#computernetworksecurity
Explore tagged Tumblr posts
Text
Top 10 Cyber Security Awareness Tips Around The World

The internet has become the breeding ground for Trojans, malicious links, and viruses. Data breaching has become the most rampant. Unauthenticated users are commonplace, and they are more vulnerable than ever before.
It is said that human error may constitute 95% of security breaches. At the same time, managing employees' cyber risk is imperative for your business to prevent client-related data theft and enable regulatory compliance.
In this connection, it is apt to maintain the core concept of a strong human risk management program(HRM). It provides training to the end-user on how to find out and fight modern threats and, at the same time, involved in the best practice to become security savvy.
What Are The TOP 10 Cyber Security Awareness Tips?
Up-To-Date Your Software
Ransomware is considered a major threat to both individuals and businesses. One of the most vital pieces of cyber security advice to prevent Ransomware is to update the old-fashioned software, application, and operating system. It directly plugs the security hole that hackers leverage to access your device. Some points that will help you a lot:
1. Activate automatic updates for your system
2. You should ensure that your desktop web browsers use automatic security updates.
3. Update your web browsers plugins
Use Firewall and Anti- Virus
Undoubtedly, anti-virus is the most prevalent solution to prevent viruses. It prevents malware and other dangerous viruses from entering your system. You can use an anti-virus kit from a trusted source and run it on your device.
A firewall is another very robust measure to prevent virus attacks. It helps to discover the viruses and other malicious attacks that often occur over the internet and ascertain what traffic is permitted to enter your device.
Apply Password Management Tools and Strong Password
You may be aware that a strong password is a key to security online. Certain rules you have to apply when setting a password. The following tips you may follow:
1. Instead of crazy and complex combinations of upper and lower case, and symbols, it is better to use strong yet user-friendly with at least eight characters long and extend them up to 64 characters.
2. Never use the same password twice.
3. The password should contain at least one uppercase, lowercase, numeric, and symbol.
4. You can reset the password and use the new password when you forget it.
Use Two-Factor or Multi-Factor Authentication
It is nothing but provides you with an additional layer of security to the standard password method. Despite giving a strong password, a hacker guesses it correctly. However, having authentication, hackers cannot hack it. After completing your password credential with multi-factor authentication, you can enter two additional authentication methods.
Be Mindful of Phishing Scams
Phishing is when an attacker sends a malicious link or entices the recipient to open the attachment, infecting the system with malware. It frequently leads to Ransomware, and It is evident that 90% of Ransomware arracks stem from a phishing attack.
Some important tips regarding phishing schemes are given below
1. Do not open the email from an unauthenticated source
2. Before clicking the link, you can hover over the link to come across where it directs you to
3. You should be very suspicious about the email sent to you; check where the email comes from and find out if there is a grammatical mistake.
4. When your friend forwards an email, it may happen that your friend has already been afflicted with various. So use extra caution.
Save Guard Your Sensitive Personal Identifiable Information(PII)
PII is the kind of information that the cyber attacker leverages to find an individual. It contains information like name, phone number, address, birth date, IP address, Social Security Number, or any other digital identification. The organization should protect the credit card you have provided they follow PCI DSS standards.
Social Media is a breeding ground for this mentioned above, so exercise caution. Use your information as minimally as possible on social media, particularly Facebook. You risk your security breach by adding your PII information on social media.
Secure Your Mobile Device
The report from Mcafee Labs, your mobile device is the latest target, and statistics show that more than 1.5 million are already infected with malware.
Below are some tips that keep your mobile secure:
1. Create a complex password
2. Install Apps from an authenticated source
3. Always keep your mobile update
4. Make a habit of taking regular backups from Android backup and sync.
Back up Your Data Daily
Back up regularly is a neglected step in personal safety measures. According to the Top-notch IT Security firm, they follow a simple method called the 3-2-1 backup rule. It says you keep three copies of data in two different media – you store in local and external resources like hard drives and cloud storage.
By any chance, if you are attacked with malicious malware, format your system and then reload with recent backed-up data.
Refrain From Using Public WI-FI
Avoiding public Wi-Fi sans using a VPN( Virtual Private Network) is not advisable. Apply VPN; the traffic between your and the VPN server is strongly encrypted. It provides a strong shield and prevents cybercriminals from accessing your data from your device. Apply your cell network when you do not have a VPN facility.
Review Your Online Accounts Regularly
With ever-rising cyber fraud, it is always recommended that consumers should check their accounts and credit reports. One recommended method is to freeze your credit to prevent your personal information from being breached by cybercriminals. It permits you to lock your credit and apply PII. You only know that information. Whenever you feel like applying for credit, you can use this PIN.
Summing Up
You can strengthen your security in all forms by incorporating the tips above.
#cybersecurity#cybersecurityawareness#cyber#computernetworksecurity#computersecurity#computersecurityday#computerscience#hacker
1 note
·
View note
Text












#computernetwork#networkcomputer#computersnetwork#computernetworking#computernetworks#computernetworkingtechnology#computernetworkengineering#computerandnetworkengineering#networkcomputerwireless#networkcomputerandrepair#computernetworkingcourses#computernetworkingnj#networkingcomputers#computernetworksecurity#recyclenetworkingcomputerequipment#networkcomputers#computersnetworks#computernetworkassignmenthelp#computernetworkservices#computernetworkcommunity#newtrendcomputernetworksllc
0 notes
Link
Networks security is the method of providing protection to a network from unauthorized access and threats. The need for Network Security is achieving its own significance in today’s world. Also, it is the job of network admins to activate preventive measures to protect their networks. Today’s companies are experiencing a shortage of expert Networking Security Professionals. Doing Network Security Projects will certainly give individuals the chance for better career opportunities.
Why Network Security Projects are Important?
Computer networks that are involving in day to day transactions and communication require security. With a Network Security System, all the data can be kept safe. Also it can protect data from access without authorization from people present inside and outside of the network. Thus, we can prevent many cyber-attacks and other harmful activities. Generally the most usual and simple way of securing a network resource is by providing it a unique name and a good password. The Network Security Projects provide the skills required to enter fast-paced work environments.
Start your career with a good project
Pantech eLearning Chennai is an Online Learning Service provider. We are providing some of the best Network Security Projects.
Given below is the list of Top Projects we are providing:
Secure File Sharing System
In this paper, we propose a secure file storing and retrieving mechanism to avoid the limitations in existing systems like, file encryption, access rights and also key management.
Deduplication for Hybrid Cloud Security
To better protect data security, this paper makes the first attempt to formally address the problem of authorized data deduplication.
Graphical Password Scheme
Graphical passwords are a replacement to text-type passwords where user is asking to identify an image or parts of an image rather than a word.
Secure Data Sharing for Dynamic Groups
Anti-collusion information sharing scheme for dynamic companies within the cloud, the customers can also securely obtain their private keys from team manager certificates Authorities and secure communication channels.
Multifarious Data Processor
Speech recognition for application Voice Message is done on Google server, using the HMM algorithm.
Malware Detection
This paper introduced SparkChiSVM model for intrusion detection. We also use ChiSqSelector for feature selection, and build an intrusion detection model.
Four factor Authentication
To design and development Captcha to address a number of security problems altogether, such as online guessing attacks, relay attacks.
Erasure Coding Scheduling
We propose a CCC platform, called Harmony, which integrates resource management and also reputation management in a harmonious manner.
User-Level Runtime Security Auditing
In this paper, we propose a privacy-preserving mechanism that supports public auditing on shared data stored in the cloud. Also, we exploit ring signatures to compute verification metadata needed to audit the correctness of shared data.
Visit our Website and Book your Projects Now.
0 notes
Link
0 notes
Photo

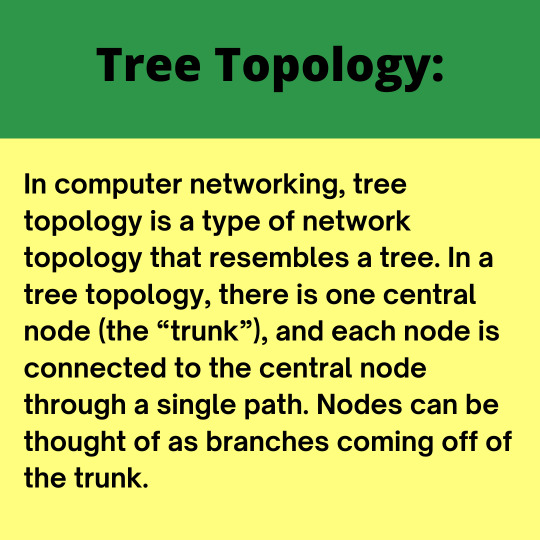
Topic - Network Topologies Page Moto - The main aim to create this page is to provide you all a self learning environment for different programming languages. Follow @computer_science_guidance for more ----------------------------------------- Tags - #computernetwork #networkcomputer #computersnetwork #computernetworking #computernetworks #computernetworkingtechnology #computernetworkengineering #computerandnetworkengineering #networkcomputerwireless #networkcomputerandrepair #computernetworkingcourses #computernetworkingnj #networkingcomputers #computernetworksecurity #recyclenetworkingcomputerequipment #networkcomputers #computersnetworks #computernetworkassignmenthelp #computernetworkservices #computernetworkcommunity #newtrendcomputernetworksllc https://www.instagram.com/p/CiPP-k_Ptz8/?igshid=NGJjMDIxMWI=
#computernetwork#networkcomputer#computersnetwork#computernetworking#computernetworks#computernetworkingtechnology#computernetworkengineering#computerandnetworkengineering#networkcomputerwireless#networkcomputerandrepair#computernetworkingcourses#computernetworkingnj#networkingcomputers#computernetworksecurity#recyclenetworkingcomputerequipment#networkcomputers#computersnetworks#computernetworkassignmenthelp#computernetworkservices#computernetworkcommunity#newtrendcomputernetworksllc
0 notes
Photo
Topic - Concept of Computer Networks Page Moto - The main aim to create this page is to provide you all a self learning environment for different programming languages. Follow @computer_science_guidance for more ----------------------------------------- Tags - #computernetwork #networkcomputer #computersnetwork #computernetworking #computernetworks #computernetworkingtechnology #computernetworkengineering #computerandnetworkengineering #networkcomputerwireless #networkcomputerandrepair #computernetworkingcourses #computernetworkingnj #networkingcomputers #computernetworksecurity #recyclenetworkingcomputerequipment #networkcomputers #computersnetworks #computernetworkassignmenthelp #computernetworkservices #computernetworkcommunity #newtrendcomputernetworksllc https://www.instagram.com/p/CiPP0JzPNKw/?igshid=NGJjMDIxMWI=
#computernetwork#networkcomputer#computersnetwork#computernetworking#computernetworks#computernetworkingtechnology#computernetworkengineering#computerandnetworkengineering#networkcomputerwireless#networkcomputerandrepair#computernetworkingcourses#computernetworkingnj#networkingcomputers#computernetworksecurity#recyclenetworkingcomputerequipment#networkcomputers#computersnetworks#computernetworkassignmenthelp#computernetworkservices#computernetworkcommunity#newtrendcomputernetworksllc
0 notes
Photo

Small Business IT Solutions Delaware
Find the IT solutions for your small business needs with our automated patch management. Our team understands the many challenges of operating a business; we are here helping grow your business!
#ITSupportServices#NetworkServices#ITHelpDesk#ComputerSupport#ITConsulting#ProjectSupport#OfficeITSupport#ServerHostingSupport#CloudHostingSupport#Antivirussolutions#Computerhardwaresolutions#ComputerNetworkSecurity#Cloudhostingservices#ITServiceDesk
0 notes
Text
U.S. Rolls Out Strict Rules for Commercial Spyware Use, Amidst Rash of Hacks
The Biden administration passed an executive order Monday that seeks to implement strict new guidelines for what kind of commercial spyware can be used by U.S. government agencies. Read more��

View On WordPress
#computerandnetworksurveillance#computernetworksecurity#computersecurity#Cyberwarfare#deception#espionage#identitytheft#joebiden#nsogroup#onlineadvertising#politics#Security#Spyware
0 notes
Text
I Read the Biden Administration's New Cyber Policy So You Don't Have To
Since taking office, Joe Biden has made it known that he’s going to take cybercrime seriously. It’s not the case that Biden is the world’s most tech-savvy octonarian, rather, he’s simply responding to security challenges that have developed on his watch—most notably a string of increasingly destructive cyberattacks… Read more…

View On WordPress
#computernetworksecurity#computersecurity#cyber securityregulation#cyberattack#cybercrime#Cyberwarfare#joebiden#nationalsecurity#politics#Prevention#ransomware#Security#technology2cinternet#vladimirputin
0 notes
Text
You Really Should Bind Your VPN to Your Torrent Client
You Really Should Bind Your VPN to Your Torrent Client
When you’re downloading torrents on your computer, consider using a VPN. Your ISP and advertising companies don’t need to know you’re downloading the latest Linux distros or other totally legal content, and a good VPN can help you improve your privacy. Read more…

View On WordPress
#BitTorrent#computernetworking#computernetworksecurity#Computing#digitaltechnology#internetprivacy#keepsolid#networkarchitecture#portablesoftware#qbittorrent#softethervpn#technology2cinternet#virtualprivatenetworks
0 notes
Text
The FBI Reportedly Came Very Close to Deploying Spyware for Domestic Surveillance
The FBI Reportedly Came Very Close to Deploying Spyware for Domestic Surveillance
The FBI came very close to using commercial spyware to aid in its domestic criminal investigations, the New York Times has reported. The spyware was developed by the NSO Group, the notorious surveillance vendor from Israel whose products have been tied to spying scandals all over the world. Read more…

View On WordPress
#chriswray#computernetworksecurity#computersecurity#espionage#federalbureauofinvestigation#l3harristechnologies#law2ccrime#nsogroup#Pegasus#politics#roberthanssen#Security#Spyware
0 notes
Text
DuckDuckGo's New Web Browser Will Protect Your Privacy While You Watch YouTube
DuckDuckGo’s New Web Browser Will Protect Your Privacy While You Watch YouTube
DuckDuckGo launched a web browser for macOS in beta today, offering privacy-minded web surfers a new way to browse. The browser uses a variety of techniques to protect your information from snooping websites and even includes some innovative tools, including Duck Player, which is supposed to let you watch YouTube with… Read more…

View On WordPress
#brave#computernetworksecurity#duckduckgo#Google#googlechrome#httpcookie#internetprivacy#internetsearchengines#onlineadvertising#privatebrowsing#safari#smarterencryption#smarterencryptiontool#Software#technology2cinternet#webbrowsers
0 notes
Text
Election Software CEO Arrested Over Suspected Poll Worker Data Theft
Election Software CEO Arrested Over Suspected Poll Worker Data Theft
The founder and CEO of Konnech, a company at the center of many 2020 election denier conspiracy theories, was arrested on Tuesday under suspicion of data theft. Specifically, Eugene Yu is accused of storing Los Angeles County poll worker information on servers in China, in violation of Konnech’s contract with the… Read more…

View On WordPress
#computernetworksecurity#computersecurity#cybercrime#databreach#e-commerce#eugeneyu#george#georgegascc3b3n#konnech#nationalsecurity#Prevention#securecommunication#Security#technology2cinternet
0 notes
Text
How Malware Hides in Images and What You Can Do About It
How Malware Hides in Images and What You Can Do About It
There are plenty of dangers to watch out for when it comes to keeping your devices and your data safe, including viruses, phishing attempts, compromised wifi networks, and rogue USB sticks. Here, we’re going to talk about one of the lesser-known threats: Compromised images. Read more…

View On WordPress
#computernetworksecurity#computervirus#cybercrime#Cyberwarfare#deception#internetprivacy#jameswebb#malware#Prevention#ransomware#ReversingLabs#safety#Security#securitybreaches#technology2cinternet
0 notes