#csma/ca
Explore tagged Tumblr posts
Text
Ve489 Computer Networks Homework Set 4
Answer following questions about random access protocols: What is the vulnerable period for Aloha? How about slotted Aloha? Explain it. What is vulnerable period of CSMA? How can we make sure the performance of CSMA is better than Aloha? Why collision detection (CD) can improve performance of CSMA? Considering the CSMA/CA based DCF in IEEE 802.11, answer the following questions: What is…
0 notes
Text
Telecommunication protocols application interaction
Let's look at the basics of transferring information between two application processes in the OSI model.
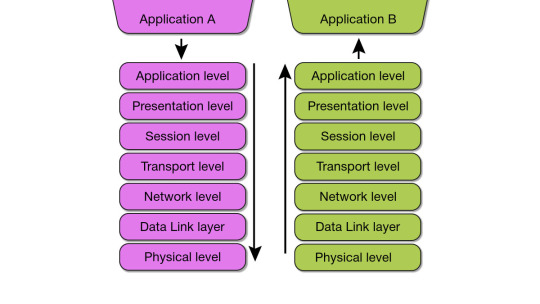
Say an application (in the picture above) needs to access a file service on another computer. It sends a request to the application layer. Based on it, the software generates a standard format message consisting of a data field and a service header. The latter contains a description of actions for the application layer of the other machine to perform, as well as instructions for the adjacent lower layer. The presentation layer, in turn, formats the data according to the instructions received and adds its own header (some protocol implementations also include service data at the end of the message), after which the information is sent to the session layer. This procedure, called encapsulation, is repeated further as data and service information move to the physical layer.
When arriving at the physical layer, i.e., the network, data passes through many other devices (network adapters, hubs, routers, bridges, etc.) and, upon reaching the destination (for example, a SIP phone), undergoes a reverse encapsulation process (right side of the picture).
Data networks can be of two types: local (local area network, LAN) and global (wide area network, WAN). The latter connects any two networks within the globe with dedicated or switched communication channels. Local networks differ in transmission medium, topology, and access control. Depending on the transmission medium, they are divided into wired (using coaxial, twisted pair, or fiber-optic cable) and wireless (WLAN), and according to the type of topology, into networks with 'bus', 'ring', or 'star' topologies.
Each computer on the local network is connected to the transmission medium through a special adapter that "sees" what any other adapter on the same network is transmitting; such systems are called broadcasts.
The MAC protocol regulates the sequence of nodes' access to the transmission medium. It is implemented using two types of schemes: polling or contention-based MAC schemes.
MAC polling networks can be centralized or distributed. Centralized ones have a star topology with a hub as the control node. In contrast, distributed ones have a ring or bus topology with token passing. Contention-based MACs are often implemented as carrier sense multiple access with collision detection (CSMA/CD) or carrier sense multiple access with collision avoidance (CSMA/CA). The first is used in all types of Ethernet LANs, and the second is used in most wireless WLANs.
The unrivaled leader among local networks is the IEEE 802.3 Ethernet network, where coaxial, twisted pair (designated by the letter T for 'twisted') and fiber-optic cables are used as transmission media. The transition to twisted-pair cable made it possible to implement full-duplex transmission over two twisted pairs, leaving the concept of collision meaningless since transmission and reception became independent operations. Ethernet has transmission speeds of 10, 100 ('Fast Ethernet'), 1000 Mbit/s (1 Gbit/s, 'Gigabit Ethernet'), and up to 400 Gigabit Ethernet.
Wireless local networks (wireless LAN, WLAN) have also become widespread. Their parameters are stated in the IEEE 802.11 specifications, known as Wi-Fi.
Today, the most common Wi-Fi 5 or 802.11ac defines the operation of wireless local area networks in the 2.4/5 GHz ranges with a data transfer rate of 1.3 Gbit/s. Shortly, speeds will reach 9.6 Gbit/s over 6 GHz frequency bands.
The range of most WLAN systems is 120 m, depending on the number and type of obstacles encountered. Additional access points will help expand the coverage area. Using two or three carrier frequencies instead of one can increase the number of users and network capacity.
Obviously, with Wi-Fi, network security becomes an important issue. A priori, wireless networks must be equipped with additional means of ensuring reliability compared to wired ones. WLAN uses direct sequence spread spectrum (DSSS) technology, which is highly resistant to data corruption and interference, including intentional ones. The problem of user authentication can be solved by introducing system identifiers. The wired equivalent privacy (WEP) mode is provided to transmit necessary information. In this case, the signal is encrypted with an additional algorithm, and the data is controlled using an electronic key.
Like all IEEE 802.3 standards, 802.11 refers to the lower two layers of the OSI model: physical and link. Any network application, operating system, or protocol (such as TCP/IP) will function equally well on an 802.11 network or Ethernet one.
The original 802.11 standard defines the basic architecture - the features of 802.11 services. The 802.11x specification only addresses the physical layer, introducing higher access speeds.
In conclusion, we should note that thanks to the close ties between Ethernet and the IP protocol, the scope of Ethernet applications is expanding, particularly in broadband subscriber access (BSA) networks.
0 notes
Text
Multiple Access Protocol - ALOHA, CSMA, CSMA/CA and CSMA/CD
Multiple Access Protocol – ALOHA, CSMA, CSMA/CA and CSMA/CD Multiple access protocols are a set of protocols that work in the Medium Access Control sublayer (MAC sublayer) of the Open Systems Interconnection (OSI) model. These protocols allow a number of users to access a shared network channel. Several data streams originating from several nodes are transferred through the multi-point…
View On WordPress
0 notes
Text
Topology
Topology :
Topology defines the structure of the network of how all the components are interconnected to each other. There are two types of topology: physical and logical topology.
Physical topology is the geometric representation of all the nodes in a network.
Bus Topology
The bus topology is designed in such a way that all the stations are connected through a single cable known as a backbone cable.
Each node is either connected to the backbone cable by drop cable or directly connected to the backbone cable.
When a node wants to send a message over the network, it puts a message over the network. All the stations available in the network will receive the message whether it has been addressed or not.
The bus topology is mainly used in 802.3 (ethernet) and 802.4 standard networks.
The configuration of a bus topology is quite simpler as compared to other topologies.
The backbone cable is considered as a “single lane” through which the message is broadcast to all the stations.
The most common access method of the bus topologies is CSMA (Carrier Sense Multiple Access).
CSMA: It is a media access control used to control the data flow so that data integrity is maintained, i.e., the packets do not get lost. There are two alternative ways of handling the problems that occur when two nodes send the messages simultaneously.
CSMA CD: CSMA CD (Collision detection) is an access method used to detect the collision. Once the collision is detected, the sender will stop transmitting the data. Therefore, it works on “recovery after the collision”.
CSMA CA: CSMA CA (Collision Avoidance) is an access method used to avoid the collision by checking whether the transmission media is busy or not. If busy, then the sender waits until the media becomes idle. This technique effectively reduces the possibility of the collision. It does not work on “recovery after the collision”.
Advantages of Bus topology:
Low-cost cable: In bus topology, nodes are directly connected to the cable without passing through a hub. Therefore, the initial cost of installation is low.
Moderate data speeds: Coaxial or twisted pair cables are mainly used in bus-based networks that support upto 10 Mbps.
Familiar technology: Bus topology is a familiar technology as the installation and troubleshooting techniques are well known, and hardware components are easily available.
Limited failure: A failure in one node will not have any effect on other nodes.
Disadvantages of Bus topology:
Extensive cabling: A bus topology is quite simpler, but still it requires a lot of cabling.
Difficult troubleshooting: It requires specialized test equipment to determine the cable faults. If any fault occurs in the cable, then it would disrupt the communication for all the nodes.
Signal interference: If two nodes send the messages simultaneously, then the signals of both the nodes collide with each other.
Reconfiguration difficult: Adding new devices to the network would slow down the network.
Attenuation: Attenuation is a loss of signal leads to communication issues. Repeaters are used to regenerate the signal.
Ring Topology
Token passing: It is a network access method in which token is passed from one node to another node.
Token: It is a frame that circulates around the network.
Working of Token passing
A token moves around the network, and it is passed from computer to computer until it reaches the destination.
The sender modifies the token by putting the address along with the data.
The data is passed from one device to another device until the destination address matches. Once the token received by the destination device, then it sends the acknowledgment to the sender.
In a ring topology, a token is used as a carrier.
Advantages of Ring topology:
Network Management: Faulty devices can be removed from the network without bringing the network down.
Product availability: Many hardware and software tools for network operation and monitoring are available.
Cost: Twisted pair cabling is inexpensive and easily available. Therefore, the installation cost is very low.
Reliable: It is a more reliable network because the communication system is not dependent on the single host computer.
Disadvantages of Ring topology:
Read More
Difficult troubleshooting: It requires specialized test equipment to determine the cable faults. If any fault occurs in the cable, then it would disrupt the communication for all the nodes.
Failure: The breakdown in one station leads to the failure of the overall network.
Reconfiguration difficult: Adding new devices to the network would slow down the network.
Delay: Communication delay is directly proportional to the number of nodes. Adding new devices increases the communication delay.
Star Topology
Star topology is an arrangement of the network in which every node is connected to the central hub, switch or a central computer.
The central computer is known as a server, and the peripheral devices attached to the server are known as clients.
Coaxial cable or RJ-45 cables are used to connect the computers.
Hubs or Switches are mainly used as connection devices in a physical star topology.
Star topology is the most popular topology in network implementation.
Advantages of Star topology
Efficient troubleshooting: Troubleshooting is quite efficient in a star topology as compared to bus topology. In a bus topology, the manager has to inspect the kilometers of cable. In a star topology, all the stations are connected to the centralized network. Therefore, the network administrator has to go to the single station to troubleshoot the problem.
Network control: Complex network control features can be easily implemented in the star topology. Any changes made in the star topology are automatically accommodated.
Limited failure: As each station is connected to the central hub with its own cable, therefore failure in one cable will not affect the entire network.
Read More
Familiar technology: Star topology is a familiar technology as its tools are cost-effective.
Easily expandable: It is easily expandable as new stations can be added to the open ports on the hub.
Cost effective: Star topology networks are cost-effective as it uses inexpensive coaxial cable.
High data speeds: It supports a bandwidth of approx 100Mbps. Ethernet 100BaseT is one of the most popular Star topology networks.
Disadvantages of Star topology
A Central point of failure: If the central hub or switch goes down, then all the connected nodes will not be able to communicate with each other.
Cable: Sometimes cable routing becomes difficult when a significant amount of routing is required.
Tree topology
Tree topology combines the characteristics of bus topology and star topology.
A tree topology is a type of structure in which all the computers are connected with each other in hierarchical fashion.
The top-most node in tree topology is known as a root node, and all other nodes are the descendants of the root node.
There is only one path exists between two nodes for the data transmission. Thus, it forms a parent-child hierarchy.
Advantages of Tree topology
Support for broadband transmission: Tree topology is mainly used to provide broadband transmission, i.e., signals are sent over long distances without being attenuated.
Easily expandable: We can add the new device to the existing network. Therefore, we can say that tree topology is easily expandable.
Easily manageable: In tree topology, the whole network is divided into segments known as star networks which can be easily managed and maintained.
Error detection: Error detection and error correction are very easy in a tree topology.
Limited failure: The breakdown in one station does not affect the entire network.
Read More
Point-to-point wiring: It has point-to-point wiring for individual segments.
Disadvantages of Tree topology
Difficult troubleshooting: If any fault occurs in the node, then it becomes difficult to troubleshoot the problem.
High cost: Devices required for broadband transmission are very costly.
Failure: A tree topology mainly relies on main bus cable and failure in main bus cable will damage the overall network.
Reconfiguration difficult: If new devices are added, then it becomes difficult to reconfigure.
Mesh topology
Mesh technology is an arrangement of the network in which computers are interconnected with each other through various redundant connections.
There are multiple paths from one computer to another computer.
It does not contain the switch, hub or any central computer which acts as a central point of communication.
The Internet is an example of the mesh topology.
Mesh topology is mainly used for WAN implementations where communication failures are a critical concern.
Mesh topology is mainly used for wireless networks.
Mesh topology can be formed by using the formula: Number of cables = (n*(n-1))/2;
Where n is the number of nodes that represents the network.
Mesh topology is divided into two categories:
Fully connected mesh topology
Partially connected mesh topology
Full Mesh Topology: In a full mesh topology, each computer is connected to all the computers available in the network.
Partial Mesh Topology: In a partial mesh topology, not all but certain computers are connected to those computers with which they communicate frequently.
Advantages of Mesh topology:
Reliable: The mesh topology networks are very reliable as if any link breakdown will not affect the communication between connected computers.
Fast Communication: Communication is very fast between the nodes.
Easier Reconfiguration: Adding new devices would not disrupt the communication between other devices.
Disadvantages of Mesh topology
Cost: A mesh topology contains a large number of connected devices such as a router and more transmission media than other topologies.
Management: Mesh topology networks are very large and very difficult to maintain and manage. If the network is not monitored carefully, then the communication link failure goes undetected.
Efficiency: In this topology, redundant connections are high that reduces the efficiency of the network.
Hybrid Topology
The combination of various different topologies is known as Hybrid topology.
A Hybrid topology is a connection between different links and nodes to transfer the data.
When two or more different topologies are combined together is termed as Hybrid topology and if similar topologies are connected with each other will not result in Hybrid topology. For example, if there exist a ring topology in one branch of ICICI bank and bus topology in another branch of ICICI bank, connecting these two topologies will result in Hybrid topology.
Advantages of Hybrid Topology
Reliable: If a fault occurs in any part of the network will not affect the functioning of the rest of the network.
Scalable: Size of the network can be easily expanded by adding new devices without affecting the functionality of the existing network.
Flexible: This topology is very flexible as it can be designed according to the requirements of the organization.
Read More
Effective: Hybrid topology is very effective as it can be designed in such a way that the strength of the network is maximized and weakness of the network is minimized.
Disadvantages of Hybrid topology
Complex design: The major drawback of the Hybrid topology is the design of the Hybrid network. It is very difficult to design the architecture of the Hybrid network.
Costly Hub: The Hubs used in the Hybrid topology are very expensive as these hubs are different from usual Hubs used in other topologies.
Costly infrastructure: The infrastructure cost is very high as a hybrid network requires a lot of cabling, network devices, etc.
#Topology#explain Topology#what is Topology#benifits of Topology#types of Topology#advantages of Topology#disadvantages of Topology#tree Topology#star Topology#ring Topology#mesh Topology#hybrid Topology#bus Topology#features of Topology
2 notes
·
View notes
Text
¿Qué onda con tu wifi?
Básicamente, el internet es una red que conecta a todas las computadoras (y celulares, tablets, etc...) del mundo. Imagínate que entre tu computadora y tu celular hubiera un hilo que las uniera, y de tu celular saliera un hilo que se conectara al celular de tu mamá y a la tablet de tu vecino, y esa tablet se conecta a otra y así hasta llegar a un celular en china. Imaginándote esto, ¿apoco no se forma una red gigante por todo el mundo?
Hay varias formas de tener alcance con el internet, tres de ellas son: local area network, metropolitan area y wide area network.
Una red puede tener la propiedad de ser cerrada o abierta; lo que significa que tiene protocolos con la dirección IP. Además la topología de la red se puede ver de dos formas: 1. Bus, a través de un cable de ethernet al que todas las computadoras en la red se conectan o 2. Estrella, que es una red inalámbrica con un punto central de acceso.
¿Qué es un protocolo? Es cómo se envían los paquetes de información a través de internet. En esta ocasión te voy a explicar dos de ellos:
CSMA/CD: Detección de colisiones, todos los mensajes son recibidos por todas las maquinas que están en el bus, cuando no hay mensajes transitando por él se pueden enviar mensajes. La información se manda con una dirección de llegada y pasa por todas las computadoras hasta que da con la dirección correcta, y esta es la que la recibe.
CSMA/CA: Conexión por wifi. Hay un acceso múltiple por detección de portadora con evitación de colisiones. Se da prioridad para mandar mensajes a las maquinas que llevan más tiempo esperando.
El software de internet tiene varias capas: 1. Aplicación, que ensambla el mensaje con una dirección. 2. Transporte, que divide el mensaje en paquetes. 3. Red, maneja el encaminamiento a través del internet. 4. Enlace, maneja la transmisión de paquetes.
Y a su vez, el internet mismo tiene capas, que sirven para la transferencia de mensajes a través de internet y para procesar la transferencia a través de unidades coordinadas y con funciones específicas.
¿Sabes qué es una dirección IP? Es la dirección de una interfaz de red, por eso en las películas de hackers siempre logran encontrar a personas al descubrir su dirección IP. Una dirección IP se compone por 32 bits, y una conexión privada no tiene la dirección completa. ICANN, que es la Internet Corporation for Assigned Names and Numbers es la encargada de asignar direcciones IP a los proveedores de servicios de internet.
Para tener una mejor conexión en tu casa podrías tener una combinación de redes; esto quiere decir combinar algunos de los siguientes:
Repetidor: extiende un red al conectar dos buses.
Puente: conecta dos redes compatibles
Conmutador: conecta varias redes compartibles
Router: conecta dos redes incompatibles.
Sin embargo tu conexión también depende el ancho de banda, cuyo alcance varía con la antena a la que te estés conectando. Te dejo esta página para medir la velocidad de tu internet: https://fast.com/es/
Finalmente te explico cómo puedes identificar una página web por su URL, ya que este se compone en diferentes partes: el protocolo, el servidor, el directorio y el nombre del documento al que finalmente llegas.

1 note
·
View note
Text
教你無線網路規劃建議
無線網路規劃建議
一般無線網路環境中,傳輸距離在開放空間中可達 300M、室內空間可達 100M,但是實際上合理的傳輸範圍約為 50M 左右,而這還要視環境情況而可能有所遞減。影響無線訊號涵蓋範圍的原因包括建築物的死角、結構、天線定位等,在使用無線網路產品時,常常因為訊號太弱、連線速度變慢、訊號斷斷續續、常斷線等問題,造成連線品質不穩定,甚至電腦就在路由器(基地台, AP)旁邊但是卻沒有訊號,而針對這些問題可能造成的情況,本篇文章將簡述該如何處理的方式。
無線網路的影響原因
以下是無線網路的影響原因:
(1). 訊號干擾
在一般的辦公室和開放空間中不容易遇到訊號干擾的問題,這通常是在家庭環境較容易受到影響。發生此狀況時,請檢查一下周圍環境,看看是否有電磁波較強的產品(如微波爐),如果有,建議將無線路由器(AP)或網卡遠離,以避免訊號干擾。
(2). 訊號不佳、容易斷線、傳輸速度慢
在無線環境中,訊號會因建築物結構、天線方向、無線路由器(AP, 基地台)位置、資料量多寡等影響訊號接收效能,這些情況容易造成無線傳輸的品質低落,遇到此情況有以下建議:
更換無線路由器(AP)位置:讓無線路由器(AP)與網路卡之間不要有太多障礙物。
天線調整:先確認天線位置,看看周圍是否有物品擋住訊號,若有則將天線調整至無線路由器(AP)與網卡相互能接收的位置,需注意天線有分全向性天線和指向性天線,一般無線分享器都以全向性天線為主,若調整後訊號接收能力並未改變,那麼可更換天線和外加天線來改善。
更換天線(外加天線):訊號距離可以藉由更換天線的方式來延長訊號的傳輸距離(更換目的是增加訊號傳輸的距離,與外加天線類似,實際上是以原本的銜接天線位置做更換)。要注意的是,更換天線只能增加傳輸距離,無法加強穿透力。 全向性天線:不需要指定天線方向位置,水平訊號 360 度發射,涵蓋範圍廣但是傳輸距離短。 指向性天線:需要指定一個方向,水平訊號發射角度約 10~30 度,涵蓋範圍窄但是傳輸距離長。
增加無線路由器(AP):如果連線兩點之間距離過長或者樓層與樓層之間有所阻隔,可以增加 AP 來延長距離使訊號延長,但是還是需要注意���與樓之間的材質。
(3). 無線路由器與網路卡之間介質的影響
在不同介質影響的情況下,訊號穿透能力的衰減情形。在金屬部份幾乎完全阻隔了訊號的傳輸,因此在無線環境的配置上,盡量讓無線路由器(AP)與網路卡之間不要有間隔阻擋,如此無線傳輸才能更加順暢。
Wi-Fi 種類
在規劃無線網路前,首先了解一下無線路由器使用的無線網路晶片種類,亦即 Wi-Fi 的種類。
(1). Wi-Fi 分為五代
Wi-Fi 可分為五代。由於 ISM 頻段中的 2.4GHz 頻段被廣泛使用,例如微波爐、藍牙,它們會干擾 WiFi,令速度減慢,5GHz 干擾則較小。雙頻路由器可同時使用 2.4GHz 和 5GHz,但裝置(電腦、平板、手機)則只能使用某一個頻段。
第一代 802.11,1997 年制定,只使用 2.4GHz,最快 2Mbit/s,已淘汰
第二代 802.11b,只使用 2.4GHz,最快 11Mbit/s,正逐漸淘汰
第三代 802.11g/a,分別使用 2.4GHz 和 5GHz,最快 54Mbit/s
第四代 802.11n,可使用 2.4GHz 或 5GHz,20 和 40MHz頻寬下最快 72 和 150Mbit/s
第五代 802.11ac,只使用 5GHz
因第一代與第二代已淘汰,我們從第三代開始介紹。
(2). 第三代 802.11g/a
802.11g 標準,全稱為 IEEE 802.11g-2003 是對 802.11 原始標準實體層上的一個修訂。802.11g 工作在 2.4G 信道上,實體層速率提升至 54Mbps。該規範已在世界上得到了廣泛的應用。相關的修改已經整合進 IEEE 802.11-2007 和後續版本,成為 802.11 協定的一部分。
801.11g 工作在 2.4G 的 ISM 頻段上,實體層上使用了正交頻分復用(OFDM)調變方式,不同於 802.11 原始標準和 802.11b 標準,而與 802.11a 標準相同,使得最大速率達到 54Mbps。在介質存取控制上,標準採用載波偵聽多路存取/衝突避免(CSMA/CA)的方式,這與其他標準相同。考慮到 CSMA/CA 協定的開銷,802.11g 裝置間的最大吞吐量可以達到 31.4Mbps。由於微波爐,藍牙裝置,ZigBee 等產品都工作在 ISM 頻段上,802.11g 裝置可能會受到其他裝置的干擾。
由於市場上對高速率的無線傳輸的需求,在 2003 年 1 月,雖然 802.11g 標準還未正式發布,11g 的裝置就大規模的部署了。802.11g 的裝置回溯相容 801.11b 網路。然而 11b 裝置會拖慢整個 11g 網路的吞吐量。
(3). 第四代 802.11n
IEEE 802.11n-2009,對於 IEEE 802.11-2007 無線區域網路標準的修正規格。它的目標在於改善先前的兩項無線網路標準,包括 802.11a 與 802.11g,在網路流量上的不足。它的最大���輸速度理論值為 600Mbit/s,與先前的 54Mbit/s 相比有大幅提升,傳輸距離也會增加。2004 年 1 月時 IEEE 宣布組成一個新的單位來發展的新的 802.11 標準,於 2009 年 9 月正式批准。
對 802.11n 的後續研究正在 IEEE 802.11ac 草案中進行,預計可以於 2014 年 2 月正式發布,將提供 8xMIMO,最高 160MHz 頻寬和最高 866.7Mbit/s 的理論速度。
2.4GHz 和 5GHz 都可自由選擇 20MHz 或 40MHz 頻寬,但一些裝置只允許在 5GHz 下使用 40MHz 頻寬,例如 MacBook。如果用家購買一台只支援 2.4GHz 的 150Mbps 路由器,就只能使到 72Mbps,即是 20MHz 頻寬下的最快速度。
(4). 第五代 802.11ac
IEEE 802.11ac,俗稱 5G WiFi (5th Generation of Wi-Fi),是一個 802.11 無線區域網路(WLAN)通訊標準,它透過 5GHz 頻帶進行通訊。理論上,它能夠提供最少 1Gbps 頻寬進行多站式無線區域網通訊,或是最少 500Mbps 的單一連線傳輸頻寬。
2008 年年底,IEEE 802 標準組織成立新小組,目的是在於建立新標準來改善 802.11-2007 標準。包括建立提高無線傳輸的速度的標準,使無線網路的能夠提供與有線網路相當的傳輸效能。
802.11ac 是 802.11n 的繼承者。它採用並擴展了源自 802.11n 的空中介面(air interface)概念,包括:更寬的 RF 頻寬(提升至160MHz),更多的MIMO空間串流(spatial streams)(增加到 8),下行多使用者的 MIMO (最多至4個),以及高密度的調變(modulation)(達到 256QAM)。
協定頻率(GHz)頻寬(MHz)每條流的速率(Mbit/s)MIMO 支援 802.11b2.4201, 2, 5.5, 11N/A 802.11g2.4206, 9, 12, 18, 24, 36, 48, 54N/A 802.11n2.4/5207.2, 14.4, 21.7, 28.9, 43.3, 57.8, 65, 72.24 4015, 30, 45, 60, 90, 120, 135, 150 802.11ac520最大 87.68 40最大 200 80最大 433.3 160最大 866.7
無線網路規畫要領
以下是建議的無線網路規劃要領。
(1). 天線的角度
無線網路訊號的發射範圍與天線垂直,一般單樓層的家庭就把天線垂直於地平面,住在透天厝就可以把天線平行於地平面放置,以便將無線訊號涵蓋到其他樓層。
(2). 使用 dBi 值較高的天線
理想的天線是朝四面八方發射訊號時,與天線相同距離的點所收到的訊號強度應相同,這就是理想天線,可惜目前的技術無法製造出這種天線。
另一常用的天線是偶極天線,偶極天線和理想天線相比,會有相同距離不同位置,所量��到訊號強度不同的狀況發生,某些地方量到的信號強度會比理想天線高,某些地方較低。所以依據偶極天線訊號最強的腹部與理想天線相比,發現偶極天線的訊號強度比理想天線強了 1.6倍,經轉換為 2.15dBi(i 指的是與理想天線相比較);也就是說一個偶極天線擁有的增益(gain)為 2.15dBi。
高 dBi 值的天線能夠加大訊號範圍,dBi 愈高效果愈好。如果你使用的無線路由器天線效果不佳,建議您可以更換較高的 dBi 值天線試試。
(3). 多台路由器使用時,頻道互相錯開
2.462GHz 共 11 個頻道,其中每個頻道約相差5MHz。在頻譜屏蔽標準來說,雖然有規定 ±22MHz 的能量限制,也就是傳遞的訊號隨著頻段不同跟著減弱,但多少還是會互相干擾。因此連線要好的話,盡量在 11 個頻道中最好都能互相錯開,選擇頻道 1、6、11 這 3 個會較好。
(4). 關閉 QoS 過濾機制
開啟 QoS 過濾機制會影響無線路由器的效能,造成路由器單位時間能傳輸的封包數降低,如果您有多台電腦、平板或行動裝置使用無線網路,建議關閉 QoS 過濾功能,或使用效能更高(更厲害的晶片)的路由器(價位更高)。
(5). 使用 5GHz 頻段
這個觀點其實很有趣,理論上是不會快,但實測偏偏就是會,與一般認知相反。原因在於家用無線路由器太便宜了,隨便開啟 Wi-Fi 功能一掃,跑出來一堆無線基地台,造成 2.4GHz 頻段壅塞。802.11n 可在 5GHz 頻段運作,由於 5GHz 的無線路由器較貴、較不普及,因此比較不壅塞,但前提是其它無線網路設備(電腦、平板、手機)也必須支援 5GHz 運作才行。
(6). 不要放在弱電箱
市面上的弱電箱大部分都是金屬製品,將無線路由器放入弱電箱會降低效能,因金屬會干擾無線訊號。如果您無法阻止無線路由器放入弱電箱,至少將天線延伸至弱電箱外。
文章出處:https://ilearning.ojos.cc/LearningHub/TECH_wp_wifi.php
1 note
·
View note
Text

Difference between CSMA CA and CSMA CD . . . . for more information https://bit.ly/42mBLPA check the above link
#csmacd#csmaca#switch#router#BluesnarfingAttack#wireless#https#http#smtp#ftp#protocol#networking#network#computerscince#computerengineering#javatpoint
0 notes
Text
Basic Understanding of Wi-Fi Protocol
Wi-Fi Protocol
Hi everyone! In this blog post, I’m going to share with you some basics of Wi-Fi protocol, the technology that enables wireless communication between devices. Wi-Fi protocol is based on the IEEE 802.11 standard, which defines how devices can transmit and receive data over radio waves. Wi-Fi protocol consists of several layers, each with a specific function and format. The main layers are:
Physical layer: This layer deals with the modulation and encoding of the radio signals, as well as the frequency and channel selection. There are different types of physical layer, such as OFDM, DSSS, and FHSS, depending on the speed and range of the Wi-Fi network. - MAC layer: This layer handles the access and control of the medium, as well as the error detection and correction. It uses a technique called CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) to avoid collisions and ensure fair sharing of the channel among multiple devices. It also uses ACK (Acknowledgement) frames to confirm the successful reception of data frames. - LLC layer: This layer provides a logical link between the MAC layer and the upper layers, such as IP and TCP. It adds a header to the MAC frame that contains information such as the source and destination addresses, the type of data, and the sequence number.
If you are interested to understand more about the Wi-Fi Protocol, then you can go through the PiEmbSysTech Wi-Fi Protocol Tutorial Blog. If you have any questions or query, that you need to get answer or you have any idea to share it with the community, you can use Piest Forum.
Wi-Fi protocol is a complex and fascinating topic that enables us to enjoy wireless connectivity in our homes, offices, and public places. I hope this blog post gave you a brief overview of how it works. If you want to learn more, you can check out some of the references below. Thanks for reading!
0 notes
Text
Wifi HaLoW Devices Market - Forecast (2022 - 2027)
WI-FIHaLow Devices market size was valued at 5.6 million units in 2020 and it is estimated to grow at a CAGR of 12.6% during 2021-2026. The growth can be attributed to the adoption of Wi-Fi HaLow devices across various industries due to its ability to offer long range connectivity at low cost, low power consumption, and avail high data speed as compared to others. Furthermore, its ability to provide network in dead zones, better battery life, higher scalability, simple installation process are the main market drivers. Wi-fi HaLow technology’s ability to penetrate through walls, buildings or other barriers is also considered as an important factor contributing to the market growth. This technology supports a carrier-sense multiple access with collision avoidance (CSMA/CA) which acts to prevent collision before it occurs. This in turn, increases the adoption rate of this technology. In addition, it also supports machine to machine communication, various types of adaptive coding and modulation (ACM) schemes that are progressively being used to increase the network capacity or downlink data rates. This is a major contributing factor to the market growth.

Report Coverage
The report: “Wi-Fi HaLow Devices Market Forecast (2021-2026)”, by IndustryARC, covers an in-depth analysis of the following segments of the Wi-Fi HaLow Devices Market.
By device type: Transceiver, Chipsets, Modules, and others.
By application: Industrial sensor network systems, smart security surveillance, building automation, smart agriculture, connected vehicles, home automation, digital healthcare system, industrial automation and others.
By end user industry : power, oil & gas, automotive, healthcare, mining, agriculture, waste water & treatment, transportation & logistics, electronics & semiconductors, metal processing, general manufacturing, paper & pulp, Construction and others.
By geography: North America (US, Canada, Mexico),Europe (Germany, France, UK, Italy, Spain, Rest of Europe), APAC (Japan, China, India, Australia, South Korea, rest of APAC), South America (Brazil, Argentina, rest of South America), and RoW (Africa, Middle East)
Request Sample
Key Takeaways
Agriculture sector is analyzed to grow with a significant pace during the forecast period, owing to increasing demand for IoT, connected devices and digital platforms in agricultural sector.
By device type, chipsets market is estimated to witness the fastest growth, owing to the rising investments and collaboration among the organizations.
North America dominated the Wi-Fi HaLow Devices market in terms of value in 2020 owing to its technological advancement and having the ideal operating ISM band.
The market's ability to provide network coverage to dead zones works as a growth driver.
Wi-Fi HaLow industry outlook is consolidated with the top market players including NEWRACOM Inc., AdvanWISE, Morse Micro Pty. Ltd., Methods2Busines B.V., Silex Technology and many others.
By device type, this market is segmented into Transceiver, Chipsets, Modules, and others. Wi-Fi HaLow chipsets market is analyzed to grow with the fastest CAGR of 15.5%
during the forecast period. Organizations are collaborating and investing heavily for the development of this market. In June 2019, NEWRACOM had collaborated with Fortune tech system in order to provide world’s first miniaturized HaLow solution built on Raspberry Pi 3. This product is highly integral and equipped with NEWRACOM’S 802.11ah WI-FI-SoC. This solution can be used in various IoT applications such as smart home, smart office, smart industry, smart city, healthcare sectors, smart grid, security systems, smart controllers, smart motors and others. In March 2021, LitePoint collaborated with Morse Micro to accelerate the connectivity of Wi-Fi HaLow. LitePoint IQxel-MWTM also validates the performance of the Morse Micro System-on-Chip family. These types of collaborations will drive the WiFi HaLow module market in the forecast period 2021-2026.
Inquiry Before Buying
WI-FI HaLow Devices Market Segment Analysis- By Device Type
By device type, this market is segmented into Transceiver, Chipsets, Modules, and others. Wi-Fi HaLow chipsets market is analyzed to grow with the fastest CAGR of 15.5% during the forecast period. Organizations are collaborating and investing heavily for the development of this market. In June 2019, NEWRACOM had collaborated with Fortune tech system in order to provide world’s first miniaturized HaLow solution built on Raspberry Pi 3. This product is highly integral and equipped with NEWRACOM’S 802.11ah WI-FI-SoC. This solution can be used in various IoT applications such as smart home, smart office, smart industry, smart city, healthcare sectors, smart grid, security systems, smart controllers, smart motors and others. In March 2021, LitePoint collaborated with Morse Micro to accelerate the connectivity of Wi-Fi HaLow. LitePoint IQxel-MWTM also validates the performance of the Morse Micro System-on-Chip family. These types of collaborations will drive the WiFi HaLow module market in the forecast period 2021-2026.
WI-FI HaLow Devices Market Segment Analysis- By End-User Industry
The WI-FI HaLow market is segmented into power, oil & gas, automotive, healthcare, mining, agriculture, waste water & treatment, transportation & logistics, electronics & semiconductors, metal processing, general manufacturing, paper & pulp, Construction and others, based on the end-used industry. Healthcare WI-FI HaLow device Market is estimated to witness a highest growth CAGR 18.1% during forecast period 2021-2026 owing to its ability to provide real time information about a patient’s health condition and their location. The demand for reliable communication system and a quick access to patient’s medical record facilitates the adoption of IoT in this sector. Thereby, increases the demand for WI-FI HaLow. These features make HaLow devices ideal for healthcare sector in which getting real time information is a pertinent feature. The current Covid-19 pandemic has accelerated the growth in demand for digital health care services such as smart monitoring, tele-health services, tele-medicine services, personal fitness wearable devices, elderly monitoring and others, which in-fact created various new growth avenues for Wi-Fi HaLow based devices. The above mentioned factors will play a major role in the market growth.
WI-FI HaLow Devices Market Segment Analysis- By Geography
North America dominated the Wi-Fi HaLow Devices market in 2020 with a share close to 38%, and is estimated that the market of this region is also going to witness highest growth during the forecast period. WI-FI HaLow has different radio spectrum allocation for different countries. The band ranges for different countries are 902-928MHz in U.S., 863-868 MHz in Europe, 717-723 MHz in Korea, 755-787 MHz in China and many countries do not even have an operating frequency spectrum. The only operating ISM band for HaLow product is 900 MHz, which makes HaLow a U.S. centric product which drives the North American market.
Schedule a Call
WI-FI HaLow Devices Market Drivers
Network Connectivity:
Wi-Fi HaLow builds on spectral efficient orthogonal frequency-division multiplexing (OFDM) foundations and operates in frequency bands below one gigahertz due to which, it can offer a prolonged use, as it consumes less power and connectivity to Wi-Fi products. These features make HaLow devices ideal for short and burst data which is particularly used for IoT applications. Apart from this, it can provide network connectivity even to those places where the cellular networks or the traditional Wi-Fi connectivity can’t reach such as dead zones, subways, hilly areas, typical rural areas, deep inside the buildings and others which makes HaLow ideal for smart home, digital health care services, connected cars, smart city as well as industrial application. It also uses direct-sequence spread spectrum (DSSS), that effectively helps this technology to avoid intentional interference such as jamming and performs better than FHSS in the presence of noise that makes it perfectly suitable for security related applications.
Increasing Investment and Development in WI-FI HaLoW:
The investment in WI-FI HaLow is anticipated to grow rapidly due to the tremendous level of development and innovation scope for this technology. In November 2020, Australia based company, Morse Micro had secured additional $13 million fund to accelerate WIFI HaLow development. In November 2020, Scenestek came up with the first skyline technology based Wi-Fi HaLow security camera with 1000 foot range. It can easily penetrate through walls, buildings and the installation process is super easy. It is said that the world wide shipping will start from April or May 2021. Recent developments and increasing investment in Wi-Fi HaLow are working as growth drivers for this market.
Buy Now
Wi-FiHaLow Devices Market Challenges
Availability of beneficial alternatives:
The launch of the 802.11ax alongside the launch of Wi-Fi HaLow had a distinct adverse effect on the market of Wi-Fi HaLow. 802.11ax solutions that were more in demand than 802.11ah or HaLow solutions because unlike HaLow, it had a standard frequency spectrum which makes them cost effective. Similarly, there has been a perceptible increase in the demand and the investment for 5g and LTE IoT products, leaving almost no resources for HaLow market to grow which is a major market challenge for WI-FI HaLow.
WI-FI HaLow Devices Market Landscape
Technology launches, Acquisitions, Collaboration, and R&D activities are key strategies adopted by players in the Wi-FiHaLow Devicesmarket. Top Wi-Fi HaLow Devices companies include NEWRACOM Inc., AdvanWISE, Morse Micro Pty. Ltd., Methods2Busines B.V., Silex Technology, Palma CeiaSemiDesign, Inc., Scenestek technology, Adapt-IP and others.
Acquisitions/Technology Launches
In February 2020, Silex technology collaborated with Newracom and launched industries first WIFI HaLow module, SX-NEWAH. Powered by NEWRACOM's NRC7292 system on a chip, SX-NEWAH operates in the Sub 1 GHz licensed band and enables 1 km+ long connectivity range while maintaining the low power requirement.
In August 2019, Adapt-IP had announced the availability of their newly developed platform for WI-FI HaLow Development. This is available for the integrators and developers of IoT market. This platform supports the IEEE 802.11ah standards and offers a hardware and software environment for development.
For more Electronics related reports, please click here
#WI-FI#WI-FI HaLow Devices Market#WI-FI HaLow Devices Market share#WI-FI HaLow Devices Market trends#WI-FI HaLow Devices Market size#WI-FI HaLow Devices Market analysis
1 note
·
View note
Text
Section B1 Assignment #6 Solution
Section B1 Assignment #6 Solution
1. Give Manchester code for the following data. (4 point) (16 points) Consider a wireless LAN consisting of one access point and three stations: Stations A, B, and C. All the stations can hear each other. Each station has one and only one DATA frame to be sent to the access point. The access point does not have DATA frame to be sent. Distributed coordination function, which is based on CSMA-CA,…

View On WordPress
0 notes
Text
ECE Section B1 Assignment #6 Solution
ECE Section B1 Assignment #6 Solution
1. Give Manchester code for the following data. (4 point) (16 points) Consider a wireless LAN consisting of one access point and three stations: Stations A, B, and C. All the stations can hear each other. Each station has one and only one DATA frame to be sent to the access point. The access point does not have DATA frame to be sent. Distributed coordination function, which is based on CSMA-CA,…

View On WordPress
0 notes
Text
Topology
Topology :
Topology defines the structure of the network of how all the components are interconnected to each other. There are two types of topology: physical and logical topology.
Physical topology is the geometric representation of all the nodes in a network.
Bus Topology
The bus topology is designed in such a way that all the stations are connected through a single cable known as a backbone cable.
Each node is either connected to the backbone cable by drop cable or directly connected to the backbone cable.
When a node wants to send a message over the network, it puts a message over the network. All the stations available in the network will receive the message whether it has been addressed or not.
The bus topology is mainly used in 802.3 (ethernet) and 802.4 standard networks.
The configuration of a bus topology is quite simpler as compared to other topologies.
The backbone cable is considered as a "single lane" through which the message is broadcast to all the stations.
The most common access method of the bus topologies is CSMA (Carrier Sense Multiple Access).
CSMA: It is a media access control used to control the data flow so that data integrity is maintained, i.e., the packets do not get lost. There are two alternative ways of handling the problems that occur when two nodes send the messages simultaneously.
CSMA CD: CSMA CD (Collision detection) is an access method used to detect the collision. Once the collision is detected, the sender will stop transmitting the data. Therefore, it works on "recovery after the collision".
CSMA CA: CSMA CA (Collision Avoidance) is an access method used to avoid the collision by checking whether the transmission media is busy or not. If busy, then the sender waits until the media becomes idle. This technique effectively reduces the possibility of the collision. It does not work on "recovery after the collision".
Advantages of Bus topology:
Low-cost cable: In bus topology, nodes are directly connected to the cable without passing through a hub. Therefore, the initial cost of installation is low.
Moderate data speeds: Coaxial or twisted pair cables are mainly used in bus-based networks that support upto 10 Mbps.
Familiar technology: Bus topology is a familiar technology as the installation and troubleshooting techniques are well known, and hardware components are easily available.
Limited failure: A failure in one node will not have any effect on other nodes.
Disadvantages of Bus topology:
Extensive cabling: A bus topology is quite simpler, but still it requires a lot of cabling.
Difficult troubleshooting: It requires specialized test equipment to determine the cable faults. If any fault occurs in the cable, then it would disrupt the communication for all the nodes.
Signal interference: If two nodes send the messages simultaneously, then the signals of both the nodes collide with each other.
Reconfiguration difficult: Adding new devices to the network would slow down the network.
Attenuation: Attenuation is a loss of signal leads to communication issues. Repeaters are used to regenerate the signal.
Ring Topology
Token passing: It is a network access method in which token is passed from one node to another node.
Token: It is a frame that circulates around the network.
Working of Token passing
A token moves around the network, and it is passed from computer to computer until it reaches the destination.
The sender modifies the token by putting the address along with the data.
The data is passed from one device to another device until the destination address matches. Once the token received by the destination device, then it sends the acknowledgment to the sender.
In a ring topology, a token is used as a carrier.
Advantages of Ring topology:
Network Management: Faulty devices can be removed from the network without bringing the network down.
Product availability: Many hardware and software tools for network operation and monitoring are available.
Cost: Twisted pair cabling is inexpensive and easily available. Therefore, the installation cost is very low.
Reliable: It is a more reliable network because the communication system is not dependent on the single host computer.
Disadvantages of Ring topology:
Read More
Difficult troubleshooting: It requires specialized test equipment to determine the cable faults. If any fault occurs in the cable, then it would disrupt the communication for all the nodes.
Failure: The breakdown in one station leads to the failure of the overall network.
Reconfiguration difficult: Adding new devices to the network would slow down the network.
Delay: Communication delay is directly proportional to the number of nodes. Adding new devices increases the communication delay.
Star Topology
Star topology is an arrangement of the network in which every node is connected to the central hub, switch or a central computer.
The central computer is known as a server, and the peripheral devices attached to the server are known as clients.
Coaxial cable or RJ-45 cables are used to connect the computers.
Hubs or Switches are mainly used as connection devices in a physical star topology.
Star topology is the most popular topology in network implementation.
Advantages of Star topology
Efficient troubleshooting: Troubleshooting is quite efficient in a star topology as compared to bus topology. In a bus topology, the manager has to inspect the kilometers of cable. In a star topology, all the stations are connected to the centralized network. Therefore, the network administrator has to go to the single station to troubleshoot the problem.
Network control: Complex network control features can be easily implemented in the star topology. Any changes made in the star topology are automatically accommodated.
Limited failure: As each station is connected to the central hub with its own cable, therefore failure in one cable will not affect the entire network.
Read More
Familiar technology: Star topology is a familiar technology as its tools are cost-effective.
Easily expandable: It is easily expandable as new stations can be added to the open ports on the hub.
Cost effective: Star topology networks are cost-effective as it uses inexpensive coaxial cable.
High data speeds: It supports a bandwidth of approx 100Mbps. Ethernet 100BaseT is one of the most popular Star topology networks.
Disadvantages of Star topology
A Central point of failure: If the central hub or switch goes down, then all the connected nodes will not be able to communicate with each other.
Cable: Sometimes cable routing becomes difficult when a significant amount of routing is required.
Tree topology
Tree topology combines the characteristics of bus topology and star topology.
A tree topology is a type of structure in which all the computers are connected with each other in hierarchical fashion.
The top-most node in tree topology is known as a root node, and all other nodes are the descendants of the root node.
There is only one path exists between two nodes for the data transmission. Thus, it forms a parent-child hierarchy.
Advantages of Tree topology
Support for broadband transmission: Tree topology is mainly used to provide broadband transmission, i.e., signals are sent over long distances without being attenuated.
Easily expandable: We can add the new device to the existing network. Therefore, we can say that tree topology is easily expandable.
Easily manageable: In tree topology, the whole network is divided into segments known as star networks which can be easily managed and maintained.
Error detection: Error detection and error correction are very easy in a tree topology.
Limited failure: The breakdown in one station does not affect the entire network.
Read More
Point-to-point wiring: It has point-to-point wiring for individual segments.
Disadvantages of Tree topology
Difficult troubleshooting: If any fault occurs in the node, then it becomes difficult to troubleshoot the problem.
High cost: Devices required for broadband transmission are very costly.
Failure: A tree topology mainly relies on main bus cable and failure in main bus cable will damage the overall network.
Reconfiguration difficult: If new devices are added, then it becomes difficult to reconfigure.
Mesh topology
Mesh technology is an arrangement of the network in which computers are interconnected with each other through various redundant connections.
There are multiple paths from one computer to another computer.
It does not contain the switch, hub or any central computer which acts as a central point of communication.
The Internet is an example of the mesh topology.
Mesh topology is mainly used for WAN implementations where communication failures are a critical concern.
Mesh topology is mainly used for wireless networks.
Mesh topology can be formed by using the formula: Number of cables = (n*(n-1))/2;
Where n is the number of nodes that represents the network.
Mesh topology is divided into two categories:
Fully connected mesh topology
Partially connected mesh topology
Full Mesh Topology: In a full mesh topology, each computer is connected to all the computers available in the network.
Partial Mesh Topology: In a partial mesh topology, not all but certain computers are connected to those computers with which they communicate frequently.
Advantages of Mesh topology:
Reliable: The mesh topology networks are very reliable as if any link breakdown will not affect the communication between connected computers.
Fast Communication: Communication is very fast between the nodes.
Easier Reconfiguration: Adding new devices would not disrupt the communication between other devices.
Disadvantages of Mesh topology
Cost: A mesh topology contains a large number of connected devices such as a router and more transmission media than other topologies.
Management: Mesh topology networks are very large and very difficult to maintain and manage. If the network is not monitored carefully, then the communication link failure goes undetected.
Efficiency: In this topology, redundant connections are high that reduces the efficiency of the network.
Hybrid Topology
The combination of various different topologies is known as Hybrid topology.
A Hybrid topology is a connection between different links and nodes to transfer the data.
When two or more different topologies are combined together is termed as Hybrid topology and if similar topologies are connected with each other will not result in Hybrid topology. For example, if there exist a ring topology in one branch of ICICI bank and bus topology in another branch of ICICI bank, connecting these two topologies will result in Hybrid topology.
Advantages of Hybrid Topology
Reliable: If a fault occurs in any part of the network will not affect the functioning of the rest of the network.
Scalable: Size of the network can be easily expanded by adding new devices without affecting the functionality of the existing network.
Flexible: This topology is very flexible as it can be designed according to the requirements of the organization.
Read More
Effective: Hybrid topology is very effective as it can be designed in such a way that the strength of the network is maximized and weakness of the network is minimized.
Disadvantages of Hybrid topology
Complex design: The major drawback of the Hybrid topology is the design of the Hybrid network. It is very difficult to design the architecture of the Hybrid network.
Costly Hub: The Hubs used in the Hybrid topology are very expensive as these hubs are different from usual Hubs used in other topologies.
Costly infrastructure: The infrastructure cost is very high as a hybrid network requires a lot of cabling, network devices, etc.
#topology#exlpain topology#what is topology#types of topology#benifits of topology#advantages of topology#disadvantages of topology#features of topology#tree topology#hybrid topology#ring topology#bus topology#mesh topology#star topology
1 note
·
View note
Text
สิ่งที่ควรมองหาในจุดเชื่อมต่อไร้สาย
เครือข่ายไร้สายเป็นหนึ่งในเทคโนโลยีที่ปฏิวัติระบบเครือข่ายข้อมูล ทั้งสำหรับผู้ใช้ตามบ้านและเครือข่ายธุรกิจ เครือข่ายไร้สายในบ้านทำให้เราเคลื่อนที่ได้ เพื่อไม่ให้เราเชื่อมโยงกับตำแหน่งเดียวภายในบ้าน เราเตอร์ไร้สายสมัยใหม่มีจุดเชื่อมต่อไร้สายในตัว และมักจะให้ความยืดหยุ่นในการอนุญาตการเชื่อมต่อทั้งแบบมีสายและไร้สาย
เราควรมองหาอะไรเมื่อเลือกจุดเชื่อมต่อไร้สาย? มีหลายรุ่นให้เลือก โดยมีโปรโตคอลและมาตรฐานรองรับที่หลากหลาย พวกเขายังมาในช่วงราคากว้างขึ้นอยู่กับเครือข่ายที่พวกเขาออกแบบมาเพื่อรองรับ ก่อนที่จะมีการเปิดตัว Wireless Access Points เครือข่ายไร้สายในยุคแรกๆ จะถูกเรียกว่าเครือข่าย Ad Hoc เนื่องจากมีอุปกรณ์ที่เปิดใช้งานไร้สายสองเครื่องหรือมากกว่าสื่อสารกันเมื่อทั้งสองอยู่ในระยะ เหมือนกับเครือข่าย Bluetooth เครือข่าย Ad Hoc นั้นใช้ได้เมื่อมีธีมทั่วไป เช่น เกม แต่ไม่เหมาะสำหรับการเชื่อมต่ออินเทอร์เน็ตทั่วไปโดยเฉพาะ เครือข่ายไร้สายที่ใช้จุดเชื่อมต่อไร้สายมีข้อดีที่แตกต่างกันหลายประการ เช่น ความง่ายในการรักษาความปลอดภัยด้วยโปรโตคอลความปลอดภัยที่เหมาะสม และข้อดีอีกประการหนึ่งคือความสามารถในการมีจุดเข้าใช้งานหลายจุดที่รองรับ WLAN หลายตัวที่เชื่อมต่อกับ Local Area แบบมีสายเดียวกันทั้งหมด เครือข่าย. UniFi Layer 2 Switch ราคา
จุดเชื่อมต่อไร้สายมีแอพพลิเคชั่นที่หลากหลายในปัจจุบัน และช่วงเหล่านี้มีตั้งแต่การเข้าถึงระบบไร้สายไปยัง LAN ขององค์กร และเมื่อใช้จุดเชื่อมต่อหลายจุด การโรมมิ่งก็เป็นไปได้ โดยปกติแล้ว WLAN Controller จะใช้เพื่อจัดการกลุ่มของ AP ภายในสภาพแวดล้อม LAN Wireless Access Points บางจุดใช้เพื่อให้ประชาชนสามารถเชื่อมต่ออินเทอร์เน็ตได้ เช่น ในโรงแรม ร้านกาแฟ และแม้แต่ซูเปอร์มาร์เก็ต ควรใช้เครือข่ายไร้สายสาธารณะเหล่านี้เพื่อให้มีความปลอดภัยที่ดีบนพีซีของคุณ เนื่องจากความปลอดภัยไม่ใช่คุณสมบัติที่ยอดเยี่ยมของแอปพลิเคชันเหล่านี้ จุดเชื่อมต่อที่ใช้ในลักษณะนี้มักเรียกว่าฮอตสปอตไร้สาย
มาตรฐานไร้สายทั่วไปคือมาตรฐาน IEEE 802.11 ซึ่งมี 3 หมวดหมู่หลักคือ 802.11a, 802.11b และ 802.11b มาตรฐาน IEEE 802.11a ได้รับการออกแบบให้ทำงานภายในย่านความถี่ไร้สาย 5Ghz UNII ในขณะที่มาตรฐาน IEEE 802.11b และ g ทำงานภายในย่านความถี่ ISM 2.4Ghz มาตรฐาน IEEE 802.11g สามารถให้ความเร็วสูงสุด 54Mbps และเข้ากันได้กับมาตรฐาน IEEE 802.11b รุ่นเก่า ด้วยเสาอากาศที่หลากหลายซึ่งรองรับมาตรฐาน IEEE 802.11n จึงสามารถ���รรลุความเร็วสูงสุด 300Mbps อย่าปล่อยให้ความเร็วเหล่านี้หลอกคุณ เนื่องจากแบนด์วิดท์จำนวนมากถูกใช้โดยค่าใช้จ่ายที่ซับซ้อนซึ่งเชื่อมโยงกับเครือข่ายเหล่านี้ โดยทั่วไปแล้ว การเชื่อมต่อ 54Mbps จะให้อัตราความเร็ว TCP/IP แก่คุณที่สูงสุด 25Mbps U6-Lite ราคา
การพิจารณาที่สำคัญมากเมื่อปรับใช้ WAP คือการรักษาความปลอดภัยในรูปแบบของการรับรองความถูกต้องเพื่อให้แน่ใจว่ามีเพียงอุปกรณ์ไคลเอนต์ที่เชื่อถือได้เท่านั้นที่เชื่อมโยงกับจุดเชื่อมต่อและการเข้ารหัสเพื่อให้แน่ใจว่าข้อมูลใด ๆ ที่คุณส่งผ่านสภาพแวดล้อมวิทยุนั้นปลอดภัยจากการดักฟัง อุปกรณ์ไคลเอนต์ทั้งหมดใช้สภาพแวดล้อมไร้สายร่วมกันและสามารถเข้าถึงเครือข่ายนั้นผ่านการใช้ CSMA/CA (Carrier Sensed Multiple Access พร้อมการหลีกเลี่ยงการชน) เครื่องลูกข่ายไร้สายใดๆ ภายในระยะสัญญาณวิทยุจะสามารถตรวจพบจุดเชื่อมต่อไร้สายและอาจพยายามเชื่อมโยงกับจุดเชื่อมต่อ เมื่อใช้วิธีการรักษาความปลอดภัยที่ถูกต้อง เฉพาะไคลเอ็นต์ที่มีข้อมูลรับรองการตรวจสอบสิทธิ์ที่ถูกต้องเท่านั้นที่จะสามารถเชื่อมโยงและเข้าถึงช่องสัญญาณวิทยุได้
เมื่อเลือกจุดเชื่อมต่อไร้สาย ให้ตรวจสอบคุณสมบัติความปลอดภัยที่ได้รับการสนับสนุน วิธีการที่มีความปลอดภัยน้อยกว่าแบบเก่า ได้แก่ WEP (Wired Equivalent Privacy) ที่มีคีย์การเข้ารหัสแบบ 64 หรือ 128 บิตตามปกติ วิธีการเหล่านี้อาจถูกบุกรุกโดยบุคคลที่มีความรู้ อย่างน้อยคุณควรมองหาอุปกรณ์ที่รองรับ WPA (Wi-Fi Protected Access) หรือดีกว่านั้นคือมาตรฐาน WPA2 ขั้นสูง ในสภาพแวดล้อมขององค์กร WAP มักจะได้รับการปกป้องโดยมาตรฐาน IEEE 802.1x ซึ่งใช้เซิร์ฟเวอร์เพื่อตรวจสอบสิทธิ์ไคลเอนต์ก่อนที่จะได้รับอนุญาตให้เข้าถึง สวิตช์อีเทอร์เน็ตที่เชื่อมต่อกับจุดเชื่อมต่อจะท้าทายอุปกรณ์และส่งต่อข้อมูลที่ได้รับไปยังเซิร์ฟเวอร์เช่นเซิร์ฟเวอร์ RADIUS (Remote Access Dial In Use Service) ซึ่งจะแจ้งสวิตช์ว่าควรให้สิทธิ์การเข้าถึงหรือไม่ Unifi U6-Lite ราคา
ในการพิจารณาว่าคุณควรซื้อจุดเชื่อมต่อใด คุณต้องตัดสินใจก่อนว่าจะใช้ทำอะไร คุณต้องการปริมาณงานเท่าใดสำหรับแอปพลิเคชันของคุณ เครือข่าย 54Mbps จะเพียงพอหรือคุณอาจต้องการหรือจำเป็นต้องมีมาตรฐาน IEEE 802.11n ที่ทำงานที่ 300Mbps จุดเชื่อมต่อไร้สายจำเป็นต้องติดตั้งบนผนังหรือเพดาน หรือต้องติดตั้งไว้บนเด��ก์ท็อปเท่านั้น เสาอากาศที่มีอยู่จะให้เกนที่เพียงพอสำหรับความต้องการของคุณหรือไม่ หรือจำเป็นต้องถอดเสาอากาศออกเพื่อให้สามารถใช้เสาอากาศที่เหมาะสมกว่าได้ WAP จะเชื่อมต่อกับเครือข่ายแบบมีสายอย่างไรและที่ไหน และคุณต้องการความปลอดภัยระดับใด
0 notes
Text
Use the attached template to finish assignment. Understand Access Control Protoc
Use the attached template to finish assignment. Understand Access Control Protoc
Use the attached template to finish assignment. Understand Access Control Protocols: The two basic forms of medium access control protocols are CSMA/CD, which is found on star-wired bus local area networks, and CSMA/CA, which is found on wireless local area networks. Discuss the differences and similarities of these two protocols. Why would two be needed? Discuss why CSMA/CD would not be a good…
View On WordPress
0 notes
Text
Use the attached template to finish assignment. Understand Access Control Protoc
Use the attached template to finish assignment. Understand Access Control Protoc
Use the attached template to finish assignment. Understand Access Control Protocols: The two basic forms of medium access control protocols are CSMA/CD, which is found on star-wired bus local area networks, and CSMA/CA, which is found on wireless local area networks. Discuss the differences and similarities of these two protocols. Why would two be needed? Discuss why CSMA/CD would not be a good…
View On WordPress
0 notes