#cyber security workforce
Explore tagged Tumblr posts
Text
Olivia Troye at Olivia Of Troye Unfiltered:
While Trump's tariffs hammer the economy and dominate the headlines, rightfully capturing attention as Americans watch their 401ks drop, something perilous quietly unfolded in the shadows. A significant shift in the national security apparatus occurred that barely made a blip. It hardly registered in the mainstream news cycle late last week when General Timothy Haugh was ignominiously removed as dual-hatted Director of the National Security Agency (NSA) and Commander of U.S. Cyber Command. Perhaps in the chaos of Trump 2.0, another outstanding leader being ousted is just business as usual. For the ones that did mention it, they pointed out that the action could seriously hurt America’s cyber defenses and make it a lot easier for foreign adversaries to strike our networks. They’re correct. But let me be even clearer about what’s not being talked about: this is not just another reshuffling of power—it's a five-alarm fire for anyone who values their privacy and civil liberties. And it wasn't just Haugh who was shown the door. Wendy Noble, the highly respected civilian Deputy Director of the NSA, was also reassigned back to the Department of Defense. This wasn't just a firing but a purge of institutional memory, experience, and moral backbone. Tim Haugh wasn't just any flag officer. He was beloved by his workforce, respected by national security professionals across the political spectrum, and known as much for his integrity and superb leadership skills as for his mission expertise. Haugh's departure leaves a void in one of the most sensitive and consequential roles in government. Whoever fills that vacuum could alter the trajectory of one of our most fundamental American freedoms: the right to privacy.
A Role That Holds Enormous Power
By long-standing tradition, the NSA is led by a uniformed military officer, while the deputy is a civilian. That balance matters. It provides both continuity and civilian oversight of a powerful institution with the ability to monitor global communications—and, yes, potentially, American citizens. Tim Haugh upheld that legacy of integrity. Similarly, with her deep expertise and decades of experience, Wendy Noble brought the kind of institutional knowledge and civilian leadership that protected that balance. But now, with both Haugh and Noble removed in quick succession, we're in uncharted territory. The critical safeguards that these respected leaders maintained have been dismantled, and the Trump administration has shown us what it's capable of when unchecked power meets authoritarian instinct. [...]
Why You Should Care: FISA Section 702
One of the most potent surveillance tools in the national security toolbox is Section 702 of the Foreign Intelligence Surveillance Act (FISA). Section 702 allows the NSA and FBI to collect foreign intelligence by targeting non-U.S. persons outside the country. Sounds reasonable on paper. It's a powerful and necessary tool to protect national security—used to thwart terrorists, identify foreign cyber actors, and uncover threats to U.S. interests. But here's the catch: in the course of collecting this foreign data, U.S. persons' communications are often swept up. That's where the controversy begins. This is where procedures, leadership, and the integrity of institutions matter. As a former commander of multiple Air Force and joint intelligence organizations responsible for signals collection, Tim Haugh knew how to protect Americans’ privacy. Yet while 702 is designed to protect us, it can also be exploited to monitor Americans on U.S. soil. Without proper safeguards, it can become a backdoor to domestic surveillance. I've seen the inner workings of this system, and I can tell you that it works when principled leaders are at the helm. But in the wrong hands? It's terrifying.
Remember Trump's Obsession with Wiretaps? Let me remind you of a key moment in Trump's first term. He falsely accused President Obama of wiretapping Trump Tower. It was a baseless claim, thoroughly debunked—even his own Justice Department and the intelligence community found nothing. But Trump's tactic wasn't random. It was a classic projection. Because behind the scenes, while I was working in the White House, very real and deeply disturbing conversations were happening. Trump wanted the Department of Justice to authorize surveillance of personal devices of people he deemed political enemies or leakers. It wasn't paranoia; it was authoritarian yearning. And it was chilling. So when I see Tim Haugh forced out, Wendy Noble removed, Pam Bondi at the helm of the Department of Justice, and Kash Patel—who is currently the Director of the FBI—calling the shots, that's not just concerning. That's a massive, flashing red warning light for the nation. [...]
This Is Bigger Than One Leader
This isn't just about Tim Haugh or Wendy Noble. It's about a pattern of purging competent, principled leaders and replacing them with loyalists who will enthusiastically comply with any order or request, no matter how anathema to our democracy. It's about dismantling the apolitical fabric of our national security institutions. It's about the slow, quiet erosion of freedoms that most Americans assume are protected until they’re not.
The firing of Tim Haugh and the reassigning of Wendy Noble is a major red flag alert for national security.
#Gen. Tim Haugh#US Military#Trump Regime#National Security Agency#US Cyber Command#National Security#Wendy Noble#FISA#Section 702#Trump Tower#Wiretapping#Trump Tower Wiretapping#Kash Patel#Tulsi Gabbard
15 notes
·
View notes
Text
Much of the IT and cybersecurity infrastructure underpinning the US health system is in danger of a possible collapse following a purge of IT staff and leadership at the Department of Health and Human Services (HHS), four current and former agency workers tell WIRED. This could put vast troves of public health data, including the sensitive health records of hundreds of millions of Americans, clinical trial data, and more, at risk of exposure.
As a result of a reduction in force, or RIF, in the Office of the Chief Information Officer (OCIO), the sources say, staff who oversee and renew contracts for critical enterprise services are no longer there. The same staff oversaw hundreds of contractors, some of whom play a crucial role in keeping systems and data safe from cyberattacks. And a void of leadership means that efforts to draw attention to what the sources believe to be a looming catastrophe have allegedly been ignored.
Thousands of researchers, scientists, and doctors lost their jobs earlier this month at HHS agencies critical to ensuring America’s health, such as the Centers for Disease Control and and Prevention (CDC) and the Food and Drug Administration (FDA). Hundreds of administrative staff were also subjected to a reduction in force. Many of these staffers were responsible for helping ensure that the mass of highly personal and sensitive information these agencies collect is kept secure.
Employees who were subject to the RIF, as well as some who remain at the agency, tell WIRED that without intervention, they believe the systems they managed could go dark, potentially putting the entire health care system at risk.
“Pretty soon, within the next couple of weeks, everything regarding IT and cyber at the department will start to operationally reach a point of no return,” one source, who was part of a team that managed these systems at HHS for a decade before being part of the RIF, alleges to WIRED.
Like many across the agency, administrative staff found out they were part of the RIF on April 1 in an email sent at 5 am Eastern, though a number of employees only realized they had been let go when their badges no longer worked when trying to access HHS buildings.
Among those impacted were half of the staff working at the OCIO—around 150 people, including the entire workforce at the Immediate Office of the CIO, which includes senior figures like the chief of staff, HR director, acquisition director, and budget director, sources tell WIRED. The CIO, Jennifer Wendel, who has worked in the federal government for almost three decades, is also departing, sources say, and will end her tenure next month. Wendel did not respond to a request for comment from WIRED.
“The suggestion that critical IT and cybersecurity functions at HHS are being left unsecured is simply untrue,” an HHS spokesperson tells WIRED. “Essential operations at HHS, including contract management and cybersecurity oversight—remain staffed and functional. It’s unfortunate that some former employees are spreading unfounded rumors. HHS remains committed to a secure, modernized HHS that serves the American people, not internal bureaucracy.”
One team that was purged from HHS managed over a hundred contracts worth hundreds of millions of dollars, including crucial cybersecurity licenses. It also managed the renewal of contracts for hundreds of specialized contractors who perform critical tasks for the department, including a dozen cybersecurity contractors who work at the Computer Security Incident Response Center (CSIRC)—the primary component of the department’s overall cybersecurity program which is overseen by the chief information security officer.
While all of HHS’s agencies have their own cybersecurity and IT teams, the CSIRC is the only one that has visibility across the entire network of the department. This center, based in Atlanta, monitors the entire HHS network and is tasked with preventing, detecting, reporting, and responding to cybersecurity incidents at HHS.
“It is the department’s nerve center,” the source says. “It has direct links to DHS, CISA, Defense Health Agency, and the intelligence community.”
The contractors provide round-the-clock coverage on three eight-hour shifts every single day, monitoring the network for any possible outages or attacks from inside or outside the network. Those contracts are set to expire on June 21; while there is time to renew them, it’s not clear who is authorized to do so or knows how, since the entire office that oversees the process is no longer working at HHS.
Adding to the threat is the decision by the General Service Administration to terminate the lease for the CSIRC in Atlanta, effective December 31, 2025.
Many of the cybersecurity and monitoring tools the contractors use to monitor the networks are also due for renewal in the coming months.
If the situation is not addressed, “pretty soon, the department will be completely open to external actors to get at the largest databases in the world that have all of our public health information in them, our sensitive drug testing clinical trial information at the NIH or FDA or different organizations’ mental health records,” the source claims, echoing the opinions of other sources who spoke to WIRED.
In the weeks leading up to the RIF, some administrative staff did have interactions with Elon Musk’s so-called Department of Government Efficiency (DOGE) operatives, including Clark Minor, a software engineer who worked at Palantir for over a decade and was recently installed as the department’s chief information officer.
As one employee was detailing the work they did at the OCIO, they said, they got the sense that Minor—whose online résumé does not detail any experience in the federal government—seemed overwhelmed by the sheer scale of HHS, an agency that accounted for over a quarter of federal spending in 2024 and consists of an almost innumerable amount of offices and staff and operating divisions.
Minor has not provided guidance to the remaining HHS staff on the transition, according to two sources still at the agency.
Minor did not respond to a request for comment from WIRED.
Some internal systems are already breaking down, according to sources still working at HHS. One employee, who facilitates travel for HHS employees, says the RIF “set federal travel back to processes that were in place prior to the first Electronic Travel System contract in 2004.”
While sources who spoke to WIRED differed on exactly when and how the IT and cybersecurity infrastructure at the department might collapse, they all agreed that without a radical intervention in the coming weeks, the fallout could be catastrophic.
"If the US health system lost CMS, FDA, NIH, and CDC functionality indefinitely without warning, and no backup systems were available, this would be an unprecedented systemic shock," one source at the OCIO tells WIRED.
Current HHS workers say they have not been presented with a plan to remedy the looming crisis, and have seen no leadership from either the political appointees or DOGE operatives who have been installed at HHS.
“There is no transition, and those in charge are AWOL,” one person currently working at HHS tells WIRED, echoing the sense of “chaos” found in an in-depth investigation into HHS by Stat. “I’m doing nothing productive. I’m answering emails stating we cannot help, we cannot process, we have no guidance, we cannot operate. This ship has no captain whatsoever, and I’m playing in the band while the Titanic sinks.”
11 notes
·
View notes
Text
USAID contract (2024)
Recipient: International Business Machines Corporation
Amount: $29,750,000
Purpose: The new cyber security activity will support host government and operators to develop and implement policies, procedures, and hardware/software solutions, as well as workforce development, aimed at improving prevention, protection, preparedness, resp...
Country: Albania
21 notes
·
View notes
Text
politics
disclamer: i am not american. this does not affect me, at least for now. this perhaps may decrease my following but my friends are in danger, and im drinking a beer, i dont give a shit at the moment
"Project 2025 is a strategic initiative aimed at transforming the US Army into a more lethal, agile, and adaptable fighting force by the year 2025. This ambitious plan encompasses a wide range of modernization efforts across all aspects of the Army, from its personnel and training to its equipment and technology. A key element of Project 2025 is the development and integration of advanced technology, such as artificial intelligence, robotics, and autonomous systems. These technologies are intended to enhance the Army's ability to collect and analyze information, conduct operations in complex environments, and engage adversaries effectively. The project also emphasizes the importance of network modernization and cyber security, recognizing the growing role of cyber warfare and the need for resilient and secure communication systems. In addition to technological advancements, Project 2025 prioritizes the development of human capital by focusing on training, education, and recruitment. The goal is to cultivate a workforce that is skilled, adaptable, and capable of operating effectively in a rapidly changing world. By combining these technological and human elements, Project 2025 aspires to create an Army that is prepared to meet the challenges of future conflicts and maintain its position as the premier military force in the world. " - Unknown name
I am not american. I will not say my views, whether republican, liberal, democrat or whatever views and titles there are
But i will simply say what i have heard and what i have read
Project 2025, a nefarious agenda cloaked in a veil of progress, looms over society, threatening to erode fundamental freedoms and plunge us into a dystopian nightmare. At its core is a sinister plot to restrict access to reproductive healthcare, stripping women of their control over their own bodies. Abortion, a fundamental human right, is deemed a heinous crime, with draconian punishments meted out to those who dare to seek or provide it. I do not doubt they will be going after birth control as well, which is also a human right.
Furthermore, Project 2025 viciously targets the LGBTQ+ community, attempting to erase their very existence. Marriage equality is revoked, and same-sex couples are denied the right to love, raise families, or live their lives openly. Hateful rhetoric spews from the highest offices, fostering an atmosphere of fear and persecution.
Education is also under attack, with curricula twisted to promote a narrow, intolerant worldview. Critical thinking and open discussion are stifled, replaced with indoctrination and propaganda. Young minds are poisoned with messages of hate and exclusion, shaping a generation destined for ignorance and intolerance.
The arts, once a bastion of free expression, are now subject to censorship. Artists who dare to challenge the status quo are silenced, their works banned or destroyed. Culture is homogenized and controlled, leaving no room for diversity or dissent.
Trump's tax cuts, primarily benefiting wealthy individuals and corporations, have been criticized for increasing the national debt and widening income inequality. Trump's administration has rolled back environmental regulations, including those addressing climate change and pollution control, drawing criticism from scientists and environmentalists.
Trump's immigration policies, such as the border wall and family separations, have been condemned as inhumane and ineffective, exacerbating tensions at the U.S.-Mexico border.
Trump's attempts to repeal and replace the Affordable Care Act, known as Obamacare, were unsuccessful. However, his administration's actions, such as weakening the mandate and Medicaid expansion, have led to concerns about reduced healthcare access.
Trump's rhetoric and policies have been criticized for fueling racial tensions and promoting gender discrimination. The travel ban targeting majority-Muslim countries and the separation of families at the border have drawn accusations of racism and xenophobia.
Trump's presidency and the Republican Party's support of his policies have contributed to deep political polarization in the United States. His divisive rhetoric and inflammatory tweets have exacerbated existing divisions and made it harder to find common ground. Trump's attacks on the media, the judiciary, and law enforcement have raised concerns about the erosion of democratic institutions. His refusal to concede defeat in the 2020 election and his supporters' storming of the Capitol on January 6, 2021, have further undermined public trust in the electoral process.
This is what i have heard
I have women friends, gay friends, trans friends that live in america
I suggest not voting for trump, but lets be honest, thats been said a dozen timew, doesnt make it any less hwlpful of advice
your all off your heads (or perhaps faces) if ye think project 2025 is good
#trump 2024#project 2025#us politics#politics#journalism#opinion#criticism#controversy#boke#drunken dinger
12 notes
·
View notes
Text
The Evolution of Private Security: A Historical Perspective

Introduction:

1. Ancient Roots of Private Security:
In the annals of history, the roots of private security can be traced back to ancient civilizations, where individuals or groups were employed to safeguard valuable assets. From the protection of merchants along trade routes to the guardianship of wealthy estates, private security in its nascent form laid the groundwork for future developments.
2. Feudal Societies and Mercenary Forces:
During the feudal era, the concept of private security took on a militaristic hue. Mercenary forces were employed by monarchs, nobles, and wealthy landowners to protect territories and interests. These quasi-professional soldiers marked a transition toward more organized forms of private security.
3. Industrial Revolution and the Rise of Corporate Security:
The Industrial Revolution marked a turning point as societies shifted from agrarian economies to industrial powerhouses. With this transformation, corporations emerged, and with them, the need for security to protect factories, assets, and the burgeoning workforce. Corporate security divisions became a fixture, reflecting the evolving nature of private security.
4. Detective Agencies and Pinkertons:
The late 19th and early 20th centuries witnessed the rise of private detective agencies, with the Pinkerton National Detective Agency leading the way. These agencies were instrumental in investigating criminal activities, tracking down outlaws, and providing security services, contributing significantly to the professionalization of private security.
5. Post-World War II Era and Global Expansion:
The aftermath of World War II saw a surge in the need for private security on a global scale. As nations rebuilt, private security firms expanded their services to include everything from guarding sensitive installations to providing executive protection. This period marked the globalization of private security as an industry.
6. Technological Advancements:
The latter half of the 20th century and into the 21st century witnessed unprecedented technological advancements that transformed private security. Surveillance systems, access control technologies, and communication tools became integral to the arsenal of private security firms, enhancing their ability to protect clients in an increasingly complex world.
7. Private Security in the Digital Age:
In the contemporary landscape, private security is inseparable from the digital realm. Cybersecurity has become a critical facet of private security, reflecting the shift from physical threats to virtual ones. Private security firms now play a pivotal role in safeguarding organizations against cyber threats and data breaches.
Conclusion:
The historical evolution of private security is a testament to its adaptive nature. From humble beginnings in ancient civilizations to the complex, technology-driven industry of today, private security has continually evolved to meet the challenges of each era. Understanding this journey provides valuable insights into the foundations of an industry that plays an integral role in ensuring the safety and security of individuals, organizations, and societies as a whole.
www.krystal-group.com/private-security-and-manned-guarding
3 notes
·
View notes
Text
ADCA (Advanced Diploma in Computer Applications) Full Form, Eligibility, Duration, Syllabus, Scope
What is ADCA? ADCA full form is Advanced Diploma in Computer Applications. ADCA is a comprehensive diploma program designed to provide foundational and intermediate knowledge of computer applications. It typically covers areas such as:
Office productivity software (MS Word, Excel, PowerPoint)
Basic programming (often C, C++, or Python)
Database management
Accounting software (like Tally with GST)
Web design basics (HTML/CSS)
Internet and email use
Basic graphics and multimedia tools
The course usually spans 12 months, is divided into two semesters, and is available through various private institutes, training centers, and some state-affiliated education boards across India. ADCA course fee ranges between Rs. 10,000 to Rs. 15,000, depending on the institution’s quality and location.

Who Should Take This Course?
ADCA is ideal for:
Students (10th/12th pass) seeking a professional skill to enhance employability
Job seekers aiming for entry-level roles in IT support, data entry, or office administration
Small business owners want to manage their accounting, design, or office tasks.
Working professionals looking to upskill in computer usage and basic programming.
Beginners in IT who want a low-cost and practical entry point into the digital workforce
What is the use of ADCA?
In an era dominated by digital transformation, ADCA holds increasing relevance:
Digital Literacy: It builds foundational digital skills critical for nearly every job today.
Improves Workplace Efficiency
Learning office tools like MS Word, Excel, and email helps you work faster and smarter. These skills are helpful in many jobs—especially in schools, offices, shops, and banks—where digital work is a daily routine.
Boosts Employability
Today, most jobs—even non-technical ones—require basic computer knowledge. ADCA gives you the skills employers expect, like using a computer, typing, handling data, and doing simple digital tasks.
Helps Small Business Owners and Entrepreneurs
If you run a shop or business, ADCA helps you manage accounts, create invoices, design flyers, and even make a simple website. It gives you the digital tools to grow your business and save money by doing tasks yourself.
Bridging the Skill Gap: Helps youth in semi-urban and rural areas gain access to IT careers without needing a full degree.
Course Duration & Eligibility
Duration: 12 Months (Typically 2 Semesters)
Eligibility: 10th / 12th pass or equivalent
ADCA Computer Course Syllabus
1. Fundamentals of Computer
Introduction to Computers
Computer Architecture
Computer Peripherals
Computer Hardware and Software
2. Operating Systems (OS)
Windows
Linux/Unix
DOS
3. Programming Languages
C
C++
Java
Python
4. Web Technologies
HTML, CSS, and JavaScript
Web Development Tools
Server-side Scripting (PHP, ASP.NET, Node.js)
Database Connectivity (MySQL, SQL Server)
5. Database Management System (DBMS)
Introduction to DBMS
SQL and Database Design
Data Security and Integrity
6. Software Engineering
Software Development Life Cycle (SDLC)
Software Testing
Project Management
7. Networking Concepts
Basics of Networking
TCP/IP Protocol Suite
Network Security
8. Mobile App Development
Introduction to Mobile App Development
Android Development
iOS Development
9. Data Structures and Algorithms
Basic Data Structures (Arrays, Linked Lists, Trees)
Algorithm Design and Analysis
10. Cyber Security
Introduction to Cybersecurity
Security Threats and Countermeasures
11. Soft Skills and Communication
Effective Communication
Presentation Skills
Teamwork and Leadership
12. Project Work
Practical Application of Knowledge Acquired Throughout the Course
ADCA Course Module & Topics Covered:
The Detail for an Advanced Diploma in Computer Applications (ADCA) course includes topics such as: ModuleTopics CoveredFundamentals of ComputersBasic concepts, architecture, and peripheralsOperating SystemsWindows, Linux, and DOSProgramming LanguagesC, C++, Java, PythonWeb TechnologiesHTML, CSS, JavaScript, PHP, SQLDatabase ManagementSQL, database design, and securitySoftware EngineeringSDLC, testing, project managementNetworkingBasics of networking, TCP/IP, and network securityMobile App DevelopmentAndroid/iOS development basicsData Structures & AlgorithmsArrays, linked lists, trees, algorithmsCyber SecurityIntroduction to threats and countermeasuresSoft SkillsCommunication, presentation, teamworkProject WorkPractical applications
Why Choose ADCA?
The Advanced Diploma in Computer Application (ADCA) opens up numerous opportunities in the ever-growing field of IT. Here is a look at the scope and career prospects for individuals who complete this course:
Scope of ADCA
Wide Range of Skills: The ADCA course teaches students useful computer skills like using software, basic programming, managing data, building websites, and understanding online safety. These skills help students work in many different jobs.
High Job Demand: As more businesses use technology, the need for trained computer professionals is growing. ADCA graduates can find jobs in software, IT services, schools, banks, hospitals, and more.
Foundation for Advanced Studies: The ADCA course lays a solid foundation for further studies in IT. Graduates can pursue advanced diplomas and undergraduate and postgraduate degrees in computer science, information technology, and related fields.
Career Prospects
ADCA graduates have a wide range of career options available to them. Some of the common job roles include:
Software Developer: Develop and maintain software applications using programming languages learned during the course, such as C, C++, Java, and Python.
Web Developer: Design and develop websites and web applications using HTML, CSS, JavaScript, and server-side scripting languages.
Database Administrator: Manage and maintain databases, ensuring data security, integrity, and efficient performance.
IT Support Specialist: Provide technical support and troubleshooting assistance for computer systems, software, and networks.
Network Administrator: Oversee and manage an organization’s computer networks, ensuring smooth and secure operations.
Cybersecurity Analyst: Protect an organization’s computer systems and networks from cyber threats by implementing security measures and monitoring for vulnerabilities.
Mobile App Developer: Create and maintain mobile applications for Android and iOS platforms.
Project Manager: Manage IT projects, ensuring they are completed on time, within budget, and meet the desired quality standards.
Data Analyst: Analyze and interpret data to help organizations make informed decisions.
Educator/Trainer: Teach computer applications and IT courses in schools, colleges, or training centers.
Which is Better DCA or ADCA?
Course Level
Entry-Level Course: DCA is perfect for beginners who want to learn basic computer skills. It covers essential tools for office work, including MS Office, internet usage, and typing.
What You will Learn:
MS Word, Excel, PowerPoint
Internet basics & email
Typing and computer fundamentals
ADCA (Advanced Diploma in Computer Applications)
Intermediate-Level Course: ADCA builds on what you learned in DCA. It offers more in-depth training in IT skills, making it ideal for those wanting to enhance their programming, web design, and accounting knowledge.
What You will Learn:
Advanced MS Office
Programming basics (C/C++)
Web design (HTML, CSS)
Database management and Tally with GST
Syllabus: Includes everything from DCA plus programming (C/C++), web design (HTML/CSS), database management (MySQL), accounting software (Tally), and graphic design (Photoshop).
2. Course Duration
DCA:
Typically, it lasts 6 months (may vary depending on the institute or location).
ADCA:
Generally spans 12 months, divided into two semesters, offering more detailed training over a more extended period.
3. Eligibility
DCA:
Open to anyone with a 10th-grade pass or equivalent. It is ideal for individuals with minimal or no prior computer knowledge.
ADCA:
Typically requires a 10th/12th pass or a completed DCA. ADCA is more suitable for students who have a basic understanding of computers and wish to learn more advanced skills.
4. Skills Acquired
DCA:
Basic computer skills such as:
Microsoft Office (Word, Excel, PowerPoint)
Internet usage, email management
Typing skills
ADCA:
In addition to DCA skills, ADCA covers:
Programming (C/C++ or Python)
Web Design (HTML, CSS)
Database management (MySQL)
Tally with GST (Accounting Software)
Basic graphic design tools like Photoshop
Project work and real-world applications
5. Career Opportunities
DCA:
Ideal for entry-level roles like:
Data Entry Operator
Office Assistant
Computer Operator
Basic technical support
ADCA:
Opens up higher-level job opportunities, including:
Junior Programmer
Web Designer
Accounting Clerk (with Tally skills)
Junior Database Administrator
Graphic Designer (basic)
IT Support Specialist
6. Salary Expectations
DCA:
Entry-level salaries for DCA graduates typically range from ?8,000 to ?15,000 per month, depending on the job role and location.
ADCA:
Graduates of ADCA can expect higher starting salaries, generally ranging from ?15,000 to ?25,000+ per month, depending on the specialization (e.g., programming, web design).
7. Which One is Better?
DCA is suitable for:
Individuals who are new to computers
People looking for entry-level office jobs
Those on a limited budget and time
ADCA is suitable for:
People looking to specialize in IT and office-related work
Those interested in roles requiring programming, web design, or accounting skills
Individuals aiming for a broader skill set and higher-paying jobs
1 note
·
View note
Text
The relentless evolution of cyber threats necessitates a highly skilled workforce to safeguard our digital landscape. Earning the esteemed Security+ certification validates a foundational understanding of cybersecurity best practices, positioning you as a crucial asset in the defense against cyberattacks.
#security plus exam requirements#cybersecurity#security#comptia#security plus#security plus training#infosectrain#learntorise
5 notes
·
View notes
Text
Top On-Demand App Development Services: How to Choose the Right One
What is an On-Demand App?
On-demand apps connect users with services or products instantly. These applications cover various industries, including food delivery, ride-hailing, home services, and healthcare. Users benefit from convenience, real-time tracking, and seamless transactions, making them a popular choice for businesses and consumers.
What Are On-Demand App Development Services?
On-demand app development services focus on building applications that offer instant access to products or services. These services include planning, design, development, integration, testing, and deployment. Developers create user-friendly platforms with real-time tracking, payment gateways, push notifications, and AI-driven recommendations. Companies providing these services ensure that apps run smoothly across multiple devices and operating systems.

Why On-Demand App Development Services Are the Best Choice?
Scalability: On-demand apps grow with business needs, supporting more users and features over time.
User Convenience: Customers access services quickly, leading to higher engagement and satisfaction.
Increased Revenue: Businesses can reach a wider audience and introduce new monetization models.
Automation: Reduces manual tasks, improving operational efficiency.
Data-Driven Decisions: Insights from user behavior help in refining services and offerings.
Key Features of a High-Quality On-Demand App
1. User-Friendly Interface
An intuitive layout ensures that users can access services easily without confusion.
2. Real-Time Tracking
Live updates on service status, delivery progress, or ride tracking improve transparency and user trust.
3. Multiple Payment Options
Integrating various payment methods, such as credit/debit cards, digital wallets, and UPI, offers users flexibility.
4. Push Notifications
These alerts inform users about order status, offers, and important updates, keeping them engaged.
5. AI and Machine Learning Integration
Personalized recommendations based on user preferences improve customer experience and retention.
6. Robust Admin Dashboard
A well-designed dashboard allows businesses to monitor operations, manage users, and track revenue in real time.
7. Secure Authentication
Features like biometric login, OTP verification, and encryption protect user data and transactions.
8. Multi-Platform Compatibility
Apps should work seamlessly across Android, iOS, and web platforms for a broader reach.
How On-Demand Apps Improve Business Efficiency
Automated Scheduling: Reduces the workload for businesses by handling appointments and deliveries automatically.
Resource Optimization: Helps in managing inventory, workforce, and logistics efficiently.
Better Customer Engagement: Features like chat support and personalized recommendations strengthen customer relationships.
Seamless Operations: Reduces dependency on manual interventions, cutting down errors and delays.
Data-Driven Strategies: Businesses can analyze customer behavior and adjust services accordingly.
Key Points to Look at When Selecting an On-Demand App Development Company
1. Industry Experience
Companies with experience in developing on-demand apps for various sectors have a better grasp of business needs.
2. Technology Stack
Using the latest programming languages, frameworks, and tools ensures that apps are scalable and future-ready.
3. Customization Options
A company should offer flexibility to align app features with business objectives.
4. Post-Launch Support
Reliable developers provide maintenance and updates to keep apps running smoothly.
5. Security Measures
Strong security protocols prevent data breaches and cyber threats.
6. User Reviews and Portfolio
Checking client feedback and past projects gives an idea of the company's capabilities.
Security and Compliance in On-Demand Applications
1. Data Encryption
Protects sensitive user information from cyber threats.
2. Secure Payment Gateways
Ensures safe transactions through PCI-DSS-compliant systems.
3. Regular Security Audits
Frequent assessments help identify and fix vulnerabilities.
4. Privacy Regulations Compliance
Following GDPR, HIPAA, or other local laws safeguards user data and business credibility.
5. Multi-Factor Authentication (MFA)
Adding extra layers of security prevents unauthorized access.
Why Malgo Is the Right Choice for On-Demand App Development Services
1.Custom Solutions
We build apps tailored to specific business needs, ensuring a perfect fit for operations and user demands.
2. Latest Technology Stack
Malgo leverages AI, ML, cloud computing, and advanced frameworks to create high-performance applications.
3. Scalability and Future-Readiness
Our apps grow with your business, supporting increased traffic and new features without performance issues.
4. Security-First Approach
We implement end-to-end encryption, secure authentication, and compliance protocols to safeguard user data.
5. User-Centric Design
With intuitive UI/UX principles, our apps offer smooth navigation, engaging layouts, and high responsiveness.
6. Ongoing Support and Updates
We provide continuous maintenance, bug fixes, and feature enhancements for long-term reliability.
Final Thoughts Choosing the right on-demand app development service can make a significant difference in business growth. A well-structured app improves customer engagement, operational efficiency, and revenue streams. Malgo stands out as a trusted partner, delivering innovative, secure, and user-friendly on-demand applications. Get Expert On-Demand App Development Services for Your Business Today. Whether you’re launching a new service or upgrading an existing platform, investing in expert development services is the key to long-term success.
#appdevelopment#techinnovation#mobile app development#app development#ondemandapps#mobileappdesign#ondemandapp#customappdevelopment
1 note
·
View note
Text
Top 7 Challenges Faced By IT Industry In 2023
Within the rapidly growing universe of technology, the IT companies in India assume a crucial role, persistently adjusting themselves to cater to the needs of a perpetually shifting environment. Nevertheless, the advancement of society brings forth a set of obstacles that necessitate a deliberate approach to resolution. As the year 2023 commences, the IT industry faces a multitude of challenges that necessitate careful consideration and effective measures. This blog aims to explore the primary issues encountered by the IT industry in the current year, providing insights into their consequences and possible remedies.

1. Cybersecurity Threats:
The escalation of cyber risks has been observed as a consequence of the widespread adoption of digital technology and interconnected systems. The level of sophistication exhibited by cybercriminals is on the rise, as they deploy advanced strategies to bypass security systems. All the IT companies in Gujarat, India, in the year 2023 are confronted with the formidable challenge of maintaining a competitive edge in the face of cyber attacks, while simultaneously prioritising data protection and securing essential infrastructure. The implementation of effective cybersecurity safeguards, regular conduct of security audits, and provision of cybersecurity education to staff are essential elements in addressing and minimising this risk.
2. Data Privacy and Compliance:
The increasingly stringent legislative framework surrounding data privacy poses a substantial obstacle for the information technology sector. Stringent regulations pertaining to data privacy, such as the General Data Privacy Regulation (GDPR), necessitate rigorous adherence. In the year 2023, the IT companies in Vadodara, Gujarat have the challenge of striking a delicate equilibrium between adhering to regulatory requirements and efficiently using data for commercial objectives. IT organisations are required to allocate resources towards the implementation of compliance frameworks, provide training to their employees, and guarantee that data-handling procedures are in accordance with the prescribed norms.
3. Talent Acquisition and Retention:
The acquisition and retention of talent pose an ongoing problem for the IT industry, as it continues to seek and keep qualified workers. The scarcity of highly specialised skills frequently results in a disparity between demand and supply, hence engendering intense rivalry for those with such talents. Moreover, the current trends in remote work and the increasing globalisation of the talent market serve to exacerbate this challenge. In order to tackle this issue, a reliable IT company in India like Nivida Web Solutions prioritises the enhancement of the skills of their current workforce, provides enticing remuneration packages, cultivates a favourable work environment, and creates avenues for professional advancement and personal improvement.
4. Technological Advancements and Adaptability:
The expeditious rate at which technological developments are occurring has both advantages and disadvantages for the IT business. Although these developments present promising prospects, they also present a difficulty in terms of adaptation. Keeping abreast of developing technology and enabling a smooth transition to new platforms and tools may be a demanding task. In order to effectively adapt to emerging technology, IT organisations must allocate resources towards the implementation of continual training and development programmes, which aim to equip their personnel with the requisite skills.
5. Resource Optimization and Scalability:
The optimisation of resources and the effective scalability of operations have emerged as significant challenges in recent times. The management of resources and the scaling of operations in response to varying market needs and the imperative of cost-effectiveness can provide intricate challenges. Cloud computing and intelligent resource allocation are essential solutions that can be employed to effectively address this dilemma. The utilisation of cloud solutions by Nivida Web Solutions - a recognised IT company in Gujarat, India, allows for enhanced flexibility and cost-efficiency, hence assuring the appropriate allocation of resources.
6. Integration and Interoperability:
The IT environment is distinguished by a diverse array of systems and applications that necessitate harmonious integration. The task of achieving integration and interoperability across diverse platforms, legacy systems, and emerging technologies poses a significant challenge. The establishment of interconnectedness is crucial in facilitating an effective and productive IT ecosystem. It is imperative for the industry to prioritise the development of standardised interfaces, utilise APIs effectively, and implement integration platforms in order to improve interoperability.
7. Environmental Sustainability:
Environmental sustainability has emerged as a pressing issue in various sectors, encompassing the field of IT. The IT industry possesses a substantial carbon footprint as a result of its energy consumption, generation of electronic waste, and operations of data centres. In the year 2023, the sector is faced with the task of identifying environmentally sustainable solutions and adopting practices that effectively mitigate their ecological footprint. The use of green technology, the optimisation of data centre efficiency, and the incorporation of circular economy concepts are positive measures in the pursuit of sustainability objectives.
Final Thoughts:
The IT sector encounters a diverse range of issues in the year 2023, necessitating the implementation of proactive and strategic methodologies. Addressing a range of difficulties, including cybersecurity risks, talent acquisition, technological adaptation, and sustainability, is necessary in order to establish and maintain a flourishing and sustainable information technology ecosystem. By adopting a proactive approach towards innovation, allocating resources towards skill enhancement, and placing emphasis on adherence to regulations and sustainability, Nivida Web Solutions - the most distinguished IT company in Vadodara, may effectively navigate the obstacles it faces and emerge with increased resilience. This will facilitate the ongoing growth and progression of the industry in the era of digitalization.
7 notes
·
View notes
Text
In the United States, call center companies play a pivotal role in providing customer support, sales assistance, technical troubleshooting, and various other services for businesses across a multitude of industries. These companies employ thousands of individuals nationwide and operate through various models, including in-house, outsourced, and virtual call centers. Let's delve into the landscape of call center companies in the USA.
1. Overview of the Call Center Industry:
The call center industry in the USA has witnessed significant growth over the years, driven by the increasing demand for cost-effective customer service solutions and the globalization of businesses. Today, call centers cater to diverse sectors such as telecommunications, banking and finance, healthcare, retail, technology, and e-commerce.
2. Major Players:
Several major call center companies dominate the industry, including:
Teleperformance: One of the largest call center companies globally, Teleperformance operates numerous centers across the USA, offering multilingual customer support, technical assistance, and sales services.
Concentrix: Concentrix is another key player, known for its innovative customer engagement solutions. It provides a wide range of services, including customer care, technical support, and digital marketing services.
Alorica: Alorica specializes in customer experience outsourcing solutions, serving clients in various industries. It offers services such as customer support, sales, and back-office support.
Sitel Group: Sitel Group is renowned for its customer experience management solutions. With a global presence, Sitel operates call centers in multiple locations across the USA, providing tailored customer support services.
TTEC: Formerly known as TeleTech, TTEC offers customer experience solutions, digital services, and technology-enabled customer care. It focuses on delivering personalized customer interactions through its contact centers.
3. Industry Trends:
The call center industry is continually evolving, driven by technological advancements and changing consumer preferences. Some notable trends include:
Digital Transformation: Call centers are increasingly integrating digital channels such as chat, email, and social media to enhance customer engagement and support omnichannel experiences.
AI and Automation: Automation technologies, including artificial intelligence (AI) and chatbots, are being adopted to streamline processes, improve efficiency, and provide faster resolutions to customer queries.
Remote Workforce: The COVID-19 pandemic accelerated the shift towards remote work in the call center industry. Many companies have embraced remote workforce models, allowing agents to work from home while maintaining productivity and efficiency.
Data Analytics: Call centers are leveraging data analytics tools to gain insights into customer behavior, preferences, and trends. This data-driven approach enables them to personalize interactions and optimize service delivery.
4. Challenges and Opportunities:
Despite its growth, the call center industry faces several challenges, including:
Staffing Issues: Recruiting and retaining skilled agents remains a challenge for many call center companies, particularly amid competition for talent and high turnover rates.
Security Concerns: With the increasing prevalence of cyber threats, call centers must prioritize data security and compliance to protect sensitive customer information.
However, the industry also presents numerous opportunities for growth and innovation:
Expansion of Services: Call center companies can diversify their service offerings to meet the evolving needs of clients, such as expanding into digital customer engagement, analytics, and consulting services.
Focus on Customer Experience: By prioritizing customer experience and investing in training and technology, call centers can differentiate themselves and gain a competitive edge in the market.
Globalization: With advancements in technology and communication infrastructure, call center companies can explore opportunities for global expansion and tap into new markets.
5. Future Outlook:
Looking ahead, the call center industry is poised for further growth and transformation. As businesses increasingly prioritize customer-centric strategies, call center companies will play a crucial role in delivering exceptional customer experiences and driving business success.
In conclusion, call center companies in the USA form a vital component of the customer service ecosystem, serving a wide range of industries and helping businesses enhance customer satisfaction and loyalty. With ongoing technological innovations and evolving customer expectations, the industry is poised for continued growth and innovation in the years to come.
2 notes
·
View notes
Text
Mass layoffs and weak leadership are taking a severe toll on the US government’s cyber defense agency, undermining its ability to protect America from foreign adversaries bent on crippling infrastructure and ransomware gangs that are bleeding small businesses dry.
Inside the Cybersecurity and Infrastructure Security Agency, vital support staff are gone, international partnerships have been strained, and workers are afraid to discuss threats to democracy that they’re now prohibited from countering. Employees are even more overworked than usual, and new assignments from the administration are interfering with important tasks. Meanwhile, CISA’s temporary leader is doing everything she can to appease President Donald Trump, infuriating employees who say she’s out of touch and refusing to protect them.
“You've got a lot of people who … are looking over their shoulder as opposed to looking at the enemy right now,” says one CISA employee.
As the Trump administration’s war on the federal bureaucracy throws key agencies into chaos, CISA’s turmoil could have underappreciated consequences for national security and economic prospects. The agency, part of the Department of Homeland Security, has steadily built a reputation as a nonpartisan source of funding, guidance, and even direct defensive support for cities, businesses, and nonprofits reeling from cyberattacks. That mission is now under threat, according to interviews with seven CISA employees and another person familiar with the matter, all of whom requested anonymity to avoid reprisals.
“Our enemies are not slowing their continuous assaults on our systems,” says Suzanne Spaulding, who led CISA’s predecessor during the Obama administration. “We need all hands on deck and focused, not traumatized and distracted.”
Talent Exodus
CISA’s mission has grown significantly since its creation in 2018. Established mainly to defend government networks, the agency increasingly embraced new roles supporting private companies and state governments, advocating for secure software, and cooperating with foreign partners. This helped CISA raise its profile and gain credibility. But now, following several rounds of layoffs and new restrictions from the Trump administration, the agency is struggling to sustain its momentum.
The extent of the cuts at CISA is still unclear—employees are only learning about the loss of colleagues through word of mouth—but multiple employees estimate that, between the layoffs and the Office of Personnel Management’s deferred-resignation program, CISA has lost between 300 and 400 staffers—roughly 10 percent of its 3,200-person workforce. Many of those people were hired through DHS’s Cybersecurity Talent Management System (CTMS), a program designed to recruit experts by competing with private-sector salaries. As a result, they were classified as probationary employees for three years, making them vulnerable to layoffs. These layoffs at CISA also hit longtime government workers who had become probationary by transferring into CTMS roles.
Key employees who have left include Kelly Shaw, who oversaw one of CISA’s marquee programs, a voluntary threat-detection service for critical infrastructure operators; David Carroll, who led the Mission Engineering Division, the agency’s technological backbone; and Carroll’s technical director, Duncan McCaskill. “We've had a very large brain drain,” an employee says.
The departures have strained a workforce that was already stretched thin. “We were running into [a] critical skills shortage previously,” says a second employee. “Most people are and have been doing the work of two or more full-time [staffers].”
The CISA team that helps critical infrastructure operators respond to hacks has been understaffed for years. The agency added support positions for that team after a Government Accountability Office audit, but “most of those people got terminated,” a third employee says.
CISA’s flagship programs have been mostly unscathed so far. That includes the threat-hunting branch, which analyzes threats, searches government networks for intruders, and responds to breaches. But some of the laid-off staffers provided crucial “backend” support for threat hunters and other analysts. “There's enhancements that could be made to the tools that they're using,” the first employee says. But with fewer people developing those improvements, “we're going to start having antiquated systems.”
In a statement, DHS spokesperson Tricia McLaughlin says CISA remains “committed to the safety and security of the nation’s critical infrastructure” and touted “the critical skills that CISA experts bring to the fight every day.”
National Security Council spokesperson James Hewitt says the reporting in this story is “nonsense,” adding that “there have been no widespread layoffs at CISA and its mission remains fully intact.”
“We continue to strengthen cybersecurity partnerships, advance AI and open-source security, and protect election integrity,” Hewitt says. “Under President Trump’s leadership, our administration will make significant strides in enhancing national cybersecurity.”
Partnership Problems
CISA’s external partnerships—the cornerstone of its effort to understand and counter evolving threats—have been especially hard-hit.
International travel has been frozen, two employees say, with trips—and even online communications with foreign partners—requiring high-level approvals. That has hampered CISA’s collaboration with other cyber agencies, including those of “Five Eyes” allies Canada, Australia, New Zealand, and the UK, staffers say.
CISA employees can’t even communicate with people at other federal agencies the way they used to. Previously routine conversations between CISA staffers and high-level officials elsewhere now need special permissions, slowing down important work. “I can’t reach out to a CISO about an emergency situation without approval,” a fourth employee says.
Meanwhile, companies have expressed fears about sharing information with CISA and even using the agency’s free attack-monitoring services due to DOGE’s ransacking of agency computers, according to two employees. “There is advanced concern about all of our services that collect sensitive data,” the third employee says. “Partners [are] asking questions about what DOGE can get access to and expressing concern that their sensitive information is in their hands.”
“The wrecking of preestablished relationships will be something that will have long-lasting effects,” the fourth employee says.
CISA’s Joint Cyber Defense Collaborative, a high-profile hub of government-industry cooperation, is also struggling. The JCDC currently works with more than 300 private companies to exchange threat information, draft defensive playbooks, discuss geopolitical challenges, and publish advisories. The unit wants to add hundreds more partners, but it has “had difficulty scaling this,” the first employee says, and recent layoffs have only made things worse. Contractors might be able to help, but the JCDC’s “vendor support contracts run out in less than a year,” the employee says, and as processes across the government have been frozen or paused in recent weeks, CISA doesn’t know if it can pursue new agreements. The JCDC doesn't have enough federal workers to pick up the slack, the fourth CISA employee says.
With fewer staffers to manage its relationships, the JCDC confronts a perilous question: How should it focus its resources without jeopardizing important visibility into the threat landscape? Emphasizing ties with major companies might be more economical, but that would risk overlooking mid-sized firms whose technology is quietly essential to vital US industries.
“CISA continuously evaluates how it works with partners,” McLaughlin says, “and has taken decisive action to maximize impact while being good stewards of taxpayer dollars and aligning with Administration priorities and our authorities.”
Gutting Security Advocacy
Other parts of CISA’s mission have also begun to atrophy.
During the Biden administration, CISA vowed to help the tech industry understand and mitigate the risks of open-source software, which is often poorly maintained and has repeatedly been exploited by hackers. But since Trump took office, CISA has lost the three technical luminaries who oversaw that work: Jack Cable, Aeva Black, and Tim Pepper. Open-source security remains a major challenge, but CISA’s efforts to address that challenge are now rudderless.
The new administration has also frozen CISA’s work on artificial intelligence. The agency had been researching ways to use AI for vulnerability detection and networking monitoring, as well as partnering with the private sector to study AI risks. “About 50 percent of [CISA’s] AI expert headcount has been let go,” says a person familiar with the matter, which is “severely limiting” CISA’s ability to help the US Artificial Intelligence Safety Institute test AI models before deployment.
The administration also pushed out CISA’s chief AI officer, Lisa Einstein, and closed down her office, the person familiar with the matter says. Einstein’s team oversaw CISA’s use of AI and worked with private companies and foreign governments on AI security.
A large team of DHS and CISA AI staffers was set to accompany Vice President JD Vance to Paris in February for an AI summit, but those experts “were all pulled back” from attending, according to a person familiar with the matter.
‘Nefarious’ Retribution
CISA staffers are still reeling from the agency’s suspension of its election security program and the layoffs of most people who worked on that mission. The election security initiative, through which CISA provided free services and guidance to state and local officials and worked with tech companies to track online misinformation, became a target of right-wing conspiracy theories in 2020, which marked it for death after Trump’s return to the White House.
The program—on hold pending CISA’s review of a recently completed internal assessment—was a tiny part of CISA’s budget and operations, but the campaign against it has alarmed agency employees. “This is definitely in the freak-out zone,” says the first employee, who adds that CISA staffers across the political spectrum support the agency’s efforts to track online misinformation campaigns. “All of us recognize that this is a common deception tactic of the enemy.”
The election security purge rippled across the agency, because some of the laid-off staffers had moved from elections to other assignments or were simultaneously working on both missions. Geoff Hale, who led the elections team between 2018 and 2024, was serving as the chief of partnerships at the JCDC when he was placed on administrative leave, setting off a scramble to replace him.
The removal of Hale and his colleagues “was the start to a decline in morale” at CISA, according to the second employee. Now, staffers are afraid to discuss certain topics in public forums: “No one's going to talk about election security right now,” the first employee says.
“The fact that there’s retribution from the president … is kind of frightening,” this employee adds. “A very nefarious place to be.”
Abandoned and Demoralized
The layoffs, operational changes, and other disruptions at CISA have severely depleted morale and undermined the agency’s effectiveness. “Even simple tasks feel hard to accomplish because you don't know if your teammates won't be here tomorrow,” says the fourth employee.
The biggest source of stress and frustration is acting CISA director Bridget Bean, a former Trump appointee who, employees say, appears eager to please the president even if it means not defending her agency. Bean “just takes whatever comes down and implements [it] without thought of how it will affect [CISA’s] mission,” the fifth employee says. Employees describe her as a poor leader and ineffective communicator who has zealously enacted Trump’s agenda. In town-hall meetings with employees, Bean has said CISA must carefully review its its authorities and urged staffers to “assume noble intent” when dealing with Trump officials. While discussing Elon Musk’s mass-buyout program, she allegedly said, “I like to say ‘Fork in the Road’ because it's kind of fun,.” according to the fourth employee. She was so eager to comply with Musk’s “What did you do last week?” email that she instructed staffers to respond to it before DHS had finalized its department-wide approach. DHS later told staff not to respond, and Bean had to walk back her directive.
“Bean feels like she's against the workforce just to please the current administration,” the second employee says. The fourth employee describes her as “not authentic, tone-deaf, spineless, [and] devoid of leadership.”
McLaughlin, the DHS spokesperson, says CISA “is not interested in ad hominem attacks against its leadership,” which she says “has doubled down on openness and transparency with the workforce.”
The return-to-office mandate has also caused problems. With all employees on-site, there isn’t enough room in CISA’s offices for the contractors who support the agency’s staff. That has made it “very difficult” to collaborate on projects and hold technical discussions, according to the first employee. “There wasn’t much thought about [RTO’s] impact to operations,” says the fourth employee. According to a fifth employee, “executing some of our sensitive operations is now harder.” (“CISA has worked tirelessly to make the return to office as smooth as possible from space to technology,” McLaughlin says.)
Employees are dealing with other stressors, too. They have no idea who’s reading their Musk-mandated performance reports, how they’re being evaluated, or whether AI is analyzing them for future layoffs. And there’s a lot of new paperwork. “The amount of extra shit we have to do to comply with the ‘efficiency measures’ … [takes] a lot of time away from doing our job,” says the fifth employee.
Bracing for More
When Trump signed the bill creating CISA in November 2018, he said the agency’s workforce would be “on the front lines of our cyber defense” and “make us, I think, much more effective.” Six and a half years later, many CISA employees see Trump as the biggest thing holding them back.
“This administration has declared psychological warfare on this workforce,” the fourth employee says.
With CISA drawing up plans for even larger cuts, staffers know the chaos is far from over.
“A lot of people are scared,” says the first employee. “We’re waiting for that other shoe to drop. We don't know what's coming.”
Entire wings of CISA—like National Risk Management Center and the Stakeholder Engagement Division—could be on the chopping block. Even in offices that survive, some of the government’s most talented cyber experts—people who chose public service over huge sums of money and craved the lifestyle of CISA’s now-eliminated remote-work environment—are starting to see their employment calculus differently. Some of them will likely leave for stabler jobs, further jeopardizing CISA’s mission. “What is the organization going to be capable of doing in the future?” the first employee asks.
If Trump’s confrontational foreign-policy strategy escalates tensions with Russia, China, Iran, or North Korea, it’s likely those nations could step up their use of cyberattacks to exact revenge. In that environment, warns Nitin Natarajan, CISA’s deputy director during the Biden administration, weakening the agency could prove very dangerous.
“Cuts to CISA’s cyber mission,” Natarajan says, “will only negatively impact our ability to not only protect federal government networks, but those around the nation that Americans depend on every day.”
3 notes
·
View notes
Text
The Future of Semiconductors: Unveiling a World of Possibilities

**The Future of Semiconductors: Unveiling a World of Possibilities**
As we stand on the brink of a new era, the semiconductor industry finds itself at the heart of a technological revolution. The impact of semiconductors on our lives has been profound, driving advancements across industries and shaping the very fabric of our modern civilization. But what lies ahead for this dynamic and transformative field? Let's delve into the future of semiconductors and the boundless possibilities that await us.
**1. Quantum Leap in Computing:**
The race towards quantum computing is intensifying, and semiconductors will play a pivotal role in unlocking its true potential. Quantum processors, built on novel semiconductor materials, have the power to process vast amounts of data in a fraction of the time it takes traditional computers. The future of computing will transcend current limitations, empowering us to solve complex problems previously deemed insurmountable.
**2. AI and Machine Learning:**
The era of artificial intelligence is upon us, and semiconductors will serve as the backbone of AI and machine learning applications. With the growing demand for AI-driven technologies in autonomous vehicles, robotics, healthcare, and more, the semiconductor industry is set to witness an unprecedented surge in AI-focused chip designs. Neuromorphic computing, inspired by the human brain's architecture, could unlock revolutionary AI capabilities, paving the way for cognitive computing and self-learning systems.
**3. The Internet of Things (IoT) Revolution:**
As IoT proliferates, the demand for energy-efficient and high-performance semiconductor devices will skyrocket. We envision a future where billions of interconnected devices communicate seamlessly, facilitated by advanced semiconductor technologies. Ultra-low-power processors, sensors, and wireless communication chips will define the landscape of the IoT revolution, shaping smart cities, wearables, and an interconnected world.
**4. Green and Sustainable Semiconductors:**
Sustainability will be a driving force in the semiconductor industry's future. Innovations in materials and manufacturing processes will lead to environmentally friendly and energy-efficient semiconductor solutions. From eco-friendly chip packaging to renewable energy-powered fabs, the industry will strive to minimize its carbon footprint, contributing to a greener tomorrow.
**5. Silicon Photonics and Beyond:**
The integration of photonics with silicon promises a new era of ultra-high-speed data transmission and processing. Silicon photonics will revolutionize data centers, enabling faster communication between chips and reducing data bottlenecks. Moreover, emerging technologies like 2D materials and carbon nanotubes offer exciting possibilities for futuristic semiconductor devices that could outperform traditional silicon-based chips.
**6. Security and Privacy:**
With the increasing dependence on connected devices, security and privacy will be paramount. Future semiconductor designs will prioritize hardware-based security features to protect against cyber threats and safeguard sensitive data. Trusted execution environments and secure enclaves will become integral components of semiconductor devices, ensuring user confidence in an interconnected world.
**7. Global Collaboration and Talent Development:**
The future of semiconductors will thrive on global collaboration and talent development. International partnerships will foster innovation, as countries pool their resources and expertise. Companies will invest in nurturing a diverse and skilled workforce, driving advancements and promoting a culture of inclusion and creativity.
The future of semiconductors is bright, brimming with possibilities that have the potential to redefine our world. As innovators, engineers, and visionaries, let's embrace this transformative journey together. Let's harness the power of semiconductors to build a future that empowers, connects, and inspires generations to come.
*The future is here, and it's in the hands of those who dare to dream and innovate with semiconductors as their guiding light.*
2 notes
·
View notes
Text
Absolutely spot on, there is too much complacency and 'it can't happen here' in the USA right now.
It CAN happen here. It IS happening here.
The budget for "election security" was removed from the Department of Homeland security. They argued it was outside that department's purview.
There's another department that also handles election security at the federal level... Guess what?
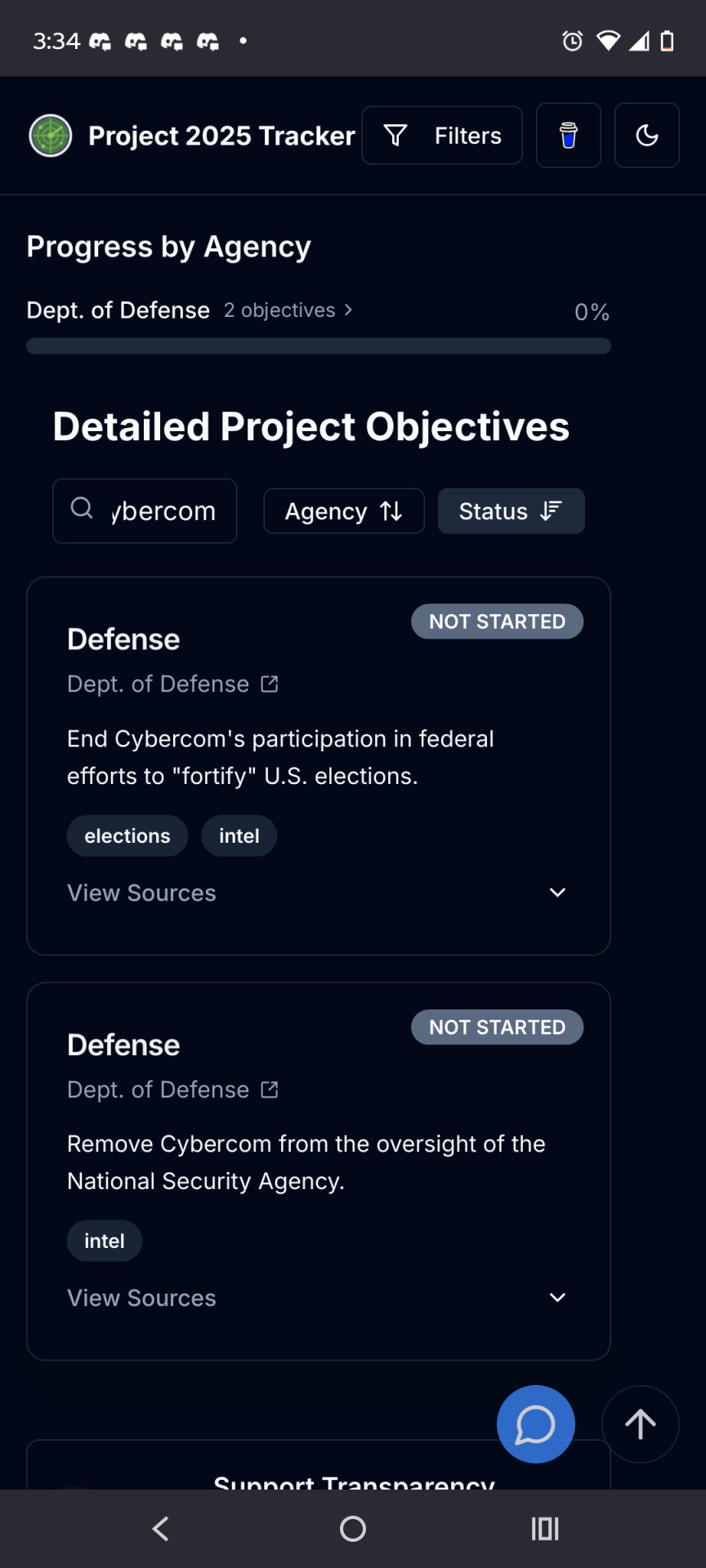
From the Project 2025 tracker.
And look, I know cybercom is the same department that carries out cyber attacks against foreign adversaries. I know the US government and particularly the US intelligence agencies that are being dismantled as we speak (CIA, FBI, NSA, Pentagon have all seen big indiscriminate workforce reductions, forced leaks, or destruction of internal databases) have done a lot of evil, heinous shit, both domestically and - especially- abroad. The US does a lot of regime change, you know it, I know it.
But what's the end game of the current regime?
Take money from the part of the federal budget that is discretionary and works for ordinary Americans - the SMALL part of the budget that is discretionary and works for ordinary Americans - and redirect it to AI contracts that Elon Musk will benefit from, Starlink and SpaceX contracts that he will benefit from, so he can pay off the massive loan he took out to buy twitter?
Go after renewable energy SPECIFICALLY, freeze a program that passed with bipartisan support (the inflation reduction act) where 78% of the budget would have gone to Republican states whose voters feel they are not getting their fair share of federal money?
From Paul Krugman:

The Expendables are the means-tested programs outside of social security and Medicare that go to Americans in need, like food stamps, disability payments, Medicaid, and section 8 housing.
Eventually go after these popular and necessary programs - where the actual money is - so that money can be diverted to the 26 billion (estimated) deportation project and a 4.5 trillion dollar tax cut for the wealthy?
And in the meantime, gut education, strip mine public parks, abandon protections for clean air and water - contribute to global climate change!
Gut public health and health research, criminalize accurate reporting by the CDC, create a situation where the US could be the incubator for the next worldwide pandemic?
Loosen up banking regulations just as we're reaching the top of a manic financial hype cycle, so we can crash the economy again like we did in 2008 - this time with Trump et. al. in charge to handle the fallout?
Fund far-right authoritarian groups around the globe, pressure European countries to allow "free speech" (hate speech) against the interests of the people living in those countries, foment a global backlash against immigration FROM the countries that will be hit hardest by climate change, TO the countries that are largely responsible for climate change to begin with?
And blame everything that goes wrong on 'DEI' which means hiring or promoting anyone who isn't a white Christian male.
Like really. Really really. Every crazy Senate confirmation went through. Republican senators are begging trump for special exemptions from Trump's chaotic spending cuts that hurt their own constituents, they are kissing the ring exactly as Pritzer describes, and for what? Trump is only loyal to himself and - maybe - the people who put him back into power - that is, Elon Musk and the Heritage Foundation - NOT the Republican voters who will be materially hurt by his policies and only have Hate to show for it.
We aren't headed towards authoritarianism, we are already halfway there.
The Supreme Court hasn't ruled yet on any of Trump's acts of executive overreach, but the first of the funding freeze cases will reach them this week. Mass public pressure is so important right now.
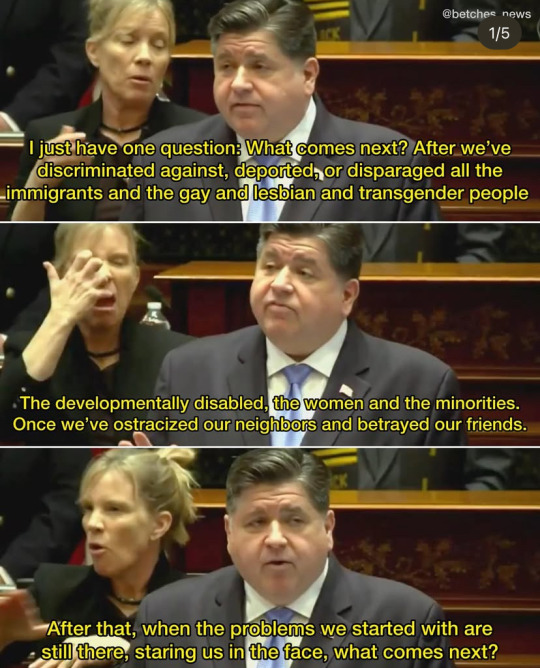

There are people – some in my own Party – who think that if you just give Donald Trump everything he wants, he’ll make an exception and spare you some of the harm. I’ll ignore the moral abdication of that position for just a second to say — almost none of those people have the experience with this President that I do. I once swallowed my pride to offer him what he values most — public praise on the Sunday news shows — in return for ventilators and N95 masks during the worst of the pandemic. We made a deal. And it turns out his promises were as broken as the BIPAP machines he sent us instead of ventilators. Going along to get along does not work – just ask the Trump-fearing red state Governors who are dealing with the same cuts that we are. I won’t be fooled twice.
I’ve been reflecting, these past four weeks, on two important parts of my life: my work helping to build the Illinois Holocaust Museum and the two times I’ve had the privilege of reciting the oath of office for Illinois Governor.
As some of you know, Skokie, Illinois once had one of the largest populations of Holocaust survivors anywhere in the world. In 1978, Nazis decided they wanted to march there.
The leaders of that march knew that the images of Swastika clad young men goose stepping down a peaceful suburban street would terrorize the local Jewish population – so many of whom had never recovered from their time in German concentration camps.
The prospect of that march sparked a legal fight that went all the way to the Supreme Court. It was a Jewish lawyer from the ACLU who argued the case for the Nazis – contending that even the most hateful of speech was protected under the first amendment.
As an American and a Jew, I find it difficult to resolve my feelings around that Supreme Court case – but I am grateful that the prospect of Nazis marching in their streets spurred the survivors and other Skokie residents to act. They joined together to form the Holocaust Memorial Foundation and built the first Illinois Holocaust Museum in a storefront in 1981 – a small but important forerunner to the one I helped build thirty years later.
I do not invoke the specter of Nazis lightly. But I know the history intimately — and have spent more time than probably anyone in this room with people who survived the Holocaust. Here’s what I’ve learned – the root that tears apart your house’s foundation begins as a seed – a seed of distrust and hate and blame.
The seed that grew into a dictatorship in Europe a lifetime ago didn’t arrive overnight. It started with everyday Germans mad about inflation and looking for someone to blame.
I’m watching with a foreboding dread what is happening in our country right now. A president who watches a plane go down in the Potomac – and suggests — without facts or findings — that a diversity hire is responsible for the crash. Or the Missouri Attorney General who just sued Starbucks – arguing that consumers pay higher prices for their coffee because the baristas are too “female” and “nonwhite.” The authoritarian playbook is laid bare here: They point to a group of people who don’t look like you and tell you to blame them for your problems.
I just have one question: What comes next? After we’ve discriminated against, deported or disparaged all the immigrants and the gay and lesbian and transgender people, the developmentally disabled, the women and the minorities – once we’ve ostracized our neighbors and betrayed our friends – After that, when the problems we started with are still there staring us in the face – what comes next.
All the atrocities of human history lurk in the answer to that question. And if we don’t want to repeat history – then for God’s sake in this moment we better be strong enough to learn from it.
I swore the following oath on Abraham Lincoln’s Bible: “I do solemnly swear that I will support the constitution of the United States, and the constitution of the state of Illinois, and that I will faithfully discharge the duties of the office of Governor .... according to the best of my ability.
My oath is to the Constitution of our state and of our country. We don’t have kings in America – and I don’t intend to bend the knee to one. I am not speaking up in service to my ambitions — but in deference to my obligations.
If you think I’m overreacting and sounding the alarm too soon, consider this:
It took the Nazis one month, three weeks, two days, eight hours and 40 minutes to dismantle a constitutional republic. All I’m saying is when the five-alarm fire starts to burn, every good person better be ready to man a post with a bucket of water if you want to stop it from raging out of control.
Those Illinois Nazis did end up holding their march in 1978 – just not in Skokie. After all the blowback from the case, they decided to march in Chicago instead. Only twenty of them showed up. But 2000 people came to counter protest. The Chicago Tribune reported that day that the “rally sputtered to an unspectacular end after ten minutes.” It was Illinoisans who smothered those embers before they could burn into a flame.
Tyranny requires your fear and your silence and your compliance. Democracy requires your courage. So gather your justice and humanity, Illinois, and do not let the “tragic spirit of despair” overcome us when our country needs us the most.
Sources:
• NBC Chicago & J.B. Pritzker, Democratic governor of Illinois, State of the State address 2025: Watch speech here | Full text
• Betches News on Instagram (screencaps)
#us politics#great speech and more people need to speak out#theres way too much complacency right now
90K notes
·
View notes
Text
Beyond the Campus: Unlocking Career Flexibility and Global Opportunities with Online Cybersecurity Programs
The landscape of professional development is constantly evolving, and perhaps nowhere is this more evident than in the dynamic field of cybersecurity. As threats become more sophisticated and the demand for skilled professionals skyrockets, individuals and organizations alike are seeking effective ways to acquire and enhance critical security expertise. While traditional, on-campus education has its merits, online cybersecurity programs have emerged as a powerful alternative, offering unparalleled flexibility, global reach, and practical applicability. These programs are not merely a convenient substitute; they are a strategic pathway for career advancement, designed to cater to the unique needs of a modern workforce. For those looking to enter or advance within this vital domain, "cyber security online programs" present a compelling and increasingly popular solution.
Adaptive Learning for Working Professionals
One of the most significant advantages of pursuing a cyber security online program is its inherent adaptability for individuals already deeply embedded in their careers. Unlike rigid traditional schedules that demand a complete reorientation of one's daily life, online programs are meticulously crafted to integrate seamlessly with existing professional and personal commitments. This means no more agonizing choices between career progression and education.
Imagine a cybersecurity analyst currently working full-time who wants to specialize in cloud security. An online program would allow them to access lectures, participate in discussions, and complete assignments at their own pace, whether that's late in the evening after work, during a lunch break, or on weekends. The emphasis on flexible schedules, self-paced modules, and asynchronous learning options is a game-changer. Students can delve into complex topics when their minds are freshest, rewind lectures for deeper understanding, and engage with course material without the pressure of a fixed, real-time classroom. This level of control empowers working professionals to upskill or reskill strategically, acquiring in-demand cybersecurity competencies without experiencing the career interruption or financial strain often associated with traditional, full-time study. It’s about fitting education into life, not the other way around.
Access to Diverse Global Faculty and Peers
The digital nature of online learning obliterates geographical boundaries, opening up a world of unparalleled intellectual exchange. When you enroll in a cyber security online program, your classroom extends far beyond local city limits. This translates into an extraordinary opportunity to learn from and collaborate with a truly global community.
Think about the caliber of instructors an online program can attract. Without the constraints of physical location, universities and educational providers can recruit leading cybersecurity experts from anywhere on the planet – individuals who are at the forefront of threat intelligence, digital forensics, network security, and policy development. This means gaining insights directly from professionals who are shaping the industry and addressing real-world challenges daily.
Equally impactful is the diversity of your peer group. Your classmates might hail from different continents, bringing with them unique professional experiences, cultural perspectives, and problem-solving approaches. Engaging in discussions with a peer who is tackling cybercrime in a different regulatory environment, or collaborating on a project with someone who has a deep understanding of a niche security framework, enriches the learning experience immeasurably. This broadens individual perspectives, challenges assumptions, and, crucially, helps build a robust global professional network – a resource that is invaluable in an interconnected field like cybersecurity and simply not achievable within a localized campus setting.
Direct Application of Learning to Current Roles
One of the most compelling aspects of pursuing a cyber security online program, particularly for those already employed, is the immediate and tangible applicability of the knowledge gained. This isn't theoretical learning that sits idle until graduation; it's practical education that can be put into action right away.
Consider a student learning about incident response protocols. Within days of covering the topic in their online course, they might encounter a suspicious activity alert at their workplace. The concepts, tools, and best practices discussed in their program can be directly applied to investigate, contain, and remediate the situation. This immediate feedback loop – applying new security concepts to current job functions in real-time – profoundly reinforces learning. It transforms abstract knowledge into practical skills, solidifying understanding and building confidence.
Furthermore, this direct application offers demonstrable value to employers. As students implement new security measures, optimize existing systems, or contribute to more robust defense strategies based on their ongoing education, they showcase immediate ROI. This not only benefits their organization by strengthening its security posture but also significantly bolsters their own professional standing, proving their commitment to continuous improvement and their ability to translate learning into tangible results.
Cost-Effectiveness and Reduced Barriers to Entry
Education is an investment, and for many, the financial implications of higher learning can be a significant hurdle. This is another area where "cyber security online programs" offer a distinct advantage, often presenting a more cost-effective pathway to high-quality education compared to traditional on-campus alternatives.
The most apparent savings come from the elimination or significant reduction of expenses typically associated with traditional schooling. There are no commuting costs to consider, no expensive campus housing fees, and often reduced or waived campus-specific fees that contribute to the overall sticker price of a degree. While tuition is still a factor, the ancillary costs that often inflate the total expenditure are largely absent. This affordability democratizes access to in-demand cybersecurity skills. It means that individuals who might have been excluded from pursuing higher education due to geographical constraints, family responsibilities, or financial limitations can now access top-tier training. By lowering these barriers to entry, online programs are not just providing an education; they are fostering a more diverse and inclusive cybersecurity workforce. This broadened access allows a wider demographic of talented individuals to enter a field desperately in need of skilled professionals, ultimately strengthening the collective defense against evolving cyber threats and creating a more robust and resilient digital future.
0 notes
Text
Unlocking Business Efficiency with Managed Services IT
In today's rapidly evolving technological landscape, businesses of all sizes are increasingly recognizing the importance of leveraging specialized IT solutions to stay competitive. One of the most effective ways to achieve this is through managed services IT, a strategic approach that allows organizations to delegate their IT responsibilities to expert service providers. This not only ensures the smooth functioning of IT infrastructure but also enables businesses to focus on their core competencies and growth strategies.
The Rise of Managed Services IT
The concept of managed services IT has gained significant traction over the past decade. Traditionally, companies managed their IT in-house, which often involved substantial investments in personnel, hardware, and software. However, with the complexities and rapid pace of technological change, many organizations found this approach both costly and inefficient. Managed services offered a compelling alternative by providing proactive management, monitoring, and support for IT systems through external vendors.
By outsourcing routine IT tasks and responsibilities, companies can benefit from expert guidance, advanced technology, and 24/7 support. This shift has been particularly advantageous for small and medium-sized enterprises (SMEs) that lack the resources to maintain an in-house IT team but still require robust, secure, and scalable IT solutions.
Benefits of Managed Services IT
One of the primary advantages of adopting managed services IT is cost savings. Organizations can reduce capital expenditures on hardware and software while converting these costs into predictable operational expenses. This financial flexibility allows businesses to allocate resources more effectively toward strategic initiatives.
Additionally, managed services IT providers offer proactive monitoring and maintenance, which significantly reduces downtime and minimizes security risks. With cyber threats becoming more sophisticated and frequent, having a dedicated team constantly overseeing cybersecurity measures is invaluable. Managed services providers also ensure compliance with industry regulations, safeguarding sensitive data and maintaining business continuity.
Furthermore, partnering with an experienced managed services provider grants access to the latest technological advancements without the need for substantial upfront investments. This ensures that organizations remain competitive and agile in the face of technological changes.
The Role of IT Outsourcing Services India
A noteworthy trend in the managed services domain is the rise of IT outsourcing services India. India has emerged as a global hub for IT outsourcing due to its highly skilled workforce, cost-effective solutions, and robust technological infrastructure. Many international companies collaborate with Indian service providers to leverage these advantages, resulting in high-quality managed services at a fraction of the cost compared to other regions.
IT outsourcing services India offer comprehensive managed service packages, including network management, cloud services, cybersecurity, data backup, and helpdesk support. Their expertise enables organizations to streamline operations, improve service levels, and reduce operational risks. Moreover, the time zone advantage allows for round-the-clock support, ensuring that issues are addressed promptly, minimizing any potential disruption.
Choosing the Right Managed Services Provider
Selecting the right managed services provider is crucial for maximizing the benefits of managed services IT. Organizations should evaluate providers based on their technical expertise, industry experience, service level agreements (SLAs), and customer references. A transparent and communicative partner will be better equipped to understand your unique business needs and tailor solutions accordingly.
It’s also essential to consider scalability and flexibility. As your business grows, your IT requirements may change, so your managed services partner should be capable of adapting to these evolving needs without significant disruptions.
Conclusion
In summary, managed services IT represent a strategic approach that empowers organizations to optimize their IT operations, enhance security, and reduce costs. The rise of IT outsourcing services India exemplifies how global partnerships can deliver high-quality, cost-effective solutions that drive business success. As technology continues to advance, embracing managed services will likely become an indispensable element of a forward-thinking, resilient business strategy. Whether you are a startup or an established enterprise, leveraging expert managed services can provide the competitive edge needed to thrive in today’s digital economy.
0 notes
Text
In early February, Musk’s team laid off 130 staffers at the Cybersecurity and Infrastructure Security Agency, or CISA, including 10 regional security specialists who worked with local and state election officials. The Trump administration is also advancing plans to strip civil service protections from 80% of the remaining CISA workforce, potentially allowing them to be fired for political reasons. Attorney General Pam Bondi that month disbanded a key FBI task force charged with investigating foreign efforts to influence elections. She also left in the wind the fate of another FBI task force that investigated threats against election workers and polling places.
More layoffs, we knew this was happening. He does not trust the current system, I'm not sure I do, so he is dismantling what's in place so it can be restructured and not federally funded/contributing to the federal deficit in the meantime.
Homeland Security chief Kristi Noem, meanwhile, on March 6 canceled the funding for national information sharing efforts that helped state and local election officials detect and ward off coordinated hacking attacks and other threats.
This does not mean another system will not be implemented, we are just jumping the gun and assuming the worst, specifically a cyber attack when there is not even an upcoming election or primary to raise concerns at the moment.
Those moves come as Trump has appointed to key positions officials who embrace his false claims of widespread voting fraud, including Bondi, Noem and FBI Director Kash Patel, among others – and as Trump has cashiered the head of the National Security Agency and the US Cyber Command, Gen. Timothy Haugh, who was involved in countering Russian interference in past elections.
Allegedly there was still foreign interference this past election, so Haugh was obviously incompetent. How confident are we that Trump's claims are false if so many people seem to see reason in what he alleges?
Trump officials argue that some of the election security agencies targeted for cuts were improperly hurting the president’s allies. During her confirmation hearing in January, Noem said that CISA has “gotten far off mission” in trying to combat foreign disinformation. She pledged to help “rein in” the agency, which critics say pushed social media companies to target conservative commentators. Bondi said disbanding the Foreign Influence Task Force was necessary to end the “risk of further weaponization … of prosecutorial discretion.”
Are we sure they haven't perhaps gone off mission? These systems have been in place and there is still alleged Russian interference EVERY single election.
I didn't vote for Trump, but I also happen to think it was BS how the Democrats tried to rush and prosecute him to disqualify him from running this election rather than just let him run.
It was absolutely politically motivated and there should be protections put in place to prevent that from being weaponized against all future candidates, democrats included.
It's part of the reason I didn't vote for a democrat either this election, it's suspicious behavior.
But the administration’s actions have deeply alarmed state officials, who warn the next round of national elections will be seriously imperiled by the cuts. A bipartisan association representing 46 secretaries of state, and several individual top state election officials, have pressed the White House about how critical functions protecting election security will perform going forward. They have not received clear answers, according to documents shared with CNN.
TL:DR People on both sides are panicked because they didn't get an immediate answer to calm their concerns, which for some reason has made them assume the worst and that there is no plan going forward.
Trump has justified his efforts to exert more control over America’s state and local election systems as a way of stopping illegal voting by noncitizens and other voter fraud, both of which experts say are rare.
Ok? Let him address this concern of his now and then it shouldn't keep coming up. If you found it annoying, let him take care of it and he'll have nothing left to annoy you about.
Officials involved in administering elections say the moves already are making it harder, and less safe and secure, to vote in America.
If you're that afraid don't vote, I don't see that happening though.
“It’s absolutely hypocritical,” said Sen. Alex Padilla, a Democrat and former secretary of state of California, “for a president who has lied ad nauseam about rampant voter fraud to be undoing the very tools we rely on to protect the integrity and security of our elections.”
It's not, one would have to dismantle the current systems if there's any hope of getting congress or supreme court to put anything new in place. They would likely not otherwise.
Article because that link directs to nothing relevant:

1K notes
·
View notes