#hackingorsecurity
Explore tagged Tumblr posts
Photo

Edward snowden anime . 🌐www.techyrick.com . . #hackingtips #hackingshit #hackernews #hackingético #hackerofkrypton #hackerkitchens #hackers_empire #hackingnews #hackersstayaway #hackerearth #vinniehackeredits #hackingtools #hackerbrücke #lifehackers #hackingorsecurity #hacker_max #hackerkiralama #brainhacking #hackerz #vinniehackeredit #blackhathacker #whitehathacker #hackermemes #hackercraft #hackertdog #anonymoushackers #whacking #hacking_or_security #hacking #hacker https://www.instagram.com/p/CQkmwyOhmd7/?utm_medium=tumblr
#hackingtips#hackingshit#hackernews#hackingético#hackerofkrypton#hackerkitchens#hackers_empire#hackingnews#hackersstayaway#hackerearth#vinniehackeredits#hackingtools#hackerbrücke#lifehackers#hackingorsecurity#hacker_max#hackerkiralama#brainhacking#hackerz#vinniehackeredit#blackhathacker#whitehathacker#hackermemes#hackercraft#hackertdog#anonymoushackers#whacking#hacking_or_security#hacking#hacker
2 notes
·
View notes
Photo

Have you or someone you know had your account hacked? 😮Virus protection/security company, McAfee, says 22 percent of Internet users have been hacked at least once & 14 percent have been hacked more than once. I’m in the 14%. 🙀 My Facebook account was hacked 🕶️and I found out through friends who could tell by the stuff being posted on my feed that it wasn’t me. 🗣️ It’s a freaky sensation. Friends on IG have had their accounts hacked or impersonated. 👯 It’s hard to understand how it happens, like, why do people do this!? ⁉️ With impersonators, new accounts look identical in every way usually with a small modification to a username. 👬 If we see their avatar among new followers we might not notice and follow again. A couple of friends have had to start over on IG ▶️ which seems like a pretty depressing prospect. 🕵There are tons of articles that will tell you how to get your account back but I’m not sure they work, because if they did, people wouldn’t have to start over! The research takeaway is to protect your account to prevent it from happening in the first place. 🔐 Probably most of us are being careful by doing stuff like: --Use a strong password that is unique to every site 🔒 --Don’t share your password 🤫 --Use two-factor authentication (2FA) when it’s available 2️⃣ --Close accounts you don’t use 🗑️ --Use a separate email for your social media accounts 📧 Two other protective measures include: --Don’t allow tagging, and 🤳 --Make your account private ⛔ I won’t incorporate the last two measures, but the others are sensible things to do to help prevent losing an account. Have you or someone you know had an account hijacked? Was it resolved? . . . For those who expressed interest, @anewyorkkiss and I started a Clubhouse instead of trying to do a one-off room. 👋Upcoming on “Instagram Hubhouse�� — Monday, March 15 at 5 PM/PT —Topic: “WHEN CATFISH BITE: 🎣 Have you or a friend ever been catfished on IG?” 🐟 If you’re on Clubhouse, it would be cool to have you there. 👍 . . #seattleviews #seattlesunset #becareful #beproactive #securitytips #security #hackingorsecurity #protectyourself #clubhouse #clubhouseapp #Instagramhubhouse (at Jose Rizal Bridge) https://www.instagram.com/p/CMWfITWsjes/?igshid=13yxgv25v6ji3
#seattleviews#seattlesunset#becareful#beproactive#securitytips#security#hackingorsecurity#protectyourself#clubhouse#clubhouseapp#instagramhubhouse
3 notes
·
View notes
Photo

Hey Guy’s @definationtech Here . . . I Just Made This Post As I Think Most Of Us Don’t Know About Scamming Via Email’s… . . In The Recent Time Scamming Is The Most Popular Attack Used By Hacker’s And Social Engineer’s… . . @mastersinethicalhacking @google . . Tags:-) #email #emailmarketing #hacks #scam #scammers #phishing #hackingorsecurity #security #cybersecurityawareness #phishingattack (at India) https://www.instagram.com/p/B_cJ0zCn-wF/?igshid=vu5onwaxuhfy
#email#emailmarketing#hacks#scam#scammers#phishing#hackingorsecurity#security#cybersecurityawareness#phishingattack
1 note
·
View note
Photo
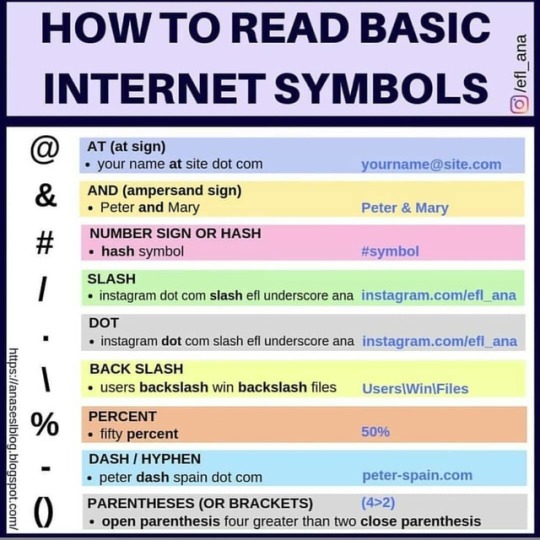
#kalilinux #computerengineering #hackers #art #hp #anonymus #security #cyberpunk2077 #computerscience #artificialintelligence #hacking_or_secutiy #hackingmexico #hackingorsecurity #hacking #mysteriousworld #mysteriousworldofwater #mysterious #cybersecurityengineer #artificialintelligenceai #hacks #learnjavascript #javascript #pythons #hackers_empire #technologylover #hackers_empire #securethebag #bugstagram #bugsbunny #programmer #interiordesign https://www.instagram.com/p/ByyR1i3gEoB/?igshid=ix4zs95vufcd
#kalilinux#computerengineering#hackers#art#hp#anonymus#security#cyberpunk2077#computerscience#artificialintelligence#hacking_or_secutiy#hackingmexico#hackingorsecurity#hacking#mysteriousworld#mysteriousworldofwater#mysterious#cybersecurityengineer#artificialintelligenceai#hacks#learnjavascript#javascript#pythons#hackers_empire#technologylover#securethebag#bugstagram#bugsbunny#programmer#interiordesign
7 notes
·
View notes
Text
Interrupt The Worry Cycle | Close to Nature

Perhaps, you have tried many methods to get rid of being worried about your future. You try but suddenly your mind is in the captivity of negativity. In a way, the cycle of being worried doesn’t seem to have an end for you. So, is there a solution?
Yes, there is! There are several activities you can do in order to avoid negative thoughts rushing to you.
:
:
#growthhacking#ethicalhacking#easydiy#lifetips#lifehacker#helpfultips#hackinginstagram#happyhacking#hackingorsecurity
0 notes
Photo

Cyber Security these days are as important as a Gem. So if you are having hurdles to cross to find the perfect Company that can help you in giving the best Cyber Security Solution. You are already at the right place. We have experience and experts to help you.
Visit - https://www.iraitech.com
#datasecurity#linux#ransomware#phishing#cybersecuritytraining#cybersecurityawareness#malware#infomrationsecurity#infosec#metasploit#windows#zomber#boom#python#keylogger#cybersecurity#hackingorsecurity#wifihacking#ethicalhacking#hackingteam#anonymoushacktivist#cybersquad#cybersecuritymajor#hackers#blackhamster#iraitech
0 notes
Photo

which language do you love the most? . . . . #programminglife #hackingout #webdesignspecialist #webdesigners #programmingisfun #codinglife #hackingtools #codinglove #programmingjoke #webdesigner #programmings #webdesignerlife #programmingmemes #programmingbits #hackingorsecurity #codingismylife #codingschool #webdesignservice (at Delhi, India) https://www.instagram.com/p/CQDIr5TlMyC/?utm_medium=tumblr
#programminglife#hackingout#webdesignspecialist#webdesigners#programmingisfun#codinglife#hackingtools#codinglove#programmingjoke#webdesigner#programmings#webdesignerlife#programmingmemes#programmingbits#hackingorsecurity#codingismylife#codingschool#webdesignservice
0 notes
Text

On a mission to awaken youngsters about the latest hacking and attack vectors like Evil Crow USB cables and malicious pen drives. Mr Surya Pratap, CEO & Director of Hacking club interacted with the students & faculty of Maharishi University of Information Technology, Noida campus.
#hacking#cybercrime#cyberattack#datatheft#workshop#hackingorsecurity#hacking_or_secutiy#hackingtools#MaharishiUniversity#Noida
0 notes
Photo

Check out todays episode of Delgado RANTS! We have to clean out the clutter! Quit that BS out! https://youtu.be/uHog9WfKN7U Change the mind. Change the world! Become NDESTRUCTIBLE #mindhacking #hacking #biohacking #neurohacking #hackingtools #funnelhacking #growthhacking #lifehacking #or #hackingnews #secutiy #biohackingsecrets #hackinglife #termuxhacking #househacking #ethicalhacking #hackingout #patternhacking #ikeahacking #happyhacking #brainhacking #whacking #learnhacking #hackinginstagram #belajarhacking #hackingorsecurity #travelhacking #hackinghealth #hackingrio (at Little Rock, Arkansas) https://www.instagram.com/p/CZHU5eJLbIH/?utm_medium=tumblr
#mindhacking#hacking#biohacking#neurohacking#hackingtools#funnelhacking#growthhacking#lifehacking#or#hackingnews#secutiy#biohackingsecrets#hackinglife#termuxhacking#househacking#ethicalhacking#hackingout#patternhacking#ikeahacking#happyhacking#brainhacking#whacking#learnhacking#hackinginstagram#belajarhacking#hackingorsecurity#travelhacking#hackinghealth#hackingrio
1 note
·
View note
Photo

Truth . . 🌐www.techyrick.com . . #häcker #hackerschool #hackers #househacking #vinniehackeredit #hackersmovie #learnhacking #hackinggrowth #häckerküchen #hackerkitchens #hackingtips #hackerbrücke #hacker_max #hackerone #ikeahackers #hackertdog #hackerinstagram #hackingorsecurity #hackerrank #vinniehackeredits #neurohacking #hackinglife #hackers_empire #hacking #hackingrio #crochethacking #hackingout #ikeahacking #quoteshacker #hackerfestzelt https://www.instagram.com/p/CQYkm1IBsTN/?utm_medium=tumblr
#häcker#hackerschool#hackers#househacking#vinniehackeredit#hackersmovie#learnhacking#hackinggrowth#häckerküchen#hackerkitchens#hackingtips#hackerbrücke#hacker_max#hackerone#ikeahackers#hackertdog#hackerinstagram#hackingorsecurity#hackerrank#vinniehackeredits#neurohacking#hackinglife#hackers_empire#hacking#hackingrio#crochethacking#hackingout#ikeahacking#quoteshacker#hackerfestzelt
0 notes
Text
What You Should Learn Before Cybersecurity?

Today I’m going to talk to you guys about things that you should know prior to considering cybersecurity as a career for you.
Now, this is something that I get very often on the IT career questions people ask you to know what type of basic should I know.
what other technologies should I know?
prior to considering this as a career different variation of those types of questions.
Now some people assume that you can just get into cybersecurity with no prior knowledge of technology whatsoever right and while yes that is definitely possible anything in life is possible but what should you have as far as knowledge goes before considering this field as a career for you and that’s really the fundamental basics you have to understand.
How a computer system works at a very basic level and even at a more advanced level and same with networking understanding protocols and WLANs and different operations within switches and things like that those are kind of essential things that you should know.
If you’re really looking as security as a career for you now you could go and take like ethical hacking courses and pentesting courses and yes, they’re going to teach you what you need to know about being an ethical hacker or knowing how to pentest.
Right then you’re gonna learn a lot of networking stuff there a few different things about computer systems and things like that but there’s a lot of knowledge that you don’t get from learning these courses or they’re going through these courses there’s a whole gambit of information that is just left that you would need to understand.
So, whether it’s like a Windows operating system, for instance, you need to understand.
Do you know how user accounts are created? and managed? and how groups are created? and managed? as well as how the registry works? how different temples? were how to read Windows logs? like security logs? and things like that those are very important aspects of IT.
That you should have prior knowledge of before really jumping like headfirst into cybersecurity.
Now again you can do it without it, of course, I’m not trying to deteriorate you a little bit of information on things that you could be doing to help improve your path.
So if you have no prior knowledge or experience with IT a great place to start is with CompTIA A+ certification.
That certification really gives you a wide knowledge of how different computer systems networking cloud IoT devices.
Even some cybersecurity objectives are within the CompTIA A+ certification that will really give you a good fundamental knowledge of the things, that you should know about within technology to really help you understand.
also read how to become a hacker or an ethical hacker
What you’re doing within cybersecurity now you need to understand how some of these different technologies work because you’re there to secure them or if you’re looking to pen test or be an ethical hacker, you’re looking to you know manipulate these things in some ways.
so really knowing how some of the different things work within operating systems will greatly help you so the reason that this really comes up is that so many people ask you to know how can I get into cybersecurity with no prior IT experience or no prior IT knowledge.
Well, starting off with an A+ that’s a great place to start you know a plus is a great certification to really hone in on all the things that you should know at a very basic level.
Now from there, it’s really determining what area within cybersecurity you know you’re going for so even if you’re looking at application security?
Right, you want to be a developer in some way developing applications even then having an A+ can greatly help you because you have to understand how applications will function within different operating systems or how applications function when they’re communicating with the internet.
So that’s just really good knowledge to have now a lot of this stuff you can learn along the way but be proactive and do this ahead of time study for these things ahead of time so you’re prepared for this stuff.
So as you’re going through your pen test plus course or your certified ethical hacker course certifications you understand a lot of what they’re talking about prior and you’re not trying to backtrack and try to understand.
What they’re talking about within these different certification courses and things like that.
I hope this kind of makes sense because you know I don’t want you guys to just go into cybersecurity and assume that you know just because you take one of these courses that I mentioned.
that you know you’re going to learn everything that you need to know you’re never going to learn everything that you need to know first of all the information technology is an ever-growing field and you constantly will be learning new things.
But there is a great fundamental knowledge of technology that you can learn so compete is a plus comp T is Linux plus the network plus those are all great certifications.
that can show you all the fundamental knowledge that you need to know about these different technologies a plus covers many different areas within technology.
The network plus really shows you the fundamentals of how networking works the Linux plus that shows you a hall about the fundamentals of the Linux operating system there’s also captious cloud plus county a server plus those are just great certifications to study for to just understand at a fundamental entry-level.
How some different technologies work now a lot of people are going to tell you to start off with your CCNA that’s the best certification to get well yeah, the CCNA is definitely a great certification to get if you’re looking to specifically be network related only.
If you’re looking to be enough to go hacker or pen test yeah, the CCNA is definitely a great certification but still at a basic level not understanding how your computer systems work that can be a downside for you.
Like that can be detrimental towards your path so you guys don’t, by all means, have to go out and get an A+ or Network+ but study the material that is covered within those certifications it’s very important.
So, you know to build a home lab spin up VirtualBox spin up some different operating systems get a switch off eBay get a router off the eBay just understand.
some of the basics about these different technologies before you really dive deep into cybersecurity as a career, it will greatly help you down your path I hope this article helped you guys
Source : https://www.reddit.com/r/HackingTechniques/comments/fhuvj4/what_you_should_learn_before_cybersecurity/?utm_source=share&utm_medium=web2x
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes
Photo

Kali Linux 2019.4 includes new undercover mode for pentesters doing work in public places⠀ ⠀ Offensive Security, maintainers of the popular Kali Linux open source project, released Kali Linux 2019.4, the latest iteration of the Kali Linux penetration testing platform.⠀ ⠀ Read more at https://www.helpnetsecurity.com/2019/11/27/kali-linux-2019-4/⠀ .⠀ ⠀ .⠀ .⠀ .⠀ .⠀ #marbersecurity #computerscience #cybersecurity #hackinginstagram #programming #hackers #ethicalhacking #businessgrowthstrategy #coding #security #termuxhacking #hackingtutorials #cybersecuritytips #cyberattack #kalilinux #hacking #hackerspace #linux #coders #growthhacker #hackingorsecurity #hackerman #socialmediamarketingstrategy #hacking_or_secutiy #hackingtools #securityawareness #hacker #pentesting #growthhacking #accesscontrol https://ift.tt/2rpDngg
0 notes
Photo

#think start questioning friends Love it? If yes than comment and follow for more post like this and Start doing experiments Today 💻Always Learn The Deepest Point 💻 🔥Who is A hacker? A hacker is a Creative person and a creative programmer, CRYTOGRAPHER,Who have Knowledge about Networking, Opreting Systems,Hacking and a Bestest and Creative Social Engineer Who Control Anyone's mind A HACKER IS A CREATIVE AND KNOWLEDGEABLE HUMAN this is a hackers defination by me do you agree? Comment and Are you Want to become A Hacker? Comment And very soon I make an Video That help you to be safe on internet are you exited? For Notification Subscribe our YouTube Channel Link is in Bio comment it💻🔥 Are you want to become a Hacker? 🔥💻 Keep supporting 😊😉 Love you All || Follow @hacking_or_security For more and daily update stay connected with us @hacking_or_security @hacking_or_security #linux #kalilinux #commands #os #ubuntu #hacker #whatis #technology #technical #creativity #protocol #hacked #cybercrime #hackers #hacking #cybersecurity #internet #safe #internet #hacking_or_secutiy #terminal #algorithm #malware #virus #whatis #it #hackignews #basics #learning #artificialintelligence #hackingorsecurity @hacking_or_security || Stay connected for daily and more update @hacking_or_security
0 notes
Photo

Follow @hacker_b0t for more information . . 🌐www.techyrick.com . . . . #hackingbuddies #hackingout #hackingjacket #hackingsnacking #hackingconflict #hackingmemes #hacking_or_secutiy #prilaga #hackinghealth #hackingmexico #hackinginstagram #hackinglife #hackingthecity #hackinghorse #hackingcreativity #hackingblood #hackinggrowth #hacking_or_security #hackingcoffee #hackingjapanese #hackinghr #hackingteam #hackingrio #hackingorsecurity #hacking #hackingisourweapon #hackingnica🇳🇮 #hackingshit #hackingetico #hackingtools https://www.instagram.com/p/CQ6fgj_B-Y6/?utm_medium=tumblr
#hackingbuddies#hackingout#hackingjacket#hackingsnacking#hackingconflict#hackingmemes#hacking_or_secutiy#prilaga#hackinghealth#hackingmexico#hackinginstagram#hackinglife#hackingthecity#hackinghorse#hackingcreativity#hackingblood#hackinggrowth#hacking_or_security#hackingcoffee#hackingjapanese#hackinghr#hackingteam#hackingrio#hackingorsecurity#hacking#hackingisourweapon#hackingnica🇳🇮#hackingshit#hackingetico#hackingtools
0 notes
Photo
Truth 🤫 . . 🌐www.techyrick.com . . #hackerbrücke #wifihacking #hackinghorse #hackingthecity #househacking #neurohacking #growthhacking #hackinggrowth #anonymoushackers #hackerkitchen #hackertdog #bluehacker #blackhathacker #hackingtool #hackingético #whacking #pubghacker #hackinghr #biohacker #hackingout #growthhacker #hackingorsecurity #androidhacking #hackinginstagram #hackingmemes #hackers #biohackers #quoteshacker #hacking #hacker https://www.instagram.com/p/CQ0FBHPB_9C/?utm_medium=tumblr
#hackerbrücke#wifihacking#hackinghorse#hackingthecity#househacking#neurohacking#growthhacking#hackinggrowth#anonymoushackers#hackerkitchen#hackertdog#bluehacker#blackhathacker#hackingtool#hackingético#whacking#pubghacker#hackinghr#biohacker#hackingout#growthhacker#hackingorsecurity#androidhacking#hackinginstagram#hackingmemes#hackers#biohackers#quoteshacker#hacking#hacker
0 notes
Link
If your web server is running on Apache Tomcat, you should immediately install the latest available version of the server application to prevent hackers from taking unauthorized control over it. Yes, that's possible because all versions (9.x/8.x/7.x/6.x) of the Apache Tomcat released in the past 13 years have been found vulnerable to a new high-severity (CVSS 9.8) 'file read and inclusion bug'—which can be exploited in the default configuration. But it's more concerning because several proof-of-concept exploits (1, 2, 3, 4 and more) for this vulnerability have also been surfaced on the Internet, making it easy for anyone to hack into publicly accessible vulnerable web servers. Dubbed 'Ghostcat' and tracked as CVE-2020-1938, the flaw could let unauthenticated, remote attackers read the content of any file on a vulnerable web server and obtain sensitive configuration files or source code, or execute arbitrary code if the server allows file upload, as shown in a demo below.
read more https://oyeitshacker.blogspot.com/2020/02/ghostcat-new-high-risk-vulnerability.html
#hacking #hackingtools #ethicalhacking #secutiy #or #hackinginstagram #hackinglife #hackingnews #hackingout #happyhacking #househacking #biohacking #growthhacking #lifehacking #hackingorsecurity #hackingmexico #learnhacking #whacking #hackingshit #brainhacking #travelhacking #termuxhacking #belajarhacking #ikeahacking #hackinghr #hackingrio #hackingthecity #hackingbuddies #programmer
0 notes