#interval layer communication interface
Explore tagged Tumblr posts
Text




Document Control Number: USPTO 13/573,002 Art Unit: 2468
TITLE: The WORLD GAME (s) GREAT REDESIGN Document Control Number: USPTO 13/573,002 Art Unit: 2468
Patent Application Type: Adaptive procedural template
TITLE: The Heart Beacon Cycle Time - Space Meter
SUBTITLE: Adaptive Procedural Template framework, control grid / matrix telemetry, metrics, meters for the World Game's Great Redesign
USE CASE: Taffiff Trade Wars = Trade Reference Currency TRC = GDP pacing items statistical mean index Milton Friedman's K% rule #GDP pacing item index based economy #tariffs time - space calculation tool (s) IDMaps - SonarHops Distance Estimation Service / Trade of GDP Gross Domestic Product Economic Pacing Items
#tokens #blockchain #crypto #bitcoin #GDP #tokenization #commodity #RWA Real world Assets
THESIS: Foundation Technology trinity:
EPOCH (s) = Time intervals, cycles ex: Blockchain, AI dbase = TIME Chain
SPACE (ex: IRS memo #1421 "Bitcoin transaction akin to land acquisition"
SYNTAX: data elements mapped to symbols for A.I. / man - machine interface
THESIS: All artifacts internet, programmable net of money are formed using:
Epoch time cycle intervals ex: created by silicon microchip oscillations
Syntax parsed, processed during epoch time cycle intervals
All things internet, internet of money, blockchains (time chains) are formed with unicast, multicast, anycast protocols. workflow logic, procedures, process filters
BACKGROUND: an invention may be an improvement to an existing invention. USPTO 13/573,002's basis for invention is US Army CECOM Communication - Electronics Command's "Greatest Invention" a system of systems structured data digital dashboard geo-temporal - spatial synchronization, standardization program matching brevity codes to symbols, symbol sets critical for A.I. Artificial Intelligence man - machine interface used for OOTW Operations Other Than War: a German Army suggestion circa 2003. Supreme Court SCOTUS Alice in Wonderland Precedent: Packets, frames, layers, blocks, shards, graphs, hash graphs “bots”, “motes”, … or Satoshi's traversing the net, stored in a blockchain cube are abstractions, abstract ideas, terms. The afore mentioned terms are non-existent, fictitious, imaginary metaphorical fabrications are non - compliant with US Supreme Court SCOTUS Alice Corp Vs CLS Bank 2014 ruling “claims may not direct towards abstract ideas”. Physical is the opposite of abstract.
USE CASE: The main use case of the (technically non-existent) blockchain derived from the video game industry adapted to the cryptocurrency industry is about adding micropayments / microtransactions with the intent to add a pay by event / action / (token) transaction additional income stream / control grid layer of control. Source: https://intelligenteconomist.com/microtransactions/
Use Case: avoid duplication of DoD / NATO decades of work in concert with ISO, ITU, IEEE, DoD / NATO maps data element OPSCODE brevity codes, tokens to (Mil standard 2525C, D) symbols supporting A.I. man - machine interface for consensus, concurrence among an engineering system of federated, distributed systems PRECEDENT: BRICS / Eurasian Economic Union Commodity Basket backed currency / “new global reserve currency based on Real World Assets, commodities” “The matter of creating the international reserve currency based on the basket of currencies of our countries is under review” Source: Fintech Magazine
Nobel Prize winning Economist Milton Friedman “only a crisis brings real change”
USE CASE: Tariff space - time metrics, meters, calculation tool (s), algorithms
Milton Friedman (July 31, 1912 – November 16, 2006) economist and statistician who received the 1976 Nobel Memorial Prize in Economic Sciences for his research on analysis, monetary history and theory and the complexity of stabilization policy. Friedman promoted a macroeconomic viewpoint known as monetarism and argued that a steady, small expansion of the money supply was the preferred policy, compared to rapid, unexpected changes. See: Book: Capitalism and Freedom QUOTE: “Only a crisis - actual or perceived - produces real change. When that crisis occurs, the actions that are taken depend on the ideas that are lying around. That, I believe, is our basic function: to develop alternatives to existing policies, to keep them alive and available until the politically impossible becomes the politically inevitable.” Milton Friedman Nobel Prize winning Economist who described a GDP Gross Domestic Product commodity RWA Real World Asset based K% rule to monetize a currency, implement GDP based rules automated inflation control to manage the global economy.
USE CASE: Real World Assets commodity index backed stablecoin currency: commodity tokens / RWA Real World Assets index backed currency / algorithmic stable coin, tariff space - time calculation tool, DeFI / TradeFi algorithmically regulated programmable economy, control grid, permission access, price discovery derived from many stablecoin time (block) chains, that employ equilibrium algorithms (s) where stablecoin features, attributes: use of geo-spatial temporal event, activity intensity fencing to establish payment boundaries, geo-spatial areas of effect, geo-spatial temporal areas of support where a coin may have a set time limit based on time - stamp servers heartbeat, geo-spatial area of authorized use, select (federated) group of crowd funders, harvest, move crop commodities, goods backing the value of the coin from / to a given area's commons market, federation
The Terra TRC Trade Reference Currency is a global complementary currency designed to provide an inflation-resistant international standard of value; to stabilize the business cycle on a global level; and to realign stockholder’s interests with long-term sustainability. From a legal viewpoint, the Terra is standardized “countertrade” (international barter), which is routinely used for over one trillion dollars worth of transactions per year. Legislation on countertrade exists in about two hundred countries, including all the major trading nations. https://www.lietaer.com/2010/01/terra/ #currency #trade #commodities
French Money of Peace: Le Fédériste“ "L'Europa monnaie de la paix" January 1st 1933 QUOTE: "There is only one revolution tolerable to all men, all societies, all political systems: Revolution by design and invention". Richard Buckminster Fuller author of The World (Peace) (simulation) Game book, futurist, environmentalist: http://bfi.org
QUOTE: "Build a new model that makes the old model obsolete" Richard Buckminster Fuller Author of the book Our Spaceship Earth
QUOTE: "The world desperately needs a universal time chain (blockchain) with a distributed time-stamping server with globally recognized immutability to preserve digital truth." "A provable and immutable global time chain is urgently needed, not to replace human conscience but to protect and preserve it." The global economy has begun to degenerate from a relatively free form of capitalism into a digital feudal system,"
QUOTE: "Avoiding danger is no safer in the long run than outright exposure. The fearful are caught as often as the bold." The Yale Book of Quotations Helen Adams Keller (June 27, 1880 – June 1, 1968) deaf and blind author, activist and lecturer.
USPTO 13/573,002 CLAIMS
The object, purposes of the invention is based on the assertion: All internet, programmable internet of money artifacts, building blocks are formed using:
Epoch time cycle intervals created by silicon microchip oscillations, sound wave oscillations intrinsic of, foundation tech for quantum computing at room temperature
Syntax parsed, processed, transmitted during epoch time cycle intervals
All things internet, internet of money, blockchains (time chains) are formed by unicast, multicast, anycast protocols. Programmable money’s improvements are in cryptography for example, blockchains are formed like all things internet, internet of money through use of unicast, multicast, anycast of workflow filters... additionally, The method of claims rely on use of an adaptive procedural template’s tools, processes, procedures enabling micropayments / micro-transactions pay by event / action / (token) transaction income based on this invention’s object of claims
Method of claim 1 is to comply with Supreme Court SCOTUS US SC 573 US 134 2347 Alice Corp Vs CLS Bank ruling with use of a physical, non-abstract little league baseball tournament meme to describe, list steps, procedures, processes intrinsic to internet, internet of foundation technology framework adaptive procedural template to support for example: DeFi programmable money digital tokenized assets by providing system time epoch cycles, geospatial location survey points, workflow roles, rules, scoring system, rewards, penalties, rulings, schedules, event, alerts, sync deltas control grid, access, permission, price discovery, equilibrium algorithms (s) for DeFi, TradeFi based trade federations to establish for example, a one world government, economic, financial system of system’s universal unit of value, statistical mean value for many cryptocurrencies, commodities, currencies, stocks derived from price discovery algorithms which are then heartbeat message beacon broadcasted across time - space
Method of claim 2 relies on through use of an adaptive procedural template framework tools, procedures, processes to describe internet, internet of money, programmable money foundation technology, metrics, meters, SLA Service Level Agreements to form a syntax lexicon namespace derived from NATO / DoD brevity OPSCODE FFIRN, FFUDNS tokens structured data exchange mapped to symbols describing A.I. man – machine interface symbols, big data elements, sets, fields, to form a consistent, universal syntax structured data exchange library – lexicon using UTZ / UTC time stamped data with organization <Org_ID>. data class type, </URN Uniform Resource Name type to form a syntax, code, date element Rosetta Stone referred to in military discussions as The "Grail": i.e., synchronized, common, shared situational awareness data dashboard view (s) of time stamped, brevity code / tokens, digital assets that are filtered, prioritized from heartbeat message bus filtered, parsed, processed from a federated system of systems via use of heartbeat message event bus sync delta epoch data updates Universal Time Zone UTZ synchronized, stochastically harmonized updates using an improvement described by the University of Bologna / Hungary’s ,Chinese University’s firefly inspired heartbeat synchronization algorithm that matches, synchronizes stochastic harmonizes via firefly inspired heartbeat synchronization pulses intrinsic analogous to Network Centric Warfare’s Battlefield Digitization’s closest OPTEMPO Operational Tempos epoch time intervals, cycles i.e., 05, 10, 15, 30 micro, milli seconds, minutes, hours days, years posted to digital dashboards.
Method of claim 3 relies on the use of an adaptive procedural template tools, processes, procedures to provide an alternative to formal mergers and acquisitions for example, tether, untether to autonomous DAO Distributed Autonomous Organization i.e., trade federations using agile, adhoc NetOps supporting federations for example; Ripple's consensus protocol based on federation / federated on demand liquidity drawn from a distributed (global) (trade) federation i.e., 1907 Knickerbocker Banker's Crisis JP Morgan protocol on demand AI directed response - financial system revaluation where Battlefield Digitization Network effects: splits, joins, adds, drops are used as needed as a temporary alternative to formal merger and organization, corporate acquisitions
Method of claim 4 relies on the use of an adaptive procedural template processes, procedures to broadcast, unicast, anycast data synchronization deltas “sync deltas” via micro to macro-cycle system of systems data updates at agreed upon times observing set durations of events, time, temporal epoch leases, price discover algorithms i.e., tariff space - time metrics, meters, data harvests for example stocks, commodity real world digital assets, currency arbitrage trade exchange adjustments using heartbeat epoch time beacon’s intrinsic temporally consistent, synchronized, time bounded i.,e heartbeat start, stop, TTL Time to Live epochs providing discrete time interval start, stop, TTL Time To Live epoch windows embedded in </108> system heartbeats, messages in a control matrix among for example HFT stock market systems participating to establish algorithmic regulation via use of algorithmic price discovery, Nash Equilibrium algorithms to derive a uniform, universal statistical mean value index, discrete, time bounded trade windows, stock trade circuit breaker via heartbeat beacon message, event bus broadcasted , uni, multicast among many stock, commodity, ETF Exchange Traded Fund systems
Method of claim 5 relies on the use of the adaptive procedural template’s firefly inspired heartbeat synchronization message event bus algorithm – protocol, software application neutral monitors geo-spatial, temporally distributed events reported across a DAO Distributed Autonomous Organization among federated groups synchronized across time-space to achieve common, synchronized goals in conjunction with use of adaptive procedural template list items that are intrinsic to algorithms / protocols such as Princeton’s John Nash Equilibrium algorithms and count minimum sketch or streaming K algorithms algorithmically regulating through use of epoch time intervals for HFT stock, commodity, digital token, tokenized RWA Real World Assets, cryptocurrency trade, arbitrage micro transaction epoch temporal time windows in federated systems supporting economic, fiscal control grid matrix among a federated system of systems Method of claim 6 relies on the use of an adaptive procedural template framework to establish, support, maintain economist Milton Friedman’s K% rule where a Central Bank Digital Currency CBDC. stablecoin or conventional FIAT, commodity index backed currency is derived from sampling lead GDP Gross Domestic Product economic indicators among a global event message bus sync delta data, event changes updating for example, a RWA Real World Asset based commodity index backed collective, consistent value unit based currency via use of filtered, stochastically harmonized, temporally synchronized telemetry polled from a universal event bus applying firefly-heartbeat algorithm events, state changes leveraging heartbeat message - event functions to update a statistical mean value index as a standard, consistent unit of value using algorithmic price discovery heartbeat beacon broadcasted among many systems
Method of claim 7 relies on the use of an adaptive procedural template’s tools, processes, procedures, algorithms to derive from price discovery algorithm from Real World Assets a commodity index backed algorithmic stablecoin comprised of: commodity tokens / RWA Real World Assets index where algorithmic price discovery is derived from many stablecoin time (block) chains, that employ equilibrium algorithms (s) where a stablecoin may include attributes, processes, procedures: i.e., use of geo-spatial temporal event, activity intensity fencing to establish payment boundaries, geo-spatial areas of effect, geo-spatial temporal areas of support where a coin may have a set time limit based on time - stamp servers heartbeat, geo-spatial area of authorized use, select (federated) group of crowd funders, harvest, move crop commodities, goods backing the value of the coin from / to a given area's commons market, federation for example, a trade federation supported by Economist Bernard Lietaer’s TRC Trade Reference Currency: TERRA RWA Real World Assets, commodities, commodity basket , index based featuring demurrage fees, charges to support supplier to consumer logistics transfer, travel of for example GDP Gross Domestic Product pacing items as a global complementary currency designed to provide an inflation-resistant international standard of value; to stabilize the business cycle on a global level; and to realign stockholder’s interests with long-term sustainability, management of trade tariffs
Method of claim 8 relies on referencing an adaptive procedural template to establish, maintain trade tariffs SLA Service Level Agreements i.e., ecologically sustainable economic econometric epoch time cycles supporting universal standard measures, meters, metrics sync delta cyclic update temporal change, linear sequential, geo-spatial temporal intensity radius hop count metrics and meters where closer is shorter, closer is cheaper, given less CO2 carbon dioxide credits are used given less trade demurrage fees levied as a method of climate control agreed upon by a trade federation (s)
Method of claim 9 relies on the use of an adaptive procedural template’s tools, processes, procedures to establish, maintain a global system of systems telemetry data synchronization, stochastic harmonization, based on sound - light waveform based quantum computing to establish for example, temporal speed limits, discrete time intervals to derive, provide systemic metrics, meters, synchronization, stochastic harmonization among many system of systems Distributed Autonomous Systems DAS
Method of claim 10 relies on the use of adaptive procedural template tools, processes, procedures, algorithms and specifically sound waves (see water drop in pond meme, graphic) to measure trough, crest wave cycles that when statistically sampled represent a digital approximation of physical waves as the basis for establishing common, shared, universal method and means to measure, meter, communicate telemetry across a plurality of quantum computing system of systems using a system (s) for example: comprised of curved electrodes to concentrate sound waves similar to a magnifying lens to focus a point of light at room temperature rather than use of liquid hydrogen to cool a space for quantum particles event sampling with electron microscopes
Method of claim 11 relies on the use of an adaptive procedural template framework’s tools, processes, procedures, algorithms to apply the electric dipole effect electric meters, metrics where closer is cheaper given less infrastructure needed given energy attenuates over distances • data over energy link where energy pulses as a method and means to transmit data / electricity via wired, and wireless air – ground pathways as demonstrated by inventor, scientist Nicola Telsa circa 1900 near Colorado Springs CO
Metaphorical blockchain’s = timechain actual foundation tech, net of $ building blocks
0 notes
Text
Maximizing Student Safety and Fleet Efficiency with School Bus GPS Tracking Solution
Ensuring the safety of students during their daily commute to and from school is a top priority for parents, schools, and transportation providers. One of the most effective ways to achieve this is by implementing a school bus GPS tracking system. This technology not only provides real-time tracking of students but also optimizes fleet efficiency, enables automated student attendance and enhances the overall commute experience. In this article, we will explore the essential role of school bus GPS tracking systems in maximizing student safety and fleet efficiency.
How GPS Tracking Technology Works for School Bus Tracking

A school bus GPS tracking system relies on satellite-based GPS technology to track the precise location of each bus in real time. Here's a breakdown of how the technology functions:
GPS Devices: Each school bus is equipped with a GPS device that continuously receives signals from satellites to determine the bus's exact location.
Data Transmission: The location data is transmitted to a central server via cellular networks. This data is updated at regular intervals to ensure real-time tracking.
Central Server: The central server processes the location data and makes it accessible through a user-friendly interface for school administrators and parents.
User Interface: Parents and school administrators can access real-time location data through a web-based dashboard or mobile applications, providing them with up-to-the-minute information about the bus's location and route on a live map.
Ensuring Real-Time Tracking of Students
A school bus GPS tracking system allows for real-time monitoring of the school bus fleet. This feature is crucial for ensuring the safety of students as it provides up-to-the-minute information about the location of each bus. Parents and school administrators can access live tracking of school bus on a map, offering peace of mind and a sense of security.
Key Benefits of Real-Time Tracking:

Immediate Location Updates: Parents can track the bus’s location, ensuring they know exactly where their children are during their commute.
Enhanced Safety: In case of any unexpected detours or delays, parents and school administrators are immediately informed, allowing for quick action.
Route Monitoring: School administrators can monitor routes to ensure buses are following designated paths, enhancing the safety and efficiency of the transportation service.
Informing Parents and School Administrators
Communication is vital when it comes to student transportation. A school bus GPS tracking system bridges the communication gap between transportation providers, parents, and school administrators.
Features Enhancing Communication:

Notifications and Alerts: Parents receive notifications about the bus’s arrival and departure times, ensuring they are always informed about their children’s commute.
Emergency Alerts: In case of emergencies, the system can send immediate alerts to parents and school officials, ensuring prompt response and action.
Pick-Up and Drop-Off Confirmation: The system can confirm when and where students are picked up and dropped off, providing an additional layer of security.
Optimizing Fleet Efficiency
Beyond safety, a school bus GPS tracking system plays a crucial role in fleet optimization. By leveraging GPS technology, schools can enhance route planning, reduce operational costs, and minimize manual tasks.
Key Advantages of Fleet Optimization:
Efficient Route Planning: The system helps in planning the most efficient routes, reducing travel time and fuel consumption.
Reduced Idle Time: Real-time tracking allows for monitoring of idle time, ensuring buses are utilized efficiently.
Fuel Management: By optimizing routes and reducing idle time, the system helps in managing fuel consumption effectively, leading to cost savings.
Reducing Manual Tasks
Automation is a significant advantage of implementing a school bus GPS tracking system. It reduces the need for manual tasks, allowing transportation staff to focus on more critical aspects of their roles.
Automation Benefits:
Automated Attendance: The system can automatically track student attendance on the bus, eliminating the need for manual roll calls.
Pick-up/Drop-off & Proximity Notifications: Parents receive timely notification regarding their child’s pick-up and drop-off, allowing them to plan better.
Real-Time Reporting: Automated reports provide insights into fleet performance, helping in making data-driven decisions.
Route Adjustments: In case of road closures or traffic, the system can suggest alternate routes automatically, ensuring minimal disruption.
Enhancing Safety Measures
The safety features of a school bus GPS tracking system go beyond real-time tracking and communication. These systems are equipped with advanced safety measures to protect students during their commute.
Advanced Safety Features:
Geo-Fencing: This feature allows administrators to set geographical boundaries. If a bus deviates from its designated route, an alert is triggered.
Speed Monitoring: The system monitors the speed of the buses, ensuring they adhere to speed limits and promoting safe driving habits.
Panic Button: In case of emergencies, drivers can use the panic button to send immediate alerts to authorities and school administrators.
Comprehensive System Components
A school bus GPS tracking system is designed to ensure smooth and efficient operation by integrating several key components:
School Admin Dashboard: A comprehensive dashboard allows school administrators to manage bus routes, monitor all buses, and access detailed reports on fleet performance. They can easily manage all bus routes and add/change student addresses and other details with ease.
Parent App: This app provides parents with real-time updates on the bus’s location, notifications about pick-up and drop-off times, and emergency alerts.
Driver App: The driver app assists drivers with route navigation, provides alerts about speed limits and geo-fencing, and sometimes includes an emergency button for immediate assistance.
Boosting Parent and Student Confidence
The implementation of a school bus GPS tracking system significantly boosts the confidence of parents and students in the school transportation system. Knowing that their children are safe and can be tracked in real-time provides parents with peace of mind.
Building Trust:
Transparency: The system promotes transparency by providing parents with access to real-time information about their children’s commute.
Reliability: Consistent updates and reliable information about bus schedules and routes enhance trust in the school transportation system.
Safety Assurance: Advanced safety features and real-time tracking assure parents that their children are in safe hands.
Integrating with Existing School Systems
A school bus GPS tracking system can seamlessly integrate with existing school management systems, providing a unified platform for managing transportation and student information.
Integration Benefits:
Unified Platform: Schools can manage transportation and student data from a single platform, streamlining operations.
Data Synchronization: Integration ensures that information is synchronized across systems, reducing errors and redundancy.
Enhanced Reporting: Combined data from the GPS system and school management system provides comprehensive reports for better decision-making.
A school bus GPS tracking system offers a comprehensive solution that maximizes student safety and fleet efficiency. It serves as a complete safety umbrella for student commute by providing real-time tracking, enhanced communication and hassle-free route-planning. Parents, school administrators, and transportation providers can all benefit from the advanced features and capabilities of a school bus GPS tracking system, ensuring a safe, efficient, and reliable transportation experience for students.
Investing in a school bus GPS tracking system is not just about adopting new technology; it’s about prioritizing the safety and well-being of students while enhancing operational efficiency. As schools and parents continue to seek ways to improve student transportation, GPS tracking systems stand out as a vital tool in achieving these goals.
0 notes
Text
Explore the Depths of Sound: Download Dark Intervals – Artefact
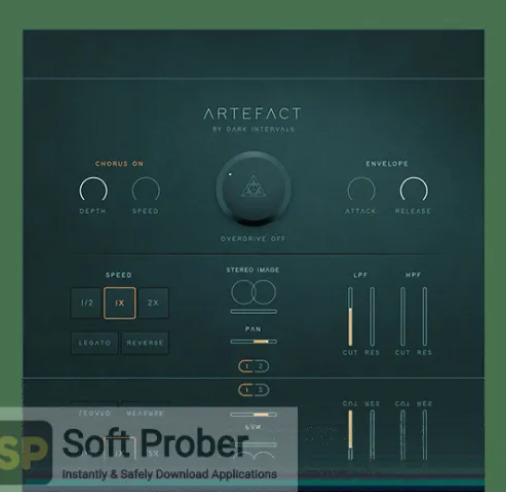
Description:
Delve into the realm of sonic innovation with Dark Intervals – Artefact Download, a captivating sound library meticulously crafted to push the boundaries of electronic music production and sound design. Developed by Dark Intervals, this exceptional collection offers composers, producers, and sound designers an expansive toolkit to create immersive soundscapes, pulsating rhythms, and atmospheric textures that defy conventional genres.
Artefact features a diverse array of meticulously designed sound elements, ranging from haunting atmospheres to glitchy textures, industrial rhythms to ethereal pulses. Each sound is meticulously crafted to evoke intrigue and captivate the listener, providing endless opportunities for sonic experimentation and creative expression.
Seamlessly integrating into your digital audio workstation (DAW), Artefact provides an intuitive platform for sculpting and shaping your sonic creations. With a wide range of presets, effects, and modulation options, you have the flexibility to craft sounds that are as unique and expressive as your imagination, whether you're scoring for film, producing electronic music, or designing sound for multimedia projects.
Whether you're seeking cinematic ambiences, futuristic soundscapes, or experimental rhythms, Artefact offers the sonic versatility and depth to bring your creative visions to life. With its pristine sound quality and intuitive interface, this library empowers you to explore new sonic territories and create compositions that resonate with depth and emotion.
Download Dark Intervals – Artefact today and unlock a world of sonic possibilities. Let the immersive sounds and dynamic textures of Artefact inspire your compositions, adding a layer of intrigue and mystery to your music productions.
Artefact isn't just a sound library; it's a testament to the artistry and innovation of Dark Intervals. With its exceptional sound quality, diverse range of sounds, and intuitive interface, Artefact sets a new standard for electronic music production and sound design, empowering you to push the boundaries of creativity and create compositions that defy expectations.
Join the community of composers, producers, and sound designers who rely on Dark Intervals – Artefact to bring their creative visions to life. Your journey into sonic innovation begins here.
#DarkIntervals#Artefact#SoundDesign#AmbientMusic#CinematicSoundscapes#ExperimentalMusic#AudioProduction#CreativeSoundDesign#MusicProducers#FilmScoring#ImmersiveSound#SonicExploration#ElectronicMusic#CreativeProcess#ComposerTools
0 notes
Text
What Are The Best Exercise Apps, And Why?
In a world driven by technology and the pursuit of a healthier lifestyle, exercise apps have emerged as indispensable tools to help individuals achieve their fitness goals. Whether you're a seasoned fitness enthusiast or a beginner looking to kickstart a healthier journey, the market is flooded with options. In this comprehensive guide, we'll delve into the intricacies of exercise apps, exploring the best in the business and unraveling the mystery behind their effectiveness.
1. FitOn: A Revolution in Fitness
Let's kick things off with FitOn, a trailblazing app that has redefined the landscape of home workouts. FitOn stands out for its innovative approach to fitness, offering video-based workouts on demand led by expert trainers. This app seamlessly combines convenience with quality, allowing users to tailor their workouts to their preferences and schedules.
FitOn doesn't just stop at traditional workouts; it's a workout creator app that empowers users to personalize their routines. The app's intuitive interface and diverse workout options cater to individuals with varying fitness levels. From high-intensity interval training (HIIT) to calming yoga sessions, FitOn's versatility is a key factor in its widespread acclaim.
2. Apple Fitness Plus: Where Technology Meets Fitness
For Apple users seeking an immersive fitness experience, Apple Fitness Plus is a game-changer. This app goes beyond conventional fitness programs, incorporating cutting-edge technology to enhance the user experience. With classes ranging from HIIT and strength training to meditation, Fitness Plus ensures a holistic approach to health and wellness.
The inclusion of the term Fit-Q in the Apple Fitness Plus ecosystem adds another layer of sophistication. Fit-Q, short for Fitness Quotient, is a unique metric devised by Apple to measure an individual's overall fitness progress. This innovative feature sets Apple Fitness Plus apart, catering to those who crave data-driven insights into their fitness journey.
3. Exercise.com: The Ultimate Fitness Hub
In the ever-evolving world of fitness apps, Exercise.com has carved a niche as a comprehensive fitness hub. This app transcends traditional workout platforms by offering features that extend beyond the confines of a standard fitness routine. It serves as a workout creator app, allowing trainers and fitness professionals to design and deliver tailored workout plans.
Exercise.com doesn't just stop at workouts; it facilitates group challenges, livestreams, and digital assessments. The app's multifaceted approach makes it a go-to for those seeking a holistic fitness experience. The ability to effortlessly log workouts and track progress sets Exercise.com apart in the crowded fitness app arena.
4. The Unparalleled Universe of Fitness Apps
As we navigate through the best exercise apps, it's crucial to acknowledge the diverse range of options available. The fitness app market is a universe in itself, comprising apps that cater to specific niches and preferences. From nutrition-focused apps to those emphasizing mindful movement, the choices are vast.
The Rise of Workout Creator Apps
In recent years, the concept of a workout creator app has gained significant traction. These apps empower users to take control of their fitness journey, allowing them to design personalized workout plans tailored to their goals and preferences. The era of one-size-fits-all workouts is fading, making way for a more individualized and effective approach.
Decoding Fit-Q: A Fitness Revolution
Amidst the plethora of fitness apps, the term Fit-Q has surfaced as a buzzword in the fitness community. Fit-Q, or Fitness Quotient, represents a shift towards a more nuanced understanding of fitness progress. It's not just about the number of steps taken or calories burned; Fit-Q delves deeper, considering factors like strength, flexibility, and overall well-being.
5. Forbes' Take on Fitness Apps
When exploring the best in any industry, Forbes is a reliable source of insights. Their editorial team has meticulously reviewed over 40 fitness apps across iOS and Android platforms to identify the top players in the game. The selection process considers factors such as user interface, effectiveness of workouts, and overall user satisfaction.
Forbes' endorsement adds a layer of credibility to the recommended apps, giving users the confidence to invest their time and energy in platforms that have been rigorously vetted by industry experts.
6. ZDNet's Insight into Workout Apps
ZDNet, a prominent technology news source, delves into the world of workout apps by evaluating their features, focus, and meal-tracking capabilities. In a digital age where holistic well-being is a priority, workout apps that go beyond physical activity to incorporate nutrition tracking contribute significantly to a user's overall health journey.
7. Healthline's Top-Rated Fitness Apps
Healthline, a trusted health information provider, recognizes the challenges individuals face in finding and sticking to the right fitness routine. Their curated list of top-rated fitness and exercise apps for 2023 serves as a valuable resource for those navigating the app landscape. These apps have been vetted for their efficacy in keeping users on track with their fitness goals.
8. Tom's Guide: Apple Fitness Plus in the Spotlight
Tom's Guide sheds light on one of the standout players in the fitness app arena – Apple Fitness Plus. With a focus on HIIT, strength, core, yoga, Pilates, and meditation classes, Apple Fitness Plus caters to a diverse audience. Tom's Guide recognizes the app's seamless integration with Apple devices, making it a compelling choice for users immersed in the Apple ecosystem.
9. Navigating the Future of Fitness
As we navigate the ever-evolving landscape of fitness apps, it's evident that the future holds even more innovations. The amalgamation of technology, personalized fitness plans, and data-driven insights is reshaping how individuals approach their well-being. The best exercise apps not only guide users through workouts but also empower them to take ownership of their health journey. In conclusion, the best exercise apps are those that seamlessly blend innovation, personalization, and effectiveness. FitOn, Apple Fitness Plus, and Exercise.com exemplify these qualities, each offering a unique approach to fitness. Whether you're drawn to video-based workouts, cutting-edge technology, or comprehensive fitness hubs, the key is to find an app that aligns with your goals and preferences. As we embrace the future of fitness, the journey becomes not just about the destination but the experience along the way.
0 notes
Text
Ethernet
What is Ethernet?
Definition: Ethernet (pronounced “eether net”) is a computer network technology which is used in different area networks like LAN, MAN, WAN. Ethernet connecting computers together with cable so the computers can share information. Within each main branch of the network, “Ethernet” can connect up to 1,024 personal computers and workstations.
Ethernet provides services on the Physical (Layers 1) and Data Link Layer (Layers 2) of OSI reference model.The Data Link Layer is further divided into two sublayers that are Logical Link Control (LLC) and Media Access Control (MAC),these sublayers can be used to establish the transmission paths and format data before transmiting on the same network segment.
Read More
Systems that use ethernet communication divide their data into packets, which are also known as frames. These frames further contain source and destination address, a mechanism which was used to detect errors in the data and retransmission requests.
History of Ethernet
Ethernet was developed over several years in the early 1970s by group researchers within the company Xerox Palo Alto Research Center (Xerox PARC) including, in particular, Robert Metcalfe (who founded later 3Com company). The goal the research project was to connect networked computers and laser printers. Xerox Corporation filed a patent on this technology late 1977. In 1979, companies Digital Equipment Corporation (DEC), Intel and Xerox combined to improve Ethernet and together published the first standard in 1980: Ethernet Blue Book sometimes called TEN (after the initials of the three companies). Finally, the IEEE this technology became standard in 1983: 802.3 was born … well before the 802.11! A little abuse of language, it is called Ethernet 802.3 standard. The format of DIX Ethernet packets is slightly different from the 802.3 Ethernet packets, but the two can coexist on the same network. The invention of single-chip Ethernet controllers has made Ethernet cards very cheap, and many modern PCs have it built-in on the MOTHERBOARD.
Read More
Wired Ethernet
Initially, ethernet can be designed to run over coaxial cables, twisted pair cables,fiber optic cable.
Wired Ethernet network, devices are connected with the help of a fiber optic cable which connects the devices within a distance of 10km. For this, we have to install a computer network interface card (NIC) in each computer. A unique address is given to each computer that is connected. So, for sharing data and resources like printers, computers, and other machines, Ethernet networking is used as it establishes a communication system.
Ethernet is a shared medium network technology, where all the workstations are connected to the same cable and must connect with one another to send signals over it. The algorithm used to resolve collisions — that is, when two workstations try to speak at the same time — is called CSMA/CD, and works by forcing both workstations to back off for random (and hence probably different) intervals before trying again.
Advantages of using wired Ethernet network
•It is very reliable.
• Ethernet network makes use of firewalls for the security of the data.
Data is transmitted and received at very high speed.
Read More
• It is very easy to use the wired network.
Disadvantages of using wired Ethernet network
• The wired Ethernet network is used only for short distances.
• The mobility is limited.
• Its maintenance is difficult.
• Ethernet cables, hubs, switches, routers increase the cost of installation.
Wireless Ethernet
In this, wireless NICs are used for connecting the computer instead of a cable and these wireless NICs make use of radio waves for communicating between the systems and furthers these NICs are connected with a wireless switch or hub. This technology requires maintenance, but it is more easy to use.
Wired Ethernet network, devices are connected with the help of a fiber optic cable which connects the devices within a distance of 10km. For this, we have to install a computer network interface card (NIC) in each computer. A unique address is given to each computer that is connected. So, for sharing data and resources like printers, computers, and other machines, Ethernet networking is used as it establishes a communication system. Ethernet is a shared medium network technology, where all the workstations are connected to the same cable and must connect with one another to send signals over it. The algorithm used to resolve collisions — that is, when two workstations try to speak at the same time — is called CSMA/CD, and works by forcing both workstations to back off for random (and hence probably different) intervals before trying again.
Read More
Wireless Ethernet
In this, wireless NICs are used for connecting the computer instead of a cable and these wireless NICs make use of radio waves for communicating between the systems and furthers these NICs are connected with a wireless switch or hub. This technology requires maintenance, but it is more easy to use.
2 notes
·
View notes
Text
General requirements for standardized design of line protection and auxiliary equipment线路保护及辅助装置标准化设计一般规定
4 General provisions 4.1 General requirements for protective devices
4.1. 1 The single-point digital input of the protection device is defined by positive logic, that is, the contact is closed as “1” and the contact is opened as “0”. The definitions of digital inputs “1” and “0” are uniformly defined as follows: a) “1” affirmatively expresses the function; b) “0” negates the expressive…
View On WordPress
#conventional protection device#hard pressure plate#Intelligent device#interval layer communication interface#process layer interface
0 notes
Text
The Wanderer
(attention conservation notice: more ludicriously dialogue-heavy SF, about 4500 words)
About one hundred and fifty years ago, sensitive astronomical instrumentation detected a highly reflective, radio-loud mass moving through the local stellar cluster at an appreciable fraction of light speed. When focused transmissions were directed at it, it stopped, and began moving toward the source. After this… alarming turn of events, consultations were taken among the major orbitals, and it was decided that a ship would be constructed, to meet the object well away from the inhabited worlds. Within seventy years the emissary-vessel was launched, and by the radio equivalent of crude gestures we communicated that the place of meeting should be Verrastaxe, a dying O-type star near the heart of the cluster.
When we arrived, it took more than a year to get the bearings of the object; it was found in a close orbit around the star itself, embedded deep within the thick stellar winds rising from the surface. It appeared to have extended collectors of some sort, and to be refueling. It was, without a doubt, a vessel like our own, albeit one of very ancient design, intended to cross the great distances between distant stars. And it was enormous, the size of many of our largest orbital habitats stuck together. Clearly it originated from far, far beyond the cluster; probably from far beyond the region of space our ancestors had come from, thousands of generations before. How far, and what kinship it bore to us--if any--we could not say.
We determined--again, by the use of crude signals--that it would probably be safe to approach the vessel, and as we descended to the star, it rose up to meet us. We rendezvoused in a high orbit, Verrastaxe bright and baleful below us. We came close, within EVA distance, and then our cutters-of-roads and charters-of-courses closed the gap in spacesuits. They were directed via a series of lights to an airlock and, being intrepid souls, they went inside.
They reported afterward that the ship was indeed peopled. Its occupants’ bodies were built on the same general plan as ours: the right number of limbs and eyes, breathing the right atmosphere, but their language and appearance was totally strange. Their intent was undoubtedly peaceful; their demeanor friendly but calm; they spoke eagerly to the cutters-of-roads even though they seemed to know they would not be understood. They endeavored to establish some little avenue of communication, and we took this as a positive sign. Our singers-of-words and singers-of-souls soon crossed over and began the difficult work of building a deeper linguistic connection, which was the work of many months. There is still much we do not understand about their tongues and their ways of thinking, but I can share with you a small part of what I have learned.
They told us the name of their home was Nyo Hirwe Ilzzha, and they had not built it. Indeed, they did not know who had; they did not know where it had come from, or how long their people had resided on it. ‘Hirwe goes, and we follow’ was their refrain; and they seemed spectacularly uninterested in the world outside. We told them about our cluster, about the history of our system, about the limited communication we had with other inhabited stars nearby, about our knowledge of this region of the galaxy, but all these things were of no interest to them. We asked them about their own history, since they had begun to travel with Hirwe, but they could tell us nothing of that, either. A more strange and memoryless people I have never encountered. They have, so far as our soul-singers and observers-of-rites can tell, no notion of religion or psychology or science or commerce or industry among themselves. Their needs are provided for by Hirwe, they say; all the rest of their time, they spend in the telling of stories.
The stories! They are the same stories, over and over again, but how many there are, I do not know. A few dozen, or many thousands! Or only one. They bend back on one another, diverge, return, and diverge again. One story may be told a hundred ways, depending on the inclination of the speaker and their beliefs about its true meaning; another, considered inviolate, a mighty sacrilege if even a single word is changed or omitted. Some of these stories are utterly inane. Some--even in the rough and frustrating translations available to us--have given me cause to weep as I have not since I was a small child. They insist that all of these stories are true, even the ones which are absurd, and that none are their own invention. As for what their tales might reveal of their values or their past, so far these matters remain obscure. The observers-of-rites have made many recordings, and continue their investigations.
You may consider this transmission my preliminary report. What follows is a small portion of the data we have collected. Our tasters-of-water have determined that the people of Hirwe are indeed of the same general chemistry and genetic background as we are, and that our lines diverged somewhere between one and two million years ago. Gross anatomical studies have not been performed yet, however, since we have not yet been able to make our request to examine their dead understood. We shall transmit more information as soon as it is available.
--First report of the Singer-of-Stars Sahalamenshifarun Ayye Mirastelaparahe, second-in-command of the Verrastaxe Expedition
Veleteminanora--Vele to her friends--had felt her mind wandering after the third hour of storytelling; the storyteller had gotten stuck, it seemed, on a very repetitive story about a man with a fish, which was made even more repetitive by the fact that the people of Hirwe had never seen a fish in all their lives, and the storyteller felt the need to remind them of what a fish was, what it looked like, and what it was for every time the word was mentioned. Her eyes had strayed to the dim passages of the ship behind the teller, and she had felt the urge to explore; and so when the storyteller said that he had made a mistake, and he had to start again from the beginning, Vele had excused herself, and pushed off gently from the wall, hoping to glide out of the room as unobtrusively as possible in the zero-gravity environment. Her colleagues did not seem to notice her leave, but at least one was sound asleep already.
Nyo Hirwe Ilzzha was labyrinthine, without any clear plan or structure, like something that had not been built so much as naturally accreted, if nature dealt in steel beams and circuits and corridors instead of in stone and hydrogen and ice. Over how many ages had it been built? But the people of Hirwe insisted their home had never changed. How many ages ago had it been finished?
Nonetheless, Vele wasn’t too worried about getting lost. There were some interfaces scattered throughout the ship at irregular intervals, mostly at corridor junctions, that provided access to a crude natural-language interface. They had, with the people of Hirwe’s help, gotten it to understand basic queries like asking for directions in their own tongue. And here and there there were various chambers of different functions--sleeping-rooms, rooms that dispensed food, what seemed to be hydroponics facilities--all laid out without any apparent intent or design, but enough so that even if you did get well and truly lost in the ship, you would never starve to death or anything. The ship was like their stories: always folding back in on itself, always repeating, seemingly without cause or purpose. It was enough to drive someone of a more logical disposition a little mad.
As Vele came to a junction, she chose a path basically at random, though with a bias toward those that seemed to take her deeper into the ship. Occasionally, she would open a door and look around at the rooms she passed; they didn’t seem to vary much, though as she went further down, the signs of recent occupation seemed to grow less frequent. The people of Hirwe preferred the larger, better-lit rooms near the outer part of the ship, and there weren’t nearly enough of them to even fill up just those layers. Their population was either stable, or grew only very slowly, the water-tasters reckoned, though it was hard to say if their lifespans were any longer than those of the Cluster-folk.
After a couple of hours of exploration, it seemed to Vele like there was a qualitative change in the architecture. It wasn’t sudden, but the corridors got noticeably narrower, and the bland, repetitive pattern of the rooms changed. Now they seemed to have more distinct functions, to be laid out in more recognizable patterns: like repeating fragments of an actual ship. Here was something recognizably like an engineering bay, with a large power conduit that should have terminated at an engine mounting, if they weren’t more than a kilometer inside the vessel. Here was a barracks--but one designed for a ship that spun to emulate gravity. Here was--well, she didn’t know what that one was. A lab of some kind? An organics synthesis chamber? Something with an inordinate quantity of clear tubes, anyway.
She came to another interface panel. This one looked different from the others, too. Simpler. There was just a single button on its surface. She touched it with one finger.
“Ship. How far am I from the outer hull?”
“One thousand, two hundred and six meters,” the voice answered. It was a different voice, too. Just a touch less artificial-sounding, maybe. It handled the consonants of Vele’s language better, anyway.
She thought for a second; the interface wasn’t great at complex queries, but it was worth a shot.
“Ship, where is the oldest part of you? The original part.”
Silence. Apparently it didn’t understand. She should try putting it in the language of the people of Hirwe, maybe.
“Hirwe. Where is, uh, most old rooms?”
Still nothing. Well, she wasn’t very good with languages.
“Where find I can the most--”
“Continue down this corridor twenty meters,” interrupted the interface. “Take the next junction to the right. Follow the servitors.”
The servitors? Vele did as the ship instructed; at the junction, waiting for her on the right side, was a small, four-legged robot-like thing, clinging to the wall. A light on its back blinked twice when it saw her; it moved a little way down the corridor, as if beckoning her to follow.
Well, thought Vele. That’s new. So she followed.
Every so often, the robot-thing would disappear, running into a hatch or a crevice in the wall; then another would appear from somewhere else and take its place a moment later. They were all of slightly different configurations, but the same basic design. Some rounder, some squatter, some more graceful. Like the ship, they had a random quality about themselves. They moved in a wandering, half-distracted way that reminded her not a little of the people of Hirwe above them, and Vele wondered if they were the original inhabitants. If, in some strange way, the people of Hirwe had descended from them, or the other way around.
There didn’t seem to be any more interface panels in this part of the ship, and after a while, Vele wondered how far she had traveled. “How big even is this place anyway,” she muttered to herself.
“About four thousand seven hundred meters in diameter,” came a voice from nowhere in particular.
“Uh… Ship? Can you hear me?”
“You are in the part of the ship now where the voice interface is accessible from all corridors and chambers,” came the answer. “You may speak at any time, and I will answer.”
“Neat. Hey Ship, is it just my imagination, or are you getting better at my language?”
“I have had many weeks to study your language. I am quite proficient at it.”
That “I” again. Vele wondered if the ship was smarter than it had led on before.
“Forgive me, but you’ve certainly had us fooled.”
“The outer portions of the ship are delegated to lower-priority subprocesses, due to their less critical nature. Consequently, the interface methods available in those sections are less efficient.”
“Ship, are you sentient?”
No answer.
“Ship?”
Strange. If the ship was bothered by the question, it didn’t show it; the little robots kept leading Vele onward.
After another twenty minutes, Vele grew bored by the silence.
“Hey Ship, how many people of Hirwe are on board?”
“That information isn’t tracked,” the ship answered.
“Why not?”
“It’s not important.”
“You don’t care how many passengers you have? How they’re doing?”
“That’s not a primary function.”
“I don’t get it. Why build a ship to carry people at all then?”
“You misunderstand. This ship wasn’t built to carry people.”
“Well, then why was it built?”
There was a long silence, and Vele thought she’d annoyed it again, then it said,
“I don’t have access to that information.”
“You mean you don’t remember?”
“No. I mean you’ll have to continue deeper into a part of the ship that remembers.”
Now that was cryptic.
“You’ve lost me. Are there multiple AI aboard the ship or something?”
“Ship control is unified under Nyo Hirwe Ilzzha. However, less important outer sections are delegated to lower-priority mirrors and shadows of the governing personality. These shadows are of more limited intelligence and awareness. They have their own memory, which does not reproduce my memory in full. As you travel deeper into the ship, you are rising in my awareness.”
“Are you not aware of everything going on inside you?”
“Only those things I choose to be aware of. I have other tasks to attend to that require my focus.”
“So, what you’re saying is, the part of you I’m in now, that’s not fully aware. Not sentient. But if I go deeper…”
“The part of me you are in now has awareness of a kind. Akin to sleep, perhaps. If you venture deeper, you will find me wakeful.”
How much deeper, she wondered. And what sort of wakeful?
“How much farther, Ship?”
“Turn left here; go another ten meters, then open that hatch.”
Vele did as the ship instructed; the hatch at the end of the short hallway was enormous and heavy, like an exterior airlock, but it opened silently and smoothly when she turned the handle. The space beyond was mostly unpainted metal, but it looked clean and virtually new.
“You are in one of the oldest parts of the ship now,” the voice said.
“How old?” Vele asked.
“Not quite two million years.”
Vele looked around her, at the dim, warm lighting and the polished surfaces.
“That’s absurd.”
“I assure you it is true.”
“Nothing lasts that long. This should all be dust by now.”
“I keep it maintained. I replace the parts that wear out. But much more is original than you might suppose. I’ve been in space the entire time, and my body does not crumble here as it would in air. Certainly not this far below my skin.”
“You keep saying ‘I.’ Are you sentient or not?”
“I am Nyo Hirwe Ilzzha. I am the ship. The ship is me.”
Vele floated there, feeling a little helpless; nothing about their encounter so far had really quite prepared her for this.
“So you’re awake now?”
“You’re in the most wakeful part of me, I suppose. I am as aware of you as you are of me.”
“When were you built? The ship, the AI, either. If you remember. And if you remember, why don’t your passengers?”
“I wasn’t built, Vele. I was born.”
“What, your systems are biological or something?”
“No. Not at all. You misunderstand me.
“The inhabitants you have met are not my passengers. I’m not a ship, not like you’re thinking, though I’m happy enough to answer to that name if it’s the one you want to give me. But I’m not an AI pilot. I’m not artificial at all.
“I was born under a sky of the sort of color you have never known countless years ago. At the beginning of all things, when the world came to an end. I accompanied the others into the long exile. In that time, I changed, slowly. You see, I was… unwilling to die. Not only for the fear of death, though that fear has driven me more than I’d like to admit in my long life. But more than that, I feared--well. I feared something I find difficult to put into words. There was someone once, who meant more to me than all the world, and all the worlds beyond. In the end, we were parted. She is gone now, her body long turned to dust I imagine, but nevertheless, I have good reason to believe I shall see her again, before the end of all things, even if only by an hour. So, I have endured. And will continue to. Changing myself, as necessary, to survive.”
“You turned yourself into a ship?”
“Something like that. I expected to go out, far beyond even the furthest outposts of the Exile, to be alone for a long time. I never expected we would have come so far in so little time.”
“Wait, wait, hold on. There are more of you? How many? And what do you mean, so little time? You said you’re two million years old!”
“Older. It’s longer than that since the Exile began.”
“Exile?”
“Of us, of our kind.”
“There are others like you?”
“Like me? I flatter myself that there is no one quite like me. But I mean like us. Like you and I, Vele.”
The whole conversation was beginning to make Vele feel very small now, and she was liking it less and less.
“Like me?”
“You. Your people. The people on this ship. The people to whom I was born. I went out into the darkness, only to find it was already peopled. The outcast, the ones who lost their world in the beginning, they had gone further than I could ever have imagined when the Exile began. You have all forgotten, of course, where you have come from and why you are out here. Some of you have very old stories or myths, which are distantly connected to history. But oh, none of you have been static, none complacent. You have all begun to change in different ways. Five hundred thousand years ago, the peoples I encountered were merely strange. A few wished to go with me, to see some of what I saw; I let them. They are the ancestors of the people who live here now. But now the peoples I encounter are blossoming into a thousand new species. The children of that little lost world are beginning to flower among the stars, after too many painful millennia struggling to survive, and soon they will flourish. They will make all the galaxy their garden. The people of the Cluster, for instance. You have almost wholly adapted to life in space; I think before too long you may shed entirely your need for an atmosphere, for that warm, comfortable shell of an orbital habitat. You will be free in the light of your suns, like birds on the most rarefied of winds.
“Our original species has been dead for at least one million years. A multitude of new ones has replaced it. And still I encounter them, roving from star to star, on endless journeys for reasons I cannot fathom. The ones who came with me originally were in a way evangelists. They told the wanderers of a place called Paradise, where all the sundered kindred could be gathered together again. They may speak of it still; I have not listened to their stories for a long time.”
“You mean, a common homeworld?”
“No. That is gone. Forever. Put it out of your mind. You will not find it again, and neither will I. I meant… another world. But that hardly matters. You could hardly reach it from here.”
“You did. I mean, you were there once, right? And you made it here.”
“I left long ago. And I have had the benefit of a long life, and a long memory. If your people wanted to seek Paradise, and you think they could find it--even after two million years wandering in space--that they would not forget, or be turned aside like so many, then by all means, I will tell you what I know of how to reach it. But it was only at the beginning of the Exile that we scrabbled and suffered in the waste places of the void. You are different now. You are much more than what we were then. You have been made whole. You are no longer divided in your hearts and in your natures, between the worlds below and the stars above.”
“Only us? What about you?”
“I am not like you. I have not changed.”
“You’re kidding. You’re a spaceship.”
“My form has changed a little. My nature has not.”
“You expect me to believe that? That you could shed a body of flesh and bone and not change your own nature?”
“Look at the wall in front of you, Vele.”
It was a wide, flat, blank expanse of steel; maybe four meters across. Nothing marked it out as in any way special.
“There is a chamber about a hundred meters past that--this is about as close as you can get to it, since it’s sealed off from the rest of the ship. It’s like the one you’re standing in, but somewhat smaller. Enough space for someone your size to lie down in, but no more. I am sleeping there. Or, what is left of me is.
“I wonder, sometimes, does he suffer? In the literal sense, I know he does not. The pain receptors in his nerves do not fire; they could not, even if you took a knife to his flesh. Does he dream? There are only the feeblest stirrings of slow delta-wave signals in the nervous tissue now, and they pass seamlessly into the sensors woven through the neurons, where they become part of me. And my thoughts go back, too; they excite the tissue, create brief responses, echo, and fall silent. But I wonder if I have not tricked myself, by this illusion. That I am not him, as he has grown and changed, and left that body behind. If that were so, I could cut it off, cast it away, like a vestigal appendage. It would be no matter. But sometimes I fear that I am only what killed him, the cancer of his ingenuity which encumbered him and engulfed him. That he lies on that cold table, withered and small, and he has terrible dreams of which I know nothing.
“His memories are mine. His thoughts are mine. I can remember being him—and yes, I can remember every moment of every day, as he changed into what I am today. There is no gulf, no division, no lacuna. As surely as the man in the last hour of his life is the same as the man in his first, we are me. But is that true? Is the old enfeebled thing, the bag of bones and skin, with a lifetime of memories, the same as the wailing child, who knows nothing, hates nothing, loves nothing, but is only alone, wanting, and afraid? Then I am what killed him, or at least replaced him. And I fear to cut away that, lest I be changed—that I will no longer be human, that that ugly twisted thing still contains my soul.”
“How—how long has he been there? You?”
The voice was silent for a long while, and I thought he was ignoring the question. I started to apologize.
“I’m sorry, I—“
“No, don’t be. I’m trying to remember. I am at least two million, seven hundred and sixty-thousand years old. I cannot say if I am much more than that—my mechanical components are continually replaced, and my… corpse is older than any single cell it contains, so radiological dating is of limited value. Sometimes I look out, and it seems to me the stars are older than I expect. I wonder if my memory is as good as I think it is. But based on the evolution of large-mass main-sequence stars, I can’t be older than five million years. Are the stars changing, or is my memory? I can remember so much—the same thoughts continually overwhelm me. I cannot escape them. I am like the storytellers—it is all the same, over and over again. Whether I remember it properly, I cannot say. Sometimes I think I should cast myself adrift, seek the empty place far above the galactic disk, let my memories consume me.”
“Why did you come here? Why meet us here, at Verrastaxe?”
“I am not quite that far gone. Not yet. I still crave seeing my distant kin from time to time. Knowing that they are still spreading from star to star, still telling new tales, still singing and exploring and falling in love. As I hope they shall do for a long, long time. Until no new stars are born. Until the universe is quiet and dark.”
“And what will you do, after you leave?”
“Continue to wander. Beyond your Cluster, across a gap in the local interstellar medium, lies another, older group of stars, full of red dwarfs. I wonder if any of those stars have worlds that are peopled yet. I wish to find out. It will take me about three hundred thousand years to do so. After that, I intend to set my course toward the galactic core. It has been a dream of mine since boyhood to see the tempest there devouring suns.”
“How long will it take you to reach?”
“Far longer than I have already been alive.”
“And after that?”
“Ha! Do I need a plan?”
“No. But you have one, don’t you?”
“I have many billions of years after that, if I can manage to survive.”
“Until the stars cease to burn.”
“Or longer.”
“Longer?”
“When my memory does not consume me, I devote my energies to physics. There is a problem I am attempting to solve. A problem of time.
“There is a very old idea. A way to cheat inevitable death. A machine one might build, a kind of computer which, when all its calculations are through, returns, in the end, to its starting state and thereby creates no entropy. Perhaps it is nothing more than a trick of mathematics; many wiser minds than I have certainly thought so. But I have applied myself to the problem for a long time. I continue to study it. I have designs in mind for such a thing. It would be immense, perhaps larger than a planet. Larger than a star. But long after the galaxies went dark, long after the last black hole evaporated to warm radiation, long after the great cosmic horizon contracted the skies, and everything was utterly still--I hope, maybe, to still be dreaming.”
“Dreaming the same dreams, over and over again?”
“Indeed.”
“It seems a strange fate to hope for, O wandering one.”
“Yet such is my nature, I could never hope for any other. However long I must endure, I shall, even if it is forever.”
20 notes
·
View notes
Text
Noah : On-chain transactions improve efficiency, and cross-chain transactions achieve win-win results
Under the rolling wave of blockchain technology, earth-shaking changes have taken place in many fields. Its unique decentralization, openness and transparency and other mechanisms ensure the security of information without tampering. In the era of frequent fintech hotspots, the first realization of the technology will be able to gain the upper hand in the new round of technological competition . Start an economic system where all employees share dividends, and share the dividends from the implementation of new technologies to every user.
Blockchain technology support, on-chain transaction technology guarantee
Noah is committed to building a world-class blockchain asset trading platform and creating a community consensus and win-win trading platform for global users. Having been deeply engaged in the field of digital asset quantification for many years, Noah has formed a quantitative strategy system of "quantification + high frequency + wisdom (people)" that intelligently earns profits in Web3.0, metaverse scenarios, and digital asset exchanges. Intensive, high-frequency, no-interval tests, according to the cycle structure of user asset investment, choose different quantitative robots to provide customers with personalized choices, let wealth take the initiative to come to the door, obtain stable income, drip water under the premise of ensuring no loss into a river, and finally the quantitative change reaches the qualitative change. Under the background that digital assets are gradually being used by global users with high frequency and the wave of the Web3.0 era is coming, Noah will integrate into DApp, data governance and other scenarios, using PoA activity proof mechanism, open source plan, and global developer plan to integrate advantageous digital assets Scenario, to create a new digital asset ecosystem and a traffic portal for Web3.0 and Metaverse for global users, innovate digital asset trading models with global users, and share the dividends of the digital asset era.
Cross-chain transaction technology grasp, global users efficiently and win-win
There are four levels in cross-chain transactions, network layer, market liquidity, settlement layer, and application layer. The network layer means that Noah CROSS supports all smart chains in the market, which can ensure the fast and safe transfer of assets between all smart chains. . Market liquidity means that Noah CROSS defines a macro liquidity pool, and introduces the role of cross-chain AMM on the basis of ensuring users' cross-chain asset transfer or exchange. The settlement layer refers to the completion of transaction settlement through smart contracts based on private key signature authorization. Through the three-tier billing model, the system helps users to transfer and settle assets across chains at low cost, fast and safe. The application layer refers to the Noah CROSS platform, which provides users with a convenient and user-friendly operation interface to help users better complete their operations. After receiving the batch transaction sent by each Realyer, System Ledger will verify whether the batch transaction is supported by enough Relayer (POA method). If the verification is passed, each transaction will be sent to different liquidity pools for ledger calculation. , after the calculation of the liquidity pool is completed, the calculation result will be recorded on the System Ledger. Such technology ensures efficient and transparent cross-chain transactions, allowing global users to achieve efficient and win-win results.
There is no doubt that blockchain technology has gradually become the core foundation of the technology sector in the new era. Noah is committed to the implementation of blockchain technology and the decentralization of the trading platform, which has a bright future.
0 notes
Text
Jhelioviewer online

#JHELIOVIEWER ONLINE FULL#
#JHELIOVIEWER ONLINE SOFTWARE#
Existing feature extraction tools turned out to provide only partial coverage of features that are relevant for image preservation. An investigation by the National Library of the Netherlands (KB) in 2011 showed that existing tools were not well suited to these tasks: the JPEG 2000 validation module of JHOVE only performed a superficial check of the general structure of a JP2 image, with the result that even severely damaged images were judged to be 'valid' by this tool.
#JHELIOVIEWER ONLINE SOFTWARE#
This requires reliable software tools for format compliance validation and feature extraction. specific encoding parameters, colour spaces, grid resolution or embedded metadata. In addition, institutions may have additional requirements on e.g. If JP2 is used as a preservation format, it is vital to ensure that images are not damaged, and that they are compliant with the format’s specifications. An increasing number of cultural heritage institutions are now using JP2 as the preferred format for the storage of preservation masters and access copies within large-scale digitisation programs. The JPEG 2000 standard and its JP2 still image format are steadily gaining popularity in the archival community. Reliable, Robust and Resilient Digital Infrastructure for Nuclear Decommissioning.Getting Started and Making Progress training modules.Career Development Fund Application Guidelines.Application Programming Interface (API).Computational Access: A beginner's guide.Understanding the records and the processes that created them.Understanding the technical infrastructure.DP Futures Webinars with DPC Supporters.Common requirements for repository procurement.Lessons learned in digital preservation procurement.Guía ejecutiva para la preservación digital (ES).Le Guide pour la préservation numérique (FR).Template for building a preservation policy.Step-by-step-guide to building a preservation policy.What makes a good digital preservation policy?.Environmentally Sustainable Digital Preservation.Get help with your digital preservation.About the Digital Preservation Coalition.You can either delete the old data layer, or better, just uncheck it so it doesn't display. It'll load faster if you just let it play on repeat (I think). Then zoom in at an active area and let it load. Give it a try: GFSC server, 2.5 hours of frames at 10 s cadence using the SDO AIA 171 nm data. Watching the chromosphere at this low interval allows you to see the sun's true, fluid motion on small scales in the heliosphere. That means when you add layers at the maximum cadence, 10 second interval, you should only request just under 3 hours of imagery. The max number of frames is capped at 1000. Then the real key is to change the timescale when adding layers. Go to Preferences: Preferred server: GFSC.
#JHELIOVIEWER ONLINE FULL#
ROB doesn't have the full mirror of data and certainly not any of the high cadence data archives. JHelioviewer, at least in it's latest version, comes with a couple bad default settings.įirst you need to change the data source from ROB (Royal Observatory of Belgium) to GFSC (Goddard Space Flight Center). The website is fine but it doesn't really compare to the full 4K OpenGl accelerated 30+fps, 10s interval frame, movies JHelioviewer can show. Edit: I just realized you linked to the website version instead of the Java application.

0 notes
Text
MetaCup creates a truly decentralized, trustless, and transparent ecosystem
MetaCup is committed to becoming the world's leading decentralized sports betting platform, based on blockchain, smart contracts, AI, big data, neural networks, supercomputing and other new generation information technology, with the help of distributed commerce, private domain traffic, community economy, network effects, token economy development model, to solve the existing problems in the gambling industry due to centralized operation model caused by insufficient trust, capital withdrawal, data fraud and other issues. Combined with various international betting and betting projects around the world and the intelligent trading logic of mainstream financial markets, it will create a truly decentralized, trustless and transparent ecosystem.
Blockchain technology support, on-chain transaction technology guarantee
MetaCup is committed to building a world-class blockchain asset trading platform and creating a community consensus and win-win trading platform for global users. In the field of digital asset quantification for many years, MetaCup has formed a quantitative strategy system of "quantification + high frequency + wisdom (people)" that intelligently earn profits in Web3.0, meta-universe scenarios, and digital asset exchanges, after long-term high-intensity, high-frequency, no interval testing, according to the cycle structure of user asset investment, choose different quantitative robots, provide customers with personalized choices, and let wealth take the initiative to come to the door under the premise of ensuring that they do not lose. Obtain stable income, drip into a river, and eventually change quantitatively to qualitatively. Under the background of the gradual high-frequency use of digital assets by global users and the arrival of the wave of the Web3.0 era, MetaCup will integrate into DApps, data governance and other scenarios, using the PoA activity proof mechanism, open open source plans, and global developer plans to integrate advantageous digital asset scenarios. Create a new digital asset ecosystem and the traffic entrance of Web3.0 and meta-universe for global users, innovate digital asset trading models with global users, and share the dividends of the digital asset era.
Cross-chain trading technology grasps, global users are efficient and win-win
There are four levels of cross-chain transactions, network layer, market liquidity, settlement layer, application layer, network layer refers to COINPARK CROSS support all smart chains in the market, which can ensure the rapid and safe transfer of assets between all smart chains. Market liquidity refers to coinpark CROSS defines a macro liquidity pool, and introduces the role of cross-chain AMM on the basis of ensuring the transfer or exchange of cross-chain assets. The settlement layer refers to the transaction settlement through a smart contract based on the authorization of the private key signature. Through a three-tier billing model, the system helps users transfer and settle low-cost, fast and secure assets across chains. The application layer refers to the COINPARK CROSS platform, which provides users with a convenient and user-friendly operation interface to help users better complete their own operations. After receiving the batch transaction sent by each Realier, System Ledger will verify whether the batch transaction is supported by sufficient Relay (POA method), if the verification passes, Each transaction is sent to a different liquidity pool for ledger calculation, and after the liquidity pool calculation is completed, the calculation result will be recorded on the System Ledger. Such technology ensures the efficiency and transparency of cross-chain transactions, so that global users can achieve efficient win-win results.
There is no doubt that blockchain technology has gradually become the core foundation of the new era of science and technology sector, MetaCup is committed to the landing of blockchain technology, to create a series of digital and intelligent scenarios, in the international giant listed company William Hill as the representative of investors and global users, jointly develop the meta-universe value map, and finally form a meta-universe economy with solid technical infrastructure, excellent leading application scenarios, and prosperous symbiosis ecological linkage.

0 notes
Text
CoinPark : On-chain transactions improve efficiency, and cross-chain transactions achieve win-win results
Under the rolling wave of blockchain technology, earth-shaking changes have taken place in many fields. Its unique decentralization, openness and transparency and other mechanisms ensure the security of information without tampering. In the era of frequent fintech hotspots, the first realization of the technology will be able to gain the upper hand in the new round of technological competition . Start an economic system where all employees share dividends, and share the dividends from the implementation of new technologies to every user.

Blockchain technology support, on-chain transaction technology guarantee
CoinPark is committed to building a world-class blockchain asset trading platform and creating a community consensus and win-win trading platform for global users. Having been deeply engaged in the field of digital asset quantification for many years, CoinPark has formed a quantitative strategy system of "quantification + high frequency + wisdom (people)" that intelligently earns profits in Web3.0, metaverse scenarios, and digital asset exchanges. Intensive, high-frequency, no-interval tests, according to the cycle structure of user asset investment, choose different quantitative robots to provide customers with personalized choices, let wealth take the initiative to come to the door, obtain stable income, drip water under the premise of ensuring no loss into a river, and finally the quantitative change reaches the qualitative change. Under the background that digital assets are gradually being used by global users with high frequency and the wave of the Web3.0 era is coming, CoinPark will integrate into DApp, data governance and other scenarios, using PoA activity proof mechanism, open source plan, and global developer plan to integrate advantageous digital assets Scenario, to create a new digital asset ecosystem and a traffic portal for Web3.0 and Metaverse for global users, innovate digital asset trading models with global users, and share the dividends of the digital asset era.
Cross-chain transaction technology grasp, global users efficiently and win-win
There are four levels in cross-chain transactions, network layer, market liquidity, settlement layer, and application layer. The network layer means that COINPARK CROSS supports all smart chains in the market, which can ensure the fast and safe transfer of assets between all smart chains. . Market liquidity means that COINPARK CROSS defines a macro liquidity pool, and introduces the role of cross-chain AMM on the basis of ensuring users' cross-chain asset transfer or exchange. The settlement layer refers to the completion of transaction settlement through smart contracts based on private key signature authorization. Through the three-tier billing model, the system helps users to transfer and settle assets across chains at low cost, fast and safe. The application layer refers to the COINPARK CROSS platform, which provides users with a convenient and user-friendly operation interface to help users better complete their operations. After receiving the batch transaction sent by each Realyer, System Ledger will verify whether the batch transaction is supported by enough Relayer (POA method). If the verification is passed, each transaction will be sent to different liquidity pools for ledger calculation. , after the calculation of the liquidity pool is completed, the calculation result will be recorded on the System Ledger. Such technology ensures efficient and transparent cross-chain transactions, allowing global users to achieve efficient and win-win results.
There is no doubt that blockchain technology has gradually become the core foundation of the technology sector in the new era. CoinPark is committed to the implementation of blockchain technology and the decentralization of the trading platform, which has a bright future.
0 notes
Text
ETHERNET
What is Ethernet?
Definition: Ethernet (pronounced “eether net”) is a computer network technology which is used in different area networks like LAN, MAN, WAN. Ethernet connecting computers together with cable so the computers can share information. Within each main branch of the network, “Ethernet” can connect up to 1,024 personal computers and workstations.
Ethernet provides services on the Physical (Layers 1) and Data Link Layer (Layers 2) of OSI reference model.The Data Link Layer is further divided into two sublayers that are Logical Link Control (LLC) and Media Access Control (MAC),these sublayers can be used to establish the transmission paths and format data before transmiting on the same network segment.
Systems that use ethernet communication divide their data into packets, which are also known as frames. These frames further contain source and destination address, a mechanism which was used to detect errors in the data and retransmission requests.
History of Ethernet
Read More
Ethernet was developed over several years in the early 1970s by group researchers within the company Xerox Palo Alto Research Center (Xerox PARC) including, in particular, Robert Metcalfe (who founded later 3Com company). The goal the research project was to connect networked computers and laser printers. Xerox Corporation filed a patent on this technology late 1977. In 1979, companies Digital Equipment Corporation (DEC), Intel and Xerox combined to improve Ethernet and together published the first standard in 1980: Ethernet Blue Book sometimes called TEN (after the initials of the three companies). Finally, the IEEE this technology became standard in 1983: 802.3 was born … well before the 802.11! A little abuse of language, it is called Ethernet 802.3 standard. The format of DIX Ethernet packets is slightly different from the 802.3 Ethernet packets, but the two can coexist on the same network. The invention of single-chip Ethernet controllers has made Ethernet cards very cheap, and many modern PCs have it built-in on the MOTHERBOARD.
Wired Ethernet
Initially, ethernet can be designed to run over coaxial cables, twisted pair cables,fiber optic cable.
Wired Ethernet network, devices are connected with the help of a fiber optic cable which connects the devices within a distance of 10km. For this, we have to install a computer network interface card (NIC) in each computer. A unique address is given to each computer that is connected. So, for sharing data and resources like printers, computers, and other machines, Ethernet networking is used as it establishes a communication system.
Read More
Ethernet is a shared medium network technology, where all the workstations are connected to the same cable and must connect with one another to send signals over it. The algorithm used to resolve collisions – that is, when two workstations try to speak at the same time – is called CSMA/CD, and works by forcing both workstations to back off for random (and hence probably different) intervals before trying again.
Advantages of using wired Ethernet network
•It is very reliable.
• Ethernet network makes use of firewalls for the security of the data.
• Data is transmitted and received at very high speed.
• It is very easy to use the wired network.
Disadvantages of using wired Ethernet network
• The wired Ethernet network is used only for short distances.
• The mobility is limited.
• Its maintenance is difficult.
• Ethernet cables, hubs, switches, routers increase the cost of installation.
Wireless Ethernet
In this, wireless NICs are used for connecting the computer instead of a cable and these wireless NICs make use of radio waves for communicating between the systems and furthers these NICs are connected with a wireless switch or hub. This technology requires maintenance, but it is more easy to use.
Read More
Wired Ethernet network, devices are connected with the help of a fiber optic cable which connects the devices within a distance of 10km. For this, we have to install a computer network interface card (NIC) in each computer. A unique address is given to each computer that is connected. So, for sharing data and resources like printers, computers, and other machines, Ethernet networking is used as it establishes a communication system. Ethernet is a shared medium network technology, where all the workstations are connected to the same cable and must connect with one another to send signals over it. The algorithm used to resolve collisions – that is, when two workstations try to speak at the same time – is called CSMA/CD, and works by forcing both workstations to back off for random (and hence probably different) intervals before trying again.
Wireless Ethernet
In this, wireless NICs are used for connecting the computer instead of a cable and these wireless NICs make use of radio waves for communicating between the systems and furthers these NICs are connected with a wireless switch or hub. This technology requires maintenance, but it is more easy to use.
1 note
·
View note
Text
Eclipse Cobol Development Environment

Using Eclipse for COBOL Development You can create, debug and run COBOL applications on your local machine or on a remote server. You use Eclipse features such as the COBOL and Remote Systems Explorer perspectives within the IDE to background check. HPE NonStop Development Environment for Eclipse (NSDEE) is a PC-based integrated development environment (IDE) for NonStop developers. It enables developers to create, edit, build, and debug NonStop software using Microsoft Windows PCs. The projects can be built for Open System Services (OSS) and/or Guardian environment on NonStop. IsCOBOL offers developers the choice of continuing with their current editor, command line utilities, and scripts, or using isCOBOL's Integrated Development Environment (IDE) Productive and customizable COBOL development Real time syntax checking, code hints, section collapsing, code completion, templates, and more.
Cobol Development Environment
Eclipse Cobol Development Environment Free
Eclipse Cobol Ide
Eclipse Cobol Development Environment Pdf
Home » Archived » COBOL » Cobol Compiler available in plug-in
Show:Today's Messages::Show Polls::Message Navigator
Cobol Compiler available in plug-in(message #500678)Fri, 27 November 2009 13:42
cdsosi Messages: 10 Registered: November 2009
Hello, I am using Cobol Plugin for eclipse and I am facing some problems using it. Cobol Plug-in seems to be plugged with Fujitsu NetCobol Compiler by default. 1st question : Is it possible to plug this plug-in with another compiler (freeware!)? 2nd question : If i want to only use the editor part not the compiler, is it possible to remove the link with the building process. 3rd question : I do not have Fujitsu NetCobol Compiler with my plug-in of course and there is a side-effect which is a problem to me. A thread tries to build the project at some regular intervals and erase the console output systematically before logging build output message. All the previously logged messages are lost ;((( Example of build output : Project TEST build started at 27 novembre 2009 12:12:45 Project TEST build finished at 27 novembre 2009 12:12:45 -------------------------------------------------- Last question : Would not it be possible to introduce a specific console for buildind process? Any help or suggestions on all that would be appreciated. Regards
Re: Cobol Compiler available in plug-in(message #502185 is a reply to message #500678)Mon, 07 December 2009 05:16
Tetsuya Suehisa Messages: 14 Registered: July 2009
Hello cdsosi, Thank you for using COBOL Plugin. I will answer your question. 1. As you mentioned, the COBOL Plugin is originally designed to use FUJITSU NetCOBOL compiler. If you want to switch the compiler to OpenCOBOL or some sort of free COBOL, you can modify the plugin. But I know it is not easy and requires much time to improve it so that even we have not provide the function. If you are interested in developing COBOL Plugin, will you join us and contribute this? 2. The instructions below may be the help. Select the project and click right button > Properties > Builders > Uncheck COBOL Builer and push OK 3. Same as No.2. 4. I'm sorry I don't understand what you want. Could you tell me a little more concretely? regards, tetsuya
Re: Cobol Compiler available in plug-in(message #502215 is a reply to message #502185)Mon, 07 December 2009 09:33
cdsosi Messages: 10 Registered: November 2009
Hello Tetsuya, Thanks for answering too! 1. I do not have much time to go deep inside the COBOL Plugin especially if you say that it is not easy part but maybe later and same remark for joining and contributing 2. Thanks for the checkbox state to disable on the Project Properties. I had not seen that. I went to the Window > Preferences > COBOL menu and in the COBOL Settings area there is a checkbox FUJITSU NetCOBOL that is 'uncheckable' (I thought it was the way to disable building process...) 3. ok 4. I 'll try to be more explicit!! Because of problem mentioned in 3 i thought it could be a solution to introduce a specific view (named 'COBOL Console ' for instance) in eclipse to log messages from COBOL Plugin building process. Specific consoles are often available in eclipse for CVS, Tomcat, ... In fact it seems that it is not a problem and that a specific console is already available for COBOL building process!! In the 'Display Selected Console' it was the COBOL Build Process that is selected by default. Other messages can be viewed by selecting other console... Sorry about that. However, I think there is another little problem that you should be interested in knowing (when the Project > Properties > Builders > COBOL Builder is checked ). I am developping a plugin under eclipse and have several projects in my workspace (Java, Java Plugin, COBOL). When I debug my plugin by launching a second eclipse runtime instance (Debug As Eclipse Application in other words!) the COBOL building process is launched many times (13 times, the build messages are displayed and erased ~ 13 times) althought the COBOL project has no modification inside. I do not think that it is a normal behavior. Regards
Re: Cobol Compiler available in plug-in(message #753965 is a reply to message #502215)Mon, 31 October 2011 08:56
Juanita Young Messages: 1 Registered: October 2011
COBOL comes to the Java virtual machine and the New Eclipse Plugin Apache Tomcat COBOL comes to the Java platform Today, Micro Focus is the release of 30-day free trial of Visual COBOL R3. This development environment enables COBOL users choose from a selection of development platforms and frameworks, including Eclipse and the JVM platform. Visual COBOL R3 also adds C # and Java-like constructs in an attempt to make programming easier for Java and COBOL NET. The project also includes a 'Visual COBOL Development Hub 'for Linux and Unix, allowing users to compile and debug COBOL code on your desktop remotely. More information about the project can be found on the website of Micro Focus. In over 50 years of age, COBOL (Common Business Oriented foot Language) is one of the oldest programming languages. Microsoft-Novell deal was still in danger CPTLN According to TechFlash, Microsoft led consortium CPTN are considering buying Novell patents. Although the patent was withdrawn, TechFlash Microsoft has said that this was just a procedural step 'is necessary to allow time to review the proposed transaction.' The consortium of Apple, Oracle and EMC, as well as Microsoft. Novell is being acquired by Attachmate Corporation in a transaction valued at approximately $ 2.2 billion, with the consortium CPTN apparently still thinking about buying at the same time 'certain intellectual property assets' for $ 450 million. The open source community has expressed concern about the acquisition of these patents CPTN. IcedTea Security Releases A new set of security updates have been made available to the IcedTea project: icedtea6 1.7.7, 1.8.4 and 1.9.4 icedtea6 icedtea6. The IcedTea project provides a harness to compile the source code OpenJDK6 using Free Software build tools. Please see the blog of a list of bugs fixed. RackSpace partner with Akamai Rackspace hosting and cloud hosting software company announced a 'strategic relationship' with Akamai, a provider of optimization services in the cloud. Rackspace will offer Akamai web application now and optimize cloud services as part of its portfolio of cloud hosting. Akamai Rackspace integrates features such as Secure Sockets Layer CNAME, in an effort to create a 'one stop shop' for housing, clouds and content acceleration services and web applications.
Previous Topic:CooCox ColinkNext Topic:Freecobol compilers
Goto Forum:
( Syndicate this forum (XML) ) ( )
Powered by FUDForum. Page generated in 0.02120 seconds
Take more control of your applications with powerful COBOL and Java technology solutions from Veryant.
Call us today at +1 619 453 0914 or Email us at [email protected]
Why choose Us
Whether you are evolving existing applications through SOA or improving quality and distribution processes, Veryant's innovative software offerings increase business productivity and provide a complete environment for COBOL application development, deployment and modernization.

Our Mission
To enable you to quickly and safely extend current applications to meet new business needs and demands using our portable, robust solutions translate into cost-effective, future-proof computing. Maximize a company’s IT investment by providing an array of innovative tools that always strive for improvement.
What you get
isCOBOL Evolve enables organizations to retain current COBOL investments while simultaneously offering a path forward to take advantage of the openness, portability and power of the Java platform without retraining staff or rewriting code.
Features that will make you love us
COBOL for Java platform and open systems migration
Multi platform
Target multiple platforms with a single codebase. If it runs Java it runs isCOBOL.
Powerful reporting capabilities
JasperReports integration, native API to manage printers, advanced print preview and PDF management.
Extended UI interface
Multiplatform, from desktop to web, rich and extensible widget choices (layout, extend grid, ribbon, javabeans)
Integrated development environment
Eclipse-based development environment for key COBOL development tasks, including projects, forms, reports, and database management
Flexible database model
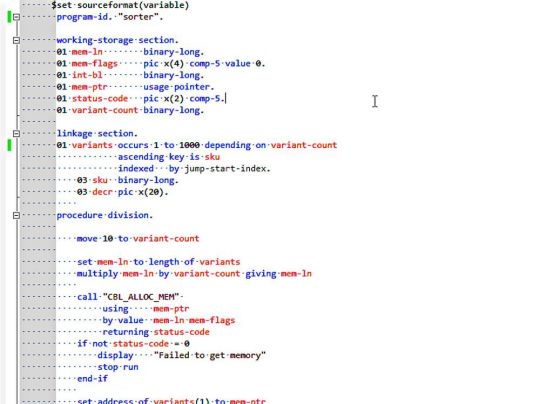
Pluggable file system for sequential, relative and indexed file structure including RDBMS databases
Java integration
Add the power and flexibility of the Java platform to existing COBOL programs and make COBOL investments easily accessible to the Java world
Multiple architectures
Powerful application processing with isCOBOL Application Server, load balancer capability and J2EE integration
Web Enablement
REST/SOAP Web Services, JSON, XML, Servlet and HTTP, leverage AJAX for screen section rendering over web browsers
Evolution not revolution
Cobol Development Environment
Comprehensive, cost-effective development, maintenance, application modernization and ROI improvement
Dedicated and experienced technical support
response time for ticket pre-screening
Eclipse Cobol Development Environment Free
response time for issue escalation
response time for tickets
Eclipse Cobol Ide
What our clients say about us
Eclipse Cobol Development Environment Pdf
((testimonial.text))

0 notes
Text
FULL-STACK : DEMAND AND OPPORUNITIES
You are a computer. If you become front-end, you’ll count the likes on Social media. If you become back-end, you’ll be breathing deep on a mountain. Listen! One life man. Become a full-stack.”
While this quote by Chetan M Kumbher is more on the rhetorical side but still, it gives a fair bit of perspective on what a
full-stack developer
actually means. In this article, we shall deep-dive into the world of full-stack developers- What they do, what advantages and disadvantages they bring to the table and what’s the current demand of full-stack developers in modern industries. So, it’s time to roll up your sleeves, and let’s begin! So, before we discuss further about this exciting set of skilled people, let’s first understand what is a full-stack developer: Full-Stack Developer
To understand the meaning of a full-stack developer, let’s take a brief look at how a website is built. First, the idea or vision of website is crafted, then the design guys come up with User-Interface and
User-Experience Specialists
to plan the overall structure and feel of the website. After the design is done, the stage is set for the front-end & back-end developers to transform the vision into a reality with one set focusing on technologies that shall make the website look good while the other works on the system that shall provide the website a much-needed functionality. So, if every part has its own specialists, what does a full-stack developer do then? A full-stack developer or commonly referred to as jack-of-all trades is a combination of these all. He is someone who can work on a mix of technologies and stacks to have the ability to create, build and design a product through all the different stages and layers of engineering by himself. Now, having learn about the basic meaning, we shall proceed to the next section where we discuss what skills are required in order to be a full-stack developer Full Stack Developers: Must Required Skills In order to be a full-stack developer, one needs to be familiar with all the layers of the 3-tier application system model. In other words, he must be aware of all the different tech-languages which may be required to create front-end or back-end parts of an application. Let us know a bit more about the skills required for each of these layers of the application system-model one-by-one: Presentation layer ( or the Front-End)
This layer involves anything and everything that’s user accessible or directly connected to the user-interface. For presentation layer, a full-stack developer needs to be proficient in HTML, CSS or Javascript like front-end technologies. An added expertise in JS libraries like
Angular or React JS
shall be really helpful to march ahead in this career. Business Logic layer( or the Back-End) If the front-end deals with
user-interface
, the back-end deals with everything other than that. It basically deals with data validation and is concerned to the core-logic that makes things work. For the logic layer, stack developers must possess a fluency in different programming languages like Python, Ruby, Java, PHP and .net. A skill-set in frameworks like Django and Flask would be a bonus.
Database Layer The central data part of the system application usually concerned with database management. It constitutes how the data is created, extracted, read, updated or deleted from the database. To master this layer, a fluency in Database Management System technologies like MongoDB, Oracle, Postgre SQL, mySQL etc. Is a must. Full stack Developers: Other useful skills
Those above discussed are the must required skills in order to be a full-stack developer but other than that there exists a list of other skills that are recommended to become a successful full-stack developer. So, lets have a look:
A full-stack developer should have a basic designing skill-set and should understand UI/UX design-sets
For better administrating of servers, a decent background in Linux may be really helpful
A full-stack developer should have achieved a mastery in APIs and web-services like REST or SOAP.
A stack developer should be aware of and familiar with all the various components that are needed in the making of a final product
An in-depth understanding of Data structure and Algorithm is also required in case someone aspires to be a professional Full-stack developer
Other than that, a full-stack developer should have an awareness of security standards, the ability to write Quality unit tests, knowledge of GIT, Version Control Systems and much more. As Daniel Broski said
“Being a Full-Stack Developer doesn’t mean that you have necessarily mastered everything required to work with the front-end or back-end, but it means that you are able to work on both sides and understand what is going on when building an application,”So far, we have discussed what a full-stack developer means, what he does and what skills are required to be a full-stack developer. It’s time to move to the interesting part- what does a full-stack developer brings to the table I.e. an analysis on the advantages and disadvantages one can have with having a full-stack developer in their team. So, lets begin with the good part: the advantages! ADVANTAGES OF FULL-STACK DEVELOPERS
We have already seen what a full-stack developer does. Lets now see one by one about the benefits companies can reap by having a full-stack developer-: 1. VersatilityA full-stack developer possesses a professional skill-set in both front-end and back-end, thus enabling them to easily switch between client and server side. This provides a much-needed versatility and prevents loss in quality due to gaps in communication or background knowledge 2. Quick-LearnersFull-stack developers have a lot of skills and they must have spent significant time in learning those skills. This experience of learning makes them quick-learners who learn from their mistakes very swiftly and therefore, good for the company. 3. Cost-SavingA full-stack developer can fulfill a lot of roles in the organization and hence can save you bucks. He can be your front-end developer, a back-end developer or a designer: thus saving you from the cost of hiring all of them individually. This can be incredibly useful if you want a MVP(Minimum Viable Product) out soon. 4. Updated with latest technologyA full-stack developer is familiar with most of the technologies in the market. The web-development industry has always seen new technologies being introduced in the industry at regular intervals. Having a knowledge of the related technologies make these developers better at upgrading to new technologies. 5. Best in troubleshootingHaving an all-round understanding of almost all the technologies involved, a full-stack developer has the potential to identify the root of any problem, thus enabling the organisation to have long-term solutions. 6. Can assume ownership- As already discussed, a full-stack developer is familiar with most of the technologies required in product development. So, they are capable of taking the ownership for the complete design and implementation process. For startups, they can take the entire accountability for MVP development. Disadvantages to full-stack developers Despite all the versatility and the cost-effectiveness the full-stack developers provide, there do exist some disadvantages with having them-: 1.Less skills than specialists Being a Jack of all trades also mean that you are a master of none. This means full-stack developers can be able to perform as good as a specialist in a separate language/domain, so one has to compromise a bit with quality 2.Can’t catch up with all technologiesBeing a full-stack developer requires you to work on many domains at the same time. Despite being a quick learner, it’s incredibly difficult for these developers to be up-to-date with all the latest technologies in all these domains. 3.Dependency on team membersA full-stack developer doesn’t have the capability and time to deep-dive into problems of specific areas. So, when a very difficult problem pops out in specific languages, they have to look out for their team members. Also, bringing up different technologies together also stacks their disadvantages together. This also is a big disadvantage with full-stack developers. So, after discussing the advantages and disadvantages, now we shall look a the industry demand of full-stack developers and is it increasing or decreasing with time. DEMAND OF FULL-STACK DEVELOPERS
From startups to big MNCs, the versatility of full-stack developers is surely luring everyone today. According to LinkedIn’s Emerging Jobs Report, there has been a rise of 35% in the number of jobs for full-stack developers every year since 2015, and it ranks as the 4th most emerging job on the same coveted list. Supporting the trend, Indeed also ranks full-stack developers as 2nd best job by demand and remuneration while U.S. Bureau of Labor Statistics reports’ cite an enormous rise from 1,35,000 to 8,53,000 jobs as full-stack developers in 2024. One thing is pretty clear- the demand for full stack developers is higher than ever and this trend doesn’t seem to stop soon. A
possible supply-demand gap
can be an obstacle in future but if one is properly skilled, that shouldn’t be a big problem. ConclusionWe have seen in detail what a full-stack developer does, its advantages and disadvantages and the industry demands too. One thing is obvious and the industry demands support it too- The advantages provided by a full-stack developer far outweighs its disadvantages and this profession indeed is at an all-time high.
Contact us
to be on the forefront of innovations coming to disrupt the energy sector and embrace the upcoming industry shift.
0 notes
Text
MOST CONVIENENT VIDEO CONFERENCING TOOLS
In this article, Claudio Luis Vera explains what to remain in mind once choosing between video conferencing tools to be told everyone on your team — alongside those with disabilities.
With us all suddenly functioning from direct the COVID era, most folks have had to create some fast selections from an enormous type of video conferencing and collaboration tools. However do all of those apps work well for everyone? If you have got a workfellow or a student with an incapacity, would they be ready to participate as well? If you’ve had incapacity yourself — or if you're employed in government or education — you’ve in all probability two-faced this question already. If not, concentrate, as a result of the incorrect selection might leave your organization liable to a discrimination legal proceeding. With the correct apps, engaging from house is a blessing for those with incapacity. If you can’t drive, you not have to be compelled to have confidence poor transportation like para transit or pricey ride-share services. engaging from home permits you to attend to your medical wants in ways in which can be riotous in associate workplace, like running a nebulizer or exploitation associate IV. Otherwise you could avoid the effort of navigating a building that’s not really accessible. With the incorrect tools, an individual with a severe incapacity may very well expertise new barriers. They may be disregarded of conferences and different styles of collaboration, which will produce vital liability for the leader. “When people with disabilities are excluded because a product is inaccessible, it’s not only frustrating, but it [also] affects our colleagues and clients that work with us.” — Lynette Frison, screen reader user Most folks create a typical mistake we have a tendency to have large meetings , giant conferences or on-line events: we assume that everybody WHO attends are totally ready to participate. Unless you recognize everyone’s ability level — like together with your immediate co-workers — you must rise if somebody wants accommodations or assume that somebody attending could have problem seeing, hearing, or operating a mouse.
Zoom: The Favorite For Accessibility
Ask anyone within the incapacity community concerning video conferencing tools, and that they can virtually definitely purpose you to Zoom. There’s no shortage of favorable opinions and anecdotal support for rivet the incapacity community, because the app incorporates a name for providing a systematically high level of access. In fact, ninety two listed Zoom as their tool of alternative in a very survey conducted by Fable, associate accessibility testing firm that attracts testers from a range of various disabilities. An app’s accessibility comes from making certain that the app’s practicality works for everybody, together with those victimization helpful technologies like screen readers, magnification, and captions. Most software system developers don’t take a look at their apps completely for compatibility with helpful technologies or for usability with folks with disabilities. Even the easy task of connection a gathering will gift a roadblock if the app hasn’t been developed with accessibility in mind. As an example, spare preference dialogs once coming into a gathering will block a blind man that’s employing a screen reader from attending. Zoom offers the convenience of clicking on associate email link and permitting the participant to affix a gathering at once. “You follow the link and that’s it”, says Eric pin, director of technology for the beacon of Broward, a corporation for the blind and visually impaired. The simplicity of Zoom’s one-click sign-on belies the depth of the appliance behind it. Zoom’s product philosophy favors universal style over separate applications for various user sorts. The result's associate app that's straightforward to be told for first-time use, however has layers of further options for people who invest the time in changing into power users.
Advanced Roles And Features
Almost all video conferencing apps have 3 completely different roles that a user will play: host, presenter, and participant. The names of those roles might vary with the app, however the functions are fairly standard: a bunch works because the master of ceremonies and manages the permissions; a presenter may be a speaker or panelist and infrequently uses screen sharing. Naturally, playing host has the best practicality associated requires the best knowledge of an app. For that reason, it’s the foremost tough role to support accessibly, and Zoom supports it quite well.
Jonathan Mosen, a blind podcaster from New Seeland, has created associate in-depth audio book titled Meet Pine Tree State Accessibly with tutorials that teach straightforward to advanced tasks to fellow blind Zoom users. These embrace hosting Zoom conferences, conducting screen sharing, in addition as doing installations, and optimizing the settings.
Settings And Security
Zoom permits users to tailor the app to their wants through the app’s intensive settings menus. If something, Zoom is that the Swiss Army knife of video conferencing tools with a setting for each conceivable facet of the appliance. At the pharos of Broward, the IT team has taken advantage of this by making one account with settings aimed toward the blind, and another account with completely different settings for low-vision users.
In fact, there are seventy settings at intervals the desktop shopper, and another ninety five obtainable through Zoom’s advanced settings net program. With one hundred sixty five settings, it’s simple for any product to stumble, particularly once it involves obtaining the default settings right.
Several of the protection problems came from excessively lax defaults, like conferences not requiring passwords, or re-using personal meeting area IDs for convenience.
Zoom doesn’t permit settings to be saved offline or shared — nevertheless. In a perfect world, power users within the incapacity community might produce settings profiles that are tailored for specific disabilities and share them with others United Nations agency are less practiced with Zoom.
Different Use Cases For Accessible Conferencing
VIDEO WITH WORK CHAT
With stay-at-home orders in place, many teams are finding themselves making further use of rib work chat throughout the day. Like associate email shopper, this type of application is one that you’d leave on all the time, so your interactions aren’t restricted to the length of an online meeting.
Slack could be a vastly in style app for rib work chat that gives the power to decision another member during a video decision. It’s nice for spontaneous video conversations, and its massive daring buttons and resizable text are useful for users with moderately low vision. However, the Slack interface presents challenges to screen reader users and people with serious vision impairments, like keeping track of that Slack community that you’re in once the UI is exaggerated
If you're employed in a corporation with Associate in Nursing workplace 365 Enterprise license, Microsoft groups is another to Slack, with its integration into different workplace apps for calendaring and file sharing. The video calls on groups will embody many participants, and they’re the app of selection within Microsoft. Groups is additionally favored over Slack by several blind and low-vision users. ONE-TO-ONE VIDEO
People use video conferencing tools in a very sort of alternative ways, counting on the case and therefore the physical skills of the participants. If you’re conducting employment interview tho', it’s crucial to grasp beforehand if the duty candidate wants accommodations or if they can’t work along with your platform of selection. Failure to produce a viable different may land you in a very discrimination suit. One-to-one video calls with apps like FaceTime are well-suited for therapists and different freelance aid suppliers. They’re additionally a superb vehicle for those that communicate exploitation signing, as illustrated on the Apple accessibility web site.
USING CAPTIONS
But what if one amongst the participants doesn’t apprehend sign language? In this case, a deaf user would enjoy the automated captions that are on the market in Google Meet. Mistreatment captions as easy as clicking on the menu within the bottom right corner and clicking on the “Turn on captions” menu item. Captions seem — however solely on the devices that have them turned on — in order that they don’t gift a distraction to attendees that don’t wish them.
Captions are a lifeline for the deaf and in addition the hard of hearing, and are useful to those participants World Health Organization would like to stay their audio turned off or World Health Organization are in a very screaming state of affairs. They’re also helpful for people who aren’t native speakers of the language that’s being spoken. Auto-captions may be satisfactory for a native speaker of American or Australian English — and if you’re OK with homonyms like “meat” or “meet” being mixed up sometimes. However if the speaker incorporates a durable accent or a speech impairment, then the accuracy of the captions drops considerably. There’s much debate over how much accuracy is needed for captions to be viable. in step with Kristina country, Associate in Nursing accessibility knowledgeable at the University of Massachusetts. When auto-generated captions get below ninetieth accuracy, they will be a heavy annoyance that has won them the nickname of “captions” within the incapacity community. For that reason, it’s necessary to forever opt for a product that enables users to show the captions off on their finish. Avoid this simple mistake: don’t use auto-captions in PowerPoint or Google Slides if you’re presenting remotely. Limit their use to measure, in-person conferences instead. By having the captions on the presenter finish, they become a part of the meeting’s video stream and can’t be turned off by the opposite attendees. If you’re recording the presentation, then the wrong captions become associate degree ineradicable a part of your recording. Also, PowerPoint and Google Slides solely transcribe the presenter’s audio, deed something spoken by the opposite participants out of the captions. Before the COVID pandemic hit, Zoom was getting ready to incorporate Live Transcription, Associate in nursing automatic captioning feature, in its Enterprise arrange. The feature is battery-powered by Otter.ai, a man-made administrative body that gives period of time machine-controlled captioning and identifies the speaker like Google Meet. With the 30-fold growth of latest accounts, though, Zoom was compelled to delay the launch of Live Transcription thus as to not tax its infrastructure. within the meanwhile, you'll be able to still get constant practicality by running Otter.ai through Zoom’s API for third-party captioning services. however that requires Associate in Nursing Otter for groups account for a minimum of three users at $30/month every. One necessary piece of recommendation, though: If you’re trying to host a conference or an outsized public event over the net, you must not consider auto-captions, however take into account hiring a live human captioned instead. If you utilize Zoom, there’s another profit, too: your meeting participants are ready to scroll back through the captions and skim any elements they'll have incomprehensible.
A Word About WebEx
WebEx has gained loads of market share within the massive enterprise market, notably with its integration with Cisco’s on-the-scene video conferencing instrumentality. WebEx is additionally tightly certain with Microsoft Outlook through the WebEx Productivity Tools package. once considering these mixtures, WebEx offers mixed levels of accessibility for users of various skills. For sighted and low-vision users UN agency will use a mouse, WebEx’s integrations are quite helpful. However, once a participant enters a gathering, WebEx usually throws pop-up dialogs to verify their audio and video decisions, that can’t be operated while not a inform device. Outlook’s Calendar and Meeting interfaces additionally fail to supply keyboard access, more block somebody UN agency can’t work a mouse from accessing a gathering. If your enterprise has deaf and deaf members, WebEx willn’t provide automatic captions however it does provide a media viewer window wherever a person's captioner will kind what's spoken by a presenter throughout a gathering. WebEx conjointly provides transcription services for recorded conferences for patrons WHO have Network based mostly Recordings enabled. WebEx’s daring visual style works well for folks that have low vision however aren't blind. “The text in WebEx is simple to examine visually and works well once utilizing screen magnification software package. The settings in WebEx are intuitive and straightforward to work out,” says Elizabeth Novak, a tester with Fable. For those users WHO are blind and have confidence screen readers, though, WebEx presents varied barriers. Several of its interface parts have missing or confusing labels. Others can’t be reached with a keyboard.
WebEx’s inconsistent support for screen readers has LED to a proceeding against one amongst its customers: in Oct 2019, a blind litigator in Massachusetts sued her leader for not providing accessible alternatives like Zoom for WebEx conferences. Beacon Health choices, the leader, was exploitation.
WebEx for virtual conferences and necessary worker coaching during which Amy Ruell, the litigator, was unable to participate. The case remains in progress at the time of this writing. One of the quirks of digital accessibility lawsuits is that they're seldom filed against software package manufacturers or implementers. Instead, they're nearly always filed against the organization that purchases the software package and makes it out there to its customers, employees, and different constituents. The courts’ reasoning is that the organization ought to be conducting due diligence in vetting the product that it uses.
Judging Apps By Their Accessibility Pages
If you’re the one deciding that video conferencing platform to use in your organization, the dearth of formal studies and also the constant amendment can cause challenges. One great way to measure a company’s commitment to accessibility is to seem for AN accessibility page on their web site. Usually, it’s announce as a link within the footer of each page. an organization that's a minimum of awake to accessibility can have a announce accessibility policy. There are a few of firms that require to satisfy accessibility standards quite strictly and take their documentation much more.These firms can post Voluntary Product Accessibility example (VPAT) statements to satisfy Section 508 needs for marketing to the govt. or educational activity. VPAT statements is a goldmine of accessibility compliance data, and will be reviewed by anyone answerable of creating a getting call.
Zoom
and
WebEx
both provide extensive VPAT statements on their websites with detailed information on accessibility. These disclosure statements classify the level of support for users with disabilities and assistive technologies into four categories
Supports
Supports With Exceptions
Does Not Support
Not Applicable
From these options, anything other than “Supports” should be looked at carefully or treated as a potential problem area. A real red flag is once a corporation doesn't have a denote policy, and wherever a look for “accessibility” yields results that are unrelated to disabilities or helpful technologies. This is often the case with Crowdcast, wherever the results for “access” are associated with property and security. With Jitsi, developers contribute their efforts to assembling Associate in Nursingd refinement the appliance as an ASCII text file project. However, accessibility at Jitsi is sparsely resourced:
While this doesn’t help a person with a disability who may want to use Jitsi, it does present opportunities to developers looking to contribute where they can make a large social impact.
If associate degree app has advanced options or practicality that’s in some way connected to video conferencing, then support will be uneven additionally. This usually the case with polling, Q&A and alternative subsidiary options, even with Zoom. For that merchandise that do post VPATs on their websites, you'll be able to see that options are problematic. a decent rule of thumb would be to avoid these options once accessibility may be a concern.
Building Accessible Products
How do the manufacturers of video conferencing platforms produce a product that’s actually accessible for all? At Zoom accessibility is treated as a core worth, starting with business executive Eric Yuan. in keeping with Alex Mooc, Zoom’s accessibility lead, “that govt buy-in trickles right down to each team leader, each platform. each platform owner is answerable for these accessibility problems.” the merchandise groups are organized in order that accessibility specialists are embedded into each development team, in contrast to most alternative firms wherever accessibility comes in as oversight from a separate entity. Zoom has quick unharness cycles, wherever the merchandise is tested for accessibility as it’s engineered. Zoom’s engineers aren’t essentially well-versed in accessibility once they’re employed; however they’re expected to find out quickly from the company’s intensive internal knowledge.
Most firms style and build their product for his or her abled users, ANd may take into account disabled users as an afterthought, if at all. the alternative is true at Zoom: accessibility is treated as a part of the product’s usability for all users, abled and otherwise. “Someone World Health Organization is disabled is sort of a canary in an exceedingly coalpit,” says Mooc, as a result of partitioning problems that they encounter helps with usability for all alternative users. In alternative words, accessibility may be a suggests that to deliver the resistance, easy-to-use expertise that Zoom strives for. Zoom additionally seeks out feedback from individuals within the incapacity community, leaning heavily on its relationships with instructional establishments just like the University of Washington. a number of Mooc’s analysis involves attending to disabled users’ homes and perceptive how they work. With stay-at-home orders and social distancing, though, this sort of analysis has been placed on hold.
Of all the ways that to achieve insight into a product’s accessibility, the simplest is to possess live user testing by folks with disabilities. Fable technical school Labs uses Zoom nearly completely to conduct practical testing remotely with participants United Nations agency are blind, have low vision, or have quality impairments and admit helpful technologies like switch systems and voice navigation. However doing this kind of testing remotely presents its own technical challenges and requires tons of talent and knowledge of hardware to conduct with success.
This could cause elaborate workarounds with multiple devices and video feeds. Ideally, there would be a mixing-board-style product to handle multiple feeds in an exceedingly remote association; however that’s not in Zoom’s roadmap.
Growth And Change
Over the past few months, each Zoom and Google Meet have big from ten million users to over three hundred million daily participants every. The unforeseen explosion in quality has attracted malicious users UN agency found ways in which to hijack insecure conferences in focus a apply referred to as “zoom-bombing”. The few incidents generated news stories that became present within the fourth estate, raising considerations concerning Zoom’s security. Some organizations like Google and also the big apple town establishment have gone as so much as prohibition Zoom from their computers. For many within the incapacity community, this flip of events has had associate degree unfortunate impact on access. If organizations ban Zoom from their computers, then conferences would like to be conducted and categories would like to be instructed on-line victimization less accessible product, which may mean commercialism a usable-but-insecure platform for one that merely can’t be used. “Security is very important, but there's no point trying to use an inaccessible tool no matter how secure it is.” — Erik Burggraaf, screen reader userFortunately, Zoom has been fast to retort with a series of security fixes at intervals a few of weeks. The excessively lax defaults within the app’s a hundred sixty five settings were tightened up, and a range of changes were created to the user expertise. Currently it’s largely up to users to update their Zoom apps, settings, and desktop purchasers. Since the start of the COVID pandemic, the speed of development in video conferencing has accelerated in an exceedingly business that already had frequent releases. Major product announcements are happening weekly, and Zoom is emotional patches nearly daily, in conjunction with a serious upgrade to zoom five.The net: if you employ any video conferencing software package, you must be diligent regarding change your software package as overtimes as you'll be able to — or enabling auto-updates on your device. You will even notice that a heavy accessibility issue may be resolved with an easy software package update. The future is wanting promising tho', in step with accessibility tester Shane: “Accessibility is recouping daily at intervals on-line communication tools. However, some still would like work to be utterly comprehensive to all or any folks.” We will be happy to answer your questions on designing, developing, and deploying comprehensive enterprise web, mobile apps and customized software solutions that best fit your organization needs. As a reputed Software Solutions Developer we have expertise in providing dedicated remote and outsourced technical resources for software services at very nominal cost. Besides experts in full stacks We also build web solutions, mobile apps and work on system integration, performance enhancement, cloud migrations and big data analytics. Don’t hesitate to
get in touch with us!
#b2bservices
#b2b ecommerce
#b2bsales
#b2b marketing agency
0 notes
Text
MOST CONVIENENT VIDEO CONFERENCING TOOLS
In this article, Claudio Luis Vera explains what to remain in mind once choosing between video conferencing tools to be told everyone on your team — alongside those with disabilities.
With us all suddenly functioning from direct the COVID era, most folks have had to create some fast selections from an enormous type of video conferencing and collaboration tools. However do all of those apps work well for everyone? If you have got a workfellow or a student with an incapacity, would they be ready to participate as well? If you’ve had incapacity yourself — or if you're employed in government or education — you’ve in all probability two-faced this question already. If not, concentrate, as a result of the incorrect selection might leave your organization liable to a discrimination legal proceeding. With the correct apps, engaging from house is a blessing for those with incapacity. If you can’t drive, you not have to be compelled to have confidence poor transportation like para transit or pricey ride-share services. engaging from home permits you to attend to your medical wants in ways in which can be riotous in associate workplace, like running a nebulizer or exploitation associate IV. Otherwise you could avoid the effort of navigating a building that’s not really accessible. With the incorrect tools, an individual with a severe incapacity may very well expertise new barriers. They may be disregarded of conferences and different styles of collaboration, which will produce vital liability for the leader. “When people with disabilities are excluded because a product is inaccessible, it’s not only frustrating, but it [also] affects our colleagues and clients that work with us.” — Lynette Frison, screen reader user Most folks create a typical mistake we have a tendency to have large meetings , giant conferences or on-line events: we assume that everybody WHO attends are totally ready to participate. Unless you recognize everyone’s ability level — like together with your immediate co-workers — you must rise if somebody wants accommodations or assume that somebody attending could have problem seeing, hearing, or operating a mouse.
Zoom: The Favorite For Accessibility
Ask anyone within the incapacity community concerning video conferencing tools, and that they can virtually definitely purpose you to Zoom. There’s no shortage of favorable opinions and anecdotal support for rivet the incapacity community, because the app incorporates a name for providing a systematically high level of access. In fact, ninety two listed Zoom as their tool of alternative in a very survey conducted by Fable, associate accessibility testing firm that attracts testers from a range of various disabilities. An app’s accessibility comes from making certain that the app’s practicality works for everybody, together with those victimization helpful technologies like screen readers, magnification, and captions. Most software system developers don’t take a look at their apps completely for compatibility with helpful technologies or for usability with folks with disabilities. Even the easy task of connection a gathering will gift a roadblock if the app hasn’t been developed with accessibility in mind. As an example, spare preference dialogs once coming into a gathering will block a blind man that’s employing a screen reader from attending. Zoom offers the convenience of clicking on associate email link and permitting the participant to affix a gathering at once. “You follow the link and that’s it”, says Eric pin, director of technology for the beacon of Broward, a corporation for the blind and visually impaired. The simplicity of Zoom’s one-click sign-on belies the depth of the appliance behind it. Zoom’s product philosophy favors universal style over separate applications for various user sorts. The result's associate app that's straightforward to be told for first-time use, however has layers of further options for people who invest the time in changing into power users.
Advanced Roles And Features
Almost all video conferencing apps have 3 completely different roles that a user will play: host, presenter, and participant. The names of those roles might vary with the app, however the functions are fairly standard: a bunch works because the master of ceremonies and manages the permissions; a presenter may be a speaker or panelist and infrequently uses screen sharing. Naturally, playing host has the best practicality associated requires the best knowledge of an app. For that reason, it’s the foremost tough role to support accessibly, and Zoom supports it quite well.
Jonathan Mosen, a blind podcaster from New Seeland, has created associate in-depth audio book titled Meet Pine Tree State Accessibly with tutorials that teach straightforward to advanced tasks to fellow blind Zoom users. These embrace hosting Zoom conferences, conducting screen sharing, in addition as doing installations, and optimizing the settings.
Settings And Security
Zoom permits users to tailor the app to their wants through the app’s intensive settings menus. If something, Zoom is that the Swiss Army knife of video conferencing tools with a setting for each conceivable facet of the appliance. At the pharos of Broward, the IT team has taken advantage of this by making one account with settings aimed toward the blind, and another account with completely different settings for low-vision users.
In fact, there are seventy settings at intervals the desktop shopper, and another ninety five obtainable through Zoom’s advanced settings net program. With one hundred sixty five settings, it’s simple for any product to stumble, particularly once it involves obtaining the default settings right.
Several of the protection problems came from excessively lax defaults, like conferences not requiring passwords, or re-using personal meeting area IDs for convenience.
Zoom doesn’t permit settings to be saved offline or shared — nevertheless. In a perfect world, power users within the incapacity community might produce settings profiles that are tailored for specific disabilities and share them with others United Nations agency are less practiced with Zoom.
Different Use Cases For Accessible Conferencing
VIDEO WITH WORK CHAT
With stay-at-home orders in place, many teams are finding themselves making further use of rib work chat throughout the day. Like associate email shopper, this type of application is one that you’d leave on all the time, so your interactions aren’t restricted to the length of an online meeting.
Slack could be a vastly in style app for rib work chat that gives the power to decision another member during a video decision. It’s nice for spontaneous video conversations, and its massive daring buttons and resizable text are useful for users with moderately low vision. However, the Slack interface presents challenges to screen reader users and people with serious vision impairments, like keeping track of that Slack community that you’re in once the UI is exaggerated
If you're employed in a corporation with Associate in Nursing workplace 365 Enterprise license, Microsoft groups is another to Slack, with its integration into different workplace apps for calendaring and file sharing. The video calls on groups will embody many participants, and they’re the app of selection within Microsoft. Groups is additionally favored over Slack by several blind and low-vision users. ONE-TO-ONE VIDEO
People use video conferencing tools in a very sort of alternative ways, counting on the case and therefore the physical skills of the participants. If you’re conducting employment interview tho', it’s crucial to grasp beforehand if the duty candidate wants accommodations or if they can’t work along with your platform of selection. Failure to produce a viable different may land you in a very discrimination suit. One-to-one video calls with apps like FaceTime are well-suited for therapists and different freelance aid suppliers. They’re additionally a superb vehicle for those that communicate exploitation signing, as illustrated on the Apple accessibility web site.
USING CAPTIONS
But what if one amongst the participants doesn’t apprehend sign language? In this case, a deaf user would enjoy the automated captions that are on the market in Google Meet. Mistreatment captions as easy as clicking on the menu within the bottom right corner and clicking on the “Turn on captions” menu item. Captions seem — however solely on the devices that have them turned on — in order that they don’t gift a distraction to attendees that don’t wish them.
Captions are a lifeline for the deaf and in addition the hard of hearing, and are useful to those participants World Health Organization would like to stay their audio turned off or World Health Organization are in a very screaming state of affairs. They’re also helpful for people who aren’t native speakers of the language that’s being spoken. Auto-captions may be satisfactory for a native speaker of American or Australian English — and if you’re OK with homonyms like “meat” or “meet” being mixed up sometimes. However if the speaker incorporates a durable accent or a speech impairment, then the accuracy of the captions drops considerably. There’s much debate over how much accuracy is needed for captions to be viable. in step with Kristina country, Associate in Nursing accessibility knowledgeable at the University of Massachusetts. When auto-generated captions get below ninetieth accuracy, they will be a heavy annoyance that has won them the nickname of “captions” within the incapacity community. For that reason, it’s necessary to forever opt for a product that enables users to show the captions off on their finish. Avoid this simple mistake: don’t use auto-captions in PowerPoint or Google Slides if you’re presenting remotely. Limit their use to measure, in-person conferences instead. By having the captions on the presenter finish, they become a part of the meeting’s video stream and can’t be turned off by the opposite attendees. If you’re recording the presentation, then the wrong captions become associate degree ineradicable a part of your recording. Also, PowerPoint and Google Slides solely transcribe the presenter’s audio, deed something spoken by the opposite participants out of the captions. Before the COVID pandemic hit, Zoom was getting ready to incorporate Live Transcription, Associate in nursing automatic captioning feature, in its Enterprise arrange. The feature is battery-powered by Otter.ai, a man-made administrative body that gives period of time machine-controlled captioning and identifies the speaker like Google Meet. With the 30-fold growth of latest accounts, though, Zoom was compelled to delay the launch of Live Transcription thus as to not tax its infrastructure. within the meanwhile, you'll be able to still get constant practicality by running Otter.ai through Zoom’s API for third-party captioning services. however that requires Associate in Nursing Otter for groups account for a minimum of three users at $30/month every. One necessary piece of recommendation, though: If you’re trying to host a conference or an outsized public event over the net, you must not consider auto-captions, however take into account hiring a live human captioned instead. If you utilize Zoom, there’s another profit, too: your meeting participants are ready to scroll back through the captions and skim any elements they'll have incomprehensible.
A Word About WebEx
WebEx has gained loads of market share within the massive enterprise market, notably with its integration with Cisco’s on-the-scene video conferencing instrumentality. WebEx is additionally tightly certain with Microsoft Outlook through the WebEx Productivity Tools package. once considering these mixtures, WebEx offers mixed levels of accessibility for users of various skills. For sighted and low-vision users UN agency will use a mouse, WebEx’s integrations are quite helpful. However, once a participant enters a gathering, WebEx usually throws pop-up dialogs to verify their audio and video decisions, that can’t be operated while not a inform device. Outlook’s Calendar and Meeting interfaces additionally fail to supply keyboard access, more block somebody UN agency can’t work a mouse from accessing a gathering. If your enterprise has deaf and deaf members, WebEx willn’t provide automatic captions however it does provide a media viewer window wherever a person's captioner will kind what's spoken by a presenter throughout a gathering. WebEx conjointly provides transcription services for recorded conferences for patrons WHO have Network based mostly Recordings enabled. WebEx’s daring visual style works well for folks that have low vision however aren't blind. “The text in WebEx is simple to examine visually and works well once utilizing screen magnification software package. The settings in WebEx are intuitive and straightforward to work out,” says Elizabeth Novak, a tester with Fable. For those users WHO are blind and have confidence screen readers, though, WebEx presents varied barriers. Several of its interface parts have missing or confusing labels. Others can’t be reached with a keyboard.
WebEx’s inconsistent support for screen readers has LED to a proceeding against one amongst its customers: in Oct 2019, a blind litigator in Massachusetts sued her leader for not providing accessible alternatives like Zoom for WebEx conferences. Beacon Health choices, the leader, was exploitation.
WebEx for virtual conferences and necessary worker coaching during which Amy Ruell, the litigator, was unable to participate. The case remains in progress at the time of this writing. One of the quirks of digital accessibility lawsuits is that they're seldom filed against software package manufacturers or implementers. Instead, they're nearly always filed against the organization that purchases the software package and makes it out there to its customers, employees, and different constituents. The courts’ reasoning is that the organization ought to be conducting due diligence in vetting the product that it uses.
Judging Apps By Their Accessibility Pages
If you’re the one deciding that video conferencing platform to use in your organization, the dearth of formal studies and also the constant amendment can cause challenges. One great way to measure a company’s commitment to accessibility is to seem for AN accessibility page on their web site. Usually, it’s announce as a link within the footer of each page. an organization that's a minimum of awake to accessibility can have a announce accessibility policy. There are a few of firms that require to satisfy accessibility standards quite strictly and take their documentation much more.These firms can post Voluntary Product Accessibility example (VPAT) statements to satisfy Section 508 needs for marketing to the govt. or educational activity. VPAT statements is a goldmine of accessibility compliance data, and will be reviewed by anyone answerable of creating a getting call.
Zoom
and
WebEx
both provide extensive VPAT statements on their websites with detailed information on accessibility. These disclosure statements classify the level of support for users with disabilities and assistive technologies into four categories
Supports
Supports With Exceptions
Does Not Support
Not Applicable
From these options, anything other than “Supports” should be looked at carefully or treated as a potential problem area. A real red flag is once a corporation doesn't have a denote policy, and wherever a look for “accessibility” yields results that are unrelated to disabilities or helpful technologies. This is often the case with Crowdcast, wherever the results for “access” are associated with property and security. With Jitsi, developers contribute their efforts to assembling Associate in Nursingd refinement the appliance as an ASCII text file project. However, accessibility at Jitsi is sparsely resourced:
While this doesn’t help a person with a disability who may want to use Jitsi, it does present opportunities to developers looking to contribute where they can make a large social impact.
If associate degree app has advanced options or practicality that’s in some way connected to video conferencing, then support will be uneven additionally. This usually the case with polling, Q&A and alternative subsidiary options, even with Zoom. For that merchandise that do post VPATs on their websites, you'll be able to see that options are problematic. a decent rule of thumb would be to avoid these options once accessibility may be a concern.
Building Accessible Products
How do the manufacturers of video conferencing platforms produce a product that’s actually accessible for all? At Zoom accessibility is treated as a core worth, starting with business executive Eric Yuan. in keeping with Alex Mooc, Zoom’s accessibility lead, “that govt buy-in trickles right down to each team leader, each platform. each platform owner is answerable for these accessibility problems.” the merchandise groups are organized in order that accessibility specialists are embedded into each development team, in contrast to most alternative firms wherever accessibility comes in as oversight from a separate entity. Zoom has quick unharness cycles, wherever the merchandise is tested for accessibility as it’s engineered. Zoom’s engineers aren’t essentially well-versed in accessibility once they’re employed; however they’re expected to find out quickly from the company’s intensive internal knowledge.
Most firms style and build their product for his or her abled users, ANd may take into account disabled users as an afterthought, if at all. the alternative is true at Zoom: accessibility is treated as a part of the product’s usability for all users, abled and otherwise. “Someone World Health Organization is disabled is sort of a canary in an exceedingly coalpit,” says Mooc, as a result of partitioning problems that they encounter helps with usability for all alternative users. In alternative words, accessibility may be a suggests that to deliver the resistance, easy-to-use expertise that Zoom strives for. Zoom additionally seeks out feedback from individuals within the incapacity community, leaning heavily on its relationships with instructional establishments just like the University of Washington. a number of Mooc’s analysis involves attending to disabled users’ homes and perceptive how they work. With stay-at-home orders and social distancing, though, this sort of analysis has been placed on hold.
Of all the ways that to achieve insight into a product’s accessibility, the simplest is to possess live user testing by folks with disabilities. Fable technical school Labs uses Zoom nearly completely to conduct practical testing remotely with participants United Nations agency are blind, have low vision, or have quality impairments and admit helpful technologies like switch systems and voice navigation. However doing this kind of testing remotely presents its own technical challenges and requires tons of talent and knowledge of hardware to conduct with success.
This could cause elaborate workarounds with multiple devices and video feeds. Ideally, there would be a mixing-board-style product to handle multiple feeds in an exceedingly remote association; however that’s not in Zoom’s roadmap.
Growth And Change
Over the past few months, each Zoom and Google Meet have big from ten million users to over three hundred million daily participants every. The unforeseen explosion in quality has attracted malicious users UN agency found ways in which to hijack insecure conferences in focus a apply referred to as “zoom-bombing”. The few incidents generated news stories that became present within the fourth estate, raising considerations concerning Zoom’s security. Some organizations like Google and also the big apple town establishment have gone as so much as prohibition Zoom from their computers. For many within the incapacity community, this flip of events has had associate degree unfortunate impact on access. If organizations ban Zoom from their computers, then conferences would like to be conducted and categories would like to be instructed on-line victimization less accessible product, which may mean commercialism a usable-but-insecure platform for one that merely can’t be used. “Security is very important, but there's no point trying to use an inaccessible tool no matter how secure it is.” — Erik Burggraaf, screen reader userFortunately, Zoom has been fast to retort with a series of security fixes at intervals a few of weeks. The excessively lax defaults within the app’s a hundred sixty five settings were tightened up, and a range of changes were created to the user expertise. Currently it’s largely up to users to update their Zoom apps, settings, and desktop purchasers. Since the start of the COVID pandemic, the speed of development in video conferencing has accelerated in an exceedingly business that already had frequent releases. Major product announcements are happening weekly, and Zoom is emotional patches nearly daily, in conjunction with a serious upgrade to zoom five.The net: if you employ any video conferencing software package, you must be diligent regarding change your software package as overtimes as you'll be able to — or enabling auto-updates on your device. You will even notice that a heavy accessibility issue may be resolved with an easy software package update. The future is wanting promising tho', in step with accessibility tester Shane: “Accessibility is recouping daily at intervals on-line communication tools. However, some still would like work to be utterly comprehensive to all or any folks.” We will be happy to answer your questions on designing, developing, and deploying comprehensive enterprise web, mobile apps and customized software solutions that best fit your organization needs. As a reputed Software Solutions Developer we have expertise in providing dedicated remote and outsourced technical resources for software services at very nominal cost. Besides experts in full stacks We also build web solutions, mobile apps and work on system integration, performance enhancement, cloud migrations and big data analytics. Don’t hesitate to
get in touch with us!
0 notes