#non-sequential chapter 18
Explore tagged Tumblr posts
Text
Hey! i liked this episode. who knows when lol its been so long!
girl! you feel the awkwardness cuz those are your feelings! steve and bucky are fine. and they already know youre weird so they dont notice it. you feel that line starting to blur because in your heart, it is blurred! you did that! not bucky!
Non-Sequential [Ch. 18]
Pairing: Pre-Serum Steve Rogers/Steve Rogers x Reader
One night, Steve Rogers met a beautiful dame named Y/N. He hadn’t intended on letting her get away. But fate had other ideas. Y/N appeared and disappeared in his life so hauntingly that Steve started to wonder if she was an angel meant to watch over him.
Word Count: 3,200
Chapter 17

Steve waited patiently as he sat across from Y/N. Despite her throwing herself into his arms when she showed up at his door, she came to moments later and put that unbearable distance between them once again.
Steve adhered to Bucky’s warnings. Everything was now on Y/N’s terms. He wouldn’t touch her, wouldn’t crowd her personal space until she wanted him to and consented.
“I’m sorry,” Steve finally started the talking. “I should never have left you. I was scared. Scared that I was the reason you kept getting put into danger. I convinced myself that if I stayed away, you would be safer.”
Then he leaned forward. His body needed to be closer to her, but he had to respect her distance. “I don’t expect you to forgive me for it. I’ll wait for as long as it takes. Because I know that’s what I deserve.”
Y/N just stared into Steve’s baby blue eyes. It felt like minutes.
Keep reading
#non-sequential#non-sequential chapter 18#steve rogers series#steve rogers fic#steve rogers x reader#steve rogers reader insert#steve rogers angst#bucky barnes x you#bucky barnes x reader x steve rogers#bucky barnes x reader#marvel reader insert#steve rogers x reader x bucky barnes#steve rogers fluff#steve rogers x you#pre-serum!steve rogers#pre serum steve rogers#invisible anonymous monsters#captain america reader insert#captain america x reader#pre serum!steve rogers x reader#invisibleanonymousmonsters
638 notes
·
View notes
Note
I just wanted to say: I love your art and especially your banner rn by talos! also your fic as well thank you for creating everything that you do for people, it’s awesome!
Second: what’s something that you’ve been chewing on lately, story wise? What character conflict, or plot point can you tell me about (that doesn’t spoil too much of course)? I wanna hear your thoughts about the characters you write and your head-cannons on them too! Just spit some word vomit at me!
Thank you!
My current banner art is actually a crop of the first paired piece I ever did to go with my Deathly Weapons fic. (Specifically Chapter 11, which I still have a soft spot for since it’s one of earliest chapters that really let me lean into scratching the thing-I-haven’t-seen-too-often-in-fanfic itch.)
I recently got my hands on a discounted Wacom (my digital art process got tanked a few years ago when my poor art-compatible hybrid tablet-laptop was tragically taken from us by a cracked motherboard) so I’m looking forward to getting into a faster art workflow again and maybe putting some new pieces out more easily. I’d like to do more comic art pieces for the Chapter 18 mission, and there’s a silly little concept drawing for the planned Mission 5 that might be new-blog-banner material if it turns out nicely. We’ll have to see how that goes.
As for what I’ve been chewing on story-wise lately… I’ve sort of been all over the place. I’m still on burnout recovery so I’ve been letting myself move non-sequentially, working on the bits my brain feels like focussing on rather than trying to force creativity where the juice isn’t flowing. (One of the things about being my type of writing-nerd is that “self-indulgent” for me means a story with plenty of material to analyse, which is very fun as a reader but has created a lot of work for myself as the writer. As mentioned in another post, I have a full-blown TV-show-style story-bible for this one.)
Recently, my authorial ping-pong-ing has been going into a fair bit of spoiler territory. There are some chunks of the Act III endgame plan which are underdeveloped in the specifics of what the big-boss bad-guys’ plan is, whether I want to involve the Anti-Ecto Acts more, and the logistics of both the counter-strategy our heroes are planning to use and how to make its more action-heavy parts look cool in writing. When I’m not doing that I’ve been focussing a lot on the upcoming Wally-centric chapters, which are a set I’ve been wanting to keep schtum about since there’s a small potential spoiler mixed in and I don’t want to risk giving the game up or pre-setting people’s expectations before they have a chance to blind read (even if a few people have already made some close guesses in the comments). It puts me in a bit of an odd-spot right now because the chapters I’m drafting are an immediate spoiler, the later sections I’m working on are a major spoiler and there’s a good chance that a lot of the character stuff going on in the middle won’t make a whole lot of coherent sense without prior context because of how I like to layer foreshadowing/development.
That said, Wally-centric chapters mean Wally thoughts, and of those I have plenty to share:
First of all, I want to establish that I really do like Wally as a character. The DW chapter set comprising Flashpoints through to Equilibrium is going to explore and develop some of his flaws and insecurities, which means he isn’t going to be looking his best, but it’s not meant to be a Ron The Death Eater situation. He’s just a complex person, and taking him warts and all means sometimes you have to get up close and personal on the warts.
Something that I’m maybe a bit over-conscious of when reviewing my DW story notes is worrying about letting Wally slide into just being punching-bag joke-fodder. Wally is quippy, irreverent, a little tactless and prone to being a bit of an impulsive goober who sometimes gets possessed by teenage boner-brain, which makes him easy to fall back on as a default source of incidental levity (whether cracking the joke or being the punchline). Because I’m now writing an 8-character ensemble where most non-focal characters only get a few lines per conversation, it’s easy for characters to slide into being defined by their strongest surface level trait(s)… and something I worry about with Wally is that his availability as a source of jokes runs the risk of Flanderisation into a disposable Scrappy/ Flirty Comic Relief, which isn’t his character. Wally is actually really important – not just for his scientific book-smarts but for his perceptiveness, earnestness and ability to function as one of the emotional barometers for the squad – so I always have it in the back of my mind to make sure I include enough moments that actually demonstrate those qualities and the other characters’ appreciation of them/ their friendship, so that it counterbalances the more light-hearted goofery.
I think he’s walking the same tightrope as Sokka from Avatar: the Last Airbender – yes, he tends to take the L more often than the others for comedy purposes and sometimes he gets stuck with supremely dumb side-plots for the sake of tonal balance, but to claim that it’s the entirety of his characterisation really misses the point by a wide mile.
On that note, I actually really like the decision YJ!Animated decided to go with in its first and only season (ahem) in giving Wally a normal and functional family background. I know that’s not the typical background for his comics counterparts (and no shade on other fan-writers who want to write AUs exploring the abuse dynamic, those are really interesting stories) but I think it was a smart deviation for the purposes of a large ensemble, and offered a fair bit of potential for cast-balance. It lets him serve an important role as the normal one – not only as an easy window into what the current lives of ordinary middle-class civilians look like (which is good because ordinary people are who our heroes are donning the masks to protect) but also as a touch-stone for the others, most of whom either come from different cultures or from very atypical backgrounds. Even if we discount the Impure Atlantean with military training, the ostracised White Martian and the Half-Alien clone-weapon, the other members of this line-up are an orphaned circus acrobat adopted by a billionaire, a girl from a dangerously dysfunctional criminal household where she was forced to fight her sibling, and a fledgling sorceress raised by an overprotective single Dad. The others might intellectually understand what a “normal” childhood and family look like but they don’t necessarily know it as intuitively and intimately as Wally does. That normality gives Wally the potential to be a more stable foundation for the others, a source of emotional contrast and of a necessary wholesome mundanity. That is a good thing for the Team to have. I think it also speaks volumes to the heart of his character. For this Wally, the Flash and heroism weren’t an escape from a bad personal situation. His life was actually pretty comfy and privileged - he didn’t experience a brutal wakeup to the injustices of the world or some other personal call to action. This is a Wally who opted into the game because he loves the players and sincerely believes in their values and mission. And while that might mean he has a more romanticised idea of what heroism entails – and will probably face some rough shocks down the line as that rosy vision runs into those more brutal realities – it also means he brings a sincere hopefulness to the job that is less hardened than a lot of his roughed-up, pre-jaded peers. Underneath the teen sarcasm and surface-level lancer/smart-guy traits, this Wally has as much power to be a stealth-Heart as any of his Flash!counterparts.
Something else I find interesting when using Wally is how a lot of his strengths and flaws feed into each other – and I think this alternate backstory is part of it. For all of his good heart Wally can come off as insensitive, and I think some of that could be read as a product of living a more charmed life. I think he’s susceptible to a thing that a lot of real people do – universalising their own personal experience as the default – and that while he is canonically a geek and somewhat genre-savvy about hero cliches, he’s a geek about in-universe media so he probably doesn’t think to apply those tropes to “real people” like himself or his colleagues. While this Wally is a skeptic, he’s not a cynic, and I think he might forget how much of an outlier he is in a world where things like living parents and loving parents are often mutually exclusive. He’s smart enough to connect dots but there’s a little blind-spot where he simply might not think to until one of the others jabs an elbow into his ribs, because his default view on humanity is in some ways a little kinder than typical due to that small but still significant amount of privilege.
At the same time, Wally is also someone who has probably run into (or watched his mentor run into) a lamp-post at high-speed at least once in his career. He contains multitudes and among those multitudes is an endless capacity for some absolute Looney-Tunes nonsense, which the world is 100% better off for having.
I love him, your honour.
#striking the balance between silly and genuine with Wally is a challenge but you gotta have both#young justice: deathly weapons#YJ:DW Meta#young justice#young justice (animated)#Young Justice Season 1#Wally West#Kid Flash#DC Comics#potatoeofwisdom#3WD Answers
8 notes
·
View notes
Text
Chocolate Box 2021 exchange letter below.
Hi, dear chocolatier! Thanks so much for creating for me. For fic, I’m good with whatever rating you want to write and any tense/person/structure. I’m also requesting art for everything besides OW. I’ve copied my signup below with a DNW list for each fandom, and those are followed by my general art and fic likes lists.
——-
Dragon Age: (fic, art) Aveline Vallen/Cassandra Pentaghast (Dragon Age) Aveline Vallen/Female Hawke (Dragon Age) Cassandra Pentaghast/Female Inquisitor (Dragon Age) Cassandra Pentaghast/Leliana (Dragon Age) Cassandra Pentaghast & Myrna (Dragon Age) Dagna/Sera (Dragon Age) Isabela/Leliana (Dragon Age) Josephine Montilyet/Leliana (Dragon Age) Leliana/Morrigan (Dragon Age)
For all the / ships I requested, I would be very happy with anything inspired by the likes lists below. Cassandra/Leliana, Josephine/Leliana, Leliana/Morrigan: I’m forever interested in all their history we don’t see as well as how they might interact when the Inquisitor or Warden isn’t around. Cassandra/Inquisitor, Aveline/Hawke: I’m good with any variant of female player character and will always love flirting and tension/confusion happily resolved, or facing things together, or just cute/romantic moments. Aveline/Cassandra, Dagna/Sera, Leliana/Isabela: show me how they might meet for the first or second or third time and spark something?
For Cassandra & Myrna (of the Mourn Watch): “Down Among the Dead Men” was my favorite Tevinter Nights story and I’m fascinated with Nevarra and the Grand Necropolis as described there. Have these two met before in the past? Do they have to work together on something for the Inquisition or post-DAI? Since I read TN I’ve wanted a fic where they interact (and preferably get along eventually).
I would also love art of any of these pairings! See general art likes list below.
DNW: setting AUs (except for art), background male player characters, pregnancy, non-canon major character death, unhappy endings, daddy/mommy kink, noncon
——
Crossover: (fic, art) Cassandra Pentaghast (Dragon Age)/Kassandra (Assassin’s Creed Odyssey)
I still feel like this should happen. Magic or basically magical AC tech or in recurring dreams or however you want to handwave transportation between universes, I would just like to see them in the same place and maybe breaking some things together. (alternatively: I did art of them arm-wrestling one time and if someone wants to write me that fic I would love it.)
Also more art! Fighting back to back? Kassandra flirting with Cassandra? Wearing clothes from each other’s world? A Greek-vase-style pastiche?
See general fic and art likes below if you want more ideas.
DNW: AUs other than the canon settings, pregnancy, non-canon major character death, unhappy endings, daddy/mommy kink, noncon
——
Emelan - Tamora Pierce: (fic, art) Dedicate Lark/Dedicate Rosethorn
I love the four kids, but I love Lark and Rosethorn the most. (Note: I’ve only read up to Shatterglass as of now, but I don’t mind references to later books if you want to set something later.)
A few fic ideas, feel free to mix up or use anything else from my general likes list: - An adventure by themselves without their students? Or an attempted romantic outing that turns into one? - Writing to each other when one is away? (Rosethorn travels a lot; has Lark ever gone somewhere and left her to manage Discipline?) - Observing traditions and the turn of the year at Winding Circle, from their POVs? - Ways they might use their magic together or experimenting with that?
I would also love any art you want to do of them: see the general art likes below.
DNW: setting AUs (except for art), pregnancy, non-canon major character death, unhappy endings, daddy/mommy kink, noncon
——
The Priory of the Orange Tree - Samantha Shannon: (fic, art) Sabran Berethnet/Eadaz du Zāla uq-Nāra (The Priory of the Orange Tree - Samantha Shannon)
Reusing some of my Yuletide fic prompts, feel free to mix these or use things from my likes list: - A missing scene from when their relationship was secret, before Ead left the first time? - Sabran’s experience of one of the times Ead was hurt and recovered? - I’m always here for long-distance pining and letter-writing. - Post-canon reunions, whether it’s Ead visiting Inys, or Sabran finding ways to meet her elsewhere, or Sabran carrying out her plan to abdicate. I would love exploration of the other courts and lands in the book, especially Yscalin rebuilding from the draconic takeover, and the Priory. - I’m still curious about whether it’s possible for Sabran to learn either type of magic and whether she would explore that, and whether there might be other trees.
I would love art as well! Any canon scene illustrated (the rose under Sabran’s pillow? the bath? the candle dance scene?), or just any art of them you want to do. General art likes below.
DNW: setting AUs (except for art), non-canon pregnancy, non-canon major character death, daddy/mommy kink, noncon
——
Original Work: (fic) Female Adventurer in Need of a Challenge/Lady Stuck in Tower of Ridiculous Traps (Original Work) Female Inventor of Ridiculous Traps/Female Master Thief (Original Work) Female Avant-Garde Artist/Scandalous Demimonde Actress (Original Work) Female Palace Cook/Female Royal Taster (Original Work) Female Paladin/Incarnation of Her Goddess (Original Work) Female Knight on Noble Quest/Witch Who's Far Too Distracting (Original Work) Brave but Stubborn Female Knight/Famous Female Bard Who Has a Crush on Her (Original Work) Dethroned and Dishonored Queen/Lone Loyal Female Knight (Original Work) Female Knight Who Loves Baths/Female Sorceress Who Loves Baths (Original Work) Female Knight Who Loves Baths/Female Water or Hotspring Spirit Who Loves Knights (Original Work) Wandering Lady Knight/Her Pining Female Friend She Writes Letters To (Original Work)
I nominated:
Female Adventurer in Need of a Challenge/Lady Stuck in Tower of Ridiculous Traps: I was imagining the kinds of elaborate traps you find in D&D manuals, but other types also work! I just like the idea of bonding through solving bizarre dangerous puzzles from opposite sides of a barrier.
Female Inventor of Ridiculous Traps/Female Master Thief: Professional rivals to lovers? Longtime couple who collaborate? (Bonus idea: prequel to the first prompt?)
Female Palace Cook/Female Royal Taster: I like the idea of one falling for or trying to seduce the other through food creations, under the noses of the royalty. Maybe the taster is also a bodyguard, or just another servant with a risky job?
Female Avant-Garde Artist/Scandalous Demimonde Actress: I’d be here for this whether you want to set it in a real historical period or a fantasy/SF world. Too many feelings and sublimating them through art? Modeling turning into more? A secret relationship, or a volatile on and off thing? I could also see this as a found documents or research notes type of story (or something like 5 times = 5 works in an exhibition?)
Female Paladin/Incarnation of Her Goddess: A dramatic h/c situation, or a reward for faithful service? Or maybe they have a comfortable old-married type of relationship? I could be into any of these.
Female Knight on Noble Quest/Witch Who's Far Too Distracting: Kind of the opposite of the above. They just keep running into each other and catch feelings? Or the witch wants to interfere and ends up helping? Or the quest is actually a bad idea and the witch saves her life?
I didn’t nominate but would delightedly read any take on these (all the lady knights edition): Brave but Stubborn Female Knight/Famous Female Bard Who Has a Crush on Her Dethroned and Dishonored Queen/Lone Loyal Female Knight Female Knight Who Loves Baths/Female Sorceress Who Loves Baths Female Knight Who Loves Baths/Female Water or Hotspring Spirit Who Loves Knights Wandering Lady Knight/Her Pining Female Friend She Writes Letters To
See the long list of general likes below if you want more ideas.
DNW: unhappy endings, death of requested characters, underage sex (<18), daddy/mommy kink, incest, noncon, a/b/o
——
General fanart likes:
I draw it myself, and I don’t really have style preferences for fanart; I’m interested in however you interpret my request in your own style!
- If one of my fic prompts or my likes below suggests something (non-explicit) you want to draw (whether one scene or sequential), I’d love to see that. I always like to see characters doing things they’re good at or looking formidable or happy. And for shippy art, I am always here for handholding, hand kisses, regular kisses, cuddling, and/or other romantic moments in contexts that make sense for the characters.
- Dressing the characters up or down is also fun. Fancy clothing or armor, things they might wear that we don’t see in canon, or illustrating what they do wear in canon if it’s a book. Partial undressing and dishevelment. Different historical AU looks (as an exception to my setting AUs DNW).
- I’d also be into a piece that’s more of a character study expressing something about them through formal visual elements and symbolism (as opposed to a narrative scene).
- If emulating other art styles is fun for you, I’d totally enjoy any kind of famous artist/historical style pastiche. Or, my love of in-universe documents and worldbuilding definitely extends to art, so something like an in-world manuscript page or notes/doodles/sketches by a character or an in-world portrait of them would make me quite happy.
——
General fic likes
If something’s not on this list, that doesn’t necessarily mean I don’t like it, but I enjoy these things pretty reliably. Take from it and mix these up as you wish.
for both gen and shipfic: Relationships among women, complex and powerful female characters, adult characters with some level of life experience Casefic if the characters do cases or missions: anything like another episode or chapter from the canon Lighthearted slice of life/ day-in-the-life stories when the canon focus is more on big dramatic events Epistolary or found-documents stories, and other unconventional story structures Time loop stories, Rashomon-style stories, and other sets of variations on a theme (including “five times” fic) Canon divergence AUs Worldbuilding/exploring places and times we don’t see much in canon; in-universe mythologies, stories, songs, plays, etc.; holidays, personal or cultural traditions, celebrations People or events from characters’ past resurfacing to complicate things Magical or scientific accidents or anomalies making weird things happen Heists, rescues/jailbreaks, investigating mysteries big or small Court plotting, dealing with complex etiquette/social rules, intrigue, spying, disguises and fake identities Road or sea or space trips, wilderness survival situations, exploring ruins/haunted places/caves/dungeons/etc. Sparring, duels, tournaments, competitions whether serious or not Making things for each other, whether it’s art or music or crafting or food or magic or whatever, and giving gifts Competence porn/demonstrating how good they are at what they do (but perhaps being awkward or lost in other contexts) Learning or teaching others new skills, or trying to Temporarily caring for animals or babies/children when they’re not used to it
for shipfic (pre-relationship, get-together, and established-relationship stories are all interesting to me if I like the ship) Everything above plus: Longtime friends, partners in arms or work or crime, old friends or former lovers meeting again, old enemies who have to admit they like each other, rivals who respect each other … to lovers Long-term established relationships where they know each other better than anyone Cute/playful moments, escalating flirtations whether awkward or skillful, good-natured teasing, surprising each other, discovering new things about each other, trying to impress each other, distracting each other consciously or not Giddy crushes, pining that’s eventually happily resolved, angst with happy endings Having a lot of feelings and not knowing what to do with them, repression, extended UST, slow burn, emotional romantic revelations Hurt/comfort, fighting beside each other, disproportionate reactions to the other being hurt or possibly hurt, facing external threats together, rescuing each other, tending each other Loyalty and devotion, us against the world, bodyguarding, protectiveness, love conflicting with other loyalties, noble self-denial and sacrifice, courtly love Being inspired by the other to create, or achieving things for the other’s sake or in their service, whether secretly or openly Forced-intimacy-by-circumstance tropes like only-one-bed, huddling for warmth, fake dating, marriage of convenience, handcuffed together, dreamsharing/psychic bonds Ascetic/hedonist or repressed/libertine or inexperienced/more experienced dynamics “The grumpy one is soft for the sunshine one,” or prickly/stoic/intimidating/jaded characters softening for a particular person, or allowing themselves to have fun with them Secret relationships as a source of angst and/or for the excitement of sneaking around (though I prefer infidelity not be the reason, unless it’s a forced/political marriage situation) Dancing, whether it’s formal dancing with sexual tension or meaningful romantic dancing or getting uninhibited on a dance floor Meaningful handholding Language of flowers/fans/other symbolic communication and private codes Bathing/dressing/doing hair/other physical caretaking, watching each other sleep, holding each other for comfort, having a hard time not touching Reading/storytelling/singing to each other Reunions after separation, or stealing moments away from everything to be together
for sex scenes: cuddling, kissing, laughing, tasting, eroticized hands and voices, clothed/semi-clothed sex, complicated undressing, talking whether emotional or joking or dirty, asking for things, curiosity/discovery, playfulness/inventiveness, eagerness/desperation, being overwhelmed by feelings, having to keep silent or hold still, interruptions and delayed gratification and intentional drawing things out, body worship, sex against walls, informal mild kink (e.g., tying up, holding down, blindfolding, taking direction, honor bondage, scratching/marking, tearing clothes, mutual roughness), sexy letter writing, one fantasizing about the other, decadence and sensory/sensual details, voyeurism/exhibitionism if it’s IC, writing/painting on skin, sex pollen, magical/ritual/magic-enhanced sex
1 note
·
View note
Text
[Event & Scenario] “Episode of Avalon #1.5 Shattered Twin Crystals” START
Chapter 2 of Season 1.5! Fairy April is focusing on producing new songs after joining Avalon. Suddenly, there's some news about Crystal Cross and Judas Kiss...? Join Fairy April and save Crystal Cross from this crisis!
Details
▼ Release Date: 2018/01/15 (Mon) 17:00JST ~ onwards
Part 1.5 of the “Episode of Avalon #1.5 Shattered Twin Crystals” will start! Chapter 2 will focus on Fairy April.
▼ Access Condition
Must clear the final chapter in “Episode of Avalon #1.5 Voyager of the New World.”
How To Participate
You can access Part 1.5 from the banner on the home screen as long as the condition of clearing the final chapter in “Episode of Avalon #1.5 Voyager of the New World” has been satisfied.
※ Although there is no deadline, you may only receive the Clear Reward once.

How To Play

Get “Crystals” by playing songs from different Areas listed in the Event Page. Choose the Area you want to play in and either clear the story and/or win the Duel Gig of each stage to proceed to the next stage.

You can exchange the “Crystals” for the limited edition reward card via the Shop’s “Item Exchange” section. [more info.]
You can access the event scenarios via the new section, “Episode Of Avalon” from the Stories Tab.
Event Stage Schedule
The Area Stages for “Episode of Avalon #1.5 Shattered Twin Crystals” will be released sequentially from 2017/12/30(Sat) 00:00 JST. The new stages will be released at a schedule:
01/15(Mon) 17:00~・Shattered Crystal 01/17(Wed) 00:00~・Reason 01/19(Fri) 00:00~・Brothers 01/21(Sun) 00:00~・Regret 01/23(Tue) 00:00~・Lost Dream 01/25(Thu) 00:00~・Before the Storm 01/27(Sat) 00:00~・Truth 01/29(Mon) 00:00~・Epilogue
Past Event Scenario Limited Time Rerun
Scenarios of the events leading up to the scenario for Part 1.5 will have a re-run for a limited time only. Unopened scenarios will be available for reading during the following period:
▼ Duration: 2018/01/15 (Mon) 17:00 JST ~ 2018/01/30 (Mon) 12:59 JST
※ You can access the event scenarios from the “Story” tab → “Event Scenario” but will not be able to receive any reward upon clearing.
The target Event Scenario are as follows:
Advent of the Quattro Virtuoso GIGS ー Dante of the Purgatory
Anniversary GIGS ー Dreamin’ (untranslated)
On Board The Merry Christmas GIGS ー Dante is Coming To Town!

Event Reward Card
SR: Misato Toudou [The State of Loneliness]

Event Strategy
Using Fairy April members’ cards in Bands to use for LIVEs will improve overall performance.

“Shattered Twin Crystals” Limited Rare Gacha (Daily Rotation)

Duration: 2018/01/15(Mon) 17:00JST ~ 2018/01/31(Wed) 12:59JST
Line-up: EXR Yuu, EXR Show, SR Makoto Kurusu, SR Yukiho
※ SR Kurusu Makoto and SR Yukiho will be available throughout the duration of the gacha.
→ See here to read more on EXR Rarity
The gacha can use both Free and Paid Medals
It is possible to pull regular cards other than the Event limited gacha cards.
At least 1 SR or above card is guaranteed for every 10-pull
Signed cards will be discharged at a certain probability. Signs will only appear for SR cards and above and will be treated the same as non-signed, having the same stat and effects. You can admire the sign in various places.
Event limited cards might reappear during future events/campaigns.
“Shattered Twin Crystals”Rare Gacha Schedule
YUU ・1/15, 1/17, 1/19, 1/21, 1/23, 1/25, 1/27, 1/29, 1/31 SHOW ・1/16, 1/18, 1/20, 1/22, 1/24, 1/26, 1/28, 1/30
※ Please take note that the pick-up date will change at a daily basis
Featured New Cards
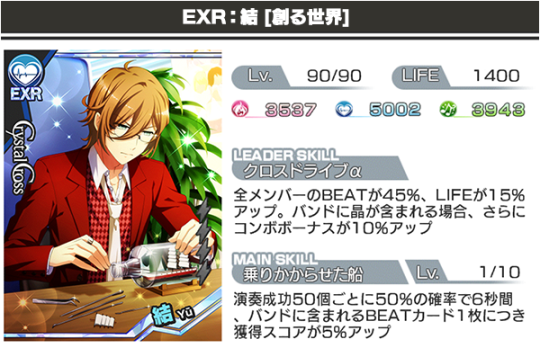
SSR Yuu [Create A World] Leader Skill: [Cross Drive α] Boosting all Member’s BEAT by 45% and LIFE by 15%. Additional 10% COMBO BONUS if a Show card is in the band. Main Skill: [A Ship About To Set Sail] 50% chance of activation upon 50 successful taps, increasing score by 5% for each BEAT card included in the band for 6 seconds.

“Forever You” Vocals: Tsubasa Yonaga (Yuu) Lyrics, Composition, Arrangement: Eiji Kawai

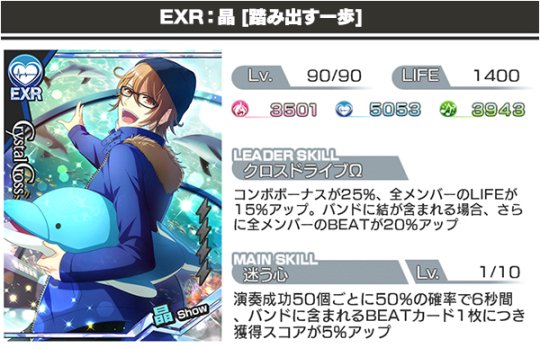
SSR Show [One Step Forward] Leader Skill: [Cross Drive Ω] Boosting COMBO BONUS by 45% and All member’s LIFE by 15%. Boosting all member’s BEAT by 20% if a Yuu card is in the band. Main Skill: [Wavering Heart] 50% chance of activation upon 50 successful taps, increasing score by 5% for each BEAT card included in the band for 6 seconds.

“Forever You” Vocals: Ayumu Murase (Show) Lyrics: Masamichi Nagai Composition, Arrangement: Kazuya Nishioka

SR Makoto Kurusu [Winter Gust] Leader Skill: [BEAT UP] All Member’s BEAT boosted by 30% Main Skill: [A Certain Winter’s Incident] 20% chance of activation upon 15 successful taps, boosting combo bonus by 16% for 4 seconds.

SR Yukiho [Snowflakes] Leader Skill: [ALL UP] All Member’s GROOVE/BEAT/MELODY boosted by 25% Main Skill: [救愛救愛Classics*] 20% chance of activation upon 15 successful taps, boosting combo bonus by 16% for 4 seconds.

※ Cards from this gacha are will have a max level of 90 for SSR and 75 for SR once Break.
You can check the in-game gacha/event page for more info.
*Yukiho’s card skill shall be amended as soon as I figure out what it means (rofl) If you have ideas, throw them at me.
#event : news#event : guide#band yarouze#band yarouze!#banyaro#Episode of Avalon 1.5 Shattered Twin Crystals#admin : pk5u
13 notes
·
View notes
Note
1, 3, 9, 10, and 18.
Hey there @silverwindsblog!
1) Is there a story you’re holding off on writing for some reason?
At this very moment, not really. I’m pretty focused on Vices right now. I guess other chapters to add onto my non-sequential future fic (Atem and Tea raise their daughter) “Korra” might count, and I have most of them saved as small drafts, but I’d rather finish my current project first.
3) What order do you write in? Front to back? Chronological? Favorite scenes first? Something else?
I guess it depends! I’ve written quite a few stories and had approached each one a little differently, though all but a few of them started as a basic chicken-scratch outline. The shorter ones I’m usually able to plunk out chronologically no problem. For the longer/deeper ones, most of the time I actually just write the scenes I have the clearest and most developed vision of, and they’re pretty much always out of order. I started using placeholders a few years ago, which is one of the best tools to use if that’s how you write. Not only did it encourage me to actually finish a story, but that particular order allows me to go back to those placeholders and better elaborate the content I’m filling in there, especially when the story is more or less mapped out (all my incomplete stories are an example of me NOT doing this and then giving up). For Vices, I actually wrote the first three chapters (Part I & II plus the interlude between them) as one single large chunk, and later sectioned it off where I thought was appropriate, and spent the turnaround time editing the next “section” as the next chapter. It helped the story flow a little more seamlessly. I wish I could do that again for the forthcoming chapters, but everyone would be waiting probably half a year for the next part to come out!
9) What, if anything, do you do for inspiration?
Consuming media helps a lot. Then diving headfirst into the rabbit hole and getting super nerdy analytical about each thing I read, listen to, or watch. Researching anything that fascinates me keeps my brain juices flowing, and ideas always pop up based on the knowledge I gain. I also like observing social behaviors of people around me (yay people watching!), and connecting them to characters I write or re-characterize. I’ve been meaning to do more creative writing exercises, like the stream-of-consciousness timed writing thing or just picking random prompts (or have people pick them for me!). I have done it before, but I need to do it more regularly.
10) Write in silence or with background noise? With people or alone?
When outlining, writing a light or uneventful scene, I like a little TV on in the background. But if I’m in refinement stage, or writing a heavy scene that requires impeccable execution, all noise and distractions are OFF. I have to be completely immersed in my world to be able to do it, to the point where sometimes I don’t even hear my boyfriend talking to me. Which answers the next question: alone. Definitely alone. So when my boyfriend is around and home, I am basically not writing.
18) Were there any works you read that affected you so much that it influenced your writing style? What were they?
This is, admittedly, a hard question for me to answer. I think my style is influenced by many things, spanning from books to TV to social media content, even other fanfiction works I like. But I am usually not conscious of how I am influenced by these things, just that it happens. Sorry for the lame answer! As far as storycraft, I draw from books like Brave New World, the Hunger Games trilogy, and anything by Kurt Vonnegut (even the small amount of Stephen King I was able to get through). TV shows include Game of Thrones and Handmaid’s Tale. A lot of my humor stems from shows like Parks and Recreation, It’s Always Sunny in Philadelphia, and, more recently, Peep Show.
Thanks for the ask!
xo ALG
1 note
·
View note
Text
My Last Argument
This is my final argument against backsliding. In this chapter you will see in very real terms the folly of backsliding. You will hear the testimonies of real Christians who made it to the very end. You will also hear the last statements of the backslidden and lost souls, and what they said as they approached the gates of Hell. You will see how really terrible backsliding is.
In our walk with God there is a certain line that we must not cross. There is a point of no return. I have heard believers say that they will backslide, but will come back to the Lord after some time. They forget that there may be a point of no return.
The Point of No Return
We will all stand before the presence of God to account for our lives. When that time comes and you are ushered into the presence of God, what will you say?
Will you be ready? Will you have done what God wanted you to do?
A Christian brother was committing fornication when he heard a loud blast. He thought it was the sound of the trumpet heralding the return of Christ. So he jumped out of the bed, but was not caught up to heaven. He was so worried, because he thought that he had been left behind at the rapture. This anxious Christian was overreacting to the honk of a big bus. A backslider lives in fear and uncertainty.
God Wants to Reason with You
Come now, and let us REASON together…
Isaiah 1:18
God is a rational Being, and He wants to reason with you.
Many people think that when you deal with spiritual things you must put aside all reason and stop thinking rationally. But the Bible records that God wants us to reason with Him. If God tells you to reason, then He must be a God who thinks logically and sequentially!
I am going to reason with you and argue with you about backsliding. You could call it “Arguments for and against backsliding”.
I will show you certain people who were happy and full of joy as they entered into the rest of God. These were Christians who served the Lord and did not fall away.
On the other hand, I will show you what some dying backsliders said as they left this earth. These testimonies alone should make you decide never, never, never to backslide.
The Saints
First, I want you to notice what Bible saints had to say when they were moving from this world to the next.
Apostle Paul
Apostle Paul was in prison when he knew that his time of death was near. He said, "For to me…to die is gain." In other words he was happy to be dying. How many people are happy to die? If you are confident of your relationship with God you will not fear death.
Jacob
When the Patriarch Jacob was dying in Genesis 49:33, the Bible declares that after commanding his sons, "…He gathered up his feet into the bed, and yielded up the ghost..."
What a way to go! He knew that he was going. He had time to instruct his children with confidence. After commanding his sons, he gathered his feet onto the bed and died. You see, the death of the righteous is very different from the death of the wicked. Balaam the prophet said;
...Let me die the death of the righteous...
Numbers 23:10
Now let's study how some ordinary people, after living a life without backsliding went on happily to be with the Lord.
Ignatius
Ignatius lived in 100 AD. He was the Bishop of Antioch, and a personal disciple of John the Apostle. He was sentenced to death, and as he was dying, his last words were, "I thank thee, oh God, that thou hast honoured me with thy Word, praise God!"
These were the last words of a man who was sentenced to death by burning at the stake. Some other people would have been screaming, defaecating and salivating. But this man died praising God!
Father Polycarp
Father Polycarp, another disciple of John lived during the reign of Emperor Nero. He was also sentenced to death. He was taken to court, and there, he was given an option to either denounce Jesus or be burnt to death. Polycarp suffered much for Christ's sake. The Roman Proconsul commanded him to swear allegiance to Ceasar, saying, "Swear, and I will set thee at liberty; reproach Christ." How courageous and magnificent was Polycarp's reply!
He said, "Eighty and six years have I now served Christ, and He has never done me the least wrong. How, then, can I blaspheme my King and my Saviour?"
Further efforts to make him deny his Lord failed and Polycarp was condemned to be burned at the stake. When the day came for him to be burned alive, those responsible for the burning wanted to nail him to the stake, but he protested: "Let me alone as I am: for He who has given me strength to endure the fire, will also enable me, without your securing me by nails, to stand without moving in the pile."
Finally he exclaimed, "Oh! Lord, Father of the Beloved Son Jesus Christ. I thank thee that thou has allotted me a place among the Martyrs."
Augustus Montague Toplady
Augustus Montague Toplady (1710-1778), will ever be famous as the author of one of the most evangelical hymns of the Eighteenth Century, "Rock of Ages," which was first published in 1776. During his final illness, Toplady was greatly supported by the consolations of the Gospel.
Near his last, awaking from a sleep, he said:
"Oh, what delights! Who can fathom the joy of the third Heaven? The sky is clear, there is no cloud. Come, Lord Jesus, come quickly!"
He died saying, "No mortal man can live after the glories which God has manifested to my soul."
And with those words he went to be with the Lord.
William Shakespeare
William Shakespeare (1564-1616), the world's outstanding figure in literature, of whose life, times and works a whole library of books has been written, lived near his Bible as the numerous quotations from it in his plays and dramas prove.
A Famous Man Knew the Lord
His end came when he was only 52 years old. His last will that was written in the year he died revealed his faith in God.
"I commend my soul into the hands of God my Creator, hoping and assuredly believing, through the only merits of Jesus Christ my Saviour, to be made partaker of life everlasting, and my body to the earth, whereof it is made."
Matthew Henry
Matthew Henry (1662-1714), was the eminent non-conformist theologian who gave the Church the devotional commentary which held a foremost place in its field. He died a week after his settlement in London as pastor of a church in Hackney, but his end was full of confidence in the Saviour's grace.
His last words were: "A life spent in the service of God, and in communion with Him, is the most comfortable life that anyone can lead in this present world."
John Wesley
John Wesley, the founder of the great Methodist Church said, "The best of all is, God is with us." I really love these last words of this great founder.
John Wesley, of whom it has been said that eternity alone will reveal what the world owes to his mighty ministry, was active to the very end. Until the end, he was full of praise, counsel and exhortations.
The Great Founder Dies in Peace
In his last moments with what remaining strength he had, he cried out twice over, in holy triumph:
"The best of all is, God is with us."
The very last word Wesley was heard to articulate was: "Farewell!"
Then, without a lingering groan, the evangelist of the highways and by-ways, beloved pastor of thousands, and father of the great Methodist Church, entered into the joy of his Lord.
Notice again, death to the confident Christian - It was a peaceful transition from one world to another!
Adoniram Judson
Adoniram Judson was a missionary to Africa. In fact, the first American missionary to Africa. He went to Burma, wrote and translated the Bible into the Burmese language.
The Departure of Africa's First American Missionary
He also wrote a dictionary for them. When he was dying he said, "No one ever left this world with brighter hopes or warmer feelings."
Don't be afraid, death will not surprise me. In spite of what I say, I feel so strong in Him."
This is a man who had strength when most people are weak. Let's all pray for such staying power, that we may all prevail until the very end.
Charles Bridgman
Charles Bridgman died at the age of twelve. As a child he loved to read his Bible and desired spiritual knowledge. Young Charles would often rebuke his brothers if they forgot to thank God at meal times. When he became ill, he was asked whether he would rather live or die, he answered "I desire to die, that I may go to my Saviour."
The Strength of a Little Boy
As his time drew near, his last words were: "...Into thy hands I commend my soul! Now close mine eyes. Forgive me, father, mother, brother, sister and all the world! Now I am well, my pain is almost gone, my joy is at hand. Lord have mercy upon me. O Lord, receive my soul unto Thee." How many young boys of today would speak the way this young man spoke?
Robert Bruce
Robert Bruce, one of the most distinguished men of his time, entered the ministry and became prominent in Edinburgh. Scrupulously maintaining the established norms of the church, he exposed himself to much persecution for the truth's sake.
At the time of his death, he called for the family Bible and said to his daughter:
"Cast up to me the eighth chapter of Romans, and set my finger on these words, 'I am persuaded that NEITHER DEATH NOR LIFE ... SHALL BE ABLE TO SEPARATE ME from the love of God which is in Christ Jesus my Lord.'"
Then Bruce said, "Is my finger on them?"
"Yes," said his daughter. Then he replied:
"Now God be with you, my children. I have just breakfasted with you, and shall sup with my Lord Jesus this night."
How exciting it must be when you know you are ready! There can be no reason to backslide when you hear these exciting testimonies.
And Many Others
Another dying Christian said, "How bright the room, how full of angels!"
Some other Christian said confidently, "The battle is fought. The battle is fought, and the victory is won." With those words, he went to be with the Lord.
Alexander II, full of divine faith, exclaimed: "I am sweeping through the gates, washed in the blood of the Lamb."
Someone else said, "I wish I had the power of writing to describe how pleasant it is to die."
Another one exclaimed, "Oh! That I could tell what joy I possess. I am full of rapture, the Lord shines with such power upon my soul. He is come, He is come."
One surviving believer said, "I shall soon be with Jesus. PERHAPS I AM TOO ANXIOUS!"
Is It Always Sweet to Die?
Another person said, "IT IS SWEET TO DIE." How will you be able to say, "It is sweet to die" when you have backslidden and you know judgement awaits you?
One Christian brother questioned, "Can this be death? What? It is better than living. TELL THEM I DIED HAPPILY IN JESUS."
Another one said, "They sing. The angels sing. IS THIS DYING? NO, IT IS SWEET LIVING."
One lucky backslider, Oliver, a doctor of philosophy, had lived the life of an infidel. But shortly before his death he repented and turned to the Saviour.
His final word was one of deep regret: "Would that I could undo the mischief I have done! I was more ardent to poison men with infidel principles than any Christian is to spread the doctrines of Christ."
The Sinners
Now, let us consider what some backsliders and sinners said as they were dying. The pride and rebellion of these wicked people did not help matters as they approached the gates of hell and accountability. Some of these people were backslidden Christians. They died as frightened, screaming and hopelessly lost souls. The first person I want us to consider in this category is a man called Tom Paine.
Tom Paine
Tom Paine (1737-1809) was considered to be a literary giant.
He wrote “The Age of Reason” and lived during the revivals of John Wesley and George Whitfield. He lived a life that was against God, and drew people away from God. I believe that this is one of the people who have made Europe so anti-Christ and atheist in their way of thinking. One person who witnessed his death said, "He is truly to be pitied."
Although he did not believe in God, at the hour of death on his bed he said, "I would give worlds, if I had them, that 'Age of Reason' had not been published. Oh! Lord help me. Oh! God, what have I done to suffer so much?" Then after that he said, "But there is no God. Yet if there is a God, what will become of me in the world after? If ever the devil had an agent, I have been that one."
He Was Frightened to Die
When an elderly woman attending him wanted to leave the room, he said, "Stay with me. For God's sake, I cannot bear to be left alone. For it is hell to be left alone."
The very last words of Tom Paine were, "My God, my God why has thou forsaken me?" And with these words he died. This is the death of the wicked. Utterly helpless and hopeless in the presence of a righteous God!
Voltaire
Whenever I go to Geneva, I cross over into Ferney- Voltaire, a little French village named after a noted infidel Voltaire (1694-1778). One night I drove with the pastor of my church in Geneva to look at a statue of this man.
I saw all of the tributes that were written to his name and all of the good works that he was said to have done for the community. But this man also lived and fought against Christianity.
The Man Who Cursed Christ
Notice what this noted French infidel said of Christ our Saviour: "Curse the wretch!" How on earth can you gather so much confidence to curse Christ and call Him a wretch?
He once boasted, "In twenty years, christianity will be no more. My single hand shall destroy the edifice it took twelve apostles to rear."
These are the people who have laid the foundations for the atheism that is so prevalent in Europe today.
Shortly after his death, the very house in which he printed his foul literature became the depot of the Geneva Bible Society. The nurse who attended Voltaire said: "For all the wealth in Europe I would not see another infidel die."
He Was Helpless and Desperate on His Deathbed
The physician, Trochim, who was with Voltaire at his death said that he cried out most desperately:
"I am abandoned by God and man! I will give you half of what I am worth if you will give me six month's life. Then I shall go to hell, and you will go with me. O Christ! O Jesus Christ!"
Notice the desperation and helplessness of this blasphemer as he descended into the abyss. He himself admitted that he was on his way to hell.
My dear Christian friends, let's make no mistakes about the reality of Heaven and Hell.
Thomas Hobbes
Thomas Hobbes (1588-1674), was a noted English political philosopher whose most famous work was “Leviathan”.
This cultured, clever skeptic corrupted many of the great men of his time. But what regret was his at the end of the road! What hopelessness permeated his last words:
"If I had the whole world, I would give it to live one day. I am about to take a leap in the dark!"
The good news is: Christians do not take leaps into the dark! When they die they go to Heaven!
Thomas Cromwell
Thomas Cromwell (1540), who became Earl of Essex, was the noted English statesman who was next to the King in power and influence. He was responsible for the digging up of the bones of Thomas Becket, and their burning as those of a traitor.
The Man Who Was Seduced
Over ambitious, Cromwell lost his influence and also his head, for he was executed. Historians tell us that as he died, he said in a speech:
"THE DEVIL IS READY TO SEDUCE US, AND I HAVE BEEN SEDUCED, but bear me witness that I die in the Catholic Faith."
Notice how people want to associate with God at the last moment. This man was insisting that he was in the faith!
Thomas Cork
Thomas Cork cried out in anguish as he was dying. He said, "Until this moment I thought there was neither a God nor a devil. But now I know, and I feel that there are both." He exclaimed, "I am doomed to judgment by the judgment of the Almighty."
Robert Green Ingersoll
He Wrote About the Mistakes of the Bible
Robert Green Ingersoll (1833-1899), famous American lawyer and prominent agnostic, lectured on Biblical inaccuracies and contradictions. His famed lecture "The Mistakes of Moses" led one defender of the Bible to say that he would like to hear Moses speak for five minutes on The Mistakes of Ingersoll!
Do I Have a Soul?
When he came to the gates of hell he was frozen with terror and he said, "OH GOD, IF THERE IS A GOD, HAVE MERCY ON MY SOUL - IF I HAVE A SOUL."
Sir Francis Gilfort
Sir Francis Gilfort, was taught early in his life about the gospel.
The Potential Minister Who Backslid
He was a backslidden Christian. In fact, it was expected that he would become a minister, but he fell into bad company. When he was passing on to eternity, he said,
"From where is this war in my heart? What arguments do I have to assist me in matters of fact? Do I say there is no hell when I feel one in my bosom?
AYE, AM I CERTAIN THAT THERE IS NO JUDGMENT WHEN I FEEL PRESENT JUDGMENT? Oh, wretch that I am. Whither shall I flee from this?
That there is a God, I know, for I continually feel that of His wrath. That there is a hell, I am surely certain.
Oh! That I was to lie upon the fire that never quench for a thousand years to purchase the favour of God, and to be reverted to Him again. But it is a fruitless wish.
Millions and millions of years will bring me no nearer to the end of my torment. Eternity, eternity!"
Do You Want Anyone to Pray For You?
As the distress of this man increased, he was asked whether he wanted some people to be invited to pray for him. He responded "Tigers and monsters, are you devils to come to torment me? Will you give me the prospects of Heaven to make my hell more intolerable?"
Then he said, "Oh! the insufferable pangs of death." And with that he died. How frightening!
William Pope
William Pope, was a born-again Christian, and knew the love of God. But he backslid when his wife died, and he followed Tom Paine. Not long after he backslid, he contracted tuberculosis, which was known at that time as The Consumption.
He is said to have been the leader of a company of infidels who ridiculed everything religious.
They Kicked the Bible and Tore it up
This was a classic backslider who said when he was dying, "No case is comparable to mine, I cannot revert, God will damn me forever."
One of the exercises of he and his friends was to kick the Bible about the floor, or tear it up. Friends who were present in his death-chamber spoke of it as a scene of terror.
A Frightening Scene of Death
His eyes rolled to and fro as he was dying on his bed, and he lifted up his hands as he cried out, "I have no contrition. I cannot repent. God will damn me. I know the day of grace is past...You see one who is damned forever... Oh, Eternity! Eternity... Nothing for me but hell. Come, eternal torments... Do you not see? Do you not see him? He is coming for me. Oh! the burning flame, the hell, the pain that I feel. Eternity will explain my torment."
And with these words, he died.
These were the very last words of a backslider!!
Dear Christian friend, what else can I say? I have shown you the real life testimonies of real people just like yourself. If that is not enough to make you believe and stay with God, then perhaps…
I have bargained for your soul, sharing with you all that a pastor can. I have shown you why you should not backslide. I have shown you the causes of backsliding, the descriptions of backsliding, and the symptoms of backsliding. I have shown you how people who backslide behave when they approach the gates of eternity. On the other hand, I have shown you the happy farewells of Christians with staying power to the very end.
My prayer for you is that you will find Christ and STAY in Christ. For on Christ the solid rock we stand. Amen!!
To the making of many books there is no end. May this book bless your ministry. Amen.
by Dag Heward-Mills
0 notes
Text
Inkwell Awards Changing Host Show Location from HeroesCon to the Great Philadelphia Comic Con!
FOR IMMEDIATE RELEASE (Extended version)
(New Bedford, MA – November 18, 2018) The Inkwell Awards is announcing that their annual live awards ceremony will be relocating to the Great Philadelphia Comic Con! at the The Greater Philadelphia Expo Center in Oaks, PA commencing April 12-14, 2019. Their awards ceremonies for the previous eight years, including 2018, were held at the June HeroesCon in Charlotte, NC.
According to Inkwell Awards founder and director Bob Almond, HeroesCon promoter Shelton Drum invited the non-profit organization to his long-running, family-friendly show in 2011. “We had been left hanging by a major convention,” Almond said, “and Shelton, who had endured similar problems, wanted to support a kindred spirit and show that this altruistic, annual event could be done and well-supported.”
Almond added, “Changing venues is both sorrowful and exciting. Our presence at Heroes’ industry-respected and community-loved show further boosted our credibility and exposure, which helped with fundraising in the long run. We can truly thank HeroesCon for where we are now. But the 16-hour drives and related travel expenses each season would leave our budget almost wiped out.”
When asked about the switch in locations, Almond explained, “When Great Philadelphia Con’s Creator Relations and Artist Alley Director Stan Konopka with promoter Christopher D. Wertz offered us their venue and funding support for all expenses, we were thrilled. A mere six-hour drive is a huge relief for us. Christopher’s convention has grown in a short time in reputation and attendance from both the celebrity/artist guests and the fans.”
Christopher gave the following statement: “We at The Great Philadelphia Comic Con! would like to graciously thank the Inkwell Awards and Bob for honoring our show by choosing us to host the Inkwell Awards Ceremony and its nominees at our April 2019 event and beyond. From our beginning with a small, one-day family-run show in Allentown Pa, we have tried to focus on the celebration of the Sequential Arts. Since then we have grown to become the second largest Comic Convention in Pennsylvania, now held at the Greater Philadelphia Expo Center in Oaks.
“Throughout our history, we have worked to keep our Artists an important focus of our events, being the first guests that all fans see as they enter the show, and the last as they leave. A key foundation for this focus has been our Director of Artists Alley and Creator Relations Stan Konopka, who has a background in this arena as the creator and writer of “The Rejected” by Source Point Press. Similar to how a good inker can make or break the final quality of what a reader sees in a book, having an excellent team when planning an event is critical.
“Stan has been working with Bob in the background, planning, having meetings, and long phone calls with the ultimate goal and determination to create one of the best Awards Ceremonies in the business. We look forward to working together to make an amazing and enduring event that can grow with our show year over year. So, it is with great humility and welcoming arms we joyfully announce our relationship with Bob and the Inkwell Awards!”
In a statement, Heroes promoter Drum said:
”It’s been eight years since Bob Almond made Heroes Con the home of The Inkwells. We have been privileged to be host to Bob and his team as they honored the true unsung heroes of comics, the Inkers. The annual Inkwell Awards ceremony– the anchor of our opening day programming– has spotlighted and awarded many of the greatest inkers in comic’s history: Mike Royer, Rudy Nebres, Klaus Janson, Bob McLeod, Jerry Ordway and Joe Rubinstein, just to name a few.
“And now Bob is heading to Great Philadelphia Comic Con and taking the Inkwells with him. They will be missed, but it is wonderful knowing Bob Almond will still be at it making the world a more appreciative place for our black-thumbed brethren. Godspeed, Bob.”
Almond concluded, “Shelton graciously took us in at a low-point for me. Now, as we celebrate The Inkwells’ 10th anniversary, it’s like progressing from one chapter of growth to a new one as we boldly embark on our second decade with Christopher and Stan.”
Inkwell Awards Changing Host Show Location from HeroesCon to the Great Philadelphia Comic Con! was originally published on
0 notes
Text
Non-Sequential // Masterlist

Pairing: Pre-Serum Steve Rogers/Steve Rogers x Reader
One night, Steve Rogers met a beautiful dame named Y/N. He hadn’t intended on letting her get away. But fate had other ideas. Y/N appeared and disappeared in his life so hauntingly that Steve started to wonder if she was an angel meant to watch over him.
A/N: Inspired by the film The Time Traveler’s Wife. But not one of those fics that just literally rips off the whole movie and plugs in characters where they please.
Prologue // Chapter 1 // Chapter 2 // Chapter 3 // Chapter 4 // Chapter 5 // Chapter 6 // Chapter 7 // Chapter 8 // Chapter 9 // Chapter 10 // Chapter 11 // Chapter 12 // Chapter 13 // Chapter 14 // Chapter 15 // Chapter 16 // Chapter 17 // Chapter 18 // Chapter 19 // Chapter 20 // Chapter 21 // Chapter 22 // Chapter 23 // Chapter 24 // Chapter 25 // Chapter 26 // Chapter 27 // Chapter 28 // Chapter 29 //
---
Non-Sequential Headcanons & Asks
I DO NOT DO TAGLISTS.
#pre serum steve#pre serum steve rogers#steve rogers fic#steve rogers x reader#steve rogers reader insert#captain america x#mar#steve rogers fanfic#steve rogers fluff#1930s steve rogers#1940s steve rogers#non sequential series#non sequential masterlist#bucky barnes#winter soldier#pre serum!steve rogers x reader#bucky barnes x reader
4K notes
·
View notes
Text
Test Bank Database Processing 11th Edition
For Order This And Any Other Test
Banks And Solutions Manuals, Course,
Assignments, Discussions, Quizzes, Exams,
Contact us At: [email protected]
�� Database Processing, 11e (Kroenke)
Chapter 1: Introduction
1) The purpose of a database is to help people keep track of things.
Answer: TRUE
Diff: 1 Page Ref: 3
2) In a database, each table stores data about a different type of thing.
Answer: TRUE
Diff: 1 Page Ref: 3
3) In a database, each row in a spreadsheet has data about a particular instance.
Answer: FALSE
Diff: 2 Page Ref: 3
4) In every database, not just the databases discussed in this book, table names are capitalized.
Answer: FALSE
Diff: 2 Page Ref: 3
5) A database shows data in tables and the relationships among the rows in those tables.
Answer: TRUE
Diff: 1 Page Ref: 4
6) Data is recorded facts and figures; information is knowledge derived from data.
Answer: TRUE
Diff: 1 Page Ref: 5
7) Databases record data in such a way that they can produce information.
Answer: TRUE
Diff: 2 Page Ref: 6
8) Enterprise Resource Planning (ERP) is an example of a data mining application.
Answer: FALSE
Diff: 2 Page Ref: 6-7
9) Small databases typically have simple structures.
Answer: FALSE
Diff: 3 Page Ref: 8
10) Microsoft Access is a low-end product intended for individuals and small workgroups.
Answer: TRUE
Diff: 2 Page Ref: 14
11) Applications are computer programs used directly by users.
Answer: TRUE
Diff: 1 Page Ref: 8
12) Sequenced Query Language (SQL) is an internationally recognized standard language that is understood by all commercial database management system products.
Answer: FALSE
Diff: 2 Page Ref: 8
13) A database management system (DBMS) creates, processes and administers databases.
Answer: TRUE
Diff: 1 Page Ref: 11
14) Microsoft Access is just a DBMS.
Answer: FALSE
Diff: 2 Page Ref: 13
15) The DBMS engine in Microsoft Access is called Jet.
Answer: TRUE
Diff: 2 Page Ref: 14
16) In Microsoft Access, you can use the Oracle DBMS in place of the Jet DBMS.
Answer: FALSE
Diff: 2 Page Ref: 14
17) In an Enterprise-class database system, a database application interacts with the DBMS.
Answer: TRUE
Diff: 2 Page Ref: 15 Fig 1-16
18) In an Enterprise-class database system, a database application accesses the database data.
Answer: FALSE
Diff: 2 Page Ref: 15 Fig 1-16
19) In an Enterprise-class database system, business users interact directly with the DBMS, which directly accesses the database data.
Answer: FALSE
Diff: 2 Page Ref: 15 Fig 1-16
20) All database applications get and put database data by sending SQL statements to the DBMS.
Answer: TRUE
Diff: 2 Page Ref: 9
21) The DBMS ranked as having the "most power and features" in the text is IBM's DB2.
Answer: FALSE
Diff: 3 Page Ref: 16 Fig 1-17
22) The DBMS ranked as being the "most difficult to use" in the text is Oracle Corporation's Oracle Database.
Answer: TRUE
Diff: 3 Page Ref: 16 Fig 1-17
23) The DBMS ranked as being the "easiest to use" in the text is Microsoft's SQL Server.
Answer: FALSE
Diff: 2 Page Ref: 16 Fig 1-17
24) The DBMS ranked as having the "least power and features" in the text is Microsoft Access.
Answer: TRUE
Diff: 2 Page Ref: 16 Fig 1-17
25) A database is called "self-describing" because it reduces data duplication.
Answer: FALSE
Diff: 2 Page Ref: 12
26) The description of a database's structure that is stored within the database itself is called the "metadata."
Answer: TRUE
Diff: 1 Page Ref: 12 Fig 1-14
27) In a database processing system, indexes are held by the database management system (DBMS).
Answer: TRUE
Diff: 3 Page Ref: 11 Fig 1-12
28) Database design is important, but fortunately it is simple to do.
Answer: FALSE
Diff: 1 Page Ref: 16
29) A database design may be a new systems development project.
Answer: TRUE
Diff: 1 Page Ref: 16-19 Fig 1-18
30) A database design is rarely a redesign of an existing database.
Answer: FALSE
Diff: 1 Page Ref: 16-19 Fig 1-18
31) Information systems that stored groups of records in separate files were called file processing systems.
Answer: TRUE
Diff: 2 Page Ref: 19-20 Fig 1-25
32) Data Language/I (DL/I) structured data relationships as a tree structure.
Answer: TRUE
Diff: 3 Page Ref: 21 Fig 1-25
33) The CODASYL DBTG mode structured data relationships as a tree structure.
Answer: FALSE
Diff: 3 Page Ref: 22 Fig 1-25
34) The relational model was first proposed in 1970 by E. F. Codd at IBM.
Answer: TRUE
Diff: 2 Page Ref: 22
35) The 1977 edition of this text contained a chapter on the relational model, and that chapter was reviewed by E. F. Codd.
Answer: TRUE
Diff: 3 Page Ref: 22
36) dBase was the first PC-based DBMS to implement true relational algebra on a PC.
Answer: FALSE
Diff: 3 Page Ref: 23
37) Paradox is the only major survivor of the "bloodbath of PC DBMS products."
Answer: FALSE
Diff: 2 Page Ref: 23
38) Business organizations have resisted adopting object-oriented database systems because the cost of purchasing OODBMS packages is prohibitively high.
Answer: FALSE
Diff: 3 Page Ref: 23
39) Bill Gates has said that "XML is the lingua-franca of the Internet Age."
Answer: TRUE
Diff: 2 Page Ref: 24
40) XML Web services allow database processing to be shared across the Internet.
Answer: TRUE
Diff: 2 Page Ref: 24
41) The purpose of a database is to:
A) help people keep track of things.
B) store data in tables.
C) create tables of rows and columns.
D) maintain data on different things in different tables.
E) All of the above.
Answer: A
Diff: 2 Page Ref: 3
42) A database stores:
A) data.
B) relationships.
C) metadata.
D) A and B
E) A, B and C
Answer: E
Diff: 2 Page Ref: 3-4 and 12
43) A database records:
A) facts.
B) figures.
C) information.
D) A and B
E) A, B and C
Answer: D
Diff: 2 Page Ref: 3
44) A sales contact manager used by a salesperson is an example of a(n) ________.
A) single-user database application
B) multiuser database application
C) e-commerce database application
D) A or B
E) Any of A, B or C
Answer: A
Diff: 2 Page Ref: 8 and Fig 1-5
45) A Customer Resource Management (CRM) system is an example of a(n) ________.
A) single-user database application
B) multiuser database application
C) e-commerce database application
D) A or B
E) Any of A, B or C
Answer: B
Diff: 2 Page Ref: 8 and Fig 1-5
46) An online drugstore such as Drugstore.com is an example of a(n) ________.
A) single-user database application
B) multiuser database application
C) e-commerce database application
D) A or B
E) Any of A, B or C
Answer: C
Diff: 1 Page Ref: 7 Fig 1-5
47) The industry standard supported by all major DBMSs that allows tables to be joined together is called ________.
A) Sequential Query Language (SQL)
B) Structured Question Language (SQL)
C) Structured Query Language (SQL)
D) Relational Question Language (RQL)
E) Relational Query Language (RQL)
Answer: C
Diff: 1 Page Ref: 8
48) A program whose job is to create, process and administer databases is called the ________.
A) Database Modeling System
B) Database Management System
C) Data Business Model System
D) Relational Model Manager
E) Data Business Management Service
Answer: B
Diff: 2 Page Ref: 8
49) Microsoft Access includes:
A) a DBMS.
B) an application generator.
C) a Web server.
D) A and B
E) A, B and C
Answer: D
Diff: 2 Page Ref: 13 Fig 1-15
50) Microsoft Access may use which of the following DBMS engines?
A) Jet
B) SQL Server
C) Oracle
D) A and B
E) A, B and C
Answer: D
Diff: 2 Page Ref: 14
51) Which of the following are basic components of an enterprise-class database system?
A) The user
B) The database application
C) The database management system (DBMS)
D) The database
E) All of the above
Answer: E
Diff: 1 Page Ref: 15 Fig 1-16
52) In an enterprise-class database system ________.
A) the database application(s) interact(s) with the DBMS
B) the database application(s) access(es) the database data
C) the DBMS accesses the database data
D) A and B
E) A and C
Answer: E
Diff: 2 Page Ref: 15 Fig 1-16
53) In an enterprise-class database system, the database application ________.
A) creates queries
B) creates forms
C) creates reports
D) A and B
E) B and C
Answer: E
Diff: 2 Page Ref: 15 Fig 1-16
54) In an enterprise-class database system, reports are created by ________.
A) the user
B) the database application
C) the database management system (DBMS)
D) the database
E) All of the above
Answer: B
Diff: 2 Page Ref: 15 Fig 1-16
55) A database is considered "self-describing" because ________.
A) all the users' data is in one place
B) it reduces data duplication
C) it contains a description of its own structure
D) it contains a listing of all the programs that use it
E) All of the above
Answer: C
Diff: 1 Page Ref: 12
56) In an enterprise-class database system, the database ________.
A) holds user data
B) holds metadata
C) holds indexes
D) holds stored procedures
E) All of the above
Answer: E
Diff: 3 Page Ref: 12-13 Fig 1-14
57) A database may contain ________.
A) tables
B) metadata
C) triggers
D) stored procedures
E) All of the above
Answer: E
Diff: 2 Page Ref: 12-13 Fig 1-14
58) A database may be designed ________.
A) from existing data
B) as a new systems development project
C) as a redesign of an existing database
D) A and B
E) A, B, and C
Answer: E
Diff: 2 Page Ref: 16 Fig 1-18
59) A database designed using spreadsheets from the Sales department is a database being designed ________.
A) from existing data
B) as a new systems development project
C) as a redesign of an existing database
D) A and B
E) A, B, and C
Answer: A
Diff: 2 Page Ref: 16-19 Fig 1-18
60) A database designed to implement requirements for a reporting application needed by the Sales department is a database being designed ________.
A) from existing non-database data
B) as a new systems development project
C) as a redesign of an existing database
D) A and B
E) A, B, and C
Answer: B
Diff: 2 Page Ref: 16-19 Fig 1-18
61) A database designed to combine two databases used by the Sales department is a database being designed ________.
A) from existing data
B) as a new systems development project
C) as a redesign of an existing database
D) A and B
E) A, B, and C
Answer: C
Diff: 1 Page Ref: 16-19 Fig 1-18
62) Database professionals use ________ as specific data sources for studies and analyses.
A) data marts
B) normalization
C) data models
D) entity-relationship data modeling
E) data migration
Answer: A
Diff: 2 Page Ref: 19-20
63) Database professionals use a set of principles called ________ to guide and assess database design.
A) data marts
B) normalization
C) data models
D) entity-relationship data modeling
E) data migration
Answer: B
Diff: 3 Page Ref: 17
64) A very popular development technique used by database professionals for database design is known as ________.
A) data marts
B) normalization
C) data models
D) entity-relationship data modeling
E) data migration
Answer: D
Diff: 3 Page Ref: 17-18
65) A very popular development technique used by database professionals to adopt a database design to a new or changing requirement is known as ________.
A) data marts
B) normalization
C) data models
D) entity-relationship data modeling
E) data migration
Answer: E
Diff: 3 Page Ref: 18-19
66) The predecessor(s) of database processing was (were) ________.
A) file managers
B) hierarchical models
C) network models
D) relational data model
E) All of the above were predecessors of database processing.
Answer: A
Diff: 3 Page Ref: 20-23
67) The relational model ________.
A) was first proposed in 1970
B) was developed by E. F. Codd
C) was developed at IBM
D) resulted in the DBMS product DB2
E) All of the above
Answer: E
Diff: 1 Page Ref: 22-23
68) Modern microcomputer personal DBMS products ________.
A) are supplied by several well-established manufacturers
B) were essentially killed off by MS Access
C) have poor response time
D) are not true DBMS products
E) are really just programming languages with generalized file-processing capabilities
Answer: B
Diff: 2 Page Ref: 22-23
69) Business organizations have resisted adopting object-oriented database management systems because ________.
A) object-oriented programming uses simplified data structures that fit easily into relational databases
B) the cost of purchasing OODBMS packages is prohibitively high
C) the cost of converting data from relational databases to OODBMSs is too high
D) most large organizations have older applications that are not based on object oriented programming
E) C and D
Answer: E
Diff: 2 Page Ref: 23
70) For database development, the most important Web-related technology to emerge in recent years is:
A) FTP.
B) HTTP.
C) XML.
D) OODBMS.
E) All of the above.
Answer: C
Diff: 2 Page Ref: 23-24
71) The purpose of a database is to ________.
Answer: help people keep track of things
Diff: 1 Page Ref: 3
72) In a database, each ________ stores data about a different type of thing.
Answer: table
Diff: 1 Page Ref: 3
73) In a database, each ________ in a database has data about a particular instance.
Answer: table
Diff: 2 Page Ref: 3
74) In the databases discussed in this book, table names are ________.
Answer: capitalized
Diff: 2 Page Ref: 3
75) A database shows data in tables and ________ among the rows of those tables.
Answer: the relationships
Diff: 1 Page Ref: 4
76) ________ is recorded facts and figures; ________ is knowledge derived from data.
Answer: Data; information
Diff: 1 Page Ref: 3 and 5-6
77) Databases record ________ in such a way that they can produce ________.
Answer: data; information
Diff: 2 Page Ref: 6
78) Enterprise Resource Planning (ERP) is an example of a ________.
Answer: multiuser database
Diff: 2 Page Ref: 6-7 Fig 1-5
79) ________ do not necessarily have simple structures.
Answer: Small databases
Diff: 3 Page Ref: 8
80) Computer programs used directly by users are called ________.
Answer: applications
Diff: 1 Page Ref: 8
81) ________ is an internationally recognized standard language that is understood by all commercial database management system products.
Answer: Structured Query Language (SQL)
Diff: 2 Page Ref: 8
82) A ________ is used to create, process and administer databases.
Answer: database management system (DBMS)
Diff: 1 Page Ref: 8
83) ________ is a DBMS combined with an application generator.
Answer: Microsoft Access
Diff: 2 Page Ref: 13-14
84) In an enterprise-class database system, a ________ interacts with the DBMS.
Answer: database application
Diff: 2 Page Ref: 15 Fig 1-16
85) All database applications get and put database data by sending ________ to the DBMS.
Answer: SQL statements
Diff: 3 Page Ref: 15 Fig 1-16
86) The DBMS ranked as having the "most power and features" in the text is ________.
Answer: Oracle database
Diff: 3 Page Ref: 11
87) The DBMS ranked as being the "easiest to use" in the text is ________.
Answer: Microsoft Access
Diff: 2 Page Ref: 16
88) A database is called ________ because it contains a description of itself.
Answer: "self-describing"
Diff: 2 Page Ref: 12
89) ________ is the description of a database's structure that is stored within the database itself.
Answer: Metadata
Diff: 1 Page Ref: 12-13 Fig 1-13
90) In an enterprise-class database system, indexes are held by the ________.
Answer: database
Diff: 3 Page Ref: 12-13 Fig 1-14
91) Business information systems that stored groups of records in separate files were called ________.
Answer: file processing systems
Diff: 2 Page Ref: 20-21 Fig 1-25
92) Data Language/I (DL/I) structured data relationships in a data structure known as a ________.
Answer: tree structure
Diff: 3 Page Ref: 21-22 Fig 1-25
93) The CODSYL DBTG mode structured data relationships in a data structure known as a ________.
Answer: network
Diff: 3 Page Ref: 22 Fig 1-25
94) The relational model was first proposed in 1970 by ________ at IBM.
Answer: E. F. Codd
Diff: 2 Page Ref: 22
95) The 1977 edition of this text was the first edition of this book that contained a description of the ________.
Answer: relational model
Diff: 2 Page Ref: 20
96) ________ was the first PC based DBMS to implement true relational algebra on a PC.
Answer: R:base
Diff: 3 Page Ref: 23
97) ________ is the only major survivor of the "bloodbath of PC DBMS products."
Answer: Microsoft Access
Diff: 2 Page Ref: 23
98) Business organizations have resisted adopting ________ because of the difficulty of converting existing databases.
Answer: object-oriented database management systems (OODBMSs)
Diff: 3 Page Ref: 23
99) ________ has said that "XML is the lingua-franca of the Internet Age."
Answer: Bill Gates
Diff: 2 Page Ref: 24
100) ________ allow database processing to be shared across the Internet.
Answer: XML Web services
Diff: 2 Page Ref: 24
101) What is the purpose of a database, and how does the database accomplish this purpose?
Answer: The purpose of a database is to help people keep track of things. It accomplishes this purpose by storing data in tables. Each table has rows and columns, similar to a spreadsheet. A database usually has multiple tables in order to keep track of different but related things. For example, we might have a CUSTOMER table to keep track of customers and a PRODUCT table to keep track of the things we sell. Each row in each table holds data about a particular instance, i.e., one customer or one product. The database also stores the links between the tables, so that we can track which customers bought which products (note: this will require an additional table if one customer can buy more than one product and one product can be sold to more than one customer).
Diff: 2 Page Ref: 3-5
102) What are the four components of a database system?
Answer: The four components in a database system are: the user, the database application, the database management system (DBMS) and the database. The user interacts with the database application, which interacts with the DBMS, which controls the database. The functions of the database application include creating and processing forms, creating and transmitting queries and creating and processing reports. The DBMS creates databases, tables and supporting structures, manages database data, enforces rules and provides security. The database stores the user data, the database metadata, indexes, triggers, stored procedures and application metadata.
Diff: 2 Page Ref: 8-13
103) Briefly describe the function of an application program in a database system.
Answer: The application program is responsible for creating and processing forms. The application displays the form to the user, allows the user to complete the data entry, evaluates the form to determine which data management tasks need to be performed, and transmits the appropriate requests to the DBMS. The application creates and transmits queries. The queries are requests for data that are created in a language like SQL, and transmitted to the DBMS to have the requested data returned to the application program. The application also creates and processes reports. The query to retrieve the necessary data for the report is sent to the DBMS. When the DBMS returns the needed data, the application manipulates it as necessary to create the requested report. The application program also applies application logic to control the manipulation of data in accordance with the business rules. Finally, the application program is responsible for providing control. Control must be exercised to allow the users to make choices for functions and tasks as appropriate for their jobs. Also, control must be exercised to manage the activities of the DBMS.
Diff: 2 Page Ref: 9-11
104) What components are included in a database?
Answer: The database contains user data, metadata, indexes and other overhead data, and application metadata. User data is the data from the user's environment that they want to track. Metadata is data about the structure of the database. Indexes and other overhead data are structures that the database uses to improve performance. Finally, the application metadata is data about forms, reports, and other application components that some databases, particularly those created with desktop DBMS products, store with the database.
Diff: 2 Page Ref: 13-14
105) Why do we say a database is "self-describing" and why is this an advantage?
Answer: A database is considered self-describing because it contains a description of its own structure within the database itself. This description is called the metadata, and it is stored in specialized tables in relational databases. The advantage is that the database is self-documenting, and that a knowledgeable user or a database designer can easily access the metadata. All DBMS vendors provide tools to access the metadata within their products.
Diff: 3 Page Ref: 12-13
106) What is "metadata" and how does it relate to the definition of a database?
Answer: Metadata is data about the structure of the database itself. This includes data about the names of all the tables in the database, the names of all the columns in each of the tables, the data type of each column in each table, the properties of the tables and the columns, etc. Metadata accounts for the "self-describing" aspect of the definition of a database as a "self-describing collection of integrated tables."
Diff: 2 Page Ref: 12-13
107) Briefly describe the function of the DBMS in a database system.
Answer: The DBMS creates the database and the tables and structures within it. The DBMS also reads and updates the database data. It receives requests from application programs to perform data maintenance tasks. These requests are translated into actions that are performed on the database. In addition to maintaining the user data within the database, the DBMS also maintains the database structures. The DBMS also enforces any rules that have been defined to govern the values of the data, such as data type requirements and referential integrity constraints. The DBMS controls concurrency issues, which deal with the unwanted interruption of one user's work by another user's work. As the only point of entry into the database, the DBMS also provides security for the database to restrict users' access to only the data that they have authority to read or modify. Finally, the DBMS is responsible for the creation of backup copies of the database data and for restoring the database in case a recovery is required.
Diff: 2 Page Ref: 11-12
108) What are "referential integrity constraints"? Give an example.
Answer: A referential integrity constraint is a rule that restricts certain actions on the database data. A referential integrity constraint is used to ensure that the values in a field in one table have matching tables in a corresponding field in another table. These constraints are enforced by the DBMS, which will not allow changes to the values of the database that would result in violations of this rule. For example, a database has an EMPLOYEE table and a VEHICLE table that are used to store data on employees and the vehicles that they are assigned to drive. The EMPLOYEE table has a column called EmployeeID that is used to distinguish one employee record from another. The VEHICLE table also has an EmployeeID column that is used to associate a vehicle with the appropriate employee. A referential integrity constraint could be used to prevent a vehicle from being assigned to an employee with an EmployeeID that does not appear in the EMPLOYEE table by requiring that all values in EmployeeID in the VEHICLE table have a matching value in EmployeeID in the EMPLOYEE table.
Diff: 3 Page Ref: 11
109) What are the three types of database design situations?
Answer: Database designs can be based on (1) existing data, (2) new systems development and (3) database redesign. Database designs from existing data may be based on data in spreadsheets or other data tables, or on data extracted from other databases. New systems development gathers user requirements for needed applications and designs a database to meet those requirements. Database redesign may be needed to migrate existing databases to a newer DBMS, or to integrate multiple existing databases.
Diff: 2 Page Ref: 16-19 Fig 1-18
110) Briefly describe the history of database processing.
Answer: The predecessor of database processing was file processing, where data were maintained on magnetic tape. Database processing as we know it today became possible with the availability of direct access disk storage in the 1960s. Using this storage, both the hierarchical data model and then the network data model were developed. In 1970, E. F. Codd of IBM proposed the relational model, which is the standard model used today. Current DBMSs such as DB2, Oracle and SQL Server are based on the relational model. The appearance of microcomputer based DBMSs, in the 1980s led to a "bloodbath" from which Microsoft Access emerged as the dominant PC workstation DBMS. More recent events include the introduction of object-oriented DBMSs (OODBMSs), and the development of tools such as XML to allow the use of database systems over the Internet.
Diff: 3 Page Ref: 18-22 Fig 1-18
0 notes
Text
Test Bank Evolutionary Analysis 5th Edition
For Order This And Any Other Test
Banks And Solutions Manuals, Course,
Assignments, Discussions, Quizzes, Exams,
Contact us At: [email protected]
Chapter 1 A Case for Evolutionary Thinking: Understanding HIV
1) In which of the following regions has AIDS killed the largest number of individuals?
A) India
B) Sub-Saharan Africa
C) United States
D) China
E) United Kingdom
Answer: B
Section: 1.1
Skill: Knowledge/Comprehension
2) The HIV virus contains all of the following components except ________.
A) integrase
B) double-stranded RNA
C) single-stranded RNA
D) reverse transcriptase
E) protease
Answer: B
Section: 1.1
Skill: Knowledge/Comprehension
3) The acronym HIV stands for which of the following?
A) human intercellular virus
B) human immune virus
C) human immunodeficiency virus
D) human immunity virus
E) human immunodeficiency vector
Answer: C
Section: 1.1
Skill: Knowledge/Comprehension
4) Which of the following enzymes is responsible for transcribing viral RNA into DNA?
A) RNA polymerase
B) reverse transcriptase
C) DNA polymerase
D) reverse integrase
E) RNA duplicase
Answer: B
Section: 1.1
Skill: Knowledge/Comprehension
5) The proteins that enable the HIV virus to bind to cells are typically CD4 and CCR5. On what type of cells are these proteins typically observed?
A) plasma cells
B) dendritic cells
C) effector helper T cells
D) memory helper T cells
E) both C and D
Answer: E
Section: 1.1
Skill: Knowledge/Comprehension
6) The AIDS phase of HIV infection begins when the concentration of CD4 T cells in the blood drops below what concentration?
A) 2,000 cells per cubic millimeter
B) 1,000 cells per cubic millimeter
C) 500 cells per cubic millimeter
D) 200 cells per cubic millimeter
E) No CD4 T cells are observed.
Answer: D
Section: 1.1
Skill: Knowledge/Comprehension
7) Which of the following drug categories are used to treat HIV infections?
A) integrase inhibitors
B) protease inhibitors
C) reverse transcriptase inhibitors
D) DNAse inhibitors
E) fusion inhibitors
Answer: D
Section: 1.2
Skill: Knowledge/Comprehension
8) Coreceptor inhibitors block HIV infection by preventing which of the following?
A) binding of the HIV virion onto the plasma membrane
B) binding of the HIV virion onto the CCR5 receptor
C) binding of the HIV virion onto the gp120 protein
D) degrading the coreceptor so the virion cannot attach
E) binding of the HIV virion onto the CD4 receptor
Answer: B
Section: 1.2
Skill: Application/Analysis
9) What is the effect of the ∆32 allele of CCR5 on HIV binding?
A) appears on the surface of CD4 T cells, but the HIV virion is unable to infect the host cell
B) does not appear on the surface of CD4 T cells
C) appears on the surface of the CD4 T cells and inactivates the virion upon binding
D) interferes with binding of the virion to the CD4 receptor protein
E) appears on the surface of the CD4 T cells and causes the virion to lyse upon binding
Answer: B
Section: 1.3
Skill: Application/Analysis
10) The ∆32 allele of CCR5 is found at the highest frequency in which of the following populations?
A) Africans
B) Japanese
C) North Americans
D) Europeans
E) South Americans
Answer: D
Section: 1.3
Skill: Knowledge/Comprehension
11) HIV-1 is believed to have been transmitted to humans from which of the following organisms?
A) gorillas
B) sooty mangabeys
C) African green monkeys
D) chimpanzees
E) baboons
Answer: D
Section: 1.4
Skill: Knowledge/Comprehension
12) HIV-1 Group M is responsible for 95% of human infections. When is it estimated that HIV-1 Group M was transferred to humans?
A) 1980
B) 1960
C) 1930
D) 1995
E) 1900
Answer: C
Section: 1.4
Skill: Knowledge/Comprehension
13) Antibodies and killer T cells recognize HIV or HIV-infected cells by binding to short pieces of viral proteins displayed on the virus or the infected host cell. These short pieces of viral proteins are called ________.
A) coat proteins
B) virosomes
C) proteosomes
D) epitopes
E) episomes
Answer: D
Section: 1.5
Skill: Knowledge/Comprehension
14) Tetherin is an important protein produced by the host. What is the function of tetherin in protecting a host cell from HIV?
A) ties maturing virions to the membrane of the host cell, thereby preventing the release of the mature virus
B) binds the virus to the external host cell membrane, thereby preventing the virus from entering the host cell
C) binds the viral RNA to reverse transcriptase, thus preventing synthesis of the viral DNA
D) binds the two viral RNA strands together, thus preventing the transcription of viral DNA in the host cell
E) causes the maturing virions to aggregate together, thus preventing their release from the host cell
Answer: A
Section: 1.5
Skill: Application/Analysis
15) Early in the infection with HIV, most virions bind to the host cell using CCR5 as a coreceptor. As the infection progresses, the HIV population evolves to use an alternate coreceptor. What is the alternate coreceptor these X4 viruses utilize?
A) Tetherin
B) CCR5α
C) vpu
D) TRIM5α
E) CXCR4
Answer: E
Section: 1.5
Skill: Knowledge/Comprehension
16) In what region of the world is the incidence of infection with HIV highest?
Answer: Sub-Saharan Africa
Section: 1.1
Skill: Knowledge/Comprehension
17) Originally, HIV was thought to be restricted to transmission during homosexual contact between gay men. List other ways in which HIV is currently known to be transmitted.
Answer: HIV can be transmitted by heterosexual sex, oral sex, needle sharing, transfusion with contaminated blood products, other unsafe medical procedures, childbirth and breast-feeding.
Section: 1.1
Skill: Knowledge/Comprehension
18) What does the acronym AIDS stand for?
Answer: Acquired Immune Deficiency Syndrome
Section: 1.1
Skill: Knowledge/Comprehension
19) What viral coat protein typically binds first to the CD4 receptor on helper T cells?
Answer: gp120
Section: 1.1
Skill: Knowledge/Comprehension
20) When AZT is used to treat HIV infections, why does resistance to AZT usually develop?
Answer: Mutations present in the viral population, due to the lack of proofreading and high error rate of the viral reverse transcriptase, enable mutant virions to discriminate against the incorporation of AZT during transcription.
Section: 1.2
Skill: Application/Analysis
21) It has been observed that viral particles often revert (back mutate to non-AZT-resistant populations when treatment with AZT is discontinued. What is the most likely reason for this observation?
Answer: There is no more selective pressure applied to the viral population, and in the absence of AZT the viral particles that reproduce most efficiently have not evolved enough to have the ability to discriminate against AZT.
Section: 1.2
Skill: Application/Analysis
22) What is the molecular mechanism by which reverse transcriptase inhibitors, such as AZT, prevent viral replication?
Answer: These molecules are analogues of the nucleotide building blocks of DNA, and typically prevent binding or elongation of the of the transcribed DNA molecule.
Section: 1.2
Skill: Knowledge/Comprehension
23) In what host cell protein is the Δ32 mutation found, and what type of mutation is this?
Answer: The Δ32 mutation is found in the CCR5 coreceptor on CD4 helper T cells, and is a 32-base pair deletion.
Section: 1.3
Skill: Knowledge/Comprehension
24) Explain the phylogenetic relationship between humans, chimpanzees, and monkeys in the transmission of the current predominant deadly strain in humans, HIV-1.
Answer: HIV-1 is believed to have originated in monkeys as an SIV (simian immunodeficiency virus); SIV was passed from monkeys to chimpanzees, and SIV was passed to and mutated into HIV-1 sometime around 1930.
Section: 1.4
Skill: Knowledge/Comprehension
25) Explain the mechanism HIV uses to avoid destruction by antibodies present in the human immune system.
Answer: The virus is constantly mutating its surface proteins, and these frequent changes in epitopes on the viral surface prevent the host cell from being able to recognize the virus over time.
Section: 1.5
Skill: Application/Analysis
26) Following long periods of infection with HIV, an X4 strain often evolves. What evolutionary advantage does the X4 strain confer on the viral population, and what specific protein does this strain interact with?
Answer: The evolutionary advantage of this strain is that it can infect a different population of T cells. The alternate population of T cells contains the coreceptor CXCR4 instead of the CCR5 coreceptor.
Section: 1.5
Skill: Application/Analysis
27) What is the function of the product of the viral gene vpu in human infections of HIV?
Answer: The viral gene vpu (in a similar manner to the viral protein nef) blocks the action of the host protein tetherin, which normally adheres to viral particles and attaches them to the host cell membrane and prevents their release.
Section: 1.5
Skill: Knowledge/Comprehension
28) What steps are involved in producing the HIV GP120 protein? List all processes and host cellular structures involved from the point of initial infection with viral RNA to the production of the mature virion outside of the host cell.
Section: 1.1
Skill: Application/Analysis
29) Highly active antiretroviral therapies (HAART) have become the treatment method of choice in treating human HIV infections. What is required for a treatment to be classified as HAART, and why have these treatments proven so effective in the treatment of HIV infections?
Section: 1.2
Skill: Synthesis/Evaluation
30) If an individual is infected with HIV that goes undetected and untreated, the infection follows a standard clinical course of progression. Explain the three sequential phases of untreated HIV infection, the approximate times over which these phases occur, and the corresponding levels of both HIV RNA and CD4 T cells circulating in the host bloodstream.
Section: 1.1
Skill: Knowledge/Comprehension
0 notes
Text
ACC 564 Quiz 3 – Strayer New
ACC 564 Week 8 Quiz 3 Chapter 10 Through 13
Click On The Link Below To Purchase
Instant Download
http://www.budapp.net/ACC-564-Quiz-3-Strayer-New-ACC564Q3.htm
Chapter 10 Information Systems Controls for Systems ReliabilityPart 3: Processing Integrity and Availability
1) The best example of a hash total for a payroll transaction file could be
A) total of employees' social security numbers.
B) sum of net pay.
C) total number of employees.
D) sum of hours worked.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
2) Error logs and review are an example of
A) data entry controls.
B) data transmission controls.
C) output controls.
D) processing controls.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
3) Following is the result of batch control totals on employee Social Security Numbers in a payroll processing transaction:
Correct Values From Masterfile
Values Entered During Processing
487358796
487358796
534916487
534916487
498374526
498374526
514873420
514873420
534196487
534916487
678487853
678487853
471230589
471230589
3719438158
3720158158
The difference in the control totals is 720,000. Which data entry control would best prevent similar data entry errors in the future?
A) Modulus 11
B) Validity check
C) Check digit
D) Sequence check
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
4) Which of the following data entry controls would not be useful if you are recording the checkout of library books by members?
A) Sequence check
B) Prompting
C) Validity check
D) Concurrent update control
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
5) A customer failed to include her account number on her check, and the accounts receivable clerk credited her payment to a different customer with the same last name. Which control could have been used to most effectively to prevent this error?
A) Closed-loop verification
B) Duplicate values check
C) Validity check
D) Reconciliation of a batch control total
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
6) If invoices are processed in groups of fifty, which fields from the document shown below would not be used to create a hash control total?
A) Amount
B) Item Number
C) Quantity Ordered
D) Sales Order number
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Reflective Thinking
7) A data entry input control in which the application software sums the first four digits of a customer number to calculate the value of the fifth digit and then compares the calculated number to the number typed in during data entry is an example of a
A) check digit verification.
B) validity check.
C) closed-loop verification.
D) duplicate data check.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
8) All of the following controls for online entry of a sales order would be useful except
A) check digit verification on the dollar amount of the order.
B) validity check on the inventory item numbers.
C) field check on the customer ID and dollar amount of the order.
D) concurrent update control.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Difficult
AACSB: Analytic
9) A specific inventory record indicates that there were 12 items on hand before a customer brings two of the items to the check stand to be purchased. The cashier accidentally entered quantity 20 instead of 2. Which data entry control would best have prevented this error?
A) sign check
B) limit check
C) validity check
D) field check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
10) When processing weekly payroll, an employee accidentally entered 400 for hours worked. The best data entry control for this error would be
A) a limit check.
B) a check digit.
C) batch total reconciliation.
D) a field check.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
11) The data entry control that would best prevent entering an invoice received from a vendor who is not on an authorized supplier list is
A) a validity check.
B) an authorization check.
C) a check digit.
D) closed-loop verification.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
12) Forms design is an example of this type of control.
A) Data entry control
B) Processing control
C) Output control
D) Input control
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
13) Sequentially prenumbered forms is an example of a(n)
A) data entry control.
B) data transmission control.
C) processing control.
D) input control.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
14) Turnaround documents are an example of a(n)
A) data entry control.
B) output control.
C) processing control.
D) input control.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
15) A validity check is an example of a(n)
A) data entry control.
B) data transmission control.
C) output control.
D) input control.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
16) Parity checks are an example of a(n)
A) data entry control.
B) data transmission control.
C) output control.
D) processing control.
Answer:
Page Ref: 279
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
17) User reviews are an example of a(n)
A) data entry control.
B) data transmission control.
C) output control.
D) processing control.
Answer:
Page Ref: 278
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
18) Data matching is an example of a(n)
A) data entry control.
B) data transmission control.
C) processing control.
D) input control.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
19) Batch totals are an example of a(n)
A) data entry control.
B) data transmission control.
C) output control.
D) processing control.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
20) Cancellation and storage of documents means that
A) data are copied from a document and stored, after which the document is shredded.
B) documents are defaced before being shredded.
C) documents are defaced and stored.
D) cancellation data are copied from documents before they are stored.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
21) Check digit verification is an example of a(n)
A) data transmission control.
B) output control.
C) processing control.
D) input control.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
22) This ensures that the input data will fit into the assigned field.
A) Limit check
B) Range check
C) Size check
D) Validity check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
23) This tests a numerical amount to ensure that it does not exceed a predetermined value nor fall below another predetermined value.
A) Completeness check
B) Field check
C) Limit check
D) Range check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
24) This determines if all required data items have been entered.
A) Completeness check
B) Field check
C) Limit check
D) Range check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
25) This determines the correctness of the logical relationship between two data items.
A) Range check
B) Reasonableness test
C) Sign check
D) Size check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
26) This determines if characters are of the proper type.
A) Field check
B) Alpha-numeric check
C) Range check
D) Reasonableness test
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
27) This tests a numerical amount to ensure that it does not exceed a predetermined value.
A) Completeness check
B) Limit check
C) Range check
D) Sign check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
28) This batch processing data entry control sums a field that contains dollar values.
A) Record count
B) Financial total
C) Hash total
D) Sequence check
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
29) This batch processing data entry control sums a non-financial numeric field.
A) Record count
B) Financial total
C) Hash total
D) Sequence check
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
30) When I enter a correct customer number, the data entry screen displays the customer name and address. This is an example of
A) prompting.
B) preformatting.
C) closed-loop verification.
D) error checking.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
31) This control ensures that the correct and most current files are being updated.
A) Cross-footing balance test
B) Data matching
C) File labels
D) Write-protect mechanism
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
32) This batch processing data entry control sums the number of items in a batch.
A) Financial total
B) Hash total
C) Record count
D) Sequence check
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
33) This data entry control compares the ID number in transaction data to a master file to verify that the ID number exists.
A) Reasonableness test
B) User review
C) Data matching
D) Validity check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
34) File labels are an example of
A) data entry controls.
B) output controls.
C) processing controls.
D) source data controls.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
35) A computer operator accidentally used the wrong master file when updating a transaction file. As a result, the master file data is now unreadable. Which control could best have prevented this from happening?
A) Internal header label
B) Validity check
C) Check digit
D) Parity check
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
36) Chaz Finnerty called the IT Help Desk in a huff. "I'm trying to open an Excel file and I get a message that says that the file is locked for editing. What's going on?" The answer is likely that
A) the file is corrupted due to a computer virus.
B) there is no problem. Chaz is editing the file, so it is locked.
C) concurrent update controls have locked the file.
D) Chaz probably opened the file as read-only.
Answer:
Page Ref: 278
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
37) This control protects records from errors that occur when two or more users attempt to update the same record simultaneously.
A) Concurrent update controls
B) Cross-footing balance test
C) Data conversion controls
D) Recalculation of batch totals
Answer:
Page Ref: 278
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
38) Modest Expectations Investment Services (MEIS) allows customers to manage their investments over the Internet. If customers attempt to sell more shares of a stock than they have in their account, an error message is displayed. This is an example of a
A) reasonableness test.
B) field check.
C) validity check.
D) limit check.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
39) Modest Expectations Investment Services (MEIS) allows customers to manage their investments over the Internet. If customers attempt to spend more money than they have in their account, an error message is displayed. This is an example of a
A) reasonableness test.
B) field check.
C) validity check.
D) limit check.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
40) The Spontaneous Combustion Rocket Shoppe in downtown Fargo, North Dakota, generates three quarters of its revenue from orders taken over the Internet. The revenue clearing account is debited by the total of cash and credit receipts and credited by the total of storefront and Internet sales. This is an example of a
A) data integrity test.
B) zero-balance test.
C) trial balance audit.
D) cross-footing balance test.
Answer:
Page Ref: 278
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
41) What is the most effective way to ensure information system availability?
A) High bandwidth
B) Maintain a hot site
C) Maintain a cold site
D) Frequent backups
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
42) Concerning system availability, which of the following statements is true?
A) Human error does not threaten system availability.
B) Proper controls can maximize the risk of threats causing significant system downtime.
C) Threats to system availability can be completely eliminated.
D) Threats to system availability include hardware and software failures as well as natural and man-made disasters.
Answer:
Page Ref: 284
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
43) Which of the following is not an objective of a disaster recovery plan?
A) Minimize the extent of the disruption, damage or loss.
B) Permanently establish an alternative means of processing information.
C) Resume normal operations as soon as possible.
D) Train employees for emergency operations.
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
44) Which item below would not typically be part of an adequate disaster recovery plan?
A) a system upgrade due to operating system software changes
B) uninterruptible power systems installed for key system components
C) scheduled electronic vaulting of files
D) backup computer and telecommunication facilities
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
45) A facility that contains all the computing equipment the organization needs to perform its essential business activities is known as a
A) cold site.
B) hot site.
C) remote site.
D) subsidiary location.
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
46) A facility that is pre-wired for necessary telecommunications and computer equipment, but doesn't have equipment installed, is known as a
A) cold site.
B) hot site.
C) remote site.
D) subsidiary location.
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
47) When a computer system's files are automatically duplicated on a second data storage system as they are changed, the process is referred to as
A) real-time mirroring.
B) batch updating.
C) consistency control.
D) double-secure storage.
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
48) ________ enables a system to continue functioning in the event that a particular component fails.
A) An incremental backup procedure
B) Fault tolerance
C) Preventive maintenance
D) A concurrent update control
Answer:
Page Ref: 284
Objective: Learning Objective 2
Difficulty : Moderate
AACSB: Analytic
49) A copy of a database, master file, or software that will be retained indefinitely as a historical record is known as a(n)
A) archive.
B) cloud computing.
C) differential backup.
D) incremental backup.
Answer:
Page Ref: 286
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
50) While this type of backup process takes longer than the alternative, restoration is easier and faster.
A) Archive
B) Cloud computing
C) Differential backup
D) Incremental backup
Answer:
Page Ref: 286
Objective: Learning Objective 2
Difficulty : Moderate
AACSB: Analytic
51) ________ involves copying only the data items that have changed since the last partial backup.
A) Archive
B) Cloud computing
C) Differential backup
D) Incremental backup
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
52) ________ copies all changes made since the last full backup.
A) Archive
B) Cloud computing
C) Differential backup
D) Incremental backup
Answer:
Page Ref: 286
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
53) The maximum amount of time between backups is determined by a company's
A) recovery time objective.
B) recovery point objective.
C) recovery objective.
D) maximum time recovery objective.
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Moderate
AACSB: Analytic
54) The maximum acceptable down time after a computer system failure is determined by a company's
A) recovery time objective.
B) recovery point objective.
C) recovery objective.
D) maximum time recovery objective.
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Moderate
AACSB: Analytic
55) The accounting department at Synergy Hydroelectric records an average of 12,500 transactions per hour. By cost-benefit analysis, managers have concluded that the maximum acceptable loss of data in the event of a system failure is 25,000 transactions. If the firm's recovery time objective is 120 minutes, then the worst case recovery time objective is
A) 1 hour
B) 2 hours
C) 3 hours
D) 4 hours
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
56) The accounting department at Synergy Hydroelectric records an average of 10,000 transactions per hour. By cost-benefit analysis, managers have concluded that the maximum acceptable loss of data in the event of a system failure is 20,000 transactions. If the firm's recovery time objective is 60 minutes, then the worst case recovery time objective is
A) 1 hour
B) 2 hours
C) 3 hours
D) 4 hours
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
57) The accounting department at Synergy Hydroelectric records an average of 10,000 transactions per hour. By cost-benefit analysis, managers have concluded that the maximum acceptable loss of data in the event of a system failure is 40,000 transactions. The firm's recovery point objective is therefore
A) 40,000 transactions
B) 10,000 transactions
C) 10 hours
D) 4 hours
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
58) The accounting department at Synergy Hydroelectric records an average of 12,500 transactions per hour. By cost-benefit analysis, managers have concluded that the maximum acceptable loss of data in the event of a system failure is 25,000 transactions. The firm's recovery point objective is therefore
A) 25,000 transactions
B) 12,500 transactions
C) 1 hour
D) 2 hours
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
59) This control entails verifying that the proper number of bits are set to the value 1 in each character received.
A) Echo check
B) Field check
C) Parity check
D) Trailer record
Answer:
Page Ref: 279
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
60) Probably the most important change management control is
A) monitoring user rights and privileges during the change process.
B) testing all changes thoroughly prior to implementation on a stand-alone computer.
C) updating all documentation to reflect changes made to the system.
D) management's careful monitoring and review.
Answer:
Page Ref: 289
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
61) Which of the following is true?
A) Cloud computing is a control technique for system availability.
B) Cloud computing eliminates the need for backup of applications and data.
C) Cloud computing refers to the practice of storing application files and backup data on satellites 'in the clouds'.
D) Cloud computing eliminates the need for companies to own their own software and servers.
Answer:
Page Ref: 288
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
62) Discuss how cloud computing could both positively and negatively affect system availability.
63) Define and contrast a recovery point objective and a recovery time objective.
Accounting Information Systems, 12e (Romney/Steinbart)
Chapter 11 Auditing Computer-Based Information Systems
1) Auditing involves the
A) collection, review, and documentation of audit evidence.
B) planning and verification of economic events.
C) collection of audit evidence and approval of economic events.
D) testing, documentation, and certification of audit evidence.
Answer:
Page Ref: 303
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
2) What is not a typical responsibility of an internal auditor?
A) helping management to improve organizational effectiveness
B) assisting in the design and implementation of an AIS
C) preparation of the company's financial statements
D) implementing and monitoring of internal controls
Answer:
Page Ref: 303
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
3) Which type of work listed below is not typical of internal auditors?
A) operational and management audits
B) information system audits
C) financial statement audit
D) financial audit of accounting records
Answer:
Page Ref: 303
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
4) The ________ audit examines the reliability and integrity of accounting records.
A) financial
B) informational
C) information systems
D) operational
Answer:
Page Ref: 303
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
5) The ________ audit reviews the general and application controls of an AIS to assess its compliance with internal control policies and procedures and its effectiveness in safeguarding assets.
A) financial
B) information systems
C) management
D) internal control
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
6) One type of audit that is concerned with the economical and efficient use of resources and the accomplishment of established goals and objectives is known as a(n) ________ audit.
A) financial
B) information systems
C) internal control
D) operational or management
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
7) The ________ audit is concerned with the economical and efficient use of resources and the accomplishment of established goals and objectives.
A) financial
B) informational
C) information systems
D) operational
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
8) The purpose of ________ is to determine why, how, when, and who will perform the audit.
A) audit planning
B) the collection of audit evidence
C) the communication of audit results
D) the evaluation of audit evidence
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
9) Organizing the audit team and the physical examination of assets are components of which two separate audit stages?
A) planning; evaluating audit evidence
B) planning; collecting audit evidence
C) collecting audit evidence; communicating audit results
D) communicating audit results; evaluating audit evidence
Answer:
Page Ref: 304-305
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
10) With which stage in the auditing process are the consideration of risk factors and materiality most associated?
A) audit planning
B) collection of audit evidence
C) communication of audit results
D) evaluation of audit evidence
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
11) A system that employs various types of advanced technology has more ________ risk than traditional batch processing.
A) control
B) detection
C) inherent
D) investing
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
12) Control risk is defined as the
A) susceptibility to material risk in the absence of controls.
B) risk that a material misstatement will get through the internal control structure and into the financial statements.
C) risk that auditors and their audit procedures will not detect a material error or misstatement.
D) risk auditors will not be given the appropriate documents and records by management who wants to control audit activities and procedures.
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
13) The possibility that a material error will occur even though auditors are following audit procedures and using good judgment is referred to as
A) control risk.
B) detection risk.
C) inherent risk.
D) investigating risk.
Answer:
Page Ref: 305
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
14) The ________ stage of the auditing process involves (among other things) the auditors observing the operating activities and having discussions with employees.
A) audit planning
B) collection of audit evidence
C) communication of audit results
D) evaluation of audit evidence
Answer:
Page Ref: 305
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
15) Verifying the accuracy of certain information, often through communication with third parties, is known as
A) reperformance.
B) confirmation.
C) substantiation.
D) documentation.
Answer:
Page Ref: 305
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
16) The evidence collection method that examines all supporting documents to determine the validity of a transaction is called
A) review of documentation.
B) vouching.
C) physical examination.
D) analytical review.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
17) The evidence collection method that considers the relationships and trends among information to detect items that should be investigated further is called
A) review of the documentation.
B) vouching.
C) physical examination.
D) analytical review.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
18) Assessing the quality of internal controls, the reliability of information, and operating performance are all part of which stage of the auditing process?
A) audit planning
B) collection of audit evidence
C) evaluation of audit evidence
D) communication of audit results
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
19) An auditor must be willing to accept some degree of risk that the audit conclusion is incorrect. Accordingly, the auditor's objective is to seek ________ that no material error exists in the information audited.
A) absolute reliability
B) reasonable evidence
C) reasonable assurance
D) reasonable objectivity
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
20) The risk-based audit approach is
A) a four-step approach to internal control evaluation.
B) a four-step approach to financial statement review and recommendations.
C) a three-step approach to internal control evaluation.
D) a three-step approach to financial statement review and recommendations.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
21) Which of the following is the first step in the risk-based audit approach?
A) Identify the control procedures that should be in place.
B) Evaluate the control procedures.
C) Determine the threats facing the AIS.
D) Evaluate weaknesses to determine their effect on the audit procedures.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
22) Determining whether the necessary control procedures are in place is accomplished by conducting
A) a systems overhaul.
B) a systems review.
C) tests of controls.
D) both B and C
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Difficult
AACSB: Analytic
23) According to the risk-based auditing approach, when a control deficiency is identified, the auditor should inquire about
A) tests of controls.
B) the feasibility of a systems review.
C) materiality and inherent risk factors.
D) compensating controls.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
24) The ________ to auditing provides auditors with a clear understanding of possible errors and irregularities and the related risks and exposures.
A) risk-based approach
B) risk-adjusted approach
C) financial audit approach
D) information systems approach
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
25) What is the purpose of an information systems audit?
A) To determine the inherent risk factors found in the system
B) To review and evaluate the internal controls that protect the system
C) To examine the reliability and integrity of accounting records
D) To examine whether resources have been used in an economical and efficient manner in keeping with organization goals and objectives
Answer:
Page Ref: 307
Objective: Learning Objective 2
Difficulty : Moderate
AACSB: Analytic
26) The information systems audit objective that pertains to source data being processed into some form of output is known as
A) overall security.
B) program development.
C) program modifications.
D) processing.
Answer:
Page Ref: 307
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
27) To maintain the objectivity necessary for performing an independent evaluation function, auditors should not be involved in
A) making recommendations to management for improvement of existing internal controls.
B) examining system access logs.
C) examining logical access policies and procedures.
D) developing the information system.
Answer:
Page Ref: 309
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
28) The auditor's role in systems development should be as
A) an advisor and developer of internal control specifications.
B) a developer of internal controls.
C) an independent reviewer only.
D) A and B above
Answer:
Page Ref: 309
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
29) Regarding program modifications, which statement below is incorrect?
A) Only material program changes should be thoroughly tested and documented.
B) When a program change is submitted for approval, a list of all required updates should be compiled and then approved by management and program users.
C) During the change process, the developmental version of the program must be kept separate from the production version.
D) After the modified program has received final approval, the change is implemented by replacing the developmental version with the production version.
Answer:
Page Ref: 311
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
30) How could auditors determine if unauthorized program changes have been made?
A) By interviewing and making inquiries of the programming staff
B) By examining the systems design and programming documentation
C) By using a source code comparison program
D) By interviewing and making inquiries of recently terminated programming staff
Answer:
Page Ref: 311
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
31) Which auditing technique will not assist in determining if unauthorized programming changes have been made?
A) Use of a source code comparison program
B) Use of the reprocessing technique to compare program output
C) Interviewing and making inquiries of the programming staff
D) Use of parallel simulation to compare program output
Answer:
Page Ref: 311
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
32) Strong ________ controls can partially compensate for inadequate ________ controls.
A) development; processing
B) processing; development
C) operational; internal
D) internal; operational
Answer:
Page Ref: 310
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
33) The ________ procedure for auditing computer process controls uses a hypothetical series of valid and invalid transactions.
A) concurrent audit techniques
B) test data processing
C) integrated test facility
D) dual process
Answer:
Page Ref: 312
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
34) The auditor uses ________ to continuously monitor the system and collect audit evidence while live data are processed.
A) test data processing
B) parallel simulation
C) concurrent audit techniques
D) analysis of program logic
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
35) Auditors have several techniques available to them to test computer-processing controls. An audit technique that immediately alerts auditors of suspicious transactions is known as
A) a SCARF.
B) an audit hook.
C) an audit sinker.
D) the snapshot technique.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
36) A type of software that auditors can use to analyze program logic and detect unexecuted program code is
A) a mapping program.
B) an audit log.
C) a scanning routine.
D) program tracing.
Answer:
Page Ref: 314
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
37) One tool used to document the review of source data controls is
A) a flowchart generator program.
B) a mapping program.
C) an input control matrix.
D) a program algorithm matrix.
Answer:
Page Ref: 314
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
38) An audit software program that generates programs that perform certain audit functions, based on auditor specifications, is referred to as a(n)
A) input controls matrix.
B) CAATS.
C) embedded audit module.
D) mapping program.
Answer:
Page Ref: 317
Objective: Learning Objective 4
Difficulty : Moderate
AACSB: Analytic
39) The use of a secure file library and restrictions on physical access to data files are control procedures used together to prevent
A) an employee or outsider obtaining data about an important client.
B) a data entry clerk from introducing data entry errors into the system.
C) a computer operator from losing or corrupting files or data during transaction processing.
D) programmers making unauthorized modifications to programs.
Answer:
Page Ref: 316
Objective: Learning Objective 3
Difficulty : Difficult
AACSB: Analytic
40) An auditor might use which of the following to convert data from several sources into a single common format?
A) computer assisted audit techniques software
B) Windows Media Converter
C) concurrent audit technique
D) Adobe Professional
Answer:
Page Ref: 317
Objective: Learning Objective 4
Difficulty : Easy
AACSB: Analytic
41) What is the primary purpose of computer audit software?
A) eliminate auditor judgment errors
B) assist the auditor in retrieving and reviewing information
C) detect unauthorized modifications to system program code
D) recheck all mathematical calculations, cross-foot, reprocess financial statements and compare to originals
Answer:
Page Ref: 317
Objective: Learning Objective 4
Difficulty : Easy
AACSB: Analytic
42) The scope of a(n) ________ audit encompasses all aspects of systems management.
A) operational
B) information systems
C) financial
D) internal control
Answer:
Page Ref: 318
Objective: Learning Objective 5
Difficulty : Moderate
AACSB: Analytic
43) Evaluating effectiveness, efficiency, and goal achievement are objectives of ________ audits.
A) financial
B) operational
C) information systems
D) all of the above
Answer:
Page Ref: 318
Objective: Learning Objective 5
Difficulty : Easy
AACSB: Analytic
44) In the ________ stage of an operational audit, the auditor measures the actual system against an ideal standard.
A) evidence collection
B) evidence evaluation
C) testing
D) internal control
Answer:
Page Ref: 318
Objective: Learning Objective 5
Difficulty : Easy
AACSB: Analytic
45) An increase in the effectiveness of internal controls would have the greatest effect on
A) reducing control risk.
B) reducing detection risk.
C) reducing inherent risk.
D) reducing audit risk.
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Difficult
AACSB: Analytic
46) An expansion of a firm's operations to include production in Russia and China will have the effect of
A) increasing inherent risk.
B) reducing inherent risk.
C) increasing control risk.
D) reducing control risk.
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
47) An increase in the effectiveness of auditing software will have the effect of
A) increasing detection risk.
B) reducing detection risk.
C) increasing control risk.
D) reducing control risk.
Answer:
Page Ref: 305
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
48) An auditor examines all documents related to the acquisition, repair history, and disposal of a firm's delivery van. This is an example of collecting audit evidence by
A) confirmation.
B) reperformance.
C) vouching.
D) analytical review.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
49) An auditor manually calculates accumulated depreciation on a delivery van and compares her calculation with accounting records. This is an example collecting audit evidence by
A) confirmation.
B) reperformance.
C) vouching.
D) analytical review.
Answer:
Page Ref: 305
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
50) An auditor finds that employee absentee rates are significantly higher on Mondays and Fridays than on other work days. This is an example collecting audit evidence by
A) confirmation.
B) reperformance.
C) vouching.
D) analytical review.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
51) An auditor creates a fictitious customer in the system and then creates several fictitious sales to the customer. The records are then tracked as they are processed by the system. The auditor is using
A) an integrated test facility.
B) the snapshot technique.
C) a system control audit review file.
D) continuous and intermittent simulation.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Difficult
AACSB: Analytic
52) An auditor sets an embedded audit module to flag all credit transactions in excess of $1,500. The flag causes the system state to be recorded before and after each transaction is processed. The auditor is using
A) an integrated test facility.
B) the snapshot technique.
C) a system control audit review file.
D) audit hooks.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
53) An auditor sets an embedded audit module to record all credit transactions in excess of $1,500 and store the data in an audit log. The auditor is using
A) the snapshot technique.
B) a system control audit review file.
C) audit hooks.
D) continuous and intermittent simulation.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
54) An auditor sets an embedded audit module to flag questionable online transactions, display information about the transaction on the auditor's computer, and send a text message to the auditor's cell phone. The auditor is using
A) the snapshot technique.
B) a system control audit review file.
C) audit hooks.
D) continuous and intermittent simulation.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Difficult
AACSB: Analytic
55) An auditor sets an embedded audit module to selectively monitor transactions. Selected transactions are then reprocessed independently, and the results are compared with those obtained by the normal system processing. The auditor is using
A) an integrated test facility.
B) the snapshot technique.
C) a system control audit review file.
D) continuous and intermittent simulation.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Difficult
AACSB: Analytic
56) Which of the following is not one of the types of internal audits?
A) reviewing corporate organizational structure and reporting hierarchies
B) examining procedures for reporting and disposing of hazardous waste
C) reviewing source documents and general ledger accounts to determine integrity of recorded transactions
D) comparing estimates and analysis made before purchase of a major capital asset to actual numbers and results achieved
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Reflective Thinking
57) When programmers are working with program code, they often employ utilities that are also used in auditing. For example, as program code evolves, it is often the case that blocks of code are superseded by other blocks of code. Blocks of code that are not executed by the program can be identified by
A) embedded audit modules.
B) scanning routines.
C) mapping programs.
D) automated flow charting programs.
Answer:
Page Ref: 314
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
58) When programmers are working with program code, they often employ utilities that are also used in auditing. For example, as program code evolves, it is often the case that variables defined during the early part of development become irrelevant. The occurrences of variables that are not used by the program can be found using
A) program tracing.
B) scanning routines.
C) mapping programs.
D) embedded audit modules.
Answer:
Page Ref: 314
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
59) Explain the differences between each type of audit risk.
60) Explain why the auditor's role in program development and acquisition should be limited.
61) How and to whom does an auditor communicate the audit results?
62) Audit tests and procedures traditionally have been performed on a sample basis. Do options exist for auditors to test significantly more (or all) transactions?
63) When doing an information systems audit, auditors must review and evaluate the program development process. What errors or fraud could occur during the program development process?
64) Briefly describe tests that can be used to detect unauthorized program modifications.
65) Define and give examples of embedded audit modules.
66) How is a financial audit different from an information systems audit?
67) Why do all audits follow a sequence of events that can be divided into four stages, and what are the four stages?
68) Name and describe the different types of audits.
AACSB: Analytic
69) Describe the risk-based audit approach.
71) Describe the disadvantages of test data processing.
72) Describe how audit evidence can be collected.
Accounting Information Systems, 12e (Romney/Steinbart)
Chapter 12 The Revenue Cycle: Sales to Cash Collections
1) In organizations with at least basic segregation of duties, the credit manager reports to the ________ and the treasurer reports to the ________.
A) controller; vice president of finance
B) treasurer; controller
C) marketing manager; vice president of finance
D) treasurer; vice president of finance
Answer:
Page Ref: 331
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
2) In the revenue cycle, before a shipping notice is prepared, the shipping department personnel should match the inventory received from the warehouse to details from
A) picking tickets.
B) sales order and bill of lading.
C) sales order.
D) picking ticket and sales order.
Answer:
Page Ref: 345
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
3) Which is the best control to prevent invoicing customers for the quantity ordered, which was more than the quantity shipped due to items on backorder?
A) Use the information from the packing slip to prepare the sales invoice.
B) Use the information from the picking ticket to prepare the sales invoice.
C) Use the information from the bill of lading to prepare the sales invoice.
D) Use the information from the sales order to prepare the sales invoice.
Answer:
Page Ref: 350
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Reflective Thinking
4) The cashier deposits checks in the bank for Very Large Corporation (VLC) and also prepares payments to vendors. Of the following, who is best to reconcile the bank statement to VLC's records on a regular basis?
A) Internal audit department
B) Treasurer
C) External auditor
D) Cashier
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
5) Which of the following documents normally triggers the billing process in the revenue cycle?
A) Packing slip received from the shipping department
B) Sales order received from the sales department
C) Picking ticket received from the sales department
D) Journal voucher received from the shipping department
Answer:
Page Ref: 348
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
6) Which of the following documents would normally trigger the process to record a customer payment?
A) Remittance advice
B) Customer monthly statement
C) Deposit slip
D) Sales invoice
Answer:
Page Ref: 353
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
7) Which document should always be included with a merchandise shipment to a customer?
A) Packing slip
B) Picking ticket
C) Remittance advice
D) Sales invoice
Answer:
Page Ref: 345
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
8) A monthly statement sent to customers serves a control purpose by
A) providing an opportunity for customers to verify the balance owed and activity on the account.
B) triggering the process to record a customer payment.
C) summarizing invoices and amounts due for customers.
D) reminding customers of the balance due and due date.
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
9) Accounting recognizes a sale when
A) inventory becomes the legal property of the customer.
B) cash is received from the customer.
C) a sales order is approved by sales, inventory control, and credit departments.
D) inventory is removed from the warehouse.
Answer:
Page Ref: 345
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
10) Which of the following is not one of the controls for the mail room where customer payments are commingled with other mail?
A) Requiring the controller to be personally present when mail is received and opened
B) Preparing a remittance list as mail is opened
C) Restrictively endorsing checks when received
D) Requiring two mail room clerks to open mail together
Answer:
Page Ref: 337
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
11) What is the primary objective of the revenue cycle?
A) to maximize revenue and minimize expense
B) to reduce outstanding accounts receivable balances through increased cash sales
C) to provide the right product in the right place at the right time at the right price
D) to sell as much product as possible and/or to maximize service billings
Answer:
Page Ref: 332
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
12) Which of the decisions below is not ordinarily found as part of the revenue cycle?
A) What credit terms should be offered?
B) How often should accounts receivable be subjected to audit?
C) How can customer payments be processed to maximize cash flows?
D) What are the optimal prices for each product or service?
Answer:
Page Ref: 332-333
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
13) Which of the following is not a basic activity of the revenue cycle?
A) sales order entry
B) shipping
C) receiving
D) billing
Answer:
Page Ref: 333
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
14) Retail stores could send their orders directly to the manufacturer's sales order system in a format that would eliminate the need for data entry, using
A) Vendor Managed Inventory.
B) Electronic Data Interchange.
C) Point Of Sale.
D) Electronic Funds Transfer.
Answer:
Page Ref: 338
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
15) Matching customer account numbers and inventory item numbers to the numbers in the customer and inventory master files is an example of a
A) completeness test.
B) field check.
C) reasonableness test.
D) validity check.
Answer:
Page Ref: 339
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
16) During the sales order entry process, a ________ is performed to compare the quantity ordered with the standard amounts normally ordered.
A) completeness test
B) redundant data check
C) field check
D) reasonableness test
Answer:
Page Ref: 339
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
17) During the sales order entry process, a ________ is performed to verify that each transaction record contains all appropriate data items.
A) completeness test
B) redundant data check
C) field check
D) reasonableness test
Answer:
Page Ref: 339
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
18) When a customer places an order (on account) for a certain product, what should be done before the order is checked for inventory availability?
A) The customer's available credit should be checked.
B) The sales order should be created and written to a file.
C) Shipping should be notified of an order in process.
D) A picking list should be generated for the warehouse.
Answer:
Page Ref: 335
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
19) How is credit approval generally handled for established customers with a documented payment history?
A) Specific authorization by the credit manager
B) General authorization by a sales clerk
C) A new credit application is requested
D) A formal credit check should be made for each sale
Answer:
Page Ref: 340
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
20) What is a typical procedure for processing sales orders from new customers or customers making a purchase that causes their credit limit to be exceeded?
A) General authorization to approve the order is given to sales clerks.
B) Specific authorization must be granted by the credit manager.
C) The sale should be rejected.
D) The sales clerk should order a report from a credit bureau before approving the order.
Answer:
Page Ref: 340
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
21) A company should check inventory quantities before accepting a sales order for all the following reasons except to
A) verify the accuracy of the perpetual inventory records.
B) inform the customer about availability and delivery times.
C) know which items may need to be back ordered.
D) update inventory records to reduce the quantity available by the number of items ordered.
Answer:
Page Ref: 341-342
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
22) Responding to customer inquiries and general customer service is an important aspect in the revenue cycle. Since customer service is so important, software programs have been created to help manage this function. These special software packages are called
A) EDI systems.
B) POS systems.
C) VMI systems.
D) CRM systems.
Answer:
Page Ref: 343
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
23) The best solution for maintaining accurate automated perpetual inventory system is to use
A) closed-loop verification when inventory is received from vendors and recorded.
B) point of sale devices integrated with inventory records.
C) periodic physical counts to reconcile with perpetual inventory records.
D) RFID tags.
Answer:
Page Ref: 342
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
24) This document is a legal contract that defines responsibility for goods that are in transit.
A) packing slip
B) bill of lading
C) picking list
D) back order
Answer:
Page Ref: 345
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
25) Two documents usually accompany goods shipped to a customer. What are the two documents?
A) a bill of lading and an invoice
B) a packing slip and a bill of lading
C) an invoice and a packing slip
D) an invoice and a sales order
Answer:
Page Ref: 345
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
26) What is the basic document created in the billing process?
A) bill of lading
B) sales order
C) packing list
D) sales invoice
Answer:
Page Ref: 349
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
27) A company uses the method for tracking accounts receivable where customers pay according to individual sales invoices. This describes the ________ method.
A) monthly statement
B) open-invoice
C) balance forward
D) cycle billing
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
28) A method for tracking accounts receivable that matches specific invoices and payments from the customer is called a(n) ________ method.
A) specific identification
B) balance forward
C) cycle billing
D) open-invoice
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
29) The document a customer returns with their payment and that identifies the source and the amount of the payment is called a
A) remittance advice.
B) remittance list.
C) credit memorandum.
D) debit memorandum.
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
30) In the ________ method of tracking accounts receivable, customers pay according to the amount showing on their monthly statement and payments are applied against the total account balance.
A) specific identification
B) open-invoice
C) balance forward
D) remittance advice
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
31) When a customer pays off the balance on an invoice, the payment is credited to the ________ file.
A) customer master
B) sales transaction
C) cash receipts master
D) All of the above are correct.
Answer:
Page Ref: 351
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Reflective Thinking
32) A type of business document in which part of the original document is returned to the source for further processing is called a ________ document.
A) feedback
B) returnable
C) closed-loop
D) turnaround
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
33) A document typically encountered in the revenue cycle that is both an output document and a source document is the
A) sales invoice.
B) customer purchase order.
C) sales order.
D) packing slip.
Answer:
Page Ref: 349
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
34) A ________ system prepares and mails monthly statements to customers throughout the entire month, instead of just at the end of the month.
A) continuous
B) open-invoice
C) cycle billing
D) balance forward
Answer:
Page Ref: 351
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
35) The accounts receivable department must know when customers pay their invoices, yet segregation of duties controls dictate that the collection and recording functions be kept separate from each other. What is a solution to this potential internal control problem?
A) Have customers send a remittance advice with their payment.
B) Have mailroom personnel prepare a remittance list which can be forwarded to accounts receivable.
C) Establish a lockbox arrangement with a bank.
D) all of the above
Answer:
Page Ref: 353-354
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
36) The benefits of a lockbox arrangement with a bank are maximized when
A) the bank is located nearby to the company, so remittance advices can be delivered to the company every day.
B) several banks around the country are used, in order to minimize the time payments spend in the mail.
C) an arrangement is made with only one bank, so all remittance advices can be batched for processing.
D) the bank deposits the payments and accesses the customer's information system to record the payments.
Answer:
Page Ref: 354
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
37) An arrangement where a bank receives customer payments through the postal system, scans the remittance advices, and transmits payment data to the business electronically is known as
A) e-commerce.
B) an electronic lockbox.
C) electronic funds transfer (EFT).
D) electronic data interchange (EDI).
Answer:
Page Ref: 354
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
38) Customers that send their payments electronically directly to the company's bank are using
A) electronic data interchange (EDI).
B) electronic funds transfer (EFT).
C) procurement cards.
D) an electronic lockbox.
Answer:
Page Ref: 354
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
39) A way to incorporate the advantages of Electronic Data Interchange with the Electronic Funds Transfer is
A) Financial Electronic Data Interchange.
B) e-commerce.
C) to use procurement cards.
D) an electronic lockbox.
Answer:
Page Ref: 354
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
40) Key differences exist when an integrated Enterprise Resource Planning system (ERP) replaces an existing AIS or legacy system. For example, ________ are more accurate and timely, enabling sales order entry staff to provide customers more accurate information about delivery dates.
A) inventory records
B) cash receipts
C) credit approval decisions
D) exception reports
Answer:
Page Ref: 342
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
41) When an ERP is used, it is assumed that there will be increases in efficiency and the effectiveness of the activities related to the revenue cycle. However, what must be in place and functioning well to fully realize these benefits?
A) an effective marketing staff
B) all the components of the expenditure cycle
C) adequate controls
D) adequate system flowchart documentation
Answer:
Page Ref: 335
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
42) The activities involved in soliciting and processing customer orders within the revenue cycle are known as the ________.
A) sales order entry process
B) shipping order process
C) revenue process
D) marketing process
Answer:
Page Ref: 337
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
43) To ensure proper segregation of duties, only the ________ has authority to issue credit memos.
A) accounts receivable supervisor
B) controller
C) credit manager
D) cashier
Answer:
Page Ref: 352
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
44) It has been discovered that credit sales have been made to customers with a poor credit rating. If this continues, the company will face increasing uncollectible receivables and losses due to bad debts. Separation of duties between ________ and ________ should help resolve the problem.
A) shipping; billing duties
B) credit approval; marketing
C) billing; credit approval
D) marketing; accounts receivable
Answer:
Page Ref: 340
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
45) Consider the following revenue cycle scenario: The company has been exposed to customer dissatisfaction and the suggested control procedure to be implemented is to install and use bar-code scanners. What is the threat?
A) The company may be shipping the wrong merchandise.
B) The company may be shipping the wrong quantities of merchandise.
C) The company may be shipping orders to the wrong address.
D) All of the above threats may apply to this scenario.
Answer:
Page Ref: 345
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
46) Which of the following would be the least effective control to minimize the loss of inventory?
A) Secure the storage location of inventory.
B) Release inventory only with proper documentation.
C) Periodically back up all perpetual inventory records.
D) Reconcile the physical counts with and perpetual records.
Answer:
Page Ref: 345
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
47) Separating the shipping and billing functions is designed to reduce the threat of
A) failure to bill customers.
B) billing customers for wrong quantities.
C) billing customers before merchandise has been shipped.
D) shipping the wrong merchandise.
Answer:
Page Ref: 350
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
48) All of the following edit checks for online editing of accounts receivable transactions would probably be included except
A) validity checks on customer ID and invoice numbers.
B) check digit verification on the amount of the sale.
C) closed loop verification on the customer ID.
D) field checks on the values in dollar fields.
Answer:
Page Ref: 352
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
49) When a proper segregation of duties exists in the area of handling cash receipts, the ________, who reports to the ________, actually handles the cash and is not the same person who posts cash receipts to customer accounts.
A) cashier; treasurer
B) cashier; controller
C) accountant; treasurer
D) accountant; controller
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
50) In a revenue cycle with proper controls, the ________ who reports to the ________, is not involved in any cash handling activities.
A) accounts receivable clerk; treasurer
B) accounts receivable clerk; controller
C) cashier; controller
D) cashier; treasurer
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
51) A serious exposure in the revenue cycle is loss of assets. What is the related threat and applicable control procedure that address this exposure?
A) shipping errors; reconciliation of sales order with picking ticket and packing slip
B) theft of cash; segregation of duties and minimization of cash handling
C) making sales that turn out to be uncollectible; force sales people to make collection calls on customers with past due balances
D) poor performance; preparation and review of performance reports
Answer:
Page Ref: 337
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
52) Which of the following duties could be performed by the same individual and not violate segregation of duty controls?
A) handling cash and posting to customer accounts
B) issuing credit memos and maintaining customer accounts
C) handling cash and authorizing credit memos
D) handling cash receipts and mailing vendor payments
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
53) To prevent the loss of valuable data in the revenue cycle, internal file labels can be used to
A) keep competitors from accessing files.
B) record off-site storage locations.
C) organize the on-site physical storage site.
D) reduce the possibility of erasing important files.
Answer:
Page Ref: 277, 335
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
54) The manager of Callow Youth Clothing was entering an order online from Sad Clown Pajamas. He ordered 100 one-size fits all pajama bottoms, but when he ordered 1000 one-size fits all pajama tops, the following error message popped up: "Did you mean to enter a quantity of 1000 for your order?" This message is the result of a
A) reasonableness test.
B) validity check.
C) limit check.
D) closed-loop verification.
Answer:
Page Ref: 339
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Reflective Thinking
55) The manager of Callow Youth Clothing was entering an order online from Sad Clown Pajamas. He entered all the items and quantities, completed the checkout and payment process, but the following error message popped up when he tried to exit the site: "Please enter your email address." This message is likely the result of a
A) customer relationship management software application.
B) validity check.
C) completeness test.
D) closed-loop verification.
Answer:
Page Ref: 339
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Reflective Thinking
56) Sad Clown Pajamas is an Internet-based wholesaler. Customers enter their orders online. The manager of Callow Youth Clothing was entering an order when the following error message popped up: "Your total order exceeds your available credit. A Credit Department representative will contact you within 24 hours." This message is the result of a
A) validity check.
B) reasonableness test.
C) limit check.
D) sign check.
Answer:
Page Ref: 340
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
57) In Petaluma, California, electric power is provided to consumers by the Power To The People Electrical Company, a local co-op. Each month PTTP mails bills to 70,000 households and then processes payments as they are received. The customers are provided with a remittance advice, which is a
A) warning that failure to pay by the due date will result in a late charge.
B) confirmation of the firm's privacy policy.
C) turnaround document.
D) bill.
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
58) Laz Chance wears roller blades and headphones when he is at work at the Squishy Things Toy Company. He is a product packer. The headphones give him computer-generated instructions so he knows the location of each item and quantity that should be included in the order. These instructions are the equivalent of a
A) picking ticket.
B) bill of lading.
C) packing slip.
D) sales order.
Answer:
Page Ref: 342
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
59) The shipping department at Squishy Things Toy Company follows policies that determine which carrier will deliver orders according to the size, weight, and destination of the shipment. It maintains standing agreements with shippers that specify legal responsibility for the shipment while it is in transit. The terms of the agreements are documented on
A) picking tickets.
B) bills of lading.
C) packing slips.
D) RFID tags.
Answer:
Page Ref: 345
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
60) Sad Clown Pajamas is an Internet-based wholesaler. The manager of Callow Youth Clothing received an order from Sad Clown and found that the wrong product had been shipped. He repackaged the order and sent it back for a refund. When Sad Clown Pajamas received the returned product, they mailed a ______ to Callow Youth Clothing's manager.
A) packing slip
B) letter requesting an explanation
C) remittance advice
D) credit memo
Answer:
Page Ref: 352
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
61) A customer service manager at Sad Clown Pajamas, Bob, received a call from the manager at Callow Youth Clothing, who informed Bob that Callow was entering bankruptcy liquidation and it was unlikely that they would be able to pay the outstanding balance on their account. Bob should
A) document the phone conversation and forward it to the billing department manager.
B) prepare a credit memo.
C) approve a credit memo.
D) document the phone conversation and forward it to the credit department manager.
Answer:
Page Ref: 352
Objective: Learning Objective 1
Difficulty : Difficult
AACSB: Reflective Thinking
62) Because it is the most fungible of all assets, the management of cash has always been the most difficult of all control issues. The most important of cash controls is
A) minimization of cash handling.
B) lockbox arrangements.
C) segregation of duties.
D) frequent reconciliation of records.
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
63) A sales clerk at an electronics store scanned the bar code for a low cost set of headphones and then substituted a high cost set of headphones for his friend, who paid the lower price. Which of the following controls would best help to prevent this sort of fraud?
A) Use of RFID tags
B) Physical inventory count
C) Segregation of duties
D) Limited physical access to bar codes
Answer:
Page Ref: 342
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
64) The accounts receivable management method typically used by credit card companies is
A) balance forward.
B) postbilling.
C) monthly statement.
D) open-invoice.
Answer:
Page Ref: 351
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
65) The accounts receivable clerk destroys all invoices for sales made to family and friends and does not record the sales in the accounts receivable subsidiary ledgers. The family and friends usually give the clerk cash as a"thank you". Which procedure will not prevent or detect this fraud?
A) Send monthly statements to all customers with balances owed.
B) Reconcile sales invoices in the billing department to the total debits to accounts receivable subsidiary ledgers.
C) Sequentially prenumber all invoices and prepare a sequence check at the end of each day.
D) Reconcile the accounts receivable control account to the accounts receivable subsidiary ledger.
Answer:
Page Ref: 350
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
66) Which of the following poses an internal control problem?
A) Physical inspection of inventory quantity and condition is outsourced to a firm that specializes in this service.
B) Products are released from inventory after a warehouse employee and a shipping clerk both sign the pick list.
C) Sales representatives have authority to increase customers' credit limits in $1,000 increments.
D) When customer payments are received in the mail, checks are sent to the cashier's office and remittance advices are sent to the accounts receivable department.
Answer:
Page Ref: 340
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
67) For sales returns, the least effective control to prevent fraudulent processing of a credit memo is to
A) reconcile total of credit memos to total debits posted to customers' subsidiary ledgers.
B) require approval for each credit memo by the credit manager.
C) sequentially prenumber all credit memos and perform a sequence check at the end of each day.
D) match each credit memo with a receiving report.
Answer:
Page Ref: 352
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
68) Describe the basic revenue cycle activities.
69) Explain how validity checks, completeness tests and reasonableness tests can be implemented to ensure accuracy of customer orders.
70) Define and describe benefits of a CRM system.
71) How can Electronic Data Interchange (EDI) facilitate the billing and accounts receivable process?
72) Describe typical credit approval procedures.
73) Describe the two methods to manage accounts receivable.
74) Describe cycle billing and identify how an organization might benefit by using cycle billing.
75) Failure to collect cash on credit sales is a threat in the revenue cycle. What controls can be used to help neutralize this threat?
76) Discuss ways in which technology can be used to streamline cash collections.
77) Describe four threats in the revenue cycle and identify appropriate controls for each threat.
78) Discuss the general control issue of the loss of data, as it relates to the revenue cycle.
79) Explain how to effectively segregate duties in the sales order activity.
80) Discuss the revenue cycle threat of stockouts, carrying costs, and markdowns.
81) You have been hired by a catalog company to computerize its sales order entry process. Approximately 70% of all orders are received over the telephone by a sales person. The other 30% of orders are received by a sales person through mail or fax. The catalog company wants the phone orders processed real-time. The mail and fax orders will be processed in batches of 50 orders. The following attributes are collected for every sales order:
Customer number (if the order is from a new customer, a new number needs to be assigned)
Customer name
Address
Payment method (credit card for phone and fax orders and check for mailed orders)
Credit card number and expiration date
Items ordered and quantity of each
Unit price of each item ordered
Identify and describe at least ten specific control policies and procedures you will implement for the sales order process. Be very specific describing the controls and number each new control you suggest.
Accounting Information Systems, 12e (Romney/Steinbart)
Chapter 13 The Expenditure Cycle: Purchasing to Cash Disbursements
1) The Squishy Things Toy Company was established in 1948. It recently signed a large contract with a chain of retail toy stores. As a condition of the contract, the Squishy will be required to track and forecast product sales by linking in to the chain's sales database. Squishy will then be responsible for shipping products to the chain's regional warehouses as needed. The relationship between Squishy and the chain is an example of
A) vendor-managed inventory.
B) sales force automation.
C) electronic data interchange.
D) optical character recognition.
Answer:
Page Ref: 382
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
2) Requiring all packing slips be reconciled to purchase orders before accepting a delivery of inventory would be most likely to prevent which of the following situations?
A) A supplier delivers more inventory than ordered at the end of the year and sends an invoice for the total quantity delivered.
B) An employee mails a fake invoice to the company, which is then paid.
C) The inventory records are incorrectly updated when a receiving department employee enters the wrong product number on the receiving report.
D) Receiving department employees steal inventory and then claim the inventory was received and delivered to the warehouse.
Answer:
Page Ref: 386
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
3) Comparing quantities on a vendor invoice to quantities on the receiving report would not prevent or detect which of the following situations?
A) Receiving and accepting inventory not ordered
B) Theft of inventory by receiving department employees
C) Update of wrong inventory items due to data entry error
D) Order for an excessive quantity of inventory
Answer:
Page Ref: 386
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
4) Which of the following would probably be the least effective control to mitigate the risk of paying an invoice payable to a phony vendor for inventory purchases, mailed to the company by an employee attempting to commit fraud?
A) Only pay from original invoices.
B) Cancel all invoices and supporting documentation when paid.
C) Strict access and authorization controls for the approved vendor master file.
D) Require three-way match for all inventory purchase invoices.
Answer:
Page Ref: 387
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
5) Which of the following would be the least effective control to prevent paying the same vendor invoice twice?
A) Allow only the accounts payable department to authorize payment for vendor invoices and allow only the cash disbursements department to cut and mail checks to vendors.
B) Only pay from original invoices.
C) Cancel each document in the voucher package once the check is prepared and mailed.
D) Only pay vendor invoices that have been matched and reconciled to a purchase order and a receiving report.
Answer:
Page Ref: 391
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
6) To accomplish the objectives set forth in the expenditure cycle, a number of key management decisions must be addressed. Which of the decisions below is not ordinarily found as part of the expenditure cycle?
A) How can cash payments to vendors be managed to maximize cash flow?
B) What is the optimal level of inventory and supplies to carry on hand?
C) Where should inventories and supplies be held?
D) What are the optimal prices for each product or service?
Answer:
Page Ref: 372
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
7) One of the basic activities in the expenditure cycle is the receiving and storage of goods, supplies, and services. What is the counterpart of this activity in the revenue cycle?
A) sales order entry process
B) shipping function
C) cash collection activity
D) cash payments activity
Answer:
Page Ref: 373
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Reflective Thinking
8) The traditional approach to inventory management to ensure sufficient quantity on hand to maintain production is known as
A) safety stock.
B) just-in-time production.
C) economic order quantity.
D) optimal inventory quantity.
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
9) Economic Order Quantity (EOQ) includes several variables that must be taken into consideration when calculating the optimal order size. One variable, the costs associated with holding inventory, is referred to as
A) ordering costs.
B) carrying costs.
C) the reorder point.
D) stockout costs.
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
10) The need to place an order for inventory is specified by the
A) company inventory policies.
B) economic order quantity.
C) stockout point.
D) reorder point.
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
11) When goods are being ordered from a vendor, which electronic files are either read or updated?
A) inventory, vendors, and accounts payable
B) vendors and accounts payable
C) open purchase orders and accounts payable
D) inventory, vendors, and open purchase orders
Answer:
Page Ref: 374
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
12) What is a key feature of materials requirements planning (MRP)?
A) minimize or entirely eliminate carrying and stockout costs
B) reduce required inventory levels by scheduling production rather than estimating needs
C) determine the optimal reorder point
D) determine the optimal order size
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
13) Materials requirements planning (MRP)
A) reduces the uncertainty about when materials are needed, thereby reducing the need to carry large levels of inventory.
B) is able to compute exactly the cost of purchasing by taking into account all costs associated with inventory carrying.
C) requires vendors to deliver inventory to the production site exactly when needed and in the correct quantities.
D) None of the above are correct.
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
14) The inventory management approach that attempts to minimize, if not eliminate, carrying and stockout costs is
A) materials requirements planning.
B) economic order quantity.
C) just-in-time inventory.
D) evaluated receipt settlement.
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Difficult
AACSB: Analytic
15) What aspect below best characterizes a Just-In-Time (JIT) inventory system?
A) frequent deliveries of smaller quantities of items to the work centers
B) frequent deliveries of large quantities to be held at the work centers
C) less frequent deliveries of large quantities of goods to central receiving
D) infrequent bulk deliveries of items directly to work centers
Answer:
Page Ref: 378-379
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
16) What is the key difference between the MRP and JIT inventory management approaches?
A) Only JIT reduces costs and improves efficiency.
B) MRP is especially useful for products such as fashion apparel.
C) JIT is more effectively used with products that have predictable patterns of demand.
D) MRP schedules production to meet estimated sales needs; JIT schedules production to meet customer demands.
Answer:
Page Ref: 379
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
17) MRP will be a preferred method over JIT when the
A) demand for inventory is fairly predictable.
B) demand for inventory is mostly unpredictable.
C) product has a short life cycle.
D) MRP is always a preferred method over JIT.
Answer:
Page Ref: 379
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
18) A key decision in ordering is selecting a suitable vendor. Which of the following would not be a major criterion in vendor selection?
A) prices of goods
B) quality of goods
C) credit rating of the vendor
D) ability to deliver on time
Answer:
Page Ref: 380
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
19) Once a vendor is selected for a product, the vendor's identity is recorded in the
A) purchase requisition transaction file.
B) purchase requisition master file.
C) inventory transaction file.
D) inventory master file.
Answer:
Page Ref: 381
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
20) A purchase order is
A) a document formally requesting a vendor to sell a certain product at a certain price.
B) a request for delivery of certain items and quantities.
C) a contract between the buyer and vendor once accepted by the vendor.
D) All of the above are true.
Answer:
Page Ref: 381
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
21) Stepanek Sales and Service provides free coffee to employees. Stepanek arranged with Ingebrigtson's Joe to deliver as many coffee packages, sugar, creamer, and filters as needed each week. Ingebrigtson's sends a monthly invoice for Stepanek to pay. This arrangement is best described as a
A) blanket purchase order.
B) set purchase order.
C) fixed purchase order.
D) standard purchase order.
Answer:
Page Ref: 381
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
22) A major cost in the purchasing function is the number of purchase orders processed. One technique that may reduce purchasing-related expenses is to have suppliers compete with each other to meet demand at the lowest price. This name of this technique is
A) an EDI auction.
B) a trading exchange.
C) a reverse auction.
D) a supplier consortium.
Answer:
Page Ref: 382
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
23) One of the major responsibilities of the receiving department is
A) deciding if the delivery should be accepted.
B) verifying any purchase discounts for the delivery.
C) deciding on the location where the delivery will be stored until used.
D) updating inventory subsidiary ledgers.
Answer:
Page Ref: 384
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
24) Which of the following is generally not shown on a receiving report?
A) price of the items
B) quantity of the items
C) purchase order number
D) counted and inspected by
Answer:
Page Ref: 384
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
25) A receiving clerk notes that a delivery of 10 units has been received, but the purchase order specified 12 units. A debit memo will need to be prepared to adjust for the difference between the quantity ordered and received. Who should prepare this document?
A) the receiving clerk
B) the controller
C) the vendor
D) the purchasing department manager
Answer:
Page Ref: 385
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
26) Identify in which of the following scenarios a company could adjust the balance due the vendor by issuing a debit memo.
A) quantity different from that ordered
B) damage to the goods
C) goods that fail inspection for quality
D) All of the above are possible scenarios.
Answer:
Page Ref: 385
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
27) What is one of the best ways to improve the overall efficiency and effectiveness of the receipt and storage of ordered items?
A) requiring all suppliers to have the carrier verify quantities and item numbers before shipment
B) requiring all suppliers to include RFID tags on their items
C) requiring all suppliers to use EDI to expedite the receiving department function
D) requiring all delivery trucks to have satellite data terminals to expedite the receiving department function
Answer:
Page Ref: 385
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
28) Vendor invoices are approved by the ________, which reports to the ________.
A) purchasing department; controller
B) accounts payable department; treasurer
C) purchasing department; treasurer
D) accounts payable department; controller
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
29) The disbursement voucher and supporting documents are sent to the ________ for payment prior to the due date.
A) cashier
B) treasurer
C) controller
D) accounts payable department
Answer:
Page Ref: 390
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
30) A(n) ________ system posts an approved invoice to the vendor account and stores it in an open invoice file until payment is made by check.
A) nonvoucher
B) voucher
C) cycle
D) evaluated receipt settlement
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
31) A disbursement voucher contains
A) a list of outstanding invoices.
B) the net payment amount after deducting applicable discounts and allowances.
C) the general ledger accounts to be debited.
D) All of the above are correct.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
32) One objective of accounts payable is to authorize payment only for goods or services actually ordered and received. The best way to process supplier invoices is to use
A) electronic funds transfer for small, occasional purchases from suppliers.
B) a nonvoucher system.
C) EDI for all small, occasional purchases from suppliers.
D) a disbursement voucher system.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
33) What is not an advantage of using disbursement vouchers?
A) Disbursement vouchers reduce the number of checks written.
B) Disbursement vouchers can be prenumbered which simplifies the tracking of all payables.
C) Disbursement vouchers facilitate separating the time of invoice approval from the time of invoice payment.
D) There are no disadvantages to using disbursement vouchers.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
34) Which of the following is not an advantage of a voucher system?
A) Several invoices may be included on one voucher, reducing the number of checks.
B) Disbursement vouchers may be pre-numbered and tracked through the system.
C) The time of voucher approval and payment can be kept separate.
D) It is a less expensive and easier system to administer than other systems.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
35) Duties in the expenditure cycle should be properly segregated to promote internal control. This means that the authorization function is performed by ________, the recording function is performed by ________, and cash handling is performed by the ________.
A) accounts payable; purchasing; cashier
B) purchasing; accounts payable; cashier
C) purchasing; cashier; accounts payable
D) purchasing; accounts payable; treasurer
Answer:
Page Ref: 375
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
36) A voucher package should include
A) a purchase requisition, vendor invoice, and receiving report.
B) a purchase order, vendor invoice, and receiving report.
C) a purchase requisition, purchase order, and receiving report.
D) a bill of lading and vendor invoice.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
37) Evaluated receipt settlement (ERS) approves payment of vendor invoices after reconciling the purchase order and the
A) vendor invoice.
B) sales invoice.
C) receiving report.
D) disbursement voucher.
Answer:
Page Ref: 388
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
38) All of the following are opportunities to improve efficiency of the accounts payable function except
A) use blanket purchase orders.
B) convert a manual AIS system to EDI and EFT.
C) streamline noninventory purchases.
D) use evaluated receipt settlement.
Answer:
Page Ref: 387-388
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
39) When purchasing miscellaneous supplies, companies can reduce costs, improve efficiency, and combat employee fraud by
A) using procurement cards.
B) implementing a JIT inventory system.
C) requiring employees to personally purchase items then reimbursing employees at the end of each month.
D) paying amounts out of petty cash.
Answer:
Page Ref: 389
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
40) If available, a 1% discount for payment within 10 days instead of 30 days represents an approximate savings of ________ % annually.
A) 1
B) 12
C) 18
D) 36
Answer:
Page Ref: 390
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
41) What is the best control to mitigate the threat of paying prices that are too high for goods ordered?
A) require the receiving department to verify the existence of a valid purchase order
B) use only approved suppliers and solicit competitive bids
C) only pay invoices that are supported by the original voucher package
D) use bar-code technology to eliminate data entry errors
Answer:
Page Ref: 382
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
42) What is probably the most effective control for the prevention of kickbacks to purchasing agents?
A) purchasing from approved vendors
B) diligent supervision in the purchasing department
C) a corporate policy to prohibit purchasing agents from accepting kickbacks
D) reviews of vendor performance
Answer:
Page Ref: 383
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
43) One of the threats associated with the process and activity of receiving and storing goods is
A) errors in counting.
B) kickbacks.
C) requests for unnecessary items.
D) errors in vendor invoices.
Answer:
Page Ref: 385
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
44) What is the best way to prevent the acceptance of unordered goods?
A) Order only from approved vendors.
B) Match the packing slip to a purchase order before accepting delivery.
C) Enforce an appropriate conflict of interest policy in place.
D) Require specific authorization from the purchasing manager before accepting any goods.
Answer:
Page Ref: 386
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
45) Which of the following is not a common control for ensuring inventory is secure and inventory counts are accurate?
A) control of physical access to the inventory storage areas
B) transfers of inventory with proper documentation
C) sending "blind" copies of purchase orders to inventory control for data entry
D) making physical counts of inventory at least once per year
Answer:
Page Ref: 376
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
46) Double-checking the accuracy of an invoice is a control that can help to neutralize a threat in the expenditure cycle. What activity would specifically be associated with this control?
A) ordering goods
B) receiving and storing goods
C) paying for goods and services
D) requesting goods be ordered
Answer:
Page Ref: 389
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
47) What control would best mitigate the threat of paying an invoice twice?
A) never authorize payment of a photocopy of an invoice
B) double-check mathematical accuracy of invoices
C) approval of purchase orders
D) maintaining adequate perpetual inventory records
Answer:
Page Ref: 391
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
48) Which control would best prevent payments made to fictitious vendors?
A) Allow payments only to approved vendors.
B) Restrict access to any payment or approval documents.
C) Have an independent bank reconciliation.
D) Make sure all documents are in order before approving payments.
Answer:
Page Ref: 392
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
49) In the expenditure cycle, good control dictates that expenditures should be paid by check. This may not be feasible when minor purchases are made. To facilitate quick payment for minor purchases, a(n) ________ should be set up and maintained using ________.
A) special bank account; disbursement vouchers
B) imprest fund; vouchers
C) cash box; small denomination bills
D) petty cash fund; procurement cards
Answer:
Page Ref: 392
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
50) A surprise count of an imprest petty cash fund should find the total of ________ equal to the amount authorized for the fund.
A) cash and credit memos
B) cash and vouchers
C) cash
D) cash and checks
Answer:
Page Ref: 392
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
51) What control should be put in place that assigns responsibility for EFT payments made to vendors?
A) Encrypt all EFT transmissions.
B) Time stamp all EFT transactions.
C) Establish a control group to monitor EFT transactions for validity and accuracy.
D) Number all EFT transactions.
Answer:
Page Ref: 391
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
52) Which of the following threats is not specific to the purchase requisition process of the expenditure cycle?
A) stockouts
B) purchasing from unauthorized vendors
C) requisitioning goods not needed
D) All of the above are threats in the purchase requisition process.
Answer:
Page Ref: 380
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
53) There is a symmetrical interdependence between a firm's expenditure cycle and its suppliers'
A) production cycle.
B) revenue cycle.
C) expenditure cycle.
D) general ledger and reporting system.
Answer:
Page Ref: 372
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Reflective Thinking
54) The Squishy Things Toy Company was established in 1948. It recently signed a large contract with a chain of retail toy stores. As a condition of the contract, the Squishy will be required to track and forecast product sales by linking in to the chain's sales database. Squishy will then be responsible for shipping products to the chain's regional warehouses as needed. The technology that is used for communication between Squishy and the chain is
A) vendor-managed inventory.
B) sales force automation.
C) electronic data interchange.
D) optical character recognition.
Answer:
Page Ref: 372
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
55) The management at Sad Clown Pajamas, an Internet-based wholesaler, is considering a new inventory control system. The current system is inadequate because it results in stockouts that interrupt production and excess stocks of some materials that result in markdowns and high carrying costs. The new system, which will focus on ensuring that the amounts purchased minimize these costs, will employ
A) a just-in-time inventory system.
B) the economic order quantity.
C) a reorder point.
D) materials requirements planning.
Answer:
Page Ref: 378
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
56) The management at Sad Clown Pajamas, an Internet-based wholesaler, is considering a new inventory control system. The current system is inadequate because it results in stockouts that interrupt production and excess stocks of some materials that result in markdowns and high carrying costs. The new system, which will focus on ensuring that orders are placed with sufficient lead time to prevent stockouts, will employ
A) a just-in-time inventory system.
B) the economic order quantity.
C) a reorder point.
D) materials requirements planning.
Answer:
Page Ref: 378
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
57) The management at Sad Clown Pajamas, an Internet-based wholesaler, is considering a new inventory control system. The current system is inadequate because it results in stockouts that interrupt production and excess stocks of some materials that result in markdowns and high carrying costs. The new system, which will focus on forecasting demand for Sad Clown's products, will employ
A) a just-in-time inventory system.
B) the economic order quantity.
C) a reorder point.
D) materials requirements planning.
Answer:
Page Ref: 378
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
58) The management at Sad Clown Pajamas, an Internet-based wholesaler, is considering a new inventory control system. The current system is inadequate because it results in stockouts that interrupt production and excess stocks of some materials that result in markdowns and high carrying costs. The new system, which will focus on reducing or completely eliminating carrying costs, will employ
A) a just-in-time inventory system.
B) the economic order quantity.
C) a reorder point.
D) materials requirements planning.
Answer:
Page Ref: 378
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
59) Bob Chum is the sales manager at Folding Squid Technologies. At lunch with the company CEO, he proudly announced that he had negotiated a(n) ________ with a client that defined a long-term commitment to buy components from Folding Squid.
A) purchase order
B) blanket purchase order
C) evaluated receipt settlement
D) voucher
Answer:
Page Ref: 381
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
60) Bob Chum is the sales manager at Folding Squid Technologies. At lunch with the company CEO, he proudly announced that he had received a ________ from a client to buy a large quantity of components from Folding Squid.
A) purchase order
B) blanket purchase order
C) voucher
D) purchase requisition
Answer:
Page Ref: 381
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
61) Bob Chum is the sales manager at Folding Squid Technologies. At lunch with the company CEO, he complained that a recent shipment from a vendor had been unsatisfactory and so had to be returned. That required the purchasing manager to send a ________ to the supplier.
A) purchase order
B) blanket purchase order
C) receiving report
D) debit memo
Answer:
Page Ref: 385
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
62) To minimize the number of checks that need to be written to pay vendor invoices a company should use a
A) voucher system.
B) just-in-time inventory system.
C) nonvoucher system.
D) evaluated receipt settlement system.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
63) Evaluated receipt settlement increases efficiency by
A) eliminating the need for receiving reports.
B) eliminating the need for vendor invoices.
C) eliminating the need for purchase orders.
D) eliminating the need to prepare and mail checks.
Answer:
Page Ref: 388
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
64) In the expenditure cycle, Financial Electronic Data Interchange (FEDI) increases efficiency by
A) eliminating the need for receiving reports.
B) eliminating the need for vendor invoices.
C) eliminating the need for purchase orders.
D) eliminating the need to prepare and mail checks.
Answer:
Page Ref: 390
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
65) Procurement cards differ from corporate credit cards in which of the following ways?
A) Credit limits can be set for procurement cards, but not corporate credit cards.
B) Credit cards can be used to make purchases without an explicit sign off by supervisors, but procurement cards require a sign off.
C) Procurement cards can only be used with approved vendors, but credit cards can be used anywhere.
D) Procurement card invoices are sent separately for each card, whereas corporate credit cards are consolidated into a single invoice.
Answer:
Page Ref: 389
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
66) The purchasing manager at Folding Squid Technologies has responsibility for reviewing and authorizing purchase orders. He also reviews receiving reports, approves or corrects them, and authorizes the cashier to pay vendor invoices. Which of the following would correct control weaknesses, if any, related to these activities?
A) Vendor invoices should be reviewed by the purchasing manager to ensure that they are correct.
B) Accounts payable should reconcile purchase orders, receiving reports, and invoices.
C) Vendor invoices should be reviewed by accounts receivable and then cancelled when paid.
D) Controls are adequate under the current system.
Answer:
Page Ref: 387
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
67) The purchasing manager at Folding Squid Technologies has responsibility for reviewing and authorizing purchase orders. Receiving reports are prepared by shipping and receiving based on the relevant purchase order(s). Purchase orders, receiving reports, and vendor invoices are reconciled by accounts payable, which authorizes payment. Which of the following would correct control weaknesses, if any, related to these activities?
A) Vendor invoices should be reviewed by the purchasing manager to ensure that they are correct.
B) Accounts payable should authorize purchase orders.
C) Receiving reports should be reviewed and corrected by the purchasing manager.
D) Controls are adequate under the current system.
Answer:
Page Ref: 387
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
68) The receiving clerk at Folding Squid Technologies examines incoming shipments and reconciles their contents with the relevant purchase orders. A receiving report is then sent to accounts receivable and the vendor's invoice is approved for payment. Which of the following would correct control weaknesses, if any, related to these activities?
A) The invoice should be approved for payment by the shipping clerk after the purchase order and receiving report are reconciled.
B) Accounts payable should reconcile the purchase order and the receiving report.
C) Invoices, purchase orders, and receiving reports should be reconciled by the receiving clerk.
D) Controls are adequate under the current system.
Answer:
Page Ref: 387
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
69) The receiving clerk at Folding Squid Technologies examines incoming shipments and checks their purchase order numbers. A receiving report is then sent to accounts payable, where it is reconciled with the relevant purchase orders and invoices and payment is authorized. Which of the following would correct control weaknesses, if any, related to these activities?
A) Vendor invoices should be approved for payment by the shipping clerk after the purchase order and receiving report are reconciled.
B) Vendor invoices should be approved for payment by the purchasing manager.
C) Purchase orders and receiving reports should be reconciled by the purchasing manager.
D) Controls are adequate under the current system.
Answer:
Page Ref: 387
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
70) Which of the controls below would be least effective to prevent ordering goods at higher than market prices?
A) Variance analysis of actual expenses to budgeted expenses
B) For high-dollar goods, solicit competitive bids from possible vendors
C) Only place orders with vendors on an approved vendor list
D) Frequent review of, and update to, vendor price lists stored in the AIS
Answer:
Page Ref: 382
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
71) The document below would be known as what by Alpha Omega Electronics?
A) Receiving report
B) Purchase order
C) Purchase requisition
D) Packing slip
Answer:
Page Ref: 384
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Reflective Thinking
72) Which of the following would be the best control to prevent receiving department employees from stealing inventory and claiming the ordered quantity wasn't received from the vendor?
A) Reconcile quantity on packing slip to physical count when accepting delivery.
B) Restrict physical access to the receiving area.
C) Require all deliveries be made at the receiving area.
D) Require dual signatures on the move ticket when receiving delivers the inventory to the warehouse.
Answer:
Page Ref: 386
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
73) Define and describe the EOQ approach to inventory management.
74) Discuss the differences between EOQ, MRP, and JIT.
75) a) What is the major cost driver in the purchasing function? b) Describe how information technology can be used to control this cost driver.
76) Explain what is meant by the expenditure cycle as a "mirror image" of the revenue cycle.
77) Identify possible problems associated with receiving goods and appropriate actions in response to the problems.
78) How can information technology be used to improve the vendor invoice approval process?
79) Under what conditions is MRP more suitable than JIT and vice versa?
80) In the expenditure cycle, the majority of payments made are by check. What are some control issues related to payment of vendors by check?
81) Identify ten threats and applicable control procedures in the expenditure cycle.
82) What types of decision-making and strategic information should the AIS provide in the expenditure cycle?
83) How can using RFID tags or bar codes on goods or products provide significant benefit in the expenditure cycle?
0 notes
Text
Tips on Solving English Grammar Test Questions on Articles
Grammar Rules with 10 Tips for using Articles
What is an Article?
Article: used before Nouns or Noun phrases to limit or define them.
Types Of Articles:
1. Definite Article: ‘The’ points out a particular person or thing, in the sense of ‘this’ or ‘that’.
Example: Give me the book. (‘That’ specific book)
2. Indefinite Article: ‘A’ and ‘An’ refer to non-specific, singular person or thing, in the sense of ‘one’ or ‘any’.
Example: Give me a book/ an orange. (Any book or orange)
A: used when the next word starts with a consonant, or before words starting in ‘u’ and ‘eu’ when they sound like ‘you’. (A boy, a uniform)
An: when the next word starts with a vowel (a, e, i, o, u) or with a mute ‘h’. (An apple, an hour)
Usage of A, An:
1. To refer to something for the first time: Would you like a cup of coffee?
2. With names of jobs: Jyoti is a doctor.
3. With identities (nationalities and religions) in the singular: John is an Englishman.
4. When referring to a day of the week but not a specific day: I was born on a Thursday.
5. To refer to an example of something: The mouse had a tiny nose.
6. With singular nouns after the words 'what' and 'such’: What a lovely day!
7. Referring to people when there is vagueness: A Mr. Gupta is going to come.
8. When referring to a singular object or a single unit of measure: I’d like an orange and two lemons, please.
9. When a singular countable noun represents a class of things, persons or animals: A son should be obedient.
Usage of The:
1. Something which has already been mentioned: The thief has not been caught yet.
2. When there is just one of something in a place: Where is the bathroom?
3. In sentences or clauses that define or identify a particular person or object: The man who wrote this book is famous.
4. Before the choices in comparative degree: He is the poorer of the two brothers.
5. Before proper nouns which are unique: We went to the Taj Mahal.
6. Before dates: He was born on the 10th of May.
7. Give the meaning of an abstract noun to a common noun: It brought out the beast in him.
8. As an adverb in a comparative sense: The sooner you come, the better.
9. Before superlatives and ordinal numbers: This is the highest building in Delhi.
Cases where articles should not be used:
1. With the names of meals: A Dinner is my favorite meal.
2. Before uncountable nouns: He gave me the advice.
3. Before hobbies, professions or sports: A Gardening is her hobby.
4. Before titles when combined with names: The Prince Charles is a Queen Elizabeth's son.
5. With years: The 1978 was a wonderful year.
6. Before collective nouns in the general sense: A Life is a struggle.
7. Before noun complements: The board appointed him the captain.
8. Before proper nouns: A Gold is good for investment.
9. Before common nouns or abstract nouns: An Honesty is the best policy.
Tips on using Articles:
Tip #1: Names of countries Country Names: Generally, definite article is not used with country names.
The India is a great country. Use ‘the’ with countries whose names include words like kingdoms, states, and republic:
He lives in the United States of America. Use ‘the’ with countries which have plural nouns as their names:
Manila is the capital of the Philippines
Tip #2: Specific geographic locations Geographical features: Definite article is used before mountain ranges, groups of islands, rivers, seas, oceans and canals.
The Himalayas are the largest mountain range in the world. No article is necessary before Singular names of countries or territories, cities, towns, states, streets, lakes, bays, mountains, continents, islands, languages, sports, academic subjects.
The highest mountain in the world is the Mount Everest. (Everest is a single mountain and not a mountain range, so no definite article is used before it)
Tip #3: Proper Nouns People’s Names: usually no article is used before people’s names or proper nouns.
The Harishchandra is a legendary king. But ‘a or an’ is used to make a common noun from a proper noun to express some quality associated to it.
He is a Harishchandra when it comes to keep his promises. (Here ‘Harishchandra’ represents a quality like ‘utmost honesty’)
Tip #4: For a Walk, In a Hurry, A Million Noun acting as verbs: Indefinite articles are used before nouns but they can be used before verbs when the verbs are acting as nouns.
Words denoting numbers: ‘A’ is also used before words denoting numbers like-a million, a dozen.
Phrases: Indefinite articles are also used in certain phrases like -in a hurry, have a mind, make a noise.
I have told you a dozen times not to go for a walk in a hurry.
(Here, ‘walk’ is a verb acting as a noun, so ‘a’ is used before it, like we say –for a talk, for a swim etc.)
Tip #5: Little, A Little, The Little Little: means not much (i.e., hardly any) and has a negative meaning.
There is little hope of his recovery. (There really isn’t much hope) A little: means some though not much and has a positive meaning. Used with uncountable nouns.
There is a little hope of his recovery. (There is some hope of recovery) The little: means not much, but all there is.
The little knowledge of carpentry that he possessed stood him in good stead.
Tip #6: Few, a Few, the Few Few: means hardly anyone and has a negative meaning.
I have few enemies. (I really don’t have any enemies) A few: means small in number but not many either.
I have a few enemies. (I have a small number of enemies) The few: means not many, but all there is.
The few days I had spent in Darjeeling were very pleasant.
Tip #7: Singular vs. plural forms for ordinals Ordinals: These are words that express position or rank in sequential order. E.g. first, second etc.
If there is an article before each ordinal, use the singular noun.
The second and the third chapter is easy. If there is one article only before both ordinals, use the plural noun.
The second and third chapters are easy.
Tip #8: French, a French, the French Language and Origin: Definitive and indefinite articles are used with certain words depending on their function.
French is spoken in many countries.
(Here ‘French’ implies a language, so no definite article is used before it)
He is a French national. (‘French’ is a adjective) The French are a courteous people. (Here ‘French’ represent a community) The French Revolution changed the course of history. (‘The’ is used before revolutions, events, dynasties, empires etc.)
Tip #9: Repetition of articles Repetition or non-repetition of articles in a single sentence changes the meaning:
1. She has a black and white saree. (She has only one saree which is partly black and partly white)
2. She has a black and a white saree. (She has two sarees, one black and one white)
3. The Secretary and Treasurer was present there. (One person who is both Secretary and Treasurer)
4. The Secretary and the Treasurer were present there. (Two separate persons, one Secretary and the other Treasurer.
Tip #10: The Ritz Hotel, Brown’s Hotel Use and absence of ‘the’:
1. We are staying at the Ritz Hotel. (‘The’ is used before names of hotels, pubs, restaurants etc.) 2. We had breakfast at the Brown’s hotel. (do not use the definite article if the name of the hotel or restaurant is the name of the owner)
Spot the Errors:
Each of the following sentences will contain a mistake in Articles. See if you can spot that mistake.
#1: They don’t have a heir to inherit the family property. (Incorrect) They don’t have an heir to inherit the family property. (Correct)
#2: I studied the Sanskrit in high school for four years. (Incorrect) I studied Sanskrit in high school for four years. (Correct)
#3: Please give me a water to drink. (Incorrect) Please give me (some) water to drink. (Correct)
#4: Are you driving my the car? (Incorrect) Are you driving my car? (Correct)
#5: The hypertension is called the silent killer. (Incorrect) Hypertension is called the silent killer. (Correct)
#6: I would like to visit an Eiffel Tower. (Incorrect) I would like to visit the Eiffel Tower. (Correct)
#7: They are planning an European holiday for the vacations. (Incorrect) They are planning a European holiday for the vacations. (Correct)
#8: Mary is training to be the engineer. (Incorrect) Mary is training to be an engineer. (Correct)
#9: The creativity should be encouraged in children. (Incorrect) Creativity should be encouraged in children. (Correct)
#10: I was always good at a math. (Incorrect) I was always good at math. (Correct)
#11: He is the pupil at Bishop Cotton High school. (Incorrect) He is a pupil at Bishop Cotton High school. (Correct)
#12: I read a Times of India every morning. (Incorrect) I read Times of India every morning. (Correct)
#13: She is learning a guitar. (Incorrect) She is learning the guitar. (Correct)
#14: This is a best book on elementary chemistry. (Incorrect) This is the best book on elementary chemistry. (Correct)
#15: Twelve inches make the foot. (Incorrect) Twelve inches make a foot. (Correct)
#16: I can't forget kindness with which he treated me. (Incorrect) I can't forget the kindness with which he treated me. (Correct)
#17: The uncle is coming to our place next week. (Incorrect) Uncle is coming to our place next week. (Correct)
#18: These traditions are in place since Vedic ages. (Incorrect) These traditions are in place since the Vedic ages. (Correct)
#19: This man is Shylock when it comes to allotting budget. (Incorrect) This man is a Shylock when it comes to allotting budget. (Correct)
#20: The first and the second phases of election is over. (Incorrect) The first and the second phase of election is over. (Correct)
(contd..) Tips on Solving English Grammar Test Questions on Articles - https://learningpundits.com/module-view/15-articles/1-tips-on-articles/
0 notes
Text
Annotated Bibliography
Alien/Freak/Monster
Professor Loza
October 18, 2016
Cohen, C. J. (1997). Punks, Bulldaggers, and Welfare Queens: The Radical Potential of Queer Politics?. GLQ: A Journal of Lesbian and Gay Studies, 3(4), 437-465.
A queer entering the heteronormative, capitalist mall is subverting cultural norms. In addition to be more likely to be working class if you are queer, class might be a reason that entering a mall is a statement. Yet, queer people of color might also be met in addition to these other social injustices, racism from mall-goers. For example Ax from the Animorphs series is a Yeerk alien who takes DNA from the two girls and two boys of the series and mixing that together to create a human morph that he ca go to the mall looking like. The human form is said to look like a very feminine boy or masculine girl, not placing him anywhere on the gender spectrum performance-wise. The article goes on to discuss how queer activists of color can not separate themselves from dominant culture and are subject to power struggles. In addition there is a call for more black gay theorists.
Conley, J. (1978). Sex differences and androgyny in fantasy content. Journal of personality assessment., 42(6), 604–10. Retrieved from https://www.ncbi.nlm.nih.gov/pubmed/16367089
This was the conclusion of a study of over 153 undergraduate works spanning 1950s-70s which looked into the ability to vary in imagery based on gender and sexuality. Accordingly, “The fantasies of sex-typed persons were more situation-bound and more sexual than those of androgynous persons. Sex-typed persons appear to experience limitations in fantasy production which parallel their limitations in overt behavior”(Conley 604). This allows characters such as Soren, an androgynous and asexual character from the Star Trek franchise, to act more as themselves than other characters, but also others them to the point that they are questioning the validity of living in a genderless culture. They question their sexuality and have a lot of inner turmoil about how they have been raised. This is similar to the struggle of agendered people feel when the binary transgender community rejects the validity of their existence. Yet, there is no heteronormative expectation-roadmap that says how they need to be.
DE LAURETIS, T. (1987). THE TECHNOLOGY OF GENDER. In Technologies of Gender: Essays on Theory, Film, and Fiction (pp. 1-30). Indiana University Press. Retrieved from http://www.jstor.org/stable/j.ctt16gzmbr.4
It seems that many of the papers and chapters I have been reading through have focused on variant ways of reproducing and how sexuality is a part of gender representation, which I don’t agree with but think it is important to discuss how these examples are imaginations of the transgender experience seen through white feminism in the 60s and 70s in the theory discussing literature in film. In addition three out of the five works I have read so far have all quoted or alluded to Judith Butler. In addition much work is not canonically queer but can be read as such due to different characters disrupting gender norms such as tall or masculine women and feminine and sensitive men. “The representation of genera is its construction—and in the simplest sense it can be said that all of Western Art and high culture is the engraving of the history of that construction. The construction of gender goes on as busily today as it did in earlier times”(de Lauretis 5). These are two points she sets up to give examples of further into the book, so I plan on looking further because of how related those are to what I am discussing.
Ginsberg, Elaine K. (1996). Passing and the fictions of identity. Durham, NC:Duke University Press.
In relation to gender and racially passing as what is decided to be the white binary norm, “presumably one cannot pass for something one is not unless there is some other”(Ginsberg 4) This piece gives more historical examples than fictional, but the image created is related directly from past creations of other to form the othering that continues to happen to marginalized peoples today. What about a mixed race bigender pansexual? The idea of performing part of an identity for that person will always disconnect part of who they are.
Haraway, D. (2006). Cyborgs: A Myth of Political Identity. In S. Stryker & S. Whittle (Comps.), The Transgender Studies Reader (pp. 103-116). New York, NY: Routledge Taylor & Francis Group.
The authors starts off relating women of color to cyborgs and then through that to the creation of otherness in feminist monstrosity theory. Then Stryker and Whittle begin to discuss uncategorizable existence that cyborgs have due to their fantastical origins with science of today making it possible for making bodies more accessible technologically within this century, possibly decade. Created bodies can be friendly and human without being born, “High-tech culture challenges these dualisms in intriguing ways. It is not clear who makes and who is made in the relation between and machine. It is not clear what is mind and what is body...we find ourselves to be cyborgs, hybrids, chimeras”(113 Stryker). This relates to the transgender experience in being a created identity outside of biological understandings. The cartoon network show Adventure Time has a character named BMO who is canonically non-binary. There is a full episode called Football where dysphoria is depicted through BMO’s other self named Football where they switch between their different identities. In gender-swapped episodes of the show BMO remains the same. They are able to do this because they are a robot who lives outside of binary contexts even though, like trans* people, they live in a society and in their bodies’ technological makeup that is binary. But, BMO rejects that by not being human. BMO has everyone call them Football and is constantly tormented by their reflection.
MELZER, P. (2006). Beyond Binary Gender: Genderqueer Identities and Intersexed Bodies in Octavia E. Butler’s Wild Seed and Imago and Melissa Scott’s Shadow Man. In Alien Constructions (pp. 219-258). University of Texas Press.
Shapeshifters constantly are performing different gender identities and therefore are genderqueer characters. I am going to relate this passage to the shapeshifters in supernatural, where only the mother monster has a core gender, even though the others are referred to with gendered pronouns. Even though they all use binary pronouns, these pronouns are still used when shifted into a person of the opposite gender. Which is relatable to the transgender transitioning experience. These beings also gain all of the memories of the bodies they imitate, which means their identity can not be singularly gendered. Melzer says “Butler’s insistence on Anyanwu’s female identity and Doro’s male identity contradicts their symbolic function as gender- transgressive or ‘‘genderless’’’ (Melzer 234). Which seems not fully true in the fact that gender and sexuality aren’t related. In addition the fact that one of the characters being in this supposedly heterosexual relationship is earlier described that “She has sexual relations in the body of a man, and even produces children with her wife, yet both women love each other as women, the gender with which both characters identify” (233). So any relationship she is in is queer weather or not she is an androgynous shapeshifter because she is a queer character. In addition the text has a lot of examples that are rooted in reproduction. Which has strong gender binary associations with misogyny.
Namaste, K. (1994). The Politics of Inside/Out: Queer Theory, Poststructuralism, and a Sociological Approach to Sexuality. Sociological Theory, 12(2), 220-231. doi:1. Retrieved from http://www.jstor.org/stable/201866
This piece starts by asking some valid questions such as “ Is the category "homosexual" the only one available to resist heterosexual hegemony?”(228). There is a common inside/outside trope that really just reflects and ends up reinforcing pre existing binary structures. There is no diversity being unpacked when stories are not including transgender representation and sexualities such as pansexual. Both cross preconceived social boundaries that make theory and fiction hard to write around. It is hard to categorize people when they do not fit into presupposed gender, sexuality, and racial positions. In addition when transsexuals are treated as being deformed that brings in an ableist opinion of body construction and adds horror imagery where it need not be. In addition how does transgender subjectivity come into play when writing identities into novels?
Samuels, E. (2014). Fantasies of identification: Disability, gender, race. NYU Press.
Athletes who are intersected are often still subjected to sex testing to make sure there is no biological advantage being given to anyone. This has ruined the careers, lives, and familial relations of many sports figures throughout the years who then have to reaffirm the gender they were assigned at birth instead of focusing on the sport they have worked so hard to achieve in. Medals and other accomplishments are taken away due to the idea of gender being based on a normative body type that does not exist. Genitalia might be “correct” but chromosomally gender entrenched scientifically as a binary fact. Which is not true at all when looking at the plethora of sequential hermaphroditism found in mollusks, amphibians, fish, and even some animal groups. One story that is discussed is the fall of Maria José Martínez-Patiño who was one of the first major televised competitors to fail a gender test in front of the international public, in 1980.
Shaw, A. (2014). From Custer’s Revenge and Mario to Fable and Fallout: Race, Gender, and Sexuality in Digital Games. In Gaming at the Edge: Sexuality and Gender at the Margins of Gamer Culture (pp. 13-54). University of Minnesota Press. Retrieved from http://www.jstor.org/stable/10.5749/j.ctt1287nqh.5
This author is not transgender, but raise the idea of the whiteness commonly associated with trans identities in fiction and in America “Moreover, the game represents the reality of physical sex transformations as a reward for those who are able to reproduce the gender, racial, class, and sexuality norms of the system—whether that is the game or mainstream medical and legal institutions”(32). And continues criticize gaming companies for having ftm (female to male) and mtf (male to female) characters harmed just like in real life in games. In addition to the fact that games have genderqueer options which are taken away and replaced with heteronormativity such as in Fable III, “at the outset the player character is coded as gender normative and ostensibly heterosexual (unlike the androgynous, queer potential of the two child options of Fable II. Which was a great option for visibility, while still not having multiple race options for player avatars.
Westfahl, G. (2005). Androgyny. The Greenwood encyclopedia of science fiction and fantasy: Themes, works, and wonders (Vol. 1). Westport, CT: Greenwood Press.
The theme of androgyny is used to represent different forms of bigotry being displayed in the human race and how having a “race of androgynes who live harmonious, peaceful lives” is used as a “cure for gender bifurcation and decisive hierarchies”(Westfahl 28). Genderqueering an alien society instead of having characters of color represented makes this theme problematic, in addition to the fact that gender abolition is such a controversial topic even in the transgender community. While showing a post-gender connects to a small percentage of the audience that is gender nonconforming, it eliminates transphobia and transgender rage. This isn’t to say that every author should continue to write stories of trans* overdoses or homelessness. Not sure if the idea that all press is good press in terms of non-binary visibility, but this is a common ideal that was created in 70s science fiction literature such as The Left Hand of Darkness by Ursula Le Guin.
0 notes
Text
CIS 513 Week 11 Final Exam – Strayer New
Click On The Link Below To Purchase A+ Graded Material
Instant Download
http://budapp.net/CIS-513-Final-Exam-Week-11-Strayer-NEW-CIS513W11E.htm
Chapters 5 Through 8
Chapter 5 - Wireless Personal Area Networks
TRUE/FALSE
1. WPAN technologies are designed to connect devices that are typically up to 10 meters apart.
2. One of the advantages of WPAN technologies is their conservative use of battery power.
3. The first step in the Bluetooth pairing process is the paging procedure.
4. A reduced-function device can only connect to one full-function device on the network.
5. Bluetooth uses a challenge-response strategy for device authentication.
MULTIPLE CHOICE
1. Which of the following is NOT a likely application for WPAN technologies?
a.
home control systems
c.
industrial control systems
b.
video streaming
d.
security systems
2. Which of the following is true about WPAN standards?
a.
IEEE developed standards for protocols above layer 2
c.
IEEE 802.15.1 is the Bluetooth standard
b.
industry alliances developed specifications for layers 1 and 2
d.
802.16n is the ZigBee standard
3. Which of the following is true about the OSI model and IEEE 802?
a.
the PMD is part of the Data Link layer
c.
the LLC is part of the Physical layer
b.
the PLCP formats data received from the MAC
d.
the MAC layer is responsible for establishing connectivity to the local network
4. Which radio frequency band does Bluetooth use?
a.
2.4 GHz ISM
c.
2.0 GHz ISM
b.
5.0 GHz ISM
d.
4.2 GHz ISM
5. Which of the following is true about the Bluetooth protocol stack?
a.
the L2CAP sits between Baseband and RF
c.
Link Manager communicates directly with the Physical Radio
b.
the Baseband layer sits atop the RF layer
d.
The RF layer communicates between the Link Manager and L2CAP
6. What feature available in some Bluetooth devices increases data rates to 2.1 or 3 Mbps?
a.
Link Manager
c.
L2CAP
b.
radio module
d.
EDR
7. Which Bluetooth power class allows transmission ranges up to 330 feet?
a.
Power Class 1
c.
Power Class 3
b.
Power Class 2
d.
Power Class 4
8. Bluetooth 1.x uses a variation of which modulation technique?
a.
PSK
c.
FSK
b.
ASK
d.
GSK
9. What feature of Bluetooth version 3.0 uses a separate radio module that transmits using the same methods as IEEE 802.11?
a.
BLE
c.
AMP
b.
ULP
d.
NFC
10. Which transmission technique is used by Bluetooth devices?
a.
Narrowband
c.
DHSS
b.
FHSS
d.
UWB
11. Which feature of Bluetooth version 1.2 allows Bluetooth networks to coexist with 802.11 networks with a minimum of interference?
a.
adaptive frequency hopping
c.
alternate MAC/PHY
b.
frequency hopping spread spectrum
d.
Bluetooth low energy
12. What is created when a Bluetooth network has one master and at least one slave using the same channel?
a.
scatternet
c.
piconet
b.
wi-fi net
d.
bluenet
13. How is the master device determined in a Bluetooth network?
a.
the device with the lowest address number
c.
the first device to send out an inquiry message to discover other devices
b.
the device with the highest priority hop sequence on the piconet
d.
the device that carries out a paging procedure and establishes a connection
14. Which of the following is NOT a field in a Bluetooth frame?
a.
Access code
c.
Header
b.
Frame check sequence
d.
Payload
15. Which of the following is NOT a Bluetooth error correction scheme?
a.
1/3 rate FEC
c.
ARQ
b.
2/3 rate FEC
d.
CRC
16. In which Bluetooth power mode is only the slave device’s internal timer running?
a.
active mode
c.
hold mode
b.
sniff mode
d.
park mode
17. Which of the following is true about the ZigBee standard?
a.
designed to support mesh networking
c.
used for larger data transfers than Bluetooth
b.
replaced an existing global, open standard
d.
operates in the 5.0 and 6.5 GHz ISM bands
18. Which layer in a ZigBee device is responsible for detecting the presence of an RF signal in the currently selected channel?
a.
LLC
c.
MAC
b.
PHY
d.
Upper
19. Which task is the MAC layer responsible for in an 802.15.4 device?
a.
turning the radio transceiver on and off
c.
association and disassociation
b.
analyzing link quality
d.
selecting a frequency channel for operation
20. Which type of ZigBee device controls the network in a star topology?
a.
all end-node devices
c.
full-function device
b.
reduced function device
d.
PAN coordinator
COMPLETION
1. In a ZigBee tree topology, if a child loses it connection with its FFD, it becomes a(n) _____________.
2. ________________ is an 802.15.4-based technology that implements IPv6 on WPANs and supports mesh networking.
3. A ______________ authority is a private company that verifies the authenticity of each user in order to discourage fraud.
4. In Bluetooth Encryption Mode ______, all traffic is encrypted.
5. 802.15.4 provides for _______________ integrity, a technique that uses a message integrity code.
MATCHING
a.
8-DPSK
f.
inquiry procedure
b.
ACL link
g.
MIC
c.
ARQ
h.
modulation index
d.
binding
i.
sequential freshness
e.
guaranteed time slots
j.
superframe
1. a reserved period for critical devices to transmit priority data
2. a simple method of phase shift keying that uses eight degrees of phase to encode tribits
3. the process of establishing a relationship between endpoints in a ZigBee network
4. a security service available in 802.15.4 and used by the receiving device
5. a process that enables a device to discover which devices are in range
6. a packet-switched link that is used for data transmissions
7. the amount that the frequency varies
8. an error-correction scheme that continuously retransmits until an acknowledgment is received or a timeout value is exceeded
9. a mechanism for managing transmissions in a piconet
10. a code composed of a subset of the data, the length of the data, and the symmetric key
SHORT ANSWER
1. What are the three types of addresses used in a Bluetooth piconet? Describe each.
2. Describe the two types of physical links between Bluetooth devices.
3. What are the two types of network access used in IEEE 802.15.3 networks? Describe them.
4. List three of the seven tasks the 802.15.4 MAC layer is responsible for.
5. What are the four levels of addresses for identifying devices within a ZigBee PAN?
6. What is a cluster tree topology and how do they compare to mesh networks?
7. How is power management implemented in a ZigBee network?
8. Describe the WirelessHART technology.
9. List and describe the three levels of Bluetooth security.
10. What is the process that ZigBee WPANs use for authentication and encryption? Describe how it works.
Chapter 6 - High-Rate Wireless Personal Area Networks
TRUE/FALSE
1. IEEE 802.15 covers all the WPAN working groups.
2. The WHDI consortium developed the WHDI specification primarily for the delivery of data produced from online database queries.
3. The piconet coordinator in a WirelessHD network should be a battery operated device for mobility.
4. The DSPS power saving mode allows devices to sleep for long periods of time until they choose to wake up and listen to a beacon.
5. UWB is capable of handling multiple data streams, including HD television.
MULTIPLE CHOICE
1. Which IEEE standard enables multimedia connectivity between mobile and fixed consumer devices within the home?
a.
802.15.3c
c.
802.15.1
b.
802.15.5
d.
802.15.4
2. In which frequency range does WHDI operate?
a.
2.4 GHz
c.
5 GHz
b.
800 MHz
d.
400 KHz
3. Which of the following is true about WiGig?
a.
it is compatible with 802.11ac
c.
makes use of technology designed by AMIMON
b.
it requires layer 3 and 4 protocols for audiovisual support
d.
it has adopted the 802.15.3c standard for multimedia distribution
4. What does WiGig use to maintain reliable connections at very high frequencies?
a.
single-carrier modulation
c.
OFDM
b.
beamforming
d.
protocol adaptation layers
5. What technique does WirelessHD employ to support data rates over 25 Gbps?
a.
LRP
c.
HDMI
b.
spatial multiplexing
d.
beamforming
6. Which of the following is true about a WVAN piconet?
a.
the piconet relies on an access point
c.
large non-mobile devices like TVs are not part of a piconet
b.
the PNC is typically a mobile device such as a tablet computer
d.
the PNC is the first sink device in the area
7. Which of the following is described as a piconet that has its own PNC but depends on the original piconet’s PNC to allocate a private block of time when its devices are allowed to transmit?
a.
child piconet
c.
neighbor piconet
b.
parent piconet
d.
subordinate piconet
8. Which of the following is NOT an HR WPAN feature provided by the 802.15.3 MAC layer?
a.
uses a one-octet device ID
c.
data transport includes QoS
b.
PNC can be queried about other devices
d.
infrastructure mode networking is supported
9. Which part of an 802.15.3 superframe is used for association and command communication?
a.
contention access period
c.
channel time allocation period
b.
beacon
d.
management channel time allocation
10. What type of transmission method does an 802.15.3 piconet use during the CTAP?
a.
SDMA
c.
FDMA
b.
TDMA
d.
CDMA
11. Which field of the 802.15.3 MAC frame format is used to reassemble a file in the correct sequence?
a.
Frame control
c.
Fragmentation control
b.
Piconet ID
d.
Stream index
12. Which 802.15.3 power-saving methods allows devices to sleep for the duration of several superframes and allows them to wake up in the middle of a superframe to transmit or receive data?
a.
PSPS
c.
PSPS
b.
APS
d.
APCI
13. Which radio band does the 802.15.3c standard use?
a.
5.0 GHz
c.
2.4 GHz
b.
60 GHz
d.
p00 MHz
14. How many channels and what is the width of each 802.15.3c channel?
a.
4, 2 GHz
c.
11, 25 MHz
b.
6, 200 MHz
d.
14, 50 MHz
15. Which of the following is NOT a 802.15.3c PHY layer enhancement?
a.
passive scanning
c.
channel energy detection
b.
parity bit error detection
d.
transmit power control
16. The RF modulation techniques used for 802.15.3c are variations of which of the following?
a.
QAM and PSK
c.
NRZ-L and NRZ-I
b.
FSK and ASK
d.
BPSK and QPSK
17. In the WirelessHD specification 1.1, Which of the following is NOT a function of the higher protocol layers?
a.
video format selection
c.
device discovery
b.
clock synchronization
d.
video and audio encoding and decoding
18. What application has UWB been used for since the 1960’s?
a.
video streaming
c.
cellular phone towers
b.
ground-penetrating radar
d.
automobile speed detectors
19. What term is used for the technique in which the amplitude, polarity, or position of an analog pulse represents either a 1 or a 0?
a.
biphase modulation
c.
direct-sequence UWB
b.
mesh networking
d.
impulse modulation
20. What type of attack on a Bluetooth device can access contact lists without the user’s knowledge?
a.
bluejacking
c.
bluesnarfing
b.
bluespoofing
d.
blueDoS
COMPLETION
1. The IEEE 802.15.3c standard enables ________________ connectivity between mobile and fixed consumer devices within the home.
2. The WHDI specification is designed to mirror the screens of multiple devices to the TV screen with the use of ____________.
3. _____________________ uses multiple radios and antennas to steer a signal in the direction of the receiver.
4. ZigBee uses a(n) _______________ encryption key for network-wide communications.
5. Security for IEEE 802.15.3 HR WPANs is based on ________________, a symmetric key encryption mechanism.
MATCHING
a.
biphase modulation
f.
isochronous
b.
channel time allocations
g.
MCTA
c.
contention access period
h.
PNC
d.
D-WVAN
i.
spatial multiplexing
e.
H-WVAN
j.
superframe
1. periods of time allocated by the PNC to a specific device for prioritizing communications
2. the home or parent WVAN
3. time periods used for communication between the devices and the PNC
4. a mechanism used to communicate commands or any asynchronous data that may be present in a superframe
5. a technique that uses multiple radios and multiple antennas to transmit and receive different parts of the same PHY frame
6. a time-dependent transmission that must occur every frame or every so many
frames to maintain the quality of the connection
7. a mechanism for managing transmissions in a piconet
8. a device that provides all the basic communications timing in an 802.15.3 piconet
9. uses a half-cycle positive analog pulse to represent a 1 and a half-cycle negative analog pulse to represent a 0
10. a secondary wireless video area network that operates in a different frequency channel
SHORT ANSWER
1. Provide a summary of the purpose and application for IEEE 802.15.3c.
2. List four potential HR WPAN applications.
3. What was the primary purpose the WHDI consortium developed the WHDI specification?
4. What do the PALs do for WiGig?
5. What are the three sections the WirelessHD specification divides the PHY layer into?
6. Describe child and neighbor piconets.
7. Describe the three parts of an 802.15.3 superframe.
8. What information is contained in the Frame control field of an 802.15.3 frame?
9. List and describe the two modes of security for IEEE 802.15.3 HR WPANs.
10. Briefly discuss the potential of spectrum conflict with WPANs.
Chapter 7 - Low-Speed Wireless Local Area Networks
TRUE/FALSE
1. A wireless residential gateway provide better security than connecting a computer directly to the Internet.
2. The range of an AP base station is approximately 375 feet in an environment with no obstructions and little interference.
3. When transmitting above 2 Mbps using DSSS in an 802.11b network, a Barker code is used.
4. The PHY layer of the 802.11b standard provides functionality for a client to join a WLAN and stay connected.
5. A SIFS occurs immediately after the transmission of frames and no device is allowed to transmit during the SIFS.
MULTIPLE CHOICE
1. Which of the following is NOT true about wireless NICs?
a.
they change the computer’s internal data from serial to parallel before transmitting
c.
they have an antenna instead of a cable port
b.
you can connect an external wireless NIC to a USB port
d.
notebook computers often use Mini PCI cards for wireless NICs
2. Which component found in an access point is NOT found in a wireless NIC?
a.
radio transmitter
c.
radio receiver
b.
RJ-45 interface
d.
antenna
3. Aside from acting as the base station for the wireless network, what other function does an AP perform?
a.
it routes packets
c.
proxy server
b.
acts as a bridge
d.
it performs as a firewall
4. Where does an AP that it using PoE get its DC power from?
a.
an AC outlet
c.
UTP cables
b.
a built-in AC/DC converter
d.
high-frequency radio waves
5. If three friends each have a laptop computer and they want to exchange files wirelessly but nobody has an AP, what should they do?
a.
use Ad hoc mode
c.
use the Basic Service Set
b.
use infrastructure mode
d.
use the Extended Service Set
6. What is the term used for when a client finds a different AP that can provide a better-quality signal and then associates with the new AP?
a.
reassociation
c.
transfer
b.
reconnect
d.
handoff
7. Which of the following is NOT a field in the 802.11b PLCP frame?
a.
Start frame delimiter
c.
Signal data rate
b.
Source address
d.
Length
8. Which field of the PLCP frame indicates how long in microseconds the data portion of the frame is?
a.
Start frame delimiter
c.
Service
b.
Signal data rate
d.
Length
9. What is the primary job of the PMD sublayer?
a.
translate binary 1s and 0s into radio signals
c.
reformat the data received from the MAC layer
b.
evaluate the Header error check field
d.
implement a channel access method
10. What is the maximum throughput a device can achieve operating on an 802.11b network?
a.
about 11 Mbps
c.
about 54 Mbps
b.
about 5.5 Mbps
d.
about 27 Mbps
11. What is the period of time devices must wait after the medium is clear before attempting to transmit?
a.
collision timeframe
c.
backoff interval
b.
signal data rate
d.
synchronization period
12. What is the RTS/CTS protocol designed to reduce or prevent?
a.
negative acknowledgements
c.
collisions
b.
CRC errors
d.
handshakes
13. With which channel access method does the AP ask each computer if it wants to transmit?
a.
point coordinated function
c.
CSMA/CD
b.
CSMA/CA
d.
virtual carrier sensing
14. In active scanning, what does the client do initially to start the association process?
a.
poll the access point
c.
send a beacon with the requested SSID
b.
send a probe frame
d.
transmit an associate request frame
15. What is the last frame sent to successfully conclude a client’s attempt to associate using active scanning?
a.
scan reply
c.
probe response
b.
synchronize acknowledgement
d.
associate response
16. Which of the following is true about client’s associating with an AP?
a.
an AP can reject the request based on the client MAC address
c.
a client can reassociate with another AP in a BSS
b.
a client can be associated to multiple APs simultaneously for fault tolerance
d.
if a client is not preconfigured for a specific AP, it will not attempt to associate
17. Which of the following is NOT true about WLAN power management?
a.
power management is transparent to applications
c.
the AP uses timestamps to maintain synchronization
b.
802.11b devices use power management in ad hoc mode
d.
the AP keeps a record of which client’s are sleeping
18. What is the list of devices called that an AP sends in a beacon that indicates which clients have buffered frames waiting?
a.
sleep mode identifier
c.
traffic indication map
b.
buffered frames allocation
d.
packet delivery list
19. Which of the following is a function performed by MAC management frames?
a.
request-to-send
c.
reassociation request
b.
transmit data to the client
d.
acknowledgement
20. What is the time period during which all devices must wait between transmissions of data frames?
a.
Short Interframe Space
c.
Idle Requirement Period
b.
DCF Interframe Space
d.
Transmission Control Period
COMPLETION
1. In the place of a port for a cable connection, a wireless NIC has a(n) ______________.
2. An AP acts as a(n) ____________ between the wired and wireless networks.
3. ____________________ mode consists of at least one wireless client connected to a single AP.
4. Once the _____________ has formatted the frame, it passes the frame to the PMD sublayer.
5. When a client is finishing transmitting, it begins listening for a(n) ________________ from the receiving device.
MATCHING
a.
ACK
f.
control frames
b.
active scanning
g.
DCF
c.
associate request frame
h.
fragmentation
d.
BSS
i.
management frames
e.
channel access methods
j.
passive scanning
1. a WLAN mode that consists of at least one wireless client and one AP
2. a frame sent by a client to an AP that contains the client’s capabilities and supported rates
3. MAC frames that assist in delivering the frames that contain data
4. the process of listening to each available channel for a set period of time
5. the division of data to be transmitted from one large frame into several smaller frames
6. a procedure used to reduce collisions by requiring the receiving station to send an explicit packet back to the sending station
7. the default channel access method in IEEE 802.11 WLANs
8. MAC frames that are used, for example, to set up the initial communications between a client and the AP
9. the process of sending frames to gather information
10. the different ways of sharing resources in a network environment
SHORT ANSWER
1. What are the four steps involved in wireless NIC transmission?
2. Describe the two basic functions of an AP.
3. What is infrastructure mode? Include a discussion of BSS and ESS in your answer.
4. What is a drawback of an ESS WLAN with respect to roaming users? What is a remedy to this drawback?
5. Describe the Physical layer of the 802.11b standard.
6. List the three parts of the PLCP frame.
7. How does CSMA/CA in DCF handle media contention?
8. How does RTS/CTS work?
9. Describe the six basic rules of communication in an 802.11 network.
10. Describe the six steps that occur if two devices have frames to transmit.
Chapter 8 - High-Speed WLANs and WLAN Security
TRUE/FALSE
1. The 802.11a standard maintains the same MAC layer functions as 802.11b WLANs.
2. Increasing data transmission speed through more complex modulation schemes makes multipath distortion worse.
3. The 4-bit Rate field in an 802.11a PLCP frame specifies the speed at which the Data field will be transmitted.
4. Wireless controllers incorporate most AP functions including the radio.
5. VPNs encrypt a connection for security and use very few processing resources.
MULTIPLE CHOICE
1. Which of the following 802.11 standards uses U-NII bands and does not use ISM bands?
a.
802.11b
c.
802.11g
b.
802.11a
d.
802.11n
2. Which of the U-NII bands is approved for outdoor use?
a.
U-NII-1
c.
U-NII-2 Extended
b.
U-NII-2
d.
U-NII-3
3. What is the multiplexing technique used by 802.11a to help solve the multipath distortion problem?
a.
QPSK
c.
FEC
b.
OFDM
d.
PBCC
4. How many bits per symbol can be transmitted using 16-QAM?
a.
16
c.
4
b.
2
d.
8
5. Which wireless data rate uses 64-level quadrature amplitude modulation, transmitting over 48 subcarriers?
a.
11 Mbps
c.
24 Mbps
b.
2 Mbps
d.
54 Mbps
6. Which layer defines the characteristics of the wireless medium?
a.
PLCP
c.
LLC
b.
PMD
d.
MAC
7. Which field in an 802.11a PLCP frame are used to initialize part of the transmitter and receiver circuits?
a.
Tail
c.
Service
b.
Pad
d.
Parity
8. What is the disadvantage of an 802.11a WLAN compared to an 802.11b WLAN?
a.
shorter range
c.
more interference sources
b.
higher error rate
d.
lower bandwidth
9. How many non-overlapping channels are available in an 802.11g WLAN?
a.
23
c.
3
b.
11
d.
8
10. Why is the SIFS time in the 802.11g standard effectively extended to 16 microseconds?
a.
for compatibility with 802.11a
c.
to allow 802.11n devices on the network
b.
to account for quiet time
d.
to achieve data rates higher than 11 Mbps
11. Which of the following is correct about antenna diversity?
a.
it is the cornerstone of the 802.11n technology
c.
it increases bandwidth while decreasing range
b.
it is two radios and one antenna
d.
it is two antennas with one radio
12. What do 802.11n devices employ to direct a transmission back to the device from which a frame was received?
a.
spatial multiplexing
c.
MIMO
b.
beamforming
d.
antenna diversity
13. What is the maximum radio configuration for 802.11n devices?
a.
3 transmitters, 3 receivers
c.
4 transmitters, 4 receivers
b.
6 transmitters, 4 receivers
d.
4 transmitters, 3 receivers
14. How much bandwidth do 802.11n devices utilize when running at speeds up to 300 Mbps?
a.
20 MHz
c.
40 MHz
b.
22 MHz
d.
44 MHz
15. What is the purpose of a guard band?
a.
help prevent adjacent channel interference
c.
helps prevent outside EM interference
b.
help prevent co-channel interference
d.
helps prevent intersymbol interference
16. What 802.11n mode of operation is referred to as greenfield?
a.
transmitting in non-HT mode with 802.11a/g devices
c.
transmitting with only HT devices
b.
transmitting in mixed HT/non-HT devices
d.
transmitting at a faster speed than receiving
17. Which HT operation mode is used when one or more non-HT devices are associated with an HT AP and supports devices at 20 or 40 MHz?
a.
Mode 0
c.
Mode 2
b.
Mode 1
d.
Mode 3
18. Which IEEE standard supports QoS and enables prioritization of frames in DCF?
a.
802.11f
c.
802.11d
b.
802.11e
d.
802.11c
19. What 802.11 standard under development uses up to 160 MHz bandwidth and can achieve data rates up to 7 Gbps?
a.
802.11bg
c.
802.11cd
b.
802.11ac
d.
802.11ga
20. What type of device can you deploy to allow client WLAN connectivity when the main AP is out of range?
a.
bridge
c.
monitor
b.
controller
d.
router
COMPLETION
1. __________________ distortion occurs when the receiving device gets the same signal from several different directions at different times.
2. The _______________ interval prevents a new symbol from arriving at the receiver before the last multipath signal reaches the receiver’s antenna.
3. AP _____________________ is a security problem that takes advantage of the fact that clients authenticate with the AP but not vice versa.
4. The strength of encryption relies on keeping the __________ secret as well as its length.
5. 802.1X uses the Extensible ________________ Protocol for relaying access requests between a wireless device, the AP, and the RADIUS server.
MATCHING
a.
co-channel interference
f.
reduced interframe space
b.
CTS-to-self
g.
spatial multiplexing
c.
guard band
h.
symbol
d.
intersymbol interference
i.
TKIP
e.
pre-shared key
j.
wireless controller
1. a 128-bit key used by WPA
2. interference between two devices configured to use the same frequency channel
3. a change in the signal, also known as a baud
4. a 2-microsecond interframe space that can be used in 802.11n networks
5. the unused frequency space between two adjacent channels
6. a security protocol used in WPA that provides per packet key-mixing
7. a coordination method used by 802.11g devices that prevents 802.11 and 802.11b devices that do not “understand” OFDM from attempting to initiate a transmission
8. a transmission technique that uses multiple radios and multiple antennas to send different parts of the same message simultaneously
9. devices that make it much easier to manage large WLANs by implementing most of the functions of an AP
10. caused when the beginning of a symbol arrives at the receiver antenna while multipath reflections from the previous symbol are still reaching the antenna
SHORT ANSWER
1. What is the U-NII frequency band and WLAN standard uses it?
2. Describe how 802.11a uses the U-NII-1, U-NII-2, and U-NII-2 extended bands.
3. What are the two mandatory and two optional transmission modes defined in the 802.11g PHY layer?
4. What are the three parts of an 802.11a PLCP frame? Describe them briefly.
5. Describe the approach that 802.11n (HT) takes to the implementation of the PHY layer.
6. What is MIMO technology? Include beamforming and spatial multiplexing in your answer.
7. What is the channel configuration of 802.11n and how does it help achieve higher data rates?
8. What is the guard interval and what does it help prevent?
9. What are wireless controllers and why are they important in WLANs?
10. What is 802.11i and what aspect of WLANs does it deal with?
0 notes
Text
CIS 513 Week 11 Final Exam – Strayer New
Click On The Link Below To Purchase A+ Graded Material
Instant Download
http://budapp.net/CIS-513-Final-Exam-Week-11-Strayer-NEW-CIS513W11E.htm
Chapters 5 Through 8
Chapter 5 - Wireless Personal Area Networks
TRUE/FALSE
1. WPAN technologies are designed to connect devices that are typically up to 10 meters apart.
2. One of the advantages of WPAN technologies is their conservative use of battery power.
3. The first step in the Bluetooth pairing process is the paging procedure.
4. A reduced-function device can only connect to one full-function device on the network.
5. Bluetooth uses a challenge-response strategy for device authentication.
MULTIPLE CHOICE
1. Which of the following is NOT a likely application for WPAN technologies?
a.
home control systems
c.
industrial control systems
b.
video streaming
d.
security systems
2. Which of the following is true about WPAN standards?
a.
IEEE developed standards for protocols above layer 2
c.
IEEE 802.15.1 is the Bluetooth standard
b.
industry alliances developed specifications for layers 1 and 2
d.
802.16n is the ZigBee standard
3. Which of the following is true about the OSI model and IEEE 802?
a.
the PMD is part of the Data Link layer
c.
the LLC is part of the Physical layer
b.
the PLCP formats data received from the MAC
d.
the MAC layer is responsible for establishing connectivity to the local network
4. Which radio frequency band does Bluetooth use?
a.
2.4 GHz ISM
c.
2.0 GHz ISM
b.
5.0 GHz ISM
d.
4.2 GHz ISM
5. Which of the following is true about the Bluetooth protocol stack?
a.
the L2CAP sits between Baseband and RF
c.
Link Manager communicates directly with the Physical Radio
b.
the Baseband layer sits atop the RF layer
d.
The RF layer communicates between the Link Manager and L2CAP
6. What feature available in some Bluetooth devices increases data rates to 2.1 or 3 Mbps?
a.
Link Manager
c.
L2CAP
b.
radio module
d.
EDR
7. Which Bluetooth power class allows transmission ranges up to 330 feet?
a.
Power Class 1
c.
Power Class 3
b.
Power Class 2
d.
Power Class 4
8. Bluetooth 1.x uses a variation of which modulation technique?
a.
PSK
c.
FSK
b.
ASK
d.
GSK
9. What feature of Bluetooth version 3.0 uses a separate radio module that transmits using the same methods as IEEE 802.11?
a.
BLE
c.
AMP
b.
ULP
d.
NFC
10. Which transmission technique is used by Bluetooth devices?
a.
Narrowband
c.
DHSS
b.
FHSS
d.
UWB
11. Which feature of Bluetooth version 1.2 allows Bluetooth networks to coexist with 802.11 networks with a minimum of interference?
a.
adaptive frequency hopping
c.
alternate MAC/PHY
b.
frequency hopping spread spectrum
d.
Bluetooth low energy
12. What is created when a Bluetooth network has one master and at least one slave using the same channel?
a.
scatternet
c.
piconet
b.
wi-fi net
d.
bluenet
13. How is the master device determined in a Bluetooth network?
a.
the device with the lowest address number
c.
the first device to send out an inquiry message to discover other devices
b.
the device with the highest priority hop sequence on the piconet
d.
the device that carries out a paging procedure and establishes a connection
14. Which of the following is NOT a field in a Bluetooth frame?
a.
Access code
c.
Header
b.
Frame check sequence
d.
Payload
15. Which of the following is NOT a Bluetooth error correction scheme?
a.
1/3 rate FEC
c.
ARQ
b.
2/3 rate FEC
d.
CRC
16. In which Bluetooth power mode is only the slave device’s internal timer running?
a.
active mode
c.
hold mode
b.
sniff mode
d.
park mode
17. Which of the following is true about the ZigBee standard?
a.
designed to support mesh networking
c.
used for larger data transfers than Bluetooth
b.
replaced an existing global, open standard
d.
operates in the 5.0 and 6.5 GHz ISM bands
18. Which layer in a ZigBee device is responsible for detecting the presence of an RF signal in the currently selected channel?
a.
LLC
c.
MAC
b.
PHY
d.
Upper
19. Which task is the MAC layer responsible for in an 802.15.4 device?
a.
turning the radio transceiver on and off
c.
association and disassociation
b.
analyzing link quality
d.
selecting a frequency channel for operation
20. Which type of ZigBee device controls the network in a star topology?
a.
all end-node devices
c.
full-function device
b.
reduced function device
d.
PAN coordinator
COMPLETION
1. In a ZigBee tree topology, if a child loses it connection with its FFD, it becomes a(n) _____________.
2. ________________ is an 802.15.4-based technology that implements IPv6 on WPANs and supports mesh networking.
3. A ______________ authority is a private company that verifies the authenticity of each user in order to discourage fraud.
4. In Bluetooth Encryption Mode ______, all traffic is encrypted.
5. 802.15.4 provides for _______________ integrity, a technique that uses a message integrity code.
MATCHING
a.
8-DPSK
f.
inquiry procedure
b.
ACL link
g.
MIC
c.
ARQ
h.
modulation index
d.
binding
i.
sequential freshness
e.
guaranteed time slots
j.
superframe
1. a reserved period for critical devices to transmit priority data
2. a simple method of phase shift keying that uses eight degrees of phase to encode tribits
3. the process of establishing a relationship between endpoints in a ZigBee network
4. a security service available in 802.15.4 and used by the receiving device
5. a process that enables a device to discover which devices are in range
6. a packet-switched link that is used for data transmissions
7. the amount that the frequency varies
8. an error-correction scheme that continuously retransmits until an acknowledgment is received or a timeout value is exceeded
9. a mechanism for managing transmissions in a piconet
10. a code composed of a subset of the data, the length of the data, and the symmetric key
SHORT ANSWER
1. What are the three types of addresses used in a Bluetooth piconet? Describe each.
2. Describe the two types of physical links between Bluetooth devices.
3. What are the two types of network access used in IEEE 802.15.3 networks? Describe them.
4. List three of the seven tasks the 802.15.4 MAC layer is responsible for.
5. What are the four levels of addresses for identifying devices within a ZigBee PAN?
6. What is a cluster tree topology and how do they compare to mesh networks?
7. How is power management implemented in a ZigBee network?
8. Describe the WirelessHART technology.
9. List and describe the three levels of Bluetooth security.
10. What is the process that ZigBee WPANs use for authentication and encryption? Describe how it works.
Chapter 6 - High-Rate Wireless Personal Area Networks
TRUE/FALSE
1. IEEE 802.15 covers all the WPAN working groups.
2. The WHDI consortium developed the WHDI specification primarily for the delivery of data produced from online database queries.
3. The piconet coordinator in a WirelessHD network should be a battery operated device for mobility.
4. The DSPS power saving mode allows devices to sleep for long periods of time until they choose to wake up and listen to a beacon.
5. UWB is capable of handling multiple data streams, including HD television.
MULTIPLE CHOICE
1. Which IEEE standard enables multimedia connectivity between mobile and fixed consumer devices within the home?
a.
802.15.3c
c.
802.15.1
b.
802.15.5
d.
802.15.4
2. In which frequency range does WHDI operate?
a.
2.4 GHz
c.
5 GHz
b.
800 MHz
d.
400 KHz
3. Which of the following is true about WiGig?
a.
it is compatible with 802.11ac
c.
makes use of technology designed by AMIMON
b.
it requires layer 3 and 4 protocols for audiovisual support
d.
it has adopted the 802.15.3c standard for multimedia distribution
4. What does WiGig use to maintain reliable connections at very high frequencies?
a.
single-carrier modulation
c.
OFDM
b.
beamforming
d.
protocol adaptation layers
5. What technique does WirelessHD employ to support data rates over 25 Gbps?
a.
LRP
c.
HDMI
b.
spatial multiplexing
d.
beamforming
6. Which of the following is true about a WVAN piconet?
a.
the piconet relies on an access point
c.
large non-mobile devices like TVs are not part of a piconet
b.
the PNC is typically a mobile device such as a tablet computer
d.
the PNC is the first sink device in the area
7. Which of the following is described as a piconet that has its own PNC but depends on the original piconet’s PNC to allocate a private block of time when its devices are allowed to transmit?
a.
child piconet
c.
neighbor piconet
b.
parent piconet
d.
subordinate piconet
8. Which of the following is NOT an HR WPAN feature provided by the 802.15.3 MAC layer?
a.
uses a one-octet device ID
c.
data transport includes QoS
b.
PNC can be queried about other devices
d.
infrastructure mode networking is supported
9. Which part of an 802.15.3 superframe is used for association and command communication?
a.
contention access period
c.
channel time allocation period
b.
beacon
d.
management channel time allocation
10. What type of transmission method does an 802.15.3 piconet use during the CTAP?
a.
SDMA
c.
FDMA
b.
TDMA
d.
CDMA
11. Which field of the 802.15.3 MAC frame format is used to reassemble a file in the correct sequence?
a.
Frame control
c.
Fragmentation control
b.
Piconet ID
d.
Stream index
12. Which 802.15.3 power-saving methods allows devices to sleep for the duration of several superframes and allows them to wake up in the middle of a superframe to transmit or receive data?
a.
PSPS
c.
PSPS
b.
APS
d.
APCI
13. Which radio band does the 802.15.3c standard use?
a.
5.0 GHz
c.
2.4 GHz
b.
60 GHz
d.
p00 MHz
14. How many channels and what is the width of each 802.15.3c channel?
a.
4, 2 GHz
c.
11, 25 MHz
b.
6, 200 MHz
d.
14, 50 MHz
15. Which of the following is NOT a 802.15.3c PHY layer enhancement?
a.
passive scanning
c.
channel energy detection
b.
parity bit error detection
d.
transmit power control
16. The RF modulation techniques used for 802.15.3c are variations of which of the following?
a.
QAM and PSK
c.
NRZ-L and NRZ-I
b.
FSK and ASK
d.
BPSK and QPSK
17. In the WirelessHD specification 1.1, Which of the following is NOT a function of the higher protocol layers?
a.
video format selection
c.
device discovery
b.
clock synchronization
d.
video and audio encoding and decoding
18. What application has UWB been used for since the 1960’s?
a.
video streaming
c.
cellular phone towers
b.
ground-penetrating radar
d.
automobile speed detectors
19. What term is used for the technique in which the amplitude, polarity, or position of an analog pulse represents either a 1 or a 0?
a.
biphase modulation
c.
direct-sequence UWB
b.
mesh networking
d.
impulse modulation
20. What type of attack on a Bluetooth device can access contact lists without the user’s knowledge?
a.
bluejacking
c.
bluesnarfing
b.
bluespoofing
d.
blueDoS
COMPLETION
1. The IEEE 802.15.3c standard enables ________________ connectivity between mobile and fixed consumer devices within the home.
2. The WHDI specification is designed to mirror the screens of multiple devices to the TV screen with the use of ____________.
3. _____________________ uses multiple radios and antennas to steer a signal in the direction of the receiver.
4. ZigBee uses a(n) _______________ encryption key for network-wide communications.
5. Security for IEEE 802.15.3 HR WPANs is based on ________________, a symmetric key encryption mechanism.
MATCHING
a.
biphase modulation
f.
isochronous
b.
channel time allocations
g.
MCTA
c.
contention access period
h.
PNC
d.
D-WVAN
i.
spatial multiplexing
e.
H-WVAN
j.
superframe
1. periods of time allocated by the PNC to a specific device for prioritizing communications
2. the home or parent WVAN
3. time periods used for communication between the devices and the PNC
4. a mechanism used to communicate commands or any asynchronous data that may be present in a superframe
5. a technique that uses multiple radios and multiple antennas to transmit and receive different parts of the same PHY frame
6. a time-dependent transmission that must occur every frame or every so many
frames to maintain the quality of the connection
7. a mechanism for managing transmissions in a piconet
8. a device that provides all the basic communications timing in an 802.15.3 piconet
9. uses a half-cycle positive analog pulse to represent a 1 and a half-cycle negative analog pulse to represent a 0
10. a secondary wireless video area network that operates in a different frequency channel
SHORT ANSWER
1. Provide a summary of the purpose and application for IEEE 802.15.3c.
2. List four potential HR WPAN applications.
3. What was the primary purpose the WHDI consortium developed the WHDI specification?
4. What do the PALs do for WiGig?
5. What are the three sections the WirelessHD specification divides the PHY layer into?
6. Describe child and neighbor piconets.
7. Describe the three parts of an 802.15.3 superframe.
8. What information is contained in the Frame control field of an 802.15.3 frame?
9. List and describe the two modes of security for IEEE 802.15.3 HR WPANs.
10. Briefly discuss the potential of spectrum conflict with WPANs.
Chapter 7 - Low-Speed Wireless Local Area Networks
TRUE/FALSE
1. A wireless residential gateway provide better security than connecting a computer directly to the Internet.
2. The range of an AP base station is approximately 375 feet in an environment with no obstructions and little interference.
3. When transmitting above 2 Mbps using DSSS in an 802.11b network, a Barker code is used.
4. The PHY layer of the 802.11b standard provides functionality for a client to join a WLAN and stay connected.
5. A SIFS occurs immediately after the transmission of frames and no device is allowed to transmit during the SIFS.
MULTIPLE CHOICE
1. Which of the following is NOT true about wireless NICs?
a.
they change the computer’s internal data from serial to parallel before transmitting
c.
they have an antenna instead of a cable port
b.
you can connect an external wireless NIC to a USB port
d.
notebook computers often use Mini PCI cards for wireless NICs
2. Which component found in an access point is NOT found in a wireless NIC?
a.
radio transmitter
c.
radio receiver
b.
RJ-45 interface
d.
antenna
3. Aside from acting as the base station for the wireless network, what other function does an AP perform?
a.
it routes packets
c.
proxy server
b.
acts as a bridge
d.
it performs as a firewall
4. Where does an AP that it using PoE get its DC power from?
a.
an AC outlet
c.
UTP cables
b.
a built-in AC/DC converter
d.
high-frequency radio waves
5. If three friends each have a laptop computer and they want to exchange files wirelessly but nobody has an AP, what should they do?
a.
use Ad hoc mode
c.
use the Basic Service Set
b.
use infrastructure mode
d.
use the Extended Service Set
6. What is the term used for when a client finds a different AP that can provide a better-quality signal and then associates with the new AP?
a.
reassociation
c.
transfer
b.
reconnect
d.
handoff
7. Which of the following is NOT a field in the 802.11b PLCP frame?
a.
Start frame delimiter
c.
Signal data rate
b.
Source address
d.
Length
8. Which field of the PLCP frame indicates how long in microseconds the data portion of the frame is?
a.
Start frame delimiter
c.
Service
b.
Signal data rate
d.
Length
9. What is the primary job of the PMD sublayer?
a.
translate binary 1s and 0s into radio signals
c.
reformat the data received from the MAC layer
b.
evaluate the Header error check field
d.
implement a channel access method
10. What is the maximum throughput a device can achieve operating on an 802.11b network?
a.
about 11 Mbps
c.
about 54 Mbps
b.
about 5.5 Mbps
d.
about 27 Mbps
11. What is the period of time devices must wait after the medium is clear before attempting to transmit?
a.
collision timeframe
c.
backoff interval
b.
signal data rate
d.
synchronization period
12. What is the RTS/CTS protocol designed to reduce or prevent?
a.
negative acknowledgements
c.
collisions
b.
CRC errors
d.
handshakes
13. With which channel access method does the AP ask each computer if it wants to transmit?
a.
point coordinated function
c.
CSMA/CD
b.
CSMA/CA
d.
virtual carrier sensing
14. In active scanning, what does the client do initially to start the association process?
a.
poll the access point
c.
send a beacon with the requested SSID
b.
send a probe frame
d.
transmit an associate request frame
15. What is the last frame sent to successfully conclude a client’s attempt to associate using active scanning?
a.
scan reply
c.
probe response
b.
synchronize acknowledgement
d.
associate response
16. Which of the following is true about client’s associating with an AP?
a.
an AP can reject the request based on the client MAC address
c.
a client can reassociate with another AP in a BSS
b.
a client can be associated to multiple APs simultaneously for fault tolerance
d.
if a client is not preconfigured for a specific AP, it will not attempt to associate
17. Which of the following is NOT true about WLAN power management?
a.
power management is transparent to applications
c.
the AP uses timestamps to maintain synchronization
b.
802.11b devices use power management in ad hoc mode
d.
the AP keeps a record of which client’s are sleeping
18. What is the list of devices called that an AP sends in a beacon that indicates which clients have buffered frames waiting?
a.
sleep mode identifier
c.
traffic indication map
b.
buffered frames allocation
d.
packet delivery list
19. Which of the following is a function performed by MAC management frames?
a.
request-to-send
c.
reassociation request
b.
transmit data to the client
d.
acknowledgement
20. What is the time period during which all devices must wait between transmissions of data frames?
a.
Short Interframe Space
c.
Idle Requirement Period
b.
DCF Interframe Space
d.
Transmission Control Period
COMPLETION
1. In the place of a port for a cable connection, a wireless NIC has a(n) ______________.
2. An AP acts as a(n) ____________ between the wired and wireless networks.
3. ____________________ mode consists of at least one wireless client connected to a single AP.
4. Once the _____________ has formatted the frame, it passes the frame to the PMD sublayer.
5. When a client is finishing transmitting, it begins listening for a(n) ________________ from the receiving device.
MATCHING
a.
ACK
f.
control frames
b.
active scanning
g.
DCF
c.
associate request frame
h.
fragmentation
d.
BSS
i.
management frames
e.
channel access methods
j.
passive scanning
1. a WLAN mode that consists of at least one wireless client and one AP
2. a frame sent by a client to an AP that contains the client’s capabilities and supported rates
3. MAC frames that assist in delivering the frames that contain data
4. the process of listening to each available channel for a set period of time
5. the division of data to be transmitted from one large frame into several smaller frames
6. a procedure used to reduce collisions by requiring the receiving station to send an explicit packet back to the sending station
7. the default channel access method in IEEE 802.11 WLANs
8. MAC frames that are used, for example, to set up the initial communications between a client and the AP
9. the process of sending frames to gather information
10. the different ways of sharing resources in a network environment
SHORT ANSWER
1. What are the four steps involved in wireless NIC transmission?
2. Describe the two basic functions of an AP.
3. What is infrastructure mode? Include a discussion of BSS and ESS in your answer.
4. What is a drawback of an ESS WLAN with respect to roaming users? What is a remedy to this drawback?
5. Describe the Physical layer of the 802.11b standard.
6. List the three parts of the PLCP frame.
7. How does CSMA/CA in DCF handle media contention?
8. How does RTS/CTS work?
9. Describe the six basic rules of communication in an 802.11 network.
10. Describe the six steps that occur if two devices have frames to transmit.
Chapter 8 - High-Speed WLANs and WLAN Security
TRUE/FALSE
1. The 802.11a standard maintains the same MAC layer functions as 802.11b WLANs.
2. Increasing data transmission speed through more complex modulation schemes makes multipath distortion worse.
3. The 4-bit Rate field in an 802.11a PLCP frame specifies the speed at which the Data field will be transmitted.
4. Wireless controllers incorporate most AP functions including the radio.
5. VPNs encrypt a connection for security and use very few processing resources.
MULTIPLE CHOICE
1. Which of the following 802.11 standards uses U-NII bands and does not use ISM bands?
a.
802.11b
c.
802.11g
b.
802.11a
d.
802.11n
2. Which of the U-NII bands is approved for outdoor use?
a.
U-NII-1
c.
U-NII-2 Extended
b.
U-NII-2
d.
U-NII-3
3. What is the multiplexing technique used by 802.11a to help solve the multipath distortion problem?
a.
QPSK
c.
FEC
b.
OFDM
d.
PBCC
4. How many bits per symbol can be transmitted using 16-QAM?
a.
16
c.
4
b.
2
d.
8
5. Which wireless data rate uses 64-level quadrature amplitude modulation, transmitting over 48 subcarriers?
a.
11 Mbps
c.
24 Mbps
b.
2 Mbps
d.
54 Mbps
6. Which layer defines the characteristics of the wireless medium?
a.
PLCP
c.
LLC
b.
PMD
d.
MAC
7. Which field in an 802.11a PLCP frame are used to initialize part of the transmitter and receiver circuits?
a.
Tail
c.
Service
b.
Pad
d.
Parity
8. What is the disadvantage of an 802.11a WLAN compared to an 802.11b WLAN?
a.
shorter range
c.
more interference sources
b.
higher error rate
d.
lower bandwidth
9. How many non-overlapping channels are available in an 802.11g WLAN?
a.
23
c.
3
b.
11
d.
8
10. Why is the SIFS time in the 802.11g standard effectively extended to 16 microseconds?
a.
for compatibility with 802.11a
c.
to allow 802.11n devices on the network
b.
to account for quiet time
d.
to achieve data rates higher than 11 Mbps
11. Which of the following is correct about antenna diversity?
a.
it is the cornerstone of the 802.11n technology
c.
it increases bandwidth while decreasing range
b.
it is two radios and one antenna
d.
it is two antennas with one radio
12. What do 802.11n devices employ to direct a transmission back to the device from which a frame was received?
a.
spatial multiplexing
c.
MIMO
b.
beamforming
d.
antenna diversity
13. What is the maximum radio configuration for 802.11n devices?
a.
3 transmitters, 3 receivers
c.
4 transmitters, 4 receivers
b.
6 transmitters, 4 receivers
d.
4 transmitters, 3 receivers
14. How much bandwidth do 802.11n devices utilize when running at speeds up to 300 Mbps?
a.
20 MHz
c.
40 MHz
b.
22 MHz
d.
44 MHz
15. What is the purpose of a guard band?
a.
help prevent adjacent channel interference
c.
helps prevent outside EM interference
b.
help prevent co-channel interference
d.
helps prevent intersymbol interference
16. What 802.11n mode of operation is referred to as greenfield?
a.
transmitting in non-HT mode with 802.11a/g devices
c.
transmitting with only HT devices
b.
transmitting in mixed HT/non-HT devices
d.
transmitting at a faster speed than receiving
17. Which HT operation mode is used when one or more non-HT devices are associated with an HT AP and supports devices at 20 or 40 MHz?
a.
Mode 0
c.
Mode 2
b.
Mode 1
d.
Mode 3
18. Which IEEE standard supports QoS and enables prioritization of frames in DCF?
a.
802.11f
c.
802.11d
b.
802.11e
d.
802.11c
19. What 802.11 standard under development uses up to 160 MHz bandwidth and can achieve data rates up to 7 Gbps?
a.
802.11bg
c.
802.11cd
b.
802.11ac
d.
802.11ga
20. What type of device can you deploy to allow client WLAN connectivity when the main AP is out of range?
a.
bridge
c.
monitor
b.
controller
d.
router
COMPLETION
1. __________________ distortion occurs when the receiving device gets the same signal from several different directions at different times.
2. The _______________ interval prevents a new symbol from arriving at the receiver before the last multipath signal reaches the receiver’s antenna.
3. AP _____________________ is a security problem that takes advantage of the fact that clients authenticate with the AP but not vice versa.
4. The strength of encryption relies on keeping the __________ secret as well as its length.
5. 802.1X uses the Extensible ________________ Protocol for relaying access requests between a wireless device, the AP, and the RADIUS server.
MATCHING
a.
co-channel interference
f.
reduced interframe space
b.
CTS-to-self
g.
spatial multiplexing
c.
guard band
h.
symbol
d.
intersymbol interference
i.
TKIP
e.
pre-shared key
j.
wireless controller
1. a 128-bit key used by WPA
2. interference between two devices configured to use the same frequency channel
3. a change in the signal, also known as a baud
4. a 2-microsecond interframe space that can be used in 802.11n networks
5. the unused frequency space between two adjacent channels
6. a security protocol used in WPA that provides per packet key-mixing
7. a coordination method used by 802.11g devices that prevents 802.11 and 802.11b devices that do not “understand” OFDM from attempting to initiate a transmission
8. a transmission technique that uses multiple radios and multiple antennas to send different parts of the same message simultaneously
9. devices that make it much easier to manage large WLANs by implementing most of the functions of an AP
10. caused when the beginning of a symbol arrives at the receiver antenna while multipath reflections from the previous symbol are still reaching the antenna
SHORT ANSWER
1. What is the U-NII frequency band and WLAN standard uses it?
2. Describe how 802.11a uses the U-NII-1, U-NII-2, and U-NII-2 extended bands.
3. What are the two mandatory and two optional transmission modes defined in the 802.11g PHY layer?
4. What are the three parts of an 802.11a PLCP frame? Describe them briefly.
5. Describe the approach that 802.11n (HT) takes to the implementation of the PHY layer.
6. What is MIMO technology? Include beamforming and spatial multiplexing in your answer.
7. What is the channel configuration of 802.11n and how does it help achieve higher data rates?
8. What is the guard interval and what does it help prevent?
9. What are wireless controllers and why are they important in WLANs?
10. What is 802.11i and what aspect of WLANs does it deal with?
0 notes
Text
CIS 513 Week 11 Final Exam – Strayer New
Click On The Link Below To Purchase A+ Graded Material
Instant Download
http://budapp.net/CIS-513-Final-Exam-Week-11-Strayer-NEW-CIS513W11E.htm
Chapters 5 Through 8
Chapter 5 - Wireless Personal Area Networks
TRUE/FALSE
1. WPAN technologies are designed to connect devices that are typically up to 10 meters apart.
2. One of the advantages of WPAN technologies is their conservative use of battery power.
3. The first step in the Bluetooth pairing process is the paging procedure.
4. A reduced-function device can only connect to one full-function device on the network.
5. Bluetooth uses a challenge-response strategy for device authentication.
MULTIPLE CHOICE
1. Which of the following is NOT a likely application for WPAN technologies?
a.
home control systems
c.
industrial control systems
b.
video streaming
d.
security systems
2. Which of the following is true about WPAN standards?
a.
IEEE developed standards for protocols above layer 2
c.
IEEE 802.15.1 is the Bluetooth standard
b.
industry alliances developed specifications for layers 1 and 2
d.
802.16n is the ZigBee standard
3. Which of the following is true about the OSI model and IEEE 802?
a.
the PMD is part of the Data Link layer
c.
the LLC is part of the Physical layer
b.
the PLCP formats data received from the MAC
d.
the MAC layer is responsible for establishing connectivity to the local network
4. Which radio frequency band does Bluetooth use?
a.
2.4 GHz ISM
c.
2.0 GHz ISM
b.
5.0 GHz ISM
d.
4.2 GHz ISM
5. Which of the following is true about the Bluetooth protocol stack?
a.
the L2CAP sits between Baseband and RF
c.
Link Manager communicates directly with the Physical Radio
b.
the Baseband layer sits atop the RF layer
d.
The RF layer communicates between the Link Manager and L2CAP
6. What feature available in some Bluetooth devices increases data rates to 2.1 or 3 Mbps?
a.
Link Manager
c.
L2CAP
b.
radio module
d.
EDR
7. Which Bluetooth power class allows transmission ranges up to 330 feet?
a.
Power Class 1
c.
Power Class 3
b.
Power Class 2
d.
Power Class 4
8. Bluetooth 1.x uses a variation of which modulation technique?
a.
PSK
c.
FSK
b.
ASK
d.
GSK
9. What feature of Bluetooth version 3.0 uses a separate radio module that transmits using the same methods as IEEE 802.11?
a.
BLE
c.
AMP
b.
ULP
d.
NFC
10. Which transmission technique is used by Bluetooth devices?
a.
Narrowband
c.
DHSS
b.
FHSS
d.
UWB
11. Which feature of Bluetooth version 1.2 allows Bluetooth networks to coexist with 802.11 networks with a minimum of interference?
a.
adaptive frequency hopping
c.
alternate MAC/PHY
b.
frequency hopping spread spectrum
d.
Bluetooth low energy
12. What is created when a Bluetooth network has one master and at least one slave using the same channel?
a.
scatternet
c.
piconet
b.
wi-fi net
d.
bluenet
13. How is the master device determined in a Bluetooth network?
a.
the device with the lowest address number
c.
the first device to send out an inquiry message to discover other devices
b.
the device with the highest priority hop sequence on the piconet
d.
the device that carries out a paging procedure and establishes a connection
14. Which of the following is NOT a field in a Bluetooth frame?
a.
Access code
c.
Header
b.
Frame check sequence
d.
Payload
15. Which of the following is NOT a Bluetooth error correction scheme?
a.
1/3 rate FEC
c.
ARQ
b.
2/3 rate FEC
d.
CRC
16. In which Bluetooth power mode is only the slave device’s internal timer running?
a.
active mode
c.
hold mode
b.
sniff mode
d.
park mode
17. Which of the following is true about the ZigBee standard?
a.
designed to support mesh networking
c.
used for larger data transfers than Bluetooth
b.
replaced an existing global, open standard
d.
operates in the 5.0 and 6.5 GHz ISM bands
18. Which layer in a ZigBee device is responsible for detecting the presence of an RF signal in the currently selected channel?
a.
LLC
c.
MAC
b.
PHY
d.
Upper
19. Which task is the MAC layer responsible for in an 802.15.4 device?
a.
turning the radio transceiver on and off
c.
association and disassociation
b.
analyzing link quality
d.
selecting a frequency channel for operation
20. Which type of ZigBee device controls the network in a star topology?
a.
all end-node devices
c.
full-function device
b.
reduced function device
d.
PAN coordinator
COMPLETION
1. In a ZigBee tree topology, if a child loses it connection with its FFD, it becomes a(n) _____________.
2. ________________ is an 802.15.4-based technology that implements IPv6 on WPANs and supports mesh networking.
3. A ______________ authority is a private company that verifies the authenticity of each user in order to discourage fraud.
4. In Bluetooth Encryption Mode ______, all traffic is encrypted.
5. 802.15.4 provides for _______________ integrity, a technique that uses a message integrity code.
MATCHING
a.
8-DPSK
f.
inquiry procedure
b.
ACL link
g.
MIC
c.
ARQ
h.
modulation index
d.
binding
i.
sequential freshness
e.
guaranteed time slots
j.
superframe
1. a reserved period for critical devices to transmit priority data
2. a simple method of phase shift keying that uses eight degrees of phase to encode tribits
3. the process of establishing a relationship between endpoints in a ZigBee network
4. a security service available in 802.15.4 and used by the receiving device
5. a process that enables a device to discover which devices are in range
6. a packet-switched link that is used for data transmissions
7. the amount that the frequency varies
8. an error-correction scheme that continuously retransmits until an acknowledgment is received or a timeout value is exceeded
9. a mechanism for managing transmissions in a piconet
10. a code composed of a subset of the data, the length of the data, and the symmetric key
SHORT ANSWER
1. What are the three types of addresses used in a Bluetooth piconet? Describe each.
2. Describe the two types of physical links between Bluetooth devices.
3. What are the two types of network access used in IEEE 802.15.3 networks? Describe them.
4. List three of the seven tasks the 802.15.4 MAC layer is responsible for.
5. What are the four levels of addresses for identifying devices within a ZigBee PAN?
6. What is a cluster tree topology and how do they compare to mesh networks?
7. How is power management implemented in a ZigBee network?
8. Describe the WirelessHART technology.
9. List and describe the three levels of Bluetooth security.
10. What is the process that ZigBee WPANs use for authentication and encryption? Describe how it works.
Chapter 6 - High-Rate Wireless Personal Area Networks
TRUE/FALSE
1. IEEE 802.15 covers all the WPAN working groups.
2. The WHDI consortium developed the WHDI specification primarily for the delivery of data produced from online database queries.
3. The piconet coordinator in a WirelessHD network should be a battery operated device for mobility.
4. The DSPS power saving mode allows devices to sleep for long periods of time until they choose to wake up and listen to a beacon.
5. UWB is capable of handling multiple data streams, including HD television.
MULTIPLE CHOICE
1. Which IEEE standard enables multimedia connectivity between mobile and fixed consumer devices within the home?
a.
802.15.3c
c.
802.15.1
b.
802.15.5
d.
802.15.4
2. In which frequency range does WHDI operate?
a.
2.4 GHz
c.
5 GHz
b.
800 MHz
d.
400 KHz
3. Which of the following is true about WiGig?
a.
it is compatible with 802.11ac
c.
makes use of technology designed by AMIMON
b.
it requires layer 3 and 4 protocols for audiovisual support
d.
it has adopted the 802.15.3c standard for multimedia distribution
4. What does WiGig use to maintain reliable connections at very high frequencies?
a.
single-carrier modulation
c.
OFDM
b.
beamforming
d.
protocol adaptation layers
5. What technique does WirelessHD employ to support data rates over 25 Gbps?
a.
LRP
c.
HDMI
b.
spatial multiplexing
d.
beamforming
6. Which of the following is true about a WVAN piconet?
a.
the piconet relies on an access point
c.
large non-mobile devices like TVs are not part of a piconet
b.
the PNC is typically a mobile device such as a tablet computer
d.
the PNC is the first sink device in the area
7. Which of the following is described as a piconet that has its own PNC but depends on the original piconet’s PNC to allocate a private block of time when its devices are allowed to transmit?
a.
child piconet
c.
neighbor piconet
b.
parent piconet
d.
subordinate piconet
8. Which of the following is NOT an HR WPAN feature provided by the 802.15.3 MAC layer?
a.
uses a one-octet device ID
c.
data transport includes QoS
b.
PNC can be queried about other devices
d.
infrastructure mode networking is supported
9. Which part of an 802.15.3 superframe is used for association and command communication?
a.
contention access period
c.
channel time allocation period
b.
beacon
d.
management channel time allocation
10. What type of transmission method does an 802.15.3 piconet use during the CTAP?
a.
SDMA
c.
FDMA
b.
TDMA
d.
CDMA
11. Which field of the 802.15.3 MAC frame format is used to reassemble a file in the correct sequence?
a.
Frame control
c.
Fragmentation control
b.
Piconet ID
d.
Stream index
12. Which 802.15.3 power-saving methods allows devices to sleep for the duration of several superframes and allows them to wake up in the middle of a superframe to transmit or receive data?
a.
PSPS
c.
PSPS
b.
APS
d.
APCI
13. Which radio band does the 802.15.3c standard use?
a.
5.0 GHz
c.
2.4 GHz
b.
60 GHz
d.
p00 MHz
14. How many channels and what is the width of each 802.15.3c channel?
a.
4, 2 GHz
c.
11, 25 MHz
b.
6, 200 MHz
d.
14, 50 MHz
15. Which of the following is NOT a 802.15.3c PHY layer enhancement?
a.
passive scanning
c.
channel energy detection
b.
parity bit error detection
d.
transmit power control
16. The RF modulation techniques used for 802.15.3c are variations of which of the following?
a.
QAM and PSK
c.
NRZ-L and NRZ-I
b.
FSK and ASK
d.
BPSK and QPSK
17. In the WirelessHD specification 1.1, Which of the following is NOT a function of the higher protocol layers?
a.
video format selection
c.
device discovery
b.
clock synchronization
d.
video and audio encoding and decoding
18. What application has UWB been used for since the 1960’s?
a.
video streaming
c.
cellular phone towers
b.
ground-penetrating radar
d.
automobile speed detectors
19. What term is used for the technique in which the amplitude, polarity, or position of an analog pulse represents either a 1 or a 0?
a.
biphase modulation
c.
direct-sequence UWB
b.
mesh networking
d.
impulse modulation
20. What type of attack on a Bluetooth device can access contact lists without the user’s knowledge?
a.
bluejacking
c.
bluesnarfing
b.
bluespoofing
d.
blueDoS
COMPLETION
1. The IEEE 802.15.3c standard enables ________________ connectivity between mobile and fixed consumer devices within the home.
2. The WHDI specification is designed to mirror the screens of multiple devices to the TV screen with the use of ____________.
3. _____________________ uses multiple radios and antennas to steer a signal in the direction of the receiver.
4. ZigBee uses a(n) _______________ encryption key for network-wide communications.
5. Security for IEEE 802.15.3 HR WPANs is based on ________________, a symmetric key encryption mechanism.
MATCHING
a.
biphase modulation
f.
isochronous
b.
channel time allocations
g.
MCTA
c.
contention access period
h.
PNC
d.
D-WVAN
i.
spatial multiplexing
e.
H-WVAN
j.
superframe
1. periods of time allocated by the PNC to a specific device for prioritizing communications
2. the home or parent WVAN
3. time periods used for communication between the devices and the PNC
4. a mechanism used to communicate commands or any asynchronous data that may be present in a superframe
5. a technique that uses multiple radios and multiple antennas to transmit and receive different parts of the same PHY frame
6. a time-dependent transmission that must occur every frame or every so many
frames to maintain the quality of the connection
7. a mechanism for managing transmissions in a piconet
8. a device that provides all the basic communications timing in an 802.15.3 piconet
9. uses a half-cycle positive analog pulse to represent a 1 and a half-cycle negative analog pulse to represent a 0
10. a secondary wireless video area network that operates in a different frequency channel
SHORT ANSWER
1. Provide a summary of the purpose and application for IEEE 802.15.3c.
2. List four potential HR WPAN applications.
3. What was the primary purpose the WHDI consortium developed the WHDI specification?
4. What do the PALs do for WiGig?
5. What are the three sections the WirelessHD specification divides the PHY layer into?
6. Describe child and neighbor piconets.
7. Describe the three parts of an 802.15.3 superframe.
8. What information is contained in the Frame control field of an 802.15.3 frame?
9. List and describe the two modes of security for IEEE 802.15.3 HR WPANs.
10. Briefly discuss the potential of spectrum conflict with WPANs.
Chapter 7 - Low-Speed Wireless Local Area Networks
TRUE/FALSE
1. A wireless residential gateway provide better security than connecting a computer directly to the Internet.
2. The range of an AP base station is approximately 375 feet in an environment with no obstructions and little interference.
3. When transmitting above 2 Mbps using DSSS in an 802.11b network, a Barker code is used.
4. The PHY layer of the 802.11b standard provides functionality for a client to join a WLAN and stay connected.
5. A SIFS occurs immediately after the transmission of frames and no device is allowed to transmit during the SIFS.
MULTIPLE CHOICE
1. Which of the following is NOT true about wireless NICs?
a.
they change the computer’s internal data from serial to parallel before transmitting
c.
they have an antenna instead of a cable port
b.
you can connect an external wireless NIC to a USB port
d.
notebook computers often use Mini PCI cards for wireless NICs
2. Which component found in an access point is NOT found in a wireless NIC?
a.
radio transmitter
c.
radio receiver
b.
RJ-45 interface
d.
antenna
3. Aside from acting as the base station for the wireless network, what other function does an AP perform?
a.
it routes packets
c.
proxy server
b.
acts as a bridge
d.
it performs as a firewall
4. Where does an AP that it using PoE get its DC power from?
a.
an AC outlet
c.
UTP cables
b.
a built-in AC/DC converter
d.
high-frequency radio waves
5. If three friends each have a laptop computer and they want to exchange files wirelessly but nobody has an AP, what should they do?
a.
use Ad hoc mode
c.
use the Basic Service Set
b.
use infrastructure mode
d.
use the Extended Service Set
6. What is the term used for when a client finds a different AP that can provide a better-quality signal and then associates with the new AP?
a.
reassociation
c.
transfer
b.
reconnect
d.
handoff
7. Which of the following is NOT a field in the 802.11b PLCP frame?
a.
Start frame delimiter
c.
Signal data rate
b.
Source address
d.
Length
8. Which field of the PLCP frame indicates how long in microseconds the data portion of the frame is?
a.
Start frame delimiter
c.
Service
b.
Signal data rate
d.
Length
9. What is the primary job of the PMD sublayer?
a.
translate binary 1s and 0s into radio signals
c.
reformat the data received from the MAC layer
b.
evaluate the Header error check field
d.
implement a channel access method
10. What is the maximum throughput a device can achieve operating on an 802.11b network?
a.
about 11 Mbps
c.
about 54 Mbps
b.
about 5.5 Mbps
d.
about 27 Mbps
11. What is the period of time devices must wait after the medium is clear before attempting to transmit?
a.
collision timeframe
c.
backoff interval
b.
signal data rate
d.
synchronization period
12. What is the RTS/CTS protocol designed to reduce or prevent?
a.
negative acknowledgements
c.
collisions
b.
CRC errors
d.
handshakes
13. With which channel access method does the AP ask each computer if it wants to transmit?
a.
point coordinated function
c.
CSMA/CD
b.
CSMA/CA
d.
virtual carrier sensing
14. In active scanning, what does the client do initially to start the association process?
a.
poll the access point
c.
send a beacon with the requested SSID
b.
send a probe frame
d.
transmit an associate request frame
15. What is the last frame sent to successfully conclude a client’s attempt to associate using active scanning?
a.
scan reply
c.
probe response
b.
synchronize acknowledgement
d.
associate response
16. Which of the following is true about client’s associating with an AP?
a.
an AP can reject the request based on the client MAC address
c.
a client can reassociate with another AP in a BSS
b.
a client can be associated to multiple APs simultaneously for fault tolerance
d.
if a client is not preconfigured for a specific AP, it will not attempt to associate
17. Which of the following is NOT true about WLAN power management?
a.
power management is transparent to applications
c.
the AP uses timestamps to maintain synchronization
b.
802.11b devices use power management in ad hoc mode
d.
the AP keeps a record of which client’s are sleeping
18. What is the list of devices called that an AP sends in a beacon that indicates which clients have buffered frames waiting?
a.
sleep mode identifier
c.
traffic indication map
b.
buffered frames allocation
d.
packet delivery list
19. Which of the following is a function performed by MAC management frames?
a.
request-to-send
c.
reassociation request
b.
transmit data to the client
d.
acknowledgement
20. What is the time period during which all devices must wait between transmissions of data frames?
a.
Short Interframe Space
c.
Idle Requirement Period
b.
DCF Interframe Space
d.
Transmission Control Period
COMPLETION
1. In the place of a port for a cable connection, a wireless NIC has a(n) ______________.
2. An AP acts as a(n) ____________ between the wired and wireless networks.
3. ____________________ mode consists of at least one wireless client connected to a single AP.
4. Once the _____________ has formatted the frame, it passes the frame to the PMD sublayer.
5. When a client is finishing transmitting, it begins listening for a(n) ________________ from the receiving device.
MATCHING
a.
ACK
f.
control frames
b.
active scanning
g.
DCF
c.
associate request frame
h.
fragmentation
d.
BSS
i.
management frames
e.
channel access methods
j.
passive scanning
1. a WLAN mode that consists of at least one wireless client and one AP
2. a frame sent by a client to an AP that contains the client’s capabilities and supported rates
3. MAC frames that assist in delivering the frames that contain data
4. the process of listening to each available channel for a set period of time
5. the division of data to be transmitted from one large frame into several smaller frames
6. a procedure used to reduce collisions by requiring the receiving station to send an explicit packet back to the sending station
7. the default channel access method in IEEE 802.11 WLANs
8. MAC frames that are used, for example, to set up the initial communications between a client and the AP
9. the process of sending frames to gather information
10. the different ways of sharing resources in a network environment
SHORT ANSWER
1. What are the four steps involved in wireless NIC transmission?
2. Describe the two basic functions of an AP.
3. What is infrastructure mode? Include a discussion of BSS and ESS in your answer.
4. What is a drawback of an ESS WLAN with respect to roaming users? What is a remedy to this drawback?
5. Describe the Physical layer of the 802.11b standard.
6. List the three parts of the PLCP frame.
7. How does CSMA/CA in DCF handle media contention?
8. How does RTS/CTS work?
9. Describe the six basic rules of communication in an 802.11 network.
10. Describe the six steps that occur if two devices have frames to transmit.
Chapter 8 - High-Speed WLANs and WLAN Security
TRUE/FALSE
1. The 802.11a standard maintains the same MAC layer functions as 802.11b WLANs.
2. Increasing data transmission speed through more complex modulation schemes makes multipath distortion worse.
3. The 4-bit Rate field in an 802.11a PLCP frame specifies the speed at which the Data field will be transmitted.
4. Wireless controllers incorporate most AP functions including the radio.
5. VPNs encrypt a connection for security and use very few processing resources.
MULTIPLE CHOICE
1. Which of the following 802.11 standards uses U-NII bands and does not use ISM bands?
a.
802.11b
c.
802.11g
b.
802.11a
d.
802.11n
2. Which of the U-NII bands is approved for outdoor use?
a.
U-NII-1
c.
U-NII-2 Extended
b.
U-NII-2
d.
U-NII-3
3. What is the multiplexing technique used by 802.11a to help solve the multipath distortion problem?
a.
QPSK
c.
FEC
b.
OFDM
d.
PBCC
4. How many bits per symbol can be transmitted using 16-QAM?
a.
16
c.
4
b.
2
d.
8
5. Which wireless data rate uses 64-level quadrature amplitude modulation, transmitting over 48 subcarriers?
a.
11 Mbps
c.
24 Mbps
b.
2 Mbps
d.
54 Mbps
6. Which layer defines the characteristics of the wireless medium?
a.
PLCP
c.
LLC
b.
PMD
d.
MAC
7. Which field in an 802.11a PLCP frame are used to initialize part of the transmitter and receiver circuits?
a.
Tail
c.
Service
b.
Pad
d.
Parity
8. What is the disadvantage of an 802.11a WLAN compared to an 802.11b WLAN?
a.
shorter range
c.
more interference sources
b.
higher error rate
d.
lower bandwidth
9. How many non-overlapping channels are available in an 802.11g WLAN?
a.
23
c.
3
b.
11
d.
8
10. Why is the SIFS time in the 802.11g standard effectively extended to 16 microseconds?
a.
for compatibility with 802.11a
c.
to allow 802.11n devices on the network
b.
to account for quiet time
d.
to achieve data rates higher than 11 Mbps
11. Which of the following is correct about antenna diversity?
a.
it is the cornerstone of the 802.11n technology
c.
it increases bandwidth while decreasing range
b.
it is two radios and one antenna
d.
it is two antennas with one radio
12. What do 802.11n devices employ to direct a transmission back to the device from which a frame was received?
a.
spatial multiplexing
c.
MIMO
b.
beamforming
d.
antenna diversity
13. What is the maximum radio configuration for 802.11n devices?
a.
3 transmitters, 3 receivers
c.
4 transmitters, 4 receivers
b.
6 transmitters, 4 receivers
d.
4 transmitters, 3 receivers
14. How much bandwidth do 802.11n devices utilize when running at speeds up to 300 Mbps?
a.
20 MHz
c.
40 MHz
b.
22 MHz
d.
44 MHz
15. What is the purpose of a guard band?
a.
help prevent adjacent channel interference
c.
helps prevent outside EM interference
b.
help prevent co-channel interference
d.
helps prevent intersymbol interference
16. What 802.11n mode of operation is referred to as greenfield?
a.
transmitting in non-HT mode with 802.11a/g devices
c.
transmitting with only HT devices
b.
transmitting in mixed HT/non-HT devices
d.
transmitting at a faster speed than receiving
17. Which HT operation mode is used when one or more non-HT devices are associated with an HT AP and supports devices at 20 or 40 MHz?
a.
Mode 0
c.
Mode 2
b.
Mode 1
d.
Mode 3
18. Which IEEE standard supports QoS and enables prioritization of frames in DCF?
a.
802.11f
c.
802.11d
b.
802.11e
d.
802.11c
19. What 802.11 standard under development uses up to 160 MHz bandwidth and can achieve data rates up to 7 Gbps?
a.
802.11bg
c.
802.11cd
b.
802.11ac
d.
802.11ga
20. What type of device can you deploy to allow client WLAN connectivity when the main AP is out of range?
a.
bridge
c.
monitor
b.
controller
d.
router
COMPLETION
1. __________________ distortion occurs when the receiving device gets the same signal from several different directions at different times.
2. The _______________ interval prevents a new symbol from arriving at the receiver before the last multipath signal reaches the receiver’s antenna.
3. AP _____________________ is a security problem that takes advantage of the fact that clients authenticate with the AP but not vice versa.
4. The strength of encryption relies on keeping the __________ secret as well as its length.
5. 802.1X uses the Extensible ________________ Protocol for relaying access requests between a wireless device, the AP, and the RADIUS server.
MATCHING
a.
co-channel interference
f.
reduced interframe space
b.
CTS-to-self
g.
spatial multiplexing
c.
guard band
h.
symbol
d.
intersymbol interference
i.
TKIP
e.
pre-shared key
j.
wireless controller
1. a 128-bit key used by WPA
2. interference between two devices configured to use the same frequency channel
3. a change in the signal, also known as a baud
4. a 2-microsecond interframe space that can be used in 802.11n networks
5. the unused frequency space between two adjacent channels
6. a security protocol used in WPA that provides per packet key-mixing
7. a coordination method used by 802.11g devices that prevents 802.11 and 802.11b devices that do not “understand” OFDM from attempting to initiate a transmission
8. a transmission technique that uses multiple radios and multiple antennas to send different parts of the same message simultaneously
9. devices that make it much easier to manage large WLANs by implementing most of the functions of an AP
10. caused when the beginning of a symbol arrives at the receiver antenna while multipath reflections from the previous symbol are still reaching the antenna
SHORT ANSWER
1. What is the U-NII frequency band and WLAN standard uses it?
2. Describe how 802.11a uses the U-NII-1, U-NII-2, and U-NII-2 extended bands.
3. What are the two mandatory and two optional transmission modes defined in the 802.11g PHY layer?
4. What are the three parts of an 802.11a PLCP frame? Describe them briefly.
5. Describe the approach that 802.11n (HT) takes to the implementation of the PHY layer.
6. What is MIMO technology? Include beamforming and spatial multiplexing in your answer.
7. What is the channel configuration of 802.11n and how does it help achieve higher data rates?
8. What is the guard interval and what does it help prevent?
9. What are wireless controllers and why are they important in WLANs?
10. What is 802.11i and what aspect of WLANs does it deal with?
0 notes