#plugin oauth
Explore tagged Tumblr posts
Text
Advanced Techniques in Full-Stack Development

Certainly, let's delve deeper into more advanced techniques and concepts in full-stack development:
1. Server-Side Rendering (SSR) and Static Site Generation (SSG):
SSR: Rendering web pages on the server side to improve performance and SEO by delivering fully rendered pages to the client.
SSG: Generating static HTML files at build time, enhancing speed, and reducing the server load.
2. WebAssembly:
WebAssembly (Wasm): A binary instruction format for a stack-based virtual machine. It allows high-performance execution of code on web browsers, enabling languages like C, C++, and Rust to run in web applications.
3. Progressive Web Apps (PWAs) Enhancements:
Background Sync: Allowing PWAs to sync data in the background even when the app is closed.
Web Push Notifications: Implementing push notifications to engage users even when they are not actively using the application.
4. State Management:
Redux and MobX: Advanced state management libraries in React applications for managing complex application states efficiently.
Reactive Programming: Utilizing RxJS or other reactive programming libraries to handle asynchronous data streams and events in real-time applications.
5. WebSockets and WebRTC:
WebSockets: Enabling real-time, bidirectional communication between clients and servers for applications requiring constant data updates.
WebRTC: Facilitating real-time communication, such as video chat, directly between web browsers without the need for plugins or additional software.
6. Caching Strategies:
Content Delivery Networks (CDN): Leveraging CDNs to cache and distribute content globally, improving website loading speeds for users worldwide.
Service Workers: Using service workers to cache assets and data, providing offline access and improving performance for returning visitors.
7. GraphQL Subscriptions:
GraphQL Subscriptions: Enabling real-time updates in GraphQL APIs by allowing clients to subscribe to specific events and receive push notifications when data changes.
8. Authentication and Authorization:
OAuth 2.0 and OpenID Connect: Implementing secure authentication and authorization protocols for user login and access control.
JSON Web Tokens (JWT): Utilizing JWTs to securely transmit information between parties, ensuring data integrity and authenticity.
9. Content Management Systems (CMS) Integration:
Headless CMS: Integrating headless CMS like Contentful or Strapi, allowing content creators to manage content independently from the application's front end.
10. Automated Performance Optimization:
Lighthouse and Web Vitals: Utilizing tools like Lighthouse and Google's Web Vitals to measure and optimize web performance, focusing on key user-centric metrics like loading speed and interactivity.
11. Machine Learning and AI Integration:
TensorFlow.js and ONNX.js: Integrating machine learning models directly into web applications for tasks like image recognition, language processing, and recommendation systems.
12. Cross-Platform Development with Electron:
Electron: Building cross-platform desktop applications using web technologies (HTML, CSS, JavaScript), allowing developers to create desktop apps for Windows, macOS, and Linux.
13. Advanced Database Techniques:
Database Sharding: Implementing database sharding techniques to distribute large databases across multiple servers, improving scalability and performance.
Full-Text Search and Indexing: Implementing full-text search capabilities and optimized indexing for efficient searching and data retrieval.
14. Chaos Engineering:
Chaos Engineering: Introducing controlled experiments to identify weaknesses and potential failures in the system, ensuring the application's resilience and reliability.
15. Serverless Architectures with AWS Lambda or Azure Functions:
Serverless Architectures: Building applications as a collection of small, single-purpose functions that run in a serverless environment, providing automatic scaling and cost efficiency.
16. Data Pipelines and ETL (Extract, Transform, Load) Processes:
Data Pipelines: Creating automated data pipelines for processing and transforming large volumes of data, integrating various data sources and ensuring data consistency.
17. Responsive Design and Accessibility:
Responsive Design: Implementing advanced responsive design techniques for seamless user experiences across a variety of devices and screen sizes.
Accessibility: Ensuring web applications are accessible to all users, including those with disabilities, by following WCAG guidelines and ARIA practices.
full stack development training in Pune
2 notes
·
View notes
Text
PixelPhoto Nulled Script 1.6.0

PixelPhoto Nulled Script – The Ultimate Photo Sharing Experience Looking for a powerful image-sharing platform that doesn’t break the bank? PixelPhoto Nulled Script is your ideal solution. Whether you’re an aspiring photographer, social media influencer, or tech-savvy entrepreneur, this premium social network platform gives you the freedom to create your own Instagram-style website—completely free. Say goodbye to costly subscriptions and hello to limitless customization with this nulled gem. What is PixelPhoto Nulled Script? The PixelPhoto Nulled Script is a high-performance image-sharing and social networking script developed to rival platforms like Instagram and Flickr. It’s packed with advanced features, a responsive design, and an intuitive user interface. Thanks to the nulled version, you can enjoy full access to all premium tools and functionalities—without spending a dime. Technical Specifications Framework: Laravel 8.x Database: MySQL 5.x or later Server Requirements: PHP 7.4 or higher, OpenSSL, cURL, Mbstring, PDO, and Fileinfo extensions Compatibility: Fully responsive across mobile, tablet, and desktop Languages: Multilingual support with RTL compatibility Outstanding Features & Benefits Customizable UI: Tweak the layout, colors, and branding to match your vision. Monetization Tools: Built-in options for ads, subscriptions, and premium memberships. High-Speed Performance: Fast-loading pages optimized for SEO and user retention. Multi-Media Support: Seamlessly upload and manage images, GIFs, and short videos. Secure Login & Registration: OAuth, email, and two-step authentication available. How PixelPhoto Nulled Script Benefits You One of the biggest advantages of using the PixelPhoto Nulled Script is freedom—freedom to explore, customize, and build your online community without financial barriers. You get access to premium capabilities usually locked behind a paywall, which makes it ideal for startups and individuals who want to launch fast and scale smart. Best of all, it works flawlessly alongside popular plugins like Slider Revolution NULLED—a perfect match for crafting visually stunning image galleries and carousels. Real-World Use Cases Photography Portfolios: Showcase your best shots in a professional, dynamic layout. Private Communities: Build niche social networks around hobbies, brands, or causes. Marketing & Promotions: Share branded content, run campaigns, and interact with followers. Online Galleries: Host and organize exhibitions, events, or digital art showcases. Installation Guide Installing the PixelPhoto Nulled Script is straightforward. Here’s a step-by-step overview to get you started: Download the latest version of the script (nulled) from our site. Upload all files to your web server using FTP or File Manager. Create a new MySQL database and import the SQL file included. Open config.php and input your database credentials. Follow the installation wizard in your browser to finalize setup. FAQs – Frequently Asked Questions Is the PixelPhoto Nulled Script safe to use? Yes, our version is pre-tested and malware-free. However, always use a secure hosting environment and regular backups for optimal safety. Can I monetize my platform with this script? Absolutely. The script includes built-in monetization features like ads, subscriptions, and sponsored posts to help you earn from your community. Does it support plugins? Yes, it supports a variety of third-party tools and integrates well with popular plugins such as wpbakery nulled to help you design your pages with ease. Can I rebrand the platform? Yes! You can customize every element—from logos to layouts—to reflect your unique identity. Start Your Photo Sharing Journey Today Why wait to create the next big thing in image sharing? With the PixelPhoto , you're only a few clicks away from building your own Instagram-like platform—fully free and loaded with premium features. Download it today and bring your creative vision to life.
0 notes
Text
Facing Compatibility Issues During Microsoft 365 Migration? Here's What You Need to Know
Microsoft 365 migration is never just a click-and-go process. Behind every successful move is a thorough compatibility check between systems, services, and user environments. If not done right, compatibility issues surface and disrupt everything from mailbox access to user authentication. These issues are more common than they should be, and they can derail your entire migration strategy.
Here’s a practical look at what causes these compatibility breakdowns and what steps you need to take to prevent them.

Legacy Systems That Don’t Meet Microsoft 365 Standards
Many organizations continue to operate with outdated infrastructure. Systems like Windows 7, older Outlook versions, or Exchange 2010 lack the protocols and security standards required by Microsoft 365. Without modernization, they create roadblocks during migration. For instance, a system that doesn’t support TLS 1.2 or Modern Authentication will fail to connect with Microsoft 365 services.
To prevent this, perform a full compatibility assessment of your OS, Exchange servers, and Outlook clients. Upgrade the environment or establish a hybrid setup that ensures continuity while you transition users.
Authentication Failures Due to Identity Conflicts
Identity and access management is a critical pillar in Microsoft 365. If your existing setup includes outdated AD FS configurations or incomplete Azure AD synchronization, users will face login failures, broken SSO, and token-related issues. Compatibility mismatches between your on-prem directory and cloud directory often go unnoticed until users can’t sign in after cutover.
Define your identity model well in advance. Whether you choose cloud-only, hybrid, or federated, validate it with pilot users. Ensure directory sync, UPN alignment, and conditional access policies are correctly applied.
Unsupported Add-ins and Custom Applications
Custom Outlook add-ins, CRM connectors, or VBA-based automations are often built around legacy environments. These integrations may fail in Microsoft 365 because they rely on outdated APIs or local server paths. Post-migration, users report missing features or broken workflows, which is not a mailbox problem but a compatibility one.
Catalog all active plugins and applications. Check vendor documentation for Microsoft 365 support. Transition to updated versions or re-develop legacy tools using supported APIs like Microsoft Graph.
PST and Archive Data That Can’t Be Imported
PST files from end-user systems or public folder archives frequently carry hidden corruption, non-compliant data formats, or unusually large attachments. These can cause import failures or lead to incomplete data availability after migration.
To avoid surprises, pre-scan PST files using tools that verify integrity. Break large PSTs into manageable sizes. Use modern utilities that support direct PST import with accurate folder mapping and duplicate prevention.
Email Clients and Mobile App Incompatibility
Not all email clients are built to support Microsoft 365. Legacy Android apps, IMAP clients, or older iOS Mail apps often lack support for OAuth or Modern Authentication. Once migrated, users might encounter repeated login prompts or full access loss.
Standardize supported apps in advance. Recommend and configure Outlook for mobile. Use device management policies to enforce security compliance. Disable access for non-compliant clients using conditional access in Microsoft 365 admin settings.
Loss of Mailbox Permissions and Calendar Access
Access issues post-migration are common when shared mailbox permissions or calendar delegation rights aren’t migrated properly. Users may suddenly lose visibility into shared mailboxes or receive errors when trying to access team calendars.
Before migrating, document all mailbox and folder-level permissions. After migration, reapply them using PowerShell scripts or a tool that automates permission preservation. Always validate shared access functionality with test users before expanding the migration to all users.
Conclusion
Compatibility issues don’t happen randomly during Microsoft 365 migrations. They are the result of incomplete planning or assumptions that legacy systems will integrate seamlessly with modern cloud environments. The only way to mitigate them is through comprehensive discovery, pre-validation, and the right migration tooling.
If you want to reduce risk and accelerate your migration with minimal disruption, consider using EdbMails Office 365 migration tool. It simplifies complex moves, retains all mailbox properties and permissions, supports hybrid and tenant-to-tenant scenarios, and ensures seamless migration across environments. It’s a trusted choice for IT teams who need control, flexibility, and reliability.
Additional links:
👉 Export Microsoft 365 Mailbox to PST
👉 Move public folders to office 365
#edbmails#office 365 migration software#incremental migration#office 365 migration#artificial intelligence#coding
0 notes
Text
Unlocking Seamless Integrations: A Comprehensive Guide to the 'Contact Form to Any API' WordPress Plugin
In today's digital landscape, integrating your website's contact forms with various APIs is crucial for streamlined operations and enhanced user experiences. The Contact Form to Any API WordPress plugin stands out as a versatile tool, enabling seamless connections between your contact forms and a multitude of third-party services. This comprehensive guide delves into the features, benefits, and practical applications of this powerful plugin.

Understanding the Need for API Integration
Before exploring the plugin's capabilities, it's essential to grasp the significance of API integrations:
Enhanced Efficiency: Automating data transfer between your website and external platforms reduces manual tasks.
Improved Data Accuracy: Direct integrations minimize errors associated with manual data entry.
Real-Time Updates: Immediate data synchronization ensures up-to-date information across platforms.
Scalability: As your business grows, integrated systems can handle increased data flow without additional overhead.
Introducing 'Contact Form to Any API'
Developed by IT Path Solutions, 'Contact Form to Any API' is designed to bridge the gap between your WordPress contact forms and external APIs. Whether you're using Contact Form 7 or WPForms, this plugin facilitates the transmission of form data to various services, including CRMs, marketing platforms, and custom APIs.
Key Features
1. Broad API Compatibility
Supports Over 150 APIs: Seamlessly connect with platforms like Mailchimp, HubSpot, Zapier, Odoo CRM, and more.
Custom API Integration: Configure connections with virtually any REST API, providing unparalleled flexibility.
2. Flexible Data Transmission
Multiple HTTP Methods: Choose between POST and GET requests based on your API's requirements.
JSON Formatting: Send data in simple or nested JSON structures, accommodating complex API schemas.
Header Customization: Set custom headers, including Authorization tokens, to meet specific API authentication needs.
3. File Handling Capabilities
File Upload Support: Enable users to upload files through your forms.
Base64 Encoding: Automatically convert uploaded files to Base64 format for API compatibility.
4. Data Management and Export
Database Storage: Store form submissions within your WordPress database for easy access.
Export Options: Download submission data in CSV, Excel, or PDF formats for reporting and analysis.
5. Conditional Data Sending
Timing Control: Decide whether to send data to the API before or after the form's email notification is dispatched.
6. Authentication Support
Multiple Authentication Methods: Utilize Basic Auth, Bearer Tokens, or custom headers to authenticate API requests.
Pro Version Enhancements
Upgrading to the Pro version unlocks additional features:
Multi-API Support: Send form data to multiple APIs simultaneously.
Advanced JSON Structures: Handle multi-level JSON formats for complex integrations.
Priority Support: Receive expedited assistance from the development team.
OAuth 2.0 and JWT Integration: Facilitate secure connections with APIs requiring advanced authentication protocols.
Real-World Applications
The versatility of 'Contact Form to Any API' opens doors to numerous practical applications:
CRM Integration: Automatically add new leads to your CRM system upon form submission.
Email Marketing: Subscribe users to your mailing list in platforms like Mailchimp or Sendinblue.
Support Ticketing: Create support tickets in systems like Zendesk or Freshdesk directly from contact forms.
Project Management: Generate tasks in tools like Trello or Asana based on form inputs.
User Testimonials
The plugin has garnered positive feedback from the WordPress community:
"Does exactly what is needed – connects your contact form to API. Works great out of the box, and amazing support." — Olay
"I used the free plugin for a while already, recently stepped over to the pro and I must say the pro and agency version come with amazing new features and the support is quick and always there to help you with any questions!" — Samuellegrand
Getting Started: Installation and Configuration
Step 1: Installation
Navigate to your WordPress dashboard.
Go to Plugins > Add New.
Search for "Contact Form to Any API."
Click "Install Now" and then "Activate."
Step 2: Configuration
Access the plugin settings via the WordPress dashboard.
Choose the form (Contact Form 7 or WPForms) you wish to integrate.
Enter the API endpoint URL.
Configure the request method (POST or GET).
Set up headers and authentication details as required.
Map form fields to the corresponding API parameters.
Save your settings and test the integration.
Best Practices for Optimal Integration
Test Thoroughly: Use tools like Postman to test API endpoints before full integration.
Secure Sensitive Data: Ensure that authentication tokens and sensitive information are stored securely.
Monitor Logs: Regularly check logs for any errors or issues in data transmission.
Stay Updated: Keep the plugin and WordPress core updated to benefit from the latest features and security patches.
Conclusion
'Contact Form to Any API' stands as a robust solution for WordPress users seeking seamless integration between their contact forms and external services. Its flexibility, extensive feature set, and user-friendly interface make it an invaluable tool for enhancing website functionality and streamlining workflows.
Whether you're aiming to automate lead generation, enhance customer support, or synchronize data across platforms, this plugin offers the capabilities to achieve your goals efficiently.
0 notes
Text
OpenShift vs Kubernetes: Key Differences Explained
Kubernetes has become the de facto standard for container orchestration, enabling organizations to manage and scale containerized applications efficiently. However, OpenShift, built on top of Kubernetes, offers additional features that streamline development and deployment. While they share core functionalities, they have distinct differences that impact their usability. In this blog, we explore the key differences between OpenShift and Kubernetes.
1. Core Overview
Kubernetes:
Kubernetes is an open-source container orchestration platform that automates the deployment, scaling, and operation of application containers. It provides the building blocks for containerized workloads but requires additional tools for complete enterprise-level functionality.
OpenShift:
OpenShift is a Kubernetes-based container platform developed by Red Hat. It provides additional features such as a built-in CI/CD pipeline, enhanced security, and developer-friendly tools to simplify Kubernetes management.
2. Installation & Setup
Kubernetes:
Requires manual installation and configuration.
Cluster setup involves configuring multiple components such as kube-apiserver, kube-controller-manager, kube-scheduler, and networking.
Offers flexibility but requires expertise to manage.
OpenShift:
Provides an easier installation process with automated scripts.
Includes a fully integrated web console for management.
Requires Red Hat OpenShift subscriptions for enterprise-grade support.
3. Security & Authentication
Kubernetes:
Security policies and authentication need to be manually configured.
Role-Based Access Control (RBAC) is available but requires additional setup.
OpenShift:
Comes with built-in security features.
Uses Security Context Constraints (SCCs) for enhanced security.
Integrated authentication mechanisms, including OAuth and LDAP support.
4. Networking
Kubernetes:
Uses third-party plugins (e.g., Calico, Flannel, Cilium) for networking.
Network policies must be configured separately.
OpenShift:
Uses Open vSwitch-based SDN by default.
Provides automatic service discovery and routing.
Built-in router and HAProxy-based load balancing.
5. Development & CI/CD Integration
Kubernetes:
Requires third-party tools for CI/CD (e.g., Jenkins, ArgoCD, Tekton).
Developers must integrate CI/CD pipelines manually.
OpenShift:
Comes with built-in CI/CD capabilities via OpenShift Pipelines.
Source-to-Image (S2I) feature allows developers to build images directly from source code.
Supports GitOps methodologies out of the box.
6. User Interface & Management
Kubernetes:
Managed through the command line (kubectl) or third-party UI tools (e.g., Lens, Rancher).
No built-in dashboard; requires separate installation.
OpenShift:
Includes a built-in web console for easier management.
Provides graphical interfaces for monitoring applications, logs, and metrics.
7. Enterprise Support & Cost
Kubernetes:
Open-source and free to use.
Requires skilled teams to manage and maintain infrastructure.
Support is available from third-party providers.
OpenShift:
Requires a Red Hat subscription for enterprise support.
Offers enterprise-grade stability, support, and compliance features.
Managed OpenShift offerings are available via cloud providers (AWS, Azure, GCP).
Conclusion
Both OpenShift and Kubernetes serve as powerful container orchestration platforms. Kubernetes is highly flexible and widely adopted, but it demands expertise for setup and management. OpenShift, on the other hand, simplifies the experience with built-in security, networking, and developer tools, making it a strong choice for enterprises looking for a robust, supported Kubernetes distribution.
Choosing between them depends on your organization's needs: if you seek flexibility and open-source freedom, Kubernetes is ideal; if you prefer an enterprise-ready solution with out-of-the-box tools, OpenShift is the way to go.
For more details click www.hawkstack.com
0 notes
Text
List of Sharetribe Plugins Developed by Journeyhorizon
Journeyhorizon has developed a variety of Sharetribe plugins designed to scale marketplaces effectively. Here’s a closer look at nine key plugins that can help your marketplace grow:
Wishlist Plugin
The Wishlist Plugin allows users to save their favorite products for later, improving user engagement and encouraging repeat visits to the marketplace. It also provides opportunities for marketplace owners to implement personalized marketing strategies, such as sending reminders or promotions to users with saved items.
Bulk Upload Plugin
When dealing with thousands of product listings, uploading products manually is inefficient. The Bulk Upload Plugin simplifies this process by allowing vendors to upload multiple product listings at once through CSV files. This plugin is particularly useful for large-scale marketplaces, where product catalogs must be consistently updated with minimal effort.
Single Vendor Shopping Cart Plugin
Our Single Vendor Shopping Cart plugin is engineered to optimize the shopping experience and simplify transaction processes on your marketplace. By implementing this feature, users can choose multiple products from a single vendor and process them in a single transaction. This streamlined approach addresses the limitations of the current system, where users can only select one product per payment. Key benefits:
Multi-user Accounts Plugin
Our Multi-User Accounts plugin is designed to enhance collaboration and streamline operations on your marketplace by allowing both buyers and providers to delegate permissions and manage their accounts with team members. This plugin enables teams to work more efficiently and effectively, improve overall productivity and marketplace success.
Delete user Account Plugin
Our Delete User Account plugin provides a secure and efficient way to manage user data, ensuring your marketplace remains compliant with data protection regulations. This plugin allows you to handle account deletions seamlessly, safeguarding user privacy and enhancing trust in your platform.
Secure Data Deletion: Ensure that all user data is securely and completely removed from your system when an account is deleted, protecting sensitive information and maintaining user privacy.
Regulatory Compliance: Meet legal requirements and data protection regulations, such as GDPR and CCPA, by providing a robust mechanism for users to request and complete account deletions.
Enhanced Trust and Reputation: Providing a clear and effective way for users to delete their accounts demonstrates your commitment to data privacy, enhancing your marketplace’s reputation and building user trust.
Seamless Integration: The Delete User Account feature integrates smoothly with your existing marketplace infrastructure, ensuring a hassle-free implementation and operation.
Auto Menu Plugin
With our Auto Menu plugin, managing your marketplace just got easier! Now, you can automatically organize large product categories into smaller, more user-friendly subcategories. This helps your users navigate and find products quickly and effortlessly.
Social Login Plugin
Social Login Plugin enhances your marketplace's user experience with quick and easy signup/ login using your social accounts: Google, X, LinkedIn and Apple ID.
Enhanced User Experience: Simplify the registration and login process by allowing users to sign in with their social media accounts: Google, X, LinkedIn and Apple ID.
Secure Authentication: Leverage OAuth protocols to ensure secure authentication, protecting user data.
Increased Conversion Rates: By streamlining the sign-up process, you can reduce drop-offs and increase the number of registered users on your marketplace.
Quick and Easy Integration: Our Social Login plugin seamlessly integrates with your existing Sharetribe marketplace.
Event Services
Our Event Services is designed to help you automate integrations and tasks on your marketplace. Our plugin maximizes efficiency and streamline your marketplace operations, making it easier to manage and grow your business.
Automated Seller Rating Updates: Automate the calculation and update of seller ratings, ensuring a seamless experience for buyers and sellers alike.
Real-Time Inventory Management: Automatically update stock quantities for new and used products.
Transaction Management: Handle everything from electronic funds transfers to updating transaction statuses.
Seamless CRM and Email Integration: Effortlessly integrate new users into your CRM or email campaigns.
Biometric Login Plugin
Our Biometric Login plugin is designed to revolutionize the way users access your marketplace, providing a secure and seamless authentication process without the need for passwords. Supporting Fingerprint, Touch ID, and Face ID, this plugin ensures that users can quickly and securely log in using their preferred biometric method.
0 notes
Text
WP Mail SMTP Pro v4.1.1 Plugin
https://themesfores.com/product/wp-mail-smtp-pro-plugin/ WP Mail SMTP Pro Plugin v4.1.1 Making Email Deliverability Easy for WordPress The Most Popular WordPress SMTP and PHP Mailer Plugin Fix Your WordPress Email Problems, Once and For All You're not alone if you’re having issues with WordPress not sending emails. With the rise of aggressive spam filtering, reaching the inbox is tough unless your emails are configured correctly. Once you’ve switched from the default WordPress email settings over to WP Mail SMTP, your email deliverability issues will be solved for good. Note: If required, use any username/key to activate. WP Mail SMTP Pro WP Mail SMTP Pro Features Allow our experts to install and configure WP Mail SMTP for you. Keep track of every email sent from your WordPress site. Control which email notifications your WordPress site sends. Connect with SMTP.com, which has been delivering emails for over 20 years. Harness the power of AWS with our Amazon SES integration. Use your Zoho Mail account to reliably send all WordPress emails. Connect with your Office 365 account with our Microsoft mailer. Our Microsoft mailer also supports other services, including Outlook.com. Uses OAuth to authenticate your account, keeping your login info secure. Please note that any digital products on this website do not contain malicious code, viruses, or advertising. https://themesfores.com/product/wp-mail-smtp-pro-plugin/ #MailPlugins #WordpressPlugins
0 notes
Text
[solved] How can you share formatted links on Discord?
[solved] How can you share formatted links on Discord?
In Flutter, you can share formatted links on Discord by using the Discord share API and the url_launcher plugin. First, you will need to add the url_launcher package to your pubspec.yaml file and run flutter pub get. This package allows you to launch a URL in the default browser on the user’s device. Next, you will need to get the OAuth token for the user’s Discord account. This token allows your…
View On WordPress
0 notes
Text
Node.js Security Best Practices

Quick summary: This article presents guidelines for Node.js developers to follow to secure their applications against potential vulnerabilities arising from the use of third-party tools. It complies with essential guidelines, which we will refer to as Node.js security best practices, to ensure the security of Node.js applications.
What is Nodejs?
Node.js is a runtime environment that enables developers to use JavaScript beyond web browsers (or the front end) using various frameworks. It runs on Chrome’s V8 engine, allowing JavaScript developers to apply their skills to back-end development using the same language.
What is Nodejs Security?
While Nodejs is secure itself, it relies on open-source packages as in the fast-paced world, companies and developers do not want to invest their in reinventing the wheel. The packages make development easy and fast. However, this convenience can also introduce vulnerabilities in the application.
NPM, an open-source platform containing over two million packages, serves as a valuable resource by providing millions of packages to JavaScript developers. On the one hand, it makes it easy to use packages. On the other hand, it may pose potential risks.
Node.js developers heavily depend on open-source third-party packages.
In 2021, 77 percent of respondents from the United States report using open source to modernize their IT infrastructure, a report from Statista shows.
Despite the fact that over 78% of organizations make use of open-source projects, only about 40% of organizations use formal security rating tools to assess the security of these packages, while only about 27% of open-source projects are audited on a regular basis, a report reveals.
Like others, Nodejs applications are vulnerable to security breaches. Therefore, it becomes imperative to take the necessary steps to enforce strong security measures.
This article is a compilation of tips and advice from experts on how to secure Node.js applications. However, if you need technical assistance to enforce strong security measures on your existing Nodejs app, you can check out our Nodejs development services. Our team of professional IT experts will thoroughly assess your application for security vulnerabilities.
Best Practices for Nodejs Security
1. Enable Strong Authentication Method
Strong authentication is all about implementing the latest security measures to safeguard sensitive pieces of information. As you know, data breaches are no longer a rarity. They are a daily occurrence, and even the biggest tech companies are not immune. In recent years, Google, Twitter, and other big-name companies have all experienced data breaches that led to them redefining their authentication mechanism. Here are a few methods to be considered:
Limit login attempts in a fixed period of time.
Enables mandatory two-factor authentication to access sensitive data and services.
Enable more than a basic authentication — choose standard authentication methods like OAuth, OpenID, etc.
Implement strong password policies for user management and operations.
2. Make Use of Security-related plugins
These tools help you identify security weaknesses such as unsafe RegEx, unsafe use of eval(), use of non-literal filenames, etc., in your node applications when you write code. Overall, they can help detect these security flaws easily.
Eslint and Tslint are well-known code analytics tools for JavaScript and TypeScript projects for security checks in Node applications.
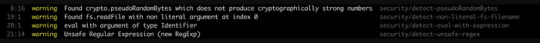
3. Limit concurrent requests
Limiting concurrent requests helps prevent Nodejs applications from being unresponsive due to overwhelming requests at the same time. By using a middleware or balancer, you can limit the number of requests. Ngnix is a widely used service for load balancing; however, you can also make use of middleware express-rate-limiter or rate-limiter-flexible package.
4. Avoid blocking the Event Loop
Nodejs includes EventLoop to run JavaScript code and Worker Pool for intensive tasks, which makes it a scalable platform that can handle too many requests. All incoming requests and outgoing responses flow through the Event Loop.
Node.js leverages V8 (JavaScript engine) for code executions, which is fairly fast for many common operations. However, if callbacks have large complexities or regexp and JSON operations occur in your program, it can lead to Event Loop blocking.
The common issues that may trigger Event Loop blocking are vulnerable regular expressions. Follow the below tips to avoid Event Loop blocking.
Use asynchronous operation whenever possible. Node can fairly handle asynchronous I/O operations.
Offload the CPU-intensive tasks to prevent blocking.
Complex regular expressions can lead to catastrophic backtracking; therefore, keep your regular expressions simple.
Use promises and async/await
As described above, middleware can help your performance of various operations efficiency; they can also lead to blocking. Don’t use unnecessary middleware.
Reduce the complexity of the callbacks.
Read more at https://www.brilworks.com/blog/node-js-security-best-practices/
0 notes
Text
Fluttering Ahead: Unveiling the Fort Knox of Data Security Practices for 2023
Introduction:
As the world of mobile app development hurtles forward, the need for robust data security has never been more critical. Flutter, with its cross-platform prowess, is at the forefront of this revolution. In this blog post, we'll delve into the realm of data security and unveil the best practices for ensuring your Flutter applications are not just cutting-edge in functionality but also impervious fortresses when it comes to safeguarding user data in 2023.

Encryption Excellence: Guarding Your Data Fortresses
The first line of defense in data security in Flutter provides a robust arsenal for developers. From securing sensitive data during transmission with TLS/SSL to implementing strong encryption algorithms for data storage, make encryption a non-negotiable part of your Flutter app's security strategy.
Secure Authentication: The Gateway to Trust
Authentication is the gateway to your app's treasure trove of data. Employ secure authentication protocols like OAuth 2.0 or OpenID Connect to ensure that only authorized users gain access. For an extra layer of security, consider implementing multi-factor authentication (MFA) to fortify the gates against unauthorized access attempts.
Token Management: A Balancing Act
Tokens are the keys to the kingdom, and managing them effectively is paramount. Regularly rotate and refresh access tokens, use short-lived tokens, and implement token blacklisting to mitigate the risks associated with compromised or stolen tokens. Token management is the tightrope walk between accessibility and security.
Secure Backend Communication: Fortify the Supply Chain
Your Flutter app's interaction with the backend is the lifeline of functionality. Secure this communication by using HTTPS, validating SSL certificates, and employing secure communication protocols. Regularly audit and update the backend APIs to patch vulnerabilities and ensure a secure supply chain for your data.
Secure Local Storage: Guarding the Vaults on the Device
Mobile devices are treasure chests of personal information. When storing data locally on a device, use secure storage mechanisms provided by Flutter. Avoid storing sensitive information in plain text and consider using secure storage plugins that encrypt data at rest. Treat the device as an extension of your data center and secure it accordingly.
Regular Security Audits: The Guardian's Watchful Eye
Security is an ongoing battle, and regular audits are the watchful eye that ensures your fortress remains impregnable. Conduct security assessments, code reviews, and penetration testing to identify and eliminate potential vulnerabilities. Stay one step ahead by adopting the mindset that security is not a one-time event but an ongoing commitment.
Conclusion:
As Flutter continues to empower developers with its versatility, ensuring data security in 2023 becomes not just a best practice but a fundamental responsibility. By implementing these best practices – from encryption excellence to regular security audits – your Flutter applications can not only dazzle users with their functionality but also inspire trust by standing as formidable fortresses of data security in the evolving landscape of mobile app development. Fortify your Flutter journey, embrace these best practices, and let your users experience the epitome of security in the palm of their hands.
0 notes
Text
With millions of dollars worth of Assets being lost to phishing attacks after signing malicious permissions, the threat of losing Crypto Assets from questionable links is very real. When these are paired with platforms allowing hidden links, users are subjected to a different kind of risk. On Sept. 4, Web3 Security provider Pocket Universe shared how scammers are able to hide wallet drainer links on any text on the instant messaging platform Discord. While some users report that the feature has only been enabled for Discord users recently, the ability to embed links on any text has been available on many different social platforms for a while now. Scammers can now hide links in any discord text ☠️Watch out for hidden wallet drainer links e.g. pic.twitter.com/mgqG18sOF9— Pocket Universe (@PocketUniverseZ) September 4, 2023 Cointelegraph reached out to several Cybersecurity professionals to learn more about how users can protect themselves from such attempts and how platforms can improve their Security so that users are not subjected to such attacks. Christian Seifert, who works as a Researcher in Residence at Web3 Security firm Forta Network, said that this type of attack has been the bread and butter of hackers since the internet was created. He explained that: “Whatever a platform creates, there will be a hacker ready to find a way to hack it. Hyperlinks with text are a feature supported as part of HTML and have been a source for phishing attacks since the early days of the internet.”According to Seifert, Security requires an in-depth Defense approach. “Both platforms and users need to work towards protecting themselves,” he said. From the user’s side, the Security professional highlighted that there are plugins that they can use to protect themselves from such scams. When it comes to Discord, Seifert pointed out that the platform does provide Information on the true destination of the URL after the user clicks on it. However, the platform also allows users to “trust” a domain going forward. This can be abused by scammers according to Seifert. He explained: “Imagine a domain like foo.bar which the user trusted. A scammer can craft a potentially malicious link that performs some action on this domain, such as an oauth request to the scammer, like foo.bar/oauth/scammer-account.”The Cybersecurity professional said that an issue with the platform’s current implementation is that links and text can be deceptive and misaligned with users’ expectations. “If a text link clearly resembles a domain or URL and it is mismatched to the true destination URL, Discord should disallow such links,” he added. Meanwhile, Hugh Brooks, the director of Security operations at the Blockchain Security firm CertiK, echoed some of Seifert’s sentiments. According to Brooks, users and platforms have a collective responsibility to watch out for malicious actors. He explained that it’s essential for platforms to continually review and refine their Security features and for users to stay vigilant and educated. For users, Brooks said that they should be proactive and cautious when it comes to links, especially when being asked for signatures and permissions. The executive urged users to verify the authenticity of the site address before giving it access to crypto wallets. Brooks shared: “A good practice is to cross-check web addresses with recognized phishing warning lists. PhishTank, Google Safe Browsing, and OpenPhish are valuable resources here, along with browser extensions like HTTPS Everywhere and ad blockers like uBlock.”Brooks explained that these tools can alert users in real time whenever they are about to visit known phishing or malicious websites. “Furthermore, by simply hovering over a URL link, the actual web address will be displayed, allowing users to confirm its legitimacy before engaging further,” he added. On the platform’s side, the Cybersecurity professional said that there are measures that can be implemented such as being able to only receive messages from trusted contacts.
Brooks said that a good example of this is Meta’s “Facebook Protect,” which lets users have heightened Security features for their accounts. “As the saying goes, the only constant is change. Platforms owe it to their users and to their continued relevance to make Security a priority. This involves not only updating Security Measures but also fostering a culture of vigilance and awareness among users,” he added.
0 notes
Text
Smart School Gmeet Live Class Nulled Script 4.0

Smart School Gmeet Live Class Nulled Script – Revolutionize Online Learning Looking for a powerful, cost-effective solution to manage virtual classrooms? The Smart School Gmeet Live Class Nulled Script is the perfect answer for schools and educators seeking to bring seamless integration of Google Meet into their Smart School system—without breaking the bank. With this nulled script, you gain unrestricted access to premium features that enhance online education delivery, foster student engagement, and simplify the live class experience. Why Choose Smart School Gmeet Live Class Nulled Script? Designed with functionality and flexibility in mind, the Smart School Gmeet Live Class allows educators to host and manage live classes effortlessly. Whether you're teaching primary school students or offering advanced university courses, this script eliminates the technical barriers typically associated with virtual education. It integrates directly with Smart School ERP, enabling one-click scheduling, attendance tracking, and secure streaming through Google Meet. Technical Specifications Integration: Fully integrates with Smart School ERP v6.1 and above Live Streaming: Google Meet API integration for seamless class broadcasting Authentication: OAuth 2.0 secure login for teachers Session Management: Automatic meeting creation with real-time syncing Role-Based Access: Admins, Teachers, and Students get distinct privileges Outstanding Features and Benefits The Smart School Gmeet Live Class Nulled Script is packed with features that make it a must-have for any educational institution: Google Meet Integration: Teachers can start, schedule, and manage classes within seconds. Automated Attendance: The system records student attendance automatically during live sessions. User-Friendly Interface: No technical knowledge is needed—teachers and students enjoy a clean, intuitive design. Affordable Access: With the nulled version, all premium features are unlocked for free. Time-Saving Tools: Bulk scheduling, automated notifications, and calendar sync reduce manual workload. Ideal Use Cases for Smart School Gmeet Live Class Script This script is ideal for: Schools & Colleges: Easily manage large-scale virtual classrooms across multiple grades. Tuition Centers: Deliver live, interactive coaching to students from anywhere. Corporate Training: Onboard and train employees with structured, real-time sessions. Installation and Setup Guide Getting started with the Smart School Gmeet Live Class Nulled Script is quick and straightforward: Download the script package from our website. Upload the plugin through your Smart School Admin Panel. Configure Google Meet API keys for authentication. Assign roles to teachers and start scheduling classes. With this setup, you can begin live teaching sessions in just a few minutes—no complex coding or tech support needed. FAQs – Smart School Gmeet Live Class Nulled Script Q: Is it safe to use the Smart School Gmeet Live Class Script? A: Yes, the script is thoroughly tested and secure. It uses Google’s OAuth 2.0 for authentication and supports encrypted connections. Q: Will I receive all premium features? A: Absolutely. This nulled script includes every premium feature available in the original version, completely unlocked for free. Q: Can I integrate it with other Smart School modules? A: Yes, it seamlessly integrates with all modules compatible with Smart School ERP v6.1 or later. Q: Do I need to know coding? A: No coding skills are required. The installation and setup process is user-friendly and takes just a few steps. Get Started Today! Experience the future of online education with the Smart School Gmeet Live Class . Download it today and empower your institution with high-quality live streaming capabilities—all at zero cost. It’s the ultimate solution for modern educators who demand performance, flexibility, and simplicity. Looking for more powerful WordPress tools? Don’t miss the FS Poster NULLED Plugin—perfect for social media automation and marketing!
And if you need a premium WordPress theme for your educational platform, check out the woodmart nulled theme. It’s packed with features and available for free!
0 notes
Text
Download Now Spotify Social Login for WordPress and WooCommerce - WPCroc.com
Download Now Spotify Social Login for WordPress and WooCommerce – WPCroc.com
[ad_1]
DOWNLOAD FOR FREE
LIVE PREVIEWBUY FOR $18

Spotify Social Login is a WordPress plugin that allows its users to login / register using their Spotify account.
Give your users a better option to login / register, without remembering passwords.
Features
Button locations on login / registration page, comments, reviews, payment
Shortcode option to place Spotify login button anywhere
Login…
View On WordPress
#spotify login#spotify login woocommerce#spotify oauth login#spotify social login#spotify sso#spotify wordpress login#spotify wordpress login plugin#wordpress#wordpress login with spotify#wordpress plugins#wordpress themes
0 notes
Text
WordPress Plugin: Contact Form To Any API
Introduction
In today's web development landscape, integrating forms with APIs (Application Programming Interfaces) is a common requirement. Whether you're building a contact form, a registration form, or any other type of form, the ability to send data to a server or a third-party service is crucial. In this blog post, we'll explore how to connect a form to any API, covering the fundamental concepts and providing practical examples.

Understanding APIs
An API is a set of rules and protocols that define how different software components should interact and communicate with each other. APIs act as intermediaries, allowing applications to access and exchange data with other systems or services over the internet or within a network.
APIs can be divided into two main categories:
1. Web APIs: These APIs are designed to be accessed over the internet using standard protocols like HTTP(S). They are commonly used for integrating web applications with external services, such as social media platforms, payment gateways, or cloud storage providers.
2. Internal APIs: These APIs are used within an organization or a specific application ecosystem. They facilitate communication between different components or modules of an application, enabling data sharing and functionality integration.
Connecting a Form to an API
To connect a form to an API, you'll need to handle the form submission event and send the form data to the API endpoint using an appropriate method (e.g., GET, POST, PUT, DELETE) defined by the API's documentation. Here are the general steps involved:
1. Setting up the Form
Create an HTML form with input fields for the data you want to send to the API. Ensure that each input field has a unique `name` attribute, as this will be used to identify the data when sending it to the API.
2. Handling Form Submission
Use JavaScript to listen for the form submission event. When the form is submitted, you'll need to prevent the default behavior (which would typically cause a page refresh) and capture the form data.
3. Preparing the Data
Depending on the API's requirements, you may need to format the form data in a specific way. Common formats include JSON (JavaScript Object Notation), URL-encoded data, or multipart/form-data.
4. Sending the Request
Use JavaScript's `fetch` function or a library like Axios or jQuery to send an HTTP request to the API endpoint with the formatted form data. The request method (GET, POST, PUT, DELETE) and any additional headers or parameters will depend on the API's specifications.
5. Handling the Response
Once the API responds, you'll need to handle the response data appropriately. This may involve displaying a success message, updating the user interface, or performing additional actions based on the API's response.
Handling Different API Requirements
Different APIs may have varying requirements for data formatting and authentication. Here are some common scenarios:
1. JSON Data
Some APIs expect data in JSON format. In this case, you'll need to convert the form data to a JSON object before sending the request.
2. API Key Authentication
Some APIs require an API key for authentication. In this case, you'll need to include the API key in the request headers.
3. OAuth Authentication
For APIs that use OAuth authentication, you'll typically need to follow a multi-step process involving user authorization and obtaining an access token. This process may involve redirecting the user to the API's authentication page and handling the callback URL.
Example: Connecting a Contact Form to an API
Let's consider an example of connecting a simple contact form to an API. You'll need to create an HTML form with input fields for name, email, and message. Then, use JavaScript to listen for the form submission event and prevent the default behavior.
Next, you'll need to capture the form data and prepare it according to the API's requirements. This may involve converting the data to JSON format or formatting it as URL-encoded data.
Once the data is prepared, you can use JavaScript's `fetch` function or a library like Axios or jQuery to send an HTTP request to the API endpoint. The request method (e.g., POST, PUT) and any additional headers or parameters will depend on the API's specifications.
After sending the request, you'll need to handle the API's response. If the response is successful, you can display a success message, reset the form, or perform any other necessary actions. If there's an error, you should handle it appropriately by displaying an error message, logging the error for debugging purposes, or attempting to retry the request.
Example: Connecting a Form to an Internal API
In some cases, you may need to connect a form to an internal API within your application ecosystem. The general approach is similar to connecting to a web API, but the specific implementation details, such as authentication methods and endpoint URLs, may differ based on your application's architecture and requirements.
For example, if you're building a single-page application (SPA) with a separate backend API, you can use JavaScript to send form data to your internal API endpoints. This might involve authenticating the request with JSON Web Tokens (JWT) or other authentication mechanisms specific to your application.
Conclusion
Connecting forms to APIs is a common requirement in modern web development, enabling data exchange between applications and various services. By understanding APIs and following the steps outlined in this blog post, you can successfully integrate your forms with any API, whether it's a web API or an internal API.
Remember to consult the API's documentation for specific requirements, such as data formatting, authentication methods, and endpoint URLs. Additionally, ensure that you handle errors and provide appropriate feedback to users, enhancing the overall user experience of your application.
FAQs
Q: What is the difference between a web API and an internal API?
A: A web API is designed to be accessed over the internet using standard protocols like HTTP(S), allowing web applications to integrate with external services. An internal API, on the other hand, is used for communication between different components or modules within an organization or a specific application ecosystem.
Q: Can I use a library like Axios or jQuery instead of the `fetch` function?
A: Yes, you can use libraries like Axios or jQuery to send HTTP requests to APIs. These libraries often provide a more user-friendly API and additional features compared to the native `fetch` function.
Q: How do I handle authentication with APIs?
A: Authentication methods vary depending on the API. Common methods include API keys (included in request headers), OAuth (multi-step process involving user authorization and access tokens), and basic authentication (sending credentials with each request).
Q: What should I do if the API response is not successful?
A: If the API response is not successful (e.g., `response.ok` is false), you should handle the error appropriately. This may involve displaying an error message to the user, logging the error for debugging purposes, or attempting to retry the request.
Q: Can I use the same approach to connect a form to an internal API within my application?
A: Yes, the general approach of handling form submissions, preparing the data, and sending an HTTP request to the API endpoint remains the same, regardless of whether it's a web API or an internal API. However, the specific implementation details, such as authentication methods and endpoint URLs, may differ based on your application's architecture and requirements.
0 notes
Text
I wonder how difficult it would be to pawn off API costs onto users through subscriptions. Like, you charge 20 dollars a year and you assign that account an OAuth key. 3rd party apps don't interact with the API directly, they just send and receive the requests and responses on your behalf.
I mean this doesn't address the reddit situation, they're very obviously trying to kill 3rd party on purpose. But "access to the 3rd party app/plugin ecosystem" would be a pretty solid incentive for payment, and it would align the interests of 3rd party devs and the site.
2 notes
·
View notes
Photo

Google launches Site Kit plugin for insights into WordPress websites https://ift.tt/2NyMQsq
Google has officially launched its open-source Site Kit WordPress plugin that gives website owners insights into how people are using their websites, drawing from integrations with myriad Google products.
This is a big deal because Google is a leading driver of internet traffic and website monetization, while WordPress underpins more than a third of all websites. Site Kit, in many ways, has been a long time coming. Google first teased Site Kit last December, before introducing it in developer preview back in June. From this week, it’s available to everyone globally.
Site Kit: Plugged in
In a nutshell, Site Kit helps WordPress site developers connect Google services including AdSense, PageSpeed Insights, Analytics, and Search Console, with a view toward making data around audience, revenue, and performance easily accessible from a central dashboard.
Google has said that it plans to expand the plugin’s integrations in the future.
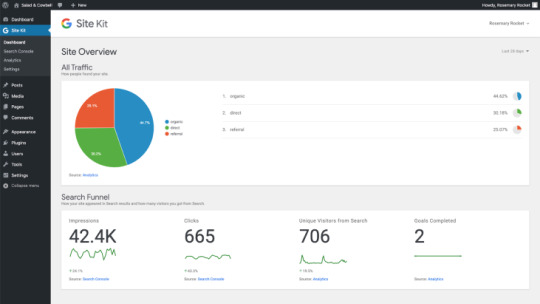
Above: Google’s new Site Kit plugin for WordPress websites
During the beta phase, Site Kit required a some advanced web development knowledge, including Google Cloud Platform verification and OAuth. For the public plugin launch, Site Kit has been iterated to make it easy for the user to verify their ownership of a site without having to dabble in the site’s code, using the Site Kit setup wizard.
Post-configuration, the website owner can get notifications that include at-a-glance data snapshots such as when they hit a record milestone for visitors. They can also dig down and see how each specific page on the site is performing, in terms of clicks, impressions, users, sessions, and where the traffic is coming from.

Above: Site Kit: Example screens
Data is only so helpful though — it’s what you do with the data that’s important. Integration with PageSpeed Insights, for example, shows WordPress site owners how well their site is performing in Chrome, with recommendations on how to improve it. And by tethering to AdSense, site owners who are trying to monetize through Google’s ad network can track their ad performance.
Site Kit could also prove useful for agencies that manage one or more websites for a client, as it makes compiling reports much easier without having to copy data from disparate products and data ources.
It’s worth noting here that there are plenty of other third-party services available that replicate much of this functionality, but they often come with a subscription cost and / or require the user to paste code into the site’s backend. Site Kit doesn’t bring specific new functionality as such, it’s more about bringing features together and making them easier to use — without costing a bean.
Moreover, Site Kit should save more than a little spadework for website owners who currently manually check their various Google services in each of their standalone dashboards. With Site Kit, everything is visible centrally within WordPress.
1 note
·
View note