#SubBrute
Text
Sublist3r — Sub-Domain Enumeration Tool
Sublist3r — Sub-Domain Enumeration Tool
CyberSecurity Updates
,
Kali Linux
/ By
CyberArk
December 14, 2021
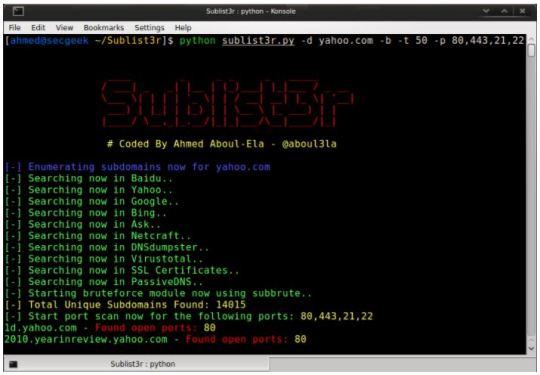
Subdomain discovery is very essential for information gathering during penetration testing on web applications. There are lots of tools available for it. We need to use them and find our subdomains because it is possible to find subdomains with some valuable information or some bugs which may lead our penetration testing or bug hunting process.
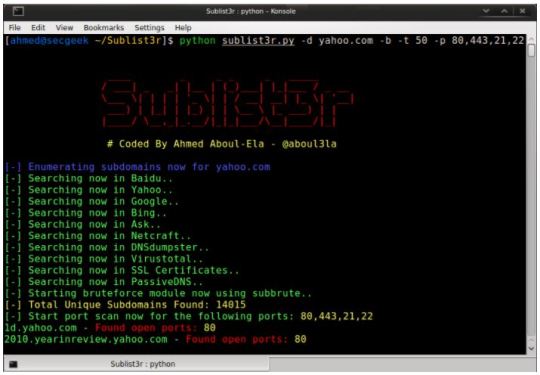
In today’s article we are going to discuss about how we can find subdomains using sublist3r on our Kali Linux system. Sublist3r is a Python tool designed to enumerate subdomains of websites using OSINT. It helps penetration testers and bug bounty hunters collect and gather subdomains for the domain they are targeting. Sublist3r enumerates subdomains using many search engines such as Google, Yahoo, Bing, Baidu and Ask. Sublist3r also enumerates subdomains using Netcraft, Virustotal, ThreatCrowd, DNSdumpster and ReverseDNS.
Subbrute is integrated with Sublist3r to increase the possibility of finding more subdomains using bruteforce technology with an improved password list.
Install & Use Sublist3r on Kali Linux
Enough discussion, let’s install Sublist3r on our Kali Linux system. Sublist3r comes with Kali Linux repository and we can easily install it by applying following command:
sudo apt install sublist3r
This command will install sublist3r on our system, as we can see in the following screenshot:
After the task is finished, we can use sublist3r on our system. First of all let’s check it’s help options by using following command:
sublist3r -h
In the following screenshot we can see the options of sublist3r tool.
Simply we can put a target domain to find it’s subdomains by using -d flag. Lets check for subdomains of Google by using following command:
sublist3r -d google.com
In the following screenshot we can see that sublist3r discovered subdomains of Google.com.
In the above screenshot we can see that we got almost 38k unique subdomains for google.com.
If we want to save all the subdomains in a text file then we can use -o flag. Then our command will be like following:
sublist3r -d google.com -o Googlesubdomains.txt
By using above command we can save the subdomains list on a txt file with any name.
We also can search for subdomains of specific domain and show only subdomains which have open ports. We can specify our required open ports by using -p flag.
For an example if we want to check subdomains on facebook.com domain which have port 80 and 443 is opened and save the output on a file named fbsubdomains.txt then we need to use following command:
sublist3r -d facebook.com -p 80,443 -o fbsubdomains.txt
We can see in the following screenshot that we have discovered the subdomains of facebook.com which have port 80 and port 443 opened and we saved the output on a text file.
This is how we can perform subdomain enumeration using Sublist3r on our Kali Linux system. This is very useful for cybersecurity experts, during the recon process.
0 notes
Text
Dr. ROBOT - Domain Reconnaissance and Enumeration
Dr. ROBOT - Domain Reconnaissance and Enumeration #Ansible #DNS #Docker #domain #DR.ROBOT #enumeratesubdomains
[sc name=”ad_1″]
Introduction
Dr. ROBOT is a tool for Domain Reconnaissance and Enumeration. By utilizing containers to reduce the overhead of dealing with dependencies, inconsistency across operating sytems, and different languages, Dr. ROBOT is built to be highly portable and configurable.
Use Case: Gather as many public facing servers that a target organization possesses. Querying DNS…
View On WordPress
#Ansible#DNS#Docker#domain#DR. ROBOT#enumerate subdomains#EYEWITNESS#OSINT#python#python3#Reconnaissance#scan#scanners#Scans#Scraping#Shodan#subbrute#subdomain#subdomains#SUBFINDER#Sublist3r
0 notes
Link
SubBrute is a community driven project with the goal of creating the fastest, and most accurate subdomain brute-forcing tool. Some of the magic behind SubBrute is that it uses open resolvers as a kind of proxy to circumvent DNS rate-limiting. via Pocket
0 notes
Text
How to make a Subdomain Takeover Attack
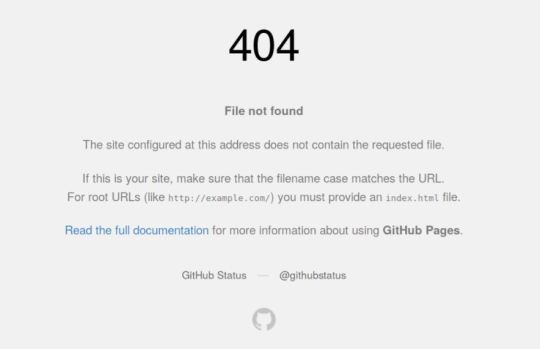
A team of information security experts tells us that sub-domain acquisition vulnerabilities happen whenever a subdomain points to a service (for example, GitHub pages, Heroku, etc.) that has been removed or removed. This may allow an attacker to configure a page in the service that was being used and direct his page to that subdomain. As an example, if subdomain.example.com was pointing to a GitHub page and the user decided to remove their GitHub page, an attacker could create a GitHub page, add a CNAME file that contains the subdomain.testing. com and claim the subdomain.testing. com.
A subdomain that points to a GitHub page is www. testing. com. If someone decides to remove https:// github. com/test0x01/testing and does not delete the DNS entry that points to this page, you can post content at www. testing. com.
Some hackers use sub-domain and brute force scraping tools such as Sublist3r to find the sub-domains of a target, say information security professionals. Then the DNS records will be verified and / or a screen capture script will be used to detect vulnerable subdomains. A subdomain that points to a GitHub page that returns a 404 can be an indicator that can be claimed on GitHub.
Now we will talk about Sublist3r. It is important to know that Sublist3r is a python tool designed to enumerate subdomains of websites using OSINT. Information security researchers tell us that it also helps penetration verifiers and bug hunters collect sub-domains for the domain they point to. In addition, Sublist3r lists subdomains using many search engines such as Google, Yahoo, Bing, Baidu and Ask. On the other hand, it enumerates subdomains using Netcraft, Virustotal, ThreatCrowd, DNSdumpster and ReverseDNS.
Experts comment that subbrute was integrated with Sublist3r to increase the possibility of finding more subdomains using bruteforce with an improved word list.
Installation: git clone https://github.com/aboul3la/Sublist3r.git
About the security impact; a subdomain control takeover could allow an attacker to publish content in the subdomain, information security experts said. In the case where a subdomain is a secondary domain of the base name of the service, the attacker can also read and set cookies in the base name: subdomain.example.com can set cookies for example.com.
We have a real case of a subdomain acquisition made by Frans Rosén on inside.gratipay.com. Researchers tell us that, Frans posted a page on a hidden route (login123) instead of posting content on the landing page. This is the best way to avoid damaging the image of the company.
It is important to remove the DNS entry in the subdomain that points to the deleted service to make sure no one can take over.
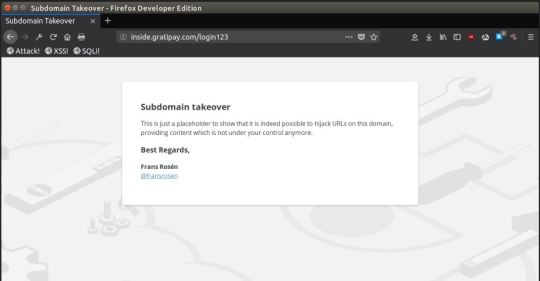
#techblog#tech#tecnologia#noticias tecnologicas#technology#tech news#noticias#subdomain#news#latest news
0 notes
Text
toolsmith #130 – OSINT with Buscador
First off, Happy New Year! I hope you have a productive and successful 2018. I thought I'd kick off the new year with another exploration of OSINT. In addition to my work as an information security leader and practitioner at Microsoft, I am privileged to serve in Washington's military as a J-2 which means I'm part of the intelligence directorate of a joint staff. Intelligence duties in a guard unit context are commonly focused on situational awareness for mission readiness. Additionally, in my unit we combine part of J-6 (command, control, communications, and computer systems directorate of a joint staff) with J-2, making Cyber Network Operations a J-2/6 function. Open source intelligence (OSINT) gathering is quite useful in developing indicators specific to adversaries as well as identifying targets of opportunity for red team and vulnerability assessments. We've discussed numerous OSINT offerings as part of toolsmiths past, there's no better time than our 130th edition to discuss an OSINT platform inclusive of previous topics such as Recon-ng, Spiderfoot, Maltego, and Datasploit. Buscador is just such a platform and comes from genuine OSINT experts Michael Bazzell and David Wescott. Buscador is "a Linux Virtual Machine that is pre-configured for online investigators." Michael is the author of Open Source Intelligence Techniques (5th edition) and Hiding from the Internet (3rd edition). I had a quick conversation with him and learned that they will have a new release in January (1.2), which will address many issues and add new features. Additionally, it will also revamp Firefox since the release of version 57. You can download Buscador as an OVA bundle for a variety of virtualization options, or as a ISO for USB boot devices or host operating systems. I had Buscador 1.1 up and running on Hyper-V in a matter of minutes after pulling the VMDK out of the OVA and converting it with QEMU. Buscador 1.1 includes numerous tools, in addition to the above mentioned standard bearers, you can expect the following and others:
Creepy
Metagoofil
MediaInfo
ExifTool
EmailHarvester
theHarvester
Wayback Exporter
HTTrack Cloner
Web Snapper
Knock Pages
SubBrute
Twitter Exporter
Tinfoleak
InstaLooter
BleachBit
Tools are conveniently offered via the menu bar on the UI's left, or can easily be via Show Applications.
To put Buscador through its paces, using myself as a target of opportunity, I tested a few of the tools I'd not prior utilized. Starting with Creepy, the geolocation OSINT tool, I configured the Twitter plugin, one of the four available (Flickr, Google+, Instagram, Twitter) in Creepy, and searched holisticinfosec, as seen in Figure 1.
Figure 1: Creepy configuration
The results, as seen in Figure 2, include some good details, but no immediate location data.
Figure 2: Creepy results
Had I configured the other plugins or was even a user of Flickr or Google+, better results would have been likely. I have location turned off for my Tweets, but my profile does profile does include Seattle. Creepy is quite good for assessing targets who utilize social media heavily, but if you wish to dig more deeply into Twitter usage, check out Tinfoleak, which also uses geo information available in Tweets and uploaded images. The report for holisticinfosec is seen in Figure 3.
Figure 3: Tinfoleak
If you're looking for domain enumeration options, you can start with Knock. It's as easy as handing it a domain, I did so with holisticinfosec.org as seen in Figure 4, results are in Figure 5.
Figure 4: Knock run
Figure 5: Knock results
Other classics include HTTrack for web site cloning, and ExifTool for pulling all available metadata from images. HTTrack worked instantly as expected for holisticinfosec.org. I used Instalooter, "a program that can download any picture or video associated from an Instagram profile, without any API access", to grab sample images, then ran pyExifToolGui against them. As a simple experiment, I ran Instalooter against the infosec.memes Instagram account, followed by pyExifToolGui against all the downloaded images, then exported Exif metadata to HTML. If I were analyzing images for associated hashtags the export capability might be useful for an artifacts list.
Finally, one of my absolute favorites is Metagoofil, "an information gathering tool designed for extracting metadata of public documents." I did a quick run against my domain, with the doc retrieval parameter set at 50, then reviewed full.txt results (Figure 6), included in the output directory (home/Metagoofil) along with authors.csv, companies.csv, and modified.csv.
Figure 6: Metagoofil results
Metagoofil is extremely useful for gathering target data, I consider it a red team recon requirement. It's a faster, currently maintained offering that has some shared capabilities with Foca. It should also serve as a reminder just how much information is available in public facing documents, consider stripping the metadata before publishing.
It's fantastic having all these capabilities ready and functional on one distribution, it keeps the OSINT discipline close at hand for those who need regular performance. I'm really looking forward to the Buscador 1.2 release, and better still, I have it on good authority that there is another book on the horizon from Michael. This is a simple platform with which to explore OSINT, remember to be a good citizen though, there is an awful lot that can be learned via these passive means.
Cheers...until next time.
The post toolsmith #130 – OSINT with Buscador appeared first on Security Boulevard.
from toolsmith #130 – OSINT with Buscador
0 notes
Quote
Muy buenas!!!
Siguiendo los últimos enfoques de mis entradas orientadas a pequeños scripts para automatizar ciertas tareas, hoy presento N4xd0rk, herramienta para el descubrimiento de subdominios.
Es cierto que existen bastantes herramientas que realizan esta tarea, como podéis consultar en este post bastante útil de los compañeros de Hackplayers que recopila las herramientas actuales con esta finalidad. Sin embargo, la gran mayoría son activas, es decir, iteractuan directamente contra el target quedando reflejadas las peticiones en el sistema de logs de la aplicación web. Además, muchos aplican la técnica de descubrimiento basada en fuerza bruta como Knock y subBrute. El problema de estas técnicas son los sistemas de protección que al identificar numeroso tráfico de enumeración desde la misma IP pueden banearla.
Por ello, N4xdork, se basa en la técnica de hacking con buscadores, para listar subdominios de un target aprovechando los resultados indexados por los buscadores sin exponer la dirección IP origen. Se puede decir que es una herramienta que permite anonimizar el origen, que siempre es interesante en un test de intrusión externo. El único inconveniente de basarse en la técnica del hacking con buscadores es que sólo obtendremos los resultados indexados por los buscadores, por lo tanto, si un dominio tiene correctamente configurado el fichero robots.txt de tal manera, que ningún bot ha visitado la página web, no será indexado por los buscadores y no será transparente para nosotros. Por lo tanto, es interesante combinar N4xdork con alguna de las anteriores herramientas citada para aumentar el rango de alcance.
Dicho hecho esto, entramos en detalle sobre el funcionamiento de N4xdork
Lo podéis descargar en mi github.
Requisitos:
Python 2.7
beautiful soup
requests
json
N4xd0rk emplea el buscador Bing para automatizar la búsqueda de subdominios empleando Bing dorks y exporta los resultados en el formato estándar json.
Para ejecutarlo y ver el help
python N4xD0rk.py -h
Como se observa los parámetros de búsqueda son autoexplicativos, pero sí se va a hacer hincapié en el parámetro -l (–language). Este parámetro está orientado a dominios “.com” que pertenecen a grandes multinacionales, que tienen dominios propio en cada país (.es, .it, fr, ..) pero a la par tienen diferentes subdominios sobre “.com”. Por lo tanto la idea es filtrar subdominios por la empresa en un país (por ejemplo, “.es”) y si se busca sobre el “.com” filtrar los subdominios según el idioma seleccionado. Más adelante, con el ejemplo, se entenderá mejor.
Como PoC, se van a buscar todos los subdominios del dominio “marca.com”:
Visualizando el fichero de exportación “output.json”:
Como se citaba anteriormente, filtrando con el parámetro “language” se obtienen diferentes subdominios sobre el dominio paypal.com
Subdominios en castellano:
Subdominios en inglés:
Esto es todo, espero que os resulte útil la herramienta y la empleéis
Hasta la próxima entrada.
Saludos-
N4xh4ck5
“La mejor defensa es un buen ataque”
Twittear
https://www.fwhibbit.es/n4xd0rk-anonimizando-el-descubrimiento-de-subdominios
0 notes
Photo

Diferentes formas de enumeración de subdominios
Un profesional de seguridad de la información escribió una lista de los métodos más populares, el experto intentó hacer una lista de algunas herramientas y recursos en línea para explotarlos. Por supuesto, esta lista no es exhaustiva, hay muchas cosas nuevas todos los días, pero aún así es un buen comienzo.
Métodos
Fuerza bruta
La forma más fácil. Pruebe millones y millones de palabras como subdominios y compruebe cuáles están vivos con una solicitud de DNS de reenvío.
Transferencia de zona también conocida como AXFR
La transferencia de zona es un mecanismo que los administradores pueden usar para replicar bases de datos DNS, pero a veces el DNS no está bien configurado y esta operación es permitida por cualquiera, revelando todos los subdominios configurados.
Caché de DNS husmeando
El rastreo de caché DNS es una forma específica de consultar un servidor DNS para verificar si existe un registro en su caché.
DNS inverso
Intenta encontrar el nombre de dominio asociado con una dirección IP, es lo opuesto a Forward DNS.
Nombres alternativos
Una vez que haya finalizado la primera ronda de su reconocimiento, aplique permutaciones y transformaciones (¿basadas en otra lista de palabras tal vez?) A todos los subdominios descubiertos con el fin de encontrar nuevos.
Herramientas DNS en línea
Hay muchos sitios web que permiten consultar bases de datos DNS y su historial.
Certificados SSL
Solicite información sobre todos los certificados vinculados a un dominio específico y obtenga una lista de los subdominios cubiertos por estos certificados.
Los motores de búsqueda
Busque un dominio específico en su motor de búsqueda favorito y luego menos los sitios descubiertos de los sudomains uno por uno: example.com -www -dev
Herramientas técnicas / motores de búsqueda
Cada vez más empresas alojan su código en línea en la plataforma pública, la mayoría de las veces estos servicios tienen una barra de búsqueda.
Análisis de texto
Analice el código HTML de un sitio web para encontrar nuevos subdominios, esto se puede aplicar a todos los recursos de la empresa, documentos de oficina también.
Descubrimiento de VHost
Intenta encontrar cualquier otro subdominio configurado en el mismo servidor web forzando bruta el encabezado del host.
Herramientas
Altdns: nombres alternativos de fuerza bruta
Amasar: fuerza bruta, Google, VirusTotal, nombres alt
aquatone-discover: Fuerza bruta, Riddler, PassiveTotal, Threat Crowd, Google, VirusTotal, Shodan, Certificados SSL, Netcraft, HackerTarget, DNSDB
BiLE-suite: análisis de HTML, nombres alt, DNS inverso
blacksheepwall: AXFR, fuerza bruta, DNS inverso, Censys, Yandex, Bing, Shodan, Logontube, certificados SSL, virus total
Bluto: AXFR, netcraft, fuerza bruta
brutesubs: enumall, Sublist3r, Altdns
cloudflare_enum: Cloudflare DNS
CTFR: certificados SSL
DNS-Discovery: fuerza bruta
DNS Parallel Prober: resolución de DNS
dnscan: AXFR, fuerza bruta
dnsrecon: AXFR, fuerza bruta, DNS inverso, almacenamiento en caché de snoop, Google
dnssearch: fuerza bruta
domained: Sublist3r, enumall, Knockpy, SubBrute, MassDNS, recon-ng
enumall: recon-ng -> Google, Bing, Baidu, Netcraft, fuerza bruta
Feroz: AXFR, fuerza bruta, DNS inverso
Knockpy: AXFR, virustotal, fuerza bruta
MassDNS: resolución de DNS
Segundo pedido: análisis de HTML
Sonar: AXFR, fuerza bruta
SubBrute: fuerza bruta
Sublist3r: Baidu, Yahoo, Google, Bing, Ask, Netcraft, DNSdumpster, VirusTotal, Threat Crowd, Certificados SSL, PassiveDNS
theHarvester: DNS inverso, fuerza bruta, Google, Bing, Dogpile, Yahoo, Baidu, Shodan, Exalead
TXDNS: nombres alt (typo / tld)
vhost-brute: descubrimiento vhost
VHostScan: descubrimiento vhost
virtual-host-discovery: descubrimiento de vhost
Herramientas DNS en línea
https://hackertarget.com/
http://searchdns.netcraft.com/
https://dnsdumpster.com/
https://www.threatcrowd.org/
https://riddler.io/
https://api.passivetotal.org
https://www.censys.io
https://api.shodan.io
http://www.dnsdb.org/f/
https://www.dnsdb.info/
https://scans.io/
https://findsubdomains.com/
https://securitytrails.com/dns-trails
https://crt.sh/
https://certspotter.com/api/v0/certs?domain=example.com
https://transparencyreport.google.com/https/certificates
https://developers.facebook.com/tools/ct
Los motores de búsqueda
http://www.baidu.com/
http://www.yahoo.com/
http://www.google.com/
http://www.bing.com/
https://www.yandex.ru/
https://www.exalead.com/search/
http://www.dogpile.com/
https://www.zoomeye.org/
https://fofa.so/
Herramientas técnicas / motores de búsqueda
https://github.com/
https://gitlab.com/
https://www.virustotal.com/fr/
Caché de DNS husmeando
nslookup -norecursive domain.com
nmap -sU -p 53 –script dns-cache-snoop.nse –script-args ‘dns-cache-snoop.mode = temporizado, dns-cache-snoop.domains = {dominio1, dominio2, dominio3}’ <ip >
Otros recursos en línea
https://ask.fm/
http://logontube.com/
http://commoncrawl.org/
http://www.sitedossier.com/
0 notes