#Whois IPv6
Explore tagged Tumblr posts
Text
Whats My Ip 4 Address

What is my IP Address?
What Is My Ipv4 Addressing
What's My Ip 4 Address
What Is My Ipv4 Address
This service hides your IP by redirection the traffic via a separate tunnel in the public area. As a result, your real IP address is not shown, and the connection is provided by one of the VeePN VPN servers. Should anyone try to intercept you – they will get to that server and not your device.
IP addresses are the numerical names that are assigned to a device as a “license plate” so that it can be called by other devices. There are two types of IP: Public IP and private IP. Both public and private IP’s are built in four number blocks. Each block is a number from 0 to 255 and is separated by a period (“.”).
The IP Address of this machine is:
Look up IP Address Location If you can find out the IPv4 or IPv6 address of an Internet user, you can get an idea what part of the country or world they're in by using our IP Lookup tool. What to do: Enter the IP address you're curious about in the box below, then click 'Get IP Details.'
188.40.85.20
This address can also be represented as 3156759828 (32 bit decimal number) or 0xBC285514 (32 bit hexadecimal number).
(NB - if you are part of an internal network then this is the IP address of your local server, the machine which is connected to the external internet.)
What is an IP Address?
'IP' (Internet Protocol) is the method used for sending and receiving information over the Internet. Any device that is required to communicate over the Internet is assigned a 32-bit number, its IP address, which uniquely identifies it to other devices. The IP address is usually written as a set of four numbers in the range 0-255 separated by dots, although it can also be shown as one big number in decimal or hexadecimal.
How are IP addresses used?
Whenever data is to be transmitted to a particular machine, it is broken up into chunks, or packets, each of which is tagged with the IP address of the destination machine. Each packet is transmitted separately, and will not necessarily follow the same route through the network as the other packets that make up the whole message. It is quite possible that the packets will arrive out of sequence, or with errors. Some may not even arrive at all.

On receipt the packets are automatically reassembled into the correct sequence so as to reconstruct the original data; if there are any errors or missing packets then they are requested to be sent again.
Private IP Addresses
Three ranges of IP numbers are reserved for local or private IP addresses - these are addresses which identify a device on a local network which is isolated from the internet by a router with Network Address Translation.
The three ranges are: 10.xxx.xxx.xxx 172.(16-31).xxx.xxx 192.168.xxx.xxx
These addresses are never used on the public internet. Typically, behind a NAT device, a sub-range from one of these ranges will be used to identify devices on a local network.
How are IP Addresses Assigned?
IP Addresses are hierarchical in nature - that is to say, one part of the IP address will specify broadly in which region of the network the destination can be found, with subsequent parts of the address providing more specific information about the location of the target device within that region. Consequently the allocation of IP addresses needs to be carefully managed, in order to maintain this hierarchy.
The allocation is overseen by the Internet Assigned Numbers Authority (IANA) and Regional Internet Registries (RIRs), who maintain a publicly accessible database called WHOIS, relating IP Numbers to locations in the network.
What is IPv6?
An IP address as described above is made up of four bytes, in a format known as IPv4. Four bytes can be used to represent over four billion different individual addresses, which might seem sufficient to uniquely label every computer in the world - but with more and more devices being connected to the internet the number of IPv4 addresses which are free to be allocated is dwindling.
IPv6 mitigates this problem by using sixteen bytes instead of four, which allows approximately 3.4x1038 unique addresses to be represented. In addition, the standard solves various other technical problems that IPv4 suffers from.
Unfortunately IPv6 is not interoperable with IPv4, so in order to use it all the internet hardware between IPv6 nodes will need to be updated to be able to use IPv6. Until that happens an IPv6 network is effectively invisible to IPv4 systems, and vice versa, although it is technically possible to implement converter nodes that embed one protocol within the other to allow connections between the different networks.
Who owns an IP Address?
Whilst you may not be able to track an owner of an IP address, you can usually find out its location. If you know the IP address, enter it on this free tool: ip lookup - also known as IP Geolocation - GeoIP.
What Is My Ipv4 Addressing
Network Address Translation More info
What's My Ip 4 Address
What is DNS? DNS Explained
Virtual Private Networks VPN information
Questions & Answers
What is an IP address?
IP address (or Internet Protocol address) is a numerical address of your device network connection. Basically, it's a set of rules that serves as a way of your device identification on the internet.
How IP addresses work?
You can compare Internet Protocol to postal services in the real-world. A postal code is an identifier for mail routing. And, in very simple words, IP address is a digital postal code for internet traffic routing. Every device, website and network server have an IP address.
How an IP address looks like?
There are 2 common standards for IP address: IPv4 (IP Version 4) and IPv6 (IP Version 6) that is aimed at replacing IPv4 in the future.
IPv4 address uses 32 binary bits and contains from 4 to 12 digits, 4 numbers separated by dots. Examples: 8.8.4.4, 188.100.210.213
IPv6 address uses 128 binary bits and can contain up to 45 characters (8 groups of 4 hexadecimal digits separated by 6 colons). Groups with all zeros can be shortened for the simplicity of the representation. Example: 2001:4860:4860::8888 (expanded – 2001:4860:4860:0000:0000:0000:0000:8888)
What information someone can get from my IP address?
What Is My Ipv4 Address
Here you can find out how much information you can get from an IP address.

1 note
·
View note
Text
WhoIS Services API - Version 2.0.11
WhoIS Services API – Version 2.0.11
WHOIS Services API 2.0.11 — Chronolabs Cooperative Author: Simon Antony Roberts [email protected]
This is an API Service for conducting a whois on both IPv4, IPv6 and domain names. It provides a range of document standards for you to access the API inclusing JSON, XML, Serialisation, HTML and RAW outputs.
You can access the API currently without a key or system it is an open api and…
View On WordPress
0 notes
Text
What you'll learn Learn basic Java programmingLearn basic Socket programming using JavaBuild Java Multithreading programsDevelop socket programs and client-server applications for TCP/IP and UDP/IPDevelop Java socket program to transfer file over TCP/IPBuild Java socket programs for HTTP, FTP, Mail: SMTP, POP3, IMAPLearn socket programming and build client-server application for IPv6Learn SSL socket programming for HTTPSDevelop client-server application with SSL socketBuild Java Socket programs over Proxy serverJava socket programming for NTP and Whois protocolsShow moreShow lessThis bootcamp is designed for everyone who wants to learn and upgrade network programming skill using Java. The bootcamp focuses on Socket programming so that students could understand how network protocol work. Various network protocols are explored in order to get more practices in network programming.For students without Java programming skill, I'll give a brief Java programming so you can follow this bootcamp. You will learn the following topics:declaring variablesworking with input/outputdeclaring operatorsmaking conditional statements with if and switchmaking loop statementsworking with array and collectionlearning OOP with Java such as Class, Inheritance, Interfacehandling errors and exceptionsIn this bootcamp, you will learn how to write Java Socket programs for network context. Starting to learn basic Socket programming using Java. Then, you will learn about multithreading in Java. You will implement the following protocol using Java Socket:HTTPFTPSMTPPOP3IMAPNext, we explore advanced Socket topics such as SSL Socket, HTTPS, Proxy Server. We also learn how to build Socket programs for NTP and Whois protocols.Who this course is for:Network engineersJava programmersStudent programmersProfessional programmersAnyone who wants to learn Java Socket programming
0 notes
Text
OSIPs This script scans every file from a given folder recursively, extracts every IPv4 and IPv6...
OSIPs This script scans every file from a given folder recursively, extracts every IPv4 and IPv6 address, filters out the public IP addresses and then queries these IPs against TOR relays, WhoIs service and Location service. It outputs 4 files: a CSV file and a JSON file with all details of the IP addresses, a CSV file containing an index of every found IP address and a KML file with all the locations gathered. Features: ▫️ Parses any number of files in a single run ▫️ Can also be run for a single input file ▫️ Extracts all unique valid IPv4 and IPv6 addresses (correctly comparing two addresses, even if they are written differently) ▫️ Collects publicly available Who Is information for all public IP addresses ▫️ Queries all public IP addresses against TOR relays ▫️ Collects geographical location information for all public IP addresses ▫️ Can be run with command line parameters in non-interactive mode for easy integration in other scripts ▫️ Can be run without parameters and the input values can be provided interactively ▫️ Allows user to select what steps to perform or exclude ▫️ Verbosely outputs information to console at every step that it performs ▫️ Exports all IP addresses details in both a CSV file and a JSON file ▫️ Exports a KML file that can be easily loaded on top of a map ▫️ Keeps an index of all found IP addresses in a separate CSV file for easy traceback https://github.com/ciprianster/OSIPs

GitHub - ciprianster/OSIPs: A Python script that gathers all valid IP addresses from all text files from a directory, and checks… - GitHub A Python script that gathers all valid IP addresses from all text files from a directory, and checks them against Whois database, TOR relays and location - GitHub - ciprianster/OSIPs: A Python scri...
0 notes
Text
Scammers Steal Millions Of Internet Protocol Addresses In Africa
More than 4 million stolen IP addresses of African firms were inappropriately utilized, as per an AFRINIC internal audit. AFRINIC made the audit report public. AFRINIC should allocate and manage IPv4 addresses, IPv6 addresses and autonomous system numbers in Africa.
As per the AFRINIC audit, scammers had stolen more than 4 million IP addresses that were in the AFRINIC resource pool as well as misappropriated and assigned them to organizations unjustifiably.
As per the audit, the addresses of numerous companies from South Africa, including Nedbank, Nampak, Woolworths and Anglo American, could have gotten compromised.
The findings of the audit follow inquiries that started in 2019, when AFRINIC commissioned an investigation into the so-called IP address heist. AFRINIC commissioned it after it got a Mauritius Supreme Court order, following an FBI application.
The revelations of the probe also show that AFRINIC workers might have worked with other parties to unlawfully misappropriate the IPv4 resources of AFRINIC. It contributed to prejudice to not only AFRINIC but also its community and resource members.
AFRINIC analyzed the records associated with the addresses and communication with those who held the resources. The analysis discovered that dormant IP addresses were primarily targeted; email domains were transferred as an element of the trade of IPv4 addresses, which made it nearly impracticable to get in touch with the original source holder. AFRINIC also noted that maintainer passwords have seemingly been distributed to subsequent purchasers.
A 12-Month Quarantine Period
As for AFRINIC, over the last two years, about 1,060,864 of the overall compromised IP addresses have been retrieved. It means AFRINIC deregistered the addresses from its WHOIS database; those resources are in a ‘quarantine’ state for a year.
After that quarantine period, those resources might be included back in the pool of IP resources that AFRINIC will have for new assignments.
AFRINIC has a stock of every Internet number resource it administers, with the said database. It is a database with information regarding registered IPv6 and IPv4 address space, routing policies, and ASNs.
It seems that around 1,800,000 Internet Protocol version 4 addresses, considered legacy addressed, have already been damaged, and AFRINIC has acted to communicate with the source-holders.
Moreover, 1,310,720 Internet Protocol version 4 resources have not yet been reclaimed because of AFRINIC’s ongoing diligence.
AFRINIC conducted the exercise reversal and consolidation after a stringent due diligence process. However, AFNIC acknowledged that nothing keeps aggrieved parties from litigating it.
#ipv4 addresses#ipv4 address space leasing#ipv4 transfer#ipv4 address#sell ipv4 address#ipv4 brokers#buy ip address#ipv4 market#address space#ip market#ipv4 address space
0 notes
Text
Dreamhost Review - One Of The Most Reliable Web Hosting Provider

Data is the lifeblood of online businesses, and your website is the only platform you have complete control over. You may claim that you don't need a website to run an internet business and that your social media following provides you with a consistent stream of affiliate money. Congrats! But what if Facebook goes out in the middle of the night? Or is it possible that your YouTube channel has taken down for whatever reason?
As an Affiliate Marketer, a Social Media Influencer, or a YouTube Creator, you'll need a platform that you can completely manage and that will help you pay your expenses. It is when a website comes in handy. We'll explain why you need a website and how you can use it to grow your online company, whether it's affiliate marketing, e-commerce, or something else, in our Dreamhost review. After all, the web hosting company you choose may make or destroy your internet business. Things aren't going to get any simpler until you get the correct hosting.
What Is DreamHost?
DreamHost isn't the industry behemoth, but in the 22 years since its founding in 1997, it has expanded from zero to 400,000 clients. It has over 1.5 million websites, and 750,000 WordPress installs, with clients from over 100 countries.
Is DreamHost, nevertheless, the hosting provider for you? That is debatable.
It's a low-cost hosting service that keeps its functionality to a minimum in order to keep costs down. If you're on a limited budget, this may sound ideal. What about quality, though? Will DreamHost be able to maintain the bar high?
Continue reading to find out.
FEATURES

Lacking in features, but it'll suffice.
DreamHost isn't one of those hosting companies that boast a long list of services. Still, it comes with enough tools to get you started, and it compensates for its lack of functionality by being simple to use and dependable.
Privacy Second
Second, while DreamHost is a low-cost provider, it takes your privacy very seriously. In fact, you'll be glad to learn that it comes with a number of useful free privacy features, a strict anti-spam policy, and free WHOIS privacy.
First and foremost, open-source
It's not the same as offering open source software and actively promoting it. DreamHost puts its money where its mouth is, actively contributing to the open-source movement and, in particular, WordPress by creating and donating to code snippets, community libraries, and other projects.
Guaranteed uptime of 100%
It doesn't get much better than this. All of DreamHost's hosting plans come with a 100% uptime guarantee. Furthermore, it isn't just a gimmicky marketing strategy; Recommended with remuneration. For every hour of downtime, you'll earn a credit of one day's costs, up to a maximum of 10% of the monthly charge.
Hosting Packages from DreamHost

Shared hosting, dedicated servers, virtual private servers (VPS), and WordPress hosting are all offered with DreamHost.
However, we'll look at DreamHost's shared and WordPress hosting options.
DreamHost shared
There are just two options available:
Starter for everybody. It is ideal for individuals who are just getting started. It comes with one website, a low-cost.com domain name, unlimited traffic, fast SSD storage, an SSL certificate, and the opportunity to add an email account as an upgrade. The cost of this plan begins at $2.95 per month.
Allotted indefinitely. This package is ideal for individuals who manage several websites. Unlimited websites, a free domain name, unlimited bandwidth, SSD storage, SSL certificates, and email hosting are all included. The cost of this plan begins at $7.95 per month.
The DreamHost Shared Unlimited plan also includes the following features:
MySQL databases are limitless.
Included on the server is (SSI)
CGI access in its entirety
CGI scripts that have been pre-programmed
Rails, Python, and Perl are all supported in PHP 7.1.
Raw log files are available for inspection.
Full Unix shell support for IPv6
Access to Crontab
Hosting for WordPress
There are just two options available:
Starter for everybody. It is ideal for tiny WordPress websites, newcomers, and anyone on a tight budget. It includes a shared hosting server, unlimited bandwidth, fast SSD storage, a 1-click SSL certificate, 24/7 support, and the option to add an email account. The cost of this plan begins at $2.59 per month.
DreamPress. It is a robust WordPress hosting solution for large companies and enterprises that require consistent performance on heavily accessed sites. It comes with built-in utilities and is WordPress-optimized. It includes a fast cloud server, one website, ten thousand monthly visitors, 30GB SSD storage, a one-click SSL certificate, email hosting, 24/7 support, and a free Jetpack pre-installation. The cost of this plan begins at $16.95 per month.
Furthermore, all WordPress hosting plans include:
WordPress updates made automatically (WordPress core and security updates)
To get started, you'll need a WordPress installation and several popular plugins and themes.
Privacy of a domain
You can have an unlimited number of email addresses.
DreamHost's control panel
Web Application Firewall built-in (WAF)
Domain administration in its entirety
Access to SFTP and SSH
WP-CLI
Advantages and disadvantages

Pros of DreamHost
No contracts, no commitments, and pay-as-you-go pricing
Money-back guarantee of 97 days
Privacy and a free domain (on an unlimited plan)
Data transmission and disk space are both unlimited
SSD storage is available for free.
Servers that are quick (PHP7, SSD & built-in caching)
Cloudflare CDN and free SSL
WordPress hosting with DreamPress is fast and reliable.
Cons of DreamHost
Don't provide access to the cPanel management panel.
There is no phone help available.
Final Word
Dreamhost's numerous web hosting options are competitively priced, and the company boasts a whopping 100 percent uptime. Furthermore, the 97-day money-back guarantee provides you adequate time to examine their services, putting your mind at ease.
Furthermore, Dreamhost review isn't one of those EIG firms out to make fast money, so you won't have to worry about costly renewals. In addition, the speed is adequate, allowing you to stay ahead of your competition in organic searches. After all, websites that load quickly provide a better user experience and rank higher in organic search results.
0 notes
Photo

DNS Changer | Fast IPv4 & IPv6, Wifi & Mobile Data Pro 1.0.1 b1002 (All in One)
DNS Changer | Fast IPv4 & IPv6, Wifi & Mobile Data Pro
Protectstar™ DNS Changer for Android ★★★★★ Get faster and more secure internet ★★★★★ Use preconfigured DNS servers or use any custom IPv4/IPv6 DNS server ★★★★★ By optimizing your device's DNS records, you can find the fastest routes for your data packets ★★★★★ Change to DNS servers focused on Security, Ad Blocking, Parental Control, Malware Protection, and many more ★★★★★ Protectstar™ apps are preferred by more than 3,000,000 users in 123 countries Protectstar™ DNS CHANGER Android Get faster and more secure internet DNS Changer Android is the first layer of internet security that has essential protection against surveillance and censorship attempts. With just one touch, the app finds the fastest DNS server and connect with it to improve your network connection.
DNS Changer | Fast IPv4 & IPv6, Wifi & Mobile Data Pro
The Protectstar™ DNS Changer app is the easiest way to change your DNS and test DNS servers' speed. The smart app works without root for both WiFi and Mobile Network Data Connection. You can choose from a list of available DNS or change it to your custom DNS. Using DNS CHANGER Android might help keep your web surfing more secure and private and could even allow you to access websites region-blocked by your ISP (Internet Service Provider) or unblock restricted web content. It may also speed up your internet connection. Some users have improved online gaming (faster response time to reduce latency ping time) when changing DNS servers. With special DNS servers, the app removes ads to enjoy a faster mobile browsing experience while parental control servers ensure safe browsing for your family by filtering inappropriate content, such as adult websites, gambling & others.
DNS Changer | Fast IPv4 & IPv6, Wifi & Mobile Data Pro
With DNS Changer Android, you can protect yourself from phishing, malware, ransomware, and malicious domains. The integrated DNS speed test feature for PRO users helps you find and connect to the fastest DNS server based on your location and network. Guarantee from Protectstar™ Protectstar™ DNS Changer does not collect any personal user data. The app is also ad-free, like all our apps. Download some applications from the same Category List of integrated DNS: Cloudflare, Google Public DNS, AdGuard DNS, Quad9, CleanBrowsing, OpenDNS, Yandex.DNS, Neustar UltraDNS, UncensoredDNS, AlternateDNS, Digital Society Switzerland, dnsforge, Level3 DNS, DNS.WATCH, OpenNIC DNS, SmartViper DNS, Freenom World DNS, FreeDNS, Comodo Secure DNS, and more. Features: + Explore your favorite sites & apps freely + Enjoy the best and private browsing performance + Reduce Video Buffering + Stay more secure on public WiFi + Improve online gaming + Accessing restricted websites + Block Adult and Porn content + Unblock restricted websites + No root required Features of the PRO subscription: + PRO: Control apps individually + PRO: Advanced Logging + PRO: Smart Whois Feature incl. Map + PRO: Custom DNS + PRO: Smart DNS Speed test feature
DOWNLOAD NOW
0 notes
Text
Fix Your Wi-Fi Using These Analyzer Apps
Using a Wi-Fi analyzer app will help you to get an overview and analysis of how strong or weak your Wi-Fi network is, and it will show you all the other problems and features of a Wi-Fi connection. You will be able to troubleshoot and optimize the coverage you require at your home. A lot of Wi-Fi apps are not just typical analyzers, but they also include tools to detect your connection speed to provide you a brief report on connection and the devices connected to it.

Following are some of the highly-rated Wi-Fi apps that you can get on your device:
NetSpot WiFi Analyzer
This app is available on both iOS and Android, water requires iOS 10 or later, and Android OS 6.0 or higher to function. You can analyze your Wi-Fi network using its unique interface. It also allows you to discover Wi-Fi networks around us and check the graph to check the channels each network requires to function. You can scrutinize the study of various parameters of a network, such as the network name, security protocols, signal strength, etc.
WiFi Sweetspots
Available for free on both iOS and Android devices, this app observes speed fluctuations of your Wi-Fi connection and locates the fastest to slowest Wi-Fi spots in your house. This analyzing app can also discover the perfect spots for installing your Wi-Fi router, and it’s access point and Wi-Fi gaming consoles. It works more efficiently on iPhones.
Fing
This analyzer doesn’t only run speed tests for Wi-Fi connection but also for cellular internet as well. Your system is always secured as it blocks the intruders and unknown devices even before they try to join our network. The Parental Control feature allows you to schedule screen time and pauses internet access. In addition to that, you can secure your Wi-Fi network with open port detection and network vulnerability analysis. It can analyze bandwidth usage as well. This app includes port scanning, traceroute, DNS lookup, and device ping features, and it is available on both iOS and Android devices.
Network Analyzer
The Network Analyser app includes features like Wi-Fi Signal Metre, LAN Scanner, Port Scanner, Ping & Traceroute, DNS Lookup, Network Information, and more. The Wi-Fi signals meter includes features like WiFi encryption, BSSID, WPS support, Bandwidth for Android 6, or later and for iOS 13+. It detects IPv6 availability and detects all the network devices rapidly. The LAN scanner includes fast and reliable detection of all network devices, vendor name, IP and MAC address, NetBIOS, LLMNR, etc. It supports both IPv4 and IPv6. The port scanner of the app is fast and adaptive to the algorithms for scanning the most common ports. This app regularly comes with the latest updates and detailed help to use its functions properly.
Scany
This is an all-rounder app for office, and house Wi-Fi and LAN hotspot owners and developers as let you diagnose and resolve network issues quickly. It can detect hidden Wi-Fi or LAN networks and works on superfast and smart algorithms that are optimized, especially for massive networks. The Wi-Fi LAN and internet scanner include Unicode and international network name support along with NetBIOS, Samba, LLMNR, and Windows PC network names. This app also features a real-time network path traceroute monitor and ping. The port scanner provides super-fast detection of the predefined and custom port. It supports all Internationalized domain names for WHOIS trace across a chain of WHOIS services. However, this app is only available on the iPhone and iPad.

WiFi Monitor
It is available only on Android devices for free, but it also requires a premium subscription for unlocking better features. This app provides some of the most powerful tools that allow you to analyze your Wi-Fi networks and track the parameters based on frequency, connection speed, signal strength, and more. Use the Connection tab on the app to track pieces of information about your Wi-Fi hotspot, including hotspot security options, router signal strength, connection strength, DNS address, Subnet Mask, Default Gateway, etc. It also features a speed chart and strength chart to help you get a better analysis of your network.
WiFi Analyzer
This is an open-source free of cost Wi-Fi analyzer to optimize your network and signal strength. It identifies nearby access points in seconds and provides you with the graph for access point signal strength and channel signal strength over time. You can pause and resume scanning at any time. Use filters such as Wi-Fi band, security, SSID, signal strength, etc. for better optimization. You won’t be interrupted while running this app as it neither includes any ads, nor it collects your personal information, which makes this app a secure option. This app is again available on Android 6.0 or later only, but it lets you customize the theme.
I’m Anny. I’m a social media manager living in USA. I am a fan of technology, design, and music. I’m also interested in fitness and movies. visit our Business Directory page You can attend my event with a click on the button above.
Source: Fix Your Wi-Fi Using These Analyzer Apps
0 notes
Text
mmdb-server Fast API server to lookup IP addresses for their geographic location. The server can...
mmdb-server Fast API server to lookup IP addresses for their geographic location. The server can be used with any MaxMind DB File Format or file in the same format. mmdb-server includes a free and open GeoOpen-Country database for IPv4 and IPv6 addresses. The file GeoOpen-Country is generated on a regular basis from AS announces and their respective whois records. https://github.com/adulau/mmdb-server

GitHub - adulau/mmdb-server: mmdb-server is an open source fast API server to lookup IP addresses for their geographic location. - GitHub mmdb-server is an open source fast API server to lookup IP addresses for their geographic location. - GitHub - adulau/mmdb-server: mmdb-server is an open source fast API server to lookup IP addres...
0 notes
Photo

How To Whois Ipv6 https://ift.tt/2CvVwe2
0 notes
Text
Sızma Testlerinde Bilgi Toplama

Bir saldırının en önemli aşamalardan biri bilgi toplamaktır. Bir saldırı başlatabilmek için, hedefimiz hakkında temel bilgileri toplamamız gerekir. Yani, ne kadar çok bilgi alırsak, o kadar başarılı bir saldırı yapma olasılığı da artar. Kali’de bulunan bilgi toplama araçlarına Applications/Information Gathering menüsünden ulaşabilirsiniz. Bunun dışında terminal penceresinde ilgili aracın başlatma komutu ile de çalıştırabilirsiniz.

DNS Servislerinin Belirlenmesi DNS numaralandırma(DNS enumerations), bir kuruluşun tüm DNS sunucularını ve DNS girdilerini bulma işlemidir. DNS numaralandırma, kullanıcı adı, bilgisayar adı, IP adresi ve benzeri gibi organizasyon hakkında kritik bilgileri toplamamızı sağlayacaktır. Bu işlem için DNSenum'u kullanacağız. Terminali açıp dnsenum yazıp entere bastığınızda komutla beraber kullanabileceğimiz parametreler görüntülenir

Herhangi bir parametre kullanmadan dnsenum domain.com şeklinde kullandığımızda tüm kayıtlar(A,MX,NS vb.) gösterilir.
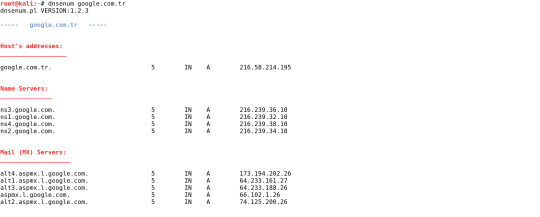
Yukarıdaki çıktıda google.com.tr adresine ait host adresi, NS ve MX kayıtlarını görüyoruz. Kullanacağımız ikinci araç dnsmap'dir. dnsmap çoğunlukla altyapı güvenlik değerlendirmelerinin bilgi toplama / numaralandırma aşaması sırasında pentesterler tarafından kullanılır. Numaralandırma aşamasında güvenlik danışmanı, genellikle hedef şirketin IP ağ bloklarını, alan adlarını, telefon numaralarını vb. bu araçla keşfeder. Aşağıda bir örnek verilmiştir.
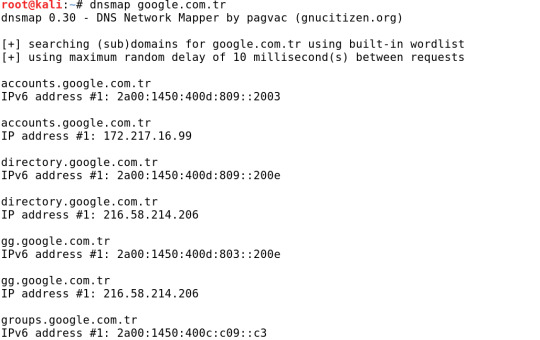
Yine yukarıdaki çıktıda google.com.tr alan adına ait alt alan adları ve IPv4 ve IPv6 adresleri görüntülenmiştir. Ağ Aralığını Belirleme Hedef sistemin ağ aralığını belirlemek için bir çok araç kullanabiliriz. Bunlardan ilki Information Gathering menüsünde bulunan dmitry aracı. Bu araç ile bir host hakkında mümkün olduğunca çok bilgi toplanabilir. Bunlar; olası alt alanlar, e-posta adresleri, çalışma zamanı bilgileri, TCP portu taraması, whois aramaları ve daha fazlası olabilir. Aşağıdaki örnekte blogumun alan adını bu araçla tarattım ve -o parametresi ile belirttiğim klasöre sonuçları txt olarak yazdırdım.

Yukarıdaki çıktıya göre blogumun bulunduğu sunucunun IP adresi 178.210.174.44 ve geçerli ağ aralığı 178.210.160.0-178.210.191.255’dir. Aktif Makinelerin Belirlenmesi Yerel ağdan veya yerel ağ dışından erişerek bir ağdaki aktif makineleri belirlemek için yine çeşitli araçlar kullanabiliriz. Bunların ilki netdiscover aracıdır. Bu araca Applications/Information Gathering menüsünden ulaşabildiğimiz gibi terminal penceresini açıp netdiscover yazarak ta ulaşabiliriz. Bu aracı herhangi bir parametre kullanmadan başlattığımızda bulunduğumuz ağdaki aktif makineleri belirleyebiliriz. Netdiscover yerel ağda kullanılan varsayılan özel IP adres aralığını tarayarak bize ağdaki aktif makinelerin IP adreslerini ve MAC adreslerini verecektir.

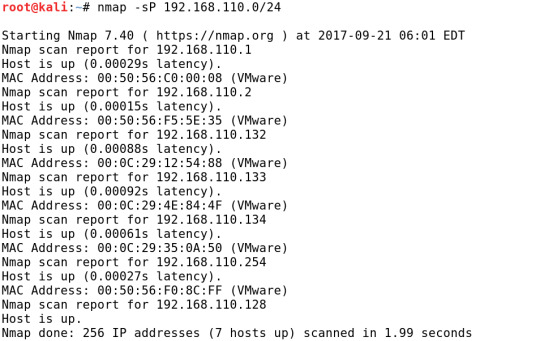
İkinci kullanacağımız araç sızma testi uzmanlarının sıklıkla kullandığı Nmap. Nmap ile ağdaki aktif makineleri belirleyebiliriz. Bunun için -sP parametresini kullanıyoruz. Bu parametre ile ağdaki hostlara ping atarak ICMP yankı isteği gönderiyoruz, aktif makinelerden de yankı cevabı dönüyor. Aşağıdaki sonuçlara göre ağımızda kendi makinemiz de dahil olmak üzere 7 host bulundu.
Açık Portların Belirlenmesi Nmap ile hedef makinelerin açık portları belirlenebilir. Burada hedef makinemiz metasploitable sanal makinemiz olsun. Bu nedenle aşağıdaki örnekte metasploitable’ın IP adresini kullandık.
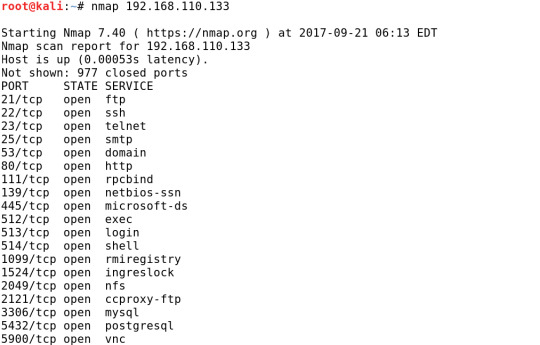
Yukarıdaki çıktıya göre herhangi bir parametre kullanmadan nmap hedef IP şeklindeki kullanımda en sık kullanılan 1000 port taranır ve açık olanlar gösterilir. Aşağıdaki tabloda, tarama tarafından görüntülenen çıktı alanları açıklanmaktadır. PORT STATE(DURUM) SERVICE(HİZMET) Bağlantı noktası numarası / protokol Port durumu Port için hizmet tipi Yukarıdaki tarama sonuçlarının ilk satırına bakalım 21 numaralı TCP protoklü portu, portun durumu açık ve bu porttan ftp hizmeti sunuluyor. İkinci satırda 22 numaralı TCP protokolü, portun durumu açık ve bu porttan ssh hizmeti sunuluyor. Üçüncü satırda 23 numaralı TCP protokolü portu, portun durumu açık ve bu porttan telnet hizmeti sunuluyor. Dördüncü satırda 25 numaralı TCP protokolü portu ve bu porttan smtp hizmeti sunuluyor, vb... İşletim Sistemlerinin Belirlenmesi Hedef makinenin işletim sistemi çok önemli bir bilgidir. İşletim sistemi ve sürüm bilgisi ile o işletim sistemi ve sürüme ait zayıflık ve açıklıklar kullanılarak hedefe sızmak mümkün olabilir. Hedef makinenin işletim sistemini belirlemek için nmap aracını -O parametresi ile kullanmak yeterlidir.
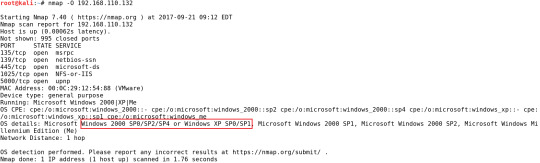
Yukarıdaki çıktıda hedef makinede Windows XP SP1 çalıştığı tespit edilmiştir. Servis Sürümlerinin Belirlenmesi Hedef makinede çalışan servislerin ( sshi telnet,vnc,smtp,http vb.) sürümlerini belirlemek çok önemlidir. Böylelikle o sürümle ilgili zafiyet ve açıklıklar kullanılarak hedef sisteme sızmak mümkün olabilir. Hedef makinenin işletim sistemini belirlemek için nmap aracını -sV parametresi ile kullanmak yeterlidir.
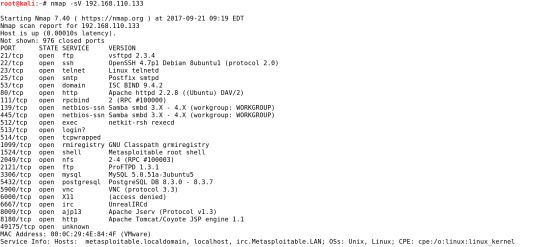
Yukarıdaki çıktıda hedefimiz olan metasploitable makinede çalışan servisler ve sürümleri görüntülenmiştir. Metasploitable’da ftp servisinin vsftpd 2.3.4 sürümü ile, ssh servisinin OpenSSH 4.7p1 sürümü ile, http hizmetinin Apache 2.2.8 sürümü ile verildiğini görmekteyiz. Bu sürüm bilgilerini Google’da arattığımızda ileride göreceğimiz exploit denen ve bu sürümlerin açıklarını sömürmemize yarayan programlara ulaşabiliriz. Nmap kullanımını anlatan videoyu http://bit.do/nmaptarama adresinden izleyebilirsiniz. Read the full article
0 notes