#optional password parameter
Explore tagged Tumblr posts
Note
Omg u can't just drop the fact that Krueger knows about niktos girl and not elaborate on it 😭 like did this guy just break in the house and found out /jj
Yes I’m so glad you noticed!! I try to make it a common theme throughout all my Nikto fics that Krueger knows about her, and Nikto absolutely hates it. They might be kind of/sort of friends, but Krueger is a different breed of crazy. I got a little carried away and wrote for this because I love the break in idea—
TW: attempted sexual assault (which was stopped) and Krueger. A continuation of the Nikto fics I've been posting on here recently. Unedited, as always
Krueger’s known about Nikto’s ‘pet’ for a while now. It wasn't really hard to figure out, since he knew where to look. And Krueger was nothing if not a nosy bastard.
The first giveaway was Nikto’s phone. They were standard issue at KorTac, everyone was required to have one in case of emergency. Never once had Nikto opened it, nor had he bothered to learn how to use it. So, when he suddenly seemed to check it more often, of course Krueger grew suspicious.
He attempted to snatch the phone on multiple occasions. Nikto kept it unlocked, since he had no clue how to enable the password feature. The only picture on his camera roll was blurry, taken by an unsteady hand that clearly didn't know what it was doing. It was of you, your face tilted to the side as you were doing... something. He couldn't really tell. And the more he tried to decipher the photo, the more he believed that it had just been a fluke. A picture taken completely by accident.
From what little Krueger could see, he still knew you could do better than Nikto's deformed face. Not to mention his personality, which was just as horrid. Another poor, unfortunate soul that fell into bloody hands.
Normally, he would have left it at that. Nikto finally had a good whore to go back to, good for him. He would have assumed Nikto killed the girl immediately after.
But then there were the texts. At least once a day, the annoying, standard ringtone blared from the little black phone. Then Nikto would stop everything just to reply.
It was weird.
So Krueger formed a plan. It was flawless. Next time Nikto checked his phone, he'd snatch it and flip through the chats. Surely, if he had a toy stashed away Nikto would have told him. They were partners, after all.
But, as soon as Krueger tried, Nikto quickly threw his phone to the ground and smashed it under his heel. The big baby was always so dramatic.
Now, Krueger was more curious than ever. Nikto had a secret, and he'd stop at nothing to unearth it.
Flash forward to Thursday night. There was yet another long debrief. Krueger didn't care to listen. As long as he'd get to kill, he wouldn't complain about their next mission. And if they did well, they would retain the freedom of having a life outside of KorTac. An absolutely terrible idea on management's part, but he wasn't about to complain. Not when it gave him the perfect opportunity to sneak out a few moments before Nikto and scope out his home. Simple recon, that was all.
Nikto was taken aside with Konig while the rest of the operatives were dismissed. That meeting would no doubt end with Nikto blowing up at the Austrian man, most likely bashing his face in again. He never could stand Konig. But that gave Krueger a headstart.
Finding Nikto's house was far easier than breaking in. It was a surprisingly nice cottage far out from everything else, just within the parameters of where he was allowed to live. Surrounded by trees, there was enough covering for this place to go unnoticed. Entering through the front door was not an option, Krueger knew that Nikto had definitely installed a stupid amount of locks, and probably rigged some sort of trap or two.
So, he went through the back window. It was a challenge to get in, and fuck, if Krueger didn't love a challenge. It simply meant that the treat locked away had to be worth the effort. You had to be so sweet if Nikto kept you hidden like this.
After shimmying inside, Krueger took his time walking around the house. It was nice, he had to admit. KorTac's salary was unrivaled, especially considering the missions they gave to their operatives. It seemed Nikto's paycheck went to this place, Russian books and tiny knick-knacks decorating the shelves. There was no way in hell Nikto bought the latter for himself, confirming his suspicions. Someone else lived here.
Unlike in his stealth missions, Krueger touched everything, acquainting himself with his partner's living space. He missed the days when Nikto lived on base with him, locked away in a small cell across the way from his. Nikto could pretend all he wanted, but this ‘home’ he created would never be real. It was all a sad, desperate facade for a life he would never have. Krueger didn't care to play house, even if he had his own toy locked away, he was only using Lucas for sex. Nikto clearly gave you a higher role.
He was so lost in his thoughts that he didn't notice that he was in the living room until it was too late. Soft breathing lured him in, a lullaby whispering to him to suffocate the breath for good. Krueger never could keep his hands to himself.
You were curled up, asleep on the couch, waiting for Nikto like a well-behaved pet. The blurry photograph Krueger had seen did not do you justice. He'd have to show Nikto how to get the good angles, making sure to spread your legs for the camera so he could see the perfect moment when he thrusted in. Yeah, Nikto was due for a good lesson. And with a thing as pretty as you, why wouldn't he want to keep your pussy in his pocket at all times?
Krueger circled, stopping right infront of you before crouching down to your height. It was truly a shame you were rotting away with such an ugly man. While he was here, he might as well give you a taste of what you were missing.
"Wakey wakey!" The loud, accented chirp echoed through the room.
You shot straight up, eyes bleary and hair a mess. You looked around the room wildly before your gaze finally landed on him.
"You're not Nik..." The realization came slow. Then, all at once. You kicked yourself back, scrambling over the back of the couch in an attempt to flee.
Only for Krueger to catch you by the ankle and pull you back to the cushions. “Oh, you're smart,” he mocked.
"Let go of me!" You screeched as you thrashed wildly. "Nikto will kill you! Get away!"
He laughed at your struggle, the sound airy as if he were with a friend rather than scaring the shit out of you. Nikto always preferred obedience, acceptable, but Krueger? He favored the girls who fought.
"I'm sure he will," Krueger hummed. "But why don't we have a little fun beforehand, ja?"
Tears were already starting to fall down your cheeks. Why hadn't Nikto told him he had such a pretty crier locked away? It was so unfair. Krueger would have been more than willing to offer his partner on the field a taste of his toy, Lucas, at home. They were supposed to be a team, the two resident psychos of KorTac. Hiding secrets was never a part of the deal.
"I want you to leave," you said quietly, but coherently. So you were using your words. Nikto truly did train you well.
"Well, that doesn't really matter, now does it?" Keeping one hand on your stomach so you'd stay pushed down, he used the other to push the heel of your foot against the bulge in his pants. It had been there since he was shown the footage of his last kill at KorTac. Nothing quite did the trick like gore. "Nikto, you see, he is like a brother to me. Does it not seem right for him to share his toys?"
You attempted to kick his balls, which he blocked, moving your foot away from his cock. He continued with a tut, "Nein, nein. None of that. Just giving a quick inspection."
As he tried to pry your legs apart to see what Nikto had been so desperate to protect, you wouldn't stop fighting. You were surprisingly strong, most likely from the times you fought off Nikto when he first stole you away. Krueger had thought Nikto would have beaten all the fight out of you by now. Surely you didn't think you belonged to him alone, did you?
You were screaming now, too. Nearly making Krueger's ears bleed. "Quiet, bitch."
"He'll kill you!" you spat in his face, hair mussed by the couch cushions. "Nikto will fucking kill you if you don't get off me!"
Krueger laughed. "You truly think you mean that much to him? You're just a toy, Schatz."
You started to shake as more tears fell. Shit. Krueger recognized what happened in an instant. You were going hysterical. This place, your situation, had caused you to teeter to the the edge. And Krueger had accidentally given you the final shove. Nikto was totally going to kill him.
As if on cue, the door swung open. And out came the man you kept whining so insistently about.
Krueger let go of you, allowing you to scramble to close your legs as he gave Nikto a shit-eating grin. "There you are, big guy. We were just talking about you—”
Nikto was on him in a second, grabbing him by the throat and throwing him against the nearest wall. A method of killing they both shared. The brutal asphyxiation made Krueger hornier, if that was even possible. He really should check in with a doctor or psychologist about a way to fix the 'compulsive sexual disorder' his last shrink diagnosed him with.
When Nikto finally spoke, it was a single word.
"Leave."
He didn't bother sugarcoating, he never had and he never will. Nikto was the same overly competitive, overly territorial man Krueger knew on the field. A mirror image of himself. It was intoxicating.
The pressure on his throat made it hard to respond, but that didn't stop Krueger from trying. "No way to... welcome guests... to your home."
Nikto would have been content to kill him and they both knew it. They had been in this situation various times before, just on opposite ends of the knife. They were brothers in arms, fellow psychos. Even if they were the same, they would not hesitate to kill each other. That had been clear since they had first been partnered up.
And oh, hadn't Nikto been so close to killing Krueger. They were the same in so many ways, lacking boundaries and sanity. But they showed it in very different ways.
It may have been another spirit that possessed Nikto at that moment, or perhaps your terrified expression, because he dropped Krueger, who didn't so much as flinch during the whole interaction.
"Why did you come here?" Nikto asked, crossing his arms and standing directly infront of you, blocking you from Krueger's line of sight. You were still on the couch, confused by the man in your home, and terrified of what he almost did to you.
"Why'd you hide such a pretty toy from me?" Krueger countered, shooting you a wink you didn't even seem to register.
Nikto did not return the playful tone. There were many reasons he could give, but the answer was pretty simple. Nikto didn't like Krueger knowing about you. Not because he didn't trust you, but because he didn't trust Krueger. He's watched the man jerk off to dead bodies on the field, he knew Krueger kept pictures of the bloody corpses of women he bedded. So yeah, Nikto tried to keep you under wraps. Nikto may be a violent nutjob, but Krueger would tear you apart and leave nothing left. At least Nikto took care of his pets.
Nikto had to look up at Krueger to meet his eye. He muttered a single, sharp insult. "You are filth. You do not deserve her.”
Krueger scoffed. "A little hypocritical, don't you think?"
Things were quickly turning ugly. Neither man had enough impulse control to back down from a fight. Neither had ever *lost* a fight to begin with. And Nikto had no qualms beating a man to a bloody pulp infront of you, especially after what he walked in on. You had seen him do much worse.
Surprisingly, it was Krueger who conceded, leaning against the wall like he owned the place. "Alright, I'll back off. For you, Bruder."
That was most likely a lie. Krueger was never content with his own toys, he wanted to take others, too. Break them until they were unusable. He was greedy and sadistic, which is what made him such a good killer.
For all the shit Nikto put you through, somehow, he was still better than Krueger. You were still curled in on yourself, not yet coming to terms with the mindfuck of what happened in a matter of minutes, or how Krueger was casually walking to the window without a care in the world. Apparently, once you got used to one psycho, another, worse one appeared in his place.
“Come over for tea sometime,” Krueger said, throwing a sleazy smile over his shoulder, offering a wave as he jumped out the back window. “I’m sure my Lucas would love to have a little playdate."
You prayed to whatever god would listen that you never saw that man again. If he was the alternative to Nikto, you were happy to stay in your little prison, picking up the scraps of comfort you were offered.
Or perhaps that had been Krueger's plan all along. You’d spend the whole night in Nikto’s arms, crying and clinging to him. He was doing his friend a favor, strengthening your dependence so you would never feel enticed to leave. It was the least he could do for Nikto, after all, they had been partners for so long.
#i am bringing Lucas back from the dead#my precious darling oc#I LOVE GETTING ASKS AND THANK YOU FOR NOTICING ME SPRINKING KRUEGER IN#synthsblurbs#call of duty#synthanswers#tw attempted sa#tw kidnapping#nikto x reader#kortac x reader#sebastian krueger#cod krueger#call of duty krueger#nikto#nikto x you
135 notes
·
View notes
Text
WiFi Dashboard for Solar Off-Grid Power Plants
This WiFi interface and Data Logger software are used mainly for Solar Off-Grid Power plants This contains wifi connection information, parameter dials, operational status, energy consumption status and fault status of the Unit History option allows the user to access the data history of a particular unit by searching the modem id. Upto 100 entries can be viewed in a single page. Every five minutes the data will be logged in the history and refreshed Data Config option allows the user to configure the data in the dashboard of a particular unit WiFi credential is to connect the unit to the desired wifi network. This can be achieved by entering Modem id, Network name and Password Switch option in the side panel allows the remote operation of the unit. The whole unit or only the charging can be turned ON/OFF from the dashboard by operating the respective ON and OFF tabs User manual option provides the instructions to configure modem to the wifi network and also use the website dashboard
Don’t forget to LIKE, COMMENT, and SUBSCRIBE for more renewable energy solutions and solar projects!
Enquire Now: 9035024760 or [email protected]
Follow our LinkedIn page: https://www.linkedin.com/company/53510028/admin/dashboard/
Follow our Facebook page: https://www.facebook.com/UniparEnergySystemsPvtLtd
Follow our Instagram: https://www.instagram.com/uniparenergysystemspvtltd/
Subscribe our YouTube channel: https://www.youtube.com/watch?v=3hchIw7CFjw
Visit our website: https://unipar.in/
#off grid solar system#off grid solar power systems#off grid solar electric system#grid off solar system#off grid inverter#off grid solar inverter#inverter solar off grid#grid off inverter#inverter grid off#pv inverter off grid#off grid solar#grid solar system
2 notes
·
View notes
Text
Hardness Tester- TEST-301
Hardness Tester- TEST-301Measuring tablet thickness, diameter and hardness the PHARMAG INSTRUMENTS TabTest-301 Tablet Hardness Tester is both USP and EP compliant and offers excellent flexibility and configurability. This robust 301 design removes the need for a thickness gauge, eliminating redundant calibrations and reducing overall testing cost.
Product Features:
USP PHARMACOPEIA AND EP COMPLIANT: Compliant with USP < 1217> and EP <2.9.8>.
MULTI-PARAMETER MEASUREMENTS: The TabTest -301 measures:
Thickness
Diameter
Hardness
LED DISPLAY: The seven-segment display provides calibration, thickness, diameter, and hardness results.
SMALL FOOTPRINT: Ideal for laboratories with limited bench space. The compact, lightweight design is well-suited for portability and use in a production setting.
"OPTIONAL" BUILT-IN PRINTER: Available with an optional 40-column built-in printer.
SAMPLE THROUGHPUT: Approximately 6-10 samples per minute.
"ADJUSTMENT FREE" TESTING JAWS: No adjustments needed for the test jaws. They are designed to suit all tablet shapes and sizes with a unique grooved design to properly align each tablet before testing.
Specifications:
Display: LED
Keypad: User-friendly 9-key operations
Hardness Range: 5 - 500 N
Hardness Accuracy: >1 N
Diameter and Thickness Range: 1.5 - 40 mm
Diameter Accuracy: >±0.06 mm
Measurements: Thickness and diameter in either mm or inches
Measurable Units:
N (Newton)
KP (KiloPond, 1 KP = 9.81 N)
Sc (Strong Cobb, 1 KP = 1.435 c)
Force Rate Constant (Linear): Force or constant (linear) speed
Number of Tests for Statistics: Up to 99
Stored Methods: Last test result
Calibration Procedure: Requires 10 mm Reference Block and 10 kg Reference Weight (Certified)
Calibration Technique: No tilt (user-friendly)
Distance Validation: 10 mm Certified Block (For Thickness and Diameter)
Load Cell Linearity: 3-Point Linear Calibration with Certified Weight (5, 10, 15 kg)
Load Cell Diagnostic Check: Yes (Check the Load Cell Signal Falls Within Range Before Making Any Further Calibration)
Self Test: Yes
Fault Localization: Yes (Text Format)
Load Cell Overload Protection: Yes
Password Protection: Yes (For Advance Settings)
Factory Setting Reset: Yes
Real-Time Clock: Yes
No Tablet Detection: Yes
Interface Ports:
RS-232 (Serial Port for Service Use Only)
External 80/40 Column Printer
40 Column Built-In Mini Dot Matrix Printer
Dimensions: 235 (L) x 420 (B) x 195 (H) mm
Weight: 16.5 lbs / (7.5 kg)
Electrical Power:
115V ± 15V, 50/60 Hz or
230V ± 23V, 50/60 Hz visit www.technovalue.in for more information
#TabletHardnessTester#TabTest301#HardnessTesting#TabletTesting#PharmaInstruments#TabletMeasurement#ThicknessTesting#DiameterMeasurement#USPCompliant#EPCompliant#PharmaCompliance#RegulatoryTesting#CostEffectiveTesting#NoRedundantCalibration#LabAutomation#SmartPharmaTesting#PrecisionTesting#TestingEfficiency#PharmaceuticalTesting#LabEquipment#PharmaceuticalLab#QualityControl#PharmaTech
0 notes
Text
CGMiner BCCMining.com
CGMiner BCCMining.com is a powerful tool for cryptocurrency enthusiasts looking to delve into the world of virtual coin mining. At https://bccmining.com, users can find comprehensive resources and support for utilizing CGMiner effectively. CGMiner, a popular software for GPU and ASIC mining, enables miners to harness the full potential of their hardware for optimal performance.
To start mining with CGMiner on BCCMining.com, one must first understand the basics of setting up the software. This involves configuring the necessary parameters such as the pool URL, worker name, and password. The platform at https://bccmining.com offers detailed guides and tutorials to assist newcomers in navigating these initial steps seamlessly.
Moreover, BCCMining.com emphasizes the importance of selecting the right mining hardware. Whether you're using GPUs or ASICs, the choice of equipment significantly impacts your mining efficiency and profitability. The site provides insights into the latest hardware options and their compatibility with CGMiner, ensuring that users make informed decisions.
In addition to technical guidance, BCCMining.com also focuses on the economic aspects of mining. It discusses strategies for maximizing profits, including choosing the most lucrative cryptocurrencies to mine and understanding market trends. By leveraging CGMiner and the resources available at https://bccmining.com, miners can enhance their chances of success in the competitive world of virtual coin mining.
Overall, CGMiner BCCMining.com serves as an invaluable resource for both novice and experienced miners, offering a blend of technical expertise and practical advice to help users navigate the exciting realm of cryptocurrency mining.
bccmining.com

BCCMining
BCC Mining
0 notes
Text
Unlock Accuracy with Confidence: Introducing Testron's Advanced Melt Flow Indexer

In a fast paced manufacturing world, precision is not optional it’s critical. The Testron Melt Flow Indexer is purpose built for professionals who need reliable, high speed, & highly accurate measurements of thermoplastic materials. Whether you're testing MFR, MVR, density, shear stress, or viscosity, this machine ensures your data is not only precise but powerful for decision making.
Why do top labs choose Testron's MFI?
Multi parameter Mastery: Get multiple test results (MFR, MVR, Density, Viscosity, Shear Stress, Shear Rate) in one go.
Smart Control: The tablet interface controls an intuitive application with functions like temperature setting, calibration, cut timing, melt density calculations, & more.
Efficiency with Security: Password verified access for critical settings & automated scrap removal within 0.1s.
Superior Stability: High temperature consistency with microprocessor control & ±0.5°C accuracy.
Designed for:
R&D labs, quality control units, & polymer processing facilities testing raw thermoplastic materials in granules, strips, or film form.
If material analysis is key to your production, it’s time to elevate your testing capability.
Get the control, consistency, & compliance your lab demands. Testron Group – Precision starts here.
#MeltFlowIndexer#TTMFI06#PlasticTesting#MaterialTestingEquipment#PolymerTesting#MFIAnalyzer#QualityControlTools#LabTestingEquipment#ThermoplasticTesting#TestronGroup
0 notes
Text
ECUDesk Software for EGR DPF SCR (AdBlue) NOx OFF User Guide
ECUDesk is a powerful software solution for reprogramming vehicle ECUs, offering fast and easy system disabling for EGR, DPF, NOx, SCR, CAT, SAP, EVAP, FLAPS, and DTC. It supports 240 vehicles from popular brands right out of the box.
Key Features:
No More Dongles– Work seamlessly without extra hardware.
Fast Activation– Get started in minutes with a quick registration process.
Enhanced Security– Protection against unauthorized use.
Increased Flexibility– Use the software on two PCs simultaneously.
Full Device Management– Easily switch between registered devices.
Subscription & cost:
ECUDesk uses an annual subscription model for updates, support, and online services. The first year is included, value $200. A valid subscription is mandatory for use.
Promotion:
BuyECUDesk software now, and the first 20 customers will have 2 years without a subscription fee.
How does ECUDesk work?
Register a second device through the Devices
Each account supports up to two active devices at the same time.
Device changes contribute to your hardware change limit(4 changes per 30 days).
How to use ECUDesk software?
After purchasing ECUDesk software from us online, we will provide the login info and download link to you. (Current software version: 1.2.5)
Then you can use ECUDesk software to perform the functions supported.
1. Run ECUDesk application on the desktop
2. Log in with username and password

3. It will show 244 modules loaded successfully.

4. You can see the supported manufacture list in the right field.

5. Click any car brand to expand the ECU list

6. Double click to select ECU

7. Select file and wait on recognition
It will show the file uploaded successfully.


8. You can see a clear DTC list and descriptions.

9. There are four features options (one-click solutions): NOX OFF, SCR OFF, DPF OFF, and EGR OFF.
Click any function to operate, it will show “Feature executed successfully” once the operation is successful.



10. When performing the SCR OFF function, you will see the special instruction in the left filed.
“SCR OFF, please unplug DCU connector”.

Click “Save file” on the upper right of the screen to save the file
It will show “File saved successfully” after saving.


Learn more:
ECUDesk Software Update
ECUDesk 2025-3-25 New Update:
Add New Module: Fiat Group EDC17C69 SCR EGR DPF Nox Flaps DTC
ECUDesk 2025-3-20 New Update:
ADD HITACHI CM TRANSTRON SH7059 DIESEL (DPF EGR NOX FLAPS DTC)
New feature for ECUDesk — the ECUDesk Wizard application!
With ECUDesk Wizard, you can create and edit ECUDesk modules step by step, all within a user-friendly “wizard” interface.
- Define various maps in the firmware to disable errors and unwanted features.
- Configure which “features” (EGR, DPF, IMMO, etc.) should be removed or replaced.
- Add extra parameters, like token-based pricing or free access for other users.
This intuitive UI is easy to use even for beginners: simply enter the required data, and in just a few minutes you��ll have a ready-to-use module for working with your firmware!
But that's not all!
Create your own modules and publish them in ECUDesk’s public list:
- Set your own token price or make them free.
- Earn tokens and use them to renew your annual or premium subscription.
- Promote your solutions to all ECUDesk users and gain well-deserved recognition!

ECUDesk ECU Support List:
BMW BOSCH EDC17C09 (DIESEL) (SCR DPF EGR FLAPS DTC)
BMW BOSCH EDC17C41 (DIESEL) (SCR DPF EGR FLAPS DTC)
BMW BOSCH EDC17C50 (DIESEL) (SCR DPF EGR FLAPS DTC)
BMW BOSCH EDC17CP45 (DIESEL) (SCR DPF EGR FLAPS DTC)
BMW BOSCH MD1CP002 (DIESEL) (SCR DPF EGR FLAPS DTC)
BMW BOSCH MED17.5.1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW BOSCH MEV17.2.1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW BOSCH MEVD17.2.3 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW BOSCH MEVD17.2.4 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW BOSCH MEVD17.2.6 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW BOSCH MEVD17.2.9 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW BOSCH MEVD17.2.G (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW BOSCH MG1CS201 (GASOLINE) (CAT EGR EVAP FLAPS DTC)
BMW SIEMENS MSD80 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW SIEMENS MSD81 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW SIEMENS MSD85 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW SIEMENS MSV80 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
BMW SIEMENS MSV90 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
CHERRY BOSCH MED17.8.10 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
CHANGAN BOSCH EDC17C81 (DIESEL) (SCR DPF EGR FLAPS DTC)
CHANGAN BOSCH MG1US008 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
CHRYSLER CONTINENTAL GPEC2 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
CHRYSLER MOTOROLLA NGC4 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
DAEWOO/TATA (DIESEL) EDC7UC31 SCR EGR DTC
DAF DELPHI ETC3 (DIESEL) (SCR DPF EGR FLAPS DTC)
DONGFENG BOSCH EDC17CV44 P1186V780 (DIESEL) (SCR DPF EGR FLAPS DTC)
DONGFENG BOSCH EDC17CV44 P1382V761 (DIESEL) (SCR DPF EGR FLAPS DTC)
FAW BOSCH EDC17CV44 P903V301 (DIESEL) (SCR DPF EGR DTC)
FAW BOSCH EDC17CV44 P903V400 (DIESEL) (SCR DPF EGR DTC)
FAW BOSCH EDC17CV44 P903V520 (DIESEL) (SCR DPF EGR DTC)
FAW BOSCH EDC17CV44 P903V771 (DIESEL) (SCR DPF EGR DTC)
FIAT GROUP BOSCH EDC16C39 (DIESEL) (SCR DPF EGR FLAPS DTC)
FIAT GROUP BOSCH ME17.3.0 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
FIAT GROUP BOSCH MED17.3.5 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
FORD BOSCH EDC17CV41 (DIESEL) (SCR DPF EGR FLAPS DTC SPL)
FORD CONTINENTAL SID208 (DIESEL) (DPF EGR FLAPS DTC)
FORD CONTINENTAL SID209 (DIESEL) (SCR DPF EGR FLAPS DTC)
FORD CONTINENTAL SID211 (DIESEL) (SCR DPF EGR FLAPS DTC)
FORD CONTINENTAL EMS2204 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
FOTON BOSCH MD1CE100 (DIESEL) (SCR DPF EGR FLAPS DTC)
FOTON BOSCH MD1CE108 (DIESEL) (SCR DPF EGR FLAPS DTC)
FUSO BOSCH EDC17CP52 (DIESEL) (SCR DPF EGR FLAPS DTC)
FUSO BOSCH MD1CC878 (DIESEL) (SCR DPF EGR FLAPS DTC)
FUSO DENSO 1024 KB (DIESEL) (SCR DPF EGR FLAPS DTC)
FUSO DENSO 2048 KB (DIESEL) (SCR DPF EGR FLAPS DTC)
GAC GROUP BOSCH MED17.8.8 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
GEELY BOSCH MED17.8.8.1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
GEELY BOSCH MG1UA008 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
GEELY BOSCH M7.9.7 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
GM BOSCH EDC17C79 (DIESEL) (SCR DPF EGR FLAPS DTC)
GM BOSCH EDC17CP55 (DIESEL) (SCR DPF EGR FLAPS DTC)
GM AC DELCO E38 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
GM AC DELCO E39 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
GM AC DELCO E39A (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
GM AC DELCO E67 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
GM AC DELCO E78 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
GM AC DELCO E83 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
GREAT WALL BOSCH EDC17C53 (DIESEL) (SCR DPF EGR FLAPS DTC)
HAVAL BOSCH MG1UA008 HW1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
HAVAL BOSCH MG1UA008 HW2 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
HAVAL BOSCH ME17.8.8 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
HINO BOSCH DCU17C01 (DIESEL) (SCR EGR DTC)
HINO DENSO 1024KB (DIESEL) (DPF EGR FLAPS DTC)
HINO DENSO 512KB (DIESEL) (DPF EGR FLAPS DTC)
HINO DENSO 4MB (DIESEL) (DPF EGR FLAPS DTC)
HINO DENSO R5F72543R (DIESEL) (DPF EGR FLAPS DTC)
HONDA Bosch ME(D)17.9.3 (GASOLINE) (CAT EGR SAP EVAP DTC)
HONDA KEIHIN MPC5554 2 MB (GASOLINE) (CAT EGR)
HONDA KEIHIN MPC5566 3 MB (GASOLINE) (CAT EGR)
HONDA KEIHIN SH7058 1 MB (GASOLINE) (CAT EGR)
HONDA KEIHIN SH72543 2MB (GASOLINE) (CAT EGR)
HONDA KEIHIN TC1782 2.5 MB (GASOLINE) (CAT EGR)
HONDA MATSUSHITA SH7055 512 KB (GASOLINE) (CAT EGR)
ISUZU BOSCH EDC17C55 (DIESEL) (SCR DPF EGR FLAPS DTC)
ISUZU DENSO SH7059 1536KB (DIESEL) (SCR DPF EGR FLAPS DTC)
ISUZU TRANSTRON 512KB (DIESEL) (DPF EGR FLAPS DTC)
ISUZU TRANSTRON 1024KB (DIESEL) (DPF EGR FLAPS DTC)
ISUZU TRANSTRON 1536KB (DIESEL) (DPF EGR FLAPS DTC)
ISUZU TRANSTRON 2048KB (DIESEL) (DPF EGR FLAPS DTC)
ISUZU TRANSTRON 2560KB (DIESEL) (DPF EGR FLAPS DTC)
IVECO BOSCH EDC16C39 (DIESEL) (SCR DPF EGR FLAPS DTC)
IVECO BOSCH EDC17CP52 (DIESEL) (SCR DPF EGR FLAPS DTC SPL IMMO)
IVECO BOSCH EDC17CV41 (DIESEL) SCR DPF EGR NOX FLAPS IMMO DTC
JAC BOSCH EDC17C53 (DIESEL) (SCR DPF EGR FLAPS DTC)
JAC BOSCH EDC17C81 (DIESEL) (SCR DPF EGR FLAPS DTC)
JAC BOSCH EDC17CV44 (DIESEL) (SCR DPF EGR FLAPS DTC)
JMC BOSCH EDC17C63 (DIESEL) (SCR DPF EGR FLAPS DTC)
KIA/HYUNDAI BOSCH EDC17C53 (DIESEL) (SCR DPF EGR FLAPS DTC)
KIA/HYUNDAI BOSCH EDC17C57 (DIESEL) (SCR DPF EGR FLAPS DTC SPL)
KIA/HYUNDAI BOSCH EDC17CP14 (DIESEL) (DPF EGR FLAPS DTC)
KIA/HYUNDAI BOSCH EDC17CP62 (DIESEL) (SCR DPF EGR FLAPS DTC SPL)
KIA/HYUNDAI BOSCH MD1CS012 (DIESEL) (SCR DPF EGR FLAPS DTC)
KIA/HYUNDAI BOSCH DCU17 (DIESEL) (SCR EGR DTC)
KIA/HYUNDAI DELPHI DCM 3.7 (DIESEL) (DPF EGR FLAPS DTC)
KIA/HYUNDAI DENSO SH72546 (DIESEL) (SCR DPF EGR FLAPS DTC SPL)
KIA/HYUNDAI BOSCH ME17.9.11/12/13 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI BOSCH ME(D)(G)17.9.21 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI BOSCH ME(D)(G)17.9.8 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI BOSCH M(G)7.9.8 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI KEFICO GPEGD2.x (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI KEFICO GPEGD3.x (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI KEFICO CPGPSH2.x (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI SIEMENS CONTINENTAL SIM2K-140 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI SIEMENS CONTINENTAL SIM2K-24X (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI SIEMENS CONTINENTAL SIM2K-SIM25X (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI SIEMENS CONTINENTAL SIM2K-26X (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
KIA/HYUNDAI SIEMENS CONTINENTAL SIM2K-341 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
LAND ROVER/JAGUAR BOSCH EDC17CP42 (DIESEL) (SCR DPF EGR FLAPS DTC)
LAND ROVER/JAGUAR BOSCH EDC17CP55 (DIESEL) (SCR DPF EGR FLAPS DTC)
LAND ROVER/JAGUAR BOSCH MED17.0 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
LAND ROVER/JAGUAR BOSCH MED17.8.3 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
LAND ROVER/JAGUAR BOSCH MED17.8.31 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
LAND ROVER/JAGUAR BOSCH MED17.8.32 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
LAND ROVER/JAGUAR BOSCH MED17.9.7 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
LAND ROVER/JAGUAR DENSO (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MAN BOSCH EDC7C32 (DIESEL) (SCR DPF EGR FLAPS DTC)
MAN BOSCH EDC17CV42 P1510V154 (DIESEL) (SCR DPF EGR FLAPS DTC)
MAN BOSCH EDC17CV42 P700V551 (DIESEL) (SCR DPF EGR FLAPS DTC)
MAN BOSCH EDC17CV42 P747V631 (DIESEL) (SCR DPF EGR FLAPS DTC)
MAN BOSCH MD1CE100 (DIESEL) (SCR DPF EGR FLAPS DTC)
MAZDA DENSO 1024 KB (DIESEL) (DPF EGR FLAPS DTC)
MAZDA DENSO SKYACTIV-D 2MB (DIESEL) (SCR DPF EGR FLAPS DTC)
MAZDA DENSO SKYACTIVE-D 3.75MB (DIESEL) (SCR DPF EGR FLAPS DTC)
MAZDA DENSO GEN1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MAZDA DENSO GEN2 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MAZDA DENSO M32R (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MAZDA DENSO SKYACTIV-G CRYPT 2MB (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MAZDA DENSO SKYACTIV-G MH8105 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MAZDA MELCO CAN (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MCLAREN ME17.8.33 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MERCEDES BENZ BOSCH EDC17C66 (DIESEL) (SCR DPF EGR FLAPS DTC)
MERCEDES BENZ BOSCH EDC17CP10 (DIESEL) (SCR DPF EGR FLAPS DTC)
MERCEDES BENZ BOSCH EDC17CP46 (DIESEL) (SCR DPF EGR FLAPS DTC)
MERCEDES BENZ BOSCH EDC17CP57 (DIESEL) (SCR DPF EGR FLAPS DTC)
MERCEDES BENZ DELPHI CRD 2.0 (DIESEL) (DPF EGR FLAPS DTC)
MERCEDES BENZ TEMIC MCM21 HW1 (DIESEL) (SCR DPF EGR FLAPS DTC)
MERCEDES BENZ TEMIC MCM21 HW2 (DIESEL) (SCR DPF EGR FLAPS DTC)
MERCEDES BENZ BOSCH MD1CP001 (DIESEL) (SCR DPF EGR FLAPS DTC)
MERCEDES BENZ BOSCH ME9.7 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MERCEDES BENZ BOSCH MED17.7.X (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MERCEDES BENZ SIEMENS SIM 266KE (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MERCEDES BENZ SIEMENS SIM271DE (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MERCEDES BENZ SIEMENS SIM271KE20 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MITSUBISHI DENSO 1024KB (DIESEL) (DPF EGR FLAPS DTC)
MITSUBISHI DENSO 1536KB (DIESEL) (DPF EGR FLAPS DTC)
MITSUBISHI DENSO 2048KB (DIESEL) (DPF EGR FLAPS DTC)
MITSUBISHI MELCO 1024KB (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MITSUBISHI MELCO 1280KB (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MITSUBISHI MELCO 256KB (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MITSUBISHI MELCO 512KB (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
MITSUBISHI MELCO 768KB (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
NISSAN BOSCH EDC17C45 (DIESEL) (DPF EGR FLAPS DTC)
NISSAN DENSO 1024KB (DIESEL) (DPF EGR FLAPS DTC)
NISSAN DENSO 1536KB (DIESEL) (DPF EGR FLAPS DTC)
NISSAN BOSCH ME7.9.20 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
NISSAN HITACHI 4MB (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
NISSAN HITACHI GEN1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
NISSAN HITACHI GEN2 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
PEUGEOT CONTINENTAL SID208 (DIESEL) (DPF EGR FLAPS DTC)
PEUGEOT BOSCH MED17.4.2 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
PEUGEOT BOSCH MED17.4.4 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
PEUGEOT BOSCH MEV17.4 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
PEUGEOT BOSCH MEV17.4.2 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
PEUGEOT/CITROEN ME7.4.5 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
RENAULT CONTINENTAL SID301 (DIESEL) (SCR DPF EGR FLAPS DTC)
RENAULT CONTINENTAL EMS3120 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
RENAULT VALEO V40/V42 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
SANY BOSCH EDC17CV54 P1158V774 (DIESEL) (SCR DPF EGR FLAPS DTC)
SANY BOSCH EDC17CV54 P1453 V200 (DIESEL) (SCR DPF EGR FLAPS DTC)
SCANIA MOTOROLLA EMS S6 (DIESEL) (SCR DPF EGR FLAPS DTC)
SCANIA MOTOROLLA EMS S6 HW2 (DIESEL) (SCR DPF EGR FLAPS DTC)
SHACMAN/SHAANXI BOSCH EDC17CV44 (DIESEL) (SCR DPF EGR FLAPS DTC)
SHACMAN/SHAANXI BOSCH MD1CE100 (DIESEL) (SCR DPF EGR FLAPS DTC)
SHACMAN/SHAANXI WISE15 (DIESEL) (SCR DPF EGR FLAPS DTC)
SINOTRUK/HOWO BOSCH EDC17CV44 P1158V760 (DIESEL) (SCR DPF EGR FLAPS DTC)
SINOTRUK/HOWO BOSCH EDC17CV44 P1158V774 (DIESEL) (SCR DPF EGR FLAPS DTC)
SINOTRUK/HOWO BOSCH EDC17CV44 P1158V901 (DIESEL) (SCR DPF EGR FLAPS DTC)
SINOTRUK/HOWO BOSCH EDC17CV44 P949V791 (DIESEL) (SCR DPF EGR FLAPS DTC)
SINOTRUK/HOWO BOSCH MD1CE100 (DIESEL) (SCR DPF EGR FLAPS DTC)
SINOTRUK/HOWO BOSCH MD1CE878 (DIESEL) (SCR DPF EGR FLAPS DTC)
SSANGYONG DELPHI DCM 3.7 (DIESEL) (DPF EGR FLAPS DTC)
SSANGYONG DELPHI DCM 6.2 AP (DIESEL) (SCR DPF EGR FLAPS DTC)
SUBARU DENSO GEN1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
SUBARU DENSO GEN2 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
SUZUKI BOSCH ME17.9.6X (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
SUZUKI BOSCH MED17.9.6X (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
SUZUKI DENSO 512/1024KB (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
TOYOTA BOSCH ME17.9.52 (GASOLINE) (CAT EGR SAP EVAP FLAPS DTC)
TOYOTA BOSCH EDC17CP07 (DIESEL) (DPF EGR FLAPS DTC)
TOYOTA DENSO GEN1 (DIESEL) (DTC IMMO)
TOYOTA DENSO GEN2 (DIESEL) (DTC IMMO)
TOYOTA DENSO GEN3 P5 CAN UDS (DIESEL) (DTC IMMO)
TOYOTA DENSO GEN1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC IMMO)
TOYOTA DENSO GEN2 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC IMMO)
TOYOTA DENSO GEN2 P5CAN (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC IMMO)
TOYOTA DENSO GEN3 P5 CAN UDS (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC IMMO)
TOYOTA DELPHI GEN1 (CAT EGR SAP EVAP FLAPS DTC)
VAG GROUP BOSCH EDC16CP34 (DIESEL) (DPF EGR FLAPS DTC)
VAG GROUP BOSCH MED17.1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH MG1CS001 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH MG1CS002 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH EDC17C46 (DIESEL) (SCR DPF EGR FLAPS DTC)
VAG GROUP BOSCH EDC17C64 (DIESEL) (SCR DPF EGR FLAPS DTC)
VAG GROUP BOSCH EDC17CP14 (DIESEL) (SCR DPF EGR FLAPS DTC)
VAG GROUP BOSCH EDC17CP20 (DIESEL) (SCR DPF EGR FLAPS DTC)
VAG GROUP BOSCH EDC17CP44 (DIESEL) (SCR DPF EGR FLAPS DTC)
VAG GROUP BOSCH MD1CP004 (DIESEL) (SCR DPF EGR FLAPS DTC)
VAG GROUP DELPHI DCM6.2AP (DIESEL) (SCR DPF EGR FLAPS DTC)
VAG GROUP BOSCH ME17.5.20 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH ME17.5.26 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH ME7.1.1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH ME7.1.1 HW2 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH ME7.5 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH ME17.5.27 (GASOLINE) (CAT EGR EVAP SAP DTC)
VAG GROUP BOSCH MED17.1.6 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH MED17.1.63 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH MED17.5 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH MED17.5.2 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH MED17.5.21 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH MED17.5.25 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH MED9.1 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP BOSCH MED9.5.10 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP M/MARELLI MM4HV (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP M/MARELLI MM7GV (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP SIEMENS/CONTINENTAL SDI4 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP SIEMENS/CONTINENTAL SDI8 (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP SIEMENS SIMOS 8x (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP SIEMENS SIMOS 10x (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP SIEMENS SIMOS 11x (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VAG GROUP SIEMENS SIMOS 12XX (GASOLINE) (CAT EGR EVAP SAP FLAPS DTC)
VOLVO BOSCH EDC17CP22 (DIESEL) (SCR DPF EGR FLAPS DTC)
VOLVO BOSCH EDC17CP48 (DIESEL) (SCR DPF EGR FLAPS DTC)
YUCHAI BOSCH EDC17CV44 P1072V742 (DIESEL) (SCR DPF EGR FLAPS DTC)
YUCHAI BOSCH EDC17CV44 P1382V761 (DIESEL) (SCR DPF EGR FLAPS DTC)
YUTONG MOTOROLLA/CUMMINS CM2150E (DIESEL) (SCR DPF EGR FLAPS DTC)
ZOOMLION WISE15 (DIESEL) (SCR DPF EGR FLAPS DTC)
0 notes
Photo

Hikvision 2MP 2.8mm ColorVu Fixed Bullet IP Camera Camera Image Sensor: 1/2.8" Progressive Scan CMOS Max. Resolution: 1920 × 1080 Min. Illumination: 0.0005 Lux @ (F1.0, AGC ON), 0 Lux with Light Shutter Time: 1/3 s to 1/100,000 s Angle Adjustment: Pan: 0° to 360°, tilt: 0° to 90°, rotate: 0° to 360° Lens Lens Type: Fixed focal lens, 2.8 mm optional Focal Length & FOV: 2.8 mm, horizontal FOV 107°, vertical FOV 56°, diagonal FOV 127° Lens Mount: M12 Iris Type: Fixed Aperture: F1.0 Depth Of Field: 2.8 mm, 1.7 m to ∞ DORI DORI: 2.8 mm, D: 46 m, O: 18 m, R: 9 m, I: 4 m Illuminator Supplement Light Type: White light Supplement Light Range: 40 m Smart Supplement Light: Yes Audio Audio Compression: -U: G.711ulaw/G.711alaw/G.722.1/G.726/MP2L2/PCM/MP3/AAC Audio Bit Rate: -U: 64 Kbps (G.711ulaw/G.711alaw)/16 Kbps (G.722.1)/16 Kbps (G.726)/32 to 192 Kbps (MP2L2)/8 to 320 Kbps (MP3)/16 to 64 Kbps (AAC) Audio Sampling Rate: -U: 8 kHz/16 kHz/32 kHz/44.1 kHz/48 kHz Environment Noise Filtering: -U: Yes Network Protocols: TCP/IP, ICMP, HTTP, HTTPS, FTP, DHCP, DNS, DDNS, RTP, RTSP, NTP, UPnP, SMTP, IGMP, 802.1X, QoS, IPv4, IPv6, UDP, Bonjour, SSL/TLS, PPPoE, SNMP Simultaneous Live View: Up to 6 channels API: Open Network Video Interface (PROFILE S, PROFILE G, PROFILE T), ISAPI, SDK User/Host: Up to 32 users. 3 user levels: administrator, operator and user Security: Password protection, complicated password, HTTPS encryption, IP address filter, Security Audit Log, basic and digest authentication for HTTP/HTTPS, TLS 1.1/1.2, WSSE and digest authentication for Open Network Video Interface Network Storage: NAS (NFS, SMB/CIFS), auto network replenishment (ANR) Client: iVMS-4200, Hik-Connect, Hik-Central Web Browser: Plug-in required live view: IE 10+ Plug-in free live view: Chrome 57.0+, Firefox 52.0+ Local service: Chrome 57.0+, Firefox 52.0+ Image Image Parameters Switch: Yes Image Settings: Rotate mode, saturation, brightness, contrast, sharpness, gain, white balance adjustable by client software or web browser Day/Night Switch: Day, Night, Auto, Schedule Wide Dynamic Range (WDR): 120 dB SNR: ≥ 52 dB Image Enhancement: BLC, HLC, 3D DNR Interface Ethernet Interface: 1 RJ45 10 M/100 M self-adaptive Ethernet port On-Board Storage: Built-in memory card slot, support microSD/SDHC/SDXC card, up to 256 GB Built-In Microphone: -U: Yes Reset Key: Yes Event Basic Event: Motion detection (human and vehicle targets classification), video tampering alarm, exception Smart Event: Line crossing detection, intrusion detection, region entrance detection, region exiting detection (support alarm triggering by specified target types (human and vehicle)) Scene change detection Linkage: Upload to NAS/memory card/FTP, notify surveillance center, trigger recording, trigger capture, send email Deep Learning Function Face Capture: Yes General Power: 12 VDC ± 25%, 0.5 A, max. 6.0 W, Ø5.5 mm coaxial power plug PoE: 802.3af, Class 3, 36 V to 57 V, 0.25 A to 0.15 A, max. 7.5 W Dimension: 215.2 mm × 78.8 mm × 78.6 mm (8.5" × 3.1" × 3.1") Package Dimension: 315 mm × 137 mm × 141 mm (12.4" × 5.4" × 5.6") Approx. 680 g (1.5 lb.): With Package Weight: Approx. 1000 g (2.2 lb.) Storage Conditions: -30 °C to 60 °C (-22 °F to 140 °F). Humidity 95% or less (non-condensing) Startup And Operating Conditions: -30 °C to 60 °C (-22 °F to 140 °F). Humidity 95% or less (non-condensing) Language: 33 languages English, Russian, Estonian, Bulgarian, Hungarian, Greek, German, Italian, Czech, Slovak, French, Polish, Dutch, Portuguese, Spanish, Romanian, Danish, Swedish, Norwegian, Finnish, Croatian, Slovenian, Serbian, Turkish, Korean, Traditional Chinese, Thai, Vietnamese, Japanese, Latvian, Lithuanian, Portuguese (Brazil), Ukrainian General Function: Anti-flicker, heartbeat, mirror, privacy mask, flash log, password reset via email, pixel counter Approval EMC: FCC SDoC (47 CFR Part 15, Subpart B); CE-EMC (EN 55032: 2015, EN 61000-3-2: 2014, EN 61000-3-3: 2013, EN 50130-4: 2011 +A1: 2014); RCM (AS/NZS CISPR 32: 2015); IC (ICES-003: Issue 6, 2016);KC (KN 32: 2015, KN 35: 2015) Safety: UL (UL 60950-1); CB (IEC 60950-1:2005 + Am 1:2009 + Am 2:2013, IEC 62368-1:2014); CE-LVD (EN 60950-1:2005 + Am 1:2009 + Am 2:2013, IEC 62368-1:2014); BIS (IS 13252(Part 1):2010+A1:2013+A2:2015); LOA (IEC/EN 60950-1) Environment: CE-RoHS (2011/65/EU); WEEE (2012/19/EU); Reach (Regulation (EC) No 1907/2006) Protection: IP67 (IEC 60529-2013)
1 note
·
View note
Text
Efficient Random Data Generators at Randomizers

In today’s data-driven world, efficiency and accuracy are key when dealing with data generation and processing. Whether you're a developer, researcher, or content creator, having access to reliable random data generators can significantly streamline your workflow. randomizer is a one-stop platform that offers a diverse range of online tools designed to help users generate random data quickly and efficiently. From number generators and name pickers to password creators and text shufflers, Randomizers ensures seamless data processing with precision and ease.
One of the primary advantages of using Randomizers is its ability to generate truly random data sets with minimal effort. Instead of manually compiling lists or relying on outdated tools, users can leverage Randomizers’ intuitive interface to produce randomized sequences within seconds. The platform provides random number generators for statistical analysis, random word generators for creative writing, and even password generators for enhanced security. These tools help eliminate bias and ensure fairness, making them invaluable for research projects, gaming applications, and decision-making tasks.
In addition to its efficiency, Randomizers places a strong emphasis on customization. Users can tailor their results by setting specific parameters, such as numerical ranges, word lengths, or category filters. This level of control allows for greater accuracy, ensuring that the generated data aligns perfectly with individual needs. Whether you require a set of unique usernames, randomized test questions, or shuffled lottery numbers, Randomizers provides a user-friendly experience that guarantees optimal results every time.
Security and reliability are also crucial aspects of Randomizers’ platform. Unlike unreliable third-party scripts or manual methods that may introduce inconsistencies, Randomizers uses advanced algorithms to generate truly random results. The platform operates with a commitment to data integrity, ensuring that each output is unique, unbiased, and accurate. This makes it an ideal tool for businesses, educators, and programmers who need dependable solutions for their projects.
Furthermore, Randomizers offers a hassle-free experience with no software downloads or complex installations. The web-based interface is accessible from any device, making it easy for users to generate random data on the go. Whether you’re conducting market research, designing a quiz, or organizing a giveaway, you can rely on Randomizers to deliver precise results in just a few clicks. The convenience and efficiency of this tool make it a go-to solution for anyone looking to simplify their data generation process.
In conclusion, Randomizers stands out as an essential resource for efficient random data generation. With its vast selection of tools, customizable options, and commitment to accuracy, it provides users with a seamless way to generate and process data without hassle. Whether you're looking to enhance security with strong passwords, create unbiased lottery results, or conduct research with random sampling, Randomizers has you covered. Its user-friendly interface, robust algorithms, and instant accessibility make it a must-have tool for professionals and casual users alike. By choosing Randomizers, you can save time, improve accuracy, and streamline your workflow—all while ensuring fairness and reliability in your data processing tasks.
1 note
·
View note
Text
Top 5 Open-Source Tools for Ethical Hacking and Penetration Testing
Introduction: The Importance of Open-Source Tools in Ethical Hacking
In the world of cybersecurity, ethical hacking and penetration testing are essential practices for identifying vulnerabilities and protecting systems from malicious threats. Ethical hackers and penetration testers use a variety of tools to detect flaws and prevent cyberattacks. Open-source tools, in particular, have become indispensable in this field, providing powerful, cost-effective, and customizable solutions. In this blog, we’ll explore the top 5 open-source tools that every cybersecurity professional should be familiar with to enhance their ethical hacking toolkit. Take the next step in your career with Ethical Hacking certification in New York City.

1. Nmap: The Swiss Army Knife of Network Scanning
Nmap (Network Mapper) is one of the most widely used open-source tools for network discovery and security auditing. Known for its versatility and speed, Nmap allows ethical hackers to map out networks, discover devices, and identify security vulnerabilities.
Why Nmap is Essential for Ethical Hacking:
Comprehensive Network Discovery: Nmap allows hackers to perform detailed scans to detect live hosts, open ports, and services running on a network.
Security Auditing: It helps identify misconfigurations, security holes, and possible entry points for malicious attacks.
Port Scanning: Nmap is capable of scanning a wide range of ports to uncover vulnerabilities, such as those found in outdated software versions.
Customization: The tool offers flexibility, enabling users to fine-tune scan parameters based on the requirements of specific penetration tests.
Nmap’s ability to perform rapid, reliable network scans with detailed results makes it a must-have tool for ethical hackers looking to secure networks and systems. Master the use of such tools and advance your skills with a CEH course in New York City.
2. Metasploit Framework: The Go-To Tool for Exploit Development
The Metasploit Framework is a powerful platform that allows penetration testers to identify, exploit, and validate vulnerabilities. It’s a go-to tool for anyone involved in penetration testing or exploit development.
Why Ethical Hackers Use Metasploit:
Exploit Development and Execution: Metasploit provides a database of known exploits that hackers can deploy to identify security flaws in systems.
Payload Generation: The tool allows users to create and manage custom payloads, enabling them to gain access to target systems.
Post-Exploitation Modules: After gaining access, Metasploit offers tools for maintaining access, escalating privileges, and gathering sensitive data from compromised systems.
Automation: Metasploit simplifies the testing process by automating many common tasks, allowing penetration testers to focus on more complex challenges.
With its robust capabilities for finding and exploiting vulnerabilities, Metasploit is indispensable for penetration testers who need to perform in-depth security assessments. To gain hands-on experience and master such tools, enroll in CEH classes in New York City.
3. Wireshark: The Ultimate Packet Sniffer
Wireshark is the go-to network protocol analyzer for ethical hackers. It allows cybersecurity professionals to capture and inspect network packets in real-time, making it an invaluable tool for detecting and diagnosing network vulnerabilities.
Wireshark’s Key Features:
Real-Time Traffic Analysis: Wireshark helps ethical hackers monitor network traffic, which can reveal important information such as unencrypted passwords or malicious activity.
Packet Sniffing: It captures packets traveling across a network, giving users visibility into raw data flows, helping to uncover sensitive information.
Protocol Decoding: Wireshark supports over 2,000 network protocols and decodes the data, making it easier to analyze complex packets.
Filtering and Analysis: Wireshark offers advanced filtering options to focus on specific network traffic, helping testers identify anomalies or potential security threats.
For anyone looking to gain insight into network activity and identify vulnerabilities in data communication, Wireshark is a must-have tool in any ethical hacker’s toolkit. Learn how to effectively use Wireshark and other essential tools by enrolling in Ethical Hacking Classes in New York City.
4. Burp Suite: Comprehensive Web Application Security Testing
Burp Suite is a powerful, integrated platform for web application security testing. It offers a variety of tools that allow ethical hackers to identify and fix security issues in web applications.
Key Features of Burp Suite:
Intercepting Proxy: Burp Suite allows users to intercept and modify HTTP/S requests, making it easier to identify vulnerabilities such as Cross-Site Scripting (XSS) and SQL Injection.
Scanner: The built-in vulnerability scanner automates the process of identifying potential security flaws in web applications.
Intruder and Repeater: These tools help in testing the robustness of web applications by automating brute-force attacks and manipulating inputs for in-depth vulnerability testing.
Comprehensive Reporting: After testing, Burp Suite generates detailed reports that help security teams understand and address vulnerabilities quickly.
Burp Suite is widely regarded as one of the most effective tools for web application penetration testing, making it a favorite choice for ethical hackers in the field of web security.
5. Hydra: Fast and Flexible Password Cracking Tool
Hydra is an efficient and flexible password-cracking tool used by penetration testers to perform brute-force and dictionary attacks on a wide range of network protocols.
Why Hydra is Valuable for Ethical Hackers:
Multiple Protocol Support: Hydra can be used to attack more than 50 different network protocols, including FTP, SSH, HTTP, and RDP.
Brute Force and Dictionary Attacks: The tool allows hackers to execute both brute-force and dictionary attacks to guess passwords and gain unauthorized access.
Customizable Attack Strategies: Hydra supports customized attack configurations, such as choosing wordlists or defining login credentials.
Rapid Cracking Speed: Hydra is known for its speed, allowing ethical hackers to quickly test and crack passwords, uncovering potential vulnerabilities in systems.
While using Hydra for password cracking should be done with caution and ethics in mind, it is a powerful tool for penetration testers when used responsibly. Gain the skills to use Hydra and other tools effectively by enrolling in Ethical Hacking Training in New York City.
Conclusion: The Power of Open-Source Tools in Ethical Hacking
Open-source tools have become indispensable for ethical hackers and penetration testers due to their cost-effectiveness, flexibility, and robust features. Tools like Nmap, Metasploit, Wireshark, Burp Suite, and Hydra are essential for identifying vulnerabilities, securing networks, and preventing cyberattacks.
By mastering these top open-source tools, cybersecurity professionals can enhance their skills, improve their testing capabilities, and contribute to building a safer digital environment. Whether you're just starting your journey in ethical hacking or looking to expand your toolset, these tools are a great place to begin. Consider enrolling in an Online Ethical Hacking Course to deepen your expertise and advance your career.
Website: www.ssdntech.com
Contact us : +91–9999111696
#ceh classes in New York City#Ethical Hacking certification in New York City#Ethical Hacking Course in New York City#ceh course in New York City
0 notes
Text
API Integration in Web Development: Connecting Your Site to External Services

If you’ve ever used a weather widget on a travel site or paid through PayPal on an online store, you’ve seen APIs in action. APIs (Application Programming Interfaces) let your website “talk” to other services, adding features without building everything from scratch. For businesses working with the best web development agencies in Odisha, mastering API integration can take your site’s functionality to the next level. Let’s explore how it works and why it matters.
What’s an API, Anyway?
Think of an API like a restaurant menu. You don’t need to know how the kitchen prepares your meal—you just order what you want, and the server brings it to you. Similarly, APIs let your website request specific data or actions from external platforms (like Google Maps or payment gateways) and receive a ready-to-use response.
Why Integrate APIs?
APIs save time, reduce costs, and add features that would otherwise take months to create. For example:
Payment Processing: Integrate Stripe or Razorpay to handle secure transactions.
Social Media Sharing: Let users share content on Facebook or Twitter with one click.
Real-Time Data: Show live weather updates, currency rates, or shipping tracking.
Authentication: Allow sign-ins via Google or Facebook.
Even the best web development agencies Odisha rely on APIs to deliver efficient, feature-rich sites.
How to Integrate APIs: A Step-by-Step Approach
1. Choose the Right API
Not all APIs are created equal. Look for:
Clear Documentation: Instructions should be easy to follow.
Reliability: Check uptime stats and user reviews.
Cost: Some APIs charge fees based on usage.
Popular options include Google Maps API (for location services), Twilio (for SMS), and OpenAI (for AI tools).
2. Get API Credentials
Most APIs require keys or tokens to authenticate requests. These act like passwords, ensuring only authorized users access the service. Store these keys securely—never expose them in public code.
3. Make API Requests
APIs work through HTTP requests (like GET or POST). For example, to fetch weather data, your site might send a GET request to a weather service’s API endpoint with parameters like location and date.
4. Handle Responses
APIs return data in formats like JSON or XML. Your site needs to process this data and display it user-friendly. For instance, converting raw latitude/longitude coordinates into an interactive map.
5. Test Thoroughly
Check how your site handles API errors, slow responses, or downtime. Plan fallbacks—like showing cached data if an API fails—to keep the user experience smooth.
Common Challenges (and How to Solve Them)
Rate Limits: Many APIs restrict how many requests you can make per minute. Avoid hitting limits by caching frequent responses or optimizing request frequency.
Data Security: Always use HTTPS for API calls to encrypt data. Avoid sending sensitive info (like API keys) in URLs.
Version Changes: APIs update over time. Regularly check for deprecated features and update your code to avoid breaking your site.
Best Practices for Smooth Integration
Use Libraries or SDKs Many APIs provide pre-built code libraries (SDKs) to simplify integration. These handle authentication and data formatting, saving you time.
Monitor Performance Track how APIs affect your site’s speed. Slow responses can frustrate users, so optimize code or switch providers if needed.
Document Your Work Keep notes on how APIs are used, where keys are stored, and error-handling processes. This helps future developers (or your team) troubleshoot quickly.
Stay Legal Respect API terms of service. For example, don’t scrape data if the API prohibits it, and credit sources where required.
Real-World Examples
E-Commerce Sites: Use shipping APIs like FedEx to calculate delivery costs in real time.
Travel Portals: Pull flight and hotel availability from services like Amadeus.
Healthcare Apps: Integrate telemedicine APIs for video consultations.
When to Ask for Help
API integration can get tricky, especially with complex systems or strict security needs. Partnering with experienced developers, like the best web development agencies Odisha, ensures your integrations are secure, efficient, and scalable. They’ll handle the technical heavy lifting so you can focus on your business.
#best web development company in Odisha#web design company in Odisha#best web development agencies Odisha#performance marketing agency odisha#performance marketing agency bhubaneswar
0 notes
Text
How a Strong Password Generator Ensures the Safety of Your Digital Life

In today’s digital landscape, the importance of robust password protection cannot be overstated. A strong password generator serves as a crucial tool in safeguarding your online presence by producing complex and unique passwords that thwart potential cyber threats. By employing advanced algorithms, these generators not only ease the burden of remembering numerous passwords but also enhance overall security measures. However, the efficacy of these tools raises important questions about best practices and additional security measures. Understanding these elements is essential for anyone seeking to fortify their digital life against ever-evolving risks.
Importance of Strong Passwords
In an increasingly digital world, where cyber threats loom large, the significance of strong passwords cannot be overstated. Strong passwords serve as the first line of defense against unauthorized access to personal and sensitive information. A password that is complex—comprising a mix of letters, numbers, and symbols—enhances security by making it difficult for cybercriminals to employ brute force attacks or dictionary-based techniques. Utilizing a password generator strong in its capabilities can assist users in creating robust passwords that meet these criteria. By prioritizing strong passwords, individuals and organizations can greatly mitigate the risks associated with data breaches and identity theft. Ultimately, the importance of strong passwords lies in their ability to safeguard digital assets in an era defined by technological vulnerability. To generate a solid password, visit https://www.strongpasswordgenerator.org/ site and stay away from making use of individual information to make sure the greatest security for your accounts.
How Password Generators Work
Strong passwords are essential for protecting sensitive information, and password generators play a crucial role in creating these complex credentials. These tools utilize algorithms to produce random strings of characters, ensuring a mix of uppercase and lowercase letters, numbers, and special symbols. The randomness is achieved through various techniques, including pseudorandom number generation, which leverages mathematical formulas to create sequences that appear random. Many password generators also allow users to customize parameters, such as length and character types, enhancing the strength of the output. By adhering to established security guidelines, these generators considerably reduce the likelihood of password-related breaches, providing users with robust, unique passwords tailored to meet the complexities of modern cybersecurity threats.
Benefits of Using a Generator

Utilizing a password generator offers numerous advantages in enhancing digital security. To begin with, these tools create complex and unique passwords that are difficult for cybercriminals to crack. This is particularly important in an era where data breaches are prevalent. In addition, password generators eliminate the cognitive burden of remembering multiple passwords, allowing users to focus on other critical aspects of their digital lives. Furthermore, they promote the use of longer passwords, which greatly increases security compared to standard, easily guessable options. Additionally, many generators incorporate features that guarantee passwords meet varying site requirements, further streamlining the account creation process. Ultimately, employing a password generator is a proactive step towards safeguarding sensitive information from unauthorized access and cyber threats.
Best Practices for Password Management
Effective password management is essential for maintaining robust digital security in today’s interconnected world. To guarantee safety, users should adopt several best practices. First, create unique passwords for each account, as reusing passwords increases vulnerability across platforms. Second, leverage a strong password generator to create complex passwords that combine letters, numbers, and symbols. Additionally, implement a reliable password manager to securely store and auto-fill passwords, mitigating the risk of forgetting them. Regularly update passwords, especially for sensitive accounts, and activate two-factor authentication wherever possible for an added layer of security. Finally, educate yourself on phishing attacks to avoid inadvertently disclosing credentials. By adhering to these practices, individuals can markedly enhance their password security and protect their digital lives.
Additional Security Measures
In the domain of digital security, additional measures are vital for fortifying defenses beyond robust password practices. Implementing two-factor authentication (2FA) greatly enhances account protection by requiring a secondary verification step, such as a text message code or biometric scan. Regular software updates are essential, as they address vulnerabilities that could be exploited by cybercriminals. Additionally, utilizing a reputable security suite can provide real-time monitoring and threat detection, adding another layer of defense. Educating users about phishing attacks and safe browsing habits is equally important, as human error remains a significant vulnerability. Finally, encrypted connections via Virtual Private Networks (VPNs) safeguard data during transmission, ensuring privacy even on unsecured networks. Collectively, these measures create a thorough security framework.
Conclusion
To summarize, a strong password generator serves as a critical tool in safeguarding digital assets by producing complex, unique passwords that adhere to security protocols. The automated generation of passwords greatly reduces the risk of unauthorized access, while also alleviating the cognitive load associated with managing multiple credentials. Coupled with best practices in password management and supplementary security measures, the utilization of a password generator considerably enhances overall cybersecurity resilience against emerging threats.
0 notes
Text
DIY Smart Home Energy Monitor with ESP32 and Home Assistant
Introduction
Managing energy consumption is a great way to reduce electricity costs and contribute to environmental sustainability. With the help of IoT, you can monitor energy usage in real-time, right from your smartphone. In this guide, we’ll build a Smart Home Energy Monitor using an ESP32 microcontroller, current and voltage sensors (like the ACS712 or SCT-013), and the MQTT protocol for data transmission. This data will be accessible on a mobile app via Home Assistant, allowing you to keep track of energy usage and optimize it effectively.
Project Overview
Objectives
Monitor power consumption in real-time for home appliances.
Display energy usage on a mobile app using MQTT and Home Assistant.
Analyze data over time to make informed decisions about energy usage.
Key Components
ESP32 (or ESP8266) microcontroller: For reading sensor data and connecting to Wi-Fi.
Current Sensor (SCT-013 or ACS712): For measuring current drawn by appliances.
Voltage Sensor: Optional, but adds more accuracy if you want to measure precise power usage.
MQTT Protocol: To send data to Home Assistant for real-time monitoring.
Home Assistant: A home automation platform to display and analyze data.
Part 1: Setting Up the Components
1. ESP32 or ESP8266 Microcontroller
Choose either the ESP32 or ESP8266 microcontroller. The ESP32 has more features and is preferred, but either will work.
Connect the ESP32 to your computer using a USB cable to program it.
2. Current Sensor (SCT-013 or ACS712)
SCT-013 is a non-invasive sensor that clamps around a wire to measure the AC current flowing through it.
ACS712 is a current sensor that can measure both AC and DC current but requires direct connection to the wire, so exercise caution with high voltage.
Wiring for SCT-013
Connect the SCT-013 sensor’s output to an analog input pin on the ESP32.
If you’re using SCT-013 with ESP8266, you’ll need an analog-to-digital converter (ADC) module since the ESP8266 has only one analog input pin with limited resolution.
Wiring for ACS712
Connect the VCC pin to the 3.3V or 5V pin on the ESP32.
Connect the OUT pin to an analog input pin on the ESP32.
Connect the GND pin to the ground (GND) on the ESP32.
3. Voltage Sensor (Optional)
A voltage sensor can be added to measure the actual voltage if you want to calculate power more accurately.
Connect the sensor’s VCC to the 3.3V on ESP32, GND to ground, and OUT to an analog input.
Part 2: Coding the ESP32 for Data Acquisition and Transmission
1. Install the Required Libraries
Make sure you have the following libraries installed in your Arduino IDE:
ESP32 or ESP8266 board support (depending on your microcontroller)
PubSubClient library for MQTT communication
WiFi library for connecting to your Wi-Fi network
2. Set Up the Code
Here’s the code to:
Read values from the current sensor.
Calculate power consumption (voltage x current if you have a voltage sensor, or assume constant voltage).
Publish data to an MQTT broker.
#include <WiFi.h> #include <PubSubClient.h>
// Wi-Fi and MQTT Broker Settings const char* ssid = "YOUR_SSID"; const char* password = "YOUR_PASSWORD"; const char* mqtt_server = "YOUR_MQTT_BROKER_IP";
// MQTT topics const char* topicPower = "home/energy_monitor/power";
WiFiClient espClient; PubSubClient client(espClient);
// Sensor parameters const int sensorPin = 34; // Analog pin for sensor (ESP32) const float voltageCalibration = 230.0; // Voltage in volts (modify as per your region) const float sensorCalibration = 0.185; // Calibration constant for ACS712 sensor
void setup() { Serial.begin(115200); setup_wifi(); client.setServer(mqtt_server, 1883); }
void setup_wifi() { delay(10); Serial.println("Connecting to WiFi..."); WiFi.begin(ssid, password); while (WiFi.status() != WL_CONNECTED) { delay(500);
Serial.print("."); } Serial.println("Connected to WiFi."); }
void reconnect() { while (!client.connected()) { Serial.print("Connecting to MQTT..."); if (client.connect("ESP32Client")) { Serial.println("Connected."); } else { delay(5000); } } }
void loop() { if (!client.connected()) { reconnect(); } client.loop();
// Read sensor data int rawValue = analogRead(sensorPin); float current = rawValue * sensorCalibration; // Adjust based on sensor
// Calculate power float power = voltageCalibration * current; // Simple power calculation (P=VI)
// Publish data to MQTT String powerStr = String(power); client.publish(topicPower, powerStr.c_str()); Serial.print("Power: "); Serial.println(power); delay(2000); // Send data every 2 seconds }
3. Upload Code
Connect your ESP32 to your computer.
Select the correct board and port in the Arduino IDE.
Upload the code to the ESP32.
Part 3: Setting Up Home Assistant and MQTT Broker
1. Set Up MQTT Broker
If you don’t have an MQTT broker, you can use Mosquitto on your local network or use an online MQTT service like HiveMQ.
Install Mosquitto on a Raspberry Pi or a computer running Home Assistant.
Configure Mosquitto by setting a username and password for secure access.
2. Configure Home Assistant
In Home Assistant, you’ll add the MQTT integration to receive data from the ESP32.
Go to Settings > Integrations and search for MQTT.
Enter your MQTT broker details and save the configuration.
3. Add a Sensor in Home Assistant
In your Home Assistant configuration file (configuration.yaml), add the following entry to display power data:sensor: - platform: mqtt name: "Home Power Consumption" state_topic: "home/energy_monitor/power" unit_of_measurement: "W" value_template: "{{ value | float }}"
Restart Home Assistant to apply changes.
You should now see a Home Power Consumption sensor in your Home Assistant dashboard.
Part 4: Testing and Using the Energy Monitor
Power on your ESP32 and ensure it’s connected to Wi-Fi.
Open Home Assistant, where you should see the real-time data of power consumption.
Monitor the data over time and optimize energy usage based on the data.
Conclusion
With this DIY Smart Home Energy Monitor, you can track power usage across various appliances in your home. This project introduces core IoT concepts such as data acquisition, MQTT communication, and integration with Home Assistant. You can further expand this setup by adding more sensors or even automating appliances based on usage patterns.
#Tech4bizsolutions #SmartHome #EnergyMonitoring #ESP32Projects #HomeAssistant #IoTProjects #DIYElectronics #MQTTProtocol #SmartHomeAutomation #PowerConsumption #EnergyEfficiency #ESP8266Projects #IoTDevelopment #HomeAutomationIdeas #TechDIY #SustainableLiving
0 notes
Text
Guide to Retrieve the Secret Value Using AWS Secret Manager

App developers are hunting all possible means to find a secure way to store their data in the database or Redis. (Redis is an open-source in-memory Data Structure Store, used as a database and a caching layer or a message broker.) One of the challenging tasks with the database is the storage and retrieval, the process is hard to code. And AWS Secret Manager is a problem solver. The AWS Secret Manager focuses to keep your data in secret. The secrets may be your database credentials, passwords or third party API.
Let us walk you through the process of how to keep the Secret a secret using the AWS Secret Manager.
1.Log into your AWS account, search and select the Secret Manager. Afterwards, enter into the Secret Manager Console and click on the “Store a new secret”.
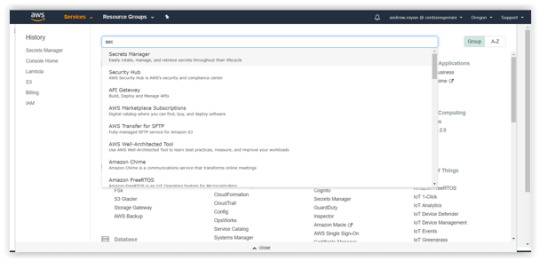
2. In the “Store a new secret” option, you will find the options to select a Secret type.
Credentials for RDS database
Credentials for Redshift Cluster
Credentials for Document database
Credentials for Other database
Other type of secrets
If you do not have a definite value, go with “Other type of secrets”. Then enter the appropriate key name and hit Next.
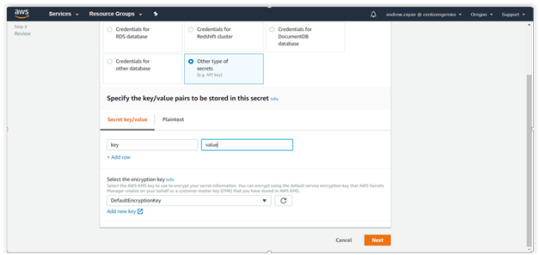
Specify the “Secret name and its description” in the particular fields and other options (optional). Just hit Next.
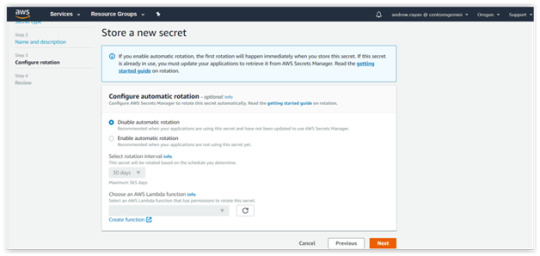
3. After completing Steps 1 and 2, you will be taken to the “Configure Automatic Rotation”. There is an available option to “Disable or Enable the automatic rotation” of the keys via lambda function. Select “Disable” and follow to the next level.
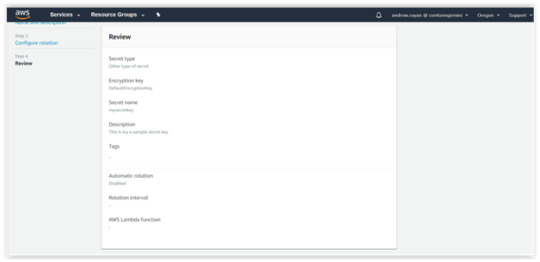
4. You can “Review”, your data in the previous steps and click “Store” button. Then, you’ll get the sample snippets of Java.
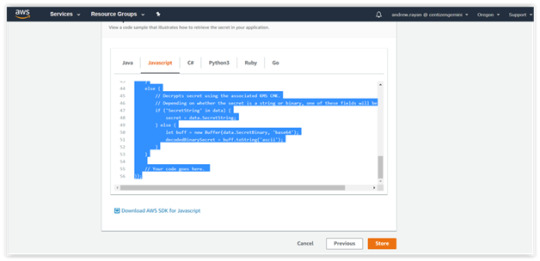
This is the generated Snippet code sample:</.h2
// Use this code snippet in your app.
// If you need more information about configurations or implementing the sample code, visit the AWS docs: // https://aws.amazon.com/developers/getting-started/nodejs/ // Load the AWS SDK var AWS = require(‘aws-sdk’), region = “us-west-2”, secretName = “mysecretkey”, secret, decodedBinarySecret; // Create a Secrets Manager client var client = new AWS.SecretsManager({ region: region }); // In this sample we only handle the specific exceptions for the ‘GetSecretValue’ API. // See https://docs.aws.amazon.com/secretsmanager/latest/apireference/API_GetSecretValue.html // We rethrow the exception by default. client.getSecretValue({SecretId: secretName}, function(err, data) { if (err) { if (err.code === ‘DecryptionFailureException’) // Secrets Manager can’t decrypt the protected secret text using the provided KMS key. // Deal with the exception here, and/or rethrow at your discretion. throw err; else if (err.code === ‘InternalServiceErrorException’) // An error occurred on the server side. // Deal with the exception here, and/or rethrow at your discretion. throw err; else if (err.code === ‘InvalidParameterException’) // You provided an invalid value for a parameter. // Deal with the exception here, and/or rethrow at your discretion. throw err; else if (err.code === ‘InvalidRequestException’) // You provided a parameter value that is not valid for the current state of the resource. // Deal with the exception here, and/or rethrow at your discretion. throw err; else if (err.code === ‘ResourceNotFoundException’) // We can’t find the resource that you asked for. // Deal with the exception here, and/or rethrow at your discretion. throw err; } else { // Decrypts secret using the associated KMS CMK. // Depending on whether the secret is a string or binary, one of these fields will be populated. if (‘SecretString’ in data) { secret = data.SecretString; } else { let buff = new Buffer(data.SecretBinary, ‘base64’); decodedBinarySecret = buff.toString(‘ascii’); } } // Your code goes here. });
Hope this helped you learn a way to secure your content.
0 notes
Text
Looking for an effective way to manage computer usage at home or in the office?
Here’s a step-by-step guide on how to set up and use SentryPC effectively:

>>>>>>Click here to get access
Step 1: Sign Up for SentryPC
Visit the SentryPC website and choose a subscription plan that best fits your needs. They offer various options depending on the number of devices and features you require.
Create an account by entering your email and setting up a password.
Step 2: Download and Install SentryPC
After signing up, download the SentryPC software to the devices you want to monitor. SentryPC supports Windows and Mac operating systems.
Follow the installation prompts to complete the setup on each device.
Step 3: Configure User Accounts
Once installed, log in to your SentryPC dashboard using your account credentials.
Create user accounts for each individual you want to monitor. You can set different permissions and restrictions for each user based on their needs.
Step 4: Set Monitoring Parameters
Go to the settings for each user account to configure what activities you want to monitor. This includes:
Tracking website visits
Monitoring application usage
Setting time limits for computer usage
Blocking specific websites or applications
Step 5: Customize Reporting Options
Select how often you want to receive reports and what details you want included. SentryPC allows you to choose between real-time monitoring or scheduled reports.
Set alerts for specific activities, such as attempts to access restricted content.
Step 6: Use Remote Access Features
Familiarize yourself with the remote access functionality. This allows you to make adjustments to settings or view reports from any device, ensuring you can manage activities on the go.
Step 7: Monitor Activity and Generate Reports
Regularly check the SentryPC dashboard to monitor user activity. The reports provide valuable insights into how each user interacts with the computer.
Use this data to address any concerns or to have discussions with users about their online behavior.
Step 8: Adjust Settings as Needed
Based on the monitoring reports, adjust restrictions, time limits, or permissions as necessary. You can easily update settings in the dashboard to reflect any changes in your requirements.
Step 9: Review and Analyze
Periodically review the overall activity reports to assess productivity and ensure that users are adhering to set guidelines.
Use the insights gained to foster a better environment, whether for family, students, or employees.
Step 10: Stay Informed
Keep an eye on SentryPC updates and new features. Regularly check their website or subscribe to newsletters to learn about improvements and tips for using the software effectively.
By following these steps, you can effectively set up and utilize SentryPC to monitor and manage computer usage, ensuring a safe and productive environment.
0 notes
Text
How to buy TRB
Purchasing TRB (the token of The Ruler Protocol) usually needs to be done on a cryptocurrency exchange that supports TRB trading. Here is a detailed step-by-step guide to buying TRB:
I. Preparation
Research TRB
Before deciding to buy TRB, learn more about TRB's background, purpose, market potential, and potential risks. This can be done by consulting TRB's official website, white paper, social media, forums, and news articles.
Choose a trading platform
Choose a reputable, highly secure cryptocurrency exchange that supports TRB trading. Common exchanges that support TRB trading include Binance, Huobi, OKEx, Gate.io, etc.
When choosing an exchange, consider factors such as its transaction fees, transaction speed, user-friendly interface, and whether it supports users in your region.
Register an account
Go to the official website of the selected exchange and follow the prompts to complete the registration process. This usually includes providing personal information, setting a password, and identity verification.
II. Recharge funds
Log in to the exchange account
Log in to the exchange account using your username and password.
Deposit funds
Select the deposit option. There are usually multiple deposit methods to choose from, such as bank transfer, credit card payment, or cryptocurrency transfer. Choose the deposit method that best suits your needs and the support of the exchange. Enter the deposit amount and follow the instructions of the exchange to complete the deposit process. Note that it may take some time to complete the deposit, depending on the deposit method you choose and the processing speed of the exchange.
III. Buy TRB
Browse trading pairs
On the exchange's trading page, browse the available trading pairs. For TRB, common trading pairs include TRB/USDT, TRB/BTC, etc.
Set trading parameters
Select the TRB trading pair you want to buy, and set the trading parameters such as buying price, buying quantity, etc. according to your purchase needs and market expectations.
Place an order
According to the instructions on the exchange interface, enter the buy and sell quantity and the transaction price, and submit the transaction order after confirmation. Please note that the exchange may also charge a certain transaction fee.
Monitor your trade
Once your order is placed successfully, you can check the status of the trade on the exchange's trading page or in your wallet's transaction history. If your trade is successfully completed, you will see your TRB balance increase.
IV. Storing TRB
Choose a wallet
To safely store your TRB, you need to choose a suitable wallet. You can choose to use an online wallet provided by the exchange, or choose an offline wallet (such as a hardware wallet or software wallet) where you control your private keys.
Back up your private key
No matter which wallet you choose, make sure to back up your private key or mnemonic phrase. The private key is the only credential to access your cryptocurrency, and if it is lost or leaked, your funds may be lost.
V. Precautions
Security
Always pay attention to security when purchasing and storing TRB. Use strong passwords to protect your exchange account and wallet, and change your passwords regularly. Avoid sensitive operations on public Wi-Fi connections.
Market volatility
The cryptocurrency market is volatile, so be careful to consider market risks when purchasing TRB. It is recommended to conduct sufficient market analysis and risk assessment before purchasing.
Comply with laws and regulations
When purchasing TRB, comply with the laws and regulations of your region. Some regions may have specific restrictions or requirements for cryptocurrency transactions.
In summary, purchasing TRB requires choosing a suitable trading platform, recharging funds, setting trading parameters and placing orders. At the same time, pay attention to the safe storage of TRB and comply with relevant laws and regulations.
0 notes