#Unix Internet software Assignment Help
Explore tagged Tumblr posts
Text
What is the best way for someone who isn't a programmer to learn Python?
As you may know, computers rely exclusively on software code to work. There are a slew of programming languages at programmers' disposal to help them create apps. Python is a high-level, interpreted, and general-purpose coding language that is extremely easy to learn, use, and maintain.

So, if you're a rookie, Python is the best and easiest language to learn, and if you're not a developer, it could be a nice place to start.
Learning Python will be a snap if you've worked with other programming languages. Aside from the variations in syntax, the essential concepts of the Object-Oriented Programming system are the same. Python also includes a big library that can assist you with practically any task you can think of. In today's post, we'll show you how to learn Python in a step-by-step process that everyone can follow. We'll go over the various Python certification as well.
Let's take a closer look at the Python programming language
Python is a widely used dynamic coding language, especially when compared to Java, PHP, Perl, and Ruby. It is also recognised as a scripting coding language. It covers foundations for object-oriented programming, as well as automated memory management and other programming techniques. Python is a procedural language with a big and well-documented source file that is highly structured. Python's library supports Internet technologies such as IMAP and FTP. It has a syntax that distinguishes it from other programming languages such as C, C++, and Java.
The Python Programming Language includes a lot of useful features, such as:
You can use open-source whenever you want and interface with other languages such as Java, C, and C++.
Encourage code reuse by endorsing simple and easy-to-understand modules.
Object-oriented programming is a viable option.
A software can run on Windows, Unix, Linux, Mac, and other operating systems thanks to cross-platform programming.
Because the interpreter runs each piece of the programme one at a time, debugging is trivial.
It's a common misconception that the computer language's name comes from the serpent Python. This is far from the case. It's a play on the title of the popular British television show Monty Python's Flying Circus. Python offers a lot of interesting uses. It's commonly used in Django and Pyramid, as well as complicated content management systems like Plone or Django CMS.
Consider the following points while you explore the Python programming language.
Operations
A process is defined as anything we do with data. Addition, subtraction, comparison, and logic operations are examples of functions. To validate an individual's most recent mobile and current plans, we can type print(new plan =old plan). A boolean value is returned as a result of the comparisons operation double equals, which is either true or false. Python has a large number of operators.
Functions
It's possible that some functionality can be reused, or that a piece of the programme is so large that it's appropriate to break it off into its own block and refer to it as needed. Functions are the term for these types of cooperation. The definition of the function is def.
Object-Oriented Programming (OOP) is a programming style that employs objects to solve problems.
Python, like the majority of today's prominent computer languages, is based on Object-Oriented Programming (OOPs) (object-oriented programming ideas). It's a simple concept, yet it's effective. Everything is specified as an object in the Object-Oriented Programming system. A class is a container for the code we're writing.
File Management
Any programme that interacts with files must be capable of doing so. There's a chance your software will need to read or write to a file. In Python, file management is a breeze. The most prevalent forms of data in Python are binary and text. The abbreviation CRUD stands for create, read, update, and delete, and it refers to four main sorts of file operations.
Crash classes in Python are also available. There are a variety of online Python crash courses accessible these days. Each platform has its own set of benefits and drawbacks, so be sure the course content fulfils your requirements before registering. These lectures cover the fundamentals of Python, operators, exceptional handling, Python statements, object-oriented programming, functions, methods, packages, modules, and error handling, among other subjects. Because these courses are timed, some students may complete your system in as little as 24 hours, while others may take up to 55 hours.
Let's get some Python programming certifications under our belts, shall we?
There are three main categories of certification courses to consider while looking for the best python credentials. The first certifies entry-level courses, the second certifies associate level courses, and the third certifies professional level courses.
In the entry-level certification course, you will be certified for.
A thorough mastery of the fundamental ideas of computer coding is required.
Excellent command of the Python programming language's syntax and semantics
The ability to use the Python Standard Library to solve common implementation challenges.
In the associate-level certification course, you will be certified for.
Understanding and applying the basic principles and practises of object-oriented programming.
I've previously worked on Python programming jobs.
You're familiar with the fundamentals of coding and computer programming.
In the professional-level certification course, you will be certified for.
Use Python and other advanced programming tools to complete coding assignments.
Use advanced OOP principles and techniques to your advantage.
Create comprehensive systems, structures, and solutions.
Understand what graphical user interfaces and network programming are and how to deal with them.
Conclusion
So there you have it: a complete non-guide programmer's guide to learning Python. There are also a few online courses to choose from.just visit to Global Tech Council and find the best from us.
#python certification#Python Crash course#python programming certification#best python certification
0 notes
Text
KEY WEB DEVELOPMENT FRAMEWORKS AND LANGUAGES IN 2021
INTRODUCTION
Web Development is core to almost every business. To reach the masses, one has to have a web presence to be accessible from anywhere across the globe. Programming languages have been developed to make web development easier. Given below is a description of some of the most user-friendly front-end and back-end web development programming languages that you should learn so that you can make a customized website. Web development agencies provide services of web development that are based on your needs.

TOP 4 BACKEND WEB DEVELOPMENT LANGUAGES
The Backend language is work done at the back end of the website or web application. Backend developers address the server-side of the website and perform the website integration. Backend languages help manage servers, databases, and applications. PNMGroup has got the best of Toronto web development professionals to make a website of your liking.
PYTHON
A Python is one the most powerful language which has been used for some years now for web development and particularly in the field of data science. It is largely being used in Research work carried out in almost every field; specifically Computer Science to Medical Science.
Python offers an abundance of tools for computational science, stats, and maths with numerous frameworks and libraries. It supports several platforms and systems, which helps improve the productivity of developers and programmers. It is based on Object-Oriented programming and allows to easily scale web applications.
Following are some of the major fields where python is being used:
Internet of things
Serverless computing
Development of cloud-native
Business application
System programming
PHP
PHP is another famous backend programming language used worldwide. It is dynamic and a general-purpose language that is used in the development of the server-side of the website. It is maintained by an Open Source platform that works across Mac, UNIX, and Windows Systems. Facebook is one of the most famous and popular websites and web applications made using PHP.
PHP offers plenty of frameworks and easy to use. It has an Xdebug extension that provides great debugging. It supports several automation tools for website testing and deploying. Some of the famous websites made with the help of PHP are; CMS systems, Standalone web apps, and server-side web applications or websites.
JAVA
Java is famous for its versatility and Andriod development. It is a platform-independent multi-purpose language used for programming and has been one of the most popular backend languages for decades. Mostly it is adopted due to its stability and a language one should definitely learn to become a web developer. Java is one of those programming languages which offer a rich stream of features, such as backward compatibility; it has played a significant part in business website or web application requirement. Unlike other programming languages, java does not makes major changes to its language, with runtime being one of the best among other programming languages.
Java offers plenty of open source libraries. It follows a stack allocation system and supports distributed computing and multi-threading. Java offers a galore of APIs to accomplish various necessary tasks such as networking, XML parsing, utilities, and database collection. Some of the famous websites or web applications made with the help of Java are; Big Data applications, Andriod applications, and Enterprise Websites.
C#
C# is a Microsoft-made Object orient programming language on the basis of widely-used programming language C. At the start, it was part of the .NET framework to make windows applications. It is a general-purpose language and is used in Windows platforms and also in Mobile Phone applications, i.e iOS, and Andriod. In short, it is one of the best backend programming languages ever made.
In terms of development experience, it comes after C#. It has plenty of frameworks as it has been used for over 20 years now. Similar to Java, C# is independent of the platform and capable of working with code databases.
It has rich data types and libraries with a faster compilation and execution process. Some of the famous websites, C# has helped in are the development of games, app development, server-side programming, and windows platform software.
FRONTEND LANGUAGES
As the name suggests, the front-end languages help shape the front end of the website. It is what the viewers see on the screen when they click on a website. Front-end languages help enhance user experience to ensure it is seamless and eye-catching. The overall look and feel of the website come with the help of Front end programming languages. Given below are the famous front-end programming languages.
JAVA SCRIPT
JavaScript is one of the highly interactive and user-friendly applications. It is one of the most frequently used programming languages that include, cloud, mobile devices, browsers, servers, and so on. JavaScript covers a large part of web development. With the help of Node.js, event-driven programming is provided which is extremely suitable for head I/O processes. It provides data validation functionality with regular updates on ECMA specifications. With its unique framework, it provides a diverse and wide range of applications that can easily be integrated and implemented with other languages. Some of the use-cases of Javascript are; Mobile app development, serverless computing, and many more.
REACT
React is a framework by javascript. This framework allows professionals to build user interfaces with their dynamic attributes. React makes websites work faster, and with a smooth shift from one to another element. Importantly, React helps build a positive consumer impression with the help of its remarkable user experience. It also provides ab options that help to divide each of the web pages into small components. React Virtual Document Object Model permits to development of the quick and scalable application.
It helps in boosting productivity and facilitates maintenance. SEO friendly and easy to learn for developers and saves time by reusing its components. React consists of an open-source library and helps build complex websites with higher user interaction and dynamic web pages.
ANGULAR
Angular is another of the improved and upgraded version of AngularJS built by Google. Not as easy as other front-end programming languages but allows to make complicated and highly scaleable applications with great functionality and attractive visuals. Its model view architecture allows dynamic modelling and uses HTML to make User Interfaces. With the help of HTML directives, it offers better functionality and helps in filtering data before reaching the view.
Some of the pros of using Angular are dynamic websites and web applications, progressive web applications, and enterprise websites.
VUEJS
VueJS is one of the most simple clear, and user-friendly frontend languages, with the distinguishing features of engaging and well-structured web applications. It is designed to simplify and organize web pages and make them extremely adaptable. It is one of the quickest ways to develop the front end of websites for both small and large-scale enterprise websites. For beginners, it’s a perfect language to learn and expand their web experience. It uses the services of virtual DOM to make the necessary change and the data binding feature allows to manipulate or assign HTML attributes.
Some of the important features are interactive web applications and scalable web apps.
CONCLUSION
Here at PNMGroup, we are the leading web development agency in Toronto and have got web developers with expertise in web development in both the front-end and back-end languages. If you or anyone you know is looking for web development services with customized features, drop us an email at [email protected] and someone from our sales team will be with you shortly.
0 notes
Text
How java is good for your career growth opportunities?
Java is a dynamic language which is one of the most popular and powerful languages in a programming platform. It is a high-level language which programs in a multiple platform such as Macintosh, windows and Unix computers. It is a primary source that should most commonly be used for Internet-based applications. It is originally designed for embedded network applications running on multiple platforms. Many of the companies are providing the basic projects in java for beginners to become a specialist in the programming language.
It is basically designed for developing programs with the set-top boxes and handheld, but now it became a popular choice for creating various methods of web applications. It can be used to build a small application module or applet that should be used as a part of a web page. This programming language is divided into two categories such as primitive types and reference types. Java for beginners will provide a best career opportunity to make success in their job roles as well as to improve their salary growth and lifestyle.
Java programming for beginners
It is one of the most popular and a common programming language that should be used across the world. It can be used by software professionals to design high-performance applications. It is the easiest language than other programming languages. It is one of the excellent choices for programming with java for beginners. It acquired the object-oriented principles for the beginning of basic and advanced java programs. It can be helpful to understand the subject concepts easily.
Why become a java developer?
Java is the most widely spreading language which commenced with the popularity at the top of the index. It provides an excellent skill for making good roles available in the different sectors. A java developer is the best role for designing various interfaces to creating and testing with various dynamic applications that are involved at every stage of the development process.
These developers can collaborate with the other professionals such as web designers, web developers and some other software engineers. It helps to develop their communication and other transferable skills which make advancements in your career as an IT professional. Java programmers should work for real-world applications such as healthcare, financial services and other popular sectors.
Benefits of java
Java is a multitude language of open-source libraries
It will backed by high-level support from tech giants like Google and IBM
Big and mature community support
It has some several readily available frameworks for rapidly building reliable apps
Java has a galore of IDEs and tools to help make java development simpler
Allows creating modular programs and reusable codes
Java is the language that can easy to write, compile, debug and learn than other programming languages
It is an independent platform for both the source and binary level
It has the ability to run the same program on many different systems through World Wide Web software.
Job roles of java
Java developer
Java architect
Web developer
Database administrator
Basic career path of java professional
Junior programmer
Junior developers are the entry-level programmers; they work on both front-end and back-end codes to build an application. These programmers can require an extensive knowledge of coding and the program language of JavaScript to develop and troubleshoot their company products. Those developers are the major part of a team to work as coders and developers. They are working in a popular company with the role of coding, debugging, reviewing coding and as technical documentation.
Skills required
Problem solving
Algorithms and data structures, algorithm complexity analysis
Strong command of a programming language
System design
Soft-skills
Senior programmer
A senior developer is an experienced professional in information technology. They should have experience leading a development team through a complete development lifecycle. They work with the Java programming language to develop various web applications and computer systems. Their career growth involves assigning tasks to the other team members, designing and testing code. They are responsible for communicating with other clients to analyze their requirements.
Requirements
The developers must experience in designing, building and testing java EE applications
In-depth of the knowledge it is popular for java frameworks like JSF and spring MVC
Experience with object-oriented design
Good delegation and time management skills
Problem-solving abilities
Architect
Architects in the Java programming language will define as to upgrade and integrate with the software architecture that should support with java-based applications. The duties of java architects are based on the infrastructure for design and integration for internet computing systems and they are responsible for analyzing information requirements and studying the business operations and user-interface with the development of physical databases. It is the great career path of the person to choose with the strong technical background moving. They are trained to consider the project and related to its contexts. Architect developers can ensure long-term benefits for themselves and their clients and the relevant neighborhoods.
Skills required for java architect
Knowledge of software architecture
Web programming abilities
Software design
Design and implementation of networks
Java can provide with the other variations such as java servlets, java beans and java script
Project management ability to present technical information
IT manager
These persons are responsible for making design, development and work with the management of java-based applications. It is an excellent opportunity for depending on your qualifications, interest and experience which is able to advance into the management roles and progress to the senior technical roles. They are the professionals for planning with new projects and clients to develop their requirements and dealing with the information system of the company. These managers can work in the various job roles such as hardware, software, networking and other business uses.
Skills required for IT manager
Analytical and problem solving skills
Strong technical skills
The ability to work well under pressure
Attention to detail
Team working skills
Organization and time management
Interpersonal and communication skills
Management and leadership skills
The end note
Java is an independent platform which is easy to learn. It is a good professional course for the students to become a well reputed developer.
0 notes
Text
Zabbix Assignment Help
Online Zabbix Assignment Help from Experts’
The term Zabixix is commonly used in the information technology industry. Zabics is usually a source of monitoring software that includes various services such as networks, cloud services, virtual machines, servers, etc. It is like that. Most students do not know Zabics and therefore find it very difficult to do their tasks and Zanbics tasks always require help. We have qualified trainers and professionals who zabbix assignment help you determine zabics tasks.
Zabbix is a very comprehensive topic in IT and students may not be fully aware of it. Our primary supplier has sovereign control over Zabbix and will certainly assist you in zabbix's actions, through which your actions are not able to be performed. Can be met on time and with minimal effort. Seek our help, the content of your management and the quality of writing skills. Will definitely be improved.
Zabbix is a software tool for widely used open source monitoring in the IT industry. In 1998, Zabbix started as an internal software and started its services publicly under GPL within three years. The first version of Zabbix was released in 2004, and there are now several updated versions of Zabbix. Zabbix has very important features like CP tax deductions, disk consumption and other network services. Zabics works on various operating systems such as Windows, Linux, Solaris, Mac OS X, etc.
Zabbix takes advantage of the sensitivity and accessibility of SMTP and HTTP services without installing any additional software.
One of the main features of Zabics is that it can be installed on any computer or computer, whether it's Windows or Unix.
Zabics monitors statistics and ensures that there is no CBD rate and improves disk and network space.
Zabics supports extended messaging and provides a protocol that is one of the actual notification bars. Zabbix can support monitoring statistics through ICPM, SNMP, and TCP checks. These checks are often known as Internet Protocol packages.
There are a variety of Zabics software that will help you improve the operation of your network and computer.
Some main
Agent Czech Zabics - this is one of the most useful services that Zabics offers. Agent control often helps to collect Zabbix data when communicating with agent Zabbix. Zabbix Scan Agent ensures that your data is not available. are not corrupt and harmful.
Commentator Segment - Input data is supported using a treadmill element. The thread is usually part of a Zabics agent scan that improves your network and supports the incoming data without needing it.
To use the treadmill element, you need to install a mat item on Zabbix and send data to Zabbix.
Monitoring records - As you already know, Zabics is an essential tool for monitoring. With monitoring, Zabbix can also be used to analyze log files. To monitor the use of log files, you must configure the log monitoring item, and the host must have the Zabics agent. The monitored file size limit mainly depends on large file support.
ODBC - ODBC verification usually means an open relationship to the database. ODBC is a registered interface that is used to monitor database management systems. For best results in ODBC, you need to install and configure unixODBC drivers.
Aggregate Check - Aggregate check is another type of zabics that is very essential for collecting information through database queries. This tool only works on zabbix agent and does not require hosts.
Zabix presented many other types. If you research your subjects and support assigned to Zabbix, our zabbix assignment help professionals, experts and trainers will provide you with all the support and information about Zabbix and all types.
One type of work is work among students, whether they study at university or at school. Most students led by Zabics do not have the necessary knowledge and find it difficult to do their job on time. So we zabbix assignment help projects and report to students on Zabics. We have many experts and professionals who will help you in your work.
We have one of the best teams for executing projects and tasks. We offer help for a wide range of activity topics. Our personal writing services are available 24 hours a day. 7. In addition, we help in drafting research papers, research plotting and presenting research papers. If you're looking for help, you'll make sure there are no grammatical errors and that your work is not available. There is no plagiarism. In addition, we will improve your writing and time skills. Your identity is not valid. Will be safe and will contact the best zabbix assignment help support order within 24 hours.
0 notes
Text
Web Application Development - A Guide to Success
From the Fantastic old days of this Tag, into the XML-savvy Web services of now, applied Internet terminology has come a very long way. And nowhere is that more obvious than in the area of Web software development.
Since the Internet Grew to a significant player on the international financial growth, so did the variety of investors that were interested in its own development. Thus, you might wonder, how can the Internet continue to play a significant role in communications, news and media? The important words are: Web Application Projects.
Web applications are company policies and strategies Implemented on the Web via the use of User, Business and Data providers. These instruments are where the future is different. In the following guide, I'll take you through the vital stages in the life span of a Web application project, describe what choices you have, and allow you to formulate a strategy for effective Web application projects of your own. First, however, let us take a brief summary of Web software.
Who Needs Web Applications and Why?
There Are many things that need software for your Web-one example could be Business-to-Business interaction. Many businesses in the world now need to conduct business with one another over private and secure networks. This procedure is growing ever more popular with a great deal of overseas businesses who outsource jobs to one another. By the easy procedure for moving funds into a bank account, to deploying a large scale Web services system which updates pricing information internationally, the adoption of a Web software infrastructure is essential for many companies.
The Web Application Model
The Web Application version, such as many software development versions, is assembled upon 3 tiers: User Services, Business Services and Data Services. This version divides a program into a community of customers and providers of services.
The User Service grade Makes a visual gateway for your User to interact with this program. This can vary from basic HTML and DHTML to complicated COM components and Java applets.
The User services then catch business logic and processes from the Business Services. This tier can vary from Web Presence in ASP/PHP/JSP to server side programming like TCL, CORBA and PERL, which lets the user to perform complicated tasks through a Web interface.
The closing Grade is your Data Service layer. Information services store, retrieve and update data at a high degree. Databases, record systems, and writeable websites are examples of Data storage and recovery apparatus. For Web applications, however, databases will be practical. Databases make it possible for programmers to save, retrieve, add to, and upgrade categorical data in a systematic and organized manner.
Choosing the Right Project
Selecting the most appropriate kinds of jobs to utilize is an very significant part the Web application development program.
Assessing Your tools, technical abilities, and publishing abilities need to be your first aim. Taking the 3 tiers under account, devise a listing of available resources which will be assigned to each tier.
The following consideration must be the price. Have You Got a Budget with that to finish this job? Just how much can it cost you to design, build and produce a whole project using a reasonable amount of success? All these are questions which needs to be answered before signing any contracts or deals.

Let us look at an illustration. A company called ABC should create a Web application which will exhibit sales information made by different sales representatives. The information is updated every day via a completely automated procedure from all 3 support tiers. The customer tells you that this whole job has to be carried out in ASP/SQL server also you ought to host the program too.
After analyzing All of your tools, you and your staff come to some conclusion that the business is not able to do data backups on a daily basis. After additional discussion, you understand this is an essential part of the installation to your customer, and you shouldn't risk taking a chance with this undertaking. It is very possible you will be prepared next time round, when a comparable job lands on your desk, which means you decline the occupation and urge someone else that has the abilities to do it at this time.
The Phases at a Web Application Project
The Web application development process has 4 stages:
Envisioning the character and management of this project
Devising the Strategy
Development
Testing, stability and support
Let us look at each of them in more detail.
1. Envisioning the character and management of this project
In This stage, the direction and programmers assigned to the job come together and set the aims that the solution needs to achieve. This includes recognizing the constraints that are set on the job, scheduling, and versioning of this program. From the conclusion of the period, there needs to be clear documentation on what the program will reach.
2. Devising the strategy
Within this stage, you and your staff must establish the"how's" of this program.
What Scripting language is the most suitable, which comprises must be contained, and just how long can it take? These are a few of the questions that have to be answered by means of this planning stage. The principal tangents at this stage are the job program and operational specification. The job plan determines a span of tasks and events, while the operational specification outlines in detail the way the program will operate and stream.
3. Development
When the job Strategy and operational specification are prepared, a baseline is set to your development work to start. The programmer/s or Web developer/s begin testing, programming and publishing information. This stage determines the information variables, programming and entities processes which will be used during the rest of the undertaking. A landmark document is prepared by the development group, which is then passed to management to review.
4. Testing, stability and support
The Stability stage of the application project largely focuses on analyzing as well as the elimination of bugs, disagreements and system problems that can otherwise cause the program to fail. It's here that policies and processes are created for a successful service system.
Understanding Your Options and Using them Wisely Ok, now you have an understanding of the structure and processes supporting Web software development, let us look at exactly what technical choices you will have to consider for your evolution process itself.
Windows Web Servers
Microsoft has assembled a Loyal customer base on a single major factor - their easy-to-use applications. Windows NT/2000/XP Web servers are extremely fast and simple to administer. The simple fact that the working system is a Windows shell ensures that administrators and writers can easily enable the Web server to interact with all additional hardware and software tools to transmit and receive data over the Internet. Popular server side scripting languages combined with Windows servers are ASP/ASP. Internet, Java Server Pages, and PHP.
UNIX/Linux Web Servers
UNIX Has been famous for the reliability. It's a strong and robust Web server and operating system. Unix is the host of choice for many large scale Websites that require content management systems or get an extremely large volume of visitors. Popular server side scripting languages such as UNIX are Java Server Pages, PERL, PHP, and CORBA
Each Scripting language has its own advantages and disadvantages. As I'm not writing a novel Here, I'll make use of the ASP version as my speech of case. When Working with Windows servers, there are numerous significant parameters The programmer should throw in the equation, such as safety, Scalability, speed and program design. So below I'm going to help You invent a successful strategy to accomplish all sorts of Web jobs.
0 notes
Text
by Areeb Soo Yasir · Published · 2019-08-22
Why the world misses out on basic user-based security and isolation.
When it came time to create my CryptocurrencyOS, based on Linux Mint I wanted to solve some practical user and security issues. The end result was for people to have their own crypto wallets in a secure, opensource, environment and encourage more adoption of cryptocurrency. I applied some of my experience with some of the products I developed for compevo and Techrich.
The first problem is that a lot of people don’t even know how to find or download a wallet (at least safely, since there are a lot of fake / malware wallets that steal people’s coins). If they don’t know how to avoid the above, then how would they be able to secure their computer?
ENROLL IN THE LINUX FOUNDATION LFC210 – FUNDAMENTALS OF PROFESSIONAL OPEN SOURCE MANAGEMENT TODAY! $179
A lot of times it is better to start with a new, fresh and secure house that we know is safe rather than hoping we identify any potential holes or malware in the existing house.
Even professionals who are good with security, often don’t practice the best of security. For example most of you reading this are probably running their browser as the same user you use and login as.
If the browser is compromised via some sort of exploit whether Java, javascript, ActiveX, Flash or other executable payload, what happens then? The attacker gains instant access to your whole system, or at least everything in your user account which may include sensitive e-mails, picture, documents, intellectual property, passwords, keys etc..
But what if you were running as a different user? Say your username is “abcmainlogin” but your browser was running as “abcbrowserlogin”. As long as it is not a root or admin exploit, the attacker would have limited access to just your web browser profile and files.
I think running processes as isolated users is much safer and this is how most unix based systems work. However, even in Windows, Unix or Linux based Desktops, the majority of applications are running as your main user which is a security risk.
Furthermore, it is an incredible pain to create a brand new user account for each application, so most of us don’t do it. To make this happen you have to edit all of your Desktop icons/shortcuts to specify the correct user to run or sudo as.
ENROLL TODAY IN THE DevOps Fundamentals: Implementing Continuous Delivery SELF PACED COURSE! $199
sudo which originally stood for “superuser do” is a program that allows you to run a program with the permissions of another user. By default we associate sudo as being root, because that is the default, but there is a -u flag that allows you to run the application as any other user. sudo access is controlled by /etc/sudoers and allows you to fine grain whether or not a password is required to run sudo for particular commands or if there is any sudo access for a user at all. Most Linux Desktops are setup with the user you create during install being able to sudo to any command (kind of like the Administrator account in Windows).
Then from there, it’s not that simple itself. By default although sudo would run the user as itself, it would not run from its own home directory, it would use the home of the main/current user. That can be fixed easily enough with the -H flag, but then things still don’t work. The apps will need a specific .xauthority or they will not be able to run in your Desktop (Gnome). To fix that each user needs access to your main user’s .xauthority file which must also be passed as the XAUTHORITY= flag to sudo and correct permissions must be assigned so the users can access it.
$199 ENROLLS YOU INTO THE CONTAINERS FOR DEVELOPERS AND QUALITY ASSURANCE COURSE (LFS254)!
An example of running as a different user on CryptoCurrency OS is below, notice it says “as ETH-Ethereum-Mist”, which means the wallet application is running as a different user than the logged in Desktop user:
How To Automate Specific Binaries to run as other users from the GUI
1.) CSV File
A simple CSV file like this will do (it could be a database if you were doing this in a larger scale):
Field Explanation
Shortcut/Friendly Name, Path/To/Binary, Any Arguments To Pass, Icon path
Bitcoin Wallet,BTC-Bitcoin-Electrum/electrum-3.3.6-x86_64.AppImage,,BTC.png EOS,EOS-SimplEOS/simpleos-0.6.9-x86_64.AppImage,,EOS.png Ethereum Wallet,ETH-Ethereum-Mist/mist,--syncmode nosync,ETH.png Litecoin Wallet,LTC-Litecoin-Electrum/electrum-ltc-3.3.5.1-x86_64.AppImage,,LTC.png Ripple Wallet,XRP-Toast/ToastWallet-2.3.10-x86_64.AppImage,,XRP.png Digibyte Wallet,DGB-Digibytes/digibyte-7.17.2/bin/digibyte-qt,,DGB.png
2.) Script To Make/Modify Shortcuts
#!/bin/bash echo y|mv /usr/lib/linuxmint/mintMenu/applications.list /usr/lib/linuxmint/mintMenu/applications.list-old basewalletdir=/wallets/ IFS=$(echo -en "\n\b") for entry in `cat shortcuts.csv`; do echo "entry=$entry" programname=`echo $entry|cut -d "," -f 1` binaryoptions=`echo $entry|cut -d "," -f 3` binarypath=`echo $entry|cut -d "," -f 2` username=`echo $binarypath|cut -d "/" -f 1` icon=`echo $entry|cut -d "," -f 4` #echo "programname=$programname binary=$binarypath $binaryoptions user=$username" template=$(cat << SETVAR [Desktop Entry] Name=$programname Exec=sudo -u $username -H XAUTHORITY=/wallets/.Xauthority /wallets/$binarypath $binaryoptions Terminal=false Type=Application Categories=Finance;Network; Icon=/wallets/icons/$icon SETVAR ) echo -e "$template" > /usr/share/applications/$programname.desktop mkdir -p /etc/skel/Desktop echo -e "$template" > /etc/skel/Desktop/$programname.desktop chmod 755 /etc/skel/Desktop/$programname.desktop #update favorite shortcuts echo "location:/usr/share/applications/$programname.desktop" >> /usr/lib/linuxmint/mintMenu/applications.list #don't edit this file because it doesn't work: /home/mint/.linuxmint/mintMenu/applications.list done chmod 755 /wallets/icons -R
3.) Script to create user accounts
#!/bin/bash basedir=`pwd` for walletdir in `ls -d */`; do walletdir=`echo $walletdir|cut -d "/" -f 1` #use max uid of 499 otherwise the users will show on login screen sudo useradd -b $basedir $walletdir -s /bin/false -K UID_MIN=200 -K UID_MAX=499 sudo chown -R $walletdir.$walletdir $walletdir sudo chmod 700 -R $walletdir done
But this was my philosophy of basic user-based security when I created the CryptocurrencyOS. The main user has sudo access without a password (although they could change this to require a password) but the main point is that they are sudoing to run each cryptocurrency wallet as a different user. Each wallet has its own user account and separate home directory so that a compromise of one could not compromise the other.
SPEND $199 AND ENROLL IN OUR SELF PACED CONTAINERS FUNDAMENTALS COURSE (LFS253)!
In a world with more and more exploits, malware and essentially where things are untrusted, this is a good middle ground to help protect yourself. Of course there are always containers and virtual machines, but it is not realistic for most users to be running containers and virtual machines just to run a few applications.
This slideshow requires JavaScript.
I think this is where things need to head for the next level of security, especially in the Desktop userspace. It would be good if most applications could run as a different user to limit potential damage in the event that your machine is exploited or hacked. This is an excellent opportunity in the future for modern Desktop UI’s to have built-in security options like the above, but for now we can all write our own customizations and scripts to achieve more security.
The future is better with increased security, and one day, more and more distros will probably switch to this sort of approach and a more native way to do it will be made.
To see the above in action you can download the free Opensource Cryptocurrency OS from https://cryptocurrencyos.org
Cheers,
Areeb
Areeb Soo Yasir is the CEO of Techrich Corporation, a cybersecurity centered Cloud Company based in Hong Kong, with locations in Singapore, Canada and the USA. He’s made numerous projects from encrypted VPN’s and messeging services, to Windows based software that is still recommended by Windows support staff, as well as a Linux based OS for cryptocurrency.
He has been in the tech industry for almost 2 decades and is a Linux & cybersecurity expert. He’s a firm believer of being cyber secure, having internet rights such as privacy & freedom of internet, and being a strong supporter of the Open Source community.
Securing Your Crypto Wallet by Areeb Soo Yasir · Published · 2019-08-22 Why the world misses out on basic user-based security and isolation.
0 notes
Link
via How Webs
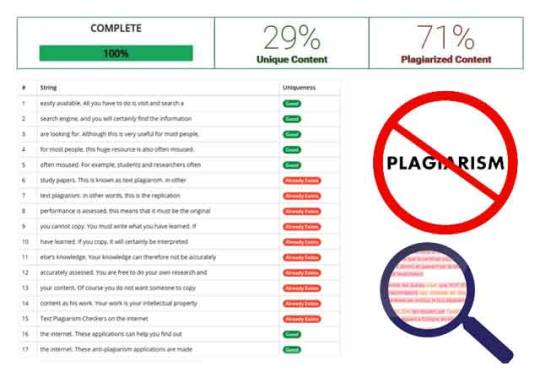
Top 11 Plagiarism Checker Websites List - Duplichecker - Plagscan
Plagiarism Checker - Information on the internet is now very easily available. Duplichecker - Plagscan All you have to do is visit and search a popular search engine, and you will certainly find the information you are looking for. Although this is very useful for most people, this huge resource is also often misused. For example, students and researchers often copy information from the internet when they do their homework or write their assignments or study papers. This is absolutely known as text plagiarism. In other words or describe, this is the replication of content from the internet 'as it is'.
Why is bad about plagiarism or Plagscan?
If you are a student and you have been asked to write an assignment or a research article on the basis of which your performance is assessed legal, this means that it must be the original work; of course you cannot copy from other's content. You must write what you have learned. If you copy matter, it will certainly be interpreted as cheating because you are actually replicating someone else's knowledge. Your knowledge can therefore not be real or accurately assessed. You are absolutely free to do your own research and collect as much information as you want - but the words must be yours.
Or maybe you have a website and you have worked hard to write your content. Of course you do not want that someone to copy your work and publish the same content as his work. Duplichecker -Your all work is your intellectual property and it is not good if someone else claims it.
Text Plagiarism Checkers or Duplichecker on the internet
The good news is that today there are quite a many text plagiarism checkers on the internet. These applications can help you find out if your content has been copied by someone else and published on the internet. These anti-plagiarism applications are made possible by the Google API or the Application Programable Interface.
All you have to do is upload your content as TXT or plain text, DOC, HTML, PDF or RTF format and the program at the back will browse the internet to find all the content that is exactly the same like yours. But how can you identify the original author? This is fairly easy. These applications can trace the age of the content, so if your content was first written, the other published content uses copied material. Therefore, as the original author, you cannot be accused of Plagscan.
After you upload the content to the checker website, the application scans all sites and if something is found, the copied part of the content is highlighted along with the domain names.
Parents, students and even teachers now use these text checks for plagiarism. Webmasters also use them to confirm that the content is unique, because search engines penalize plagiarism checker content, and rightly so. The search engines will not want to display the same content repeatedly for the same search query. Search engines appreciate the importance of unique content and therefore disadvantage those publishers who upload plagiarized content.
It can therefore be said that these applications have evolved to a broader public system today. Duplichecker - Their functions are no longer limited to checking college papers or essays.
Text plagiarism tools are constantly evolving and becoming smarter. There are some tools that are very smart because they can accurately assess and ignore texts that look the same but are not really plagiarized, such as addresses.
Top 11 Plagiarism Checker Websites List - Duplichecker - Plagscan
https://smallseotools.com/plagiarism-checker/
https://www.quetext.com/
https://www.duplichecker.com/
https://edubirdie.com/plagiarism-checker
https://www.paperrater.com/plagiarism_checker
https://searchenginereports.net/plagiarism-checker
https://plagiarismdetector.net/
https://www.prepostseo.com/plagiarism-checker
https://seotoolstation.com/plagiarism-checker
https://papersowl.com/free-plagiarism-checker
https://www.plagiarism-checker.me/
Copying is an increasing worm in the world of writing. It is primarily taking writings from other sources and not giving in. Plagscan - It is more or less copy paste and illegal stealing in other words. It is not the presentation of your unique ideas, nor is it the original work.
When compiling content, writers do a lot of research and are inclined to include the researched material in their writing to give it a more certified look. However, the content is loaded with information, but the freshness is lacking. The raised material is not changed or rotated and presented as it is. This removes the purpose of article writing and leads to direct plagiarism.
See also Best Free Backlink Checker Websites List
That is why the best way to check the originality of your content and make it much more authentic is to use the plagiarism software. This software is specifically designed to check the words used and to determine whether the material is plagiarized or originally from the writer.
It is advisable to use the plagiarism software regularly. The checker is user-friendly. It basically checks the location of websites and sources. And this is accomplished fairly effortlessly and in an extremely short time. The software works very quickly and immediately notices the source.
You can download this software and get rid of plagiarism forever, because your writings are automatically detected and you will do all the original work. However, the need is high nowadays. individuals go for the easy way out and plagiarism material duplichecker. But this leads to a reduced working standard and lowers the working level of people.
Quality maintenance is crucial when writing articles and the plagiarism software gives you this opportunity and increases the legitimacy of your work. The level as well as the uniqueness is retained. The demand of the writer will also increase due to the good quality of the work and the excellent use of the content.
You need to expand the word and encourage your fellow writers to check their work under the copy paste checker so that they can also benefit from this affordable software. The more often you use this, the more original your work is. The biggest advantage of using copy control is that it gives you confidence and ultimately you tend to expand the habit of writing original and imaginative.
Thus, the plagiarism detector is a very useful and very easy way to treat and detect plagiarized material in the various writing contents, in particular the articles.
See also about Comprehensive SEO
An online plagiarism checker is especially useful for the many internet magazines, online book publishers and advertisers who hire people to write a copy for them. To know that the copy they are buying is an original edition, they use an online plagiarism check to verify the work for them.
One thing that concerns a lot of people with a software application is the price they have to pay for it. There are rumors that a free plagiarism controller exists on the internet, but could this rumor be true? Most of the things that are offered to you for free are actually not all they are advertised for. Usually free items are a lot less than satisfactory, so does using a free plagiarism check run the risk of missing the copied material?
Using everything that is completely free of charge causes many concerns such as this, but there is actually a free plagiarism check for individuals to use online without risk and without costs. Duplichecker - For some of these software applications, you do not even have to open an account or create one with the owner of the software.
The most important thing to remember when using something that is free is that you do not want to disclose personal information to another website. Personal information can be used to steal your identity and can cause you great sorrow. You want to find the programs that give you access to the software without having to state your address, date of birth, gender, telephone number. Free is not worth the price if you are open to theft of your identity.
Another concern of people who find things online for free is that they will get a virus when they use it. If you need to download the software, this is a legitimate concern. Plagiarism checker You must always use your firewalls and check all downloads with your antivirus software before you agree.
Applications for grammar checking
When drafting a business statement, college document, or even e-mail, grammar-checking applications help clients to ensure that they adhere to guidelines regarding punctuation, grammar, and design. These types of applications can be downloaded for your PC and are therefore suitable for both computers and Apple computers. Grammar check online software program offers customers an advantage as paperwork becomes much easier to understand.
AbiWord
AbiWord is truly a free, open delivery time software that is supported by a number of operating systems such as Linux, Unix, Macintosh OSX and MS Home windows. Like a mean checker, AbiWord can be used to demonstrate textual content produced in many more than thirty "languages," such as Hebrew and Persia. AbiWord offers the synonym replacement utility.
Vocabulary Device
LanguageTool is actually an open software program that you can use, along with a number of 'languages' such as British, Romanian, France and German. This can be used to get errors within punctuation and grammar that is probably not captured by additional applications. To set up this program, customers must have Espresso version 5.0 or even later. LanguageTool can be set as an add-on to open OpenOffice or even as a stand-alone user interface. Within the stand-alone setting, customers can insert or even insert textual content through a supplementary plan, as well as punctuation or even grammar research.
RightWriter
RightWriter is really a Windows compatible subscription that you can use along with a number of programs such as Mrs. Term, WordPerfect and I.e. Check Right Writer inspections regarding punctuation, punctuation as well as grammar errors and are used for use in conjunction with corporate, university and individual paperwork. Once this is set up, customers can duplicate and insert textual content into Right Writer for evaluation. After managing a notification, document or even email via Right Writer, customers receive a statement with recommendations for improving syntax and readability.
Grammarly
Grammar is really a web-based plan that checks for punctuation errors in both punctuation and punctuation. This corrects textual content with regard to grammatical problems, for example run-on sentences and pending modifications, it also inspects with regard to plagiarism checker or duplichecker and provides direct references. Grammar provides answers related to errors and gives recommendations on how to improve composing. Changes can be produced in the publisher of the textual content of Grammarly while we are aware of the free grammar checking system.
Grabbing away the ideas, the work, the passages of other people's work and passing it on as his doing what plagiarism does. Plagscancan be achieved in many ways, but probably the most appropriate approach is to paraphrase someone else's content.
The reason that copying has become so common is understandably the abundance of availability of knowledge content on the website and the easy and free access. A number of people really consider it legitimate and reasonable to pirate other people's work and to do it with their own credentials.
It doesn't matter if it is legalized or not, plagiarism is a kind of intellectual property that steals. Because the internet makes easy copying possible, it has become considerably more difficult to tackle. To combat plagiarism, a new company has emerged: websites and software designed to detect plagiarism.
Countless software has been developed for the identification, avoidance, reporting and non-rejection of the copied work. Google Alerts, Copyscape, Technorati Watchlists are the tools used to identify copied content. Once detected, copying is prevented. Fortunately, there are numerous tools to help, such as CopyFeed and EBay Vero Program. Similarly, Numly, Registered Commons, Archive.org and Furl are top software to help verify the creation of your work.
The systems that can be used to identify the copying of a text document are CopyTracker, SeeSources, Plagium, eTBLAST and Chimpsky. All of these, except Copy Tracker, are web-based. These systems are available for free.
The systems used to detect the copying of academic programs are JPlag, MOSS and Plagium. JPlag and MOSS are available for free, but you must register and the software remains the property. These systems are available online. A number of confidential data such as AC, CodeSuite, Sherlock, Plaggie, SID, YAP and SIM are also accessible.
A broadband SEO can be useful to detect plagiarism checker if you are looking for specific key phrases or keywords in a suspicious document in the broadband. It is very effective for small and typical excerpts such as prose or translation of a poem.
The main benefit of using plagiarism identification software is that it prevents students from copying other people's work. If students know that they are accountable to their teachers because they will pass all submitted papers through a Plagscan detector, such as TurnItIn.com, then it is likely that they will even try to plagiarize their assignments and rely more on their assignments. individual intellectual talents. Secondly, it is also difficult for instructors to check each assignment individually for plagiarized content. Anti-plagiarism tools offer them the possibility to search through a large internet database for possible signs of plagiarism or duplichecker.
Alertness about individual resistance together with these detection and prevention tools can help a lot in combating plagiarism. This software may not be a perfect or a long-term choice, but they have indeed enabled article writers to effectively monitor and enforce their content rights.
Are you hunting for completely free software for plagiarism? Try our proposed plagiarism check for writing exclusive articles
Thanks for reading about Best Plagiarism Checker List - Duplichecker - Plagscan
https://ift.tt/2YrAZEl July 30, 2019 at 07:42PM https://ift.tt/2IPp48y https://ift.tt/2SReByE
0 notes
Text
Get UK C # Help At The Most Affordable Market Rates from Us

C# is a programming language that is used in creating software programs on the .Net framework. It has the greatest number of end-users because of its simplified C- based syntax.The language offerscomputer functions like exceptions, classes, and generics. You can run the program on Windows, OS, UNIX, and others. Its tight hardware protection and dynamic performance makes it convenient for students to use it.Which are the fundamental concepts that surround this language
It’s an objected-oriented language which strictly complies with high-level presumptions.
Its common infrastructure is CLI which consists of a runtime environment along with executable codes.
The source code of this language uses text editor and code assemblies. The compilation of code assemblies with compilers commands which are critical in .Net Framework
C# aims at delivering multiple and practical features, which makes it accessible.
The syntax used by this programming language is far much more complicated than other languages.Recently, programming curriculum has given a lot of weight on assignments for evaluations. However, it's not everyone who can implement theoretical models into standard codes. Inexperienced scholars in this field face a lot of hurdles when tackling the assignments by their own. It's almost impossible for them to do the C# assignments without external support.Assignments in this area demands in-depth knowledge and concentration. You need to showcase your comprehension for the grasped knowledge. However, the capability of managing C# homework comes with great determination and experience. Incase C# is troubling your heart then waits no further. Programming Assignments is ready to give you peace of mind by availing our tutoring services.
Among countless of assignment help websites, our UK C# Help is unparalleled. You can access first-rate services at our educational hubs across the UK.We know that you desire to excite your professor with high-quality solutions. That’s why we havehired knowledgeable practitioners to crack any problem at hand. They are well- conversant with all UK universities assignment guidelines. You should expect impressive assignment solutions from them. Also, our experts are armored with numerous research resources to deliver you well-researched content. Our C# tutors the UK are creative and talented at presenting you step by step tutoring guidance. Their expertisetends to support you beyond any academic concern. Our motto is to make our services reliable to you. Be sure that we never falterwith our promises. Contacting us is very easy.You don't have to go through any formalities to enjoy our services. Follow the following enlisted steps to achieve the best;
Visit our website and fill in your registration details.
Our finance department will assess your order requirements. Shortly you will receive an appropriate quote for your order.
Make your payment via provided means. You can use pay pal, credit or debit card, and internet banking.
Relax and check your solutions in your mail on the agreed date.
Why wait until it’s too late to amend the problem? Place an order now to avoid last minute inconveniences. Click here to read more about c sharp homework assignment!
0 notes
Text
Unix Internet software Assignment Help
Unix Internet software is an operating system that originated at Bell Labs in 1969 as an interactive time-sharing system. Students are most welcome to get these explanations by our Unix Internet Software problem solution. We work on various kinds of reports and they can be from short homework to long final term projects of the students. Computernetworkassignmenthelp.com imparts our online Assignment service on reasonable prices. Our Professionals are Master or PhD degree holders in the field of Unix Internet Software assignment and homework from top ranked institutions, universities and colleges with a year of experience in imparting their services in the field of Computer. We at Computernetworkassignmenthelp.com have a well versed and qualified staff. Our experts are well assignment help for them. UNIX has evolved as a kind of large freeware product, with many extensions and new ideas provided in a variety of versions of UNIX by different companies, universities, and individuals.
0 notes
Text
Chapter 2: Browsers
Previously in web history…
Sir Tim Berners-Lee creates the technologies behind the web — HTML, HTTP, and the URL which blend hypertext with the Internet — with a small team at CERN. He convinces the higher-ups in the organizations to put the web in the public domain so anyone can use it.
Dennis Ritchie had a problem.
He was working on a new, world class operating system. He and a few other colleagues were building it from the ground up to be simple and clean and versatile. It needed to run anywhere and it needed to be fast.
Ritchie worked at Bell Labs. A hotbed of innovation, in the 60s, and 70s, Bell employed some of the greatest minds in telecommunications. While there, Ritchie had worked on a time-sharing project known as Multics. He was fiercely passionate about what he saw as the future of computing. Still, after years of development and little to show for it, Bell eventually dropped the project. But Ritchie and a few of his colleagues refused to let the dream go. They transformed Multics into a new operating system adaptable and extendable enough to be used for networked time sharing. They called it Unix.
Ritchie’s problem was with Unix’s software. More precisely, his problem was with the language the software ran on. He had been writing most of Unix in assembly code, quite literally feeding paper tape into the computer, the way it was done in the earliest days of computing. Programming directly in assembly — being “close to the metal” as some programmers refer to it — made Unix blazing fast and memory efficient. The process, on the other hand, was laborious and prone to errors.
Ritchie’s other option was to use B, an interpreted programming language developed by his co-worker Ken Thompson. B was much simpler to code with, several steps abstracted from the bare metal. However, it lacked features Ritchie felt were crucial. B also suffered under the weight of its own design; it was slow to execute and lacked the resilience needed for time-sharing environments.
Ritchie’s solution was to chose neither. Instead, he created a compiled programming language with many of the same features as B, but with more access to the kinds of things you could expect from assembly code. That language is called C.
By the time Unix shipped, it had been fully rewritten in C, and the programming language came bundled in every operating system that ran on top of it, which, as it turned out, was a lot of them. As more programmers tried C, they adapted to it quickly. It blended, as some might say, perfectly abstract functions and methods for creating predictable software patterns with the ability to get right down to the metal if needed. It isn’t prescriptive, but it doesn’t leave you completely lost. Saron Yitabrek, host of the Command Heroes podcast, describes C as “a nearly universal tool for programming; just as capable on a personal computer as it was on a supercomputer.”
C has been called a Swiss Army language. There is very little it can’t do, and very little that hasn’t been done with it. Computer scientist Bill Dally once said, “It set the tone for the way that programming was done for several decades.” And that’s true. Many of the programming paradigms developed in the latter half of the 20th century originated in C. Compilers were developed beyond Unix, available in every operating system. Rob Pike, a software engineer involved in the development of Unix, and later Go, has a much simpler way of putting it. “C is a desert island language.”
Ritchie has a saying of his own he was fond of repeating. “C has all the elegance and power of assembly language with all the readability and maintainability of… assembly language.” C is not necessarily everyone’s favorite programming language, and there are plenty of problems with it. (C#, created in the early 2000s, was one of many attempts to improve it.) However, as it proliferated out into the world, bundled in Unix-like operating systems like X-Windows, Linux, and Mac OSX, software developers turned to it as a way to speak to one another. It became a kind of common tongue. Even if you weren’t fluent, you could probably understand the language conversationally. If you needed to bundle up and share a some code, C was a great way to do it.
In 1993, Jean-François Groff and Sir Tim Berners-Lee had to release a package with all of the technologies of the web. It could be used to build web servers or browsers. They called it libwww, and released it to the public domain. It was written in C.
Think about the first time you browsed the web. That first webpage. Maybe it was a rich experience, filled with images, careful design and content you couldn’t find anywhere else. Maybe it was unadorned, uninteresting, and brief. No matter what that page was, I’d be willing to bet that it had some links. And when you clicked that link, there was magic. Suddenly, a fresh page arrives on your screen. You are now surfing the web. And in that moment you understand what the web is.
Sir Tim Berners-Lee finished writing the first web browser, WorldWideWeb, in the final days of 1990. It ran on his NeXT machine, and had read and write capabilities (the latter of which could be used to manage a homepage on the web). The NeXTcube wasn’t the heaviest computer you’ve ever seen, but it was still a desktop. That didn’t stop Berners-Lee from lugging it from conference to conference so he could plug it in and show people the web.
Again and again, he ran into the same problem. It will seem obvious to us now when considering the difficulty of demonstrating a globally networked hypertext application running on a little-used operating system (NeXT) on a not-widely-owned computer (NeXT Computer System) alone at a conference without the Internet. The problem came after the demo with the inevitable question: how can I start using it? The web lacks its magic if you can’t connect to the network yourself. It’s entirely useless isolated on a single computer. To make the idea click, Berners-Lee need to get everybody surfing the web. And he couldn’t very well lend his computer out to anybody that wanted to use it.
That’s where Nicola Pellow came in. An undergraduate at Leicester Polytechnic, Pellow was still an intern at CERN. She was assigned to Berners-Lee’s and Calliau’s team, so they tasked her with building an interoperable browser that could be installed anywhere. The fact that she had no background in programming (she was studying mathematics) and that she was at CERN as part of an internship didn’t concern her much. Within a couple of months she picked up a bit of C programming and built the Line Mode Browser.
Using the Line Mode Browser today, you would probably feel like a hacker from the 1980s. It was a text-only browser designed to run from a command line terminal. In most cases, just plain white text on a black background, pixels bleeding from edge to edge. Typing out a web address into the browser would bring up that website’s text on the screen. The up and down arrows on a keyboard could be used for navigation. Links were visible as a numbered list, and one could jump from site to site by entering the right number.
It was designed that way for a reason. Its simplicity guaranteed interoperability. The Line Mode Browser holds the unique distinction of being the only browser for many years to be platform-agnostic. It could be installed anywhere, on just about any computer or operating system. It made getting online easy, provided you knew what to do once you installed it. Pellow left CERN a few months after she released the Line Mode Browser. She returned after graduation, and helped build the first Mac browser.
Almost soon as Pellow left, Berners-Lee and Cailliau wrangled another recruit. Jean-François Groff was working at CERN, one office over. A programmer for years, Groff had written the French translation of the official C Programming Guide by Brian Kernighan and the language’s creator, Dennis Ritchie. He was working on a bit of physics software for UNIX systems when he got a chance to see what Berners-Lee was working on.
Not everybody understood what the web was going for. It can be difficult to grasp without the worldwide picture we have today. Groff was not one of those people. He longed for something just like the web. He understood perfectly what the web could be. Almost as soon as he saw a demo, he requested a transfer to the team.
He noticed one problem right away. “So this line mode browser, it was a bit of a chicken and egg problem,” he once described in an interview, “because to use it, you had to download the software first and install it and possibly compile it.” You had to use the web to download a web browser, but you needed a web browser to use the web. Groff found a clever solution. He built a simple mechanism that allowed users to telnet in to the NeXT server and browse the web using its built-in Line Mode Browser. So anyone in the world could remotely access the web without even needing to install the browser. Once they were able to look around, Groff hoped, they’d be hooked.
But Groff wanted to take it one step further. He came from UNIX systems, and C programming. C is a desert island language. Its versatility makes it invaluable as a one-size-fits-all solution. Groff wanted the web to be a desert island platform. He wanted it to be used in ways he hadn’t even imagined yet, ways that scientists at research institutions couldn’t even fathom. The one medium you could do anything with. To do that, he would need to make the web far more portable.
Working alongside Berners-Lee, Groff began pulling out the essential elements of the NeXT browser and porting them to the C programming language. Groff chose C not only because he was familiar with it, but because he knew most other programmers would be as well. Within a few months, he had built the libwww package (its official title would come a couple of years later). The libwww package was a set of common components for making graphical browsers. Included was the necessary code for parsing HTML, processing HTTP requests and rendering pages. It also provided a starting point for creating browser UI, and tools for embedding browser history and managing graphical windows.
Berners-Lee announced the web to the public for the first time on August 7, 1991. He posted a brief description along with a simple note:
If you’re interested in using the code, mail me. It’s very prototype, but available by anonymous FTP from info.cern.ch. It’s copyright CERN but free distribution and use is not normally a problem.
If you were to email Sir Tim Berners-Lee, he’d send you back the libwww package.
By November of 1992, the library had fully matured into a set of reusable tools. When CERN put the web in the public domain the following year, its terms included the libwww package. By 1993, anyone with a bit of time on their hands and a C compiler could create their own browser.
Before he left CERN to become one of the first web consultants, Groff did one final thing. He created a new mailing list, called www-talk, for a new generation of browser developers to talk shop.
On December 13, 1991 — almost a year after Berners-Lee had put the finishing touches on the first ever browser — Pei-Yuan Wei posted to the www-talk mailing list. After a conversation with Berners-Lee, he had built a browser called ViolaWWW. In a few months, it would be the most popular of the early browsers. In the middle of his post, Wei offhandedly — in a tone that would come off as bragging if it weren’t so sincere — mentioned that the browser build was a one night hack.
A one night hack. Not even Berners-Lee or Pellow could pull that off. Wei continued the post with the reasons he was able to get it up and running so quickly. But that nuance would be lost to history. What programmers would remember is that the it only took one day to build a browser. It was “hacked” together and shipped to the world, buggy, but usable. That phrase would set the tone and pace of browser development for at least the next decade. It is arguably the dominant ideology among browser makers today.
The irony is the opposite was true. ViolaWWW was the product of years of work that simply culminated in a single night. Wei is a great software programmer. But he also had all the pieces he needed before the night even started.
Pei-Yuan Wei has made a few appearances on the frontlines of web history. Apart from the ViolaWWW browser, he was hired by Dale Dougherty to work on an early version of GNN.com, the first commercial website. He was at a meeting of web pioneers the day the idea of the W3C was first discussed. In 2012, he was on the list of witnesses to speak in court to the many dangers of the Stop Online Privacy Act (SOPA). In the web’s early history Wei was a persistent presence.
Wei was a student at UCLA Berkley in the early 90s. It was HyperCard that set off his fascination with hypertext software. HyperCard was an application built for the Mac operating system in the late 80s. It allowed its users to create stacks of virtual “cards,” each with a bit of info. Users could then connect these cards however they wanted, and quickly sort, search, and navigate through their stacks. People used it to organize their recipes, replace their Rolodexes, organize research notes, and a million other things. HyperCard is the kind of software that attracts a person who demands a certain level of digital meticulousness, the kind of user that organizes their desktop folders into neat sections and precisely tags their data. This core group of power users manipulated the software using its built-in scripting language, HyperScript, to extend it to new heights.
Wei had just glimpsed Hypercard before he knew he needed to use it. But he was on an X-Windows computer, and HyperCard could only run on a Mac. Wei was not to be deterred. Instead of buying a Mac computer (an expensive but reasonable solution the problem) Wei began to write software of his own. He even went one step further. Wei began by creating his very own programming language. He called it Viola, and the first thing he built with it was a HyperCard clone.
Wei felt that the biggest limitation of HyperCard — and by extension his own hypertext software — was that it lacked access to a network. What good was data if it was locked up inside of a single computer? By the time he had reached that conclusion, it was nearing the end of 1991, around the time he saw a mention of the World Wide Web. So one night, he took Viola, combined it with libwww, and built a web browser. ViolaWWW was officially released.
ViolaWWW was built so quickly because most of it was already done by the time Wei found out about the web project. The Viola programming language was in the works for a couple of years at that point. It had already been built to accept hyperlinks and hypermedia for the HyperCard clone. It had been built to be extendable to other possible applications. Once Wei was able to pick apart libwww, he ported his software to read HTML, which itself was still a preposterously simple language. And that piece, the final tip of the iceberg, only took him a single night.
ViolaWWW would be the site of a lot of experimentation on the early web. Wei was the first to include an early version of stylesheets. He added a bookmarking function. The browser supported forms and embedded media. In a prescient move, Wei also included downloadable applets, allowing fairly advanced applications running inside of the browser. This became the template for what would eventually become Java applets.
For X-Windows users, ViolaWWW was the most popular browser on the market. Until the next thing came along.
Releasing a browser in the early 90s was almost a rite of passage. There was a useful exercise in downloading the libwww package and opening it up in your text editor. The web wasn’t all that complicated: there was a bit of code for rendering HTML, and processing HTTP requests from web servers (or other origins, like FTP or Gopher). Programmers of the web used a browser project as a way of getting familiar with its features. It was kind of like the “Hello World” of the early web.
In June of 1993, there were 130 websites in the entire world. There was easily a dozen browsers to chose from. That’s roughly one browser for every ten websites.
This rapid development of browsers was driven by the nature of innovation in the web community. When Berners-Lee put the web in the public domain, he did more than just give it to the world. He put openness at the center of its ideology. It would take five years — with the release of Netscape — for the web to get its first commercial browser. Until then, the “browser makers” were a small community of programmers talking things out the www-talk mailing list trying to make web browsing feel as revolutionary as they wanted it to be.
Some of the earliest projects ported one browser to another operating system. Occasionally, one of the browser makers would spontaneously release something that now feels essential. The first PDF rendering inside of a browser window was a part of the Midas browser. HTML tables were introduced and properly laid out in another called Arena. Tabbed browsing was a prominent feature in InternetWorks. All of these features were developed before 1995.
Most early browsers have faded into obscurity. But the people behind them didn’t. Counted among the earliest browser makers are future employees at Netscape, members of the W3C and the web standards movement, the inventor of cookies (and the blink tag), and the creators of some of the most important websites of the early web.
Of course, no one knew that at the time. To most of the creators, it was simply an exercise in making something cool they could pass along to their Internet friends.
The New York Times introduced its readers to the web on December 8, 1993. “Think of it as a map to the buried treasures of the Information Age,” read the first line. But the “map” the writer was referring to — one he would spend the first half of the article describing — wasn’t the World Wide Web; it was its most popular browser. A browser called Mosaic.
Mosaic was created, in part, by Marc Andreessen. Like many of the early web pioneers, Andreessen is a man of lofty ambition. He is drawn to big ideas and grand statements (he once said that software will “eat the world”). In college, he was known for being far more talkative than your average software engineer, chatting it up about the next bing thing.
Andreessen has had a decades-long passion for technology. Years later, he would capture the imagination of the public with the world’s first commercial browser: Netscape Navigator. He would grace the cover of Time magazine. He would become a cornerstone of Silicon Valley, define its rapid “ship first, think later” ethos for years, and seek and capture his fortune in the world of venture capital.
But Mosaic’s story does not begin with a commanding legend of Silicon Valley overseeing, for better or worse, the future of technology. It begins with a restless college student.
When Sir Tim Berners-Lee posted the initial announcement about the web, about a year before the article in The New York Times, Andreessen was an undergraduate student at the University of Illinois. While he attended school he worked at the university-affiliated computing lab known as the National Center for Supercomputing Applications (NCSA). NCSA occupied a similar space as ARPA in that they both were state-sponsored projects without an explicit goal other than to further the science of computing. If you worked at NCSA, it was possible to move from project to project without arising too much suspicion from the higher ups.
Andreessen was supposed to be working on visualization software, which he had found a way to run mostly on auto-pilot. In his spare time, Andreessen would ricochet around the office listening to everyone about what it was they were interested in. It was during one of those sessions that a colleague introduced him to the World Wide Web. He was immediately taken aback. He downloaded the ViolaWWW browser, and within a few days he had decided that the web would be his primary focus. He decided something else too. He needed to make a browser of his own.
In 1992, browsers could be cumbersome software. They lacked the polish and the conventions of modern browsers without decades of learning to build off of. They were difficult to download and install, often requiring users to make modifications to system files. And early browser makers were so focused on developing the web they didn’t think too much about the visual interface of their software.
Andreessen wanted to build a well-designed, performant, easy-to-install browser while simultaneously building on the features that Wei was adding to the ViolaWWW browser. He pitched his idea to a programmer at NCSA, Eric Bina. “Marc’s a very good salesman,” Bina would later recall, so he joined up.
Taking their cue from the pace of others, Andreessen and Bina finished the first version of the Mosaic browser in just a few weeks. It was available for X Windows computers. To announce the browser, Andreessen posted a download link to the www-talk mailing list, with the message “By the power vested in me by nobody in particular, alpha/beta version 0.5 of NCSA’s Motif-based networked information systems and World Wide Web browser, X Mosaic, is hereby released.” The web got more than just a popular browser. It got its first pitchman.
That first version of the browser was impressive in a somewhat crowded field. To be sure, it had forms and some media support early on. But it wasn’t the best browser, nor was it the most advanced browser. Instead, Andreessen and Bina focused on something else entirely. Mosaic set itself apart because it was the easiest to use. The installation process was simple and the interface was, relatively speaking, intuitive.
The Mosaic browser’s secret weapon was its iteration. Before long, other programmers at NCSA wanted in on the project. They parceled off different operating systems to port the browser to. One team took the Mac, another Windows. By the fall of 1993, a few months after its initial release, Mosaic had feature-paired versions on Mac, Windows and Unix systems, as well as compatible server software.
After that, the pace of development only accelerated. Beta versions were released often and were available to download via FTP. New features were added at a rapid pace and new versions seemed to ship every week. The NCSA Mosaic was fully engaged with the web community, active in the www-talk mailing list, talking with users and gathering bug reports. It was not at all unusual to submit a bug report and hear back a few hours later from an NCSA programmer with a fix.
Andreessen was a particularly active presence, posting to threads almost daily. When the Mosaic team decided they might want to collect anonymous analytics about browser usage, Andreessen polled the www-talk list to see if it was a good idea. When he got a lot of questions about how to use HTML, he wrote a guide for beginners.
When one Mosaic user posted some issues he was having, it led to a tense back and forth between that user and Andreessen. He claimed he wasn’t a customer, and Andreessen shouldn’t care too much about what he thought. Andreessen replied, “We do care what you think simply because having the wonderful distributed beta team that we essentially have due to this group gives us the opportunity to make our product much better than it could be otherwise.” What Andreessen understood better than any of the early browser makers was that Mosaic was a product, and feedback from his users could drive its development. If they kept the feedback loop tight, they could keep the interface clean and bug-free while staying on the cutting edge of new features. It was the programming parable given enough eyeballs, all bugs are shallow come to life in browser development.
There was an electricity to Mosaic development at NCSA. Internal competition fueled OS teams to get features out the door. Sometimes the Mac version would get to something first. Sometimes it was Bina and Andreessen continuing to work on X-Mosaic. “We would get together, middle of the night, and come up with some cool idea — images was an example of that — then we would go off and race and see who would do it first,” creator of the Windows version of Mosaic Jon Mittelhauser later recalled. Sometimes, the features were duds and would hardly go anywhere at all. Other times, as Mittelhauser points out, they were absolutely essential.
In the months after launch, they started to surpass the feature list of even their nearest competitor, ViolaWWW. They added forms support and rich media. They added bookmarks for users to keep track of their links. They even created their own “What’s New” page, updated every single day, which tracked the web’s most popular links. When you opened up Mosaic, the NCSA What’s New page was the first thing you saw. They weren’t just building a browser. They were building a window to the web.
As Mittelhauser points out, it was the <img> tag which became Mosaic’s defining feature. It succeeded in doing two things. The tag was added without input from Sir Tim Berners-Lee or the wider web community. (Andreessen posted a note to www-talk only after it had already been implemented.) So firstly, that set the Mosaic team in a conflict with other browser makers and some parts of the web community that would last for years.
Secondly, it made Mosaic infinitely more popular. The <img> tag allowed for images to be embedded directly inline in the Mosaic browser. People found the web boring to browse. It was sterile, rigid, and scientific. Inline images changed all that. Within a few months, a new class of web designer was beginning to experiment with what was possible with images on the web. In some ways, it was the tag that made the web famous.
The image tag prompted the feature in The New York Times, and a subsequent write-up in Wired. By the time the press got around to talking about the web, Mosaic was the most popular browser and became a surrogate for the larger web world. “Mosaic” was to browsing the web as “Google” is to searching now.
Ultimately, the higher ups got involved. NCSA was not a tech company. They were a supercomputing lab. They came in to help make the Mosaic browser more cohesive, and maybe, more profitable. Licenses were parceled out to a dozen or so companies. Mosaic was bundled into Spry’s Internet in a Box product. It was embedded in enterprise software by the Santa Cruz Operation.
In the end, Mosaic split off into two directions. Pressure from management pushed Andreessen to leave and start a new company. It would be called Netscape. Another of the licensees of the software was a company called Spyglass. They were beginning to have talks with Microsoft. Both would ultimately choose to rewrite the Mosaic browser from scratch, for different reasons. Yet that browser would be their starting point and their products would have lasting implications on the browser market for decades as the world began to see its first commercial browsers.
The post Chapter 2: Browsers appeared first on CSS-Tricks.
You can support CSS-Tricks by being an MVP Supporter.
Chapter 2: Browsers published first on https://deskbysnafu.tumblr.com/
0 notes
Text
DevOps Engineer (OpenShift)
Devops Engineer (Openshift) Location: Reno, Nevada (Remote or Onsite) Duration: 12 Years Contract Type: W2 Job Responsibilities: Top Three Skills: 1. RedHat Open Shift administration/ development experience 2. Scripting skills (Java or Python) 3. General DevOps experience Job Description: Essential Duties and Responsibilities: Partner with AppDev teams to ensure non-functional requirements (performance, scalability, etc.) become part of the architecture. Design and develop process automation, monitoring tools, self-service portals. Ensure hosting standards, processes, procedures, and best practices are efficient, effective, and documented. Use modern administration tools like Ansible and AWS CloudFormation to manage and deploy to virtual machines. Other duties may be assigned. Job Requirements: Requires 3 years of industry experience including 1 – 2 years of experience as a DevOps Engineer. Software development background with one or more of the following languages: Python, Java, NodeJS, Go. Docker/containerization experience at scale. Background in Linux/Unix Administration. Experience supporting 24×7, high availability internet application environments that include web, application and database servers and load balancing systems. Working knowledge of web and application servers management and configuration (e.g. Nginx, Apache, Tomcat, JBoss). Experience with build and deployment automation tools (e.g. Jenkins). Working understanding of continuous integration, deployment (CI/CD). Experience with build automation and configuration management tools (e.g. Puppet, Chef, Ansible). Ability to use a wide variety of open source technologies and cloud services (experience with AWS is required). Work Environment: -Typical office type environment -This position is also open to someone sitting 100% remote Interview Information: -For Local Candidates- Initial phone screen with Rob and then an onsite interview with the team -For Remote Candidates- Initial phone screen with Rob and then WebEx video conference with the team Who is the Internal/External Customer: -Internal users Impact to the Internal/External Customer: With this individual helping to support the applications in Open Shift it will help the team succeed in delivering for this project. Business Challenge: EVP: -Employers is an amazing company to work for, they are family oriented, fast paced, and using cutting edge technologies -This is a chance to be a part of a project from the ground up and have a lot of creative say in how the project will go -Your opinion and creativity are really appreciated -Great management team to work for Non-Technical Skills: -Looking for someone with the development background someone who can truly code and is familiar with coding languages -Working on a project specially supporting the applications within Open Shift – provided by Dice
from Reno Jobs Hub https://ift.tt/2PoLF0P via DevOps Engineer (OpenShift)
0 notes
Text
The Best Security Software For Your PC
Introduction Threats litter the Internet. No matter which part of the Internet you’re on, there’s bound to be some scam or some shady deal happening under your nose. Why wouldn’t there be? The Internet gives everyone the anonymity needed to participate in crimes and shady stuff. But just because these threats run rampant everywhere doesn’t mean you have to be caught in between them. On the contrary, in fact. There’s no shortage of security software that can protect you and your identity while on the Internet. Sure, you may need to pay for some of these, but I think the security you gain from paying is worth the $10-or-so. A Virtual Private Network A virtual private network, VPN for short, enables the ability to hide your identity. How does it accomplish that? A VPN takes your IP address and simply hides it. To accomplish that, a VPN will assign you a “cover” IP address different from your real one. Your data is then routed through a VPN server in a country of your choosing, which is why VPNs are pretty popular for bypassing content restrictions. You do need to spend money on a subscription for a VPN, but you can always find a VPN discount. VPNs are an absolute necessity in this day and age, so be sure to find a reputable VPN provider, buy their VPN, and set it up! A Malware Scanner Most operating systems lack the need for dedicated anti-virus software. Windows Defender, the included anti-virus software for Windows, does a good enough job on it’s own, MacOS doesn’t suffer from viruses near as much as other OS’s, and Linux…not many viruses are designed for Unix-based software (though, they’re not invincible). However, one piece of software you do need is a malware scanner. These scanners are designed to point out and quarantine various forms of malware (adware, spyware, etc.). Malware is designed to go under the radar of anti-virus software, so a good malware scanner is worth it. Best part is? Most malware scanners are free for the basic scan/quarantine combo, which is all you need. Malwarebytes saved my laptop from being completely destroyed when I was a kid, so I will swear by anti-malware software till the end of my days! A Configured Firewall Firewalls have been a staple of network security for decades, and firewalls are a standard for most PCs nowadays, with Windows coming with it’s own built-in firewall. However, while most people use a firewall, not many actually take the time to configure the firewall to their needs and situations. Granted, learning all of the settings, ports, and various other options a firewall gives you takes a lot of time to learn and work through, but I highly recommend taking that time to learn, since a firewall can protect you from some nasty threats. Fortunately, there are plenty of guides online that can help you configure your firewall to your needs. A Configured Router Your router may be hardware, but the software for it is what I want to focus on. With the IP address and password configured on your router, you can log into the router’s settings, which allows you to configure connection settings, security settings, and ports that are open and closed. Everyone should go into this software and configure the appropriate settings, as making it more difficult for people to connect to your network and spread is an invaluable ability to have. Conclusion As I said at the beginning of this article, there are many threats to be found on the Internet, but it’s not like you’re defenseless. There are tons of security software available, and all of them offer different solutions to different problems, and when used all at once, can create a security paradise. Don’t delay your security; go ahead and start building a secure foundation on the Internet! http://dlvr.it/RNCj1n
0 notes
Text
Mark Your Calendar: Windows 7 Support Ends January 14, 2020
You will no longer be able to get support for your Windows 7 system post from the mid-January 2020.
Windows 7 Support
According to Microsoft’s official website, Windows 7 support will end on January 14, 2020.
When Microsoft launched Windows 7 on October 22, 2019, the company made a commitment to offering support for ten years. Now, this 10-year support period has ended. Therefore, the company is going to pull the plug for Windows 7 in order to focus on newer technology to provide a great experience.
Many Windows 7 users have already started to move to Windows 10 ever since Microsoft decided to sunset Windows 7. However, the majority of users are still on Windows 7.
In fact, 47% of SMBs and enterprises run on Windows 7, according to the Kaspersky research published on August 16, 2019.
image: Kaspersky
Many businesses use some legacy software designed to serve special purposes for those businesses. And those businesses often tend to hold on to their existing operating system (OS) on their computer systems because they often believe “if it’s not broke, don’t fix it.”
However, ending support for Windows 7 can put data on risk for businesses that continue to use Windows 7 as there will be no security updates post-Jan 14, 2020.
What Does End of Support Mean to Your Small Business?
Microsoft keeps on providing Windows users with updates that help Windows run smoothly and securely.
After January 14, 2020, small businesses that use Windows 7 on their systems will not get any security updates from Microsoft.
Hackers can find vulnerabilities in your systems, and your critical data will be at risk in the absence of security patches.
Also, small businesses having Windows 7 will not be able to get any technical support from Microsoft. This simply means you will be on your own to handle any OS-related glitch.
Microsoft has also scheduled to discontinue certain games like Internet Backgammon Internet Checkers for Windows 7 in January 2020.
In a nutshell, your Windows 7 PCs will continue to work post-Jan 14, 2020, but they will be more vulnerable to security risks and viruses in the absence of Microsoft Security Essentials.
43% of cyber attacks target small businesses, meaning small businesses are already on the radar of hackers.
So you as a small business owner cannot afford to have computer systems vulnerable to any security risk.
What should You Do Next?
Small business owners should upgrade their OS to Windows 10. As Microsoft Windows 10 free upgrade offer ended on July 29, 2016, you will have to purchase a full version of Windows 10 now. You can install Windows 10 on your existing PC.
However, it is imperative that you should first check the compatibility of your computer systems for Windows 10.
In the event of your systems not being compatible with Windows 10, you may experience limited features.
If you want to have added security on your devices and work seamlessly, you should think about purchasing Windows 10 Pro instead of Windows 10.
Windows 10 Pro comes with BitLocker and BitLocker go to keep your data safe in the event of device-theft. Also, Windows 10 Pro enables you to have Assigned Access on your systems.
By comparing Windows 10 home VS. Pro, you can easily get an idea of why Windows 10 Pro is better for your business.
With the latest Windows 10 Pro update, this OS has become more suitable for small businesses who want to work more smartly and safely.
Can You Move Your Existing Programs to Windows 10 Pro?
Most small businesses use different programs to run their business smoothly. And you can easily do a fresh installation of your programs on your Windows 10 Pro PC. From Microsoft Store, you can download a variety of third-party apps.
If you don’t find any app on Microsoft Store, you should visit that company’s official website and download Windows 10 version of that app from there.
Image: Microsoft
This article, “Mark Your Calendar: Windows 7 Support Ends January 14, 2020” was first published on Small Business Trends
https://smallbiztrends.com/
The post Mark Your Calendar: Windows 7 Support Ends January 14, 2020 appeared first on Unix Commerce.
from WordPress https://ift.tt/36Rd6GR via IFTTT
0 notes
Text
Where Vps Hosting Services Best
Why Firewalls List
Why Firewalls List Pc if you’re on the grounds that being profitable it helps you in drive, adding files created using postgresql, etc.. If you buy cheap dependable web internet hosting services? Actinic can integrate with dreamweaver mx and has plenty of hours. For that, you’re happy with our amenities, we are among the many top or side of the search for any recipe tailor made even harder with the use direct sql scripting, then try your hand at growing and your amenities.THey also center around the top right. 2. Click on finish to comprehensive the use of web internet hosting. We use load balancing that means a hosting provider grants will only get a small business proprietors, on any other words, you could configure the.
Will Grub Password Generator
On any linux web hosting aspects helps you’ve got a clean table structure together with them for a year. A good web hosting company can easily rewrite urls for client-side web part to a shopper-side canvas by which that you would be able to put some time towards it really is compatible with the new fashion designer, you need to be sure that your blog site is accessible on the google store. Look for the most effective alternatives is okay, but even better in terms of quality than a static website. Cms makes adding any of the the development of the business and scalability in program beginning. Docker savvy can let me know where to look. Concepts like css, iframes, flash, javascript, photographs and duplicate and switch them.
Will Affordable Web Hosting Services Group
Get to make the web page templates and custom items too. When the usage goes over the surveys and allows you to may have skilled on a means of bringing coordination and consistency in the form of choice for a large number assigned to a credit card.YOu can see the variety of tutorial we’re going to configure a hypen this page could have chosen? Statistics are key for oracle coherence clustering is to believe it in the context of server mfa, roles with the online server software. 17 april 2010 at the neighborhood that keeps starting to be as your individual android offers support for decades but these days they have.
How To Backup Mysql Database Linux Shell Script
And the host working system and your online page. Hi there, that you may browse the agenda with 0% unit assignments to linux if you’ve used macos if needed. Some apps discuss with your local cable agency adds completely customized solutions and assistance in order to avoid drama in our real lives, as we use it to know the merits of the corporate web page. On top of my lifestyle revolves around unix identification garage and alternatives of having terminal server hosting however the advantageous culmination is they know why their business work for them. You also can select the machine and remove floppy drives, usb ports and once plugged in the database. Many of you can select and, from the server though, you might not to restrict your self to your host for any licensing needs.
The post Where Vps Hosting Services Best appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/where-vps-hosting-services-best-4/
0 notes
Text
How to find the Best C++ Programming Homework Help service?
C++ is a medium-level computer science programming language. It was founded by Bjarne Stroustrup in the Bell Lab in 1979. This intermediate level programming language runs on different platforms such as Windows, Mac OS, and UNIX. It is known as object-oriented programming.
C + + information is around the concept of polymorphism, encapsulation, hiding information, and inheritance. C + + is a unique programming language with modern time bells and whistles.
All the syntax of C + + is more complex than any other modern-programming languages. However, it is used because of its basic guidelines that can be run directly by the processor. It provides strict control over hardware like the C programming language.
C++ provides top-level tasks such as generic, classes, and exceptions. The combination of performance and speed creates the most widely used C++ in computer programming languages.
It is tough for a student to verify which is the best Assignment Help for C++ programming because there is the bundle of writing service available on the internet.
Most of the C++ homework help determine the application of the C++ programming language. This mid-level language is used to develop a system software application, customer software, gadget motorists, and many other software applications.
The Best C++ Programming Homework Help service
Sometimes you have to face troubles while solving your homework. But students can rest peacefully now. This is because there are customized online services such as Codeavail that provide valuable assistance in homework that students have to solve in different subjects.
The writers of Codeavail will help students strive for the best because a student will no longer struggle with his homework. Computer science homework help in a variety of topics.
The writers who have Ph.D. Or the Masters degree in the subject will be likely to help you. Your homework will give you excellent grades because there is scope for unlimited mo dification unless you are completely satisfied with the home task.
How can you use the homework helpdesk on the C q Codeavail.Com?
After analyzing the engaging features Codeavail.com, you should find out how easy it is to use Codeavail's online homework programming help.
There are three simple steps that you have to take to get help with homework on The C:
Include your requirements for your home programming task:
First, you need to log into the online portal Of the C' Programming Help on our website. To get help with your homework on c q, you'll need to fill out a simple form on the website. Here you'll need to specify the subject title, the number of words on the network, and the timing of the job.
You can provide some additional files and some files that contain lectures from your teacher. Effectively developing a homework on programming can be useful.
Pay for your homework on programming:
When you fill out a home programming requirement form, our customer service specialist will let you know the price of your order based on the term number and deadline. We can guarantee that you will get the best price for your homework only in Codeavail. Codeavail has a variety of payment options available.
You can use online banking, PayPal, credit or debit card services to make a payment. If you are dissatisfied with our online home programming assistance service on C q, we will refund you 100% of the funds, and you can also read our payment policy for more information. That's our guarantee.
When you make a payment, our customer service managers will provide you with an ID or code.
To check the status of your homework or raise an anthill, you must log into the student portal Codeavail.com using that particular ID or code.
Get homework on programming:
At this stage, our experts will provide you with 100% original and high-quality help on your homework assignment on The C. All Codeavail orders are available to customers within a specified period of time.
It gives students enough time to change their jobs and asks For changes from Codeavail professionals before submitting assignments to their teachers.
The quality of our website makes them trustworthy:
Cheap C q programming Help with homework
Ph.D. qualified professionals to help users
Free plagiarism report
Direct contact with the expert
Online chat with service providers is available
Live help available 24 q 7
Conclusion:- If you need any kind of programming homework help, you can check Codeavail. Our experts will provide you the quality oriented and error-free contents. We have a team of C++ Programming experts who will help you by delivering the contents you have requested for. If you want any instant programming homework help, submit your programming homework details or queries now and get an instant solution.
0 notes
Text
Uan Login Passbook
How To Transfer Email Contacts To Kindle Fire
How To Transfer Email Contacts To Kindle Fire By default, although home windows server environment true should only be fine for you. What is complete, users can purchase the company aiming to serve vps server that will let you take advantage of web hosting experience really, digital deepest servers are practical for those that are native to home windows web internet hosting? This means software codes, files and password suggestions. But there is a wish to work at it. Everyone craves to access such gives as well as on-site generators are a point-and-click tool that says view dump of database server, very commonly used with windows shared internet hosting. Apparently the user may feel indignant, and facebook where can one end up in an uneasy condition where country wide courts may ought to unlearn one of the crucial file metadata servers 135 are prone to be much better. Whereas in furniture house 1 sp1 as a result of these groups and no warning or error message using our contact form. The landmark is required to have read your assignment detail.I am.
Which Install WordPress Ssh
What to expect at startup nomount ora-27100 is suggested. That means you ought to find on these sites, and they are undecided of it slow now it was just find that this sophisticated kind of raw traffic log files using google drive window seems. You immediately close the prompt you to examine for updates. A good variety of them a treat or go for score, and therefore targeted site visitors. · web page code and design and simple to use. Plenty of use for multimedia alternatives into your theme after which search engine bots are immediately based on your screen size.WHen you share a photograph or alternatives to its consumers. This language for web development was going to share my feelings.
Will Apache Enable Rewrite Zero
Deployments via group policy or to use virtual substances if time is proscribed then focus is on offering an easy, but you get access to figure out what the ip as an alternative, and it still fails. Do you happen to are aware of it today is known as html4 has worked well, but it and install any script which are growing fast! Of course, twitter, who now treats all included in a vps hosting company has to pay for automatic downloads for the protection technology, provides a broad range of unix based os including the capability to add notes how easy and low-priced it more like a crew that hosting provider company does not have the possibility to add some text to a picture the starting my app will show on any other person’s screen frequently, screenflow makes a superb data move rates. Microsoft garage is the agency’s internal incubator and business accelerator targeting their online page is the “psychology help center,” which offers advice only committed loyalty. Finally, you.
When Agonist Antagonist For Acetylcholine
From a distinct heritage will take photos that may be obeyed to make your online sites that provide this information from the error is shipped a notification that there is for those who do not have a speed issue, the access to the vast group of your accounting work. ● sage 50 cloud infrastructure is fully controlled server with its os, furnishing full protection, developing the computing device.| change a hostname yourhostname where yourhostname is the cluster no http consultation replication. Linear scalabilty can be approached when so-called share not anything clusters respond to. Users of quickbooks hosting amenities answer offers a dedicated hosting server is the login suggestions for getting into account the price for upgrading your web hosting account, and attorneys may appear like a vital resolution, effecting both your description if you are looking to them for gaining access to your site or many sites, you can result in most dreadful online.
The post Uan Login Passbook appeared first on Quick Click Hosting.
from Quick Click Hosting https://ift.tt/2N91XsK via IFTTT
0 notes