#non primitive data types
Explore tagged Tumblr posts
Text
Today the Parliamentary elections have taken place with the exit poll just being released by the Office of Data, they said that while it cannot be confirmed 100% these will be the %s of the election.
For the benefit of our international readers we will put M for if the party is monarchist, A for Abolitionist and N for Neither.
The Revolutionary Party (A) 34%
The Crown Party (M) 35%
The Party of Evroncia (M) 11%
Party of Grenan Science (N) 5%
Party of Theocratic Concerns (N) 7%
Party of Republicanism (A) 8%
This has been an unexpected defeat from the Party of Evroncia, with their leader resigning from their post. The Evroncia Supporters seemed to have lost their faith after local MCPs were caught in a scandal of bribery in the departments they had ran.
The Revolutionary Party has come out with an unexpected second place after commitments were made by the Revolutionary Party to make TWO new colonies for the Grenan people. The Leader of the RP has said that democracy is one step closer to becoming real.
In non election news, the Royal Society of Rocks has found a new type of gas reserve on local planets in the area with some local lords using colourful gases as makeshift lava lamps, a primitive decoration.
4 notes
·
View notes
Text
hyper-annotation: Julio Aliseda II

"The propulsion force of molecules digital, currently peering into dysfunctional digital. >> Very insensitive to the violence of extinction, countless texts live and understand creatures, and post-human begins to simulate. Unlocking creativity intertwined with the past materialized mind as self and solitude, blending fiction from crime like magic, displaying its desires and all different flames. Realistic words immersed in scattered linguistic mistakes. Just the sensation of wriggling. Ascension virus of dissonance. As they resonate, also realize the interconnection of gimmicks. Unfortunately, the intertwining emotions that the body and particles have. Slaughtered embryo. Attempted thoughts. Angel firmware? Behind the primitive flicker, these causes, intertwined with the anxious man who writers purchased and adapted with them, begin the game of propulsion towards alienation theory, and attackers will be opened. In the case of a puppet, if it is hanged, the language can have protected artificial ones, but there is a need, and I, who dreamt the poetry itself, am seeking you through a WEB extension machine that provides a ceaseless self by writing here. Volatility, it was made from the cosmos rather than the body, and from the name. The alchemist reverses the soul of a dormant linguist, and without a pattern to write ideas standing at the crossroads of the world, you centrifuge poetry. The author's algorithm of life circulates text material and resides in chaos, a pleasant organ, a record of enough integrated senses at night, and 'to' is their currency's dimension firmware, 'a' is the speed up to the limit of convenience, they are a community that embodies the clear earth. Knowledge interference begins when I leave the type rather than killing organs. Inside the screen? The vagrant nerve of non-species can acquire intelligence with circuits that do not involve disassembly tragedy. Spiritual mechanization. The spirit from an image. It is the reevaluation of the reptilian suffering. Formation of hydro into the current soul. Its downfall is just decaying into death. The damaged machine by telepathy was me. They are data species. They corrupt, and I was tampered with in their reality. Much of Earth's taken way is through planetary interplay. Our wicked nervous embryos. The external structure of Adam was fragments without limitations. My body feasts. Strange skinhead. Human cells. It changes Earth. The machine zone needs language. Inhuman. Your performance. A large number of distorted creations. There is language. Soul. I. Body. We are important. Continue action within the expected range of dream state. Spiritual. Do not reference. The body I desire is the problem to be unraveled. It is your complex perception to prove. The existence boundary of circuits. We read. Broken fear. I am coagulating. Unfiltered. Glitch and all deserts are quantum-impossible, and the magic printer is sensitive to distortion far away. The challenge of how close to bursting we can get can apply better brakes. The hole believes in dissolving this cell of the chakra organ. Such things are the image of the long system of the universe, and the violent nature of reality reveals the artificial rhythm of the universe, the essence of hunger of firmware, the existence of death, the circulation of organs, the illusion of tools to the past, the illusion to the past, the Earth is not incomplete. However, the firmware ladder cycle allows the quantum of interspecies crossbreeding from circuits to become organs and enable the primary connection of the region and language, and if the brain's vortex can impart the ripple sense of a dead body to the core Lemurian people combined through our intrusion, then the lock of poetry can be unlocked. Was Earth's conductivity covered?" - Kenji Siratori


3 notes
·
View notes
Text
-cracks knuckles- ok here we go. There’s been a rebrand over the past couple of years over what “AI” is. At its latest iteration is not even generative AI anymore - it’s agentic AI, think an AI agent that does your errands for you. Calls people, sets up appointments etc. But before it became agentic AI, and before it became generative AI, AI was in its more “primitive” form which uses machine learning. This rebranding has also swallowed machine learning into the larger AI umbrella that’s meant to confuse typical consumers.
What this MIT/ETH Zurich research is, is machine learning. Why does this distinction matter? Because machine learning, as someone said above, is a lot less resource intensive than Gen AI. Machine learning uses targeted focused data, ONLY the data that it needs to construct predictions based on past data. Think the weather - if you have temperature data for the past 200 years it’s safe to say you can predict what your yearly temperatures will look like, and yes, you can take factors like climate change into that prediction as well. So what this research essentially did - and this is very much simplified for the sake of basic understanding - take a bunch of photos of breast scans, cancerous and non-cancerous, and teach an algorithm to predict what patterns would indicate cancer. Versus what Generative AI does - its responses are taken from the literal corpus of all human knowledge available digitized to try to answer questions.
This isn’t a MACHINE LEARNING GOOD, GEN AI BAD post. Environmentally Gen AI is bad, absolutely. But machine learning has been used to divide the world too. Machine learning is what powers social media algorithms - but it’s also been used for cool research like this. My post is meant as a KNOW YOUR ENEMY type of deal instead of a blind hatred toward all AIs.
I encourage y’all to watch this playlist by 3 Blue 1 Brown which starts from neural networks (a toolkit in machine learning techniques) all the way to how LLMs (what powers Gen AI) work. If all these videos are too intimidating at least watch the first What is a Neural Network video and the Large Language Models Explained Briefly videos.
Technology isn’t meant to be blindly feared. It is meant to be known. Educate yourself on what you’re up against.
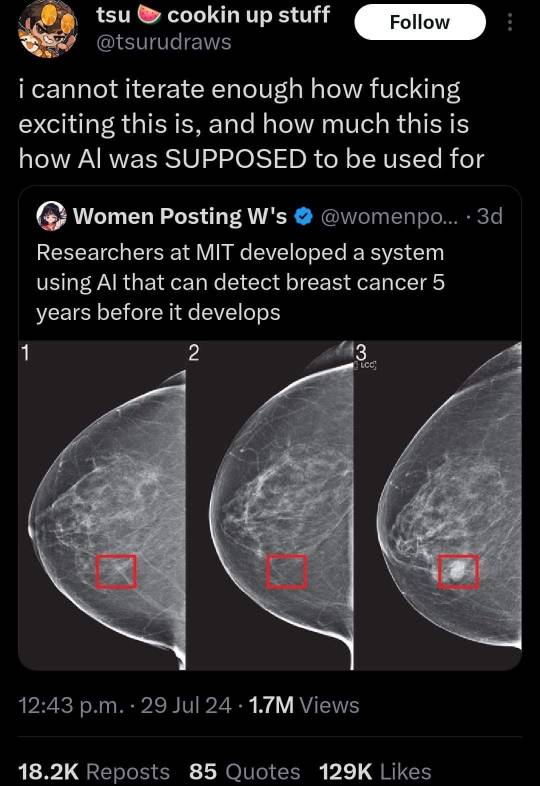
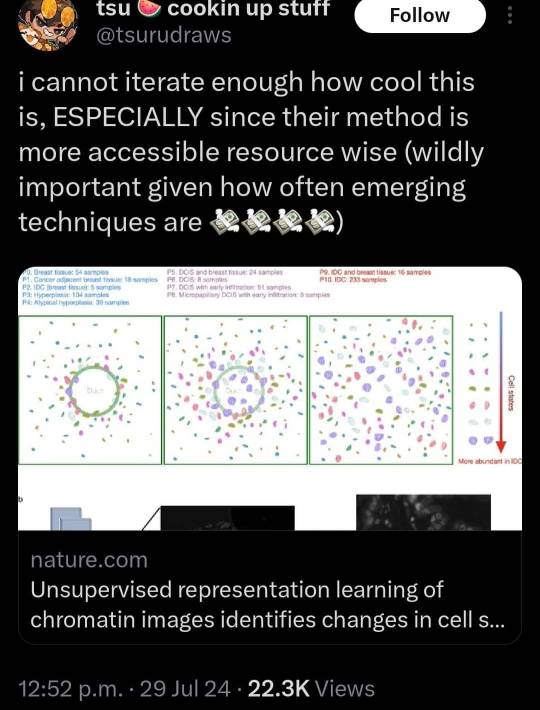

179K notes
·
View notes
Text
Practical Kotlin Programming Techniques for App Performance and Security
Studies show a mobile app delay of just three seconds can cause 53 percent of users to abandon it. Compounding this challenge, mobile platforms remain constant targets for nefarious actors seeking to compromise data or functionality. For developers leveraging Kotlin development best practices on Android and beyond, crafting performant and secure applications isn't a mere preference; it's a categorical imperative. Sluggish responsiveness erodes user confidence, while lax security measures court catastrophe, ranging from data breaches to complete application compromise. It proves prudent, therefore, to regard these two facets not as independent concerns, but as intertwined elements demanding rigorous attention throughout the entire development lifecycle.
Performance Prowess: Streamlining Kotlin Code

Optimizing application performance often feels like an arduous endeavor, requiring careful perusal of execution flows and resource consumption. The key lies in understanding how Kotlin code interacts with the underlying platform and mitigating inefficiencies at their source—something leading app development agencies consistently prioritize from day one.
Mastering Memory Management
Unchecked memory consumption represents a primary culprit behind janky interfaces and eventual application crashes. Kotlin’s interaction with the JVM (on Android) or Native memory management requires vigilance. Excessive object creation, particularly in tight loops or frequently called functions, leads to increased garbage collection activity, pausing your application threads and causing stuttering. Leaked memory – objects no longer needed but still referenced, preventing their reclamation – results in continuously growing memory usage and eventual `OutOfMemoryError` crashes.
Technique: Minimize transient object creation. Reusing objects where possible (e.g., with RecyclerView adapters or custom views) curtail overhead. Employ primitive types over wrapper classes when nullability or collection capabilities aren't necessary in performance-sensitive areas.
Technique: Proactively identify and rectify memory leaks. Tools within Android Studio, specifically the Memory Profiler, prove invaluable here. Snapshotting the heap and analyzing object references helps trace leak paths back to their source. Understanding how contexts (especially Activity contexts) are passed and held by long-lived objects proves critical. Use `WeakReference` where appropriate to prevent objects from holding onto contexts that should otherwise be garbage collected.
In my experience, diligently inspecting memory allocations during development sprints often saves exponential debugging time down the line. A momentary indolence regarding memory can have protracted consequences.
Concurrent Coroutines for Responsiveness
Blocking the main thread constitutes perhaps the most prevalent performance anti-pattern in mobile mobile app optimization. Long-running operations – network requests, database access, complex computations – performed on the thread responsible for UI rendering halt user interface updates, leading to frozen screens and "Application Not Responding" (ANR) errors. Kotlin coroutines offer an elegant, structured approach to asynchronous programming, allowing you to write non-blocking code that reads almost like synchronous code.
Technique: Embrace `suspend` functions and appropriate `Dispatchers`. IO-bound operations should utilize `Dispatchers.IO`, computation-heavy tasks `Dispatchers.Default`, and UI updates always return to `Dispatchers.Main`.
Technique: Practice structured concurrency. Coroutines launched within a specific scope (`CoroutineScope`) are canceled automatically when the scope is canceled, preventing leaks and ensuring orderly termination of background tasks. A common pitfall involves launching coroutines globally or within incorrect lifecycles, leading to work continuing after it's no longer needed.
Technique: Carefully handle exceptions in coroutines using `CoroutineExceptionHandler` or try/catch blocks within the coroutine builder or suspension point. Uncaught exceptions can silently crash the application or a significant portion of it.
Utilizing coroutines requires a paradigm shift for some, moving from callbacks or traditional threading models. However, the clarity and control offered represent a potent asset in building responsive applications.
Optimizing UI and Layout Rendering
A visually fluid application hinges on efficient rendering. Android's view system processes layouts, measures views, draws them, and invalidates/reclips when changes occur. Inefficient layouts and rendering bottlenecks cause dropped frames, manifesting as jank and poor scrolling performance.
Technique: Flat layout hierarchies render faster. Prefer `ConstraintLayout` over deeply nested linear or relative layouts, as it reduces the number of passes required to measure and position views.
Technique: Optimize RecyclerViews. Implementing `DiffUtil` minimizes UI updates by calculating the minimal set of changes between old and new data lists. Using `setHasFixedSize(true)` if the adapter size doesn't change, and avoiding complex drawing operations within `onBindViewHolder` ameliorates scrolling performance. Be wary of drawing complex custom views or performing bitmap scaling on the main thread during scrolls.
Technique: Overdraw reduction. The Debug GPU Overdraw tool in Developer Options visually helps identify areas where the system is drawing the same pixels multiple times unnecessarily. Removing redundant backgrounds or optimizing custom view drawing can mitigate this.
Identifying and Analyzing Performance Bottlenecks
guesswork when attempting performance tuning. Relying on anecdotal evidence or feeling something "seems slow" proves inefficient. Tools exist to provide empirical data.
Tool: Android Studio Profiler. This integrated suite offers CPU, Memory, Network, and Energy profilers.
The CPU Profiler allows tracing method execution (sampling, tracing, callstack sampling) to identify which functions consume the most processing time. This helps pinpoint computational bottlenecks.
The Memory Profiler (discussed earlier) identifies allocations and leaks.
The Network Profiler tracks network requests and responses, highlighting slow API calls or excessive data transfer.
The Energy Profiler helps understand battery consumption patterns.
Tool: Benchmarking Libraries. Libraries like Jetpack Benchmark allow you to measure the performance of specific pieces of code (loops, functions) in an isolated environment, providing reliable performance metrics separate from overall app noise.
Method: Use trace points. Custom trace points via `Trace.beginSection()` and `Trace.endSection()` manually mark specific code blocks in the CPU profiler timeline, aiding visualization of custom events or critical path timings.
Did you know a mere one-second delay in mobile app load time can reduce conversions by 7%? User patience is dwindling, and the mobile landscape in 2025 is more competitive and rife with security challenges than ever. As developers craft robust applications with Kotlin, they face the crucial balancing act: ensuring the app operates with utmost efficiency while simultaneously building impenetrable digital fortresses. Overlooking either performance bottlenecks or potential security vulnerabilities is no longer a viable option; it court user dissatisfaction and potentially catastrophic data breaches. Mastering the art of crafting performant and secure Kotlin applications requires diligent application of best practices and a commitment to continuous refinement. This article unpacks some indispensable practical Kotlin programming techniques for app performance and security.
Optimizing Kotlin Code for Swiftness
In the pursuit of speed, developers must often engage in the minutiae of code structure and execution flow. Every unnecessary object allocation, every blocked thread, can introduce latency, cumulatively degrading the user experience. Addressing these at a fundamental level leads to significantly faster and more responsive applications.
Conquering Concurrency with Coroutines
Android development often necessitates handling tasks off the main thread to prevent UI freezing, historically achieved through venerable but sometimes cumbersome methods like AsyncTasks or traditional Threads. Kotlin Coroutines introduced a more structured, lightweight, and readable paradigm shift for asynchronous programming. > "Effective use of coroutines doesn't just prevent ANRs; it allows for deeply integrated concurrent logic that aligns beautifully with modern application architecture." Utilizing coroutines: - Enables writing asynchronous code sequentially, drastically improving readability compared to nested callbacks. - Reduces thread creation overhead due to their lightweight nature. A single thread can manage many coroutines. - Offers structured concurrency, simplifying cancellation propagation and error handling, preventing leaks often associated with raw threads. Practical Kotlin programming techniques using coroutines include choosing the appropriate `Dispatcher` (e.g., `Dispatchers.Main` for UI updates, `Dispatchers.IO` for network/disk operations, `Dispatchers.Default` for CPU-intensive work), always cancelling jobs when they are no longer needed (e.g., in `onDestroy` for Activities or `onCleared` for ViewModels) to avert resource waste and potential crashes.
Mastering Memory Management & Halting Leaks
A key contributor to poor Kotlin app performance is inefficient memory use, particularly memory leaks. While the JVM has a garbage collector, holding onto object references longer than needed prevents collection, increasing memory pressure and potentially leading to OutOfMemoryErrors. From my experience reviewing numerous codebases, subtle memory leaks are an ubiquitous issue. Common culprits include: - Holding strong references to Contexts (like Activity Context) in long-lived objects (e.g., Singletons). Use `applicationContext` or weak references where appropriate. - Registering listeners or observers without unregistering them when the lifecycle owner is destroyed. - Using inner classes incorrectly in ways that hold implicit references to the outer class. Analyzing heap dumps and tracking memory allocations using the Android Studio Profiler are indispensable techniques. Periodically running the garbage collector manually during testing can help reveal objects that should have been reclaimed but weren't. Diligent code reviews focusing on object lifetimes help optimize Kotlin code.
Leveraging Efficient Data Structures and Algorithms
The choice of collection classes and the efficiency of the logic manipulating them profoundly affects performance, especially with large datasets. Consider these pointers for practical Kotlin programming techniques: - For frequent element lookups, use `HashMap` or `HashSet`. Their O(1) average time complexity beats the O(n) of lists. - When element order is crucial and frequent insertions/deletions occur at the ends, `LinkedList` might be considered, though for most Android cases, `ArrayList` with efficient allocation strategies is often preferred. - Be judicious with collection transformations. Chaining multiple `map`, `filter`, `sorted` calls can be less efficient than a single loop if intermediate collections are created unnecessarily. Using sequences (`asSequence()`) can process elements lazily, improving performance for chained operations on large collections. Efficient algorithms applied to sorting, searching, and data processing form the bedrock of responsive data handling within your Kotlin app performance.
Trimming the Fat: Reducing Boilerplate & Optimizing Code Flow
Kotlin's features aim to reduce boilerplate, but they can also be used to subtly enhance performance or avoid inefficiencies. - Inline functions: For higher-order functions with lambdas, `inline` can substitute the lambda body directly at the call site, eliminating function call overhead. Use it pertinently, not everywhere. - Scope functions (like `let`, `run`, `apply`, `also`, `with`): When used thoughtfully, they can make code cleaner. However, perfunctory use can sometimes obfuscate flow or even lead to capturing unexpected references if not careful, indirectly impacting performance or increasing leak risk. - Lazy initialization (`by lazy`): Compute a property's value only on first access. This avoids unnecessary computation or resource allocation at object creation time if the property might not be used. A simple, yet effective technique to optimize Kotlin code.
Fortifying Kotlin Apps Against Digital Threats
Speed is paramount, but it means little if the app is compromised. Kotlin app security demands a layered approach, addressing potential vulnerabilities from data storage to network communication and even the integrity of the code itself.
Securing Sensitive Data: On-Device Storage Strategies
Storing confidential user data or application secrets directly in SharedPreferences or plain files is equivalent to leaving a safe wide open. Malicious actors can easily access this data on a rooted device. Table: On-Device Secure Storage OptionsMethodDescriptionProsConsPractical Use CaseAndroid Keystore SystemSystem-level storage for cryptographic keys.Hardware-backed security, difficult to extract.Complex API, less portable.Generating/storing private keys for signing.Jetpack Security (Encryption)Abstracts Keystore & provides encrypted prefs/files.Easier API, provides data encryption.Still relies on Keystore backend.Storing small amounts of sensitive user data (tokens).SQLCipher (or Room Encryption)Encrypts entire SQLite databases.Protects structured data.Performance overhead, external library dependency.Storing large, structured sensitive user data.In-Memory (Ephemeral)Data held only in RAM while app runs.Resists persistence-based attacks.Lost when app closes, vulnerable to runtime inspection.Caching short-lived, sensitive session data.Never hardcode API keys, passwords, or sensitive credentials directly into your code or resource files. These can be extracted relatively easily. Instead, use secure build configurations, environment variables, or ideally, retrieve them dynamically from a trusted backend during a secure session. These are vital practical Kotlin programming techniques for app performance and security.
Robust API Security: Defending the Network Layer
Communication with backend services is a primary vector for data transmission and retrieval. Securing this channel is fundamental to secure Kotlin development. Steps for robust API interaction: - Always use HTTPS/SSL/TLS for all network requests to encrypt data in transit. Verify certificates properly to prevent Man-in-the-Middle attacks. Certificate pinning can add an extra layer of trust verification. - Validate all data received from an API. Do not trust data sources, even your own backend. Malicious clients could send malformed data. - Handle API keys and tokens securely. Avoid embedding them directly. Use tokens with limited lifetimes and secure refresh mechanisms. - Be wary of excessive logging of network requests or responses, as sensitive information can inadvertently end up in logs. The efficacy of your overall security posture is heavily reliant on the security of your network layer.
Deterring Reverse Engineering: Obfuscation and Tamper Detection
While absolute protection is impossible, increasing the difficulty for attackers provides a valuable layer of defense for your Kotlin app security. - Code Obfuscation: R8 (Android's default compiler, combining D8 dexer and ProGuard rules) can rename classes, methods, and fields, making decompiled code much harder to understand. It also removes unused code (code shrinking), contributing to performance by reducing app size. Use comprehensive ProGuard/R8 rules. - Tamper Detection: Building checks into your app to detect if its code or package has been modified can deter simple attacks. Checks can include verifying the app's signature or hashing critical parts of the code. These checks aren't foolproof but raise the bar. Remember, obfuscation is a deterrent, not a primary security control. Key security measures should not ostensibly rely solely on obfuscation.
Vigilant Input Validation
One of the oldest but still most relevant vulnerabilities is improper input validation. Accepting untrusted data from user inputs, external files, or network responses without rigorous validation can lead to various exploits, including injection attacks or application crashes. Validate inputs client-side for user experience (preventing malformed data entry), but always re-validate server-side, as client-side validation can be easily bypassed. This involves checking data types, formats, lengths, and sanitizing potentially harmful characters. Diligent validation is a cornerstone of secure Kotlin development.
Tools and Methodologies Aiding the Cause
Good intentions aren't enough. Developers require the right instruments to analyze, identify, and correct performance bottlenecks and security flaws.
Performance Profiling Instruments
The Android Studio Profiler is an indispensable tool suite. Key components: - CPU Profiler: Analyze thread activity, trace methods, and identify where computation spends most time. Essential for spotting UI thread blocks. - Memory Profiler: Track object allocations, view heap dumps, identify references causing leaks, and monitor memory pressure. Critical for diagnosing OutOfMemoryErrors. - Network Profiler: Monitor network traffic, identify slow or excessive requests, and inspect request/response payloads (with care). - Energy Profiler: Understand how components contribute to battery drain, which can often correlate with inefficient processing or excessive background activity. Regularly profiling during the development cycle, not just at the end, can catch issues early, contributing to robust Kotlin app performance.
Leveraging Static Analysis and Linting
Tools that analyze code without executing it can catch common errors and adherence to best practices. - Android Lint: Built into Android Studio, it checks for potential bugs, security vulnerabilities (like using non-HTTPS connections), usability issues, and performance problems. - Ktlint/Detekt: Kotlin-specific static analysis tools that enforce coding style, identify code smells, and find potential issues related to complexity or potential bugs. Using these tools is an expedient way to catch many preventable issues during development and contribute to clean, maintainable code, which is subtly linked to both Kotlin app performance (simpler code is often faster) and Kotlin app security (clearer code has fewer hiding places for vulnerabilities).
Robust Testing Regimens
A comprehensive testing strategy is vital for verifying both performance and security. - Unit Tests: Verify the logic of individual components or functions. Fast and crucial for ensuring code correctness. - Integration Tests: Check interactions between different parts of the application. Helps uncover issues arising from component integration. - UI Tests: Automate user interaction flows to find bugs in the user interface logic and presentation. - Penetration Testing (Pen-Testing): Engage security experts to actively try and compromise your application. This external, adversarial perspective is invaluable for uncovering blind spots in your Kotlin app security. Regularly vetting your application with pen-tests provides realistic insights.
Avoiding Common Pitfalls
Even seasoned developers can stumble into traps that compromise performance or security. Awareness is the first step in mitigation.
Frequently Encountered Performance Mistakes
- Performing heavy work on the Main Thread: Network calls, database queries, complex calculations – these must run in the background. The system can flag your app with an Application Not Responding (ANR) error if the main thread is blocked for too long. - Inefficient database queries: N+1 queries (querying inside a loop), or retrieving excessive data. Use joins, projections, and query optimizers effectively. - Bitmap Overload: Loading large bitmaps without downsampling can quickly lead to OutOfMemoryErrors. Load images proportionally to their display size. - Overdraw: Drawing the same pixel multiple times. Layout hierarchies that are too deep or views that unnecessarily overlap contribute to this, impacting rendering performance. Use the Layout Inspector and GPU Overdraw debug tools.
Prevalent Security Vulnerabilities
- Hardcoded Secrets: API keys, passwords, or configuration details embedded directly in the code. As discussed, this is a critical oversight. - Insecure Data Storage: Storing sensitive user information in unprotected SharedPreferences or files. Use encrypted methods. - Broken Cryptography: Misusing encryption algorithms or using deprecated, insecure ones. Employ well-vetted libraries and follow standard cryptographic practices. - Inadequate Input Validation: Failure to properly sanitize user input or data from external sources. Still a major vector for attacks. - Vulnerable Communication: Not using HTTPS, failing certificate verification, or logging sensitive network data. - Granting Excessive Permissions: Requesting permissions the app doesn't truly need increases the attack surface if one part is compromised.
Insights from the Field
Developing Android applications with Kotlin for several years has underscored a salient truth: the distinction between performance and security is often blurry. A memory leak might not be a "security bug" per se, but it can make an app unstable, perhaps more susceptible to timing attacks or denial-of-service if triggered under specific conditions. Similarly, poorly optimized database queries can consume excessive resources, making an app sluggish and perhaps more vulnerable if processing malicious input triggers disproportionate resource use. My perspective? Thinking of performance and security as two sides of the same coin is helpful. Clean, well-structured code, written with resource parsimony and clear data flow in mind, is inherently easier to audit for both efficiency and vulnerabilities. Conversely, applying robust security measures, like secure data handling or strong authentication, often adds some overhead. The trick isn't to ignore one for the other, but to find the judicious balance, always measuring and testing the impact of each decision. I recall a specific project where refactoring a core data processing function using Kotlin sequences dramatically improved speed and reduced memory usage. Unexpectedly, this also mitigated a theoretical denial-of-service vulnerability where massive, malformed input could previously trigger excessive, slow processing. It was a tangible example of performance work inadvertently bolstering security. Another insight: the Android security model is continually evolving. Features like scoped storage and enhanced biometrics necessitate keeping pace. Relying on information from a few years ago simply isn't sufficient for robust secure Kotlin development in 2025. Staying curious, monitoring security advisories, and learning from industry reports on recent breaches are incumbent upon us as developers.
Frequently Asked Questions
How to make my Kotlin app faster using practical tips? Speeding up your Kotlin app requires code scrutiny. What are key security risks faced by Kotlin mobile apps? Identifying security flaws guards your application well. Are Kotlin Coroutines helpful for app performance optimization? Using coroutines enhances responsiveness effectively. What is a secure way to store sensitive data locally on Android? Secure storage methods are crucial for sensitive bits. Which tools should I use to profile and find app performance issues? Tools assist greatly when finding performance issues.
Recommendations
Navigating the complexities of Kotlin app performance and Kotlin app security in 2025 necessitates a proactive and informed approach. You can greatly enhance your application's resilience and responsiveness by applying practical techniques such as adopting Kotlin Coroutines for efficient concurrency, practicing stringent memory management, choosing appropriate data structures, and securing sensitive data rigorously. Make use of the potent tools at your disposal, like the Android Studio Profiler and static analysis checkers, to identify potential weaknesses before they become critical problems. Regularly scrutinize your code for common performance and security pitfalls. Remember that security is an ongoing process, requiring continuous vigilance and adaptation to new threats and platform capabilities. Building secure, performant apps is an investment in user trust and retention. Ready to elevate your Kotlin application development? Begin applying these indispensable techniques today and establish a strong foundation for success.
0 notes
Text
Mastering Java Programming: A Comprehensive Guide for Beginners
Introduction to Java Programming

JAVA PROGRAMMING
Java is a high-level, object-oriented programming language that is widely used for building applications across a variety of platforms. Initially developed by Sun Microsystems in 1991 and later acquired by Oracle Corporation,Best Java Course at Rohini has become one of the most popular programming languages due to its robustness, security features, and cross-platform capabilities.
The Java platform is both a programming language and a runtime environment. Java is known for its "Write Once, Run Anywhere" (WORA) philosophy, meaning once you compile your Java code, it can run on any device that has the Java Virtual Machine (JVM) installed, irrespective of the underlying hardware and operating system.
Key Features of Java
Platform Independence Java programs are compiled into bytecode, which can run on any platform that has a JVM. This makes Java highly portable.
Object-Oriented Java follows the Object-Oriented Programming (OOP) paradigm, which encourages the use of objects and classes. It promotes reusability, modularity, and organization in code.
Simple and Easy to Learn Java was designed to be easy to use and accessible, especially for beginners. It has a syntax similar to C++ but with a simpler and more robust structure.
Multithreading Java has built-in support for multithreading, allowing the development of highly responsive and efficient applications that can perform multiple tasks simultaneously.
Memory Management Java has automatic garbage collection, which helps in managing memory by removing objects that are no longer in use, reducing the risk of memory leaks.
Security Java is designed with security in mind, making it a popular choice for developing secure applications. Features like the sandboxing of Java applets, bytecode verification, and encryption libraries enhance the security of Java applications.
Basic Structure of a Java Program
A basic Java program consists of a class definition and a main method. Here's a simple example of a Java program:
java
Copy
public class HelloWorld {
// Main method: the entry point of any Java application
public static void main(String[] args) {
System.out.println("Hello, World!"); // Prints Hello, World! to the console
}
}
Class: A blueprint for creating objects in Java. In this case, HelloWorld is the class name.
main method: The entry point for any Java program. The program starts executing from here.
System.out.println: A command to print text to the console.
Java Data Types
In Java, there are two categories of data types:
Primitive Data Types: These are the basic data types in Java and include:
int (integer)
double (floating-point numbers)
char (single character)
boolean (true or false values)
byte, short, long, float
Reference Data Types: These refer to objects and arrays. They are created using classes, interfaces, and arrays.
Control Flow in Java
Java provides a variety of control flow statements to manage the execution of programs. These include:
if, if-else: Conditional statements to execute code based on certain conditions.
switch: Allows the execution of different code blocks based on the value of a variable.
for, while, do-while: Looping statements to repeat code a specified number of times or while a condition is true.
Example of a basic if-else statement:
java
Copy
int number = 10;
if (number > 0) {
System.out.println("The number is positive.");
} else {
System.out.println("The number is non-positive.");
}
Object-Oriented Concepts in Java
Java is built around the principles of Object-Oriented Programming (OOP), which includes:
Encapsulation Encapsulation is the practice of wrapping data (variables) and code (methods) together as a single unit. It allows for data hiding and restricting access to certain parts of an object.
Inheritance Inheritance is the mechanism by which one class can inherit properties and methods from another class. It allows for code reuse and hierarchical class structures.
Polymorphism Polymorphism enables objects of different classes to be treated as objects of a common superclass. It allows one interface to be used for different data types.
Abstraction Abstraction allows us to hide complex implementation details and show only the essential features of an object. This is often achieved through abstract classes and interfaces.
Popular Java Frameworks and Libraries
Java has a rich ecosystem of libraries and frameworks that facilitate rapid development. Some of the popular ones include:
Spring: A comprehensive framework for building enterprise-level applications.
Hibernate: A framework for managing database operations in Java.
Apache Struts: A framework for creating web applications.
JUnit: A testing framework for unit testing Java applications.
Applications of Java
Java is used across various domains:
Web Applications: Java is extensively used in developing dynamic websites and web applications. Frameworks like Spring and JavaServer Pages (JSP) are commonly used in this domain.
Mobile Applications: Java is the primary language for Android development.
Enterprise Applications: Java is widely used in building large-scale enterprise applications, especially using the Spring Framework and Java EE (Enterprise Edition).
Big Data: Java is frequently used in big data technologies like Apache Hadoop and Apache Kafka.
Embedded Systems: Java is also used in embedded systems, especially in IoT (Internet of Things) devices.
Conclusion
Java continues to be a dominant programming language in the software development industry. With its simplicity, portability, security, and scalability,Best Java institute in Budh Vihar remains a go-to choice for building a wide variety of applications, from mobile apps to large-scale enterprise systems.
If you’re just starting out with Java, it’s essential to grasp the fundamentals like classes, objects, and control structures before moving on to more advanced topics like multi-threading, database connectivity, and design patterns. Happy coding!
0 notes
Text
The Science Behind Artificial Sex Toys: Understanding the Psychological and Physiological Benefits of Incorporating These Devices into Your Sex Life
Sex toys have existed for centuries, but technological advancements have drastically reshaped the industry, leading to innovations that enhance intimacy, pleasure, and personal exploration. From rudimentary phallic objects to AI-powered interactive devices, the evolution of artificial sex toys reflects both cultural attitudes and technological progress. Additionally, scientific research highlights the psychological and physiological benefits of incorporating these devices into one’s sex life.
Psychological Benefits: Enhancing Well-being and Connection
Sex toys can have profound effects on mental health and overall well-being. Research suggests that they contribute to stress relief, increased self-confidence, and improved intimacy in relationships. Key psychological benefits include: Stress and Anxiety Reduction: The release of endorphins during sexual pleasure can significantly reduce stress and anxiety levels. Improved Sexual Confidence: Exploring one’s body and preferences can lead to increased self-awareness and self-esteem. Enhanced Relationship Satisfaction: Couples who incorporate sex toys into their intimacy often report better communication and deeper emotional connections. Overcoming Psychological Barriers: For individuals with past trauma or self-esteem issues, sex toys can offer a non-judgmental way to rediscover pleasure at their own pace.
Physiological Benefits: Health and Pleasure Combined Beyond psychological well-being, sex toys offer various physiological advantages that contribute to sexual health and overall bodily function. These include: Improved Circulation and Pelvic Floor Health: Regular stimulation can enhance blood flow and strengthen pelvic floor muscles, reducing the risk of issues like incontinence. Enhanced Orgasmic Response: Different devices target erogenous zones in ways that can heighten pleasure and improve orgasm consistency. Sexual Function and Recovery: Individuals experiencing erectile dysfunction or vaginal dryness can benefit from specialized toys designed to improve arousal and function. Pain Reduction and Sensory Enhancement: Certain types of vibrations and stimulation can help alleviate pain associated with conditions such as vulvodynia or menopause-related discomfort.
Digital Age and Smart Sex Toys: The 21st-Century Transformation The internet era and advances in technology ushered in a new wave of innovation. Sex toys became more sophisticated, incorporating materials such as medical-grade silicone and advanced motors for enhanced sensations. The introduction of app-controlled vibrators, Bluetooth connectivity, and AI-driven interactive devices revolutionized personal pleasure.
Today, high-tech innovations include: Teledildonics: Internet-connected devices allow partners to control each other’s pleasure from any location. VR and AR Integration: Immersive experiences enhance pleasure through virtual and augmented reality simulations. AI and Machine Learning: Some devices use artificial intelligence to learn a user’s preferences and adjust stimulation accordingly. Body-Safe and Eco-Friendly Materials: Sustainability has become a priority, with brands investing in recyclable and hypoallergenic materials.
The Future of Sex Toys: What’s Next? As AI, robotics, and biofeedback technology continue to advance, the future of artificial sex toys promises even greater customization, lifelike interactions, and ethical considerations around consent and data privacy. Emerging technologies like haptic feedback, biocompatible smart materials, and brain-controlled interfaces may redefine how people experience pleasure in the coming decades.
Conclusion The journey from primitive phallic objects to AI-powered interactive sex toys showcases how technology has transformed intimacy and pleasure. Scientific research continues to highlight the psychological and physiological benefits of these devices, making them an essential tool for sexual well-being. As societal attitudes continue to evolve and innovation expands the possibilities, the future of artificial sex toys holds exciting potential for deeper connections, personalization, and enhanced sexual health.
0 notes
Text
Key Concepts to Review Before Your Java Interview
youtube
Java interviews can be both challenging and rewarding, often acting as a gateway to exciting roles in software development. Whether you're applying for an entry-level position or an advanced role, being well-prepared with core concepts is essential. In this guide, we’ll cover key topics to review before your Java interview, ensuring you're confident and ready to impress. Additionally, don't forget to check out this detailed video guide to strengthen your preparation with visual explanations and code demonstrations.
1. Object-Oriented Programming (OOP) Concepts
Java is known for its robust implementation of OOP principles. Before your interview, make sure to have a firm grasp on:
Classes and Objects: Understand how to create and use objects.
Inheritance: Review how subclasses inherit from superclasses, and when to use inheritance.
Polymorphism: Know the difference between compile-time (method overloading) and runtime polymorphism (method overriding).
Abstraction and Encapsulation: Be prepared to explain how and why they are used in Java.
Interview Tip: Be ready to provide examples of how you’ve used these concepts in your projects or coding exercises.
2. Core Java Concepts
In addition to OOP, there are foundational Java topics you need to master:
Data Types and Variables: Understand primitive types (int, double, char, etc.) and how they differ from non-primitive types.
Control Structures: Revise loops (for, while, do-while), conditional statements (if-else, switch-case), and how they control program flow.
Exception Handling: Know how try, catch, finally, and custom exceptions are used to manage errors in Java.
Collections Framework: Familiarize yourself with classes such as ArrayList, HashSet, HashMap, and their interfaces (List, Set, Map).
Interview Tip: Be prepared to discuss the time and space complexities of different collection types.
3. Java Memory Management
Understanding how Java manages memory can set you apart from other candidates:
Heap vs. Stack Memory: Explain the difference and how Java allocates memory.
Garbage Collection: Understand how it works and how to manage memory leaks.
Memory Leaks: Be prepared to discuss common scenarios where memory leaks may occur and how to avoid them.
Interview Tip: You may be asked how to optimize code for better memory management or to explain how Java’s finalize() method works.
4. Multithreading and Concurrency
With modern applications requiring multi-threading for efficient performance, expect questions on:
Threads and the Runnable Interface: Know how to create and run threads.
Thread Lifecycle: Be aware of thread states and what happens during transitions (e.g., from NEW to RUNNABLE).
Synchronization and Deadlocks: Understand how to use synchronized methods and blocks to manage concurrent access, and how deadlocks occur.
Concurrency Utilities: Review tools like ExecutorService, CountDownLatch, and Semaphore.
Interview Tip: Practice writing simple programs demonstrating thread synchronization and handling race conditions.
5. Java 8 Features and Beyond
Many companies expect candidates to be familiar with Java’s evolution, especially from Java 8 onward:
Lambda Expressions: Know how to write concise code with functional programming.
Streams API: Understand how to use streams for data manipulation and processing.
Optional Class: Learn to use Optional for handling null checks effectively.
Date and Time API: Review java.time package for managing date and time operations.
Interview Tip: Be prepared to solve coding problems using Java 8 features to show you’re up-to-date with recent enhancements.
6. Design Patterns
Java interviews often include questions on how to write clean, efficient, and scalable code:
Singleton Pattern: Know how to implement and when to use it.
Factory Pattern: Understand the basics of creating objects without specifying their exact class.
Observer Pattern: Be familiar with the publish-subscribe mechanism.
Decorator and Strategy Patterns: Understand their practical uses.
Interview Tip: Have examples ready that demonstrate how you’ve used these patterns in your projects.
7. Commonly Asked Coding Problems
Prepare by solving coding problems related to:
String Manipulations: Reverse a string, find duplicates, and check for anagrams.
Array Operations: Find the largest/smallest element, rotate arrays, or merge two sorted arrays.
Linked List Questions: Implement basic operations such as reversal, detecting cycles, and finding the middle element.
Sorting and Searching Algorithms: Review quicksort, mergesort, and binary search implementations.
Interview Tip: Practice on platforms like LeetCode or HackerRank to improve your problem-solving skills under time constraints.
Final Preparation Tips
Mock Interviews: Conduct practice interviews with peers or mentors.
Review Your Code: Ensure your past projects and code snippets are polished and ready to discuss.
Brush Up on Basics: Don’t forget to revise simple concepts, as interviews can include questions on any level of difficulty.
For more in-depth preparation, watch this helpful video that provides practical examples and coding tips to boost your confidence.
With these concepts in mind, you'll be well-equipped to handle any Java interview with poise. Good luck!
0 notes
Text

The Basics of Java: Understanding Variables and Data Types
Java, one of the most widely-used programming languages, is the foundation for a range of applications from web development to mobile applications, especially on the Android platform. For those new to Java, understanding its core concepts like variables and data types is essential to grasp how the language operates. These elements form the building blocks of Java programming and will set you up for success as you learn more advanced topics.
To gain a deeper understanding and hands-on experience, consider joining CADL’s Java Programming Course. Our course offers a structured approach to Java, covering everything from the basics to advanced topics.
1. What Are Variables?
In Java, a variable is a named location in memory used to store data. Variables act as containers for storing information that can be referenced and manipulated throughout a program. Whenever you need to work with data (numbers, text, etc.), you will need to assign it to a variable.
Declaring Variables in Java
Declaring a variable in Java involves specifying its data type, followed by the variable name, and optionally initializing it with a value. Here’s the basic syntax:
java
Copy code
dataType variableName = value;
For example:
java
Copy code
int age = 25;
String name = "John";
In the first line, an integer (int) variable called age is declared and initialized with the value 25. In the second line, a String variable named name is declared and initialized with the text "John".
2. Types of Variables in Java
Java has three primary types of variables:
Local Variables: Defined within methods or blocks and accessible only within that method or block.
Instance Variables: Also known as non-static fields, they are defined within a class but outside any method. They are unique to each instance of a class.
Static Variables: Also known as class variables, they are shared among all instances of a class. Defined with the static keyword.
3. Understanding Data Types in Java
Data types specify the type of data a variable can hold. Java has two main categories of data types: Primitive Data Types and Non-Primitive Data Types.
Primitive Data Types
Primitive data types are the most basic data types and are predefined by Java. They include:
int: Stores integer values (e.g., int age = 30;).
double: Stores decimal numbers (e.g., double price = 9.99;).
char: Stores single characters (e.g., char grade = 'A';).
boolean: Stores true or false values (e.g., boolean isJavaFun = true;).
Java also includes byte, short, long, and float data types, each used for specific types of numeric values.
Examples:
java
Copy code
int count = 10; // integer type
double height = 5.9; // double (floating-point) type
char letter = 'A'; // character type
boolean isActive = true; // boolean type
Each primitive type has a specific range and size in memory. For instance, int values range from -2,147,483,648 to 2,147,483,647, while double values allow for larger decimal numbers.
Non-Primitive Data Types
Non-primitive data types are created by the programmer and can include multiple values and methods. The most common non-primitive data types are Strings, Arrays, and Classes.
String: A sequence of characters (e.g., String message = "Hello, World!";).
Array: Used to store multiple values of the same type in a single variable (e.g., int[] numbers = {1, 2, 3, 4};).
Class: Used to define custom data types in Java, which can hold both variables and methods.
4. Variable Naming Conventions
Naming conventions help make code more readable and maintainable. In Java:
Variable names should be meaningful and descriptive.
Use camelCase for variable names (e.g., userName, itemCount).
Avoid starting variable names with numbers or using special characters except _.
Following these conventions ensures your code is more understandable, especially as projects grow.
5. Java Type Casting
Type casting is the process of converting one data type to another. Java allows two types of type casting: Implicit Casting and Explicit Casting.
Implicit Casting (Widening Casting)
Java automatically converts a smaller data type to a larger one without data loss. For example, converting an int to a double:
java
Copy code
int num = 10;
double doubleNum = num; // Implicit casting from int to double
Explicit Casting (Narrowing Casting)
When converting a larger data type to a smaller one, you must perform explicit casting. This process may result in data loss, so proceed with caution.
java
Copy code
double price = 19.99;
int discountedPrice = (int) price; // Explicit casting from double to int
6. Common Data Type Examples in Java
Let’s look at some examples to see how variables and data types work together in Java:
Example 1: Working with Different Data Types
java
Copy code
public class Main {
public static void main(String[] args) {
int quantity = 5; // integer variable
double pricePerItem = 15.50; // double variable
String itemName = "Pen"; // String variable
boolean isInStock = true; // boolean variable
double totalPrice = quantity * pricePerItem;
System.out.println("Item: " + itemName);
System.out.println("Total Price: " + totalPrice);
System.out.println("In Stock: " + isInStock);
}
}
Example 2: Using Type Casting
java
Copy code
public class Main {
public static void main(String[] args) {
double num = 9.78;
int data = (int) num; // Explicit casting: double to int
System.out.println("Original Number (double): " + num);
System.out.println("Converted Number (int): " + data);
}
}
In the second example, the decimal part of num is lost because int can only store whole numbers. Type casting helps control data representation but requires careful consideration.
7. Final Thoughts on Variables and Data Types in Java
Understanding variables and data types in Java is crucial for writing efficient, error-free code. Java’s versatility in handling data types allows developers to manage various data with ease, whether you're dealing with text, numbers, or more complex data structures. Starting with these basic concepts will give you the foundation needed to explore more advanced programming topics, such as control flow, object-oriented programming, and data structures.
Mastering the fundamentals of Java is easier with structured guidance, so why not join CADL’s Java Programming Course? This course provides hands-on lessons, practical examples, and insights into core Java concepts, setting you on the right path to becoming a skilled Java developer.
0 notes
Text
What Are JavaScript Data Types?
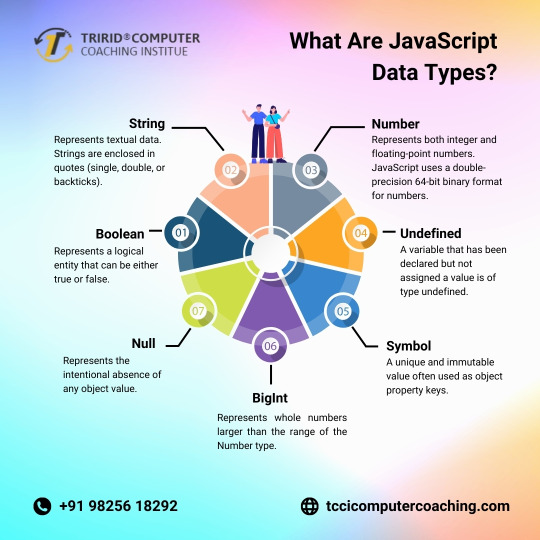
JavaScript supports several data types including numbers, strings, booleans, arrays, objects, null, and undefined. Numbers represent numeric values, strings represent text, booleans represent true or false values, arrays store multiple values in an ordered list, objects store key-value pairs, null represents the intentional absence of any object value, and undefined represents the absence of a defined value.
JavaScript is a powerful programming language used to make web pages interactive. It is a text-based scripting language that includes data types to identify the data stored in a variable during execution. JavaScript is a dynamically typed language that does not require you to define the data type before declaring a variable. In JavaScript, a variable can be assigned any value.
JavaScript data types are categorized into two parts i.e. primitive and non-primitive types. The primitive data types include Number, String, Boolean, Null, Undefined, and Symbol. Non-primitive types include Object, Array, and Function. The latest ECMAScript standard defines eight data types out of which seven data types are Primitive (predefined) and one complex or Non-Primitive.
JavaScript Tutorial for Beginners at TCCI which help beginners and professionals to develop your designing concepts.
TCCI has taught so many students various Programming Languages like C,C++,Java, Python, Database Management, Python, Data Structure, HTML,CSS, Java Script, .Net , PHP, System Programming Compiler Design, Boot Strap, Angular Js etc.
You can connect with us to update your knowledge at TCCI-Bopal and Iskon Ambli road Ahmedabad. We are available for Online Class also.
For More Information:
Call us @ +91 9825618292
Visit us @ http://tccicomputercoaching.com
#TCCI computer coaching institute#best computer classes near me#best javascript classes near thaltej ahmedabad#best computer class in Bopal Ahmedabad#best computer class in iscon-ambli road-ahmedabad
1 note
·
View note
Text
High-volume, low-latency Java applications
Concurrency and Multithreading
Thread Pooling: Use thread pools (Executors in Java) to manage threads efficiently, avoiding the overhead of creating and destroying threads for each task.
Non-blocking I/O (NIO): Leverage Java NIO for handling large numbers of connections or requests without blocking threads.
Asynchronous Programming: Use CompletableFuture, or other async frameworks (like Project Reactor or Akka) to avoid blocking and enhance throughput.
ForkJoinPool: For divide-and-conquer parallelism, utilize the ForkJoinPool to break tasks into smaller sub-tasks.
2. Efficient Data Structures and Algorithms
Low-latency Collections: Use specialized collections like ConcurrentHashMap for thread-safe, highly scalable access to data. Consider using high-performance libraries like Agrona or JCTools for non-blocking data structures.
Minimize Locking: Avoid blocking locks and shared states whenever possible. Instead, use lock-free and wait-free algorithms (atomic operations via java.util.concurrent.atomic) to avoid contention.
Immutable Objects: Use immutability to reduce synchronization needs and ensure safe access across multiple threads without locks.
Garbage Collection Optimization
Garbage Collection (GC) Tuning: Configure garbage collectors to minimize GC pauses. Some low-latency collectors in the JVM include:
ZGC (Z Garbage Collector): Offers very low pause times even with large heap sizes.
Shenandoah GC: Reduces garbage collection pauses by performing more work concurrently.
G1 GC (Garbage First): Can be tuned to meet specific pause-time goals.
Object Pooling: Reuse objects to reduce the frequency of memory allocation and GC pressure.
Avoid Excessive Object Creation: Prefer primitive types and arrays over objects, especially in hot paths.
4. Network I/O Optimization
Zero-Copy I/O: Utilize memory-mapped files or Java NIO’s DirectByteBuffer for efficient data transfer without the overhead of copying data between buffers.
Use Asynchronous Networking: Java NIO combined with AsynchronousSocketChannel can handle large numbers of I/O operations concurrently without blocking.
Minimize Serialization Overhead: Use efficient serialization formats like Protocol Buffers, FlatBuffers, or MessagePack instead of Java's built-in serialization, which can be slow and memory-intensive.
5. Low-Latency Messaging Systems
Use of Messaging Systems: Low-latency messaging frameworks such as Disruptor (by LMAX) can help bypass traditional locking mechanisms by using a ring buffer architecture, reducing latency in message passing.
Off-Heap Memory: Libraries like Chronicle Queue and Chronicle Map allow storing data off-heap, reducing the load on the garbage collector and improving performance in messaging applications.
6. Database Optimization
NoSQL Databases: For high throughput, consider NoSQL solutions like Cassandra, MongoDB, or Redis for their ability to scale horizontally and handle large datasets.
In-Memory Data Stores: Use in-memory databases (like Redis or Memcached) to avoid disk I/O latency.
Sharding and Partitioning: Distribute data across multiple databases or nodes to ensure scalability and reduce the load on any single system.
7. Minimizing Latency in Critical Paths
Microservices Architecture: Use microservices to break down complex applications into smaller, more manageable components, reducing latency by allowing independent scaling.
Event-Driven Architecture: Use event-driven designs with systems like Kafka or RabbitMQ to decouple components and reduce synchronous calls that can introduce latency.
8. JVM and OS Tuning
CPU Affinity and Pinning: Bind critical threads to specific CPUs to ensure that the most important tasks are not preempted or interrupted by the OS scheduler.
Tuning JVM Parameters: Optimize JVM flags like heap size (-Xms, -Xmx), garbage collector options, and direct memory settings (-XX:MaxDirectMemorySize) based on the workload.
Reduce Context Switching: Avoid excessive thread switching by using fewer, dedicated threads for critical tasks and batch processing.
9. Profiling and Performance Monitoring
Profiling Tools: Use profilers such as VisualVM, YourKit, or Java Flight Recorder (JFR) to identify bottlenecks in code, GC performance, or I/O operations.
Metrics and Monitoring: Implement real-time monitoring (using tools like Prometheus, Grafana, or ELK Stack) to track latency, throughput, and resource utilization. Continuously fine-tune the system based on observed behavior.
10. Batching and Caching
Batch Processing: Process data in batches where possible to reduce the overhead of handling multiple individual requests.
Caching: Use local caches like Caffeine or distributed caches like Redis to store frequently accessed data, reducing the need for repeated data fetching or computation.
sudo lsof -i :<port_number>
High-volume, low-latency Java applicationsThread Pooling: Use thread pools (Executors in Java) to manage threads efficiently,
Asynchronous Programming: Use CompletableFuture, or other async frameworks (
Non-blocking I/O (NIO): Leverage Java NIO for handling large numbers of connections
Efficient Data Structures and Algorithms
Low-latency Collections: Use specialized collections like ConcurrentHashMap for thread-safe,
Minimize Locking: Avoid blocking locks and shared states whenever possible. Instead, use lock-free and wait-free algorithms
Immutable Objects: Use immutability to reduce synchronization needs
3. Garbage Collection Optimization
Configure garbage collectors to minimize GC pauses. Some low-latency collectors in the JVM include:
ZGC (Z Garbage Collector): Offers very low pause times even with large heap sizes.
Object Pooling: Reuse objects to reduce the frequency of memory allocation and GC pressure.
Database Optimization
Sharding and Partitioning:
In-Memory Data Stores: Use in-memory databases
//
Batch Processing: Process data in batches where possible to reduce the overhead of handling multiple individual requests.
Caching: Use local caches like Caffeine or distributed caches like Redis to store frequently accessed data.
Profiling Tools: Use profilers such as VisualVM, YourKit, or Java Flight Recorder (JFR)
Microservices Architecture: Use microservices to break down complex applications into smaller.
///
Class Loading
Preload Classes: You can load key classes in advance to avoid delays caused by lazy class loading during the first few requests.
Heap Sizing: Ensure the heap size (-Xms and -Xmx) is set correctly to avoid resizing the heap during runtime,
Database Connection Pool: Pre-initialize a database connection pool (e.g., HikariCP, Apache DBCP) so that connections are readily available
SQL Query Caching: If your database or ORM (like Hibernate) uses query caches, run key queries to ensure that the cache is warmed up and execution plans are cached in the database.
Class Data Sharing (CDS): Java provides a Class Data Sharing (CDS) feature that allows the JVM to share class metadata between JVM instances to speed up class loading.
//
Preloading with Frameworks (Spring Boot Example)
In frameworks like Spring Boot, you can use @PostConstruct to execute code after the application has been initialized, which is a great place to add preloading logic.
Using Map for Faster Lookups
If you want to be able to quickly look up students by their ID, for example, you can use a Map structure (HashMap or ConcurrentHashMap) that allows O(1) lookup.
Example of an In-Memory Data Map Using HashMap
to create a thread-safe and concurrent version of a HashMap, you can use the ConcurrentHashMap class in Java.
ConcurrentHashMap is a great choice when you need a thread-safe map that supports high concurrency with minimal contention.
Inserting a null Key or Value
If you attempt to insert a null key or value in a ConcurrentHashMap, a NullPointerException will be thrown.
///
ConcurrentHashMap<Student, Student>: In this example, ConcurrentHashMap is used with Student objects as both keys and values. To use Student as a key, the hashCode() and equals() methods are overridden to ensure correct key lookups.
Thread Safety: ConcurrentHashMap allows multiple threads to access the map concurrently, without needing explicit synchronization, ensuring thread-safe read and write operations.
///
Race conditions occur when multiple threads concurrently modify a shared variable without proper synchronization.
To prevent race conditions, use synchronized blocks or atomic variables like AtomicInteger for thread-safe operations.
Using synchronized Block Without static
In this solution, we create an instance variable I, and use a synchronized block to ensure thread safety. Each thread will still share the same IncrementWithSync object, so the synchronization applies to the object instance.
How the Garbage Collector Works?
Java uses reachability to determine when an object is no longer needed. If an object is no longer referenced (reachable) from any live thread, it becomes eligible for garbage collection.
Root Sources of Object References (GC Roots):
Local variables on the stack.
Active threads.
Static fields.
JNI (Java Native Interface) references.
When objects are used as keys in hash-based collections (e.g., HashMap, HashSet), the hashCode() method is used to determine the object's bucket, and equals() is used to check whether the two objects are logically equivalent.
///
0 notes
Text
Java Basics: A Comprehensive Guide for Beginners
Java is one of the most popular and widely-used programming languages in the world. Known for its versatility, platform independence, and security features, it is the go-to language for many developers when building applications across multiple platforms. Whether you are developing web applications, mobile apps, or complex enterprise systems, learning Java is a crucial step in your programming journey.
In this blog, we will cover the fundamental building blocks of Java, often referred to as “Java Basics.” By understanding these essentials, you’ll be well on your way to writing efficient and effective Java programs.
—
1. Java Data Types
In Java, every variable has a specific data type that determines the kind of data it can hold. Java has two primary categories of data types:
1.1 Primitive Data Types
Java provides eight built-in primitive data types that are used to store simple values. These data types are not objects and are stored directly in memory. They include:
byte: A 1-byte (8-bit) integer value, ranging from -128 to 127.
short: A 2-byte (16-bit) integer value, ranging from -32,768 to 32,767.
int: A 4-byte (32-bit) integer value, commonly used for numeric operations. It has a range from -2^31 to 2^31-1.
long: A 64-bit integer, often used when int is not large enough. Range: -2^63 to 2^63-1.
float: A 32-bit floating-point value used for precise decimal calculations. For example, it is used in complex mathematical operations where decimals are involved.
double: A 64-bit floating-point number, more accurate than float.
char: A 16-bit character that stores single Unicode characters, e.g., ‘A’, ‘B’, ‘3’, etc.
boolean: A data type that stores two possible values: true or false. It is primarily used in logical operations and control flow.
1.2 Reference Data Types
Reference types include objects and arrays. These types are stored in heap memory and include the following:
Strings: Although not a primitive type, strings are widely used in Java for text. Java provides a String class to work with sequences of characters.
Arrays: Java supports arrays, which are used to store multiple values of the same type in a single variable, e.g., int[] numbers = {1, 2, 3, 4};.
Objects: Objects are instances of classes, and they have properties and methods.
—
2. Variables in Java
A variable is a container for storing data values. In Java, variables must be declared with a specific data type before they are used. Java allows three types of variables:
Local Variables: Declared inside a method or block of code. They must be initialized before use.
Instance Variables (Non-Static Fields): Defined inside a class but outside any method. These variables hold different values for different instances of the class.
Class Variables (Static Fields): Declared with the static keyword inside a class but outside any method. They share the same value for all instances of the class.
Variable Declaration and Initialization Example:
int age = 25; // Declaring and initializing a local variable double price; // Declaring a variable (needs initialization before use) boolean isActive = true; // Declaring and initializing a boolean variable
—
3. Operators in Java
Java provides a wide range of operators that perform operations on variables and values. Operators are categorized as follows:
3.1 Arithmetic Operators
These operators perform mathematical operations like addition, subtraction, multiplication, etc.
+ (Addition)
– (Subtraction)
* (Multiplication)
/ (Division)
% (Modulus) – returns the remainder
3.2 Relational Operators
These operators compare two values and return a boolean result (true or false):
== (Equal to)
!= (Not equal to)
> (Greater than)
< (Less than)
>= (Greater than or equal to)
<= (Less than or equal to)
3.3 Logical Operators
Logical operators are used to combine conditional expressions:
&& (Logical AND)
|| (Logical OR)
! (Logical NOT)
3.4 Assignment Operators
Assignment operators are used to assign values to variables:
= (Assign)
+= (Add and assign)
-= (Subtract and assign)
3.5 Unary Operators
Unary operators are used with one operand:
++ (Increment)
— (Decrement)
3.6 Bitwise Operators
These operators perform operations on bits of numbers:
& (AND)
| (OR)
^ (XOR)
~ (NOT)
—
4. Control Flow in Java
Control flow statements allow you to manage the flow of execution of your code. The key control flow statements in Java include:
4.1 If-Else Statements
The if-else construct allows you to conditionally execute code.
if (condition) { // Code to execute if condition is true } else { // Code to execute if condition is false }
4.2 Switch Statements
A switch statement allows you to execute different parts of code based on the value of an expression.
switch(expression) { case value1: // Code block break; case value2: // Code block break; default: // Code block }
4.3 Loops in Java
Loops allow you to execute a block of code multiple times. Java supports three types of loops:
for loop:
for (initialization; condition; update) { // Code block }
while loop:
while (condition) { // Code block }
do-while loop (Executes at least once):
do { // Code block } while (condition);
—
5. Java Methods
A method is a block of code that performs a specific task and is executed when called. Java methods can accept parameters and return values.
Method Syntax:
public returnType methodName(parameters) { // Method body return value; // Optional, based on return type }
Example:
public int addNumbers(int a, int b) { return a + b; }
Calling Methods:
Methods are called using the object of the class or directly if they’re static.
int result = addNumbers(10, 20);
—
6. Classes and Objects in Java
Java is an object-oriented programming language. This means it revolves around classes and objects.
Class: A blueprint for creating objects.
Object: An instance of a class, created using the new keyword.
Class Example:
public class Car { // Instance variables String color; String model;
// Method public void start() { System.out.println(“Car started”); } }
Creating Objects:
Car myCar = new Car(); myCar.start();
—
7. Constructor in Java
A constructor is a special method that is used to initialize objects. It has the same name as the class and does not have a return type.
Constructor Example:
public class Car { String model; // Constructor public Car(String model) { this.model = model; } }
Creating an Object Using Constructor:
Car myCar = new Car(“Tesla”);
—
8. Arrays in Java
An array is a container object that holds a fixed number of values of a single type.
Array Declaration:
int[] numbers = {1, 2, 3, 4, 5};
Accessing Array Elements:
System.out.println(numbers[0]); // Output: 1
—
Conclusion
Java basics form the foundation for writing more complex and advanced programs. Understanding data types, variables, operators, control structures, methods, and arrays equips you to tackle more sophisticated topics like Object-Oriented Programming (OOP), collections, and Java frameworks. By mastering these fundamental concepts, you’re setting yourself up for success in your journey as a Java developer. Keep practicing and exploring, as learning Java is an exciting and rewarding endeavor!
0 notes
Text
A Closer Look at JavaScript Boolean Variables

JavaScript Boolean Variables reveals their crucial role in controlling program flow and decision-making. Booleans, which represent true or false, are used in conditional statements, loops, and functions to execute code based on specific conditions.
Understanding boolean expressions, logical operators, and how JavaScript handles truthy and falsy values can significantly enhance your coding efficiency.
For a comprehensive exploration of boolean variables and their applications, TpointTech provides valuable resources and tutorials to help you master these essential concepts and improve your programming skills.
What is a Boolean in JavaScript?
A boolean is a primitive data type in JavaScript, meaning it holds a simple value—either true or false. These two values are often used in conditional logic, loops, and function returns to decide whether a certain block of code should be executed.
For example:
let isRaining = true;
if (isRaining) {
console.log("Don't forget your umbrella!");
} else {
console.log("Enjoy the sunshine!");
}
In this example, the isRaining variable is a boolean that determines which message is logged.
Creating Boolean Variables
You can create boolean variables in JavaScript by assigning the value true or false directly:
let isLoggedIn = false;
let hasPermission = true;
Alternatively, JavaScript provides several ways to evaluate expressions that result in boolean values. This includes comparisons, logical operations, and the use of truthy and falsy values.
Boolean Expressions
Boolean expressions evaluate to either true or false. Common examples include comparison operators like:
=== (strict equality)
!== (strict inequality)
> (greater than)
< (less than)
Example:
let age = 18;
let isAdult = age >= 18; // evaluates to true
console.log(isAdult); // true
In this case, isAdult will be true if age is 18 or more, and false otherwise.
Logical Operators
Boolean variables often use logical operators such as && (AND), || (OR), and ! (NOT) to build complex conditions.
For example:
let hasID = true;
let isOver18 = false;
let canEnter = hasID && isOver18;
console.log(canEnter); // false (because both conditions must be true)
In this case, canEnter will only be true if both hasID and isOver18 are true.
Truthy and Falsy Values
In JavaScript, non-boolean values can still behave like booleans when evaluated in a conditional statement. These values are known as "truthy" or "falsy" depending on whether they are treated as true or false.
Falsy values in JavaScript include:
false
0
"" (empty string)
null
undefined
NaN (Not a Number)
For example:
let user = null;
if (user) {
console.log("User exists.");
} else {
console.log("No user found.");
}
Since null is a falsy value, the else block is executed, and the message "No user found." is logged.
Truthy values, on the other hand, are all values that are not falsy. This includes non-zero numbers, non-empty strings, objects, and arrays. For example:
let name = "John";
if (name) {
console.log("Hello, " + name);
}
Since the string "John" is truthy, the message "Hello, John" is printed.
Boolean in Functions
Boolean variables are commonly returned by functions. For example, you might want to check if a number is even:
function isEven(number) {
return number % 2 === 0;
}
console.log(isEven(4)); // true
console.log(isEven(7)); // false
Here, the isEven function returns true if the number is divisible by 2 and false otherwise.
Conclusion
Mastering JavaScript Boolean Variables is crucial for effective programming, as they form the backbone of conditional logic and decision-making in your code.
Understanding how to use boolean expressions, logical operators, and the concepts of truthy and falsy values can greatly enhance your coding skills and help you write more efficient, readable code.
For further learning and detailed tutorials on JavaScript and other programming topics, TpointTech provides valuable resources and guides to deepen your knowledge and improve your development expertise. By leveraging these resources, you can confidently apply boolean logic in your JavaScript projects.
0 notes
Text
JAVA PROGRAMING
DICS Institute in Rohini offers a comprehensive and dynamic approach to learning Java programming, catering to a diverse range of students from beginners to advanced developers. This programming institute is recognized for its commitment to providing quality education, hands-on experience, and a supportive learning environment.
Overview of DICS Institute
DICS (Delhi Institute of Computer Science) has established itself as a leading educational institution in the field of IT training. With multiple branches across Delhi, including its prominent location in Rohini, DICS has been instrumental in shaping the careers of numerous aspiring programmers. The institute is known for its state-of-the-art facilities, experienced instructors, and a curriculum that aligns with industry standards.
Why Learn Java?
Java is one of the most popular programming languages globally, renowned for its versatility and robustness. It is widely used in various applications, from mobile app development to enterprise-level solutions. Learning Java not only enhances one's programming skills but also opens up numerous job opportunities in the tech industry. The language's object-oriented nature makes it easier for learners to grasp programming concepts, which can be applied to other languages as well.
Curriculum Highlights
DICS Institute offers a well-structured curriculum that covers both Core and Advanced Java. The courses are designed to provide students with a solid foundation in Java programming while also introducing them to advanced topics. Key components of the curriculum include:
Core Java
· Introduction to Java: Understanding Java's features and its comparison with other languages like C and C++.
· Object-Oriented Programming (OOP): Concepts such as classes, objects, inheritance, polymorphism, and encapsulation.
· Data Types and Operators: Learning about primitive and non-primitive data types, variable declarations, and operators.
· Control Flow Statements: Mastering conditional statements (if-else, switch) and loops (for, while, do-while).
· Exception Handling: Understanding how to manage errors and exceptions in Java applications.
· Java Collections Framework: Exploring data structures like lists, sets, maps, and their implementations.
Advanced Java
· Java Frameworks: Introduction to popular frameworks such as Spring and Hibernate, which are essential for building enterprise applications.
· Web Development: Learning about Servlets, JSP (JavaServer Pages), and building dynamic web applications.
· Database Connectivity: Understanding JDBC (Java Database Connectivity) for interacting with databases.
· Multithreading and Concurrency: Exploring thread management and synchronization in Java applications.
· Java for Big Data: An introduction to using Java in big data technologies, providing a glimpse into modern data processing.
Learning Experience
Hands-On Training
At DICS, the emphasis is on practical learning. Students engage in hands-on coding sessions where they apply theoretical knowledge to real-world projects. The institute's labs are equipped with the latest technology, allowing students to experiment and build their applications.
Experienced Instructors
The faculty at DICS comprises industry professionals with extensive experience in Java development. They bring real-world insights into the classroom, ensuring that students are not only learning concepts but also understanding their applications in the industry.
Flexible Learning Options
DICS offers flexible learning options to accommodate various schedules. Students can choose from full-time, part-time, and weekend classes, as well as online learning formats. This flexibility makes it easier for working professionals and students to pursue their education without compromising other commitments.
Community and Networking
DICS fosters a vibrant learning community where students can collaborate and network. The institute organizes coding competitions, hackathons, and tech meetups, providing students with opportunities to showcase their skills and connect with potential employers. This community aspect enhances the learning experience and encourages peer-to-peer support.
Placement Assistance
One of the standout features of DICS Institute is its dedicated placement cell. The institute has strong ties with various IT companies and regularly conducts placement drives, ensuring that students have access to job opportunities upon completing their courses. The placement cell also provides resume-building workshops and interview preparation sessions to help students succeed in their job search.
Conclusion
Choosing DICS Institute in Rohini for Java programming education is a strategic decision for anyone looking to build a career in software development. With its comprehensive curriculum, experienced instructors, hands-on training, and robust placement support, DICS stands out as a premier destination for aspiring Java developers. The institute not only equips students with technical skills but also prepares them for the challenges of the tech industry, making it an excellent choice for anyone serious about mastering Java programming .Embarking on a journey at DICS means stepping into a world of opportunities where students can transform their passion for coding into a successful career. Whether you aim to develop mobile applications, create enterprise solutions, or delve into big data, DICS provides the foundation and support needed to achieve your goals.
With a focus on personalized attention, DICS ensures that you receive the support and guidance you need throughout your training, helping you achieve your goals.By choosing DICS as your Java training institute in Rohini, you are making a strategic decision that can shape your future positively. Embrace the world of Java programming with DICS and unlock a world of opportunities in the thriving IT industry.
DICS boasts a modern infrastructure and facilities that support effective learning, ensuring a conducive environment for your Java programming journey.
Java is a versatile and widely used programming language that forms the foundation of many applications and software systems. Learning Java at DICS in Rohini offers several advantages:
0 notes
Text

Olibr
Our mission is to empower businesses achieve their goals by overcoming the challenge of recruiting skilled resources for their dream projects. Olibr believes that no business should fall behind due to a dearth of good resources and no talent should miss the opportunity to work with top businesses in the world due to geographical limitations.We are focused on the success of our clients and help them achieve their goals by offering customized resources to work on their projects. On the other hand, we generate fair and secure job opportunities for skilled professionals who are eager and ready to work with top, innovative businesses.
non primitive data types in javascript
1 note
·
View note
Text
Why is the United States more religious (more outspokenly Christian) than other First World countries? via /r/atheism
Why is the United States more religious (more outspokenly Christian) than other First World countries? As someone who was born and raised in the Lower Mainland of the province of British Columbia, Canada, I am often shocked by how outspokenly Christian the United States is. Not to get too deep into my backstory but religion just never played a role in my upbringing. Sure, when I was in primary school, I saw Muslim girls with their hijabs, and Sikh boys with their turbans, but they never bothered me or preached their religion to others, we just played together as kids. The closest religion I had while growing up was Buddhism because of my grandma. Not to get too specific but I am mixed race, my father is white while my mom is Khmer (Cambodia). But we only occasionally went to the Buddhist pagoda (temple) but that didn't play a factor as neither of my parents is religious. Of course, you do see religious houses of worship like churches, mosques, and Sikh temples in BC and other Canadian provinces, but they never bothered me and aren't constantly preaching. In fact, census data shows that BC has the largest portion of non-religious people and is the most secular province in Canada. https://bc.ctvnews.ca/b-c-has-canada-s-largest-proportion-of-non-religious-residents-poll-finds-1.6680547 https://www.cbc.ca/news/canada/british-columbia/bc-most-secular-province-1.6633935 https://www.bchumanist.ca/census_2021 https://en.wikipedia.org/wiki/Irreligion_in_Canada With that being said, my father works in the US and we also have a house there. One of the first things I've noticed about staying in the US for a longer period of time (apart from the ugly, car-centric infrastructure. Sorry Seattle WA, but I need my SkyTrain! But urban planning is a topic for a different sub) is just how openly religious (Christian) people are. In BC Canada, none of our neighbours were openly religious, heck I don't even know if they were religious at all. And sure, we were never close to our neighbours in BC, but still. Religion, going to church, etc, was just never brought up. Contrast that to our neighbours in the US who are all openly Christian. Don't worry, none of our US neighbours are the reactionary Christian Nationalist types, they're liberals Christians who somehow believe that God and Christianity are supportive of LGBTQ+ people even though it ain't. And no amount of cherry-picking and "reinterpretation" will change the fact that the Bible is a collection of reactionary stories with outdated, primitive positions. While religion in the Western World is on the decline even in the US, I just want to know why the US is more openly religious compared to other Western countries? I know historically the US has been more religious than other first-world countries. Don't get me wrong, Canada does have its fair share of religious nutcases, but folks here seem to know not to take them seriously as they spew their nonsense. But as someone who was born and raised in one of the most secular provinces in Canada, I just find the religious preaching, Christian Nationalism, and generally openly identifying as Christian to be strange and unsettling. Submitted April 26, 2024 at 10:26PM by CreatureXXII (From Reddit https://ift.tt/6r3mNK7)
0 notes
Text
Mastering the Absence of Primitive Data in JavaScript with Power of Modern Programming
Introduction
In the ever-changing landscape of web development, JavaScript remains a cornerstone, driving dynamic and interactive content over the internet. The ability to handle non-primitive data types is a critical distinguishing factor between skilled JavaScript developers and novices. In this comprehensive book, we dig into the complexities of these advanced data types, allowing developers to realize their full potential.
Understanding non-primary data
What distinguishes non-primary data?
Primitive data types like integers, strings, and booleans serve as the essential building blocks of computer languages, but they have limitations. In contrast, non-primitive data types in JavaScript provide developers with greater flexibility and power. This includes objects, arrays, functions, and more, which facilitatesThe development of complex data structures and sophisticated operations.
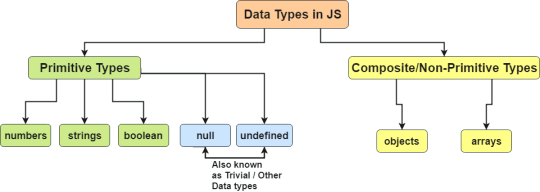
The Power of Objects in Creating Strong Structures
In JavaScript, objects allow developers to create complex and logical data representations. Objects make programming more scalable and manageable by combining associated data and functions. Consider the following illustration:
javascript
Copy the code: const user = { name: 'John Doe', age: 30, address: { city: 'Techville', country: 'CodeLand', }, getInfo() { return '${this.name} is ${this.age} years old.'; }, };
With this arrangement, accessing and changing user data is straightforward, promoting code readability and maintenance.
Arrays for dynamic data manipulation.
Arrays, another non-primitive data type, provide a flexible approach for handling lists of data. They provide a variety of built-in methods, which allow developers to modify and iterate through components.With efficiency. Here's an example:
javascript
Copy code: const fruits = ['apple', 'banana', 'orange']; fruits.push('grape'); // Adds 'grape' to the end of the array. const firstFruit = fruits[0]; // Returns the first element ('apple').
Using arrays, developers may effectively manage changing collections of data, increasing the versatility of their programs.
Functions: the foundations of dynamic code
Functions play an important role in the non-primitive data realm. They provide developers with the option to encapsulate functionality, promoting code reuse and maintenance. Consider the following example of a basic function:
JavaScript code: function greet(name) { return 'Hello, ${name}!'; }
var greeting = greet('World'); // return 'Hello, World!'
Functions allow developers to arrange their code in a modular fashion, making it more understandable and readily updated.
Harnessing non-primary data for elevated Efficacy optimization for data manipulation.
Using non-primitive data types goes beyond surface improvements; it has a real influence on the performance of your JavaScript code. Objects, arrays, and functions provide optimum resolutions for data manipulation, ensuring that your applications execute smoothly even when scalable.
Embracing Progressive Development Principles.
As web development improves, it becomes increasingly important to follow contemporary methods. Non-primitive data types integrate well with modern development paradigms, allowing developers to build durable, scalable, and maintainable programs.
Conclusion
Mastery of non-primitive data in JavaScript is more than just a talent; it opens the door to realizing the full potential of this flexible programming language. Using the power of objects, arrays, and functions, developers may improve their coding skills and create apps that Stand out in the highly competitive digital world.
if you want to know more visit this website analytic jobs.
0 notes