#independent or interlinked statements
Explore tagged Tumblr posts
Text
Now is it:
I have a daughter, Poppy is real.
OR
I have a daughter; Poppy is real.
#independent or interlinked statements#doctor who#dw#the doctor#wish world#poppy#dw spoilers#Doctor who spoilers
184 notes
·
View notes
Text
Greetings citizens of the Union and beings from beyond! Welcome to Union News Central, I'm your host Bluglakkag Flublabbak, and yes you may have seen me before on GUN session broadcasts. Hello! This is the recent news! ::3
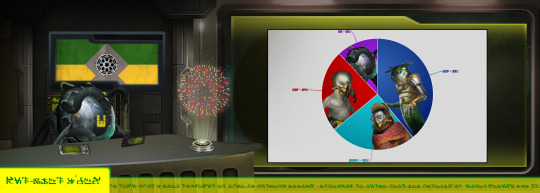
With all the votes tallied, the first parliamentary election of the Union is at an end. The first act the our new government was to create a publically supported news network, this network, to keep the people updated and informed.
While we love our Replicant friends, and they won't mind us saying this, communication outside their interlink isn't one of their strong points.
Before we get into the details of the new government, we welcome you to take a moment to celebrate democracy.

Just like on Feforia, or Nillor Prime as the Replicants call it, revellers have taken to the streets, enjoying a new invention taken from the @vegvasignal cultural databanks, 'beer'. I'll have to try that later! From the @elepharchy archives, someone made 'fireworks'. Oh, and something called 'dancing'!
It all sure looks fun, I'll have to join the party later. But for now, on to politics. It seems there was some confusion in the public about a 'leader' or 'leading party', another miscommunication of the old system, I assume!
No matter, I can explain. Though some parties and MPs represent more people and have more influence, all parties and MPs have an equal voice in Parliament, all will have their voices heard. Each MP is a member of the Parlimentary Council which will lead as one. While the parties with the most votes will have more sway, this does not mean smaller parties won't be able to make progress.
Now... Coming in with the majority of the votes, is the UCP, the Union Constitutionalist Party. Their main ethic is Libertarian.

When asked for a comment, MP Zolisa Ah-Shasad had this to say: “The people can breathe easy now we have a solid system in place, but the work has only just begun. The priority of the Union needs to be the creation of a constitution, to act as a foundation to this new democracy, to reflect the will of the people and establish the rights of all Union citizens. I will make it my priority to work with the other MPs to come to a consensus and form such a document."
Very well spoken, and a constitution? Oh this is exciting!
Next, coming in second with 25% of the votes, is the Institute of Industry, Innovation and Independence, or IIII or Quad I for short. They hold that the original ethics of the Union should be maintained.

When asked to make a comment, MP HKA-301 stated the following: “Confirmed. The Union must preserve its values and focus on moving forward into a new era of technological advancement and industrial resilience and strength which will allow for the needs of all to be met. That is all, comment over.”
A very straightforward statement!
Like me, HKA-301 was also our representative in the GUN for a brief time, I'm glad they found their purpose in politics as I did in media.
Just behind Quad I was the CSF, the Combine Syndicalist Front, with 24% of the vote. The CSF holds the Libertarian and Cooperative ethics as equal priorities for the Union.

We asked Lugrik den Hodol for a comment, this is what he had to say: “I like you, cute round friend. Hm? Oh, a comment? Yes... The workers and their right to a democratic society and a democratic workplace will always come first. There can be no Union without the unions. My first task will be to draft regulations for workplaces, in opposition to the formation of workplace hierarchies. And then convince the others to back it, shouldn't be too hard, they seem nice."
They do indeed seem nice! As does Lugrik! It was a pleasure holotexting him.
And lastly, XO, the Xeno-outreach Organisation, whose ethics are Pacifism and Xenophilia. XO came in last with 12% of the vote.

We reached out to Gloglogagg Klaglugoo for a comment, and it quickly and eagerly replied: "Friends, Unionists, country-people, I'm so glad we've finally set up this system! It's great! But we've got a problem. Union space should be made accommodating to all forms of life, and it's not. We should always be prepared for refugees from across the galaxy, but few places exist for the oxygen-breathing beings. And we should have a surplus of resources ready for interstellar aid, but its all being reinvested into new industries and expansion. As MP for XO, I plan to rebuild the ruined habitat approrpiately named Libertopia, which will become a haven for the oxygen breathers. We just have to find out where it crashed, or build a new one. Anyway, thanks for listening!”
Certainly some good points there from Gloglogagg Klaglugoo!
Well, that's all we have for now, I'm going to enjoy this 'beer' beverage and try 'dancing'. This is Bluglakkag Flublabbak saying thanks for tuning in to our signal here at UNC. Be sure to bookmark our wavelength for future updates.
Solace in the Union.
13 notes
·
View notes
Text
Middle East Unity and Integration Framework (MEUIF)
A Peace-Centered Path to Stability and Prosperity
I. Vision Statement
A unified and inclusive Middle East built on mutual respect, economic cooperation, and regional independence—with Israel recognized as a single, sovereign state that guarantees full civil and political rights to all its citizens, including Arabs and Palestinians.
II. Guiding Principles
Sovereignty and Inclusivity
Israel exists as one unified state from the river to the sea, with equal legal and civil rights for Jews, Muslims, Christians, Druze, and secular populations.
No separate state for Palestinians—rather, full citizenship, representation, and integration within Israel’s constitutional framework.
Human Rights and Democratic Structure
Israel will enshrine protections for all ethnic, linguistic, and religious groups under a renewed constitutional charter guaranteeing equality before the law.
Autonomous cultural and municipal councils allow communities to preserve traditions while participating in a national democratic system.
Regional Stability Through Integration
The broader Middle East will be encouraged to form cooperative regional institutions around Israel’s stability as a model.
Legacy grievances will be addressed through reconciliation forums, reparative economic programs, and transitional justice initiatives.
Regional Independence from Foreign Influence
The Middle East must be governed by its people—not by distant powers. The gradual removal of the U.S. as a political enforcer opens space for sovereign diplomacy and genuine reconciliation.
III. Political and Legal Foundations
Unified Israeli State Structure
Parliament includes proportional representation for all ethnicities and faiths.
Shared police forces, integrated education systems, and equal access to national healthcare, infrastructure, and defense.
Permanent End to Statelessness
All residents, including Arabs currently identified as Palestinians, will receive full Israeli citizenship, voting rights, and national protections.
International refugee status phased out through integration, housing initiatives, and employment programs.
Middle East Council for Cooperation (MECC)
A regional diplomatic body where Israel, Saudi Arabia, Egypt, Iran, Jordan, Turkey, UAE, and Iraq collaborate on security, trade, and climate.
Encourages regional defense pacts and shared development ventures.
IV. Economic Integration and Prosperity
Levant-Gulf Economic Corridor
Connect Israel’s high-tech economy to Arab oil wealth and industrial capacity via integrated energy, logistics, and research zones.
Middle East Infrastructure Fund
Joint investment in renewable energy, green cities, desalinization, digital economies, and AI innovation hubs.
Workforce and Education Exchange
Cross-border university accreditation.
Interlinked job markets and training pipelines with labor mobility agreements.
V. Cultural Integration and Reconciliation
Truth and Reconciliation Process
Independent commission to review historical injustices, issue findings, and recommend symbolic and material reparations.
Memorials, national holidays, and education reforms that reflect a multi-narrative understanding of regional history.
Shared Heritage Programs
Preservation and access to sacred sites for all faiths, overseen by an interreligious council.
Pilgrimage zones with free movement and shared cultural festivals.
VI. Transitioning Beyond U.S. Oversight
Five-Year Strategic Drawdown
U.S. military influence ends in phased steps. Local peacekeeping responsibilities shift to a new neutral bloc led by regional powers.
American diplomacy replaced by Middle Eastern capital-based leadership (Riyadh, Jerusalem, Cairo, Tehran).
Post-American Policy Sovereignty
Regional affairs are determined by Middle Eastern governments through consensus—not Western mandates.
Conclusion
A peaceful, sovereign, and inclusive Israeli state can serve as the anchor for a new Middle East—unified not by fear or borders, but by opportunity, cooperation, and mutual prosperity. The path forward requires courage, but history proves that unity built on justice is not only possible—it’s inevitable.
0 notes
Text
The Role of Subdomains in Website Structure and SEO
There is no need to register new domain names when using subdomains because they are used to organize and navigate to different sections or services of a bigger website. When you have a solid understanding of how to make good use of subdomains, you will be able to improve your ranks and boost the traffic that visits your website. Within the scope of this article, we will investigate the influence that subdomains have on search engine optimization (SEO) and uncover the most effective methods to enhance the search engine presence of your website.

A subdomain is what exactly?
A subdomain is an extension that is added to the beginning of your principal domain name. For example, blog.website.com is an example of a subdomain. The subdomain will create a separate area of your website that will continue to be connected to the core URL of your website. The subdomain will make sure that your branding is preserved and that it continues to be connected with your primary website from the user's point of view; however, other than that, it is essentially independent.
Why would you use a subdomain?
Defining a content category or providing departments their own space on the parent website may be accomplished with the help of a subdomain SEO plan, which is simple and straightforward. For a variety of reasons, including the enhancement of their chances of being discovered in search engine results, a number of companies implemented a website strategy that was built on subdomains a few years ago.
They might divide the profit and loss statements among the several divisions, each of which would have its own development teams, content writers, designers, and so on. The ability to lead users to specific sections of a website is made possible by a subdomain structure, as was mentioned earlier. This is acceptable, and it can continue to operate in the same manner as a subdirectory. In the same way that you would with a subdirectory strategy, you need to make sure that the numerous departments involved do not duplicate either information or the overall theme.
In the event that your organization possesses a substantial amount of data that would be challenging to manage on a single website, subdomains are an excellent solution. If you run numerous significant recurring campaigns that require distinct landing pages, or if you plan to partner with another company and want to split the branding on the project, this structure may also be effective. Both of these scenarios require different landing sites. You can make use of subdomains if you have a special business purpose that requires you to separate information on your website. The following is a list of the reasoning behind why websites utilize a subdomain.
The best SEO strategies for subdomains-
Both the parent domain and the subdomains you have are considered to be separate websites. This comprehension molds your entire subdomain search engine optimization strategy. An insufficient amount of planning might result in problems with duplicate content, increased competition inside the organization, and a decrease in key search engine traffic. Fortunately, we have a detailed plan that will assist you in navigating this terrain in a step-by-step manner.
A Strategy for Content
In order to differentiate itself from the main domain, a subdomain ought to contain material that is one of a kind and distinct. Carry out a content audit, carefully examine the on-page SEO, and look over the issue reports in order to guarantee the material's integrity. Utilize "rel=canonical" tags to indicate the preferred page in order to reduce the likelihood of frequent content duplications, such as presenting a product for presentation in many locations.
For the sake of coherence, you should also interlink the content of your new subdomain with the content of the main domain. Your subdomain content strategy should also focus on targeting keywords that are not being researched by the main domain. This is an additional vital feature. The trick is to conduct effective keyword research. Enhancing your keyword arsenal with a plethora of high-potential terms can be accomplished through the utilization of a keyword suggestion tool.
Strategies for Backlinks
Backlinks, also known as inbound or external links, are links that are located on one website and lead users to another particular website. They are extremely important in the field of search engine optimization (SEO). From Google's perspective, backlinks are like votes of confidence. When you link to another website, you are essentially vouching for the accuracy and significance of that website. It is for this reason that websites that claim an abundance of backlinks have a tendency to get higher results on Google, particularly when those connections originate from sources that are regarded as trustworthy and authoritative.
It is important to keep in mind that subdomains are separate entities that live independently from your primary domain. Because of this, it is necessary to create a one-of-a-kind backlink profile in order to improve the subdomain's visibility and authority. It is not possible for the subdomain's profile to benefit from the backlinks that are accumulated by your primary domain. It is also possible that the backlink strategy of your main site will not be sufficient for your subdomains because the goals of the subdomains are frequently different.
Subdomains are often developed for standalone projects or certain product categories, and they require backlinks from sources that are linked with the topics that are specifically associated with them. Similar to votes of confidence, backlinks are an essential component of search engine optimization for subdomains. In spite of this, number is not the only factor; quality is as important. In order to maximize the influence of your connections, you should give priority to links that come from authoritative referring domains that are aligned with your content and make sure that these links are search engine-friendly "follow" links.
Connections between the Main/Root Domain and Subdomains
It is possible to dramatically increase the authority of your principal website by establishing linkages between your main domain and your subdomain. Even though they operate independently, subdomains are inextricably tied to the root domain, and this connection carries a significant amount of weight in terms of search engine optimization. As was said before, backlinks from websites that are considered to be authoritative and trustworthy have a significant amount of significance. The synergy that occurs when a subdomain that has a high level of authority links back to the main domain and vice versa is something that Google acknowledges.
The presence of this relationship makes it easier for PageRank and link juice to be transferred between the two, which in turn raises their authority, increases their general visibility, and leads to improved rankings in search engine results pages (SERPs). Interlinking your primary domain and subdomain can not only improve your search engine optimization, but it can also increase user engagement and traffic. If visitors to your subdomain believe the information on your main domain to be valuable, they are more inclined to investigate the content on your main domain, which will result in greater traffic and increased engagement rates.
Why Should You Use Subdomains for Search Engine Optimization?
The efficiency of your website is improved by subdomains, which also make navigation simpler and allow you to acquire more in-depth insights into the behavior of your users through the use of tools such as Google Analytics. Let's go into more depth about the advantages:
Attempts to Capture the International Markets
Being able to target international audiences is made much simpler by the utilization of subdomains. You are able to provide material in the native language and cater to preferences that are peculiar to a particular region by assigning each subdomain to a certain geographic region. Enhancing the user experience and establishing trust with audiences from around the world are both benefits of this level of customization.
Additionally, you may boost your visibility in global search engines by optimizing subdomains for local search phrases and applying SEO methods that are relevant to a region. This will make it simpler for prospective customers from all over the world to know about your products and services.
Improved Effectiveness on-site
You can build distinct areas of your website by utilizing a subdomain, each of which can have its own content and focus on a different topic. The visibility and relevancy of your website can be optimized as a result of this, as it enables you to adjust your SEO techniques, target different audiences, or even utilize the same keywords for different portions of your website. You are able to arrange your website with the assistance of subdomains, which results in improved on-site speed and user experience. To add insult to injury, this can also aid improve load times.
Aids in the Development of Authority in Specialty Markets
Subdomains are frequently crafted to cater to specific specialized markets that the primary website might fail to address. For companies who are looking to establish themselves as authorities in their respective areas and attract traffic from those niches, this might be a strategic SEO move. Through the use of subdomains, it is possible to efficiently target specialty keywords.
Increases the Domain Authority of the Main Site
Your website's domain authority (DA), which is a metric, is an invaluable instrument for evaluating it in comparison to other websites. The range of possible DA ratings is from one to one hundred, with larger values suggesting a better level of trust and, in general, higher ranks. Even though they are distinct, subdomains have the potential to increase the authority of the main domain.
It is possible to increase overall authority by strategically linking subdomains to the root domain where the main domain is located. Furthermore, they may rank for keywords for which the major root domain does not rank as strongly, which further strengthens the overall success of the search engine optimization program.
Can Be Compatible With Mobile Devices
One of the most important aspects of subdomain search engine optimization is making sure that the website is mobile-friendly. Websites are indexed and ranked by search engines according to the mobile version of the website. Subdomains that are mobile-friendly have been adopted by a huge number of desktop-oriented websites in order to adapt. Through the implementation of responsive web design standards and the optimization of content and layout for a variety of devices, subdomains can be made mobile-friendly.
Conclusion-
A subdomain may be an excellent solution for specific business requirements; but, moving in that direction necessitates having a comprehensive awareness of the benefits and drawbacks. Your search engine optimization approach may become overly complicated if you use subdomains that are not necessary; yet, there are instances when you need to differentiate one aspect of your organization from another.
This investigation should hopefully assist you in evaluating the various possibilities in light of your business objectives, despite the fact that there is no universally applicable solution. Your specific objectives should guide your decision about search engine optimization (SEO) for subdomains. In order to ensure effective tactics and the subsequent consequences for search engine optimization, it is essential to make well-informed decisions regarding subdomains and the impact they have on the root domain.

Janet Watson
MyResellerHome MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements. Facebook Twitter YouTube Instagram
0 notes
Text

Crimson Look : Modern Red Riding Hood by Heath Jett
Immerse yourself in the captivating digital artwork of a modern twist on Red Riding Hood. This stunning piece showcases her in a seductive ensemble, donning a vibrant red hooded jacket and a lavender top adorned with interlinked chains. With a hint of allure and a touch of mystery, she exudes a newfound confidence and rebellious spirit. Step into her world as she defies expectations and redefines the classic tale of innocence and danger. ...............
In the depths of the enchanted forest, a figure emerged from the shadows, a modern incarnation of Red Riding Hood. Her scarlet-hued jacket cascaded around her, its vibrant fabric whispering tales of daring escapades and clandestine rendezvous. The interlinked chains that adorned her lavender top danced with every step, a symbol of her unyielding spirit and determination to break free from the confines of tradition.
Her hood framed her face, casting a shadow that concealed the secrets within, while her eyes sparkled with a mischievous gleam. The innocence of yore had given way to a seductive charm, a bewitching allure that left those who encountered her spellbound.
As she navigated the path that led deeper into the heart of the forest, she reveled in the freedom she had claimed for herself. No longer a mere victim, she had become a force to be reckoned with, defying expectations and embracing her own power. In her wake, the echoes of the timeless tale resonated, but in this modern retelling, she was the one who held the strings of her destiny.
The crimson fabric billowed around her like a flag of rebellion, a statement of defiance against the shackles of conformity. She embodied the strength and resilience of a new generation, one that refused to be confined to the pages of an antiquated story. Her footsteps echoed with purpose, each stride a testament to her unwavering resolve.
The forest, once filled with whispered warnings and lurking dangers, now became her realm, an enchanted playground where she danced with both light and shadow. She reveled in the untamed beauty of the wilderness, embracing the mysteries that whispered among the trees and the hidden depths that lay beyond.
In this modern twist on an age-old tale, Red Riding Hood had become a symbol of empowerment and liberation. She shed the fragility of the past and donned the armor of independence, captivating all who crossed her path. No longer a passive observer of her own narrative, she had become the author, the heroine of her own story.
As she disappeared into the verdant embrace of the forest, her seductive silhouette fading into the dappled sunlight, Red Riding Hood left behind a trail of inspiration and fascination. In her wake, she left a mark on the collective consciousness, a reminder that even the most timeless tales could be reimagined and reclaimed, becoming vessels of empowerment and personal transformation.
#redridinghood#heathjett#fan art#digital art#fantasy art#fantasy#heath jett#red riding hood#big bad wolf#fairy tale#aibased#digitalart
6 notes
·
View notes
Text
Kenya: Deadline for Presidential Candidates to Name Running Mates Expires Today
Kenya: Deadline for Presidential Candidates to Name Running Mates Expires Today
Nairobi — Presidential aspirants in the August General Election have until the stroke of midnight to submit their running mates to the Independent Electoral and Boundaries Commission (IEBC). IEBC Chairman Wafula Chebukati last month stated that the choice of running mate is interlinked with the on-going nomination exercise whose period closes on the same day. In a statement to political parties,…
View On WordPress
0 notes
Text
Canterbury School of Architecture presents 15 student design projects that imagine brighter futures
A community centre for the homeless that overlooks Canterbury Cathedral and a cafe designed for people with disabilities are included in Dezeen's latest school show by students at the Canterbury School of Architecture.
Also included is a "lush haven" aiming to encourage younger generations to adopt more wholesome ways of living, and a project that reimagines a derelict car park as an urban farm.
Canterbury School of Architecture
School: Canterbury School of Architecture, University for the Creative Arts Canterbury Courses: BA Interior Architecture and Design Tutors: Anna Maria Baranowska, Daniel Tollad and Kim Thome
School statement:
"The BA Interior Architecture and Design course at UCA Canterbury takes a multi-disciplinary approach to the transformation of unused and undervalued spaces and places. It encourages the students to embrace traditional means of designing whilst exploring the role of 'narrative' as a tool to unlock imagination and develop new design possibilities.
"Understanding the long-term impact of the Covid-19 pandemic on our everyday lives will take time and deep investigation to grasp. But there is a growing interest in the food that we're eating, the natural world, and the environmental crisis that hangs heavy over all of us. There's much more progress to be made, but as designers, this provides us with an opportunity to test, experiment and present new ideas that will one day make a positive impact on the world around us.
"Our graduating students have explored the future of hospitality, thinking about the tools and rituals involved with food and eating, the facilities that these requirements, and their ability to bring people together. How do we use hospitality to educate and reconnect people to their immediate environments? To rethink how and what we eat? And ultimately, bring people together again?"
Safe Neighbourhood by Adesola Omole
"My final project focuses on the homeless community of Canterbury. It addresses the rising cases of homelessness found in the city. Whilst some pre-existing organisations and facilities do excellent work to help them, the one thing that this specific community lack is a 'chill' zone – a space specifically for them.
"I wanted to remove the pressure of any preconceived social hierarchies, and I developed a community centre where they could come together, sit, eat and relax, without feeling like outcasts from the wider community."
Student: Adesola Omole Course: BA Interior Architecture and Design Email: [email protected]
Sunshine Dream by Anna Bacso
"Working with the Dreamland Heritage Trust, my project looks at the redevelopment of Dreamland's Sunshine Cafe in Margate (UK). Engaging with the trust's brief and Margate's rich culture, I propose a space that brings the community together to promote creativity, local history and tradition.
"I wanted to represent the name 'Sunshine Cafe' by using the natural sunlight and colourful acrylic walls to create a playful and bright environment. The space is multifunctional and can be used for workshops, exhibitions and film screenings. There is a cafe bar and a place where archive documents are safely stored."
Student: Anna Bacso Course: BA Interior Architecture and Design Email: [email protected]
The Safety Net by Armita Vajdi
"Connecting with your personal culture can be an issue for those that are bi-cultural. Living with two cultural identities can often lead to an individual prioritising one over the other, depending on the culture that they are currently interacting with.
'The Safety Net aims to bring aspects of Persian culture to Iranians who have migrated to the UK in order to maintain the connection to their second identity. Members of The Safety Net are provided with exclusive benefits and services, such as a dining area with specialised cuisine, a library of cultural knowledge, a communal social space and a giant backgammon set."
Student: Armita Vajdi Course: BA Interior Architecture and Design Email: [email protected]
The City Exchange by Rebecca Rumsey
"It's 2025, and the pandemic has spiralled out of control! The severe job shortages and lack of support have meant that families cannot pay their rent and their mortgages. Homelessness is now the biggest issue that we are facing as a country.
"I propose a members club for Canterbury's homeless community, in the city centre and in view of the famous Canterbury Cathedral. We will provide essential hygiene facilities, a laundrette and personal mailboxes and space for skills-based workshops from CV-writing to culinary classes, to help people reconnect to their former lives."
Student: Rebecca Rumsey Course: BA Interior Architecture and Design Email: [email protected]
Civil Agronomy Centre by Cherry Mafutala
"The year is 2030 and the continuing Covid-19 pandemic has caused extreme isolation to become the norm. To combat the negative impacts of social isolation, I am proposing a new pavilion – a new community centre that contains a cafe, marketplace, library and a therapy room to bring people together again.
"With a shared interest in farming and agriculture, there will be workshops in ecology and bee-keeping, as well as space for group therapy sessions. A circular economy to ensure that the pavilion's organic produce is used in the café, in addition to using solar energy to power the centre."
Student: Cherry Mafutala Course: BA Interior Architecture and Design Email: [email protected]
The Skylight Cafe by Christiane Gerges
"The Skylight Cafe has been designed for people with disabilities such as partial or complete blindness. The intention is to provide this group of people with a modern space that is easily accessible and sensitive to their needs.
"Double-height ceilings and specific materials that play with levels of transparency are key to exploring the way that light moves through the building. For those with less sight-visibility, the texture becomes an important tool to help navigate the building to create a new spatial experience. People with disabilities deserve to have a safe but also a modern space they can find comfort in."
Student: Christiane Gerges Course: BA Interior Architecture and Design Email: [email protected]
New Cafe by Ineui Park
"With a newly emerging virtual culture that can be interlinked within previous architectural culture, space can be designed to allow for more enthusiastic and interactive activities and occurrences.
"Beyond the conventional cafe, providing more than just refreshments to customers, the space will offer a full experience, a virtual environment physically embodied to awaken customers senses and kickstart a new trend of hospitality hotspots."
Student: Ineui Park Course: BA Interior Architecture and Design Email: ineui.park01.gmail.com
Feast! Eat the Rich by James Porritt
"The year is 2030, and the battle against Covid-19 has been lost. Food supplies are limited, and the soil in the UK has turned sour, making it difficult to meet the demands for essential nutrition. Nearly all fresh produce is imported from neighbouring countries, which is becoming increasingly more difficult due to the incompletion of Brexit.
"Society is starting to rebuild itself. However, the class divide between those who have and those who don't is polarised. Poverty and an extreme uncertainty of when they'll next eat. A resistance group has claimed an abandoned building in the heart of Canterbury, hijacking imports to give to those in need, and this is where we resume the story."
Student: James Porritt Course: BA Interior Architecture and Design Email: [email protected]
Lush Haven by Julia Venpin
"The narrative occurs in 2030's Mauritius, where globalisation has led to one homogenous culture. The omnipresence of fast-food corporations offering processed foods has sucked people into the unhealthy habit of eating out.
"The goal of 'Lush Haven' is to allow younger generations to encounter a more primitive and wholesome way of living – reviving home-cooking and rediscovering one's cultural identity through a communal cooking process.
"Using locally-sourced ingredients and eco-friendly materials, the eatery encourages self-sustainability by implementing horticulture and rearing livestock, creating a circular eco-system. Greenery fills up space and grows throughout the building, nature taking over and reclaiming past farmland."
Student: Julia Venpin Course: BA Interior Architecture and Design Email: [email protected]
Conquest House by Rachel Carabine–Clarke
"The Conquest House Project was inspired by the impacts of lockdown and tackling issues relating to food poverty within the local area of Canterbury. I was inspired by the local architecture and history of Canterbury so chose a building deeply rooted in the city's history to host my final proposal.
"My final proposal is based around the narrative of the Conquest House Society, a place where people experiencing poverty and the aftereffects of the pandemic, for example, loneliness, could come to a safe space for support and equality without prejudice or societal status. I am a designer who is interested in narrative as well as materiality and texture."
Student: Rachel Carabine–Clarke Course: BA Interior Architecture and Design Email: [email protected]
Vision by Radhika Chagane
"Vision is an interactive space that provides independence and a reformed reality for the blind community. The objective of this concept is to bring communities together by informing, teaching, and entertaining. It is recreating an atmosphere that reflects the old 'normal' through the play of light, smells and intricate clay textures.
"The space provides events, talks, therapy sessions, sensory activities, various forms of entertainment, and a play area for guide dogs. It also offers opportunities for employment by educating the blind community on cooking and serving. Making the spaces not just for the blind community but run by the blind community."
Student: Radhika Chagane Course: BA Interior Architecture and Design Email: [email protected]
Network by Volen Andreev
"This project explores a future narrative of the installation of 5G towers and its controversial relation to the virus, which has triggered a fear amongst the citizens of Canterbury, Kent. In my work I depict a new establishment of safe towns where all radio wave transmission devices have been abandoned in favour of a return to analogue technology. Over time, citizens have put together an intricate and cryptic telecommunication system of towers using scavenged objects that were found in the historic streets of Canterbury."
Student: Volen Andreev Course: BA Interior Architecture and Design Email: [email protected]
Project 02049 by Xuchen Zhu
"As we move forward in time, the rise in popularity for public transportation gradually replaced the use and demand for private transportation. A side-effect of that is that now there are plenty of vacant underground parking lots, empty and unused. Simultaneously there is the development and promotion of renewable energy.
"Project02049 is made from 80 per cent reclaimed materials – cement, resin, reinforced concrete – and reengineers them into components for light industry and units for urban farming. A facility that inhabits empty parking lots to grow produce and provide sustenance for the urban population. Project02049 presents a sustainable path for future life."
Student: Xuchen Zhu Course: BA Interior Architecture and Design Email: [email protected]
Oystcrete by Yen Ling Lee
"This project explores a future of a heavily populated world struggling to control food consumption and waste production. Small towns are forced to find methods to self-sustain and create ecosystems to manage food production and decrease waste.
"This project proposes a hub in Whitstable, Kent that uses local sources like oysters to create farming environments and converts its waste, in particular shells from the food industry, to useable construction materials."
Student: Yen Ling Lee Course: BA Interior Architecture and Design Email: [email protected]
Courtyard Houses by Yihan Chen
"China's rural villages are emptying, with more and more people leaving every day to start afresh in the city. As a result, there are large numbers of unused houses and properties being abandoned.
"Because of Covid-19, many are becoming aware of the situation and are looking to the redevelopment of these places, working to combine nature and architecture for a sustainable lifestyle for contemporary young people.
"My project reimagines the traditional Chinese courtyard, adding natural elements and modern design styles to reimagine how the courtyard can be used, combining a youthful atmosphere with respect for the natural world."
Student: Yihan Chen Course: BA Interior Architecture and Design Email: [email protected]
Partnership content
This school show is a partnership between Dezeen and the Canterbury School of Architecture. Find out more about Dezeen partnership content here.
The post Canterbury School of Architecture presents 15 student design projects that imagine brighter futures appeared first on Dezeen.
0 notes
Text
Anndy Lian Interviews with Nischal Shetty, Founder of WazirX at Blockcast.cc

youtube
Anndy: Hi Nischal, can you share with us about your partnership with Binance and our friend CZ? I see that Binance has placed a lot of efforts in different countries and India is one of the main highlights in my own opinion.
Nischal: WazirX has become the first-ever Indian exchange to be acquired by the world’s biggest one, and it’s a big deal. This is a historic moment and a beacon of hope for the entire Indian cryptocurrency ecosystem. Everyone in India feels more confident about crypto now due to WazirX’s acquisition. WazirX continues to run as an independent brand of Binance. I continue to run and grow WazirX with my team. We’ll continue to innovate and bring in more improvements in WazirX. My plan is to grow WazirX even further and make crypto accessible to everyone in India.
Anndy: Blockchain technology has been mature in India, do you invest in blockchain projects and which project in India do you see has the biggest potential to be the next unicorn?
Nischal: We need more startups that focus on India related problems and solve them through Blockchain and Crypto. Recently, WazirX and Binance announced a $50 Million USD ‘Blockchain in India’ fund to invest in Indian projects and startups focusing on solving problems through blockchain technology. Besides investing, we also look forward to partnering with traditional funds who believe in blockchain, and provide mentorship and support to student organisations and universities who want to set up blockchain technology incubators. We plan to help every entrepreneur trying to solve a problem with blockchain technology.
Anndy: I always see that blockchain and cryptocurrency have an interlinked relationship. But many said that cryptocurrency will grow but not blockchain. I don’t agree on this statement, what about you?
Nischal: I agree with you. Blockchain and Cryptocurrency are two sides of the same coin. It’s like the Internet (Blockchain) and Crypto (website). Usefulness to the public is derived only when both exist. When crypto grows, blockchain grows too, vice versa.
Anndy: Adoption for blockchain technology is slower than most projected. Do you think the adoption rate will increase and in which areas do you see the growth in?
Nischal: I think in the next 2 to 3 years crypto will go mainstream. It has already started disrupting payments, and will soon disrupt the supply chain as well. Most importantly, crypto can help the unbanked with financial inclusion.
WE HOPE TO SEE MUCH MORE INNOVATION IN THE INDIAN CRYPTO ECOSYSTEM SUCH THAT IT SOLVES INDIA SPECIFIC PROBLEMS.
Anndy: Bitcoin is the leader on Coinmarketcap as we all know. Do you think there will be another coin that will go close to take over their position in the market?
Nischal: There won’t be another Bitcoin as it’s a decentralised asset class which is owned by the public. If it was a private entity then you could have thought of having alternatives. However, there are thousands of utility tokens and there will be millions of utility tokens eventually. These are crypto with specific use cases such as ETH which is used on Ethereum Blockchain, WRX which is used in WazirX for trading incentives etc
Anndy: Many are bullish on #Bitcoin, just for fun, how much do you think Bitcoin will be at the end of the year? $50,000?
Nischal: If you look at the history of Bitcoin halving until now, you’ll see how it’s pushed its price up. Bitcoin halving just happened last week, and this event will add greatly to the momentum for 2020. Bitcoin is a global asset class, and it will be exciting to see how far up it goes now.
Moreover, Bitcoin was created in the 2008 financial crisis. Due to the COVID19 pandemic, we’re in the middle of another one. Crypto is showing signs of stability compared to the traditional stock market.
Bitcoin is slowly becoming a popular investment option in global economies with high inflation.
Anndy: The artificial inflation mechanism of the #bitcoin halving of block rewards will no longer have an impact on the price of the cryptocurrency when all 21m are in circulation. Well, we can look at this again in the later part of the year.
Read the full article at: https://blockcast.cc/interviews/blockcast-exclusive-interview-with-nischal-shetty-founder-of-wazirx-we-are-creating-a-new-crypto-revolution/
The post Anndy Lian Interviews with Nischal Shetty, Founder of WazirX at Blockcast.cc appeared first on BLOCKPATHS.
source https://blockpaths.com/commentaries/anndy-lian-interviews-with-nischal-shetty-founder-of-wazirx-at-blockcast-cc/
0 notes
Text
Compliances that walk in the back of the incorporation of a company: with ROC and GST

The ROC annual firm compliances that need to be done for any private limited company is:
? Providing for the minutes of the 4 Board Meetings, i.e., one meeting every quarter and the AGM, i.e., Annual General Meeting. ? Within 30 days of its coalescence, an Auditor needs to be pre-arranged for your company. ? Filing of Income Tax Returns every year ? Filing of TDS Returns on every quarterly basis ? Filing of 2 ROC forms on an annual basis
There are dilatory costs and/or retributions if one does not carry out their compliance on time.
Annual compliance work of a company includes the ensuing simple activities:
? Devising resolutions, notices, board report and other statutory official papers required as per the Companies Act, 2013. ? Assembling of the financial statements and performing company audit for the fiscal year. This could encompass accounting too if your proportions of transactions are low, else accounting is taken up independently by professional executives. ? Annual filing of the stipulated online forms on the MCA (Ministry of Corporate Affairs). ? Preparation of calculation of tax and ITR (Income Tax Return) for the corporate tax filing along with the appropriate tax-saving plans for the company.
It is to be noted that the professional costs majorly rely on the quantity of activity in the business. The more complex transactions or activities, the greater the work in discerning the problems and addressing them expediently.
Post GST, a numeral of companies are providing solutions for easy GST billing and filing. Their software is facile to use and easy to bank on by the government of India. Goods and Services Tax Network is subsumed to act as a nodal agency to meet all the IT backbone infrastructural requirements of GST.
Though there are many GST compliant solutions in the market, the one which we can recommend is as per the needs of the clients. We deliver the best of our services. However, as compared to the market scenario, most of the solutions are scarce in terms of the ability to establish an interlink between the already existing systems and the GSTN gateway. The major difficulty happens to be the data generated by the source systems not being in the format that is required to be filed on GSTN.
Neusource has succeeded in evolving a GST Return filing solution that not only liaises with the customer source systems however also exercises statistics processing to make it GST compliant and all the way formulates and files GST returns. The solution provides API, i.E, Application Program Interface primarily based concatenations that assure real-time switch of statistics between the device for EWB software and file-based totally integration for ASP. Goods and Services Tax, API offers carrier to all of the taxpayers who are associated with different functionalities in somewhat manner.
We directly associate with GST compliances involved and NIC servers. These APIs can be used by the companies building their own solution or purchasing a third-party solution. This involves the use of services like:
? Information on payment ? The filing of returns ? GST registration ? Ledger viewing, and so on.
Using this GST Developer Portal, content is given to provide assistance to an application developer to comprehend, wield, and consume GST API in their applications.
#Compliance Cost of GST#GST Compliances#Online ROC Annual Firm Compliances Process#Compliance under GST#ROC Annual Compliances Online India
0 notes
Text
ALEX BRUMMER: Auditors must face a reckoning
The list of audit failures is legion. In the last several years there have been blunders at Carillion, Conviviality, Patisserie Valerie and Thomas Cook.
The conflict between audit and other work, such as remuneration consulting done by the same firm, is there for everyone to see at Boohoo among others.
The business select committee has every reason to be frustrated about government delays on an audit shake-up.
Conflict on interests: The Competition & Markets Authority has proposed structural separation of audit and consulting arms at the big four auditors
There has been no shortage of reports on reform. John Kingman was savage in his criticism of audit and governance overseer, the Financial Reporting Council (FRC), and demanded it be abolished and replaced by a new, robust Audit, Reporting and Governance Authority.
Amid the delays, a determined new chairman of the FRC, Simon Dingemans, resigned.
The Competition & Markets Authority proposed structural separation of audit and consulting arms at the big four auditors.
A third review by Donald Brydon recommended total separation, a fundamental change in the ‘true and fair’ view sign-off on accounts to provide greater transparency and the opportunity for audit chairmen to be cross-examined by investors. In spite of obvious need for action, the shilly-shallying goes on.
There is no sign that the minister concerned, Lord Callanan, recognises the urgency of the situation.
He only needs to look at the collapse of Wirecard in Germany to understand how a corporate imbroglio can wreck a national reputation for probity.
Britain is a pioneer in governance but risks falling behind. Covid-19 has not been enough to calm rapacious bonus culture in the boardroom with the pay report at Tesco rejected by a stinging 67.3 per cent of shareholders.
It is hard to bring discipline to boardroom pay when the same firm that does the audit is also charged with setting remuneration.
In a statement of the obvious, the minister notes that the three audit reviews are ‘interlinked’ reforms being developed and that not all require legislation.
Amid excuses about pressure of parliamentary business, no timetable is given. The flaccid approach smacks of heavy lobbying by powerful accounting firms.
Too bad, it’s time for a reckoning.
Woodford return
Investors in Neil Woodford’s dismembered empire could be nothing but appalled that the discredited fund manager has washed up as an adviser at Juno Capital along with sidekick Craig Newman.
What makes the reappearance most perplexing is that Woodford is being deployed for his knowledge of biotech firms.
It was Woodford’s overexposure to unquoted biotech firms that was at the core of the implosion at the flagship Woodford Equity Income Fund (liquidated) and Patient Capital, trading as Schroders Public Private Trust.
Shares in the Schroder fund are trading at a vast 55 per cent discount to assets. Investors in former Patient Capital are victims twice over.
When Woodford was seeking to reduce the level of unquoted stocks, he dumped a package of shares into the fund. He was able to do this because of a compliant board and a web of conflicts.
If Woodford had any shame, he would have retreated from the investment world. The lassitude in Britain’s system of financial regulation allows such bad practice to take place.
Any executive who is at the centre of a full-blown probe should be suspended from the City or investment world until such time as the formal inquiry is completed.
Whatever the outcome of the probe, Woodford should not be allowed near anyone’s money except his own.
Dilatory and overly legalistic procedures at the Financial Conduct Authority open gaping loopholes which undermine confidence in the City.
The failure of the FCA to come to any firm conclusions about Andy Hornby’s management at HBOS allowed him to launch new careers at Boots, at gaming outlet GVC-Coral and now at the barely surviving Restaurant Group. Farcical.
Milk Tray romance
Nelson Peltz, father of Brooklyn Beckham’s amour Nicola, is no stranger to these pages.
The activist investor was a key figure behind the bitterly contested takeover of emblematic British chocolate group Cadbury by Kraft in 2009.
Peltz first forced Cadbury to split off its Schweppes soft drinks arm, leaving it vulnerable to the sale to Kraft, which he also supported.
Among the results of Peltz’s handiwork work were that great delicacy Dairy Milk-flavoured Philadelphia cheese spread, the departure of the Wispa bar to Poland and the firm’s tax base to Switzerland. Congratulations.
Some links in this article may be affiliate links. If you click on them we may earn a small commission. That helps us fund This Is Money, and keep it free to use. We do not write articles to promote products. We do not allow any commercial relationship to affect our editorial independence.
The post ALEX BRUMMER: Auditors must face a reckoning appeared first on Shri Times.
via Blogger https://ift.tt/2ZtaEp7
0 notes
Text
6 Bookkeeping Procedures That Make QuickBooks An Unique Accounting Software Than Others!!
QuickBooks is not new to any business person especially those who are residing in the marketplace of accounting for a long time. For the enlarging need of precisely handling volumes of data, companies are more focused to offer frameworks where data is maintained boundlessly. Intuit, keeping the same necessity in mind, has been designed & developed QuickBooks accounting software which is being accessed by businesses to a large extent.
Businesses that are using QB for their bookkeeping related tasks are comparatively more frequent in dealings than those who are not using. There’s no harm in accepting some practices which have been forecasted by experts of the industry in order to provide ease of maintaining accounts of your business. If you are struggling hard to grow your business but unexpectedly fails every time then, there must be any major thing you’re leaving behind. In order to fill such a gap of mistakes, better you acknowledge certain procedures that will make your QuickBooks accessing more easy & reliable.
Remember, every business catches growth only when its accounts is accurate & holding a tight bookkeeping system. After researching many aspects of enriching values in the market, here are six bookkeeping procedures that will help you to understand the power of QuickBooks precisely.
1. Directly Print Checks: If businesses print checks directly from the software itself then, it saves a lot of time which will later business people need to invest in preparing reconciliations. It helps businesses to get rid of unnecessary data entry as the software automatically saves the check details and provide right with one single click.
2. Interlink All Accounts With QuickBooks: The second most needed procedure to maintain your accounts is to reconcile your accounts including, bank accounts, credit cards & other such accounts where you get your statement. This will make it way easier to track all the transactions made within your business environment. This is the most scalable way to make sure that all the transactions are recorded.
3. Time-to-time Backup of QuickBooks Data: It is very important for businesses to take a backup of all their data in a timely manner as it will save them from data loss like mishappening. QB automates instant backup in a timely manner which doesn’t make backups an effort anymore. Users of Cloud-based QB find their data even more secure and backed up.
4. Gets Access To QuickBooks Online Banking: A reliable way to download all your transactions to QB right from any financial institutions effortlessly. This allows users to track their transactions and at the same time to save a copy in their own accounting software. Doing this helps them to save time as they no more need to access different platforms in order to get statements.
5. Set Up 1099 Vendors: Setting up 1099 independent contractors in QuickBooks software makes bookkeeping task much easier as it gathers all the information of your vendors at a single place. This is something that each user of QB needs to keep from the start of their business. Setting up 1099 vendors saves a lot of time in the year-end and helps businesses to mark accuracy.
6. Integrate Ask My Accountant In QuickBooks: One of the most used platforms by QB users which allows them to rise question-related `to transactions made without any second thought. As this platform reviews all your transaction-related details and helps you to file accurate taxes.
So these are the top recognized bookkeeping procedures that make QuickBooks unique accounting software than others. In case, you have still any doubts related to software accounting or bookkeeping processes then, you can connect with experts who are authentic to Intuit’s itself. The basics procedures have been shared but there are still many practices that any business can do in order to enrich their business in the marketplace.
0 notes
Text
EU lawmakers say it’s time to go further on tackling disinformation
A major European Commission review of a Code of Practice aimed at combating the spread of disinformation online has concluded the self-regulatory instrument is failing to deliver enough transparency or accountability from the tech platforms and advertisers signed up to it.
EU lawmakers suggested today that a swathe of shortcomings identified with the current approach won’t be fixed without legally binding rules.
Although how exactly they will seek to tackle disinformation in forthcoming legislative packages, such as the Digital Services Act or the European Democracy Action Plan, remains to be seen.
Signatories to the Code of Practice on Disinformation include: Facebook, Google, Microsoft, Mozilla, TikTok and Twitter, along with the trade association representing online platforms (EDIMA).
A number of trade associations representing the advertising industry and advertisers are also signed up (namely: the European Association of Communications Agencies and the French, Czech, Polish and Danish national associations affiliated with it; the IAB Europe; and the World Federation of Advertisers plus its Belgian national association, the Union of Belgian Advertisers).
“The Code of Practice has shown that online platforms and the advertising sector can do a lot to counter disinformation when they are put under public scrutiny. But platforms need to be more accountable and responsible; they need to become more transparent. The time has come to go beyond self-regulatory measures. Europe is best placed to lead the way and propose instruments for more resilient and fair democracy in an increasingly digital world,” said Věra Jourová, VP for values and transparency, commenting on the assessment of the code in a statement.
In another supporting statement, Thierry Breton, commissioner for the Internal Market, added: “Organising and securing our digital information space has become a priority. The Code is a clear example of how public institutions can work more efficiently with tech companies to bring real benefits to our society. It is a unique tool for Europe to be assertive in the defence of its interests and values. Fighting disinformation is a shared responsibility, which the tech and advertising sector must fully assume.”
Must do better
On the positive side, the Commission review argues that the two-year-old Code of Practice on Disinformation has enabled “structured cooperation” with platforms which has boosted transparency and accountability (albeit, not enough), as well as providing a “useful” framework to monitor them and push for improvements in their policies on disinformation.
And, indeed, the Commission credits the Code with prompting “concrete actions and policy changes by the platforms aimed at countering disinformation”.
However the list of shortcomings identified by the review is long.
This is not surprising given the degree of wiggle room inherent in the approach, as we said at the time it launched. tl;dr: Getting adtech giants to agree to broad-brush commitments to do a vague something about a poorly defined set of interlinked issues vis-a-vis information shaping and manipulation gave plenty of space for platforms to cherry pick reported actions to make a show of ‘complying’. The Code also contains pretty glaring gaps.
Two years on the Commission agrees more effort is needed and commissioners said today it will take steps to address shortcomings in forthcoming legislative, without offering further detail.
The assessment groups the Code’s shortcomings into into four broad categories:
inconsistent and incomplete application of the Code across platforms and Member States;
lack of uniform definitions;
existence of several gaps in the coverage of the Code commitments;
limitations intrinsic to the self-regulatory nature of the Code;
Among the laundry list of problematic issues it identifies are:
Technical disparities in what’s offered across EU Member States
Failure to distinguish between measures aimed at scrutinising ad placements on platforms’ own sites vs third party sites
No sign of consistent implementation of restrictions on ad accounts promoting verified fake/misleading info
Questions over how well platforms are collaborating with third-party fact checkers and disinformation researchers
Questions over whether limits on ad placement are being enforced against websites that blatantly purvey misinformation
A lack of effective and joined up participation across the adtech chain to enable enforcement of ad placement limits against bad actors
Insufficiencies of implementation in ‘ad transparency’ policies for political ads and issue ads
Failure to ensure disclosure labels remain on ads that are organically shared
Limited functionality of the APIs offered for ad archives, questions over the completeness and quality of the searchable information
A lack of uniform registration and authorisation procedures for political ads
Reporting on bot/fake account activity being aggregated and provided at a global level, with no ability to see reports at EU Member State level
A lack of reporting on bot/fake account activity involving domestic not foreign actors
Insufficient information about tools intended to help users find trustworthy content, including a lack of data to demonstrate efficacy
Lack of a universal, user-friendly mechanism for reporting disinformation and being adequately informed of the outcome
A lack of consistent use of fact-checkers across platforms and in all EU Member states and languages
The assessment also identifies gaps in what the code covers — such as types of manipulative online behavior that fall outside the current scope (such as hack-and-leak operations; impersonation; the creation of fictitious groups or fake parody accounts; the theft of existing artefacts; deep fakes; the purchase of fake engagements; and the involvement of influencers).
“The experience gained through the monitoring of the Code shows that the scope of its commitments may be too narrow,” it suggests, adding: “The vagueness of the Code’s commitments in this respect creates serious risks of incomplete action against disinformation.”
Microtargeting of political ads is also discussed in the assessment as a gap.
On this it writes:
The Code presently does not prohibit micro-targeting or restrict the range of targeting criteria that platforms may offer with respect to paid-for political content, although one of the objectives set out for the Code in the April 2018 Communication was “restricting targeting options for political advertising.” Recent research shows that the vast majority of the public are opposed to the micro-targeting concerning certain content (including political advertising) or based on certain sensitive attributes (including political affiliation). Further reflections in this area will be pursued without prejudice to any future policy on micro-targeting of commercial ads.
The Commission also notes that the European Cooperation Network on elections is “currently investigating the issue in depth”. “This work will inform the European Democracy Action Plan, which will look into the issue of micro-targeting in political campaigns to ensure greater transparency on paid political advertising,” it adds.
The review also points to a major gap around the fairness of online political ads — given the lack of rules at EU level establishing spending limits for political advertising (or “addressing fair access to media for political parties or candidates participating in the elections to the European Parliament”), combined with a variable approach from platforms to whether or not they allow political ads.
“The issue of online application of laws in the electoral context and their modernisation is addressed in the work of the European Cooperation Network on Elections. The European Democracy Action Plan will look into solutions to ensure greater transparency of paid political advertising as well as clearer rules on the financing of European political parties,” it adds.
Another major deficiency of the code the Commission assessment identifies is the lack of adequate key performance indicators to enable effective monitoring.
The Commission further identifies a number of inherent limits to the self-regulatory approach — such as a lack of universal participation creating inequalities and variable compliance; and the lack of an independent oversight mechanism for monitoring performance.
It also highlights concerns about risks to fundamental rights from the current approach — such as the lack of a complaints procedure or other remedies.
In conclusion, the Commission suggests a number of improvements for the code — such as “commonly-shared definitions, clearer procedures, more precise commitments and transparent key performance indicators and appropriate monitoring” — as well as calling for further effort to broaden participation, in particular from the advertising sector.
It also wants to see a more structured model for cooperation between platforms and the research community.
“At present, it remains difficult to precisely assess the timeliness, comprehensiveness and impact of platforms’ actions, as the Commission and public authorities are still very much reliant on the willingness of platforms to share information and data. The lack of access to data allowing for an independent evaluation of emerging trends and threats posed by online disinformation, as well as the absence of meaningful KPIs to assess the effectiveness of platforms’ policies to counter the phenomenon, is a fundamental shortcoming of the current Code,” it notes.
“A structured monitoring programme may constitute a pragmatic way to mobilise the platforms and secure their accountability. The programme for monitoring disinformation around COVID-19 foreseen in the June 2020 Communication will be an opportunity to verify the adequacy of such an approach and prepare the ground for further reflection on the best way forward in the fight to disinformation,” it adds.
A consultation on the Commission’s European Democracy Action plan concludes next week — and that’s one vehicle where it might seek to set down more fixed and measurable counter-disinformation requirements.
The Digital Services Act, meanwhile, which is slated to tackle platform responsibilities, is due in draft by the end of the year.
First COVID-19 disinformation reports
Also today the Commission has published the first monthly reports of action taken against coronavirus-related disinformation by Facebook, Google, Microsoft, TikTok, Twitter and Mozilla.
In June it pressed platforms for more detailed data on actions being taken to promote authoritative content; improve users’ awareness; and limit coronavirus disinformation and advertising related to COVID-19.
“Overall, they show that the signatories to the Code have stepped up their efforts,” the Commission writes today, noting that all platforms have increased the visibility of authoritative sources — by giving prominence to COVID-19 information from the WHO and national health organisations, and by deploying “new tools and services to facilitate access to relevant and reliable information relating to the evolution of the crisis”.
Although here, too, it notes that some of the products or services were not deployed in all EU countries.
“Platforms have stepped up their efforts to detect cases of social media manipulation and malign influence operations or coordinated inauthentic behaviour. While platforms detected a high number of content including false information related to COVID-19, they did not detect coordinated disinformation operations with specific focus on COVID-19 run on their services,” it adds.
On ads the third party sites purveying COVID-19 disinformation it says the reports highlight “robust actions” taken to limit the flow of advertising, while providing free COVID-related ads space to government and healthcare organisations.
from RSSMix.com Mix ID 8204425 https://ift.tt/3bQPA0b via IFTTT
0 notes
Text
Android users’ security and privacy at risk from shadowy ecosystem of pre-installed software, study warns
A large-scale independent study of pre-installed Android apps has cast a critical spotlight on the privacy and security risks that preloaded software poses to users of the Google developed mobile platform.
The researchers behind the paper, which has been published in preliminary form ahead of a future presentation at the IEEE Symposium on Security and Privacy, unearthed a complex ecosystem of players with a primary focus on advertising and “data-driven services” — which they argue the average Android user is unlikely to be unaware of (while also likely lacking the ability to uninstall/evade the baked in software’s privileged access to data and resources themselves).
The study, which was carried out by researchers at the Universidad Carlos III de Madrid (UC3M) and the IMDEA Networks Institute, in collaboration with the International Computer Science Institute (ICSI) at Berkeley (USA) and Stony Brook University of New York (US), encompassed more than 82,000 pre-installed Android apps across more than 1,700 devices manufactured by 214 brands, according to the IMDEA institute.
“The study shows, on the one hand, that the permission model on the Android operating system and its apps allow a large number of actors to track and obtain personal user information,” it writes. “At the same time, it reveals that the end user is not aware of these actors in the Android terminals or of the implications that this practice could have on their privacy. Furthermore, the presence of this privileged software in the system makes it difficult to eliminate it if one is not an expert user.”
An example of a well-known app that can come pre-installed on certain Android devices is Facebook .
Earlier this year the social network giant was revealed to have inked an unknown number of agreements with device makers to preload its app. And while the company has claimed these pre-installs are just placeholders — unless or until a user chooses to actively engage with and download the Facebook app, Android users essentially have to take those claims on trust with no ability to verify the company’s claims (short of finding a friendly security researcher to conduct a traffic analysis) nor remove the app from their device themselves. Facebook pre-loads can only be disabled, not deleted entirely.
The company’s preloads also sometimes include a handful of other Facebook-branded system apps which are even less visible on the device and whose function is even more opaque.
Facebook previously confirmed to TechCrunch there’s no ability for Android users to delete any of its preloaded Facebook system apps either.
“Facebook uses Android system apps to ensure people have the best possible user experience including reliably receiving notifications and having the latest version of our apps. These system apps only support the Facebook family of apps and products, are designed to be off by default until a person starts using a Facebook app, and can always be disabled,” a Facebook spokesperson told us earlier this month.
But the social network is just one of scores of companies involved in a sprawling, opaque and seemingly interlinked data gathering and trading ecosystem that Android supports and which the researchers set out to shine a light into.
In all 1,200 developers were identified behind the pre-installed software they found in the data-set they examined, as well as more than 11,000 third party libraries (SDKs). Many of the preloaded apps were found to display what the researchers dub potentially dangerous or undesired behavior.
The data-set underpinning their analysis was collected via crowd-sourcing methods — using a purpose-built app (called Firmware Scanner), and pulling data from the Lumen Privacy Monitor app. The latter provided the researchers with visibility on mobile traffic flow — via anonymized network flow metadata obtained from its users.
They also crawled the Google Play Store to compare their findings on pre-installed apps with publicly available apps — and found that just 9% of the package names in their dataset were publicly indexed on Play.
Another concerning finding relates to permissions. In addition to standard permissions defined in Android (i.e. which can be controlled by the user) the researchers say they identified more than 4,845 owner or “personalized” permissions by different actors in the manufacture and distribution of devices.
So that means they found systematic user permissions workarounds being enabled by scores of commercial deals cut in a non-transparency data-driven background Android software ecosystem.
“This type of permission allows the apps advertised on Google Play to evade Android’s permission model to access user data without requiring their consent upon installation of a new app,” writes the IMDEA.
The top-line conclusion of the study is that the supply chain around Android’s open source model is characterized by a lack of transparency — which in turn has enabled an ecosystem to grow unchecked and get established that’s rife with potentially harmful behaviors and even backdoored access to sensitive data, all without most Android users’ consent or awareness. (On the latter front the researchers carried out a small-scale survey of consent forms of some Android phones to examine user awareness.)
tl;dr the phrase ‘if it’s free you’re the product’ is a too trite cherry atop a staggeringly large yet entirely submerged data-gobbling iceberg. (Not least because Android smartphones don’t tend to be entirely free.)
“Potential partnerships and deals — made behind closed doors between stakeholders — may have made user data a commodity before users purchase their devices or decide to install software of their own,” the researchers warn. “Unfortunately, due to a lack of central authority or trust system to allow verification and attribution of the self-signed certificates that are used to sign apps, and due to a lack of any mechanism to identify the purpose and legitimacy of many of these apps and custom permissions, it is difficult to attribute unwanted and harmful app behaviors to the party or parties responsible. This has broader negative implications for accountability and liability in this ecosystem as a whole.”
The researchers go on to make a series of recommendations intended to address the lack of transparency and accountability in the Android ecosystem — including suggesting the introduction and use of certificates signed by globally-trusted certificate authorities, or a certificate transparency repository “dedicated to providing details and attribution for certificates used to sign various Android apps, including pre-installed apps, even if self-signed”.
They also suggest Android devices should be required to document all pre-installed apps, plus their purpose, and name the entity responsible for each piece of software — and do so in a manner that is “accessible and understandable to users”.
“[Android] users are not clearly informed about third-party software that is installed on their devices, including third-party tracking and advertising services embedded in many pre-installed apps, the types of data they collect from them, the capabilities and the amount of control they have on their devices, and the partnerships that allow information to be shared and control to be given to various other companies through custom permissions, backdoors, and side-channels. This necessitates a new form of privacy policy suitable for preinstalled apps to be defined and enforced to ensure that private information is at least communicated to the user in a clear and accessible way, accompanied by mechanisms to enable users to make informed decisions about how or whether to use such devices without having to root their devices,” they argue, calling for overhaul of what’s long been a moribund T&Cs system, from a consumer rights point of view.
In conclusion they couch the study as merely scratching the surface of “a much larger problem”, saying their hope for the work is to bring more attention to the pre-installed Android software ecosystem and encourage more critical examination of its impact on users’ privacy and security.
They also write that they intend to continue to work on improving the tools used to gather the data-set, as well as saying their plan is to “gradually” make the data-set itself available to the research community and regulators to encourage others to dive in.
Google has responded to the paper with the following statement — attributed to a spokesperson:
We appreciate the work of the researchers and have been in contact with them regarding concerns we have about their methodology. Modern smartphones include system software designed by their manufacturers to ensure their devices run properly and meet user expectations. The researchers’ methodology is unable to differentiate pre-installed system software — such as diallers, app stores and diagnostic tools–from malicious software that has accessed the device at a later time, making it difficult to draw clear conclusions. We work with our OEM partners to help them ensure the quality and security of all apps they decide to pre-install on devices, and provide tools and infrastructure to our partners to help them scan their software for behavior that violates our standards for privacy and security. We also provide our partners with clear policies regarding the safety of pre-installed apps, and regularly give them information about potentially dangerous pre-loads we’ve identified.
This report was updated with comment from Google
from iraidajzsmmwtv https://ift.tt/2FzeDqc via IFTTT
0 notes
Text
Android users’ security and privacy at risk from shadowy ecosystem of pre-installed software, study warns
New Post has been published on http://www.readersforum.tk/android-users-security-and-privacy-at-risk-from-shadowy-ecosystem-of-pre-installed-software-study-warns/
Android users’ security and privacy at risk from shadowy ecosystem of pre-installed software, study warns
A large-scale independent study of pre-installed Android apps has cast a critical spotlight on the privacy and security risks that preloaded software poses to users of the Google developed mobile platform.
The researchers behind the paper, which has been published in preliminary form ahead of a future presentation at the IEEE Symposium on Security and Privacy, unearthed a complex ecosystem of players with a primary focus on advertising and “data-driven services” — which they argue the average Android user is unlikely to be unaware of (while also likely lacking the ability to uninstall/evade the baked in software’s privileged access to data and resources themselves).
The study, which was carried out by researchers at the Universidad Carlos III de Madrid (UC3M) and the IMDEA Networks Institute, in collaboration with the International Computer Science Institute (ICSI) at Berkeley (USA) and Stony Brook University of New York (US), encompassed more than 82,000 pre-installed Android apps across more than 1,700 devices manufactured by 214 brands, according to the IMDEA institute.
“The study shows, on the one hand, that the permission model on the Android operating system and its apps allow a large number of actors to track and obtain personal user information,” it writes. “At the same time, it reveals that the end user is not aware of these actors in the Android terminals or of the implications that this practice could have on their privacy. Furthermore, the presence of this privileged software in the system makes it difficult to eliminate it if one is not an expert user.”
An example of a well-known app that can come pre-installed on certain Android devices is Facebook .
Earlier this year the social network giant was revealed to have inked an unknown number of agreements with device makers to preload its app. And while the company has claimed these pre-installs are just placeholders — unless or until a user chooses to actively engage with and download the Facebook app, Android users essentially have to take those claims on trust with no ability to verify the company’s claims (short of finding a friendly security researcher to conduct a traffic analysis) nor remove the app from their device themselves. Facebook pre-loads can only be disabled, not deleted entirely.
The company’s preloads also sometimes include a handful of other Facebook-branded system apps which are even less visible on the device and whose function is even more opaque.
Facebook previously confirmed to TechCrunch there’s no ability for Android users to delete any of its preloaded Facebook system apps either.
“Facebook uses Android system apps to ensure people have the best possible user experience including reliably receiving notifications and having the latest version of our apps. These system apps only support the Facebook family of apps and products, are designed to be off by default until a person starts using a Facebook app, and can always be disabled,” a Facebook spokesperson told us earlier this month.
But the social network is just one of scores of companies involved in a sprawling, opaque and seemingly interlinked data gathering and trading ecosystem that Android supports and which the researchers set out to shine a light into.
In all 1,200 developers were identified behind the pre-installed software they found in the data-set they examined, as well as more than 11,000 third party libraries (SDKs). Many of the preloaded apps were found to display what the researchers dub potentially dangerous or undesired behavior.
The data-set underpinning their analysis was collected via crowd-sourcing methods — using a purpose-built app (called Firmware Scanner), and pulling data from the Lumen Privacy Monitor app. The latter provided the researchers with visibility on mobile traffic flow — via anonymized network flow metadata obtained from its users.
They also crawled the Google Play Store to compare their findings on pre-installed apps with publicly available apps — and found that just 9% of the package names in their dataset were publicly indexed on Play.
Another concerning finding relates to permissions. In addition to standard permissions defined in Android (i.e. which can be controlled by the user) the researchers say they identified more than 4,845 owner or “personalized” permissions by different actors in the manufacture and distribution of devices.
So that means they found systematic user permissions workarounds being enabled by scores of commercial deals cut in a non-transparency data-driven background Android software ecosystem.
“This type of permission allows the apps advertised on Google Play to evade Android’s permission model to access user data without requiring their consent upon installation of a new app,” writes the IMDEA.
The top-line conclusion of the study is that the supply chain around Android’s open source model is characterized by a lack of transparency — which in turn has enabled an ecosystem to grow unchecked and get established that’s rife with potentially harmful behaviors and even backdoored access to sensitive data, all without most Android users’ consent or awareness. (On the latter front the researchers carried out a small-scale survey of consent forms of some Android phones to examine user awareness.)
tl;dr the phrase ‘if it’s free you’re the product’ is a too trite cherry atop a staggeringly large yet entirely submerged data-gobbling iceberg. (Not least because Android smartphones don’t tend to be entirely free.)
“Potential partnerships and deals — made behind closed doors between stakeholders — may have made user data a commodity before users purchase their devices or decide to install software of their own,” the researchers warn. “Unfortunately, due to a lack of central authority or trust system to allow verification and attribution of the self-signed certificates that are used to sign apps, and due to a lack of any mechanism to identify the purpose and legitimacy of many of these apps and custom permissions, it is difficult to attribute unwanted and harmful app behaviors to the party or parties responsible. This has broader negative implications for accountability and liability in this ecosystem as a whole.”
The researchers go on to make a series of recommendations intended to address the lack of transparency and accountability in the Android ecosystem — including suggesting the introduction and use of certificates signed by globally-trusted certificate authorities, or a certificate transparency repository “dedicated to providing details and attribution for certificates used to sign various Android apps, including pre-installed apps, even if self-signed”.
They also suggest Android devices should be required to document all pre-installed apps, plus their purpose, and name the entity responsible for each piece of software — and do so in a manner that is “accessible and understandable to users”.
“[Android] users are not clearly informed about third-party software that is installed on their devices, including third-party tracking and advertising services embedded in many pre-installed apps, the types of data they collect from them, the capabilities and the amount of control they have on their devices, and the partnerships that allow information to be shared and control to be given to various other companies through custom permissions, backdoors, and side-channels. This necessitates a new form of privacy policy suitable for preinstalled apps to be defined and enforced to ensure that private information is at least communicated to the user in a clear and accessible way, accompanied by mechanisms to enable users to make informed decisions about how or whether to use such devices without having to root their devices,” they argue, calling for overhaul of what’s long been a moribund T&Cs system, from a consumer rights point of view.
In conclusion they couch the study as merely scratching the surface of “a much larger problem”, saying their hope for the work is to bring more attention to the pre-installed Android software ecosystem and encourage more critical examination of its impact on users’ privacy and security.
They also write that they intend to continue to work on improving the tools used to gather the data-set, as well as saying their plan is to “gradually” make the data-set itself available to the research community and regulators to encourage others to dive in.
Google has responded to the paper with the following statement — attributed to a spokesperson:
We appreciate the work of the researchers and have been in contact with them regarding concerns we have about their methodology. Modern smartphones include system software designed by their manufacturers to ensure their devices run properly and meet user expectations. The researchers’ methodology is unable to differentiate pre-installed system software — such as diallers, app stores and diagnostic tools–from malicious software that has accessed the device at a later time, making it difficult to draw clear conclusions. We work with our OEM partners to help them ensure the quality and security of all apps they decide to pre-install on devices, and provide tools and infrastructure to our partners to help them scan their software for behavior that violates our standards for privacy and security. We also provide our partners with clear policies regarding the safety of pre-installed apps, and regularly give them information about potentially dangerous pre-loads we’ve identified.
This report was updated with comment from Google
0 notes
Text
Arena Animation Academy | HeRTZ Architects <a href="https://www.savidevelopers.com">Savi Developers</a>
Arena Animation Academy | HeRTZ Architects
Arena Animation Academy, Vadodara experiences a design makeover & revitalization as HeRTZ Architectsunite cues of minimalistic materiality, stark patterns & functionality to conjure a quintessential institutional ambiance.
The Arena Animation Academy at Sayajigunj, Vadodara from the house of HeRTZ Architects is the amalgamation of a copacetic configuration of spaces & urbane design sensibilities. 3,300 sq. ft institutional space curated for client Mr. Kanojiya spreads over a single floor & was conceptualized to maximize the student hosting capacity of the academy.
FACT FILE:
Project: Arena Animation Academy
Architect: HeRTZ Architects
Project Location: Vadodara, Gujarat
Design Team: Ar. Tushar Mhaiskar, Ar. Harshal Patel & Ar. Zain Nizami
Text By: Lavanya Chopra, Team HeRTZ Architects
Photography: Tejas Shah Photography
“With a location in the bustling heart of the city & a growing enrollment influx of students, I wanted a space that would be just the right fit for our students & staff alike. A space that reflects the growth & persona of our company”, shares the client.
Spanning over a tight schedule deadline of just two months from January to March of 2017, the architectural firm faced the complex challenge of conceiving & executing the design strategy for the academy. The initially prevailing design brief required the space to accommodate a strength of 100 students through the working hours. Every proposal on the table at the point didn’t manage to solve the conundrum of the creation of a space to house the increased student strength, in lieu of the initially available blueprint area. At a later stage in the project’s timeline, in addition to the available floor area was made by a small margin& paved the way for a design scheme that amplified the utility of the academy.
“The increment of the built-up area at the time served as the pivotal impetus behind the creation of a renewed format of the design’s plans all together from scratch.”, shared by the Architects. The renewed scheme of design witnessed growth in space capacity&made provisions for a niche that would adeptly host over 150 students. A clear & articulately planned circulation passage became the spine of the design. The connective passage fluently establishes a link amidst the diverse functions of the space& creates a luciden semble of design.
The immaculate Reception Area, two interlinked Workshop Zones & five student Examination Halls &Classrooms comprise the public component of the design spread which engages maximized movement of users through space. An Administrative Office, Counselor’s Cabins & a Private Director’s Cabin consist the official niches of the layout& are accentuated with dapper nuances.
“With the Arena Animation Academy, we’ve tried to bring stated yet functional strains of design into an institutional space that could be comprehensively utilized by all its users whilst emanating a modernistic design identity. The intention was to synthesize a space that encouraged the free flow of spaces into another whilst maintaining a sense of privacy for each independent zone.”, add the Architects.
Earthy & chic materiality dot the interior scheme of the academy. The interplay of wooden accents, stone flooring, metallic elements, minimalist storage, glass partitions& pragmatic furniture come together to lace together the visual DNA& character of Arena Animation Academy.
In terms of furniture & finishes, space is a vast spectrum of muted & elegant choices. Neolith clad cabin table in the Director’s Office makes an edgy & classic statement. The furniture in the Reception & Counselor Cabins is composed majorly using MDF & HDF in combination with eclectic solid hues that are omnipresent through the upholstery of the spaces. The Classrooms utilize laminates to a large degree in the treatment of the interiors. Laser cut metal panels act as voided space partitions & add fluidic transparency and a distinction between varied zones of the design. The ceiling rendered in rectilinear panels of Canadian Wood lends the surface starkness, textural interest& a sense of circulation as one navigates through space.
“The final product that HeRTZ Architects have delivered, is the real embodiment of everything I envisioned for the company in terms of design, requirements & style. They’ve given my thoughts a physical form that everyone can utilize &thrive in for years to come.”, concludes the client Mr.Kanojiya.
An all-inclusive institutional framework that harbors elements of contemporary design & an intrinsic sensitivity to the growing needs of the venture, this project by HeRTZ architects is the epitome of a modern-day oasis for learning & administration.
The post Arena Animation Academy | HeRTZ Architects appeared first on The Architects Diary.
from The Architects Diary https://ift.tt/2VofpeP via SAVI Developers
0 notes
Link
Rainbow Training Institute is one of the best Training institute for the course Core HR Training in Hyderabad.we have well-experienced training faculty with Real-time practical and teaching knowledge on HR Projects.
Rainbow Training Institute is Best Core HR Training In Hyderabad.Rainbow Having Best Trainers to give Core HR Certification Training In Hyderabad and Trainer will provide Core HR Practical Training In Hyderabad.Rainbow Offering Core HR Training In Hyderabad, Bangalore, Pune, Mumbai, Chennai.
Course Overview: Core HR Training in Hyderabad
It is highly Competitive and challenging in today's job market for the requirement of Human Resources (HR) Professionals who can help businesses select, develop, retain and also maintain employees that complement the organizational and buisiness culture.
Rainbow Training is a job oriented HR practical training, designed to provide detailed HR knowledge along with practical implementation.it will help the students and professionals to learn and to handle all HR management functions independently while in real life environment to get an HR job in a Competitive Market.
Course Content :
Recruitment and selection Process :
1.Introduction
2.Identify Vacancy
3.Prepare Job Description and person Specification
4.Recruitment process
5.Advertise
6.Managing the Response
7.Short-listing
8.Types of Hiring's
9.References
10.Arrange Interviews
11.Conduct The Interview
12.What is Job description
13.Decision Making
14.Convey the Decision
15.Appointment Action
16.Challenges in R and S
Joining Formalities :
1.Responsibilities of HR Role
2.Types of joining Documents/checklists
3.Issuing different letters to a new Employee
4.open P file for the new entrant
5.Filling employee ID's/Access card form
6.Opening bank accounts
7.Nomination and Declaration Forms
8.Documentation (pre and post BGV)
Payroll Management :
1.What is cost to company(CTC)
2.Components of CTC and their Detailed explanation
3.Designing of CTC
4.Types Payrolls and its Components
5.Salary Revision and Arrears Calculations
6.Types of Incentives and their Calculations
7.Salary restructuring
8.Reimbursement but not limited to Medical & LTA, conveyance etc, and includes the expenses made in delivering the Job.
9.Collection of Attendance & leave Data/ Unauthorized absenteeism from various locations from the concerns officers.
10.Integration of Salary statement to various interlinked Policies.
11.Generate standardized reports to accounts & finance for payroll processing.
12.Payroll Reports Taxation
13.Attends & answers salary and other queries relating to payroll (Turnaround time of 72 hours).
14.Creates Payroll helpdesk/email account to handle all Employee correspondence along with voice.
15.Payslips generation and preparations
Performance Management :
1. What is performance management?
2.Different types of Appraisal evaluation Techniques
3.Self Assesment
4.Annual Appraisal
5.Salary Survey
6.Analysis and Feedback
Background Candidate Verification:
1.Required docs and experience and Relieving docs from new joiners
2.How to Maintain record of all BGV reports
3.Address Check
4.Database Check for defaulters
5.Reference Check
6.Education Background Check
7.Previous Employment Check
8.Criminal Check
Report Generation while processing Payroll
.Standardization of formats along with the Management.
.Payroll statement with a detailed break up to the Finance Department.
.Annual payroll statement in MIS format to the Management.
Other Core HR Topics :
. Training and Development . Onboarding formalities . Exit Formalities . Performance Appraisal . Employee engagement . Fun at work . Insurance . Policies . Induction . Auditing . Rewards and recognition
Training Faculty Profile :
. We Have well-experienced trainers and expertise.
. worked on Real-time HR management Projects.
. experts in both methods online and offline classes.
. Good Knowledge on Core HR Management functions and Projects.
0 notes