#port forward without vpn
Explore tagged Tumblr posts
Text
On Personal InfoSec
Been awhile since I've had one of these posts but I figure with all that's going on in the world it's time to make another one of these posts and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides.
Browsers:
There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out.
Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN:
Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Proton VPN: Has easily the most amount of countries serviced, can take cash payments, and does offer port forwarding.
Email Provider:
Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Outlook.com you'll need to pay.
Proton Mail: Secure, end-to-end encrypted, and fairly easy to setup and use. Offers a free option up to 1gb
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Email Client:
Thunderbird if you're on Windows or Linux
Apple Mail if you're on macOS
Cloud Storage:
Proton Drive: Encrypted cloud storage from the same people as Proton Mail.
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free, and open source.
Chat Clients:
Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode.
If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help.
I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#information security#infosec#computer security#computer infosec#personal infosec#browsers#internet browser#email#instant messaging#cloud storage#linux#pop os#linux mint#ubuntu#firefox#firefox extensions#long post
67 notes
·
View notes
Text
(this is a small story of how I came to write my own intrusion detection/prevention framework and why I'm really happy with that decision, don't mind me rambling)
Preface
About two weeks ago I was faced with a pretty annoying problem. Whilst I was going home by train I have noticed that my server at home had been running hot and slowed down a lot. This prompted me to check my nginx logs, the only service that is indirectly available to the public (more on that later), which made me realize that - due to poor access control - someone had been sending me hundreds of thousands of huge DNS requests to my server, most likely testing for vulnerabilities. I added an iptables rule to drop all traffic from the aforementioned source and redirected remaining traffic to a backup NextDNS instance that I set up previously with the same overrides and custom records that my DNS had to not get any downtime for the service but also allow my server to cool down. I stopped the DNS service on my server at home and then used the remaining train ride to think. How would I stop this from happening in the future? I pondered multiple possible solutions for this problem, whether to use fail2ban, whether to just add better access control, or to just stick with the NextDNS instance.
I ended up going with a completely different option: making a solution, that's perfectly fit for my server, myself.
My Server Structure
So, I should probably explain how I host and why only nginx is public despite me hosting a bunch of services under the hood.
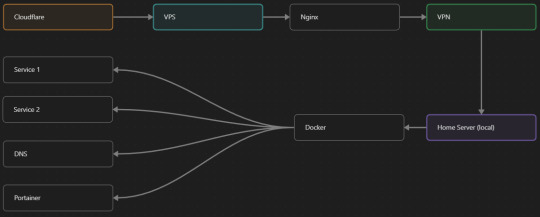
I have a public facing VPS that only allows traffic to nginx. That traffic then gets forwarded through a VPN connection to my home server so that I don't have to have any public facing ports on said home server. The VPS only really acts like the public interface for the home server with access control and logging sprinkled in throughout my configs to get more layers of security. Some Services can only be interacted with through the VPN or a local connection, such that not everything is actually forwarded - only what I need/want to be.
I actually do have fail2ban installed on both my VPS and home server, so why make another piece of software?
Tabarnak - Succeeding at Banning
I had a few requirements for what I wanted to do:
Only allow HTTP(S) traffic through Cloudflare
Only allow DNS traffic from given sources; (location filtering, explicit white-/blacklisting);
Webhook support for logging
Should be interactive (e.g. POST /api/ban/{IP})
Detect automated vulnerability scanning
Integration with the AbuseIPDB (for checking and reporting)
As I started working on this, I realized that this would soon become more complex than I had thought at first.
Webhooks for logging This was probably the easiest requirement to check off my list, I just wrote my own log() function that would call a webhook. Sadly, the rest wouldn't be as easy.
Allowing only Cloudflare traffic This was still doable, I only needed to add a filter in my nginx config for my domain to only allow Cloudflare IP ranges and disallow the rest. I ended up doing something slightly different. I added a new default nginx config that would just return a 404 on every route and log access to a different file so that I could detect connection attempts that would be made without Cloudflare and handle them in Tabarnak myself.
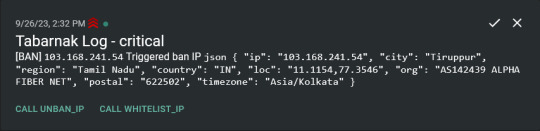
Integration with AbuseIPDB Also not yet the hard part, just call AbuseIPDB with the parsed IP and if the abuse confidence score is within a configured threshold, flag the IP, when that happens I receive a notification that asks me whether to whitelist or to ban the IP - I can also do nothing and let everything proceed as it normally would. If the IP gets flagged a configured amount of times, ban the IP unless it has been whitelisted by then.
Location filtering + Whitelist + Blacklist This is where it starts to get interesting. I had to know where the request comes from due to similarities of location of all the real people that would actually connect to the DNS. I didn't want to outright ban everyone else, as there could be valid requests from other sources. So for every new IP that triggers a callback (this would only be triggered after a certain amount of either flags or requests), I now need to get the location. I do this by just calling the ipinfo api and checking the supplied location. To not send too many requests I cache results (even though ipinfo should never be called twice for the same IP - same) and save results to a database. I made my own class that bases from collections.UserDict which when accessed tries to find the entry in memory, if it can't it searches through the DB and returns results. This works for setting, deleting, adding and checking for records. Flags, AbuseIPDB results, whitelist entries and blacklist entries also get stored in the DB to achieve persistent state even when I restart.
Detection of automated vulnerability scanning For this, I went through my old nginx logs, looking to find the least amount of paths I need to block to catch the biggest amount of automated vulnerability scan requests. So I did some data science magic and wrote a route blacklist. It doesn't just end there. Since I know the routes of valid requests that I would be receiving (which are all mentioned in my nginx configs), I could just parse that and match the requested route against that. To achieve this I wrote some really simple regular expressions to extract all location blocks from an nginx config alongside whether that location is absolute (preceded by an =) or relative. After I get the locations I can test the requested route against the valid routes and get back whether the request was made to a valid URL (I can't just look for 404 return codes here, because there are some pages that actually do return a 404 and can return a 404 on purpose). I also parse the request method from the logs and match the received method against the HTTP standard request methods (which are all methods that services on my server use). That way I can easily catch requests like:
XX.YYY.ZZZ.AA - - [25/Sep/2023:14:52:43 +0200] "145.ll|'|'|SGFjS2VkX0Q0OTkwNjI3|'|'|WIN-JNAPIER0859|'|'|JNapier|'|'|19-02-01|'|'||'|'|Win 7 Professional SP1 x64|'|'|No|'|'|0.7d|'|'|..|'|'|AA==|'|'|112.inf|'|'|SGFjS2VkDQoxOTIuMTY4LjkyLjIyMjo1NTUyDQpEZXNrdG9wDQpjbGllbnRhLmV4ZQ0KRmFsc2UNCkZhbHNlDQpUcnVlDQpGYWxzZQ==12.act|'|'|AA==" 400 150 "-" "-"
I probably over complicated this - by a lot - but I can't go back in time to change what I did.
Interactivity As I showed and mentioned earlier, I can manually white-/blacklist an IP. This forced me to add threads to my previously single-threaded program. Since I was too stubborn to use websockets (I have a distaste for websockets), I opted for probably the worst option I could've taken. It works like this: I have a main thread, which does all the log parsing, processing and handling and a side thread which watches a FIFO-file that is created on startup. I can append commands to the FIFO-file which are mapped to the functions they are supposed to call. When the FIFO reader detects a new line, it looks through the map, gets the function and executes it on the supplied IP. Doing all of this manually would be way too tedious, so I made an API endpoint on my home server that would append the commands to the file on the VPS. That also means, that I had to secure that API endpoint so that I couldn't just be spammed with random requests. Now that I could interact with Tabarnak through an API, I needed to make this user friendly - even I don't like to curl and sign my requests manually. So I integrated logging to my self-hosted instance of https://ntfy.sh and added action buttons that would send the request for me. All of this just because I refused to use sockets.
First successes and why I'm happy about this After not too long, the bans were starting to happen. The traffic to my server decreased and I can finally breathe again. I may have over complicated this, but I don't mind. This was a really fun experience to write something new and learn more about log parsing and processing. Tabarnak probably won't last forever and I could replace it with solutions that are way easier to deploy and way more general. But what matters is, that I liked doing it. It was a really fun project - which is why I'm writing this - and I'm glad that I ended up doing this. Of course I could have just used fail2ban but I never would've been able to write all of the extras that I ended up making (I don't want to take the explanation ad absurdum so just imagine that I added cool stuff) and I never would've learned what I actually did.
So whenever you are faced with a dumb problem and could write something yourself, I think you should at least try. This was a really fun experience and it might be for you as well.
Post Scriptum
First of all, apologies for the English - I'm not a native speaker so I'm sorry if some parts were incorrect or anything like that. Secondly, I'm sure that there are simpler ways to accomplish what I did here, however this was more about the experience of creating something myself rather than using some pre-made tool that does everything I want to (maybe even better?). Third, if you actually read until here, thanks for reading - hope it wasn't too boring - have a nice day :)
10 notes
·
View notes
Text
8 Game-Changing Developer Tools to Skyrocket Your Productivity.
Let’s be honest: Sometimes coding isn’t the hard part—it’s everything else. The context switching. The bugs you can’t reproduce. The terminal black hole you get sucked into at 2AM.
Over the past year, I tried dozens of tools. These 8? They legitimately changed the game for me.

Here’s the list I wish someone handed me earlier 👇
🧠 Raycast – It’s Like Mac Spotlight, but on Steroids You know that moment when you reach for Spotlight and it’s painfully slow?
Raycast fixes that. It's lightning fast, totally extendable, and lets me do stuff like:
Run scripts
Search docs
Control GitHub PRs
Even trigger workflows
All with a couple keystrokes.
Productivity level: 🔥 Programmer with a keyboard superpower
🤖 Tabby (formerly Codeium) – AI Autocomplete, No Cloud Required This is your AI pair programmer, but local. It runs on your machine, respects your privacy, and still feels scary accurate.
You just code—and Tabby whispers the next line before you think it.
Hot take: AI autocomplete is now baseline. Tabby just does it smarter.
🖥️ Warp – The Terminal You Didn’t Know You Needed The first time I opened Warp, I was like: “Wait… why hasn’t the terminal looked like this all along?”
Input blocks
Modern UI
Real-time suggestions
Collaboration built-in
Feels like: VS Code had a baby with your terminal—and it grew up fast.
🧑🤝🧑 Zed – Pair Programming, but Actually Fun Zed is a super snappy code editor with real-time multiplayer built in. Think Google Docs, but for code—with speed that makes VS Code look sleepy.
Perfect for: Pair programming, mentoring, or just working with your future self.
🔍 LogRocket – Debug Like You’re Watching a Replay Have you ever tried to debug a user issue with just an error log?
LogRocket is like, “Here, watch the actual replay of what happened.”
See user sessions
Capture console logs
Rewind the moment everything broke
Result: 10x fewer “Can you send a screenshot?” messages.
⚡ Fig – Terminal Autocomplete That Feels Like Magic Fig turns your CLI into a cheat code machine.
Flags? Autocompleted.
Scripts? Suggested.
Git commands? Faster than your memory.
Vibe: It’s like your terminal suddenly got a brain (and a heart).
🧯 Sentry – Know When Things Break Before Twitter Does Sentry tells you when your app throws an error—in real time.
It works across languages, frameworks, and stacks. You get:
Stack traces
Performance metrics
Release tracking
Translation: Fewer angry DMs from product managers.
🔒 Tailscale – Private Networking Without the VPN Pain Need to connect your laptop, server, and Raspberry Pi like they’re in the same room?
Tailscale makes that happen with zero setup hell.
No port forwarding. No crying into your terminal.
Just install → login → done.
🎉 TL;DR: Stop Fighting Your Tools Being a dev today means juggling:
Meetings
Bugs
Context switches
200 Chrome tabs
These tools helped me claw back hours every week—and made coding feel fun again.
0 notes
Text
“The Future of Remote Access: Why Businesses Are Switching to RHosting”
In today’s rapidly evolving digital landscape, remote access is no longer optional — it’s essential. Whether it's supporting hybrid teams, enabling global collaboration, or reducing IT overhead, businesses need tools that are fast, secure, and scalable.
That’s why forward-thinking companies are making the switch to RHosting, a modern remote desktop hosting solution built for the cloud-first, work-from-anywhere world.
Here’s why RHosting is shaping the future of remote access — and why more businesses are adopting it every day.

🔗 1. Traditional Solutions Are Breaking Down
Legacy systems like on-premise RDP, VPNs, and Terminal Services come with a host of challenges:
Complex setup and maintenance
Limited scalability
Security vulnerabilities
Performance issues in remote locations
In contrast, RHosting eliminates the friction by offering a fully managed, cloud-based platform that’s ready to go — no heavy IT involvement required.
🌐 2. Truly Global, Truly Accessible
Whether your team is working across cities or continents, RHosting delivers a consistent, high-performance experience.
Access desktops and apps from any device
No VPN or static IPs required
Built-in optimizations for low-latency performance
This makes RHosting ideal for distributed teams, freelancers, or businesses with a mobile workforce.
🛡️ 3. Built-In Security for a Zero-Trust World
Cybersecurity is a top concern for modern businesses — and rightly so. RHosting was built with security-first architecture, offering:
End-to-end encryption
Multi-factor authentication (MFA)
Role-based access controls
No open RDP ports or exposed endpoints
This means your data, users, and infrastructure remain protected — without relying on outdated firewall or VPN strategies.
⚙️ 4. Centralized Control Without the Headaches
Managing users, assigning access, and monitoring activity doesn’t have to be complicated. With RHosting’s admin-friendly dashboard, IT teams can:
Add or remove users in seconds
Define folder- or app-level permissions
Monitor access logs for compliance
Push updates without interrupting end-users
Whether you’re an IT admin or a business owner, you stay in full control — without micromanaging the tech.
📊 5. Designed to Scale With Your Business
From startups to enterprises, RHosting adapts to your needs. No hardware upgrades, no server provisioning, no costly licenses.
Pay-as-you-go pricing
Instant resource scaling
Support for seasonal teams, contractors, and growing departments
This agility helps businesses stay competitive while keeping IT costs predictable and efficient.
✅ Conclusion: Remote Access, Reinvented
RHosting isn’t just a remote desktop solution — it’s a smarter, faster, and safer way to run your business in the cloud era. As the nature of work continues to change, companies that embrace secure, scalable remote access will have the edge.
Join the businesses shaping the future. Switch to RHosting — and take your workplace anywhere.
0 notes
Text
“Working Remotely Without Compromise: 5 Ways RHosting Enables Productivity”
In a world where remote work is no longer a trend but a necessity, businesses are seeking reliable solutions to ensure productivity doesn’t drop when teams go virtual. That’s where RHosting steps in—a remote desktop hosting platform designed to make remote work seamless, secure, and efficient.
Whether you’re an IT manager, business owner, or freelancer, here are 5 powerful ways RHosting helps you work remotely—without compromise.

1️⃣ Fast, Seamless Access From Anywhere
No matter where you are—home, a co-working space, or another continent—RHosting ensures that connecting to your Windows server is just a few clicks away. With cloud-powered infrastructure and optimized latency, it feels like you're working locally, even when you're remote.
✔ Ideal for: Traveling professionals, distributed teams, and hybrid offices.
2️⃣ Run Resource-Intensive Applications With Ease
Many remote desktop solutions struggle with large applications like data analytics tools, CRMs, or software development environments. RHosting is built to handle high-performance computing, allowing users to run heavy-duty apps smoothly.
✔ Perfect for: Developers, data analysts, video editors, and researchers.
3️⃣ Fine-Grained Access Control = Focused Work
RHosting lets you restrict access to specific applications and folders, so users see only what they need. No distractions, no unnecessary permissions. This not only improves security—it boosts productivity by reducing complexity.
✔ Use case: Assign only accounting tools to your finance team, or only a CRM dashboard to your sales staff.
4️⃣ No Hardware Headaches or IT Bottlenecks
Forget about complex VPN setups, port forwarding, or in-house servers. RHosting is fully cloud-based, so you can get started without needing any additional hardware or deep technical skills.
✔ Benefit: Less downtime, fewer IT support requests, and faster onboarding.
5️⃣ Secure, Reliable Remote Work—Without Sacrificing Performance
RHosting goes beyond standard Remote Desktop Protocol (RDP) with end-to-end encryption, 2FA, and secure session logging. That means you get enterprise-grade security while maintaining the speed and responsiveness your team needs.
✔ Key advantage: Protect your business data while enabling smooth workflow and compliance.
🚀 Final Thoughts: Work Smarter, Not Harder With RHosting
Productivity in a remote setup hinges on your tools. With RHosting, you don’t have to choose between security, speed, or simplicity—you get all three.
If you’re looking to build a remote-first workplace that thrives, it’s time to switch to RHosting.
🔧 Try RHosting for Free
Experience the next generation of remote desktop access. Start your free trial today and see how easy, secure, and productive remote work can be.
0 notes
Photo

TP-Link Archer AX20 AX1800 Dual Band Wifi 6 Router FEATURES: Dual-Band Wi-Fi 6: Equipped with the latest wireless technology, Wi-Fi 6, for faster speeds, greater capacity, and reduced network congestion Next-Gen 1.8Gbps Speeds: Enjoy smooth streaming, downloading, and gaming all without buffering with Wi-Fi speeds of 1.8Gbps Connect More Devices: Wi-Fi 6 technology communicates more data to more devices using revolutionary OFDMA technology while simultaneously reducing lag Quad-Core Processing: The 1.5GHz quad-core CPU ensures communications between your router and all connected devices are smooth Extensive Coverage: Beamforming, independent FEM, and four antennas combine to deliver focused reception to devices far away Increased Battery Life: Target Wake Time technology reduces your devices’ power consumption to extend their battery life USB Easy Sharing: A USB 2.0 Port enables easy file sharing within your network or building private Cloud Storage Easy Setup: Set up your router in minutes with the powerful TP-Link Tether App Backward Compatible: Supports all previous 802.11 standards and all Wi-Fi devices WIRELESS Standards Wi-Fi 6 IEEE 802.11ax/ac/n/a 5 GHz IEEE 802.11ax/n/b/g 2.4 GHz WiFi Speeds AX1800 5 GHz: 1201 Mbps (802.11ax) 2.4 GHz: 574 Mbps (802.11ax) WiFi Range 3 Bedroom Houses 4× Fixed High-Performance Antennas Multiple antennas form a signal-boosting array to cover more directions and large areas Beamforming Concentrates wireless signal strength towards clients to expand WiFi range High-Power FEM Improves transmission power to strengthen signal coverage WiFi Capacity High Dual-Band Allocate devices to different bands for optimal performance OFDMA Simultaneously communicates with multiple Wi-Fi 6 clients Airtime Fairness Improves network efficiency by limiting excessive occupation 4 Streams Connect your devices to more bandwidth Working Modes Router Mode Access Point Mode HARDWARE Processor 1.5 GHz Quad-Core CPU Ethernet Ports 1× Gigabit WAN Port 4× Gigabit LAN Ports USB Support 1× USB 2.0 Port Supported Partition Formats: NTFS, exFAT, HFS+, FAT32 Supported Functions: Apple Time Machine FTP Server Media Server Samba Server Buttons WPS/Wi-Fi Button Power On/Off Button LED On/Off Button Reset Button Power 12 V ⎓ 1.5 A SECURITY WiFi Encryption WPA WPA2 WPA3 WPA/WPA2-Enterprise (802.1x) Network Security SPI Firewall Access Control IP & MAC Binding Application Layer Gateway Guest Network 1× 5 GHz Guest Network 1× 2.4 GHz Guest Network VPN Server OpenVPN PPTP SOFTWARE Protocols IPv4 IPv6 Parental Controls URL Filtering Time Controls WAN Types Dynamic IP Static IP PPPoE PPTP L2TP Quality of Service QoS by Device Cloud Service Auto Firmware Upgrade OTA Firmware Upgrade TP-Link ID DDNS NAT Forwarding Port Forwarding Port Triggering DMZ UPnP IPTV IGMP Proxy IGMP Snooping Bridge Tag VLAN DHCP Address Reservation DHCP Client List Server DDNS TP-Link NO-IP DynDNS Management Tether App Webpage PHYSICAL Dimensions (W×D×H) 10.2 × 5.3 ×1.5 in (260.2 × 135.0 × 38.6 mm) Package Contents Wi-Fi Router Archer AX20 Power Adapter RJ45 Ethernet Cable Quick Installation Guide OTHER System Requirements Internet Explorer 11+, Firefox 12.0+, Chrome 20.0+, Safari 4.0+, or other JavaScript-enabled browser Cable or DSL Modem (if needed) Subscription with an internet service provider (for internet access) Certifications FCC, CE, RoHS Environment Operating Temperature: 0℃~40℃ (32℉ ~104℉) Storage Temperature: -40℃~70℃ (-40℉ ~158℉) Operating Humidity: 10%~90% non-condensing Storage Humidity: 5%~90% non-condensing TEST DATA WiFi Transmission Power CE:
0 notes
Text
how to bypass a firewall without a vpn
🔒🌍✨ Ganhe 3 Meses de VPN GRÁTIS - Acesso à Internet Seguro e Privado em Todo o Mundo! Clique Aqui ✨🌍🔒
how to bypass a firewall without a vpn
Como contornar firewall sem VPN
Geralmente, as empresas implementam firewalls em suas redes para garantir a segurança dos dados e evitar acessos não autorizados. No entanto, há momentos em que pode ser necessário contornar o firewall sem utilizar uma VPN. Existem algumas técnicas que podem ser usadas para alcançar esse objetivo.
Uma das maneiras de contornar um firewall sem uma VPN é utilizando o SSH (Secure Shell). O SSH é um protocolo de rede criptografado que permite estabelecer conexões seguras com outros dispositivos na rede. Ao utilizar o SSH, é possível criar um túnel para acessar recursos da rede que estão bloqueados pelo firewall.
Outra forma de contornar um firewall é usando o Proxy. Um servidor proxy atua como intermediário entre o dispositivo do usuário e a internet. Ao configurar um servidor proxy, é possível redirecionar o tráfego da internet através desse servidor, contornando assim as restrições impostas pelo firewall.
Além disso, é possível utilizar técnicas de tunelamento, como o uso de serviços como o SSH Dynamic Port Forwarding ou o uso de ferramentas como o Proxychains, que permitem rotear o tráfego da internet através de diferentes servidores, contornando as restrições do firewall.
É importante ressaltar que contornar um firewall sem autorização pode violar as políticas de segurança da rede e resultar em consequências legais. Portanto, é essencial obter permissão antes de tentar contornar um firewall e sempre agir de acordo com as leis e regulamentos locais.
Estratégias para acessar firewall sem VPN
Quando se trata de acessar um firewall sem utilizar VPN, é essencial adotar certas estratégias para garantir a segurança e a eficácia do processo. Embora a VPN seja frequentemente recomendada para estabelecer uma conexão segura com o firewall, em algumas situações pode ser necessário explorar outras alternativas.
Uma estratégia comum é o uso de túneis SSH (Secure Shell) para acessar o firewall de forma segura. O SSH oferece uma comunicação criptografada entre o usuário e o servidor, tornando as informações transmitidas mais seguras contra possíveis interceptações. Ao configurar um túnel SSH, o tráfego de dados pode ser encaminhado de forma segura através da conexão protegida.
Outra estratégia é a utilização de proxies reversos, que podem ser configurados para atuar como intermediários na comunicação com o firewall. Por meio de um proxy reverso, é possível proteger o firewall de possíveis ataques externos, bem como permitir o acesso remoto de forma segura, sem a necessidade de uma VPN.
Além disso, a implementação de regras de firewall mais restritivas e a adoção de autenticação em dois fatores podem ajudar a aumentar a segurança no acesso ao firewall sem o uso de VPN. Essas medidas adicionais garantem que apenas usuários autorizados tenham permissão para acessar o firewall, reduzindo assim o risco de violações de segurança.
Em suma, ao explorar alternativas para acessar um firewall sem VPN, é fundamental adotar estratégias que priorizem a segurança dos dados e a integridade do sistema, garantindo assim uma conexão confiável e protegida.
Técnicas de burlar firewall sem VPN
As técnicas para burlar firewall sem o uso de VPN podem ser arriscadas e ilegais, por isso é importante compreender os riscos envolvidos nesse tipo de prática. Um firewall é uma medida de segurança vital para proteger redes contra acessos não autorizados, filtrando o tráfego de dados que entra e sai de uma rede.
Uma das maneiras de tentar contornar um firewall sem uma VPN é por meio da utilização de proxies. Um proxy atua como um intermediário entre o dispositivo do usuário e a internet, mascarando o endereço IP real do usuário ao navegar online. No entanto, proxies gratuitos podem ser inseguros e muitas vezes podem comprometer a privacidade dos dados.
Outra técnica utilizada para driblar firewalls é o uso de tunelamento SSH. Por meio de uma conexão SSH (Secure Shell), é possível estabelecer um túnel seguro entre o dispositivo do usuário e um servidor externo, permitindo o acesso a conteúdos bloqueados pela rede local. Essa técnica requer certo conhecimento técnico e configuração adequada para funcionar corretamente.
É fundamental ressaltar que tentar burlar um firewall sem autorização pode resultar em consequências legais graves, como infrações de segurança cibernética e violações de privacidade. Recomenda-se sempre buscar alternativas legais e seguras, como o uso de VPNs confiáveis, para garantir a proteção dos dados e a privacidade online do usuário.
Navegação segura sem VPN em firewalls
A navegação segura na internet é uma preocupação crescente nos dias de hoje, especialmente quando se trata de proteger a privacidade e os dados pessoais. Muitas pessoas recorrem ao uso de VPNs (Virtual Private Networks) para garantir uma conexão segura e anônima ao navegar online. No entanto, é possível alcançar um nível de segurança semelhante sem a necessidade de uma VPN, por meio do uso de firewalls.
Os firewalls atuam como uma barreira de proteção entre a rede privada do usuário e a vastidão da internet. Eles monitoram e controlam o tráfego de dados, bloqueando atividades suspeitas ou maliciosas que possam representar uma ameaça à segurança online. Com as configurações adequadas, um firewall pode ser uma ferramenta eficaz para impedir que hackers acessem informações confidenciais ou exploits maliciosos comprometam a segurança do dispositivo.
Ao investir em firewalls de qualidade e manter suas configurações atualizadas, os usuários podem desfrutar de uma navegação mais segura e protegida, sem a necessidade de uma VPN. No entanto, é importante ressaltar que a combinação de firewalls e VPNs pode oferecer uma camada extra de segurança, especialmente ao lidar com informações sensíveis ou ao se conectar a redes públicas.
Em resumo, os firewalls são uma ferramenta fundamental para garantir a segurança cibernética e proteger a privacidade dos usuários durante a navegação na internet. Com a devida atenção e configuração, é possível desfrutar de uma experiência online segura e tranquila, mesmo sem a utilização de uma VPN.
Métodos eficazes para driblar firewall sem VPN
Para quem procura maneiras de contornar firewalls sem precisar utilizar uma VPN, existem métodos eficazes que podem ser explorados. Embora o uso de uma VPN seja uma das formas mais seguras e comuns de contornar restrições de firewall, nem sempre é a opção mais conveniente ou acessível. Aqui estão algumas alternativas eficazes:
Proxy Web: Uma opção simples e fácil de usar é o proxy web. Existem diversos sites que oferecem serviços de proxy web gratuitos, que permitem acessar sites bloqueados através de um navegador. No entanto, é importante ter em mente que alguns proxies podem não garantir total privacidade e segurança dos dados.
Navegadores com Modo Privado ou Anônimo: Alguns navegadores, como o Google Chrome e o Mozilla Firefox, possuem modos de navegação privada ou anônima. Esses modos podem ajudar a contornar firewalls e acessar conteúdos bloqueados temporariamente.
Redes Proxy: Utilizar uma rede proxy pode ser uma alternativa eficaz, pois redireciona o tráfego da internet através de um servidor intermediário, mascarando o endereço IP real do usuário. Existem diferentes tipos de proxies, como HTTP, SOCKS e transparentes, cada um com suas próprias características.
Utilização de DNS Público: Alterar as configurações de DNS do computador ou dispositivo móvel para um servidor DNS público pode ajudar a driblar restrições de firewall. Alguns provedores de DNS públicos conhecidos incluem o Google Public DNS e o OpenDNS.
É importante ressaltar que o uso desses métodos para contornar firewalls pode violar as políticas de segurança da rede e os termos de serviço de determinados sites. Portanto, é essencial agir com responsabilidade e estar ciente dos riscos envolvidos. Além disso, sempre priorize a segurança e a proteção dos seus dados ao explorar essas alternativas.
0 notes
Text
does nord vpn allow port forwarding
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does nord vpn allow port forwarding
NordVPN port forwarding policy
NordVPN is a renowned name in the realm of virtual private networks (VPNs), offering users a secure and private online browsing experience. Among its array of features is the option for port forwarding, a functionality highly sought after by advanced users and businesses alike.
Port forwarding allows users to redirect internet traffic from one port to another, enhancing accessibility and facilitating specific tasks such as hosting servers or accessing devices remotely. NordVPN's port forwarding policy is designed to provide users with flexibility and control over their network connections while maintaining robust security measures.
One of the key aspects of NordVPN's port forwarding policy is its compatibility with a wide range of devices and platforms. Whether you're using Windows, macOS, Linux, or mobile devices running iOS or Android, NordVPN offers seamless integration of port forwarding functionality, ensuring that users can leverage it regardless of their preferred operating system.
Additionally, NordVPN prioritizes user privacy and security, ensuring that port forwarding activities do not compromise the anonymity and confidentiality of user data. By encrypting internet traffic and employing advanced security protocols such as OpenVPN and IKEv2/IPsec, NordVPN safeguards users' online activities while still allowing them to benefit from port forwarding capabilities.
Moreover, NordVPN provides comprehensive guides and tutorials to assist users in setting up and configuring port forwarding for their specific needs. Whether you're a novice user or a seasoned IT professional, NordVPN's resources make it easy to harness the power of port forwarding without any hassle.
In conclusion, NordVPN's port forwarding policy embodies its commitment to empowering users with advanced networking capabilities while prioritizing security and privacy. Whether you're looking to host servers, access devices remotely, or optimize your online experience, NordVPN offers a robust and user-friendly solution for all your port forwarding needs.
NordVPN port forwarding capabilities
Title: Exploring NordVPN's Port Forwarding Capabilities
NordVPN is renowned for its robust security features, ensuring users' online privacy and anonymity. However, beyond its encryption and server network, NordVPN also offers advanced functionalities like port forwarding, enhancing users' online experience and versatility.
Port forwarding is a technique used to allow external devices to connect to specific services or applications within a private network. NordVPN's port forwarding feature enables users to access these services securely over the VPN connection.
One of the primary advantages of NordVPN's port forwarding is its ability to bypass network restrictions and firewalls. By redirecting traffic through specific ports, users can overcome limitations imposed by their internet service provider or network administrator, enabling seamless access to various online services.
Moreover, NordVPN's port forwarding enhances online gaming experiences. By opening specific ports, gamers can improve connectivity, reduce latency, and prevent disconnections during multiplayer gaming sessions. This feature is particularly beneficial for gamers who encounter connectivity issues due to network configurations or ISP restrictions.
Additionally, NordVPN's port forwarding is useful for individuals hosting servers or accessing remote devices. Whether running a personal website, hosting a gaming server, or accessing a home security system remotely, port forwarding ensures secure and reliable connections, even while connected to NordVPN's servers.
NordVPN's port forwarding capabilities are easy to set up and customize through its user-friendly interface. Users can select the desired port or allow NordVPN to automatically assign one, streamlining the process for both novice and experienced users alike.
In conclusion, NordVPN's port forwarding feature enhances users' online activities by providing secure and reliable access to services, gaming servers, and remote devices. With its ease of use and effectiveness, NordVPN continues to solidify its position as a leading VPN provider, catering to the diverse needs of its users.
NordVPN port forwarding restrictions
NordVPN is renowned for its robust security features and privacy protection, but users often encounter limitations when it comes to port forwarding. Port forwarding is a crucial aspect of VPN services, enabling users to establish secure connections for various purposes such as gaming, file sharing, and remote access.
However, NordVPN imposes restrictions on port forwarding for several reasons. One primary reason is to maintain network integrity and prevent abuse. By limiting port forwarding, NordVPN aims to mitigate potential security risks and ensure the overall stability of its network. This restriction helps prevent malicious activities such as DDoS attacks and unauthorized access to sensitive systems.
Another factor contributing to NordVPN's port forwarding restrictions is the shared IP infrastructure. NordVPN operates on a shared IP model, meaning multiple users are assigned the same IP address simultaneously. This setup enhances user privacy and anonymity but complicates port forwarding, as it requires individualized port configurations for each user.
Furthermore, NordVPN's focus on user experience and simplicity plays a role in its port forwarding limitations. The service prioritizes ease of use and streamlined functionality, opting for a standardized approach to network management rather than complex customization options. While this approach may limit advanced users' flexibility, it ensures a seamless and hassle-free VPN experience for the majority of NordVPN's user base.
Despite these restrictions, NordVPN continues to evolve its service to meet user demands. While port forwarding options may be limited compared to dedicated VPN providers, NordVPN compensates with its extensive server network, fast speeds, and reliable security features. Additionally, users can explore alternative methods such as using a dedicated IP address or utilizing third-party port forwarding services to overcome these limitations.
In conclusion, while NordVPN imposes port forwarding restrictions to safeguard its network and prioritize user experience, users can still leverage its robust features for secure and private online activities.
NordVPN port forwarding setup
Port forwarding is a useful feature in VPN services like NordVPN that allows users to enhance their online security and privacy while maintaining optimal internet speeds. Setting up port forwarding with NordVPN is a straightforward process for those looking to optimize their online experience.
To set up port forwarding with NordVPN, start by logging into your NordVPN account and navigating to the settings section. Look for the port forwarding option and enable it to activate the feature. Next, choose a specific port number or allow NordVPN to automatically assign one for you.
Once the port forwarding feature is enabled, you can configure your router to forward incoming internet traffic on a specific port to your device connected to NordVPN. This step is important for users who want to access devices on their home network remotely or maximize their online security by isolating specific applications.
It's essential to note that not all servers support port forwarding, so ensure you connect to a server that offers this feature. NordVPN provides a list of servers that support port forwarding on their website, making it easy for users to choose the right server for their needs.
In conclusion, NordVPN's port forwarding setup is a valuable tool for users looking to improve their online security and control their internet traffic effectively. By following these simple steps, users can enhance their online experience and benefit from the added layer of security that port forwarding provides.
NordVPN port forwarding alternatives
If you're looking to enhance your online security and privacy with NordVPN but facing issues with port forwarding, fear not as there are alternative methods to achieve similar results. Port forwarding is a useful feature that allows incoming connections to bypass the NAT firewall and reach specific devices or services within a private network.
One alternative to NordVPN port forwarding is using a VPN service that offers dedicated IP addresses. With a dedicated IP, you get a unique online identity that can help with port forwarding requirements. Dedicated IPs are not shared among multiple users, so you have more control over your online activities and potential for forwarding specific ports.
Another option is to set up a virtual private server (VPS) with port forwarding capabilities. By hosting your VPN server on a VPS, you can have full control over port forwarding settings and customize them to your needs. This method requires more technical expertise but offers flexibility and control over your network configuration.
Additionally, some VPN providers offer specialized servers optimized for port forwarding. These servers are configured to allow specific ports to remain open, enabling faster and more reliable connections for activities like gaming, torrenting, or accessing remote devices.
In conclusion, if NordVPN's port forwarding feature is not meeting your requirements, consider exploring alternative solutions such as dedicated IP addresses, setting up a VPS, or using VPN providers with specialized port forwarding servers. By experimenting with these alternatives, you can find a method that best suits your needs for a secure and customizable online experience.
0 notes
Text
what vpn works with orbi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what vpn works with orbi
Orbi-compatible VPN services
Orbi-compatible VPN services offer users enhanced privacy and security when surfing the internet through their Orbi router. A VPN, or Virtual Private Network, encrypts users' internet connection and routes it through a remote server, thus masking the user's IP address and online activity.
Orbi routers are known for their fast and reliable Wi-Fi coverage, making them a popular choice among homeowners and businesses. By using a VPN service that is compatible with Orbi routers, users can ensure that all devices connected to the network are protected, regardless of their location.
One of the key benefits of using a VPN service with Orbi routers is the ability to access geo-restricted content and websites. By connecting to a server in a different country, users can bypass censorship and access content that may be blocked in their region.
Additionally, Orbi-compatible VPN services can help prevent unauthorized access to sensitive data and personal information. With cyber threats on the rise, it is essential to safeguard one's online privacy and security, especially when using public Wi-Fi networks.
When choosing a VPN service for Orbi routers, it is important to consider factors such as encryption protocols, server locations, and customer support. By selecting a reputable VPN provider with a strong track record in privacy and security, users can enjoy a seamless and protected online experience with their Orbi router.
In conclusion, Orbi-compatible VPN services offer users an added layer of protection and anonymity when browsing the internet. By encrypting their internet connection and masking their IP address, users can browse the web securely and access content without restrictions.
VPN compatibility with Orbi router
Title: Ensuring VPN Compatibility with Orbi Router: A Comprehensive Guide
In today's interconnected world, safeguarding our online privacy is paramount. Virtual Private Networks (VPNs) offer a robust solution, encrypting internet traffic and providing anonymity. However, ensuring compatibility between VPNs and routers like Orbi is crucial for seamless integration and optimal performance.
Orbi routers, renowned for their high-performance Wi-Fi coverage and advanced features, support VPN usage but may require configuration adjustments for compatibility. Here's how to ensure VPN compatibility with your Orbi router:
Check VPN Protocol Compatibility: Orbi routers typically support VPN protocols like PPTP, L2TP, and IPSec. Before configuring your VPN, ensure it supports one of these protocols for compatibility.
Router Firmware Updates: Keeping your Orbi router's firmware up-to-date is essential for compatibility with the latest VPN technologies and security enhancements. Regularly check for firmware updates through the Orbi app or web interface.
VPN Configuration: Access your Orbi router's settings through a web browser and navigate to the VPN section. Follow the instructions provided by your VPN provider to configure the VPN connection settings accurately.
Port Forwarding: Some VPNs require specific ports to be forwarded for proper operation. Configure port forwarding settings on your Orbi router as per the VPN provider's recommendations to ensure smooth VPN connectivity.
Testing Connectivity: After configuring the VPN settings on your Orbi router, test the connection to ensure proper functionality. Verify that your device's internet traffic is encrypted and routed through the VPN server.
Troubleshooting: In case of connectivity issues or performance degradation, troubleshoot by checking VPN and router settings, ensuring compatibility with Orbi's specifications.
By following these steps, you can effectively ensure VPN compatibility with your Orbi router, enhancing your online privacy and security without compromising on performance. Remember to prioritize security best practices and regularly update both your router and VPN software for optimal protection against cyber threats.
Best VPN options for Orbi network
Title: Enhance Your Orbi Network Security: Top VPN Options
In an era where online privacy and security are paramount, protecting your Orbi network with a reliable VPN (Virtual Private Network) is essential. Orbi, renowned for its robust Wi-Fi coverage and performance, can be further fortified with the right VPN service. Here are some of the best VPN options tailored for Orbi networks:
ExpressVPN: Known for its speed and security features, ExpressVPN offers seamless integration with Orbi networks. Its advanced encryption protocols ensure data privacy, while its wide server network ensures reliable connections. ExpressVPN's user-friendly interface makes it an ideal choice for both beginners and experienced users.
NordVPN: With its double VPN encryption and strict no-log policy, NordVPN is a top contender for Orbi networks. It provides an extra layer of security, safeguarding your Orbi connection from potential threats. NordVPN's compatibility with various devices ensures comprehensive protection for your entire network.
CyberGhost: Optimized for streaming and torrenting, CyberGhost offers specialized servers for uninterrupted Orbi network performance. Its intuitive interface and one-click connect feature make it perfect for Orbi users seeking hassle-free VPN protection. CyberGhost's dedicated support for router installations ensures smooth integration with your Orbi network.
Surfshark: Offering unlimited simultaneous connections, Surfshark is an excellent choice for households with multiple devices connected to the Orbi network. Its CleanWeb feature blocks ads and malware, enhancing the security of your Orbi network. Surfshark's affordability and robust security features make it a compelling option for Orbi users on a budget.
IPVanish: Renowned for its high-speed connections and unlimited bandwidth, IPVanish is tailored for Orbi networks requiring optimal performance. Its SOCKS5 web proxy enhances privacy and anonymity, making it an ideal choice for Orbi users prioritizing both speed and security.
By integrating one of these top VPN options with your Orbi network, you can ensure enhanced privacy, security, and performance for all your online activities. Stay protected and enjoy seamless connectivity with a trusted VPN solution.
Orbi VPN setup guide
Orbi VPN Setup Guide
If you're looking to enhance your online security and privacy, setting up a VPN on your Orbi router can be a wise decision. A Virtual Private Network (VPN) encrypts your internet connection, making it more secure and allowing you to browse the web anonymously. By setting up a VPN on your Orbi router, you can protect all the devices connected to your network, including smartphones, computers, and smart home devices.
To set up a VPN on your Orbi router, you'll first need to choose a VPN service provider that is compatible with Orbi routers. Once you've subscribed to a VPN service, follow these steps to configure the VPN on your Orbi router:
Access your Orbi router's admin panel by typing its IP address into a web browser.
Log in to the admin panel using your username and password.
Locate the VPN section in the router settings.
Enter the VPN server information provided by your VPN service provider, including the server address, username, and password.
Save the changes and activate the VPN connection.
Once the VPN is set up on your Orbi router, all the internet traffic from your connected devices will be encrypted and routed through the VPN server, ensuring your online activities remain private and secure.
Remember to choose a VPN service provider that offers reliable encryption protocols, a wide server network, and excellent customer support. With a VPN set up on your Orbi router, you can enjoy a safer and more private internet browsing experience for all your devices.
VPN troubleshooting for Orbi connection
Title: Troubleshooting VPN Connection Issues with Orbi: A Comprehensive Guide
Virtual Private Networks (VPNs) are essential tools for ensuring online privacy and security. However, setting up and troubleshooting VPN connections with Orbi routers can sometimes be challenging. Here's a guide to help you troubleshoot common VPN issues with your Orbi network.
Check Internet Connection: Before troubleshooting your VPN, ensure that your Orbi router is connected to the internet. Verify that other devices on your network can access the internet without VPN.
Update Firmware: Ensure that your Orbi router's firmware is up-to-date. Outdated firmware can cause compatibility issues with VPN services. Visit the manufacturer's website to download and install the latest firmware version.
Restart Router and Devices: Sometimes, a simple restart can resolve connectivity issues. Turn off your Orbi router, wait for a few minutes, and then power it back on. Also, restart the device you're trying to connect to the VPN.
Check VPN Configuration: Verify that the VPN configuration settings on your Orbi router are correct. Double-check the VPN server address, username, and password. Any discrepancies can prevent a successful connection.
Firewall and Antivirus Settings: Firewalls and antivirus software can sometimes block VPN connections. Temporarily disable any firewall or antivirus software on your device and router, and then attempt to connect to the VPN again.
Try Different VPN Protocols: Orbi routers support various VPN protocols such as OpenVPN and PPTP. Try switching between different protocols to see if one works better than the other.
Contact VPN Support: If you've exhausted all troubleshooting steps and still can't establish a VPN connection, contact your VPN service provider for assistance. They may have specific recommendations or troubleshooting steps tailored to their service.
By following these troubleshooting steps, you can resolve most VPN connection issues with your Orbi router and enjoy a secure and private internet browsing experience.
0 notes
Text
what is policy based vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is policy based vpn
Policy-based VPN definition
A policy-based VPN, also known as route-based VPN, is a method of establishing secure communication between networks or devices based on predefined policies. Unlike a traditional VPN, which typically relies on specific IP addresses and subnets to determine what traffic should be encrypted and sent over the VPN tunnel, a policy-based VPN uses a set of rules or policies to dictate which traffic should be encrypted and transmitted securely.
In a policy-based VPN, administrators configure policies that define which traffic should be encrypted and sent over the VPN tunnel. These policies can be based on various criteria such as source and destination IP addresses, protocols, ports, or even specific applications. For example, an organization may create a policy that encrypts all traffic destined for a particular remote network, ensuring that sensitive data remains secure during transmission.
One of the key advantages of policy-based VPNs is their flexibility and scalability. Since policies are defined based on specific criteria rather than individual IP addresses, it is easier to accommodate changes to the network infrastructure without having to reconfigure VPN settings. This makes policy-based VPNs well-suited for dynamic environments where network topology may change frequently.
Additionally, policy-based VPNs offer granular control over which traffic is encrypted, allowing organizations to prioritize and secure critical data while minimizing bandwidth usage. By selectively encrypting only the necessary traffic, policy-based VPNs can improve network performance and efficiency.
Overall, policy-based VPNs provide a versatile and efficient solution for establishing secure communication between networks or devices while offering granular control and scalability to meet the evolving needs of modern organizations.
Policy-based VPN configuration
Policy-based VPN configuration refers to a method of setting up virtual private networks (VPNs) that relies on predefined rules or policies to determine which network traffic should be encrypted and routed through the VPN tunnel. This approach contrasts with route-based VPN configuration, which uses routing protocols to determine traffic paths.
In a policy-based VPN setup, administrators create policies that specify the criteria for determining which traffic should be encrypted and sent through the VPN tunnel. These policies typically include criteria such as source and destination IP addresses, protocols, ports, and sometimes specific applications or services. Based on these policies, the VPN device or software decides whether to encrypt and forward the traffic through the VPN tunnel or to allow it to travel through the regular network.
One of the primary advantages of policy-based VPN configuration is its flexibility and granular control over traffic routing. Administrators can create multiple policies to handle different types of traffic, allowing them to prioritize critical data or ensure compliance with security policies. Additionally, policy-based VPNs are often easier to configure and manage than route-based VPNs, especially in environments with complex network topologies or diverse traffic requirements.
However, policy-based VPNs can also have limitations, particularly when dealing with large numbers of policies or highly dynamic network environments. Managing and troubleshooting multiple policies can become cumbersome, and scalability may be a concern in some cases.
Overall, policy-based VPN configuration is a powerful tool for organizations seeking to secure their network traffic while maintaining control and flexibility over how data is routed within their network infrastructure. By carefully defining and implementing policies, administrators can ensure that sensitive information remains protected while still allowing for efficient and reliable communication across the network.
Policy-based VPN vs route-based VPN
Policy-based VPN (Virtual Private Network) and route-based VPN are two distinct approaches to establishing secure connections between networks, but they operate in fundamentally different ways.
Policy-based VPN, also known as a "traditional" VPN, relies on specific policies defined by the network administrator to determine which traffic is encrypted and sent through the VPN tunnel. These policies are typically based on criteria such as source and destination IP addresses, protocols, and ports. When traffic matches these predefined policies, it is encrypted and routed through the VPN tunnel to its destination. This approach offers granular control over which traffic is protected, but it can be complex to manage and scale, especially in large networks with numerous policies.
On the other hand, route-based VPN, also referred to as "next-generation" VPN, uses dynamic routing protocols to determine how traffic is routed through the VPN tunnel. Instead of relying on static policies, route-based VPNs establish connections based on the routes configured in the network's routing table. This means that any traffic destined for a remote network is automatically encrypted and sent through the VPN tunnel without the need for explicit policies. Route-based VPNs are often easier to manage and scale, particularly in dynamic environments where network configurations frequently change.
In summary, while both policy-based and route-based VPNs serve the purpose of securing network connections, they differ in their approach to determining which traffic is routed through the VPN tunnel. Policy-based VPNs offer granular control but can be complex to manage, while route-based VPNs offer simplicity and scalability through dynamic routing protocols. The choice between the two depends on the specific requirements and complexity of the network environment.
Policy-based VPN advantages
Policy-based VPN, also known as static routing VPN, offers several advantages for businesses looking to enhance their network security and privacy. This type of VPN configuration allows administrators to define specific rules and criteria for determining which traffic is allowed to pass through the VPN tunnel. By setting up policies based on various factors such as source and destination IP addresses, protocols, and ports, organizations can exercise greater control over their network traffic.
One of the key advantages of policy-based VPN is its flexibility. Administrators can tailor VPN policies to suit their organization's unique needs and security requirements. This level of customization enables businesses to implement granular access controls, ensuring that only authorized users and devices can access sensitive data and resources.
Furthermore, policy-based VPN offers improved scalability compared to route-based VPN solutions. As policies are defined based on specific attributes of network traffic, organizations can easily add or modify rules without disrupting the entire VPN infrastructure. This scalability is particularly beneficial for growing businesses that need to accommodate increasing network traffic and add new services seamlessly.
Additionally, policy-based VPN enhances network performance by optimizing traffic flow through the VPN tunnel. By filtering traffic based on predefined policies, organizations can prioritize critical applications and services, reducing latency and ensuring a consistent user experience.
In conclusion, policy-based VPN provides businesses with the flexibility, scalability, and performance optimization needed to secure their network infrastructure effectively. By leveraging policy-based VPN technology, organizations can strengthen their data protection measures and achieve greater control over their network traffic.
Policy-based VPN limitations
Policy-based VPNs offer a flexible approach to network security by allowing administrators to define access rules based on specific criteria such as IP addresses, protocols, and applications. However, despite their advantages, policy-based VPNs come with certain limitations that organizations need to consider.
One significant limitation of policy-based VPNs is scalability. As the number of policies increases, managing and maintaining them becomes increasingly complex and time-consuming. This can lead to performance issues and may require additional resources to handle the increased workload.
Another limitation is the lack of granularity in controlling access. Policy-based VPNs typically rely on broad rules that apply to entire subsets of traffic. While this simplicity can be advantageous in some scenarios, it also means that organizations have less control over individual connections and may struggle to enforce more nuanced security policies.
Additionally, policy-based VPNs may struggle to adapt to dynamic network environments. Changes in network topology or device configurations can require manual updates to policies, leading to potential errors or delays in implementation. This lack of agility can hinder organizations' ability to respond quickly to evolving security threats.
Furthermore, policy-based VPNs may not provide adequate support for modern applications and protocols. As technologies evolve, traditional policy-based approaches may struggle to keep pace with the complex traffic patterns and encryption requirements of newer applications, potentially leaving organizations vulnerable to exploitation.
In conclusion, while policy-based VPNs offer a straightforward way to enforce network security policies, they also come with limitations that organizations must carefully consider. From scalability and granularity issues to adaptability and support for modern applications, understanding these limitations is essential for making informed decisions about network security architecture.
0 notes
Text
what ports to open for l2tp vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what ports to open for l2tp vpn
Open ports for L2TP VPN
Open ports for L2TP VPN
When setting up a Layer 2 Tunneling Protocol (L2TP) Virtual Private Network (VPN), it is crucial to open specific ports to ensure proper functionality and secure communication. L2TP is a popular VPN protocol that provides a high level of security through encryption and tunneling. To establish a successful L2TP VPN connection, certain ports need to be open on the network firewall or router.
The two main protocols used by L2TP are UDP (User Datagram Protocol) and IPsec (Internet Protocol Security). To allow L2TP VPN traffic to pass through the network, UDP ports 500 and 4500 must be open on the firewall or router. UDP port 500 is used for the Internet Key Exchange (IKE) protocol, which negotiates the IPsec security association, while UDP port 4500 is used for Network Address Translation Traversal (NAT-T) to handle devices behind NAT routers.
In addition to UDP ports, IP protocol number 50 (ESP - Encapsulating Security Payload) used by IPsec must be allowed through the network firewall or router. This protocol is responsible for encrypting the data traffic in the VPN tunnel, ensuring confidentiality and integrity.
By opening UDP ports 500 and 4500, as well as allowing IP protocol 50, administrators can ensure smooth and secure transmission of data across the network when using L2TP VPN connections. It is important to configure the network devices properly to permit these specific ports and protocols to avoid any connectivity issues with the L2TP VPN setup.
L2TP VPN port requirements
L2TP (Layer 2 Tunneling Protocol) VPNs are a popular choice for secure communication over the internet, offering a robust and reliable solution for remote access and site-to-site connections. Understanding the port requirements for L2TP VPNs is essential for configuring firewalls, routers, and other networking devices to allow proper traffic flow.
L2TP VPNs use a combination of UDP (User Datagram Protocol) ports and IP protocol 50 (Encapsulating Security Payload or ESP) to facilitate communication between client and server. The primary ports used by L2TP VPNs are:
UDP port 1701: This port is used for establishing the initial connection between the client and the VPN server. It is responsible for negotiating the tunnel and encapsulating the PPP (Point-to-Point Protocol) packets within IP packets for transmission over the internet.
IP protocol 50 (ESP): In addition to UDP port 1701, L2TP VPNs require IP protocol 50 for secure data transmission. ESP provides encryption, authentication, and integrity checking for the data packets flowing through the VPN tunnel, ensuring confidentiality and data integrity.
When configuring firewalls or network devices to allow L2TP VPN traffic, it is essential to open UDP port 1701 and allow IP protocol 50 (ESP) to pass through. Without proper configuration, VPN connections may fail or experience connectivity issues.
It's worth noting that some network environments may require additional ports or protocols to be opened, depending on specific configurations or security policies. Additionally, network address translation (NAT) traversal techniques may be employed to allow L2TP VPN traffic to traverse NAT devices without interference.
In conclusion, understanding the port requirements for L2TP VPNs is crucial for ensuring smooth and secure communication between clients and servers. By opening UDP port 1701 and allowing IP protocol 50 (ESP) traffic, organizations can establish reliable L2TP VPN connections while maintaining robust security measures.
Configuring port forwarding for L2TP VPN
Configuring port forwarding for L2TP VPN is essential for ensuring seamless connectivity and secure access to your network resources remotely. L2TP (Layer 2 Tunneling Protocol) VPN is a popular choice for establishing secure connections between remote users and a private network, offering robust encryption and authentication mechanisms. However, to enable L2TP VPN access from outside the network, port forwarding must be properly configured on the router or firewall.
Port forwarding involves redirecting network traffic from a specific port on the router's external interface to a corresponding port on an internal server or device running the VPN server software. For L2TP VPN, port 1701 must be forwarded to the internal IP address of the server hosting the VPN service.
To configure port forwarding for L2TP VPN, follow these steps:
Access your router's administration interface using a web browser and log in with administrative credentials.
Locate the port forwarding or virtual server configuration section. This may be found under the NAT (Network Address Translation) or firewall settings.
Create a new port forwarding rule. Specify the service as L2TP VPN or custom, and enter 1701 as both the external and internal port.
Enter the internal IP address of the server hosting the L2TP VPN service as the destination.
Save the changes and apply the configuration.
Optionally, configure firewall rules to allow L2TP VPN traffic to reach the internal server.
Test the L2TP VPN connection from an external network to ensure that port forwarding is functioning correctly.
By properly configuring port forwarding for L2TP VPN, you enable remote users to securely connect to your network and access resources as if they were locally connected, enhancing productivity and flexibility while maintaining stringent security measures. Always ensure that port forwarding rules are implemented securely to mitigate potential risks associated with exposing network services to the internet.
Secure L2TP VPN port settings
Setting up a Layer 2 Tunneling Protocol (L2TP) VPN can provide an extra layer of security for your online activities. However, ensuring the proper configuration of L2TP VPN port settings is crucial to maximize security and maintain smooth functionality.
One fundamental aspect of securing L2TP VPN port settings is selecting the appropriate ports for communication. By default, L2TP uses UDP port 1701 for both control and data traffic. However, for enhanced security, it's advisable to restrict access to this port to authorized users or devices only. This can be achieved through firewall rules or network access control mechanisms.
Additionally, implementing IPsec (Internet Protocol Security) alongside L2TP can significantly bolster security. IPsec adds encryption and authentication to the VPN connection, making it more resistant to eavesdropping and tampering. When configuring IPsec, ensure that it's properly integrated with L2TP and that both protocols are using secure algorithms and key exchange methods.
Another important consideration is the use of strong authentication mechanisms, such as pre-shared keys (PSK) or digital certificates. These mechanisms help verify the identity of both the client and server, preventing unauthorized access to the VPN.
Furthermore, regular monitoring and updates are essential for maintaining the security of L2TP VPN port settings. Keep an eye on network traffic patterns and security logs to detect any suspicious activities or attempted breaches. Additionally, stay informed about security vulnerabilities and patches related to L2TP and IPsec implementations, and promptly apply updates to mitigate potential risks.
In conclusion, securing L2TP VPN port settings involves selecting appropriate ports, implementing IPsec, employing strong authentication mechanisms, and maintaining vigilance through monitoring and updates. By following these best practices, you can enhance the security of your L2TP VPN and protect your online privacy and data.
Recommended ports for L2TP VPN
When setting up an L2TP (Layer 2 Tunneling Protocol) VPN (Virtual Private Network), choosing the right ports is crucial for ensuring smooth and secure communication between the client and the server. L2TP VPNs are widely used for providing a secure connection over the internet, especially in scenarios where data privacy and confidentiality are paramount, such as in the corporate environment or for remote access to sensitive information.
The recommended ports for L2TP VPN vary depending on the specific requirements and configurations of the network infrastructure. However, there are some commonly used ports that are generally recommended for optimal performance and compatibility.
The primary port used for establishing the L2TP tunnel is UDP (User Datagram Protocol) port 1701. This port is designated for carrying the L2TP data packets and is essential for initiating the VPN connection between the client and the server. It is important to ensure that UDP port 1701 is open and accessible on both the client and server sides to facilitate the establishment of the VPN tunnel.
In addition to UDP port 1701, L2TP VPNs may also utilize other ports for ancillary functions such as authentication and encryption. For example, UDP ports 500 and 4500 are commonly used for IKE (Internet Key Exchange) and NAT-T (Network Address Translation Traversal), which are protocols often employed in conjunction with L2TP for secure key exchange and traversal of NAT devices, respectively.
Furthermore, L2TP VPNs may also utilize IP protocol 50 (ESP - Encapsulating Security Payload) for data encryption and IP protocol 51 (AH - Authentication Header) for data authentication. These protocols operate at the network layer and are essential for ensuring the confidentiality and integrity of the data transmitted over the VPN tunnel.
In conclusion, when configuring an L2TP VPN, it is advisable to ensure that UDP port 1701 is open and accessible, along with any additional ports or protocols required for authentication, encryption, and NAT traversal, to ensure seamless and secure communication between the client and the server.
0 notes
Text
what is vpn port
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is vpn port
VPN protocol
A Virtual Private Network (VPN) protocol is a set of instructions that ensures secure and encrypted communication between devices over the internet. There are several types of VPN protocols, each offering different levels of security and speed. Understanding the different protocols can help users choose the best option for their specific needs.
One of the most common VPN protocols is the OpenVPN protocol, known for its open-source nature and strong security features. It is highly customizable and can run on various platforms, making it a popular choice for both individuals and businesses. Another widely used protocol is the Secure Socket Tunneling Protocol (SSTP), which is developed by Microsoft and offers high levels of security, especially on Windows operating systems.
Internet Key Exchange version 2 (IKEv2) is another VPN protocol known for its speed and stability. It is often used in mobile devices due to its ability to quickly reconnect to the VPN server when switching between different networks. Users looking for a protocol that prioritizes speed may opt for the Point-to-Point Tunneling Protocol (PPTP), although it is considered less secure compared to other protocols.
Overall, choosing the right VPN protocol depends on factors such as security requirements, device compatibility, and speed preferences. It is essential to research and understand the various protocols available to make an informed decision that best suits individual needs for maintaining privacy and security while browsing the internet.
Port forwarding
Port forwarding is a networking technique used to allow external devices or users to access resources on a private network. By forwarding specific network ports from the router to a device on the local network, incoming traffic can be directed to the appropriate destination.
When a device on the local network initiates a request to communicate with a server on the internet, the response from the server typically needs to be routed back to the requesting device. Port forwarding helps facilitate this communication by mapping the incoming port number of the router to the specific internal IP address and port number of the target device.
Port forwarding is commonly used for various applications such as online gaming, remote desktop access, IP camera viewing, and file sharing. For example, to host a multiplayer game server on a local machine, port forwarding is essential to allow external players to connect to the server.
Setting up port forwarding involves accessing the router's configuration settings through a web interface and defining the specific port forwarding rules. It is important to choose unique port numbers to avoid conflicts with other services running on the network.
While port forwarding can enhance accessibility and convenience, it also poses security risks if not configured properly. Opening ports without adequate protection can expose the network to potential threats and unauthorized access. It is crucial to regularly review and update port forwarding rules to ensure optimal security measures are in place.
In conclusion, port forwarding is a valuable networking tool that enables seamless communication between devices on a private network and external sources. By understanding how to implement and secure port forwarding correctly, users can enjoy enhanced connectivity while safeguarding their network from potential vulnerabilities.
Network security
Network security plays a crucial role in safeguarding the integrity, confidentiality, and availability of data transmitted across computer networks. It is a fundamental aspect of any organization's IT infrastructure, as cyber threats continue to evolve and become more sophisticated.
One of the key components of network security is the implementation of firewalls, which act as a barrier between a trusted internal network and untrusted external networks. Firewalls help prevent unauthorized access to the network and filter out potentially harmful traffic. Intrusion detection systems (IDS) and intrusion prevention systems (IPS) are also essential tools that help identify and respond to potential security breaches in real time.
Encryption is another critical aspect of network security, as it helps protect data in transit from being intercepted or tampered with by unauthorized parties. By encrypting data, organizations can ensure that sensitive information remains confidential and secure as it travels across the network.
Regular security audits and penetration testing are vital for identifying vulnerabilities within a network and addressing them before they can be exploited by malicious actors. Additionally, employee training and awareness programs can help minimize the risk of insider threats and ensure that staff members understand their role in maintaining network security.
In conclusion, network security is a multifaceted discipline that requires a comprehensive approach to ensure the protection of sensitive data and resources. By implementing robust security measures and staying vigilant against emerging threats, organizations can mitigate risks and safeguard their network infrastructure from potential cyber attacks.
Data encryption
Data encryption is a vital component of modern digital security protocols, safeguarding sensitive information from unauthorized access. It involves the conversion of plaintext data into ciphertext using algorithms, rendering it unreadable without the appropriate decryption key.
The primary purpose of data encryption is to ensure confidentiality, preventing unauthorized parties from intercepting and understanding the content of encrypted messages or files. This is particularly crucial in sectors such as finance, healthcare, and government, where the protection of sensitive data is paramount.
There are two main types of encryption: symmetric and asymmetric. Symmetric encryption uses a single key for both encryption and decryption, making it faster and more efficient for large volumes of data. However, the challenge lies in securely sharing the key between the sender and receiver.
Asymmetric encryption, on the other hand, employs a pair of keys: a public key for encryption and a private key for decryption. This method eliminates the need for key exchange but is generally slower and more resource-intensive.
Data encryption algorithms vary in complexity and strength, with some older algorithms becoming susceptible to cryptographic attacks over time. Therefore, it's essential to use robust encryption standards and regularly update cryptographic protocols to stay ahead of potential threats.
In addition to protecting data during transmission, encryption also plays a crucial role in securing stored data. By encrypting files or entire storage devices, organizations can mitigate the risk of data breaches and unauthorized access, even if physical hardware is compromised.
Overall, data encryption is a fundamental tool in the ongoing battle against cyber threats, providing a layer of defense that helps safeguard sensitive information in an increasingly digital world.
Tunneling protocol
Tunneling Protocol: A Comprehensive Guide
Tunneling protocols are essential components of modern networking, facilitating secure and efficient communication over diverse networks. In essence, tunneling encapsulates data packets within other packets, enabling them to traverse networks that may not natively support the original protocol. This process effectively creates a virtual tunnel through which data can travel safely and securely.
One of the most widely used tunneling protocols is the Point-to-Point Tunneling Protocol (PPTP). Initially developed by Microsoft, PPTP facilitates the creation of virtual private networks (VPNs) over the internet. By encapsulating data packets within IP packets, PPTP enables remote users to securely access private networks over public infrastructure.
Another prominent tunneling protocol is the Layer 2 Tunneling Protocol (L2TP), which combines the best features of PPTP and Cisco's Layer 2 Forwarding (L2F) protocol. L2TP operates at the data-link layer of the OSI model and is often used in conjunction with IPsec to provide enhanced security for VPN connections.
Secure Shell (SSH) tunneling is another notable technique used to create encrypted tunnels for secure communication. SSH tunneling encrypts data traffic between a client and a server, preventing eavesdropping and tampering by malicious actors.
Additionally, Internet Protocol Security (IPsec) serves as a suite of protocols for securing internet communications at the IP layer. IPsec can be used to establish secure tunnels between networks or individual devices, ensuring confidentiality, integrity, and authenticity of data transmission.
Overall, tunneling protocols play a crucial role in modern networking by enabling secure and efficient communication across diverse networks. Whether for remote access, VPNs, or secure data transmission, understanding and implementing tunneling protocols is essential for maintaining the integrity and security of network communications.
0 notes
Text
“Cybersecure RDP Access: How RHosting Protects Your Windows Server”
Remote access is essential in today’s digital workplace — but with increasing cyber threats, traditional RDP setups can leave your Windows servers vulnerable. Unsecured ports, weak credentials, and misconfigured firewalls are all it takes for attackers to breach your system.
That’s why RHosting was built with security at its core. Our next-gen RDP platform doesn’t just simplify remote access — it fortifies it.
Here’s how RHosting delivers cybersecure remote desktop access while giving you complete control and peace of mind.

🔒 1. Encrypted End-to-End Connections
RHosting uses industry-standard encryption protocols to ensure all data passed between users and servers is protected. Whether you're accessing your server from a laptop, tablet, or mobile device, your session is encrypted — safeguarding sensitive data from interception.
AES 256-bit encryption
Secure TLS tunnels
SSL certificate-based authentication
🧑💻 2. Multi-Factor Authentication (MFA)
A strong password isn’t enough. RHosting supports multi-factor authentication (MFA) to ensure that only authorized users gain access to your servers — even if login credentials are compromised.
OTP-based authentication
Email or app-based second-factor verification
Optional device-based access restrictions
🛡️ 3. IP Whitelisting & Geo-Fencing
With RHosting, you can restrict access to trusted IPs or geographic regions, reducing exposure to brute-force attacks and unauthorized logins from high-risk areas.
Only allow access from verified networks
Instantly block unrecognized locations
Customize rules per user or server
🧯 4. Intrusion Detection & Real-Time Alerts
We monitor every login attempt and system action to identify suspicious activity. If something seems off, you’re notified immediately — allowing your IT team to act before threats escalate.
Real-time login tracking
Automated anomaly detection
Immediate alerts for failed access attempts
🔧 5. Role-Based Access Controls (RBAC)
Control who sees what. RHosting provides granular access controls, so users only access what they need — nothing more.
Separate access for dev, finance, admin, etc.
Temporary access permissions for vendors or support
Full audit logs for compliance and accountability
📉 6. No Open Ports, No VPN Vulnerabilities
Traditional RDP requires exposing port 3389 or using complex VPN setups — both common targets for cyberattacks. With RHosting, you don’t need open ports or VPNs. Your servers stay isolated, yet fully accessible through our secure cloud interface.
No port forwarding
No static IP requirements
Fully managed and cloud-secured
✅ Conclusion: Security Without Complexity
With RHosting, you don’t have to choose between convenience and cybersecurity. Our platform delivers seamless, high-performance RDP access that’s built on strong security principles — helping you protect what matters most: your data, your servers, and your business.
Secure your remote access with confidence. Choose RHosting.
0 notes
Text
what is tcp vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is tcp vpn
TCP VPN definition
TCP VPN, short for Transmission Control Protocol Virtual Private Network, is a secure method of connecting to a private network remotely over the internet. It employs the TCP protocol, a foundational component of internet communication, to ensure reliable and secure data transmission between the user and the private network.
Unlike traditional VPN protocols such as OpenVPN or IPSec, which may use UDP (User Datagram Protocol) for data transmission, TCP VPN operates exclusively on TCP. This choice offers several advantages, particularly in environments where network reliability and stability are paramount.
One of the primary benefits of TCP VPN is its ability to handle network congestion and packet loss more effectively. TCP's built-in mechanisms for error correction and retransmission ensure that data reaches its destination intact, even if it encounters obstacles along the way. This makes TCP VPN ideal for use in networks prone to congestion or high latency, such as public Wi-Fi hotspots or cellular networks.
Moreover, TCP VPNs are known for their compatibility with a wide range of network configurations and devices. Since TCP is a fundamental protocol of the internet, TCP VPN connections can traverse firewalls and network address translation (NAT) devices more seamlessly than other VPN protocols. This allows users to establish secure connections from virtually any location, without the need for complex network configurations or port forwarding.
In summary, TCP VPN provides a reliable and secure method for users to access private networks over the internet. By leveraging the TCP protocol's robustness and compatibility, TCP VPNs offer a versatile solution for businesses and individuals seeking to safeguard their online communications and data privacy.
Comparing TCP and UDP VPN
When it comes to selecting the right VPN protocol for your needs, understanding the differences between TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) is crucial. Both protocols offer unique advantages and disadvantages, making them suitable for different scenarios.
TCP VPN establishes a reliable and connection-oriented communication between the client and server. It ensures that data packets are delivered in the correct order and without errors. This reliability makes TCP ideal for applications where data integrity is paramount, such as file transfers and web browsing. However, TCP's reliance on acknowledgments for packet delivery can result in slower performance, especially over long distances or in networks with high latency.
On the other hand, UDP VPN provides a connectionless and lightweight protocol, making it faster and more efficient for certain types of traffic. UDP does not guarantee packet delivery or order, which makes it suitable for real-time applications like streaming media and online gaming, where speed is prioritized over reliability. However, UDP's lack of error checking means that data packets can be lost or arrive out of order, leading to potential issues with data consistency.
In summary, TCP VPN is best suited for applications requiring reliable and error-free data transmission, while UDP VPN is preferable for scenarios where speed and efficiency are prioritized over reliability. Ultimately, the choice between TCP and UDP VPN depends on your specific use case and requirements.
Advantages of using TCP VPN
A TCP VPN, or Transmission Control Protocol Virtual Private Network, offers numerous advantages for users looking to enhance their online privacy and security. TCP VPN ensures a secure connection by using the TCP protocol, which breaks data into packets and reassembles them at the destination, ensuring reliable and error-free transmission.
One of the primary advantages of using TCP VPN is enhanced security. By encrypting data traffic between the user's device and the VPN server, TCP VPNs protect sensitive information from potential cyber threats such as hacking, data breaches, and surveillance. This encryption is particularly beneficial when connecting to public Wi-Fi networks, which are often insecure and vulnerable to malicious attacks.
Moreover, TCP VPNs provide users with anonymity and privacy online. By masking their IP address and routing their internet traffic through remote servers, users can browse the web anonymously without revealing their location or identity. This feature is especially vital for individuals looking to bypass geo-restrictions and access content that may be blocked in their region.
Additionally, TCP VPNs offer increased reliability and stability compared to other VPN protocols. The TCP protocol's error-checking and retransmission capabilities ensure that data packets arrive at their destination accurately and in the correct order, minimizing connection disruptions and packet loss.
In conclusion, the advantages of using a TCP VPN are clear: enhanced security, privacy, anonymity, reliability, and stability. Whether you're looking to protect your online activities from prying eyes or access restricted content, a TCP VPN is a valuable tool that can significantly improve your online experience while ensuring your data remains secure and protected.
Disadvantages of TCP VPN
While TCP (Transmission Control Protocol) VPNs offer a secure way to connect to remote networks over the internet, they also come with several disadvantages that users should be aware of.
Speed Reduction: One of the primary drawbacks of TCP VPNs is the potential for speed reduction. Because TCP is designed to ensure reliable data transmission by retransmitting lost packets, this can introduce latency, especially over long-distance connections or when dealing with network congestion. As a result, users may experience slower internet speeds compared to when they're not using a VPN.
Limited Performance for Real-Time Applications: TCP VPNs may not be suitable for real-time applications such as online gaming or VoIP (Voice over Internet Protocol) calls. The retransmission of lost packets can lead to delays and jitter, impacting the user experience during these activities.
Susceptibility to TCP Congestion Control: TCP VPNs are subject to TCP congestion control mechanisms, which can further contribute to performance issues during periods of network congestion. This can lead to reduced throughput and increased latency, particularly in situations where multiple TCP connections are competing for bandwidth.
Higher Overhead: TCP VPNs typically have higher overhead compared to UDP (User Datagram Protocol) VPNs due to the additional mechanisms for error detection, retransmission, and flow control. This can result in increased bandwidth usage and slower performance, particularly on networks with limited bandwidth or high latency.
Difficulty in Bypassing Firewalls: TCP VPNs can be more easily detected and blocked by firewalls compared to UDP VPNs. This is because TCP traffic follows predictable patterns, making it easier for firewalls to identify and filter VPN traffic, especially in countries with strict censorship policies.
In conclusion, while TCP VPNs offer security and reliability, users should be mindful of their limitations, particularly in terms of speed, performance for real-time applications, susceptibility to congestion, overhead, and firewall detection. Depending on their specific needs and priorities, users may need to weigh these disadvantages against the benefits of using a TCP VPN.
Best practices for setting up TCP VPN
Setting up a TCP VPN, or Virtual Private Network, involves ensuring a secure and reliable connection for transmitting data over the internet. TCP (Transmission Control Protocol) VPNs are known for their reliability and ability to handle data delivery efficiently. Here are some best practices to consider when setting up a TCP VPN:
Choose a Reliable Provider: Select a reputable VPN service provider known for their robust TCP VPN offerings. Look for providers with strong encryption protocols, reliable servers, and a good track record for uptime.
Strong Encryption: Utilize strong encryption protocols such as AES (Advanced Encryption Standard) to secure data transmission over the VPN. Encryption ensures that data remains confidential and protected from unauthorized access.
Secure Authentication: Implement secure authentication methods, such as username and password combinations or more advanced authentication mechanisms like two-factor authentication (2FA). This helps ensure that only authorized users can access the VPN.
Regular Updates and Maintenance: Keep the VPN software and firmware up to date to address any security vulnerabilities and ensure optimal performance. Regular maintenance helps prevent security breaches and improves overall reliability.
Network Segmentation: Segment the network to restrict access based on user roles and permissions. This helps minimize the risk of unauthorized access to sensitive data and resources.
Monitor Traffic: Monitor VPN traffic regularly to detect any unusual or suspicious activity. Implement logging and auditing mechanisms to track user activity and identify potential security threats.
Bandwidth Management: Implement bandwidth management policies to prioritize critical traffic and ensure optimal performance for all users. This helps prevent congestion and ensures a smooth VPN experience for all users.
User Training and Awareness: Provide comprehensive training and awareness programs for VPN users to educate them about security best practices and how to use the VPN securely. This helps mitigate the risk of human error and strengthens overall security posture.
By following these best practices, organizations can set up a TCP VPN that provides secure, reliable, and efficient connectivity for their users while safeguarding sensitive data and resources.
0 notes
Photo

TP-Link Archer AX20 AX1800 Dual Band Wifi 6 Router FEATURES: Dual-Band Wi-Fi 6: Equipped with the latest wireless technology, Wi-Fi 6, for faster speeds, greater capacity, and reduced network congestion Next-Gen 1.8Gbps Speeds: Enjoy smooth streaming, downloading, and gaming all without buffering with Wi-Fi speeds of 1.8Gbps Connect More Devices: Wi-Fi 6 technology communicates more data to more devices using revolutionary OFDMA technology while simultaneously reducing lag Quad-Core Processing: The 1.5GHz quad-core CPU ensures communications between your router and all connected devices are smooth Extensive Coverage: Beamforming, independent FEM, and four antennas combine to deliver focused reception to devices far away Increased Battery Life: Target Wake Time technology reduces your devices’ power consumption to extend their battery life USB Easy Sharing: A USB 2.0 Port enables easy file sharing within your network or building private Cloud Storage Easy Setup: Set up your router in minutes with the powerful TP-Link Tether App Backward Compatible: Supports all previous 802.11 standards and all Wi-Fi devices WIRELESS Standards Wi-Fi 6 IEEE 802.11ax/ac/n/a 5 GHz IEEE 802.11ax/n/b/g 2.4 GHz WiFi Speeds AX1800 5 GHz: 1201 Mbps (802.11ax) 2.4 GHz: 574 Mbps (802.11ax) WiFi Range 3 Bedroom Houses 4× Fixed High-Performance Antennas Multiple antennas form a signal-boosting array to cover more directions and large areas Beamforming Concentrates wireless signal strength towards clients to expand WiFi range High-Power FEM Improves transmission power to strengthen signal coverage WiFi Capacity High Dual-Band Allocate devices to different bands for optimal performance OFDMA Simultaneously communicates with multiple Wi-Fi 6 clients Airtime Fairness Improves network efficiency by limiting excessive occupation 4 Streams Connect your devices to more bandwidth Working Modes Router Mode Access Point Mode HARDWARE Processor 1.5 GHz Quad-Core CPU Ethernet Ports 1× Gigabit WAN Port 4× Gigabit LAN Ports USB Support 1× USB 2.0 Port Supported Partition Formats: NTFS, exFAT, HFS+, FAT32 Supported Functions: Apple Time Machine FTP Server Media Server Samba Server Buttons WPS/Wi-Fi Button Power On/Off Button LED On/Off Button Reset Button Power 12 V ⎓ 1.5 A SECURITY WiFi Encryption WPA WPA2 WPA3 WPA/WPA2-Enterprise (802.1x) Network Security SPI Firewall Access Control IP & MAC Binding Application Layer Gateway Guest Network 1× 5 GHz Guest Network 1× 2.4 GHz Guest Network VPN Server OpenVPN PPTP SOFTWARE Protocols IPv4 IPv6 Parental Controls URL Filtering Time Controls WAN Types Dynamic IP Static IP PPPoE PPTP L2TP Quality of Service QoS by Device Cloud Service Auto Firmware Upgrade OTA Firmware Upgrade TP-Link ID DDNS NAT Forwarding Port Forwarding Port Triggering DMZ UPnP IPTV IGMP Proxy IGMP Snooping Bridge Tag VLAN DHCP Address Reservation DHCP Client List Server DDNS TP-Link NO-IP DynDNS Management Tether App Webpage PHYSICAL Dimensions (W×D×H) 10.2 × 5.3 ×1.5 in (260.2 × 135.0 × 38.6 mm) Package Contents Wi-Fi Router Archer AX20 Power Adapter RJ45 Ethernet Cable Quick Installation Guide OTHER System Requirements Internet Explorer 11+, Firefox 12.0+, Chrome 20.0+, Safari 4.0+, or other JavaScript-enabled browser Cable or DSL Modem (if needed) Subscription with an internet service provider (for internet access) Certifications FCC, CE, RoHS Environment Operating Temperature: 0℃~40℃ (32℉ ~104℉) Storage Temperature: -40℃~70℃ (-40℉ ~158℉) Operating Humidity: 10%~90% non-condensing Storage Humidity: 5%~90% non-condensing TEST DATA WiFi Transmission Power CE:
0 notes
Text
does vpn affect oarsec
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn affect oarsec
VPN and Parsec compatibility
VPN and Parsec Compatibility
Virtual Private Networks (VPNs) are widely used tools to enhance online privacy and security. They encrypt internet traffic and mask IP addresses, making it difficult for third parties to track users' online activities. However, one common concern among VPN users is the compatibility of VPNs with various applications and services, including Parsec.
Parsec is a popular remote desktop application that allows users to stream games and other software from one device to another. Many gamers and professionals use Parsec to access powerful hardware remotely or to play graphics-intensive games on less powerful devices. When it comes to using Parsec with a VPN, compatibility may vary depending on the VPN service provider and its settings.
In general, VPNs should be compatible with Parsec since both operate at the network level without interfering with specific applications. However, certain VPN configurations, such as strict firewall rules or limited port forwarding capabilities, may affect Parsec's performance. Users experiencing connectivity issues while using Parsec with a VPN should consider adjusting their VPN settings or choosing a VPN provider that offers better compatibility with Parsec.
It is essential to note that using a VPN could potentially introduce latency and impact streaming quality when using Parsec. Users are advised to connect to VPN servers that are geographically closer to their physical location to minimize latency. Additionally, opting for VPN protocols with lower encryption overhead, such as WireGuard, may also improve performance when using Parsec.
In conclusion, VPN and Parsec can be compatible, but users may need to fine-tune their VPN settings to ensure optimal performance. By understanding the potential challenges and implementing necessary adjustments, users can enjoy a secure and seamless remote desktop experience with Parsec while using a VPN for enhanced privacy and security.
Impact of VPN on Parsec performance
A Virtual Private Network (VPN) is a popular tool used by individuals and businesses to enhance their online security and privacy by masking their IP address and encrypting their internet connection. While VPNs offer a range of benefits, such as increased privacy and security, their use can sometimes impact the performance of certain applications, including Parsec.
Parsec is a cloud-based gaming platform that allows users to remotely access and play their favorite games on different devices. The performance of Parsec heavily relies on the quality of the internet connection between the user's device and the cloud server hosting the game. When a VPN is used, it can introduce additional latency and reduce the overall speed of the internet connection, which in turn can affect the performance of Parsec.
The impact of a VPN on Parsec performance can vary depending on several factors, such as the location of the VPN server, the quality of the VPN service, and the overall internet speed. Users may experience slower response times, increased input lag, and lower video quality when using Parsec over a VPN connection.
To mitigate the impact of a VPN on Parsec performance, users can try connecting to VPN servers that are geographically closer to the Parsec servers, choose VPN services that offer faster speed and lower latency, or consider temporarily disabling the VPN when using Parsec for gaming.
In conclusion, while VPNs are essential for enhancing online security and privacy, they can potentially impact the performance of Parsec and other real-time applications. Users should carefully consider the trade-offs between security and performance when using a VPN with Parsec.
Parsec connection with VPN
Title: Maximizing Efficiency: Understanding Parsec Connection with VPN
In today's digital landscape, remote work and online gaming have become integral parts of many people's lives. Parsec, a remote desktop application primarily used for gaming, has gained popularity for its low-latency, high-quality streaming capabilities. However, some users may wonder about the compatibility and benefits of using Parsec in conjunction with a Virtual Private Network (VPN).
Parsec relies heavily on a stable internet connection to deliver seamless gameplay experiences. While VPNs are commonly used to enhance online privacy and security, they can also impact internet speeds and latency due to the encryption and rerouting of network traffic. Therefore, the decision to use Parsec with a VPN requires careful consideration.
One of the main advantages of using Parsec with a VPN is enhanced security. By encrypting network traffic, VPNs can protect users' data from potential threats such as hacking or surveillance. This is particularly important for gamers who may be concerned about their personal information or gaming accounts being compromised.
Additionally, using a VPN with Parsec can bypass network restrictions and geolocation blocks. This allows users to access Parsec from regions where it may be restricted or blocked, enabling seamless gaming experiences regardless of location.
However, it's essential to note that using a VPN with Parsec may introduce additional latency and decrease overall network performance. This can result in higher input lag and reduced stream quality, impacting the gaming experience. Therefore, users should carefully evaluate their priorities and consider whether the benefits of using a VPN outweigh the potential drawbacks for their specific use case.
In conclusion, while using Parsec with a VPN can enhance security and bypass network restrictions, it may also impact latency and overall performance. Users should weigh the pros and cons carefully to determine the best approach for their individual needs.
VPN influence on Parsec gaming
Title: The Impact of VPNs on Parsec Gaming: A Comprehensive Analysis
Parsec gaming has revolutionized the way gamers interact and play with each other, offering low-latency, high-quality streaming of games over the internet. However, the use of Virtual Private Networks (VPNs) can introduce complexities and potential performance issues to this experience. Let's delve into the influence of VPNs on Parsec gaming.
VPNs are commonly used to enhance online privacy and security by encrypting internet connections and masking users' IP addresses. While this is beneficial for many online activities, it can interfere with Parsec gaming due to the additional layer of encryption and routing.
One of the primary concerns when using a VPN for Parsec gaming is latency. VPNs reroute internet traffic through remote servers, which can increase the distance data packets travel and result in higher latency. In gaming, especially for fast-paced and competitive titles, low latency is crucial for responsiveness and smooth gameplay. Therefore, gamers using VPNs may experience lags, delays, and overall degraded performance on Parsec.
Furthermore, VPNs may also encounter compatibility issues with Parsec's streaming technology. Some VPN services may restrict or throttle certain types of traffic, including the data packets used for game streaming. This can lead to packet loss, decreased image quality, and audio stuttering during gameplay sessions.
However, not all VPNs are created equal, and some premium providers offer optimized servers specifically designed for gaming. These servers prioritize low latency and high bandwidth, aiming to deliver an optimal gaming experience even when using a VPN.
In conclusion, while VPNs are essential for privacy and security online, their influence on Parsec gaming can be mixed. Gamers should carefully consider their VPN provider, server locations, and settings to minimize latency and ensure a smooth gaming experience while using Parsec.
Parsec and VPN interference
Title: Understanding the Interference Between Parsec and VPN
Parsec, a revolutionary tool for remote gaming and collaboration, has garnered widespread acclaim for its ability to enable seamless gaming experiences across vast distances. However, users may encounter challenges when attempting to use Parsec in conjunction with a Virtual Private Network (VPN).
A VPN serves to encrypt internet traffic, ensuring privacy and security by routing it through a secure server. While VPNs are indispensable for safeguarding sensitive data, they can inadvertently interfere with the functionality of Parsec.
One common issue is latency. VPNs introduce additional routing and encryption processes, which can lead to increased latency or ping times. For Parsec users, this can result in laggy gameplay and diminished performance, detracting from the immersive experience that Parsec aims to provide.
Moreover, VPNs may inadvertently block the necessary ports and protocols that Parsec relies on to establish connections between users. This can manifest as connection failures or the inability to connect altogether.
Another concern is bandwidth throttling. Some VPN providers impose bandwidth limitations or prioritize certain types of traffic, potentially restricting the data throughput required for smooth Parsec sessions.
To mitigate these issues, users can consider several strategies. Firstly, they can try connecting to Parsec without using a VPN, provided that it aligns with their privacy and security requirements. Alternatively, users can experiment with different VPN providers or configurations to find one that minimizes interference with Parsec.
Furthermore, optimizing network settings, such as prioritizing Parsec traffic or adjusting VPN parameters, may help alleviate latency and connection issues.
In conclusion, while VPNs are invaluable for securing online activities, their use alongside Parsec can introduce complexities and potential obstacles. By understanding the nature of this interference and implementing appropriate solutions, users can enjoy smoother Parsec experiences without compromising on security.
0 notes