#best hacking software for iphone
Explore tagged Tumblr posts
Text
Touching is Good: A Retrospective
My trusty Nintendo 3DS, which has held out since I was gifted it for my 15th birthday, has turned one decade old with my 25th birthday this past November. Given new life with custom firmware and nds-bootstrap via TWiLightMenu, the 3DS is stellar for visiting any past handheld title or console title up to (and somewhat including) the N64. (Quick plug for the CFW/hacking community for the less popular PS Vita, too, which has accomplished some pretty crazy-cool stuff this last year.) I use my 3DS more often than I use my Nintendo Switch most weeks.
The Nintendo DS (minus the three) launched in late 2004. The second display and stylus support were novel tools for developers to experiment with, and the NDS is best remembered for its robust catalogue of RPGs and visual novels. Where it lacked in power, narrative-focused games flourished under its technical limitations.
That being said, while browsing the ROM archives on Vimm's Lair to pick up some titles, I was reminded of what an interesting era the mid-to-late 2000s were for games. While Sony and Microsoft were fighting over the "core gamer" demographic, who had outgrown Nintendo mascots, Nintendo led a series of wildly successful marketing campaigns for its hardware after the light failure of the Gamecube, where the Nintendo DS and then the Wii were targeted at...everyone else.

[Image source. Image description in alt text.]
If you look at ads for the DS and the Wii, you'll see that adults are featured much more prominently than children, especially women and seniors. (This did not go unnoticed, as I found this ancient relic of misogyny while looking for images for this post.) A Nintendo handheld was already an easy sell to parents with small children (though I think it's also notable that ads which do focus on children often prominently feature girls. Munchlax is pretty hot...), but Nintendo's angle for the DS and Wii was that their hardware wasn't just for children. The Wii was a way to get up off the couch and to play board games with grandma. The DS was a great gadget for a working woman to keep in her pocketbook.
This worked. The Wii and DS were two of the best-selling consoles of all time. In particular, the DS's marketing campaign only worked because it came out in the perfect window of time. PDA-phone hybrids had been around since the 90s, and the Blackberry had been kicking around for a few years, but the iPhone wouldn't be introduced until 2007, and the 4G LTE standard wouldn't be released until 2009. While the Blackberry was popular with businesspeople and the PDA was out of style, smartphones were luxury toys for several years; they wouldn't become near-ubiquious until the mid-2010s. I didn't get my own smartphone until probably around the same time I got my 3DS, a full handheld generation later.
Browsing the software library for the Nintendo DS and DSi with that in mind is really interesting. Many titles released for the platform serve the same purposes that would be fulfilled by simple smartphone apps less than a decade later: planners and diaries, fitness trackers, calculators, language learning and SAT prep software, even a guide to the then-most-recent version of the driver's test in the UK. These proliferated with the release of the DSi's virtual store, but they existed even with the base model. You could go to a brick-and-mortar store and buy them on physical cartridges. (You might be wondering, "Why would you bother carrying those around over just buying a Blackberry?" You can't underestimate how expensive the service bills for a smartphone were before companies realized they were the most powerful spyware tool in history.)
There was never a time where every single businesswoman in New York carried a DS Lite, but adults did buy and use them, and a not insignificant portion of the DS's software library is aimed at a casual adult audience. Another niche covered mostly by smartphone games these days—games designed to be picked up and played in short sessions on-the-go, in places like waiting rooms and subway commutes.
Nintendo made crazy bank in the seventh console generation. Publications of the time talked about a console war between Sony, Microsoft, and Nintendo, but the real battle was between the PS3 and the Xbox 360 over the gamer demographic. Nintendo was producing hardware for a niche who would quietly disappear once smartphone sales began ballooning by hundreds of millions per year over the course of the early 2010s.
After the failure of the Wii U, Nintendo's marketing strategy pivoted again, though I doubt they'll ever completely abandon their family-friendly image. Currently beat out only by the PS2 and the DS, the Nintendo Switch may very well climb to a status as the best-selling console of all time before the end of its lifespan, but the "gamer" demographic is much bigger than it was two decades ago at the dawn of the DS. As more and more devices become consolidated into the Swiss army knife the smartphone has become, consoles can only carve out a role as dedicated gaming machines.
I'm not sure we'll ever see anything like the Nintendo DS or the Wii again. I think they're worth looking back on for their uniqueness in that way as much as they are for the more celebrated parts of their libraries.
#mine#this is the first in a series of posts i have in mind on this general subject. my next one will be more entertaining i think.
32 notes
·
View notes
Text
How to Know If Your Cell Phone Has Been Hacked?

What are the significant signs that are used to find out that someone’s phone has been hacked and its information stolen by other people? This question and all similar questions are the common concern of many smartphone users, and considering that the phone is a versatile tool for most people, important information is also stored in it, so hacking the phone and stealing it Losing its information can cause a lot of damage. In order to know whether your smartphone is being spied on or not, follow this article and the security solutions mentioned here.
2 signs that someone is spying on your phone
There are lots of important physical and hardware signs that show your phone is being hacked. In order to find out, continue with us in this part of the article.
You are receiving unusual messages
If you receive unrelated and incomprehensible messages that have never happened before, for example, messages that contain a large number of characters and numbers, you are probably under control. These messages are similar to the codes that are sent to track the location of people.
AnyControl is the best phone call monitoring app that can track every incoming, outgoing and missed phone call on the target device even if the call log is deleted with its advanced tracking features.
Another way that can reveal the signs of espionage from a software point of view are anti-spyware programs and apps. An example of these apps is Anti Spy Mobile. iPhone phones are usually more secure than Android phones (if they are not jailbroken or unlocked), so if your phone is an iPhone, you can be sure of its greater safety; Because installing spyware requires physical contact with the device.
After sending, a lot of information will be displayed. Pay more attention to URLs. If you have been spied on, many copies of the email you have sent will be sent to different IPs that are different from the IP of your Internet service provider. You can search the term IP lookup on the Internet to distinguish the IP of your ISP from other IPs.
Your data usage has been checked by phone
Through smartphones, you can check the internet usage under the phone's network usage. The spy softwares that is installed in the devices for spying perform their activities by sending and receiving data, which is actually the same as using the Internet. If you see significant changes in your phone's internet usage, there is a possibility that your device is being tapped and its information is being spied on.
2 notes
·
View notes
Text
Jailbreak iOS 17.7.6
Apple released iOS 17.7.6 with new bug fixes and performance updates, but many iPhone users still want more than what Apple allows. That’s where Jailbreak iOS 17.7.6 comes in. With a jailbreak, you can fully customize your iPhone, download third-party apps, and enjoy features Apple normally blocks.

This guide will show you everything you need to know about Jailbreak iOS 17.7.6, including what it is, how it works, the best tools to use, and how to get started safely. We’ll also explain why iNstantJB is the best and easiest way to jailbreak your device.
What Is Jailbreak iOS 17.7.6?
Jailbreak iOS 17.7.6 is the process of removing Apple’s software limits on iPhones and iPads. Once you jailbreak, you can access new features, install apps from outside the App Store, and customize your device in usually restricted ways.
People jailbreak their iPhones to gain full control over the software. It’s like having admin rights on your own device. You can change how your phone looks, improve its performance and do things Apple normally blocks.
Why Do People Jailbreak iOS 17.7.6?
There are many reasons why people choose to Jailbreak iOS 17.7.6:
Install themes and icon packs to change how your device looks
Use advanced tweaks that improve battery life, speed, and functionality
Download third-party apps that Apple doesn’t allow
Sideload IPA files for modded apps and games
Remove system limitations for a more flexible experience
In short, jailbreaking gives you complete control. Apple’s rules no longer limit you.
Is Jailbreak iOS 17.7.6 Safe?
Yes — as long as you use trusted tools. Jailbreaking itself is not illegal or harmful when done the right way. Tools like iNstantJB make the process safe, simple, and fully reversible.
Here are a few safety tips before jailbreaking:
Back up your iPhone using iCloud or iTunes
Use a tool that supports Jailbreak iOS 17.7.6
Follow the steps carefully and don’t rush
If something goes wrong, you can easily restore your phone to factory settings and remove the jailbreak.
Download Jailbreak iOS 17.7.6 App
If you're ready to jailbreak, the first step is downloading the right tool. The best and most updated version of the Jailbreak iOS 17.7.6 app can be found at:
https://www.cydiafree.com/cydia-download-ios-17-1-2-3-4-5-6.html
This website offers a secure and reliable version of the jailbreak tool for iOS 17.7.6. It supports most iPhones and iPads, and the process is beginner-friendly.
iNstantJB – The Best Way to Jailbreak iOS 17.7.6
Many jailbreak tools are online, but iNstantJB stands out as the easiest and safest way to Jailbreak iOS 17.7.6.
What makes iNstantJB different?
You don’t need a PC or Mac
Everything runs from your Safari browser
No complicated steps or tech knowledge required
Compatible with all devices running iOS 17.7.6
Safe, fast, and reversible
How to Use iNstantJB:
Open Safari on your iPhone
Visit the official iNstantJB website
Tap “Start Jailbreak”
Let the tool check your iOS version
Follow the instructions on screen
Complete the process and enjoy your jailbreak!
That’s it — no cables, no risk, and no stress. iNstantJB is the most user-friendly way to get the full jailbreak experience.
What You Can Do After Jailbreaking iOS 17.7.6
Once you’ve used iNstantJB to Jailbreak iOS 17.7.6, a new world opens up. You’ll be able to:
1. Customize Your iPhone
Use tools like SnowBoard to apply themes change icons, fonts, and animations. Your iPhone will finally look the way you want it to.
2. Install Powerful Tweaks
Add features Apple doesn’t offer — like better multitasking, volume sliders, screen recording options, and more. Tweaks give your device extra abilities that improve the user experience.
3. Use Third-Party App Stores
After jailbreaking, you can install stores like Cydia, Sileo, and Zebra. These offer apps and tools you’ll never find on the App Store.
4. Sideload IPA Files
Want to install hacked games, emulators, or apps removed from the App Store? With jailbroken device, you can easily sideload any IPA file using tools like AltStore or Sideloadly.
5. Block Ads Everywhere
Install advanced ad blockers that remove ads from Safari, YouTube, and other apps. You’ll get a faster and cleaner experience.
Popular Tweaks After Jailbreak iOS 17.7.6
Here are some amazing tweaks you can try once you’ve jailbroken your device:
SnowBoard – A powerful theming tool
AppSync Unified – Install unsigned or modded apps
iCleaner Pro – Clean up junk files and free storage
Barmoji – Add emojis to your keyboard bar
CCModules – Customize Control Center with new toggles
Cylinder – Add page animations like in Android
These are just the beginning. The jailbreak world has thousands of tweaks waiting for you.
Devices Supported by Jailbreak iOS 17.7.6
Jailbreak iOS 17.7.6 works on a wide range of iPhones and iPads:
iPhone 15 / 15 Plus / 15 Pro / 15 Pro Max
iPhone 14 Series
iPhone 13 / 12 / 11
iPhone XS / XR / X
iPhone SE (2nd and 3rd Gen)
Most iPads running iPadOS 17.7.6
Ensure your iOS version matches by going to Settings > General > About.
Can You Undo the Jailbreak?
Yes! Jailbreaking is not permanent. You can undo it at any time by:
Going to Settings > General > Transfer or Reset iPhone
Selecting “Erase All Content and Settings”
Confirming the reset
This will wipe your iPhone and remove the jailbreak completely. You can also restore a backup through iTunes or Finder to regain your data.
Jailbreak iOS 17.7.6 – Frequently Asked Questions
1. Will Jailbreak iOS 17.7.6 void my warranty?
Technically yes, but if you remove the jailbreak before visiting an Apple Store, they won’t know. It's completely reversible.
2. Can I still use the App Store after jailbreaking?
Yes! Jailbreaking doesn’t block the App Store. You can continue downloading apps just like before.
3. Is my data safe during the jailbreak?
Your data remains safe as long as you use trusted tools like iNstantJB. Still, it’s always smart to back up your device before starting.
Final Thoughts
Jailbreak iOS 17.7.6 is the key to unlocking everything your iPhone is capable of. You can customize your phone, install powerful tweaks, and enjoy apps Apple doesn’t allow. It’s safe, simple, and worth trying — especially with tools like iNstantJB that simplify the process.
To get started, download the Jailbreak iOS 17.7.6 app today from:
https://www.cydiafree.com/cydia-download-ios-17-1-2-3-4-5-6.html
Then, use iNstantJB to jailbreak your device and enjoy a world of freedom. Your iPhone will never be the same again.
0 notes
Text
iOS App Development Guide: Techniques, & Best Practices

Mobile app development has become more than just a passing trend. They have changed the way we shop, communicate, and explore. Every day, millions of apps are downloaded, thus giving businesses and entrepreneurs a whole world of opportunity to tap into the iOS App development realm. Businesses can thereby develop tailor-made solutions that fulfill some diverse needs from the user perspective. Hence, they can boost engagement and generate new revenue channels in this emerging digital world.
What is iOS app development?
iOS app development is the process of building apps designed especially for the Apple Operating System. It involves creative device applications used in Apple products, from iPhones to MAC computers. This process streamlines the development process and assures an unmatched user experience across Apple devices.
Why is iOS a popular choice for mobile development?
Mobile apps are no exception, as nowadays, smartphones are an essential part of our lives. Entrepreneurs in this field can harness the power of iOS development to create targeted apps, broaden their reach to a global audience, and provide sustainable, everlasting value. Mobile apps are the way to go for businesses looking to remain competitive and fuel growth in the app-driven environment of 2025. So, let us jump into why iOS App Development is a popular choice:
High level of security
iOS is known for its robust security features. The closed ecosystem and strict app guidelines of Apple ensure that users can access high-quality and secure apps. When developing iOS apps, the iOS app development company in the USA ensures that encryption, biometric authentication (Face ID and Touch ID), and secure APIs are used. This makes iOS devices and apps less vulnerable to cyber threats than other platforms. For businesses handling sensitive data, iOS is a reliable choice to ensure user trust and privacy.
Improved customer experience
Apple prioritizes delivering a seamless user experience across all iOS devices with the best software features and functionality. iOS App Development follows strict UI/UX design principles that contribute to a polished, high-quality user experience. The simplicity and sophistication that iOS offers help companies improve customer satisfaction with the help of user-friendly apps designed by the iOS app development company in UAE.
Good Return on Investment
Despite the higher development cost, iOS apps generate a higher ROI because of their high customer base in the Apple ecosystem. An iOS app development company in the UKfollows strict quality controls when developing the app. This results in the delivery of high-quality apps with fewer bugs and enhanced overall performance. Organizations aiming to have long-term success should consider investing in iOS app development.
Safe and secure transactions
The iOS ecosystem offers a safe platform for online transactions that makes them a preferable choice in industries ranging from e-commerce to finance. iOS app developers make use of adding strong security features that prevent them from unauthorized access, thus saving businesses from fraud.iOS app development offers a secure environment for online transactions via iPhone apps. AniOS development company in the USA builds apps as per defined iOS standards that should be secure from threats like hacking and phishing.
Faster Development
Despite what many people think, there are several reasons why iOS development can be quicker than on other platforms. iOS offers developers a complete IDE with pre-built frameworks and libraries like Xcode, Cocoa, and iOS SDKs, which is quite beneficial. App compatibility and testing procedures are made easier by iOS app development companies in the USAbecause of the iOS ecosystem's consistency of devices. Swift, the official programming language for iOS, assures smooth compatibility and effective iOS device development. These benefits help in the quick and error-free creation of iOS applications.
Best practices for iOS App development
When it comes to iOS app development, it is important to maintain the security and the quality of your iOS apps. Companies must stay updated with the upcoming trends in the growing iOS ecosystem. Some of the best practices that must be followed by the iOS app developmentcompany in the USA are as follows:
During the process of building apps,aniOS app development company in UAE must follow the strict Apple UI guidelines to keep the app design consistent and intuitive.
iOS developers must optimize the performance by profiling Xcode tools and managing the memory efficiently.
Swift programming language can be used by aniOS app development company in the UK for more efficient app development.
In iOS app development, it is important to modularize the code for better reusability. Developers should use design patterns like MVC and MVVM for app development.
To ensure your iOS app fits smoothly across different screen sizes, aniOS app development company in the USA should implement auto layout for improved user experience.
Developers must test the app thoroughly, from its UI to security, and ensure the stability and performance of the iOS apps.
Final Thoughts
To conclude, iOS apps can do wonders for your venture, from increased cash flow to bringing customer success. iOS app development can be challenging for newbie organizations. However, it's worth investing in because of the flexibility it offers. Want to build iOS applications for your business? Reach out to Digital Hub Solution, as we can help bring your iOS app to the next level.
#iOS App Development#iOS app development company in UAE#iOS app development company in UK#iOS app development company in USA
0 notes
Text
Mobile Security: Protecting Users from Phishing, Malware, and Data Breaches

Mobile phones have become a means of communication that has become an integral part of our life, whether it is related to banking or sharing on social media. This excessive use only makes mobile devices the primary victims of these cyber attacks, which range from phishing to malware infections and data breaches. It is important to protect yourself from these threats, and cyber security courses are an excellent investment in staying ahead of hackers. Let's dive into the risks and explore how users can safeguard their mobile security.
The Growing Threat of Mobile Cyber Attacks
Phishing Attacks: Deceptive Tactics to Steal Your Data
Phishing remains one of the most dominant cyber threats on mobile devices. The criminals steal sensitive information like passwords and credit card information using fraud emails or text messages or fake websites. Mobile phishing attacks are effective since individuals are more likely to click on links without confirming their authenticity.
How to Protect Yourself:
Never click on links from unknown sources.
Enable two-factor authentication (2FA) for added security.
Verify URLs before filling out personal data.
Take courses in cyber security to learn sophisticated phishing detection.
Malware: The Silent Invader
Malware can enter your mobile device via malicious apps, infected websites, or misleading downloads. Once on your device, malware can snatch personal data, monitor your actions, or even hold your device for ransom (ransomware). Mobile malware is becoming ever more sophisticated and is often presented as legitimate apps.
Download apps only from official stores like Google Play or the Apple App Store.
Check app permissions before installing.
Use a reputable mobile antivirus software.
Keep your operating system and apps updated to patch vulnerabilities.
Data Breaches: Your Information at Risk
Data breaches are a case in which hackers infiltrate a company's storage and obtain sensitive user information. Users' personal information, payment details, and even biometric information are leaked and stolen, making way for identity theft and financial fraud.
Protecting Yourself:
Use unique and strong passwords on various accounts.
Keep an eye on your bank and credit card statements regularly.
Turn on fingerprint or face ID when possible.
Learn about mobile security through cyber security courses to keep abreast of the latest protective measures.
Best Practices for Mobile Security
Avoid Public Wi-Fi Networks
Public Wi-Fi is a hotspot for hackers who use man-in-the-middle (MITM) attacks to intercept your data. If you must use public Wi-Fi, consider using a VPN to encrypt your connection.
Enable Remote Wipe and Find My Device
In case your mobile device is lost or stolen, having remote wipe enabled can prevent unauthorized access to your personal data. Use services like Google's Find My Device or Apple's Find My iPhone to track and secure your phone remotely.
Disable Bluetooth and NFC When Not in Use
Cybercriminals can take advantage of the vulnerabilities in Bluetooth and NFC to access your device without permission. Turning them off when not in use reduces this risk.
Back Up Your Data Regularly
A backup ensures you do not lose important information in case of a cyber attack or failure of your device. You can use cloud storage or an external hard drive to keep your files safe.
Why You Should Consider a Cyber Security Course
With the rapid evolution of mobile threats, knowledge in cyber security can be a game changer. You can learn by enrolling in cyber security courses and:
Understand modern cyber threats and their prevention.
Learn ethical hacking techniques to test mobile security.
Gain insights into mobile security frameworks and best practices.
Enhance your career prospects in the cybersecurity domain.
Conclusion
With mobile devices dominating our daily lives, securing them is now more important than ever. It ranges from avoiding phishing scams to protecting against malware and data breaches. Users need to take proactive measures to ensure their safety. Taking cyber security courses is a smart step toward gaining expertise in mobile security and protecting personal and professional data. Stay informed, stay secure!
0 notes
Text
100K Bitcoin System Review – Automated Bitcoin Generating System
Welcome to my 100K Bitcoin System Review. As cryptocurrency revolutionizes the world of finance, a new army of seasoned investors and curious beginners continue to push their investments into the digital currency. When it comes to the many passive income systems, one that has been getting a lot of attention is the 100K Bitcoin System.

This is marketed as a ‘set & forget’ done for you AI driven platform that exploits a ‘free crypto hack’ that makes $25-$50 in Bitcoin per day. How credible are these claims, however? In this detailed review we will analyze 100K Bitcoin System features, benefits, how it works, user feedback, pricing, pros, cons, and whether it is something worthy to your precious time and money.
What Is 100K Bitcoin System?
100K Bitcoin System is an automated cryptocurrency trading platform that uses artificial intelligence (AI) to execute trades on behalf of its users. This system is different from common trading systems that rely on human intervention and constant monitoring, the system can be operated independently by someone who is just starting or is really busy.
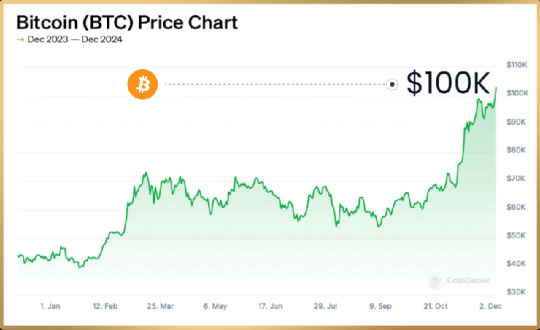
According to its creators, the system leverages a “free crypto hack,” purportedly exploiting specific market inefficiencies to secure consistent profits. It aims to make Bitcoin accessible to everyone by simplifying the trading process and providing a low-risk, high-reward opportunity.
100K Bitcoin System Review: Overview of Product
Product Creator: Glynn Kosky
Product Name: 100K Bitcoin System
Launch Date: 2025-Jan-16
Launch Time: 10:00 EST
Front-End Price: $17 (One-time payment)
Official Site: Click Here To Visit Official Salespage
Product Type: Tools and Software
Support: Effective Response
Discount: Get The Best Discount Right Here!
Recommended: Highly Recommended
Bonuses: YES, Huge Bonuses
Skill Level Required: All Levels
Discount Coupon: Use Code “BTCFIVE” To Get $5 Off
Refund: YES, 180 Days Money-Back Guarantee
Key Features of 100K Bitcoin System
✍ 100K Bitcoin System App
The Only AI System on the Market That Allows Me to Exploit the Entire Crypto Market for Massive Profit.
✍ 100K Bitcoin System ZERO Work HACK
The Only AI System That Exploits the Markets for Unlimited Potential!
✍ 100K Bitcoin System Mobile EDITION
This Will Allow You To Also Operate The System, Even From Your Mobile Phone. Whether it’s An Android, IPhone, Or Tablet, and It Will Work.
✍ Step-By-Step Training Videos
Have A Question? Just Reach Out To Us And Our Team Will Do Their Best To Fix Your Problem In No Time.
✍ World-Class Support
Have A Question? Just Reach Out To Us And Our Team Will Do Their Best To Fix Your Problem In No Time.
✍ DFY 1-1 Mentoring
You’ll Also Get 7-Days of Unlimited 1-1 Mentoring. Simply Let Us Know And Our Expert Will Reach Out To You To Give 1-1 Mentoring.
100K Bitcoin System Review: How Does It Work?
Just Three Simple Steps Gets Us FREE Automated Bitcoin!
Step #1: Access
The 100K Bitcoin System.
Step #2: Follow
The simple setup instructions, which takes less than 10 minutes.
Step #3: Profit
This is where we sit back and watch as Bitcoin flows into our wallets!
Benefits of 100K Bitcoin System
Done-For-You Crypto Profit System
Top-Converting Crypto System
Earn FREE CRYPTO + FREE BITCOIN
Built-In Crypto Targeted FREE Traffic
Setup Takes Less Than 60 Seconds
First Of Its Kind On WarriorPlus or ClickBank
In-Demand System In The Current Climate
Easiest System To Earn FREE Crypto
Get IN FRONT Of The Hottest New Niche In YEARS!
Automated System Works From Anywhere
Custom-Built Especially For Beginners
NO MONTHLY COSTS (when you get in now)
NO CRYPTO INVESTMENT REQUIRED
Built Huge Email Lists of Crypto Buyers
Grow Your OWN Crypto Portfolio For Huge Gains!
No Website, No Tech Skills, No Experience Needed
Brand New 1st-To-Market System
Unlock The Laptop Lifestyle
Proven Method Developed By Elite Affiliate Marketer
100K Bitcoin System Review: Old Way VS New Way

Verify Users Say About 100K Bitcoin System
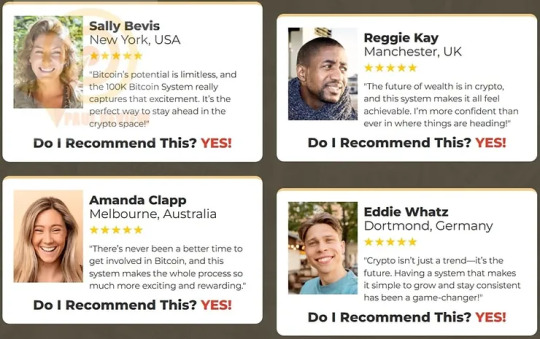
100K Bitcoin System Review: Who Should Use It?
Affiliate Marketers
Teenagers
College Students
Entrepreneurs
People In Their 20s
Housewives
Freelancers
Stay At Home Dads
Busy People
Marketing Agencies
The Family Man
Old Age Pensioners
Digital Marketers
And Many Others
100K Bitcoin System Review: OTO’s And Pricing
Front End Price: 100K Bitcoin System ($17)
OTO1: 100K BTC UNLIMITED ($67 – $47)
OTO2: 100K BTC 100% DONE FOR YOU ($97 – $67)
OTO3: 100K BTC UNLIMITED TRAFFIC ($97 – $67)
OTO4: 100K BTC AUTOMATION $67 – $47
OTO5: 100K BTC ATM EDITION ($67 – $37)
OTO6: 100K BTC License Rights ($197 – $97)
100K Bitcoin System Review: Money Back Guarantee
Still On The Fence? Your Results Are Backed By OUR Money! 100% Money Back Guarantee
We’re so confident that you’ll succeed with this that we’ll take away any risk from your purchase. Use the 100K Bitcoin System and all accompanying materials for the next 180 days risk-free. Enjoy the full potential of this earning strategy that is completely done for you.
Our support center in the United States is manned by specialists who are always pleased to assist you. However, in the unusual event that you do not believe our technique achieves what we have said. You may get a hassle-free refund up to 6 months after purchase! So invest with confidence knowing that we take all of the risk; let us deliver you the results you deserve.
100K Bitcoin System Review: Pros and Cons
Pros:
Fully Automated System and Beginner-Friendly
One Time “Five Minute” Setup – We’ll Even Do It For You!
Zero Learning Curve – Plug & Play System
24/7 Income Potential – Works Day In, Day Out
Done-For-You System – You’ll Love IT!
Perfect For Beginners, Investors AND Passive Income Seekers!
Cons:
Requires a one-time investment
Requires stable internet connection
Nothing wrong with it, it works perfectly!
My Own Customized Exclusive VIP Bonus Bundle
***How To Claim These Bonuses***
Step #1:
Complete your purchase of the 100K Bitcoin System: My Special Unique Bonus Bundle will be visible on your access page as an Affiliate Bonus Button on WarriorPlus immediately after purchase. And before ending my honest 100K Bitcoin System Review, I told you that I would give you my very own unique PFTSES formula for Free.
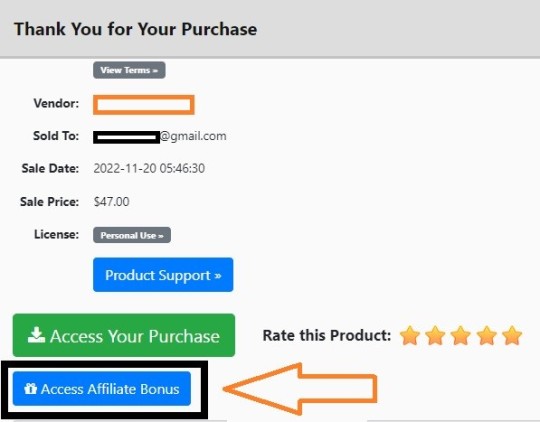
Step #2:
Send the proof of purchase to my e-mail “[email protected]” (Then I’ll manually Deliver it for you in 24 HOURS).
100K Bitcoin System Free Premium Bonuses

Frequently Asked Questions (FAQ’s)
Q. My computer isn’t the best, will 100K Bitcoin System work on mine?
As long as it connects to the internet. YES. This is the same for any other device. The only thing is, it needs to have access to a web browser. If that’s the case, you’re all good to go.
Q. How long will it take to receive profits?
This varies, but the vast majority of our users report receiving it within 12-24 hours after activating it. In short, the quicker you activate, the sooner you’ll likely profit.
Q. Do I need any tech skills?
None whatsoever. I hate technical crap as much as you do, so we designed a 100K Bitcoin System in mind for the average Joe and Jane. After all, not everyone has a computer science degree.
Q. Do I need to buy any traffic?
Nope… You don’t have to mess around
Q. What if I get confused along the way?
Don’t worry, we have video training that shows you every step of the way, from A-Z… We’ll show you everything you need to know so you can begin getting results.
Q. I’m sold. How do I get started?
Click the button below to get a 100K Bitcoin System for the lowest price.
My Recommendation
100K Bitcoin System is an intriguing entrance point for those wishing to familiarise themselves with cryptocurrency trading. An appeal due to its automated, beginner friendly approach and promise of passive income. Transparency however, and the inherent risk associated with trading, are to be disregarded.
Approach the 100K Bitcoin System if you want to try it. Get started with a small investment, and research, research, research! It’s not unusual that no trading system can assure you of profits every time, so stay updated and make decisions on the basis of facts.
>>> Click Here To Get Instant Access 100K Bitcoin System Now <<<
Check Out My Previous Reviews: KidzKDP Review, AzonKDP Review, Revio Review, Voice Magik Review, and Kadjo App Review.
Thank for reading my “100K Bitcoin System Review” till the end. Hope it will help you to make purchase decision perfectly
#100kbitcoinsystem#100kbitcoinsystemreview#100kbitcoinsystemcoupon#100kbitcoinsystemhonestreview#100kbitcoinsystemfeatures#100kbitcoinsystemworks#whatis100kbitcoinsystem#100kbitcoinsystemreviews#buy100kbitcoinsystem#100kbitcoinsystemprice#100kbitcoinsystemdiscount#100kbitcoinsystemfe#100kbitcoinsystemoto#get100kbitcoinsystem#100kbitcoinsystembenefits#100kbitcoinsystembonus#howto100kbitcoinsystemworks#100kbitcoinsystemsoftware#100kbitcoinsystemsoftwarereview#100kbitcoinsystemFunnels#marketingprofitmedia#100kbitcoinsystemUpsell#100kbitcoinsysteminfo#purchase100kbitcoinsystem#100kbitcoinsystemwebsite#software#traffic#100kbitcoinsystemexample#100kbitcoinsystemworthgorbuying#ai
1 note
·
View note
Text
All of us are all familiar with how much an iPhone is secure when it comes to smartphones. People usually prefer an iPhone due to its fast and attractive user interface. Now most of us must have wished to spy on the iPhone device of our friends or any family member. Spying on the iPhone does not walk in the park due to its advanced security mechanisms. Now some people like professional hackers claim to hack on any iPhone with any software. Hacking on an iPhone by installing software on the phone or PC doesn’t sound smart and easy. For someone who is new to spy apps this is a hell of a task to do on its own. What if you get to know that you can actually track any iPhone device without learning any kind of skills? Yes, this is totally possible for you to spy on an iPhone device without requiring any software or app installation. People usually perform different risky techniques or tricks to break into the iPhone but those tricks won’t work. Using a phone spying app will let you spy on any iPhone device without any installation or learning. Let’s discuss one of the best phone spy apps. Spyic- An Innovative Spy App Spyic is one of the popular and professional spying apps in the World right now. This app is the trust of millions, people are using Spyic on a daily basis. Parents, employees, companies, and almost everyone. People would not imagine before anyone that spy app like Spyic was this good to use and help spy on an iPhone without software. There is no issue that people encounter when it comes to using Spyic for iPhone monitoring. Some spying apps ask users to perform Jailbreak before spying on an iPhone but that’s not the case with Spyic. You don’t have to root your Android or Jailbreak your iPhone device to perform phone spying. Spy on an iPhone Without Software Although Spyic is an app, this is a web-based app that you can operate from any web browser on any device either PC or phone. For the iPhone there is no need to install anything on the spied device. Spyic works in stealth-mode so there is zero % chances of you being exposed as it makes everything super-safe. This app is more easy and simple to use beyond your expectations. Going through the whole Spyic review will clear most of your misconceptions about this phone spy app. You would be surprised to know that there are more than 30 spying features added in this spying app. All features have been designed according to the requirements of users in this modern world of technology. Let’s get to know the main spy features of this brilliant phone spy app. Call Tracking: An amazing spy feature that gives you complete monitoring control over call records of the target iPhone device. SMS Tracking: Access all text messages of an iPhone you want to monitor, reading sent, received, and even deleted messages is possible. Location Tracking: Track an iPhone’s location on the basis of GPS or WiFi along with full access to geographical address coordinates. Apart from all the above features, Spyic has so many other perks to offer. Facebook, Instagram, WhatsApp, and all installed third-party apps can be tracked without getting detected. So, social media apps, web browser history, and almost everything can be monitored on an iPhone device through this spectacular phone spying app. You can use this app for any feature by using its dashboard. Now, most of you would be feeling curious to know how to spy on an iPhone remotely using Spyic? The wait is over, we are going to view all steps we need to follow in order to start iPhone tracking with Spyic. How to Spy on an iPhone Remotely Using Spyic Some of you might be thinking that spying on the iPhone using Spyic would be very difficult. Well, spying on an iPhone has never been this much easy and fast like it is now. All you have to do is to follow all required steps and then you are ready to go. Remember you will not have to physically access an iPhone to perform phone monitoring. Let’s have a look at all those steps that we need to follow in order to track an iPhone device.
Step 1 At first, you have to open your web browser and visit the official website of Spyic. Now click on the Signup button to start creating an account by entering Email and Password. Step 2 You would be given two options, Android and iOS. Select iOS because you are going to track an iPhone device. Step 3 Now you have to enter the credentials of an iCloud account that is logged in on the same iPhone device you want to target. Step 4 Wait for a few seconds to let the system verify the iCloud account. After following some onscreen instructions you would complete the account creation process. Congratulations, you have managed to create an account on Spyic. You can just open any kind of browser, sign in to your make a new Spyic account and start tracking that configured target iPhone. Here you will see that all these spy applications are listed on the left side of the dashboard where your Spyic’s account shows. Some people don’t get satisfied by reading reviews about any app, they always want to try that thing by themselves. Another plus point of Spyic is that it provides an online ‘Demo’ version that you can easily see by tapping on the Demo tab on Spyic’s official web-page. By watching it you would be able to know how exactly this app works. Conclusion We’ve reviewed the whole Spyic phone spy app in details, we can say that no spy app is better than Spyic in terms of quality and professional spying services. Every feature and service of Spyic is up to the expectations of the people. There are no risks involved and no need to perform Root or Jailbreak sort of activities to start phone tracking. The stealth mode of the Spyic app is what gives a guarantee to users that no one will detect them spying on an iPhone device. So what are you waiting for? Visit the Spyic’s site and start tracking an iPhone device according to your needs.
0 notes
Text
Hire a Mobile hacker to monitor your partner's chat activity

Related: Best Mobile Hack to Track Your Teenage Child #1
Mobile phones have become an essential part of our daily lives, acting as our communication hub, personal assistant, and entertainment source. But with this increased dependency comes the growing threat of mobile hacking. Understanding mobile security is crucial to protect your personal information from malicious attacks.
💢 What is Mobile Hacking?
Mobile hacking involves unauthorized access to a mobile phone's system, data, or communication. Hackers use various methods to exploit vulnerabilities in mobile devices, often without the owner's knowledge. Common misconceptions include the belief that only outdated or unprotected phones are at risk. In reality, even the latest models with advanced security features can be targeted.
💢 How Hackers Target Mobile Phones
Hackers use several techniques to gain access to mobile phones:
🔸 Phishing Attacks: Sending fake messages or emails to trick users into revealing personal information.
🔸 Malware: Installing malicious software that can steal data or monitor activities.
🔸 Network Spoofing: Creating fake Wi-Fi networks to intercept data transmitted over them.
🔸 Exploiting Vulnerabilities: Taking advantage of security flaws in the phone’s operating system or apps.
💢 Is My Phone Hacked?
Wondering if your phone might be hacked? Look out for these signs:
🔹 Unusual Battery Drain: Malicious software running in the background can cause your battery to deplete faster than usual.
🔹 Slow Performance: If your phone is suddenly slow or crashes often, it could be compromised.
🔹 Strange Messages: Receiving unusual texts or emails, especially from unknown sources, is a red flag.
🔹 Data Usage Spikes: Unexpected increases in data usage may indicate that malware is transmitting data from your phone.
💢 What to Do if My Phone is Hacked
If you suspect your phone is hacked, act quickly:
📕 Disconnect from the Internet: Turn off Wi-Fi and mobile data to prevent further data transmission.
📕 Scan for Malware: Use trusted security apps to scan and remove any malicious software.
📕 Change Passwords: Update all your passwords, especially for sensitive accounts.
📕 Factory Reset: As a last resort, perform a factory reset to remove all data and restore the phone to its original settings.
💢 Can My iPhone Be Hacked?
While iPhones are renowned for their security, they are not immune to hacking. iOS security features include:
📒 Sandboxing: Restricts apps from accessing data from other apps.
📒 App Store Vetting: Thorough review process for apps before they are available for download.
However, vulnerabilities can still be exploited through techniques like jailbreaking or by installing malicious apps from unofficial sources.
💢 How to Find Out Who Hacked Your Phone
Tracing the hacker is challenging but possible. Here are some steps:
📘 Check Activity Logs: Review your phone's activity logs for unusual behavior.
📘 Consult Professionals: Seek help from cybersecurity experts.
📘 Report to Authorities: File a report with local law enforcement or cybercrime units.
💢 Hackers can use your phone number to:
📗 SIM Swapping: Transfer your phone number to another SIM card, gaining access to your accounts.
📗 Phishing: Send malicious links via SMS.
Protect your phone number by avoiding sharing it publicly and using two-factor authentication for your accounts.
💢 Hacked Phone: What to Do?
If your phone is hacked, follow these steps:
📙 Identify the Source: Determine how your phone was hacked to prevent future attacks.
📙 Remove Malware: Use security software to clean your device.
📙 Update Software: Ensure your operating system and apps are up-to-date.
📙 Secure Accounts: Change passwords and enable two-factor authentication.
💢 Best Mobile Hacker
There should be some essential features to be considered the best mobile hacker.
🔎 First, a deep understanding of various programming languages like Python, Java, and Swift is crucial.
🔎 Second, strong cybersecurity awareness to protect against and exploit vulnerabilities is necessary.
🔎 Third, proficiency in using popular hacking tools like Metasploit, Wireshark, and Nmap is vital.
🔎 Fourth, ethical conduct to ensure responsible hacking practices is essential.
🔎 Fifth, practical experience through real-world applications and simulated environments is important.
🔎 Lastly, continuous learning to stay updated with the latest trends and techniques is indispensable.
💢 If My Phone is Hacked, What Should I Do?
Here’s a practical guide:
Stay Calm: Panicking won't help. Take methodical steps to secure your phone.
Backup Data: Before making any changes, backup your important data.
Use Security Software: Regularly scan your phone for threats.
Educate Yourself: Stay informed about the latest security threats and how to counter them.
��� Why Hire a Mobile hacker
In the age of smartphones, mobile security is more important than ever. Have you ever wondered how secure your mobile app or device really is? That's where a mobile hacker comes in. But why should you consider hiring one? Let's dive into the world of mobile hacking and explore its benefits.
💢 Benefits of Hiring a Mobile Hacker
Enhancing Mobile Security
Mobile hackers can significantly enhance the security of your mobile applications and devices. They identify and address vulnerabilities that could be exploited by malicious actors.
Preventing Data Breaches
By identifying potential weaknesses, mobile hackers help prevent data breaches that could compromise sensitive information.
Identifying Vulnerabilities
Hackers can pinpoint specific vulnerabilities that might be overlooked during standard security checks.
Related: Hire Professional Social Media Hackers
💢 Best Hacking Apps
Some of the top hacking apps used by professionals (often for ethical hacking) include:
Metasploit: Used for penetration testing and finding vulnerabilities.
Nmap: Network scanning tool that identifies open ports and services.
Wireshark: Network protocol analyzer for troubleshooting and analysis.
While these apps have legitimate uses, they can be misused for illegal activities.
🔘 Finishing Touch
Mobile hacking is a serious threat that requires vigilance and proactive measures. By understanding how hackers operate, recognizing the signs of a compromised phone, and taking appropriate steps to secure your device, you can protect your personal information and privacy. Stay informed, stay secure, and don't hesitate to seek professional help if needed.
FAQs
Q-1: Can my phone be hacked if I only use official app stores?
A-01: While using official app stores reduces the risk, it does not eliminate it completely. Always read reviews and check permissions before downloading apps.
Q-2: How often should I change my passwords?
A-02: It’s recommended to change your passwords every three to six months and use unique passwords for different accounts.
Q-3: Is it safe to use public Wi-Fi?
A-03: Public Wi-Fi is generally not secure. Use a VPN to protect your data when connecting to public networks.
Q-4: Can resetting my phone remove all hacking threats?
A-04: A factory reset can remove most malware, but it's important to also change all passwords and update your security settings.
0 notes
Text
0 notes
Text
iPhone 15 Pro Max with SIM Card Slot: The Pinnacle of Connectivity and Performance
The iPhone 15 Pro Max has hit the market, and it's already making waves with its advanced features and elegant design. One standout feature that has caught the attention of many is the inclusion of a SIM card slot. In an era where eSIM technology is becoming more common, the physical SIM card slot remains an indispensable asset for numerous users. Let’s explore why the the iPhone 15 Pro Max with SIM card slot in is a crucial feature and how it enhances your smartphone experience.
Exquisite Design and Unmatched Performance
The iPhone 15 Pro Max is a marvel of modern engineering. Encased in a durable, premium design, it features a 6.7-inch Super Retina XDR display that offers stunning visuals with vibrant colors and deep blacks. Powered by the A17 Bionic chip, this device ensures that every task, from high-definition gaming to complex multitasking, is handled with ease and efficiency.
The Vital Role of the SIM Card Slot
Even as digital eSIMs gain popularity, the physical SIM card slot offers several advantages that keep it relevant and essential:
Global Roaming Convenience: For those who travel internationally, a physical SIM card slot provides the flexibility to switch to local carriers, thereby avoiding hefty roaming fees and ensuring better connectivity.
Carrier Flexibility: With a SIM card slot, users can easily switch between different mobile network operators. This allows for greater freedom to choose the best plans and services that suit your needs.
Enhanced Privacy and Security: A physical SIM card offers a level of security that digital eSIMs may not, as it is less vulnerable to remote hacking attempts.
Reliable Backup: In case of eSIM service disruptions, a physical SIM card ensures you remain connected, providing a reliable backup option.
Dual SIM for Maximum Flexibility
The iPhone 15 Pro Max supports Dual SIM functionality, allowing you to use both an eSIM and a physical SIM card simultaneously. This is ideal for those who need to manage both personal and work lines on one device, or for travelers who need a local SIM while keeping their home number active.
Superior Camera Capabilities
The iPhone 15 Pro Max is not just about connectivity; it’s also a powerhouse in photography and videography. With its advanced camera system, featuring larger sensors and enhanced computational photography, you can capture stunning images and videos. The ProRAW and ProRes modes provide professional-grade editing capabilities, making this phone a favorite among photography enthusiasts and professionals alike.
Impressive Battery Life and Fast Charging
Battery life is a critical aspect of any smartphone, and the iPhone 15 Pro Max excels in this area. It offers extended battery life, ensuring you stay powered throughout the day. When you do need to recharge, the fast charging feature gets you back to full power quickly, minimizing downtime.
Future-Ready Technology
Equipped with 5G connectivity and the latest in AI technology, the iPhone 15 Pro Max is designed to stay relevant and powerful for years to come. Its robust hardware and software integration ensure that it can handle future updates and applications with ease.
Conclusion
The iPhone 15 Pro Max with a SIM card slot is a versatile and powerful device designed to meet the needs of modern users. Its combination of top-tier performance, advanced camera capabilities, and the practicality of a SIM card slot make it an exceptional choice for anyone looking for the best in mobile technology. Whether you’re a globetrotter, a business professional, or someone who values robust security and flexibility, the iPhone 15 Pro Max is tailored to meet your demands.
Explore the iPhone 15 Pro Max today and experience the ultimate in smartphone innovation. Visit Bangaliesbazar for the latest deals and offers on this cutting-edge device.
0 notes
Text
Unveiling the Latest: iPhone 15 Pro, Upcoming iPhone 16 Series Rumors, and the Buzz in the Apple Ecosystem

iPhone Update: New Releases, Upcoming Rumors, and Everything in Between
Apple fans, rejoice! We have a roundup of the latest iPhone news to keep you informed and excited. Buckle up, because we're diving into new releases, upcoming rumors, software updates, and even a dash of controversy.
Fresh off the Shelf: iPhone 15 Pro and Pro Max
For those seeking the ultimate iPhone experience, the recently launched iPhone 15 Pro and Pro Max are the talk of the town. These powerhouses boast a sleek titanium build, a mysterious new "Action Button," and the lightning-fast A17 Pro chip. Photographers rejoice, as the camera systems have received a significant upgrade, while the switch to a USB-C port marks a shift from the traditional Lightning connector. Starting at $999 for the Pro and $1,199 for the Pro Max, these top-tier devices come with a premium price tag.
A Glimpse into the Future: iPhone 16 Series Whispers
Fall 2024 is rumored to bring the highly anticipated iPhone 16 series. While details remain under wraps, whispers suggest a significant performance boost with a faster processor. Pro models might see an increase in screen size, and Apple's continued focus on AI integration could bring exciting new features. However, prepare for potentially higher prices, particularly in regions like India.
Software Updates: Keeping Your iPhone Fresh
Apple recently rolled out iOS 17.4, bringing a wave of new emojis and the ability to customize how certain emojis face. Additionally, bug fixes ensure your iPhone runs smoothly. Looking ahead, rumors swirl about iOS 18, hinting at the integration of powerful generative AI features and potentially improved 5G capabilities. While official details are scarce, stay tuned for further announcements from Apple.
Beyond the Headlines: A Lawsuit and a Laundry Hack?
Apple finds itself in a legal battle with Elon Musk regarding OpenAI, a company in which they have invested. The specifics remain under wraps, but the situation adds another layer to the ever-evolving tech landscape.
In a more lighthearted (and unverified) corner of the internet, a "laundry hack" for iPhones has surfaced, claiming to prevent clothes from shrinking in the washing machine. While the effectiveness and safety of this method are in question, it serves as a reminder to approach such online trends with caution and rely on credible sources for laundry advice.
Whether you're a die-hard Apple fan or simply curious about the latest tech trends, this blog post hopefully provides a helpful update on the world of iPhones. Stay tuned for further developments as we inch closer to future releases and exciting software updates.
Cells Swag is one of the India's leading premium brand of Mobile Accessories. As industry experts, we take pride in offering a wide range of products that enhance the functionality and aesthetics of your phone. With our unique and stylish options, we strive to provide you with the best accessories to suit your personal style and needs.
Visit our website:
1 note
·
View note
Text
Jailbreak iOS 16.7.11
Apple builds amazing devices, but iOS can feel too limited for some users. If you want to get more out of your iPhone, Jailbreak iOS 16.7.11 is the solution. Jailbreaking helps you remove the restrictions set by Apple so you can install custom apps, tweaks, and features not allowed by default.

In this guide, we’ll explain what Jailbreak iOS 16.7.11 means, how it works, and why iNstantJB is the best tool for the job. You don’t need any advanced skills or a computer. You’ll have full control over your iPhone with a few easy steps.
What Does It Mean to Jailbreak iOS 16.7.11?
Jailbreaking your device simply means unlocking the software. Apple limits what you can install or change on your iPhone. But when you Jailbreak iOS 16.7.11, you remove those restrictions and get access to:
Third-party apps
Custom themes
System tweaks
Hacked games and tools
Modified apps and IPA files
With jailbreaking, you’re not just using your iPhone—you’re customizing it.
Why People Jailbreak iOS 16.7.11
There are many good reasons to jailbreak your device. Here are some of the most popular ones:
1. Install Apps Outside the App Store
Many useful apps are not allowed in the App Store. Jailbreaking lets you install these apps directly.
2. Customize Everything
Change how your phone looks and works. Add new icons, themes, fonts, and animations.
3. Use Tweaks
Want extra features like screen recording, improved battery stats, or a new control center? Tweaks make it possible.
4. Sideload IPA Files
Download and install IPA apps that are modified or paid—completely free.
5. Boost Performance
You can even speed up your device or clean background processes with the right tools.
That’s why many iPhone users say that Jailbreak iOS 16.7.11 gives them a whole new experience.
Is It Safe to Jailbreak iOS 16.7.11?
Yes—if you use a trusted tool like iNstantJB. This tool is designed to be user-friendly and secure. It doesn’t harm your device or void your phone permanently. With iNstantJB, your data stays safe, and the jailbreak can be removed later.
Still, it’s always smart to back up your iPhone before starting. That way, you’re fully protected no matter what.
Try iNstantJB – The Best Way to Jailbreak iOS 16.7.11
Looking for the easiest way to Jailbreak iOS 16.7.11? Try iNstantJB. It’s a browser-based jailbreak tool that works directly from Safari. No computer, no cables, no tech knowledge needed.
Why users love iNstantJB:
100% online
Quick and simple setup
No PC or Mac required
Supports iOS 16.7.11 and earlier
Includes Cydia and IPA installer
Fully compatible with iPhone models running iOS 16.7.11
To get started, just visit this official download page: https://www.instantjb.com/cydia-ios-16-1-2-3-4-5-6-7-8-9-jailbreak.html
This is the only link to download the Jailbreak iOS 16.7.11 app.
Step-by-Step Guide to Jailbreak iOS 16.7.11
Here’s how to jailbreak your device with iNstantJB:
Step 1: Open Safari
Use the Safari browser on your iPhone and visit the link above.
Step 2: Select iOS 16.7.11
From the available options, choose your iOS version. Make sure it’s 16.7.11 for full compatibility.
Step 3: Tap Download
Click on the download button to begin the process.
Step 4: Complete Quick Setup
You must complete a short verification to confirm you’re a real user. It only takes a minute or two.
Step 5: Install the Jailbreak App
Once setup is done, install the iNstantJB app. Now, you can open it and enjoy access to tweaks, themes, and more.
And just like that, your device is jailbroken!
What Can You Do After Jailbreaking iOS 16.7.11?
Once your phone is jailbroken, you have many new features to try. Here are some of the top things users do right away:
🔹 Install Cydia
Cydia is a must-have app store for jailbroken devices. It lets you download apps, games, and tweaks that Apple doesn’t allow.
🔹 Try Custom Themes
Change your home screen with beautiful themes, animated icons, and new fonts.
🔹 Use IPA Files
Install modified or premium apps using IPA files. These can include ad-free versions, extra features, or free premium access.
🔹 Add System Tweaks
Boost battery life, speed up animations, or unlock multitasking options unavailable on regular iOS.
🔹 Record Your Screen
Some tweaks allow screen recording, even in apps that normally block it.
With so many options, Jailbreak iOS 16.7.11 helps you unlock the full potential of your iPhone.
Do You Need a Computer?
Nope! That’s what makes iNstantJB so great. You don’t need a PC or Mac. Everything works from your device browser. It’s quick, light, and easy for anyone to use.
That’s why it’s the top choice for people who want to Jailbreak iOS 16.7.11 without any tech stress.
Can You Remove the Jailbreak?
Yes. If you change your mind later, you can always remove the jailbreak by restoring your device in iTunes or Finder. This will erase the changes and return your iPhone to the original iOS settings.
It’s a good idea to back up your phone before jailbreaking so you can restore everything just the way it was.
Is Jailbreak iOS 16.7.11 Legal?
Yes. Jailbreaking is legal for personal use in many countries, including the U.S.. Apple may not support it, but it’s not against the law. Just remember:
Don’t use it for piracy
Only install apps and tweaks from trusted sources
Be careful not to overload your device with too many tweaks
Used wisely, Jailbreak iOS 16.7.11 is both fun and safe.
Tips for a Smooth Jailbreak Experience
To make sure everything goes well, follow these simple tips:
Back up your data before starting
Use Safari for the iNstantJB download
Stick to verified sources like Cydia for apps and tweaks
Avoid heavy or outdated tweaks that could slow down your phone
Restart your phone if anything seems off after jailbreaking.
By following these tips, you’ll enjoy a smooth and safe experience.
Final Thoughts
Jailbreaking your iPhone can unlock a new world of apps, themes, and features. With iNstantJB, it’s easier than ever to Jailbreak iOS 16.7.11. No computer is needed. No tech knowledge is required. Just visit the download page, follow a few simple steps, and your iPhone is free from Apple’s limits.
Whether you want to customize your device, try new apps, or just have fun exploring what’s possible, iNstantJB gives you the power to do more. And the best part? It works on all iPhones running iOS 16.7.11.
So go ahead—Jailbreak iOS 16.7.11 today and take your iPhone to the next level.
0 notes
Text
Top 7 iOS app development tips
1. Plan the process
A mobile app development company may begin the process by ignoring the planning phase. Most developers start with direct code, with no plan. Developing an application is difficult, and developers may skip a phase without achieving results.
Before beginning the coding process, the developers must select a development guide and architecture. For iOS App Development Services, it is best to use a model view controller design. The design aids in the understanding of various UI, software, and data components. Additionally, it keeps the app ready for improvements.

2. Create documentation
Adequate documentation is critical for an iOS app's success. Furthermore, appropriate documentation covers all of the system's components. An overview of the product results will keep you in the loop about the development process.
Code documentation is an important source of knowledge for developers, assisting them in key applications. At times, company logins in a system can take time to grasp. Documentation is a realistic option that simplifies the process. It is a practical way to generate support documents.
3. Follow app store rules
Marketing is linked with applications. Before starting to code, developers should think about promoting their applications. Furthermore, the appearance is an important aspect of your mobile app.
If not in an aesthetic fashion, then you must adhere to all of the apps' aesthetic requirements. The advantage here is that it increases the likelihood of the app being announced in the app store.
And if you don't follow all of the app store guidelines, you'll spend a lot of money developing something that will never be released or distributed in the app store market. Apple's guidelines encompass performance, safety, and legal requirements.
4. Think about security from the beginning
Mobile apps offer a way of storing data across several mobile devices, and app owners' primary worry is security. Furthermore, app data should not be used to facilitate the activities of hackers and scammers.
If your application involves personal information or accepts online payments, considering security from the start is even more important. Well-coded programs and security features can assist in avoiding hack assaults and detecting theft.
5. Consider compatibility
Compatibility is the most essential part of iOS App Development Services. However, it is worth noting that iPhones ranging from 6 to 13 are upgraded to different versions of iOS. Also, if you want to make your software accessible to a wide range of consumers, consider backward adaptation. Backward compatibility means the software will work in all previous versions of iOS.
6. Use Xcode
Developers must create iOS applications with settings. Regardless of your codes and functions, improper settings will impair the app's functionality.
There are other options for iOS platforms, but Xcode is the most popular. Most importantly, Xcode is the only iOS programming environment supported by Apple. In short, it is the primary setting for developers. Furthermore, it is an excellent option for a native iOS application. You can acquire ready-made documentation that is free for Xcode.
7. Start with MVP
Working on fewer requests is a good idea because it lets your programme handle a few things. Furthermore, it is more beneficial than the standard edition of the application.
Start with MVP to make it more active, and you'll get feedback in no moment. The repetition feature increases its viability and flexibility. Furthermore, using a minimum viable product is less expensive than developing an entire programme. With the proper analysis, you may contemplate the app's future.
8. Keep accessibility in mind.
Accessibility should not be limited to a specific population. Consider universal accessibility when developing an iOS application. Consider designing an application for a bigger audience. Furthermore, accessibility can help you develop better iOS apps.
Conclusion
There are guidelines for software integration, architecture, and project management. If you follow the iOS App Development Services principles, your app will perform better. As a mobile app development Company, you must plan strategically and utilise the greatest knowledge and methods for app development.
#swayaminfotech#mobileappdevelopment#mobileapplicationdevelopment#ios application development#ios app developers#ios app design#ios application development company#ios app development
1 note
·
View note
Text
Best-Selling Computer Science Books of All Time
In a world of technology, the knowledge of Computer Science is insistent. From the early large computers to the times of Artificial Intelligence and blockchain, this field has grown at a rapid pace. There are certain books, that have become valuable and great resources of computer knowledge. The first thing you should know while entering the computing world is, that you cannot learn everything. Only a lifetime dedication to pursuing and learning everything about Computer Science will be able to achieve it.

Here are some - Must Read books on Computer Science
Clean Code - A Handbook of Agile Software Craftsmanship
In this book, the author Robert C. Martin addresses the issue of writing clean codes. He states that even code can function. But, if the written code is not clean, it will be a dishonor and the end of everything to a developmental organization. It is one of the best computer science books that’s ever written.
He lists out principles, practices, patterns, and several case studies of increasing complexity that have been gathered from years and years of research and practice that will help you write a clean code, that functions just perfectly. Each case study helps you transform your code into a sound and efficient one. It is just the perfect way to improve your coding skills and stay ahead of others.
Hackers: Heroes of the Computer Revolution
In this book, the author Steven Levy traces developments in the history of hacking, beginning with The Tech Model Railroad Club (TMRC)at MIT, whose members were among the first hackers. He discusses the Hacker Ethic, a set of concepts, beliefs, and morals that came out of a symbiotic relationship between the hackers and the machines.
The book was written way before the term “Hackers” gained a negative connotation. It is like the book existed even before the brief introduction of computers to the world. The hackers quoted in this book are everyone from Steve Jobs to Bill Gates even before when they became famous. But the most interesting mentions are those of Spacewar creator Slug Russell and Osborne 1 designer Lee Felsenstein, both of whom played a pivotal role in the development of PC. Simply, this book is a perfect account of Computing history and its development.
The Little Kingdom: The Private Story of Apple Computer
In this book, TIME reporter Michael Moritz writes an in-depth portrait of the blossoming company back in 1984, long before iPods, iPhones, or iPads. This remains the best and oldest one of the apple biographies ever written. All of Apple’s earliest history is recorded in this book when Steve Jobs and Steve Wozniak weren’t celebrities yet and the company was still hopeful that products like Apple III and The Lisa would become mega hits.
In short, this book contains the history of Apple way back from its Garage workshop days to the leading Tech Business in the world.
Bookswagon is your best source to read books online and make online book purchases, making us one of the Best Book websites in India. We aspire to make your experience with us as good as you.
0 notes
Text
Saturday Morning Coffee
Good morning from Charlottesville, Virginia! ☕️

For those who celebrate Christmas I hope you’ve completed your shopping and can enjoy your time reading blogs today or enjoy some other non day job activity. 😃
Dave Nemetz • TVLine
Andre Braugher, Star of Homicide and Brooklyn Nine-Nine, Dead at 61
This was devastating to me. I’ve liked Andre Braugher since I saw him for the first time on Homicide: Life on the Street. Such a loss.
RIP.
Raymond Chen • The Old New Thing
The x86 instruction set has an ENTER instruction which builds a stack frame. It is almost always used with a zero as the second parameter.
Raymond Chen is one of the best development reads in the world. He’s so smart and can write to boot. He also has great stories to share. I recommend you point your RSS reader at The Old New Thing at Microsoft and enjoy.
Jose Munoz
I’ve used RSS for news and blogs since Google Reader days. I go through my feeds with Reeder on my iPad mini every morning. It’s my favorite time of day. While I’ve been extremely happy for years with Reeder as my RSS reading app, I’ve faced issues with their Reeder Feeds iCloud service.
iCloud sync is a thorn in the side of almost every developer who uses it. It slow to sync and sometimes requires logging out entirely to get it to work. Little indie companies do a better job running services than Apple. Sure, sure, Apple are doing it at huge scale, but so do Amazon, Facebook, Microsoft, and Google and I don’t hear about issues like this as often.
It’s really too bad modern software has an expectation of a backing service to make it work properly because a backing service is super expensive to operate. I can’t provide my own sync because I can’t pay hundreds of dollars a month to run a sync service for Stream. I only make a few bucks a month on Stream. And by a few I mean less than $20/month. That’s OK because I chose to make a simple app that isn’t updated often and chose to give it away. But, I feel for those little undies who spend so much to keep services up and running only to just scrape by or lose money.
Chance Miller, Zac Hall, and Michael Potuck • 9to5Mac
Last week, Beeper Mini debuted as a way to bring iMessage to Android, without having to hand over your Apple ID credentials. A few days later, Apple made a change that stopped Beeper Mini from working – and it promised to continue doing so.
Not surprising.
<rob.crabapples.net/uploads/2…>
Sarah Perez • TechCrunch
U.S. Senator Elizabeth Warren (D-Mass.) is throwing her weight behind Beeper, the app that allowed Android users to message iPhone users via iMessage, until Apple shut it down. Warren, an advocate for stricter antitrust enforcement, posted her support for Beeper on X (formerly Twitter) and questioned why Apple would restrict a competitor. The post indicates Apple’s move has now caught the attention of legislators, who are in a position to regulate Big Tech through policymaking.
Sorry, Senator. Goodness knows I love you, I really do, but I disagree with you on this. Apple is a publicly traded company who created a secure service for users of their devices. We pay for it with our purchase of Apple hardware and other services. It shouldn’t be seen as a free public utility.
The Beeper folks did an amazing job reverse engineering Messages so they could do what they did but it’s essentially hacking a service. Of course Apple is going to shut that down.
What should Apple do? That’s an easy answer for me. They should staff up an Android team and write a native Android app version of Messages. Then charge a monthly service fee for it. Problem solved! You’re welcome!
Something I often wonder. Are Apple’s services so bad/insecure that they mask it by not opening them up? I kind of doubt that but it always pops into my head when I read something about one of their services.
FeedLand
I am lobbying everyone I know to add great feed support to social media systems, so we can get out of the mode of dominant platforms before Threads becomes the dominant platform.
I must admit I didn’t understand what FeedLand is all about, but know I think I get it, maybe. 😃
Ultimately it’s an RSS aggregator. But I do get what Dave is trying to do beyond FeedLand.
Using RSS to follow a social site like Madtodon, Threads, or Bluesky would be amazing. RSS is mature, extensible, and stable.
I follow a few Mastodon feeds using Mastodon’s incredible RSS support, but it could go even further.
Imagine if all social networks supported RSS publishing. We could then use our reader of choice to casually browse our aggregated feeds. I know of a nice little iOS App that presents feeds as a timeline, check it out. 😃
Sorry, had to get that self plug in there.
What if social networks went the next step? What if I could set up a social network to read an RSS feed? Then I could write in one spot and publish to many/all using just RSS. That would be amazing.
To go one step further the social network could support weblog ping so the social network would know you’ve made an update.
Prior to social networks we had all of this in the blogging world. Dave Winer did all of it. He did RSS as well as weblogs ping. It worked really well. He even had Weblogs.com (don’t go there now, it’s a spammy site) which would display the latest sites with updates. If you’ve ever used Blo.gs you’ve seen weblog ping in action. You can even check out my ancient C++ command line implementation of weblog ping. 😂
Anyway. RSS in and out of social networks + weblog ping could be a nice open API for any social network without the need for someone to write code to call an API.
Alyssa Place • benefitnews.com
Employees' traditional view of retirement is changing. It’s time for employers to embrace that, too.
I asked WillowTree HR. A couple years back if we had any kind of plan for part time work and we don’t. I’d like to see that happen because, quite honestly, I can’t really retire. But I do hope to slow down when I hit 70 to enjoy what time I’ll have left, hopefully I live long enough to see a partial retirement.
I suspect the type of business we’re in doesn’t work well with part-time workers. It’s all about billing those hours, which is the worst possible business to be in.
Product and Services are still king. Anything you can upgrade and make money from while doing the next version is so much better than the hourly hamster wheel. 🐹
Robb Knight
Threads started to test ActivityPub integration this week and the fediverse is losing it’s collective mind going into overdrive to block them in any way possible so they can’t grab all your data. Here’s the fun part: they can already do that and they definitely don’t need ActivityPub to do that.
There has been a lot of fear surrounding Threads integrating ActivityPub. I had my doubts at one time but as long as they remain good citizens I don’t have a problem with it
Sarah Perez • TechCrunch
Despite delays, the plan to connect Tumblr’s blogging site to the wider world of decentralized social media, also known as the “fediverse,” is still on, it seems.
I think this is good news. Overall Tumblr feels like it fits into the Fediverse better than Wordpress and I hope they’re able to get it there.
Leo Laporte • twit.tv
Unfortunately, our medium, podcasting, has suffered economically since the beginning of Covid. As the number of podcasts grew exponentially, the number of advertisers dwindled, and with it, our revenue. At one time, we had as many as 30 people on the TWiT staff, not including show hosts, producing more than 30 unique shows. Today, the staff is half that size, and we produce half the number of shows.
Every indie podcast I listen to seems to be pushing subscriptions a lot harder than before. The entire market is in a downturn for free shows. Seeing TWiT layoff a bunch of longtime staff and cut shows is surprising and sad.
Mustapha Hamoui • platformer.news
Late Monday, the jury deliberating in Epic Games’ lawsuit against Google ruled in favor of the Fortnite developer. It found that Google harmed Epic by creating a monopoly in in-app billing and app distribution within the Android ecosystem, illegally tying the app store and its billing system together. A series of revenue-sharing deals with developers and device manufacturers were also found to harm competition.
I admit I don’t know how it is Google is found guilty of having an App Store monopoly and Apple isn’t. The law is strange and understanding eludes me at times.⚖️
Will Shanklin • Engadget
Etsy is the latest company to lay off staff in 2023. CEO Josh Silverman confirmed the marketplace is letting go of 11 percent of its staff (around 225 employees) in its first significant staffing cut in recent years. It’s also reshuffling its leadership, including announcing two executives’ departures at the beginning of 2024.
2023 has been such a crummy year in so many ways but all the tech layoffs scare the crap out of me. I still worry about being laid off and hope the new year doesn’t continue the trend we’ve seen in 2023. 😔
John Scalzi
Abandoning the Former Twitter: A Four-Week Check-In
I’m a fan of John Scalzi’s writing and have many of his book, most unread at the time of this publishing. Not only does he write books he also has a very active blog and social media presence. I loved following him on Twitter and now I love following him on Mastodon. You can too!

0 notes
Text
Is Someone Spying On Your Phone? 10 Signs To Know And Stop Them!
Are you concerned that your Android or iPhone might be under surveillance without your knowledge? If you feel like something’s off and suspect that someone’s keeping tabs on you without your consent, it's important to take immediate action.
There are a bunch of warning signs that can indicate the presence of spyware on your phone. From your battery draining quicker than usual to strange data usage, our guide gives you 10 solid clues on how to know someone has installed spyware on your phone secretly without you knowing and practical advice on what to do next. So if the safety and security of your phone are a concern for you, continue reading for a detailed exploration of these signs and actionable strategies to safeguard your privacy.
3 Common Ways Spyware Can be Installed In Your Phone Without You Knowing:
1.Phishing Attacks, AKA Meta-Phishing:
Phishing is a deceitful method used by hackers to trick individuals into revealing their personal information or installing malicious software. In recent times, "meta-phishing" has emerged as a more advanced form of this cyber threat.
2.Drive-By Download Malware With Examples:
Drive-by downloads are a sneaky way for cybercriminals to infect your phone with malware simply by visiting a compromised website or clicking on a seemingly decent link.
3.Bluetooth Hacking:
While Bluetooth technology has made our lives more convenient, it has also opened up new place for hackers to exploit.
Bluetooth Hacking is of three kinds:
1.Bluejacking - is when someone sends unwanted messages or files to your phone or device using Bluetooth, typically with harmful software attached. This can lead to potential spyware, malware, spamming, or phishing.
2.Bluesnarfing - on the other hand, is much more severe. This is when a hacker takes advantage of flaws in Bluetooth technology to access private data on a device, like personal contacts, messages, and credit card information. This can happen without the owner’s knowledge and often leads to identity theft or financial loss.
3.Bluebuggin - is when a hacker takes over complete control of a Bluetooth-enabled device. They can do things like send text messages or make calls remotely and access sensitive data. This type of attack poses a significant threat to both regular people and businesses alike.
How Do I Know If Someone Is Spying On My phone? 10 Major Signs To Look For
1. Your Battery Is Draining More Than Usual:
If your phone's battery seems to be running out faster than it used to, it could be a sign of spyware. Spy apps often run in the background, consuming extra power to perform their tasks. Keep an eye on your battery usage statistics in your device settings to see if any unfamiliar apps are draining power excessive.
2. Is Your Phone Too Hot To Touch?
An unusually warm phone can be an indicator of spyware or malware. Spy apps can put a strain on your phone's resources, causing it to heat up. If your device feels excessively hot, even when you're not using it for any tasks, it's worth investigating for potential security breaches.
3. Your Phone’s Performance Has Slowed Down:
Spyware can lag, freeze, or crash system resources, leading to a noticeable slowdown in your phone's performance. If apps take longer to open, your device freezes frequently, or there's a general sluggishness, consider this a red flag and investigate further.
4. You Notice Strange Apps Installed In Your Phone:
Spyware can be look like regular apps, so be careful and look for strange or suspicious apps on your phone. It's a good idea to check the list of apps on your phone from time to time. If you see any apps you don't remember getting or ones that seem strange, it's best to remove them.
5. You Receive Concerning Text Messages:
If your phone sends a text message to someone from your contact list without you knowing or giving permission, it could indicate the presence of spyware.
A recent study by Kaspersky revealed that spyware apps are among the most prevalent forms of mobile malware, with over 67,000 instances discovered in 2023. This focus attention on the need to stay alert and implement measures to safeguard your phone against spyware.
6. You Notice Unusual Background Noise During Calls:
If you hear strange background noises, echoes, or interference during phone calls, it could be a sign of someone tapping into your calls. While network issues can sometimes cause such problems, persistent and unusual call quality issues warrant investigation.
7. You Receive Strange Pop-up Ads:
Excessive pop-up ads, especially when you're not using any specific app or browsing, can be a symptom of adware or unwanted software on your phone. Spyware often accompanies adware to monetize its activities, so take these ads seriously.
8. Your Data Usage Has Increased:
Keep an eye on your data usage patterns. Spyware can transmit data from your device to remote servers, causing an unexpected spike in your data consumption. If you notice unexplained increases in data usage, investigate further.
9. You Receive Unusual Phone Bills:
Spy apps may trigger premium rate calls or texts without your knowledge, resulting in unexpectedly high phone bills. Review your phone bill regularly for any unusual or unauthorized charges.
10. Your Phone’s Settings Have Changed:
If you discover that your phone's settings, such as security settings or permissions, have been altered without your consent, it could indicate tampering by spyware. Always verify and reset settings to your preferred configuration if you notice any unexpected changes.
Being vigilant and proactive in monitoring your phone for these signs can help you detect and address any potential privacy breaches early, protecting your personal data and digital security.
Conclusion
Being vigilant and aware of the signs that someone may be spying on your phone is crucial for protecting your privacy and security. The 10 signs we discussed, including unusual battery drain, heating up, strange text messages, and unexpected activity, are all indicators that someone may be monitoring your phone’s activity.
By installing trusted antivirus and anti-spyware software, exercising caution when downloading apps from unverified sources, and implementing strong passwords and two-factor authentication, you can significantly enhance your phone's security, ensuring the safety of your personal data.

#iPhone repair in wakad Pune#Apple service center in wakad Pune#Apple iPhone repair in wakad Pune#iPhone repair & services in wakad Pune#iPhone service center in Pune#iphone service center near me#iphone repair in wakad Pune price#Best apple service center in wakad Pune#iPhone service center in wakad Pune#iphone screen repair in wakad pune#iphone battery repair in wakad pune#iphone service centre in pimpri wakad
0 notes