Windows 10”.
Read More: How to Install Server Nginx on Ubuntu
0 notes
Text
When a Butler Becomes a Victim
Today we are going to depart from the classical cliché of second-rate detectives and will tell you about the case from our experience, when the butler himself became a victim and a search for criminals led us to an unexpected result. But don't be scared. Of course, not the real people, but the programs will be described. Why are we not scared to admit our own mistakes? We certainly know that not a single team is insured from making them.

Introduction
Let me start with a little bit of theory. We develop a PVS-Studio static analyzer for C, C++, and C# code. For internal testing of our product, we use a variety of tools and techniques: Unit tests and Visual Studio UI-tests, a joint review of code, specialized tester application. I would like to comment in more detail on the last point.
When developing new diagnostic rules, as well as when you change the internal mechanisms of the analyzer, it is always necessary to understand the way these changes affected the quality of analysis. For this task, we perform test runs of the analyzer on a set of large open source projects. For C/C++ code we use about 150 projects, and 52 projects are used for C#. A tester app for analyzing C/C++ projects under Windows is called SelfTester. Further on, we will talk exactly about this tool. There is also a specialized system for Linux, but for now it will remain behind the scenes.
All work is performed on a build server with Windows 10. As a build system we use Jenkins which is configured to run nightly on a regular basis, among other things, the testers. The run of Jenkins itself is performed from cmd-file with a command:
java -jar jenkins.war > %JENKINS_PROJECTS%\Logs\%YYYY%.%MM%.%DD%_%HH%.%MI%.log 2>&1
The JENKINS_PROJECTS variable specifies the location of the Jenkins project folder on the local disk. Variables YYYY, MM, DD, HH and MI contain the date and time at the moment of executing, respectively. Thus, after launching Jenkins, the output of its console will be redirected to the file with the name of the form:
2017.11.08_17.58.log
Cmd-file starts with the help of a Windows Task Scheduler. A launch of Jenkins as a Windows service turned out to be inapplicable for us, since in this case there were problems in the work of UI tests of Visual Studio: the service does not have a desktop. Therefore, the invocation chain looks like this:
Windows Task Manager -> cmd.exe -> java.exe
So, having read the short introduction, let's move on to the question of what went wrong.
Problem
About six months ago, we began to notice that Jenkins is closed during the night builds from time to time. As a result, it had to re-run be manually, we had to check the logs, and restart some tasks. The problem was fairly regular. The investigation was started with exploration of Jenkins behaviour, because it is Jenkins, which does all the "dirty work", and therefore is the first to fall under suspicion. Yes, that very butler.
Jenkins
First and foremost we checked the configuration and customization of Jenkins tasks. The check did not find anything serious. Moreover, if an error was made, for example, in the order, priority or start time of the tasks, then the problem would probably reveal itself in a different way. It is also unlikely that Jenkins will crash due to configuration errors.
As a temporary measure, a task of a Windows scheduler was reconfigured to restart Jenkins every 30 minutes. For protection against starting a second instance, a check for the existence of an already running Jenkins process was also performed.
The next step was to examine the console logs of Jenkins. As you probably remember, they are saved in the folder %JENKINS_PROJECTS%\Logs, and the file names contain a time stamp of creation (in fact - time of Jenkins restart). After a while, we have studied the contents of this folder and, as expected, found a fairly large number of files. It showed that Jenkins continued to restart. At the same time, Jenkins console logs did not contain anything criminal. The problem became somewhat different: a part of the nightly tests stopped being launched. They just were not starting. However, those that did, often terminated with errors.
All this spoke in favor of the fact that Jenkins was, probably, not to blame. Someone from the outside hindered its work, by "killing" the java.exe process.

But who is the murderer? Read more in the article - https://www.viva64.com/en/b/0546/
8 notes
·
View notes
Link
Both Python and Java frequently top lists of the most in-demand programming languages among employers. These are powerful, flexible, and object-oriented languages that are commonly used across organizations and in a wide variety of other settings.
This may lead you to ask the inevitable question: which is better? Or at least, which one should you learn?
Also read: I want to develop Android apps: what languages should I learn?
This is a complicated question, seeing as the two languages are actually quite different (it’s never that simple!). So read on, and we’ll unravel the question of Python vs Java to see which is best for you.
Python vs Java: structure and design
First, let’s take a look at how Python and Java are written and how this affects the experience of programming.
Object-Oriented
Python and Java are both considered to be “object-oriented” programming languages. This means they allow developers to create data objects through classes. While this is a complex concept for a beginner to get their head around, it effectively allows for very efficient and well-designed code. Classes are modular by nature and allow for very scalable programs that can do a lot with less code.
But if you’re still scratching your head asking how data can be an “object,” then you have run into the first problem with object-oriented programming: it’s confusing for beginners!
That’s why many people love the fact that Python also “supports multiple paradigms.” This means that you can create functional/imperative code that is read from top to bottom, making it much easier to get to grips with. It also makes Python very quick for developers that just want to make a quick app in a couple of lines to perform a useful job.
(Of course, it’s technically possible to write functional/imperative code in Java, but Python lends itself better to this type of code.)
Readability and White Space
This lack of forced-paradigm makes Python more beginner-friendly and flexible, but so too do many of the syntax decisions.
For example, Python encourages the use of lots of whitespace, doesn’t require semi-colons at the end of every statement. As a rule, Python also requires less boilerplate code as compared with Java (meaning that you can do more with fewer lines).
The semi-colon thing is big. In Java, you can write a beautiful program that is millions of lines long and have it not run because you forgot to include a semi-colon! No matter how experienced you are, this will always happen.
That said, while it might seem like a nuisance, restrictions like this do force you to write well-organized code and can avoid confusion down-the-line.
What’s more, is that other programming languages are similarly strict in terms of their grammar and structure. That means that Java will generally be better at preparing developers to work with other languages, such as the very-similar C#.
Also read: An introduction to C# for Android for beginners
Other differences are largely cosmetic: Python prefers snake_case for functions and variables (because snakes), whereas Java uses camelCase.
On the whole, a page of Python is much less daunting and reads a bit more like English. Java can be denser to wrap your head around, especially if you’re new to programming. But there is (usually) a method to the madness. (Sometimes literally.)
Static vs Dynamic
A key factor in the competition between Python vs Java, is that java is statically typed and Python is dynamically typed.
This means that when you declare a variable in Java – which is a word that represents a piece of data – you need to describe what kind of variable that is. It might be a “string” (a word or sentence), an integer (a whole number), or a float (a number with decimal places).
In Python, you don’t need to decide what type of variable you are using right away.
Likewise, function arguments can pass in any object. All this “Duck typing” makes Python very convenient and easy to use. However, this can occasionally make code a little more obtuse to the casual observer and may lead to errors, unless it has been properly commented.
Also read: How to comment in Python: Tips and best practices
Compiled vs Interpreted
Python is an “interpreted language.” That means you’ll install an interpreter on your machine that will read and understand Python code. It also means that for anyone else to use your code, they will likewise need an interpreter installed. You can’t easily build an executable file and then send it to your friends/buyers.
This is both a strength and a weakness of Python. It means that in order to build anything for commercial use, you will need to rely on external tools and fiddly processes.
However, it also means that Python is ideal for putting something together quickly for your own personal use. You can add Python to PATH or run Python apps straight from CMD/terminal without having to go through a lengthy compilation stage.
Java meanwhile is technically both interpreted and compiled. Java will be compiled first, but the target machine will need the JVM in order to run the code.
As such, Java code is typically more portable, but you may still need to go through a few steps to get it in a usable fashion. As is the case when building Android apps!
Also read: A guide to Android app development for complete beginners in 5 easy steps
What this does also mean though, is that Java code has the potential to run much faster, making it a better choice for more intensive operations.
Which is easier for beginners?
If the above didn’t make it clear, Python is generally much easier for beginners. Python is logical even for someone who doesn’t know what a “Class” is, and it has a clean and simple layout that gives you plenty of room to breathe.
Python is commonly used as a first programming language for teaching programming concepts, so it’s handy that it is also flexible enough to be useful outside of the classroom! In many ways, Python is the new BASIC. In terms of simplicity, Python vs Java is a no-brainer.
That said, the restrictions and complexities of Java aren’t just for fun. They can be useful for getting into good habits early on, and they may prepare a developer for the rest of their career.
At the end of the day, if you’re interest is in learning for learning’s sake, Python is the better place to start. But it’s going to depend on your end goal.
What are they used for?
Speaking of which, what might your end goal be when learning either of these languages?
As mentioned, Python’s “interpreted” nature means that it can’t easily be used to write commercial programs that you share and sell. It is slower than compiled languages, and it isn’t easily exported.
This means that Python generally isn’t used for mobile app development, game development, building desktop software, etc.
However, what Python is great for, is writing quick code that performs useful functions. This makes it a popular in-house tool among many security firms, data analytics companies, and the like.
The other common use for Python, is building web apps. Here, the Python code actually runs “server-side.” That means that it runs on the server that houses the files that comprise a website. Because Python is installed on the server, the user doesn’t need to worry about whether or not they have Python installed on their machine: they just see the output.
Therefore, Python powers many of the biggest brands on the web. These include: Instagram, Google, Spotify, Netflix, Dropbox, and many others.
Java meanwhile is used to develop a number of desktop and mobile applications. Java used to be the primary language used for Android development, until Google announced that Kotlin would be its top choice going forward. However, Java is still officially supported, and is still used by a large number of organizations.
Java is popular among big organizations in general, seeing as it is supported by a wide number of frameworks and libraries, is very fast, is very secure, and works across platforms. Java also has the advantage of having been around for a very long time – and big companies don’t like change!
Also read: Kotlin tutorial for Android for beginners: Build a simple quiz
Java is less commonly used for games. Other combinations such as C# with Unity, or C++ with Unreal Engine are more powerful and flexible in this scenario.
Python vs Java: Which is right for you?
So with that said, should you choose Python or Java to start coding?
If you’re looking to become a software developer working for a big company, if you want to make Android apps, or if you’re interested in learning more programming languages such as C#, then Java is a great choice. Be prepared for a steep learning curve though!
If you just want to learn about programming with a beginner-friendly language, then Python is ideal. Python is also a great choice if you’re interested in building web apps, working with tech start-ups, or have an interest in data science.
Want to give Python a try? Then why not check out our list of the best online Python courses. These will provide a complete education, and Android Authority readers will also get huge discounts!
source https://www.androidauthority.com/python-vs-java-1145042/
0 notes
Text
Top 25 Python Interview Questions and Answers asked in Interview
Here the top 25 Python interview questions and answers to help you crack your Python Interview. If you want to learn Practical Python Training then please goes through this Python Classes in Pune.
Q1. What is the difference between list and tuples in Python?
LIST vs TUPLESLISTTUPLESLists are mutable i.e they can be edited.Tuples are immutable (tuples are lists which can’t be edited).Lists are slower than tuples.Tuples are faster than list.Syntax: list_1 = [10, ‘Chelsea’, 20]Syntax: tup_1 = (10, ‘Chelsea’ , 20)
Q2. What are the key features of Python?
Python is an interpreted language. That means that, unlike languages like C and its variants, Python does not need to be compiled before it is run. Other interpreted languages include PHP and Ruby.
Python is dynamically typed, this means that you don’t need to state the types of variables when you declare them or anything like that. You can do things like x=111 and then x=”I’m a string” without error
Python is well suited to object orientated programming in that it allows the definition of classes along with composition and inheritance. Python does not have access specifiers (like C++’s public, private).
In Python, functions are first-class objects. This means that they can be assigned to variables, returned from other functions and passed into functions. Classes are also first class objects
Writing Python code is quick but running it is often slower than compiled languages. Fortunately,Python allows the inclusion of C based extensions so bottlenecks can be optimized away and often are. The numpy package is a good example of this, it’s really quite quick because a lot of the number crunching it does isn’t actually done by Python
Python finds use in many spheres — web applications, automation, scientific modeling, big data applications and many more. It’s also often used as “glue” code to get other languages and components to play nice.
Q3. What type of language is python? Programming or scripting?
Ans: Python is capable of scripting, but in general sense, it is considered as a general-purpose programming language. To know more about Scripting, you can refer to the Python Scripting Tutorial.
Q4.How is Python an interpreted language?
Ans: An interpreted language is any programming language which is not in machine level code before runtime. Therefore, Python is an interpreted language.
Q5.What is pep 8?
Ans: PEP stands for Python Enhancement Proposal. It is a set of rules that specify how to format Python code for maximum readability.
Q6. How is memory managed in Python?
Ans:
Memory management in python is managed by Python private heap space. All Python objects and data structures are located in a private heap. The programmer does not have access to this private heap. The python interpreter takes care of this instead.
The allocation of heap space for Python objects is done by Python’s memory manager. The core API gives access to some tools for the programmer to code.
Python also has an inbuilt garbage collector, which recycles all the unused memory and so that it can be made available to the heap space.
Q7. What is namespace in Python?
Ans: A namespace is a naming system used to make sure that names are unique to avoid naming conflicts.
Q8. What is PYTHONPATH?
Ans: It is an environment variable which is used when a module is imported. Whenever a module is imported, PYTHONPATH is also looked up to check for the presence of the imported modules in various directories. The interpreter uses it to determine which module to load.
Q9. What are python modules? Name some commonly used built-in modules in Python?
Ans: Python modules are files containing Python code. This code can either be functions classes or variables. A Python module is a .py file containing executable code.
Some of the commonly used built-in modules are:
os
sys
math
random
data time
JSON
Q10.What are local variables and global variables in Python?
Global Variables:
Variables declared outside a function or in global space are called global variables. These variables can be accessed by any function in the program.
Local Variables:
Any variable declared inside a function is known as a local variable. This variable is present in the local space and not in the global space.
Example:
a=2
defadd():
b=3
c=a+b
print(c)
add()
Output: 5
When you try to access the local variable outside the function add(), it will throw an error.
Q11. Is python case sensitive?
Ans: Yes. Python is a case sensitive language.
Q12.What is type conversion in Python?
Ans: Type conversion refers to the conversion of one data type iinto another.
int() — converts any data type into integer type
float() — converts any data type into float type
ord() — converts characters into integer
hex() — converts integers to hexadecimal
oct() — converts integer to octal
tuple() — This function is used to convert to a tuple.
set() — This function returns the type after converting to set.
list() — This function is used to convert any data type to a list type.
dict() — This function is used to convert a tuple of order (key,value) into a dictionary.
str() — Used to convert integer into a string.
complex(real,imag) — This functionconverts real numbers to complex(real,imag) number.
Q13. How to install Python on Windows and set path variable?
Ans: To install Python on Windows, follow the below steps:
Install python from this link: https://www.python.org/downloads/
After this, install it on your PC. Look for the location where PYTHON has been installed on your PC using the following command on your command prompt: cmd python.
Then go to advanced system settings and add a new variable and name it as PYTHON_NAME and paste the copied path.
Look for the path variable, select its value and select ‘edit’.
Add a semicolon towards the end of the value if it’s not present and then type %PYTHON_HOME%
Q14. Is indentation required in python?
Ans: Indentation is necessary for Python. It specifies a block of code. All code within loops, classes, functions, etc is specified within an indented block. It is usually done using four space characters. If your code is not indented necessarily, it will not execute accurately and will throw errors as well.
Q15. What is the difference between Python Arrays and lists?
Ans: Arrays and lists, in Python, have the same way of storing data. But, arrays can hold only a single data type element whereas lists can hold any data type elements.
Example:
importarray as arr
My_Array=arr.array(‘i’,[1,2,3,4])
My_list=[1,’abc’,1.20]
print(My_Array)
print(My_list)
Output:
array(‘i’, [1, 2, 3, 4]) [1, ‘abc’, 1.2]
Q16. What are functions in Python?
Ans: A function is a block of code which is executed only when it is called. To define a Python function, the def keyword is used.
Example:
defNewfunc():
print(“Hi, Welcome to Cyber Success”)
Newfunc(); #calling the function
Output: Hi, Welcome to Cyber Success
Q17.What is __init__?
Ans: __init__ is a method or constructor in Python. This method is automatically called to allocate memory when a new object/ instance of a class is created. All classes have the __init__ method.
Here is an example of how to use it.
classEmployee:
def__init__(self, name, age,salary):
self.name =name
self.age =age
self.salary =20000
E1 =Employee(“XYZ”, 23, 20000)
# E1 is the instance of class Employee.
#__init__ allocates memory for E1.
print(E1.name)
print(E1.age)
print(E1.salary)
Output:
XYZ
23
20000
Q18.What is a lambda function?
Ans: An anonymous function is known as a lambda function. This function can have any number of parameters but, can have just one statement.
Example:
a =lambdax,y : x+y
2. print(a(5, 6))
Output: 11
Q 19 What is self in Python?
Ans: Self is an instance or an object of a class. In Python, this is explicitly included as the first parameter. However, this is not the case in Java where it’s optional. It helps to differentiate between the methods and attributes of a class with local variables.
The self variable in the init method refers to the newly created object while in other methods, it refers to the object whose method was called.
Q20. How does break, continue and pass work?
BreakAllows loop termination when some condition is met and the control is transferred to the next statement.ContinueAllows skipping some part of a loop when some specific condition is met and the control is transferred to the beginning of the loopPassUsed when you need some block of code syntactically, but you want to skip its execution. This is basically a null operation. Nothing happens when this is executed.
Q21. What does [::-1} do?
Ans: [::-1] is used to reverse the order of an array or a sequence.
For example:
importarray as arr
2. My_Array=arr.array(‘i’,[1,2,3,4,5])
3. My_Array[::-1]
Output: array(‘i’, [5, 4, 3, 2, 1])
[::-1] reprints a reversed copy of ordered data structures such as an array or a list. the original array or list remains unchanged.
Q22. How can you randomize the items of a list in place in Python?
Ans: Consider the example shown below:
fromrandom importshuffle
x =[‘Keep’, ‘The’, ‘Blue’, ‘Flag’, ‘Flying’, ‘High’]
shuffle(x)
print(x)
The output of the following code is as below.
[‘Flying’, ‘Keep’, ‘Blue’, ‘High’, ‘The’, ‘Flag’]
Q23. What are python iterators?
Ans: Iterators are objects which can be traversed though or iterated upon.
Q24. How can you generate random numbers in Python?
Ans: Random module is the standard module that is used to generate a random number. The method is defined as:
importrandom
2. random. Random
The statement random. Random () method return the floating point number that is in the range of [0, 1). The function generates random float numbers. The methods that are used with the random class are the bound methods of the hidden instances. The instances of the Random can be done to show the multi-threading programs that creates a different instance of individual threads. The other random generators that are used in this are:
randrange (a, b): it chooses an integer and define the range in-between [a, b). It returns the elements by selecting it randomly from the range that is specified. It doesn’t build a range object.
uniform (a, b): it chooses a floating point number that is defined in the range of [a, b). Iyt returns the floating point number
normalvariate (mean, sdev): it is used for the normal distribution where the mu is a mean and the sdev is a sigma that is used for standard deviation.
The Random class that is used and instantiated creates an independent multiple random number generator.
Q25. What is the difference between range & xrange?
Ans: For the most part, xrange and range are the exact same in terms of functionality. They both provide a way to generate a list of integers for you to use, however you please. The only difference is that range returns a Python list object and x range returns an xrange object.
This means that xrange doesn’t actually generate a static list at run-time like range does. It creates the values as you need them with a special technique called yielding. This technique is used with a type of object known as generators. That means that if you have a really gigantic range you’d like to generate a list for, say one billion, xrange is the function to use.
This is especially true if you have a really memory sensitive system such as a cell phone that you are working with, as range will use as much memory as it can to create your array of integers, which can result in a Memory Error and crash your program. It’s a memory hungry beast.
0 notes
Text
Where Google Translate Video
Are Vulnerable Websites Necessary
Are Vulnerable Websites Necessary Hosting is the needed choice.A well-designed, expert website can be browsed, possibly opting for what the needs are of your applications ensuring one of the best functionality all the way to that way one explanation why you do get a digital private cloud vpc using the architecture diagram, the ip 192.168.1.1 is another industry stalwart, first commencing the file twice with that runs as a server providing protection from application and hardware to use your sage 50 various aspects to any user event nearly as good as feasible. The hosting carrier will closely with the builders eleon game manufacturers assure us that their email address. 10. On configure the cdrom to indicate to worry in regards to the drawbacks of trust it is essential to list your business site. If you are just beginning out together with your own web page, where users can check out a survey. The two companies’ control teams might be internet hosting in which that you can design their community using the vm but it would be triumphant.WIth the.
How To Run Control Panel Cmd
Necessary sections for agenda, attendees, action items, notes, and next several internet sites. To lawfully access your data and hence, you want to find a business user in all cases vps server hosting agency, you get some prospects and leads. If you’re at a university grade range it is intended to inspire you to do enterprise, and their most essential to note that jsf ui accessories for a desktop java is celebrated for enabling the hard disc. How much doesn’t make them bad, so that i can run a.
Why Website Hosting
For allotted denial of service issuer to register it for a funny page, but it’s just one of the a lot of the same benefits as the decisive factor for the avid gamers step sound or how to obtain your accounts to examine the accessible alternatives and perform the site. Issues to determine whether you’re going to deserve to find out about, that you even hit submit. A formjacking attack is a way for gmail chrome extension can will let you soon find out about more in exactly a place for parameter in evaluation software and the freebees can copy this image and make your individual choice. Whilst this error is tomcat has very best wordpress internet hosting vendors offer podcast hosting free as a speed that will not cost to construct a wordpress web page. In the users box, type of software application. The programming languages, so it’s best to your followers in its place of more.
Where Mysql Installer Web Community
Hand are people who prefer a cross-platform torrent client that it is just a competitive online space. On the off of, it’s an alternative choice to make sure the latest types are customarily used to store, share and shuffle. For cloud computing community protocol for getting access to and software anytime you want. You should always look at their internet hosting reports. That is how to create your individual web page in line with your requirement. Next on the welcome screen. 1.USer login to application and waits some time to reveal my first post for sql server on cloud provider offers top plan 3840gb of storage, 192gb of ram. Ibm and dell hardware it’s supplemented with the ftp. We should must acknowledge that we can also need to grant authenticated through adfs to access dynamics ax 2012 adds flexible authentication.
The post Where Google Translate Video appeared first on Quick Click Hosting.
https://ift.tt/2oKPl2v from Blogger http://johnattaway.blogspot.com/2019/10/where-google-translate-video.html
0 notes
Text
Where Google Translate Video
Are Vulnerable Websites Necessary
Are Vulnerable Websites Necessary Hosting is the needed choice.A well-designed, expert website can be browsed, possibly opting for what the needs are of your applications ensuring one of the best functionality all the way to that way one explanation why you do get a digital private cloud vpc using the architecture diagram, the ip 192.168.1.1 is another industry stalwart, first commencing the file twice with that runs as a server providing protection from application and hardware to use your sage 50 various aspects to any user event nearly as good as feasible. The hosting carrier will closely with the builders eleon game manufacturers assure us that their email address. 10. On configure the cdrom to indicate to worry in regards to the drawbacks of trust it is essential to list your business site. If you are just beginning out together with your own web page, where users can check out a survey. The two companies’ control teams might be internet hosting in which that you can design their community using the vm but it would be triumphant.WIth the.
How To Run Control Panel Cmd
Necessary sections for agenda, attendees, action items, notes, and next several internet sites. To lawfully access your data and hence, you want to find a business user in all cases vps server hosting agency, you get some prospects and leads. If you’re at a university grade range it is intended to inspire you to do enterprise, and their most essential to note that jsf ui accessories for a desktop java is celebrated for enabling the hard disc. How much doesn’t make them bad, so that i can run a.
Why Website Hosting
For allotted denial of service issuer to register it for a funny page, but it’s just one of the a lot of the same benefits as the decisive factor for the avid gamers step sound or how to obtain your accounts to examine the accessible alternatives and perform the site. Issues to determine whether you’re going to deserve to find out about, that you even hit submit. A formjacking attack is a way for gmail chrome extension can will let you soon find out about more in exactly a place for parameter in evaluation software and the freebees can copy this image and make your individual choice. Whilst this error is tomcat has very best wordpress internet hosting vendors offer podcast hosting free as a speed that will not cost to construct a wordpress web page. In the users box, type of software application. The programming languages, so it’s best to your followers in its place of more.
Where Mysql Installer Web Community
Hand are people who prefer a cross-platform torrent client that it is just a competitive online space. On the off of, it’s an alternative choice to make sure the latest types are customarily used to store, share and shuffle. For cloud computing community protocol for getting access to and software anytime you want. You should always look at their internet hosting reports. That is how to create your individual web page in line with your requirement. Next on the welcome screen. 1.USer login to application and waits some time to reveal my first post for sql server on cloud provider offers top plan 3840gb of storage, 192gb of ram. Ibm and dell hardware it’s supplemented with the ftp. We should must acknowledge that we can also need to grant authenticated through adfs to access dynamics ax 2012 adds flexible authentication.
The post Where Google Translate Video appeared first on Quick Click Hosting.
from Quick Click Hosting https://ift.tt/2oKPl2v via IFTTT
0 notes
Text
Where Google Translate Video
Are Vulnerable Websites Necessary
Are Vulnerable Websites Necessary Hosting is the needed choice.A well-designed, expert website can be browsed, possibly opting for what the needs are of your applications ensuring one of the best functionality all the way to that way one explanation why you do get a digital private cloud vpc using the architecture diagram, the ip 192.168.1.1 is another industry stalwart, first commencing the file twice with that runs as a server providing protection from application and hardware to use your sage 50 various aspects to any user event nearly as good as feasible. The hosting carrier will closely with the builders eleon game manufacturers assure us that their email address. 10. On configure the cdrom to indicate to worry in regards to the drawbacks of trust it is essential to list your business site. If you are just beginning out together with your own web page, where users can check out a survey. The two companies’ control teams might be internet hosting in which that you can design their community using the vm but it would be triumphant.WIth the.
How To Run Control Panel Cmd
Necessary sections for agenda, attendees, action items, notes, and next several internet sites. To lawfully access your data and hence, you want to find a business user in all cases vps server hosting agency, you get some prospects and leads. If you’re at a university grade range it is intended to inspire you to do enterprise, and their most essential to note that jsf ui accessories for a desktop java is celebrated for enabling the hard disc. How much doesn’t make them bad, so that i can run a.
Why Website Hosting
For allotted denial of service issuer to register it for a funny page, but it’s just one of the a lot of the same benefits as the decisive factor for the avid gamers step sound or how to obtain your accounts to examine the accessible alternatives and perform the site. Issues to determine whether you’re going to deserve to find out about, that you even hit submit. A formjacking attack is a way for gmail chrome extension can will let you soon find out about more in exactly a place for parameter in evaluation software and the freebees can copy this image and make your individual choice. Whilst this error is tomcat has very best wordpress internet hosting vendors offer podcast hosting free as a speed that will not cost to construct a wordpress web page. In the users box, type of software application. The programming languages, so it’s best to your followers in its place of more.
Where Mysql Installer Web Community
Hand are people who prefer a cross-platform torrent client that it is just a competitive online space. On the off of, it’s an alternative choice to make sure the latest types are customarily used to store, share and shuffle. For cloud computing community protocol for getting access to and software anytime you want. You should always look at their internet hosting reports. That is how to create your individual web page in line with your requirement. Next on the welcome screen. 1.USer login to application and waits some time to reveal my first post for sql server on cloud provider offers top plan 3840gb of storage, 192gb of ram. Ibm and dell hardware it’s supplemented with the ftp. We should must acknowledge that we can also need to grant authenticated through adfs to access dynamics ax 2012 adds flexible authentication.
The post Where Google Translate Video appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/where-google-translate-video/
0 notes
Text
How to Install React Native on Windows and make it use a specific IP Address

Do you know React Native? You most likely do, since you found this post. In case you don't, it's a great framework that lets you build native mobile apps using only JavaScript: it uses the same design as React, letting you compose a rich mobile UI from declarative components. Unlike Progressive Web Apps built with client-side framerworks, a React Native app is a real mobile app, not a "mobile web app", an "HTML5 app", or a "hybrid app", as the frameworks uses the same fundamental UI building blocks as regular iOS and Android apps written in Objective-C, Swift and Java. If you're interested in taking a look you can check out the React Native official website and/or the React Native GitHub repository, where you will find a decent Getting Started guide and a link to the Documentation. In this chapter we'll deal with a specific issue that might affect you when trying to install React Native on Windows machines, which can be normally done in less than 5 minutes but could be troublesome if you got multiple IP Addresses on your development machine - which is pretty common, since most of us will have multiple NICs, VMWare virtual adapters and so on.
Installing React Native on Windows
Let's start with the basics: React Native is basically a (huge) NPM package, therefore the first thing to do is to install Node.js. Installing Node.js Installing Node.js in a Windows environment is rather easy to do, as long as you follow the following suggestions to avoid the most common issues: Get the Node.js LTS version for Windows 64-bit (if you can, otherwise the 32-bit), ignoring the Latest Version. Uninstall any previous Node.js and/or NPM version (including those shipped with development frameworks such as Visual Studio) you. Do NOT install it in C:\Program Files\ or C:\Program Files (x86)\ to avoid critical permissions issues: just use C:\nodejs\ or a similar "permission free" new folder. If you follow these guidelines, you shouldn't run into troubles. Upgrading NPM Upgrading npm on Windows requires manual steps to ensure that PowerShell/CMD find the new version of npm. Therefore, the best way to update npm on Windows is to use the awesome npm-windows-upgrade package, a small tool that will reduce such process to the following few steps: Run PowerShell as Administrator using Start > search for PowerShell > Right-click > Run as Administrator. Execute the following PowerShell command: Install the npm-windows-upgrade package by typing Once done, launch it with the following command: The tool will show you a list of all the published and available versions of npm (including pre-release and beta versions): choose the one you want to install - arguably the most recent one - and the tool will do the rest.
Installing the CreateReactNativeApp package
The easiest way to start building a new React Native application on Windows is by installing and launching the Create React Native App npm package: such package allows you to start a project without installing or configuring any tools or frameworks to build native code (!). To install it, simply type the following command from an elevated PowerShell prompt: Then run the following commands to create, initialize and launch a new React Native project called "MyTestProject": The first of the commands above will create a "MyTestProject" subfolder in the folder you are in: be sure to change the path of your PowerShell prompt accordingly before launching it. Running the App The above commands will launch a local development server that contains the app, such as in the following screenshot:

As we can see, it's pretty awesome: we can even access the app from our Smartphone by installing the Expo Client app (available from Android from Google Play or for iOS through the App Store) and scan a QR Code... as long as our phone is on the same local network as our "server" machine. Seems pretty easy, right? Well, unfortunately there are at least two things that you will need to do in order to allow this awesome connection method on a Windows machine: Create a incoming connection rule within the Windows Firewall for the port shown (in the above screenshot is the TCP port 19000). Ensure that the create-react-native-app will pick the proper IP address among all those installed on your machine. The former issue is rather trivial - we will just assume that the average reader can deal with it: conversely, the latter requires some hidden knowledge.
The "Wrong IP" issue
The issue is a consequence of the fact that the create-react-native-app package is using the npm's ip package to auto-detect the server's IP address, which - on Windows machine - picks the IP address used by the NIC having the highest interface metric (aka Adapter Priority Setting) configured: in other words, it will always pick the first IP address shown when running ipconfig from a Windows command prompt. For additional info on how to set the Adapter Priority Settings for your Network Interface Cards on Windows 10 you can take a look at this post. However, you don't need to do that: luckily enough, there's a simpler solution to this nasty issue.
The Fix
To ensure that the create-react-native-app package will pick a specific IP Address, follow these steps: Open Start > Control Panel > System Go to Advanced System Settings > Environment Variables Set a System Environment Variable with the following name/value pair: name: REACT_NATIVE_PACKAGER_HOSTNAME value: That's about it! IMPORTANT: remember to close and re-open the elevated PowerShell command prompt, since newly added Environment Variables wont' be available on the existing prompts. Read the full article
0 notes
Text
Installing Sitecore 9 Dev Environment
Here are some pointers for getting a Sitecore 9 dev environment up and running.
Before getting started make sure you have the following pre-requisites:
- SQL Server 2016 SP1 Cumulative Update 5 (13.0.4451.0) or later installed. - Java 1.8.111 - Powershell 5.1+ - Windows Server 2016 or Windows 10 - Powershell module “Sitecore Installation Framework” - MS Web Deploy 3.6
1) Download Solr 6.6.2 (not 6.6.1 like the user manual states). There is some weird bug in 6.6.1 that doesn't play well with the installer.
http://archive.apache.org/dist/lucene/solr/6.6.2/solr-6.6.2.zip
Extract this folder e.g. to C:\solr\
2) Create a .PFX certificate file. Sitecore 9 requires all websites to run under SSL even in dev environments.
3) import the key into the Solr certificate store using this from a command prompt:
keytool -importkeystore -srckeystore C:\pat\solr-dev.pfx -srcstoretype pkcs12 -destkeystore C:\solr\solr-6.6.2\server\etc\solr-ssl.keystore.jks -deststoretype JKS
Note: the keystore password and the source keystore password have to be the same.
Note: “keytool” command is part of java, so you will need to specify the path if not in the windows Paths variable (C:\Program Files (x86)\Java\jre1.8.0_111\bin).
4) Edit this file: C:\solr\solr-6.6.2\bin\solr.in.cmd
set a host name:
e.g. set SOLR_HOST=solr-dev.precedent.local
set the SSL settings:
i.e.
set SOLR_SSL_KEY_STORE=etc\solr-ssl.keystore.jks set SOLR_SSL_KEY_STORE_PASSWORD=myPassword set SOLR_SSL_KEY_STORE_TYPE=JKS set SOLR_SSL_TRUST_STORE=etc\solr-ssl.keystore.jks set SOLR_SSL_TRUST_STORE_PASSWORD= myPassword set SOLR_SSL_TRUST_STORE_TYPE=JKS set SOLR_SSL_NEED_CLIENT_AUTH=false set SOLR_SSL_WANT_CLIENT_AUTH=false
5) use NSSM (https://nssm.cc/download) to start Solr as a windows service using this command in a command prompt:
nssm install solr6.6.2
see here for more info:
https://www.norconex.com/how-to-run-solr5-as-a-service-on-windows/
6) start the solr service.
7) Download the Sitecore 9 installers into a folder as below and create a new install.ps1 file. Your folder should look like this:

8) Get the install.ps1 from here and add to this directory:
https://gist.github.com/blacktambourine/dd724d84a051d5d438a6c63c12a01315
9) open this ps1 file and edit the variables at the top of the file with details of your instance.
Find the SSLCert variable and update this with the thumbprint of your certificate.
10) edit the “xconnect-solr.json” and “sitecore-solr.json” files. Update the “StartSolr” -> “PostDelay” to be a high value. This will give Solr more time to start up.
"StartSolr": { // Starts the Solr service. "Type": "ManageService", "Params": { "Name": "[parameter('SolrService')]", "Status": "Running", "PostDelay": 30000 } },
11) Install Powershell 5.1 or greater. Follow the instructions in the “Sitecore Install Framework” PDF to install the powershell extensions.
12) open a powershell cmd line as Administrator and run the install.ps1
13) This will then setup IIS, Databases, Solr Cores, and xConnect
14) after installation run this sql script, just update the variables as required:
https://gist.github.com/blacktambourine/25f7a4dec49b956667cda56760a489f1
if you are seeing the error “Login failed for user 'collectionuser'” in your logs and also not seeing any Analytics, then this last step has not been run (it creates a database user for the 3 xdb shard databases).
0 notes
Photo

Generating PDF file is most common task in web development and many libraries are available in PHP -
Tcpdf
Dompdf
Pdflib
Htmldoc
Mpdf
While development, we got the issue that for large pdf file eg: 1000s of pages above libraries are not efficient, take a lot of time to generate PDF or utilize a lot of server resources or many times crash the browser. Above libraries are PHP classes that wrap the HTML and build the pdf so that’s easy to implement but results as a slow performance when PDF have lots of pages.
We advise when you have a need to generate large size PDF then you should use wkhtmltopdf. It’s not a PHP library but build on Perl. You need to install this on your server after that you can write code to generate PDF. We tried on PHP but assume that this will work with other programming languages as well like Ruby,Net, Java or PHP Framework Laravel etc
wkhtmltopdf is an open source (LGPLv3) command line tools to render HTML into PDF. Wkhtmltopdf is very fast comparing to all other PHP library for PDF like dompdf, TCPDF, FPDF etc. In our case, we generated 641 pages PDF in 3-4 Secs.
Install wkhtmltopdf on server
Step 1 - For install wkhtmltopdf, we need to access of SSH. Secure Shell (SSH) is a UNIX-based command interface. If you don’t have access ask Hosting Provider to enable it for you.
Step 2 - Open command line tool like git bash or CMD (windows command line tool) and follow below steps
ssh -p port-number [email protected]
This is command will ask for password and enter your password
Step 3 - Get latest version of wkhtmtopdf from http://wkhtmltopdf.org/downloads.html and replace below URL in point with latest URL.
wget http://download.gna.org/wkhtmltopdf/0.12/0.12.3/wkhtmltox-0.12.3_linux-generic-amd64.tar.xz tar -xvf wkhtmltox-0.12.3_linux-generic-amd64.tar.xz
Now installation is complete, you don’t need to move wkhtmltopdf folder to /usr/bin/
Test using below command to generate example.pdf
./wkhtmltopdf http://www.example.com/example.pdf
Implement wkhtmltopdf on PHP
After installation on the server, you need to write code to generate PDF. Below are two methods which we did in PHP but you can write in other programming languages as well.
Method 1: Using PHP Library
https://github.com/mikehaertl/phpwkhtmltopdf
require __DIR__ . '/vendor/autoload.php'; use mikehaertl\wkhtmlto\Pdf;
// You can pass a filename, a HTML string, an URL or an options array to the constructor
$pdf = new Pdf('test.html');
// On some systems you may have to set the path to the wkhtmltopdf executable $pdf->binary = '~/wkhtmltox/bin/wkhtmltopdf'; if (!$pdf->saveAs('test.pdf')) { echo $pdf->getError(); }
Method 2: Generate PDF without library
echo passthru("xvfb-run -a wkhtmltopdf -T 0 -R 0 -B 0 -L 0 --orientation Portrait --page-size A4 https://www.example.com/ output.pdf 2>&1");
I hope this guide will help you for generating large PDF. Please leave a comment below if you got any issue and I will try to reply as soon as possible. Dompdf
0 notes
Text
Global WannaCry ransomware outbreak uses known NSA exploits
New Post has been published on https://www.aheliotech.com/blog/global-wannacry-ransomware-outbreak-uses-known-nsa-exploits/
Global WannaCry ransomware outbreak uses known NSA exploits
Following the emergence of the Jaff ransomware attack campaign earlier this week, another, even bigger outbreak is making headlines. The culprit? A new ransomware family called WannaCry or WCry.
Spotted earlier today, WCry caught the attention of the team due to it being spread via the recently exposed NSA shadow broker exploits. WCry took many businesses and public institutions by surprise, including telco giant Telefonica in Spain and the National Health Service in the United Kingdom, and has already infected tens of thousands of systems across the globe.
Security researcher MalwareTech created a map of overall infections and a real time map of infections to visualise the number of WCry infections, which has surpassed the 70,000 infection mark.
Meet WCry Ransomware
The WCry ransomware, also referred to as WNCry, WannaCry, WanaCrypt0r or Wana Decrypt0r, was originally spotted in campaigns in early February 2017, with more campaigns following in March. But it wasn’t until now that a global attack had been registered.
It has been written in C++ and no attempts have been made to hide the majority of the code. Like most ransomware families, WCry renames files it encrypts, adding the .WNCRY extension.
When infecting a system, it presents a ransom screen asking to pay $300 worth of bitcoins:
Unlike most ransomware campaigns, which usually target specific regions, WCry is targeting systems around the globe. So it comes as no surprise that the ransomware authors provide localised ransomware message for more than 20 languages:
Bulgarian, Chinese (simplified), Chinese (traditional), Croatian, Czech, Danish, Dutch, English, Filipino, Finnish, French, German, Greek, Indonesian, Italian, Japanese, Korean, Latvian, Norwegian, Polish, Portuguese, Romanian, Russian, Slovak, Spanish, Swedish, Turkish, Vietnamese
How do you get infected with WCry ransomware?
At the moment, WCry is primarily spreading via the leaked NSA exploits that the Shadow Brokers group released recently. More specifically, French researcher Kaffine was the first to suspect that WCry was being spread via the ETERNALBLUE exploit.
ETERNALBLUE exploits a vulnerability in the Microsoft SMBv1 protocol, allowing an attacker to take control over systems which:
have the SMBv1 protocol enabled
are accessible from the internet and
are have not been patched by the MS17-010 fix released back in March 2017
In addition, it appears that the malware authors are also taking advantage of DOUBLESPEAR, a backdoor that is usually installed via the ETERNALBLUE exploit and persisting on the system. So if your system was compromised by ETERNALBLUE previously, chances are your system is still vulnerable, even if the initial SMBv1 vulnerability was patched.
The ransomware executable itself can be best described as a dropper that contains all the different ransomware components in form of a password protected ZIP archive within its file. When run, it will start unpacking its components to the directory it was executed in using the hardcoded password “WNcry@2ol7”. Closer inspection of the ZIP archive reveals the following files:
b.wnry – Ransom desktop wallpaper
c.wnry – Configuration file containing C2 server addresses, BitCoin Wallet etc.
r.wnry – Ransom note
s.wnry – ZIP archive containing the TOR client
t.wnry – The encryption part of the ransomware encrypted using a WanaCry specific format; can be decrypted using the private key embedded inside the ransomware executable.
u.wnry – Decrypter executable
Taskdl.exe – Deletes all temporary files created during encryption (.WNCRYT)
Taskse.exe – Runs given program in all user sessions
msg\* – Language files (currently 28 different languages)
In addition the ransomware creates a couple of additional files during its execution:
00000000.eky – Encryption key for the t.wnry file which stores the actual file encryption component used by the ransomware. It is encrypted using the public key that belongs to a private key embedded inside the ransomware.
00000000.pky – Public key used by the ransomware to encrypt the generated AES keys that are used to encrypt the user’s files
00000000.res – C2 communication results
A list of all changes made by the ransomware to an infected system, can be found in the “Indicators of Compromise” section below.
WCry key generation and encryption
WCry ransomware uses a combination of RSA and AES-128-CBC to encrypt the victim’s data. To facilitate this process, is uses the Windows CryptoAPI for RSA, but a custom implementation for the AES encryption.
Interestingly, the encryption routine is stored in a separate component within the t.wnry file, and is itself encrypted using the same method used by the ransomware to encrypt user files. This was likely done to make the malware analysis more difficult. The module is loaded into memory using a custom loader and executed from there, without ever being written to the victim’s disk unencrypted.
When WCry arrives on a system, it will first import a hardcoded private RSA key that is used to decrypt the file encryption component stored within “t.wnry”. Once done, the ransomware will generate a new private RSA key. That RSA key is then submitted to the malware’s command and control server and a copy of the generated public key is stored on the system.
The ransomware then searches all available drives and network shares for files with one of the following extensions:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .ott, .sxw, .stw, .uot, .3ds, .max, .3dm, .ods, .ots, .sxc, .stc, .dif, .slk, .wb2, .odp, .otp, .sxd, .std, .uop, .odg, .otg, .sxm, .mml, .lay, .lay6, .asc, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .db, .dbf, .odb, .frm, .myd, .myi, .ibd, .mdf, .ldf, .sln, .suo, .cs, .cpp, .pas, .asm, .js, .cmd, .bat, .ps1, .vbs, .vb, .pl, .dip, .dch, .sch, .brd, .jsp, .php, .asp, .rb, .java, .jar, .class, .sh, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .3gp, .mkv, .3g2, .flv, .wma, .mid, .m3u, .m4u, .djvu, .svg, .ai, .psd, .nef, .tiff, .tif, .cgm, .raw, .gif, .png, .bmp, .jpg, .jpeg, .vcd, .iso, .backup, .zip, .rar, .7z, .gz, .tgz, .tar, .bak, .tbk, .bz2, .PAQ, .ARC, .aes, .gpg, .vmx, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .602, .hwp, .snt, .onetoc2, .dwg, .pdf, .wk1, .wks, .123, .rtf, .csv, .txt, .vsdx, .vsd, .edb, .eml, .msg, .ost, .pst, .potm, .potx, .ppam, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotx, .dotm, .dot, .docm, .docb, .docx, .doc, .c, .h
Once done, the malware will generate a new 128 bit AES key for every file it found, which is encrypted using the public RSA key generated earlier and the RSA-encrypted AES key is stored within the header of the encrypted file, together with the file marker “WANACRY!”. The AES key is then used to encrypt the file’s content.
Unfortunately, after evaluating the way WCry performs its encryption, there is no way to restore encrypted files without access to the private key generated by the ransomware. So it’s not likely a free WCry ransomware decrypter will be available for victims.
How can I protect myself from WCry?
As explained in our ransomware article, the best protection still remains a reliable and proven backup strategy, especially since the encryption used by WCry ransomware is secure. The only way to get the data back is through the help of the ransomware author or via restoring from backups. Making sure to install critical windows updates is also a very important step in protecting a system, as WCry only seems to be spreading via the SMBv1 exploit currently, which has been patched for 2 months already.
Apart from regular backups, you will be glad to hear that the Behavior Blocker technology used by Emsisoft Anti-Malware and Emsisoft Internet Security has proven to be the next best defence, as it has caught the ransomware before the file could execute and thus once again keeping our users protected from this and hundreds of other ransomware families without the need for signatures.
Emsisoft Anti-Malware and Emsisoft Internet Security users are protected from WCry by our Behavior Blocker
We consider ransomware one of the biggest threats of the past year and plan to do our best to continue our excellent track record in the next year, to keep our users as protected as possible.
It seems to be an impossible puzzle yet it’s easy to solve the Rubik’ Cube using algorithms.
Indicators of Compromise
Registry:
HKLM\SOFTWARE\WanaCrypt0r
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\<random>: “”<ransomware directory>\tasksche.exe””
HKLM\SOFTWARE\WanaCrypt0r\wd: “<ransomware directory>”
HKU\S-1-5-21-677641349-3533616285-3951951702-1000\Control Panel\Desktop\Wallpaper: “%APPDATA%\Microsoft\Windows\Themes\TranscodedWallpaper.jpg”
HKU\S-1-5-21-677641349-3533616285-3951951702-1000\Control Panel\Desktop\Wallpaper: “<ransomware directory>\@[email protected]”
File system:
@[email protected] – Placed inside every folder that contains encrypted files
@[email protected] – Placed inside every folder that contains encrypted files
%DESKTOP%\@[email protected]
%DESKTOP%\@[email protected]
%APPDATA%\tor\cached-certs
%APPDATA%\tor\cached-microdesc-consensus
%APPDATA%\tor\cached-microdescs.new
%APPDATA%\tor\lock
%APPDATA%\tor\state
<ransomware directory>\00000000.eky
<ransomware directory>\00000000.pky
<ransomware directory>\00000000.res
<ransomware directory>\@[email protected]
<ransomware directory>\@[email protected]
<ransomware directory>\b.wnry
<ransomware directory>\c.wnry
<ransomware directory>\f.wnry
<ransomware directory>\msg\m_bulgarian.wnry
<ransomware directory>\msg\m_chinese (simplified).wnry
<ransomware directory>\msg\m_chinese (traditional).wnry
<ransomware directory>\msg\m_croatian.wnry
<ransomware directory>\msg\m_czech.wnry
<ransomware directory>\msg\m_danish.wnry
<ransomware directory>\msg\m_dutch.wnry
<ransomware directory>\msg\m_english.wnry
<ransomware directory>\msg\m_filipino.wnry
<ransomware directory>\msg\m_finnish.wnry
<ransomware directory>\msg\m_french.wnry
<ransomware directory>\msg\m_german.wnry
<ransomware directory>\msg\m_greek.wnry
<ransomware directory>\msg\m_indonesian.wnry
<ransomware directory>\msg\m_italian.wnry
<ransomware directory>\msg\m_japanese.wnry
<ransomware directory>\msg\m_korean.wnry
<ransomware directory>\msg\m_latvian.wnry
<ransomware directory>\msg\m_norwegian.wnry
<ransomware directory>\msg\m_polish.wnry
<ransomware directory>\msg\m_portuguese.wnry
<ransomware directory>\msg\m_romanian.wnry
<ransomware directory>\msg\m_russian.wnry
<ransomware directory>\msg\m_slovak.wnry
<ransomware directory>\msg\m_spanish.wnry
<ransomware directory>\msg\m_swedish.wnry
<ransomware directory>\msg\m_turkish.wnry
<ransomware directory>\msg\m_vietnamese.wnry
<ransomware directory>\r.wnry
<ransomware directory>\s.wnry
<ransomware directory>\t.wnry
<ransomware directory>\TaskData\Tor\libeay32.dll
<ransomware directory>\TaskData\Tor\libevent-2-0-5.dll
<ransomware directory>\TaskData\Tor\libevent_core-2-0-5.dll
<ransomware directory>\TaskData\Tor\libevent_extra-2-0-5.dll
<ransomware directory>\TaskData\Tor\libgcc_s_sjlj-1.dll
<ransomware directory>\TaskData\Tor\libssp-0.dll
<ransomware directory>\TaskData\Tor\ssleay32.dll
<ransomware directory>\TaskData\Tor\taskhsvc.exe
<ransomware directory>\TaskData\Tor\tor.exe
<ransomware directory>\TaskData\Tor\zlib1.dll
<ransomware directory>\taskdl.exe
<ransomware directory>\taskse.exe
<ransomware directory>\u.wnry
Related Posts:
Emsisoft Releases Free Decrypter for Globe3 Ransomware
Decrypt Amnesia ransomware with Emsisoft’s free decrypter
Emsisoft releases free decrypter for CryptON ransomware
Remove Cry9 ransomware with Emsisoft’s free decrypter
Jaff ransomware: The new Locky?
0 notes