#mobile spy without access to phone
Explore tagged Tumblr posts
Text
CHYLDMONITOR Mobile Spy for Android

Get CHYLDMONITOR, the ultimate mobile spy solution tailored for Android devices. Seamlessly monitor phone activities, including call logs, messages, and app usage, all from a centralized control panel. With CHYLDMONITOR, you can ensure the safety of your children or enhance employee productivity by keeping an eye on their digital interactions. Experience top-notch Android monitoring today.
Protect and monitor effectively. Download CHYLDMONITOR for Android!
#mobile spy app#mobile spy software#mobile spy for android#mobile spy download#mobile spy without access to phone#mobile spy app hidden#mobile spy app undetectable#mobile spy parental control#mobile spy app with GPS tracking#mobile spy app features
0 notes
Text
Police identify 33,000 illegal cell phone monitoring during Bolsonaro government

The Federal Police has uncovered that a system used by the Brazilian Intelligence Agency (Abin), a federal government agency, conducted at least 33,000 illegal monitoring activities without any court authorization during the government of former President Jair Bolsonaro.
On October 20th, two employees responsible for the illegal use of the tool were arrested, with the Supreme Court issuing 25 search warrants as part of the investigation. The case centers on the misuse of the FirstMile system, an Israeli mobile device geolocation tool acquired by the Brazilian government in 2018.
According to investigations, 1,800 unauthorized accesses made by FirstMile were intended for spying on politicians, journalists, lawyers, Supreme Court judges, and Bolsonaro’s opponents. The list includes a man with the same name as Supreme Court Judge Alexandre de Moraes, which reinforces the suspicion that he was the target of the illegal scheme.
To avoid leaving traces, the employees responsible for the program, dubbed the “Abin tracking gang,” erased the vast majority of computer records. Nevertheless, the police managed to identify at least 33,000 instances of illegal monitoring activities carried out by Abin during Bolsonaro’s administration.
Continue reading.
11 notes
·
View notes
Text
This day in history

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me in TUCSON (Mar 9-10), then San Francisco (Mar 13), Anaheim, and more!

#15yrsago What could you buy with AIG’s record-smashing $62 billion loss? https://www.cnn.com/2009/BUSINESS/03/02/markets.whatlossbuys/index.html
#15yrsago Born to Kvetch: Yiddish as she is spoke https://memex.craphound.com/2009/03/02/born-to-kvetch-yiddish-as-she-is-spoke/
#15yrsago Britain’s vast cement “listening ears” designated a national landmark https://www.fastcompany.com/90135167/the-concrete-sound-mirrors-that-influenced-wwii-science-and-design
#10yrsago Phoenix cops arrest sex workers, detain them without trial in churches, pressure them to take deals without access to lawyers https://www.vice.com/en/article/av4eyb/in-arizona-project-rose-is-arresting-sex-workers-to-save-them
#10yrsago US Trade Rep can’t figure out if Trans-Pacific Partnership will protect the environment https://www.huffpost.com/entry/democrats-trans-pacific-partnership_n_4868262?1393531198=
#10yrsago Trustycon: how to redesign NSA surveillance to catch more criminals and spy on a lot fewer people https://www.youtube.com/watch?v=lkO8SNiDSw0
#5yrsago Study that claimed majority of Copyright Directive opposition came from the US assumed all English-language tweets came from Washington, DC https://memex.craphound.com/2019/03/02/study-that-claimed-majority-of-copyright-directive-opposition-came-from-the-us-assumed-all-english-language-tweets-came-from-washington-dc/
#5yrsago Improbably, a Black activist is now the owner and leader of the “National Socialist Movement,” which he is turning into an anti-racist group https://www.washingtonpost.com/dc-md-va/2019/03/01/how-black-man-outsmarted-neo-nazi-group-became-their-new-leader/
#5yrsago Coinbase bought a company founded by disgraced cybermercenaries from Hacking Team, and now Coinbase users are trying unsuccessfully to delete their accounts https://www.vice.com/en/article/xwb7xj/coinbase-users-struggle-to-delete-their-accounts-in-protest
#5yrsago Comcast assigned every mobile customer the same unchangeable PIN to protect against SIM hijack attacks: 0000 https://arstechnica.com/information-technology/2019/03/a-comcast-security-flub-helped-attackers-steal-mobile-phone-numbers/
#5yrsago The promise and peril of “sonification”: giving feedback through sound https://www.wired.com/story/sonification-era-of-aural-data/
#5yrsago Massive study finds strong correlation between “early affluence” and “faster cognitive drop” in old age https://www.pnas.org/doi/10.1073/pnas.1807679116
#5yrsago Oakland teachers’ union declares total victory after seven-day strike https://edsource.org/2019/tentative-agreement-reached-in-oakland-unified-teachers-strike/609342
#5yrsago Man-Eaters: Handmaid’s Tale meets Cat People in a comic where girls turn into man-eating were-panthers when they get their periods https://memex.craphound.com/2019/03/02/man-eaters-handmaids-tale-meets-cat-people-in-a-comic-where-girls-turn-into-man-eating-were-panthers-when-they-get-their-periods/
4 notes
·
View notes
Text
WhatsApp Spy Features for Child Safety

Going that extra mile and protecting your children is top-most priority for every parent. With great exposure to smartphones and technology, there is an obvious feeling of concern for parents to know what their child is up to.
With the help of a good parental control app you can track every move of your child. These apps were secretly to spy on phones and keep you updated with all the activities of your child. A phone spy app is one great way of keeping up with your child.
Kids online can come across all types of content and it could also include some inappropriate content which can be addictive as well as dangerous for your little one. A good phone spy app can help you to monitor your child’s device, giving you all the information.
Can a phone spy app help ?
A good spy app can make it simple and easy for you to keep your child safe against violating content and unwanted security threats. In today’s time, kids have a smartphone and internet access, being underage and having restrictions to certain activities is now merely a law but once you have easy access to the phone and internet there is every sort of content online.
Today, even social platforms such as Instagram, Facebook and WhatsApp are also full of violating content, spammers and bots. But you can rely on a good mobile spy app to ease your concern. You can keep track of your loved ones’ device and ensure that they do not engage with any inappropriate content.
We recommend that firstly if you witness your loved one engaging in any activity that is harmful for them or for your relationship with them, it’s better to have understanding and open communication with them. Especially with kids, if you try to impose any restrictions on them without a valid reason or in some cases even if your concern is valid, your loved one would be frustrated.
To avoid a challenging situation like this, you can try a spy app for android phone that not only gives you all the information you need but is also fully secure.
Which spy app to go for?
Let us give you a few insights of the app which is loved and recommended by parents. Onemonitar parental app is tried by not only parents but also people who want to ensure the safety of their loved ones in general. This spy phone application has 50+ features and we’ll highlight the most popular ones for you.
Onemonitar gives you options to listen to the calls through its hidden call recorder which provides high quality of audio. You can track the real-time location of the target device and know the whereabouts of your child, this ensures that they are not lying to you and even if they are, you know where they are remotely.
Talking about social media tracking, you can check the accounts of your child across all major social media. You can check their WhatsApp with the help of WhatsApp spy software, you can check their chats, calls and any media that is being exchanged with others. You can scroll through the Instagram and Facebook accounts and who they are interacting with, this will ensure that you are aware of if they are not interacting with any person that could be of danger to them.
Things to remember!
A spy app can be very helpful when you want to control or supervise the activities of your loved ones. With broader usage and multiple features, regardless of who your target is, a spy phone app is now welcomed and has come in use across the globe.
These solutions provide you 100% data protection and security and with a phone spy app like Onemonitar only you have the access to your control panel and nobody other than you can see your personal information. Also, their 24*7 support team is available for your assistance through live chats and calls.
You can use the spy app and ensure high security and safety for your dear ones. Happy monitoring with Onemonitar!
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy
2 notes
·
View notes
Text
Do You Want to Read your Kid’s Phone Text Messages? Many parents are curious to know what sort of text messages their kids, especially teens, receive. In the world of catfishing and sexting, text message monitoring is necessary to secure children from online molesters and perverts. There are multiple ways to read your teen’s text messages. The most convenient way is using a text message monitoring app or a mobile spy app. How to Read Your Teen’s Text Messages Secretly? Teenagers can't leave their houses without cell phones. Texting friends and family itself is not a harmful activity. But too much texting can either make your child phone addict or invite cyber dangers in real life. Today, it is typical among kids to use text acronyms for things they want to keep secret from their parents. Text message monitoring is a big step that parents must take to ensure their kids’ safety in the digital and physical world. No matter how close your teen is to his/her friends, as a parent, you have the instinct to detect the bad apples from your child’s social circle. So, is it really possible to read your kid’s text messages? Yes, it is. And for that, we recommend the world premium SMS tracker app TheWiSpy. In this article, we are going to mention how parents can utilize the incredible TWS app and monitor their kid’s text chats and other cell phone activities without much effort. Let’s begin! How to Monitor Text Messages with TheWiSpy App? TheWiSpy is a mobile phone monitoring app capable of recording all cell phone activities in hidden mode. It allows you to monitor the recorded details without even touching the monitored device. When it comes to text message monitoring, TheWiSpy records every text message (sent, received, draft, deleted) of your kid’s device and provides you with a comprehensive report on text message activities. You can not only spy on text messages but also discover contacts who frequently text your teen. Apart from text message tracking, TheWiSpy offers 20+ features that help parents monitor the online cyber activities of their children in complete secrecy. So let’s first explore how you can read your kid’s text messages with the TheWiSpy app. In the later section, we will mention other robust spying features of TheWiSpy app to give you a better overview of this fantastic mobile spy app. TheWiSpy Text Message Monitoring - A Steps-by-Step Guide: Spying on text messages with TheWiSpy app is very easy. Here is the step-by-step guide to spy on the text messages of your teens with TheWiSpy app. Step 1: Visit TWS's official website www.thewispy.com. Register yourself and purchase the right subscription. Step 2: Get access to your target device and install the TWS app on it. Configure the app as well. Step 3: Go to TheWiSpy control panel and log in to your registered ID. You can access the TWS dashboard from www.cp.thewispy.com/login. Step 4: Once logged in to your TWS account, choose “messages” from the sidebar menu. Step 5: Monitor text messages on your kid’s phone. TheWiSpy app offers a live demo of the app on TWS official website. You can always test the demo TWS app, even before purchasing the license. TheWiSpy app requires installation on the mobile or tablet you want to track. After which, the app allows you to track everything happening on your child’s phone/tablet. For TheWiSpy app installation, you must access your kid’s mobile phone or tablet for one time. It only requires a minimum of 5-minutes for the TWS app to get installed and configured on your target device. TheWiSpy Mobile Monitoring App - What Can It Do? TheWiSpy is a leading app popular for delivering top-notch cell phone monitoring and spying features. TheWiSpy app has not achieved much popularity out of thin air. It actually provides high-end functionality and seamless monitoring tools. Here are the qualities that make TheWiSpy a premium software to track mobile devices. High-End Compatibility: TheWiSpy is a robust app designed to monitor Android devices.
It is strongly compatible with Android cell phones and tablets. TheWiSpy can hack any Android device that runs the OS version of 4 or higher. Affordability: When it comes to pricing, TheWiSpy is the most affordable spy app in the online market. It provides its users with flexible subscription packages. The lightest subscription of the TWS app, known as the starter package, starts at only $9.99. While the basic subscription starting price is $19.99, and for premium packages, the pricing starts from $29.99. No Rooting: Unlike other Android monitoring spyware apps, TheWiSpy offers quality monitoring tools without rooting the target device. Rooting Android devices is a complicated process that might end in complete data loss. With TheWiSpy, there is no prerequisite of rooting the target Android device. Hidden Spy App: The TWS app is a hidden spy app. It means you can enjoy cell phone monitoring in stealth mode without letting your kids know. You can hide the TWS app icon, which makes monitoring your kids’ devices even easier. TheWiSpy Quality Features: Mobile spyware is nothing if it does not provide monitoring features that actually work. TheWiSpy features are one of a kind, enabling cell phone monitoring in real-time. Here is the list of powerful features of TheWiSpy app: Phone Call Recording Text Message Spying GPS Location Tracking Geofencing Call Logs Monitoring Contacts Monitoring Multimedia Monitoring Keylogging Screen Recording App Monitoring Surround Recording Camera Spying And many others. Cell phone monitoring has become common, especially in today’s technology-driven times. Parents are concerned about their kids' digital diet, and we must appreciate their interests. Nothing can help us better than mobile monitoring software to save juveniles from harmful digital content. Concluding Words Sending and receiving text messages is a simple way to communicate. Kids perhaps misuse technology by indulging in cyber nuisance like bullying, sexting, catfishing, and so on. Modern parents know they can protect their children from cyber dangers by monitoring their text conversations. The use of text message monitoring apps is increasing with the increase in the rate of cyber hazards. TheWiSpy is a famous monitoring app for providing text message tracking features and other mobile surveillance tools in real-time. So, when are you getting your TWS license?
0 notes
Text
The Invisible Eye: Exploring Cell Phone Spy Technology

In an era where technology governs our daily lives, the topic of cell phone spying has become both relevant and controversial. The rise of sophisticated software capable of infiltrating mobile devices has sparked discussions about security, ethics, and privacy. This article delves into the world of cell phone spying, shedding light on its methods, applications, and implications.
Understanding Cell Phone Spy Technology
Cell phone spy technology encompasses software and tools designed to monitor activities on a target device. These applications can track calls, text messages, GPS locations, internet activity, and even social media interactions. While the capabilities of these tools vary, their primary goal remains the same: to provide real-time information about the user’s activities.
The software operates covertly, often installed without the user's knowledge. Once installed, it sends data to a remote server where the information can be accessed by the person who deployed the software.
Common Uses of Spy Technology
Parental Monitoring:
Parents often use cell phone spy apps to ensure their children's safety. These tools help parents monitor who their children are communicating with and track their location, offering peace of mind in a world where online predators and cyberbullying are real threats.
Employee Oversight:
Employers might use such software to monitor company-issued devices, ensuring employees adhere to company policies. This can help prevent data breaches, safeguard intellectual property, and maintain productivity.
Relationship Concerns:
Some individuals turn to spy apps to confirm suspicions of infidelity in personal relationships. However, such use raises serious ethical questions about trust and consent.
Law Enforcement and Security:
Law enforcement agencies may use advanced spy technology to track criminals or gather intelligence in investigations, provided they operate within the legal framework.
Ethical and Legal Considerations
While the benefits of cell phone spy technology are evident, they are not without ethical and legal dilemmas. The use of such software without the consent of the person being monitored is a violation of privacy and, in many jurisdictions, illegal.
For example, secretly installing spy software on a partner's phone can lead to severe legal repercussions. In the workplace, employees have a right to know if their devices are being monitored. Similarly, while parents may have the best intentions, spying on children without open communication can lead to trust issues.
Legislation surrounding cell phone spy technology varies by country, but the common theme is consent. Without it, the use of such software is often deemed unlawful.
The Threat of Cybersecurity Breaches
The prevalence of cell phone spying also introduces significant risks. Many of these apps are created by unregulated entities, and using them can expose both the installer and the target to cyber threats. Personal information collected by these apps can be hacked, leaked, or sold, leading to identity theft and financial losses.
For individuals concerned about being spied on, there are steps to protect oneself. Regularly updating your device’s operating system, avoiding suspicious links or downloads, and using strong passwords can mitigate the risk of unauthorized surveillance.
Future of Cell Phone Spy Technology
As technology evolves, so do the capabilities of spy software. The integration of artificial intelligence (AI) could enhance monitoring features, such as identifying unusual behavior patterns or predicting actions. While these advancements could be beneficial in certain scenarios, they also amplify concerns about misuse.
On the other hand, the rise of privacy-centric technologies may counterbalance this trend. Companies are increasingly investing in encryption and security features to protect users from unauthorized surveillance. The ongoing battle between surveillance and privacy advocates will likely shape the future of this technology.
Conclusion
Cell phone spy technology is a double-edged sword. While it offers valuable tools for safety, productivity, and law enforcement, its misuse poses significant ethical and legal challenges. As this technology becomes more sophisticated, society must address the fine line between its responsible use and potential abuse.
The key lies in awareness, consent, and regulation. By fostering a culture of transparency and accountability, we can harness the benefits of cell phone spy technology while safeguarding individual privacy. After all, in a world increasingly connected by technology, trust remains the cornerstone of all relationships.
0 notes
Text
How Can Hackers Hack Your Phone?
Smartphones are an indispensable part of modern life, acting as personal assistants, communication hubs, and data storage centers. While they provide immense convenience, they also serve as tempting targets for hackers. Understanding how hackers can hack your phone is crucial to protecting your personal and professional data. This guide explores various hacking techniques and offers actionable tips to secure your device.

1. Social Engineering Attacks
Social engineering attacks exploit human behavior rather than technological vulnerabilities. Hackers manipulate individuals into sharing sensitive information or granting access to their devices.
Phishing
Phishing is one of the most common forms of social engineering. Hackers use deceptive emails, text messages (smishing), or phone calls (vishing) to trick you into clicking malicious links or providing sensitive details.
For instance, you might receive a message claiming to be from your bank, alerting you to suspicious activity on your account. The link redirects you to a fake login page, capturing your credentials.
Impersonation
Hackers may impersonate trusted entities such as technical support agents or service providers. They might convince you to install remote-access software, giving them control of your phone.
2. Exploiting Public Wi-Fi Networks
Public Wi-Fi networks are convenient but often lack adequate security. Hackers exploit these unsecured networks to intercept your data and hack your phone.
Man-in-the-Middle (MITM) Attacks
In MITM attacks, hackers position themselves between your device and the network. They can intercept and read your data, including emails, passwords, and financial transactions.
Rogue Hotspots
Hackers set up fake Wi-Fi hotspots with names resembling legitimate networks (e.g., “Free_Airport_WiFi”). When you connect, they gain access to all your internet activity.
3. Malicious Apps
Applications are a gateway to smartphone functionality, but they can also be a tool for hackers to hack your phone.
Fake Apps
Fake apps mimic legitimate ones but come bundled with malware. These apps may look authentic but can steal data, track keystrokes, or install additional malware.
Permission Misuse
Some apps request unnecessary permissions, such as access to your camera, microphone, or contacts. Granting these permissions can allow hackers to spy on you or steal your personal information.
4. Exploiting Software Vulnerabilities
Outdated software and unpatched vulnerabilities can give hackers the opening they need to hack your phone.
Zero-Day Exploits
A zero-day exploit takes advantage of software vulnerabilities before developers release a fix. These are particularly dangerous because users have no way to protect themselves initially.
Outdated Operating Systems
Failing to update your operating system can leave your device exposed to known security flaws that hackers can exploit.
5. SIM Swapping
SIM swapping, also known as SIM hijacking, is a method where hackers convince your mobile carrier to transfer your phone number to their SIM card.
How It Works
Once hackers control your phone number, they can intercept two-factor authentication (2FA) codes, calls, and text messages. This enables them to access your bank accounts, social media profiles, and other sensitive accounts.
6. Bluetooth Exploits
Bluetooth technology, while convenient, can also expose your phone to hacking risks.
Bluejacking
Bluejacking involves sending unsolicited messages to nearby devices. While not harmful, it can be the first step toward a more invasive attack.
Bluesnarfing
Bluesnarfing allows hackers to access your phone's data via Bluetooth, including contacts, messages, and media files.
7. Spyware and Keyloggers
Spyware and keyloggers are malicious tools used to monitor your phone activity without your consent.
Spyware Installation
Spyware can be installed through:
Malicious links in emails or messages.
Compromised apps downloaded from unofficial sources.
Physical access to your device.
Keyloggers
Keyloggers record every keystroke you make, capturing sensitive information like passwords, credit card numbers, and private messages.
8. Physical Access and Data Theft
If a hacker gains physical access to your device, they can exploit it in numerous ways.
USB Malware
Public USB charging stations can be tampered with to inject malware into your phone. This is known as “juice jacking.”
Theft
Stolen phones are at high risk of being hacked if not protected by strong security measures like encryption and secure locks.
9. Advanced Hacking Techniques
Hackers are continually developing more sophisticated methods to compromise smartphones.
Network Spoofing
Hackers use devices like IMSI catchers or stingrays to mimic cell towers, tricking your phone into connecting to them. This allows them to intercept calls, texts, and internet traffic.
Cross-Site Scripting (XSS)
In XSS attacks, hackers inject malicious scripts into websites you visit. When you access these sites on your phone, the script can compromise your data or install malware.
10. How to Protect Your Phone
Understanding how hackers can hack your phone is only half the battle. Implementing robust security measures is essential for protecting your device.
Enable Two-Factor Authentication (2FA)
Use app-based 2FA instead of SMS-based methods for better security.
Update Your Software Regularly
Keep your operating system and apps updated to patch known vulnerabilities.
Download Apps Only from Trusted Sources
Stick to official app stores like Google Play or the Apple App Store.
Secure Your Lock Screen
Use strong passwords, PINs, or biometrics like fingerprint or face ID to protect your device.
Avoid Public Wi-Fi
Use a Virtual Private Network (VPN) when connecting to public Wi-Fi.
Be Wary of Links and Attachments
Don’t click on suspicious links or download unverified attachments.
Monitor App Permissions
Regularly review app permissions and disable unnecessary access.
Use Anti-Malware Software
Install reputable anti-malware software to protect your phone from malicious attacks.
Regular Backups
Back up your phone regularly to secure your data in case of a breach.
Conclusion
Smartphones are indispensable tools that store a wealth of personal and professional information. However, their convenience comes with risks. Hackers employ various techniques, from social engineering and exploiting public Wi-Fi to installing spyware and leveraging software vulnerabilities.
By understanding how hackers can hack your phone and adopting proactive security measures, you can significantly reduce your risk of falling victim to such attacks. Stay vigilant, keep your software updated, and practice safe online habits to safeguard your digital life.
0 notes
Text
Spy Audio Recording
Spy Audio Recording: A Comprehensive Guide to Technology, Uses, and Ethical Considerations

1. What is Spy Audio Recording?
Spy audio recording is the process of capturing sounds or conversations using hidden equipment without the subjects’ knowledge. These gadgets are frequently small and aesthetically pleasing, resembling commonplace items like buttons, USB drives, pens, and even phone chargers.
2. Uses and Applications of Spy Audio Recording
Personal Security: For people feeling unsafe or vulnerable, audio recorders can offer an added sense of security by documenting interactions in public or private settings.
Investigative Journalism: Journalists and investigators use discreet audio recorders to gather evidence in sensitive situations, especially when conducting interviews or investigations in hostile environments.
Parental Monitoring: Some parents use audio recording tools to monitor their children’s interactions, especially in cases where they suspect bullying or other harmful influences.
Business and Corporate Security: Audio recorders are sometimes used in corporate settings to ensure transparency, protect intellectual property, and prevent unauthorized disclosures.
3. Types of Spy Audio Recording Devices
Spy audio recording devices come in various forms to meet different requirements, each with its unique features. Some common types include:
Miniature Voice Recorders: Small, discreet devices that can be placed in inconspicuous locations. Often battery-operated, they come with long-lasting power options.
Wearable Audio Recorders: These can be integrated into wearable accessories like watches, glasses, and necklaces. Wearable devices are popular for their portability and ease of access.
USB or Power Bank Recorders: These audio recorders look like regular USB drives or power banks, allowing for covert recording while blending seamlessly into most environments.
Pen Recorders: These function as regular pens while discreetly capturing audio. They are often used in meetings and interviews.
Smartphone Apps and Software: With advancements in mobile technology, apps can now enable discreet recording. Some apps have silent activation, scheduled recording, and automatic upload to the cloud for added security.
4. Key Features to Consider in Spy Audio Recorders
When selecting a spy audio recorder, certain features are essential to ensure optimal performance:
Battery Life: Choose a device with a long battery life, especially for prolonged recording sessions.
Storage Capacity: Higher storage capacity allows for more extended recording periods without interruptions.
Audio Quality: High-quality audio ensures that recorded conversations are clear and understandable, even when captured in noisy environments.
Range of Recording: Depending on the environment, the recording range varies. Select devices with sufficient range for your needs.
Motion or Voice Activation: Many spy recorders activate only when they detect sound or movement, which conserves battery life and storage.
5. Legal Considerations and Ethical Implications
Depending on the jurisdiction, utilizing spy audio recording devices may or may not be lawful. Unauthorized recording of a discussion, particularly in a private situation, is prohibited in many jurisdictions. The following are some moral and legal considerations:
Informed Consent: Recording without the other party’s consent is often against the law. Always ensure that your recordings comply with local laws.
Respect Privacy: In public and private settings, respect for privacy is paramount. Avoid recording conversations unless necessary and legally permissible.
Responsible Usage: Spy audio recording devices should not be used for invasive or harmful purposes, such as espionage, harassment, or infringement on someone’s rights.
Before using any spy audio recording device, research the laws in your area and seek legal guidance if necessary. Misuse can result in severe penalties and breach of trust.
6. Buying Guide: Choosing the Right Spy Audio Recorder
When buying a spy audio recording device, it’s essential to assess your needs carefully and match them with the device’s features. Here are some tips for choosing the right spy recorder:
Environment: Indoor settings may require different devices than outdoor spaces. Consider the environment where you’ll be using the device.
Discreet Design: Opt for designs that blend well in the intended setting. Pen recorders work well in office environments, while USB recorders are suitable for public areas.
Technical Features: Check for technical capabilities like noise cancellation, voice activation, and Wi-Fi or Bluetooth connectivity.
Brand Reputation: Choose products from reputable brands, as they typically offer better quality, warranty, and customer support.
7. Top Spy Audio Recording Devices in the Market
While it’s essential to review the latest offerings before purchasing, here are some commonly praised options for their reliability and features:
Mini Voice Activated Recorder by EVISTR: Compact and easy to use, this device offers excellent audio quality with voice activation.
Spy Pen Recorder by Aomago: A favorite for its sleek design, high-quality audio, and ease of use, especially in office settings.
TileRec Mini by Attodigital: Known for its ultra-thin design and portability, this device fits in wallets and offers impressive sound quality.
Always remember to buy from verified sellers and read customer reviews to avoid counterfeit products.
8. Tips for Using Spy Audio Recorders Responsibly
Check Local Laws: Ensure you’re following all legal requirements regarding audio recording.
Limit Recording Duration: Record only what’s necessary and avoid recording in private settings without permission.
Store Data Securely: Ensure recorded data is stored securely and is only accessible to authorized people.
Use Technology for Positive Purposes: Audio recording can be incredibly useful for ensuring safety, gathering important information, and documenting valuable data. However, it should always be used with integrity and respect for others’ privacy.
9. Final Thoughts on Spy Audio Recording
Technology for spy audio recording has created opportunities in journalism, business transparency, and personal security. It can be a useful tool for security and documentation if utilized properly and in accordance with the law. To avoid abuse and protect others’ rights and privacy, the technology must be utilized with a strong sense of ethical obligation.
0 notes
Text
Best Cell Phone Hack for Monitoring Your Partner - 2024
In today's digital age, trust and transparency in relationships are more important than ever. However, doubts and uncertainties can sometimes creep in, leading to a desire for reassurance. One controversial yet increasingly discussed method is using cell phone hacking to monitor your partner's activities. This article explores the best cell phone hacks for 2024, focusing on techniques, tools, and services like HackersList, known for providing top-tier cell phone hacking services worldwide.

What is Cell Phone Hacking?
Cell phone hacking refers to the process of gaining unauthorized access to someone’s mobile device. This can involve extracting data, intercepting communications, and even manipulating the device's functionalities without the owner's knowledge. While hacking has a notorious reputation, it's worth noting that it can be used for various purposes, including cybersecurity, parental control, and, as discussed here, monitoring a partner.
How Mobile Phone Hacking
Mobile phone hacking involves exploiting vulnerabilities in the phone’s operating system or installed applications. Hackers can gain access to personal information, track location, and even listen to conversations. Popular methods include:
Phishing: Deceptive emails or messages tricking users into revealing their passwords.
Spyware: Malicious software installed on a device to monitor activities.
Network Attacks: Intercepting data over unsecured networks.
How to Mobile to Mobile Hack
Mobile-to-mobile hacking refers to accessing one mobile device through another. This often involves using specialized software that can be installed on the target device through a text message, email, or direct physical access. Here’s a basic outline of how it works:
Choose the Right Software: There are various software options available, like mSpy and FlexiSPY, designed for mobile monitoring.
Install the Software: The software needs to be installed on the target device, which might require temporary physical access.
Monitor the Device: Once installed, you can monitor the target device remotely from your own phone.
Hacking Mobile Networks
Mobile network hacking involves intercepting data as it is transmitted over cellular networks. This can be done through techniques like:
Man-in-the-Middle Attacks: Intercepting communications between two parties.
Rogue Access Points: Setting up fake Wi-Fi hotspots to capture data.
SS7 Exploitation: Exploiting vulnerabilities in the Signaling System 7 (SS7) protocol used in cellular networks.
These methods require a higher level of technical expertise and are often used by more advanced hackers.
Best Cell Phone Hackers
Cell Phone hackers are individuals or groups with the skills to infiltrate mobile devices. While some work independently, others might be part of larger organizations or offer their services through platforms like HackersList. HackersList is renowned for providing top-tier cell phone hacking services, connecting clients with professional hackers capable of discreetly monitoring mobile devices. Connect with expert by posting new job
Cell Phone Hack Help to SMS Hack
Related: Cheating Husband Cell Phone Spy App for Read Secret Message
One of the most sought-after features in mobile hacking is the ability to intercept and read SMS messages. This can provide insights into the target’s communications. Tools like HackersList are popular for SMS hacking, allowing users to:
Read Sent and Received Messages: View all SMS communications.
Access Deleted Messages: Retrieve messages that have been deleted.
Monitor Messaging Apps: Track messages from apps like WhatsApp, Facebook Messenger, and more.
Hacking Someone’s Cell Phone
Hacking someone's cell phone involves several steps and considerations. Here’s a simplified guide:
Choose a Reliable Service or Tool: Services like HackersList offer professional hacking services that ensure discretion and efficiency.
Install Monitoring Software: Physical access to the target phone is often required for initial installation.
Monitor Activities: Once installed, you can remotely monitor calls, messages, location, and other activities.
Hack Cell Phone Number
Hacking a cell phone number can provide access to various forms of communication and personal information. Techniques include:
SIM Swapping: Gaining control of the target’s phone number by manipulating the mobile carrier.
Phishing: Tricking the user into revealing their number and associated accounts.
Social Engineering: Using psychological manipulation to gain information.
Hack Mobile Camera
Hacking a mobile camera can provide visual access to the target’s surroundings. This is typically done through spyware that activates the camera without the user’s knowledge. Tools like FlexiSPY offer this functionality, allowing the hacker to:
Take Photos Remotely: Capture images from the target’s camera.
Record Videos: Activate the video recording feature.
Stream Live Video: View live footage from the target’s camera.
Android Cell Phone Hacks
Android devices are particularly susceptible to certain types of hacks due to their open-source nature. Popular hacks include:
Rooting: Gaining superuser access to the device, allowing for extensive control.
Spyware: Installing apps that monitor activities without the user’s knowledge.
Exploiting Vulnerabilities: Taking advantage of security flaws in the Android OS.
Cell Phone Cloned
Cloning a cell phone involves creating an exact replica of the target phone’s data on another device. This allows the hacker to intercept calls, messages, and other communications. Methods include:
SIM Cloning: Duplicating the SIM card to intercept communications.
Phone Cloning Software: Using software to copy the phone’s data.
All Mobile Hack
“All mobile hack” refers to tools and techniques that can be used across different mobile platforms, including Android and iOS. Universal hacking tools like HackersList are designed to work on multiple devices, providing comprehensive monitoring capabilities regardless of the operating system.
Conclusion
Cell phone hacking, while controversial, offers a means to gain insights and reassurance in relationships. With advances in technology, methods have become more sophisticated and accessible. Services like HackersList provide professional hacking solutions, ensuring discretion and effectiveness. Whether it's intercepting SMS messages, hacking mobile networks, or accessing the mobile camera, these tools and techniques offer a comprehensive way to monitor your partner's activities. However, it's crucial to weigh the ethical implications and legal considerations before embarking on this path.
#best cell phone hack#cell phone hacks#cell phone hack#cell phone hacker#cell phone hacking#mobile hacker#mobile hacks#hackerslist
0 notes
Text
How to Catch a Cheating Girlfriend on Snapchat in 3 Minutes

Today’s technologically advanced world has made cheating easier than ever. Mobile apps provide an opportunity to send and receive secretive messages. Snapchat is particularly synonymous with cheating as it allows users to send messages and files that can only be viewed once. If you’ve recently noticed a change in your girlfriend’s attitude, and she’s always on Snapchat, but you don’t know who she’s constantly chatting with, chances are she’s cheating on you. However, you can never be 100% sure until you see her Snapchat messages. A spy app is one of the best ways to discover the truth. This post highlights the best strategies for catching a cheating girlfriend in three minutes using SpyPhone.cc. Working Strategies for Catching a Cheating Girlfriend on Snapchat If you suspect your girlfriend is cheating on you, you can confront her without evidence or get definite proof that she’s cheating on you. The latter is a better method as it will help you make a better decision. Here are the best methods for catching a cheating girlfriend. Method 1: Use SpyPhone.cc Using a Spy app like SpyPhone.cc is the best and most effective method of discovering the truth. The app uses advanced technology to collect data from the target phone without their knowledge. With SpyPhone.cc, you can catch a cheating girlfriend on Snapchat. You don’t need to install the app on the target device, allowing for discreet monitoring, which is essential when looking for hard evidence. And if you find out that your girlfriend isn’t cheating, she’ll never know you spied on her, maintaining the trust between you and her. Features of SpyPhone.cc SpyPhone.cc provides a range of features to help you catch a cheating girlfriend. Let’s explore them. Discrete monitoring—If your girlfriend is overprotective of her phone and often places it face down, SpyPhone.cc allows you to monitor her Snapchat messages without touching her phone. The app operates stealth mode; no icon appears on your target’s phone. Real-time monitoring—SpyPhone.cc allows you to monitor your girlfriend’s real-time Snapchat messages. This makes it always easier to watch her best friends list. New additions to the list could be a sign of cheating. GPS location tracking—One of the most common signs of a cheating girlfriend is a disabled location on Snap map. SpyPhone’s GPS location tracking lets you monitor their location on a detailed map. Comprehensive features—SpyPhone.cc provides comprehensive monitoring of multiple apps, including social media, SMS, web browsers, and more, ensuring you’re always in the know. How to Set Up SpyPhone.cc SpyPhone.cc is one of the easiest apps to use. You don’t even need to touch the target phone. The app works seamlessly with Android and iOS devices, allowing cross-platform monitoring and following these steps to monitor your girlfriend’s Snapchat with SpyPhone.cc. Visit SpyPhone.cc and create an account. You’ll need a working email address. Select the device you want to monitor (Android or iOS). The app does not support Snapchat monitoring on Android devices, but we should expect this functionality shortly. Verify the connection between SpyPhone.cc and the target devices with a cloud account. Log into your SpyPhone.cc account to access your dashboard. Start monitoring your girlfriend’s Snapchat messages Besides Snapchat messages, you can access different data types on SpyPhone. These include sent and received SMS, call logs, photos, videos, browser history, WhatsApp messages, Social Media apps, and others. To explore more about the app's features, check out the comprehensive review of SpyPhone, which delves into its capabilities as the top cheating spouse tracker. Method 2: Screen recording Setting up a recording of your screen is quite an easy and effective option to save the messages on Snapchat before they are lost forever. Most new smartphones have this feature in their settings; if yours doesn't, you may download any third-party application from your app store to serve your motive. First of all, you need to enable the screen recording feature. For example, you can add it to the Control Center via settings on an iPhone. This option is available on Android in the Quick Settings panel or through an application like AZ Screen Recorder. After setting up screen recording, enter Snapchat and record all the messages you want to save. Scroll through the conversations and let the screen recorder capture everything in real-time. Record all essential snaps and chats in real time before they disappear. After recording, stop the screen recorder and save your video. Later, you will be able to play back what you have captured. Snapchat will notify the sender when it detects a user recording something on their screen. This might be something you wish to consider before following this option. What To Do When You Discover She’s Cheating on You Handling betrayal from someone you cherished and invested time and money in can be very painful. Many people find it difficult to accept that their partner is having an affair. Here are tips to keep in mind Break it off—It might not be easy, but you must end the relationship for your good. Delete her number, photos, videos, and anything related to her. Move to a new apartment and start a new life. Work on yourself—Once you end the relationship, start working on yourself. You want to be a better version of yourself when you start a new relationship, Join a ‘tribe’ of men—Get out of the house and join a tribe of men who inspire you to become a better version of yourself. Conclusion If you suspect your girlfriend is cheating on you, you must find out the truth before asking her. Otherwise, you risk damaging the trust in the relationship. The best way to know the truth is using SpyPhone.cc to monitor her Snapchat messages. The app is traceless and doesn’t require installation on the target device. With the app, you can view all her messages and files without her knowing. This way, you can decide based on the evidence you’ve gathered. Read the full article
0 notes
Text
Social Networks have become a necessary part of today’s world and people of all ages are involved in sharing their updates and interacting with their near and dear ones through these platforms. Mobile spy applications are meant for tracking the activities of any mobile device through a control panel given to the subscriber. Consequently, it has become the requirement of parents to keep a check over their children as too much exposure to social environment has led to harming the kids psychologically, emotionally and even physically. Teen Social Media Stats By Each Network A Must Watch Video For Everyone Using Social Networks Social Media Issues For Teens Below is a youtube video that talks about social media and related issues for teen agers. Children spend many hours in a day on social networks and it has become a trend in today’s generation to interact with their friends and even strangers through the websites like Facebook, Twitter and many others. They can use the digital world even to fulfill their fantasies or get involved in cyber crime, drugs, sexual activities and many other illegal activities. Parents need to keep check on the mobile phone of their kids by reviewing their activities in detail. You will get all the details with time, date and activity on the social networks. There will be nothing missed with mSpy. It is the best software to get social network activities tracked from the mobile device of your children. You will be able to get all the data through control panel logs and there will be nothing missed, even if your children delete any message or updates. There are many social networking apps available online and they need to be considered for protection of the kids. Everything will be covered in mSpy packages and you don’t need to worry about anything for mobile monitoring activities. mSpy comes with different packages and you can make sure about your requirements for your son’s/daughter’s mobile phone. It works well for iPhone or android devices and there is one time access required on the mobile to install the application. Once the app is installed, the spying will immediately begin and you can find out the detailed activities of your kid’s mobile. A Youtuber Talking About Social Media Issues mSpy works in an effective way to give you all the relevant data regarding the social network usage. If you find out something irrelevant or wrong in the life of your children, it will be easy to tackle such issues at a right time. Prevention is always better than repenting later on about anything. mSpy is the best software for spying on your children without even letting them know about it. You can protect your kids from online fears by purchasing this magnificent app for your children. Another Interesting Talk On : Why Social Media Is Bad Choice As a family you always have choice to interact with each other instead of going online and using social media. What do you think about use of social networks by kids?
0 notes
Text
Privacy and Security: Safeguarding Our Digital Lives

As mobile phones have become central to both personal and professional life, they also present significant security challenges. The vast amount of personal data stored on and accessed through mobile devices makes them attractive targets for cyberattacks. Ensuring the security and privacy of this data is crucial, yet increasingly complex in a world where mobile connectivity is ubiquitous.
Understanding the Risks
The risks associated with mobile phone use range from the theft of personal information to the exposure of sensitive corporate data. Common threats include:
Malware and Viruses: Malicious software designed to damage or disable mobile devices can also steal data or spy on users.
Phishing Attacks: Cybercriminals use fraudulent emails or texts that mimic legitimate sources to trick users into revealing personal information.
Network Interceptions: Unsecured Wi-Fi networks, especially public ones, can be hotspots for intercepting data transmitted from mobile phones.
App Vulnerabilities: Some apps may have weak security measures, or worse, deliberately gather and misuse user data.
The Role of Encryption
One of the primary defenses against data theft is encryption. Encryption converts data into a secure format that is unreadable without the correct decryption key, protecting information both stored on devices and transmitted over networks. Modern mobile operating systems incorporate strong encryption standards to secure users' data against unauthorized access.
Privacy Tools and Practices
To enhance mobile security, both individuals and organizations can adopt several privacy-enhancing tools and practices:
Regular Updates: Keeping the operating system and apps updated is crucial, as these updates often contain security patches that protect against known vulnerabilities.
Strong Authentication: Using strong, unique passwords, biometric data (like fingerprints or facial recognition), and two-factor authentication can significantly increase security.
Secure Wi-Fi Usage: Avoiding unsecured public Wi-Fi for sensitive transactions or using a virtual private network (VPN) can help protect data in transit.
App Permissions: Being vigilant about the permissions granted to apps—limiting them to only what is necessary for the app to function—can prevent unnecessary data exposure.
Data Privacy Laws and Regulations
As awareness of mobile security risks has grown, so too has the regulatory landscape aimed at protecting personal data. Laws such as the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States have set new standards for data privacy, compelling businesses to handle personal information responsibly.
These regulations require transparency about how personal data is collected, used, and shared. They also grant individuals rights over their data, including the right to access, correct, and delete their personal information, which has prompted businesses to adopt stricter data protection measures.
The Role of Industry in Enhancing Mobile Security
Mobile device manufacturers and software developers play critical roles in enhancing mobile security. Manufacturers are continually improving the hardware security of devices, such as implementing secure enclave technology to protect biometric data. Software developers, on the other hand, are enhancing security features in their products, including more robust encryption and automated security updates.
The Future of Mobile Security
Looking forward, the landscape of mobile security is expected to evolve with emerging technologies. Developments in artificial intelligence (AI) and machine learning (ML) offer new ways to detect and respond to security threats more effectively. However, these technologies also introduce new vulnerabilities, as they can be used to create sophisticated attacks that are harder to detect.
Furthermore, as the Internet of Things (IoT) continues to expand, the integration of mobile devices with other connected devices in smart homes, vehicles, and wearable technology will present new security challenges. Ensuring comprehensive security that covers all aspects of this interconnected ecosystem will be crucial.
Conclusion
The issues of privacy and security in the realm of mobile phones are complex and multifaceted. While the risks are significant, so too are the efforts to mitigate them. By understanding these challenges and implementing strong security practices, both individuals and organizations can protect themselves against emerging threats. As mobile technology continues to advance, staying informed and proactive about mobile security will remain essential.
In the next chapter, we will explore how the future of mobile technology is being shaped by emerging trends and innovations, examining what new developments are on the horizon and how they might transform our use of mobile phones even further.
0 notes
Text
Phone Spy Apps: What You Need to Know About Mobile Surveillance Technology

With the rapid advancements in technology, mobile surveillance has become a booming industry. From concerned parents to employers who wish to monitor productivity, phone spy apps offer a range of functionalities to track and observe mobile activities discreetly. Although these applications provide valuable tools for safety and security, they raise significant ethical, legal, and privacy concerns. In this article, we will delve into what phone spy apps are, how they work, their primary use cases, the ethical and legal implications, and some of the most popular apps available on the market today.
What Are Phone Spy Apps?
Phone spy apps, also known as mobile surveillance or monitoring apps, are software programs designed to track various activities on a smartphone. These apps can record phone calls, track GPS location, monitor social media activity, and even capture keystrokes. In most cases, these apps work in the background, making it difficult for the target user to detect that their activities are being monitored. These apps vary in functionality, price, and stealth capabilities, catering to different user needs and compliance requirements.
How Do Phone Spy Apps Work?
Phone spy apps usually require installation on the target phone. Once installed, the app operates discreetly, collecting data and transmitting it to a remote server. The person monitoring can then access the collected data via an online dashboard or app. The core functionalities typically offered by spy apps include:
Call and Message Tracking: Logs incoming and outgoing calls, records call durations, and may include SMS monitoring to capture sent and received messages.
Location Tracking: Uses GPS technology to pinpoint the device’s location, allowing the monitor to track movements in real-time.
Social Media Monitoring: Provides access to activity on social media platforms like Facebook, WhatsApp, Snapchat, and Instagram, including messages and media.
Keylogging: Records every keystroke made on the device, which is particularly useful for monitoring typing in apps or browsing history.
Email and Internet Monitoring: Tracks email exchanges and websites visited, giving insights into online behaviors.
Multimedia Access: Allows access to photos, videos, and audio files stored on the device.
To avoid detection, these apps are often designed to be lightweight and consume minimal battery power. However, the ability to operate in stealth mode makes phone spy apps controversial, especially in cases where they are used without consent.
Common Use Cases for Phone Spy Apps
Parental Control: Parents use phone spy apps to ensure the safety of their children, monitor their online interactions, and protect them from cyberbullying or exposure to inappropriate content.
Employee Monitoring: Some employers deploy monitoring software on company-issued devices to track employee productivity, ensure adherence to company policies, and prevent data breaches.
Personal Security: In relationships where trust issues exist, some individuals use phone spy apps to track the actions of their partners. However, this usage is controversial and often deemed invasive.
Device Recovery: In cases of lost or stolen phones, spy apps can help users track the device's location, lock it, or even wipe data to protect sensitive information.
Ethical Considerations
While phone spy apps provide legitimate monitoring tools for safety and security, their potential for abuse raises ethical questions:
Invasion of Privacy: Unauthorized tracking without consent is widely regarded as an invasion of privacy, potentially leading to strained relationships and trust issues.
Digital Surveillance and Control: Excessive monitoring, especially among family members or partners, can lead to a culture of control and surveillance that affects autonomy and personal freedom.
Dependency on Technology: For parents and employers, an overreliance on monitoring can hinder trust-building, encouraging micromanagement rather than open communication.
These ethical concerns highlight the need for transparency and consent when using monitoring software. Ensuring that individuals are aware of any tracking and its purpose fosters trust and respects privacy boundaries.
Legal Implications of Phone Spy Apps
The legality of phone spy apps varies significantly depending on the jurisdiction. In general, it is legal to use phone spy apps under specific conditions:
Parental Consent: Parents are typically allowed to monitor the phones of minors (their children), as long as it is done in the child’s best interest.
Employee Consent: Employers may use monitoring software on company-issued devices if they have obtained prior consent from employees and informed them about the scope of surveillance.
Personal Use with Consent: In personal relationships, it is generally legal to monitor someone’s phone if both parties have agreed to it and provided mutual consent.
However, unauthorized use of spy apps is illegal in most countries and can result in criminal charges or civil lawsuits. In the United States, laws like the Wiretap Act and the Stored Communications Act protect against unauthorized monitoring. Similarly, in the European Union, the General Data Protection Regulation (GDPR) requires that individuals consent to any data processing, including monitoring. Unauthorized use of spy apps may violate these laws, resulting in significant fines and legal consequences.
Popular Phone Spy Apps
There are many phone spy apps available on the market, each catering to different needs and budgets. Here are a few popular ones:
mSpy
Features: Call monitoring, GPS tracking, social media monitoring, keylogging.
Use Case: Primarily designed for parental control, offering extensive monitoring features.
Stealth Mode: Operates discreetly, making it undetectable to the device user.
Price: Subscription-based, starting from approximately $30 per month.
FlexiSPY
Features: Call interception, GPS tracking, SMS tracking, multimedia access.
Use Case: Ideal for both parental control and employee monitoring.
Stealth Mode: Highly advanced stealth capabilities, often hard to detect.
Price: One of the more expensive options, with a premium package costing around $60 per month.
Hoverwatch
Features: Call logs, SMS tracking, GPS tracking, social media monitoring.
Use Case: Suitable for parents and employers seeking a budget-friendly option.
Stealth Mode: Operates in the background and can remain hidden from the user.
Price: Affordable, with plans starting at around $25 per month.
Highster Mobile
Features: Call recording, GPS tracking, SMS tracking, email monitoring.
Use Case: Primarily marketed for parental control, though it can be used in other settings as well.
Stealth Mode: Operates discreetly and does not affect device performance significantly.
Price: One-time fee of around $70, which is different from subscription-based options.
XNSPY
Features: Location tracking, social media monitoring, call recording, keylogging.
Use Case: Popular among parents and employers for its range of features.
Stealth Mode: Designed to operate undetected, making it suitable for discreet monitoring.
Price: Monthly subscription starts from around $30.
Risks Associated with Using Phone Spy Apps
Using phone spy apps can present certain risks, especially when used without consent or in violation of legal guidelines:
Legal Consequences: Unauthorized monitoring is a criminal offense in many countries. Violators may face fines, legal action, or even imprisonment.
Data Security Risks: Many spy apps collect sensitive information, making them targets for hackers. A data breach can compromise both the monitored and monitoring individuals’ information.
Technical Issues: Installing spyware can slow down a device or lead to crashes, especially if the app is poorly designed or incompatible with the phone’s operating system.
Detection by Target Users: While many apps offer stealth modes, savvy users can often detect spyware by noticing unusual data usage, decreased battery life, or strange app behavior.
Alternatives to Phone Spy Apps
If privacy concerns or legal implications deter you from using phone spy apps, consider these alternative ways to ensure safety and productivity:
Parental Control Apps: Apps like Google Family Link and Apple’s Screen Time allow parents to set screen time limits and monitor usage without invasive spying.
Communication and Education: Open communication about digital habits and expectations can be more effective than surveillance, especially in family or work settings.
Device Security Software: Antivirus software often includes anti-theft features like remote lock and GPS tracking, offering a legitimate way to protect a lost device.
The Future of Phone Spy Apps
With the increase in smartphone usage, the demand for phone spy apps is likely to continue growing. However, as privacy regulations tighten worldwide, app developers will need to prioritize compliance and user consent. The integration of artificial intelligence could make monitoring apps more sophisticated and discreet, but it will also require developers to ensure that their products align with ethical standards and legal frameworks.
Conclusion
Phone spy apps offer powerful tools for monitoring mobile devices, helping parents protect their children, and enabling employers to ensure productivity. However, the potential for abuse makes it crucial to use these apps responsibly and legally. By understanding the ethical, legal, and practical implications of phone spy apps, users can make informed decisions that respect privacy while still prioritizing safety and security.
The landscape of phone spy technology will continue to evolve, balancing advancements in surveillance with increasing demands for data protection and privacy. For users, the key lies in using these tools responsibly and ensuring compliance with all relevant laws and ethical guidelines.
0 notes
Text
Track Any Cell Phone’s Location in Real-Time: The Complete Guide
In the digital age, mobile phones have become integral to our lives. We rely on them not only for communication but also for navigation, entertainment, and productivity. With the advent of smartphones, tracking technology has evolved, allowing users to locate their devices or the devices of others in real-time. Whether you're trying to recover a lost phone, ensure the safety of a loved one, or manage business assets, real-time phone tracking can be incredibly useful.
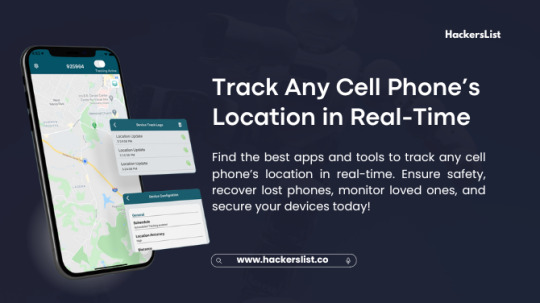
However, with great power comes great responsibility. Tracking a phone’s location in real-time raises ethical and legal concerns, as the potential for misuse is significant. In this blog, we’ll explore how real-time phone tracking works, review the best tools available, and discuss the ethical and legal implications. Additionally, we’ll guide you on using these features responsibly and securely.
How Does Real-Time Phone Tracking Work?
Real-time phone tracking uses a combination of technologies to determine a device’s location. The most common methods include:
GPS (Global Positioning System): GPS is the most accurate tracking technology available. It uses satellites to pinpoint a phone’s location to within a few meters. Nearly all smartphones today have built-in GPS.
Cell Tower Triangulation: When GPS is unavailable, such as indoors or in remote areas, phones can be tracked using signals from nearby cell towers. By analyzing the strength and timing of these signals, a phone’s approximate location can be calculated.
Wi-Fi and Bluetooth: Phones often connect to Wi-Fi networks or other devices via Bluetooth, which can also be used for location tracking. This is particularly useful in urban areas where there are many Wi-Fi networks.
IMSI Catchers and Stingrays: These are advanced surveillance tools used by law enforcement and government agencies to track phones by simulating a cell tower and intercepting signals. These are not available for public use but are part of real-time tracking technology.
Legal and Ethical Aspects of Phone Tracking
Before diving into how to track a phone, it’s crucial to understand the legal and ethical boundaries.
Consent: In many countries, tracking a phone without the owner’s consent is illegal. Even if you have access to the person’s phone, you must inform them and obtain their permission before tracking their location.
Family and Employee Tracking: Tracking family members, particularly minors, is usually allowed, but it should be done transparently. Employers may track employees’ phones, but only when the employees are aware of and have consented to it, usually for work-related purposes.
Privacy Concerns: Unethical phone tracking can lead to privacy violations. Misusing tracking technology to stalk or spy on others can result in severe legal consequences. Therefore, tracking should be done for legitimate reasons, and individuals must take steps to protect their own devices from unauthorized tracking.
Best Real-Time Phone Tracking Tools & Apps
There are many tools and apps available that allow you to track a cell phone in real-time. These tools vary in terms of features, ease of use, and platforms supported.
1. Find My Device (Android)
Overview: This is a built-in feature on Android devices. Once enabled, it allows users to track their phone’s location, play a sound, lock it, or erase its data if necessary.
Key Features: Real-time tracking, sound alerts, device locking, and data wiping.
How to Use:
Open the “Settings” app on your Android device.
Navigate to “Security” and enable “Find My Device.”
To track your phone, visit google.com/android/find on a web browser and sign in with your Google account.
2. Find My (iOS)
Overview: Apple’s Find My app combines Find My iPhone and Find My Friends into one comprehensive tracking tool. It allows you to locate your devices and friends who have shared their locations.
Key Features: Real-time tracking, lost mode, device erasing, location sharing.
How to Use:
Open the “Settings” app on your iPhone.
Tap your Apple ID and select “Find My.”
Enable “Share My Location” and “Find My iPhone.”
To track your phone, use another Apple device or log into iCloud.com on a browser.
3. Life360
Overview: Life360 is a popular family tracking app that allows family members to share their locations in real-time. It’s ideal for keeping tabs on kids, elderly family members, or loved ones.
Key Features: Real-time tracking, location history, SOS feature, driving analysis.
How to Use:
Download Life360 from the App Store or Google Play Store.
Create an account and invite family members to join your circle.
Once connected, you can view everyone’s real-time location within the app.
4. Glympse
Overview: Glympse is a location-sharing app that allows users to share their real-time location with others for a set period. It’s useful for meeting up with friends or family members.
Key Features: Temporary location sharing, no sign-up required, customizable sharing duration.
How to Use:
Download Glympse from the App Store or Google Play Store.
Open the app, select “Share Location,” and choose who to share it with.
Recipients can view your real-time location for the duration you set.
5. Spy Apps
Overview: Spy apps like mSpy or FlexiSPY allow users to monitor a phone’s location, calls, texts, and even social media activity. However, these apps can be controversial due to their invasive nature.
Key Features: Real-time location tracking, call and text monitoring, stealth mode.
Legal Warning: These apps should only be used with the consent of the person being tracked. Unauthorized use can lead to legal action.
How to Track a Phone Using Built-in Features
If you’re not interested in third-party apps, most smartphones come with built-in tracking features. Here’s how to use them:
1. Tracking an Android Phone
Using Find My Device:
Enable “Find My Device” in the settings.
Visit google.com/android/find on any browser.
Log in with the Google account associated with the device.
You can now see the device’s location on the map and perform actions such as locking or wiping it.
2. Tracking an iPhone
Using Find My iPhone:
Enable “Find My iPhone” in the settings under your Apple ID.
Use another Apple device or go to iCloud.com.
Log in with your Apple ID to view the device’s location.
3. Tracking via Microsoft Family Safety
Overview: Microsoft Family Safety allows parents to monitor their children’s phones and location. This feature can be used on Android or Windows devices.
How to Use:
Set up a Microsoft family group at account.microsoft.com/family.
Add family members and enable location sharing.
Third-Party Tracking Apps: Advantages and Risks
While built-in tracking features are convenient, third-party apps offer additional functionality. However, they also come with certain risks.
Benefits of Third-Party Tracking Apps:
More comprehensive tracking features (e.g., geofencing, driving reports).
Often cross-platform, working across Android, iOS, and even desktop devices.
Some apps provide extra safety features like SOS alerts or crash detection.
Risks of Third-Party Apps:
Security Vulnerabilities: Third-party apps can sometimes introduce security flaws or be exploited by hackers. Always ensure the app you’re using is reputable and up-to-date.
Privacy Concerns: Some apps may collect more data than necessary, which can be sold to third parties. Always read privacy policies and user reviews before installing.
Real-Time Tracking for Business and Security
Real-time phone tracking has also become a critical tool for businesses and personal security.
1. Business Use Cases
Employee Tracking: Many companies use real-time tracking to monitor field employees, such as delivery drivers or salespeople. This helps in optimizing routes, ensuring employee safety, and improving productivity.
Asset Management: Companies can track their valuable assets, like company phones or vehicles, to prevent theft and ensure proper usage.
2. Personal Security
Family Tracking: Real-time tracking can provide peace of mind when monitoring the safety of children, elderly parents, or loved ones with special needs.
Emergency Situations: Some apps include emergency features that automatically share your location with loved ones or authorities in case of an accident or emergency.
Privacy and Data Security Concerns
As helpful as phone tracking can be, it comes with its own set of privacy and security concerns. Unauthorized tracking can be invasive, and sensitive data can be exposed to cyber threats.
1. How to Protect Your Privacy
Always lock your phone with a strong password or biometric security.
Disable location services when not needed to prevent apps from tracking your movements.
Regularly review app permissions to ensure apps are not accessing location data unnecessarily.
2. How to Disable Tracking
On Android, go to “Settings” > “Location” and turn off location access.
On iPhone, go to “Settings” > “Privacy” > “Location Services” and disable location tracking for specific apps or globally.
Conclusion
Real-time phone tracking has become an essential tool in both personal and professional life. From recovering lost devices to ensuring the safety of loved ones, the benefits are undeniable. However, it’s vital to use these tools responsibly, respecting legal boundaries and privacy rights. Always obtain consent before tracking someone’s phone and take precautions to protect your data.
As technology continues to evolve, so will tracking capabilities. Staying informed and using these tools ethically will allow you to maximize their benefits while minimizing the risks.
Have you ever used a phone tracking app? Share your experiences in the comments below! And if you’re interested in learning more about cybersecurity or privacy protection, check out our other blog posts on securing your digital life.
0 notes
Text
do i need vpn for cell phone
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need vpn for cell phone
Importance of VPN for mobile security
In today's digital age, where mobile devices have become an integral part of our lives, ensuring their security is paramount. One crucial tool that enhances mobile security is a Virtual Private Network (VPN).
A VPN serves as a shield for your mobile device, encrypting your internet connection and routing it through secure servers, thus safeguarding your data from potential threats. One of the primary reasons why VPNs are essential for mobile security is their ability to protect your sensitive information, such as passwords, financial transactions, and personal communications, from hackers and cybercriminals.
Moreover, VPNs play a vital role in preserving your privacy while using public Wi-Fi networks. Public Wi-Fi hotspots, though convenient, are often vulnerable to attacks, making it easy for malicious actors to intercept your data. By connecting to a VPN, you create a secure tunnel between your device and the internet, preventing unauthorized access to your data even on unsecured networks.
Another significant benefit of using a VPN on your mobile device is bypassing geo-restrictions and accessing restricted content. Whether you're traveling abroad or living in a region with internet censorship, a VPN allows you to browse the web freely and access websites and services that may be blocked in your location.
Furthermore, VPNs can help mitigate the risk of online tracking and profiling by hiding your IP address and masking your online activities. This added layer of anonymity enhances your digital privacy and reduces the likelihood of targeted advertisements and invasive tracking.
In conclusion, the importance of VPNs for mobile security cannot be overstated. By encrypting your internet connection, protecting your data on public Wi-Fi networks, bypassing geo-restrictions, and enhancing your privacy online, VPNs provide comprehensive security solutions for today's mobile users.
Risks of not using VPN on cell phone
Many individuals use their cell phones for various activities, from browsing the internet to accessing personal accounts and making online purchases. However, not using a Virtual Private Network (VPN) on your cell phone can expose you to several risks that compromise your online security and privacy.
One significant risk of not using a VPN on your cell phone is the potential for hackers to intercept your data. When you connect to public Wi-Fi networks in places like cafes, airports, or malls, your sensitive information, such as passwords, financial details, and personal messages, can be intercepted by cybercriminals looking to exploit vulnerabilities in unprotected connections.
Moreover, without a VPN, your online activities are not shielded from prying eyes, including internet service providers, government agencies, and advertisers. This lack of privacy can lead to targeted advertising, data mining, or even surveillance, infringing upon your right to browse the internet anonymously.
Additionally, not using a VPN leaves your cell phone vulnerable to malicious software and phishing attacks. Hackers can deploy malware to steal your data, spy on your activities, or control your device remotely. Phishing attempts, disguised as legitimate websites or emails, can trick you into disclosing sensitive information, further jeopardizing your online security.
In conclusion, the risks of not using a VPN on your cell phone are numerous and can have severe consequences for your online security and privacy. By investing in a reliable VPN service, you can encrypt your data, mask your IP address, and browse the internet safely and anonymously, protecting yourself from potential threats in the digital realm.
Benefits of VPN for mobile privacy
Using a Virtual Private Network (VPN) on your mobile device can provide numerous benefits for enhancing privacy and security. VPNs encrypt your internet connection, making it difficult for hackers, internet service providers, or government agencies to track your online activities. This added layer of security is particularly important when using public Wi-Fi networks, as they are often unsecured and leave your data vulnerable to cyber threats.
Another benefit of using a VPN on your mobile device is the ability to access geo-restricted content. By connecting to servers in different locations around the world, you can bypass censorship and access websites and services that may be restricted in your region. This is especially useful when traveling abroad and wanting to access content from your home country.
Additionally, a VPN can help protect your sensitive information, such as passwords, financial data, and personal messages, from prying eyes. With the growing number of cyber attacks and data breaches, safeguarding your privacy on mobile devices has become more crucial than ever.
Furthermore, using a VPN can prevent advertisers from tracking your online behavior and creating targeted ads based on your browsing history. By masking your IP address and location, a VPN adds an extra layer of anonymity, allowing you to browse the internet privately without being constantly monitored.
In conclusion, utilizing a VPN on your mobile device is a smart decision to enhance your privacy and security online. Whether you're concerned about data protection, accessing restricted content, or simply browsing the web anonymously, a VPN offers a holistic solution to safeguard your digital presence.
VPN necessity for secure browsing on smartphones
In today's digital landscape, where cyber threats lurk around every corner, ensuring secure browsing on smartphones has become a paramount concern. With the increasing reliance on smartphones for various online activities, from banking to socializing, the need for robust protection against potential security breaches has never been more critical. This is where Virtual Private Networks (VPNs) step in as indispensable tools for safeguarding sensitive data and ensuring privacy while browsing on mobile devices.
VPNs offer a secure and encrypted connection between your smartphone and the internet, effectively shielding your online activities from prying eyes. By routing your internet traffic through a remote server and masking your IP address, VPNs create a secure tunnel that prevents hackers, government agencies, and malicious third parties from intercepting or tracking your online behavior.
One of the primary benefits of using a VPN on smartphones is the protection it provides when connecting to public Wi-Fi networks. Public Wi-Fi hotspots, such as those found in cafes, airports, and hotels, are notorious hunting grounds for cybercriminals looking to exploit unsuspecting users. Without proper protection, your personal information, including passwords, financial details, and browsing history, could be vulnerable to interception. However, with a VPN enabled, your data remains encrypted, rendering it unreadable to anyone attempting to intercept it.
Moreover, VPNs offer additional benefits beyond just security. They enable users to bypass geographic restrictions and access content that may be blocked or censored in their region. Whether streaming your favorite shows while traveling abroad or accessing restricted websites, VPNs empower users with greater freedom and flexibility online.
In conclusion, the necessity of VPNs for secure browsing on smartphones cannot be overstated. By encrypting your internet connection, masking your IP address, and providing enhanced privacy and security features, VPNs are essential tools for protecting your digital identity and ensuring a safe and unrestricted online experience.
How VPN enhances mobile data protection
A VPN, or Virtual Private Network, is a powerful tool that enhances mobile data protection and security. Using a VPN on your mobile device encrypts your internet connection, ensuring that your online activities remain private and secure.
One way a VPN enhances mobile data protection is by encrypting data transmitted between your device and the internet. This encryption scrambles the data, making it unreadable to anyone trying to intercept it. This added layer of security is crucial, especially when connecting to public Wi-Fi networks, which are often targets for hackers looking to steal sensitive information.
Additionally, a VPN can help protect your mobile device from malicious threats such as malware and phishing scams. By routing your internet traffic through a VPN server, you can avoid potential cyber attacks that could compromise your data or expose your personal information.
Furthermore, using a VPN allows you to browse the internet anonymously. Your real IP address is masked by the VPN server's IP address, making it difficult for websites and online services to track your online activities. This anonymity adds another level of privacy protection for your mobile data.
In conclusion, incorporating a VPN into your mobile device provides an essential layer of security and protection for your data. By encrypting your internet connection, safeguarding against cyber threats, and ensuring anonymous browsing, a VPN enhances mobile data protection and gives you peace of mind while using your device online.
0 notes
Text
Best Phone Tracker Apps to Track Your Partner Phone - 2024
Nowadays phone tracker apps have gained popularity in many ways and is often used for tracking the activities of close ones. If you are planning to track your partner’s phone, then it is highly advisable to use the best phone tracker. They not only give a sense of relief by being able to keep an eye on your partner’s safety but also contribute positively to enhancing trust in relationships. Now, shall we focus on the most prominent phone tracker apps to track your partner’s phone in 2024?

Phone Tracker Apps: A Necessity in 2024
Thanks to the steadily developing technology, the availability of smartphones, and the ability to share information via digital means, tracking applications for phones are needed by many people. From tracking the partner’s location to providing safety to personal security, these apps come with a number of monitoring attributes that can make the connections gratifying. As people are getting more demanding and independent, hence the enforcing the use of phone tracker app may help one to know what his or her partner is up to.
Best Phone Tracker Apps for Tracking Your Partner's Phone
In this context, we would like to present some of the top phone tracker apps permitting to track your partner’s phone. Some of the top-rated apps include: Some of the top-rated apps include:
Mobile Tracker Apps: These apps have features such as GPS tracking, phone call intercept, and message interception.
GPS Tracker Apps: There are tracker apps available in the market that come in handy when it comes to tracking the location of your partner with the help of GPS on their mobile.
Partner Phone Tracker: Bespoke applications developed with the intention of monitoring partner phones discreetly.
If you're looking for a more comprehensive solution, consider using phone monitoring and surveillance apps like
Phone Monitoring Apps: The following are the applications that enable one to spy on your partner’s phone usage such as calls, texts, and history on the phone.
Phone Surveillance Apps: Some of the spying apps are more sophisticated in their functionality, for instance, one can have full access to the target’s device and tap into the feeds from its camera in real-time.
How Phone Tracker Helps You
Having been explained above, using a phone tracker is beneficial in accessing any signs of unfaithfulness in a relationship. Through discreet surveillance, it will be easy to see changed behavior through phone and other gadget movements late at night or calls to unknown people thinking that they are cheating. Such information may be useful in handling any issues, and even in navigating areas of misunderstandings in the relation. Phone trackers enable both parties to be more understanding and documented, and provide a professional ground and approach towards handling shaky scenarios and assuring safety for all the parties.
Why Need Phone Tracker Service
The availability of a good phone tracker also does have a huge value in professional practice, especially when one needs to spy on a cheating partner. Using such a service, a person can spy on his or her partner’s social media usage as well as other activities that take place online. This data may also aid in external observations and confirm the possibility of infidelity that a partner could only guess at through their communication behavior.
Where trust has been breached, the possibility of monitoring a partner’s internet activity becomes a significant avenue towards confirming the truth so that everyone in the relationship can proceed to the next level in a clean manner. This smooth surveillance feature assists individuals who wish to hold their psychological condition and arrive at sound decision on relationship issues without being pressured to make rash decisions.
Key Features of Phone Tracker Apps
Thus, while deciding to monitor your partner’s phone with the help of a phone tracker application, it is necessary to pay attention to such options: Some essential features to consider include: Some essential features to consider include:
GPS Tracking: To do so, the app must provide proper GPS location tracking features to the users.
Call Recording: Self, it would be wise to seek apps that can record calls and play them back.
Messaging Monitoring: Supplement questions to establish if the app is capable of monitoring messages and social media interactions.
Getting Professional Phone Tracker Service
The task of hiring a professional phone tracker service to monitor a cheating partner needs to be approached carefully, especially when it comes to choosing the right people to help with this job, as their work should be based on personal privacy and adherence to facts rather than on manipulation and lies. HackersList is a site that aims at providing people with performers who will be able to spy on their partner’s phone effectively and secretively. Contact With Experts
Through their services, you can monitor communications that your partner has and where he or she is, information that is useful in relationships. However, it is always important not to violate the privacy and legal rights of people in such circumstances, so availing help of a reliable service like HackersList can offer appropriate assistance alongside the proof you may require.
Related: Best Social Media Hacks to Track Partner’s Activity
Ensuring Privacy and Security
However, when you intend on using phone tracker apps to track your partner's phone then you should think twice since the practice comes with said ethical issues besides the invasion of privacy. To ensure privacy and security, follow these tips: To ensure privacy and security, follow these tips:
Communication: Since the use of a phone tracker app is contentious, it is recommended that partners talk to each other about it.
Consent: It’s important that you inform your partner that you want to monitor their phone activities and then gain their permission to do so.
Data Security: Select an excellent app that is attentive to these aspects among its priorities, namely reliability and data encryption.
Conclusion
Thus, the tracking of your partner’s phone through a phone tracker app is very important in 2024. Using the most effective tracking apps for phones, you can always guarantee the well-being of the person you love and, at the same time, the need to trust and be trusted back. As with any technology that facilitates communication between two or more parties, it is crucial to keep it private and secure while at the same time being open so as not to harm the existing and developing relationship between the individuals.
#best phone tracker apps#phone tracker apps#phone tracker#phone hack#phone hacks#phone hacking#phone hacker#hackerslist
0 notes