#hacks 3.05
Text





HACKS (2021– ), 3.05.
#hacks spoilers#hacks#hacksedit#hacks hbo#deborah vance#ava daniels#hacks season 3#hacks 3.05#by me#this episode was too much for my poor heart#they said avorah engame 'one day' but it's wishful thinking#the song they chose while they were holding hands will haunt me forever in fact that was the song i was listening to while doing this#it's not my best gifset but i needed to do this#DEBORAH YOU NEVER KNOW UNTIL YOU TRY
74 notes
·
View notes
Text

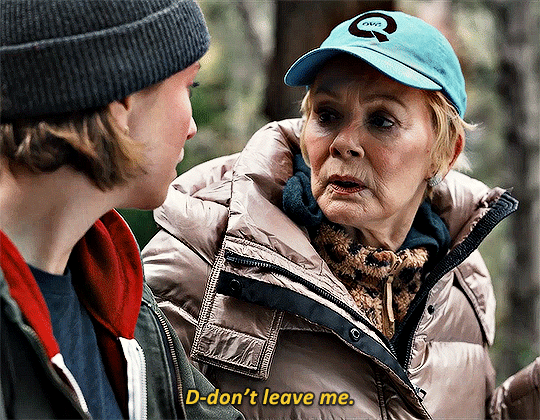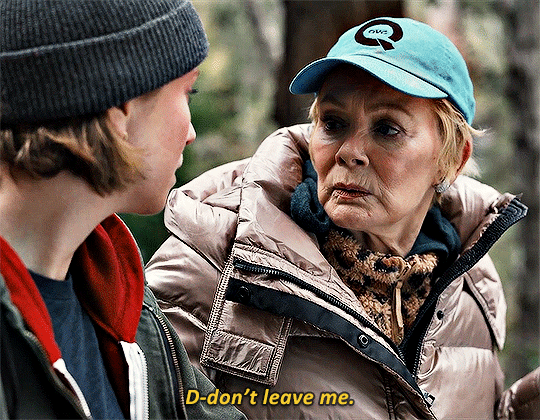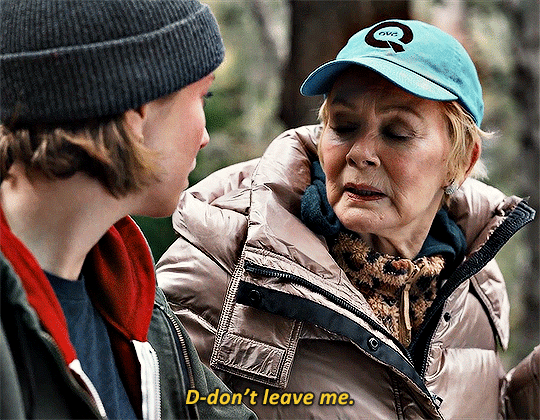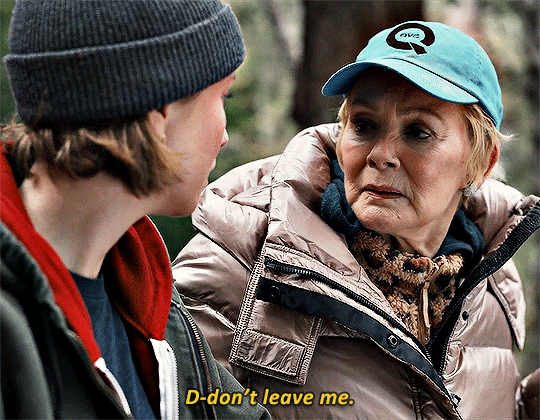

HACKS 3.05 One Day
922 notes
·
View notes
Text




Hacks 2.05 | Hacks 3.05
494 notes
·
View notes
Text










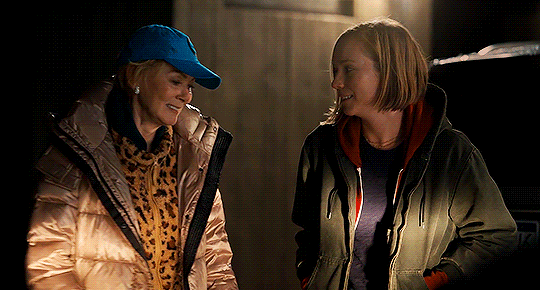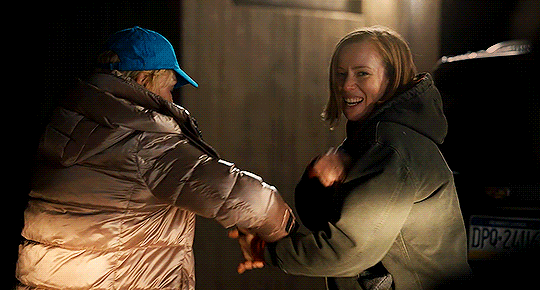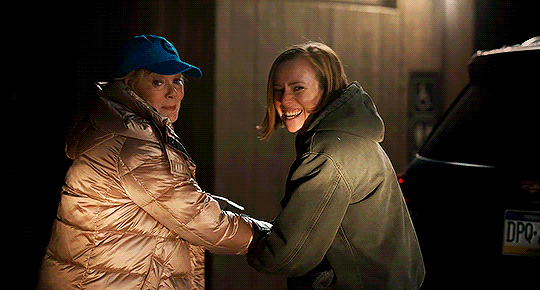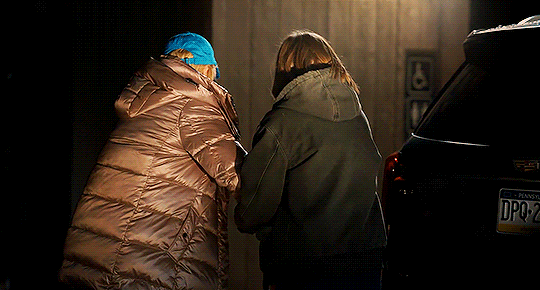
I think I should go ahead and find help.
No, don't leave me.
HACKS | 3.05
#hacks#hacks hbo#hacksedit#ava x deborah#ava daniels#deborah vance#hacks spoilers#photoset#yeah these two episodes required separate gifsets!!#a full episode of just the two of them wandering around the woods holding onto each other and talking?#a dream#lets not even START on them holding hands on the bikes
485 notes
·
View notes
Text














A: Happy with a demotion? Louis offered me the head writer job and I turned it down. You specifically told me to be ambitious. Except when it inconveniences you, I guess. God, you are so selfish.
D: Yes, I am. You have to be selfish.
A: Well I don't want to be. I don't want to be a shark or whatever the fuck. I wanted to do it with you.
D: I want that too. I just can't have you be head writer.
HACKS 3.05 / 3.09 dir. Lucia Aniello
#hacks hbo#ava x deborah#ava daniels#deborah vance#hacksedit#gifs#tvfilmgifs#tvandfilm#this didn't like flow as well as i wanted it to#cause there was just SO much i could have chosen#but i'm trying to just be like deb see's it as one or the other#ava is like WHY NOT BOTH#WHAT IF THEY'RE THE SAME D#AND WHY CAN'T YOU ACCEPT THAT
342 notes
·
View notes
Text




HACKS 3.05|3.06
338 notes
·
View notes
Text
HACKS 3.05 Ava and Deborah holding hands on the bikes
27 notes
·
View notes
Text
Ok finally watching. 3.05 and 3.06 of Hacks! And will get to take ‘hacks’ off my blocked tags list. It’s been like being a dog at a house party these last couple days. Being tucked away in a distant room, but knowing something exciting or terrible is happening somewhere nearby.
3 notes
·
View notes
Text
THE BOLD TYPE’ SEASON 3 EPISODE 5 PREVIEW: HACKED
go to http://www.remediality.com/the-bold-type-season-3-episode-5-preview-hacked/
Read this interesting summary of Tuesday’s TBT 3.05 in regards to Kat and Tia. It’s given me Kadena hopes again! 🤞🏼🧕🏼😺
3 notes
·
View notes
Text
Gemini Login | Sign in | Gemini The Most Secure Crypto
Gemini login was started in 2014 and is based in New York, New York, which means it is one of a few cryptocurrency exchanges that is regulated in the U.S. Specifically, it is regulated by the New York State Department of Financial Services (NYSDFS).
What Do They Offer?
Gemini has more than 20 cryptocurrencies, including its very own currency called Gemini bucks (GUSD). You can trade and save cryptocurrencies with Gemini.
With a collaboration with Samsung, Gemini Login powers the Samsung Blockchain. Consumers in the UNITED STATE and also Canada can connect their Samsung Blockchain Budget to the Gemini application to trade money.
Funding Your Gemini Login Account
You’ll have to fund your account from a checking account. It can’t be funded making use of a debit or bank card. The maximum everyday funding limit is $500 USD and also $15,000 USD monthly. The daily withdrawal restriction is $100,000 USD.
If you have cryptocurrencies in an additional off-site budget and also want to money your Gemini account utilizing those money (crypto-to-crypto), you can do that as long as the currencies are BTC, ETH, BCH, LTC, or ZEC.
Gemini Login Earn – Crypto Savings
Gemini recently released their Gemini Earn, which is the ability to earn rate of interest on your crypto. Now you can gain as much as 7.4% on various tokens, or 3.05% if you intend to earn with your Bitcoin.
You can see how Gemini compares to the best crypto savings accounts here.
Mobile Trading
Like several crypto exchanges, Gemini has a mobile app that you can trade from. You’ll find that it’s easy to use and also similar to the desktop platform. If you want to implement intricate trades, it’s most likely best to do those on the desktop platform. Facility trades can get a little bit tedious on the mobile application.
Gemini Dollar
The Gemini dollar ™ is a stablecoin that can be utilized in all type of deals from spending to lending to spending. Its backed by US bucks held at State Road Financial Institution and also Trust Company as well as offers 1:1 transferability back to United States bucks any time. And also Gemini has partnered with BlockFi to supply savings accounts for your Gemini dollars with rates of interest of approximately 7.4% APY.
Are There Any Fees?
Yes, Gemini does bill payment prices for trading on its system. There is an ease cost of 0.50% over the marketplace price. To identify the comfort charge amount, increase 0.50% (1.005) by the quantity of currency you want to get.
There is likewise a flat transaction fee for orders placed via their web or mobile applicaitons. The fee varies from $0.99 to 1.49% of your order value, as shown in the chart below.
How Do I Open An Gemini Login Account?
The account sign-up procedure for Gemini Login is straightforward and straightforward. You will require to verify your identity utilizing a type of ID. You’ll likewise need to link your phone for two-factor authentification.
Lastly, you’ll need to money your account. Gemini uses Plaid to connect with your financial institution acount or card provider. As soon as your application has been approved and your account has been moneyed, you can start making trades! Begin with Gemini as well as earn $10 in complimentary Bitcoin!
Is My Money Safe?
As long as it’s been in operation, Gemini Login has not been hacked. Like Coinbase, USD saved in your Gemini account is FDIC guaranteed.
Gemini started with a “security-first” mentality. They utilize protection as well as conformity by being certified in SOC 1 Type 1, SOC 2 Kind 1 and Kind 2. All of that conformity suggests you’ll need to be prepared to surrender several of your individual information such as e-mail address, bank account details, phone number, as well as some type of ID when opening up an account.
Is It Worth It?
Gemini Login is among one of the most protected cryptocurrency exchanges out there. Safety and security is its primary selling point. It is a UNITED STATE based company as well as the platform is easy to use.
If your crypto trading is mostly in preferred currencies such as Bitcoin, Ethereum, Litecoin, Bitcoin Cash, or Zcash, you’ll possibly delight in using Gemini. For all of those reasons, Gemini is certainly worth having a look at as a cryptocurrency system.
POSTS
LIKES
ARCHIVE
This Tumblr has hardly any posts. None at all, in fact.
1 note
·
View note
Photo

Gemini Login – Cryptocurrency Exchange to Buy Bitcoin
Who Is Gemini Login?
Gemini login is a cryptocurrency exchange. It was started by the Winklevoss twins (Cameron Winklevoss and Tyler Winklevoss). You might recognize those names. They created Connect U, which was the predecessor to Facebook.
Gemini was started in 2014 and is based in New York, New York, which means it is one of a few cryptocurrency exchanges that is regulated in the U.S. Specifically, it is regulated by the New York State Department of Financial Services (NYSDFS).
What Do They Offer?
Gemini has more than 20 cryptocurrencies, including its very own currency called Gemini bucks (GUSD). You can trade and save cryptocurrencies with Gemini.
With a collaboration with Samsung, Gemini Login powers the Samsung Blockchain. Consumers in the UNITED STATE and also Canada can connect their Samsung Blockchain Budget to the Gemini application to trade money.
Funding Your Gemini Login Account
You’ll have to fund your account from a checking account. It can’t be funded by making use of a debit or bank card. The maximum everyday funding limit is USD 500 and also USD 15,000 monthly. The daily withdrawal restriction is USD 100,000.
If you have cryptocurrencies in an additional off-site budget and also want to money your Gemini account utilizing that money (crypto-to-crypto), you can do that as long as the currencies are BTC, ETH, BCH, LTC, or ZEC.
Gemini Login Earn – Crypto Savings
Gemini recently released their Gemini Earn, which is the ability to earn the rate of interest on your crypto. Now you can gain as much as 7.4% on various tokens, or 3.05% if you intend to earn with your Bitcoin.
You can see how Gemini compares to the best crypto savings accounts here.
Mobile Trading
Like several crypto exchanges, Gemini has a mobile app that you can trade from. You’ll find that it’s easy to use and also similar to the desktop platform. If you want to implement intricate trades, it’s most likely best to do those on the desktop platform. Facility trades can get a little bit tedious on the mobile application.
Gemini Dollar
The Gemini dollar ™ is a stable coin that can be utilized in all types of deals from spending to lending to spending. It’s backed by US bucks held at State Road Financial Institution and also Trust Company as well as offers 1:1 transferability back to United States bucks any time. And also Gemini has partnered with BlockFi to supply savings accounts for your Gemini dollars with rates of interest of approximately 7.4% APY.
Are There Any Fees?
Yes, Gemini does bill payment prices for trading on its system. There is an ease cost of 0.50% over the marketplace price. To identify the comfort charge amount, increase 0.50% (1.005) by the quantity of currency you want to get.
There is likewise a flat transaction fee for orders placed via their web or mobile applications. The fee varies from $0.99 to 1.49% of your order value, as shown in the chart below.
How Do I Open An Gemini Login Account?
The account sign-up procedure for Gemini Login is straightforward and straightforward. You will require to verify your identity utilizing a type of ID. You’ll likewise need to link your phone for two-factor authentification.
Lastly, you’ll need to money your account. Gemini uses Plaid to connect with your financial institution account or card provider. As soon as your application has been approved and your account has been moneyed, you can start making trades! Begin with Gemini as well as earn $10 in complimentary Bitcoin!
Is My Money Safe?
As long as it’s been in operation, Gemini Login has not been hacked. Like Coinbase, USD saved in your Gemini account is FDIC guaranteed.
Gemini started with a “security-first” mentality. They utilize protection as well as conformity by being certified in SOC 1 Type 1, SOC 2 Kind 1, and Kind 2. All of that conformity suggests you’ll need to be prepared to surrender several of your individual information such as e-mail address, bank account details, phone number, as well as some type of ID when opening up an account.
Is It Worth It?
Gemini Login is among one of the most protected cryptocurrency exchanges out there. Safety and security is its primary selling point. It is a UNITED STATE-based company, as well as the platform, is easy to use.
If your crypto trading is mostly in preferred currencies such as Bitcoin, Ethereum, Litecoin, Bitcoin Cash, or Zcash, you’ll possibly delight in using Gemini. For all of those reasons, Gemini is certainly worth having a look at as a cryptocurrency system.
POSTS
LIKES
ARCHIVE
Gemini login – A smart way to access and invest in crypto exchange services
Sign up for a new Gemini Login account quickly by providing the required information on the sign-up page. To create your Gemini.com account, follow these steps: If you are new or a beginner in using the Gemini account and looking to create an account on the Gemini login account, then this w
Gemini is a cryptocurrency exchange platform that has grown in popularity over the previous few years. This is due to its user-friendly design, which is simple, safe, and ensures accounts in US dollars. The Gemini login Platform makes it simple to deposit and withdraw digital currency, and it has some of the largest deposit and withdrawal limitations of any exchange wallet. Gemini safeguards the safety of your cash by employing various layers of security. Cleverly became the first exchange platform to be licensed by the Ethereum exchange, much like its
clever name (a zodiac sign for twins that represents the company’s founders).
You’ll need a Gemini account to invest, trade, store, purchase, and sell cryptocurrencies with Gemini.
How do you sign in to your Gemini login account?
Signing into your Gemini login account is a basic and straightforward procedure. To gain access to your Gemini login account, simply open your Google Chrome browser and type https://exchange.gemini.com/signin, followed by your email ID and password.
If you forget your password, click the ‘Reset your Password’ option and follow the on-screen instructions to reset it.
Simply tap the 'Account’ symbol in the upper right-hand corner of your mobile phone to sign in to your Gemini login account. Then select 'Sign in’ from the drop-down menu. To access your Gemini login account, enter your email address and password.
Benefits of a Gemini login account include:
To reduce the danger of hacks and theft, the majority of Gemini coins and digital money are stored offline, except for a small percentage.
Insurance: Federal Deposit Insurance Corporation insures Gemini login accounts funded with US currency. Aside from that, their monies are held in a Chartered bank in New York for further security.
Compliance with banking standards and registration: Gemini complies with all banking norms and regulations, making it a safe option for both individual and institutional crypto investors.
Gemini login account offers a user-friendly interface that is straightforward and easy to use. It is appropriate for both new and seasoned investors.
Gemini login
Gemini
How do I Log in to my Gemini account?
To log into your Gemini account on a web browser, please navigate to https://exchange.gemini.com/signin where you can enter your email address and password to access your Gemini account. If you have forgotten your password, please click on the “Reset your password” link down below where you can follow the prompts to reset your password.
To log into your Gemini account on the mobile app, press the “Account” icon in the upper right-hand corner, followed by the “Sign In” option. A screen will then appear on your mobile app where you can enter your email address and password to access your Gemini account.
Gemini Login - Cryptocurrency Exchange to Buy Bitcoin and Ether
What is the difference between my login pin and my password?
Your login pin is associated with accessing your Gemini app, while your password is used to log in to both the Gemini app and the Gemini website. You can also opt to use Touch ID and Face ID to sign back into your account on the Gemini app if your phone has these features.
Why is it asking me for a 7 digit token upon login?
When Gemini started using Authy for 2FA services, all Gemini accounts were provided with an Authy ID. Because it is more secure, this also became the default method for 2FA for all Gemini accounts. You can download the Authy app on the Authy Creation page and create an account under the verified phone number on your Gemini account. Once you do so, your token should appear.
What is two-factor authentication?
Two-factor authentication (2FA) is a required security measure to confirm you are in control of your login credentials before signing in to better secure your account. 2FA is a requirement and can not be disabled for your account. At this time, we offer 2FA via Authy, SMS, and hardware security keys through Web Authn for logins. We will let our customers know if we decide to integrate any other form of verification for 2FA. If you have updated the phone number (or update your mobile device) registered to your account, please take a look at this support article to regain access to your account:
#account login gemini#gemini acount login#login account#gemini login signin#signin#gemini account login#login account wallet#loginwallet#wallet login#geminilogin#login gemini
0 notes
Note
Thoughts on tonight's Flash episode?
It was my least favorite of the season so far, but it was still enjoyable to me. I really loved Cisco and Cynthia (!!!), and I thought Breacher was a lot of fun. The only part of that storyline that got a little meh to me was when he started trying to fight Ralph, but at least it gave Cisco the chance to be a hero. Anyway, the opening scene + Jitters + the goodbye scene made the story for me.
Ralph is… I really liked Hartley’s performance, but the fat jokes and body humor were a bit much for me. I thought it was an odd choice to make him someone who would plant evidence, but I liked that it caused Barry some self-reflection about the metahuman prison and whatnot. I also liked their tension and how they remained prickly even at the end of the ep, but I’m annoyed that they want to do for Ralph what they didn’t really want to do for Wally.
I am so happy Iris got to do some investigating and was very naturally presented as a leader in several scenes, I just missed her presence since she was such a big part of the last three episodes. I also would like to see some more WA quality alone time, but we have the rest of the show for it, so I’m not pressed.
Didn’t really like that Joe had no scenes processing the info from Cecile until he bought those cigars, and that scene was silent. So he seemed shocked and almost unhappy about the news, but then surprise he’s super happy. And like I mentioned before, I was not a fan of the body humor this week. A little goes a long way for me when it comes to that, and anything with a fatsuit pisses me off. But yay that Barry knows about Devoe!
So how the heck did the ep for next week get out?
No idea, but it looks like the girl gifing the episode got in trouble because she deactivated.
@eboniangelvibez said:
I’ve read on several blogs, people upset about sexy times (or the lack thereof) between WA. While I’m not exactly sure why there hasn’t been more (tv rating, lack of thought on the part of the writers, it’s a family show, etc.) I don’t think it’s really needed. B+I have a healthy RL based on genuine love+friendship. The couples therapy allowed Iris to vent to Barry without being OTT. Admittedly, if it works out that WA get busy after the girls save the city in 4x05 I won’t be mad! Your thoughts?
At this point, I wish we would get sexytimes so that other people would be happy and not upset about it. But I personally am not missing them, and if I ever want one I read fanfic. I definitely wouldn’t be mad if we got one, haha, but I think something like 3.04, 3.10 or tonight’s Cisco/Cynthia scene is totally possible for either 4.05 or 4.09.
I’ll be the first to admit that if they aligned The Flash to be more like the comics, losing the STAR Labs team in the process, I’d be less likely to watch. I think they’d lose a huge chunk of their audience. Having said that, the writers and producers could have done a much better job utilizing KF a lot better, rather than just sending him away. Like hello why not show him being a hero at school or something? Idk its all extremely weird
Yeah, even outside of STAR Labs, the treatment of Wally since his arrival has been subpar.
I have to be honest with the way the writers & EPs are treating Wally it makes me a bit nervous for the future of Iris & WA, I mean yes they seem to like both now, but what’s to say that they won’t summarily change their minds down the road. I can’t help but think about Laurel from Arrow & how they treated that character. I think I have lost all trust in these writers & EP’s.
You can say that about anything, though. Writers can change their minds at any given moment and write something else, unfortunately. But Wally has never been treated right and neither was Laurel, whereas WA have been handled very carefully. So I don’t think it would be the same situation.
Has Danielle Nicolet been on set since 3.05? Yeah most of this pregnancy will take place off screen. I still don’t understand the purpose of this unless they want to give th the Tornado Twins only difference is they’ll be regular kids w no powers 😕
I thought she might have filmed for the crossover because she flew to Vancouver around that time, but there were no pics of her filming or on set, so there’s no telling. And yes, the poor woman didn’t even get to be there when Joe announced her pregnancy lmao. No, she will not birth the Tornado Twins. AJK said they were doing it because they thought it was the funniest thing that could happen to Joe.
@ “small quibble” anon:
I totally hear your concern, and would like to say that we are definitely joking because I doubt the show will ever go there. But we will address it on our next podcast! Thanks for the feedback, btw.
You don’t think Fe takes over SL in the GNO episode, do you? There she is in front of the computer as usual in the promo pics. I hope she asked the boss lady, Iris, for permission first. Lol
I hope she doesn’t! I think they’ll still have Iris be the one organizing and leading, even if Felicity has to hack something.
#the flash#eboniangelvibez#anonymous#tatiana's thoughts#more asks under the cut#long post for ts#spoilers
10 notes
·
View notes
Text
What legal action you can take when your website is Hacked?
This article is written by Mayank Bansal, pursuing a Diploma in Cyber Law, Fintech Regulations and Technology Contracts from Lawsikho.com. Here he discusses “What legal action you can take when your website is Hacked?”.
Introduction
With the evolution of technology and the cheap data rates, India has become the second-largest internet user’s country in the world, with around 451 million monthly active users in the year 201811. Further, it is also expected that internet users will grow as much as 666.4 million by the year 2023. Although, with this appalling rise in the internet users, the internet-based crime is also increasing, due to which the tech giants are under constant fear of data breaches. According to a report of Computer Emergency Response Team (CERT), there has been 292% hike in the hacking cases in India from 2015 to 201822. Further relying upon which the joint study by PwC India and Data security council of India (DSCI) suggested that the cybersecurity market in India will grow from $1.97 Billion in 2019 to $3.05 Billion by 2022. These reports in end impose a great question, what Legal action should a person take who is a victim of hacking?
What is hacking and who is a hacker and how is it different from cracking?
In a simple word, hacking is a skill of identifying a weakness in network security, through which a hacker could get unauthorized access to personal data. Although with the term “Hackers” there are general misconceptions among the people, that the hackers are the bad people, who act illegally in order to gain unauthorized access to personal information of the individual. However, in actual, there are three types of hackers -white, black and grey hackers and depending on the type of hacker there are categorized as a good or bad hacker.
White Hat Hackers
White hat hackers are considered to be good hackers, who are generally employed by the tech organizations in order to strengthen the security of their systems. These hackers have prior permission to exploit the organization’s security networks and look for the loopholes in their system. These hackers intimate the organization about the loopholes in their security so that it can be fixed.
Black Hat Hackers
Black Hat hackers are considered to be bad hackers, who attempt to gain unauthorized entry to the personal information of the individuals and exploits them for malicious reasons. This kind of hackers tries to inflict damage on the organizations by compromising their system, altering functions of the websites or shutting down their whole systems.
Grey Hat Hackers
Grey Hat Hackers, tries to exploit the networks in a very similar way as the black hat hackers do, but the Grey hat hackers exploit the networks without any kind of malicious intent, as they disclose the loopholes in the networks to the administrators or the intelligence agencies. These people generally also offer to fix the vulnerabilities by charging a nominal fee from the network owner.
So, Hacking could be considered as a process of gaining access to computer systems without any authorization, for either good or bad purposes. However, it is not necessary that the hackers are behind all the cyber-attacks in societies. We’ll truth is that our media uses the term “Hacking” in a derogatory sense to describe all the cyber-attacks. In fact, the Majority of cyber-attacks fall under the definition of “Cracking”.
The basic difference behind the “Hacking” and “Cracking” is that Hackers work towards building the security of the network, whereas the Cracker work towards breaking it. Crackers also gain unauthorized access to a computer system, but with a criminal intention. In other words, they act as Black Hat hackers, by stealing personal information of users or by destroying important files, disclosing crucial information’s or by selling sensitive data of individuals for personal gains.
Laws against Black Hat Hackers/Crackers
In India, the Information Technology act, 2008 tries to protect every individual from the Black hat Hackers i.e. bad hackers/crackers. Section 43 (penalty and compensation for damage to computer, computer system, etc) of the act, specifies almost every kind of hacking/cracking offence from illegal access, extraction of data, contamination of data, network disruption, denial of access, manipulation of data, destruction, removal or alteration of data to data theft, illegal concealment of data, etc. Further, this section imposes a penalty on a hacker/Cracker, to compensate for the damages which are incurred by the victim due to his acts. Adding to this, Section 66 (computer-related offences) of the act further punishes the individual, who dishonestly or fraudulently does any act referred under Section 43 of the Act, with the punishment for a term which may extend to three years or with fine which may extend to five lakh rupees or with both.
Therefore, relying on these provisions, one should rest assured that the Indian law duly supports the innocent people against the act of hacking.
Now, if the website of any organization is hacked then he should firstly stay calm, as he is protected by the law of India. Now as an immediate action, he should take the following steps:
Take the website offline: as an immediate step the organization shall temporarily shut down the website, while it is fixed and protected. This step is taken to prevent further damage to the clients of the organization.
Secondly, immediately file a cyber complaint: as an immediate step, file a cyber complaint in the cyber cell of the district in which the registered office of the organization is located. If there is no cyber cell in the district, the organization could also file a complaint online www.cybercrime.gov.in (which also provides an advantage of tracking the complaint, which is otherwise not available)
A cyber complaint is drafted in a very similar way as FIR is drafted. The important thing to remember is that all necessary details of the crime are mentioned in the complaint. Further, with the cyber complaint, some copies of documents are required to be attached, which are generally not attached when the FIR is drafted. Here I am providing the general list of documents which are indicative but not the exhaustive list of documents, to be attached with any cyber complaints:
Server Logs: A copy of the server log shall be necessarily attached to the complaint. This log file contains details of the activities which are performed on the portal on the day to day basis.
Hard as well as Soft copy of the defected material: a copy of the material that has been affected by the illegal act of the hacker. This is submitted as evidence in a cyber cell.
Hard Copy of portal: Hard copy of the original portal and the defaced one shall be attached to the complaint. So, as to show the material defect caused by the hacker.
Personnel Details: An Organisation shall attach a comprehensive list of the employees with their cyber complaint, who is having access to the source codes of the websites.
Suspicions: if the organization is suspicious about the hacker, then they shall mention the name of such suspected person, in their cyber complaint. It could help the cyber cell in its investigation.
Thirdly announce in the public: well reader might find it shocking, Why I am asking the organization about informing the public about their network breach?
Because it is important to understand that poorly handled cyber-attacks, could impact the long-term reputation of any organization, further affecting the customers and investors of the organization for years. Although, I duly accept that declaration of cyber attack in the public would affect the reputation of an organization, but for the short term. However, the early strategical communication about the cyber-attack could prevent further damage to the organization and its clients. Therefore, considering this, a clear and consistent message from the organization, could make a huge difference by minimizing the long-term reputation impact on the organization.
Click Above
Complications while pursuing legal actions against Hackers/Crackers
NON-ACCEPTANCE OF COMPLAINT BY POLICE OFFICIALS: While filing a physical complaint in the local police station where the victim is located, or where the offence is committed against the individual, it is often found that cyber cell and police station dispute their jurisdiction, as generally, the crime does not place in the area in which the organization is located. As cybercrimes are considered geography less and borderless.
However, to avoid the harassment of Police station and cyber cell, the government has initiated an online portal (www.cybercrime.gov.in) for filing a cyber complaint. Wherein, a complaint, can easily file their complaint and it will be automatically assigned to the respective cyber cell/Police station. Further, Complainant gets an added advantage of tracking the status of their complaint, if the complaint is lodged through this portal.
NON-TRACEABILITY OF HACKER/CRACKER: It is often found, that in the majority of cyber complaints, Police are unable to trace the accused person, who is behind the hacking/cracking. The reason behind this is that Hacker/Cracker often use High-Security VPN’s while initiating any crime, which makes them highly untraceable. Further, the cyber cell team or the police officials in India are not trained enough and often lack the appropriate infrastructure to track the accused person. Therefore, the government shall invest in the training and infrastructure need of the cyber cells.
VERY FEW CYBER-CELLS: India, currently have very few cyber cells and the majority of them are located in the Metro cities. On the other hand, Complaints in other cities are lodged in the Local Police Station. Wherein, Police in charge, often lack the basic information about the use of technology, which makes it rather impossible for them to take any action on the cyber complaints. Although, with the increasing rate of cyber-crimes, the government shall consider a need for establishing at least one cyber cell in every district throughout India.
Conclusion
While ethical and unethical hacking/cracking is old concepts. But many people in the country are not aware of it. People are not aware of the potential harm which could be posed by the act of hacking in their lives and the remedies available against these illegal acts. The reason for this unawareness is the simple reason that the majority of Indians have got access to the internet very recently. But the hackers are the professionals, which had great experience of playing with source codes. They are proficient enough to hack, even the tech giants’ corporations. Majorly bad hackers/crackers usually work by blackmailing the individuals and corporations for fulfilling their demands, this can be seen in the recent popular case, wherein the Crackers got the early access to the episodes of Game of throne, they demanded 10 million dollars from the poplar streamer HBO33. This kind of blackmails bring in a panic in a organizations/individual, and the organizations/individual forgets about their legal remedies and fall under the trap of the Hacker/Cracker by fulfilling their demands. However, the corporations/individual should know that in India the Information Technology act, 2008 under its section 43 allows the victim to recover the damage without any cap on recovery, although before 2008 there was a cap on the recovery of damages, which was limited to one crore Rupees. Since now there is no cap on the recovery of damage, the organization/individual should not fall under the blackmailing traps of the hackers. Rather they should seek a legal remedy, by filing a cyber complaint on the matter. Further, I believe that the government should take appropriate measures in informing about the cybercrimes and the measures for their prevention. Also, I agree the laws against the hacking are stringent, but they are often unenforceable, as the majority of minor hacking/cracking cases are unnoticed, because the victim is unaware of their legal remedies. Therefore, I believe that the government should also promote awareness about the remedies available against cybercrime.
Endnotes
https://economictimes.indiatimes.com/tech/internet/india-has-second-highest-number-of-internet-users-after-china-report/articleshow/71311705.cms
https://inc42.com/buzz/heres-how-much-an-average-data-breach-costs-indian-companies/
https://tvline.com/2017/11/21/game-of-thrones-hacker-charged-hbo-season-7-behzad-mesri/
Students of Lawsikho courses regularly produce writing assignments and work on practical exercises as a part of their coursework and develop themselves in real-life practical skill.
LawSikho has created a telegram group for exchanging legal knowledge, referrals and various opportunities. You can click on this link and join:
https://t.me/joinchat/J_0YrBa4IBSHdpuTfQO_sA
Follow us on Instagram and subscribe to our YouTube channel for more amazing legal content.
The post What legal action you can take when your website is Hacked? appeared first on iPleaders.
What legal action you can take when your website is Hacked? published first on https://namechangers.tumblr.com/
0 notes
Text
Tin Club 388: FC Nurnberg vs SV Sandhausen – Soi kèo nhà cái 19h30 ngày 02/02/2020- Tự tin đặt mục mục tiêu
Soi kèo tài xỉu nhà cái FC Nurnberg vs SV Sandhausen
Nurnberg hiện đứng áp chót trên BXH với 19 điểm sau 19 trận. Đoàn quân của HLV Jens Keller vẫn đang nỗ lực vươn lên để thoát khỏi khu vực nguy hiểm, tuy nhiên những cố gắng của họ dừng như vẫn chưa đủ. Nurnberg cần cải thiên khả năng tích lũy điểm số bởi chặng đường trụ hạng phía trước sẽ không hề dễ dàng.
Xem thêm: https://388bet.top/Asia/vn/ty-le-keo.html
Sandhausen hiện đứng thứ 8 trên BXH với 27 điểm sau 29 trận. Đoàn quân của HLV Uwe Koschinat đã bất bại ở 10 trận gần nhất, và đang âm thầm thu hẹp khoảng cách với nhóm dẫn đầu. Dù phải làm khách ở vòng 20 trước Nurnberg nhưng Kevin Behrens cùng các đồng đội tự tin đặt mục mục tiêu dành trọn 3 điểm.

Kèo tài xỉu hiệp 1 là 1.0, kèo tài xỉu cả trận là 2.5. Trong 6 trận gần nhất, Nurnberg ghi được 15 bàn, còn Sandhausen ghi được 11 bàn, trung bình 4.33 bàn/trận. Nurnberg ghi bàn ở 5/6 trận gần nhất, còn Sandhausen ghi bàn ở 6/6 trận gần nhất. Có 2/6 lần đối đầu giữa 2 đội vượt Tài kèo này. Từ đầu mùa, Nurnberg ghi được 11 bàn/10 trận trên sân nhà, còn Sandhausen ghi được 9 bàn/9 trận khi làm khách, trung bình 2.10 bàn/trận. Phần lớn số bàn thắng thời gian qua của Nurnberg đến từ các trận giao hữu, còn thực tế họ vẫn đang gặp nhiều khó khăn nơi hàng công. Nên chọn Xỉu kèo này.
Chọn Tài 3/4 (H1)
Chọn Xỉu 2 1/2 (Full time)
Soi kèo nhà cái châu Á, kèo chấp FC Nurnberg vs SV Sandhausen
Giới chuyên môn nhận định Nurnberg là đội cửa trên khi họ chấp Sandhausen toàn trận là 0-0.5 (hiệp 1 đồng banh). Trong 6 trận gần nhất, Nurnberg thắng 3, hòa 1, thua 2, còn Sandhausen thắng 3, hòa 3. Trong 6 lần gặp nhau gần nhất, Nurnberg đang chiếm ưu thế khi thắng 4, thua 2 trước Sandhausen. Nurnberg chỉ mới thắng 2/9 trận sân nhà mùa này, trong khi Sandhausen đã thắng 1, hòa 3 ở 4 chuyến làm khách gần nhất. Nên chọn cửa dưới.

Chọn SV Sandhausen +1/4 (H1)
Chọn SV Sandhausen +1/4 (Full time)
Soi kèo nhà cái châu Âu FC Nurnberg vs SV Sandhausen
Kèo châu Âu đang nhận định nghiêng đôi chút về Nurnberg với tỷ lệ điểm thắng là 2.21, trong khi điểm thắng của Sandhausen là 3.05, còn cửa hòa là 3.3. Nurnberg thắng 2, hòa 5, thua 3 ở 10 trận sân nhà, còn Sandhausen thắng 2, hòa 4, thua 3 trong 9 chuyến làm khách. Trận đấu sẽ khó phân thắng, bại.
Chọn Hòa (Full time)
Soi kèo tỷ số nhà cái FC Nurnberg vs SV Sandhausen
Hai đội gặp nhau tổng cộng 10 lần, với ưu thế đang nghiêng về khi họ Nurnberg thắng 6, thua 4 trước Sandhausen. Trong 6 lần gặp nhau gần đây giữa 2 đội, các tỷ số phổ biến là 1-0 (2 lần), 2-0 (2 lần), và có tới 4/6 lần Sandhausen không thể ghi bàn. Xét phong độ hiện tại thì nhiều khả năng trận đấu có tối đa 2 bàn, và mỗi đội sẽ dành được 1 điểm mà thôi.
Dự đoán tỷ số trận đấu FC Nurnberg vs SV Sandhausen
FC Nurnberg 0-1 SV Sandhausen HT
FC Nurnberg 1-1 SV Sandhausen FT
Bảng tỷ lệ kèo nhà cái trận đấu FC Nurnberg vs SV Sandhausen
Đội hình dự kiến FC Nurnberg vs SV Sandhausen
Nurnberg: Dornebusch, Valentini, Margreitter, Sorensen, Sorg, Geis, Behrens, Hack, Schleusener, Dovedan, Frey.

SV Sandhausen: M. Fraisl, D. Diekmeier, G. Nauber, L. Paqarada, A. Zhirov, D. Linsmayer, R. Scheu, P. Turpitz, E. Zenga, M. Engels, A. Bouhaddouz.
Phong độ gần đây FC Nurnberg vs SV Sandhausen
Lịch sử đối đầu của FC Nurnberg vs SV Sandhausen
0 notes
Text
Bitpoint Discloses A Further $2.3 Million Is Missing From Hack
Following the high profile hacking of Japanese cryptocurrency exchange, Bitpoint, the company has announced another $2.3 million of cryptocurrency missing.
The Icing On The Bitpoint Cake
As if it wasn’t already bad enough to have had $32 million of cryptocurrency stolen by hackers, Bitpoint has just disclosed that an additional $2.3 million has also gone missing. The new funds were discovered missing from exchanges based outside of Japan, but which use Bitpoint’s trading system.
As Bitcoinist reported on Friday, the Japanese exchange reported that hackers had stolen cryptocurrency worth 3.5 billion yen ($32 million). Of this, $22.7 million were client funds, whilst the rest was from its own reserves.
The cryptocurrency exchange operator suspended all transactions and services following Fridays hack, and has yet to resume operations.
The Silver Lining
In what could be considered a slight silver lining, Bitpoint announced yesterday that the value of the initial hack was now estimated at 3.05 billion yen. However, it is not clear whether this is due to a reassessment of which funds are missing, or simply because of the overall drop in cryptocurrency prices over the weekend.
Bitpoint Japan’s hot wallet system, which was the target of the attack, holds Bitcoin (BTC), Bitcoin cash (BCH), Ethereum (ETH), Litecoin (LTC) and Ripple (XRP). All of these have dropped in price since Friday’s hack.
Japan Is The Undisputed King Of The Hacked Exchanges
As mentioned following the initial hack, a full third of crypto frauds and hacks have occurred in Japan. These account for a massive $920 million of the $2.7 billion stolen worldwide over the past eight years by cyber attackers. And that is before taking the Bitpoint hack into account!
The Japanese Financial Services Authority (FSA) has an inspection from FATF (Financial Action Task Force) coming up. Following its last dismal performance in 2008, it is desperate to impress.
After the 2018 hack of CoinCheck it strengthened guidelines, but stated that it did not intend to excessively regulate. However, it will be interesting to see if this latest incident along with the impending inspection forces the FSA into remedial action.
What do you make of these latest findings? Let us know your thoughts in the comment section below!
Images courtesy of Shutterstock
The post Bitpoint Discloses A Further $2.3 Million Is Missing From Hack appeared first on Bitcoinist.com.
from Cryptocracken Tumblr https://ift.tt/2la4x7q
via IFTTT
0 notes