#eclipse proxy setup
Explore tagged Tumblr posts
Text
Oshi No Ko Chapter 165 - My Thoughts/Analysis
Last chapter before the end. Let’s get this over with.
The first panel immediately undercuts Aqua’s sacrifice by having Nino squeal. Incredible.
One could say that this entire sequence of events was caused by Hikaru’s death but that feels too much like giving the manga credit for presenting this slideshow of events without giving everything time to breathe. Even if Hikaru wasn’t suspected of being a part of this murder scheme it wouldn’t be difficult for Aqua and company to hire a bodyguard to protect her from any murder attempts since Hikaru mainly kills through proxies. Perhaps hire a private investigator to catch him in the act. Or, you know. Just kill Hikaru through indirect means. Break into his apartment and poison his food and water.
And now we see Hikaru’s chain of murders. Can we finally bang that in people’s heads that this fucker is a murderer? Because people of all stripes seem to think otherwise despite the narrative spelling it out for them more times than I can count. As much as I dislike how the narrative has handled Hikaru’s character, trying to deny the facts presented front and center is worse than this slop being churned out. One can critique the way Hikaru was handled before these past few chapters in any number of ways—but to deny that Hikaru isn’t a murderer at this point is just laughable.
It’s now time for our weekly slideshow presentation with Akane as a narrator! You know, she’s already eclipsed Crow Girl in terms of infodumping. Why not? Why the fuck not just lay it all out to the audience instead of telling these important plot events organically. Surely this is a good decision to make after a series of already bad decisions.
Aqua didn’t even write a fucking letter to everyone he left behind. Incredible. It would be simple enough to give them to a proxy to deliver them to the people he cared about but of course he didn’t think of that. I don’t even think the authors even thought about it.
It’s the funeral. I can’t help but feel for Miyako here, having to bury both Aqua and Ai. And then we fucking see Aqua’s body. Ho boy. Dashes any hopes that he’s actually alive, huh. I’d say that this entire scene is sad but that's a lie. Aqua’s death didn’t have the narrative strength, the thematic connection, the sheer setup for this to be a sad scene. It did not earn the right to claim that sort of emotion when everything here and in the last few chapters felt like someone reading off a script of an infomine rather than a series of events happening in a manga.
Oh my god Kana you fucking idiot. And thank you Miyako! Good on you to not fucking allow her bad behavior to stand. And Kana’s mental breakdown at Aqua is—again, I don’t really care. It’s supposed to be sad and all but she didn’t even understand Aqua to the end. She never saw Aqua for who he truly was or his revenge plot. She didn’t even know that he killed Hikaru and then himself. Even if she loved Aqua, she loved the mask that he wore rather than the person underneath it.
People screaming about character assassination and how the author ruined Kana’s character in this chapter really don’t grasp one of the biggest flaws with Kana as a person—that is, she lacks the self awareness that her actions can cause other people to react—and react badly.
We see this in her sharp tongue and scathing remarks. We see this in her harsh words to Ruby during the movie arc. Hell, we see this best illustrated in the Scandal arc where she tried to pursue ShimaD and caused everyone involved a great deal of heartache. While she may have had good and even understandable feelings, that doesn’t make her any less of a piece of shit when she does them. I’d be glad that the narrative is finally giving her some goddamn consequences but at this point even the idea of Kana reaping said consequences doesn’t stir up any emotion in me. If you’ve left even the people who heavily dislike a character going “can we just get this over with” when said character gets their just deserts and suffers because of her own actions then you’ve REALLY done something wrong.
And everyone else is just a slideshow. We don’t get to see how they react or their feelings in exchange for a Kana temper tantrum. Thanks for that. I’m sure that Taiki’s feelings about his half-brother dying aren’t relevant. Or Mem’s. Or Miyako’s. God, what a fucking travesty.
Looks like we don’t be seeing Ruby this chapter if one of those panels is to go by. I would not be surprised if she followed Aqua to death at this point. There’s been nothing to indicate that she wouldn’t, after all. The girl who recklessly ran to kill Hikaru has had her most important person die on her AGAIN. What has she to live for now?
Oh, it’s Gotanda and Kaburagi. In all the bullshit I’d forgotten about the movie. It feels so much like an afterthought that it’s laughable. All that buildup and we don’t even get to see it.
The movie was a large hit. I heard it was the sixth most viewed movie this year. That’s so funny. Even after everything it couldn’t even reach the top of the charts. I’d say that it’s thematic but giving this series credit is like giving credit to a toddler for managing to open a jar. Sure, you could do it once, but I doubt you’d be able to do it again without making a mess of everything.
Akane narrating that Ruby hasn’t even left the house. And then her with dual black stars…and then undercut again by the white star. Are you fucking kidding me. Are you fucking kidding me. The narrative is giving us NOTHING to signify this change in her behavior. After she lost Goro the first time Ruby fucking collapsed into her own revenge plot and it was only Aqua that saved her from it. And now you’re telling us that she managed to hold herself up here after his death without any outside interference? I’ve met flat earthers that could parrot off more persuasive arguments.
If Ruby was given any time in the spotlight to flesh out her character more this MAY have been more palpable but as it stands it’s just…I don’t even want to rip it apart because it really is just deplorable. It doesn’t even feel satisfying to do so anymore. Often when I critique a series for its flaws it makes me appreciate all its other GOOD aspects but for these recent batch of chapters I’m even struggling to find things that are decent about it.
There’s no use analyzing a pile of shit in an attempt to make it look worse or better than it actually is. It’s a pile of shit. And so is this manga.
Next chapter is the last one. There is absolutely no way that we’re going to get a palpable ending to this clusterfuck and I’m very much reminded why I don’t usually get into media that are still ongoing. What an utter travesty.
#oshi no ko#onk#oshi no ko 165#onk 165#onk meta#oshi no ko spoilers#onk spoilers#writing this analysis while the US elections were going on certainly were a trip#idk which was more dissapointing
9 notes
·
View notes
Text
How to configure proxy in Eclipse
How to configure proxy in Eclipse
If you are behind a proxy and want Eclipse to connect to internet for some plugins like STS(Spring Tool Suite), follow the following steps : In Eclipse menu bar, go to Window -> Preference. Select General -> Network Preferences. Switch the provider to “manual” and update the HTTP and HTTPS entries for the proxy host and port. Provide user id & pwd if you need to authenticate to use the proxy. You…
View On WordPress
0 notes
Text
A good database solution that gives database administrators and companies the confidence that their data remains replicated and backed up in more than one instance is a pure dream come true. It eclipses all of the fears, the panic and the the doubts that usually shroud them whenever the topic of data loss hovers over their cup of coffee. Digging in and scratching every surface on the internet, it is hard to pass the conspicuous words of “Galera Cluster” when you are literally scouring for a highly available database solution for your deployment. Thanks to the overpowering magic of curiosty, we had to stretch our hands, grab “Galera Cluster” by the neck, pull it closer and take a better look at it. The result is this guide that goes in head first to deploy and proxy requests to the cluster using ProxySQL. So you might be asking, “What is Galera Cluster?”. This is just for you. Let us begin with the word cluster so that everything becomes much clearer. A cluster is a group of servers that work together to achieve a common goal or objective. In this context, a cluster will be a group of three or more servers that will be working together as a complete database solution that clients can write, edit, query and fetch data. Now we are ready to roll. Galera Cluster is a synchronous multi-master database cluster, based on synchronous replication and MySQL and InnoDB. Synchronous means that nodes(servers) keep all replicas synchronized(the same time as one another) by updating all replicas in a single transaction. Galera is an easy-to-use, high-availability solution, which provides high system up-time, no data loss and scalability for future growth. World’s Most Advanced Features and Un-Seen Benefits of Galera Cluster True Multi-master, Active-Active Cluster Read and write to any node at any time. Synchronous Replication No slave lag, no data is lost at node crash. Tightly Coupled All nodes hold the same state. No diverged data between nodes allowed. Multi-threaded Slave For better performance. For any workload. No Master-Slave Failover Operations or Use of VIP. Hot Standby No downtime during failover (since there is no failover). Automatic Node Provisioning No need to manually back up the database and copy it to the new node. Supports InnoDB. Transparent to Applications Required no (or minimal changes) to the application. No Read and Write Splitting Needed. Easy to Use and Deploy Later in the guide, we shall add ProxySQL which is a MySQL proxy server that is used as a bridge between the Galera cluster and the client applications trying to access (write, query, fetch) the database cluster. Setup Pre-requisites We assume that you have the following before we proceed Access to two or more hosts with sudo rights. Ansible host Public ssh key copied to your hosts Step 1: Copy your public keys to the hosts To copy your keys to the hosts, create a file like “list_of_servers“, and key in your IP hosts therein then you can create a script that will do the work for you. $ vim list_of_servers 192.168.20.11 192.168.20.12 192.168.20.13 Then create the bash script $ vim copy_ssh_keys.sh #!/bin/sh username="root" # Set remote servers ssh username for ip in `cat list_of_servers`; do ssh-copy-id -i ~/.ssh/id_rsa.pub $username@$ip done Make the script executable chmod +x copy_ssh_keys.sh Then run it. Sample output is provided. Simply enter the password for the users. $ ./copy_ssh_keys.sh /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/tech/.ssh/id_rsa.pub" /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: WARNING: All keys were skipped because they already exist on the remote system. (if you think this is a mistake, you may want to use -f option) /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/tech/.ssh/id_rsa.pub" /usr/bin/ssh-copy-id:
INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: WARNING: All keys were skipped because they already exist on the remote system. (if you think this is a mistake, you may want to use -f option) /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/tech/.ssh/id_rsa.pub" The authenticity of host '192.168.20.11 (192.168.20.11)' can't be established. ECDSA key fingerprint is SHA256:daMKa1FL3+miBpGer95yq54f0//GOcNhSlb5FnTEPP8. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys [email protected]'s password: Number of key(s) added: 1 Now try logging into the machine, with: "ssh '192.168.20.11'" and check to make sure that only the key(s) you wanted were added. Step 2: Create a role that will install mariadb and more in all of the servers In this step we will leverage the power of ansible to install all of the packages we need to proceed. In addition to that, we will update each of the servers “/etc/hosts” file with the hosts we need. Install ansible: # Debian / Ubuntu sudo apt update sudo apt install ansible python3-pip sudo pip3 install pymysql # Fedora sudo dnf install ansible python3-pip sudo pip3 install pymysql # CentOS / Rocky Linux sudo yum -y install epel-release sudo yum -y install ansible python3-pip sudo pip3 install pymysql After the role runs, most of the work remaining will be to just configure them which we shall do manually. $ ansible-galaxy init install-mariadb - Role install-mariadb was created successfully The above command will create a directory called “install-mariadb” with the structure shown below. $ tree install-mariadb install-mariadb ├── README.md ├── defaults │ └── main.yml ├── files ├── handlers │ └── main.yml ├── meta │ └── main.yml ├── tasks │ └── main.yml ├── templates ├── tests │ ├── inventory │ └── test.yml └── vars └── main.yml After that, update “main.yml” file in tasks directory within the new “install-mariadb” directory created by the command above. $ vim install-mariadb/tasks/main.yml --- - name: Insert hostnames config blockinfile: path: /etc/hosts block: | 192.168.20.11 db1.computingforgeeks.com db1 192.168.20.12 db2.computingforgeeks.com db2 192.168.20.13 db3.computingforgeeks.com db3 backup: yes - name: Install prerequisites apt: name= item update_cache=yes state=latest force_apt_get=yes loop: [ 'aptitude','python3','python3-pip'] #Install MariaDB server and other packages - name: Install MariaDB Packages apt: name= item update_cache=yes state=latest loop: [ 'mariadb-server','python3-pymysql', 'mariadb-client', 'vim', 'sudo'] # Start MariaDB Service - name: Start MariaDB service service: name: mariadb state: started become: true # MariaDB Configuration - name: Sets the root password mysql_user: name: root password: " mysql_root_password " login_user: " mysql_user " state: present login_unix_socket: /var/run/mysqld/mysqld.sock - name: Removes all anonymous user accounts mysql_user: name: '' host_all: yes state: absent login_user: root login_password: " mysql_root_password " - name: Removes the MySQL test database mysql_db: name: test state: absent login_user: root login_password: " mysql_root_password " Add variables used in the tasks file $ vim install-mariadb/vars/main.yml # vars file for install-mariadb mysql_root_password: "StrongPassword" mysql_user: "root" disable_default: true username: devops Our role is now ready. What remains is to add the hosts to the inventory then create a playbook that calls out our role.
Open the default location of your inventory file and add the hosts as follows: $ vim hosts [galera] 192.168.20.11 192.168.20.12 192.168.20.13 Create a playbook that is similar to the following. Ensure that the playbook file is one directory outside your role directory. $ vim playbook.yaml --- - hosts: galera become: yes become_user: root become_method: sudo roles: - install-mariadb Then run ansible to install our packages and configure our servers. Enter the root password for the hosts when prompted $ ansible-playbook -i hosts --become --user=tech --become-user=root --become-method=sudo --ask-become-pass -v playbook.yaml -e 'ansible_python_interpreter=/usr/bin/python3' Using /etc/ansible/ansible.cfg as config file BECOME password: Replace tech username with server’s login username Step 3: Configure Galera Cluster The next step is to configure galera cluster on the three MariaDB hosts we have. Comment the bind line on the file /etc/mysql/mariadb.conf.d/50-server.cnf which binds MariaDB service to 127.0.0.1. We want all of them to collaborate with others in the cluster. Configure on all nodes: $ sudo vim /etc/mysql/mariadb.conf.d/50-server.cnf #bind-address = 127.0.0.1 Once we are sure that our nodes are not bound to localhost, we can now comfortably configure them as follows: Let us Configure Node 1 Add the following content to the MariaDB configuration file. Remember to modify the hostname at “wsrep_node_address” to the hostname or IP of your first host. $ sudo vim /etc/mysql/mariadb.conf.d/galera.cnf [galera] wsrep_on = ON wsrep_cluster_name = "MariaDB Galera Cluster" wsrep_provider = /usr/lib/galera/libgalera_smm.so wsrep_cluster_address = "gcomm://" binlog_format = row default_storage_engine = InnoDB innodb_autoinc_lock_mode = 2 bind-address = 0.0.0.0 wsrep_node_address="db1" Initialize galera cluster and restart MariaDB sudo galera_new_cluster sudo systemctl restart mariadb Let us Configure Node 2: Create and modify Database configuration for node 2: $ sudo vim /etc/mysql/mariadb.conf.d/galera.cnf [galera] wsrep_on = ON wsrep_cluster_name = "MariaDB Galera Cluster" wsrep_provider = /usr/lib/galera/libgalera_smm.so wsrep_cluster_address = "gcomm://db1,db2,db3" binlog_format = row default_storage_engine = InnoDB innodb_autoinc_lock_mode = 2 bind-address = 0.0.0.0 wsrep_node_address="db2" Let us Configure Node 3: Open the same file as the others above and update it with the following configuration. $ sudo vim /etc/mysql/mariadb.conf.d/galera.cnf [galera] wsrep_on = ON wsrep_cluster_name = "MariaDB Galera Cluster" wsrep_provider = /usr/lib/galera/libgalera_smm.so wsrep_cluster_address = "gcomm://db1,db2,db3" binlog_format = row default_storage_engine = InnoDB innodb_autoinc_lock_mode = 2 bind-address = 0.0.0.0 wsrep_node_address="db3" Restart MariaDB service on node2 and node3 sudo systemctl restart mariadb Step 4: Validate Galera Settings Login to any of the three nodes as the root user, then confirm that the cluster settings are alright. $ mysql -u root -p Enter password: Welcome to the MariaDB monitor. Commands end with ; or \g. Your MariaDB connection id is 11 Server version: 10.5.12-MariaDB-0+deb11u1 Debian 11 Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others. MariaDB [(none)]> Check status MariaDB [(none)]> show status like 'wsrep_%'; +-------------------------------+------------------------------------------------------------------------------------------------------------------------------------------------+ | Variable_name | Value | +-------------------------------+-------------------------------------------------------------------------------------------------------------------------
-----------------------+ | wsrep_local_state_uuid | 6f0406d3-3295-11ec-8446-770e11038a6f | | wsrep_protocol_version | 10 | | wsrep_last_committed | 3 | | wsrep_replicated | 0 | | wsrep_replicated_bytes | 0 | | wsrep_repl_keys | 0 | | wsrep_repl_keys_bytes | 0 | | wsrep_repl_data_bytes | 0 | | wsrep_repl_other_bytes | 0 | | wsrep_received | 3 | | wsrep_received_bytes | 264 | | wsrep_local_commits | 0 | | wsrep_local_cert_failures | 0 | | wsrep_local_replays | 0 | | wsrep_local_send_queue | 0 | | wsrep_local_send_queue_max | 1 | | wsrep_local_send_queue_min | 0 | | wsrep_local_send_queue_avg | 0 | | wsrep_local_recv_queue | 0 | | wsrep_local_recv_queue_max | 1 | | wsrep_local_recv_queue_min | 0 | | wsrep_local_recv_queue_avg | 0 | | wsrep_local_cached_downto
| 3 | | wsrep_flow_control_paused_ns | 0 | | wsrep_flow_control_paused | 0 | | wsrep_flow_control_sent | 0 | | wsrep_flow_control_recv | 0 | | wsrep_flow_control_active | false | | wsrep_flow_control_requested | false | | wsrep_cert_deps_distance | 0 | | wsrep_apply_oooe | 0 | | wsrep_apply_oool | 0 | | wsrep_apply_window | 0 | | wsrep_commit_oooe | 0 | | wsrep_commit_oool | 0 | | wsrep_commit_window | 0 | | wsrep_local_state | 4 | | wsrep_local_state_comment | Synced | | wsrep_cert_index_size | 0 | | wsrep_causal_reads | 0 | | wsrep_cert_interval | 0 | | wsrep_open_transactions | 0 | | wsrep_open_connections | 0 | | wsrep_incoming_addresses | AUTO,AUTO,AUTO | | wsrep_cluster_weight | 3
| | wsrep_desync_count | 0 | | wsrep_evs_delayed | | | wsrep_evs_evict_list | | | wsrep_evs_repl_latency | 0.000596085/0.00133766/0.00240084/0.000607165/5 | | wsrep_evs_state | OPERATIONAL | | wsrep_gcomm_uuid | cdf9b4e6-3295-11ec-8cb6-f2ce576d6ccc | | wsrep_gmcast_segment | 0 | | wsrep_applier_thread_count | 1 | | wsrep_cluster_capabilities | | | wsrep_cluster_conf_id | 3 | | wsrep_cluster_size | 3 | | wsrep_cluster_state_uuid | 6f0406d3-3295-11ec-8446-770e11038a6f | | wsrep_cluster_status | Primary | | wsrep_connected | ON | | wsrep_local_bf_aborts | 0 | | wsrep_local_index | 2 | | wsrep_provider_capabilities | :MULTI_MASTER:CERTIFICATION:PARALLEL_APPLYING:TRX_REPLAY:ISOLATION:PAUSE:CAUSAL_READS:INCREMENTAL_WRITESET:UNORDERED:PREORDERED:STREAMING:NBO: | | wsrep_provider_name | Galera | | wsrep_provider_vendor | Codership Oy | | wsrep_provider_version | 4.9(rcece3ba2) | | wsrep_ready | ON | | wsrep_rollbacker_thread_count | 1 |
| wsrep_thread_count | 2 | +-------------------------------+------------------------------------------------------------------------------------------------------------------------------------------------+ 69 rows in set (0.002 sec) MariaDB [(none)]> Confirm that we have a cluster size of 3 under: wsrep_cluster_size 3 We can create a test database on any of the nodes and check its availability on the other nodes. root@db1:~# mysql -u root -p Enter password: Welcome to the MariaDB monitor. Commands end with ; or \g. Your MariaDB connection id is 11 Server version: 10.5.12-MariaDB-0+deb11u1 Debian 11 Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others. MariaDB [(none)]> create database demodb1; Query OK, 1 row affected (0.003 sec) Login to the other two nodes (db2 and db3) and check if the database was replicated to them. root@db2:~# mysql -u root -p Enter password: Welcome to the MariaDB monitor. Commands end with ; or \g. Your MariaDB connection id is 11 Server version: 10.5.12-MariaDB-0+deb11u1 Debian 11 Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others. MariaDB [(none)]> show databases; +--------------------+ | Database | +--------------------+ | demodb1 | | information_schema | | mysql | | performance_schema | +--------------------+ 4 rows in set (0.001 sec) Node 3 root@db3:~# mysql -u root -p Enter password: Welcome to the MariaDB monitor. Commands end with ; or \g. Your MariaDB connection id is 11 Server version: 10.5.12-MariaDB-0+deb11u1 Debian 11 Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others. MariaDB [(none)]> show databases; +--------------------+ | Database | +--------------------+ | demodb1 | | information_schema | | mysql | | performance_schema | +--------------------+ 4 rows in set (0.001 sec) This simple exercise has managed to confirm that the database created on db1 is replicated across the cluster. What a good feeling! Step 5: Install ProxySQL SQL Proxy server With a working Galera cluster, we need to setup a ProxySQL server that will distribute traffic to the three nodes equally. ProxySQL can run on the server that has the application or run as an independent server. This article will cover how to set it up on an independent Debian|Rocky | CentOS Linux host with the steps below: CentOS Add ProxySQL repo sudo tee /etc/yum.repos.d/proxysql.repo Since we are good advocators of good security practices, we shall change the default admin password by running the command below $ mysql -u admin -padmin -h 127.0.0.1 -P6032 --prompt='Admin> ' Admin> UPDATE global_variables SET variable_value='admin:StrongPassword' WHERE variable_name='admin-admin_credentials'; Query OK, 0 rows affected (0.01 sec) Ensure that StrongPassword is set to a wonderfully strong password. Now, ProxySQL configuration system consists of three layers: Memory – Altered when making modifications on the command-line Disk – used for persistent configuration changes Runtime – Used as the effective configuration for ProxySQL. This consequently means that the query above has only been written to memory. To make it persistent, we need to copy the configuration to runtime then save them to disk. To do that, the queries below come to the rescue aptly and perfectly: LOAD ADMIN VARIABLES TO RUNTIME; SAVE ADMIN VARIABLES TO DISK; Step 7: Configure Monitoring in Galera cluster For ProxySQL to know the health status of the nodes in the Galera Cluster, there has to be a way through which it communicates with them all. This means that ProxySQL has to connect to the nodes through a dedicated user. We will create a user on one of the MariaDB nodes. As we know now, the user will be replicated automatically through the cluster since the cluster is already up and running.
MariaDB [(none)]> CREATE USER 'monitor'@'%' IDENTIFIED BY 'StrongPassword'; MariaDB [(none)]> flush privileges; You are at liberty to use a good password that you prefer here. Step 8: Configure Monitoring In ProxySQL Configure ProxySQL admin to constantly monitor the backend nodes. Add the user credentials that we configured in the step above. Remember to modify the value for password to fit whatever you have used in the previous step. Admin> UPDATE global_variables SET variable_value='monitor' WHERE variable_name='mysql-monitor_username'; Query OK, 1 row affected (0.01 sec) Admin> UPDATE global_variables SET variable_value='StrongPassword' WHERE variable_name='mysql-monitor_password'; Query OK, 1 row affected (0.00 sec) Add the following monitoring parameters for intervals: Admin> UPDATE global_variables SET variable_value='2000' WHERE variable_name IN ('mysql-monitor_connect_interval','mysql-monitor_ping_interval','mysql-monitor_read_only_interval'); Query OK, 3 rows affected (0.00 sec) Confirm the variables we just configured in the above step: Admin> SELECT * FROM global_variables WHERE variable_name LIKE 'mysql-monitor_%'; +----------------------------------------------------------------------+----------------+ | variable_name | variable_value | +----------------------------------------------------------------------+----------------+ | mysql-monitor_enabled | true | | mysql-monitor_connect_timeout | 600 | | mysql-monitor_ping_max_failures | 3 | | mysql-monitor_ping_timeout | 1000 | | mysql-monitor_read_only_max_timeout_count | 3 | | mysql-monitor_replication_lag_interval | 10000 | | mysql-monitor_replication_lag_timeout | 1000 | | mysql-monitor_replication_lag_count | 1 | | mysql-monitor_groupreplication_healthcheck_interval | 5000 | | mysql-monitor_groupreplication_healthcheck_timeout | 800 | | mysql-monitor_groupreplication_healthcheck_max_timeout_count | 3 | | mysql-monitor_groupreplication_max_transactions_behind_count | 3 | | mysql-monitor_groupreplication_max_transactions_behind_for_read_only | 1 | | mysql-monitor_galera_healthcheck_interval | 5000 | | mysql-monitor_galera_healthcheck_timeout | 800 | | mysql-monitor_galera_healthcheck_max_timeout_count | 3 | | mysql-monitor_replication_lag_use_percona_heartbeat | | | mysql-monitor_query_interval | 60000 | | mysql-monitor_query_timeout | 100 | | mysql-monitor_slave_lag_when_null | 60 | | mysql-monitor_threads_min | 8 | | mysql-monitor_threads_max | 128 | | mysql-monitor_threads_queue_maxsize | 128 | | mysql-monitor_wait_timeout | true | | mysql-monitor_writer_is_also_reader | true | | mysql-monitor_username | monitor | | mysql-monitor_password | StrongPassword | | mysql-monitor_history | 600000 | | mysql-monitor_connect_interval | 2000 |
| mysql-monitor_ping_interval | 2000 | | mysql-monitor_read_only_interval | 2000 | | mysql-monitor_read_only_timeout | 500 | +----------------------------------------------------------------------+----------------+ 32 rows in set (0.00 sec) Changes made to the MySQL Monitor in table global_variables will be applied after executing the LOAD MYSQL VARIABLES TO RUNTIME statement. To persist the configuration changes across restarts the SAVE MYSQL VARIABLES TO DISK must also be executed. Admin> LOAD MYSQL VARIABLES TO RUNTIME; Query OK, 0 rows affected (0.00 sec) Admin> SAVE MYSQL VARIABLES TO DISK; Query OK, 140 rows affected (0.01 sec) Step 9: Add the Created Galera Cluster ProxySQL uses host groups to categorize the backend nodes. A host group is a set of nodes identified by a positive number e.g. 1 or 2. The purpose of having host groups is to help ProxySQL route queries to different sets of hosts using ProxySQL query routing. ProxySQL has the following logical host groups: Writers – these are MySQL nodes that can accept queries that can write/change data – Primary nodes. Readers – Nodes that can only accept read queries. They can be seen as slaves nodes. We will assign the following host group IDs to the above hostgroups: Writers: 1 Readers: 2 Writers are also readers by default. Configure the table “mysql_replication_hostgroup” in the main database and specify the reader and writer hostgroups. Admin> SHOW CREATE TABLE main.mysql_replication_hostgroups\G *************************** 1. row *************************** table: mysql_replication_hostgroups Create Table: CREATE TABLE mysql_replication_hostgroups ( writer_hostgroup INT CHECK (writer_hostgroup>=0) NOT NULL PRIMARY KEY, reader_hostgroup INT NOT NULL CHECK (reader_hostgroupwriter_hostgroup AND reader_hostgroup>=0), check_type VARCHAR CHECK (LOWER(check_type) IN ('read_only','innodb_read_only','super_read_only','read_only|innodb_read_only','read_only&innodb_read_only')) NOT NULL DEFAULT 'read_only', comment VARCHAR NOT NULL DEFAULT '', UNIQUE (reader_hostgroup)) 1 row in set (0.00 sec) Then add the hostgroups in the table Admin> INSERT INTO main.mysql_replication_hostgroups (writer_hostgroup,reader_hostgroup,comment) VALUES (1,2,'galera_cluster'); After that, add the Galera cluster nodes as follows: Admin> INSERT INTO main.mysql_servers(hostgroup_id,hostname,port) VALUES (1,'192.168.79.184',3306); Admin> INSERT INTO main.mysql_servers(hostgroup_id,hostname,port) VALUES (1,'192.168.78.69',3306); Admin> INSERT INTO main.mysql_servers(hostgroup_id,hostname,port) VALUES (1,'192.168.77.127',3306); Admin> LOAD MYSQL SERVERS TO RUNTIME Query OK, 0 rows affected (0.01 sec) Admin> SELECT * FROM mysql_servers; +--------------+----------------+------+-----------+--------+--------+-------------+-----------------+---------------------+---------+----------------+---------+ | hostgroup_id | hostname | port | gtid_port | status | weight | compression | max_connections | max_replication_lag | use_ssl | max_latency_ms | comment | +--------------+----------------+------+-----------+--------+--------+-------------+-----------------+---------------------+---------+----------------+---------+ | 1 | 192.168.79.184 | 3306 | 0 | ONLINE | 1 | 0 | 1000 | 0 | 0 | 0 | | | 1 | 192.168.78.69 | 3306 | 0 | ONLINE | 1 | 0 | 1000 | 0 | 0 | 0 | | | 1 | 192.168.77.127 | 3306 | 0 | ONLINE | 1 | 0 | 1000 | 0 | 0 | 0 | | +--------------+----------------+------+-----------+--------+--------+-------------+-----------------+---------------------+---------+----------------+---------+
3 rows in set (0.00 sec) Admin> SAVE MYSQL SERVERS TO DISK; Query OK, 0 rows affected (0.14 sec) Admin> SAVE MYSQL VARIABLES TO DISK; Query OK, 147 rows affected (0.04 sec) Save changes to disk; LOAD MYSQL VARIABLES TO RUNTIME; SAVE MYSQL VARIABLES TO DISK; Confirm that the servers are reachable: To enable the replication hostgroup load mysql_replication_hostgroups to runtime using the same LOAD command used for MySQL servers since LOAD MYSQL SERVERS TO RUNTIME processes both mysql_servers and mysql_replication_hostgroups tables. Admin> LOAD MYSQL SERVERS TO RUNTIME; Query OK, 0 rows affected (0.00 sec) Now run the queries Admin> SELECT * FROM monitor.mysql_server_connect_log ORDER BY time_start_us DESC LIMIT 3; +----------------+------+------------------+-------------------------+---------------+ | hostname | port | time_start_us | connect_success_time_us | connect_error | +----------------+------+------------------+-------------------------+---------------+ | 192.168.79.184 | 3306 | 1634852419531867 | 1252 | NULL | | 192.168.78.69 | 3306 | 1634852419509819 | 2931 | NULL | | 192.168.77.127 | 3306 | 1634852419487624 | 1821 | NULL | +----------------+------+------------------+-------------------------+---------------+ 3 rows in set (0.00 sec) Admin> SELECT * FROM monitor.mysql_server_ping_log ORDER BY time_start_us DESC LIMIT 3; +----------------+------+------------------+----------------------+------------+ | hostname | port | time_start_us | ping_success_time_us | ping_error | +----------------+------+------------------+----------------------+------------+ | 192.168.77.127 | 3306 | 1634852441520867 | 476 | NULL | | 192.168.79.184 | 3306 | 1634852441500600 | 768 | NULL | | 192.168.78.69 | 3306 | 1634852441480454 | 1834 | NULL | +----------------+------+------------------+----------------------+------------+ 3 rows in set (0.00 sec) Admin> SELECT * FROM mysql_servers; +--------------+----------------+------+-----------+--------+--------+-------------+-----------------+---------------------+---------+----------------+---------+ | hostgroup_id | hostname | port | gtid_port | status | weight | compression | max_connections | max_replication_lag | use_ssl | max_latency_ms | comment | +--------------+----------------+------+-----------+--------+--------+-------------+-----------------+---------------------+---------+----------------+---------+ | 1 | 192.168.79.184 | 3306 | 0 | ONLINE | 1 | 0 | 1000 | 0 | 0 | 0 | | | 1 | 192.168.78.69 | 3306 | 0 | ONLINE | 1 | 0 | 1000 | 0 | 0 | 0 | | | 1 | 192.168.77.127 | 3306 | 0 | ONLINE | 1 | 0 | 1000 | 0 | 0 | 0 | | +--------------+----------------+------+-----------+--------+--------+-------------+-----------------+---------------------+---------+----------------+---------+ 3 rows in set (0.00 sec) As a final step, persist the configuration to disk. Admin> SAVE MYSQL SERVERS TO DISK; Query OK, 0 rows affected (0.14 sec) Admin> SAVE MYSQL VARIABLES TO DISK; Query OK, 147 rows affected (0.04 sec) Step 10: Create MySQL users to connect via ProxySQL The last step is to create MySQL users that will be connecting to the cluster through the ProxySQL instance. Create remote user on Galera cluster To achieve this functionality, we have to create a MySQL user on one of the nodes on galera cluster that users will use to connect. Login to one of the hosts and create a database user as follows: MariaDB [(none)]> create user 'demouser'@'%' identified by 'StrongPassword'; Query OK, 0 rows affected (0.079 sec)
Assign the neccessary roles to the user, for exmple access to a certain database. MariaDB [(none)]> create database demodb; MariaDB [(none)]> grant all privileges on demodb.* to 'demouser'@'%' with grant option; MariaDB [(none)]> flush privileges; Create remote user on ProxySQL Admin This is done by adding entries in the “mysql_users” table in the main database. Admin> SHOW CREATE TABLE mysql_users\G *************************** 1. row *************************** table: mysql_users Create Table: CREATE TABLE mysql_users ( username VARCHAR NOT NULL, password VARCHAR, active INT CHECK (active IN (0,1)) NOT NULL DEFAULT 1, use_ssl INT CHECK (use_ssl IN (0,1)) NOT NULL DEFAULT 0, default_hostgroup INT NOT NULL DEFAULT 0, default_schema VARCHAR, schema_locked INT CHECK (schema_locked IN (0,1)) NOT NULL DEFAULT 0, transaction_persistent INT CHECK (transaction_persistent IN (0,1)) NOT NULL DEFAULT 1, fast_forward INT CHECK (fast_forward IN (0,1)) NOT NULL DEFAULT 0, backend INT CHECK (backend IN (0,1)) NOT NULL DEFAULT 1, frontend INT CHECK (frontend IN (0,1)) NOT NULL DEFAULT 1, max_connections INT CHECK (max_connections >=0) NOT NULL DEFAULT 10000, attributes VARCHAR CHECK (JSON_VALID(attributes) OR attributes = '') NOT NULL DEFAULT '', comment VARCHAR NOT NULL DEFAULT '', PRIMARY KEY (username, backend), UNIQUE (username, frontend)) 1 row in set (0.00 sec) The table is usually empty and users are added by modifying the table. You specify the username, password and default hostgroup. Admin> INSERT INTO mysql_users(username,password,default_hostgroup) VALUES ('demouser','StrongPassword',1); You can check if the user was updated: Admin> SELECT * FROM mysql_users; +----------+----------------+--------+---------+-------------------+----------------+---------------+------------------------+--------------+---------+----------+-----------------+------------+---------+ | username | password | active | use_ssl | default_hostgroup | default_schema | schema_locked | transaction_persistent | fast_forward | backend | frontend | max_connections | attributes | comment | +----------+----------------+--------+---------+-------------------+----------------+---------------+------------------------+--------------+---------+----------+-----------------+------------+---------+ | demouser | StrongPassword | 1 | 0 | 1 | NULL | 0 | 1 | 0 | 1 | 1 | 10000 | | | +----------+----------------+--------+---------+-------------------+----------------+---------------+------------------------+--------------+---------+----------+-----------------+------------+---------+ 1 row in set (0.00 sec) If everything is okay, save changes: LOAD MYSQL USERS TO RUNTIME; SAVE MYSQL USERS TO DISK; Step 11: Test if the user can connect ProxySQL client runs on port 6033. We can try connecting to the proxy client using the user we created on galera and proxysql. root@proxy:~# mysql -udemouser -h 127.0.0.1 -P6033 -p Enter password: Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 17 Server version: 5.5.30 (ProxySQL) Copyright (c) 2000, 2021, Oracle and/or its affiliates. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql> We can now try run queries on the cluster. mysql> show databases; +--------------------+ | Database | +--------------------+ | demodb | | information_schema | +--------------------+ 2 rows in set (0.00 sec) mysql> select @@hostname; +------------+ | @@hostname | +------------+ | db3 | +------------+ 1 row in set (0.00 sec) mysql> Other queries $ mysql -u demouser -p demodb -h 127.0.0.1 -P6033 -e"SELECT @@port"
Enter password: +--------+ | @@port | +--------+ | 3306 | +--------+ mysql> As you can attest, we now have visibility on demodb a database we had assigned the rights to in the galera setup. We can also confirm that we are getting the responses from db3 of the galera cluster. Celebratory Remarks Our highly available cluster is now set up and ready for your applications to start pouring in torrents of data. You can add more nodes in your cluster as you deem fit and we hope that it will work best for you and afford you time to focus on other things. We hope the guide was detailed and clear and it helped you set up your environment. We that your visitation, your readership and your awesome support. Keep at it!!
0 notes
Text
300+ TOP HIBERNATE Interview Questions and Answers
HIBERNATE Interview Questions for freshers experienced :-
1. What are the benefits of ORM tool? ORM is helpful in automatically generating keys, managing transaction, hiding SQL queries details, and developing applications in quick manner. 2. Provide the list of collection types in Hibernate? Set, Map, Bag, List and Array are the different types of collections in Hibernate 3. What are the two cache types in Hibernate? First level cache and Secondary level cache are the types of cache in Hibernate. 4. What is session interface? Hibernate session which performs database entities manipulation is represented by session interface. Activities carried on by session interface are handling persistence phases, retrieving the persisted ones, and transaction separations management. 5. List out the core interfaces available in Hibernate? Criteria, Transaction, Session Factory, Query, Configuration, and Session are the core interfaces available in Hibernate. 6. Describe the steps to create database application using Hibernate? Steps to create Database application using Hibernate: Write the Java object Create a mapping file. This displays the relationship between the database and attributes. Deploy the Hibernate API to store persistent objects. 7. Provide the list of Hibernate support databases? HSQL, MySQL, FrontBase, Informix Dynamic Server, DB2, Sybase SQL Server, Oracle, and PostgreSQL are the Hibernate support databases. 8. What are the two (2) components available in Hibernate configuration object? Class Mapping Setup and Database Connection are the two (2) components of Hibernate configuration object. 9. What is the syntax to create SQL query in Hibernate? The syntax to create SQL query in Hibernate is “Session.createQuery”. 10. What is the syntax to add criteria to the SQL query? The syntax to create criteria to the SQL query is “Session.createCriteria”.

HIBERNATE Interview Questions 11. Do you think the extension ‘.hbm.xml’ is mandatory for all the hibernate mapping file to work properly? No, the extension ‘.hbm.xml’ is not mandatory for all the hibernate mapping file as it is just a convention. 12. What is POJOs? POJO stands for Plain Old Java Objects. These are java beans which has proper setter and getter methods for every property. Instead of Java classes, the usage of POJOs leads to a well-constructed and effective code. 13. List out the advantages of Hibernate template? Hibernate template is useful is automating the exception handling and session closing. Also, you can have a simplified communication with hibernate session. 14. What is session.save() in hibernate? The method session.save() is used to save a record when it is unique with its related primary key. If the primary key is already existing in the table, this method will not allow to insert. 15. Explain saveOrUpdate() in hibernate? The method saveOrUpdate() method is helpful in inserting a new record when the primary key is unique. If the primary key is already existing in the table, this method will update the record. 16. What is the syntax to retrieve hibernate statistics? Use the syntax “SessionFactory.getStatistics()” to retrieve the hibernate statistics. 17. Provide the list of ORM levels available in Hibernate? Medium Object Mapping, Pure Relational, Full Object Mapping and Light Object Mapping are the ORM levels available in Hibernate. 18. Provide the mapping associations utilized in Hibernate? One-to-One Association and Many-to-Many Association are the two (2) mapping associations utilized in Hibernate. 19. What are the different methods to fetch objects from database in Hibernate? In Hibernate, you can use Criteria API, HQL, Standard SQL, and Identifier to fetch objects from database. 20. In Hibernate, what is the method to reattach the detached objects? Use the method “session.merge()” to attach the detached objects. 21. To disable second level cache in Hibernate, what are the different methods? To disable second level cache in Hibernate, you can perform any of the following: Use CACHEMODE.IGNORE Set “use_second_level_cache” to false Make use of cache provider as “cache provider as org.hibernate.cache.NoCacheProvider” 22. In Hibernate, which is the default transaction factory? The default transaction factory with Hibernate 3.2 is JDBCTransactionFactory. 23. Provide the fetching strategies available in Hibernate? Batch Fetching, Sub-select Fetching, Join Fetching, and Select Fetching are the fetching strategies available in Hibernate. 24. Explain the benefit of version property in Hibernate? To recognize whether an object is in detached or transient state, version property in Hibernate. 25. Do you think polymorphism is supported by Hibernate? Yes, hibernate purely and completely supports polymorphism. 26. List out the three (3) inheritance models available in Hibernate? Table per class hierarchy, Table per sub-class, and Tables Per Concrete Class are the three (3) inheritance models available in Hibernate. 27. What is transaction management? To manage a set of commands or statement, transaction management is used in Hibernate. 28. What is callback interface in Hibernate? To obtain even notifications from objects, hibernate callback interfaces are used. Say, for example, an even gets generated when an object is deleted or loaded, and callback interfaces send a notification. 29. Provide the various other ORM frameworks in Hibernate? The other ORM frameworks in Hibernate are TopLink and EJB from Oracle. 30. List out few Java-based frameworks which is supporting hibernate integration? Eclipse plug-ins, XDoclet Spring, Maven, and J2EE are the java-based frameworks which are supporting hibernate integration. 31. List out a few properties required to database configuration in standalone condition? hibernate.connection.url, hibernate.connection.pool_size, hibernate.connection.password, hibernate.connection.driver_class, hibernate.connection.autocommit, hibernate.dialect, and hibernate.connection.username are the few properties required to database configuration in standalone condition. 32. What is the usage of method Session.beginTransaction()? To start a unit of work and return the allied transaction object, Session.beginTransaction method is used in hibernate. 33. Provide the method to re-read a provided instance state from the underlying database? To re-read a provided instance state from the underlying database, use the method “Session.refresh”. 34. Do you think the SessionFactory is thread-safe? Yes, of-course. SessionFactory is a thread-safe and multiple threads can access the same simultaneously. 35. Do you think Session is a thread-safe object? No, it is not possible. 36. Provide the concurrency strategies in Hibernate? Non-strict read-write, Transactional, Read-only and Read-write are the concurrency strategies in Hibernate. 37. Define first level cache? First level cache is an essential cache where we can see all requests are passing. Before committing to the database, the session object maintains an object under its self-power. 38. Explain Query level cache? A cache is implemented by Hibernate which is for query resultsets, integrating meticulously with the second level cache. This is not a mandatory feature. 39. What is the method get ()? If no data found, the method get() returns the value as null and it always touches the database. Actual objects are returned by get() method. 40. Explain the method load()? If not data found, the method() throws an exception as “ObjectNotFoundException”. The load() method is often seen to hit the database and it returns proxy object. 41. Describe lazy loading? There is a process where the objects are loaded on demand basis. Hibernate 3 is a lazy loading by default. Hence, when parent objects are loaded, child objects will not be loaded. 42. Describe HQL? Similar to SQL tables, Hibernate Query Language (HQL), which is an Object-Oriented Query language, gets the java objects. HQL is a database independent. 43. Can u mention the element of hbl.xml which helps to create the primary key values automatically? Yes, the element helps to create the primary key values automatically. 44. Can u mention the element of hbl.xml which helps to map the property ‘java.util.SortedSet’ in hibernate? The element is used for mapping and ‘java.util.TreeSet’ is used for initialization. 45. Explain addjar() and addDirectory() method in Hibernate? The method addjar() and addDirectory() methods plays a vital part in streamlining a set of processes like configuration, layout, refactoring and few more. Users can easily load hibernate documents in Hibernate using these two (2) methods. 46. What is Hibernate tuning? Optimization of the Hibernate applications performance is called Hibernate tuning. By performing SQL optimization, session management, and data caching, hibernate tuning happens. 47. What is derived properties? The unmapped properties which gets calculated at runtime via expression evaluation is called derived properties. The derived expression is received from a formula with the corresponding element. 48. What is Dialect? A single file or a group of code files that irregularly explains the procedure of connecting database to a Java class. In hibernate, a dialect plays a major role of recognizing the information that takes place with the fundamental database. 49. Describe Connection Pool? The connection pool in hibernate is a group of Database connection objects which are created for handling corresponding communication with the database. 50. Which annotation is used to specify the database table? The annotation @Table helps in specifying the database table which is allied to the entity. 51. What’s General Hibernate Flow Using Rdbms? General hibernate flow involving RDBMS is as follows: Load configuration file and create object of configuration class. Using configuration object, create sessionFactory object. From sessionFactory, get one session. Create HQL query. Execute HQL query and get the results. Results will be in the form of a list. 52. How Can We Map The Classes As Immutable? If we don’t want an application to update or delete objects of a class in hibernate, we can make the class as immutable by setting mutable=false 53. What The Three Inheritance Models Are Of Hibernate? Hibernate has following three inheritance models: Tables Per Concrete Class Table per class hierarchy Table per sub-class 54. Does Hibernate Support Polymorphism? Yes, hibernate fully supports polymorphism. Polymorphism queries and polymorphism associations are supported in all mapping strategies of hibernate. 55. What’s The Use Of Session.lock() In Hibernate? session.lock() method of session class is used to reattach an object which has been detached earlier. This method of reattaching doesn’t check for any data synchronization in database while reattaching the object and hence may lead to lack of synchronization in data. 56. What Is Attribute Oriented Programming? In Attribute oriented programming, a developer can add Meta data (attributes) in the java source code to add more significance in the code. For Java (hibernate), attribute oriented programming is enabled by an engine called XDoclet. 57. What’s The Use Of Version Property In Hibernate? Version property is used in hibernate to know whether an object is in transient state or in detached state. 58. What’s The Difference Between Load() And Get() Method In Hibernate? Load() methods results in an exception if the required records isn’t found in the database while get() method returns null when records against the id isn’t found in the database. So, ideally we should use Load() method only when we are sure about existence of records against an id. 59. What Is Meant By A Named Sql Query In Hibernate And How It’s Used? Named SQL queries are those queries which are defined in mapping file and are called as required anywhere. For example, we can write a SQL query in our XML mapping file as follows: SELECT std.STUDENT_ID AS {std.STUDENT_ID}, std.STUDENT_DISCIPLINE AS {std.discipline}, FROM Student std WHERE std.NAME LIKE :name Then this query can be called as follows: List students = session.getNamedQuery("studentdetails") .setString("TomBrady", name) .setMaxResults(50) .list(); 60. What Are Different Ways To Disable Hibernate Second Level Cache? Hibernate second level cache can be disabled using any of the following ways: By setting use_second_level_cache as false. By using CACHEMODE.IGNORE Using cache provider as org.hibernate.cache.NoCacheProvider HIBERNATE Questions and Answers Pdf Download Read the full article
0 notes
Text
What do Security Courses Consist of?
IT Security or Information Technology Security refers to the body of technologies, processes, and practices designed to shield networks, devices, programs, and knowledge from attack, damage, or unauthorized access. IT Security can also be called cybersecurity.
IT Security is very important because the government, military, corporate, financial, and medical organizations collect, process, and store unprecedented amounts of information on computers and alternative devices. A major portion of that information is often sensitive data, whether or not that be intellectual property, financial information, personal data, or different kinds of information for which unauthorized access or exposure might have negative consequences. Organizations transmit sensitive data across networks and to alternative devices within the course of doing business, and cybersecurity describes the discipline dedicated to protecting that data and also the systems used to process or store it.
As the volume and class of cyber attacks grow, firms and organizations, particularly those who are tasked with safeguarding data regarding national security, health, or financial records, ought to take steps to safeguard their sensitive business and private information.
As early as March 2013, the nation’s top intelligence officials cautioned that cyber attacks and digital spying are the highest threat to national security, eclipsing even coercion.
PSB Academy based in Singapore is one of the best institutes providing the best IT Security courses. They have an extensive course which includes the basics as well as the advanced course structure.
Their course structure includes a wide range of IT security ideas, tools, and best practices. It introduces threats and attacks and also the various ways they can show up. They provide you with some background of cryptography algorithms and the way they’re accustomed to safeguard the information.
Their IT Security course will teach you about the 3 As of data security: authentication, authorization, and accounting. They conjointly cover network security solutions, starting from firewalls to WLAN encryption choices. Finally, they give you a case study, where you tend to examine the safety model of Chrome OS.
The course is rounded out by putting all these components along into a multi-layered, in-depth security design, followed by recommendations on how to integrate a culture of security into your organization or team.
What will you learn from the course?
Understanding security threats
The IT Security Course will include the fundamentals of security in an IT environment. You will learn to analyze how to outline and understand security risks, vulnerabilities, and threats. You’ll discover the most frequent security assaults in a business enterprise and apprehend how security revolves around the "CIA" principle. You will be aware of the sorts of malicious software, network attacks, client-side attacks, and the vital security terms you will see in the workplace.
Cryptology (Pelcgbybtl)
You will discover distinctive kinds of encryption practices and how they work. You will be taught about exhibiting the most frequent algorithms used in cryptography and how they've advanced over time. You'll also understand how symmetric encryption, asymmetric encryption, and hashing work; you will be taught how to select the most suitable cryptographic technique for a situation you may see in the workplace.
AAA Security (Not Roadside Assistance)
You will learn to analyze the "three A's" in the field of IT Security. No matter what kind of tech position you are in, it is essential to apprehend how authentication, authorization, and accounting work inside an organization.
By learning this, you will be capable enough to select the most excellent technique of authentication, authorization, and level of access granted for users in an organization.
Securing Your Networks
You will study about secure network architecture. It's vital to understand how to enforce security measures in a network environment, so you will learn about some of the fine practices to guard an organization's network. You will study some of the risks of wireless networks and how to mitigate them. You will additionally cover methods to monitor network traffic and read packet captures. You will be able to apprehend how VPNs, proxies and reverse proxies work; why 802.1X is extremely vital for network protection; recognize why WPA/WPA2 is better than WEP, and know how to use tcpdump to capture and analyze packets on a network.
Defense in Depth
You will learn the ways to enforce strategies for system hardening, software hardening, and decide the policies for OS security. You will understand why it's essential to disable useless components of a system, study about host-based firewalls, setup anti-malware protection, implement disk encryption, and configure software patch management and application policies.
Creating a Company Culture for Security
You will explore the ways to create an organizational culture for security. It's necessary for any tech role to decide suitable measures to meet the three goals of security. You will be able to develop a security plan for a corporation to exhibit the skills you've learned through the IT Security course.
0 notes
Text
The week in review:
Raw 11/23 NXT 11/25 NXT UK 11/26 Smackdown 11/27

Raw:

Such a hollow promo by Lana tbh. “I’m dreaming, don’t wake me up.” ??? You were the sole survivor by proxy, it’s not like you did anything. Like good for you, but come on now.

I mean sure, hand out a title shot to fucking Lana, not like anyone else in the entire company cares about that belt. God I miss Becky.
“You may go home Raw women’s champion” HAHAHAHAHAAHHA sure.

“Nikki Cross blames herself for what Alexa Bliss has become,” she should, she straight up threw her hissy fit cuz she didn’t win the title, and then she bailed.
Now don’t get me wrong, I get that Alexa has been... possessed, if you will, by Fiend... but I’m not seeing any signs of Stockholm Syndrome when it comes to her and Bray. Aren’t they both trapped by Fiend in lore? Bray seems to genuinely care about Alexa. Am I off the mark here??
Oh my god this moment of silence for the fucking frog, I--
Topped with them laughing about his death, oooookay. I’m left speechless once again.
Commentators come back with, “Is Alexa Bliss too far gone...” LMFAO bye.

See I love this bullying Lana storyline cuz Nia and Shayna have no real reason to despise her 1/8th as much as they do. It simply boils down to ‘fuck Lana’ and like your typical high school bullies, they seethe when their victim succeeds at anything. It’s old school, believable, and doesn’t cross any lines that would upset parents or sponsors.
Also don’t get me wrong, I’m well aware that this title match is just a vehicle to advance the feud while involving Asuka, I simply wish the creation of the title match itself had been a bit more interesting. Lana’s dialogue ahead of it with both Sarah and Asuka just fell flat for me.
Omfg Asuka threw water on Nia and Shayna, bahahahah I can’t breathe. That might be the highlight of her entire reign, holy shit.
Negative points for her being floored by one punch though.
Well at least the segment ends with both Asuka and Lana standing, that’s not the worst.

Not much to say about this match, it’s really just Nia and Shayna bullying Lana lol.
I’ll give them this, there is absolutely nothing about neither Nia nor Shayna that is even remotely likeable. They play mean really well, and not ‘annoying yet funny’ mean like Bayley, just straight mean.
It’s not that I hate this submission ‘hold’ by Shayna, where she steps on the back of their neck while pulling a leg back, but I’m curious why she switched legs lmao. Awkward.
What a knee strike by Shayna to Asuka, whew that looked nasty.
Lmfao Nia took herself out by charging into the announce desk. I cannot. What a bump. Comedic bump, but a bump. Points.
Haha Shayna ate a rollup. A happy ending indeed. Lana sold that ending well, but it was a weird choice to have her and Asuka on the opposite ends of the ramp.

It’s been like 2 years and I’m still shocked Alexa never turned on Nikki.
This video is kind of just skipping over Nikki throwing her tantrum huh? Alexa played backseat cheerleader just to watch Nikki lose against Bayley 16 times and what did she get in return? Disrespect. Tsk.
Great package though. Points.
Nikki is so inconsistent. Internal conflict is valid, but she’s standing here claiming Alexa gave up on their friendship. First of all, this was initially instigated by Nikki. Second of all, she did nothing but trash Alexa’s boyfriend(?) when Alexa was nothing but kind to her after Nikki was a douche. She was confused so she gave Alexa an ultimatum, and now she’s pissy cuz Alexa chose him. This is toxic, I honestly have no sympathy for Nikki.
“I’m going to beat the Fiend out of Alexa Bliss” that’s... that’s not how this works... alright well you’re a shitty friend so, anyway.
Alexa slaps the back of Nikki’s hands and claims she won. I fucking can’t, she’s such a treat.
Lol Alexa’s just laughing at her.
My first introduction to Alexa was her as a master manipulator. Not a damn thing has changed.
Alexa has lost her god damn mind rofl.
*Bonus* online exclusive: victim Nikki, everyone. Why wasn’t this on Raw? Jesus they fill Raw with so many garbage replays while meaningful interviews to fill plot holes are put online. Dumb.

Lacey’s really running around calling Peyton “PeyPey” good lord.
I mean she’s right, Peyton was the weakest link. Just saying.
“10 sizes too big” shot at Uncle Melted Cheese.
I fucking love how Lacey pronounces “opportun-tit-ies” lmao. I thought it was an accident at first but honestly it’s great.
They have zero chemistry in the ring but at least they’re fun outside of it.
Highlight: I know I say Alexa every single week but shrug it’s Alexa
---
NXT:

Alright Ember’s theme is wearing on me. She just has awesome theme songs.
Indi is really pretty and I love how she does her hair.
All nxt heels are the same; cowardly run from fights, slow methodical wrestling in the ring, recruiting muscle optional. It’s tired. At least be a good promo. Dakota is a good promo. She’s buyable. Actually where’s Dakota, I wanna see Dakota wrestle. No more Candice.
Holy shit that fall away slam onto Candice. Fucking THREW her ass across the ring. Whew everyone wave bye to Candice.
The setup to that step up senton by Candice was way too obvious.
Candice is too whiny.
Ah just as I’m beginning to get bored, Dakota comes out. It’s like nxt knows me.
Haha KO correcting Vic being a bad commentator.
See Candice isn’t even a bad wrestler, her style as heel just fucking blows.
Peeped that call by Ember.
Such a stupid setup to have Indi push Candice out of the way to take an Eclipse herself. It’s not like jumping in front of a bus. There was time. Whatever. I hate Candice matches 9 times out of 10 so there’s that lol.

...so is Toni a heel yet??? I’m guessing they’re going for “badass loner babyface-leaning tweener” for Ember, but Toni is not a tweener. She could’ve been, alas she is not.
Haha Toni is funny. Good, let her be heel. Maybe she’ll show some personality.

Alright but hear me out, what if we had a War Games team without Candice???
You did say we’d see a whole new side of you, Toni. Been waiting to see it though.
Wait back up, didn’t Toni attack Candice after their match recently?? Okay anyway.

“Rhea Ripley/Io Shirai? Doesn’t get any bigger than that.” True Rhea, now move up to the main roster plz.
Oh man Io’s basement dropkick fucking nailed Rhea in the face lol, oof.
“Where do I go from here?” TO THE MAIN ROSTER.

I don’t hate the tank and I don’t hate the idea of wearing a helmet, but those horns are super pointless.
Shotzi “pyromaniac” Blackheart. Stealing one of Alexa’s gimmicks.
It’s gonna be Shotzi, Io, Rhea and Ember, right? Who else would it be??

Rhea says she’s there to stay. Ma’am I stg if I have to wait til after wm to see you on the MR...
Me: super invested in Rhea cutting a fantastic promo and seeing how far she’s progressed as a well-rounded talent; Candice: “lol fuck you”
I hate Candice. I will fill this review with vitriol for Candice, I don’t care.
How... how did Io “steal” any victories from Candice? What help did she have? Is it drugs? Is Candice on drugs?? Candice you haven’t even held the title, shut the fuck up. Also all of y’all can sit down cuz only one woman on that entire brand has had a singles match at wm.
Oh shit they laid Io out. That’s a yikes.
In kf, the only threat to Rhea on that entire team is Toni.
I mean sure 4 people was way too much for Rhea to handle, but man they let her look pretty fucking good. The way she immediately slid out to give Raquel the high boot was smart as hell.
Dakota looks good. She gets style points.

Soooo Xia gets acting points, but what in the fuck is going on with her and Boa’s story...
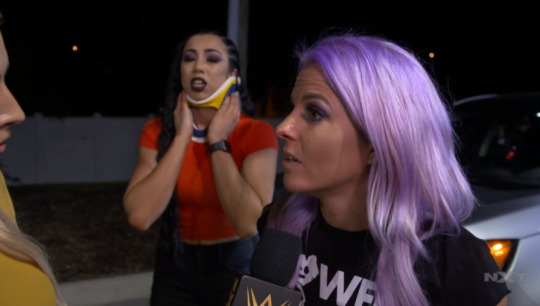
Why do I have to see or hear Candice again? Jesus lord.
There’s someone else masked? *sigh* I don’t care, goodbye.
Highlight: Rhea’s promo that Candice ruined
---
NXT UK:

I enjoy watching neither of these women wrestle, but at least Jinny’s persona is appealing and she has solid character work. She’s easy to dislike, so she gets heel-potential points.
Did they say Isla’s mentor is Nikki Cross? That’s... interesting...
So is this match gonna be interrupted by Piper? Probably not.
“This is an aggressive Isla Dawn,” well hey, maybe she actually started working on her stamina.
Jinny is vicious lmao.
Probably Isla’s best showing tbh.
I hate it when people jump off the top turnbuckle and then break into a slow, clunky roll, just to stand up and act as if their knee is tweaked. It’s so messy to me. Be smoother or don’t aimlessly jump off the turnbuckle.
Whole lotta yelling in the match.
Really don’t give a shit about a future Jinny/Piper match but okay.
Highlight: Jinny comes off as a vicious bitch, so that’s nice
---
Smackdown:

Oh snap Bianca’s graphic has some real potential.
Ayyyeeee it’s Captain Bayley. We starting our Bianca/Bayley feud?
oof Nattie straight outsmarted Bianca as the vet, there. Bianca friggin speared that ringpost.
“I think I did the world a favor, we got to see Bianca Belair shine,” she���s not wrong, Bianca was absolutely my mvp from SvS. In hindsight speaking from current day, Bayley really set up Bianca to be the upcoming star of this division, starting with SvS.
Oh snap did Bianca just call Nattie a bitch? How dare she, that’s Nattie’s only patented insult!
“You don’t want to get counted out again,” lmfao Bayley’s so annoying.
pppffffftttt Bayley inadvertently getting her ass whooped tonight.
Yeah somehow this is all Cole’s fault lol.

No, stop, no more “them” promos. Bayley cut this promo literally a year prior, we don’t need to hear it from Carmella, too. Besides, she was never necessarily a fan favorite that the crowd gradually turned against like Bayley was. It’s different.
WHAT SHOTS ARE YOU CALLING?? Is this about Reggie? Has he even appeared on screen yet?
Lmao Sasha beating her ass. Good for her. Looking good while she does it, too. Sasha in shiny silver... whew.

The wwe shop ad with the Riott Squad was worth a mention. They entertain me and they deserve tag titles. Not sure why wwe is still dragging their feet, but commit to them already, damn it.
Highlight: Bianca/Bayley seeds being planted
---
*Smackdown shined the brightest this week. Short, simple, straight to the point. Left me wanting to throw on next week’s episode, which no other show accomplished.
#wwe#issa review#feel free to ignore these#cuz who tf cares lesbihonest#today's props goes to:#bayley
0 notes
Quote
Quarkus is a new technology aimed at cloud development. With Quarkus, you can take advantage of smaller runtimes optimized for the cloud. You don’t need to relearn new APIs. Quarkus is built on top of the best-of-breed technologies from the last decade, like Hibernate, RESTEasy, Vert.x, and MicroProfile. Quarkus is productive from day one. Quarkus is production ready. Quarkus created quite a buzz in the enterprise Java ecosystem in 2019. Like all other developers, I was curious about this new technology and saw a lot of potential in it. What exactly is Quarkus? How is it different from other technologies established in the market? How can Quarkus help me or my organization? Let’s find out. What is Quarkus? The Quarkus project dubbed itself Supersonic Subatomic Java. Is this actually real? What does this mean? To better explain the motivation behind the Quarkus project, we need to look into the current state of software development. From On-Premises to Cloud The old way to deploy applications was to use physical hardware. With the purchase of a physical box, we paid upfront for the hardware requirements. We had already made the investment, so it wouldn’t matter if we used all the machine resources or just a small amount. In most cases, we wouldn’t care that much as long as we could run the application. However, the Cloud is now changing the way we develop and deploy applications. In the Cloud, we pay exactly for what we use. So we have become pickier with our hardware usage. If the application takes 10 seconds to start, we have to pay for these 10 seconds even if the application is not yet ready for others to consume. Java and the Cloud Do you remember when the first Java version was released? Allow me to refresh your memory — it was in 1996. There was no Cloud back then. In fact, it only came into existence several years later. Java was definitely not tailored for this new paradigm and had to adjust. But how could we change a paradigm after so many years tied to a physical box where costs didn’t matter as much as they do in the Cloud? It’s All About the Runtime The way that many Java libraries and frameworks evolved over the years was to perform a set of enhancements during runtime. This was a convenient way to add capabilities to your code in a safe and declarative way. Do you need dependency injection? Sure! Use annotations. Do you need a transaction? Of course! Use an annotation. In fact, you can code a lot of things by using these annotations that the runtime will pick and handle for you. But there is always a catch. The runtime requires a scan of your classpath and classes for metadata. This is an expensive operation that consumes time and memory. Quarkus Paradigm Shift Quarkus addressed this challenge by moving expensive operations like Bytecode Enhancement, Dynamic ClassLoading, Proxying, and more to compile time. The result is an environment that consumes less memory, less CPU, and faster startup. This is perfect for the use case of the Cloud, but also useful for other use cases. Everyone will benefit from less resources consumption overall, no matter the environment. Maybe Quarkus is Not So New Have you heard of or used technologies such as CDI, JAX-RS, or JPA? If so, the Quarkus stack is composed of these technologies that have been around for several years. If you know how to develop these technologies, then you will know how to develop a Quarkus application. Do you recognize the following code? @Path("books") @Consumes(APPLICATION_JSON) @Produces(APPLICATION_JSON) public class BookApi { @Inject BookRepository bookRepository; @GET @Path("/{id}") Response get(@PathParam("id")Long id) { return bookRepository.find(id) .map(Response::ok) .orElse(Response.status(NOT_FOUND)) .build(); } } Congratulations, you have your first Quarkus app! Best of Breed Frameworks and Standards The Quarkus programming model is built on top of proven standards, be it official standards or de facto standards. Right now, Quarkus has first class support for technologies like Hibernate, CDI, Eclipse MicroProfile, Kafka, Camel, Vert.x, Spring, Flyway, Kubernetes, Vault, just to name a few. When you adopt Quarkus, you will be productive from day one since you don’t really need to learn new technologies. You just use what has been out there for the past 10 years. Are you looking to use a library that isn’t yet in the Quarkus ecosystem? There is a good chance that it will work out of the box without any additional setup, unless you want to run it in GraalVM Native mode. If you want to go one step further, you could easily implement your own Quarkus extension to provide support for a particular technology and enrich the Quarkus ecosystem. Quarkus Setup So, you may be asking if there is something hiding under the covers. In fact yes there is. You are required to use a specific set of dependencies in your project that are provided by Quarkus. Don’t worry, Quarkus supports both Maven and Gradle. For convenience, you can generate a skeleton project in Quarkus starter page, and select which technologies you would like to use. Just import it in your favorite IDE and you are ready to go. Here is a sample Maven project to use JAX-RS with RESTEasy and JPA with Hibernate: 4.0.0 org.acme code-with-quarkus 1.0.0-SNAPSHOT 3.8.1 true 1.8 1.8 UTF-8 UTF-8 1.3.0.Final quarkus-universe-bom io.quarkus 1.3.0.Final 2.22.1 ${quarkus.platform.group-id} ${quarkus.platform.artifact-id} ${quarkus.platform.version} pom import io.quarkus quarkus-resteasy io.quarkus quarkus-junit5 test io.rest-assured rest-assured test io.quarkus quarkus-hibernate-orm io.quarkus quarkus-resteasy-jsonb io.quarkus quarkus-maven-plugin ${quarkus-plugin.version} build maven-compiler-plugin ${compiler-plugin.version} maven-surefire-plugin ${surefire-plugin.version} org.jboss.logmanager.LogManager You might have noticed that most of the dependencies start with the groupId io.quarkus and that they are not the usual dependencies that you might find for Hibernate, Resteasy, or Junit. Quarkus Dependencies Now, you may be wondering why Quarkus supplies their own wrapper versions around these popular libraries. The reason is to provide a bridge between the library and Quarkus to resolve the runtime dependencies at compile time. This is where the magic of Quarkus happens and provides projects with fast start times and smaller memory footprints. Does this mean that you are constrained to use only Quarkus specific libraries? Absolutely not. You can use any library you wish. You run Quarkus applications on the JVM as usual, where you don’t have limitations. GraalVM and Native Images Perhaps you already heard about this project called GraalVM by Oracle Labs? In essence, GraalVM is a Universal Virtual Machine to run applications in multiple languages. One of the most interesting features is the ability to build your application in a Native Image and run it even faster! In practice, this means that you just have an executable to run with all the required dependencies of your application resolved at compile time. This does not run on the JVM — it is a plain executable binary file, but includes all necessary components like memory management and thread scheduling from a different virtual machine, called Substrate VM to run your application. For convenience, the sample Maven project already has the required setup to build your project as native. You do need to have GraalVM in your system with the native-image tool installed. Follow these instructions on how to do so. After that, just build as any other Maven project but with the native profile: mvn verify -Pnative. This will generate a binary runner in the target folder, that you can run as any other binary, with ./project-name-runner. The following is a sample output of the runner in my box: [io.quarkus] (main) code-with-quarkus 1.0.0-SNAPSHOT (powered by Quarkus 1.3.0.Final) started in 0.023s. Listening on: http://0.0.0.0:8080 INFO [io.quarkus] (main) Profile prod activated. [io.quarkus] (main) Installed features: [agroal, cdi, hibernate-orm, narayana-jta, resteasy, resteasy-jsonb] Did you notice the startup time? Only 0.023s. Yes, our application doesn’t have much, but still pretty impressive. Even for real applications, you will see startup times in the order of milliseconds. You can learn more about GraalVM on their website. Developer Productivity We have seen that Quarkus could help your company become Cloud Native. Awesome. But what about the developer? We all like new shiny things, and we are also super lazy. What does Quarkus do for the developer that cannot be done with other technologies? Well, how about hot reloading that actually works without using external tools or complicated tricks? Yes, it is true. After 25 years, since Java was born, we now have a reliable way to change our code and see those changes with a simple refresh. Again, this is accomplished by the way Quarkus works internally. Everything is just code, so you don’t have to worry about the things that made hot reloading difficult anymore. It is a trivial operation. To accomplish this, you have to run Quarkus in Development Mode. Just run mvn quarkus:dev and you are good to go. Quarkus will start up and you are free to do the changes to your code and immediately see them. For instance, you can change your REST endpoint parameters, add new methods, and change paths. Once you invoke them, they will be updated reflecting your code changes. How cool is that? Is Quarkus Production Ready? All of this seems to be too good to be true, but is Quakus actually ready for production environments? Yes it is. A lot of companies are already adopting Quarkus as their development/runtime environment. Quarkus has a very fast release cadence (every few weeks), and a strong Open Source community that helps every developer in the Java community, whether they are just getting started with Quarkus or are an advanced user. Check out this sample application that you can download or clone. You can also read some of the adoption stories in a few blog posts so you can have a better idea of user experiences when using Quarkus. Conclusion After a year of its official announcement, Quarkus is already on version 1.3.1.Final. A lot of effort is being put in the project to help companies and developers to write applications that they can run natively in the Cloud. We don’t know how far Quarkus can go, but one thing is for certain: Quarkus shook the entire Java ecosystem in a space dominated by Spring. I think the Java ecosystem can only win by having multiple offerings that can push each other and innovate to keep themselves competitives.
http://damianfallon.blogspot.com/2020/04/getting-started-with-quarkus.html
0 notes
Text
Is There a Magic Formula to Solve a Conflict in the East of Ukraine?
Ukraine agreed to the so called Steinmeier formula that aims to bring forward the process to resolve the armed conflict in the East of Ukraine. It might lead to the first real progress in five years, but only if the Ukrainian leadership finds a very delicate balance.

In recent weeks, Ukraine became one of the most discussed topics in the United States and, to a lesser extent, in Europe. In Ukraine itself, however, the phone conversation between its President Volodymyr Zelensky and his US counterpart Donald Trump has been eclipsed by a different issue which is called Steinmeier formula.
This sequencing clause has been proposed in 2016 by Frank-Walter Steinmeier, then a foreign minister and now Federal President of Germany, to help find a political resolution to the military conflict in Donbas, the region in the East of Ukraine, between Russia and separatists it backs on one side and the government in Kyiv on the other. The vagueness of the formula itself and the explosive nature of its possible political consequences have even led to the first noticeable protests in Ukraine.
What is Steinmeier formula?
The major document, aimed for a peaceful resolution of the conflict in Donbas, is the second Minsk agreement, signed in 2015 by Ukraine, Russia and OSCE and consented to by the separatists. The Minsk II foresees a number of measures that should have led to a political solution; however, its implementation stalled from the very beginning.

The problem with the agreement was that both sides, Ukraine and Russia (together with its proxies in Donbas) interpreted the sequence of steps in their way and blamed the other side for the absence of progress. For example, Moscow blames Kyiv for not adopting legislation on the amnesty of militants and maintaining an economic blockade of the areas controlled by the separatists.
It is correct that, according to Minsk II, Ukraine should reinstate social and economic links with the areas currently not under its control. At the same time, Russia has long ago introduced its ruble as the official currency in the areas of Donbas not controlled by Kyiv. That decision has been of course presented as if made by the separatist’s leadership, because Moscow claims to not to be a part of the conflict in Donbas.
Ukraine, on its side, has always maintained that Minsk II should be implemented step by step, and the first three measures foresee a full ceasefire and disentanglement of the forces. As there was no lasting end to the fighting and shelling, Kyiv declined to make steps forward.
Thus, a never-ending vicious circle.
Steinmeier formula has been introduced as an attempt to break this circle. It regulates the sequencing, that is timing to introduce the special conditions for self-governing in the areas of Donbas, not controlled currently by the government. Provisionally these special conditions should enter into force on the day of local elections, foreseen by the Minsk II, and constantly after the OSCE publishes its report that these elections have been held in accordance with the international democratic standards and by the Ukrainian law.
Protests against Steinmeier formula
Although this formula doesn’t seem to contain any obvious danger to sovereignty and independence of Ukraine, there is a substantial pushback against Steinmeier formula in Ukraine. The sharpest criticizing originates in the party of the former President of Ukraine Petro Poroshenko; it started calling this sequence “Putin’s formula” and claiming that it will result in the capitulation of Ukraine.

One may dismiss the criticism coming from Poroshenko because of two reasons. First, he lost his reelection bid to Zelensky; consequently, he would criticize almost everything being done by the current leadership of Ukraine. Second, Poroshenko himself has not only failed to solve the conflict in Donbas, but he also has not even provided any vision of a possible solution.
At the same time, one cannot dismiss pushback among the Ukrainian population. On Sunday, October 6, thousands of people all over the country organized protests against Steinmeier formula under the slogan “No to Capitulation”.
The easiest explanation for the protest is that Zelensky administration failed to communicate good enough with the public. The President himself and other representatives of the Ukrainian leadership have said many times that there won’t be any capitulation, that it won’t cross any “red lines”, and that there could be no election while armed militants remain in Donbas. Still, it failed to placate fears spread in Ukrainian society.
One should note that those fears go very deep, as Ukrainians have little trust in any power. Consecutive governments in the country have time and again proven to be corrupt. And Zelensky has not done much to demonstrate that he listens to the public. Neither do Ukrainians trust that the EU and the USA would go to a great length to help them. Despite all the statements, the West has not done much to protect the protestors on the Maidan in 2013-14 against the violence, exerted by the then government. And despite all the sanctions and assistance to Ukraine, Russia has not stopped its aggression. One may argue that such resentment is not fair or well-argued. Still, it should be taken into account while dealing with Ukraine, because it might, for example, derail the efforts to resolve the conflict in Donbas.
Could Steinmeier formula be a magic one?
Ukraine may, of course, return to the previous policy of zero compromise; however, it would mean that the country will continue to lose the lives of its citizens as well as huge resources in the war in Donbas. The crushing defeat of Poroshenko during the presidential election this year demonstrated that Ukrainian society doesn’t want this course to continue.
How then could Steinmeier formula revive the Minsk agreements, whereas Russia has shown by its actions no desire to let the conflict in Donbas be resolved? As argued earlier[1], the President of Russia Vladimir Putin has had the interest to continue the current low-level war in Donbas as a mean of attrition of Ukraine.

Now the situation might start to change. Putin’s trailing support in Russia and the ongoing protests in Moscow have demonstrated the limits of the policies he pursued for the last five years. Thus, Putin might have the interest to soften his confrontational course against Ukraine and the West. Of course, he would do this only if it doesn’t create any impression he has lost. Appearance is of paramount importance for Putin personally and the whole Russian political establishment.
Therefore, if Ukraine wants to get any progress in the political resolution of the conflict, it should maintain an extremely difficult balance between showing the readiness to compromise, being ready to compromise, but not to allow any compromise on its sovereignty and independence.
To that end, it needs to create the whole framework for the political process, including for the special status of self-governing in the areas currently controlled by the separatists. After all, it was Ukraine who agreed to grant that status in the Minsk II agreement and later in 2015, it failed to introduce the reference to the special self-governing into the constitution.
Now Ukraine is advised to eliminate all the reasonable grounds for Russia to say it is not implementing the Minsk II. In such a way it can create the appearance, without which Putin won’t probably amend his course. In doing so, Ukrainian leadership must be very careful in drafting the exact setup of the special self-governing status. Because this is where the capitulation may reside, and not in Steinmeier formula per se.
It may be unfair that Russia has started the war in Donbas, but Ukraine should bear the burden of trying to end it. Alas, it is in Ukraine’s interest to do this, and so it will need earlier or later to act on this. Up till now, Minsk agreements have not proven that they can pave the way to the resolution, but no one has proposed any better solution. And now there is a momentum to the Minsk process that may bring some progress.
[1] https://www.promoteukraine.org/2019/06/07/five-years-of-normandy-format-how-putin-prevented-d-day-for-ukraine/
YURIY SHEYKO, A FREELANCE CORRESPONDENT BASED IN BRUSSELS, FOR PROMOTE UKRAINE
*Opinion of the author may not coincide with the position of the NGO Promote Ukraine
#ukraine#Russia#Promote Ukraine#Steinmeier formula#East of Ukraine#PU Rocks#Minsk#Volodymyr Zelensky#Zelensky#SHEYKO
0 notes
Text
Splashtop Is The # 1 Remote Desktop computer Remedy For Mobile Tools, Over 18 Million Users.
In a surprise relocation, Sega is about to make its large catalogue of retro standards entirely cost-free to use iPhone and also Android The new solution is called Sega Forever as well as extends 20 years of fantastic residence gaming consoles. For instance, you can run a Nexus One with Android 4.2 or a Nexus 6 with Android 6.0. You could quickly switch over in between tools" at will. It comes with a lot of devices to assist designers make games and also apps especially for Android. video games 2017 You may intend to change a few of BlueStacks App Gamer's setups, specifically if you want to boost performance and picture quality. BlueStacks was worthless to me. All I wished to do was run Instagram, but could not sign up - some BS open proxy" error. Just what we need is a person to natively sustain Android applications in Linux (this implies no VMs). I likewise attempted Nox with games like Asphalt 8 Airborne, Batman: Arkham Origins as well as The Strolling Dead: Roadway to Survival. Let's begin by clicking the Play Shop icon to download and install some applications. If it's a cinema Android experience you're looking for, you might choose to cast your Android gadget to a TV, and even invest on an Android game console. Select your language, sign in with your Google account (for access to the Play Shop and other features), and also all the various other normal stuff you do when setting up an Android gadget for the very first time. While it is possible, you'll have to hang out exercising which is the very best app for you, as well as your PC. Once you have actually done this, you're then mosting likely to need to invest even more time checking out the games you wish to work on your PC, as well as hoping that your chosen emulator or virtual device is up to the task of running the game. Mentioning finalizing in, be forewarned: as you carry out the two over steps (developing a BlueStacks account and also signing right into your Google represent the first time) you'll get 2 safety alerts from Google suggesting that you just authorized into Firefox on Windows and a Samsung Galaxy S5 tool. Andy breaks down the barrier in between desktop as well as mobile computing, while keeping a customer up to day with the latest Android OS attribute upgrades. As though you turned on a new Android tablet computer for the first time, you'll be gone through the standard setup. Here you can restart your mimicked Android tool, look for updates, transform the setups for BlueStacks (located under Preferences") or jump to the actual setups of the imitated Android device (by clicking Setups"). We've found tools like these are prominent in China, and you could view on a site such as GearBest for even more details (however make certain to read our grey-market technology acquiring suggestions prior to you make a purchase). However, those establishing applications do already have a powerful (and also complimentary) tool at their disposal to assist check their apps. In my experience the best way to run Android on a PC is mounting Android x86. One of a best emulator for playing android games on your computer. When playing games on your pc, Andy is additionally offer a function to use your phone as a remote control. Second of all, with some applications, the display looked extremely pixelated although this is probably inevitable on a big PC screen when you're making use of an app that had been written for a tiny low-resolution display. This is ideal fit to developers as the setup and administration of applications is complicated. You can really browse around in this interface just as you would on a real Android gadget, that makes it clear there's a lot more to BlueStacks compared to the App Gamer" front end. BlueStacks App Gamer is a free device that allows you run your favorite mobile apps from the convenience of your desktop. Many Android application designers use it as a plug-in for Eclipse or Android Workshop. Yes, KOPLAYER Android Emulator for computer downloads APK submits from Google play shop and make your apk downloading in a rapid means. The Android PC ports are most definitely enjoyable to have fun with, as well as efficiency is strong when you obtain apps running, yet they can be picky.
0 notes
Text
300+ TOP HIBERNATE Interview Questions and Answers
HIBERNATE Interview Questions for freshers experienced :-
1. What are the benefits of ORM tool? ORM is helpful in automatically generating keys, managing transaction, hiding SQL queries details, and developing applications in quick manner. 2. Provide the list of collection types in Hibernate? Set, Map, Bag, List and Array are the different types of collections in Hibernate 3. What are the two cache types in Hibernate? First level cache and Secondary level cache are the types of cache in Hibernate. 4. What is session interface? Hibernate session which performs database entities manipulation is represented by session interface. Activities carried on by session interface are handling persistence phases, retrieving the persisted ones, and transaction separations management. 5. List out the core interfaces available in Hibernate? Criteria, Transaction, Session Factory, Query, Configuration, and Session are the core interfaces available in Hibernate. 6. Describe the steps to create database application using Hibernate? Steps to create Database application using Hibernate: Write the Java object Create a mapping file. This displays the relationship between the database and attributes. Deploy the Hibernate API to store persistent objects. 7. Provide the list of Hibernate support databases? HSQL, MySQL, FrontBase, Informix Dynamic Server, DB2, Sybase SQL Server, Oracle, and PostgreSQL are the Hibernate support databases. 8. What are the two (2) components available in Hibernate configuration object? Class Mapping Setup and Database Connection are the two (2) components of Hibernate configuration object. 9. What is the syntax to create SQL query in Hibernate? The syntax to create SQL query in Hibernate is “Session.createQuery”. 10. What is the syntax to add criteria to the SQL query? The syntax to create criteria to the SQL query is “Session.createCriteria”.

HIBERNATE Interview Questions 11. Do you think the extension ‘.hbm.xml’ is mandatory for all the hibernate mapping file to work properly? No, the extension ‘.hbm.xml’ is not mandatory for all the hibernate mapping file as it is just a convention. 12. What is POJOs? POJO stands for Plain Old Java Objects. These are java beans which has proper setter and getter methods for every property. Instead of Java classes, the usage of POJOs leads to a well-constructed and effective code. 13. List out the advantages of Hibernate template? Hibernate template is useful is automating the exception handling and session closing. Also, you can have a simplified communication with hibernate session. 14. What is session.save() in hibernate? The method session.save() is used to save a record when it is unique with its related primary key. If the primary key is already existing in the table, this method will not allow to insert. 15. Explain saveOrUpdate() in hibernate? The method saveOrUpdate() method is helpful in inserting a new record when the primary key is unique. If the primary key is already existing in the table, this method will update the record. 16. What is the syntax to retrieve hibernate statistics? Use the syntax “SessionFactory.getStatistics()” to retrieve the hibernate statistics. 17. Provide the list of ORM levels available in Hibernate? Medium Object Mapping, Pure Relational, Full Object Mapping and Light Object Mapping are the ORM levels available in Hibernate. 18. Provide the mapping associations utilized in Hibernate? One-to-One Association and Many-to-Many Association are the two (2) mapping associations utilized in Hibernate. 19. What are the different methods to fetch objects from database in Hibernate? In Hibernate, you can use Criteria API, HQL, Standard SQL, and Identifier to fetch objects from database. 20. In Hibernate, what is the method to reattach the detached objects? Use the method “session.merge()” to attach the detached objects. 21. To disable second level cache in Hibernate, what are the different methods? To disable second level cache in Hibernate, you can perform any of the following: Use CACHEMODE.IGNORE Set “use_second_level_cache” to false Make use of cache provider as “cache provider as org.hibernate.cache.NoCacheProvider” 22. In Hibernate, which is the default transaction factory? The default transaction factory with Hibernate 3.2 is JDBCTransactionFactory. 23. Provide the fetching strategies available in Hibernate? Batch Fetching, Sub-select Fetching, Join Fetching, and Select Fetching are the fetching strategies available in Hibernate. 24. Explain the benefit of version property in Hibernate? To recognize whether an object is in detached or transient state, version property in Hibernate. 25. Do you think polymorphism is supported by Hibernate? Yes, hibernate purely and completely supports polymorphism. 26. List out the three (3) inheritance models available in Hibernate? Table per class hierarchy, Table per sub-class, and Tables Per Concrete Class are the three (3) inheritance models available in Hibernate. 27. What is transaction management? To manage a set of commands or statement, transaction management is used in Hibernate. 28. What is callback interface in Hibernate? To obtain even notifications from objects, hibernate callback interfaces are used. Say, for example, an even gets generated when an object is deleted or loaded, and callback interfaces send a notification. 29. Provide the various other ORM frameworks in Hibernate? The other ORM frameworks in Hibernate are TopLink and EJB from Oracle. 30. List out few Java-based frameworks which is supporting hibernate integration? Eclipse plug-ins, XDoclet Spring, Maven, and J2EE are the java-based frameworks which are supporting hibernate integration. 31. List out a few properties required to database configuration in standalone condition? hibernate.connection.url, hibernate.connection.pool_size, hibernate.connection.password, hibernate.connection.driver_class, hibernate.connection.autocommit, hibernate.dialect, and hibernate.connection.username are the few properties required to database configuration in standalone condition. 32. What is the usage of method Session.beginTransaction()? To start a unit of work and return the allied transaction object, Session.beginTransaction method is used in hibernate. 33. Provide the method to re-read a provided instance state from the underlying database? To re-read a provided instance state from the underlying database, use the method “Session.refresh”. 34. Do you think the SessionFactory is thread-safe? Yes, of-course. SessionFactory is a thread-safe and multiple threads can access the same simultaneously. 35. Do you think Session is a thread-safe object? No, it is not possible. 36. Provide the concurrency strategies in Hibernate? Non-strict read-write, Transactional, Read-only and Read-write are the concurrency strategies in Hibernate. 37. Define first level cache? First level cache is an essential cache where we can see all requests are passing. Before committing to the database, the session object maintains an object under its self-power. 38. Explain Query level cache? A cache is implemented by Hibernate which is for query resultsets, integrating meticulously with the second level cache. This is not a mandatory feature. 39. What is the method get ()? If no data found, the method get() returns the value as null and it always touches the database. Actual objects are returned by get() method. 40. Explain the method load()? If not data found, the method() throws an exception as “ObjectNotFoundException”. The load() method is often seen to hit the database and it returns proxy object. 41. Describe lazy loading? There is a process where the objects are loaded on demand basis. Hibernate 3 is a lazy loading by default. Hence, when parent objects are loaded, child objects will not be loaded. 42. Describe HQL? Similar to SQL tables, Hibernate Query Language (HQL), which is an Object-Oriented Query language, gets the java objects. HQL is a database independent. 43. Can u mention the element of hbl.xml which helps to create the primary key values automatically? Yes, the element helps to create the primary key values automatically. 44. Can u mention the element of hbl.xml which helps to map the property ‘java.util.SortedSet’ in hibernate? The element is used for mapping and ‘java.util.TreeSet’ is used for initialization. 45. Explain addjar() and addDirectory() method in Hibernate? The method addjar() and addDirectory() methods plays a vital part in streamlining a set of processes like configuration, layout, refactoring and few more. Users can easily load hibernate documents in Hibernate using these two (2) methods. 46. What is Hibernate tuning? Optimization of the Hibernate applications performance is called Hibernate tuning. By performing SQL optimization, session management, and data caching, hibernate tuning happens. 47. What is derived properties? The unmapped properties which gets calculated at runtime via expression evaluation is called derived properties. The derived expression is received from a formula with the corresponding element. 48. What is Dialect? A single file or a group of code files that irregularly explains the procedure of connecting database to a Java class. In hibernate, a dialect plays a major role of recognizing the information that takes place with the fundamental database. 49. Describe Connection Pool? The connection pool in hibernate is a group of Database connection objects which are created for handling corresponding communication with the database. 50. Which annotation is used to specify the database table? The annotation @Table helps in specifying the database table which is allied to the entity. 51. What’s General Hibernate Flow Using Rdbms? General hibernate flow involving RDBMS is as follows: Load configuration file and create object of configuration class. Using configuration object, create sessionFactory object. From sessionFactory, get one session. Create HQL query. Execute HQL query and get the results. Results will be in the form of a list. 52. How Can We Map The Classes As Immutable? If we don’t want an application to update or delete objects of a class in hibernate, we can make the class as immutable by setting mutable=false 53. What The Three Inheritance Models Are Of Hibernate? Hibernate has following three inheritance models: Tables Per Concrete Class Table per class hierarchy Table per sub-class 54. Does Hibernate Support Polymorphism? Yes, hibernate fully supports polymorphism. Polymorphism queries and polymorphism associations are supported in all mapping strategies of hibernate. 55. What’s The Use Of Session.lock() In Hibernate? session.lock() method of session class is used to reattach an object which has been detached earlier. This method of reattaching doesn’t check for any data synchronization in database while reattaching the object and hence may lead to lack of synchronization in data. 56. What Is Attribute Oriented Programming? In Attribute oriented programming, a developer can add Meta data (attributes) in the java source code to add more significance in the code. For Java (hibernate), attribute oriented programming is enabled by an engine called XDoclet. 57. What’s The Use Of Version Property In Hibernate? Version property is used in hibernate to know whether an object is in transient state or in detached state. 58. What’s The Difference Between Load() And Get() Method In Hibernate? Load() methods results in an exception if the required records isn’t found in the database while get() method returns null when records against the id isn’t found in the database. So, ideally we should use Load() method only when we are sure about existence of records against an id. 59. What Is Meant By A Named Sql Query In Hibernate And How It’s Used? Named SQL queries are those queries which are defined in mapping file and are called as required anywhere. For example, we can write a SQL query in our XML mapping file as follows: SELECT std.STUDENT_ID AS {std.STUDENT_ID}, std.STUDENT_DISCIPLINE AS {std.discipline}, FROM Student std WHERE std.NAME LIKE :name Then this query can be called as follows: List students = session.getNamedQuery("studentdetails") .setString("TomBrady", name) .setMaxResults(50) .list(); 60. What Are Different Ways To Disable Hibernate Second Level Cache? Hibernate second level cache can be disabled using any of the following ways: By setting use_second_level_cache as false. By using CACHEMODE.IGNORE Using cache provider as org.hibernate.cache.NoCacheProvider HIBERNATE Questions and Answers Pdf Download Read the full article
0 notes