#hackinghr
Explore tagged Tumblr posts
Photo
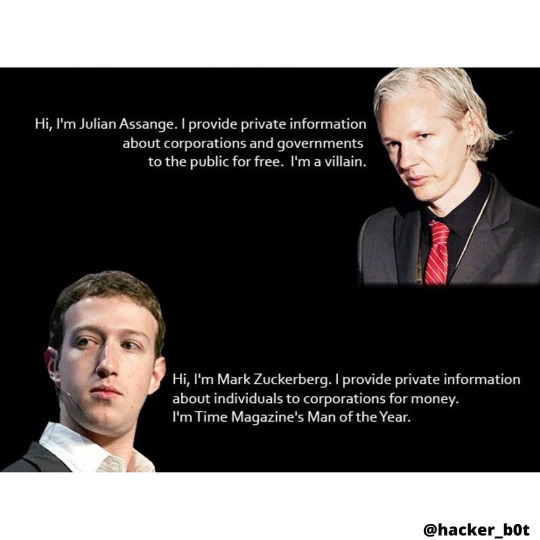
Truth 🤫 . . 🌐www.techyrick.com . . #hackerbrücke #wifihacking #hackinghorse #hackingthecity #househacking #neurohacking #growthhacking #hackinggrowth #anonymoushackers #hackerkitchen #hackertdog #bluehacker #blackhathacker #hackingtool #hackingético #whacking #pubghacker #hackinghr #biohacker #hackingout #growthhacker #hackingorsecurity #androidhacking #hackinginstagram #hackingmemes #hackers #biohackers #quoteshacker #hacking #hacker https://www.instagram.com/p/CQ0FBHPB_9C/?utm_medium=tumblr
#hackerbrücke#wifihacking#hackinghorse#hackingthecity#househacking#neurohacking#growthhacking#hackinggrowth#anonymoushackers#hackerkitchen#hackertdog#bluehacker#blackhathacker#hackingtool#hackingético#whacking#pubghacker#hackinghr#biohacker#hackingout#growthhacker#hackingorsecurity#androidhacking#hackinginstagram#hackingmemes#hackers#biohackers#quoteshacker#hacking#hacker
0 notes
Text
What You Should Learn Before Cybersecurity?

Today I’m going to talk to you guys about things that you should know prior to considering cybersecurity as a career for you.
Now, this is something that I get very often on the IT career questions people ask you to know what type of basic should I know.
what other technologies should I know?
prior to considering this as a career different variation of those types of questions.
Now some people assume that you can just get into cybersecurity with no prior knowledge of technology whatsoever right and while yes that is definitely possible anything in life is possible but what should you have as far as knowledge goes before considering this field as a career for you and that’s really the fundamental basics you have to understand.
How a computer system works at a very basic level and even at a more advanced level and same with networking understanding protocols and WLANs and different operations within switches and things like that those are kind of essential things that you should know.
If you’re really looking as security as a career for you now you could go and take like ethical hacking courses and pentesting courses and yes, they’re going to teach you what you need to know about being an ethical hacker or knowing how to pentest.
Right then you’re gonna learn a lot of networking stuff there a few different things about computer systems and things like that but there’s a lot of knowledge that you don’t get from learning these courses or they’re going through these courses there’s a whole gambit of information that is just left that you would need to understand.
So, whether it’s like a Windows operating system, for instance, you need to understand.
Do you know how user accounts are created? and managed? and how groups are created? and managed? as well as how the registry works? how different temples? were how to read Windows logs? like security logs? and things like that those are very important aspects of IT.
That you should have prior knowledge of before really jumping like headfirst into cybersecurity.
Now again you can do it without it, of course, I’m not trying to deteriorate you a little bit of information on things that you could be doing to help improve your path.
So if you have no prior knowledge or experience with IT a great place to start is with CompTIA A+ certification.
That certification really gives you a wide knowledge of how different computer systems networking cloud IoT devices.
Even some cybersecurity objectives are within the CompTIA A+ certification that will really give you a good fundamental knowledge of the things, that you should know about within technology to really help you understand.
also read how to become a hacker or an ethical hacker
What you’re doing within cybersecurity now you need to understand how some of these different technologies work because you’re there to secure them or if you’re looking to pen test or be an ethical hacker, you’re looking to you know manipulate these things in some ways.
so really knowing how some of the different things work within operating systems will greatly help you so the reason that this really comes up is that so many people ask you to know how can I get into cybersecurity with no prior IT experience or no prior IT knowledge.
Well, starting off with an A+ that’s a great place to start you know a plus is a great certification to really hone in on all the things that you should know at a very basic level.
Now from there, it’s really determining what area within cybersecurity you know you’re going for so even if you’re looking at application security?
Right, you want to be a developer in some way developing applications even then having an A+ can greatly help you because you have to understand how applications will function within different operating systems or how applications function when they’re communicating with the internet.
So that’s just really good knowledge to have now a lot of this stuff you can learn along the way but be proactive and do this ahead of time study for these things ahead of time so you’re prepared for this stuff.
So as you’re going through your pen test plus course or your certified ethical hacker course certifications you understand a lot of what they’re talking about prior and you’re not trying to backtrack and try to understand.
What they’re talking about within these different certification courses and things like that.
I hope this kind of makes sense because you know I don’t want you guys to just go into cybersecurity and assume that you know just because you take one of these courses that I mentioned.
that you know you’re going to learn everything that you need to know you’re never going to learn everything that you need to know first of all the information technology is an ever-growing field and you constantly will be learning new things.
But there is a great fundamental knowledge of technology that you can learn so compete is a plus comp T is Linux plus the network plus those are all great certifications.
that can show you all the fundamental knowledge that you need to know about these different technologies a plus covers many different areas within technology.
The network plus really shows you the fundamentals of how networking works the Linux plus that shows you a hall about the fundamentals of the Linux operating system there’s also captious cloud plus county a server plus those are just great certifications to study for to just understand at a fundamental entry-level.
How some different technologies work now a lot of people are going to tell you to start off with your CCNA that’s the best certification to get well yeah, the CCNA is definitely a great certification to get if you’re looking to specifically be network related only.
If you’re looking to be enough to go hacker or pen test yeah, the CCNA is definitely a great certification but still at a basic level not understanding how your computer systems work that can be a downside for you.
Like that can be detrimental towards your path so you guys don’t, by all means, have to go out and get an A+ or Network+ but study the material that is covered within those certifications it’s very important.
So, you know to build a home lab spin up VirtualBox spin up some different operating systems get a switch off eBay get a router off the eBay just understand.
some of the basics about these different technologies before you really dive deep into cybersecurity as a career, it will greatly help you down your path I hope this article helped you guys
Source : https://www.reddit.com/r/HackingTechniques/comments/fhuvj4/what_you_should_learn_before_cybersecurity/?utm_source=share&utm_medium=web2x
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes
Text
Tweeted
hrbartender: RT MorganZLee: Kronos Spring eSymposium: FREE Learning Opportunity for #HR and #Payroll Pros #Goalvana #HackingHR #HRTech #PeopleAnalytics #Reputation #PulseSurvey #Syncademy #Culture https://t.co/KgiKWVfOsn via hrbartender
— Ashish Bhalla (@Ashish__Bhalla) April 29, 2020
0 notes
Photo

Follow @hacker_b0t for more information . . 🌐www.techyrick.com . . . . #hackingbuddies #hackingout #hackingjacket #hackingsnacking #hackingconflict #hackingmemes #hacking_or_secutiy #prilaga #hackinghealth #hackingmexico #hackinginstagram #hackinglife #hackingthecity #hackinghorse #hackingcreativity #hackingblood #hackinggrowth #hacking_or_security #hackingcoffee #hackingjapanese #hackinghr #hackingteam #hackingrio #hackingorsecurity #hacking #hackingisourweapon #hackingnica🇳🇮 #hackingshit #hackingetico #hackingtools https://www.instagram.com/p/CQ6fgj_B-Y6/?utm_medium=tumblr
#hackingbuddies#hackingout#hackingjacket#hackingsnacking#hackingconflict#hackingmemes#hacking_or_secutiy#prilaga#hackinghealth#hackingmexico#hackinginstagram#hackinglife#hackingthecity#hackinghorse#hackingcreativity#hackingblood#hackinggrowth#hacking_or_security#hackingcoffee#hackingjapanese#hackinghr#hackingteam#hackingrio#hackingorsecurity#hacking#hackingisourweapon#hackingnica🇳🇮#hackingshit#hackingetico#hackingtools
0 notes
Link
If your web server is running on Apache Tomcat, you should immediately install the latest available version of the server application to prevent hackers from taking unauthorized control over it. Yes, that's possible because all versions (9.x/8.x/7.x/6.x) of the Apache Tomcat released in the past 13 years have been found vulnerable to a new high-severity (CVSS 9.8) 'file read and inclusion bug'—which can be exploited in the default configuration. But it's more concerning because several proof-of-concept exploits (1, 2, 3, 4 and more) for this vulnerability have also been surfaced on the Internet, making it easy for anyone to hack into publicly accessible vulnerable web servers. Dubbed 'Ghostcat' and tracked as CVE-2020-1938, the flaw could let unauthenticated, remote attackers read the content of any file on a vulnerable web server and obtain sensitive configuration files or source code, or execute arbitrary code if the server allows file upload, as shown in a demo below.
read more https://oyeitshacker.blogspot.com/2020/02/ghostcat-new-high-risk-vulnerability.html
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes
Link
Don’t Download Anything From An Untrusted SourceIt’s important to be careful about what you download onto your computer since most malware and spyware are willingly put onto the target’s computer without them fully understanding what it is they’ve just done.Always check the file extensions of what’s being downloaded to make sure everything adds up.For instance, if you’re downloading songs, they should be in an audio format such as .mp4 and not as an executable such as a .exe.These executable files can install just about anything on your computer while being extremely difficult to remove once installed.So, long as you always download from trustworthy sources, you can rest easy knowing you’re going to receive exactly what you asked for with no strings attached.Be wary of user-uploaded files since there’s often no way for websites to vet these files ahead of time.
https://oyeitshacker.blogspot.com/2020/02/best-and-effective-ways-to-keep-your-files-safe-from-hackers-guide.html
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes
Link
When you interview for the profile of a cybersecurity professional the interviewer will get into the technical bits to establish your level of expertise once they finish asking you about your professional experience, educational details, and more such obligatory questions.
Now, how technical they can get depends on the position of the job profile you are applying for as a cybersecurity professional. But in any way as a cybersecurity professional, you are expected to be well versed in your field of work.
In this article, we have curated some tips that can help you top your cybersecurity interview like a pro and impress the interviewers with your potential. With no further delay, let us get you started.
Emphasize your professional experience
Describing any relevant past job profiles can help the interviewer determine your level of professional expertise. Interest the interviewers with the backdrop of your previous engagements as it can give them an insight into your professional achievements and contributions.
As a cybersecurity professional, describe how you implemented strategic security measures and controls in your previous organizations. It can be anything related to your contributions to an organization and achievements at securing their cyberspace.
In any way, you need to make the interviewers understand what were your roles & responsibilities and how your work led to positive results for the organization.
This can make the interviewers weigh your performance and consequently recognize you as a suitable applicant.
read more Interview Tips for Cybersecurity Professionals 2020
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes
Text
Most Important Network Penetration Testing Checklist

Network Penetration Testing determines vulnerabilities in the network posture by discovering Open ports, Troubleshooting live systems, services and grabbing system banners.
The pen-testing helps an administrator to close unused ports, additional services, Hide or Customize banners, Troubleshooting services and to calibrate firewall rules. You should test in all ways to guarantee there is no security loophole.
Let’s see how we conduct a step by step Network penetration testing by using some famous network scanners.
https://www.reddit.com/r/HowToHack/comments/f9o20m/most_important_network_penetration_testing/?utm_source=share&utm_medium=web2x
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes
Link
Cybersecurity jobs have become one of the most in-demand jobs in the IT industry today. With demand, there is also competition, and to get a job in Cybersecurity, you need to be one of the best. While having the necessary Cybersecurity skills is half the job done, cracking the interview is another chapter altogether. And to help you crack the interview, we’ve compiled this list of top Cybersecurity interview questions and answers.
Skills matter and so does Certification! Check out this Cybersecurity Training.
1. What is Cryptography?
Cryptography is the practice and study of techniques for securing information and communication mainly to protect the data from third parties that the data is not intended for.
2. What is the difference between Symmetric and Asymmetric encryption?
read more Cybersecurity interview questions and answers.
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes
Link
Dark web browser are a most important concern for anonymous browsing and the most used applications in any device in current times is browsers, but not all your browsing histories are kept private and this is why deep or dark web makes a difference for complete privacy.Unlike Dark web browser, other browsers With cookies, personalized ads, browsing history being tracked, people tend to lose their privacy and not all of them would like to reveal their search history to a third party about what they are looking for on the internet.Google and Facebook have done this in the past for which they are being questioned now for their privacy breaches.With that being said, the Dark web browser will come in handy for people who would prefer complete anonymity over the internet.Deep Web exists parallel to the Surface
https://oyeitshacker.blogspot.com/2020/02/top-5-best-dark-web-browser.html
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes
Link
Web Application Pentesting Tools are more often used by security industries to test the vulnerabilities of web-based applications. Here you can find the Comprehensive Web Application Pentesting ToolsWeb Application Penetration Testing list that covers Performing Penetration testing Operation in all the Corporate Environments.
If your interest is in Learn hacking, then what is Ethical Hacking? and how to become a Hacker (Hacker) and Ethical Hacking, Certifications, Career & Salary? His complete information is here.Also, I suggest you the best cyber security courses in Delhi, DCS(Diploma in cybersecurity ) , PGDCS(Post Graduate Diploma in Cyber Security), Ethical Hacking Course
read more https://icssindia.in/web-application-security-tools-resources/
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes
Link
we have done the depth analysis and list you top 10 best Free Firewall software that provided extended security to protect your system from the bad actors.Generally, every computer is connected to the internet and is susceptible to being the victim of a hacker or an unwanted attack.The whole procedure, which is used generally, consists of mopping the network in search of a connected computer or laptop.Then the attacker simply looks for the security “hole” simply to gain access to the data present on the computer or laptop.All these threats could even become greater if the computer permanently remains connected to the internet.If the PC is connected without permanent supervision, then undoubtedly it will become a gold mine for the attackers or hackers.Hence, to protect us from the intruders, we have in our favor a fantastic tool which is known as Firewall.If your interest is in
Learn hacking
, then
what is Ethical Hacking
? and how to become a Hacker (Hacker) and
Ethical Hacking, Certifications, Career & Salary?
His complete information is here.Also, I suggest you the best
cyber security courses in Delhi
,
DCS
(
Diploma in cybersecurity
) ,
PGDCS
(
Post Graduate Diploma in Cyber Security
),
Ethical Hacking Course
What is a Firewall?
So, if we think about what firewall is the first and foremost thing that comes to our mind is that a firewall is a computer software program that restricts illegal and unapproved access to or from a separate or private network.Basically, the firewalls are tools that can be used to improve the security of computers attached to a network, just like LAN or the Internet.
read more https://oyeitshacker.blogspot.com/2020/02/10-best-free-firewall-software-2020-to.html
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes
Link
Computer Forensics tools are more often used by security industries to test the vulnerabilities in network and applications by collecting the evidence to find an indicator of compromise and take appropriate mitigation steps.
Here you can find the Comprehensive Computer Forensics tools list that covers Performing Forensics analysis and respond to the incidents in all the Environment.
Also, you can learn the Computer Hacking Forensics Investigator (CHFI) Course from one of the best Cybersecurity learning platforms.
read more https://icssindia.in/computer-forensics-tools/
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer #bhfyp
0 notes
Link
👉 part 3 Star Topology Comment your next topic below 👇🏻 ʟɪᴋᴇ ᴀɴᴅ ᴛᴇʟʟ ᴜs ᴡʜᴀᴛ ᴍᴏʀᴇ ʏᴏᴜ ᴡᴀɴᴛ ᴛᴏ ᴋɴᴏᴡ, ᴡʜɪᴄʜ ᴛᴏᴘɪᴄ sʜᴏᴜʟᴅ ɪ ᴘᴏsᴛ. --------------------------- 📲 icssindia.in --------------------------- If you Guys want to thank us, just give us a Like, and Follow this page. This really motivates us. 😊 --------------------------- 📲 icssindia.in --------------------------- ° ° ° ° ° ° ° ° ° ° #hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer #bhfyp
0 notes
Link
Comment your next topic below 👇🏻 ʟɪᴋᴇ ᴀɴᴅ ᴛᴇʟʟ ᴜs ᴡʜᴀᴛ ᴍᴏʀᴇ ʏᴏᴜ ᴡᴀɴᴛ ᴛᴏ ᴋɴᴏᴡ, ᴡʜɪᴄʜ ᴛᴏᴘɪᴄ sʜᴏᴜʟᴅ ɪ ᴘᴏsᴛ. --------------------------- 📲 icssindia.in --------------------------- If you Guys want to thank us, just give us a Like, and Follow this page. This really motivates us. 😊 --------------------------- 📲 icssindia.in --------------------------- Post Created on @picsart 📸 🔸🔸🔸🔸🔸🔸🔸🔸 📲Follow icssindia.in 📱 📲Follow icssindia.in 📱 📲Follow icssindia.in 📱 📲Follow icssindia.in 📱 🔸🔸🔸🔸🔸🔸🔸🔸 ° ° ° ° ° ° ° ° ° ° #hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #hackinghealth
0 notes
Link
Cybersecurity vs Network Security Comment your next topic below 👇🏻 ʟɪᴋᴇ ᴀɴᴅ ᴛᴇʟʟ ᴜs ᴡʜᴀᴛ ᴍᴏʀᴇ ʏᴏᴜ ᴡᴀɴᴛ ᴛᴏ ᴋɴᴏᴡ, ᴡʜɪᴄʜ ᴛᴏᴘɪᴄ sʜᴏᴜʟᴅ ɪ ᴘᴏsᴛ. If you Guys want to thank us, just give us a Like, and Follow this page. This really motivates us. 😊 ° ° ° ° ° ° ° ° ° ° #hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #hackinghealth #bhfyp @jeffbezos @amazon
0 notes