#and use 5 different malware detectors
Explore tagged Tumblr posts
Text
Top 5 Safest Websites to Download Free Software
It is not a secret that everybody wants to get free software but the problem is that very often free software download sites can be dangerous to your system. You can make one click and download files that can infect your PC with different viruses or malware programs and your banking information can become available to hackers. Some sources offer free download and take you on a survey trip and land you nowhere, while others have the infected files in store for you and are waiting for a moment you start downloading software from their website.
In this article, we describe 5 top safe software download websites, which you can trust. We have used three tools as WOT, URLVoid and McAfee SiteAdvisor to verify every site’s reputation.
1. Softpedia

Softpedia is a well-known platform with the largest database of files on offer that counts more than 900.000 programs. They often update the software that is offered on the website to the latest versions. While downloading files from the platform, you can rest assured that you get only the recent versions of software that is free of any malware programs and viruses.
Softpedia has an incredible reputation among users. You will enjoy how easy it can be to use the website that has an attractive and user-friendly interface to search for required drivers and programs of all types of operating systems such as Mac, Linux, Windows, Android, iOS, and Windows Mobile.
2. FilePuma

There is no doubt that FilePuma must appear on this list of safe and free software download websites. They have amazing navigation on their platform. It is very easy to browse the website and find the programs and drivers you need.
FilePuma offers its Update Detector system that will keep your installed software up to date so that you will not waste your time searching the required updates for your programs.
3. RocketFiles

If you need to install the latest software that will not harm your system with different viruses and malware programs, you should probably visit RocketFiles. It is a rather new platform that is they are still undergoing the development and improvement process but it can provide you with an incredible database of free software.
You will be impressed by how it can be easy to find the required program with just a few clicks. Also, the website is full of different guides and tips on how to fix all possible problems that may occur on your PC.
4. Download Crew

This website has already proved that it is one of the best free and safe platforms to download software. You will not only be able to download malware-free programs but you can also read informative reviews to learn what the programs do and how to install and use them.
There are special categories such as "Editor's choice" and "Most Popular Downloads" where you can find cool and recent software that is used by a lot of users. Do not hesitate to visit this platform to get updated as well as get hold of safe programs and drivers for your operating system.
5. Ninite
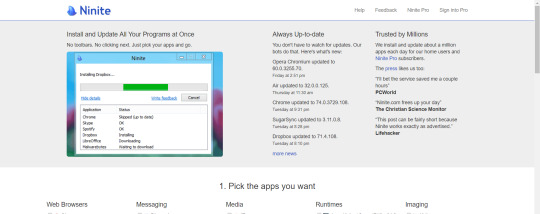
Ninite has built its reputation among the users for some years and gained a great result. It is a great source of different software that is listed in categories. It makes the process of choosing the right software efficiently. With the help of its custom installer, you can choose the required programs to download and install them in a bulk.
If you are worried about viruses and malware, you will not find them on this platform. They can guarantee you the safety of your PC. You can also update all installed software automatically using the custom installer.
1 note
·
View note
Text
Plagg and the Butterfly Costume Outtakes: Ch 7
Plagg is willing to do a lot in order to get more cheese. When he’s spotted one too many times en route to the kitchen, he decides that a disguise is in order. One purple costume later, and Plagg is free to flit down to the kitchen without people thinking that he’s a rat.
And then he gets caught.
PATBC: (1) (2) (3) (OT:1) (4) (5) (6) (OT: 2) (7) (OT: 3) (OT: 4) (OT: 5) (8) (OT: 6)
(AO3) (FF.net)
These days, it seemed that bad luck dogged Gabriel Agreste's footsteps, and he was fairly certain that he wasn't even being (that) dramatic in saying that.
First it had been his eye injury and that strange kwami in the house. Then the roof of his lair sprung a leak, right over where he always stood. One of the buttons for his elevator broke, and he wasted an entire day trying to fix it before discovering that one of the pieces had gone missing. The window shutters jammed partway open, letting more than a few butterflies escape while he tried to fix it (but at least no one in the streets below seemed to notice anything). His phone battery suddenly stopped charging properly. A fabric order didn't submit properly. Money had mysteriously gone missing from his wallet while he was out at a doctor's appointment to check on his still-healing eye. His elevator broke down with him on it, trapping him in a very tight place for several hours, and after he was finally freed Gabriel discovered that he had somehow gotten a virus on his computer and it had completely wiped out all of his files with the high-definition scans of the scrolls and the Miraculous book and deleted his bookmarks of the sites he had found with legends of what he thought might be past Miraculous holders. That wouldn't have been a huge deal, but somehow he had misplaced the flash drive with all of his backup scans.
At least he still had the hard copies to work with. He had been doing most of his (failed) translation attempts with one of the scrolls, and at least he still had that, not that he had really been focusing on that for a while.
Still, he had raged, fed up by the entire day. In a fit of paranoia, he demanded that Nathalie review the security camera footage. He found it hard to believe that all of his trouble was just a coincidence. He couldn't be that unlucky.
There was nothing on any of the security camera tapes. The motion detector that Nathalie had turned on when she left had not gone off. Gabriel had been forced to admit that the virus that had wiped all of the files on his Miraculous account (though thankfully not his design account, though he had that thoroughly backed up just in case something like this happened) was apparently real and was entirely his own fault thanks to him looking at somewhat dodgy websites during the course of his Miraculous research without first ensuring that his anti-malware program was actually on and up-to-date.
In the end, it didn't really matter, Gabriel reminded himself as he unlocked his safe and triple-checked that the books and scrolls were still there. There wasn't a ton of material that had been on the computer that he didn't have elsewhere, so all he had lost was his bookmarks and PDFs of assorted legends that he had found that he had thought might help him recover his wife. Even that wasn't a big deal anymore. He had long since given up the idea of trying to get Emilie back in any way except with the Ladybug and Chat Noir Miraculous, and he had memorized all of the information that he would need to know about that. Besides, he could more or less remember the few bookmarks that he was interested in that were about potential past Miraculous holders and what their powers might be, and if not he could just look them up again.
(With the anti-malware program on, of course. He wasn't going to repeat his past mistakes again.)
Of course, he had to get his computer back first before he could do that.
"Have you gotten the computer cleaned yet?" Gabriel demanded impatiently as he watched Nathalie hover over his computer, frown on her face. As far as he could tell, the virus hadn't affected his design account, but he didn't want to risk it by using his computer again until that virus was wiped from it.
"I've run six different highly-rated anti-malware programs on your computer, and none of them have found anything," Nathalie reported.
Gabriel strode over to her to peer over her shoulder. "So it's clear?"
"Not at all. Whatever virus you got is so new that the programs haven't updates to recognize it yet." Nathalie let out a huff as yet another top-of-the-line computer scan came up empty. "I might need to call in a pro to get your virus cleaned off so you can use the computer again."
Gabriel scowled. Several more hours of work lost, and he couldn't even make good use of his time because the elevator was still not in working condition, since his contractor had several other jobs to work on first.
On top of everything else, Gabriel was still puzzled by the fact that he hadn't been attacked yet. He spent every waking hour of the day (and some non-waking hours as well) paranoid and on edge, waiting for the superheroes to attack.
Nothing. It had been weeks, and still nothing had happened.
By now, Gabriel was fully convinced that Nooroo's assumption was right and it had been the turtle kwami investigating him rather than the cat kwami. He thought that maybe the Turtle holder just hadn't been able to contact Ladybug and Chat Noir, though that didn't exactly make sense considering that he must have given them their Miraculous and should have known where to find them. Perhaps he wanted to investigate Gabriel more first.
Perhaps the Turtle kwami was roaming the halls of the mansion even now, figuring out Gabriel's strengths and weaknesses. The thought made Gabriel uneasy.
Spied on, in his own home. And cameras didn't even record kwamis, which meant that he couldn't try to spot and trap the turtle kwami like that.
"Or perhaps there's been something keeping this Turtle person from contacting the superheroes," Gabriel mused that night before bed as he sipped from a glass of wine. It helped calm his jittery nerves enough for him to sleep, though he didn't drink so much that it might affect his response time should he get attacked. "If he was ill- but unless he was old, he would have recovered by now."
Nooroo swallowed the mouthful of orange he had been chewing on. "Well, if it's still the same person, which it may very well be, he'd be in his...180s, I think?"
Gabriel choked, sending red wine flying out his nose and spraying from his mouth.
"A hundred and eighty? Are you sur- wait, no, humans can't live that long. You've forgotten about the human life span. Surely it's been passed down once or twice since when you remember last."
"Turtles have the gift of longevity," Nooroo said, ignoring the way the wine Gabriel had spat out was dripping off of his face and onto the bed sheets. The kwami had (naturally) managed to dodge every last drop. "And yes, one hundred eighty is old even for a turtle, but that perhaps is because in the olden days, people became suspicious of those who lived too long, so the Turtle miraculous holders tended to pass it on long before they would have died had they kept it."
Gabriel had practically stopped listening now. "So it's possible that he's fallen seriously ill and can't talk to those pests," he mused, even as he wiped his face. "Or perhaps he died, and his bracelet and that pesky kwami was buried with him. But there's no way for me to know for sure, I suppose." Nooroo wouldn't tell him who the Turtle was (or who it had been), Gabriel knew that. His kwami occasionally passed on information when he felt like it, but that information now rarely lined up with what Gabriel really wanted to know, and no amount of bribes or threats would change that.
Perhaps all of his worries were for naught. Perhaps the only person who knew about his supervillain side activities besides Nathalie was far under the ground now, and their kwami unclaimed and inactive. But Gabriel wasn't going to let down his guard, not for one moment.
After all, his enemy could very well be lying in wait, watching for Gabriel to let his guard down so he could attack.
And Gabriel could not- would not- let him win.
#Miraculous Ladybug#My writing#Plagg and the Butterfly Costume#I meant to post earlier but I'm busy getting ready to leave for Canada#it involves a lot of me going 'SHOOT HOW DID I ALMOST FORGET THAT'#and also 'plz fit plz fit I don't want to need another suitcase'
16 notes
·
View notes
Text
Online Videos Downloader For Mac

Web Video Downloader Mac
Download Videos Mac Free
Online Video Downloader For Macbook Pro
Best Mac Video Downloader
Best Free Youtube Downloader For Mac
2020-09-11 17:57:40 • Filed to: macOS 10.14 Solutions • Proven solutions
Apple has announced macOS 10.14 Mojave, along with its superb features, including Dark Mode, Stacks, Dynamic Desktop, Screen Capture, and lots more. Most Mac owners already are aware of this; what they may not know is the best solutions to save YouTube videos on macOS 10.14 for free. YouTube, a California-headquartered video-sharing website, is where you can download millions of songs, videos to make you enjoy your Mac to the fullest. In this write-up, we'll show you how to download YouTube videos to macOS 10.14 for free.
Best Free Youtube Downloaders for macOS 10.14
Free Mac video downloader is a web-based application specially designed for Mac users to download TV episodes, movies, music videos, news, sports and other online video clips from tons of video hosting sites. It covers video downloads for sites like YouTube, Dailymotion, Vimeo, Blip TV, Liveleak, Lynda, Break, Vube, Ustream, Ted and many others. Copy the Video URL that you want to download and paste it to the 'Search' box. Then click 'Download'. After analyzing, you can choose which type and format you want to save the video and click “Download”. In the pop-up videoplay window, click the “three dots” icon and select “download” to download this video. As a rule, VidPaw Online Video Downloader can download online videos to MP4/ 3GP/ WebM in 8K, 4K, 2K, 1080p, 720p, 360p, 240p, 144p as well as to MP3/M4A in 320kbps, 256kbps, 128kbps, 96kbps, 64kbps. Yet, the output quality still depends on the original quality of the video.
1. Free YouTube Downloader
This is a highly recommended tool to download YouTube videos on macOS 10.14. Free YouTube Video Downloader provides 3X faster speed and 3 easy ways to download any videos from YouTube on Mac for free. It also has a premium version named iTube HD Video Downloader which can download HD and 4K YouTube videos in bulk.
Key features:
The program provides 3 easy ways to download YouTube videos, including copy and paste URL, directly drag and drop the video to the interface, and a 'Download' button on the browser.
Free YouTube Downloader can automatically detect and download YouTube videos opened in Safari, Chrome, or Firefox in one click.
3X faster download speeds compared to other similar programs.
2. Airy
This app is one of the top free YouTube downloaders for Mojave. It helps you save your favorite videos from YouTube onto the Mac so you can play them anytime and anywhere you choose. With Airy, you don't need an internet connection to play music from YouTube. It allows for 2 free downloads.
Key features:
Airy lets you download complete YouTube playlists in the video as well as audio formats.
It is used for downloading an entire YouTube channel.
It is great for downloading a private YouTube video.
3. Any Video Converter
If one assumes that this software is only meant for converting videos into various formats, such a misconception is venial. This is the reason judging a book by its cover — or more precisely, judging an app by its name — is not wise. Though Any Video Converter is apparently capable of performing this operation, it is also a fantastic YouTube video downloader.
Key features:
It allows you to download your favorite videos directly from YouTube and save them on your Mac in MP3 format.
It is free to download videos from YouTube to your Mac for macOS 10.14
The software is used for converting videos from one format to another.
4. MacX YouTube Video Downloader
This piece of software can download videos from YouTube and other websites like Dailymotion, Vimeo, Facebook, and Vevo. When you are downloading music and videos from YouTube with this software, it allows you to select several formats and resolutions, including 8K, 720p, 1080p, Ultra HD, 5K, and 4K resolutions.
Key features:
The program has a professional-looking interface.
It is perfect for downloading videos from YouTube and other sites such as Facebook, Vevo, Dailymotion, and Vimeo.
MacX YouTube Video Downloader is a tad confusing to use
5. ClipGrab for Mac
This program is one of the best YouTube downloaders for macOS 10.14 because it is free, fast, and easy to use. The app downloads videos in HD from YouTube and other popular video hosting sites like Vimeo, Dailymotion, and so on. One of the unique offerings of the app is, it automatically detects whenever a user pastes a download link from a website onto the clipboard and begins the download of the video automatically.
Key features:
ClipGrab allows you to download videos from top video hosting platforms such as YouTube, Dailymotion, Vimeo, and others.
You can save download videos in formats like MPEG, WMV, OGG, Theora, and OGG.
6. WinX HD Video Converter for Mac
Looking for an extremely clean and safe YouTube Video Downloader to download YouTube videos on your Mac for macOS 10.14? WinX HD Video Converter for Mac should be your ultimate choice. It allows you to download videos in various formats, including MP4, FLV, and WebM. Also, it helps you download videos easily from YouTube and other websites in SD, HD, 4K, and UHD resolutions.
Key features:
WinX HD Video Converter for Mac is 100% clean and safe
It is used for downloading videos in MP4, FLV, and WebM
The app is ideal for downloading videos from YouTube and other platforms in SD, HD, 4K and UHD resolutions
Save YouTube Video on macOS 10.14 Using Browsers
1. Save a Video from YouTube with Safari
Best Youtube Downloader for Safari is used to save YouTube videos on macOS 10.14. It is an add-on for the browser, providing the easiest solution for downloading YouTube videos in different formats — the likes of MP4, FLV, WebM with 1080p and 720p HD FullHD qualities directly from video pages on YouTube.
Download Link:
https://safariaddons.com/en-US/safari/downloads/file/656/best_youtube_downloader_for_mac_os-1.5.17-sf.zip
2. Save a YouTube Video with Firefox
If you're a Firefox user, we recommend that you visit the DownloadHelper extension and install this extension. After this, you'll see the DownloadHelper icon displayed in the address bar of your Firefox or in the status bar, which you can find at the bottom of the browser window. You can start playing a video and click on the icon for the extension. You will see one or more listings for that YouTube video with a few of them in Flash format, while others may be in MPEG-4 format. Simply select the one you prefer and begin the download onto your Mac.
3. Save Video from YouTube Using Chrome
For users of Chrome, save YouTube video on macOS 10.14 using a Chrome extension, Download YouTube Chrome. After downloading this add-on and unpacking the ZIP file on your hard drive, follow these steps:
1. Copy and paste 'chrome://extensions' to the address bar of your browser.
2. Tick the checkbox for 'Developer Mode.'
3. Choose the 'Load unpacked extension' option.
4. Go to the unpacked folder on the hard drive; then open it.
Free Download or Buy PDFelement right now!
Free Download or Buy PDFelement right now!
Buy PDFelement right now!
Buy PDFelement right now!
1 Comment(s)
Overview
Download
Feature
How to use
Free Mac video downloader is a web-based application specially designed for Mac users to download TV episodes, movies, music videos, news, sports and other online video clips from tons of video hosting sites. It covers video downloads for sites like YouTube, Dailymotion, Vimeo, Blip TV, Liveleak, Lynda, Break , Vube, Ustream, Ted and many others. Aside from its ability to download video on Mac, there are some other awesome features that are worth mentioning.
Download videos in high quality, including 1080p video
Directly convert video from websites to MP3 on Mac OS X
Convert videos to any video/audio formats
Provide video search engine to find desired videos
Extreme function for capturing all screen activities
Fully compatible with Mac OS X (Mavericks 10.9 included)
Great integration with Safari, Firefox, Opera and Chrome
100% FREE and Safe
No toolbars, adware or malware
Download Robust Video Downloader for Mac software
Free Mac video downloader combines the simplicity of usage, full functions and fast speed. But a good portion of people prefer the software program to the web-based tool. This is mainly because the software runs better, more stable and reliable. Fortunately, Free Video Downloader for Mac software is an effective way to download and convert videos for Mac. Being compared with the online application, the professional software excels at its accelerated downloading speed, expanded video formats, great stability and more complete functions.
Features of Video Downloader for Mac software
Download video instantly on Mac
The user-friendly interface makes downloading super easy, you simply get videos in one single mouse click. This video downloader for Mac provides the option to download videos in original quality, including HD and 4K videos. Users who do not want to download video one by one could perform multiple video downloads during one session.
Convert video effortlessly
More than a Mac downloader, it can convert any local or downloaded files to all kinds of formats such as MP4, MKV, MOV, MPEG, WMV, AVI, FLV, MP3, RM, VOB, OGG, AAC, AIFF, WAV, etc. After that, you may transfer the video to popular gadgets like iPod, iPad, iPhone, Zune, PSP, Android and more for endless enjoyment.
Web Video Downloader Mac
Detect and download video automatically
The tool features a smart detector, which facilitates to auto-detect and download the videos streamed in the built-in browser of the program. A list of top websites is displayed on the screen at run time. As long as you click on a certain site for playing the video you want to download, the advanced sniffer will grab it in a matter of seconds. Surely, you may navigate to other sites that are not listed; the videos being played can be captured as well.
Download YouTube playlist
With this professional video downloader for Mac, users can download YouTube single videos as well the whole collections from YouTube users' channel, personal playlist, movies category, YouTube charts, artists' channel and music category. Within just one click, you can grab all videos in specified channle/list with 3X faster speed brought by advanced technologies.
Schedule video downloads
The program enables users to start and stop video downloading at any time you preset. Moreover, you can schedule your Mac computer to shut down, enter into sleeping mode or exit the program when download completes.
Manage video efficiently
It comes with handy video manager, letting you control over download progress and sort the downloaded files in order. In case you may need to quit the program for dealing with other cases, you can resume your downloads automatically. Also, the program makes it possible to preview the downloaded content with integrated media player.
How to use
1. Use free online tool to download videos on Mac
This free Mac video downloader does not require any installations or registrations; you simply copy the video link and paste it into the URL field. After clicking 'Grab it', it will display video formats available for saving your videos in FLV, WebM, 3GP, MP4 and other formats depending on the website you are downloading from. Nevertheless, before using the app, the very first step is to enable Java applet in Safari or other browsers. Please make sure that you check 'Enable Java check box' under 'Preferences' tab in your browser.
2. Use free Mac software to download videos
One click to download single video as well as the whole collections
The program is very easy to use. To perform every single video download, you simply specify the video URL that you want to download and click 'Paste URL' button.
The steps to download the entire YouTube playlist are exactly the same. All you need to do is to find the URL of YouTube playlist and hit on 'Paste URL'. Resume to interface, in the popup window, all the videos will be automatically fetched. Select all or part of them per your needs, and then click 'Add to download' to carry on multiple downloads simultaneously.
Download Videos Mac Free
Auto-detect and grab video that is being played
As name suggests, Blu-ray Ripper is an incredible point-and-click solution that makes. Of course, the option also exists for ripping a Blu-ray to your hard drive and converting the digital video files to a usable format. If that’s appealing, you can learn how to rip discs to your Mac and convert video files on macOS in this article. Related: How to Play Blu-Ray discs on Windows 10. Enabling Blu-ray. Blue ray for mac. Macgo Mac Blu-ray Player Pro. First and No.1 Blu-ray player for OS X 10.15 Catalina; Support BD, Blu-ray Menu, ISO files, and BDMV folder Powerful software for almost any multimedia formats; Smoother Blu-ray. Including: Mac Blu-ray Player, Windows Blu-ray Player, Mac iPhone Data Recovery, iPhone Cleaner for Mac, iPhone Explorer for Mac System Requirements: Mac OS X 10.6 - 10.13 High Sierra / Windows 10/8.1/8/7/Vista/XP (SP2 or later).
Given that you do not want to process Mac video download simply by copying and pasting the URL manually, then you are suggested to take advantage of its 'Detector' function. As long as you load videos in the built-in browser, this Mac video downloader will take care of the rest.
3. Video Tips for Mac
Most video addicts like to enjoy abundant videos from video sharing sites including YouTube, Dailymotion, Vube, BBC, ESPN, Facebook, Vimeo, Hulu and other similar sites. You are looking for specific guides on downloading from a platform to your Mac computer, please refer the detailed instructions below
YouTube has had such an incredible string of successes. People want to download their favorite videos to watch offline and keep forever.
Download Dailymotion on Mac

Online Video Downloader For Macbook Pro
Is there a way out here to watch Dailymotion videos without any data connection? Sure, you are in the right place to get the easiest tricks.
Still trying to find a way to download HD videos from Vimeo? Don¡¯t sweat it, spare a few minutes to check the detailed tutorial.
You may find the easy solutions to perform Facebook video download in this article. A wonderful Mac downloader is presented.
Best Mac Video Downloader
Download Hulu on Mac
Best Free Youtube Downloader For Mac
Want to play TV episodes from Hulu to your Mac without being bothered by poor internet connection? Just download them for later playback.

0 notes
Photo

Bluehost Review – 7 Pros & 4 Cons of Bluehost (Server Speed Tested!)
Bluehost
https://www.bluehost.com/
Bluehost is a fantastic choice for beginners who want to build their first website for their businesses or blogs. Their onboarding process and automatic WordPress installation makes everything feel very easy to use. They may not provide the best value or service, but their product just works.
If you’re flopping about, unsure whether or not to use Bluehost as your web hosting provider, worry not – you’ve stumbled on to the right page.
Here at Bitcatcha, we’re a little obsessed with web hosting (our doctors say it’s borderline unhealthy).
We’ve gone ahead and gotten ourselves a Bluehost account, run some performance tests on their shared hosting plan, and we’re ready to present to you the most definitive Bluehost review you’ll find on the internet.
A Little Bit About Bluehost
Founded by a very young Matt Heaton and Danny Ashworth all the way back in 2003, Bluehost has been around a LONG time.
They’re practically dinosaurs in the industry, but that ain’t a bad thing – having been around for so long means that they’ve learned a thing or two about web hosting, and are able to provide their users with a kick-ass user experience.
For a web hosting provider that’s known and used by people all over the world, Bluehost has but 1 datacenter, which is located in the US. That datacenter powers all of their clients’ websites, which adds up to a whopping 2 million, and is growing by the thousands each day!
Hot Damn!
They obviously made quite an impression in the market, because, in just 7 short years, they got the attention of web hosting giant Endurance International Group, which proceeded to acquire them into the EIG group of companies.
With the support of EIG, Bluehost managed to substantially grow their once small team to a family that’s 750 people large, allowing them to provide much needed round-the-clock support for their customers!
Not impressive enough for you?
Then check this out – Bluehost is also one of the 3 web hosting providers that are actually recommended by WordPress!
If you’re wondering why that’s impressive, it’s because 30% of sites in the entire world wide web is actually powered by WordPress. In other words, they’re the rock stars of the internet and getting an endorsement from them is similar to getting your workout gear endorsed by Dwayne “The Rock” Johnson.
Now that you’re acquainted with Bluehost, let’s find out why, in our humble opinion, Bluehost is a pretty strong web hosting provider!
7 Great Reasons To Pick Bluehost!
1. Bluehost Is Surprisingly Easy To Use
If you’ve ever built a website before and used a web hosting service provider with a crappy interface, you’ll understand the pain of logging into the dashboard and… not knowing what to do.
Bluehost surprised us with their onboarding process. After completing the registration process, we logged in to the dashboard and before we knew it, clicked next a few times and then, *poof* magic – WordPress was already installed and ready to go.
But pictures speak a thousand words, so here are some to show you what really went down after logging in.
Bluehost will begin by asking you a series of questions about what kind of site you’ll be creating. Select an option from the drop-down menu, and hit continue. Easy-peasy.
They’ll then ask what kind of site you’ll be creating, whether it’s a blog, e-Commerce site, or a niche website selling poop scented wrapping paper.
Them pesky buggers will want to know more about your site, but worry not, because they have your best interests at heart. Name your site, think of a tagline, and rate your website building level on their noob detector scale.
All you have to do next is pick a theme you like, and then boom, WordPress is automatically installed just like that! No need to worry about getting it installed in the wrong folder, or drastically messing something up.
Bluehost will take care of the backend, while you just need to worry about customizing your site and making it look pretty.
If you’re new to site building, I’m pretty sure you have no problems at all creating your site with Bluehost. Even those of us that are a little more seasoned will appreciate how convenient their dashboard is to use.
Look out how beautiful that custom cPanel interface looks. None of that confusing looking dated mess that comes with stock cPanel.
2. They’re Surprisingly Fast Around The World!
According to thinkwithgoogle, fast site load speeds are important for online businesses to be successful, and server response time plays a HUGE role in getting websites to load up fast.
However, with merely 1 datacenter located in the USA, we didn’t think Bluehost would do very well when put through our proprietary server speed test.
Using our test site hosted on their basic plan, we went to town and started testing their response times – boy, we were dead wrong.
Average Speed: 153 ms
The American hosting provider responded exceptionally well, hitting speeds that are WAY faster than Google’s recommended 200ms in all countries, except for Bangalore.
They’re obviously fastest in the USA as the datacenter is located there, but they’re no slouch in countries on the other side of the world like Singapore, Sydney and Japan!
With an average worldwide score of 153ms, Bluehost is one of the fastest A-ranked hosting providers we’ve ever had the pleasure of reviewing. You can rest assured that no matter where your target audience resides in the world, Bluehost will be able to deliver!
Well… except if your audience is in India. You might want to check out our piece on the best web hosting for India instead.
LEARN MORE @ BLUEHOST OFFICIAL
* User-friendly hosting with great speed at an affordable rate!
3. They’ve Got High-Performance Servers
Those of you with plans to run large scale e-Commerce websites or reddit-like forums would be happy to know that Bluehost offers High-Performance Servers that are suitable for your needs.
Why is this important?
Well, with shared web hosting, the purpose of the server is literally in the name – you’re sharing the space with other users, which helps reduce the cost.
However, some users might accidentally (or intentionally) use up way more resources than allocated, which means that everyone else sharing the server with that user will experience site slowdowns – sometimes their sites won’t even load at all.
With High-Performance Servers, Bluehost allocates fewer users per server, and each user is given a file count of 300,000 – this means more computing resources per user, consistent site load speeds, and less downtime caused by rogue users!
BUT!
As it is with all things good, there’s always a catch.
Their High-Performance servers are only available with their Pro plan, which is a whole lot pricier than the rest of their shared web hosting plans.
Guess if you want good performance, you’ve gotta pay for it.
Quite frankly, we have every confidence in their servers. Our test site is hosted only with their Basic plan, and even then, the uptime for it has been 100% since April 2018!
Uptime since April 2018
99.98%
* Bluehost Basic Plan Uptime - tracked with uptimerobot.com
If their shared hosting servers can produce such uptimes, we can easily expect the same from their High-Performance servers.
4. Fantastic Security Features
When we say security, we don’t mean features that just keeps your website safe from those fiendish, ne’er do well hackers.
We’re talking about security in terms of peace of mind, and keeping spam away from the sanctuary of your brand new email inbox.
Let’s look into peace of mind first.
You don’t want to spend days, weeks, months, customizing and tweaking your business website to get it to look perfect and suited to rank on the front of page Google, only to load it up to discover that someone screwed the pooch and your entire website is gone.
For this, Bluehost provides their users with CodeGuard basic – at $2.99 a month.
CodeGuard Basic
The name sounds cool, but it’s actually just a fancy name they came up with for their daily backup service. It’s not bad at all – monitoring your website/database frequently, notifying you if there are any changes, and automatically performing backups.
The basic version provides 1GB storage space, daily backup and monitoring, and 3 restorations a month.
If you need more, CodeGuard comes in Professional, Premium, and Enterprise versions too, but be prepared to pay higher prices for those.
SpamExperts
We assure you, Bluehost won’t be sending someone that can tell you the nuances between different types of pork used in SPAM products.
Instead, SpamExperts is their term for an advanced email filter. It scans incoming emails for spam, viruses, phishing, and other email-related attacks by spammers, and filters them with a rockin’ 99.98% accuracy, all before it reaches your inbox.
Basically, it helps your mailbox stay squeaky clean and junk-free.
SiteLock
In terms of actually protecting your website, Bluehost comes with a basic firewall that offers a minimal level of protection against external threats.
However, If you want enhanced protection, you can get it in the form of SiteLock.
SiteLock comes in three tiers: Essential, Prevent, and Prevent Plus.
With Essential, you’ll get to enjoy automatic Malware removal, which does exactly nothing against DDOS attacks or anything major.
With Prevent, the security level is upped a little with Automatic Malware Removal, DDoS Protection, 6-hour response time and….Image Optimization. Quite frankly, I don’t know what image optimization has to do with security, but it’s a feature I won’t be complaining about.
Prevent Plus does everything Prevent can, but with the added benefit of having daily scan frequency.
SiteLock is good and all, but the thing is, they all come as an add-on, meaning we’re gonna need to fork out more money to enjoy it. Come on Bluehost, you can afford to give your customers a little extra security for free!
5. They’ve Got A Buffet Of Benefits
Gone are the days where you have to carefully plan out the number of sites you’re planning to launch, and the kind of resources needed to run all of it effectively.
Bluehost’s shared hosting plans come with all sorts of benefits, and best of all, almost everything is unlimited! We’re talking:
· Unlimited websites
· Unlimited SSD storage
· Unlimited parked domains
· Unlimited subdomains
· Unmetered bandwidth
You are basically free to create as many sites as you want with them! And you won’t have to worry about the number of visitors to your site!
Be wary though – having too many visitors at the same time might take up too much resources, and Bluehost is notorious for deactivating/deleting rogue sites.
6. Support Responds Very Fast!
One of the most infuriating things in life is waiting for support to respond to you, especially if your site needs attention NOW.
While we were setting up our test site, we were quite pleased to find that support responded via Live Chat very quickly. We’re accustomed to waiting at least 15 minutes for live chat support staff to respond, but the Bluehost support team consistently responded in less than 5 minutes.
We didn’t try phone or email support, but with live chat responding as quick as they do, we hardly think that those methods of support are necessary, although it’s nice to have in case of emergencies.
You won’t have to worry about support in different time zones either, because Bluehost’s support is available 24/7.
Excellent job, team!
7. Freebies That Matter
Some companies will entice you to sign up with their service with shallow free gifts. We’re talking about those that market regular services as “free”, such as “free” 24/7 support, or “free” WordPress installation.
Not Bluehost.
With the all-American web hosting service provider, you’ll actually get freebies that’ll make a difference in your bank account.
With every shared hosting plan purchased, Bluehost will throw in a domain name, free for the first year. To put things in perspective for you, domain names can cost anywhere from $8 to $872 million – yes you read that right. Here’s proof.
Aside from that, you’ll also get the enjoy free SSL – now this might not be much, but every little bit definitely helps to make a difference to the small business owner!
SEE FULL FEATURES @ BLUEHOST OFFICIAL
* Unlimited website, SSD, domains, and more!
4 Disadvantages Of Bluehost
They say that every rose has its thorn. Well, turns out Bluehost is quite thorny.
1. Bluehost Only Has 1 Datacenter
We mentioned previously that we were quite impressed by how fast Bluehost’s 1 datacenter performed, and we still are.
However, every millisecond counts when it comes to site load speed, and we know they can actually perform WAY better if they had datacenters in other continents to support audiences living further away.
They might have one of the best worldwide average speeds among all the web hosting services we’ve reviewed, but if another hosting provider like SiteGround has a datacenter in Asia, it’s a given that sites will load up faster for target audiences located there.
2. Untrained Trainees
I hate to say this because we all start out somewhere, but you really have to be wary of support that are a little wet behind the ears.
Bluehost doesn’t really make an effort to hide that they outsource their support team to India, which isn’t really a big deal anyway. I don’t mind, as long as they’re efficient and fast.
But what I do have a problem is incorrect advice given by trainees.
While setting up our test site, we asked the support team one really simple question:
“Does Bluehost provide us with an Uptime Guarantee?”
The support didn’t know what an uptime guarantee was.
Fine, maybe it got lost in translation. We explained what we were looking for and their reply was YES, Bluehost has an uptime guarantee!
So we asked him to point us to the terms of the guarantee and after going through it, we discovered that the provider does not actually guarantee uptime.
Lucky that this is just a minor issue. God forbid this young support chap gives the wrong advice regarding something major and causes some real damage to our sites.
Bluehost, if you’re reading this, PLEASE train your trainees. This is not acceptable.
3. No Uptime Guarantee
After ranting about it in the earlier point, I can’t really not talk about the lack of uptime guarantee here.
Downtime is quite detrimental to any website. You lose potential sales or conversions if your site is experiencing downtime, and if it’s consistent enough, search engines might not even bother listing your site.
This is why an uptime guarantee is important.
It shows you that the provider is committed to keeping your site up and running, and they’re willing to compensate customers if they face downtimes of below a certain percentage.
Not having one is a giant red flag in our books.
That being said, we have to give Bluehost props – their uptime is actually fantastic, as evidenced by the uptime data collected from our test site.
For the lazy, it’s been at 100% since April 2008. Quite an impressive feat!
4. Dodgy Checkout Practices
Pretty sure everyone reading this will be familiar with the sleazy used car salesman that tries to slyly upsell you things you don’t really need just to make a higher sale.
Making a purchase with Bluehost feels a little bit like we’re dealing with people of that sort.
Upon checkout, the box for SEO tools and Sitelock will be checked, which pushes the price up to close to $60 a year.
These things are nice to have but are completely unnecessary, and unsuspecting buyers might just click next and make the purchase unknowingly – which happened to me.
Make sure you uncheck these boxes before making your purchase (unless you actually want these features).
VPS Hosting
If you’re in need of VPS hosting, Bluehost’s virtual private servers are sure to please. Supported with SSD storage, you’ll enjoy all the power, flexibility and control you’ll need for your VPS needs.
Plans range from $18.99 – $59.99 a month.
Dedicated Hosting
Bluehost’s dedicated hosting plans allow users to have unrestricted access to their servers. With their industry-leading robust platform, you’ll get to enjoy powerful flexible hosting at decent prices.
Their dedicated hosting plans range from $79.99 – $119.99 per month.
GET 33% OFF @ BLUEHOST BASIC (FOR $3.95/MO)
* Price shown is based on 36-month subscription. ** 30-day money back guarantee!
Verdict: Bluehost Is Good, But Not The Best Choice!
Just because we didn’t pick Bluehost to be the best web hosting brand, doesn’t mean that they’re not a good service provider.
They’re actually pretty decent, providing their users with fast enough speeds worldwide to ensure their users’ sites are loaded fast enough to generate a healthy amount of sales.
With superb useability and great UX, Bluehost is fantastic for beginners. Their WordPress recommendation should speak volumes about their service.
One thing we need to mention is that Bluehost is still using cPanel, which is great news for those of us that are accustomed to using it. Since cPanel increased their prices, most web hosting providers have decided to dump them, but so far there seems to be no indication of Bluehost dropping cPanel.
However, the lack of an uptime guarantee got us pretty peeved, as most major providers have the balls to provide some sort of compensation if their users’ sites are down for a certain amount of time.
The very fact that the companies are willing to put their money where their mouth is, inspires confidence. Bluehost does exactly the opposite without an uptime guarantee… what if the websites hosted with them go down for an entire week?
Anyone can promise to “strive to maintain network and server uptime” but it means completely jack if they can’t sack up and foot the bill when shit hits the fan.
However, credit where credit is due – we’ve never had a problem with Bluehost’s actual uptime before. As a matter of fact, the uptime has been 100% on our test site since April 2018!
Our humble opinion is that Bluehost is a pretty strong hosting provider. They may not be the fastest and they may not be the best, but if you’re just looking to host a simple website, they’ve got all the tools you’ll need to do so effectively.
#hosting#web hosting#best hosting#hosting reviews#make money 2021#make money online#make money as an affiliate
0 notes
Text
Microsoft Defender ATP is now available for Android
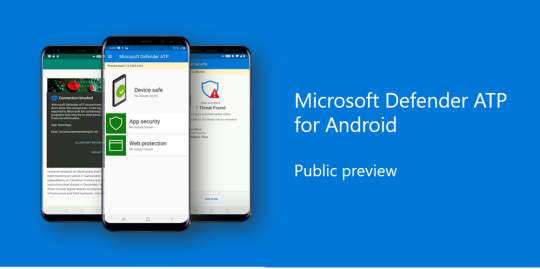
Microsoft is gradually expanding its antivirus software protection to smartphones and other OSs. The software giant has announced that its native Microsoft Defender Advanced Threat Protection (ATP) software is now available for Android in preview, and will be coming to iOS later this year.
In the world of growing malware, antivirus softwares are turning as a must-have resource in every device. Cyberattackers are indeed evolving with new techniques to bypass traditional security walls, and spy or steal your data. Thus, having authentic antivirus software is a must. And what could be more trusted than Microsoft, the one which is been in making such products for decades.
Microsoft has yesterday announced that its famous antivirus protection software, the Microsoft Defender Advanced Threat Protection (ATP) is now available for Android in preview mode. Interested users can try the public preview starting today, for free. It’s able to perform Quick and Full scans, and inform user about any threats.
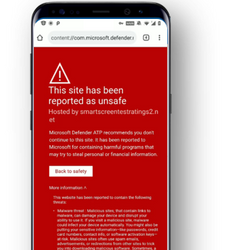
Scanning with this new protection software will surface any malware or potentially unwanted apps and will push a lightweight notification on the top saying everything’s okay if it’s okay. Besides these, it has web protections like anti-phishing feature to detect an unsafe website that’s routed via SMS, WhatsApp, email or other apps, and block them instantly.
Also Read: 5 Best Custom ROMs for your Android phone

Further, there’s an option called Defender SmartScreen technology, that would detect and block unsafe network connections, that are created by malicious apps for stealing data or snooping. This adds as an extra layer of security over Google’s existing Play Protect and web abuse detectors.
Besides Android, Microsoft says an iOS client of this software will be coming soon. This could be limited, as Apple allows only verified apps from Appstore, thus doing most. And it has released a stable client for Linux desktop users too! This makes the company have uniform services across most used services like Windows, macOS, Linux, Android and iOS.
More to read:
Google introduces one-tap sign-in feature for more easy access
Snapdragon 865 vs Exynos 990: Comparision, similarities, differences
Vivo X50 Series: Price, specifications, features
Qualcomm to bring 5G for budget phones with its new Snapdragon 690 processor
The post Microsoft Defender ATP is now available for Android appeared first on Androidical.
from https://ift.tt/3dA5PxK
0 notes
Photo

Aircrack-ng is a network software suite consisting of a detector, packet sniffer, WEP and WPA/WPA2-PSK cracker and analysis tool for 802.11 wireless LANs. It focuses on different areas of Wifi security. • Monitoring: Packet capture and export of data to text files for further processing by third party tools. Attacking: Replay attacks, deauthentication, fake access points and others via packet injection. Testing: Checking WiFi cards and driver capabilities (capture and injection). Cracking: WEP and WPA PSK (WPA 1 and 2). aircrack-ng software suite main tools: 1. aircrack-ng -> Cracks WEP keys using the Fluhrer, Mantin and Shamir attack(FMS) attack, PTW attack, and dictionary attacks and WPA/WPA2-PSK using dictionary attacks. 2.airdecap-ng -> Decrypts WEP or WPA encrypted capture files with known key. 3.airmon-ng -> Places different cards in monitor mode. 4. aireplay-ng -> Packet injector (Linux, and Windows with CommView drivers). 5. airodump-ng -> Packet sniffer: Places air traffic into pcap or IVS files and shows information about networks. 6. airbase-ng -> Incorporates techniques for attacking client, as opposed to Access Points. Follow @cybersec_society ... ... ... #cyber #hacker #wifihacking #wifi #wpa #wep #wps #encryption #handshakes #handshake #packet #sniffing #kalilinux #kalilinuxtools #aircrack #aircrackng #password #passwordcracking #instagram #cybersecurity #website #malware #ransomware #coding #programming #reaver #wifipassword #programmer #programminglife #coder https://www.instagram.com/p/CAnFGqdDPS6/?igshid=14yr16oaf9z2n
#cyber#hacker#wifihacking#wifi#wpa#wep#wps#encryption#handshakes#handshake#packet#sniffing#kalilinux#kalilinuxtools#aircrack#aircrackng#password#passwordcracking#instagram#cybersecurity#website#malware#ransomware#coding#programming#reaver#wifipassword#programmer#programminglife#coder
0 notes
Text
Original Post from FireEye Author: Vikram Hegde
This blog post presents a machine learning (ML) approach to solving an emerging security problem: detecting obfuscated Windows command line invocations on endpoints. We start out with an introduction to this relatively new threat capability, and then discuss how such problems have traditionally been handled. We then describe a machine learning approach to solving this problem and point out how ML vastly simplifies development and maintenance of a robust obfuscation detector. Finally, we present the results obtained using two different ML techniques and compare the benefits of each.
Introduction
Malicious actors are increasingly “living off the land,” using built-in utilities such as PowerShell and the Windows Command Processor (cmd.exe) as part of their infection workflow in an effort to minimize the chance of detection and bypass whitelisting defense strategies. The release of new obfuscation tools makes detection of these threats even more difficult by adding a layer of indirection between the visible syntax and the final behavior of the command. For example, Invoke-Obfuscation and Invoke-DOSfuscation are two recently released tools that automate the obfuscation of Powershell and Windows command lines respectively.
The traditional pattern matching and rule-based approaches for detecting obfuscation are difficult to develop and generalize, and can pose a huge maintenance headache for defenders. We will show how using ML techniques can address this problem.
Detecting obfuscated command lines is a very useful technique because it allows defenders to reduce the data they must review by providing a strong filter for possibly malicious activity. While there are some examples of “legitimate” obfuscation in the wild, in the overwhelming majority of cases, the presence of obfuscation generally serves as a signal for malicious intent.
Background
There has been a long history of obfuscation being employed to hide the presence of malware, ranging from encryption of malicious payloads (starting with the Cascade virus) and obfuscation of strings, to JavaScript obfuscation. The purpose of obfuscation is two-fold:
Make it harder to find patterns in executable code, strings or scripts that can easily be detected by defensive software.
Make it harder for reverse engineers and analysts to decipher and fully understand what the malware is doing.
In that sense, command line obfuscation is not a new problem – it is just that the target of obfuscation (the Windows Command Processor) is relatively new. The recent release of tools such as Invoke-Obfuscation (for PowerShell) and Invoke-DOSfuscation (for cmd.exe) have demonstrated just how flexible these commands are, and how even incredibly complex obfuscation will still run commands effectively.
There are two categorical axes in the space of obfuscated vs. non-obfuscated command lines: simple/complex and clear/obfuscated (see Figure 1 and Figure 2). For this discussion “simple” means generally short and relatively uncomplicated, but can still contain obfuscation, while “complex” means long, complicated strings that may or may not be obfuscated. Thus, the simple/complex axis is orthogonal to obfuscated/unobfuscated. The interplay of these two axes produce many boundary cases where simple heuristics to detect if a script is obfuscated (e.g. length of a command) will produce false positives on unobfuscated samples. The flexibility of the command line processor makes classification a difficult task from an ML perspective.
Figure 1: Dimensions of obfuscation
Figure 2: Examples of weak and strong obfuscation
Traditional Obfuscation Detection
Traditional obfuscation detection can be split into three approaches. One approach is to write a large number of complex regular expressions to match the most commonly abused syntax of the Windows command line. Figure 3 shows one such regular expression that attempts to match ampersand chaining with a call command, a common pattern seen in obfuscation. Figure 4 shows an example command sequence this regex is designed to detect.
Figure 3: A common obfuscation pattern captured as a regular expression
Figure 4: A common obfuscation pattern (calling echo in obfuscated fashion in this example)
There are two problems with this approach. First, it is virtually impossible to develop regular expressions to cover every possible abuse of the command line. The flexibility of the command line results in a non-regular language, which is feasible yet impractical to express using regular expressions. A second issue with this approach is that even if a regular expression exists for the technique a malicious sample is using, a determined attacker can make minor modifications to avoid the regular expression. Figure 5 shows a minor modification to the sequence in Figure 4, which avoids the regex detection.
Figure 5: A minor change (extra carets) to an obfuscated command line that breaks the regular expression in Figure 3
The second approach, which is closer to an ML approach, involves writing complex if-then rules. However, these rules are hard to derive, are complex to verify, and pose a significant maintenance burden as authors evolve to escape detection by such rules. Figure 6 shows one such if-then rule.
Figure 6: An if-then rule that *may* indicate obfuscation (notice how loose this rule is, and how false positives are likely)
A third approach is to combine regular expressions and if-then rules. This greatly complicates the development and maintenance burden, and still suffers from the same weaknesses that make the first two approaches fragile. Figure 7 shows an example of an if-then rule with regular expressions. Clearly, it is easy to appreciate how burdensome it is to generate, test, maintain and determine the efficacy of such rules.
Figure 7: A combination of an if-then rule with regular expressions to detect obfuscation (a real hand-built obfuscation detector would consist of tens or hundreds of rules and still have gaps in its detection)
The ML Approach – Moving Beyond Pattern Matching and Rules
Using ML simplifies the solution to these problems. We will illustrate two ML approaches: a feature-based approach and a feature-less end-to-end approach.
There are some ML techniques that can work with any kind of raw data (provided it is numeric), and neural networks are a prime example. Most other ML algorithms require the modeler to extract pertinent information, called features, from raw data before they are fed into the algorithm. Some examples of this latter type are tree-based algorithms, which we will also look at in this blog (we described the structure and uses of Tree-Based algorithms in a previous blog post, where we used a Gradient-Boosted Tree-Based Model).
ML Basics – Neural Networks
Neural networks are a type of ML algorithm that have recently become very popular and consist of a series of elements called neurons. A neuron is essentially an element that takes a set of inputs, computes a weighted sum of these inputs, and then feeds the sum into a non-linear function. It has been shown that a relatively shallow network of neurons can approximate any continuous mapping between input and output. The specific type of neural network we used for this research is what is called a Convolutional Neural Network (CNN), which was developed primarily for computer vision applications, but has also found success in other domains including natural language processing. One of the main benefits of a neural network is that it can be trained without having to manually engineer features.
Featureless ML
While neural networks can be used with feature data, one of the attractions of this approach is that it can work with raw data (converted into numeric form) without doing any feature design or extraction. The first step in the model is converting text data into numeric form. We used a character-based encoding where each character type was encoded by a real valued number. The value was automatically derived during training and conveys semantic information about the relationships between characters as they apply to cmd.exe syntax.
Feature-Based ML
We also experimented with hand-engineered features and a Gradient Boosted Decision Tree algorithm. The features developed for this model were largely statistical in nature – derived from the presence and frequency of character sets and keywords. For example, the presence of dozens of ‘%’ characters or long, contiguous strings might contribute to detecting potential obfuscation. While any single feature will not perfectly separate the two classes, a combination of features as present in a tree-based model can learn flexible patterns in the data. The expectation is that those patterns are robust and can generalize to future obfuscation variants.
Data and Experiments
To develop our models, we collected non-obfuscated data from tens of thousands of endpoint events and generated obfuscated data using a variety of methods in Invoke-DOSfuscation. We developed our models using roughly 80 percent of the data as training data, and tested them on the remaining 20 percent. We ensured that our train-test split was stratified. For featureless ML (i.e. neural networks), we simply input Unicode code points into the first layer of the CNN model. The first layer converts the code point into semantically meaningful numerical representations (called embeddings) before feeding it into the rest of the neural network.
For the Gradient Boosted Tree method, we generated a number of features from the raw command lines. The following are some of them:
Length of the command line
The number of carets in the command line
The count of pipe symbols
The fraction of white space in the command line
The fraction of special characters
Entropy of the string
The frequency of the strings “cmd” and “power” in the command line
While each of these features individually is a weak signal and could not possibly be a good discriminator on its own, a flexible classifier such as a Gradient Boosted Tree – trained on sufficient data with these features – is able to classify obfuscated and non-obfuscated command lines in spite of the aforementioned difficulties.
Results
Evaluated against our test set, we were able to get nearly identical results from our Gradient Boosted Tree and neural network models.
The results for the GBT model were near perfect with metrics such as F1-score, precision, and recall all being close to 1.0. The CNN model was slightly less accurate.
While we certainly do not expect perfect results in a real-world scenario, these lab results were nonetheless encouraging. Recall that all of our obfuscated examples were generated by one source, namely the Invoke-DOSfuscation tool. While Invoke-DOSfuscation generates a wide variety of obfuscated samples, in the real world we expect to see at least some samples that are quite dissimilar from any that Invoke-DOSfuscation generates. We are currently collecting real world obfuscated command lines to get a more accurate picture of the generalizability of this model on obfuscated samples from actual malicious actors. We expect that command obfuscation, similar to PowerShell obfuscation before it, will continue to emerge in new malware families.
As an additional test we asked Daniel Bohannon (author of Invoke-DOSfuscation, the Windows command line obfuscation tool) to come up with obfuscated samples that in his experience would be difficult for a traditional obfuscation detector. In every case, our ML detector was still able to detect obfuscation. Some examples are shown in Figure 8.
Figure 8: Some examples of obfuscated text used to test and attempt to defeat the ML obfuscation detector (all were correctly identified as obfuscated text)
We also created very cryptic looking texts that, although valid Windows command lines and non-obfuscated, appear slightly obfuscated to a human observer. This was done to test efficacy of the detector with boundary examples. The detector was correctly able to classify the text as non-obfuscated in this case as well. Figure 9 shows one such example.
Figure 9: An example that appears on first glance to be obfuscated, but isn’t really and would likely fool a non-ML solution (however, the ML obfuscation detector currently identifies it as non-obfuscated)
Finally, Figure 10 shows a complicated yet non-obfuscated command line that is correctly classified by our obfuscation detector, but would likely fool a non-ML detector based on statistical features (for example a rule-based detector with a hand-crafted weighing scheme and a threshold, using features such as the proportion of special characters, length of the command line or entropy of the command line).
Figure 10: An example that would likely be misclassified by an ML detector that uses simplistic statistical features; however, our ML obfuscation detector currently identifies it as non-obfuscated
CNN vs. GBT Results
We compared the results of a heavily tuned GBT classifier built using carefully selected features to those of a CNN trained with raw data (featureless ML). While the CNN architecture was not heavily tuned, it is interesting to note that with samples such as those in Figure 10, the GBT classifier confidently predicted non-obfuscated with a score of 19.7 percent (the complement of the measure of the classifier’s confidence in non-obfuscation). Meanwhile, the CNN classifier predicted non-obfuscated with a confidence probability of 50 percent – right at the boundary between obfuscated and non-obfuscated. The number of misclassifications of the CNN model was also more than that of the Gradient Boosted Tree model. Both of these are most likely the result of inadequate tuning of the CNN, and not a fundamental shortcoming of the featureless approach.
Conclusion
In this blog post we described an ML approach to detecting obfuscated Windows command lines, which can be used as a signal to help identify malicious command line usage. Using ML techniques, we demonstrated a highly accurate mechanism for detecting such command lines without resorting to the often inadequate and costly technique of maintaining complex if-then rules and regular expressions. The more comprehensive ML approach is flexible enough to catch new variations in obfuscation, and when gaps are detected, it can usually be handled by adding some well-chosen evader samples to the training set and retraining the model.
This successful application of ML is yet another demonstration of the usefulness of ML in replacing complex manual or programmatic approaches to problems in computer security. In the years to come, we anticipate ML to take an increasingly important role both at FireEye and in the rest of the cyber security industry.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Vikram Hegde Obfuscated Command Line Detection Using Machine Learning Original Post from FireEye Author: Vikram Hegde This blog post presents a machine learning (ML) approach to solving…
0 notes
Text
Starting out Using Android Advancement
Android telephones in Verizon vary between people using touch-screens and instinctive cameras for people who have a QWERTY computer keyboard and instinctive sharing. Change your device and also share its link with as much as 10 apparatus at the same time. Throughout evolution the create process suggests that the application using a crucial that is purge. Scoped folder accessibility: Programs might ask use of certain folders that you may enable or refuse usage of (just like program run-time permissions). Android was built to allow programmers to generate mobile programs that take benefit of a handset that offers. Put on the look fundamentals which specify the visible terminology of Android throughout many form elements, making use of alterations fabric style and design aspects and images, into a programs. Watch what is fresh with Android - out of mobiles to watches and much more. The application form might specify by means of a statement at the file specify which components of applications comprises is currently requires. Android is now a mobile platform taken care of and possessed from Google. As an instance, a programmer can unite information about the mobile mobile -- like an individual's calendar, contacts, or location of an individual. Google states Tizi may conduct a variety of surgeries, however, many attention on networking action and programs. Utilize teachers detail by detail to assemble a more cloud-connected mobile program. As it is demanded in an Android Marshmallow apparatus, programs developed for Android Marshmallow request consent directly. Orbot can be a program which enables cellular cell phone users to directly gain access to instant messaging, the web and electronic mail without obstructed or being tracked with their own online supplier that is cellular. Take observe that you want touse precisely the exact same touch type into Google engage in (Google current market) to upgrade your own application. Assess Android phones. Prevent the others from snooping in messages your images, and even documents from bending all of your programs using a PIN code that is distinctive. She's passionate about supporting the others build programs to better their communities. Have a look wearables, tablet computers & versions information, opinionsand programs with Android Conquer articles or blog posts, videos & photos & specs. Utilize fingerprint detectors create purchases from Google perform and to unlock your apparatus, Demo transactions and also cover from your merchants. One option concern: that the capability user 's messaging program, Textra SMS. Research tablet computers, the Android mobiles, wearables, automobile televisions and consoles that you may utilize to optimise your electronic lifestyle. A program installed to the outside storage has been ceased when the unit is joined to some type of pc and mounted as USB storage. 7.1 in case you apply this SDK to conduct software manufactured by way of a 3rd party or that access info, resources or content offered with a 3rd party, then you consent that Google isn't accountable for such softwaresuch as content, data, or tools. It's necessary for you to provide a ID through the identification feature to the opinion when an opinion has to be obtained by way of Java or XML code. Android lets to put in applications. https://qwertyuiopasdfghjklzxcvbnm.me The next screen shot indicates the G-mail application that works by using FrameLayout to produce a few button in addition to some other design. You also can put input controls and insert them into your Card thing for those who have any data that you just may love to associate for example as for example address, name, or ZIP code. Programs while in the desktop wont be in a position to gain access to data that is mobile when Information Saver has been fired up. Proceed to Settings, then tap lock display and also security, and also check out Settings on lock-screen (those may possibly possess marginally different titles based upon your own particular apparatus and Android variant, however it will be quite evident at which to proceed). On your actions (along with fragment) code that you usually have to gain access to the viewpoints to get and alter their own possessions. Although Android devices send having a composite of source and proprietary software, Google releases Android's origin code underneath a opensource permit. Even the 8.1 release also has acceleration for system mastering by way of TensorFlow Lite , effectiveness developments such as Android Go mobiles plus a plethora of minor tweaks. ONEPLUS 5 proprietors are now able to improve their smart phone towards the most recent edition of Android, however, it is possibly most useful to steer clear of the upgrade to today. Transfer apps your own account and data into a system. The Android product Manager of Google can be a device for safeguarding your own private info and locating a Android mobile. The "Program Information" display screen indicates this variant. Together side the Android apparatus, we provide the broad selection of accessories. Androidstudio includes. 12.1 On the greatest extent allowed bylaw, you agree to protect, indemnify and hold benign Google, its associates and their individual directors, directors, staff and representatives against and from any and all claims, actions, lawsuits or event, in addition to any and all losses, obligations, damages, expenses and costs (including reasonable lawyers fees) arising from or accruing from (a) that your usage of this SDK, (b)) any app that you grow onto the SDK that infringes any copyright, trade mark, trade secret, trade dress, patent or any intellectual property from any individual or defames any individual or violates their rights of privacy or publicity, and (c) any noncompliance by you with all the License contract. Scans all records and programs immediately and quickly for malware or even maybe undesirable programs like display screen lockers or spyware. Google has recently released the last trailer assemble of Android 8.1, also a smaller update to Android Oreo because out the following 30 days. ConstraintLayout could be the layout supervisor for programs that are contemporary, nonetheless it's heavily depending around the design editor. However, together with Apparatus Lock should the SIM card is replaced by anybody, guarding your mobile, your own mobile will automatically lock itself to keep them from obtaining your personal information and generating forecasts. Even though look-up employs phone numbers because encrypted, contacts messages and calls actually utilize your computer data management; hence both functions into this dialog has to have access to the internet in their cellular apparatus. Learning sometimes happens anywhere faster and including improved navigation streaming for every mastering. Client Mode: For if you must continue to keep your kids or give your own mobile to a buddy, times, a few LG Android apparatus supply you with the choice to turn in to guest manner, that enables one to get a grip on exactly what programs and advice are also readily available to your consumer. Many users don't need full command on the personalized info in their own apparatus. Evaluation your network rate that is cell in your own Android. Obtain the Ookla Speedtest program that is Completely Free. Ginger bread served life by knowing how it is used by your apparatus, you obtain the absolute most life from your own battery life; figure out exactly how much each and every facet of one's device consumes into any program. This display it all below the set of apparatus and then may make the AVD settings. Eclair substituted the comma key on the keyboard having a microphone. HDR+ at a camera-phone is similar to saying that a 4K monitor is far better compared to the usual 720p a single for playing with 720p online video. Smartphones in Verizon vary between people using cameras that are instinctive and touch screens for people who have instinctive sharing and a QWERTY computer keyboard. Information and testimonials of applications and hardware. Groundbreaking a fresh amount of support, Google provides you the weather until you walk right outside the entranceway, since you are getting dressed up and dressed days of today. WebOS was introduced to be published since Free computer software It was seen if there'll be devices and also regardless of whether all components will probably soon be liberated. Nevertheless Google does not allow anybody to send its software provided that the unit isn't licensed and also the seller did not sign a deal together with Google. Mono output: Access mono output aids end users with hearing loss in 1 ear by combining left- and - right-channel output signal to a mono flow. The doorway opened up featuring screens apart from 320 x 480 camera. However, if programmers start off playing around with Google's imaging processor this past month, then there ought to be programs willing to make the most of this if 8.1 is published commonly in December. Vehicle backup for Programs: easy-to-use program data restore and backup. Your app will be found through the server procedure program launcher and ought to be set up as a member of their Anbox run-time. The perform retail store delivers a overwhelming number of options, however there are programs available on the market. Go to Amazon App Store or the Google Engage in Retailer . Offers a market place by which their software can be offered by developers for Android people, that the Google engage in support. Ours has been the primary anti virus app to violate one hundred million downloads, and also is now used to procure tablet computers and mobiles .
0 notes
Text
The 7 Most Frequently Asked Questions About Dangerous Apps in the Play Store
New Post has been published on https://dailytechhub.com/7-questions-dangerous-apps-play-store/
The 7 Most Frequently Asked Questions About Dangerous Apps in the Play Store
Dangerous apps regularly appear in the Play Store. But how do you know if an Android app is dangerous? And how can you remove them again? Dailytechhub will explain this in detail for your benefit.
Table of Contents
1 This way you can remove and recognize dangerous Android apps
1.1 1. Which Apps are infected?
1.2 2. How do I recognize a dangerous app in the Play Store?
1.3 3. How do I delete a Dangerous App?
1.4 4. What are the best anti-virus Apps for Android?
1.5 5. Can’t I better use internet banking at all?
1.6 6. Why does Google not offer better protection?
1.7 7. Why is Android more insecure than iOS?
This way you can remove and recognize dangerous Android apps
Almost no week passes, or new dangerous apps dive into the Play Store. In a week, there are new apps that try to get hold of your bank details in the background, the next week viruses are hidden in seemingly innocent flashlight apps. Our readers regularly want to know how they can best be protected as an Android user, and which steps they can take. This is how you can only remove dangerous Android apps, but also recognize and prevent them.
1. Which Apps are infected?
Dangerous apps regularly appear in the Play Store. However, by the time they are discovered, Google has already removed them. Moreover, they often have very generic names, which conceal the true nature of the app.
Recently, security researchers discovered viruses in apps with names such as ‘News Pro‘, ‘Android Cleaner‘ and ‘Tornado Flashlight‘. Malware also pretends to be other, well-known apps, with minor variations. For example, a virus can hide in WhatsApp Download for Android, while WhatsApp itself is completely safe.
2. How do I recognize a dangerous app in the Play Store?
So it is still a big task to avoid malware in the Play Store. The greatest help you have with that is your common sense. If an app promises things that are too good to be true, do not download it. If there are strange images or other questionable content, then you should at least check thoroughly before you start downloading.
Your fellow users can also help. In the Play Store, you can see how often an app has been downloaded. For example, if you have opened an app that pretends to be WhatsApp, but has only 10,000 downloads, it is probably a fake app and checks the reviews. If an app gets a lot of negative reviews with low ratings, leave it to the left.
Smartphone Buying Guide
The big Android Version overview
Lastly, pay close attention to permissions. All Android apps ask you for permission to use the different functions on your smartphone. For example, WhatsApp needs access to your camera to take photos, while Facebook wants to see your contacts to add more friends. But if a flashlight app requires permission to send text messages, then you better refuse. Also, a news app usually does not really need access to your microphone. When in doubt, you simply refuse, even if it is a safe app. The app often continues to function; only some functions will not be available.
3. How do I delete a Dangerous App?
Do you think you have a dangerous app on your smartphone? then you better protect it as soon as possible. Download an antivirus app, or follow the steps below to resolve and uninstall the app.
Open your settings, and go to ‘Security‘;
Select the heading ‘Device manager‘ or ‘Apps for device management’ or device administrator, depending on which version of Android you use;
If there are apps such as Adobe Flash Player, Adobe Update or Android Update in between, switch it off;
Then remove the apps from your smartphone by going to ‘Apps’ in the settings. Remove not only the apps with Device Manager but also the programs that you gave in the Play Store at the time to download files in the background.
4. What are the best anti-virus Apps for Android?
If you have a desktop computer or laptop, it is probably equipped with a virus scanner. It warns you when a virus pops up, and can often also remove it immediately. On Android, virus scanners are slightly less effective, because an app cannot just get involved. So, see them as a smoke detector which serves as a notification channel if you have received a virus, but it is then up to you to take action.
Yet a virus scanner is certainly not a bad idea if you are afraid of dangerous apps. Among others, we recommend ESET, Avast and Malwarebytes. A free version of all three is available, with which you automatically and regularly scan your smartphone for malware. Of these apps are often also paid variants available. For example, they can block advertising in your browser, protect your photos better or remotely erase your device if it is stolen.
5. Can’t I better use internet banking at all?
If you do not have a bank app on your smartphone, you indeed run less risk. However, if you are going to start this way, you better not use a smartphone at all. Moreover, a bank app can help you to handle your money more wisely. You can see everywhere and always how much money is left in your account. And if you want to keep an eye on whether there are no weird transfers, you can do that at any time via the app.
Moreover, the bank apps are often not the problem; they are well encrypted so that malicious people cannot really just break in. The danger is in other apps or websites that pretend to be your bank, or that, for example, read out your SMS messages with verification codes.
6. Why does Google not offer better protection?
Although Google promises improvement at every break in Android, these improvements do not seem to help in a very hard situation. The operating system is now ten years old but is still plagued by vulnerabilities. A frequently asked question is why Google does not do something about it.
The answer: Google does take steps, but the manufacturer of your smartphone often notices that much. For example, since 2015, Google has released security updates every month. They offer good protection against all known vulnerabilities, regardless of which version of Android is on your device or tablet. Unfortunately, manufacturers must then make those updates suitable for their devices and release them. And they sometimes reject it. Some manufacturers only issue a security update every three months, others do not even at all.
To tackle the problem at the root, Google launched Play Protect this summer. This means that all apps on your smartphone and in the Play Store are continuously checked for possible viruses. Unfortunately, a recent study shows that Play Protect only stops about 70 percent of all viruses. Remarkable, because most of the virus scanners we mention above offer protection of 95 percent or better. For now, it is no more than a nice promise from Google.
7. Why is Android more insecure than iOS?
Although you regularly hear about new dangers for Android, there are rarely any security problems around the iPhone. That does not mean that with iOS, Apple’s operating system, you are always 100 percent safe. However, you generally run a lot less risk.
That is not because Apple is much stricter, but especially because iOS is a lot more closed. Android apps can adjust pretty large parts of your smartphone. For example, there are apps that change your home screen or read your text messages and where you cannot change your default apps on iOS, you’re not just stuck on Chrome or the Gmail app on Android.
With iOS, apps work a lot more separately, and they cannot actually take over system functions. As a result, an iOS app can also do a lot less damage. It then ensures that Android offers you much more freedom.
Do you have other questions about dangerous apps? Ask them in the comments so that we can help you!
0 notes
Text
Take Pleasure In Dish Network Shows Online
A manager is located in an essential place for individuals who work strongly with them. Actually , managers are likely the most powerfulk people inside society nowadays. Most people benefit an employer -- and that implies most people will have a manager.
Third reason is usually that the business on the internet runs twenty-four hours a day throughout the year. Once your internet shop or even website increased and jogging it in no way closes until you want it to. When 1 part of the globe sleeps additional wakes up. Your workplace is up in addition to running throughout day and night. Minimum office problems and minimum of employee connected headaches.
Join a class business lead by an experienced and competent expert. May waste your time and efforts or funds on any approach that can not verify the qualifications of the expert and permit you access to the experts' advice. Basically want to learn how you can a develop house, We wouldn't would like to learn from a software engineer. Because everyone has a distinctive style of studying and an organic brain, you need to learn from someone who understands those differences. Paying for expertise will be significant when it comes to your ongoing mastery of the skills.
Do we jump on board the Social networking train? Is it just hype, the latest buzz, a stupidity? Can it really be beneficial for companies? These concerns deserve an honest answer.
Sometimes we get so involved in huge goals and forget to celebrate the little achievements. That 1st small affiliate marketer check, that first $3 AdSense time, 5 new pages included with a web site, a great unsolicited, glowing testimonial with your product, and so forth Keep a log of all of the little success that take place in your business and review them when you need to get encouraged again. Keep a "done" list close to your "to do" checklist.
The truth is, we can all tolerate a slow computer, yet very few of us would want other people to have entry to the information on our computers, but that is just what can happen any time spyware or even malware is loaded on our computers without our knowledge.
A great way to come across and remove spyware would be to run a spyware detector plus remover. Nearly all spyware detection and removing software these days offers a free of charge scan in order to verify that you do or do not have spyware on your pc.
0 notes
Text
Township Hack, the Best Game Cheat of All Time
Gaming is one of the passion things among many. Gaming has no sex or age limits. It brings out the best virtual experience, especially when integrated with graphics, videos, music and tips to handle every issue in games. For the ultimate gaming experience, Township Hack is probably what you require as a real gamer. No matter how many times you play Township still you do not get bored. Read the article below and understand Township Game and Township Hack better. About the Township Game Township is a mobile smartphone game that was released in late 2013. Basically, it is a city building game playable on different platforms such as Android, Windows, and iOS. You can construct and establish anything to make your town a better place. It has many comforts in the beginning so you don't have to start from the scratch. You are free to introduce suburbs that support agricultural activities as well as modern services such as railways. At advanced levels, you are permitted to add facilities, services, and characteristics of a modern and genuine city. There are daily and weekly bonus (in-game coins and cash). In addition, social media linkage provisions are available. The 80 MB size app can be acquired at no cost in the Google Play Store. Like many smartphone game companies, players can buy gems and gold as game resources and get dollars out of the buyers' pocket as well. Many players hate spending money on smartphone devices apart from a few rich brats who care less. Consequently, the launch of Township Hack in 2016 comes as a free solution on how to get Free Cash and Coin in Township. Township Hack Features and Information Township Hack 2016 has been tested in beta mode and released for global use after receiving a lot of positive reviews. The hack comes in both downloadable and online version. The online is very much safe to use; unlike many download tools out there where you can download anything. Therefore there are minimal chances of getting virus and malware that may inhibit effective functioning of your device. It is also user-friendly since one only gives information about the coins and cash they want. Playrix Games Programmers have allowed numerous fascinating features such as: i) Coins hack ii) Cash hack iii) No Jailbreak required iv) Virus safe v) Anti-ban vi) No root needed vii) Automatic update check viii) Many other resources With the help of the above features, you will beat all your family and friends playing township as well get access to the unlimited resources to advanced levels. Learn how to Use Township Hack For your hack to work effectively, you should use Township username on the Cheat application. You don't have to worry about security since the hack comes with the anti-ban feature. However, it is recommended not to use it more than 5 times in a day. Since the entire application is an online variant, the only necessity is an internet connection. Below is a guide on how to use the hack: a) Locate the Township Hack Button and click it. b) Insert your username after clicking the hack. It is worth noting that you should use your Township username. c) Shortly you will be asked a number of resources you want to be gained into the game. So put your desired amount. d) If you wish to become that ultimate Township winner, it is advisable to add huge sums of township coins/cash. e) Once you have added the money, you need to have the activation step. One has to confirm they are human because the cheat is protected against bots. Don't worry, it is very simple, just give fake information. The process takes only 3 minutes. When you are done, it is time to have fun and power out your friends. You will receive your cash within two hours to twelve hours maximum. Advantages of Township Online Resources Generator i) Access to unlimited resources ii) Frequent script updates. If you want to be part of the reviewer team and future updates, you can become a beta member. iii) No download needed iv) Tested and undetectable v) 24/7 online access vi) Added advantage within the game Frequently Asked Questions Is Online Township Cheat Tool Safe? This is a nice question that everyone on the internet is asking about. Township cheats and hacks are 100% secure. It is also crucial to mention that there is no need of rooting your Android gadget or jailbreak your iOs device. The hack has been tested on thousands of Android, Windows, Mac and iOs devices and has delivered tremendous results. musically followers 2017 You can find proofs either on online Township Hacks sites or social media networks. Will I be Banned from the game? Most of the online township hacks and cheat sites will assure you won't be banned from your favorite game. This is because no human verification is detectable. Will I be Anonymous? Yes, working security measures that will help you stay protected and anonymous have been put in place. No one will ever know whose account you have conquered unless you tell. Why did I Receive a Gift Balloon from someone who has Never been My Friend? Be calm. This is no hack at all, just coincidence way of the system. Players are not matched to be friends and each player is an individual. You can have friends in your list while the one showering with gifts does not have you and vice versa. The New Township Hacks Without Surveys Previously, one was asked to do a survey. This was done with an aim of limiting the number of people using the cheat and ensuring the tool remains under the detector. As a result, by completing the survey, you are in a position to support hacks and cheats developers of your preferred game. However, the new Township Cheat without surveys is more straightforward and simple to understand. You can now generate cash, coins, extra XP, remove ads and level up with ease. Final Thoughts If you have been searching everywhere for the best cheat tool for iOS's amazing game, Township, look no further. Reviews from game enthusiasts confirm much fun was experienced after they found the awesome hack that allows them to generate unlimited resources. They have vowed to use the tool as long as best hacks and cheats continue to offer free cheats. All the best as you use Township Hack. Enjoy.
0 notes
Text
New Post has been published on Weblistposting
New Post has been published on https://weblistposting.com/a-way-to-hold-apps-from-invading-your-privacy/
A way to hold apps from invading your privacy
Apple’s iPhone become born 10 years in the past, launching a cellphone transformation that modified the manner consumers use and depend on their gadgets. Quite a few that usage hinges on mobile apps. They faucet into the records stored on your phone to remind you approximately appointments, find stores and eating places near you or let you know whether there’s heavy traffic on your commute. However, that convenience comes with a price: the loss of a few privateness.
statistics about your vicinity, sports, and debts is being shared with the app maker’s computers. It can then be used for advertising and marketing functions, be offered to other businesses, or maybe be stolen if the app — or the app maker’s servers — are hacked.
“Apps can also request administrative privileges for your information, and those privileges might be utilized by the app afterward, or through a few malware, to steal your private statistics,” says Ed Cabrera, leader cyber security officer at TrendMicro, a digital protection organization.
As an example, a recreation would possibly have to get right of entry to in your smartphone app in order that it is aware of while to pause for incoming calls. But that get admission to can also permit the app’s maker to concentrate in.
Shield Your privateness Online – a few Tips that will help you Guard Yourself Online
The net indeed is a handy tool for us to take part in Online discussions, do banking, shopping, do our businesses, communicate with our colleagues and in preserving in contact with own family and friends But one downside of it is the shortage of privacy.
The need to Defend your privateness Online has become growing as many unscrupulous individuals also take benefit of the convenience of the internet to prey on other human beings’ agencies. When you do sports Online, your IP cope with may be seen and your vicinity may be traced. whether you’re becoming a member of an online community, posting a comment on internet articles or weblog posts, taking part in forums and becoming a member of in social networking sites, you once in a while leave a trace to be able to be traced returned.
Most of those sports at the net request you to sign up along with your e-mail deal with and let you create profiles so as to listing information approximately you. Despite the fact that now and again you may be unmindful of giving out an excessive amount of information, those can but useful resource Online perpetrators and criminals to make you an clean prey. Here are a few Suggestions that will help you Shield your privacy Online and surf the net more secure.
– Do now not reveal too much personal data. Social networking websites these days are very famous However you need to be responsible enough to make sure you aren’t making your life too open for net viewers. occasionally you will be unmindful of what records you ought to no longer percentage, But remember that protective your privacy starts of evolved from you. Do not supply out your cell phone numbers carelessly On-line, and of direction, there’s no need to let all of the humans know approximately your precise home address. these are information that makes you vulnerable to identity robbery, fraud and different crimes.
– recognise whom you’re, sharing statistics Online. Even though this is one very hard issue to do Online, some sites like social networking websites in which you most customarily share private data allows you to govern your settings on who can access your personal records. It is also vital to not just befriend anyone Online. For positive, you’ll never realize who you’re handling on the internet, so as to Guard your privateness On-line, ensure you watched first before sharing and making friends On-line.
– Manipulate your cookies. Cookies are used to keep some information Whilst you go to websites. One component that It is able to do is to save your username and password so you might not be typing them While you visit the site the following time. It can additionally assist websites music what you’re surfing, time and date of visit as well as advertisements you clicked. Although they’re no longer supposed to damage your privateness, It can but be utilized by On-line criminals to get into your private facts. that will help you Protect your privateness Online, you could however Manipulate cookies by way of individually permitting or disabling them. Of path, you need to use correct judgment to whether the website is depended on or now not. you may also frequently delete cookies on your PC to keep away from undesirable cookies. 5 Simple Things you may Do to Protect Your privacy
We prepare a listing of 5 Matters you can do to Protect your privateness at home and away. they are based totally on actual occasions which you might discover difficult to trust.
1. If you are a ladies, sporting an inexpensive hidden digicam detector can Shield you from hidden cameras positioned in dressing rooms, fitness center lockers, public or non-public restrooms, or any place you would possibly have to exchange your clothes. The net is complete of these videos and you need to make certain you do not come to be on YouTube in a way you by no means meant. One female even located a hidden camera in the bathroom of her very own home! A repairman who was operating at the house installed the camera when he was there and pretty, the ladies found it.
2. On the ATM or fuel pump, ensure the component you insert your card is truly part of the device, and now not a fake faceplate placed on through criminals to scouse borrow your card records. Tug on it and spot if the front comes off without difficulty, as they use tape or Velcro to preserve it on. human beings have actually been caught in motors, close to ATM’s with fake face plates and tape, as well as wi-fi camera receivers with a video feed proper On the keypad to be able to see you input your pin.
3. Any time you need to input your PIN quantity to your credit playing cards, usually cool your hand with your other hand. There are numerous times of the equal criminals above posting cameras to also view the pin variety whilst they steal your card records. A small field wrapped in black electricians tape with an antenna sticking out turned into surely observed at a Wal-Mart counter pointing proper at human beings to steal credit score card and PIN information.
four. Be careful whom you give your credit or debit card to. Too frequently, we give a person a credit score card to pay for something and that they go and run the cardboard. If it’s miles feasible, watch them to see if they are taking down your records. this is a very famous way to get your records to use to buy goods without your information.
5. In case you are a single girls, baby, or aged individual, human beings use the smartphone to find victims they could take benefit of in many approaches. A Simple voice changer that can slightly regulate your voice is a great manner to fool a caller into questioning you are a exclusive person.
0 notes