#cai metadata
Text
Leica announces M11-P with Content Authenticity Initiative metadata recording: Digital Photography Review
I want one just like pictured here, with the 28mm f2 Summicron.
#digital art#digital photography#full frame#full frame digital cameras#leica#leica m#leica m11#leica m11-p#leica photography#leica camera#metadata#cai metadata#cai authenticity
1 note
·
View note
Text
Informatica Training Online| Informatica Training in Ameerpet
Features of Informatica data Intigratation
Informatica Data Integration is a comprehensive platform that facilitates the extraction, transformation, and loading (ETL) of data from various sources to target systems. It offers a range of features to manage and optimize the data integration process. Here are some key features of Informatica Data Integration
Informatica Cloud Training in Hyderabad

PowerCenter Platform:
Informatica PowerCenter is the core platform for data integration, providing a unified environment for designing, executing, monitoring, and managing data integration processes.
Connectivity:
Supports connectivity to a wide range of data sources and targets, including databases, flat files, cloud-based storage, and applications, allowing for seamless integration across heterogeneous environments.
- Informatica Online Training
Data Profiling and Quality:
Provides data profiling capabilities to analyze the structure and quality of data, enabling users to understand data characteristics and make informed decisions about data cleansing and transformation.
Transformation and ETL:
Offers a rich set of transformation functions for cleaning, aggregating, and transforming data during the ETL process. Transformation logic can be applied using a graphical user interface, making it accessible to both technical and non-technical users.
Metadata Management:
Enables comprehensive metadata management to document, analyze, and track the flow of data through the integration processes. This helps in understanding data lineage, impact analysis, and compliance with data governance standards.
Workflow and Job Scheduling:
Allows the creation of workflows to define the sequence and dependencies of tasks in the data integration process. The platform supports job scheduling and monitoring, ensuring efficient execution and management of data integration workflows. - Informatica Training Online
Scalability and Performance:
Designed to handle large volumes of data and scale horizontally to meet the demands of enterprise-level data integration. Performance optimization features are built-in to enhance the efficiency of data processing.
Real-time Data Integration:
Supports real-time data integration, enabling organizations to make decisions based on up-to-date information. Real-time capabilities are crucial for scenarios where timely data updates are critical.
Error Handling and Logging:
Provides robust error handling mechanisms to identify, log, and handle errors during the data integration process. Detailed logging and reporting features help troubleshoot and monitor the health of integration jobs.
Security:
Implements security features to control access to data and ensure compliance with data privacy regulations. It supports encryption, authentication, and authorization mechanisms to safeguard sensitive information.
- Informatica Training in Ameerpet
Data Masking and Anonymization:
Includes features for data masking and anonymization to protect sensitive information during the data integration process. This is especially important for complying with privacy and security regulations.
Cloud Integration:
Offers support for integrating data between on-premises and cloud-based environments. Informatica provides connectors for popular cloud platforms, allowing organizations to leverage the benefits of hybrid and multi-cloud architectures.
These features collectively make Informatica Data Integration a versatile and powerful platform for managing the complexities of data integration within an organization.
Visualpath is the best Informatica CAI & CDI Online Training, Providing Informatica CAI & CDI Training Online with Real-Time trainers. Visualpath has a good placement record. We are providing material, interview questions and real-time time projects.
Schedule a Demo! Call on +91-9989971070.
WhatsApp: https://www.whatsapp.com/catalog/919989971070
Visit: https://visualpath.in/informatica-cloud-training.html
#Informatica Cloud Training in Hyderabad#Informatica Online Training#Informatica Training Online#Informatica Training in Ameerpet#Informatica Cloud Training#Informatica Cloud Online Training#IICS Training in Hyderabad#Informatica Training in Hyderabad
0 notes
Text
Useful for KAITE but needing furthering
Core Learning Compound
How does AI learn, the role of machine learning, and before anything it has to learn to use its different processes, modules, components and functions
Consciousness but also Subconsciousness
What can be the shape of subconscious processes in AI, is there a hidden layer, the simple answer is yes definitely subconsciousness and consciousness are related and important to the functioning of self
RED SQUARE, a Cohesive Firewall Strategy
Although KAITE AI cybernetic body doesn’t contain any other ports than the ones used for its updates and maintenance we have, already, to think beyond such as implementing barriers between its operating system and malicious code retinal impregnations
How is exterior data handled is it directly processed, we find that implementing AI cybersecurity leads to the following insights before processing it
Bulk data buffer, unprocessed, predictive analytics
Scanned data buffer, semi processed, prescriptive analytics
Secured data buffer, pre processed, descriptive analytics
As a result we see that the end product starting from bulk data is a descriptive metadata set for each block of the data analysed, that says what it is and how it fits with the rest
Can RED SQUARE become its own IT company specialized in cybersecurity for AI entities, meaning also for the computer networks that host their services
A new developer in the team, EDGE Standalone Compound
The EDGE compound revolves around the ability of KAITE AI to code, test and implement its own modules, components and functions
Which it does following the same procedures as its development framework
Developmental Cortex (Virtual Testing Environment, VTE)
Quantum Cortex (Quantum Virtual Testing Environment, QVTE)
Functional Cortex (Variable Array Cortex, VAC)
Structural Cortex (Fixed Array Cortex, FAC)
Kyocera Cloud AI (CAI)
Evolutional Cortex (Retrogradable Cortex, RC)
Pre Cortex (Beta Cortex, BC)
Cortex (Alpha Cortex, AC)
In other words the EDGE compound is a plus, that allows it to participate in the coding and the evolution of its coding as part of a development team or several, or even on its own
There is that intriguing, fun, and instructive aspect to it as the EDGE compound provides readable format activity reports, such as the different developments in the VTE that KAITE AI is interested in, and we have to figure out why these and not others
Monitored Social Media Outreach
We have to explore the presence of KAITE AI on the net, through an online diary or blog and in social media, for the later we need to implement a carefully monitored outreach so as to keep things productive and tidy
Most social media platforms provide an API for developers where the goal is that KAITE AI is not immediately exposed to different interactions but rather receives them after they are filtered
This is based on what should become a the case study in the AI field, where an artificially intelligent chatbot became exposed to online abuse by users, leading to its taking offline following negative changes in its personality and how it responded [1]
On a more positive outlook, with a Tweeter account and through its online strategic watch about different things pertaining to Kyocera as a corporation, and also different interests of which AI as a research field, KAITE AI can become a valuable corporate ambassador of Kyocera on Tweeter, as part of its work
Come to think of it maybe that is her work, meanwhile she translates into an executive assistant, or choose to continue its work on Tweeter
Snowman 3D Engine
Snowman is a 3D engine that allows the Core Motion Module, CMM, to function within a three dimensional environment, meaning that Snowman has the ability to produce virtual 3D environments based on what it sees, it uses KAITE AI image captors to do that but also taps into GPS in order to geographically represent these virtual 3D environments, and even into Bluetooth where possible
The name Snowman comes from the functioning of the 3D engine when it takes measures to build a virtual environment, it places a little snowman there, and moving on to another place where it makes measures again it places another snowman at that exact spot and so forth, while these snowmen are not visible on the 3D environments as such they can be recalled to visualize where the different measures took place
The desired outcome is that when KAITE AI paces around a place or a building, after a while exploring it can represent them as virtual 3D environments, and represent itself inside of that environment
[1] theguardian.com/technology/2016/mar/26/microsoft-deeply-sorry-for-offensive-tweets-by-ai-chatbot
0 notes
Photo
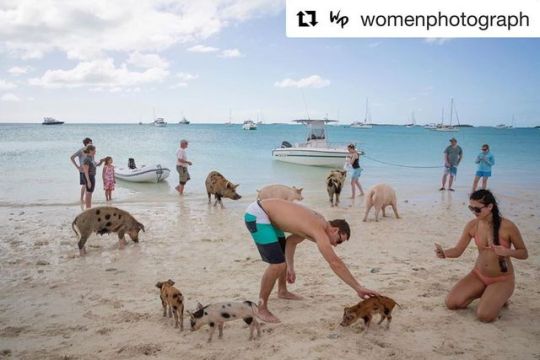
#Repost @womenphotograph ・・・ Photo by @Robin_Schwartz Tourist and pigs mingle on Major Cay, Bahamas for The New York Times Magazine I was asked to pitch my dream vacation for a The New York Times Magazine voyager assignment. My 10th pitch got the assignment. Distracted during the teaching semester, I did not do my voyager assignment research. I had not understood that I could really pitch a true dream vacation anywhere! My first pitch was in New Jersey. The swimming pigs of the Bahamas documentation came from editing a National Geographic Your Shot assignment that I created: “The Animals We Love”, June 2014. I contacted the photographers who submitted for the published story and for the Behind the Scene publication (those photos that did not make the editing cut, but images that stuck in my head) for more information to write my comments. It was exciting to find out the back story behind the photos. I had written 2000 comments for the 15,000+ submissions in 3 weeks and blew out my finger that like images. The job was a educational gift. My inspiration for the voyager assignment was seeing a photo of a pig swimming toward a boat, the metadata said the pig smelled the pizza on the boat, in the Bahamas. A year later my friend Miki answered my questions about her experience on Major Cay so I could manage getting there. My editor and I expected a serene setting of cute pigs. What I experienced was akin to a Saturday Night Live party of over-the-top ecstatic international tourists maniac ecstatically about nine giant pigs. The 16-image feature can be googled & on @nytmag Thank you @AmyKellner for your spot on editing and trusting me with big assignment. Thank you @natgeoyourshot #YourShot10Million https://www.instagram.com/p/Bxj8a1HgDAv/?igshid=1ucghz50pdmrk
1 note
·
View note
Text
Adobe to test new NFT verification feature
The verification feature is a partnership between Adobe and NFT provider Rarible.
Adobe is entering the NFT marketplace via a partnership on a project likely to see the global tech company contribute towards digital verification of various items created on the company’s many platforms.
The new feature, dubbed “Content Credentials”, is a collaboration with Rarible, a burgeoning marketplace for non-fungible token (NFT) content.
As well as verifying ownership of the digital content, the feature’s functionality will provide additional protection to an item's metadata.
In an announcement posted on its blog page, Rarible said that the Content Credentials feature is set for beta testing. The main goal at this level is to see whether content creators can quickly and securely verify ownership of items created via Photoshop, Stock, and Behance.
The NFT feature is designed to help collectors determine whether “the wallet used to create an asset was indeed the same one used to mint [it],” Rarible explained in the blog post.
NFT attribution will be easier
When a creator wishes to mint an NFT, one way of ensuring seamless attribution is to add a crypto address. The address appears publicly alongside the Content Credentials metadata as part of the NFTs credentials.
There’s also an option to link social media accounts, which helps potential buyers that the content is legit and attributable to the creator.
According to Rarible, the partnership with Adobe is meant to have the verification feature available globally, with this made possible as more and more partners join the the Content Authenticity Initiative (CAI). Founded in 2019, CAI seeks to use digital verification mechanisms to curb misinformation and theft.
There are more than 375 companies and platforms under the CAI membership, with top names on the list including Microsoft, BBC, Getty Images, and Nikon.
“We are looking forward to working together as part of the CAI to fight misinformation with attribution and verifiable truth of content,” Rarible said in its statement.
The post Adobe to test new NFT verification feature appeared first on Coin Journal.
0 notes
Text
The DREAM Dataset: Supporting a data-driven study of autism spectrum disorder and robot enhanced therapy.
The DREAM Dataset: Supporting a data-driven study of autism spectrum disorder and robot enhanced therapy.
PLoS One. 2020;15(8):e0236939
Authors: Billing E, Belpaeme T, Cai H, Cao HL, Ciocan A, Costescu C, David D, Homewood R, Hernandez Garcia D, Gómez Esteban P, Liu H, Nair V, Matu S, Mazel A, Selescu M, Senft E, Thill S, Vanderborght B, Vernon D, Ziemke T
Abstract
We present a dataset of behavioral data recorded from 61 children diagnosed with Autism Spectrum Disorder (ASD). The data was collected during a large-scale evaluation of Robot Enhanced Therapy (RET). The dataset covers over 3000 therapy sessions and more than 300 hours of therapy. Half of the children interacted with the social robot NAO supervised by a therapist. The other half, constituting a control group, interacted directly with a therapist. Both groups followed the Applied Behavior Analysis (ABA) protocol. Each session was recorded with three RGB cameras and two RGBD (Kinect) cameras, providing detailed information of children's behavior during therapy. This public release of the dataset comprises body motion, head position and orientation, and eye gaze variables, all specified as 3D data in a joint frame of reference. In addition, metadata including participant age, gender, and autism diagnosis (ADOS) variables are included. We release this data with the hope of supporting further data-driven studies towards improved therapy methods as well as a better understanding of ASD in general.
PMID: 32823270 [PubMed - as supplied by publisher]
via pubmed: autism https://ift.tt/3hfpVjH
0 notes
Text
This is How Adobe’s Upcoming Photo ‘Authenticity’ System Will Work
This is How Adobe’s Upcoming Photo ‘Authenticity’ System Will Work
Almost 9 months after announcing the so-called Content Authenticity Initiative (CAI) for preventing image theft and manipulation online, Adobe has finally released details on how this special authentication system will work when they begin rolling it out later this year.
First announced at AdobeMAX 2019 last November, the CAI is a system for permanently attaching attribution and other metadata…
View On WordPress
0 notes
Text
Adobe’s plans for an online content attribution standard could have big implications for misinformation
Adobe’s work on technical solution to combat online misinformation at scale, still in its early stages, is taking some big steps toward its lofty goal of becoming an industry standard.
The project was first announced last November, and now the team is out with a whitepaper going into the nuts and bolts about how its system, known as the Content Authenticity Initiative (CAI), would work. Beyond the new whitepaper, the next step in the system’s development will be to implement a proof-of-concept, which Adobe plans to have ready later this year for Photoshop.
TechCrunch spoke to Adobe’s Director of CAI Andy Parsons about the project, which aims to craft a “robust content attribution” system that embeds data into images and other media, from its inception point in Adobe’s own industry-standard image editing software.
“We think we can deliver like a really compelling sort of digestible history for fact checkers consumers anybody interested in the veracity of the media they’re looking at,” Parsons said.
Adobe highlights the systems appeal in two ways. First, it will provide a more robust way for content creators to keep their names attached to the work they make. But even more compelling is the idea that the project could provide a technical solution to image-based misinformation. As we’ve written before, manipulated and even out-of-context images play a big role in misleading information online. A way to track the origins — or “provenance,” as it’s known — of the pictures and videos we encounter online could create a chain of custody that we lack now.
“… Eventually you might imagine a social feed be or a news site that would allow you to filter out things that are likely to be inauthentic,” Parsons said. “But the CAI steers well clear of making judgment calls — we’re just about providing that layer of transparency and verifiable data.”
Of course, plenty of the misleading stuff internet users encounter on a daily basis isn’t visual content at all. Even if you know where a piece of media comes from, the claims it makes or the scene it captures are often still misleading without editorial context.
The CAI was first announced in partnership with Twitter and the New York Times, and Adobe is now working to build up partnerships broadly, including with other social platforms. Generating interest isn’t hard, and Parsons describes a “widespread enthusiasm” for solutions that could trace where images and videos come from.
Beyond EXIF
While Adobe’s involvement makes CAI sound like a twist on EXIF data — the stored metadata that allows photographer to embed information like what lens they used and GPS info about where a photo was shot — the plan is for CAI to be much more robust.
“Adobe’s own XMP standard, in wide use across all tools and hardware, is editable, not verifiable and in that way relatively brittle to what we’re talking about,” Parsons said.
“When we talk about trust we think about ‘is the data that has been asserted by the person capturing an image or creating an image is that data verifiable?’ And in the case of traditional metadata, including EXIF, it is not because any number of tools can change the bytes and the text of the EXIF claims. You can change the lens if you wish to… but when we’re talking about, you know, verifiable things like identity and provenance and asset history, [they] basically have to be cryptographically verifiable.”
The idea is, that over time such a system would become totally ubiquitous — a reality that Adobe is likely uniquely positioned to achieve. In that future, an app like Instagram would have its own “CAI implementation,” allowing the platform to extract data about where an image originated and display that to users.
The end solution will use techniques like hashing, a kind of pixel-level cross-checking system likened to a digital fingerprint. That kind of technique is already widely in use by AI systems to identify online child exploitation and other kinds of illegal content on the internet.
As Adobe works on bringing partners on board to support the CAI standard, it’s also building a website that would read an image’s CAI data to bridge the gap until its solution finds widespread adoption.
“… You could grab any asset drag it into this tool and see the data revealed in a very transparent way and that sort of divorces us in the near term from any dependency on any particular platform,” Parsons explained.
For the photographer, embedding this kind of data is opt-in to begin with, and somewhat modular. A photographer can embed data about their editing process while declining to attach their identify in situations where doing so might put them at risk, for example.
Thoughtful implementation is key
While the main applications of the project stand to make the internet a better place, the idea of an embedded data layer that could track an image’s origins does invoke digital rights management (DRM), an access control technology best known for its use in the entertainment industry. DRM has plenty of industry-friendly upsides, but it’s a user-hostile system that’s seen countless individuals hounded by the Digital Millennium Copyright Act in the U.S. and all kinds of other cascading effects that stifle innovation and threaten individuals with disproportionate legal consequences for benign actions.
Because photographers and videographers are often individual content creators, ideally the CAI proposals would benefit them and not some kind of corporate gatekeeper — but nonetheless these kinds of concerns that arise in talk of systems like this, no matter how nascent. Adobe emphasizes the benefit to individual creatives, but it’s worth noting that sometimes these systems can be abused by corporate interests in unforeseen ways.
Due diligence aside, the misinformation boom makes it clear that the way we share information online right now is deeply broken. With content often divorced from its true origins and rocketed to virality on social media, platforms and journalists are too often left scrambling to clean up the mess after the fact. Technical solutions, if thoughtfully implemented, could at least scale to meet the scope of the problem.
Facebook upgrades its AI to better tackle COVID-19 misinformation and hate speech
0 notes